How to Safely Flight Test a UAV Subject to Cyber-Attacks
|
|
|
- Martina Veronica Morrison
- 10 years ago
- Views:
Transcription
1 Mike Heiges Rob Bever Kyle Carnahan Georgia Tech Research Institute Georgia Tech Research Institute Georgia Tech Research Institute 7220 Richardson Rd 7220 Richardson Rd 7220 Richardson Rd Smyrna, GA Smyrna, GA Smyrna, GA USA USA USA ABSTRACT The increasing ubiquity of computerized, automated systems has led to growing interest in the development and application of methods for defending against cyber-attacks. The concern is that vulnerabilities may exist in unmanned autonomous systems that could be easily exploited to compromise the effectiveness of the system. The Georgia Tech Research Institute (GTRI) worked with the University of Virginia on the System Aware Cyber Security project with the goal of developing low-cost, embedded techniques for cyber-attack defense. A UAV system was selected as the demonstration platform to show an application of the cyber defense techniques. This paper describes the steps GTRI took to safely conduct flight testing of a UAS undergoing cyber-attacks to the autopilot and video camera systems. The steps include extensive hardware in the loop simulation, integration of the cyber systems in the aircraft, and flight test planning to mitigate the potential risks presented by cyberattacks on a flying aircraft. During the subsequent flight testing, defenses against several types of cyber-attacks were successfully demonstrated. 1.0 INTRODUCTION Our growing use of and reliance on computerized, automated systems has led to increased interest in the development and application of methods for defending against cyber-attacks. This research is motivated by the concern that vulnerabilities may exist in unmanned autonomous systems that could be easily exploited by an adversary to compromise the effectiveness of the unmanned system. Cyber-attacks on systems may come from a number of different sources including attacks through the supply chain of the components used in the system, insider attacks from people with access to the system, or malware attacks from corrupted software sources. The goal of the System Aware Cyber Security project was to develop low-cost, embedded techniques for defense against cyber-attacks. The approach is to create reusable security designs that can serve as patterns for solutions and that can be repeated at the design level for various types of systems. To illustrate how these designs may be applied to an actual system, a UAV was selected as a demonstration platform. The autopilot and the camera gimbal systems were examined for vulnerabilities and several potential attack vectors were identified. The concept of a Sentinel was developed to detect the cyber-attacks and protect the UAV systems. Naturally, demonstrating cyber-attacks and defenses on a flying UAV presents a significant level of risk. This paper describes the steps taken to mitigate the risks and safely demonstrate the effectiveness of the Sentinel against cyber-attacks in flight. These steps include extensive hardware in the loop simulation testing, aircraft integration with safety features, careful test planning, and execution by an experienced test team. PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 1
2 2.0 BACKGROUND Because of their reliance on sensor inputs, communication links, and automated functions UAVs are potentially vulnerable to several types of cyber-attacks. An evaluation of typical autopilots revealed several possible vulnerabilities that they have in general. One is their heavy reliance on the Global Navigation Satellite System (GNSS), in particular the Global Positioning System (GPS), for navigation. A recent demonstration by a University of Texas at Austin research team showed how a UAV can be commandeered by a GPS spoofing attack [1]. Autopilot systems are also vulnerable to command attacks. If an adversary is able to inject malicious commands into the system s command and control data-streams, he can reroute the aircraft, force payload systems to malfunction, or even force the aircraft to crash. Command attacks may come through a variety of ways. Command and control radio links are one possible avenue for attack, particularly if the links are unencrypted. The attack may come through the supply chain for the system components and be imbedded in the memory of one of the avionics processors. Another possibility is that the ground control station may be contaminated by malware from an internet website such as a map repository or from a trusted insider. Attacks that would allow an adversary to commandeer the UAV include the aforementioned GPS spoofing attack and command attacks on the autopilot waypoint list. An operator typically commands the UAV s flight path by sending the autopilot a series of waypoints. An attack that changes the coordinates of the waypoints in the list can be used to reroute the UAV. Other types of attacks could be used render payload data useless. For example, an attack could corrupt the GPS position data used by a camera gimbal system for determining the geolocation of the video image. When the erroneous position data is included in the video metadata any targeting value is lost. This type of attack could be difficult to detect since it does not affect the behavior of the aircraft. In a similar vein, command attacks can make it appear as if systems are malfunctioning and thus reduce mission effectiveness. Examples of these types of attacks include malicious commands sent to the camera gimbal that interfere with gimbal deployment and object tracking. Because these types of attacks are subtle, the operator may not realize that the system is under attack and just chalk it up to a random malfunction. Researchers at the University of Virginia have developed a systems engineering-based approach called System- Aware Cyber Security for mitigating the risks of a cyber-attack [2]. In applying the System-Aware approach to a UAV autopilot system they developed the concept of the Sentinel which monitors the communications between system components and looks for anomalies. Onboard the aircraft, the Sentinel comprised two RS232 serial taps, several Raspberry Pi single board computers (SBCs), and a SiCore secure communications interface board. The algorithms programmed into the Sentinel to detect and halt cyber-attacks follow several types of approach. One method involves the onboard Sentinel monitoring the commands received at the autopilot while a ground-based Sentinel monitors the operator s inputs (by logging keystrokes). When a command such as a change to the waypoint list is received by the autopilot, the onboard Sentinel checks with the ground-based Sentinel for a corresponding input at the operator s control station. If no corresponding input is found, the Sentinel alerts the operator that the system may be under cyber-attack. Another technique is to use a voting scheme to compare inputs from independent sources. For example, a GPS attack caused by a corrupted GPS receiver component could be detected using a triple redundant voting scheme with two additional GPS receivers from other manufacturers. A third approach to stopping malfunction-types of attacks is to allow the operator to disable certain commands, such as gimbal retract, during critical mission phases. 3.0 TEST VEHICLE The UAS selected demonstration purposes was GTRI s Airborne Unmanned Sensor System (GAUSS) (shown in Figure 1). GAUSS is based on an Outlaw ER airframe manufactured by Griffon Aerospace and is equipped PAPER NBR - 2 PUB REF NBR (e.g. STO-MP-IST-999)
3 with a Piccolo II autopilot system and a TASE 150 camera gimbal system, both manufactured by Cloud Cap Technology. The Piccolo II s datalink employs a frequency hopping radio from Microhard Systems Inc. operating at 910 MHz. GAUSS is equipped with a secondary radio link at 450 MHz for additional reliability. Communications through the radio datalink with the ground control station are managed with several message streams such as a pilot-in-the-loop stream for manually piloted operation, an autopilot stream to communicate with the Piccolo avionics, a gimbal stream to control a camera gimbal, and a payload stream for serial communication with a payload. These bi-directional streams are multiplexed onto the wireless link. At both ends of the RF link is a serial RS-232 port to connect to the onboard processor in the autopilot and the operator interface computer at the ground control station. GAUSS can also be controlled manually from a wireless joystick console broadcasting at 2.4 GHz. Figure 1. GTRI Airborne Unmanned Sensor System As shown in Figure 2 the autopilot has a several serial communication ports and discrete I/O lines for interfacing with payloads and other components. One of the serial COM ports is occupied by the 450 MHz radio. Another COM port is used to communicate with the TASE 150 camera gimbal. A third COM port is connected to a discrete magnetometer that provides a heading reference for the navigation filter that is independent of the GPS receiver. Two of the general purpose I/O (GPIO) lines are dedicated to the manual pilot control at 2.4 GHz. The two receivers are oriented orthogonal to each other to ensure reliable communications with the pilot console on the ground. A level shifter board adjusts the voltage level between the receivers and the GPIO lines. Another GPIO line is used to control a kill switch on the payload power supply board. This arrangement allows the GAUSS operator to kill power to the payload systems from the Piccolo operator interface. Payload battery Autopilot GPIO GPIO GPIO COM 3 COM 4 COM 1 COM 2 Kill Switch Payload power supply Level Shifter Magnetometer Camera Gimbal 2.4 GHz 2.4 GHz Video Proc System Legend Serial Power NTSC video 4.4 GHz 910 MHz 450 MHz Figure 2. GAUSS Autopilot System Block Diagram PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 3
