PayFlex FTP - Wired Commute
|
|
|
- Noah Lane
- 10 years ago
- Views:
Transcription
1 PayFlex FTP - Wired Commute What is FTP? FTP stands for File Transfer Protocol. PayFlex uses FTP to send and receive files from our clients. We do so through a secure website that uses PGP encryption to protect the data that is being transmitted to and from the website. What is PGP? PGP stands for Pretty Good Privacy. Pretty Good Privacy (PGP) is a popular software program that uses powerful new technology called "public key" cryptography to encrypt and decrypt files to send over the Internet. PGP is the most widely used privacy-ensuring program by individuals and is also used by many corporations. Developed by Philip R. Zimmermann in 1991, PGP has become a de facto standard for security. PGP can also be used to encrypt files being stored so that they are unreadable by other users or intruders. To use PGP, you will need to purchase, download and install the software on your computer system. The software is available through the PGP website. The low-cost Desktop Home version ( available for $99 should meet the needs of most clients. How It Works PGP uses a variation of the public key system where each user has a publicly known encryption key and a private key known only to that user. In this system, the entity creating the file (PayFlex) will encrypt it using the recipient s public key and place it on their FTP website. This site allows for the transferring of files between two entities. The recipient will access the PayFlex FTP site with a secure logon id and password to retrieve the encrypted data file. Once retrieved, they will decrypt the file using their private key which is known only to them. How do I use FTP to retrieve and decrypt my PayFlex files? PayFlex will provide our clients via with a secure logon id and password for our secure FTP site. Through your internet browser or Windows Explorer you will access the site and retrieve the file. The following steps can be used to walk you through the FTP process. 1) Purchase, download and install the PGP Software. (Note: The PGP Desktop Home version should meet most client needs. It is available through the PGP website at: ( However, professional and corporate versions are available should increased functionality be required. Please consult your IT department for additional recommendations. If you currently have a working version of the PGP software, this step may be skipped.) Once the software is installed, proceed to the next step.
2 2) Receive your Private and Public Keys and a Passphrase from your PayFlex representative for use in file encryption/decryption. Your PayFlex representative will provide you by a file (Purchase Orders WC) which contains the public and private keys you will need to encrypt and decrypt files from PayFlex. You will also receive a Passphrase which will be used when you decrypt files. Store this item for future reference. When you receive the file you will need to complete the following steps: Double-click the file (Purchase Orders WC). The following screen will appear. Highlight the key (WiredCommute Client Payroll). Select Import. The following screen will appear. Select OK 3) Assign Implicit trust to your new set of keys Select the Padlock icon from the system tray and choose PGPKeys from the available options. Right-Click the WiredCommute Client Payroll key and select Key Properties from the available options.
3 The following screen will appear Check the Implicit Trust box and click Close. PGP will use this new trusted key to decrypt files you retrieve from PayFlex. 4) Retrieve files from the PayFlex FTP site. PayFlex will use your public key to encrypt your files. We will place encrypted files on the PayFlex FTP site for you to retrieve. To do so, you will need a personal login and password. Obtain your personal logon ID and password from your PayFlex representative. Login: Password:
4 5) Retrieve your files When PayFlex has created a file for you, they will place it on the PayFlex FTP site. To retrieve the file you will need to access the PayFlex FTP site. To do so enter ftp.payflex.com on the address line of your internet browser or Windows Explorer screen. You will see the following screen. Logon to the site using the login and password that you were provided. Once the username and password have been entered, you will see a screen similar to the following, where the file(s) you can retrieve are located. Right-click on the file you wish to retrieve and copy it to your clipboard. You can then paste it to the desired location on your network. (Note: Once you have successfully copied the file to your network, it is advised you delete the file from the FTP site. Deleting the file is a good idea. It indicates that you have already downloaded the file for that month. It also prevents the site from being filled with multiple files. This is done by highlighting the filename and pressing delete.)
