Optimising Internet Bandwidth in Developing Country Higher Education
|
|
|
- Bertram Beasley
- 10 years ago
- Views:
Transcription
1 Optimising Internet Bandwidth in Developing Country Higher Education by The International Network for the Availability of Scientific Publications (INASP) A study presented at the Regional Training Conference on Improving Tertiary Education in Sub-Saharan Africa: Things That Work! Accra, September 23-25, 2003 Financial and material support for this training activity were generously provided by the ADEA Working Group on Higher Education, the Association of African Universities, the Agence Universitaire de la Francophonie, the Carnegie Corporation of New York, the Ghana National Council for Tertiary Education, the Government of the Netherlands, the International Network for the Availability of Scientific Publications, the Norwegian Education Trust Fund, and the World Bank.
2
3 Optimising Internet Bandwidth in Developing Country Higher Education Higher education institutions in developing countries have to deal with growing demands on their Internet infrastructures. Managing this demand usually requires that infrastructure telecommunications, computers, etc. is upgraded and extended. However, since this can be costly, other approaches need to be pursued. This report argues that, through better understanding of actual Internet usage, improved management of Internet applications, enhanced training and awarenessraising for users, and the introduction of measures to control undesirable uses and behaviours, existing bandwidth can be made to go much further. Pressures on performance With wider Internet connectivity, educational institutions in developing countries are beginning to tap the many opportunities offered by today s information societies. These digital connections act as gateways where researchers and librarians can find, download and share world knowledge and learning materials; they can be platforms where local research is published, disseminated and uploaded; and they can facilitate links and collaboration among scientists, promoting discourse and dialogue on shared issues and problems. However, the same connectivity also supports all sorts of applications and behaviours that consume bandwidth. For example, it helps to distribute spam and viruses, it allows music lovers and sports fans to keep up with their hobbies and favourite artistes from around the world, it can be used to view pornography, it can provide opportunities for computer hackers to practice their skills, and it facilitates crossborder movement by all kinds of intelligent software, agents, worms and spiders harvesting and indexing content or simply tracking usage and offering upgrades. Where these applications hamper the intended uses of the Internet conection, it can be termed abuse. These, and many other applications, all consume the limited bandwidth of higher education institutions in developing countries. As a result, response times slow down and performance drops, leading to frustrated users and IT managers. Most researchers, information providers and institutions remain unable to access the high speed, broadband connectivity that is more and more necessary for research, teaching, and learning. Typical solutions are to upgrade infrastructure, to install faster, larger, and higher performing systems, lines and facilities. However these are costly solutions, and may only solve short-term needs. As demand continues to grow, and as overall available bandwidth shrinks, performance will again decline, necessitating further upgrades. Bandwidth in developing countries is expensive. In a report for the Partnership for Higher Education in Africa, Mike Jensen calculates that Makerere University pays about $22,000/month for 1.5Mbps/768Kbps (in/out), Eduardo Mondlane pays $10,000/month for 1Mbps/384Kbps, while the University of Ghana pays $10,000/month for 1Mbps/512Kbps. These figuresindicate that African universities, outside of South Africa, are paying over $55,000/month for 4Mbps inbound and 2Mbps outbound. These figures are about 100 times more expensive than equivalent prices in North America or Europe. Clearly, one solution to controlling costs and improving access is to press for more affordable access by, for instance: suggesting that Governments open up their telecommunications markets; by joining forces with other academic institutions to negotiate better connectivity deals; by encouraging local Internet service providers to set up country Internet exchange points that route traffic within the country instead of Page 1 of 5
4 via Europe and North America; and by making use of open source systems and software. A different approach? An alternative response is to recognise that bandwidth is a valuable institutional resource or asset that needs to be managed, conserved, and shared as effectively as possible. Instead of simply extending computer and network infrastructure, or finding cheaper providers, this approach puts emphasis on ways to control and manage the many hungry Internet applications, uses, and practices that consume bandwidth. Such an approach has technical implications regarding network configuration and management. Suitable policies and guidelines are also needed to encourage proper bandwidth saving behaviour. Most critical, it requires that people with the necessary technical expertise and understanding of users needs are available to the organisation. Making a better use of bandwidth helps to ensure that high priority applications get the access and the performance that they need when it is needed. A cross-country study This report draws on a report commissioned by INASP in response to the concerns of partner organisations in Africa, Asia and Latin America. The report was prepared with input from eight countries (from Africa, Asia and Europe), and has been written for three main audiences senior management, librarians, and ICT managers. It first identifies access problems in university environments, and then explains why access is frequently slow and costly, and how it can be affected by government policies as well as by other regulatory and economic restrictions. Finally, the report identifies how each stakeholder group can influence and improve online access within their institution. For management, the report explains the institutional decisions that need to be made, including the purchase of bandwidth and delivery of Internet services (cable, satellite or wireless). The question of usage policies is discussed, including enforcement measures and incentives that help to ensure that all users are aware of their responsibilities and how their actions impinge on others. The various possibilities related to charging users for Internet access are also discussed, along with possible revenue generating options to subsidise such services. The report also looks at the roles that librarians need to play in the provision of Internet access as part of