Computers Basic Training recruits are provided access to a computer lab for completion of work assignments. Recruits may choose to bring a laptop or
|
|
|
- Avice Cook
- 9 years ago
- Views:
Transcription
1 Computers Basic Training recruits are provided access to a computer lab for completion of work assignments. Recruits may choose to bring a laptop or desktop for their use while in training. If a recruit chooses to bring a computer, there are specific requirements for usage (follows).
2 Department of Criminal Justice Training Computer Use Policy Agreement June 12, 2008 ATTENTION-WARNING The Department of Criminal Justice Training utilizes software that MONITORS ALL USAGE OF ITS COMPUTER SYSTEM. In the past, DOCJT recruits and trainees have had disciplinary charges brought against them for violation of the computer policies. PENALTIES IMPOSED HAVE INCLUDED SUSPENSION, AND EVEN EXPULSION FROM TRAINING FOR UP TO FIVE (5) YEARS. YOUR FAILURE OR WILLFUL REFUSAL TO READ AND UNDERSTAND THE POLICIES ON ACCEPTED USE OF THE INTERNET SHALL NOT CONSTITUTE A DEFENSE IF YOU VIOLATE THE POLICIES AND DISCIPLINARY CHARGES ARE BROUGHT AGAINST YOU. If you have any questions or concerns about any of the computer policies, please contact your class coordinator or a member of the DOCJT Computer Section. DOCJT Policy on Residential Use of Computing Resources The Department of Criminal Justice Training (DOCJT), as authorized by the Commonwealth Office of Technology (COT), provides computing resources and worldwide network access to members of the DOCJT electronic community for legitimate law enforcement, academic and administrative pursuits to communicate, access knowledge, and retrieve and disseminate information. All members of the DOCJT community (instructors, staff, students, recruits and authorized guests) sharing these resources also share the rights and responsibilities for their use. The Department of Criminal Justice Training functions under the following related C.A.L.E.A. Standard, Commonwealth Office of Technology and DOCJT Policies: C.A.L.E.A. Standard: 8-3-4: Acceptable Use of the Internet COT Policy: CIO-060; Acceptable Use of the Internet DOCJT Policy: ; Acceptable Use of the Internet DOCJT Policy: ; Copyright and Plagiarism DOCJT Policy: ; Computer Virus Protection Please visit (insert Link Here) to view DOCJT s and COT s complete computing and Information Systems Policies. Residential Network Acceptable Use Policy Agreement
3 General Guidelines The DOCJT Computer Use Policy Agreement binds users of computing or communications resources at the Department of Criminal Justice Training. The following information pertains to the Department of Criminal Justice Training (DOCJT), Residential Network Services (ResNet) and establishes policies and guidelines specific and unique to DOCJT residential computing. By connecting to the residential network and logging on with a valid DOCJT ID and password, each user understands and agrees to abide by these guidelines. Every computer or network device on the residential network will be subject to the Cisco Network Admission Control (NAC) Appliance and the Websense content filtering software. The Department of Criminal Justice Training filters and retains all Internet traffic of every user on the residential network. Personal accounts, (i.e. yahoo, hotmail, AOL and gmail), are considered to be private and not filtered by Websense. Every computer on the residential network is considered the personal property of the resident user. The DOCJT Computer Section is not responsible for the up keep, maintenance or repair of your personal computer. The DOCJT Computer Section personnel will not physically enter your dorm room, examine, configure, repair or touch your computer or laptop. Computer Section personnel will enter your dorm room to repair or test the residential network cabling and/or connections. The dorm attendant will provide you with the following: 15 orange network cable to connect your computer to the network wall port. (return cable when you check out) DOCJT login name and password. Detailed instruction handout explaining with illustrations how to configure your computer and connect to the residential network. Currently, the DOCJT residential network only supports the following computer Operating Systems: Windows 2000 Windows XP Windows Vista Linux Mac OS X
4 Policies Responsibility Residential users are responsible for all traffic originating from their personal computer, including user activity, regardless of whether or not: They generated it; They know what they are doing, and/or; They realize that they have violated any specific policies.
5 It is REQUIRED that all computers on the residential network; Have the Cisco NAC client, Anti Virus Protection that is updated (AVG will be provided by DOCJT free of charge) and the latest Microsoft security updates (Windows operating systems only); Is properly logged onto the network; and Has an IP Address assigned by DOCJT residential network system. Cisco NAC is about having "virus free computers" on the DOCJT residential network. If anyone intentionally masks any computer to look like a different operating system, for the purpose of bypassing the Cisco NAC security features, the computer and user will immediately be banned from the network. This type of activity or behavior could result in disciplinary action. It is RECOMMENDED that all computers on the residential network that are running Windows operating systems have the following: An updated version of Microsoft s free Anti Spyware program for the removal of spyware. Enable windows Personal Firewall to protect the computer. Change the Administrator Account to another name and use a strong password with both numbers and letters. Disable the Guest Account. Registration Registration is an automatic process where all users will be directed to a simple log on screen. Users must log onto the network using their assigned ID and Password. If you do not have an authorized ID, you must contact the dorm attendant at the Thompson Hall resident dormitory to activate your account. Any non-browser devices capable of connecting to the DOCJT residential network are not allowed. Examples of non-browser devices: Xboxes, Tivo, Nintendo Wii, Play Stations, Satellite Receivers, Netflix Players and other similar devices.
