Technical Report - Practical measurements of Security Systems
|
|
|
- Winifred Craig
- 3 years ago
- Views:
Transcription
1 A Short Study on Security Indicator Interfaces Technical Report UCSC-WASP November 2015 D J Capelis mail@capelis.dj Working-group on Applied Security and Privacy Storage Systems Research Center University of California, Santa Cruz Santa Cruz, CA This work was supported by
2 Abstract This technical report documents findings from a preliminary study on how users react to security indicators from a trusted hardware output channel. We recorded how a mixture of test messages affected users interactions with a simulated web form asking for account credentials. In this report we present the data and draw some conclusions on how this experiment informs trusted platform interface design, and specifically report findings relevant to the interface from our Lockbox project.
3 1 Introduction End-users frequently disregard, respond erratically or don t even notice the interfaces that are supposed to help them protect their machine. Here we examine hardware interfaces that provide end-users with an auxiliary security screen which displays information from a hardware security system. We are interested in finding out how users react to such a screen and determine whether or not such an interface allows user to make good security decisions. I designed an experiment where users were prompted to log in to a series of login forms. The screen displayed various iterations of text and we were able to test user s error rates as well as response times to various security displays. I observed both the timing information and the error rates of each screen. With statistical analysis, we draw several conclusions from the data. These supported some of our interface design assumptions, provide insight into phishing type attacks on these types of interfaces and suggest how the hardware should respond when there is no trusted channel present. These conclusions validated portions of the LockBox design as well as suggest possible tweaks for further accuracy in the future. 2 Experimental Design There are two very important metrics that determine success for a security system like this: Accuracy The user s ability to come to the correct conclusion. Cognitive Overhead How much thinking the user is required to do to come to a conclusion. While many, might consider the first metric to be most important, the second can be just as, or more, important. The amount of cognitive overhead a user experiences determines their willingness to use the system at all. Since the accuracy rate of a system that a user doesn t use is zero, it could be necessary to trade accuracy for lower cognitive overhead. That said, this data does not support the existence of a tradeoff between these two variables in this particular interface. Our results are consistent with the hypothesis that interfaces with lower cognitive overhead are also more accurate. Accuracy metrics were gathered by recording whether a user reached the correct decision. Tracking cognitive overhead was more difficult. Since there no neuroscientist or MRI machine was present in our lab, I recorded time between responses. This seems like a reasonable metric for cognitive overhead, but simply observing how quickly someone reacts is an indirect measure. 2.1 Subjects 20 subjects participated in the study. They were recruited from the University of California, Santa Cruz campus and Silicon Valley. The academic participants from UCSC s Computer Science department consisted of one professor, one undergraduate and five graduate students. In addition, two undergraduates and four graduate students participated from other departments at UCSC. Another was studying an unrelated field at Stanford. The remaining six participants worked full time for various Silicon Valley tech companies. The subjects ranged from 20 to 50 years of age. All were familiar with technology, but not all had chosen it as their vocation. Most were students. In general, the subjects were both young and very familiar with computers. 1
4 2.2 Pilot Study The first six participants were comprised the pilot subjects for the project. When it was found the pilot study was yielding valid data and the methodology appeared to be sufficient, we incorporated data from these subjects into our main study. The methodology did not change after the pilot study. At the conclusion, we verified that the pilot study participants did not produce significantly different results than the remaining users. 2.3 Test Procedure The test began by providing the subject with a series of instructions. Included in these instructions were information on the test, the methodology and the format. Users were given a username and password and shown an exact picture of contents of the screen they should accept. The users then moved on to a series of login forms where they were either able to login, or press a button that stated the form was insecure. The auxiliary security screen would change at each page and the user s responses where tracked. About 2/3rds of the way through the test, users were told that instead of different types of screens, they would only see two screens: the proper screen and a screen that said the input was insecure. At the conclusion of the test, the users provided feedback on a paper survey. In the first part of the study, the auxiliary screen displayed one of the following readouts during the study: A screen that read firefox. Users were instructed that this screen meant their input was secure. A screen that read Firefox. With the first letter capitalized. Users were instructed to press the button that said the form was insecure if the auxiliary security screen deviated from the lower case firefox readout. A screen that read f1refox. With the first i replaced by a 1. A screen that read internet explorer. The name of a complete different, but related program. A blank screen. In the second half of the test, users were given a screen that read out -INPUT INSECURE-. This interface of affirming an insecure state was compared to previous results where the insecure state was discovered by the lack of a proper security notification on the auxiliary screen. During the experiment, the subject sat at a computer terminal with a researcher seated behind them jotting observations on a post-it. The researcher had a view of the screen, the auxiliary screen and the user s input. Users did not appear to pick up on any signals from the observer as several thought they were doing badly when they were doing well or well when they were doing badly. The observer helped facilitate this neutrality by wearing a somber expression and a white lab coat. 3 Data The first 10 questions were screened out of the data as a training period. Since the user responded slowly at first and slowly grew better through the first 10 responses, these responses were screened out as not representative. In addition, we also screened out outliers where users took greater than 30 seconds. This happened only on a few datapoints. The observation notes confirmed the majority of these instances occurred when the subject paused during the test to ask a question or receive clarification. 2