their information services, and what questions they need to ask of ICT and management in order to ensure that their goals are met. Ways in which ICT staff can improve how they configure, manage, monitor and control their networks are also presented. The full report contains eight case studies of Internet optimisation. Each gives first-hand experience of bandwidth problems and solutions from various situations (Addis Ababa University, Ethiopia; Malawi College of Medicine; the Multilateral Initiative on Malaria network (MIMCOM); University of Zululand, South Africa; University of Moratuwa, Sri Lanka, University of Dar es Salaam, Tanzania; Makerere University, Uganda; and the University of Bristol, UK). Recommendations The findings of the report are summarised below, presented as recommendations for each of the stakeholder groups: management, information service providers, and IT staff. Recommendations for senior management Make bandwidth management a priority. Ask questions concerning Internet and network usage, security, and user behaviour. Reward staff that install the often unglamorous applications that help to conserve and share this scarce resource. Be safe. Insist on strong network and server security, firewalls, and virus protection. Once an undesirable has access to the system, any nightmare is possible. Respond to demands. Understand why and how different users make use of the Internet, prioritise among user categories and among applications, and help users to be more effective by providing appropriate training. Expect regular usage reports so that everyone knows what the Internet connection is being used for, and so the right decisions can be made when deciding how much bandwidth to get. Encourage positive behaviour. Devise a usage policy to be signed by all users before they use the Internet. This identifies good practices and appropriate netiquette and it sets out procedures to be followed. It should be relevant to the average user and it should be enforced. The existence of such a policy (which explains that browsing and other Internet uses can be monitored), can often be a sufficient scare factor to quell selfish or illegal behaviour. Page 2 of 5
5 Monitor the IT team. Sometimes the IT experts are themselves the biggest abusers of bandwidth. Competent and dedicated IT personnel are essential, not only for normal ICT functions, but also to keep bandwidth use under control. More broadly, a representative high level governance mechanism or committee can be used to set overall ICT policy goals, directions, and priorities. Give everyone an identity. Tracking usage requires that each user of the network have an individual identify or logon that confers rights and responsibilities. It is a relatively small step to also provide each with a unique local address as well as efficient ways to access it from remote locations. Providing such a facility will help to reduce the use of large bandwidth consumers like hotmail and yahoo. Evaluate connection options regularly. Bandwidth becomes cheaper every year. As the price goes down, upgrades enable a university to provide a better Internet service (and to make it available to more users). Moving to another provider or re-negotiating contracts may provide more bandwidth at lower cost. However, the benefits may not outweigh the cost of changing. It is also important to ensure that the contracted and paid for bandwidth is actually being provided. Join forces. Explore network integration create networks between academic institutions within the country that allow for joint bandwidth purchasing, help to keep local traffic local, and lobby for regulatory or other political changes. Recommendations for librarians Obtain an understanding of the technical issues, in order to ask the right questions and to demand an appropriate service from the IT team. Expect usage reports and statistics, and encourage appropriate use through training. Understand what library users are using the Internet for. Get PDF and PostScript reader software installed on library computers, so students can read online journals. Train library users in proper use of the Internet, especially in search techniques. This saves bandwidth by enabling users to find resources more easily. It also enables them to use the Internet productively, and to avoid random browsing. Consider setting up library portals or gateway websites where users are quickly directed to relevant and annotated Internet resources. This reduces random searching and, if local caching is used, saves frequently used resources to the local network. Where feasible, obtain large electronic resources, full text journals databases, or images for example, on CD- ROM or DVD formats, making them available on the local net work. This avoids online downloads that consume bandwidth. When downloading is the only option, do it during quiet times (at night for example). Saved files can then be made available locally (where copyright allows). Recommendations for IT staff Install good security and adopt anti-virus practices that prevent situations where malicious actions cause bandwidth to be used up. Track all relevant aspects of the network, bandwidth and Internet usage. Regular reports help all concerned to understand usage patterns and trends, to pinpoint problems, and to signal potential bottlenecks. Implement content filtering to block undesirable web content such as gaming, pornography and commercial streaming media. can also be restricted, to some extent, to exclude certain types of files or files that are very large. Use proxy servers and local caching DNS servers to keep local copies of previously retrieved web pages and Internet addresses. This prevents a situation where the same page (or address) is retrieved from the Internet several times per day. Use the network to locally manage upgrades and updates. Updates, fixes, and patches for software and systems (as well as commonly used software readers etc.) can be downloaded once to the network and then made available to individual workstations. This avoids situations where users are using international bandwidth to update their computers. Such downloading can be done at night when demand is low; updates to individual workstations can be automated. Make sure all user activities can, if necessary, be traced. This is only possible where there is the network has an authentication system (users must log in before they can do anything). A usage policy should spell out which data on users is collected and how it can be used. Consider implementing a bandwidth manager product that allows you to give bandwidth priority to certain protocols (such as web), and to throttle others (such as Kazaa an application used to share music files). Page 3 of 5
