Application Note User Groups
|
|
|
- Blake Carroll
- 10 years ago
- Views:
Transcription
1 Application Note User Groups
2 Application Note User Groups Table of Contents Background... 3 Description... 3 Benefits... 4 Theory of Operation... 4 Interaction with Other Features... 6 Configuration... 6 Application Example Tips and Recommendations Rev
3 Application Note User Groups Background Wi-Fi networks today are no longer the basic hotspots of a few years ago; today they have taken their place as a peer with wired networks. As wireless networks have matured with greater levels of security and increased performance, we are seeing migration to a model where wireless is becoming the primary medium of connectivity at the edge of our networks due to the mobility it provides. As this migration continues to expand, we are seeing greater numbers of users connecting wirelessly to the network. This results in the need for greater segmentation and control of the wireless clients. Segmentation via the use of SSIDs is still the most common way to separate and classify users. Within the SSID, policies can be defined that offer a set of privileges to associated clients; these include time of day access, authentication requirements, data rates, VLAN mappings, etc. These policies are key in managing a large user base, however as the number of wireless clients requiring different rights grows, so does the number of SSIDs required. A method is needed to define user policies independent of the SSID so that SSID parameters can be used to set basic rights, like time of day access and authentication type, and other methods can be used within the SSID to further define individual rights, such as VLAN mapping, allowed data rates, QoS rules, etc. These user profile based policies are identified as User Groups and sit on top of the SSID. Description The Xirrus Wi-Fi Array offers User Group services to provide simplified user management for those environments where multiple client classification policies are required. Clients are mapped to specific User Group assignments dynamically through an external RADIUS server. Any standard RADIUS server can provide this function. User Groups can be defined with any or all of the following parameters/policies applied to client traffic: VLAN Mapping Filter Lists Qos Levels Roaming Services DHCP Pools Station Limits Traffic Limits Time on / Time off Days On / Days Off Web Page Redirection Rev
4 Application Note User Groups Benefits User Groups greatly simplify the management of wireless clients and offers the following direct benefits: Simplify User Configuration One SSID can provide different levels of network access to specified groups of users. Using one SSID for multiple User Groups reduces the overhead on the wireless medium. Network Access Management Enables the administrator to define a group of users based on the level of network resources they would need to do their given job. It could also be used to segment network resources for security purposes. Up to 16 different user groups are supported per SSID. Level of Service The Array can offer different levels of service to each user when User Groups are implemented in combination with QoS, bandwidth controls, filter lists and WPR. By applying filter lists at the User Group level, administrators can be assured users are only accessing appropriate network resources. This gives administrators complete control over the end-users quality of experience. Policy Changes The administrator can make policy changes to one or a group of clients without having to make changes to existing SSIDs. Changes occur as required without impacting non-involved clients. Theory of Operation Wireless clients are mapped to User Groups based on information configured in the RADIUS server. The Wi-Fi Array s internal RADIUS server or an external RADIUS server can be used for this operation. When using an external RADIUS server, the mapping is done with the RADIUS filter-id (attribute 11). The filter-id is associated with the wireless client information in the RADIUS database. When the client is authenticated, this filter ID accompanies the authorization from the RADIUS server to the Wi-Fi Array. This information is used by the Array to map the client to the appropriate group; independent of the SSID the client has joined. This same process works even if Microsoft Active Directory information is used by the RADIUS service for client validation. Rev
5 Application Note User Groups The following diagram demonstrates the process that occurs for wireless clients authenticating into a wireless network and mapped to a specific User Group. Figure 1: Client Authentication Process Rev
6 Application Note User Groups Interaction with Other Features The Wi-Fi Array has many advanced features and management capabilities. This section identifies those features with dependencies associated with User Groups. SSIDs are always required for basic Wi-Fi connectivity and should be configured first. User Groups logically sit above SSIDs allowing a group to span SSIDs or to have multiple groups within one SSID. Network administrators can set traffic limits on an SSID level or a User Group level. Traffic limits can be used to restrict data traffic based on the day of the week, time of day, or amount of traffic. If traffic limits are specified at both the User Group and SSID levels, the more restrictive of the traffic limits will be in effect. VLANs can be defined within a User Group and should be configured prior to the groups. User Groups use static group mappings to VLANs on the Array. Caution should be taken not to classify the same user to be dynamically assigned to a VLAN and as a member of a User Group. The Array will drop the dynamic VLAN passed in the Radius Access-Accept if the Filter-ID attribute is present. Filter lists are optional when using User Groups, but using them allows the control of a User Group down to the protocol and port level. DHCP pools are optional when using User Groups, but allow the administrator to control the assigning of IP addresses at the group level. Roaming control at layer 3 is optional with User Groups, but allows the administrator the control by User Group. Configuration The configuration of User Groups in a Wi-Fi Array network requires setup of several components in the network, including a RADIUS server and switches with VLANs. The configuration of the Array can be preformed via the Web Management Interface (WMI) or Command Line Interface (CLI). User Group Configuration Using the Web Management Interface (WMI) 1. SSIDs should be configured prior to setting up User Groups. From the SSIDs/SSID Management screen in WMI, create the SSIDs that will be supported on the wireless network, in this example the SSID xirrus. As with all WMI configurations, when finished on a screen, click Apply and then Save to save the changes. Rev