5 3.1 Cognitive Overhead Metrics Cognitive overhead was based on a measure of time between responses. We present both the average responses in graph form as well as a few statistically significant statements that can be made about users cognitive overheads in one part of the experiment vs. another. Figure 1: Graph of the averages Figure 2: Graph of the averages, showing negative user responses shaded in blue and the excluded section of the results The following differences were all statistically significant: Users were quicker to respond during the phase of the test when the insecure state was affirmatively presented. (p=.029) Users were quicker to determine that the system was insecure when presented with an explicit warning instead of a blank screen. (p=.017) Users were quicker to respond after the training period. (p.01) 3.2 Accuracy Rates We present both raw and adjusted accuracy rates. The adjusted rates exclude data from three participants who produced particularly erratic and noisy data. These three participants either 3
6 didn t correctly understand the experiment or mistakenly assumed that one of the fake screens was correct and the right screen was fake through all or a portion of the experiment. (People seemed inclined to prefer a capital F in their Firefox and would actually begin reject the lowercase one even though they were prompted to use that instead.) These types of mistakes would be unlikely to occur in a design like LockBox s, so we excluded these particular cases in the adjusted results. Figure 3: The accuracy rate compared to baseline for each security screen using raw data Figure 4: The accuracy rate compared to baseline for each security screen using adjusted data 4
7 4 Findings While security interfaces are tricky and often involve high rates of user error, our findings yield two different findings security interfaces should take into account to increase their success rate. First, avoid interfaces which allow attackers to pick any strings on the security indicator. Both the accuracy and cognitive overhead data that users were faster and more accurate when they did not have to distinguish between various similar looking screens to determine which one was correct. This data supports the design approach made in LockBox to present users only with strings that they chose if a trusted channel is secure, or none at all. This design decision sets the interface in LockBox apart from interfaces which allow attackers to present users with similar name, such as in browser address bars in web browsers. The problems and challenges that present themselves for that type of interface are much greater. Second, when the system is in an insecure mode, affirmatively display this information to the user. A blank screen was less effective than an explicit message. Users were both faster and more accurate if the screen displayed an explicit warning that their input was insecure. This is not as obvious a conclusion as it might seem. Having the security screen always display one message or another runs a risk of user fatigue in the long term. A longer term study needs to be done to determine whether affirmative displays of insecure modes continue to result in increased speed and accuracy over the long term. However, the short term data in this study is consistent with the idea that explicit notification helps users reach faster determinations. These findings provide some hope that while security interfaces have often fallen short of providing the tools users need to effectively make good security decisions, better interfaces are possible. Accuracy rates increase significantly when interfaces avoid specific problems. Many existing systems have not been designed to avoid these mistakes, so continued poor results for these systems should not come as a surprise. With further study, security interfaces may one day achieve significantly higher levels of accuracy at reduced cognitive overhead. 5 Acknowledgements This material is based upon work supported by the National Science Foundation under Grant No Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation. 5
New Help Desk Ticketing System
 New Help Desk Ticketing System Starting Monday, November 30, 2009 at 6 am the University will be going live with their new help desk ticketing system. The website to access the new ticketing system is
New Help Desk Ticketing System Starting Monday, November 30, 2009 at 6 am the University will be going live with their new help desk ticketing system. The website to access the new ticketing system is
Office of Fleet and Asset Management (OFAM) www.dgs.ca.gov/ofam (Reserve a State Vehicle) Online Vehicle Reservation Instructions
 Office of Fleet and Asset Management (OFAM) www.dgs.ca.gov/ofam (Reserve a State Vehicle) Online Vehicle Reservation Instructions Revised March 2, 2012 1 You must be an active California State Employee
Office of Fleet and Asset Management (OFAM) www.dgs.ca.gov/ofam (Reserve a State Vehicle) Online Vehicle Reservation Instructions Revised March 2, 2012 1 You must be an active California State Employee
Fan Fu. Usability Testing of Cloud File Storage Systems. A Master s Paper for the M.S. in I.S. degree. April, 2013. 70 pages. Advisor: Robert Capra
 Fan Fu. Usability Testing of Cloud File Storage Systems. A Master s Paper for the M.S. in I.S. degree. April, 2013. 70 pages. Advisor: Robert Capra This paper presents the results of a usability test involving
Fan Fu. Usability Testing of Cloud File Storage Systems. A Master s Paper for the M.S. in I.S. degree. April, 2013. 70 pages. Advisor: Robert Capra This paper presents the results of a usability test involving
Web Help Desk - EASD Technology Support
 Web Help Desk - EASD Technology Support EASDʼs Technology Services department has instituted a new tech request database system called Web Help Desk. This help desk system will now allow staff members
Web Help Desk - EASD Technology Support EASDʼs Technology Services department has instituted a new tech request database system called Web Help Desk. This help desk system will now allow staff members
Accessing vlabs using the VMware Horizon View Client for OSX
 Accessing vlabs using the VMware Horizon View Client for OSX This document will demonstrate how to download, install, and connect to a virtual lab desktop from a personal Mac OSX computer using the VMware
Accessing vlabs using the VMware Horizon View Client for OSX This document will demonstrate how to download, install, and connect to a virtual lab desktop from a personal Mac OSX computer using the VMware
How To Register For A Course Online
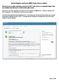 How to Register and Pay for BEST Center Classes Online Welcome to our new online registration system for The BEST Center at Genesee Community College! All of our scheduled noncredit classes are listed
How to Register and Pay for BEST Center Classes Online Welcome to our new online registration system for The BEST Center at Genesee Community College! All of our scheduled noncredit classes are listed
A Guide to the Tufts Network School of Arts and Sciences School of Engineering Fletcher School of Law and Diplomacy
 A Guide to the Tufts Network School of Arts and Sciences School of Engineering Fletcher School of Law and Diplomacy What the Tufts Network has to Offer The Tufts network allows you access to your personal
A Guide to the Tufts Network School of Arts and Sciences School of Engineering Fletcher School of Law and Diplomacy What the Tufts Network has to Offer The Tufts network allows you access to your personal
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
MANUAL USER GUIDE FOR EMR PRIMARY HEALTH CARE SYSTEM
 MANUAL USER GUIDE FOR EMR PRIMARY HEALTH CARE SYSTEM By Faustin GASHAYIJA Version 1.0 1 Table of contents Contents Table of contents... 2 Browser... 4 Log in openmrs website... 4 OpenMRS welcome page...
MANUAL USER GUIDE FOR EMR PRIMARY HEALTH CARE SYSTEM By Faustin GASHAYIJA Version 1.0 1 Table of contents Contents Table of contents... 2 Browser... 4 Log in openmrs website... 4 OpenMRS welcome page...
Reference Guide for WebCDM Application 2013 CEICData. All rights reserved.