5 6) Open your retrieved file. Through Windows Explorer find your retrieved file on your network. To decrypt and open the file, double-click the file. The PGPmail Enter Passphrase window will appear: Enter the passphrase you received from your PayFlex representative back in Step 2. Your private key will be used to unlock the file. Your file will open. You are free to work with it as you like. 7) Done
Yale Software Library. PGP 9.6 for Windows
 PGP 9.6 for Windows How to Add keys to the All Keys key ring: 1. Run the PGP application from Start->All Programs->PGP. 2. In the PGP main application window, click on Search for keys. 3. In the Search
PGP 9.6 for Windows How to Add keys to the All Keys key ring: 1. Run the PGP application from Start->All Programs->PGP. 2. In the PGP main application window, click on Search for keys. 3. In the Search
HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA. Installation
 HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
4. Click Next and then fill in your Name and E-mail address. Click Next again.
 NOTE: Before installing PGP, Word needs to be disabled as your editor in Outlook. In Outlook, go to Tools: Options: Mail Format and uncheck Use Microsoft Office Word to edit e-mail messages. Failure to
NOTE: Before installing PGP, Word needs to be disabled as your editor in Outlook. In Outlook, go to Tools: Options: Mail Format and uncheck Use Microsoft Office Word to edit e-mail messages. Failure to
How To Encrypt A Traveltrax Report On Gpg On A Pc Or Mac Or Mac (For A Free Download) On A Thumbdrive Or Ipad Or Ipa (For Free) On Pc Or Ipo (For An Ipo)
 EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
BRIEF INTRODUCTION TO CRYPTOGRAPHY. By PAGVAC. February 8, 2004
 BRIEF INTRODUCTION TO CRYPTOGRAPHY By PAGVAC February 8, 2004 What will I learn from this file? What cryptography is How encryption and decryption works Cryptography terms Symmetric cryptography Asymmetric
BRIEF INTRODUCTION TO CRYPTOGRAPHY By PAGVAC February 8, 2004 What will I learn from this file? What cryptography is How encryption and decryption works Cryptography terms Symmetric cryptography Asymmetric
HMRC Secure Electronic Transfer (SET)
 HMRC Secure Electronic Transfer (SET) How to use HMRC SET using PGP Desktop Version 2.0 Contents Welcome to HMRC SET 1 HMRC SET overview 2 Encrypt a file to send to HMRC 3 Upload files to the Government
HMRC Secure Electronic Transfer (SET) How to use HMRC SET using PGP Desktop Version 2.0 Contents Welcome to HMRC SET 1 HMRC SET overview 2 Encrypt a file to send to HMRC 3 Upload files to the Government
File Share Service User guide
 File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
HOW TO RETRIEVE FILES FROM THE TARGET ANALYTICS FTP SITE
 HOW TO RETRIEVE FILES FROM THE TARGET ANALYTICS FTP SITE Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
HOW TO RETRIEVE FILES FROM THE TARGET ANALYTICS FTP SITE Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus?
 Haas How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus? The Cisco virtual private network (VPN) client allows a computer to make secure network connections via specific
Haas How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus? The Cisco virtual private network (VPN) client allows a computer to make secure network connections via specific
How to Setup Privacy Guard Encryption.
 How to Setup Privacy Guard Encryption. Contents Setting up for the first time.... 1 Installing the Software (free)... 1 Generating your own key... 2 Share your key with your friends so they can send you
How to Setup Privacy Guard Encryption. Contents Setting up for the first time.... 1 Installing the Software (free)... 1 Generating your own key... 2 Share your key with your friends so they can send you
Ashgate FTP Web Login
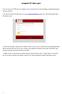 Ashgate FTP Web Login You can access our FTP site very simply via our web portal or by downloading a dedicated program (see pg. 6 below). 1. In your favourite web browser go to www.ashgatepublishing.co.uk.
Ashgate FTP Web Login You can access our FTP site very simply via our web portal or by downloading a dedicated program (see pg. 6 below). 1. In your favourite web browser go to www.ashgatepublishing.co.uk.