7 Application Note User Groups 2. VLANs should be configured prior to setting up User Groups, typically one for each group type. From VLANs/VLAN Management screen, configure VLANs. In this example, VLANs Student=169, Staff=170, and Guest=171 are created. 3. The RADIUS Server configuration on the Array should next be made. From the Security/External Radius screen, configure the IP address, Port Number, and shared secrets of the RADIUS server. Rev
8 Application Note User Groups 4. Next configure the User Groups on the Array. From the Groups/Group Management screen, configure the different groups based on user profile. Group names are case sensitive and can contain up to 32 alphanumeric characters, however cannot include spaces. The RADIUS ID field should match the Filter-ID setting on the RADIUS server. 5. The next steps provide an example configuration of a Microsoft IAS server configured to work in conjunction with User Groups on the Wi-Fi Array. Actual configuration may vary based on specific implementation requirements. 6. Configure the RADIUS client on the IAS server. The client in this case is the Array and a secret must be provided. This allows the Array to communicate to the IAS server on behalf of the clients authenticating through the Array. Rev
9 Application Note User Groups 7. Configure the Array object on the IAS server. 8. Create users on the IAS server. In this example, we have created Student1, Staff1 and Guest1. Rev
10 Application Note User Groups 9. Create Groups on the IAS server by right clicking on Users / New / Groups / Create Students / Staff. Guest is already part of the Active Directory groups. 10. Add users to Groups by double clicking the Student group and adding Student1 to this group. Do the same for the Staff and Guest groups adding user Staff1 and Guest1. Rev
11 Application Note User Groups 11. Next configure client settings on the IAS server for authentication utilizing Groups. Create a Profile name that will be unique for this Group authentication. In this example, the name is Student1, the SSID is Xirrus, and User Group is Student. Rev
12 Application Note User Groups 12. Under Security Settings for the Student profile, configure the security parameters of the wireless connection. In this example, we set WPA2-Enterprise with AES-CCMP, PEAP, MS-CHAP-V2. Insert the following credentials: User Name is Student1 and Domain is HomeLab1.net. The Roaming Identify generally must match the User Name field, so enter Student1 in this box. Rev
13 Application Note User Groups 13. The certificate being used in this example is a certificate called Homelab Test Certificate. See the Xirrus Tech Tip Xirrus Wi-Fi Array Configuration Guide WPA-EAP-PEAP with Microsoft IAS (TT-1002) for a description of how to generate a certificate. This document provides details on how to configure the IAS server, Active Directory, and additional services. 14. The next steps provide an example configuration of a Windows XP station. Actual configuration may vary based on specific implementation requirements and the operating system used. Rev
14 Application Note User Groups 15. View Available Wireless Networks by right-clicking wireless icon in Windows. 16. Go to the Change the order of preferred networks menu. 17. Select the SSID the station will be connecting to and change the properties for that SSID. 18. Configure authentication: a. Enable IEEE 802.1x authentication b. Set EAP type to PEAP c. Ensure Authenticate as computer when computer information is available is not selected (unless the computer username/password are the same used to authenticate to the User Group) Rev
15 Application Note User Groups 19. Set the PEAP Properties: a. The station should NOT validate the server certificate b. Authentication Method should be Secured password Rev
16 Application Note User Groups 20. Associate a client to verify proper user group assignment. In this example, the end user Station1 should acquire an IP address on VLAN-169 in the /24 network. Verify the station is assigned to the correct egress VLAN/User Group in the Stations table. User Group Configuration Using the Command Line Interface (CLI) 1. SSIDs should be configured prior to setting up User Groups. From configuration mode in the CLI, type ssid, then add ssidname enable encryption wpa-both. Type save to save the configuration. 2. Next configure VLANs. From configuration mode in the CLI, type vlans then add vlan-name number vlan#. In this example, configure VLANs Student=169, Staff=170, and Guest= Configure the RADIUS server next. From configuration mode in the CLI, type radius-server, then external, then primary, then ip ip-address. Set the secret next by typing secret secret. 4. Next configure the User Groups themselves. From configuration mode in the CLI, type groups then add user-group-name vlan vlan-name radius-id radius-id-name on. In this example, the User Group name, VLAN name, and RADIUS ID are all the same: Student. Repeat for the remaining groups. Rev
17 Application Note User Groups 5. Configuration of an external RADIUS server is required to operate User Groups. Refer to Steps 5-13 of the WMI configuration for an example RADIUS server configuration. 6. Once associated, verify stations are assigned to the correct User Group by typing show associated-stations. Rev
18 Application Note User Groups Application Example Following is an example of how User Groups might be implemented in an academic environment. The Student User Group represents the students, and provides access only to student resources and the Internet. The Staff User Group represents school staff and provides access to all resources on the network and the Internet. The Guest User Group represents guests and contractors and provides access only to the Internet. In addition, these users are rate limited to 2000pps. Rev
19 Application Note User Groups Tips and Recommendations When is it recommended to use User Groups? User Groups should be implemented when multiple types of user profiles exist that can share the same encryption type, but have the need for different network resources due to a security policy. When is it recommended not to use User Groups? It is not recommend to use User Groups when using dynamic VLANs. The User Group s VLAN setting will override the Dynamic VLAN settings. How do I configure SSIDs with User Groups? The number of SSIDs can be reduced when implementing User Groups. From the example in the Application Example section, 3 potentially different SSIDs can be collapsed into 2: one SSID for Students and Staff with WPA2 encryption and authentication, and one SSID for Guests and contractors that is open and authenticated through a web page. What policies should I define at the SSID level? This depends on how the SSID is going to be used. Example polices to configure at the SSID level include: Radio bands 11a/b/g/n 802.1x Authentication Encryption Type: WPA2/WPA/WEP RADIUS Server What policies should I define at the User Group level? Polices at the Group level will generally be very specific to the profiles of the user types. An example for a Student Group: Traffic limits per station Time of day access Days of the week access Web Page Redirect using authentication and agreeing to acceptable use policy Where can I find more information about RADIUS? RFC 2865 Remote Authentication Dial In User Service (RADIUS) Xirrus TechTip TT-1002 provides details on how to setup and configure a Microsoft IAS RADIUS Server. Rev