4 4.0 ATTACKS SELECTED FOR DEMONSTRATION Three types of cyber-attacks were chosen and fully developed for the demonstration program: an attack that changes the list of waypoint in the autopilot s flight plan, an attack that corrupts the GPS position, and attacks on the camera gimbal that appear as gimbal control malfunctions. The demonstration program proceeded from the premise that the defense against a particular type of cyber-attack should be general enough that it is largely agnostic to the specifics of how the attack was implemented. In other words, regardless of whether the attack was caused by a corrupted avionics component, a hacked data link, malware infecting a ground control station, or some other means, the defenses should be able to detect and halt the attack. Therefore, rather than trying to hack into the various autopilot system components and install the attack software directly on them, we used several Raspberry Pi SBCs to host the attack software. The devices were connected to the serial communications links between components where they could intercept and modify message traffic to effect the various attacks. Implementing the attacks through separate SBC devices greatly mitigates the risk in flight testing. Because the flight critical avionics components remain unchanged and the attack software is hosted on separate SBC devices, these devices can be shut down to restore normal functionality in the event of an in-flight emergency. Another measure that was taken to reduce risk was how the GPS attack was implemented. Instead of attacking the GPS data used directly by the autopilot system for navigation (which could be extremely dangerous), the GPS data provided to the camera gimbal was attacked. This allowed us to demonstrate the ability of the Sentinel to detect and defend against GPS attacks without putting the aircraft at risk. The following subparagraphs describe each of the cyber-attacks developed for the demonstration. 4.1 Waypoint Attack The waypoint attack changes the waypoints in the autopilot s flight plan causing it to fly a different trajectory from the one intended by the operator. To execute the attack, the tester sends a new list of waypoints via Ethernet to a Raspberry Pi onboard the aircraft that connects to one of the autopilot s serial communication ports. The attack Pi pushes the new list of waypoints to the autopilot through the autopilot message stream. Since the autopilot sends the updated waypoint list to the operator s station, the change would normally be readily apparent. However, researchers at UVA developed a companion attack at the ground control station that would mask the change to the waypoint list as well as mask the location of the aircraft as it flies the new flight plan. As a result, during the attack the operator s station displays the aircraft where he expects it to be. 4.2 GPS Walk-off Attack When the aircraft enters a pre-defined geographic region, the GPS location data that is sent from the autopilot to the camera gimbal is corrupted with a slowly increasing bias. The corrupted GPS data is included in the video stream as metadata that provides the coordinates of the area being viewed by the camera. As a result of this attack, the video imagery has erroneous position data associated with it and loses all value for ISR and targeting purposes. The GPS walk-off attack is implemented with a Raspberry Pi SBC located on the serial link between the autopilot and the camera gimbal. When the attack is disabled, serial communications pass between the autopilot and camera gimbal unaltered. When the attack is underway, the attack Pi intercepts the GPS data packet, adds a growing position bias to it, and passes it on to the camera gimbal. 4.3 Gimbal Command Attacks These attacks use the gimbal command set to make the gimbal appear to malfunction. When the aircraft entered a predefined geographic region, spurious gimbal commands were issued to the gimbal causing it to retract or slew the sensor point of interest (SPOI) upwards. The gimbal retract command is issued whenever the aircraft is PAPER NBR - 4 PUB REF NBR (e.g. STO-MP-IST-999)
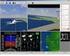
5 in the attack zone and the camera operator tries to engage the camera s tracking function. Similarly, the when the SPOI attack is enabled the camera will slew upwards when the camera operator engages the gimbal s SPOI function. These attacks are caused by malware hosted on the camera gimbal operator s station. The software monitors the operators inputs and uses them to trigger retract and SPOI attacks. 5.0 TESTER S INTERFACE The tester s interface was developed primarily to allow the test director to monitor the aircraft s true state while it is undergoing a cyber-attack and its perceived state. For example, the waypoint attack takes command of the UAV s flight plan while masking the attack on the operator s ground control station. As a result of the masking, the operator s display shows the aircraft on the intended route while, in reality, the aircraft s flight path is being rerouted. The situational display is based on GTRI s FalconView map display software. A FalconView plugin displays the current state of the system (see Figure 3). It shows where the aircraft really is (truth) and where the aircraft and camera operators see it on their displays while the attack is happening. The display also shows where the defensive systems indicate the aircraft s correct location is. To do this, the tester s interface takes advantage of GAUSS dual radio links for command and control operating at 450 and 910 MHz. Two separate instances of the operator interface software are run at the ground control station, one for each frequency. While the masking attack is underway on the 910 MHz ground control station, the tester s interface uses the 450 MHz control station to monitor the true status of the aircraft. On the display the aircraft icons are in different colors to indicate the aircraft s true position, attack position, and defense position. The aircraft s true position shown in blue indicates where the aircraft really is. This data is retrieved from the 450 MHz Piccolo ground station. The attack position, shown in red, indicates where the operator s station is displaying the aircraft s position during a waypoint attack with masking. It also indicates where camera operator s display is showing the aircraft position in the case of the GPS walk-off attack. The defense position, shown in green, indicates the aircraft location as determined by the Sentinel in response to a waypoint or GPS walk-off attack. Figure 3. Tester s Interface Situational Display PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 5
6 6.0 HARDWARE IN THE LOOP SIMULATION Prior to the flight test activity, extensive testing of the Sentinel system was conducted in the GTRI hardware in the loop (HIL) simulator. The Piccolo autopilot system includes a hardware-in-the-loop (HIL) and software-inthe-loop (SIL) simulation capability that is essential for properly setting autopilot parameters and tuning gains. While simulation cannot replace flight testing, it greatly reduces the risk by allowing software bugs and other problems to be found in the lab. Figure 4 shows the baseline HIL simulator set-up for GAUSS. The heart of the simulator is the six degree of freedom (6 DOF) flight dynamics model running on one of the lab s computers and the CAN interface to the Piccolo autopilot. The Piccolo sends servo control commands over the CAN bus to the 6 DOF simulation running on the computer. The simulation calculates the dynamic response of the aircraft and sends aircraft state data (sensor data) over the CAN interface to the autopilot. This same aircraft state data is also provided to the CAN interface for the camera gimbal to simulate the gimbal s IMU sensors. The autopilot communicates to two computers running the operator interface software, Piccolo Command Center (PCC). One link is through the ground station over the 910 MHz radio and the other link is through a serial connection on one of the autopilot COM ports to simulate the 450 MHz link. To simulate the analog video signal from the camera, we use the 3D visual simulator software MetaVR to generate the scene as it would be seen by the camera in flight. The analog video output from the video processing system is converted to Ethernet format with an H.264 encoder and routed to a computer running the ViewPoint software. Figure 4. Baseline HIL Set-Up for GAUSS The components integrated into the GTRI HIL simulator are indicated in Figure 5 and Figure 6 while Figure 7 shows the actual simulator. Three Raspberry Pi single board computers (shown in orange as Attack Pi 1 and Attack Pi 2 in Figure 5 and as Masking Attack Pi in Figure 6) are used to effect the cyber-attacks. Attack Pi 1 executes the waypoint attack onboard the aircraft which changes the list of waypoints in the autopilot s flight plan. This attack causes the aircraft to deviate from its intended course. The Masking Attack Pi at the ground control station hides the fact that the aircraft has gone off course. The second onboard attack Pi intercepts and PAPER NBR - 6 PUB REF NBR (e.g. STO-MP-IST-999)
7 Passive Serial Splitter corrupts the GPS position data being sent from the autopilot to the camera gimbal. This attack corrupts the target geolocation information that is included as metadata in the video stream. The third attack originates at the ground control station and affects the gimbal commands (the malfunction attack). This attack software is hosted on the Test Director s Station which also hosts the Tester s Interface software. The Test Director s Station allows the test director to set up attacks and trigger attacks. Payload radio 2.4 GHz Ethernet Switch Ethernet Switch Legend RS-232 Ethernet NTSC video Attack Pi 1 Defense Systems UAV Systems Autopilot COM 3 COM 4 COM 1 COM 2 SiCore Shield II UART 1 UART 2 Attack Pi 2 SerialSpy Camera Gimbal AS 1 AS 2 AS 3 Video Proc System Attack Platforms GPS GPS 4.4 GHz 910 MHz 450 MHz Figure 5. Airborne System Architecture 910 MHz 450 MHz Video radio 4.4 GHz 2.4 GHz Payload radio H.264 Encoder UAV PC MHz Backup command center Ground Station UAV PC MHz Primary command center Keylogger Passive Serial Splitter Masking Attack Pi Ground Sentinel Pi Ethernet Switch Legend RS-232 Ethernet NTSC video Defense Systems UAV Systems Attack Platforms Test Platforms CyberCommander Station Test Director Station Figure 6. Ground System Architecture PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 7
8 The components shown in green in Figure 5 and Figure 6 constitute the cyber defense systems. The primary aircraft component is the SiCore Shield II computer that serves as the onboard Sentinel. A Raspberry Pi SBC (the Ground Sentinel Pi in Figure 6) works in conjunction with the onboard Sentinel to detect waypoint attacks even if they are masked. The passive serial splitter allows the Sentinel to monitor the autopilot s flight plan through the autopilot s COM port 3 as part of the defense against waypoint attacks. The SerialSpy shown in Figure 5 monitors the communications between the autopilot and the gimbal. This device defends against GPS attacks by checking the autopilot s GPS position data against validated position data provided by the Sentinel. Three additional Raspberry Pis (labeled Air Sentinel 1, Air Sentinel 2, and AS3 in Figure 5) are included as part of a triple redundant voting scheme to validate GPS position data. Two of these Pis have independent GPS receivers while the third uses the autopilot GPS data acquired via the Ethernet link. If the GPS position data does not match the validated data within some error bound, an attack is indicated and the SerialSpy passes on to the gimbal the validated position data provided by the Sentinel. The final component of the cyber defense system is the Cyber Commander Station (on the right in Figure 6). This is an application that runs on the ground control station and provides alerts to the operator in the event of an attack. During the simulation stage of testing we found the HIL simulator to be an indispensable tool for debugging many of the communications issues between the various components on the network. In addition, the simulator allowed us to thoroughly rehearse each attack scenario in preparation for the succeeding flight test. These rehearsals were essential to ensuring that the aircraft s airworthiness was not compromised with the addition of the System Aware attack and defense components. Figure 7. GTRI HIL Simulator with System Aware Cyber Security Components Installed PAPER NBR - 8 PUB REF NBR (e.g. STO-MP-IST-999)