6 Use of IP Addresses All IP addresses within the residential network are assigned through an automatic process. IP addresses are dynamic, and are subject to change without any prior notice. Residents should have no expectation that their IP address will remain the same for any length of time. Under no circumstances may computers be configured with a static IP address. Using an IP address that you have not been assigned is grounds for losing your network privileges and immediate disconnection without notice. Additionally, users may not mask the hardware address of their machines. Any computer that is found with a masked hardware address, or consisting of all zeros will be disconnected until it is reconfigured. Hacking and Port Scanning Any unauthorized attempt to access another computer is considered hacking. It doesn t matter whether the computer being hacked into is on or off the DOCJT campus. Any report received by the Commonwealth Office of Technology (COT) or the DOCJT Computer Section that a computer on the DOCJT residential network attempted to hack into or scanned the ports of another will result in the immediate disabling of the network connection until the matter is resolved. Port scanning is considered by the vast majority of network administrators to be a hostile act and a precursor to an actual hacking attempt. In light of the recent rash of highly publicized incidents by the news media, it should be remembered that network administrators are tracking attempts to hack into their systems, and report those attempts immediately to COT and DOCJT network administrator. Security Residential users are completely responsible for the security and integrity of their systems. In cases where a computer is "hacked into", it is recommended that the system be either shut down or be removed from the DOCJT resident network as soon as possible in order to localize any potential damage and to stop the attack from spreading. In such cases, if the owner cannot be contacted in a reasonable time the DOCJT network administrator reserves the right to disable the network connection. Once the owner is made aware of the situation and agrees to take reasonable steps to ensure that the computer is not compromised, network privileges may be restored. Any computer with shared drives or directories that are pass-worded are considered private, even if others that do not own the computer know the password. Accessing pass-worded directories without the express permission of the owner is considered hacking, and may result in permanent loss of network privileges.
7 Server Services DOCJT s residential network is designed as a CLIENT network, and as such the use of servers will be aggressively controlled. Computers running any type of server that uses excessive bandwidth will be immediately disconnected from the network. Examples of server services include, but are not limited to: Peer-to- Peer services (Ares, BitTorrent, Gnutella, Kazaa, DC++, Filetopia, etc) Web or IIS; FTP; Shoutcast; WAREZ; Chat; Gaming servers; and mirc chat servers, including file servers. Music, Movies, Software and other Copyrighted Files It is common knowledge that many users are copying and illegally distributing copyrighted songs and movies. Please be aware that this activity is a violation of the Federal Copyright laws and you could be arrested and prosecuted in a criminal case or sued in a civil case. The Department of Criminal Justice Training in no way condones or encourages this illegal activity and will take action to terminate residential network privileges of any resident breaking DOCJT regulations and State or Federal laws. Websense, the DOCJT content filtering system, is designed to quickly identify, shutdown and stop this type of activity. DOCJT will cooperate completely with any criminal investigation regarding these matters. Please be aware that according to copyright law, you do not need to be making a profit to be prosecuted for distributing copyrighted materials such as these Music, Movie and Software files. Routers and DHCP Servers Hubs, Switches, Routers, Wireless Routers, Wireless Access Points and DHCP servers are not allowed on the residential network. Wireless access is not currently available on the DOCJT residential network. Network Traffic and Bandwidth Connections to the residential network are provided to allow students and recruits to fully participate in the legitimate educational and research missions of the Department of Criminal Justice Training. Unfortunately, it may not always remain feasible to provide unlimited connectivity for systems that are not strictly serving the DOCJT missions. Because of this possibility, we reserve the right to regulate the flow of traffic on the residential network to ensure that all users receive a fair and equitable use of bandwidth. This may include Traffic Shaping, limiting or blocking certain types of network traffic. The DOCJT may also request that users reduce the amount of traffic being caused by their service, or where necessary, to remove such systems from the residential network. In all but
8 extreme cases, we will attempt to contact the owner of the system before removing it from the network. Misconfigured Services or Virus Infected Computers There may be times when a computer is unintentionally misconfigured or infected with a virus that causes problems on the network. In order to preserve the best service possible for the majority of the users, every infected computer will be disconnected from the network immediately. We will attempt to notify the owner of the system that the computer has been disconnected and explain why. Computers will be allowed back onto the network after the owner notifies the DOCJT Computer Section that they have reconfigured the computer or removed the virus and resolved the problem. Any computer that is infected a second time may be disconnected for two days, and subsequent infections may result in being disconnected permanently. Commercial Use Under no circumstances will any individual be permitted to use their network connection or computing privileges for commercial purposes. You may not advertise any commercial products. Any commercial use of DOCJT facilities is explicitly prohibited and is grounds for loss of residential network privileges. Any computer that provides services for a commercial operation (e.g. a web site selling commercial products), provides services of a commercial nature (e.g. provides web services to Non-university users, whether or not a fee is charged), or has a domain name with a commercial designation (currently.com or.net) is explicitly prohibited from the DOCJT residential network. Anonymous Mailers and Spam Zombies Anonymous mail forwarders are prohibited. Running an anonymous mail forwarding service is grounds for removal from the residential network. This includes computers that have been hacked into and are being used as spam zombies. Intentional Abuse Systems found to be intentionally running programs that disrupt network activity or attack specific computers on the network will be subject to immediate removal and disciplinary action.