 Reference Guide for WebCDM Application 2013 CEICData. All rights reserved. Version 1.2 Created On February 5, 2007 Last Modified August 27, 2013 Table of Contents 1 SUPPORTED BROWSERS... 3 1.1 INTERNET
Reference Guide for WebCDM Application 2013 CEICData. All rights reserved. Version 1.2 Created On February 5, 2007 Last Modified August 27, 2013 Table of Contents 1 SUPPORTED BROWSERS... 3 1.1 INTERNET
WebSphere Application Server security auditing
 Copyright IBM Corporation 2008 All rights reserved IBM WebSphere Application Server V7 LAB EXERCISE WebSphere Application Server security auditing What this exercise is about... 1 Lab requirements... 1
Copyright IBM Corporation 2008 All rights reserved IBM WebSphere Application Server V7 LAB EXERCISE WebSphere Application Server security auditing What this exercise is about... 1 Lab requirements... 1
Student Instructions for Registration and Login
 Student Instructions for Registration and Login Before you go online to register be sure you have: - A valid e-mail address - The MyMathLab Course ID from your instructor - A student access code, which
Student Instructions for Registration and Login Before you go online to register be sure you have: - A valid e-mail address - The MyMathLab Course ID from your instructor - A student access code, which
UHC-iEnroll Offline Software Frequently Asked Questions
 UHC-iEnroll Offline Software Frequently Asked Questions Q. How do I know if I am picking the right application from the drop down my paper form doesn t look like this? Please contact the Producer Help
UHC-iEnroll Offline Software Frequently Asked Questions Q. How do I know if I am picking the right application from the drop down my paper form doesn t look like this? Please contact the Producer Help
Xerox Multifunction Devices. Verify Device Settings via the Configuration Report
 Xerox Multifunction Devices Customer Tips March 15, 2007 This document applies to these Xerox products: X WC 4150 X WCP 32/40 X WCP 35/45/55 X WCP 65/75/90 X WCP 165/175 X WCP 232/238 X WCP 245/255 X WCP
Xerox Multifunction Devices Customer Tips March 15, 2007 This document applies to these Xerox products: X WC 4150 X WCP 32/40 X WCP 35/45/55 X WCP 65/75/90 X WCP 165/175 X WCP 232/238 X WCP 245/255 X WCP
CECH Virtual Lab Guide Windows 7/Vista Edition
 CECH Virtual Lab Guide Windows 7/Vista Edition Introduction: This guide is a step-by-step walkthrough of installing, configuring, and using the VMware Horizon View Client to access the University of Cincinnati
CECH Virtual Lab Guide Windows 7/Vista Edition Introduction: This guide is a step-by-step walkthrough of installing, configuring, and using the VMware Horizon View Client to access the University of Cincinnati
How to Access the Economics Undergraduate Lab
 How to Access the Economics Undergraduate Lab Please note that only students in a few selected courses will be able to activate their Economics Undergraduate Lab account. If this account is not listed
How to Access the Economics Undergraduate Lab Please note that only students in a few selected courses will be able to activate their Economics Undergraduate Lab account. If this account is not listed
Making A Work Order IT Services
 Making A Work Order IT Services Getting There Using a working computer with internet access, open your Browser (Internet Explorer, Firefox, etc.) Login to the KACE Service Center by typing in http://kace.coastalbend.edu
Making A Work Order IT Services Getting There Using a working computer with internet access, open your Browser (Internet Explorer, Firefox, etc.) Login to the KACE Service Center by typing in http://kace.coastalbend.edu
DataDirector Getting Started
 DataDirector Getting Started LOGIN Log into the DataDirector website: https://www.achievedata.com/yourdistrictname User Name: New Password: Enter your User Name and Password o After login, you may need
DataDirector Getting Started LOGIN Log into the DataDirector website: https://www.achievedata.com/yourdistrictname User Name: New Password: Enter your User Name and Password o After login, you may need
HOW TO USE OIT EMAIL VIA THE WEB
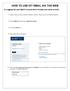 HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
(Refer Slide Time: 01:52)
 Software Engineering Prof. N. L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture - 2 Introduction to Software Engineering Challenges, Process Models etc (Part 2) This
Software Engineering Prof. N. L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture - 2 Introduction to Software Engineering Challenges, Process Models etc (Part 2) This
Virtual Owl. Guide for Windows. University Information Technology Services. Training, Outreach, Learning Technologies & Video Production
 Virtual Owl Guide for Windows University Information Technology Services Training, Outreach, Learning Technologies & Video Production Copyright 2015 KSU Division of University Information Technology Services
Virtual Owl Guide for Windows University Information Technology Services Training, Outreach, Learning Technologies & Video Production Copyright 2015 KSU Division of University Information Technology Services
MS InfoPath 2003 MS InfoPath 2007 Microsoft Office InfoPath 2003 minimally runs on the following operating systems:
 8. PREPARING AND TRANSMITTING EDGARLITE SUBMISSIONS 8.1 Purpose EDGARLite is an application that uses intelligent forms to aid in the construction of filings to be submitted to EDGAR. Each EDGARLite form
8. PREPARING AND TRANSMITTING EDGARLITE SUBMISSIONS 8.1 Purpose EDGARLite is an application that uses intelligent forms to aid in the construction of filings to be submitted to EDGAR. Each EDGARLite form
You need to be assigned and logged in to the system by the Records Management Service in order to use it.
 Guidance for using the Records Management Service software The software can be used to undertake the following tasks:- 1. Sending information about the boxes to be transferred to the Records Centre. 2.
Guidance for using the Records Management Service software The software can be used to undertake the following tasks:- 1. Sending information about the boxes to be transferred to the Records Centre. 2.
Nurse and Midwifery Career Long eportfolio summary guides: 1) Key functions: Getting started, logging on and moving around
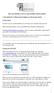 Nurse and Midwifery Career Long eportfolio summary guides: 1) Key functions: Getting started, logging on and moving around Getting started In order to log on to the eportfolio you will need your username
Nurse and Midwifery Career Long eportfolio summary guides: 1) Key functions: Getting started, logging on and moving around Getting started In order to log on to the eportfolio you will need your username
Software Requirements Specification
 METU DEPARTMENT OF COMPUTER ENGINEERING Software Requirements Specification SNMP Agent & Network Simulator Mustafa İlhan Osman Tahsin Berktaş Mehmet Elgin Akpınar 05.12.2010 Table of Contents 1. Introduction...
METU DEPARTMENT OF COMPUTER ENGINEERING Software Requirements Specification SNMP Agent & Network Simulator Mustafa İlhan Osman Tahsin Berktaş Mehmet Elgin Akpınar 05.12.2010 Table of Contents 1. Introduction...
