Recommended Approach to Encrypting GNL Files
|
|
|
- Patricia Charles
- 10 years ago
- Views:
Transcription
1 Recommended Approach to Encrypting GNL Files 1
2 2 The Needs Identify a method to securely transport and store personal and/or confidential government information, which is readily accessible to government employees
3 3 When To Use Encryption Scenarios Store or Transport Information on USB Flash Drive Attachments Store or Transport Information on CDs/DVDs Encryption Types Hardwarebased with integrated real-time encryption Hardwarebased with software supported encryption Software-based software encryption (Software, i.e. WinZip + / CDs/DVDs) (USB flash drive) (Encryption software + USB flash drive) USB USB drives drives with with encryption encryption will will be be clearly clearly labelled labelled
4 4 Scenarios Store or Transport Information on USB Flash Drive Attachments Store or Transport Information on CD/DVD Encryption Type Hardware-Based with Integrated Real-Time Encryption Hardware-Based With Software Supported Encryption Software-Based Software Encryption Content Any personal and/or confidential information Non-personal and/or confidential information Non-personal and/or confidential information and situations where hardware-based encryption method is not available (i.e. attachment) Type Example MXI Security Kanguru Solutions WinZip Price Range (Encrypted Flash Drives Master Standing Offer) $120-$330 $ $0 Where to Get Computer store Computer store GNL licensed WinZip installed on computers
5 5 Encryption Instruction Step by Step Hardware-based with integrated real-time encryption (USB flash drive) Hardware-based with software supported encryption (Encryption software + USB flash drive) Software-based software encryption (Software, i.e. WinZip + / CDs/DVDs)
6 6 Hardware-Based with Integrated Real-Time Encryption Plug the hardware-based USB flash drive to your computer The system will automatically detect the drive Does not require the installation of additional software on your computer
7 7 Hardware-Based with Integrated Real-Time Encryption This window will be displayed; Select Run the program Display may look slightly different depending on brand name of encryption USB hardware
8 8 Hardware-Based with Integrated Real-Time Encryption Select the password option
9 9 Hardware-Based with Integrated Real-Time Encryption Utilizing the password function will protect files in the encrypted USB This drive will need to be assigned a password at the Administrator level, AND another one at the User level (see next page)
10 10 Hardware-Based with Integrated Real-Time Encryption Now that Administrator level password has been established, you will need to create a User level name (eg. John) and password
11 11 Hardware-Based with Integrated Real-Time Encryption Once both passwords have been chosen, a space on the drive will be prepared for storage use (Partitioning is a procedure where a section of the drive becomes prepared for the storage of files)
12 12 Hardware-Based with Integrated Real-Time Encryption Once partitioning has completed, this window will pop open Enter your passwords and now the drive is ready for files to be imported
13 13 Hardware-Based with Integrated Real-Time Encryption User can copy sensitive data from the source to USB drive (The encryption occurs automatically) Data is copied by dragging and dropping files from the source drive onto the USB flash drive This should prompt a copying window to indicate the process Once this copying window has completed, your drive is ready to be removed
14 14 Hardware-Based with Integrated Real-Time Encryption When you are now ready to access your stored files, plug USB flash drive into computer and this window will pop up To access the files saved on the USB flash drive, you need to enter the passwords Beware! Unsuccessful password attempts will lock the drive and you will NEVER be able to access the files
15 15 Hardware-Based with Integrated Real-Time Encryption By entering the correct passwords, the encrypted files can be accessed on any computer
16 16 Encryption Instruction Step by Step Hardware-based with integrated real-time encryption (USB flash drive) Hardware-based with software supported encryption (Encryption software + USB flash drive) Software-based software encryption (Software, i.e. WinZip + / CDs/DVDs)
17 17 Hardware-Based with Software Supported Encryption Plug the hardwarebased USB flash drive to your computer The system will automatically detect the drive
18 18 Hardware-Based with Software Supported Encryption The first step is to have your IT helpdesk install the pre-loaded security software to your source computer This occurs by running the software installation file with your USB flash drive attached to the computer
19 19 Hardware-Based with Software Supported Encryption Once the pre-loaded security software has been installed, click OK USB drive is now ready for use. Files can now be encrypted using a software-based encryption product The next steps indicate software encryption for files going on a USB flash drive or going elsewhere