Online File Folder. Getting Started Guide. Become an Expert at Managing Your Files Online. wind. Online File Folder // Getting Started Guide
 Getting Started Guide Online File Folder Become an Expert at Managing Your Files Online Getting Started Guide Page 1 Getting Started Guide: Online File Folder Version 2.1 (2.22.11) Copyright 2010. All
Getting Started Guide Online File Folder Become an Expert at Managing Your Files Online Getting Started Guide Page 1 Getting Started Guide: Online File Folder Version 2.1 (2.22.11) Copyright 2010. All
GETTING STARTED SECURE FILE TRANSFER PROCEDURES A. Secure File Transfer Protocol (SFTP) Procedures
 A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
FileZilla: Uploading/Downloading Files to SBI FTP
 FileZilla Download and Installation Instructions FileZilla is a free software that uses SourceForge as an installation provider. SourceForge is bundling the FileZilla software with other products that
FileZilla Download and Installation Instructions FileZilla is a free software that uses SourceForge as an installation provider. SourceForge is bundling the FileZilla software with other products that
QUANTIFY INSTALLATION GUIDE
 QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
CBH Provider EDI Browser Manual
 CBH Provider EDI Browser Manual Table of Contents PGP Software Installation Windows XP 2 PGP Software Installation Windows 7 9 Main Screen 16 Log In Screen 19 Report: Authorizations 21 Decryption Instructions
CBH Provider EDI Browser Manual Table of Contents PGP Software Installation Windows XP 2 PGP Software Installation Windows 7 9 Main Screen 16 Log In Screen 19 Report: Authorizations 21 Decryption Instructions
IBM Client Security Solutions. Password Manager Version 1.4 User s Guide
 IBM Client Security Solutions Password Manager Version 1.4 User s Guide IBM Client Security Solutions Password Manager Version 1.4 User s Guide First Edition (October 2004) Copyright International Business
IBM Client Security Solutions Password Manager Version 1.4 User s Guide IBM Client Security Solutions Password Manager Version 1.4 User s Guide First Edition (October 2004) Copyright International Business
PGP Desktop Encrypting Removable Media. May 1 2012 Version 1.3
 PGP Desktop Encrypting Removable Media May 1 2012 Version 1.3 Table of Contents Introduction... 3 Installation Notes... 3 Encrypting Removable Media... 5 Adding and Deleting Users... 10 Changing a Passphrase...
PGP Desktop Encrypting Removable Media May 1 2012 Version 1.3 Table of Contents Introduction... 3 Installation Notes... 3 Encrypting Removable Media... 5 Adding and Deleting Users... 10 Changing a Passphrase...
User Guide. The AMF's File Transfer Service (FTS)
 User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
Overview Keys. Overview
 Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using your Encrypted BlackBerry
 Using your Encrypted BlackBerry How do I change the Language on my BlackBerry? 1. On the Home screen or in a folder, click the Options icon. 2. Click Typing and Input > Language. 3. To change the display
Using your Encrypted BlackBerry How do I change the Language on my BlackBerry? 1. On the Home screen or in a folder, click the Options icon. 2. Click Typing and Input > Language. 3. To change the display
PDG Software. Encryption Guide
 Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2006 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2006 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Methods available to GHP for out of band PUBLIC key distribution and verification.
 GHP PGP and FTP Client Setup Document 1 of 7 10/14/2004 3:37 PM This document defines the components of PGP and FTP for encryption, authentication and FTP password changes. It covers the generation and
GHP PGP and FTP Client Setup Document 1 of 7 10/14/2004 3:37 PM This document defines the components of PGP and FTP for encryption, authentication and FTP password changes. It covers the generation and
How do I share a file with a friend or trusted associate?
 Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information
Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information
Encrypting Files Using AxCrypt
 Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
New World Construction FTP service User Guide
 New World Construction FTP service User Guide A. Introduction... 2 B. Logging In... 4 C. Uploading Files... 5 D. Sending Files... 6 E. Tracking Downloads... 10 F. Receiving Files... 11 G. Setting Download
New World Construction FTP service User Guide A. Introduction... 2 B. Logging In... 4 C. Uploading Files... 5 D. Sending Files... 6 E. Tracking Downloads... 10 F. Receiving Files... 11 G. Setting Download
Please note that a username and password will be made available upon request. These are necessary to transfer files.
 Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
BillQuick Installation Guide for Microsoft SQL Server 2005 Express Edition
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Installation Guide for Microsoft SQL Server 2005 Express Edition BQE Software, Inc. 2601 Airport Drive Suite 380
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Installation Guide for Microsoft SQL Server 2005 Express Edition BQE Software, Inc. 2601 Airport Drive Suite 380
Downloading, Installing, and Updating Sophos Anti-Virus
 Downloading, Installing, and Updating Sophos Anti-Virus Part 1: Downloading Sophos Anti-Virus 1) Open your Internet browser and go to www.bol.ucla.edu. *Only use Chrome or Firefox to download this installation.
Downloading, Installing, and Updating Sophos Anti-Virus Part 1: Downloading Sophos Anti-Virus 1) Open your Internet browser and go to www.bol.ucla.edu. *Only use Chrome or Firefox to download this installation.