ITRANS PENDING CLAIMS MAILBOX
 ITRANS PENDING CLAIMS MAILBOX INSTRUCTIONS FOR EAGLESOFT USERS ON HOW TO RETRIEVE PENDING CLAIMS Updated: April 2013 OVERVIEW As of February 20 th, 2012, itrans began to send a message to Dental Offices
ITRANS PENDING CLAIMS MAILBOX INSTRUCTIONS FOR EAGLESOFT USERS ON HOW TO RETRIEVE PENDING CLAIMS Updated: April 2013 OVERVIEW As of February 20 th, 2012, itrans began to send a message to Dental Offices
1. Introduction. 1.1 Purpose of this Document
 1. Introduction 1.1 Purpose of this Document The of the Software Requirements Specification is to outline the requirements for The American Academy's Education With an Elastic Workforce (EW2) product.
1. Introduction 1.1 Purpose of this Document The of the Software Requirements Specification is to outline the requirements for The American Academy's Education With an Elastic Workforce (EW2) product.
Required Virtual Interface Maps to... mgmt0. bridge network interface = mgmt0 wan0. bridge network interface = wan0 mgmt1
 VXOA VIRTUAL APPLIANCE KVM Hypervisor In-Line Deployment (Bridge Mode) 2012 Silver Peak Systems, Inc. Support Limitations In Bridge mode, the virtual appliance only uses mgmt0, wan0, and lan0. This Quick
VXOA VIRTUAL APPLIANCE KVM Hypervisor In-Line Deployment (Bridge Mode) 2012 Silver Peak Systems, Inc. Support Limitations In Bridge mode, the virtual appliance only uses mgmt0, wan0, and lan0. This Quick
Last modified on 03-01-2010 for application version 4.4.4
 Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
Last modified on 03-01-2010 for application version 4.4.4 RemotePC User Manual Table of Contents Introduction... 3 Features... 3 Install the Remote Access Host application... 4 Install the Remote Access
Enterprise Remote Control 5.6 Manual
 Enterprise Remote Control 5.6 Manual Solutions for Network Administrators Copyright 2015, IntelliAdmin, LLC Revision 3/26/2015 http://www.intelliadmin.com Page 1 Table of Contents What is Enterprise Remote
Enterprise Remote Control 5.6 Manual Solutions for Network Administrators Copyright 2015, IntelliAdmin, LLC Revision 3/26/2015 http://www.intelliadmin.com Page 1 Table of Contents What is Enterprise Remote
Pushing the Envelope on Data-Driven Security Awareness Mark T. Chapman CFE CISSP CISM CRISC
 Pushing the Envelope on Data-Driven Security Awareness Mark T. Chapman CFE CISSP CISM CRISC Presentation Overview The Importance of Perspective. The diagram at the right represents the four perspectives
Pushing the Envelope on Data-Driven Security Awareness Mark T. Chapman CFE CISSP CISM CRISC Presentation Overview The Importance of Perspective. The diagram at the right represents the four perspectives
Access Control and Audit Trail Software
 Varian, Inc. 2700 Mitchell Drive Walnut Creek, CA 94598-1675/USA Access Control and Audit Trail Software Operation Manual Varian, Inc. 2002 03-914941-00:3 Table of Contents Introduction... 1 Access Control
Varian, Inc. 2700 Mitchell Drive Walnut Creek, CA 94598-1675/USA Access Control and Audit Trail Software Operation Manual Varian, Inc. 2002 03-914941-00:3 Table of Contents Introduction... 1 Access Control
Accessing the Illinois CRM Report Archive Database
 Accessing the Illinois CRM Report Archive Database Connecting to the Illinois CRM Report Archive Database The Illinois CRM Report Archive is a web-based database. Browsers supported are: Windows: Internet
Accessing the Illinois CRM Report Archive Database Connecting to the Illinois CRM Report Archive Database The Illinois CRM Report Archive is a web-based database. Browsers supported are: Windows: Internet
Remote Access Instructions
 document rev. 8 updated 6/28/2012 Remote Access Instructions Table of Contents... Page 1 Finding the AFS Remote Access links and the AFS home page... 2 First time login with RSA fob (AFS option 1 SSL VPN
document rev. 8 updated 6/28/2012 Remote Access Instructions Table of Contents... Page 1 Finding the AFS Remote Access links and the AFS home page... 2 First time login with RSA fob (AFS option 1 SSL VPN
SoftChalk Cloud and Desire2Learn Quick Guide This document was created with SoftChalk Create 8, available at https://uits.kennesaw.
 SoftChalk Cloud and Desire2Learn Quick Guide This document was created with SoftChalk Create 8, available at https://uits.kennesaw.edu/downloads/ Linking a SoftChalk Cloud Lesson into Desire2Learn Linking
SoftChalk Cloud and Desire2Learn Quick Guide This document was created with SoftChalk Create 8, available at https://uits.kennesaw.edu/downloads/ Linking a SoftChalk Cloud Lesson into Desire2Learn Linking
How to use SURA in three simple steps:
 How to use SURA in three simple steps: Most of SURA s functionality can be accessed through these three steps. 1) Download SURA to your computer Go to the SU Downloads page to obtain the SURA utility.
How to use SURA in three simple steps: Most of SURA s functionality can be accessed through these three steps. 1) Download SURA to your computer Go to the SU Downloads page to obtain the SURA utility.
Remote Desktop Web Access. Using Remote Desktop Web Access
 Remote Desktop Web Access What is RD Web Access? RD Web Access is a Computer Science service that allows you to access department software and machines from your Windows or OS X computer, both on and off
Remote Desktop Web Access What is RD Web Access? RD Web Access is a Computer Science service that allows you to access department software and machines from your Windows or OS X computer, both on and off
DCOM 131-01. Group Project 2: Usability Testing. Usability Test Report. Tim Harris, Zach Beidler, Sara Urner, Kacey Musselman
 0 DCOM 131-01 Group Project 2: Usability Testing Usability Test Report Tim Harris, Zach Beidler, Sara Urner, Kacey Musselman 1 Table of Contents Introduction... 2 Purpose... 2 Heuristic... 3 Participants...
0 DCOM 131-01 Group Project 2: Usability Testing Usability Test Report Tim Harris, Zach Beidler, Sara Urner, Kacey Musselman 1 Table of Contents Introduction... 2 Purpose... 2 Heuristic... 3 Participants...