9 Department of Criminal Justice Training DOCJT ResNet FAQ s (Frequently Asked Questions) How do I get set up for a network connection? See the Dorm Attendant to obtain a DOCJT ResNet Username and Password, and Follow the simple instructions in configuring your computer guide to establish the connection. What does Residential Network Services provide? The data connection in your room gives you direct access to the Internet from your personal computer. With it you can use electronic mail, and the World-Wide Web via browsers such as FireFox and Internet Explorer. We provide this access at speeds significantly faster than a modem, and there is no need to tie up a phone line. Access is immediate; no additional Internet Service Provider (ISP) is needed. Does the Residential Network require special software? YES. Because of virus infected computers, we require all users to authenticate before connecting to the network. Furthermore, we require all Windows machines to download and run our new Cisco Network Admission Control Appliance. This will help both the DOCJT Computer Section staff and the student to keep his/her computer clean and free of viruses, trojan horses and worms. If your computer is not up to date, you will be directed to the correct web site where you can download the necessary updates, including anti-virus software, updated virus definitions, and Windows security updates. Assuming you meet the minimum support requirements for DOCJT ResNet, then your operating system software, along with any software that might have come with your network card, will provide the drivers you need to connect to the Internet. Beyond that, all you need is your choice of software to access the Internet. Do I need a Virus Checking Program? YES! DOCJT Resnet provides a Windows version of AVG free of charge to any resident that needs an Anti-Virus program. If you are running a Windows machine, it is required that you install, and keep updated, a reliable anti-virus program such as AVG or McAfee. The most common reason for students being disconnected is because they are not running an anti-virus program, and their computer gets infected. Once it is infected, then it will attempt to infect others, so we have no choice but to disconnect it. Keeping your computer anti virus program updated will not only help you, but keep hundreds of other residents from being infected. What Anti-Virus Programs are supported? Any McAfee, Symantec, Trend Micro, or AVG software is supported and approved. Where can I get the free AVG Anti-Virus Software. The free AVG software can be obtained after you log on to the Cisco NAC client and your computer is scanned. Once the Cisco NAC client detects that you do not have a supported Anti- Virus Software installed you will be given a link to download the software. My computer got infected with some kind of virus or worm and it sends spam. Can you come to my room and fix it? Unfortunately, no. It is the responsibility of each resident to keep their computer passworded, virus free, and up to date. How often will I have to log in and be validated by the Cisco NAC client?
10 We have configured the validation timer for every 7 days, early Sunday morning. This means that all previously certified "Clean Machines" will need to be revalidated to ensure that all updates for the past week have been downloaded and installed. I noticed that the wall jack in my room is broken and hanging out of the wall. Can you come to my room and fix it? Yes, any part of our network that is broken we will fix. This means all our equipment and connections from the wall jack out. We can even test your Ethernet cord to see if it is working properly. What is Windows Automatic Updates and why should I use it? Windows Update is an important function that Microsoft provides to keep your Windows operating system and other programs updated. This feature must be turned ON, and whenever you are notified that an update is available, we ask that you immediately download and install the update. Our new Cisco NAC system will alert you when updates are available for both Windows and many anti-virus programs, so you will always have the most protected computer possible. What is BANDWIDTH and why is it important? Bandwidth refers to the amount of information that can flow across the network. Most residents use very little bandwidth as they browse the web, send and download an occasional file. Is our bandwidth controlled now? Yes, Residents have 768Kbps Download and 128Kbps Upload speed. This is to provide fair and equitable amount of bandwidth for all residents. Can you tell what web sites I visit and read my ? All Internet traffic is filtered and recorded through our Websense Filtering Servers. DOCJT does not filter or read personal s. What does my network connection cost? There are no additional charges for using this service. Who can connect? Every resident. All you need is a valid DOCJT ResNet Username and Password and an up-todate computer! Can two computers be connected to the same wall jack in a Residence Hall room? No, we do not allow outside routers, switches, or wireless access points to be used in the rooms. Only one Computer per Wall Jack is allowed. If you are caught using one your DOCJT ResNet will be disconnected until the equipment is removed. I notice that there are data jacks in study rooms and common areas. Can I plug my laptop into these? No, DOCJT ResNet is only available in the DOCJT dorm rooms. Once I am online, can I use peer-to-peer software to download such as Kazaa, Emule, Bittorennt etc No, we do not allow any use of peer-to-peer software. Any Attempt to use peer-to-peer software will be blocked and recorded through our Websense Filtering Servers. Once I am online, can I set up my computer as a WEB or FTP Server? No, we do not allow any Web, FTP, or any other kind of server to be running. If you are caught using one your DOCJT ResNet will be disconnected until the matter is resolved. I used a new phone cord to connect my computer to the ethernet jack on the wall, why can t I get online?