20 20 Hardware-Based with Software Supported Encryption Encryption of files via software encryption Open up your encryption software program and encrypt files accordingly Note: The actual steps for encrypting files defers with each encryption program
21 21 Encryption Instruction Step by Step Hardware-based with integrated real-time encryption (USB flash drive) Hardware-based with software supported encryption (Encryption software + USB flash drive) Software-based software encryption (Software, i.e. WinZip + / CDs/DVDs)
22 22 Software-Based Software Encryption Software-based should only be used if hardwarebased is not applicable Encrypted files can be stored to hard drive, CDs/DVDs, USB drives, any portable storage devices or transmitted through Users need to understand the limitation of software encryption before using it (Page 28)
23 23 Software-Based Software Encryption Encryption Recommendation for WinZip GNL currently has enterprise licensing for WinZip 11.0 WinZip 11.0 provides three encryption methods Zip 2.0 compatible 128-Bit AES 256-Bit AES encryption Only 256-Bit AES is recommended
24 24 Software-Based Software Encryption WinZip Configuration Select files for encryption Right click and select WinZip, then Add to Zip file
25 25 Software-Based Software Encryption WinZip Configuration This window will be displayed; Select a name for your WinZip file
26 26 Software-Based Software Encryption WinZip Configuration Be sure to select Encrypt added files
27 27 Software-Based Software Encryption WinZip Configuration Type in password that will be used by those you want to access this information Confirm password AND select 256-Bit AES encryption (stronger) Other options are not recommended (ie Zip 2.0 & 128 Bit)
28 28 The Limitation of WinZip Encryption Encryption applies only to the contents of files stored within a zip file; Some information about an encrypted file, such as its size is stored in unencrypted form in the zip file's directory Encrypted files within a final zip file can be deleted or renamed New, unencrypted, files can be added to a zip file, without a password
29 29 Software-Based Software Encryption WinZip Configuration This is what the receiver will get on their end
30 30 Password Guidelines Password Strength Having a strong password plays a key role in the encryption process The composition of the all passwords should be at least 10 characters A strong password (for example: 4pRte!ai@3) mixes uppercase, lowercase, numbers, and punctuation Password Distribution Keep passwords confidential Passwords should be exchanged via a alternative secure method (e.g. face-to-face meeting, telephone calls, or mail) When using , the password should never be included with the message that includes the encrypted information If If you you lose lose your your WinZip WinZip passwords, passwords, the the information information cannot cannot be be decrypted decrypted or or recovered recovered
31 31 For Additional Information For further information regarding policies for the management of personal or confidential information, please go to: Personal information is defined by the ATIPP Act: Contact your department Helpdesk
Encrypting Files Using AxCrypt
 Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
Encrypting Files Using AxCrypt Documents, spreadsheets, databases, and other files that contain personal information or other sensitive information MUST BE encrypted when being transmitted to someone else
SecureLock Tool Functions:
 The SecureLock utility allows users to manage the Axiom EHP Flash disk by setting passwords to the secure partition and adjust the partition size. This guide will illustrate the steps required in order
The SecureLock utility allows users to manage the Axiom EHP Flash disk by setting passwords to the secure partition and adjust the partition size. This guide will illustrate the steps required in order
User Guide. G 4 Supreme. April 2010. AES 256 Encrypted USB Flash Drive. Prepared By: Md. Zakir Hosen
 G 4 Supreme AES 256 Encrypted USB Flash Drive User Guide April 2010 Copyright TwinMOS Technologies ME All Rights Reserved Product Introduction Thank you for your purchasing TwinMOS AES 256 Encryption USB
G 4 Supreme AES 256 Encrypted USB Flash Drive User Guide April 2010 Copyright TwinMOS Technologies ME All Rights Reserved Product Introduction Thank you for your purchasing TwinMOS AES 256 Encryption USB
Encrypting with BitLocker for disk volumes under Windows 7
 Encrypting with BitLocker for disk volumes under Windows 7 Summary of the contents 1 Introduction 2 Hardware requirements for BitLocker Driver Encryption 3 Encrypting drive 3.1 Operating System Drive 3.1.1
Encrypting with BitLocker for disk volumes under Windows 7 Summary of the contents 1 Introduction 2 Hardware requirements for BitLocker Driver Encryption 3 Encrypting drive 3.1 Operating System Drive 3.1.1
Verbatim Secure Data USB Drive. User Guide. User Guide Version 2.0 All rights reserved
 Verbatim Secure Data USB Drive User Guide User Guide Version 2.0 All rights reserved Table of Contents Table of Contents... 2 1. Introduction to Verbatim Secure Data USB Drive... 3 2. System Requirements...