Use your UNNCNetID and password to log in. The first time you login to the system, you may receive the following screen:
 (Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. Personnel at UNMC occasionally need
(Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. Personnel at UNMC occasionally need
Honeywell Secure Email External User Guide August 2013
 Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
Accessing the FTP Server - User Manual
 CENTRAL BANK OF CYPRUS Accessing the FTP Server - User Manual IT Department, CENTRAL BANK OF CYPRUS TABLE OF CONTENTS 1 EXECUTIVE SUMMARY... 1 1.1 AUDIENCE... 1 1.2 SCOPE... 1 2 CHANGES FROM THE OLD FTP
CENTRAL BANK OF CYPRUS Accessing the FTP Server - User Manual IT Department, CENTRAL BANK OF CYPRUS TABLE OF CONTENTS 1 EXECUTIVE SUMMARY... 1 1.1 AUDIENCE... 1 1.2 SCOPE... 1 2 CHANGES FROM THE OLD FTP
Interact for Microsoft Office
 Interact for Microsoft Office Installation and Setup Guide Perceptive Content Version: 7.0.x Written by: Product Knowledge, R&D Date: October 2014 2014 Perceptive Software. All rights reserved Perceptive
Interact for Microsoft Office Installation and Setup Guide Perceptive Content Version: 7.0.x Written by: Product Knowledge, R&D Date: October 2014 2014 Perceptive Software. All rights reserved Perceptive
How To Encrypt a File using Windows Explorer and WinZip. For Use With All PII Data
 How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information
How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information
(You will use the login ID and password below to login through the first two websites.)
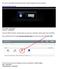 (You will use the login ID and password below to login through the first two websites.) https://providers.cvch.com Citrix Logon: Password: Press the SKIP TO LOG ON selection after
(You will use the login ID and password below to login through the first two websites.) https://providers.cvch.com Citrix Logon: Password: Press the SKIP TO LOG ON selection after
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
D&B SafeTransPort Tutorial YOUR MANAGED FILE TRANSFER SOLUTION FOR SECURE FILE TRANSFERS WITH D&B
 Tutorial YOUR MANAGED FILE TRANSFER SOLUTION FOR SECURE FILE TRANSFERS WITH D&B Overview Overview Topics Covered overview, features and benefits Account activation and password maintenance Using the User
Tutorial YOUR MANAGED FILE TRANSFER SOLUTION FOR SECURE FILE TRANSFERS WITH D&B Overview Overview Topics Covered overview, features and benefits Account activation and password maintenance Using the User
Get Smart Card Ready. How to Recover Your Old (Expired) Certificates
 How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
Preparing your Domain to transfer from Go Daddy
 Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
OnDemand. Getting Started Guide
 OnDemand Getting Started Guide Copyright Copyright 2009 ACS Technologies Group, Inc. All rights reserved. Reproduction of any part of this publication by mechanical or electronic means, including facsimile
OnDemand Getting Started Guide Copyright Copyright 2009 ACS Technologies Group, Inc. All rights reserved. Reproduction of any part of this publication by mechanical or electronic means, including facsimile
Using the Secure District File Retrieval System to Access 2008 AYP Accountability Reports
 Using the Secure District File Retrieval System to Access 2008 AYP Accountability Reports Office of Research and Statistics Mississippi Department of Education Revised October 6, 2008 Traditionally, the
Using the Secure District File Retrieval System to Access 2008 AYP Accountability Reports Office of Research and Statistics Mississippi Department of Education Revised October 6, 2008 Traditionally, the
Orbital ATK Secure Email: Receiving Encrypted Messages. Why Orbital ATK Secure Email? Initial Email: Orbital ATK Secure Email Notification
 Orbital ATK Secure Email: Receiving Encrypted Messages This document is intended for Orbital ATK Employees, Partners & Clients as an introduction & instructional user guide for Orbital ATK Secure Email.
Orbital ATK Secure Email: Receiving Encrypted Messages This document is intended for Orbital ATK Employees, Partners & Clients as an introduction & instructional user guide for Orbital ATK Secure Email.