11 Phone cords do not work. You must have an ethernet cord. They are available at the DOCJT Dorm Desk. An ethernet cord is wired differently than a phone cord. Why won t my new wireless laptop connect in the dorms? DOCJT ResNet does not offer wireless networking at this time. Plans are not being made at this time for future installations of wireless. Does DOCJT ResNet have an office or place that I can go to for network help? Yes, Please Report any problems with wall jacks or network problems to the DOCJT Dorm desk. Any part of our network that is broken we will fix. This means all our equipment and connections from the wall jack out. We can even test your Ethernet cord to see if it is working properly. A reminder that it is the responsibility of each resident to keep their computer passworded, virus free, and up to date.
ResNet Guide. Information & Learning Services. Here to support your study and research
 ResNet Guide Information & Learning Services Here to support your study and research ResNet Quick Start Guide In order to get you on-line and enjoying the service as quickly and as painlessly as possible,
ResNet Guide Information & Learning Services Here to support your study and research ResNet Quick Start Guide In order to get you on-line and enjoying the service as quickly and as painlessly as possible,
Franciscan University of Steubenville Information Security Policy
 Franciscan University of Steubenville Information Security Policy Scope This policy is intended for use by all personnel, contractors, and third parties assisting in the direct implementation, support,
Franciscan University of Steubenville Information Security Policy Scope This policy is intended for use by all personnel, contractors, and third parties assisting in the direct implementation, support,
Equipment Needed. Connecting to the Internet
 All resident students are provided with access to a high-speed Internet connection. Connection to this network is done at the students own risk. The College is not responsible for material viewed or downloaded
All resident students are provided with access to a high-speed Internet connection. Connection to this network is done at the students own risk. The College is not responsible for material viewed or downloaded
Student Halls Network. Connection Guide
 Student Halls Network Connection Guide Contents: Page 3 Page 4 Page 6 Page 10 Page 17 Page 18 Page 19 Page 20 Introduction Network Connection Policy Connecting to the Student Halls Network Connecting to
Student Halls Network Connection Guide Contents: Page 3 Page 4 Page 6 Page 10 Page 17 Page 18 Page 19 Page 20 Introduction Network Connection Policy Connecting to the Student Halls Network Connecting to
Century Commons' Internet Use
 Century Commons' Internet Use Please Note: Even though you are unable to access the Internet, the sites below are always available. Open up Internet Explorer and type any of these in your address bar to
Century Commons' Internet Use Please Note: Even though you are unable to access the Internet, the sites below are always available. Open up Internet Explorer and type any of these in your address bar to
MISSISSIPPI DEPARTMENT OF HEALTH COMPUTER NETWORK AND INTERNET ACCESS POLICY
 MEMORANDUM TO: FROM: RE: Employee Human Resources MISSISSIPPI DEPARTMENT OF HEALTH COMPUTER NETWORK AND INTERNET ACCESS POLICY Please find attached the above referenced policy that is being issued to each
MEMORANDUM TO: FROM: RE: Employee Human Resources MISSISSIPPI DEPARTMENT OF HEALTH COMPUTER NETWORK AND INTERNET ACCESS POLICY Please find attached the above referenced policy that is being issued to each
EMPLOYEE COMPUTER NETWORK AND INTERNET ACCEPTABLE USAGE POLICY
 EMPLOYEE COMPUTER NETWORK AND INTERNET ACCEPTABLE USAGE POLICY This is a statement of The New York Institute for Special Education s (NYISE s) policy related to employees Computer Network and Internet
EMPLOYEE COMPUTER NETWORK AND INTERNET ACCEPTABLE USAGE POLICY This is a statement of The New York Institute for Special Education s (NYISE s) policy related to employees Computer Network and Internet
Internet and Cable Television Connection Kit. Fall 2014
 Fall 2014 Internet and Cable Television Connection Kit Your guide to connecting to network and television services within Northeastern s residence halls. Technology Support at Northeastern ITS Welcomes
Fall 2014 Internet and Cable Television Connection Kit Your guide to connecting to network and television services within Northeastern s residence halls. Technology Support at Northeastern ITS Welcomes
Network and Workstation Acceptable Use Policy
 CONTENT: Introduction Purpose Policy / Procedure References INTRODUCTION Information Technology services including, staff, workstations, peripherals and network infrastructures are an integral part of
CONTENT: Introduction Purpose Policy / Procedure References INTRODUCTION Information Technology services including, staff, workstations, peripherals and network infrastructures are an integral part of
Technology Department 1350 Main Street Cambria, CA 93428