Verbatim Secure Data USB Drive User Guide User Guide Version 2.0 All rights reserved Table of Contents Table of Contents... 2 1. Introduction to Verbatim Secure Data USB Drive... 3 2. System Requirements...
2. To encrypt the drive for future use, click Yes (Fig 1, 2). This will start the encryption process.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
USER MANUAL. v. 11.3 ------------------------ January 2014 ------------------------
 USER MANUAL v. 11.3 ------------------------ January 2014 ------------------------ 1 Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark
USER MANUAL v. 11.3 ------------------------ January 2014 ------------------------ 1 Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark
USB Flash Drive User s Manual
 USB Flash Drive User s Manual V4.01 Introduction Thank you for your purchasing the USB Drive. This manual will guide you through the usages of the USB Drive and of all management tools coming with it.
USB Flash Drive User s Manual V4.01 Introduction Thank you for your purchasing the USB Drive. This manual will guide you through the usages of the USB Drive and of all management tools coming with it.
GoldKey Software. User s Manual. Revision 7.12. WideBand Corporation www.goldkey.com. Copyright 2007-2014 WideBand Corporation. All Rights Reserved.
 GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
EasyLock. User Manual. Intuitive Encryption Application for portable Storage Devices
 1 EasyLock User Manual Intuitive Encryption Application for portable Storage Devices User Manual Version 1.0.0.8 2004-2010 CoSoSys Ltd. 2 Table of Contents Table of Contents... 2 1. Introduction... 3 2.
1 EasyLock User Manual Intuitive Encryption Application for portable Storage Devices User Manual Version 1.0.0.8 2004-2010 CoSoSys Ltd. 2 Table of Contents Table of Contents... 2 1. Introduction... 3 2.
FAQ for USB Flash Drive
 FAQ for USB Flash Drive 1. What is a USB Flash Drive? A USB Flash Drive consists of a flash memory data storage device integrated with a USB interface. USB Flash Drives are typically removable and rewritable.
FAQ for USB Flash Drive 1. What is a USB Flash Drive? A USB Flash Drive consists of a flash memory data storage device integrated with a USB interface. USB Flash Drives are typically removable and rewritable.
How To Encrypt a File using Windows Explorer and WinZip. For Use With All PII Data
 How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information
How To Encrypt a File using Windows Explorer and WinZip For Use With All PII Data As an employee or a contractor, you share in the responsibility for protecting the privacy of individuals whose information
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Windows BitLocker Drive Encryption Step-by-Step Guide
 Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1
 INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
Royal Mail Group. getting started. with Symantec Endpoint Encryption. A user guide from Royal Mail Technology
 getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
getting started with Symantec Endpoint Encryption A user guide from Royal Mail Technology For further help, contact the IT Helpdesk on 5415 2555 (01246 282555) March 2010 Contents 1 Introduction to Symantec
BackupAssist v6 quickstart guide
 Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Using Websense Data Endpoint Client Software
 1 Using Websense Data Endpoint Client Software Related topics: Disabling the endpoint client, page 3 Viewing contained files, page 5 Viewing logs, page 6 Updating the endpoint client, page 7 Your organization
1 Using Websense Data Endpoint Client Software Related topics: Disabling the endpoint client, page 3 Viewing contained files, page 5 Viewing logs, page 6 Updating the endpoint client, page 7 Your organization
Ur-Smart Your Best Choice
 Yji4/ Ur-Smart 使 用 手 冊 Ur-Smart Your Best Choice Users Manual 1 Ur-Smart 使 用 手 冊 Ur-Smart... 1 Your Best Choice... 1 Introduction... 3 Abou Ur-Smart... 3 System requirement... 4 Using Ur-Smart...
Yji4/ Ur-Smart 使 用 手 冊 Ur-Smart Your Best Choice Users Manual 1 Ur-Smart 使 用 手 冊 Ur-Smart... 1 Your Best Choice... 1 Introduction... 3 Abou Ur-Smart... 3 System requirement... 4 Using Ur-Smart...