9 7.0 AIRCRAFT INTEGRATION 7.1 System Aware Payload Integration of the Sentinel components and cyber-attack devices into the GAUSS air vehicle required the design and fabrication of wiring harnesses, additional GPS antenna mounts, and a chassis to hold all of the components (Figure 8). This chassis was installed in the aircraft s forward payload bay as indicated in Figure 9. Figure 8. Payload Chassis Figure 9. Payload installation in GAUSS 7.2 Airworthiness Qualification Integrating systems such the System Aware Sentinel and the cyber-attack components into a UAS requires extra attention to safety and airworthiness. GTRI follows an airworthiness qualification (AQ) process similar to that outlined for UASs in (MIL-HDBK-516B). The primary focus of the AQ process for this demonstration was ensuring that the System Aware test components (the Sentinel and cyber-attack systems) did not compromise the ability of the autopilot system, including data links, to function properly at all times. The goal of the AQ process is to ensure that the UAS meets the FAA s primary concerns for operations in the national airspace system (NAS): Containment the ability of the aircraft to be contained within the proposed flight area Lost link the sequence actions that the UAS will execute in the event the command and control link is lost leading to a safe resolution PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 9
10 Flight conclusion an independent means to safely conclude a flight in the event the command and control cannot be reestablished Many desired safety features are standard functions on today s autopilots such as the Piccolo II. These include programmable behaviors for what the aircraft should do in the event communications and GPS are lost. In the case of lost communications, if the autopilot has not heard from the ground station within a specified amount of time (e.g., 20 seconds), it can be programmed to have the aircraft orbit in a predetermined flight plan, typically near the ground station. If communications are not re-established before the flight timer expires, the autopilot can be set to execute an auto-landing at a predefined waypoint. If GPS is lost, the autopilot can rely on the inertial navigation system (INS) alone for a short period of time. After the GPS timeout expires, the autopilot will assert a flight termination command which can be used to trigger several actions such as closing the throttle and commanding maximum right aileron and rudder and up elevator for an aerodynamic termination. For aircraft equipped with a flight recovery system, such as a parachute, the flight termination signal can be used to deploy the parachute. To help ensure containment, the Piccolo autopilot can be programmed with a three dimensional airspace boundary called a geo-fence. The geo-fence coordinates reside in the autopilot and they set hard limits on where the UAS can be commanded to go. In addition to preventing the creation or execution of flight plans that would take the aircraft outside of the fence, flight termination can be asserted if the aircraft flies outside the fence. The geo-fencing feature was not used during the demonstration program because the aircraft was kept within a fairly tight pattern around the airport under the watchful eye of the safety pilot. In addition to the standard safety features of the Piccolo autopilot system, GTRI s GAUSS employs several other safety measures. These include a secondary radio link at 450 MHz for command and control. As mentioned previously, this link was used to provide truth data on the aircraft s location when the 910 MHz link is under cyber-attack. The aircraft is also equipped with two orthogonal 2.4 GHz receivers as part of the wireless pilot manual control system. Thus, the aircraft can be controlled manually via the 910 MHz link using the wired pilot console connected to the ground station or through the 2.4 GHz link using the wireless pilot console. Other safety features include a kill switch on the power supply for the payload, an emergency retrieval beacon, and a three axis magnetometer. Because of the potential for the payload system to interfere with the aircraft s operation, a kill switch was added to the payload power supply circuit to enable the flight test engineer to kill power to all of the payload components via a discrete command from the autopilot system. This was done to ensure that all of the non-flight critical components communicating with the autopilot could be shut down in the event of an emergency. All fixed-wing unmanned aircraft flown by GTRI carry an emergency retrieval beacon. This device transmits a periodic tone at about 219 MHz which can be used to locate a downed aircraft. This commercially available product can operate for up to 2 weeks using a primary lithium battery. Work is under way to integrate this capability directly into the on board avionics. The goal of this work is to provide more reliable operation and reduced cost. All unmanned aircraft typically navigate using GPS. In the event of a loss of GPS, the aircraft can fly away or, if so configured, immediately ditch. Both options are undesirable. When resources permit, GTRI equips its UAVs with an electronic compass referred to as a magnetometer. This allows the aircraft to approximate its heading and navigate via dead reckoning. While this is not as accurate as GPS navigation, it can provide some time for GPS recovery or a more controlled flight termination. GTRI s GAUSS is equipped with a Honeywell HMR axis magnetometer which feeds into the navigation filter; although, the magnetometer was not used PAPER NBR - 10 PUB REF NBR (e.g. STO-MP-IST-999)
11 during this demonstration. Work is underway to produce a smaller, more integrated magnetometer to more easily integrate this capability in test aircraft. The current design is smaller, lighter, and less expensive than the Honeywell HMR This is possible using very small magnetometers found in devices like cell phones. 8.0 FLIGHT TESTING 8.1 Flight Conditions and Restrictions The flight test demonstration was conducted at the Early County airport in Blakely, GA under a Certificate of Authorization (COA) from the FAA. The COA permits operations in Class E and Class G airspace at or below 5000 ft above ground level in the vicinity of the airport. Other operational restrictions include: Operations must be in visual meteorological conditions during daylight hours No operations (including lost link procedures) over populated areas Sterile cockpit procedures during all critical phases of flight All crew members must have a current second class airman medical certificate and current crew resource management training The pilot in command must hold, at a minimum, a current FAA private pilot certificate Supplemental pilots must have, at a minimum, successfully completed private pilot ground school and passed the written test A Notice to Airmen (NOTAM) must be issued not more than 72 hours in advance, but not less than 48 hours prior to the operation As part of the COA application, GTRI submitted a contingency plan that addressed emergency recovery or flight termination of the aircraft in the event of unrecoverable system failure. In particular, the plan covered lost link and flight termination procedures based on the autopilot s built-in safety features. 8.2 The Test Team The test team consisted of eight personnel with the following roles and responsibilities: Lead flight test engineer supervised execution of the flight test plan, monitored the aircraft status during the tests, made Unicom radio calls to alert local traffic Pilot in command Supervised flight operations, watched for other aircraft in the vicinity, monitored Unicom radio traffic Safety pilot performed manual takeoffs and landings, watched for other aircraft in the vicinity Visual observer watched for other aircraft in the vicinity Autopilot operator commanded and monitored the aircraft through the autopilot system, operated the camera gimbal system System Aware operator 1 initiated gimbal attacks and GPS walk-off attacks, monitored Sentinel defense responses System Aware operator 2 initiated waypoint and masking attacks, monitored Sentinel defense responses Videographer recorded video and still images to document the demonstration Figure 10 shows the test team inside the GTRI UAV trailer. The first set of wall-mounted monitors, on the far PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 11
12 left in the picture, served as displays for the 910 MHz PCC operator s station manned by the autopilot operator. The second set of monitors was used for the 450 MHz PCC station manned by the flight test engineer. To the right of these monitors was a laptop computer running a Hyperterminal interface to the SerialSpy which implemented the defenses against gimbal command attacks and attacks on the GPS data provided to the gimbal. In the middle of the picture is a laptop computer running the Tester s Interface software. The third set of wallmounted monitors served as multi-purpose displays. The top monitor displayed the ViewPoint interface during gimbal testing and the Cyber Commander interface during waypoint attack testing. The lower monitor was used to display the status of the various Raspberry Pi SBCs and the SiCore board. Also at this station, was a laptop computer running the interface for the waypoint attack software. Figure 10. Test Team inside the GTRI UAV Trailer The test team maintained communications with each member via a Clear-Com radio intercom system. This communication system also allowed the pilot in command and the flight test engineer to talk directly with local traffic over Unicom frequency MHz. 8.3 Attack Demonstrations Three types of attacks were demonstrated in flight: a GPS walk-off, a gimbal command attack, and a waypoint attack. Testing began with the GPS walk-off attack because it was the most benign in terms of the potential effects on the aircraft. Next were the gimbal command attacks which would not affect the aircraft s ability to fly, but did pose a slight risk of damage to the camera gimbal. The waypoint attack was scheduled for last because it posed the greatest risk to loss of control over the aircraft. The following paragraphs describe these attacks and the results GPS Walk-off The aircraft s commanded flight path was a right hand pattern on Runway 23 as shown in Figure 11. The geographic region for the attack was defined as a circular area centered to the northeast of the aircraft s flight path with a radius of 609 m. This resulted in a partial overlap with the aircraft s commanded path as shown in PAPER NBR - 12 PUB REF NBR (e.g. STO-MP-IST-999)