 Technology Department 1350 Main Street Cambria, CA 93428 Technology Acceptable Use and Security Policy The Technology Acceptable Use and Security Policy ( policy ) applies to all CUSD employees and any
Technology Department 1350 Main Street Cambria, CA 93428 Technology Acceptable Use and Security Policy The Technology Acceptable Use and Security Policy ( policy ) applies to all CUSD employees and any
Computer Use Policy Approved by the Ohio Wesleyan University Faculty: March 24, 2014
 I. Introduction Computer Use Policy Approved by the Ohio Wesleyan University Faculty: March 24, 2014 Ohio Wesleyan University (OWU) provides computing resources to support the educational mission and administration
I. Introduction Computer Use Policy Approved by the Ohio Wesleyan University Faculty: March 24, 2014 Ohio Wesleyan University (OWU) provides computing resources to support the educational mission and administration
Network Security Policy
 Network Security Policy Policy Contents I. POLICY STATEMENT II. REASON FOR POLICY III. SCOPE IV. AUDIENCE V. POLICY TEXT VI. PROCEDURES VII. RELATED INFORMATION VIII. DEFINITIONS IX. FREQUENTLY ASKED QUESTIONS
Network Security Policy Policy Contents I. POLICY STATEMENT II. REASON FOR POLICY III. SCOPE IV. AUDIENCE V. POLICY TEXT VI. PROCEDURES VII. RELATED INFORMATION VIII. DEFINITIONS IX. FREQUENTLY ASKED QUESTIONS
Integra Telecom 4690 Colorado St. SE Prior Lake, Mn 55372 952.226.7097 DSL INSTALLATION GUIDE
 Integra Telecom 4690 Colorado St. SE Prior Lake, Mn 55372 952.226.7097 DSL INSTALLATION GUIDE www.getintegra.com Version 10/10 Integra Telecom, Inc. Thank you for choosing Integra Telecom s DSL High Speed
Integra Telecom 4690 Colorado St. SE Prior Lake, Mn 55372 952.226.7097 DSL INSTALLATION GUIDE www.getintegra.com Version 10/10 Integra Telecom, Inc. Thank you for choosing Integra Telecom s DSL High Speed
LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL. for INFORMATION RESOURCES
 LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL for INFORMATION RESOURCES Updated: June 2007 Information Resources Security Manual 1. Purpose of Security Manual 2. Audience 3. Acceptable
LAMAR STATE COLLEGE - ORANGE INFORMATION RESOURCES SECURITY MANUAL for INFORMATION RESOURCES Updated: June 2007 Information Resources Security Manual 1. Purpose of Security Manual 2. Audience 3. Acceptable
Reynoldsburg City Schools Computer and Technology Acceptable Use Policy Staff, Volunteers and Students
 Reynoldsburg City Schools Computer and Technology Acceptable Use Policy Staff, Volunteers and Students AUP Sections 1. Acceptable Use 2. Privileges 3. Internet Access 4. Procedures & Caveats 5. Netiquette
Reynoldsburg City Schools Computer and Technology Acceptable Use Policy Staff, Volunteers and Students AUP Sections 1. Acceptable Use 2. Privileges 3. Internet Access 4. Procedures & Caveats 5. Netiquette
Peer to Peer File Sharing and Copyright Infringement Policy
 Peer to Peer File Sharing and Copyright Infringement Policy Overview The abuse of network resources to illegally obtain and distribute media or software, through peer to peer (P2P) networks, or direct
Peer to Peer File Sharing and Copyright Infringement Policy Overview The abuse of network resources to illegally obtain and distribute media or software, through peer to peer (P2P) networks, or direct
For assistance with your computer, software or router we have supplied the following information: Tech Support 1-855-546-5000, press 1
 For assistance with your computer, software or router we have supplied the following information: Tech Support 1-855-546-5000, press 1 Talk America Services Customer Service 1-855-546-5000, press 3 TALK
For assistance with your computer, software or router we have supplied the following information: Tech Support 1-855-546-5000, press 1 Talk America Services Customer Service 1-855-546-5000, press 3 TALK
Get Connected! How to Configure Your Computer for MITnet. Red Hat Enterprise Linux Mac OS X Windows XP Professional, Vista
 Get Connected! How to Configure Your Computer for MITnet Red Hat Enterprise Linux Mac OS X Windows XP Professional, Vista 2008 Massachusetts Institute of Technology Table of Contents Introduction...3 About
Get Connected! How to Configure Your Computer for MITnet Red Hat Enterprise Linux Mac OS X Windows XP Professional, Vista 2008 Massachusetts Institute of Technology Table of Contents Introduction...3 About
High Speed Internet, Welcome Kit. If your apartment is served by Ethernet: How do I connect to the network if not using a router?:
 High Speed Internet, Welcome Kit We provide a WIRED High Speed Internet connection to your apartment. Your apartment will be served by a DSL modem or Ethernet jack. If you have multiple users in your apartment
High Speed Internet, Welcome Kit We provide a WIRED High Speed Internet connection to your apartment. Your apartment will be served by a DSL modem or Ethernet jack. If you have multiple users in your apartment
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
High-Speed Broadband Internet Guide
 High-Speed Broadband Internet Guide Welcome Welcome to SkyBest High-Speed Broadband Internet. SkyBest High-Speed Broadband Internet allows for rapid downloading of large files, such as music and graphics.