Encrypting a Single Customer View file using WinZip
 Encrypting a Single Customer View file using WinZip Introduction As part of the Financial Services Compensation Scheme (FSCS) Faster Payout project, deposit takers are required to send a sample Single
Encrypting a Single Customer View file using WinZip Introduction As part of the Financial Services Compensation Scheme (FSCS) Faster Payout project, deposit takers are required to send a sample Single
SecureLock. User Manual
 SecureLock User Manual Encryption Application for portable Storage Devices User Manual Version 1.0.0.3 2004-2011 Integral Memory plc Table of Contents Table of Contents... 2 1. Introduction... 3 2. System
SecureLock User Manual Encryption Application for portable Storage Devices User Manual Version 1.0.0.3 2004-2011 Integral Memory plc Table of Contents Table of Contents... 2 1. Introduction... 3 2. System
Sending Files to a Social Security Laptop
 Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
BitLocker To Go USB Flash Drive encryption User Guide
 BitLocker To Go USB Flash Drive encryption User Guide Introduction BitLocker To Go is a new feature of Windows 7 which allows encryption of easily misplaced portable storage devices such as USB Flash Drives
BitLocker To Go USB Flash Drive encryption User Guide Introduction BitLocker To Go is a new feature of Windows 7 which allows encryption of easily misplaced portable storage devices such as USB Flash Drives
Imation Clip USB 2.0 Flash Drive. Imation Drive Manager Software. User s Manual
 Imation Clip USB 2.0 Flash Drive Imation Drive Manager Software User s Manual Contents Introduction... 3 Features... 3 System Requirements... 4 Handling and Operating Recommendations... 4 Driver Installation...
Imation Clip USB 2.0 Flash Drive Imation Drive Manager Software User s Manual Contents Introduction... 3 Features... 3 System Requirements... 4 Handling and Operating Recommendations... 4 Driver Installation...
tips A quick and easy guide to securing your private information www.pkware.com
 tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
Hi-Speed USB 2.0 Flash Disk. User s Manual
 Hi-Speed USB 2.0 Flash Disk User s Manual Contents Introduction... 3 Features... 3 System Requirements... 4 Before Use... 4 Driver Installation... 5 Driver Installation for Windows 98/98SE... 5 Disk Partitions
Hi-Speed USB 2.0 Flash Disk User s Manual Contents Introduction... 3 Features... 3 System Requirements... 4 Before Use... 4 Driver Installation... 5 Driver Installation for Windows 98/98SE... 5 Disk Partitions
BitLocker To Go User Guide
 BitLocker To Go User Guide 1. Introduction BitLocker To Go a new feature of Windows 7 is a full-disk encryption protection technology for removable storage devices that are connected to one of the USB
BitLocker To Go User Guide 1. Introduction BitLocker To Go a new feature of Windows 7 is a full-disk encryption protection technology for removable storage devices that are connected to one of the USB
Aegis Padlock for business
 Aegis Padlock for business Problem: Securing private information is critical for individuals and mandatory for business. Mobile users need to protect their personal information from identity theft. Businesses
Aegis Padlock for business Problem: Securing private information is critical for individuals and mandatory for business. Mobile users need to protect their personal information from identity theft. Businesses
USER MANUAL. v. 11.4.1 ---------------------- December 2015 ----------------------
 USER MANUAL v. 11.4.1 ---------------------- December 2015 ---------------------- Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark 15
USER MANUAL v. 11.4.1 ---------------------- December 2015 ---------------------- Contents At a Glance Miscellaneous 3 About EncryptDisc 14 Product info 4 About this manual 15 Copyright & trademark 15
USER MANUAL DataLocker Enterprise
 USER MANUAL DataLocker Enterprise ------------------------ March 2014 ------------------------ 1 Contents At a Glance Advanced 3 Introduction 17 Special features 5 About the Enterprise 19 Master admin
USER MANUAL DataLocker Enterprise ------------------------ March 2014 ------------------------ 1 Contents At a Glance Advanced 3 Introduction 17 Special features 5 About the Enterprise 19 Master admin
McAfee Encrypted USB Hard Disk Non-Bio Quick Start Guide
 McAfee Encrypted USB Hard Disk Non-Bio Quick Start Guide COPYRIGHT Copyright 2010 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a
McAfee Encrypted USB Hard Disk Non-Bio Quick Start Guide COPYRIGHT Copyright 2010 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a
User Manual - Secure Lock Ware
 User Manual - Secure Lock Ware Drive Encryption System Ultra High Security - 256-bit Capable AES Encryption for Buffalo USB Hard Drives www.buffalotech.com v1.8 Table of Contents Introduction.................................
