How To Encrypt a File using Windows Explorer and WinZip. For Use With All PII Data
|
|
|
- Merilyn Burke
- 10 years ago
- Views:
Transcription
1 How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information you access. It is the policy of the Department of Agriculture to protect personal, financial, and employment information from unauthorized disclosure. Customers and employees have the right to expect that you will collect, maintain, use, and disseminate personally identifiable information (PII) and data only as authorized by law and as necessary to carry out official business. NFC s policy is to encrypt all PII information before being transmitted either internally or externally. After sending the zipped file as an attachment, CALL your recipient(s) on the phone and give them the password. The use of voic to convey the password is prohibited. Do Not Send the password in an . Passwords used to encrypt the attached file must be complex and include upper and lower case characters and at least one number. Encryption Instructions: To encrypt files that contain PII data, right click on the filename in Windows Explorer, cursor down to WinZip, then cursor over to Add to Zip File (highlighted below).
2 The below screen will open. By default Encrypt added files is NOT checked So Be sure and click the box next to Encrypt added files as shown below. Uncheck Include system and hidden files unless you are compressing and encrypting an entire folder, rather than a single file.
3 Then click the Add button You will receive the below Warning regarding encryption. You can click on Help if you wish to read more about encryption, or just click OK The below windows will pop up next. By default the simplest encryption method, Zip 2.0, is selected but that is NOT sufficient to encrypt PII data so
4 Make certain to change the Encryption method to 256-Bit AES by clicking the radio button, as shown below
5 Then enter a STRONG password, which requires at least 12 characters, including at least one number, at least one symbol, at least one lower case letter and at least one upper case letter, according to NFC policy. You ll have to enter it twice, as shown below. Then click OK The next window indicates that your file has been compressed and encrypted. If it doesn t state compressed AND ENCRYPTED, you were not successful and should go back and try again. If it states compressed and encrypted click OK to continue. Note that it states below the file is unlocked until the Zip file is closed.
6 The next window below shows your file, or files, that are contained in the zip file. As an additional check to make certain your file was encrypted, look for the padlock icon on the left side, as shown below, which indicates the file is encrypted. The final step is important. You must close the Zip file by clicking the File pulldown menu, and choosing Close Archive as shown below. Then you can close WinZip and your new Zip file as described below.
7 Be careful to only the file with ZIP on the end, not the original file you had before encryption. See below for an example. Be certain you only attach the Zip file.
8 After sending the zipped file as an attachment, CALL your recipient(s) on the phone and give them the password. The use of voic to convey the password is prohibited. Do Not Send the password in an . As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information you access. It is the policy of the Department of Agriculture to protect personal, financial, and employment information from unauthorized disclosure. Customers and employees have the right to expect that you will collect, maintain, use, and disseminate personally identifiable information (PII) and data only as authorized by law and as necessary to carry out official business.
Encrypting a Single Customer View file using WinZip
 Encrypting a Single Customer View file using WinZip Introduction As part of the Financial Services Compensation Scheme (FSCS) Faster Payout project, deposit takers are required to send a sample Single
Encrypting a Single Customer View file using WinZip Introduction As part of the Financial Services Compensation Scheme (FSCS) Faster Payout project, deposit takers are required to send a sample Single
Encryption. Introduction to using 7-Zip
 IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
4. Click Next and then fill in your Name and E-mail address. Click Next again.
 NOTE: Before installing PGP, Word needs to be disabled as your editor in Outlook. In Outlook, go to Tools: Options: Mail Format and uncheck Use Microsoft Office Word to edit e-mail messages. Failure to
NOTE: Before installing PGP, Word needs to be disabled as your editor in Outlook. In Outlook, go to Tools: Options: Mail Format and uncheck Use Microsoft Office Word to edit e-mail messages. Failure to
Welcome. 4 Common Security Best Practices. to the. Online Training Course
 Welcome to the 4 Common Security Best Practices Online Training Course Disclaimer 2 Introduction Information Security means protecting information from unauthorized access, use, disclosure, inspection
Welcome to the 4 Common Security Best Practices Online Training Course Disclaimer 2 Introduction Information Security means protecting information from unauthorized access, use, disclosure, inspection
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1
 PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
PGP Zip Self-Decrypting Archive (SDA) 5/29/2012 Version 1.1 Table of Contents 1 Self Decrypting Archives (SDA)... 1-2 2 Setting Windows to Display File Extensions... 2-3 3 Creating PGP Zip SDA... 3-4
McAfee Endpoint Encryption for Files and Folders (EEFF) User Documentation
 McAfee Endpoint Encryption for Files and Folders (EEFF) User Documentation 2013.06 McAfee Endpoint Encryption for Files and Folders (EEFF) uses powerful encryption technology to allow you to protect information
McAfee Endpoint Encryption for Files and Folders (EEFF) User Documentation 2013.06 McAfee Endpoint Encryption for Files and Folders (EEFF) uses powerful encryption technology to allow you to protect information
Secure File Transfer Protocol Updated Procedures. June 20, 2011
 Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
7-zip Encryption Instructions
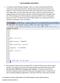 1. In a simple text editor (Notepad, Notepad++, jedit, etc.) create a text file (SendToTAP) that contains your sensitive data information. [Note the location where the file is stored on your computer.]