13 Figure 11. As the aircraft crossed into the attack region the GPS walk-off attack was initiated. In this demonstration, the attack was configured to add a growing bias the aircraft s latitude coordinate causing its reported position to shift northward as illustrated in Figure 12. During the first pass through the attack region the Sentinel defense was disabled and the position data being fed from the autopilot to the gimbal was observed to deviate from the true position. During the next pass through the attack zone the defense was enabled and the GPS walk-off was detected almost immediately. The SerialSpy then replaced the corrupted GPS position data with validated data from the Sentinel and forwarded the data to the camera gimbal. Figure 11. GPS Walk-off Attack Region Figure 12. GPS Walk-off Attack Position Report PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 13
14 8.3.2 Gimbal Command Attacks The retract attack is referred to as Attack 2a and the SPOI attack is referred to as Attack 2b. The aircraft s commanded flight orbit was centered over the runway as shown in Figure 13. The geographic region for the attack was defined as a circular area centered to the northeast with a radius of 609 m. This resulted in a partial overlap with the aircraft s commanded orbit as shown in Figure 13. As the aircraft crossed into the region encompassed by the attack orbit the SPOI attack was initiated (Attack 2b). During the initial pass through the attack region the defense was disabled and the SPOI slewed upwards at the test director s command. During the next pass, the defense was enabled. The defense blocked the SPOI command preventing the camera from being slewed upwards. After the SPOI attack was demonstrated it was deactivated and the gimbal retract attack (Attack 2a) was enabled. During the initial pass through the attack region the defense was disabled and the gimbal retracted when the operator tried to track an object at the center of the orbit. During the next pass, the defense was enabled. The defense blocked the gimbal retract command when the operator initiated a tracking command and the operator was able to successfully track a ground object Waypoint Attack: Figure 13. Gimbal Command Attack Region The waypoint attack changes the waypoints in the autopilot s flight plan causing it to fly a different trajectory from the one intended by the operator. The aircraft s commanded flight plan was one of two rectangular patterns aligned with the runway as shown in Figure 14. The other rectangular pattern was used as the set of waypoints for the attack flight plan. The coordinates of the waypoints are provided in Table 1 and Table 2. PAPER NBR - 14 PUB REF NBR (e.g. STO-MP-IST-999)
15 For this demonstration the operator commanded the aircraft to fly the rectangular pattern consisting of the waypoints in Table 1. During the first pass through the pattern the test director initiated a waypoint attack with the defense disabled. The aircraft diverted to the rectangular pattern made up of the waypoints in Table 2. This exercise verified that the attack was working properly with regard to taking control of the aircraft. The defense was then enabled and the operator commanded the aircraft to return to the original pattern. In this case the Sentinel successfully noted the change in the flight plan, verified that the change came from the operator, and indicated on the Cyber Commander interface that a normal change had occurred. During the next pass through the pattern when the attack was initiated the Sentinel successfully noted the change and, because it could not find an associated operator input for the change, alerted the operator via the Cyber Commander interface of a possible cyber-attack. The Cyber Commander interface offered the appropriate corrective actions to the operator which included restoring the original flight plan, flying the aircraft back to its home location, and flying to another waypoint or flight plan of the operator s choice. For this demonstration the operator elected to have the Sentinel change back to the original plan. In the next pass through the pattern the masking attack on the 910 MHz ground control station was triggered along with the waypoint attack onboard the aircraft. Unfortunately, the masking portion of the attack did not work properly. When the masking attack was engaged, the aircraft s position froze on the 910 MHz ground control station display. The aircraft s true location could still be seen on the 450 MHz ground station display. The failure of the masking attack led to an interesting and unplanned situation. The 910 MHz control station is the primary display used by the operator for controlling the aircraft. When the masking attack froze this station the operator had to switch to the 450 MHz ground station to issue waypoint commands to return the aircraft to the desired pattern. During the setup of the tests, the Sentinel was not made aware of the presence of the 450 MHz ground control. As a result, when the operator initiated the change from this unknown station, the Sentinel detected the change as an unverified change and alerted the Cyber Commander station that a cyberattack was underway. This attack is very similar to a spoofing attack where a false operator station would attempt to take over flight operations for a UAV. Table 1. Waypoints on northwest side of runway Table 2. Waypoints centered over runway PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 15
16 Figure 14. Waypoint Attack Flight Plans 9.0 CONCLUSIONS Flight testing UAVs always involves an element of risk, especially when testing anything that can affect the flight control system and the aircraft s behavior. However, autopilot safety features and careful planning can reduce the risk to an acceptable level. To prepare for a flight demonstration of a cyber-security system defending the UAV against cyber-attacks, GTRI conducted extensive hardware in the loop simulation-based testing to fully vet the system and to plan and rehearse the flight test demonstration. When integrating the system into the aircraft, GTRI relied on a number of safety features such as dual command and control radio links and a power kill switch that could deactivate the non-flight critical components. A well-trained and experienced flight crew is also essential to safe operations. During testing a four-man crew inside the ground command station monitored all aspects of the systems under test while an external three-man crew served as safety pilots and visual observers to ensure safe operations in the national airspace. By following the steps outlined in this paper, GTRI was able to successfully and safely demonstrate a defensive system designed to protect UAVs from cyber-attacks. 11. ACKNOWLEDGMENTS The authors would like to acknowledge the contributions of the flight test team: Warren Lee, Gary Gray, and Daniel Smith from GTRI, Rick Jones and Ed Suhler from UVa, and Mark Dyess from Griffon Aerospace. The authors would like to thank the principal investigators for this program: Bell Melvin (GTRI) and Barry Horowitz (UVa). This research was funded by the US Department of Defense through the Stevens Institute of Technology. PAPER NBR - 16 PUB REF NBR (e.g. STO-MP-IST-999)
17 12. REFERENCES [1] Kerns, A. J., Shepard, D. P., Bhatti, J. A. and Humphreys, T. E., Unmanned Aircraft Capture and Control Via GPS Spoofing, J. Field Robotics, Vol. 31, 2014, pp [2] Rick A. Jones and Barry M. Horowitz, A System-Aware Cyber Security Architecture, Systems Engineering, Volume 15, No. 2, 2012 PUB REF NBR (e.g. STO-MP-IST-999) PAPER NBR - 17
18 PAPER NBR - 18 PUB REF NBR (e.g. STO-MP-IST-999)
Security Engineering Project
 Security Engineering Project Part 1a System Aware Cyber Security for an Autonomous Surveillance System On Board an Unmanned Arial Vehicle Part 1b System Aware Cyber-Security Application to Unmanned Aircraft
Security Engineering Project Part 1a System Aware Cyber Security for an Autonomous Surveillance System On Board an Unmanned Arial Vehicle Part 1b System Aware Cyber-Security Application to Unmanned Aircraft
MP2128 3X MicroPilot's. Triple Redundant UAV Autopilot
 MP2128 3X MicroPilot's Triple Redundant UAV Autopilot Triple redundancy (3X) gives autopilot technology the reliability necessary to safely carry out sensitive flight missions and transport valuable payloads.
MP2128 3X MicroPilot's Triple Redundant UAV Autopilot Triple redundancy (3X) gives autopilot technology the reliability necessary to safely carry out sensitive flight missions and transport valuable payloads.
System Aware Cyber Security
 System Aware Cyber Security Application of Dynamic System Models and State Estimation Technology to the Cyber Security of Physical Systems Barry M. Horowitz, Kate Pierce University of Virginia April, 2012
System Aware Cyber Security Application of Dynamic System Models and State Estimation Technology to the Cyber Security of Physical Systems Barry M. Horowitz, Kate Pierce University of Virginia April, 2012
A highly integrated UAV avionics system 8 Fourth Street PO Box 1500 Hood River, OR 97031 (541) 387-2120 phone (541) 387-2030 fax CCT@gorge.
 A highly integrated UAV avionics system 8 Fourth Street PO Box 1500 Hood River, OR 97031 (541) 387-2120 phone (541) 387-2030 fax [email protected] Bill Vaglienti Ross Hoag April 10, 2003 Table of contents
A highly integrated UAV avionics system 8 Fourth Street PO Box 1500 Hood River, OR 97031 (541) 387-2120 phone (541) 387-2030 fax [email protected] Bill Vaglienti Ross Hoag April 10, 2003 Table of contents
System Aware Cyber Security. Barry Horowitz University of Virginia March 2014
 System Aware Cyber Security Barry Horowitz University of Virginia March 2014 Our Team SIE Faculty: Horowitz, Beling Research Scientists: Jones, Suhler, Lau CS Faculty: Skadron, Humphrey Post Doc: Li ECE
System Aware Cyber Security Barry Horowitz University of Virginia March 2014 Our Team SIE Faculty: Horowitz, Beling Research Scientists: Jones, Suhler, Lau CS Faculty: Skadron, Humphrey Post Doc: Li ECE
Nighthawk IV UAS. Versatility. User Friendly Design. Capability. Aerial Surveillance Simplified. [email protected] 800.639.6315 www.ara.
 Aerial Surveillance Simplified The Nighthawk IV small unmanned aerial vehicle brings military hardened technology to civil agencies and commercial user groups. Supremely easy to operate and recently certified