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
FTP Help Guide
 MCS FTP (File Transfer Protocol) Version 2 August 2004 The MCS FTP site is for large file transfers that normally would not attach and sent over email. An identity is created for each MCS employee and
MCS FTP (File Transfer Protocol) Version 2 August 2004 The MCS FTP site is for large file transfers that normally would not attach and sent over email. An identity is created for each MCS employee and
ECA IIS Instructions. January 2005
 ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
How to Send an Encrypted Email via KDADS' Outlook Client or Outlook Web Application
 How to Send an Encrypted Email via KDADS' Outlook Client or Outlook Web Application In order to ensure Personal Health Information (PHI) and Personally Identifiable Information (PII) is protected, KDADS
How to Send an Encrypted Email via KDADS' Outlook Client or Outlook Web Application In order to ensure Personal Health Information (PHI) and Personally Identifiable Information (PII) is protected, KDADS
Access your directories (home directory and shared directories) outside Tilburg University
 Access your directories (home directory and shared directories) outside Tilburg University FileZilla offers you the possibility to access your personal M-drive or other network locations through a secure
Access your directories (home directory and shared directories) outside Tilburg University FileZilla offers you the possibility to access your personal M-drive or other network locations through a secure
Introduction to Webmail. Apache County Library District April 2011
 Introduction to Webmail Apache County Library District April 2011 1 Review of terms we will be using in this tutorial: Single-click: This refers to a single click of the left mouse button. If you hold
Introduction to Webmail Apache County Library District April 2011 1 Review of terms we will be using in this tutorial: Single-click: This refers to a single click of the left mouse button. If you hold
Upon Installation, Soda
 Upon Installation, Soda Prompts you to create your user profile to register for a new profile Note: Asks your for your particulars Prompts you to select a password. You would need to provide this password
Upon Installation, Soda Prompts you to create your user profile to register for a new profile Note: Asks your for your particulars Prompts you to select a password. You would need to provide this password
Masergy Fax Solutions Virtual Fax and Fax Line User Guide
 Masergy Fax Solutions Virtual Fax and Fax Line User Guide Version 1 July 30, 2015 Table of Contents Getting Started 3 Installation 3 Print to Fax..9 Web to Fax.13 Receiving Fax..17 Page 2 of 17 Getting
Masergy Fax Solutions Virtual Fax and Fax Line User Guide Version 1 July 30, 2015 Table of Contents Getting Started 3 Installation 3 Print to Fax..9 Web to Fax.13 Receiving Fax..17 Page 2 of 17 Getting
A SHORT INTRODUCTION TO CYBERDUCK WITH CLOUD OBJECT STORAGE. Version 1.12 2014-07-01
 A SHORT INTRODUCTION TO CYBERDUCK WITH CLOUD OBJECT STORAGE Version 1.12 2014-07-01 PAGE _ 2 TABLE OF CONTENTS 1. Introduction....Page 03 2. Access Cloud Object Storage using Cyberduck...Page 04 3. Create
A SHORT INTRODUCTION TO CYBERDUCK WITH CLOUD OBJECT STORAGE Version 1.12 2014-07-01 PAGE _ 2 TABLE OF CONTENTS 1. Introduction....Page 03 2. Access Cloud Object Storage using Cyberduck...Page 04 3. Create
Using SSH Secure Shell Client for FTP
 Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using the SB Partners Client Web Portal
 Using the SB Partners Client Web Portal Note: These are instructions for clients of SB Partners LLP. Table of Contents Overview... 2 Receiving your username and password... 3 Logging on... 4 Navigating
Using the SB Partners Client Web Portal Note: These are instructions for clients of SB Partners LLP. Table of Contents Overview... 2 Receiving your username and password... 3 Logging on... 4 Navigating
Remote Access in Windows XP
 Remote Access in Windows XP Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Antivirus 2 3. Run a Full System Scan
Remote Access in Windows XP Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Antivirus 2 3. Run a Full System Scan
91.527 - Human Computer Interaction Final Project Tutorial. Hardware Inventory Management System (HIMS) By M. Michael Nourai
 91.527 - Human Computer Interaction Final Project Tutorial Hardware Inventory Management System (HIMS) By Table of Contents Introduction... 3 Running HIMS... 3 Successful Login to HIMS... 4 HIMS Main Screen...
91.527 - Human Computer Interaction Final Project Tutorial Hardware Inventory Management System (HIMS) By Table of Contents Introduction... 3 Running HIMS... 3 Successful Login to HIMS... 4 HIMS Main Screen...