VLANs. Application Note
 VLANs Application Note Table of Contents Background... 3 Benefits... 3 Theory of Operation... 4 IEEE 802.1Q Packet... 4 Frame Size... 5 Supported VLAN Modes... 5 Bridged Mode... 5 Static SSID to Static
VLANs Application Note Table of Contents Background... 3 Benefits... 3 Theory of Operation... 4 IEEE 802.1Q Packet... 4 Frame Size... 5 Supported VLAN Modes... 5 Bridged Mode... 5 Static SSID to Static
Web Page Redirect. Application Note
 Web Page Redirect Application Note Table of Contents Background... 3 Description... 3 Benefits... 3 Theory of Operation... 4 Internal Login/Splash... 4 External... 5 Configuration... 5 Web Page Redirect
Web Page Redirect Application Note Table of Contents Background... 3 Description... 3 Benefits... 3 Theory of Operation... 4 Internal Login/Splash... 4 External... 5 Configuration... 5 Web Page Redirect
Enabling Multiple Wireless Networks on RV320 VPN Router, WAP321 Wireless-N Access Point, and Sx300 Series Switches
 print email Article ID: 4941 Enabling Multiple Wireless Networks on RV320 VPN Router, WAP321 Wireless-N Access Point, and Sx300 Series Switches Objective In an ever-changing business environment, your
print email Article ID: 4941 Enabling Multiple Wireless Networks on RV320 VPN Router, WAP321 Wireless-N Access Point, and Sx300 Series Switches Objective In an ever-changing business environment, your
WIRELESS SETUP FOR WINDOWS 7
 Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, [email protected] Who should
Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, [email protected] Who should
Configuring WPA-Enterprise/WPA2 with Microsoft RADIUS Authentication
 Configuring WPA-Enterprise/WPA2 with Microsoft RADIUS Authentication This document describes how to configure WPA-Enterprise and WPA2 security protocols with RADIUS authentication for Check Point Embedded
Configuring WPA-Enterprise/WPA2 with Microsoft RADIUS Authentication This document describes how to configure WPA-Enterprise and WPA2 security protocols with RADIUS authentication for Check Point Embedded
Wireless Network Configuration Guide
 CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
How to Access Coast Wi-Fi
 How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
How To Set Up Wireless Network Security Part 1: WEP Part 2: WPA-PSK Part 3-1: RADIUS Server Installation Part 3-2: 802.1x-TLS Part 3-3: WPA
 How To Set Up Wireless Network Security Part 1: WEP Part 2: WPA-PSK Part 3-1: RADIUS Server Installation Part 3-2: 802.1x-TLS Part 3-3: WPA You can secure your wireless connection using one of the methods
How To Set Up Wireless Network Security Part 1: WEP Part 2: WPA-PSK Part 3-1: RADIUS Server Installation Part 3-2: 802.1x-TLS Part 3-3: WPA You can secure your wireless connection using one of the methods
Configure WorkGroup Bridge on the WAP131 Access Point
 Article ID: 5036 Configure WorkGroup Bridge on the WAP131 Access Point Objective The Workgroup Bridge feature enables the Wireless Access Point (WAP) to bridge traffic between a remote client and the wireless
Article ID: 5036 Configure WorkGroup Bridge on the WAP131 Access Point Objective The Workgroup Bridge feature enables the Wireless Access Point (WAP) to bridge traffic between a remote client and the wireless
WiNG5 CAPTIVE PORTAL DESIGN GUIDE
 WiNG5 DESIGN GUIDE By Sriram Venkiteswaran WiNG5 CAPTIVE PORTAL DESIGN GUIDE June, 2011 TABLE OF CONTENTS HEADING STYLE Introduction To Captive Portal... 1 Overview... 1 Common Applications... 1 Authenticated
WiNG5 DESIGN GUIDE By Sriram Venkiteswaran WiNG5 CAPTIVE PORTAL DESIGN GUIDE June, 2011 TABLE OF CONTENTS HEADING STYLE Introduction To Captive Portal... 1 Overview... 1 Common Applications... 1 Authenticated
Internet access system through the Wireless Network of the University of Bologna (last update 6.3.2012)
 Internet access system through the Wireless Network of the University of Bologna (last update 6.3.2012) Printable service summary document: the updated version is available online at the following address
Internet access system through the Wireless Network of the University of Bologna (last update 6.3.2012) Printable service summary document: the updated version is available online at the following address
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall:
 How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
Setting up a WiFi Network (WLAN)
 Setting up a WiFi Network (WLAN) How to set up Wi-Fi on your Huawei E960 InZone Step 1: In the address field on your internet browser, type http://192.168.1.1/ Step 2: Type admin into the Password box
Setting up a WiFi Network (WLAN) How to set up Wi-Fi on your Huawei E960 InZone Step 1: In the address field on your internet browser, type http://192.168.1.1/ Step 2: Type admin into the Password box
User Guide for eduroam
 User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530
 SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
802.1X AUTHENTICATION IN ACKSYS BRIDGES AND ACCESS POINTS
 APPLICATION NOTE Ref APNUS004 rev. A-0, March 08, 2007 802.1X AUTHENTICATION IN ACKSYS BRIDGES AND ACCESS POINTS Why? In addition to MAC address filtering, ACKSYS products support a more reliable authentication
APPLICATION NOTE Ref APNUS004 rev. A-0, March 08, 2007 802.1X AUTHENTICATION IN ACKSYS BRIDGES AND ACCESS POINTS Why? In addition to MAC address filtering, ACKSYS products support a more reliable authentication
Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet)
 Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet) What is WPA (Wi-Fi Protected Access)? WPA is a powerful, standards-based, interoperable security technology
Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet) What is WPA (Wi-Fi Protected Access)? WPA is a powerful, standards-based, interoperable security technology
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College
 Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
Application Note Gigabit Ethernet Port Modes
 Application Note Gigabit Ethernet Port Modes Application Note Gigabit Ethernet Port Modes Table of Contents Description... 3 Benefits... 4 Theory of Operation... 4 Interaction with Other Features... 7
Application Note Gigabit Ethernet Port Modes Application Note Gigabit Ethernet Port Modes Table of Contents Description... 3 Benefits... 4 Theory of Operation... 4 Interaction with Other Features... 7
How to connect to the diamonds wireless network with Vista.