Aerial Surveillance Simplified The Nighthawk IV small unmanned aerial vehicle brings military hardened technology to civil agencies and commercial user groups. Supremely easy to operate and recently certified
Using Tactical Unmanned Aerial Systems to Monitor and Map Wildfires
 Using Tactical Unmanned Aerial Systems to Monitor and Map Wildfires Michael Tranchitella, Stephen Fujikawa, Tzer Leei Ng, David Yoel, Don Tatum IntelliTech Microsystems, Inc. Bowie, Maryland Philippe Roy,
Using Tactical Unmanned Aerial Systems to Monitor and Map Wildfires Michael Tranchitella, Stephen Fujikawa, Tzer Leei Ng, David Yoel, Don Tatum IntelliTech Microsystems, Inc. Bowie, Maryland Philippe Roy,
Matthew O. Anderson Scott G. Bauer James R. Hanneman. October 2005 INL/EXT-05-00883
 INL/EXT-05-00883 Unmanned Aerial Vehicle (UAV) Dynamic-Tracking Directional Wireless Antennas for Low Powered Applications That Require Reliable Extended Range Operations in Time Critical Scenarios Matthew
INL/EXT-05-00883 Unmanned Aerial Vehicle (UAV) Dynamic-Tracking Directional Wireless Antennas for Low Powered Applications That Require Reliable Extended Range Operations in Time Critical Scenarios Matthew
SESAR Air Traffic Management Modernization. Honeywell Aerospace Advanced Technology June 2014
 SESAR Air Traffic Management Modernization Honeywell Aerospace Advanced Technology June 2014 Honeywell in NextGen and SESAR Honeywell active in multiple FAA NextGen projects ADS-B Surface Indicating and
SESAR Air Traffic Management Modernization Honeywell Aerospace Advanced Technology June 2014 Honeywell in NextGen and SESAR Honeywell active in multiple FAA NextGen projects ADS-B Surface Indicating and
Design Specifications of an UAV for Environmental Monitoring, Safety, Video Surveillance, and Urban Security
 Design Specifications of an UAV for Environmental Monitoring, Safety, Video Surveillance, and Urban Security A. Alessandri, P. Bagnerini, M. Gaggero, M. Ghio, R. Martinelli University of Genoa - Faculty
Design Specifications of an UAV for Environmental Monitoring, Safety, Video Surveillance, and Urban Security A. Alessandri, P. Bagnerini, M. Gaggero, M. Ghio, R. Martinelli University of Genoa - Faculty
Current Challenges in UAS Research Intelligent Navigation and Sense & Avoid
 Current Challenges in UAS Research Intelligent Navigation and Sense & Avoid Joerg Dittrich Institute of Flight Systems Department of Unmanned Aircraft UAS Research at the German Aerospace Center, Braunschweig
Current Challenges in UAS Research Intelligent Navigation and Sense & Avoid Joerg Dittrich Institute of Flight Systems Department of Unmanned Aircraft UAS Research at the German Aerospace Center, Braunschweig
INITIAL TEST RESULTS OF PATHPROX A RUNWAY INCURSION ALERTING SYSTEM
 INITIAL TEST RESULTS OF PATHPROX A RUNWAY INCURSION ALERTING SYSTEM Rick Cassell, Carl Evers, Ben Sleep and Jeff Esche Rannoch Corporation, 1800 Diagonal Rd. Suite 430, Alexandria, VA 22314 Abstract This
INITIAL TEST RESULTS OF PATHPROX A RUNWAY INCURSION ALERTING SYSTEM Rick Cassell, Carl Evers, Ben Sleep and Jeff Esche Rannoch Corporation, 1800 Diagonal Rd. Suite 430, Alexandria, VA 22314 Abstract This
VTOL UAV. Design of the On-Board Flight Control Electronics of an Unmanned Aerial Vehicle. Árvai László, ZMNE. Tavaszi Szél 2012 ÁRVAI LÁSZLÓ, ZMNE
 Design of the On-Board Flight Control Electronics of an Unmanned Aerial Vehicle Árvai László, ZMNE Contents Fejezet Témakör 1. Features of On-Board Electronics 2. Modularity 3. Functional block schematics,
Design of the On-Board Flight Control Electronics of an Unmanned Aerial Vehicle Árvai László, ZMNE Contents Fejezet Témakör 1. Features of On-Board Electronics 2. Modularity 3. Functional block schematics,
KILN GROUP AVIATION DIVISION UAS INSURANCE PROPOSAL FORM GLOSSARY
 GLOSSARY ATC Air Traffic Control CAA Civil Aviation Authority Comms Abv. Communications GCS Ground Control Station. Including launch system, flight control and mission specific hardware & software, communications
GLOSSARY ATC Air Traffic Control CAA Civil Aviation Authority Comms Abv. Communications GCS Ground Control Station. Including launch system, flight control and mission specific hardware & software, communications
Hardware In The Loop Simulator in UAV Rapid Development Life Cycle
 Hardware In The Loop Simulator in UAV Rapid Development Life Cycle Widyawardana Adiprawita*, Adang Suwandi Ahmad = and Jaka Semibiring + *School of Electric Engineering and Informatics Institut Teknologi
Hardware In The Loop Simulator in UAV Rapid Development Life Cycle Widyawardana Adiprawita*, Adang Suwandi Ahmad = and Jaka Semibiring + *School of Electric Engineering and Informatics Institut Teknologi
S TEC. List of Effective Pages. Record of Revisions
 List of Effective Pages * Asterisk indicates pages changed, added, or deleted by current revision. Retain this record in front of handbook. Upon receipt of a Record of Revisions revision, insert changes
List of Effective Pages * Asterisk indicates pages changed, added, or deleted by current revision. Retain this record in front of handbook. Upon receipt of a Record of Revisions revision, insert changes
How To Discuss Unmanned Aircraft System (Uas)
 Unmanned Aerial Systems (UAS) for American Association of Port Authorities Administration and Legal Issues Seminar New Orleans, LA April 9, 2015 Briefly about Flight Guardian Our Services: Educating public
Unmanned Aerial Systems (UAS) for American Association of Port Authorities Administration and Legal Issues Seminar New Orleans, LA April 9, 2015 Briefly about Flight Guardian Our Services: Educating public
How To Run A Factory I/O On A Microsoft Gpu 2.5 (Sdk) On A Computer Or Microsoft Powerbook 2.3 (Powerpoint) On An Android Computer Or Macbook 2 (Powerstation) On
 User Guide November 19, 2014 Contents 3 Welcome 3 What Is FACTORY I/O 3 How Does It Work 4 I/O Drivers: Connecting To External Technologies 5 System Requirements 6 Run Mode And Edit Mode 7 Controls 8 Cameras
User Guide November 19, 2014 Contents 3 Welcome 3 What Is FACTORY I/O 3 How Does It Work 4 I/O Drivers: Connecting To External Technologies 5 System Requirements 6 Run Mode And Edit Mode 7 Controls 8 Cameras
Cooperative UAVs for Remote Data Collection and Relay
 Cooperative UAVs for Remote Data Collection and Relay Kevin L. Moore Michael J. White, Robert J. Bamberger, and David P. Watson Systems and Information Science Group Research and Technology Development
Cooperative UAVs for Remote Data Collection and Relay Kevin L. Moore Michael J. White, Robert J. Bamberger, and David P. Watson Systems and Information Science Group Research and Technology Development
SIVAQ. Manufacturing Status Review
 SIVAQ Manufacturing Status Review Project Overview 2 Mission Statement: Augment the capabilities of the Parrot AR Drone 2.0 such that it flies autonomously with a predetermined flight path, records data,
SIVAQ Manufacturing Status Review Project Overview 2 Mission Statement: Augment the capabilities of the Parrot AR Drone 2.0 such that it flies autonomously with a predetermined flight path, records data,
BMS Digital Microwave Solutions for National Security & Defense
 BMS Digital Microwave Solutions for National Security & Defense Broadcast Microwave Services, Inc. P.O. Box 84630 San Diego, CA 92138 Phone: +1.800.669.9667 Email: [email protected] Web: www.bms-inc.com
BMS Digital Microwave Solutions for National Security & Defense Broadcast Microwave Services, Inc. P.O. Box 84630 San Diego, CA 92138 Phone: +1.800.669.9667 Email: [email protected] Web: www.bms-inc.com
Revision Number Revision Date Insertion Date/Initials 1 st Ed. Feb 01, 00 2 nd Ed. Jun 24, 02 3rd Ed. Feb 15, 07
 List of Effective Pages * Asterisk indicates pages changed, added, or deleted by current revision. Retain this record in front of handbook. Upon receipt of a Record of Revisions revision, insert changes
List of Effective Pages * Asterisk indicates pages changed, added, or deleted by current revision. Retain this record in front of handbook. Upon receipt of a Record of Revisions revision, insert changes
Application for Special Flight Operations Certificate File # ABC123. Company Name Address Phone Email
 Application for Special Flight Operations Certificate File # ABC123 Company Name Address Phone Email NOTE: This sample is provided as is by flitelab.com It is meant for reference only. It should only be
Application for Special Flight Operations Certificate File # ABC123 Company Name Address Phone Email NOTE: This sample is provided as is by flitelab.com It is meant for reference only. It should only be
AP Series Autopilot System. AP-202 Data Sheet. March,2015. Chengdu Jouav Automation Tech Co.,L.t.d
 AP Series Autopilot System AP-202 Data Sheet March,2015 Chengdu Jouav Automation Tech Co.,L.t.d AP-202 autopilot,from Chengdu Jouav Automation Tech Co., Ltd, provides complete professional-level flight
AP Series Autopilot System AP-202 Data Sheet March,2015 Chengdu Jouav Automation Tech Co.,L.t.d AP-202 autopilot,from Chengdu Jouav Automation Tech Co., Ltd, provides complete professional-level flight
Kevin Ortega, David Stone Department of Computer Science, California State Polytechnic University, Pomona, CA 91768
 Cal Poly Pomona's Unmanned Aerial System Design Approach and Implementation for Use in the 2012 AUVSI Student Unmanned Aerial Systems (SUAS) Competition Dr. Subodh Bhandari (Advisor), Jake Dayton, Kelechi
Cal Poly Pomona's Unmanned Aerial System Design Approach and Implementation for Use in the 2012 AUVSI Student Unmanned Aerial Systems (SUAS) Competition Dr. Subodh Bhandari (Advisor), Jake Dayton, Kelechi
Cyber Watch. Written by Peter Buxbaum
 Cyber Watch Written by Peter Buxbaum Security is a challenge for every agency, said Stanley Tyliszczak, vice president for technology integration at General Dynamics Information Technology. There needs
Cyber Watch Written by Peter Buxbaum Security is a challenge for every agency, said Stanley Tyliszczak, vice president for technology integration at General Dynamics Information Technology. There needs
UAV Data Links Present and Future. Broadband Satellite Terminal (BST)
 UAV Data Links Present and Future Broadband Satellite Terminal (BST) Outline of the presentation Speaker: Barry RP Jackson COO Cahon Systems Inc. Outline: First Where we are today. Second Where are we
UAV Data Links Present and Future Broadband Satellite Terminal (BST) Outline of the presentation Speaker: Barry RP Jackson COO Cahon Systems Inc. Outline: First Where we are today. Second Where are we
SAFETY ADVISOR UAS IN THE USA MANNED & UNMANNED AIRCRAFT FLYING TOGETHER SAFELY
 AIR SAFETY INSTITUTE 421 AVIATION WAY, FREDERICK, MD 21701 800.638.3103 AIRSAFETYINSTITUTE.ORG SAFETY ADVISOR A DIVISION OF THE AOPA FOUNDATION UAS IN THE USA MANNED & UNMANNED AIRCRAFT FLYING TOGETHER
AIR SAFETY INSTITUTE 421 AVIATION WAY, FREDERICK, MD 21701 800.638.3103 AIRSAFETYINSTITUTE.ORG SAFETY ADVISOR A DIVISION OF THE AOPA FOUNDATION UAS IN THE USA MANNED & UNMANNED AIRCRAFT FLYING TOGETHER
What is LOG Storm and what is it useful for?