High-Speed Broadband Internet Guide Welcome Welcome to SkyBest High-Speed Broadband Internet. SkyBest High-Speed Broadband Internet allows for rapid downloading of large files, such as music and graphics.
ResNet Computer Consultant Job Description
 ResNet Computer Consultant Job Description Description: ResNet is the Internet Service Provider within the Residence Halls and Family and Graduate Housing at Montana State University. In addition to providing
ResNet Computer Consultant Job Description Description: ResNet is the Internet Service Provider within the Residence Halls and Family and Graduate Housing at Montana State University. In addition to providing
STRATEGIC POLICY. Information Security Policy Documentation. Network Management Policy. 1. Introduction
 Policy: Title: Status: 1. Introduction ISP-S12 Network Management Policy Revised Information Security Policy Documentation STRATEGIC POLICY 1.1. This information security policy document covers management,
Policy: Title: Status: 1. Introduction ISP-S12 Network Management Policy Revised Information Security Policy Documentation STRATEGIC POLICY 1.1. This information security policy document covers management,
General Questions... 1. Requesting Access... 2. Client Support... 3. Downloading Issues... 4. Installation Issues... 4. Connectivity Issues...
 Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Safe internet for business use: Getting Started Guide
 Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
AVON OLD FARMS SCHOOL COMPUTER AND NETWORK ACCEPTABLE USE POLICY
 AVON OLD FARMS SCHOOL COMPUTER AND NETWORK ACCEPTABLE USE POLICY The following policy shall apply to all students, faculty, and staff of Avon Old Farms School unless otherwise specified. The computing
AVON OLD FARMS SCHOOL COMPUTER AND NETWORK ACCEPTABLE USE POLICY The following policy shall apply to all students, faculty, and staff of Avon Old Farms School unless otherwise specified. The computing
1 You will need the following items to get started:
 QUICKSTART GUIDE 1 Getting Started You will need the following items to get started: A desktop or laptop computer Two ethernet cables (one ethernet cable is shipped with the _ Blocker, and you must provide
QUICKSTART GUIDE 1 Getting Started You will need the following items to get started: A desktop or laptop computer Two ethernet cables (one ethernet cable is shipped with the _ Blocker, and you must provide
Network Security Policy
 Network Security Policy I. PURPOSE Attacks and security incidents constitute a risk to the University's academic mission. The loss or corruption of data or unauthorized disclosure of information on campus
Network Security Policy I. PURPOSE Attacks and security incidents constitute a risk to the University's academic mission. The loss or corruption of data or unauthorized disclosure of information on campus
'Namgis First Nation. 1.0 Overview. 2.0 Purpose. 3.0 Scope. 4.0 Policy
 Created: 2/18/2011 Page 1 of 8 'Namgis First Nation is hereinafter referred to as "the government." 1.0 Overview Though there are a number of reasons to provide a user network access, by far the most common
Created: 2/18/2011 Page 1 of 8 'Namgis First Nation is hereinafter referred to as "the government." 1.0 Overview Though there are a number of reasons to provide a user network access, by far the most common
Security considerations are denoted by a lock icon.
 About This Guide This guide introduces you to some of the technology resources available at the University of Iowa, with the aim of making those resources easily accessible to you. It is an overview of
About This Guide This guide introduces you to some of the technology resources available at the University of Iowa, with the aim of making those resources easily accessible to you. It is an overview of
High Speed Internet - User Guide. Welcome to. your world.
 High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
Frequently Asked Questions
 FAQs Frequently Asked Questions Connecting your Linksys router to the Internet 1 What computer operating systems does my Linksys router support? 1 Why can t I connect my computer or device to my router?
FAQs Frequently Asked Questions Connecting your Linksys router to the Internet 1 What computer operating systems does my Linksys router support? 1 Why can t I connect my computer or device to my router?