 How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
ALL1682511. 500Mbits Powerline WLAN N Access Point. User s Manual
 ALL1682511 500Mbits Powerline WLAN N Access Point User s Manual Contents 1. Introduction...1 2. System Requirements...1 3. Configuration...1 4. WPS...9 5. Wireless AP Settings...9 6. FAQ... 15 7. Glossary...
ALL1682511 500Mbits Powerline WLAN N Access Point User s Manual Contents 1. Introduction...1 2. System Requirements...1 3. Configuration...1 4. WPS...9 5. Wireless AP Settings...9 6. FAQ... 15 7. Glossary...
Eduroam wireless network Windows Vista
 Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Canterbury College Eduroam Wi-Fi Guide
 Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: [email protected] Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: [email protected] Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Wireless Local Area Networks (WLANs)
 4 Wireless Local Area Networks (WLANs) Contents Overview...................................................... 4-3 Configuration Options: Normal Versus Advanced Mode.............. 4-4 Normal Mode Configuration..................................
4 Wireless Local Area Networks (WLANs) Contents Overview...................................................... 4-3 Configuration Options: Normal Versus Advanced Mode.............. 4-4 Normal Mode Configuration..................................
A Division of Cisco Systems, Inc. GHz 2.4 802.11g. Wireless-G. USB Network Adapter with RangeBooster. User Guide WIRELESS WUSB54GR. Model No.
 A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G USB Network Adapter with RangeBooster User Guide Model No. WUSB54GR Copyright and Trademarks Specifications are subject to change without
A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G USB Network Adapter with RangeBooster User Guide Model No. WUSB54GR Copyright and Trademarks Specifications are subject to change without
User Guide. E-Series Routers
 User Guide E-Series Routers Table of Contents Table of Contents Product overview E900/E1200/E1500/E2500/E3200 1 Back view 1 Bottom view 1 E4200 2 Top view 2 Back view 2 Setting Up Your E-Series Router
User Guide E-Series Routers Table of Contents Table of Contents Product overview E900/E1200/E1500/E2500/E3200 1 Back view 1 Bottom view 1 E4200 2 Top view 2 Back view 2 Setting Up Your E-Series Router
Mac OS X Secure Wireless Setup Guide
 Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
How to Connect to UAB s Wireless Networks
 How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
Use 802.1x EAP-TLS or PEAP-MS-CHAP v2 with Microsoft Windows Server 2003 to Make a Secure Network
 How To Use 802.1x EAP-TLS or PEAP-MS-CHAP v2 with Microsoft Windows Server 2003 to Make a Secure Network Introduction This document describes how to create a secure LAN, using two servers and an 802.1xcompatible
How To Use 802.1x EAP-TLS or PEAP-MS-CHAP v2 with Microsoft Windows Server 2003 to Make a Secure Network Introduction This document describes how to create a secure LAN, using two servers and an 802.1xcompatible
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows 7
 Seamless and Secure Access (SSA) Manual Configuration Guide for Windows 7 Page 1 1 Enable Wi-Fi a) Please refer to your computer s user manual to enable the Wireless (Wi-Fi) connection. b) Please click
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows 7 Page 1 1 Enable Wi-Fi a) Please refer to your computer s user manual to enable the Wireless (Wi-Fi) connection. b) Please click
Belnet Networking Conference 2013
 Belnet Networking Conference 2013 Thursday 12 December 2013 @ http://events.belnet.be Workshop roaming services: eduroam / govroam Belnet Aris Adamantiadis, Nicolas Loriau Bruxelles 05 December 2013 Agenda
Belnet Networking Conference 2013 Thursday 12 December 2013 @ http://events.belnet.be Workshop roaming services: eduroam / govroam Belnet Aris Adamantiadis, Nicolas Loriau Bruxelles 05 December 2013 Agenda
How To Set Up Hopkins Wireless On Windows 7 On A Pc Or Mac Or Ipad (For A Laptop) On A Network Card (For Windows 7) On Your Computer Or Ipa (For Mac Or Mac) On An Ipa Or
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
RWL Tech Note Wireless 802.1x Authentication with Windows NPS
 Wireless 802.1x Authentication with Windows NPS Prepared by Richard Litchfield HP Networking Solution Architect Hewlett-Packard Australia Limited 410 Concord Road Rhodes NSW 2138 AUSTRALIA Date Prepared:
Wireless 802.1x Authentication with Windows NPS Prepared by Richard Litchfield HP Networking Solution Architect Hewlett-Packard Australia Limited 410 Concord Road Rhodes NSW 2138 AUSTRALIA Date Prepared:
Layer 2 / Layer 3 switches and multi-ssid multi-vlan network with traffic separation
 Layer 2 / Layer 3 switches and multi-ssid multi-vlan network with traffic separation This document describes the steps to undertake in configuring a Layer 2/Layer 3 switch (in this document a FMS7382S
Layer 2 / Layer 3 switches and multi-ssid multi-vlan network with traffic separation This document describes the steps to undertake in configuring a Layer 2/Layer 3 switch (in this document a FMS7382S
Interlink Networks Secure.XS and Cisco Wireless Deployment Guide
 Overview Interlink Networks Secure.XS and Cisco Wireless Deployment Guide (An AVVID certification required document) This document is intended to serve as a guideline to setup Interlink Networks Secure.XS
Overview Interlink Networks Secure.XS and Cisco Wireless Deployment Guide (An AVVID certification required document) This document is intended to serve as a guideline to setup Interlink Networks Secure.XS
Wireless @ Johns Hopkins
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Table of Contents. Cisco Wi Fi Protected Access 2 (WPA 2) Configuration Example
 Table of Contents Wi Fi Protected Access 2 (WPA 2) Configuration Example...1 Document ID: 67134...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...2 Conventions...2 Background Information...2
Table of Contents Wi Fi Protected Access 2 (WPA 2) Configuration Example...1 Document ID: 67134...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...2 Conventions...2 Background Information...2
How to configure MAC authentication on a ProCurve switch
 An HP ProCurve Networking Application Note How to configure MAC authentication on a ProCurve switch Contents 1. Introduction... 3 2. Prerequisites... 3 3. Network diagram... 3 4. Configuring the ProCurve
An HP ProCurve Networking Application Note How to configure MAC authentication on a ProCurve switch Contents 1. Introduction... 3 2. Prerequisites... 3 3. Network diagram... 3 4. Configuring the ProCurve
Configuring Microsoft RADIUS Server and Gx000 Authentication. Configuration Notes. Revision 1.0 February 6, 2003
 Configuring Microsoft RADIUS Server and Gx000 Authentication Configuration Notes Revision 1.0 February 6, 2003 Copyright 2002 Gemtek Systems Holding BV www.gemtek-systems.com Notice Gemtek Systems reserves
Configuring Microsoft RADIUS Server and Gx000 Authentication Configuration Notes Revision 1.0 February 6, 2003 Copyright 2002 Gemtek Systems Holding BV www.gemtek-systems.com Notice Gemtek Systems reserves
Management Software. Web Browser User s Guide AT-S106. For the AT-GS950/48 Gigabit Ethernet Smart Switch. Version 1.0.0. 613-001339 Rev.