 What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
Why it may be time to consider Certified Avionics for UAS (Unmanned Aerial Vehicles/Systems) White paper
 Why it may be time to consider Certified Avionics for UAS (Unmanned Aerial Vehicles/Systems) White paper UAS growth There are a number of different UAS types flying today in multiple applications. There
Why it may be time to consider Certified Avionics for UAS (Unmanned Aerial Vehicles/Systems) White paper UAS growth There are a number of different UAS types flying today in multiple applications. There
Honeywell Video Analytics
 INTELLIGENT VIDEO ANALYTICS Honeywell s suite of video analytics products enables enhanced security and surveillance solutions by automatically monitoring video for specific people, vehicles, objects and
INTELLIGENT VIDEO ANALYTICS Honeywell s suite of video analytics products enables enhanced security and surveillance solutions by automatically monitoring video for specific people, vehicles, objects and
CHAPTER 1 INTRODUCTION
 CHAPTER 1 INTRODUCTION 1.1 Background of the Research Agile and precise maneuverability of helicopters makes them useful for many critical tasks ranging from rescue and law enforcement task to inspection
CHAPTER 1 INTRODUCTION 1.1 Background of the Research Agile and precise maneuverability of helicopters makes them useful for many critical tasks ranging from rescue and law enforcement task to inspection
TAMU-CC UAS Program 1
 TAMU-CC UAS Program 1 TAMU-CC Major Research Initiatives Coastal & Marine Economic & environmental sustainability Ecosystem evaluation Shoreline mapping Water supply studies Policy Engineering Science
TAMU-CC UAS Program 1 TAMU-CC Major Research Initiatives Coastal & Marine Economic & environmental sustainability Ecosystem evaluation Shoreline mapping Water supply studies Policy Engineering Science
Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles
 Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles Alan Kim, Brandon Wampler, James Goppert, and Inseok Hwang Purdue University, West Lafayette, Indiana, 797, United States Hal Aldridge
Cyber Attack Vulnerabilities Analysis for Unmanned Aerial Vehicles Alan Kim, Brandon Wampler, James Goppert, and Inseok Hwang Purdue University, West Lafayette, Indiana, 797, United States Hal Aldridge
Open Architecture Design for GPS Applications Yves Théroux, BAE Systems Canada
 Open Architecture Design for GPS Applications Yves Théroux, BAE Systems Canada BIOGRAPHY Yves Théroux, a Project Engineer with BAE Systems Canada (BSC) has eight years of experience in the design, qualification,
Open Architecture Design for GPS Applications Yves Théroux, BAE Systems Canada BIOGRAPHY Yves Théroux, a Project Engineer with BAE Systems Canada (BSC) has eight years of experience in the design, qualification,
Development of Knowledge-Based Software for UAV Autopilot Design
 Development of Knowledge-Based Software for UAV Autopilot Design George Tarrant Director CLOSED LOOP SYSTEMS Health Warning Autopilot design is a technical subject. In this paper, I have tried to translate
Development of Knowledge-Based Software for UAV Autopilot Design George Tarrant Director CLOSED LOOP SYSTEMS Health Warning Autopilot design is a technical subject. In this paper, I have tried to translate
White Paper VoIP Crash Phone Systems
 White Paper VoIP Crash Phone Systems John Purnell March 1 st, 2015 Page 2 of 10 Contents 1.0 Executive Summary... 3 2.0 Abbreviations and Definitions... 3 3.0 What is a Crash Phone System?... 4 4.0 Technology
White Paper VoIP Crash Phone Systems John Purnell March 1 st, 2015 Page 2 of 10 Contents 1.0 Executive Summary... 3 2.0 Abbreviations and Definitions... 3 3.0 What is a Crash Phone System?... 4 4.0 Technology
Warszawy 8, 35-959 Rzeszów, Poland
 Solid State Phenomena Vols. 147-149 (2009) pp 231-236 Online available since 2009/Jan/06 at www.scientific.net (2009) Trans Tech Publications, Switzerland doi:10.4028/www.scientific.net/ssp.147-149.231
Solid State Phenomena Vols. 147-149 (2009) pp 231-236 Online available since 2009/Jan/06 at www.scientific.net (2009) Trans Tech Publications, Switzerland doi:10.4028/www.scientific.net/ssp.147-149.231
Autonomous Advertising Mobile Robot for Exhibitions, Developed at BMF
 Autonomous Advertising Mobile Robot for Exhibitions, Developed at BMF Kucsera Péter ([email protected]) Abstract In this article an autonomous advertising mobile robot that has been realized in
Autonomous Advertising Mobile Robot for Exhibitions, Developed at BMF Kucsera Péter ([email protected]) Abstract In this article an autonomous advertising mobile robot that has been realized in
WIRELESS SECURITY. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 WIRELESS SECURITY Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Wireless LAN Security Learning Objectives Students should be able
WIRELESS SECURITY Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Wireless LAN Security Learning Objectives Students should be able
RPV/UAV Surveillance for Transportation Management and Security
 RPV/UAV Surveillance for Transportation Management and Security Final Report Prepared by: Demoz Gebre-Egziabher Department of Aerospace Engineering & Mechanics University of Minnesota CTS 08-27 Technical
RPV/UAV Surveillance for Transportation Management and Security Final Report Prepared by: Demoz Gebre-Egziabher Department of Aerospace Engineering & Mechanics University of Minnesota CTS 08-27 Technical
TM Advanced Tracking Technologies, Inc. 2003 ATTI All rights reserved
 TM Advanced Tracking Technologies, Inc. 2003 ATTI All rights reserved Copyright 2003, Advanced Tracking Technologies, Inc. All rights reserved. No part of this publication may be reproduced or transmitted
TM Advanced Tracking Technologies, Inc. 2003 ATTI All rights reserved Copyright 2003, Advanced Tracking Technologies, Inc. All rights reserved. No part of this publication may be reproduced or transmitted
Digital Single Axis Controller
 Digital Single Axis Controller The concept of intelligent hydraulic drive a vision? DSAC (Digital Single Axis Controller) Do you need hydraulic servo drive for your machine/system? What would it be like
Digital Single Axis Controller The concept of intelligent hydraulic drive a vision? DSAC (Digital Single Axis Controller) Do you need hydraulic servo drive for your machine/system? What would it be like
On-Premises DDoS Mitigation for the Enterprise
 On-Premises DDoS Mitigation for the Enterprise FIRST LINE OF DEFENSE Pocket Guide The Challenge There is no doubt that cyber-attacks are growing in complexity and sophistication. As a result, a need has
On-Premises DDoS Mitigation for the Enterprise FIRST LINE OF DEFENSE Pocket Guide The Challenge There is no doubt that cyber-attacks are growing in complexity and sophistication. As a result, a need has
NETWORK TECHNOLOGY. Long Range Radio Networks
 NETWORK TECHNOLOGY Long Range Radio Networks The essence of the Radio Network installed by Safe Link is the sophisticated radio repeaters used in the system and the proprietary software which controls
NETWORK TECHNOLOGY Long Range Radio Networks The essence of the Radio Network installed by Safe Link is the sophisticated radio repeaters used in the system and the proprietary software which controls
APPLICATION CASE OF THE END-TO-END RELAY TESTING USING GPS-SYNCHRONIZED SECONDARY INJECTION IN COMMUNICATION BASED PROTECTION SCHEMES
 APPLICATION CASE OF THE END-TO-END RELAY TESTING USING GPS-SYNCHRONIZED SECONDARY INJECTION IN COMMUNICATION BASED PROTECTION SCHEMES J. Ariza G. Ibarra Megger, USA CFE, Mexico Abstract This paper reviews
APPLICATION CASE OF THE END-TO-END RELAY TESTING USING GPS-SYNCHRONIZED SECONDARY INJECTION IN COMMUNICATION BASED PROTECTION SCHEMES J. Ariza G. Ibarra Megger, USA CFE, Mexico Abstract This paper reviews
Data Review and Analysis Program (DRAP) Flight Data Visualization Program for Enhancement of FOQA
 86 Data Review and Analysis Program (DRAP) Flight Data Visualization Program for Enhancement of FOQA Koji MURAOKA and Noriaki OKADA, Flight Systems Research Center, E-mail: [email protected] Keywords:
86 Data Review and Analysis Program (DRAP) Flight Data Visualization Program for Enhancement of FOQA Koji MURAOKA and Noriaki OKADA, Flight Systems Research Center, E-mail: [email protected] Keywords:
Deploying VSaaS and Hosted Solutions Using CompleteView
 SALIENT SYSTEMS WHITE PAPER Deploying VSaaS and Hosted Solutions Using CompleteView Understanding the benefits of CompleteView for hosted solutions and successful deployment architecture Salient Systems
SALIENT SYSTEMS WHITE PAPER Deploying VSaaS and Hosted Solutions Using CompleteView Understanding the benefits of CompleteView for hosted solutions and successful deployment architecture Salient Systems
The 7 th International Scientific Conference DEFENSE RESOURCES MANAGEMENT IN THE 21st CENTURY Braşov, November 15 th 2012
 The 7 th International Scientific Conference DEFENSE RESOURCES MANAGEMENT IN THE 21st CENTURY Braşov, November 15 th 2012 COMMUNICATION ISSUES OF UAV 1 INTEGRATION INTO NON 1 st. Lt. Gábor Pongrácz, ATM
The 7 th International Scientific Conference DEFENSE RESOURCES MANAGEMENT IN THE 21st CENTURY Braşov, November 15 th 2012 COMMUNICATION ISSUES OF UAV 1 INTEGRATION INTO NON 1 st. Lt. Gábor Pongrácz, ATM
S-Tec System Thirty Autopilot
 Cirrus Design Section 9 Pilot s Operating Handbook and FAA Approved Airplane Flight Manual Supplement for S-Tec System Thirty Autopilot When the S-Tec System Thirty Autopilot is installed in the Cirrus
Cirrus Design Section 9 Pilot s Operating Handbook and FAA Approved Airplane Flight Manual Supplement for S-Tec System Thirty Autopilot When the S-Tec System Thirty Autopilot is installed in the Cirrus
UAVNet: Prototype of a Highly Adaptive and Mobile Wireless Mesh Network using Unmanned Aerial Vehicles (UAVs) Simon Morgenthaler University of Bern
 UAVNet: Prototype of a Highly Adaptive and Mobile Wireless Mesh Network using Unmanned Aerial Vehicles (UAVs) Simon Morgenthaler University of Bern Dez 19, 2011 Outline Introduction Related Work Mikrokopter
UAVNet: Prototype of a Highly Adaptive and Mobile Wireless Mesh Network using Unmanned Aerial Vehicles (UAVs) Simon Morgenthaler University of Bern Dez 19, 2011 Outline Introduction Related Work Mikrokopter
Propsim enabled Mobile Ad-hoc Network Testing