6 Discourage and control certain types of peer to peer networking. Hungry applications like Kazaa need to be rate limited, using a bandwidth manager, or prevented via network layout changes. Offer addresses and web based facilities to users, allowing them to access their s from anywhere if necessary. This reduces the need for staff and students to set up hungry web accounts like hotmail and yahoo. Configure the network to avoid open relay hosts (mail servers that will accept connections from anywhere) and open proxies (proxy servers that will accept connections from anywhere). These can easily be abused by outside interests and can lead to the blacklisting of your network. Ensure that these servers only relay mail or accept connections from the University network. Train all users to use the Internet safely and efficiently. They should especially not reply to spam, and not launch unknown programs they receive via . Encourage bandwidth-conserving behaviour. All users should be aware of the impact they can have when competing aggressively for bandwidth, for example by downloading music. They should realise the potential consequences of their actions to the whole network community. Consider outsourcing and mirroring options. Depending on which audiences the institution wants to reach, separate strategies for internal and external (international) users can be followed. For example, consider directing international users to an international site or server, guarding local bandwidth for local users and applications. Charging for bandwidth may help encourage users to use bandwidth sparingly. Charging should be based on the amount of traffic a user generates on the international link (and not per hour of use, for example). More information This report was commissioned by INASP in response to requests from Country Coordinators of the Programme for the Enhancement of Research Information (PERI), and from the 2002 Partnership for Higher Education in Africa conference that was held in Addis Ababa. Gerhard Venter of AfriConnect prepared this report ( together with a team from Ethiopia, Malawi, South Africa, Sri Lanka, Tanzania, Uganda and the UK. `The report complements another study being carried out by the Partnership for Higher Education in Africa. To be published in late This examines ways that universities in Africa can access more and cheaper bandwidth (see Copies of the printed report (without annexes) can be obtained from INASP. The full report, with annexes, is also available online: Report contents Current situation, technical background and problems Recommendations for librarians Network optimisation review Bandwidth Network design Usage policies Authentication Controlling the IT department University needs Staff issues Using free software Connection options Glossary Appendix A Practical technical implementation Appendix B Connection options Appendix C Examples of usage policies Appendices D-K Case studies Page 4 of 5
7 About INASP Enabling worldwide access to information and knowledge The International Network for the Availability of Scientific Publications (INASP) aims to enhance the flow of information within and between countries, especially those with less developed systems of publication and dissemination. The International Council for Science (ICSU) established INASP in INASP objectives are: to map, support and strengthen existing activities promoting access to and dissemination of information and knowledge; to identify, encourage and support new initiatives that will increase local publication and general access to scientific and scholarly literature, and; to promote in-country capacity building in information production, organisation, access and dissemination. International Network for the Availability of Scientific Publications (INASP) 27 Park End Street, Oxford OX1 1HU United Kingdom Tel: Fax: Web: International Network for the Availability of Scientific Publications (INASP), 2003 This report may be used in part or in full for teaching, communication, and other non-commercial purposes without authorisation from the copyright owner, but must carry full citation and acknowledgement of the publisher. Page 5 of 5
ResNet Guide. Information & Learning Services. Here to support your study and research
 ResNet Guide Information & Learning Services Here to support your study and research ResNet Quick Start Guide In order to get you on-line and enjoying the service as quickly and as painlessly as possible,
ResNet Guide Information & Learning Services Here to support your study and research ResNet Quick Start Guide In order to get you on-line and enjoying the service as quickly and as painlessly as possible,
TEAL: Transparent Email Archiving Library
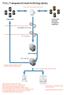 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
BANDWIDTH MANAGEMENT POSITION PAPER
 BANDWIDTH MANAGEMENT POSITION PAPER Executive Summary The delivery of information over the Internet requires a chain of essential components: Content; Connection; Local infrastructure; Bandwidth management.
BANDWIDTH MANAGEMENT POSITION PAPER Executive Summary The delivery of information over the Internet requires a chain of essential components: Content; Connection; Local infrastructure; Bandwidth management.
Top tips for improved network security
 Top tips for improved network security Network security is beleaguered by malware, spam and security breaches. Some criminal, some malicious, some just annoying but all impeding the smooth running of a
Top tips for improved network security Network security is beleaguered by malware, spam and security breaches. Some criminal, some malicious, some just annoying but all impeding the smooth running of a
COPYRIGHT AND SECURITY GUIDE FOR COMPANIES AND GOVERNMENTS
 COPYRIGHT AND SECURITY GUIDE FOR COPANIES AND GOVERNENTS DOWNLOAD 25% COPLETE PAGE 02 You are at risk if commercial music, movies or other copyrighted material is on your organisation s computer systems
COPYRIGHT AND SECURITY GUIDE FOR COPANIES AND GOVERNENTS DOWNLOAD 25% COPLETE PAGE 02 You are at risk if commercial music, movies or other copyrighted material is on your organisation s computer systems
The importance of bandwidth management and optimisation in research and education institutions
 The importance of bandwidth management and optimisation in research and education institutions Sara Gwynn The bandwidth challenge Available bandwidth is limited and insufficient to
The importance of bandwidth management and optimisation in research and education institutions Sara Gwynn The bandwidth challenge Available bandwidth is limited and insufficient to
High Speed Internet - User Guide. Welcome to. your world.
 High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
Acceptable Usage Policy
 Version 2.1 20141230 Acceptable Usage Policy Acceptable Usage Policy Contents 1. PURPOSE OF THIS POLICY... 2 2. GENERAL... 2 3. APPLICATION... 2 4. UNREASONABLE USE... 2 5. UNACCEPTABLE USE... 3 6. SPAM...
Version 2.1 20141230 Acceptable Usage Policy Acceptable Usage Policy Contents 1. PURPOSE OF THIS POLICY... 2 2. GENERAL... 2 3. APPLICATION... 2 4. UNREASONABLE USE... 2 5. UNACCEPTABLE USE... 3 6. SPAM...