What you can do prevent virus infections on your computer
 What you can do prevent virus infections on your computer A computer virus is program code which 'hides' in other files and can cause irreparable damage to your computer. Computer viruses spread easily
What you can do prevent virus infections on your computer A computer virus is program code which 'hides' in other files and can cause irreparable damage to your computer. Computer viruses spread easily
Medford Public Schools Medford, Massachusetts. Software Policy Approved by School Committee
 Software Policy Approved by School Committee General Statement of Policy The Medford Public Schools licenses the use of computer software from a variety of third parties. Such software is normally copyrighted
Software Policy Approved by School Committee General Statement of Policy The Medford Public Schools licenses the use of computer software from a variety of third parties. Such software is normally copyrighted
(606) 785-3450 Knott County (606) 439-3167 Perry County (606) 633-0778 Letcher County. [email protected]
 TVS CableNet Technical Support Guide Effective August 15, 2006 All materials 2006 TV Service, Inc. This material may not be reproduced in any form except for personal private use by TV Service Cable Internet
TVS CableNet Technical Support Guide Effective August 15, 2006 All materials 2006 TV Service, Inc. This material may not be reproduced in any form except for personal private use by TV Service Cable Internet
OSU INSTITUTE OF TECHNOLOGY POLICY & PROCEDURES
 Network Security 6-005 INFORMATION TECHNOLOGIES July 2013 INTRODUCTION 1.01 OSU Institute of Technology (OSUIT) s network exists to facilitate the education, research, administration, communication, and
Network Security 6-005 INFORMATION TECHNOLOGIES July 2013 INTRODUCTION 1.01 OSU Institute of Technology (OSUIT) s network exists to facilitate the education, research, administration, communication, and
COMPUTER USE POLICY. 1.0 Purpose and Summary
 COMPUTER USE POLICY 1.0 Purpose and Summary 1. This document provides guidelines for appropriate use of the wide variety of computing and network resources at Methodist University. It is not an all-inclusive
COMPUTER USE POLICY 1.0 Purpose and Summary 1. This document provides guidelines for appropriate use of the wide variety of computing and network resources at Methodist University. It is not an all-inclusive
Networking in the Colleges
 Networking in the Colleges A Guide For Internal & Intensive School Students Contents Appropriate Use and Your Obligations... 1 Virus Protection... 2 Minimum Computer Requirements... 2 Registering Your
Networking in the Colleges A Guide For Internal & Intensive School Students Contents Appropriate Use and Your Obligations... 1 Virus Protection... 2 Minimum Computer Requirements... 2 Registering Your
UNIVERSITY GUIDEBOOK. Title of Policy: Acceptable Use of University Technology Resources
 PAGE 1 of 6 UNIVERSITY GUIDEBOOK Title of Policy: Acceptable Use of University Technology Resources Responsible Division/Office: Information Technology Approving Officer: Vice President for Finance and
PAGE 1 of 6 UNIVERSITY GUIDEBOOK Title of Policy: Acceptable Use of University Technology Resources Responsible Division/Office: Information Technology Approving Officer: Vice President for Finance and
Responsible Administrative Unit: Computing, Communications & Information Technologies. Information Technology Appropriate Use Policy
 1.0 BACKGROUND AND PURPOSE Information Technology ( IT ) includes a vast and growing array of computing, electronic and voice communications facilities and services. At the Colorado School of Mines ( Mines
1.0 BACKGROUND AND PURPOSE Information Technology ( IT ) includes a vast and growing array of computing, electronic and voice communications facilities and services. At the Colorado School of Mines ( Mines
Policy and Procedure for Internet Use Summer Youth Program Johnson County Community College
 Policy and Procedure for Internet Use Summer Youth Program Johnson County Community College This Policy and Procedures for Internet Use booklet has been prepared for Summer Program students with access
Policy and Procedure for Internet Use Summer Youth Program Johnson County Community College This Policy and Procedures for Internet Use booklet has been prepared for Summer Program students with access
ICT Security Policy for Schools
 WOLGARSTON HIGH SCHOOL Staffordshire ICT Security Policy for Schools A Statement of Policy Author: Readability Score: Frequency of Review: J Ablewhite 15-16 years Annually Amendments 2014 JA Page 1 of
WOLGARSTON HIGH SCHOOL Staffordshire ICT Security Policy for Schools A Statement of Policy Author: Readability Score: Frequency of Review: J Ablewhite 15-16 years Annually Amendments 2014 JA Page 1 of
Cablelynx Acceptable Use Policy
 Cablelynx provides a variety of Internet Services (the Services) to both residential and business customers (the Customer). Below, you will find the terms and conditions that you agree to by subscribing
Cablelynx provides a variety of Internet Services (the Services) to both residential and business customers (the Customer). Below, you will find the terms and conditions that you agree to by subscribing
13. Acceptable Use Policy
 To view the complete Information and Security Policies and Procedures, log into the Intranet through the IRSC.edu website. Click on the Institutional Technology (IT) Department link, then the Information
To view the complete Information and Security Policies and Procedures, log into the Intranet through the IRSC.edu website. Click on the Institutional Technology (IT) Department link, then the Information
Norton Personal Firewall for Macintosh
 Norton Personal Firewall for Macintosh Evaluation Guide Firewall Protection for Client Computers Corporate firewalls, while providing an excellent level of security, are not always enough protection for
Norton Personal Firewall for Macintosh Evaluation Guide Firewall Protection for Client Computers Corporate firewalls, while providing an excellent level of security, are not always enough protection for
AASTMT Acceptable Use Policy
 AASTMT Acceptable Use Policy Classification Information Security Version 1.0 Status Not Active Prepared Department Computer Networks and Data Center Approved Authority AASTMT Presidency Release Date 19/4/2015
AASTMT Acceptable Use Policy Classification Information Security Version 1.0 Status Not Active Prepared Department Computer Networks and Data Center Approved Authority AASTMT Presidency Release Date 19/4/2015
TestNav 8 User Guide for PARCC
 TestNav 8 User Guide for PARCC Copyright 2014, Pearson Education, Inc. Published March 6, 2014 TestNav 8 User Guide for PARCC 1 TestNav 8 User Guide for PARCC Revision History What is TestNav? Technical
TestNav 8 User Guide for PARCC Copyright 2014, Pearson Education, Inc. Published March 6, 2014 TestNav 8 User Guide for PARCC 1 TestNav 8 User Guide for PARCC Revision History What is TestNav? Technical
Acceptable Usage Policy
 Version 2.1 20141230 Acceptable Usage Policy Acceptable Usage Policy Contents 1. PURPOSE OF THIS POLICY... 2 2. GENERAL... 2 3. APPLICATION... 2 4. UNREASONABLE USE... 2 5. UNACCEPTABLE USE... 3 6. SPAM...