 Management Software AT-S106 Web Browser User s Guide For the AT-GS950/48 Gigabit Ethernet Smart Switch Version 1.0.0 613-001339 Rev. A Copyright 2010 Allied Telesis, Inc. All rights reserved. No part of
Management Software AT-S106 Web Browser User s Guide For the AT-GS950/48 Gigabit Ethernet Smart Switch Version 1.0.0 613-001339 Rev. A Copyright 2010 Allied Telesis, Inc. All rights reserved. No part of
Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops
 Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops A wireless network for Faculty and Staff to use with their personal laptops, is available throughout campus with
Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops A wireless network for Faculty and Staff to use with their personal laptops, is available throughout campus with
Network Security Solutions Implementing Network Access Control (NAC)
 Network Security Solutions Implementing Network Access Control (NAC) Tested Solution: Protecting a network with Sophos NAC Advanced and Switches Sophos NAC Advanced is a sophisticated Network Access Control
Network Security Solutions Implementing Network Access Control (NAC) Tested Solution: Protecting a network with Sophos NAC Advanced and Switches Sophos NAC Advanced is a sophisticated Network Access Control
Controller Management
 Controller Management - Setup & Provisioning - 1 PRONTO SERVICE CONTROLLER (PN-CPP-A-1422) 2 PSC Key Features Fully interoperable with IEEE802.11b/g compliant products External AP support and management
Controller Management - Setup & Provisioning - 1 PRONTO SERVICE CONTROLLER (PN-CPP-A-1422) 2 PSC Key Features Fully interoperable with IEEE802.11b/g compliant products External AP support and management
UTM10 in multi-ssid, multi-vlan network with WMS5316. Network diagram
 UTM10 in multi-ssid, multi-vlan network with WMS5316 This document describes how to use the UTM10 (unified threat management system) and WMS5316 (wireless management system) to create a multi-vlan, multi-ssid
UTM10 in multi-ssid, multi-vlan network with WMS5316 This document describes how to use the UTM10 (unified threat management system) and WMS5316 (wireless management system) to create a multi-vlan, multi-ssid
Mobility System Software Quick Start Guide
 Mobility System Software Quick Start Guide Version 8.0 P/N 530-041387 Rev.05 Table of Contents About this Guide Using the Web Quick Start (WLC2, WLC8, WLC200,WLC800R, and WLC880R) Remotely Configuring
Mobility System Software Quick Start Guide Version 8.0 P/N 530-041387 Rev.05 Table of Contents About this Guide Using the Web Quick Start (WLC2, WLC8, WLC200,WLC800R, and WLC880R) Remotely Configuring
ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3
 ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3 TO THE Overview EXHIBIT T to Amendment No. 60 Secure Wireless Network Services are based on the IEEE 802.11 set of standards and meet the Commonwealth of Virginia
ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3 TO THE Overview EXHIBIT T to Amendment No. 60 Secure Wireless Network Services are based on the IEEE 802.11 set of standards and meet the Commonwealth of Virginia
eduroam wireless setup guide for Windows 7, XP and Vista
 Information Technology Services eduroam wireless setup guide for Windows 7, XP and Vista Configuring Windows to connect to the eduroam wireless network June 2011 Introduction This document describes how
Information Technology Services eduroam wireless setup guide for Windows 7, XP and Vista Configuring Windows to connect to the eduroam wireless network June 2011 Introduction This document describes how
Management Authentication using Windows IAS as a Radius Server
 Management Authentication using Windows IAS as a Radius Server OVERVIEW: In this we are using Radius server Windows IAS as a backend server for the management authentication for the controller. When the
Management Authentication using Windows IAS as a Radius Server OVERVIEW: In this we are using Radius server Windows IAS as a backend server for the management authentication for the controller. When the
Design and Implementation Guide. Apple iphone Compatibility
 Design and Implementation Guide Apple iphone Compatibility Introduction Security in wireless LANs has long been a concern for network administrators. While securing laptop devices is well understood, new
Design and Implementation Guide Apple iphone Compatibility Introduction Security in wireless LANs has long been a concern for network administrators. While securing laptop devices is well understood, new
Step-by-step Guide for Configuring Cisco ACS server as the Radius with an External Windows Database
 Step-by-step Guide for Configuring Cisco ACS server as the Radius with an External Windows Database Table of Contents: INTRODUCTION:... 2 GETTING STARTED:... 3 STEP-1: INTERFACE CONFIGURATION... 4 STEP-2:
Step-by-step Guide for Configuring Cisco ACS server as the Radius with an External Windows Database Table of Contents: INTRODUCTION:... 2 GETTING STARTED:... 3 STEP-1: INTERFACE CONFIGURATION... 4 STEP-2:
Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops
 Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops A wireless network for Students to use with their personal laptops, is available throughout campus with the SSID NCC-STUDENT. This network
Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops A wireless network for Students to use with their personal laptops, is available throughout campus with the SSID NCC-STUDENT. This network
Extension Wireless Access (EWA) v2.0
 Extension Wireless Access (EWA) v2.0 The Extension Wireless Network (EWA) is broken into two parts: the public network (vce pub) and the private network (vce wlan). The public network (vce pub) is secured