ISPA Guidelines and Recommendations on Broadband Terminology
 ISPA Guidelines and Recommendations on Broadband Terminology Version: 1.01 Date: 2011-06-27 1. Introduction The Internet Service Providers' Association (ISPA) has identified a need to develop a set of
ISPA Guidelines and Recommendations on Broadband Terminology Version: 1.01 Date: 2011-06-27 1. Introduction The Internet Service Providers' Association (ISPA) has identified a need to develop a set of
Hosted Exchange Sales Toolkit. Common objections FAQs
 Hosted Exchange Sales Toolkit Common objections FAQs Hosted Exchange Toolkit Common Objections FAQs Target Audience Usage Marketing Managers Used to create online FAQs and knowledge base content for self-service
Hosted Exchange Sales Toolkit Common objections FAQs Hosted Exchange Toolkit Common Objections FAQs Target Audience Usage Marketing Managers Used to create online FAQs and knowledge base content for self-service
Proxy Services: Good Practice Guidelines
 Programme NPFIT DOCUMENT RECORD ID KEY Sub-Prog / Project Information Governance Prog. Director Mark Ferrar Owner Tim Davis Version 1.0 Author James Wood Version Date 26/01/2006 Status APPROVED Proxy Services:
Programme NPFIT DOCUMENT RECORD ID KEY Sub-Prog / Project Information Governance Prog. Director Mark Ferrar Owner Tim Davis Version 1.0 Author James Wood Version Date 26/01/2006 Status APPROVED Proxy Services:
THE OPEN UNIVERSITY OF TANZANIA
 THE OPEN UNIVERSITY OF TANZANIA Institute of Educational and Management Technologies COURSE OUTLINES FOR DIPLOMA IN COMPUTER SCIENCE 2 nd YEAR (NTA LEVEL 6) SEMESTER I 06101: Advanced Website Design Gather
THE OPEN UNIVERSITY OF TANZANIA Institute of Educational and Management Technologies COURSE OUTLINES FOR DIPLOMA IN COMPUTER SCIENCE 2 nd YEAR (NTA LEVEL 6) SEMESTER I 06101: Advanced Website Design Gather
Network Service, Systems and Data Communications Monitoring Policy
 Network Service, Systems and Data Communications Monitoring Policy Purpose This Policy defines the environment and circumstances under which Network Service, Systems and Data Communications Monitoring
Network Service, Systems and Data Communications Monitoring Policy Purpose This Policy defines the environment and circumstances under which Network Service, Systems and Data Communications Monitoring
3 Tips for Your Email Woes: Streamline. Simplify. Cloud.
 Singtel Business Product Factsheet Email Archiving 3 Tips for Your Email Woes: Streamline. Simplify. Cloud. Secure and flexible email archival and e-discovery with Singtel Email Archiving Services. Email
Singtel Business Product Factsheet Email Archiving 3 Tips for Your Email Woes: Streamline. Simplify. Cloud. Secure and flexible email archival and e-discovery with Singtel Email Archiving Services. Email
Netsweeper Whitepaper
 Netsweeper Inc. Corporate Headquarters 104 Dawson Road Suite 100 Guelph, ON, Canada N1H 1A7 CANADA T: +1 (519) 826 5222 F: +1 (519) 826 5228 Netsweeper Whitepaper Deploying Netsweeper Internet Content
Netsweeper Inc. Corporate Headquarters 104 Dawson Road Suite 100 Guelph, ON, Canada N1H 1A7 CANADA T: +1 (519) 826 5222 F: +1 (519) 826 5228 Netsweeper Whitepaper Deploying Netsweeper Internet Content
Microsoft Exchange 2003
 Microsoft Exchange 2003 Configuration Guide Microsoft Exchange 2003 Configuration Guide Page 1 Table of Contents Introduction... 2 Document and naming conventions... 2 Outbound email protection... 3 SMTP
Microsoft Exchange 2003 Configuration Guide Microsoft Exchange 2003 Configuration Guide Page 1 Table of Contents Introduction... 2 Document and naming conventions... 2 Outbound email protection... 3 SMTP
Satellite Broadband FAQs
 Something puzzling you? Then take a look below at our quick FAQs. If you can t find the answer you want, simply give us a call on 0805 631 632 during office hours. Alternatively, if you re online, email
Something puzzling you? Then take a look below at our quick FAQs. If you can t find the answer you want, simply give us a call on 0805 631 632 during office hours. Alternatively, if you re online, email
Internet tools and techniques at this level will be defined as advanced because:
 Unit Title: Using the Internet OCR unit number: 41 Level: 3 Credit value: 5 Guided learning hours: 40 Unit reference number: F/502/4298 Unit purpose and aim This is the ability to set up and use appropriate
Unit Title: Using the Internet OCR unit number: 41 Level: 3 Credit value: 5 Guided learning hours: 40 Unit reference number: F/502/4298 Unit purpose and aim This is the ability to set up and use appropriate
How the Internet Works
 How the Internet Works Kyle Spencer, June 2014 Director, Uganda Internet exchange Point Technology for Development Specialist, UNICEF E-mail: [email protected] Agenda This talk will take approximately
How the Internet Works Kyle Spencer, June 2014 Director, Uganda Internet exchange Point Technology for Development Specialist, UNICEF E-mail: [email protected] Agenda This talk will take approximately
Internet Quick Start Guide. Get the most out of your Midco internet service with these handy instructions.
 Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Internet Security................................................................ 4
Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Internet Security................................................................ 4
Promoting Network Security (A Service Provider Perspective)
 Promoting Network Security (A Service Provider Perspective) Prevention is the Foundation H S Gupta DGM (Technical) Data Networks, BSNL [email protected] DNW, BSNL 1 Agenda Importance of Network Security
Promoting Network Security (A Service Provider Perspective) Prevention is the Foundation H S Gupta DGM (Technical) Data Networks, BSNL [email protected] DNW, BSNL 1 Agenda Importance of Network Security
Top 10 Features: Clearswift SECURE Email Gateway
 Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
Equipment Needed. Connecting to the Internet
 All resident students are provided with access to a high-speed Internet connection. Connection to this network is done at the students own risk. The College is not responsible for material viewed or downloaded
All resident students are provided with access to a high-speed Internet connection. Connection to this network is done at the students own risk. The College is not responsible for material viewed or downloaded
Articles Fighting SPAM in Lotus Domino
 Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Colt Smart Office. Flexible network services for the smaller business. / Next
 Colt Smart Office Flexible network services for the smaller business / Next Big business performance Small business flexibility Today, the Internet has become core to the success of virtually every modern
Colt Smart Office Flexible network services for the smaller business / Next Big business performance Small business flexibility Today, the Internet has become core to the success of virtually every modern
Broadband Bonding Network Appliance TRUFFLE BBNA6401
 Broadband Bonding Network Appliance TRUFFLE BBNA6401 White Paper In this brief White Paper we describe how the TRUFFLE BBNA6401 can provide an SMB with faster and more reliable Internet access at an affordable
Broadband Bonding Network Appliance TRUFFLE BBNA6401 White Paper In this brief White Paper we describe how the TRUFFLE BBNA6401 can provide an SMB with faster and more reliable Internet access at an affordable
Good Practice Set For ICT Security and Acceptable Use
 Sensible Use of Bandwidth Good Practice Guide August 2009 contents 1 Introduction to Good Practice Guides 3 2 Sensible Use of Bandwidth Overview 3 3 Applicability of Sensible Use of Bandwidth Good Practice
Sensible Use of Bandwidth Good Practice Guide August 2009 contents 1 Introduction to Good Practice Guides 3 2 Sensible Use of Bandwidth Overview 3 3 Applicability of Sensible Use of Bandwidth Good Practice
NAC at the endpoint: control your network through device compliance
 NAC at the endpoint: control your network through device compliance Protecting IT networks used to be a straightforward case of encircling computers and servers with a firewall and ensuring that all traffic
NAC at the endpoint: control your network through device compliance Protecting IT networks used to be a straightforward case of encircling computers and servers with a firewall and ensuring that all traffic
Portal Administration. Administrator Guide
 Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Sagari Ltd. Service Catalogue and Service Level Agreement For Outsource IT Services
 Sagari Ltd Service Catalogue and Service Level Agreement For Outsource IT Services Managed Services Service Level Agreement 1 Introduction This Service Catalogue and Service Level Agreement (SLA) constitutes
Sagari Ltd Service Catalogue and Service Level Agreement For Outsource IT Services Managed Services Service Level Agreement 1 Introduction This Service Catalogue and Service Level Agreement (SLA) constitutes
How To Ensure Your School Is Safe Online
 Ivy Road Primary School Policy for e-safety Updated - 2014 1. Introduction Pupils interact with the internet and other communications technologies such as mobile phones on a daily basis. The exchange of
Ivy Road Primary School Policy for e-safety Updated - 2014 1. Introduction Pupils interact with the internet and other communications technologies such as mobile phones on a daily basis. The exchange of
Protecting Your Organisation from Targeted Cyber Intrusion
 Protecting Your Organisation from Targeted Cyber Intrusion How the 35 mitigations against targeted cyber intrusion published by Defence Signals Directorate can be implemented on the Microsoft technology
Protecting Your Organisation from Targeted Cyber Intrusion How the 35 mitigations against targeted cyber intrusion published by Defence Signals Directorate can be implemented on the Microsoft technology
Architecture for ACSI33 email security requirements. Implementation using janusseal and Clearswift MIMEsweeper
 Implementation using janusseal and Clearswift MIMEsweeper Greg Colla July 2005 This paper outlines the changes in the security policy for email within Australian Government agencies, specifically the email
Implementation using janusseal and Clearswift MIMEsweeper Greg Colla July 2005 This paper outlines the changes in the security policy for email within Australian Government agencies, specifically the email
For assistance with your computer, software or router we have supplied the following information: Tech Support 1-855-546-5000, press 1
 For assistance with your computer, software or router we have supplied the following information: Tech Support 1-855-546-5000, press 1 Talk America Services Customer Service 1-855-546-5000, press 3 TALK
For assistance with your computer, software or router we have supplied the following information: Tech Support 1-855-546-5000, press 1 Talk America Services Customer Service 1-855-546-5000, press 3 TALK
Executive Brief for Sharing Sites & Digital Content Providers. Leveraging Hybrid P2P Technology to Enhance the Customer Experience and Grow Profits
 Executive Brief for Sharing Sites & Digital Content Providers Leveraging Hybrid P2P Technology to Enhance the Customer Experience and Grow Profits Executive Summary The Opportunity/Challenge The revenue
Executive Brief for Sharing Sites & Digital Content Providers Leveraging Hybrid P2P Technology to Enhance the Customer Experience and Grow Profits Executive Summary The Opportunity/Challenge The revenue
Monitoring and Logging Policy. Document Status. Security Classification. Level 1 - PUBLIC. Version 1.0. Approval. Review By June 2012
 Monitoring and Logging Policy Document Status Security Classification Version 1.0 Level 1 - PUBLIC Status DRAFT Approval Life 3 Years Review By June 2012 Owner Secure Research Database Analyst Change History
Monitoring and Logging Policy Document Status Security Classification Version 1.0 Level 1 - PUBLIC Status DRAFT Approval Life 3 Years Review By June 2012 Owner Secure Research Database Analyst Change History
AVG AntiVirus. How does this benefit you?