User Manual - Secure Lock Ware Drive Encryption System Ultra High Security - 256-bit Capable AES Encryption for Buffalo USB Hard Drives www.buffalotech.com v1.8 Table of Contents Introduction.................................
Dictamus Manual. Dictamus is a professional dictation app for iphone, ipod touch and ipad. This manual describes setup and use of Dictamus version 10.
 Dictamus Manual Dictamus is a professional dictation app for iphone, ipod touch and ipad. This manual describes setup and use of Dictamus version 10. Table of Contents Settings! 3 General! 3 Dictation!
Dictamus Manual Dictamus is a professional dictation app for iphone, ipod touch and ipad. This manual describes setup and use of Dictamus version 10. Table of Contents Settings! 3 General! 3 Dictation!
In order to enable BitLocker, your hard drive must be partitioned in a particular manner.
 ENABLE BITLOCKER ON WINDOWS VISTA - WITHOUT A TPM Requirements: You must be running Vista Enterprise or Vista Ultimate to enable BitLocker. Any other version of Vista is not compatible. It is recommended
ENABLE BITLOCKER ON WINDOWS VISTA - WITHOUT A TPM Requirements: You must be running Vista Enterprise or Vista Ultimate to enable BitLocker. Any other version of Vista is not compatible. It is recommended
Secure Data Transfer
 Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Acer erecovery Management
 Acer erecovery Management The Acer erecovery Management provides fast, reliable and safe method of restoring your computer to its factory default settings or user-defined system configuration from an image
Acer erecovery Management The Acer erecovery Management provides fast, reliable and safe method of restoring your computer to its factory default settings or user-defined system configuration from an image
BackupAssist v6 quickstart guide
 New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
Windows 8 Backup, Restore & Recovery By John Allen
 Windows 8 Backup, Restore & Recovery By John Allen Restore and recovery options for Windows 8 are different to earlier versions of Windows, and, of course, the terminology has changed. These are a lot
Windows 8 Backup, Restore & Recovery By John Allen Restore and recovery options for Windows 8 are different to earlier versions of Windows, and, of course, the terminology has changed. These are a lot
Using TrueCrypt to protect data
 Using TrueCrypt to protect data Password protecting and encrypting files one by one is a certainly an effective way to securely store and share data. However, what if you have a lot of files? Creating
Using TrueCrypt to protect data Password protecting and encrypting files one by one is a certainly an effective way to securely store and share data. However, what if you have a lot of files? Creating
Encrypting your external USB drive on Windows
 Encrypting your external USB drive on Windows To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Encrypting your external USB drive on Windows To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Setting up your Endicia Account.
 Setting up your Endicia Account. This document covers signing up for an Endicia Internet Postage account, and downloading and installing the DAZzle label printing program. First, go to the Endicia.com
Setting up your Endicia Account. This document covers signing up for an Endicia Internet Postage account, and downloading and installing the DAZzle label printing program. First, go to the Endicia.com
Encrypting a USB Drive Using TrueCrypt
 Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
Encrypting a USB Drive Using TrueCrypt This document details the steps to encrypt a USB Pen drive using TrueCrypt. TrueCrypt is free and open-source security software allowing encryption of documents and
Password Protection Application for Verbatim USB Flash Drives
 Introduction User Manual Verbatim EasyLock Password Protection Application for Verbatim USB Flash Drives Version 1.00 Copyright 2010 Verbatim Americas, LLC. All rights reserved. All other brands and product
Introduction User Manual Verbatim EasyLock Password Protection Application for Verbatim USB Flash Drives Version 1.00 Copyright 2010 Verbatim Americas, LLC. All rights reserved. All other brands and product
Table of Contents. TPM Configuration Procedure... 2. 1. Configuring the System BIOS... 2
 Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
SMARTRECEIPT SOFTWARE INSTALLATION GUIDE For POS Systems using Windows printing Version 1.0
 SMARTRECEIPT SOFTWARE INSTALLATION GUIDE For POS Systems using Windows printing Version 1.0 Page 2 PURPOSE The purpose of this document is to provide the steps needed to install and deploy SmartReceipt
SMARTRECEIPT SOFTWARE INSTALLATION GUIDE For POS Systems using Windows printing Version 1.0 Page 2 PURPOSE The purpose of this document is to provide the steps needed to install and deploy SmartReceipt
Guidelines on use of encryption to protect person identifiable and sensitive information
 Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
Hi-Speed USB Flash Disk User s Manual Guide
 Hi-Speed USB Flash Disk User s Manual Guide System Requirements Windows 98, ME, 2000, XP, Mac OS 10.1, Linux 2.4 or above AMD or Intel Pentium 133MHz or better based computer USB 1.1, USB 2.0 or higher
Hi-Speed USB Flash Disk User s Manual Guide System Requirements Windows 98, ME, 2000, XP, Mac OS 10.1, Linux 2.4 or above AMD or Intel Pentium 133MHz or better based computer USB 1.1, USB 2.0 or higher
OutDisk 4.0 FTP FTP for Email Users using Microsoft Windows and/or Microsoft Outlook. 5/1/2012 2012 Encryptomatic LLC www.encryptomatic.