2. To encrypt the drive for future use, click Yes (Fig 1, 2). This will start the encryption process.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Accessing Personal Web Folders Macon State College
 Accessing Personal Web Folders Macon State College 1. Download and Install Secure FTP Secure FTP is M State College s supported sftp client for accessing your Web folder on Webdav. You may use other FTP
Accessing Personal Web Folders Macon State College 1. Download and Install Secure FTP Secure FTP is M State College s supported sftp client for accessing your Web folder on Webdav. You may use other FTP
CISCO SECURE MAIL. External User Guide. 1/15/15 Samson V.
 1/15/15 Samson V. 1. These instructions are for users who reside outside the University of Colorado Denver that receive encrypted emails from faculty or staff of UC Denver. As a part of our HIPAA compliance
1/15/15 Samson V. 1. These instructions are for users who reside outside the University of Colorado Denver that receive encrypted emails from faculty or staff of UC Denver. As a part of our HIPAA compliance
Contents Minimum Requirements... 2 Instructions... 2 Troubleshooting... 7
 Emdeon Remote Desktop Services Contents Minimum Requirements... 2 Instructions... 2 Troubleshooting... 7 Minimum Requirements 1. A high-speed Internet connection. DSL or Cable Internet are recommended.
Emdeon Remote Desktop Services Contents Minimum Requirements... 2 Instructions... 2 Troubleshooting... 7 Minimum Requirements 1. A high-speed Internet connection. DSL or Cable Internet are recommended.
LRDC Computing Services
 LRDC Computing Services Remote Access to the LRDC Fileservers Windows XP* April 5, 2005 *While these instructions have been created for and tested on a Windows XP computer, they may also work for your
LRDC Computing Services Remote Access to the LRDC Fileservers Windows XP* April 5, 2005 *While these instructions have been created for and tested on a Windows XP computer, they may also work for your
Undergraduate Academic Affairs \ Student Affairs IT Services. VPN and Remote Desktop Access from a Windows 7 PC
 Undergraduate Academic Affairs \ Student Affairs IT Services VPN and Remote Desktop Access from a Windows 7 PC Last edited: 4 December 2015 Contents Inform IT Staff... 1 Things to Note... 1 Setting Up
Undergraduate Academic Affairs \ Student Affairs IT Services VPN and Remote Desktop Access from a Windows 7 PC Last edited: 4 December 2015 Contents Inform IT Staff... 1 Things to Note... 1 Setting Up
VPN Connection and Configuration
 VPN Connection and Configuration The assumption is made that you have already gained access to the internet either via a dialup, DSL, or cable modem connection. Please keep in mind that the slower your
VPN Connection and Configuration The assumption is made that you have already gained access to the internet either via a dialup, DSL, or cable modem connection. Please keep in mind that the slower your
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1
 PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
Installation and User Guide. MQLink Version 3.0 (Java)
 Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
QuickNotes for using Tumbleweed, ISO's FTP system.
 QuickNotes for using Tumbleweed, ISO's FTP system. These notes provide a quick guide to using ISO's file transfer protocol (FTP) system. Our hope is that you will find this system easy to use, and convenient
QuickNotes for using Tumbleweed, ISO's FTP system. These notes provide a quick guide to using ISO's file transfer protocol (FTP) system. Our hope is that you will find this system easy to use, and convenient
Connecting to LUA s webmail
 Connecting to LUA s webmail Effective immediately, the Company has enhanced employee remote access to email (Outlook). By utilizing almost any browser you will have access to your Company e-mail as well
Connecting to LUA s webmail Effective immediately, the Company has enhanced employee remote access to email (Outlook). By utilizing almost any browser you will have access to your Company e-mail as well
Bloomfield Hills Schools VPN and Viewconnect Instructions
 Connect to Bloomfield Hills Schools VPN - Open Internet Explorer. - Type https://vpn.bloomfield.org into the address bar. - Click Continue to this website (not recommended). if prompted. - If this is your
Connect to Bloomfield Hills Schools VPN - Open Internet Explorer. - Type https://vpn.bloomfield.org into the address bar. - Click Continue to this website (not recommended). if prompted. - If this is your
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client
 SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
SCADA Security. Enabling Integrated Windows Authentication For CitectSCADA Web Client. Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.