MANAGED SOFTWARE CENTER USER S GUIDE
 U N I V E R S I T Y O F S O U T H E R N C A L I F O R N I A MANAGED SOFTWARE CENTER USER S GUIDE JANUARY 2015 U N I V E R S I T Y O F S O U T H E R N C A L I F O R N I A 2015 UNIVERSITY OF SOUTHERN CALIFORNIA.
U N I V E R S I T Y O F S O U T H E R N C A L I F O R N I A MANAGED SOFTWARE CENTER USER S GUIDE JANUARY 2015 U N I V E R S I T Y O F S O U T H E R N C A L I F O R N I A 2015 UNIVERSITY OF SOUTHERN CALIFORNIA.
QMB 3302 - Business Analytics CRN 82361 - Fall 2015 W 6:30-9:15 PM -- Lutgert Hall 2209
 QMB 3302 - Business Analytics CRN 82361 - Fall 2015 W 6:30-9:15 PM -- Lutgert Hall 2209 Rajesh Srivastava, Ph.D. Professor and Chair, Department of Information Systems and Operations Management Lutgert
QMB 3302 - Business Analytics CRN 82361 - Fall 2015 W 6:30-9:15 PM -- Lutgert Hall 2209 Rajesh Srivastava, Ph.D. Professor and Chair, Department of Information Systems and Operations Management Lutgert
Optum ID Migration for Provider Express Users
 Introducing Optum ID FREQUENTLY ASKED QUESTIONS Optum ID Migration for Provider Express Users 1. What is Optum ID? A1. Optum ID is a centralized, secure identity management solution that enables a single
Introducing Optum ID FREQUENTLY ASKED QUESTIONS Optum ID Migration for Provider Express Users 1. What is Optum ID? A1. Optum ID is a centralized, secure identity management solution that enables a single
PRECISEMAIL ANTI-SPAM GATEWAY AUTHENTICATION CASE STUDIES
 PRECISEMAIL ANTI-SPAM GATEWAY WHITEPAPER EXECUTIVE SUMMARY The rapid expansion of spam is requiring most sites to implement spam filtering solutions to keep users email boxes from becoming clogged with
PRECISEMAIL ANTI-SPAM GATEWAY WHITEPAPER EXECUTIVE SUMMARY The rapid expansion of spam is requiring most sites to implement spam filtering solutions to keep users email boxes from becoming clogged with
QMB 3302 - Business Analytics CRN 80700 - Fall 2015 T & R 9.30 to 10.45 AM -- Lutgert Hall 2209
 QMB 3302 - Business Analytics CRN 80700 - Fall 2015 T & R 9.30 to 10.45 AM -- Lutgert Hall 2209 Elias T. Kirche, Ph.D. Associate Professor Department of Information Systems and Operations Management Lutgert
QMB 3302 - Business Analytics CRN 80700 - Fall 2015 T & R 9.30 to 10.45 AM -- Lutgert Hall 2209 Elias T. Kirche, Ph.D. Associate Professor Department of Information Systems and Operations Management Lutgert
7. In the boxed unlabeled field, enter the last 4 digits of your Social Security number.
 CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
Guide for Preparing Your Students
 Guide for Preparing Your Students TABLE OF CONTENTS WELCOME TO THE GUIDE FOR PREPARING YOUR STUDENTS. 3 ACTIVITY 1: CREATING A GACOLLEGE411 ACCOUNT. 4 ACTIVITY 2: ACCESSING THE APPLY TO COLLEGE GUIDEWAY
Guide for Preparing Your Students TABLE OF CONTENTS WELCOME TO THE GUIDE FOR PREPARING YOUR STUDENTS. 3 ACTIVITY 1: CREATING A GACOLLEGE411 ACCOUNT. 4 ACTIVITY 2: ACCESSING THE APPLY TO COLLEGE GUIDEWAY
Preparing your Domain to transfer from Go Daddy
 Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
Kaseya 2. Quick Start Guide. for Network Monitor 4.1
 Kaseya 2 VMware Performance Monitor Quick Start Guide for Network Monitor 4.1 June 7, 2012 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private
Kaseya 2 VMware Performance Monitor Quick Start Guide for Network Monitor 4.1 June 7, 2012 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private
Student Employment Website User Guide for Off-Campus Employers
 Student Employment Website User Guide for Off-Campus Employers Student Employment University Hall 255 2197 South University Boulevard Denver, Colorado 80208 Ph: 303.871.6792 Fax: 303.871.2341 Email: stuemp@du.edu
Student Employment Website User Guide for Off-Campus Employers Student Employment University Hall 255 2197 South University Boulevard Denver, Colorado 80208 Ph: 303.871.6792 Fax: 303.871.2341 Email: stuemp@du.edu
How do I enroll in the password portal?
 The self-serve portal is designed to allow you to change your password and unlock your locked account even if you have forgotten your password. You must enroll for this service to be able to use it. You
The self-serve portal is designed to allow you to change your password and unlock your locked account even if you have forgotten your password. You must enroll for this service to be able to use it. You
DDN CUSTOMER SUPPORT COMMUNITY QUICK START GUIDE
 DDN CUSTOMER SUPPORT COMMUNITY QUICK START GUIDE March 10, 2015 v2 Contents Getting an Account Logging In Creating a New Case Updating an Existing Case Using the Knowledgebase Welcome to the DDN Customer
DDN CUSTOMER SUPPORT COMMUNITY QUICK START GUIDE March 10, 2015 v2 Contents Getting an Account Logging In Creating a New Case Updating an Existing Case Using the Knowledgebase Welcome to the DDN Customer
From a Finder window choose Applications (shown circled in red) and then double click the Tether icon (shown circled in green).
 From a Finder window choose Applications (shown circled in red) and then double click the Tether icon (shown circled in green). You will be presented with a dialog box asking for you to enter an ad-hoc
From a Finder window choose Applications (shown circled in red) and then double click the Tether icon (shown circled in green). You will be presented with a dialog box asking for you to enter an ad-hoc
Remote Access Services Microsoft Windows - Installation Guide
 Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
USING CAMPUS ANYWARE OVER THE VPN (WINDOWS XP)
 USING CAMPUS ANYWARE OVER THE VPN (WINDOWS XP) This document will explain how to install Campus Anyware on your machine (if needed), and how to run Campus Anyware from your machine while you are connected
USING CAMPUS ANYWARE OVER THE VPN (WINDOWS XP) This document will explain how to install Campus Anyware on your machine (if needed), and how to run Campus Anyware from your machine while you are connected
EMPLOYER/EMPLOYEE RELATIONS CUSTOMER SATISFACTION SURVEY RESULTS
 EMPLOYER/EMPLOYEE RELATIONS CUSTOMER SATISFACTION SURVEY RESULTS Human Resources Division Office of Employer/Employee Relations November TABLE OF CONTENTS EXECUTIVE SUMMARY... I. RESPONDENT DEMOGRAPHICS...