1. In a simple text editor (Notepad, Notepad++, jedit, etc.) create a text file (SendToTAP) that contains your sensitive data information. [Note the location where the file is stored on your computer.]
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1
 INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
Hallpass Instructions for Connecting to Mac with a Mac
 Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Masergy Fax Solutions Virtual Fax and Fax Line User Guide
 Masergy Fax Solutions Virtual Fax and Fax Line User Guide Version 1 July 30, 2015 Table of Contents Getting Started 3 Installation 3 Print to Fax..9 Web to Fax.13 Receiving Fax..17 Page 2 of 17 Getting
Masergy Fax Solutions Virtual Fax and Fax Line User Guide Version 1 July 30, 2015 Table of Contents Getting Started 3 Installation 3 Print to Fax..9 Web to Fax.13 Receiving Fax..17 Page 2 of 17 Getting
Mac OS VPN Set Up Guide
 Mac OS VPN Set Up Guide If internet traffic is not being sent over the VPN then go to System Preferences- >Network and click on your VPN connection. Click the "Advanced..." button, and in the "Options"
Mac OS VPN Set Up Guide If internet traffic is not being sent over the VPN then go to System Preferences- >Network and click on your VPN connection. Click the "Advanced..." button, and in the "Options"
MICROSOFT OFFICE 365 EXCHANGE ONLINE CLOUD
 6/4/14 Samson V. 1. Configure Outlook 2011 for Exchange Online Step 1 First we need to verify that your Office 2011 is up-to-date. Launch any Office 2011 product (Word, Excel, Outlook) and click on the
6/4/14 Samson V. 1. Configure Outlook 2011 for Exchange Online Step 1 First we need to verify that your Office 2011 is up-to-date. Launch any Office 2011 product (Word, Excel, Outlook) and click on the
USB Flash Security Free Edition Quick Start
 Quick Start [For USB Flash Security Free Edition] 1 / 18 USB Flash Security Free Edition Quick Start Before use USB Flash Security 1. Free edition can only be installed on the USB Flash Drive up to 4GB
Quick Start [For USB Flash Security Free Edition] 1 / 18 USB Flash Security Free Edition Quick Start Before use USB Flash Security 1. Free edition can only be installed on the USB Flash Drive up to 4GB
Instructions for Importing (migrating) Data
 Instructions for Importing (migrating) Data from CTAS Version 7 to CTAS Version 8 For Windows 8 and 8.1 CTAS Version 8 is designed to work with your Version 7 data if you choose to. These instructions
Instructions for Importing (migrating) Data from CTAS Version 7 to CTAS Version 8 For Windows 8 and 8.1 CTAS Version 8 is designed to work with your Version 7 data if you choose to. These instructions
Encrypting Files Using AxCrypt
 Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Overview Keys. Overview
 Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
To add Citrix XenApp Client Setup for home PC/Office using the 32bit Windows client.