 OutDisk 4.0 FTP FTP for Email Users using Microsoft Windows and/or Microsoft Outlook 5/1/2012 2012 Encryptomatic LLC www.encryptomatic.com Contents What is OutDisk?... 3 OutDisk Requirements... 3 How Does
OutDisk 4.0 FTP FTP for Email Users using Microsoft Windows and/or Microsoft Outlook 5/1/2012 2012 Encryptomatic LLC www.encryptomatic.com Contents What is OutDisk?... 3 OutDisk Requirements... 3 How Does
Encryption. Introduction to using 7-Zip
 IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
PaperClip. em4 Cloud Client. Setup Guide
 PaperClip em4 Cloud Client Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand and product
PaperClip em4 Cloud Client Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand and product
Smart TPM. User's Manual. Rev. 1001 12MD-STPM-1001R
 Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
FLASH USB 2. 0. Introduction ENGLISH
 ENGLISH FLASH RED LED (LOCKED) GREEN LED (UNLOCKED) KEY BUTTON PIN KEYS BLUE LED (ACTIVITY) Introduction Thank you for purchasing the Corsair Your new Flash Padlock 2 is a 256-bit hardware encrypted USB
ENGLISH FLASH RED LED (LOCKED) GREEN LED (UNLOCKED) KEY BUTTON PIN KEYS BLUE LED (ACTIVITY) Introduction Thank you for purchasing the Corsair Your new Flash Padlock 2 is a 256-bit hardware encrypted USB
How to Password Protect Files & Folders in Mac OS X with Disk Images
 The best way to secure sensitive information from malware is to encrypt it. Encryption works by using a complex formula to securely scramble (or encrypt) individual files and folders, entire disks and
The best way to secure sensitive information from malware is to encrypt it. Encryption works by using a complex formula to securely scramble (or encrypt) individual files and folders, entire disks and
How To Install Ru-Vpn On A Pc Or Macbook Or Ipad (For Macbook) With A Microsoft Macbook (For Pc) With An Ipad Or Ipa (For A Macbook). Pc (For An
 RU-VPN Installation Instructions (Windows Vista and Windows 7) An RU-VPN id allows authorized users to access Ryerson s Administrative Systems via the internet. RU-VPN utilizes a digital certificate that
RU-VPN Installation Instructions (Windows Vista and Windows 7) An RU-VPN id allows authorized users to access Ryerson s Administrative Systems via the internet. RU-VPN utilizes a digital certificate that
Acer erecovery Management
 1 Acer erecovery Management Acer erecovery Management provides a fast and reliable method to restore your computer to its factory default settings or user-defined system configuration, from images stored
1 Acer erecovery Management Acer erecovery Management provides a fast and reliable method to restore your computer to its factory default settings or user-defined system configuration, from images stored
How To Encrypt A Computer With A Password Protected Encryption Software On A Microsoft Gbk (Windows) On A Pc Or Macintosh (Windows Xp) On An Uniden (Windows 7) On Pc Or Ipa (Windows 8) On
 Sophos Disk Encryption Tools guide Product version: 5.61 Document date: June 2012 Contents 1 About this guide...3 2 Download the encryption tools...4 3 Displaying the system status with SGNState...5 4
Sophos Disk Encryption Tools guide Product version: 5.61 Document date: June 2012 Contents 1 About this guide...3 2 Download the encryption tools...4 3 Displaying the system status with SGNState...5 4
Gold Lock Desktop. User Manual. Follow these simple steps to install, configure, and use Gold Lock Desktop.
 User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
Only smart people read the manual.
 Only smart people read the manual. Contents Getting Started... 1 Installing the FreeAgent Tools... 1 Using the FreeAgent Tools Icons... 9 Using the System Tray Icon... 10 Disconnecting the FreeAgent Drive...