EMPLOYER/EMPLOYEE RELATIONS CUSTOMER SATISFACTION SURVEY RESULTS Human Resources Division Office of Employer/Employee Relations November TABLE OF CONTENTS EXECUTIVE SUMMARY... I. RESPONDENT DEMOGRAPHICS...
Marcum LLP MFT Guide
 MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
Schools Remote Access Server
 Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
PISA 2015 MS Online School Questionnaire: User s Manual
 OECD Programme for International Student Assessment 2015 PISA 2015 MS Online School Questionnaire: User s Manual Doc: CY6_CBA_SCQ_MSPrincipalManual.docx September 2014 Produced by ETS, Core 2 Contractor
OECD Programme for International Student Assessment 2015 PISA 2015 MS Online School Questionnaire: User s Manual Doc: CY6_CBA_SCQ_MSPrincipalManual.docx September 2014 Produced by ETS, Core 2 Contractor
Authorize.Net. Advanced Integration Method. Miva Merchant Module. Documentation for module version 1.43. Last Updated: 5/07/03
 Authorize.Net Advanced Integration Method Miva Merchant Module Documentation for module version 1.43 Last Updated: 5/07/03 Module and documentation created by 4TheBest.net 4TheBest.net AIM Module Documentation
Authorize.Net Advanced Integration Method Miva Merchant Module Documentation for module version 1.43 Last Updated: 5/07/03 Module and documentation created by 4TheBest.net 4TheBest.net AIM Module Documentation
JIJIS Frequently Asked Questions
 JIJIS Frequently Asked Questions Contents A. About JIJIS... 2 B. Registration... 3 C. Sign in... 5 D. Setting... 7 E. Job Posting... 8 F. BR certificate... 11 G. Job Applying... 12 H. Others... 13 A. About
JIJIS Frequently Asked Questions Contents A. About JIJIS... 2 B. Registration... 3 C. Sign in... 5 D. Setting... 7 E. Job Posting... 8 F. BR certificate... 11 G. Job Applying... 12 H. Others... 13 A. About
Connecting to Wi-Fi Using Windows 7
 CALIFORNIA STATE UNIVERSITY, LOS ANGELES INFORMATION TECHNOLOGY SERVICES Connecting to Wi-Fi Using Windows 7 Summer 2015, Version 2.0 Table of Contents Introduction...2 Configuring Your Device...2 Onboarding
CALIFORNIA STATE UNIVERSITY, LOS ANGELES INFORMATION TECHNOLOGY SERVICES Connecting to Wi-Fi Using Windows 7 Summer 2015, Version 2.0 Table of Contents Introduction...2 Configuring Your Device...2 Onboarding
Lab 1: Network Devices and Technologies - Capturing Network Traffic
 CompTIA Security+ Lab Series Lab 1: Network Devices and Technologies - Capturing Network Traffic CompTIA Security+ Domain 1 - Network Security Objective 1.1: Explain the security function and purpose of
CompTIA Security+ Lab Series Lab 1: Network Devices and Technologies - Capturing Network Traffic CompTIA Security+ Domain 1 - Network Security Objective 1.1: Explain the security function and purpose of
Running Argos via VPN client
 These instructions will show you how to run Argos reports from a home PC or laptop. Argos is not a web based program. It runs from NSU s network. To establish a connection, we need three components; the
These instructions will show you how to run Argos reports from a home PC or laptop. Argos is not a web based program. It runs from NSU s network. To establish a connection, we need three components; the
1. Cloud Data Center... 1. 2. Login to ICT Marketplace Portal... 1. 3. Dashboard... 2. 3. Data center management... 3. 3.1. New data center...
 Contents 1. Cloud Data Center... 1 2. Login to ICT Marketplace Portal... 1 3. Dashboard... 2 3. Data center management... 3 3.1. New data center... 3 4. View Data Centers... 6 5. Remove Data Centers...
Contents 1. Cloud Data Center... 1 2. Login to ICT Marketplace Portal... 1 3. Dashboard... 2 3. Data center management... 3 3.1. New data center... 3 4. View Data Centers... 6 5. Remove Data Centers...
ASTP Online. Assisted School Travel Program. Student Rollover User Guide. NSW Department of Education
 ASTP Online Assisted School Travel Program Student Rollover User Guide NSW Department of Education Table of Contents Introduction 2 Accessing ASTP Online 2 Locating ASTP online 2 Orientation of ASTP Online
ASTP Online Assisted School Travel Program Student Rollover User Guide NSW Department of Education Table of Contents Introduction 2 Accessing ASTP Online 2 Locating ASTP online 2 Orientation of ASTP Online
Kaseya 2. User Guide. for Network Monitor 4.1
 Kaseya 2 Ping Monitor User Guide for Network Monitor 4.1 June 5, 2012 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Kaseya 2 Ping Monitor User Guide for Network Monitor 4.1 June 5, 2012 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations.