 Enabling Integrated Windows Authentication For CitectSCADA Web Client Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.xx Summary: What is the difference between Basic Authentication and Windows
Enabling Integrated Windows Authentication For CitectSCADA Web Client Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.xx Summary: What is the difference between Basic Authentication and Windows
PDG Software. PDG Key Manager User Guide
 PDG Key Manager User Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2000 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all
PDG Key Manager User Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2000 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all
Installing the VPN Page 2 Accessing and Using the VPN.Page 4 Accessing the Elementary Progress Report...Page 6 Accessing IEP Plus...
 Installing the VPN Page 2 Accessing and Using the VPN.Page 4 Accessing the Elementary Progress Report...Page 6 Accessing IEP Plus......Page 7 Setting up a Shortcut to Access Personal Storage Folders...Page
Installing the VPN Page 2 Accessing and Using the VPN.Page 4 Accessing the Elementary Progress Report...Page 6 Accessing IEP Plus......Page 7 Setting up a Shortcut to Access Personal Storage Folders...Page
Figure 1: Restore Tab
 Apptix Online Backup by Mozy Restore How do I restore my data? There are five ways of restoring your data: 1) Performing a Restore Using the Restore Tab You can restore files from the Apptix Online Backup
Apptix Online Backup by Mozy Restore How do I restore my data? There are five ways of restoring your data: 1) Performing a Restore Using the Restore Tab You can restore files from the Apptix Online Backup
PDG Software. Keyman Encryption Guide
 Keyman Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2004 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Keyman Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2004 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
ACS Email Encryption Recipient Guide
 ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points
 Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points Objective 1. To explore a practical application of cryptography secure e-mail 2. To use public key encryption 3. To gain experience with the various
Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points Objective 1. To explore a practical application of cryptography secure e-mail 2. To use public key encryption 3. To gain experience with the various
Accessing a Secure Message. Outside the COV Email Network
 Stay Connected! Use this Guide to help you read encrypted Accessing a Secure Message messages from DHRM sent to a non-cov email address. Outside the COV Email Network Accessing a Secure Message Outside
Stay Connected! Use this Guide to help you read encrypted Accessing a Secure Message messages from DHRM sent to a non-cov email address. Outside the COV Email Network Accessing a Secure Message Outside
Installing the VPN Page 2 Accessing and Using the VPN.Page 4 Accessing the Elementary Progress Report...Page 6 Accessing IEP Plus...
 Installing the VPN Page 2 Accessing and Using the VPN.Page 4 Accessing the Elementary Progress Report...Page 6 Accessing IEP Plus......Page 7 Setting up a Shortcut to Access Personal Storage Folders...Page
Installing the VPN Page 2 Accessing and Using the VPN.Page 4 Accessing the Elementary Progress Report...Page 6 Accessing IEP Plus......Page 7 Setting up a Shortcut to Access Personal Storage Folders...Page
Instructions for Setup and Connecting to Department of Education Secure FTP(SFTP) server January 23, 2013
 Instructions for Setup and Connecting to Department of Education Secure FTP(SFTP) server January 23, 2013 Download the Filezilla program at: http://sourceforge.net/projects/filezilla/files/filezilla_client/3.5.1/filezilla_3.5.1_win32-
Instructions for Setup and Connecting to Department of Education Secure FTP(SFTP) server January 23, 2013 Download the Filezilla program at: http://sourceforge.net/projects/filezilla/files/filezilla_client/3.5.1/filezilla_3.5.1_win32-
Olathe District Schools 1 of 11 GroupWise 7
 Olathe District Schools 1 of 11 GroupWise 7 Creating an email group To create and save a personal group: 1. Click on the toolbar. 2. Click the personal address book you want to add this group to. 3. Click
Olathe District Schools 1 of 11 GroupWise 7 Creating an email group To create and save a personal group: 1. Click on the toolbar. 2. Click the personal address book you want to add this group to. 3. Click
UBC Digital Signage Service: CoolSign 5.0 Initial Set- up Guide
 UBC Digital Signage Service: CoolSign 5.0 Initial Set- up Guide With the latest release of the CoolSign software (version 5.02) we have changed the way that users connect to the CoolSign Network Manager
UBC Digital Signage Service: CoolSign 5.0 Initial Set- up Guide With the latest release of the CoolSign software (version 5.02) we have changed the way that users connect to the CoolSign Network Manager
Global Knowledge European Remote Labs Accessing the Remote Labs portal from Windows