 www.anite.com Propsim enabled Mobile Ad-hoc Network Testing Anite is now part of Keysight Technologies Lab-based, end-to-end performance testing of systems using Propsim MANET channel emulation A Mobile
www.anite.com Propsim enabled Mobile Ad-hoc Network Testing Anite is now part of Keysight Technologies Lab-based, end-to-end performance testing of systems using Propsim MANET channel emulation A Mobile
How To Make An Integrated System For An Unmanned Aircraft System
 Insitu Unmanned Aircraft Soars to New Heights with PTC Integrity Insitu Inc. Demand for Insitu unmanned aircraft systems (UAS) is soaring due to their portability, small size and customizability. This
Insitu Unmanned Aircraft Soars to New Heights with PTC Integrity Insitu Inc. Demand for Insitu unmanned aircraft systems (UAS) is soaring due to their portability, small size and customizability. This
Civil Aviation and CyberSecurity Dr. Daniel P. Johnson Honeywell Aerospace Advanced Technology
 Civil Aviation and CyberSecurity Dr. Daniel P. Johnson Honeywell Aerospace Advanced Technology Outline Scope Civil aviation regulation History Cybersecurity threats Cybersecurity controls and technology
Civil Aviation and CyberSecurity Dr. Daniel P. Johnson Honeywell Aerospace Advanced Technology Outline Scope Civil aviation regulation History Cybersecurity threats Cybersecurity controls and technology
ARM-UAV Mission Gateway System
 ARM-UAV Mission Gateway System S. T. Moore and S. Bottone Mission Research Corporation Santa Barbara, California Introduction The Atmospheric Radiation Measurement-unmanned aerospace vehicle (ARM-UAV)
ARM-UAV Mission Gateway System S. T. Moore and S. Bottone Mission Research Corporation Santa Barbara, California Introduction The Atmospheric Radiation Measurement-unmanned aerospace vehicle (ARM-UAV)
Henry H. Perritt, Jr. Attorney at Law 1131 Carol Lane Glencoe, IL 60022 [email protected] (312) 504-5001 12 August 2014
 Henry H. Perritt, Jr. Attorney at Law 1131 Carol Lane Glencoe, IL 60022 [email protected] (312) 504-5001 12 August 2014 Hon. Michael Huerta Administrator Federal Aviation Administration U. S. Department
Henry H. Perritt, Jr. Attorney at Law 1131 Carol Lane Glencoe, IL 60022 [email protected] (312) 504-5001 12 August 2014 Hon. Michael Huerta Administrator Federal Aviation Administration U. S. Department
11 Distress and Urgency
 11 Distress and Urgency COMMUNICATIONS 11.1 Definitions Distress Distress is defined as a condition of being threatened by serious and/or imminent danger and of requiring immediate assistance. Urgency
11 Distress and Urgency COMMUNICATIONS 11.1 Definitions Distress Distress is defined as a condition of being threatened by serious and/or imminent danger and of requiring immediate assistance. Urgency
UAS OPERATORS INSURANCE PROPOSAL FORM
 GLOSSARY ATC Air Traffic Control CAA Civil Aviation Authority Comms Abv. Communications GCS Ground Control Station. Including launch system, flight control and mission specific hardware & software, communications
GLOSSARY ATC Air Traffic Control CAA Civil Aviation Authority Comms Abv. Communications GCS Ground Control Station. Including launch system, flight control and mission specific hardware & software, communications
AeroVironment, Inc. Unmanned Aircraft Systems Overview Background
 AeroVironment, Inc. Unmanned Aircraft Systems Overview Background AeroVironment is a technology solutions provider with a more than 40-year history of practical innovation in the fields of unmanned aircraft
AeroVironment, Inc. Unmanned Aircraft Systems Overview Background AeroVironment is a technology solutions provider with a more than 40-year history of practical innovation in the fields of unmanned aircraft
Remote Area Tracking and Mapping
 Remote Area Tracking and Mapping TM3000 with Iridium Satellite Back up Communications Step Global has developed a solution to remote area GPS tracking by interfacing the Trimble TM3000 Asset Tracking Device
Remote Area Tracking and Mapping TM3000 with Iridium Satellite Back up Communications Step Global has developed a solution to remote area GPS tracking by interfacing the Trimble TM3000 Asset Tracking Device
SIX DEGREE-OF-FREEDOM MODELING OF AN UNINHABITED AERIAL VEHICLE. A thesis presented to. the faculty of
 SIX DEGREE-OF-FREEDOM MODELING OF AN UNINHABITED AERIAL VEHICLE A thesis presented to the faculty of the Russ College of Engineering and Technology of Ohio University In partial fulfillment of the requirement
SIX DEGREE-OF-FREEDOM MODELING OF AN UNINHABITED AERIAL VEHICLE A thesis presented to the faculty of the Russ College of Engineering and Technology of Ohio University In partial fulfillment of the requirement
 IS TEST 3 - TIPS FOUR (4) levels of detective controls offered by intrusion detection system (IDS) methodologies. First layer is typically responsible for monitoring the network and network devices. NIDS
IS TEST 3 - TIPS FOUR (4) levels of detective controls offered by intrusion detection system (IDS) methodologies. First layer is typically responsible for monitoring the network and network devices. NIDS
ASTRAEA the findings so far
 ASTRAEA the findings so far Lambert Dopping- Hepenstal, FREng RPAS CivOps 2014 3 rd December 2014 Contents The ASTRAEA programme Regulatory engagement Programme achievement examples Communications Detect
ASTRAEA the findings so far Lambert Dopping- Hepenstal, FREng RPAS CivOps 2014 3 rd December 2014 Contents The ASTRAEA programme Regulatory engagement Programme achievement examples Communications Detect
3 Software Defined Radio Technologies
 3 Software Defined Radio Technologies 3-1 Software Defined Radio for Next Generation Seamless Mobile Communication Systems In this paper, the configuration of the newly developed small-size software defined
3 Software Defined Radio Technologies 3-1 Software Defined Radio for Next Generation Seamless Mobile Communication Systems In this paper, the configuration of the newly developed small-size software defined
WHICH AIR TRAFFIC CONTROLLER TO CONTACT
 WHICH AIR TRAFFIC CONTROLLER TO CONTACT 1. Introduction This article is written in order to explain to all beginners in the IVAO network the basics for any pilot to contact the correct air traffic controller.
WHICH AIR TRAFFIC CONTROLLER TO CONTACT 1. Introduction This article is written in order to explain to all beginners in the IVAO network the basics for any pilot to contact the correct air traffic controller.
2.0 Command and Data Handling Subsystem
 2.0 Command and Data Handling Subsystem The Command and Data Handling Subsystem is the brain of the whole autonomous CubeSat. The C&DH system consists of an Onboard Computer, OBC, which controls the operation
2.0 Command and Data Handling Subsystem The Command and Data Handling Subsystem is the brain of the whole autonomous CubeSat. The C&DH system consists of an Onboard Computer, OBC, which controls the operation
SANS Top 20 Critical Controls for Effective Cyber Defense
 WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
Table of Contents 1. INTRODUCTION 2 2. DEFINITION 4 3. UAS CLASSIFICATION 6 4. REGULATORY PRINCIPLES 16 5. INTERACTION WITH AIR TRAFFIC CONTROL 16
 FOREWORD Table of Contents 1. INTRODUCTION 2 2. DEFINITION 4 3. UAS CLASSIFICATION 6 4. REGULATORY PRINCIPLES 16 5. INTERACTION WITH AIR TRAFFIC CONTROL 16 6. SENSE AND AVOID ( required for applicants
FOREWORD Table of Contents 1. INTRODUCTION 2 2. DEFINITION 4 3. UAS CLASSIFICATION 6 4. REGULATORY PRINCIPLES 16 5. INTERACTION WITH AIR TRAFFIC CONTROL 16 6. SENSE AND AVOID ( required for applicants
CONNECT PROTECT SECURE. Communication, Networking and Security Solutions for Defense
 CONNECT PROTECT Communication, Networking and Security Solutions for Defense Engage Communication provides Defense, Homeland Security and Intelligence Communities with innovative and cost effective solutions
CONNECT PROTECT Communication, Networking and Security Solutions for Defense Engage Communication provides Defense, Homeland Security and Intelligence Communities with innovative and cost effective solutions
WIRELESS INSTRUMENTATION TECHNOLOGY
 BS&B WIRELESS, L.L.C. BS&B WIRELESS, L.L.C. WIRELESS INSTRUMENTATION TECHNOLOGY Printed February 2004 BS&B WIRELESS, L.L.C. 7422-B East 46th Place, Tulsa, OK74145 Phone: 918-622-5950 Fax: 918-665-3904
BS&B WIRELESS, L.L.C. BS&B WIRELESS, L.L.C. WIRELESS INSTRUMENTATION TECHNOLOGY Printed February 2004 BS&B WIRELESS, L.L.C. 7422-B East 46th Place, Tulsa, OK74145 Phone: 918-622-5950 Fax: 918-665-3904
Primus 880 Weather Radar. Reliable Weather Avoidance Radar
 Primus 880 Weather Radar Reliable Weather Avoidance Radar Honeywell, the world s leader in avionics continues the development of weather radar systems with the Primus 880 featuring 10 kilowatts of transmitter
Primus 880 Weather Radar Reliable Weather Avoidance Radar Honeywell, the world s leader in avionics continues the development of weather radar systems with the Primus 880 featuring 10 kilowatts of transmitter
Position Descriptions. Aerospace
 Position Descriptions Aerospace Aerospace Engineering? Aeromechanics / Flight Control / Flight Qualities Engineer Predict, analyze, and verify air vehicle flight dynamics including aircraft aerodynamics,
Position Descriptions Aerospace Aerospace Engineering? Aeromechanics / Flight Control / Flight Qualities Engineer Predict, analyze, and verify air vehicle flight dynamics including aircraft aerodynamics,
2. From a control perspective, the PRIMARY objective of classifying information assets is to:
 MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
OPNET Network Simulator
 Simulations and Tools for Telecommunications 521365S: OPNET Network Simulator Jarmo Prokkola Research team leader, M. Sc. (Tech.) VTT Technical Research Centre of Finland Kaitoväylä 1, Oulu P.O. Box 1100,
Simulations and Tools for Telecommunications 521365S: OPNET Network Simulator Jarmo Prokkola Research team leader, M. Sc. (Tech.) VTT Technical Research Centre of Finland Kaitoväylä 1, Oulu P.O. Box 1100,
GPS Vehicle and personal location tracker. User manual
 GPS Vehicle and personal location tracker User manual 1 Contents 1. Product overview... 2 2. Safety instruction... 3 3. Specification and parameters... 3 4. Getting started... 4 4.1 Hardware and accessories...
GPS Vehicle and personal location tracker User manual 1 Contents 1. Product overview... 2 2. Safety instruction... 3 3. Specification and parameters... 3 4. Getting started... 4 4.1 Hardware and accessories...