Logging into LTC Instant Access the First Time
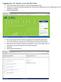 Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu Enter your LTC network username and password. These are the credentials you use to initially
Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu Enter your LTC network username and password. These are the credentials you use to initially
Kaseya 2. Quick Start Guide. for Network Monitor 4.1
 Kaseya 2 Syslog Monitor Quick Start Guide for Network Monitor 4.1 June 5, 2012 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector
Kaseya 2 Syslog Monitor Quick Start Guide for Network Monitor 4.1 June 5, 2012 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector
White Paper. Blindfolded SQL Injection
 White Paper In the past few years, SQL Injection attacks have been on the rise. The increase in the number of Database based applications, combined with various publications that explain the problem and
White Paper In the past few years, SQL Injection attacks have been on the rise. The increase in the number of Database based applications, combined with various publications that explain the problem and
CLIENT ACCESS> emoney
 CLIENT ACCESS> emoney emoney is a financial planning website that allows you to view all of your accounts in one user friendly location. Not only can you view all of your accounts held with Archstone Financial,
CLIENT ACCESS> emoney emoney is a financial planning website that allows you to view all of your accounts in one user friendly location. Not only can you view all of your accounts held with Archstone Financial,
ARMORVOX IMPOSTORMAPS HOW TO BUILD AN EFFECTIVE VOICE BIOMETRIC SOLUTION IN THREE EASY STEPS
 ARMORVOX IMPOSTORMAPS HOW TO BUILD AN EFFECTIVE VOICE BIOMETRIC SOLUTION IN THREE EASY STEPS ImpostorMaps is a methodology developed by Auraya and available from Auraya resellers worldwide to configure,
ARMORVOX IMPOSTORMAPS HOW TO BUILD AN EFFECTIVE VOICE BIOMETRIC SOLUTION IN THREE EASY STEPS ImpostorMaps is a methodology developed by Auraya and available from Auraya resellers worldwide to configure,
Sharing Data with Your Accountant or Your Client
 Chapter 15 Sharing Data with Your Accountant or Your Client Sharing QuickBooks Data QuickBooks File Types Data Sharing for the Business Owner Data Sharing for the Accountant 412 Chapter 15 Sharing Data
Chapter 15 Sharing Data with Your Accountant or Your Client Sharing QuickBooks Data QuickBooks File Types Data Sharing for the Business Owner Data Sharing for the Accountant 412 Chapter 15 Sharing Data
Team Foundation Server 2013 Installation Guide
 Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Citrix for Mac Installation
 While some MCPS applications run on Macintosh computers, other applications do not function properly. One method to get these applications (such as Outlook and Special Education s O/SS) is to add a mini-program
While some MCPS applications run on Macintosh computers, other applications do not function properly. One method to get these applications (such as Outlook and Special Education s O/SS) is to add a mini-program
Lab 2: Secure Network Administration Principles - Log Analysis
 CompTIA Security+ Lab Series Lab 2: Secure Network Administration Principles - Log Analysis CompTIA Security+ Domain 1 - Network Security Objective 1.2: Apply and implement secure network administration
CompTIA Security+ Lab Series Lab 2: Secure Network Administration Principles - Log Analysis CompTIA Security+ Domain 1 - Network Security Objective 1.2: Apply and implement secure network administration
[FREQUENTLY ASKED QUESTIONS]
![[FREQUENTLY ASKED QUESTIONS] [FREQUENTLY ASKED QUESTIONS]](/thumbs/27/12197640.jpg) 2012 [FREQUENTLY ASKED QUESTIONS] Frequently Asked Questions General Topics How do I find my Michigan Tech User ID and ISO Password? Your Michigan Tech User ID is your email address, ending right before
2012 [FREQUENTLY ASKED QUESTIONS] Frequently Asked Questions General Topics How do I find my Michigan Tech User ID and ISO Password? Your Michigan Tech User ID is your email address, ending right before
White Paper Combining Attitudinal Data and Behavioral Data for Meaningful Analysis
 MAASSMEDIA, LLC WEB ANALYTICS SERVICES White Paper Combining Attitudinal Data and Behavioral Data for Meaningful Analysis By Abigail Lefkowitz, MaassMedia Executive Summary: In the fast-growing digital
MAASSMEDIA, LLC WEB ANALYTICS SERVICES White Paper Combining Attitudinal Data and Behavioral Data for Meaningful Analysis By Abigail Lefkowitz, MaassMedia Executive Summary: In the fast-growing digital
Change Management in Projects
 Change Management in Projects Overview About Change Management The Challenge: Manage change will remaining responsive to customer needs. You cannot hope to manage change if you have not done a good job
Change Management in Projects Overview About Change Management The Challenge: Manage change will remaining responsive to customer needs. You cannot hope to manage change if you have not done a good job
Online Testing Engine
 Online Testing Engine Table of Contents Considerations...2 Minimum System Rquirements...3 School Test Leaders... 4 Teachers Administering Tests...5 Online Testing Functionality...7 Online Data Entry for
Online Testing Engine Table of Contents Considerations...2 Minimum System Rquirements...3 School Test Leaders... 4 Teachers Administering Tests...5 Online Testing Functionality...7 Online Data Entry for
WorkKeys Internet Version Test Administration and User Guide
 WorkKeys Internet Version Test Administration and User Guide ACT endorses the Code of Fair Testing Practices in Education and the Code of Professional Responsibilities in Educational Measurement, guides
WorkKeys Internet Version Test Administration and User Guide ACT endorses the Code of Fair Testing Practices in Education and the Code of Professional Responsibilities in Educational Measurement, guides
RECRUIT for Committee Members
 RECRUIT for Committee Members Online Training for UCSC Academic Recruit This training will provide information on the basic use of Recruit for academic search committee members at UC Santa Cruz Once you
RECRUIT for Committee Members Online Training for UCSC Academic Recruit This training will provide information on the basic use of Recruit for academic search committee members at UC Santa Cruz Once you
Event Notification Module TM
 Event Notification Module TM Installation Guide Version 7.0 63220-083-03A1 08/2012 Event Notification Module 63220-083-03A1 08/2012 Notices StruxureWare, StruxureWare Power Monitoring, PowerLogic, Citect,
Event Notification Module TM Installation Guide Version 7.0 63220-083-03A1 08/2012 Event Notification Module 63220-083-03A1 08/2012 Notices StruxureWare, StruxureWare Power Monitoring, PowerLogic, Citect,
Quick Reference for Parents - 1
 Quick Reference for Parents This reference will contain general information for parents including how to access Echo and what content is available for viewing. Getting Started What is Echo? Echo is an
Quick Reference for Parents This reference will contain general information for parents including how to access Echo and what content is available for viewing. Getting Started What is Echo? Echo is an