 AVG AntiVirus Award-winning antivirus protection detects, blocks, and removes viruses and malware from your company s PCs and servers. And like all of our cloud services, there are no license numbers to
AVG AntiVirus Award-winning antivirus protection detects, blocks, and removes viruses and malware from your company s PCs and servers. And like all of our cloud services, there are no license numbers to
Source-Connect Network Configuration Last updated May 2009
 Source-Connect Network Configuration Last updated May 2009 For further support: Chicago: +1 312 706 5555 London: +44 20 7193 3700 [email protected] This document is designed to assist IT/Network
Source-Connect Network Configuration Last updated May 2009 For further support: Chicago: +1 312 706 5555 London: +44 20 7193 3700 [email protected] This document is designed to assist IT/Network
Small Business Server Part 2
 Small Business Server Part 2 Presented by : Robert Crane BE MBA MCP [email protected] Computer Information Agency http://www.ciaops.com Agenda Week 1 What is SBS / Setup Week 2 Using & configuring SBS
Small Business Server Part 2 Presented by : Robert Crane BE MBA MCP [email protected] Computer Information Agency http://www.ciaops.com Agenda Week 1 What is SBS / Setup Week 2 Using & configuring SBS
Proxies. Chapter 4. Network & Security Gildas Avoine
 Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Firewall Design Principles Firewall Characteristics Types of Firewalls
 Firewall Design Principles Firewall Characteristics Types of Firewalls Special Thanks to our friends at The Blekinge Institute of Technology, Sweden for providing the basis for these slides. Fall 2008
Firewall Design Principles Firewall Characteristics Types of Firewalls Special Thanks to our friends at The Blekinge Institute of Technology, Sweden for providing the basis for these slides. Fall 2008
ehealth Ontario EMR Connectivity Guidelines
 ehealth Ontario EMR Connectivity Guidelines Version 1.3 Revised March 3, 2010 Introduction Ontario s new ehealth strategy includes the use of commercially-available high-speed Internet to meet Electronic
ehealth Ontario EMR Connectivity Guidelines Version 1.3 Revised March 3, 2010 Introduction Ontario s new ehealth strategy includes the use of commercially-available high-speed Internet to meet Electronic
Bandwidth Management and Optimization System Design (draft)
 Royal Institute of Technology Cost Effective Bandwidth Management and Optimization System: A Case of Hawassa University Bandwidth Management and Optimization System Design (draft) Date: 20 March 2009.
Royal Institute of Technology Cost Effective Bandwidth Management and Optimization System: A Case of Hawassa University Bandwidth Management and Optimization System Design (draft) Date: 20 March 2009.
EMERSON PARK ACADEMY
 1 ACCEPTABLE USE POLICY (AUP) EMERSON PARK ACADEMY (Signature of Headteacher) 1 St September 2014 2 ACCEPTABLE USE POLICY EMERSON PARK ACADEMY 'Acceptable and Responsible Use of ICT Resources' Contents
1 ACCEPTABLE USE POLICY (AUP) EMERSON PARK ACADEMY (Signature of Headteacher) 1 St September 2014 2 ACCEPTABLE USE POLICY EMERSON PARK ACADEMY 'Acceptable and Responsible Use of ICT Resources' Contents
Interactive welcome kit. 866.603.3199 Charter-Business.com CB.016.fibCD.0210
 CHARTER BUSINESS FIBER INTERNET Interactive welcome kit 866.603.3199 Charter-Business.com CB.016.fibCD.0210 CHARTER BUSINESS FIBER INTERNET 2 Turn your contacts on to affordable, powerful solutions from
CHARTER BUSINESS FIBER INTERNET Interactive welcome kit 866.603.3199 Charter-Business.com CB.016.fibCD.0210 CHARTER BUSINESS FIBER INTERNET 2 Turn your contacts on to affordable, powerful solutions from
Mailwall Remote Features Tour Datasheet
 Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Reaping the Full Benefits of a Hybrid Network
 Singtel Business Product Factsheet Managed Hybrid Network Reaping the Full Benefits of a Hybrid Network Singtel Managed Hybrid Network is an innovative offering that extends the enterprise s network coverage
Singtel Business Product Factsheet Managed Hybrid Network Reaping the Full Benefits of a Hybrid Network Singtel Managed Hybrid Network is an innovative offering that extends the enterprise s network coverage
Network Services Internet VPN
 Contents 1. 2. Network Services Customer Responsibilities 3. Network Services General 4. Service Management Boundary 5. Defined Terms Network Services Where the Customer selects as detailed in the Order
Contents 1. 2. Network Services Customer Responsibilities 3. Network Services General 4. Service Management Boundary 5. Defined Terms Network Services Where the Customer selects as detailed in the Order
Funkwerk UTM Release Notes (english)
 Funkwerk UTM Release Notes (english) General Hints Please create a backup of your UTM system's configuration (Maintenance > Configuration > Manual Backup) before you start to install the software update.
Funkwerk UTM Release Notes (english) General Hints Please create a backup of your UTM system's configuration (Maintenance > Configuration > Manual Backup) before you start to install the software update.
SKILLS AND ENTREPRENEURSHIP
 PARTNERS FOR CHANGE SKILLS AND ENTREPRENEURSHIP SUB-SAHARAN AFRICA PARTNERS FOR CHANGE SKILLS AND ENTREPRENEURSHIP PARTNERS FOR CHANGE The British Council works with governments, businesses, training and
PARTNERS FOR CHANGE SKILLS AND ENTREPRENEURSHIP SUB-SAHARAN AFRICA PARTNERS FOR CHANGE SKILLS AND ENTREPRENEURSHIP PARTNERS FOR CHANGE The British Council works with governments, businesses, training and
BSNL IDC Hosted Firewall Service. Total Network Security
 Total Network Security Advantage BSNL IDC India s first Uptime Institute Certified Tier-III data centres with combined connectivity and IT services availability from BSNL Low latency Internet Data Centres
Total Network Security Advantage BSNL IDC India s first Uptime Institute Certified Tier-III data centres with combined connectivity and IT services availability from BSNL Low latency Internet Data Centres
Remote Console Installation & Setup Guide. November 2009
 Remote Console Installation & Setup Guide November 2009 Legal Information All rights reserved. No part of this document shall be reproduced or transmitted by any means or otherwise, without written permission
Remote Console Installation & Setup Guide November 2009 Legal Information All rights reserved. No part of this document shall be reproduced or transmitted by any means or otherwise, without written permission
Welcome. Thank you for choosing Cogeco High Speed Internet.