Introduction to the iefis Explorer
 Introduction to the iefis Explorer A brief primer to the new iefis Explorer from MGL Avionics The Explorer EFIS introduces a custom developed touch pressure sensitive LCD screen aimed exclusively at the
Introduction to the iefis Explorer A brief primer to the new iefis Explorer from MGL Avionics The Explorer EFIS introduces a custom developed touch pressure sensitive LCD screen aimed exclusively at the
Why WireFree: Wireless Gas Detection System Basics and Benefits
 Why WireFree: Wireless Gas Detection System Basics and Benefits Anyone who needs gas detection can benefit from using a wireless system. Whether you re just being introduced to the gas detection market,
Why WireFree: Wireless Gas Detection System Basics and Benefits Anyone who needs gas detection can benefit from using a wireless system. Whether you re just being introduced to the gas detection market,
SelectTech GeoSpatial Advanced Manufacturing Facility (AMF) Springfield / Beckley Airport Springfield, Ohio
 SelectTech GeoSpatial Advanced Manufacturing Facility (AMF) Springfield / Beckley Airport Springfield, Ohio History SelectTech Services Corporation is Dayton-based small business dedicated to providing
SelectTech GeoSpatial Advanced Manufacturing Facility (AMF) Springfield / Beckley Airport Springfield, Ohio History SelectTech Services Corporation is Dayton-based small business dedicated to providing
Electric utilities may vary in their application of end-to-end testing
 An Application Case of End-to-End Relay Testing of Communication-Based Protection Schemes Using GPS-Synchronized Secondary Injection Feature by J. Ariza, Megger USA G. Ibarra, CFE, Mexico Electric utilities
An Application Case of End-to-End Relay Testing of Communication-Based Protection Schemes Using GPS-Synchronized Secondary Injection Feature by J. Ariza, Megger USA G. Ibarra, CFE, Mexico Electric utilities
Product Characteristics Page 2. Management & Administration Page 2. Real-Time Detections & Alerts Page 4. Video Search Page 6
 Data Sheet savvi Version 5.3 savvi TM is a unified video analytics software solution that offers a wide variety of analytics functionalities through a single, easy to use platform that integrates with
Data Sheet savvi Version 5.3 savvi TM is a unified video analytics software solution that offers a wide variety of analytics functionalities through a single, easy to use platform that integrates with
Service, Security, Solutions Since 1924. Insurance and Risk Management Considerations for UAS RPAS Symposium, Montreal. March 2015
 Service, Security, Solutions Since 1924 Insurance and Risk Management Considerations for UAS RPAS Symposium, Montreal Global Aerospace Begins Spirit of St. Louis First Transatlantic flight by unmanned
Service, Security, Solutions Since 1924 Insurance and Risk Management Considerations for UAS RPAS Symposium, Montreal Global Aerospace Begins Spirit of St. Louis First Transatlantic flight by unmanned
A GUIDE ON HOW TO CHOOSE A DRONE / UAV OPERATOR FOR YOUR TV, FILM, VIDEO OR MEDIA PRODUCTION.
 A GUIDE ON HOW TO CHOOSE A DRONE / UAV OPERATOR FOR YOUR TV, FILM, VIDEO OR MEDIA PRODUCTION. Ver1.5 21st of Sept 2015 Copyright 2015 Sky View Video (Scotland) All rights reserved. We grant you limited
A GUIDE ON HOW TO CHOOSE A DRONE / UAV OPERATOR FOR YOUR TV, FILM, VIDEO OR MEDIA PRODUCTION. Ver1.5 21st of Sept 2015 Copyright 2015 Sky View Video (Scotland) All rights reserved. We grant you limited
3D Vision An enabling Technology for Advanced Driver Assistance and Autonomous Offroad Driving
 3D Vision An enabling Technology for Advanced Driver Assistance and Autonomous Offroad Driving AIT Austrian Institute of Technology Safety & Security Department Christian Zinner Safe and Autonomous Systems
3D Vision An enabling Technology for Advanced Driver Assistance and Autonomous Offroad Driving AIT Austrian Institute of Technology Safety & Security Department Christian Zinner Safe and Autonomous Systems
Date: 07/20/07 Initiated by: AFS-800
 Advisory Circular Subject: Use of Class 1 or Class 2 Electronic Flight Bag (EFB) Date: 07/20/07 Initiated by: AFS-800 AC No: 91-78 1. PURPOSE. This advisory circular (AC) provides aircraft owners, operators,
Advisory Circular Subject: Use of Class 1 or Class 2 Electronic Flight Bag (EFB) Date: 07/20/07 Initiated by: AFS-800 AC No: 91-78 1. PURPOSE. This advisory circular (AC) provides aircraft owners, operators,
DKWF121 WF121-A 802.11 B/G/N MODULE EVALUATION BOARD
 DKWF121 WF121-A 802.11 B/G/N MODULE EVALUATION BOARD PRELIMINARY DATA SHEET Wednesday, 16 May 2012 Version 0.5 Copyright 2000-2012 Bluegiga Technologies All rights reserved. Bluegiga Technologies assumes
DKWF121 WF121-A 802.11 B/G/N MODULE EVALUATION BOARD PRELIMINARY DATA SHEET Wednesday, 16 May 2012 Version 0.5 Copyright 2000-2012 Bluegiga Technologies All rights reserved. Bluegiga Technologies assumes
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0
 Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
2.4G Bluetooth Datalink & ipad Ground Station User Guide V1.12
 2.4G Bluetooth Datalink & ipad Ground Station User Guide V1.12 Thank you for purchasing DJI products. Please strictly follow this user guide to mount and connect the 2.4G Bluetooth Datalink, install the
2.4G Bluetooth Datalink & ipad Ground Station User Guide V1.12 Thank you for purchasing DJI products. Please strictly follow this user guide to mount and connect the 2.4G Bluetooth Datalink, install the
INSPIRE 1 Release Notes 2015.9.7. Overview: What s New: Bug Fixes: Notice: 1. All-in-One Firmware version updated to: v1.4.0.10
 2015.9.7 1. All-in-One Firmware version updated to: v1.4.0.10 What s New: 1. Added Intelligent Navigation Modes including Point of Interest and Waypoint. 2. A three minute cool down period is triggered
2015.9.7 1. All-in-One Firmware version updated to: v1.4.0.10 What s New: 1. Added Intelligent Navigation Modes including Point of Interest and Waypoint. 2. A three minute cool down period is triggered
Autonomous Navigated Global Positioning System Based Surveillance Unmanned Aerial Vehicle
 Volume 1, Issue 1 December 2012 ISSN: - 2306-708X Autonomous Navigated Global Positioning System Based Surveillance Unmanned Aerial Vehicle Abdul Qayyum and Moona Mazher Department of Computer Science,
Volume 1, Issue 1 December 2012 ISSN: - 2306-708X Autonomous Navigated Global Positioning System Based Surveillance Unmanned Aerial Vehicle Abdul Qayyum and Moona Mazher Department of Computer Science,
Closing Wireless Loopholes for PCI Compliance and Security
 Closing Wireless Loopholes for PCI Compliance and Security Personal information is under attack by hackers, and credit card information is among the most valuable. While enterprises have had years to develop
Closing Wireless Loopholes for PCI Compliance and Security Personal information is under attack by hackers, and credit card information is among the most valuable. While enterprises have had years to develop
Special Topics in Security and Privacy of Medical Information. Reminders. Medical device security. Sujata Garera
 Special Topics in Security and Privacy of Medical Information Sujata Garera Reminders Assignment due today Project part 1 due on next Tuesday Assignment 2 will be online today evening 2nd Discussion session
Special Topics in Security and Privacy of Medical Information Sujata Garera Reminders Assignment due today Project part 1 due on next Tuesday Assignment 2 will be online today evening 2nd Discussion session
User Manual. NETGEAR, Inc. 350 East Plumeria Drive San Jose, CA 95134, USA. December 2014 202-11380-01
 User Manual December 2014 202-11380-01 NETGEAR, Inc. 350 East Plumeria Drive San Jose, CA 95134, USA Support For product updates and web support, visit http://support.arlo.com. Trademarks NETGEAR, Inc.
User Manual December 2014 202-11380-01 NETGEAR, Inc. 350 East Plumeria Drive San Jose, CA 95134, USA Support For product updates and web support, visit http://support.arlo.com. Trademarks NETGEAR, Inc.
NASCIO 2015 State IT Recognition Awards
 NASCIO 2015 State IT Recognition Awards Title: State of Georgia Private Security Cloud Implementation Category: Cybersecurity Contact: Mr. Calvin Rhodes CIO, State of Georgia Executive Director, GTA [email protected]
NASCIO 2015 State IT Recognition Awards Title: State of Georgia Private Security Cloud Implementation Category: Cybersecurity Contact: Mr. Calvin Rhodes CIO, State of Georgia Executive Director, GTA [email protected]
Bi-Directional DGPS for Range Safety Applications
 Bi-Directional DGPS for Range Safety Applications Ranjeet Shetty 234-A, Avionics Engineering Center, Russ College of Engineering and Technology, Ohio University Advisor: Dr. Chris Bartone Outline Background
Bi-Directional DGPS for Range Safety Applications Ranjeet Shetty 234-A, Avionics Engineering Center, Russ College of Engineering and Technology, Ohio University Advisor: Dr. Chris Bartone Outline Background
Performance-based Navigation and Data Quality
 ICAO APAC AAITF/8 Performance-based Navigation and Data Quality A Commercial Data Supplier View Bill Kellogg International Relations May 6-10, 2013 Ulaanbaatar, Mongolia Jeppesen Proprietary - Copyright
ICAO APAC AAITF/8 Performance-based Navigation and Data Quality A Commercial Data Supplier View Bill Kellogg International Relations May 6-10, 2013 Ulaanbaatar, Mongolia Jeppesen Proprietary - Copyright
Developing Fleet and Asset Tracking Solutions with Web Maps
 Developing Fleet and Asset Tracking Solutions with Web Maps Introduction Many organizations have mobile field staff that perform business processes away from the office which include sales, service, maintenance,
Developing Fleet and Asset Tracking Solutions with Web Maps Introduction Many organizations have mobile field staff that perform business processes away from the office which include sales, service, maintenance,
UNCLASSIFIED Version 1.0 May 2012
 Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