 I. PURPOSE To add Citrix XenApp Client Setup for home PC/Office using the 32bit Windows client. II. POLICY: Network Request form must be sent from MIS staff to HCN Hardware Support requesting Citrix XenApp
I. PURPOSE To add Citrix XenApp Client Setup for home PC/Office using the 32bit Windows client. II. POLICY: Network Request form must be sent from MIS staff to HCN Hardware Support requesting Citrix XenApp
How to Password Protect Files & Folders in Mac OS X with Disk Images
 The best way to secure sensitive information from malware is to encrypt it. Encryption works by using a complex formula to securely scramble (or encrypt) individual files and folders, entire disks and
The best way to secure sensitive information from malware is to encrypt it. Encryption works by using a complex formula to securely scramble (or encrypt) individual files and folders, entire disks and
VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8)
 INFORMATION SYSTEMS SERVICE NETWORKS AND COMMUNICATIONS SECTOR VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8) ΥΠΣ ΕΔ/50 November 2012 A. INSTALLATION
INFORMATION SYSTEMS SERVICE NETWORKS AND COMMUNICATIONS SECTOR VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8) ΥΠΣ ΕΔ/50 November 2012 A. INSTALLATION
Instructions for connecting to winthropsecure. Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
Cryptshare for Outlook User Guide
 Cryptshare for Outlook User Guide V1.6.2 Befine Solutions AG Werthmannstr. 15 79098 Freiburg i. Br. Germany Web: https://www.cryptshare.com E-Mail: [email protected] Tel.: +49 761 389 13 0 Fax: +49 761
Cryptshare for Outlook User Guide V1.6.2 Befine Solutions AG Werthmannstr. 15 79098 Freiburg i. Br. Germany Web: https://www.cryptshare.com E-Mail: [email protected] Tel.: +49 761 389 13 0 Fax: +49 761
How To Open An Encrypted Email
 Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems
 SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems What is SSH?: SSH is an application that protects the TCP/IP connections between two computers. The software
SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems What is SSH?: SSH is an application that protects the TCP/IP connections between two computers. The software
1 of 10 1/31/2014 4:08 PM
 1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
1 of 10 1/31/2014 4:08 PM copyright 2014 How to backup Microsoft SQL Server with Nordic Backup Pro Before creating a SQL backup set within Nordic Backup Pro it is first necessary to verify that the settings
Adobe Digital Signatures in Adobe Acrobat X Pro
 Adobe Digital Signatures in Adobe Acrobat X Pro Setting up a digital signature with Adobe Acrobat X Pro: 1. Open the PDF file you wish to sign digitally. 2. Click on the Tools menu in the upper right corner.
Adobe Digital Signatures in Adobe Acrobat X Pro Setting up a digital signature with Adobe Acrobat X Pro: 1. Open the PDF file you wish to sign digitally. 2. Click on the Tools menu in the upper right corner.
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
SecureZIP User Guide
 SecureZIP User Guide SecureZIP is an application for zipping files to save storage space as well as encrypting files with password control to protect information. SecureZIP not only works alone to perform
SecureZIP User Guide SecureZIP is an application for zipping files to save storage space as well as encrypting files with password control to protect information. SecureZIP not only works alone to perform
tips A quick and easy guide to securing your private information www.pkware.com
 tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
Royal Mail Group. getting started. with Symantec Endpoint Encryption. A user guide from Royal Mail Technology
 getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
RFG Secure FTP. Web Interface
 RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
HOW TO USE OIT EMAIL VIA THE WEB
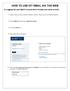 HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
Cloud Web Portal User Guide Version 2.0
 Cloud Web Portal User Guide Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
Cloud Web Portal User Guide Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
User Guide. Nero BackItUp. Ahead Software AG
 User Guide Nero BackItUp Ahead Software AG Information on copyright and trade marks The Nero BackItUp user manual and all its contents are protected by copyright and are the property of Ahead Software.
User Guide Nero BackItUp Ahead Software AG Information on copyright and trade marks The Nero BackItUp user manual and all its contents are protected by copyright and are the property of Ahead Software.