Only smart people read the manual. Contents Getting Started... 1 Installing the FreeAgent Tools... 1 Using the FreeAgent Tools Icons... 9 Using the System Tray Icon... 10 Disconnecting the FreeAgent Drive...
SafeGuard Enterprise Web Helpdesk. Product version: 6 Document date: February 2012
 SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
DOD INTERIM CREDENTIAL IMPLEMENTATION INSTRUCTIONS BlackBerry Devices
 DOD INTERIM CREDENTIAL IMPLEMENTATION INSTRUCTIONS BlackBerry Devices A. INTRODUCTION 1. The objective of this document is to provide an outline of the technical and administrative process necessary to
DOD INTERIM CREDENTIAL IMPLEMENTATION INSTRUCTIONS BlackBerry Devices A. INTRODUCTION 1. The objective of this document is to provide an outline of the technical and administrative process necessary to
PaperClip. em4 Cloud Client. Manual Setup Guide
 PaperClip em4 Cloud Client Manual Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand
PaperClip em4 Cloud Client Manual Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand
SP Widget. Users Manual
 SP Widget Users Manual 1 Contents 1. Disclaimer notice... 4 2. Product intro...5 3. System requirements... 5 4. Introduction... 6 4.1 Activating SP Widget... 6 Illustration 4.1... 6 4.2 Browser interface...
SP Widget Users Manual 1 Contents 1. Disclaimer notice... 4 2. Product intro...5 3. System requirements... 5 4. Introduction... 6 4.1 Activating SP Widget... 6 Illustration 4.1... 6 4.2 Browser interface...
DataTraveler Secure - Privacy Edition
 DataTraveler Secure - Privacy Edition This document is designed to help users become familiar with the DataTraveler Secure - Privacy Edition. For additional support, please visit our on-line technical
DataTraveler Secure - Privacy Edition This document is designed to help users become familiar with the DataTraveler Secure - Privacy Edition. For additional support, please visit our on-line technical
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Symantec Endpoint Encryption (SEE Client) Installation Instructions. Version 8.2
 Symantec Endpoint Encryption (SEE Client) Installation Instructions Version 8.2 Warning: This software is labor intensive, therefore it is important to validate that the hard drive is healthy by first
Symantec Endpoint Encryption (SEE Client) Installation Instructions Version 8.2 Warning: This software is labor intensive, therefore it is important to validate that the hard drive is healthy by first
User Guide. Active Online Backup - Secure, automatic protection
 Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Seagate Manager. User Guide. For Use With Your FreeAgent TM Drive. Seagate Manager User Guide for Use With Your FreeAgent Drive 1
 Seagate Manager User Guide For Use With Your FreeAgent TM Drive Seagate Manager User Guide for Use With Your FreeAgent Drive 1 Seagate Manager User Guide for Use With Your FreeAgent Drive Revision 1 2008
Seagate Manager User Guide For Use With Your FreeAgent TM Drive Seagate Manager User Guide for Use With Your FreeAgent Drive 1 Seagate Manager User Guide for Use With Your FreeAgent Drive Revision 1 2008
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords
 How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Herts for Learning Ltd SROB220, Robertson
How to Encrypt Files Containing Sensitive Data (using 7zip software or Microsoft password protection) How to Create Strong Passwords School IT Systems Support Herts for Learning Ltd SROB220, Robertson
PC Security System By Crypto AG.
 Total HC-6360 Information PC Security Security System By Crypto AG Crypto AG / HC6360-e.ppt / 9927 / 1 PC Security System By Crypto AG. File Encryption Message Encryption Disk Encryption Virtual Memory
Total HC-6360 Information PC Security Security System By Crypto AG Crypto AG / HC6360-e.ppt / 9927 / 1 PC Security System By Crypto AG. File Encryption Message Encryption Disk Encryption Virtual Memory
Eurobackup PRO Exchange Databases Backup Best Practices
 P a g e 1 Eurobackup PRO Exchange Databases Backup Best Practices P a g e 2 Contents Introduction... 3 How to configure Exchange database backup with Eurobackup PRO... 4 Daily backup of Exchange databases...
P a g e 1 Eurobackup PRO Exchange Databases Backup Best Practices P a g e 2 Contents Introduction... 3 How to configure Exchange database backup with Eurobackup PRO... 4 Daily backup of Exchange databases...