Extension Wireless Access (EWA) v2.0 The Extension Wireless Network (EWA) is broken into two parts: the public network (vce pub) and the private network (vce wlan). The public network (vce pub) is secured
System 800xA Operations Operator Workplace Support for Mobile Devices
 System 800xA Operations Operator Workplace Support for Mobile Devices System Version 6.0 Power and productivity for a better world TM System 800xA Operations Operator Workplace Support for Mobile Devices
System 800xA Operations Operator Workplace Support for Mobile Devices System Version 6.0 Power and productivity for a better world TM System 800xA Operations Operator Workplace Support for Mobile Devices
Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro)
 Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
On-boarding and Provisioning with Cisco Identity Services Engine
 On-boarding and Provisioning with Cisco Identity Services Engine Secure Access How-To Guide Series Date: April 2012 Author: Imran Bashir Table of Contents Overview... 3 Scenario Overview... 4 Dual SSID
On-boarding and Provisioning with Cisco Identity Services Engine Secure Access How-To Guide Series Date: April 2012 Author: Imran Bashir Table of Contents Overview... 3 Scenario Overview... 4 Dual SSID
Setting up SJUMobile (Wireless Internet Access for personal devices)
 Setting up SJUMobile (Wireless Internet Access for personal devices) St. John s University provides wireless internet access to personal devices for all current registered students. To setup a connection,
Setting up SJUMobile (Wireless Internet Access for personal devices) St. John s University provides wireless internet access to personal devices for all current registered students. To setup a connection,
Wireless LAN Client Configuration Guide for Windows 7 2015. Configuring 802.1X Authentication Client for Windows 7
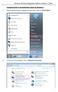 Configuring 802.1X Authentication Client for Windows 7 1. Click on Windows button to display the main menu. Click on Control Panel. 1.1 In the Control Panel window, click on Network and Internet. 1 1.2
Configuring 802.1X Authentication Client for Windows 7 1. Click on Windows button to display the main menu. Click on Control Panel. 1.1 In the Control Panel window, click on Network and Internet. 1 1.2
How to Configure Web Authentication on a ProCurve Switch
 An HP ProCurve Networking Application Note How to Configure Web Authentication on a ProCurve Switch Contents 1. Introduction... 2 2. Prerequisites... 2 3. Network diagram... 2 4. Configuring the ProCurve
An HP ProCurve Networking Application Note How to Configure Web Authentication on a ProCurve Switch Contents 1. Introduction... 2 2. Prerequisites... 2 3. Network diagram... 2 4. Configuring the ProCurve
Connecting to the University Wireless Network
 Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18
 Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Wireless Robust Security Networks: Keeping the Bad Guys Out with 802.11i (WPA2)
 Wireless Robust Security Networks: Keeping the Bad Guys Out with 802.11i (WPA2) SUNY Technology Conference June 21, 2011 Bill Kramp FLCC Network Administrator Copyright 2011 William D. Kramp All Rights
Wireless Robust Security Networks: Keeping the Bad Guys Out with 802.11i (WPA2) SUNY Technology Conference June 21, 2011 Bill Kramp FLCC Network Administrator Copyright 2011 William D. Kramp All Rights
Linksys WAP300N. User Guide
 User Guide Contents Contents Overview Package contents 1 Back view 1 Bottom view 2 How to expand your home network 3 What is a network? 3 How to expand your home network 3 Where to find more help 3 Operating
User Guide Contents Contents Overview Package contents 1 Back view 1 Bottom view 2 How to expand your home network 3 What is a network? 3 How to expand your home network 3 Where to find more help 3 Operating
ICT DEPARTMENT. Windows 7. Wireless Authentication Procedures for Windows 7 & 8 Users For Linux and windows XP users visit ICT office
 ICT DEPARTMENT Wireless Authentication Procedures for Windows 7 & 8 Users For Linux and windows XP users visit ICT office Requirements: 1. Wireless enable laptop with Valid Anti-Virus 2. Configure your
ICT DEPARTMENT Wireless Authentication Procedures for Windows 7 & 8 Users For Linux and windows XP users visit ICT office Requirements: 1. Wireless enable laptop with Valid Anti-Virus 2. Configure your
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR
 INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows Vista operating systems ΥΠΣ ΕΔ/56 Last review
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows Vista operating systems ΥΠΣ ΕΔ/56 Last review
Wireless Setup for Windows 8
 Wireless Setup for Windows 8 Wireless Names KUEMPLOYEE Only Kettering Staff and Faculty can connect to this wireless o Network Access, Internet Access, Printer Access, License Manager KUSTUDENT Active
Wireless Setup for Windows 8 Wireless Names KUEMPLOYEE Only Kettering Staff and Faculty can connect to this wireless o Network Access, Internet Access, Printer Access, License Manager KUSTUDENT Active
How to configure your Thomson SpeedTouch 780WL for ADSL2+
 How to configure your Thomson SpeedTouch 780WL for ADSL2+ Connecting up your router This guide assumes that you have successfully: unpacked your router connected it up to your phone socket using the DSL
How to configure your Thomson SpeedTouch 780WL for ADSL2+ Connecting up your router This guide assumes that you have successfully: unpacked your router connected it up to your phone socket using the DSL
Web Authentication Application Note