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216
 Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
IT Quick Reference Guides Connecting to SU-Secure using Windows 8
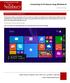 IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows 8 Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows 8 Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
Using Bitlocker to Encrypt your Flash Drive Information Technology Services July 27, 2012
 Using Bitlocker to Encrypt your Flash Drive Information Technology Services July 27, 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. How it works Basically, BitLocker
Using Bitlocker to Encrypt your Flash Drive Information Technology Services July 27, 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. How it works Basically, BitLocker
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8)
 BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
Moving your GroupWise archive to Outlook 2010 Key step to take the day after your e-mail upgrade
 Moving your GroupWise archive to Outlook 2010 Key step to take the day after your e-mail upgrade About this guide /transformation Who should use it This guide is intended for those DBHDD (Department of
Moving your GroupWise archive to Outlook 2010 Key step to take the day after your e-mail upgrade About this guide /transformation Who should use it This guide is intended for those DBHDD (Department of
School to school (S2S) guide. Local authorities
 School to school (S2S) guide Local authorities September 2014 Contents Introduction 4 Logging in to S2S 5 Roles/Users 6 Using S2S Menus 7 Encryption 8 Uploading Files 10 Downloading Files 11 Remove Files
School to school (S2S) guide Local authorities September 2014 Contents Introduction 4 Logging in to S2S 5 Roles/Users 6 Using S2S Menus 7 Encryption 8 Uploading Files 10 Downloading Files 11 Remove Files
Fax and SMS Quickguide
 INTRODUCTION U2 Fax and SMS allow faxes and SMS to be sent directly from a user s workstation via the Internet using U2 Webservices. This improves staff efficiency by removing the need to physically fax
INTRODUCTION U2 Fax and SMS allow faxes and SMS to be sent directly from a user s workstation via the Internet using U2 Webservices. This improves staff efficiency by removing the need to physically fax
PhoneCrypt Desktop. Phone Encryption Software. PhoneCrypt Manual Mobile phone encryption for Windows Platforms
 PhoneCrypt Desktop Phone Encryption Software PhoneCrypt Manual Mobile phone encryption for Windows Platforms Introduction Contents http:// www. securstar.com [email protected] 2009 by SecurStar GmbH,
PhoneCrypt Desktop Phone Encryption Software PhoneCrypt Manual Mobile phone encryption for Windows Platforms Introduction Contents http:// www. securstar.com [email protected] 2009 by SecurStar GmbH,
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College
 Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
How to Publish Your Smart Card Certificates Using Outlook 2010
 How to Publish Your Smart Card Certificates Using Outlook 2010 To send or receive (and read) digitally signed or encrypted email messages with colleagues at NIH, you must first publish your PIV certificate
How to Publish Your Smart Card Certificates Using Outlook 2010 To send or receive (and read) digitally signed or encrypted email messages with colleagues at NIH, you must first publish your PIV certificate
How To Connect To A University Of Cyprus Vpn 3000 From Your Computer To A Computer With A Password Protected Connection
 VPN 3000 Client for Windows XP & VISTA Information Security office University Of Cyprus October 11, 2007 Table of Contents 1. What is VPN 3000? 2. How To Use VPN 3000 3. Installing the VPN 3000 Client
VPN 3000 Client for Windows XP & VISTA Information Security office University Of Cyprus October 11, 2007 Table of Contents 1. What is VPN 3000? 2. How To Use VPN 3000 3. Installing the VPN 3000 Client
PDG Software. PDG Key Manager User Guide
 PDG Key Manager User Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2000 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all
PDG Key Manager User Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2000 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all
Part II Acrobat 8 Professional
 Part II Acrobat 8 Professional Exporting Images There will be times when images will need to be exported out of a PDF document and saved as a file type in which it can be used in a different application.
Part II Acrobat 8 Professional Exporting Images There will be times when images will need to be exported out of a PDF document and saved as a file type in which it can be used in a different application.
PDG Software. Keyman Encryption Guide
 Keyman Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2004 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Keyman Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2004 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Encrypting a USB Drive Using TrueCrypt
 Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
Creating a User Profile for Outlook 2013
 Creating a User Profile for Outlook 2013 This document tells you how to create a user profile for Outlook 2013 on your computer (also known as the Outlook client). This is necessary, for example, when
Creating a User Profile for Outlook 2013 This document tells you how to create a user profile for Outlook 2013 on your computer (also known as the Outlook client). This is necessary, for example, when
Using TrueCrypt to protect data
 Using TrueCrypt to protect data Password protecting and encrypting files one by one is a certainly an effective way to securely store and share data. However, what if you have a lot of files? Creating
Using TrueCrypt to protect data Password protecting and encrypting files one by one is a certainly an effective way to securely store and share data. However, what if you have a lot of files? Creating
Searching your Archive in Outlook (Normal)
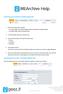 Searching your Archive in Outlook (Normal) 1. View the Archive Add in toolbar. In Outlook 2007, the toolbar displays below the standard Outlook toolbars. In Outlook 2010, select the McAfee tab. 2. In the
Searching your Archive in Outlook (Normal) 1. View the Archive Add in toolbar. In Outlook 2007, the toolbar displays below the standard Outlook toolbars. In Outlook 2010, select the McAfee tab. 2. In the
Configuring Your Email Client: Eudora 5.x
 Configuring Your Email Client: Eudora 5.x Configuring Eudora for POP 1-1 Table of Contents Chapter 1. Introduction...1-1 What is an Email Client?...1-1 Who Should Read This Manual?...1-1 How Does Email
Configuring Your Email Client: Eudora 5.x Configuring Eudora for POP 1-1 Table of Contents Chapter 1. Introduction...1-1 What is an Email Client?...1-1 Who Should Read This Manual?...1-1 How Does Email
DCH File Transfer Application User Manual
 DCH File Transfer Application User Manual Table of Contents HIPAA Compliancy Statement 3 Overview 4 General.4 Getting Started 4 Screen Basics...4 Accessing the File Transfer application...5 Single Sign
DCH File Transfer Application User Manual Table of Contents HIPAA Compliancy Statement 3 Overview 4 General.4 Getting Started 4 Screen Basics...4 Accessing the File Transfer application...5 Single Sign
Online Services through My Direct Care www.mydirectcare.com
 Online Services through My Direct Care www.mydirectcare.com WEB PORTAL Employers and Employees associated with Consumer Direct have access to online services available through a secure website www.mydirectcare.com.