Introduction to the Georgia Tech VLab Project
 Overview: Introduction to the Georgia Tech VLab Project Georgia Institute of Technology, Spring 2009 http://vlab.matrix.gatech.edu/ The VLab project (short for Virtual Lab) provides Georgia Tech students,
Overview: Introduction to the Georgia Tech VLab Project Georgia Institute of Technology, Spring 2009 http://vlab.matrix.gatech.edu/ The VLab project (short for Virtual Lab) provides Georgia Tech students,
Parental Control Setup Guide
 Parental Control Setup Guide This guide will show you how to setup parental controls on your Genexis router. The parental controls used in this guide are provided by OpenDNS. By using this you can either
Parental Control Setup Guide This guide will show you how to setup parental controls on your Genexis router. The parental controls used in this guide are provided by OpenDNS. By using this you can either
Recommended Browser Setting for MySBU Portal
 The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
Universal Health Record Patient Access v2.2.4 User Guide
 Allscripts FollowMyHealth Universal Health Record Patient Access v2.2.4 User Guide Copyright 2015 Allscripts Healthcare, LLC and/or its affiliates. All Rights Reserved. www.allscripts.com Published Date:
Allscripts FollowMyHealth Universal Health Record Patient Access v2.2.4 User Guide Copyright 2015 Allscripts Healthcare, LLC and/or its affiliates. All Rights Reserved. www.allscripts.com Published Date:
Sona Systems, Ltd. EXPERIMENT MANAGEMENT SYSTEM Master Documentation Set
 Sona Systems, Ltd. EXPERIMENT MANAGEMENT SYSTEM Master Documentation Set Version 2.65 Copyright 2006 Sona Systems, Ltd., All Rights Reserved About This Manual This manual covers usage of the system from
Sona Systems, Ltd. EXPERIMENT MANAGEMENT SYSTEM Master Documentation Set Version 2.65 Copyright 2006 Sona Systems, Ltd., All Rights Reserved About This Manual This manual covers usage of the system from
How to Use Remote Access Using Internet Explorer
 Introduction Welcome to the Mount s Remote Access service. The following documentation is intended to assist first time or active users with connecting, authenticating and properly logging out of Remote
Introduction Welcome to the Mount s Remote Access service. The following documentation is intended to assist first time or active users with connecting, authenticating and properly logging out of Remote
Avaya Credential Management System User Guide
 Avaya Credential Management System User Guide This guide provides background information and instructions on how to use the Avaya Credential Management System (CMS). Table of Contents 1. The Avaya Credential
Avaya Credential Management System User Guide This guide provides background information and instructions on how to use the Avaya Credential Management System (CMS). Table of Contents 1. The Avaya Credential
PC Installation Documentation for the Instant Messaging and MeetingPlace Features of Your New Telephone
 Copy: cupc Admin ffr.7 0 2 k9_enu.zip, from: R:\Cisco\PC Client\VOIP Client PC Installation Documentation for the Instant Messaging and MeetingPlace Features of Your New Telephone Your new telephone is
Copy: cupc Admin ffr.7 0 2 k9_enu.zip, from: R:\Cisco\PC Client\VOIP Client PC Installation Documentation for the Instant Messaging and MeetingPlace Features of Your New Telephone Your new telephone is
Registering and Purchasing Graduate LiveText Accounts Lincoln Memorial University Carter & Moyers School of Education
 Registering and Purchasing Graduate LiveText Accounts Lincoln Memorial University Carter & Moyers School of Education Read through this document before you begin so you can gather what you need to register:
Registering and Purchasing Graduate LiveText Accounts Lincoln Memorial University Carter & Moyers School of Education Read through this document before you begin so you can gather what you need to register:
Getting Started. Getting Started with Time Warner Cable Business Class. Voice Manager. A Guide for Administrators and Users
 Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Table of Contents 1. Contents...1
 Table of Contents 1. Contents...1 1.1 Introduction/Getting Started...1 1.1.1 Creating an Account...1 1.1.2 Logging In...2 1.1.3 Forgotten Password...2 1.1.4 Creating a New Project...3 1.2 My Projects...3
Table of Contents 1. Contents...1 1.1 Introduction/Getting Started...1 1.1.1 Creating an Account...1 1.1.2 Logging In...2 1.1.3 Forgotten Password...2 1.1.4 Creating a New Project...3 1.2 My Projects...3
Requestor. MyTechDesk is a service provided by the California K-12 High Speed Network
 MyTechDesk User Guide Requestor MyTechDesk is a service provided by the California K-12 High Speed Network Copyright 2008-2009 Imperial County Office of Education. All rights reserved. Table of Contents
MyTechDesk User Guide Requestor MyTechDesk is a service provided by the California K-12 High Speed Network Copyright 2008-2009 Imperial County Office of Education. All rights reserved. Table of Contents
SPHOL325: SharePoint Server 2013 Search Connectors and Using BCS
 2013 SPHOL325: SharePoint Server 2013 Search Connectors and Using BCS Hands-On Lab Lab Manual This document is provided as-is. Information and views expressed in this document, including URL and other
2013 SPHOL325: SharePoint Server 2013 Search Connectors and Using BCS Hands-On Lab Lab Manual This document is provided as-is. Information and views expressed in this document, including URL and other
Wrightstown School District
 Wrightstown School District Overview E-help desk gives you the ability to create your own Help Desk tickets. It also allows you to be able to check the status of your requests, and add updates (comments)
Wrightstown School District Overview E-help desk gives you the ability to create your own Help Desk tickets. It also allows you to be able to check the status of your requests, and add updates (comments)
How To Renew A Contract At Mymellanox Online Via Mymllanox
 Mellanox Online Renewal System- Frequently Asked Questions The Frequently Asked Questions (FAQs) and their responses are grouped into categories. Please click on the topic that you would like to learn
Mellanox Online Renewal System- Frequently Asked Questions The Frequently Asked Questions (FAQs) and their responses are grouped into categories. Please click on the topic that you would like to learn
VMware vcenter Log Insight Getting Started Guide
 VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vcenter Log Insight Getting Started Guide vcenter Log Insight 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
WAM Remote Wireless Asset Monitoring. Website User Guide
 WAM Remote Wireless Asset Monitoring Website User Guide Table of Contents Overview... 2 Login Page... 2 Quick Start Guide...3-4 Locations Page... 5 Devices Page... 5 Register Devices Page... 6 Temp or
WAM Remote Wireless Asset Monitoring Website User Guide Table of Contents Overview... 2 Login Page... 2 Quick Start Guide...3-4 Locations Page... 5 Devices Page... 5 Register Devices Page... 6 Temp or