 Welcome Welcome Thank you for choosing Cogeco High Speed Internet. Welcome to the endless range of possibilities available to you with your new High Speed Internet service. When it comes to speed, you
Welcome Welcome Thank you for choosing Cogeco High Speed Internet. Welcome to the endless range of possibilities available to you with your new High Speed Internet service. When it comes to speed, you
KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.4 REVIEWER S GUIDE. (Updated April 14, 2008)
 KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.4 REVIEWER S GUIDE (Updated April 14, 2008) WHO IS KERIO? Kerio Technologies provides Internet messaging and firewall software solutions for small to medium
KERIO TECHNOLOGIES KERIO WINROUTE FIREWALL 6.4 REVIEWER S GUIDE (Updated April 14, 2008) WHO IS KERIO? Kerio Technologies provides Internet messaging and firewall software solutions for small to medium
Are you getting the speed that you pay for? Understanding Internet Speeds
 Screamin Fast Broadband and Great Sounding ephone Service January, 2015 Rev: 01.00 Are you getting the speed that you pay for? Understanding Internet Speeds Table of Contents Change Log... 2 Overview...
Screamin Fast Broadband and Great Sounding ephone Service January, 2015 Rev: 01.00 Are you getting the speed that you pay for? Understanding Internet Speeds Table of Contents Change Log... 2 Overview...
How To Improve Interconnection
 the Internet is for everyone An Introduction to Internet Interconnection Concepts and Actors Briefing Paper An Introduction to Internet Interconnection Concepts and Actors Introduction The Internet is
the Internet is for everyone An Introduction to Internet Interconnection Concepts and Actors Briefing Paper An Introduction to Internet Interconnection Concepts and Actors Introduction The Internet is
CASSIDIAN CYBERSECURITY SECURITY OPERATIONS CENTRE SERVICES
 CASSIDIAN CYBERSECURITY SECURITY OPERATIONS CENTRE SERVICES PROTECTIVE MONITORING SERVICE In a world where cyber threats are emerging daily, often from unknown sources, information security is something
CASSIDIAN CYBERSECURITY SECURITY OPERATIONS CENTRE SERVICES PROTECTIVE MONITORING SERVICE In a world where cyber threats are emerging daily, often from unknown sources, information security is something
How To Teach Online Business Skills
 Distr.: GENERAL 4 septembre 2001 Original: English ECONOMIC COMMISSION FOR AFRICA Second Meeting of the Committee on Development Information (CODl) Addis Ababa, Ethiopia 4-7 September 2001 ESAMI ONLINE
Distr.: GENERAL 4 septembre 2001 Original: English ECONOMIC COMMISSION FOR AFRICA Second Meeting of the Committee on Development Information (CODl) Addis Ababa, Ethiopia 4-7 September 2001 ESAMI ONLINE
The Bishop s Stortford High School Internet Use and Data Security Policy
 Internet Acceptance Use and Data Security Policy Last Updated: 08/10/2012 Date of Next Review: 08/10/2015 Approved by GB: 10/10/2012 Responsible Committee: Student Welfare and Development Internet Acceptable
Internet Acceptance Use and Data Security Policy Last Updated: 08/10/2012 Date of Next Review: 08/10/2015 Approved by GB: 10/10/2012 Responsible Committee: Student Welfare and Development Internet Acceptable
Total solution for your network security. Provide policy-based firewall on scheduled time. Prevent many known DoS and DDoS attack
 Network Security Total solution for your network security With the growth of the Internet, malicious attacks are happening every minute, and intruders are trying to access your network, using expensive
Network Security Total solution for your network security With the growth of the Internet, malicious attacks are happening every minute, and intruders are trying to access your network, using expensive
Chapter 15: Advanced Networks
 Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Chapter 15: Advanced Networks IT Essentials: PC Hardware and Software v4.0 1 Determine a Network Topology A site survey is a physical inspection of the building that will help determine a basic logical
Computer Security CS 426 Lecture 36. CS426 Fall 2010/Lecture 36 1
 Computer Security CS 426 Lecture 36 Perimeter Defense and Firewalls CS426 Fall 2010/Lecture 36 1 Announcements There will be a quiz on Wed There will be a guest lecture on Friday, by Prof. Chris Clifton
Computer Security CS 426 Lecture 36 Perimeter Defense and Firewalls CS426 Fall 2010/Lecture 36 1 Announcements There will be a quiz on Wed There will be a guest lecture on Friday, by Prof. Chris Clifton
Cyber Security: Beginners Guide to Firewalls
 Cyber Security: Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers This appendix is a supplement to the Cyber Security: Getting Started
Cyber Security: Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers This appendix is a supplement to the Cyber Security: Getting Started
Guidance Regarding Skype and Other P2P VoIP Solutions
 Guidance Regarding Skype and Other P2P VoIP Solutions Ver. 1.1 June 2012 Guidance Regarding Skype and Other P2P VoIP Solutions Scope This paper relates to the use of peer-to-peer (P2P) VoIP protocols,
Guidance Regarding Skype and Other P2P VoIP Solutions Ver. 1.1 June 2012 Guidance Regarding Skype and Other P2P VoIP Solutions Scope This paper relates to the use of peer-to-peer (P2P) VoIP protocols,
References NYS Office of Cyber Security and Critical Infrastructure Coordination Best Practices and Assessment Tools for the Household
 This appendix is a supplement to the Cyber Security: Getting Started Guide, a non-technical reference essential for business managers, office managers, and operations managers. This appendix is one of
This appendix is a supplement to the Cyber Security: Getting Started Guide, a non-technical reference essential for business managers, office managers, and operations managers. This appendix is one of
INSTANT MESSAGING SECURITY
 INSTANT MESSAGING SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part
INSTANT MESSAGING SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part
GPRS and 3G Services: Connectivity Options
 GPRS and 3G Services: Connectivity Options An O2 White Paper Contents Page No. 3-4 5-7 5 6 7 7 8-10 8 10 11-12 11 12 13 14 15 15 15 16 17 Chapter No. 1. Executive Summary 2. Bearer Service 2.1. Overview
GPRS and 3G Services: Connectivity Options An O2 White Paper Contents Page No. 3-4 5-7 5 6 7 7 8-10 8 10 11-12 11 12 13 14 15 15 15 16 17 Chapter No. 1. Executive Summary 2. Bearer Service 2.1. Overview
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
International Bandwidth
 AGENDA Definition Implementation Usage of international bandwidth Definition We mean by International Bandwidth the maximum quantity of data transmission (Rate) from a country to the rest of the world.