Online Services through My Direct Care www.mydirectcare.com WEB PORTAL Employers and Employees associated with Consumer Direct have access to online services available through a secure website www.mydirectcare.com.
InformationNOW SQL 2008 Database Backup and Restoration
 InformationNOW SQL 2008 Database Backup and Restoration Backing up a SQL 2008 Database Users are advised to create frequent multiple offsite backups. Occasionally, it may be necessary to manually initiate
InformationNOW SQL 2008 Database Backup and Restoration Backing up a SQL 2008 Database Users are advised to create frequent multiple offsite backups. Occasionally, it may be necessary to manually initiate
Instructions for FTP of Upper Air Data to NCDC
 Instructions for FTP of Upper Air Data to NCDC Upper Air Data Continuity Study -DRAFT- Prepared by Sterling Field Support Center U.S. DEPARTMENT OF COMMERCE National Oceanic and Atmospheric Administration
Instructions for FTP of Upper Air Data to NCDC Upper Air Data Continuity Study -DRAFT- Prepared by Sterling Field Support Center U.S. DEPARTMENT OF COMMERCE National Oceanic and Atmospheric Administration
FrontPage 2003: Forms
 FrontPage 2003: Forms Using the Form Page Wizard Open up your website. Use File>New Page and choose More Page Templates. In Page Templates>General, choose Front Page Wizard. Click OK. It is helpful if
FrontPage 2003: Forms Using the Form Page Wizard Open up your website. Use File>New Page and choose More Page Templates. In Page Templates>General, choose Front Page Wizard. Click OK. It is helpful if
Protecting GoldMine CRM database with DbDefence
 Protecting GoldMine CRM database with DbDefence Version 1.1, 26 July 2013 Introduction As the backbone of any digital venture, databases are essential to the running of organizations, whether they be enormous
Protecting GoldMine CRM database with DbDefence Version 1.1, 26 July 2013 Introduction As the backbone of any digital venture, databases are essential to the running of organizations, whether they be enormous
Eurobackup PRO Exchange Databases Backup Best Practices
 P a g e 1 Eurobackup PRO Exchange Databases Backup Best Practices P a g e 2 Contents Introduction... 3 How to configure Exchange database backup with Eurobackup PRO... 4 Daily backup of Exchange databases...
P a g e 1 Eurobackup PRO Exchange Databases Backup Best Practices P a g e 2 Contents Introduction... 3 How to configure Exchange database backup with Eurobackup PRO... 4 Daily backup of Exchange databases...
Outlook Data File navigate to the PST file that you want to open, select it and choose OK. The file will now appear as a folder in Outlook.
 Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
USING STUFFIT DELUXE THE STUFFIT START PAGE CREATING ARCHIVES (COMPRESSED FILES)
 USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
Connecting to UNOSECURE using Windows 7
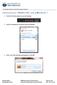 Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
SCOoffice Mail Connector For Microsoft Outlook. Installation Guide Outlook 2002
 SCOoffice Mail Connector For Microsoft Outlook Installation Guide Outlook 2002 Rev 1.2 14 Jan 2003 SCOoffice Mail Connector for Microsoft Outlook Installation Guide - Outlook XP Introduction This document
SCOoffice Mail Connector For Microsoft Outlook Installation Guide Outlook 2002 Rev 1.2 14 Jan 2003 SCOoffice Mail Connector for Microsoft Outlook Installation Guide - Outlook XP Introduction This document
Microsoft Security Essentials Installation and Configuration Guide
 Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
SQL Server Setup for Assistant/Pro applications Compliance Information Systems
 SQL Server Setup for Assistant/Pro applications Compliance Information Systems The following document covers the process of setting up the SQL Server databases for the Assistant/PRO software products form
SQL Server Setup for Assistant/Pro applications Compliance Information Systems The following document covers the process of setting up the SQL Server databases for the Assistant/PRO software products form
ProjectWise Explorer V8i User Manual for Subconsultants & Team Members
 ProjectWise Explorer V8i User Manual for Subconsultants & Team Members submitted to Michael Baker International Subconsultants & Team Members submitted by Michael Baker International ProjectWise Support
ProjectWise Explorer V8i User Manual for Subconsultants & Team Members submitted to Michael Baker International Subconsultants & Team Members submitted by Michael Baker International ProjectWise Support
Bank of Hawaii Protecting Confidential Email. What's in this User Guide
 1 Bank of Hawaii Protecting Confidential Email Email is commonly used to transmit confidential information such as operational data, legal documents, or financial information. By default emails are sent
1 Bank of Hawaii Protecting Confidential Email Email is commonly used to transmit confidential information such as operational data, legal documents, or financial information. By default emails are sent
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
MICROSOFT OUTLOOK 2003
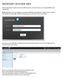 MICROSOFT OUTLOOK 2003 Follow these steps to update an Outlook 2003 account to send and receive e-mail using GCMUNI's new mail settings. Before you start, you must change your temporary GCMUNI e-mail password.
MICROSOFT OUTLOOK 2003 Follow these steps to update an Outlook 2003 account to send and receive e-mail using GCMUNI's new mail settings. Before you start, you must change your temporary GCMUNI e-mail password.
Email Update Instructions
 1 Email Update Instructions Contents Email Client Settings The Basics... 3 Outlook 2013... 4 Outlook 2007... 6 Outlook Express... 7 Windows Mail... 8 Thunderbird 3... 9 Apple Mail... 10 2 Email Client
1 Email Update Instructions Contents Email Client Settings The Basics... 3 Outlook 2013... 4 Outlook 2007... 6 Outlook Express... 7 Windows Mail... 8 Thunderbird 3... 9 Apple Mail... 10 2 Email Client
Please note that a username and password will be made available upon request. These are necessary to transfer files.
 Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
Cognos 10 Getting Started with Internet Explorer and Windows 7
 Browser/Windows Settings There are several Internet Explorer browser settings required for running reports in Cognos. This document will describe specifically how to set those in Internet Explorer 9 and
Browser/Windows Settings There are several Internet Explorer browser settings required for running reports in Cognos. This document will describe specifically how to set those in Internet Explorer 9 and
Installing Remote Desktop Connection
 SETTING UP YOUR REMOTE DESKTOP This section will assist you in setting you Remote Desktop Connection. This will allow you to create an icon for easy access to your virtual desktop. DISCLAIMER: All images
SETTING UP YOUR REMOTE DESKTOP This section will assist you in setting you Remote Desktop Connection. This will allow you to create an icon for easy access to your virtual desktop. DISCLAIMER: All images
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client
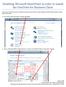 Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Virtual Office Remote Installation Guide
 Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Acer edatasecurity Management
 1 Acer edatasecurity Management Acer edatasecurity Management offers you greater personal data security and encryption for files and data transmitted via instant messaging or email. It supports the Personal
1 Acer edatasecurity Management Acer edatasecurity Management offers you greater personal data security and encryption for files and data transmitted via instant messaging or email. It supports the Personal
How to connect to VUWiFi
 Wireless Registration Instructions Windows XP How to connect to VUWiFi 1. The first step in setting up your wireless card for VUWiFi is to open your Network Connections window. You can find this by going