 Global Knowledge European Remote Labs Accessing the Remote Labs portal from Windows Summary The Remote Labs Access Portal can be accessed from a variety of operating systems and clients. This guide demonstrates
Global Knowledge European Remote Labs Accessing the Remote Labs portal from Windows Summary The Remote Labs Access Portal can be accessed from a variety of operating systems and clients. This guide demonstrates
Encryption. Introduction to using 7-Zip
 IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
ecstudent-ts Terminal Server How to Use
 ecstudent-ts Terminal Server How to Use Connect to Cisco Any Connect Connect to Terminal Server, Set Options to Use Home Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network
ecstudent-ts Terminal Server How to Use Connect to Cisco Any Connect Connect to Terminal Server, Set Options to Use Home Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network
Remote Storage Area (RSA) Basics
 Remote Storage Area (RSA) Basics Table of Contents Remote Storage Area Overview... 3 What is Remote Storage Area?... 3 Who has access to RSA?... 3 How much space is available?... 3 Basic RSA Use... 4 How
Remote Storage Area (RSA) Basics Table of Contents Remote Storage Area Overview... 3 What is Remote Storage Area?... 3 Who has access to RSA?... 3 How much space is available?... 3 Basic RSA Use... 4 How
Eduroam wireless network Windows Vista
 Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Voice-Over PowerPoint (VOPP) and FTP Instructions for Online Courses (for Windows PC Computers) December 2009
 Voice-Over PowerPoint (VOPP) and FTP Instructions for Online Courses (for Windows PC Computers) December 2009 A. How to add narration to a PowerPoint presentation: 1. Attach a microphone to your computer
Voice-Over PowerPoint (VOPP) and FTP Instructions for Online Courses (for Windows PC Computers) December 2009 A. How to add narration to a PowerPoint presentation: 1. Attach a microphone to your computer
Citrix Desktop for Home Computers Apple ios Instructions
 Citrix Desktop for Home Computers Apple ios Instructions You can use Citrix to create and access a virtual work desktop from your home computer. Step 1 Uninstall: To install the newest version of Citrix
Citrix Desktop for Home Computers Apple ios Instructions You can use Citrix to create and access a virtual work desktop from your home computer. Step 1 Uninstall: To install the newest version of Citrix
Air Resources Board File Transfer Protocol (FTP)
 Air Resources Board File Transfer Protocol (FTP) A Handbook for External Users (those not connected to the ARB network) July 2006 How do I use ARB FTP? What is the FTP server and who can use it? What software
Air Resources Board File Transfer Protocol (FTP) A Handbook for External Users (those not connected to the ARB network) July 2006 How do I use ARB FTP? What is the FTP server and who can use it? What software
QSF Creator Tool. Task Sheet. Logging Into Hosted Millennium
 Task Sheet This tool allows you, our business partner, to generate a quick setup file (QSF). You can use this file to create a copy of a Millennium database that your client can download. Your client can
Task Sheet This tool allows you, our business partner, to generate a quick setup file (QSF). You can use this file to create a copy of a Millennium database that your client can download. Your client can
Baylor Secure Messaging. For Non-Baylor Users
 Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
University of Central Florida UCF VPN User Guide UCF Service Desk
 University of Central Florida UCF VPN User Guide UCF Service Desk Table of Contents UCF VPN... 1 Cisco AnyConnect SSL Client... 2 Installation... 2 Starting New Sessions... 4 Ending a VPN Session... 5
University of Central Florida UCF VPN User Guide UCF Service Desk Table of Contents UCF VPN... 1 Cisco AnyConnect SSL Client... 2 Installation... 2 Starting New Sessions... 4 Ending a VPN Session... 5
User Guide. Active Online Backup - Secure, automatic protection
 Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Installing Novell Client Software (Windows 95/98)
 Installing Novell Client Software (Windows 95/98) Platform: Windows 95/98 Level of Difficulty: Intermediate The following procedure describes how to install the Novell Client software. This software allows
Installing Novell Client Software (Windows 95/98) Platform: Windows 95/98 Level of Difficulty: Intermediate The following procedure describes how to install the Novell Client software. This software allows
Background Information
 User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
Xythos on Demand Quick Start Guide For Xythos Drive
 Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Instructions for accessing the new TU wireless Network
 Instructions for accessing the new TU wireless Network These instructions are meant for University owned systems directly supported by ENS Computer Services. Users of other systems may find this document
Instructions for accessing the new TU wireless Network These instructions are meant for University owned systems directly supported by ENS Computer Services. Users of other systems may find this document