Secure email Retrieval (First Time)
 Department of Administration ETS is a customer based team that provides quality telecommunications & information technology services for all branches of state government. Secure email Retrieval (First
Department of Administration ETS is a customer based team that provides quality telecommunications & information technology services for all branches of state government. Secure email Retrieval (First
SafeGuard Enterprise Web Helpdesk
 SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Guide how to protect your private data with Rohos Disk Encryption
 Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
Full Disk Encryption Policy Reference
 www.novell.com/documentation Full Disk Encryption Policy Reference ZENworks 11 Support Pack 2 October 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents
www.novell.com/documentation Full Disk Encryption Policy Reference ZENworks 11 Support Pack 2 October 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents
Tutorial How to upgrade firmware on Phison S5 controller MyDigitalSSD
 Tutorial How to upgrade firmware on Phison S5 controller MyDigitalSSD Version 1.3 This tutorial will walk you through how to create a bootable USB drive and how to apply the newest firmware S5FAM030 to
Tutorial How to upgrade firmware on Phison S5 controller MyDigitalSSD Version 1.3 This tutorial will walk you through how to create a bootable USB drive and how to apply the newest firmware S5FAM030 to
Configuring Your Network s Security
 Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
User Guide May 2013. Using Certificates in Outlook Express
 User Guide May 2013 Using Certificates in Outlook Express FIGU RES... FIGURES.... T I TL E..............................................................................................................................
User Guide May 2013 Using Certificates in Outlook Express FIGU RES... FIGURES.... T I TL E..............................................................................................................................
AES Crypt User Guide
 AES Crypt User Guide Publication Date: 2013-12-26 Original Author: Gary C. Kessler ([email protected]) Revision History Date Contributor Changes 2012-01-17 Gary C. Kessler First version 2013-03-03 Doug
AES Crypt User Guide Publication Date: 2013-12-26 Original Author: Gary C. Kessler ([email protected]) Revision History Date Contributor Changes 2012-01-17 Gary C. Kessler First version 2013-03-03 Doug
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption!
 Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Backup and Restore User manual For version 5.0.0.8
 Backup and Restore User manual For version 5.0.0.8 All rights reserved 1989 2008 Microware Software - Rev. 1.0.5 October 2, 2008 Page 1 Table of Contents Backup and Restore 1.0 Overview... 3 1.1 Main features...4
Backup and Restore User manual For version 5.0.0.8 All rights reserved 1989 2008 Microware Software - Rev. 1.0.5 October 2, 2008 Page 1 Table of Contents Backup and Restore 1.0 Overview... 3 1.1 Main features...4
Here is a guide on how to encrypt a part of your USB flash drive and access it on any computer:
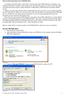 How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
Printer Support Guide. FedEx Ship Manager Software
 Printer Support Guide FedEx Ship Manager Software Printer FAQs Installing Printer Drivers How do I download and install the Zebra printer drivers? To download and install the current Zebra printer drivers
Printer Support Guide FedEx Ship Manager Software Printer FAQs Installing Printer Drivers How do I download and install the Zebra printer drivers? To download and install the current Zebra printer drivers
McAfee Endpoint Encryption for Files and Folders. Best Practices. For EEFF product version 4.0.0
 McAfee Endpoint Encryption for Files and Folders Best Practices For EEFF product version 4.0.0 McAfee, Inc. McAfee, Inc., 2821 Mission College Blvd., Santa Clara, CA 95054, USA Tel: (+1) 888.847.8766 Internet:
McAfee Endpoint Encryption for Files and Folders Best Practices For EEFF product version 4.0.0 McAfee, Inc. McAfee, Inc., 2821 Mission College Blvd., Santa Clara, CA 95054, USA Tel: (+1) 888.847.8766 Internet:
Form Builder - User Guide
 Composite 2015-12-07 Composite A/S Nygårdsvej 16 DK-2100 Copenhagen Phone +45 3915 7600 www.composite.net Contents 1 INTRODUCTION... 3 1.1 Who Should Read This Guide? 5 1.2 Getting Started 5 2 INSERTING
Composite 2015-12-07 Composite A/S Nygårdsvej 16 DK-2100 Copenhagen Phone +45 3915 7600 www.composite.net Contents 1 INTRODUCTION... 3 1.1 Who Should Read This Guide? 5 1.2 Getting Started 5 2 INSERTING