 What is Web Authentication? Web Authentication Application Note Web authentication is a Layer 3 security feature that causes the router to not allow IP traffic (except DHCP-related packets) from a particular
What is Web Authentication? Web Authentication Application Note Web authentication is a Layer 3 security feature that causes the router to not allow IP traffic (except DHCP-related packets) from a particular
Abstract. Avaya Solution & Interoperability Test Lab
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Enterasys Wireless Access Point 3000 (RBT3K-AG) to Support Avaya IP Office, Avaya IP Wireless Telephones and Avaya Phone Manager
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Enterasys Wireless Access Point 3000 (RBT3K-AG) to Support Avaya IP Office, Avaya IP Wireless Telephones and Avaya Phone Manager
Deployment Guide: Cisco Guest Access Using the Cisco Wireless LAN Controller
 Deployment Guide: Cisco Guest Access Using the Cisco Wireless LAN Controller August 2006 Contents Overview section on page 1 Configuring Guest Access on the Cisco Wireless LAN Controller section on page
Deployment Guide: Cisco Guest Access Using the Cisco Wireless LAN Controller August 2006 Contents Overview section on page 1 Configuring Guest Access on the Cisco Wireless LAN Controller section on page
Module 6. Configuring and Troubleshooting Routing and Remote Access. Contents:
 Configuring and Troubleshooting Routing and Remote Access 6-1 Module 6 Configuring and Troubleshooting Routing and Remote Access Contents: Lesson 1: Configuring Network Access 6-3 Lesson 2: Configuring
Configuring and Troubleshooting Routing and Remote Access 6-1 Module 6 Configuring and Troubleshooting Routing and Remote Access Contents: Lesson 1: Configuring Network Access 6-3 Lesson 2: Configuring
6. After connecting reopen the wireless connections window. Right click on RamNet and select properties. Page 2 of 7
 Networking & Telecommunications 001 Allegheny Hall 610-436-3535 West Chester University fax: 610-436-3110 West Chester, Pennsylvania 1938 http://www.wcupa.edu/infoservices/commservices/ RamNet Wireless
Networking & Telecommunications 001 Allegheny Hall 610-436-3535 West Chester University fax: 610-436-3110 West Chester, Pennsylvania 1938 http://www.wcupa.edu/infoservices/commservices/ RamNet Wireless
Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students.
 Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
BASIC INSTRUCTIONS TO CONFIGURE ZYXEL P8701T CPE USING THE WEB INTERFACE
 BASIC INSTRUCTIONS TO CONFIGURE ZYXEL P8701T CPE USING THE WEB INTERFACE 12/11/2012 Index 1 INTRODUCTION... 1-1 2 FACTORY DEFAULT SETTINGS... 2-1 3 CPE BASIC OPERATIONS... 3-1 3.1 PASSWORD MODIFICATION...
BASIC INSTRUCTIONS TO CONFIGURE ZYXEL P8701T CPE USING THE WEB INTERFACE 12/11/2012 Index 1 INTRODUCTION... 1-1 2 FACTORY DEFAULT SETTINGS... 2-1 3 CPE BASIC OPERATIONS... 3-1 3.1 PASSWORD MODIFICATION...
SecureW2 Client for Windows User Guide. Version 3.1
 SecureW2 Client for Windows User Guide Version 3.1 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright
SecureW2 Client for Windows User Guide Version 3.1 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright
Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services a...
 1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
Configuring a Windows 2003 Server for IAS
 Configuring a Windows 2003 Server for IAS When setting up a Windows 2003 server to function as an IAS server for our demo environment we will need the server to serve several functions. First of all we
Configuring a Windows 2003 Server for IAS When setting up a Windows 2003 server to function as an IAS server for our demo environment we will need the server to serve several functions. First of all we
Step-by-Step Secure Wireless for Home / Small Office and Small Organizations
 Step-by-Step Secure Wireless for Home / Small Office and Small Organizations Microsoft Corporation Published: October 2005 Author: Brit Weston Editor: Allyson Adley Abstract This white paper presents two
Step-by-Step Secure Wireless for Home / Small Office and Small Organizations Microsoft Corporation Published: October 2005 Author: Brit Weston Editor: Allyson Adley Abstract This white paper presents two
WiFi troubleshooting. How s your WiFi signal? Android WiFi settings. ios WiFi settings
 1 WiFi troubleshooting How s your WiFi signal? If your connection appears to keep dropping off: check in your WiFi settings that you added @kent.ac.uk to your username, and entered your password correctly.
1 WiFi troubleshooting How s your WiFi signal? If your connection appears to keep dropping off: check in your WiFi settings that you added @kent.ac.uk to your username, and entered your password correctly.
Connecting to the Rovernet WPA2 Secured Wireless Network with Windows 7
 Connecting to the Rovernet WPA2 Secured Wireless Network with Windows 7 Configuring your wireless device to use WPA2 takes a few minutes. You will, however, need to meet the following system requirements
Connecting to the Rovernet WPA2 Secured Wireless Network with Windows 7 Configuring your wireless device to use WPA2 takes a few minutes. You will, however, need to meet the following system requirements
Preparing the Computers for TCP/IP Networking
 Configuration Preparing the Computers for TCP/IP Networking Configuring Windows 98, and ME for TCP/IP Networking Verifying TCP/IP Properties Configuring Windows 2000 or XP for IP Networking Install or
Configuration Preparing the Computers for TCP/IP Networking Configuring Windows 98, and ME for TCP/IP Networking Verifying TCP/IP Properties Configuring Windows 2000 or XP for IP Networking Install or
A Division of Cisco Systems, Inc. GHz 2.4 802.11g. Wireless-G. PCI Adapter with RangeBooster. User Guide WIRELESS WMP54GR. Model No.