AGENDA Definition Implementation Usage of international bandwidth Definition We mean by International Bandwidth the maximum quantity of data transmission (Rate) from a country to the rest of the world.
Enterprise K12 Network Security Policy
 Enterprise K12 Network Security Policy I. Introduction The K12 State Wide Network was established by MDE and ITS to provide a private network infrastructure for the public K12 educational community. Therefore,
Enterprise K12 Network Security Policy I. Introduction The K12 State Wide Network was established by MDE and ITS to provide a private network infrastructure for the public K12 educational community. Therefore,
Computers Basic Training recruits are provided access to a computer lab for completion of work assignments. Recruits may choose to bring a laptop or
 Computers Basic Training recruits are provided access to a computer lab for completion of work assignments. Recruits may choose to bring a laptop or desktop for their use while in training. If a recruit
Computers Basic Training recruits are provided access to a computer lab for completion of work assignments. Recruits may choose to bring a laptop or desktop for their use while in training. If a recruit
Cyber Security Beginners Guide to Firewalls A Non-Technical Guide
 Cyber Security Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers Multi-State Information Sharing and Analysis Center (MS-ISAC) U.S.
Cyber Security Beginners Guide to Firewalls A Non-Technical Guide Essential for Business Managers Office Managers Operations Managers Multi-State Information Sharing and Analysis Center (MS-ISAC) U.S.
Setting up and controlling E-mail
 Setting up and controlling E-mail Two methods Web based PC based Setting up and controlling E-mail Web based the messages are on the Internet accessed by dial-up or broadband at your Internet Service Provider
Setting up and controlling E-mail Two methods Web based PC based Setting up and controlling E-mail Web based the messages are on the Internet accessed by dial-up or broadband at your Internet Service Provider
Government of Canada Managed Security Service (GCMSS) Annex A-5: Statement of Work - Antispam
 Government of Canada Managed Security Service (GCMSS) Date: June 8, 2012 TABLE OF CONTENTS 1 ANTISPAM... 1 1.1 QUALITY OF SERVICE...1 1.2 DETECTION AND RESPONSE...1 1.3 MESSAGE HANDLING...2 1.4 CONFIGURATION...2
Government of Canada Managed Security Service (GCMSS) Date: June 8, 2012 TABLE OF CONTENTS 1 ANTISPAM... 1 1.1 QUALITY OF SERVICE...1 1.2 DETECTION AND RESPONSE...1 1.3 MESSAGE HANDLING...2 1.4 CONFIGURATION...2
BCS IT User Syllabus IT Security for Users Level 2. Version 1.0
 BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
BCS IT User Syllabus IT for Users Level 2 Version 1.0 June 2009 ITS2.1 System Performance ITS2.1.1 Unwanted messages ITS2.1.2 Malicious ITS2.1.1.1 ITS2.1.1.2 ITS2.1.2.1 ITS2.1.2.2 ITS2.1.2.3 ITS2.1.2.4
Broadband Bonding Network Appliance TRUFFLE BBNA6401
 Broadband Bonding Network Appliance TRUFFLE BBNA6401 White Paper In this brief White Paper we describe how the TRUFFLE BBNA6401 can provide an SMB with faster and more reliable Internet access at an affordable
Broadband Bonding Network Appliance TRUFFLE BBNA6401 White Paper In this brief White Paper we describe how the TRUFFLE BBNA6401 can provide an SMB with faster and more reliable Internet access at an affordable
Acceptable Use of ICT Policy. Staff Policy
 Acceptable Use of ICT Policy Staff Policy Contents INTRODUCTION 3 1. ACCESS 3 2. E-SAFETY 4 3. COMPUTER SECURITY 4 4. INAPPROPRIATE BEHAVIOUR 5 5. MONITORING 6 6. BEST PRACTICE 6 7. DATA PROTECTION 7 8.
Acceptable Use of ICT Policy Staff Policy Contents INTRODUCTION 3 1. ACCESS 3 2. E-SAFETY 4 3. COMPUTER SECURITY 4 4. INAPPROPRIATE BEHAVIOUR 5 5. MONITORING 6 6. BEST PRACTICE 6 7. DATA PROTECTION 7 8.