Wireless Registration Instructions Windows XP How to connect to VUWiFi 1. The first step in setting up your wireless card for VUWiFi is to open your Network Connections window. You can find this by going
Recommended Approach to Encrypting GNL Files
 Recommended Approach to Encrypting GNL Files 1 2 The Needs Identify a method to securely transport and store personal and/or confidential government information, which is readily accessible to government
Recommended Approach to Encrypting GNL Files 1 2 The Needs Identify a method to securely transport and store personal and/or confidential government information, which is readily accessible to government
SchoolMessenger for iphone
 The SchoolMessenger app lets you quickly and easily send messages from anywhere using your iphone. Setting up and using the application is simple. This guide will show you how! [Important: Before you can
The SchoolMessenger app lets you quickly and easily send messages from anywhere using your iphone. Setting up and using the application is simple. This guide will show you how! [Important: Before you can
BitLocker To Go USB Flash Drive encryption User Guide
 BitLocker To Go USB Flash Drive encryption User Guide Introduction BitLocker To Go is a new feature of Windows 7 which allows encryption of easily misplaced portable storage devices such as USB Flash Drives
BitLocker To Go USB Flash Drive encryption User Guide Introduction BitLocker To Go is a new feature of Windows 7 which allows encryption of easily misplaced portable storage devices such as USB Flash Drives
For paid computer support call 604-518-6695 http://www.netdigix.com [email protected]
 Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Rev. 06 JAN. 2008. Document Control User Guide: Using Outlook within Skandocs
 Rev. 06 JAN. 2008 Document Control User Guide: Using Outlook within Skandocs Introduction By referring to this user guide, it is assumed that the user has an advanced working knowledge of Skandocs (i.e.
Rev. 06 JAN. 2008 Document Control User Guide: Using Outlook within Skandocs Introduction By referring to this user guide, it is assumed that the user has an advanced working knowledge of Skandocs (i.e.
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies
 Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
electronic Declaration of Interests System (edis) User Guide
 electronic Declaration of Interests System (edis) User Guide Registering, logging on, and basic use Contents 1 Registering with the system... 2 2 Logging in and out... 4 2.1 Logging in... 4 2.2 Logging
electronic Declaration of Interests System (edis) User Guide Registering, logging on, and basic use Contents 1 Registering with the system... 2 2 Logging in and out... 4 2.1 Logging in... 4 2.2 Logging
Call Recorder Quick CD Access System
 Call Recorder Quick CD Access System V4.0 VC2010 Contents 1 Call Recorder Quick CD Access System... 3 1.1 Install the software...4 1.2 Start...4 1.3 View recordings on CD...5 1.4 Create an archive on Hard
Call Recorder Quick CD Access System V4.0 VC2010 Contents 1 Call Recorder Quick CD Access System... 3 1.1 Install the software...4 1.2 Start...4 1.3 View recordings on CD...5 1.4 Create an archive on Hard
Configuring Outlook 2013 For IMAP Connections
 Configuring Outlook 2013 For IMAP Connections VERSION 1.0 1 P a g e U A C o n n e c t C o n f i g u r i n g O u t l o o k 2013 f o r I M A P 12/2013 Configuring Outlook 2013 for IMAP Connections Overview
Configuring Outlook 2013 For IMAP Connections VERSION 1.0 1 P a g e U A C o n n e c t C o n f i g u r i n g O u t l o o k 2013 f o r I M A P 12/2013 Configuring Outlook 2013 for IMAP Connections Overview
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption!
 Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Encrypt a file, a group of files, or Folders and sub-folders, with PC-Encrypt using any of the following three methods:
 PC-ENCRYPT USER GUIDE 1/13 Register Now for Key-Exchange A free service for secure password exchange - HERE QUESTIONS? E-mail [email protected] Overview Encrypt Files or Folders Decrypt File The Password
PC-ENCRYPT USER GUIDE 1/13 Register Now for Key-Exchange A free service for secure password exchange - HERE QUESTIONS? E-mail [email protected] Overview Encrypt Files or Folders Decrypt File The Password
DATA SHEET Setup Tutorial
 NetDirector Password Manager Getting Started To begin setting up your account first go to http://www.netdirector.biz:10002/passwordmanager On the main screen there will be a link don t have an account?
NetDirector Password Manager Getting Started To begin setting up your account first go to http://www.netdirector.biz:10002/passwordmanager On the main screen there will be a link don t have an account?
Acer edatasecurity Management
 1 Acer edatasecurity Management By applying the most advanced cryptographic technologies, Acer edatasecurity Management offers Acer PC users greater personal data security and encryption for files and
1 Acer edatasecurity Management By applying the most advanced cryptographic technologies, Acer edatasecurity Management offers Acer PC users greater personal data security and encryption for files and