 A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G PCI Adapter with RangeBooster User Guide Model No. WMP54GR Copyright and Trademarks Specifications are subject to change without notice.
A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G PCI Adapter with RangeBooster User Guide Model No. WMP54GR Copyright and Trademarks Specifications are subject to change without notice.
How to connect to VUWiFi
 Wireless Registration Instructions Windows XP How to connect to VUWiFi 1. The first step in setting up your wireless card for VUWiFi is to open your Network Connections window. You can find this by going
Wireless Registration Instructions Windows XP How to connect to VUWiFi 1. The first step in setting up your wireless card for VUWiFi is to open your Network Connections window. You can find this by going
HP M220 802.11n Access Point Configuration and Administration Guide
 HP M220 802.11n Access Point Configuration and Administration Guide HP Part Number: 5998-3140 Published: September 2012 Edition: 1 Copyright 2012 Hewlett-Packard Development Company, L.P. The information
HP M220 802.11n Access Point Configuration and Administration Guide HP Part Number: 5998-3140 Published: September 2012 Edition: 1 Copyright 2012 Hewlett-Packard Development Company, L.P. The information
netld External Authentication Setup Guide
 netld External Authentication Setup Guide Overview netld is able to integrate with authentication servers such as Active Directory and FreeRADIUS. When using this integration, you do not need to create
netld External Authentication Setup Guide Overview netld is able to integrate with authentication servers such as Active Directory and FreeRADIUS. When using this integration, you do not need to create
Wi- Fi settings for Windows XP
 Wi- Fi settings for Windows XP On the TU/e there are four Wlan network names or SSID's available. TUE-WPA2 2 The TUE-WPA2 network has WPA2 encryption. This network can be used by both TU/e students and
Wi- Fi settings for Windows XP On the TU/e there are four Wlan network names or SSID's available. TUE-WPA2 2 The TUE-WPA2 network has WPA2 encryption. This network can be used by both TU/e students and
Connecting to UNOSECURE using Windows 7
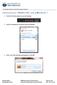 Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
How to configure 802.1X authentication with a Windows XP or Vista supplicant
 An HP ProCurve Networking Application Note How to configure 802.1X authentication with a Windows XP or Vista supplicant Contents 1. Introduction... 2 2. Prerequisites... 2 3. Network diagram... 2 4. Configuring
An HP ProCurve Networking Application Note How to configure 802.1X authentication with a Windows XP or Vista supplicant Contents 1. Introduction... 2 2. Prerequisites... 2 3. Network diagram... 2 4. Configuring
AeroLab Wireless Network Code of Conduct. Connecting to the AeroLab Wireless Network
 AeroLab Wireless Network Code of Conduct The AeroLab wireless network is intended for academic use only. Any use of the wireless network for BitTorrent or other Peer-to-Peer file sharing is strictly prohibited.
AeroLab Wireless Network Code of Conduct The AeroLab wireless network is intended for academic use only. Any use of the wireless network for BitTorrent or other Peer-to-Peer file sharing is strictly prohibited.
Immotec Systems, Inc. SQL Server 2005 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
The Importance of Wireless Security
 The Importance of Wireless Security Because of the increasing popularity of wireless networks, there is an increasing need for security. This is because unlike wired networks, wireless networks can be
The Importance of Wireless Security Because of the increasing popularity of wireless networks, there is an increasing need for security. This is because unlike wired networks, wireless networks can be
CruzNet Secure Set-Up Instructions for Windows Vista
 CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
StarMOBILE Network Configuration Guide. A guide to configuring your StarMOBILE system for networking
 StarMOBILE Network Configuration Guide A guide to configuring your StarMOBILE system for networking INTRODUCTION... 3 BEFORE YOU BEGIN... 3 1) CONFIRM YOU HAVE THE LATEST SOFTWARE... 3 2) INSTALL THE STARMOBILE
StarMOBILE Network Configuration Guide A guide to configuring your StarMOBILE system for networking INTRODUCTION... 3 BEFORE YOU BEGIN... 3 1) CONFIRM YOU HAVE THE LATEST SOFTWARE... 3 2) INSTALL THE STARMOBILE
Installation Guides - Information required for connection to the Goldfields Institute s (GIT) Wireless Network
 Installation Guides - Information required for connection to the Goldfields Institute s (GIT) Wireless Network Wireless Network Names and Credentials There are two wireless networks operating at the Goldfields
Installation Guides - Information required for connection to the Goldfields Institute s (GIT) Wireless Network Wireless Network Names and Credentials There are two wireless networks operating at the Goldfields
Particularities of security design for wireless networks in small and medium business (SMB)
 Revista Informatica Economică, nr. 4 (44)/2007 93 Particularities of security design for wireless networks in small and medium business (SMB) Nicolae TOMAI, Cluj-Napoca, Romania, [email protected]
Revista Informatica Economică, nr. 4 (44)/2007 93 Particularities of security design for wireless networks in small and medium business (SMB) Nicolae TOMAI, Cluj-Napoca, Romania, [email protected]
StoneGate Installation Guide
 SMC FW IPS SSL VPN VPN StoneGate Installation Guide SOHO Firewalls Updated for StoneGate Management Center 5.0.0 Legal Information End-User License Agreement The use of the products described in these
SMC FW IPS SSL VPN VPN StoneGate Installation Guide SOHO Firewalls Updated for StoneGate Management Center 5.0.0 Legal Information End-User License Agreement The use of the products described in these