Version 2.1 20141230 Acceptable Usage Policy Acceptable Usage Policy Contents 1. PURPOSE OF THIS POLICY... 2 2. GENERAL... 2 3. APPLICATION... 2 4. UNREASONABLE USE... 2 5. UNACCEPTABLE USE... 3 6. SPAM...
Accessing the SUNYIT wireless network for the first time
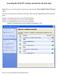 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Internet Quick Start Guide. Get the most out of your Midco internet service with these handy instructions.
 Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Internet Security................................................................ 4
Internet Quick Start Guide Get the most out of your Midco internet service with these handy instructions. 1 Contents Internet Security................................................................ 4
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
DIOCESE OF DALLAS. Computer Internet Policy
 DIOCESE OF DALLAS Computer Internet Policy October 2012 Page 1 ROMAN CATHOLIC DIOCESE OF DALLAS COMPUTER SYSTEMS AND INTERNET USE POLICY Summary Definitions: 1. The term Communication(s) Assets as used
DIOCESE OF DALLAS Computer Internet Policy October 2012 Page 1 ROMAN CATHOLIC DIOCESE OF DALLAS COMPUTER SYSTEMS AND INTERNET USE POLICY Summary Definitions: 1. The term Communication(s) Assets as used
BROADALBIN-PERTH CENTRAL SCHOOL ADOPTED 1/22/00 3 RD READING AND ADOPTION 5/21/12. Employee Computer Use Agreement. Terms and Conditions
 BOARD OF EDUCATION POLICY ADMINISTRATIVE GUIDELINE 6.6.1A(3) BROADALBIN-PERTH CENTRAL SCHOOL ADOPTED 1/22/00 3 RD READING AND ADOPTION 5/21/12 Employee Computer Use Agreement The district is pleased to
BOARD OF EDUCATION POLICY ADMINISTRATIVE GUIDELINE 6.6.1A(3) BROADALBIN-PERTH CENTRAL SCHOOL ADOPTED 1/22/00 3 RD READING AND ADOPTION 5/21/12 Employee Computer Use Agreement The district is pleased to
IT1. Acceptable Use of Information Technology Resources. Policies and Procedures
 IT1 Policies and Procedures Acceptable Use of Information Technology Resources Originator: Information Technology Governance Committee Approver: President s Council Effective: October 16, 2007 Replaces:
IT1 Policies and Procedures Acceptable Use of Information Technology Resources Originator: Information Technology Governance Committee Approver: President s Council Effective: October 16, 2007 Replaces:
HomeNet. Gateway User Guide
 HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
Linksys Gateway SPA2100-SU Manual
 Linksys Gateway SPA2100-SU Manual Manuel de l'utilisateur Table of Contents Looking for Basic Setup Instructions?... 3 Most Recent Version of this Manual... 3 Advanced Setup Instructions... 4 Wiring Your
Linksys Gateway SPA2100-SU Manual Manuel de l'utilisateur Table of Contents Looking for Basic Setup Instructions?... 3 Most Recent Version of this Manual... 3 Advanced Setup Instructions... 4 Wiring Your
How to Connect to UAB s Wireless Networks
 How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
Internet and Cable Television Connection Kit. Spring 2016
 Spring 2016 Internet and Cable Television Connection Kit Your guide to connecting to network and television services within Northeastern s residence halls. ITS Welcomes You! Information Technology Services
Spring 2016 Internet and Cable Television Connection Kit Your guide to connecting to network and television services within Northeastern s residence halls. ITS Welcomes You! Information Technology Services
Internet Filtering Appliance. User s Guide VERSION 1.2
 Internet Filtering Appliance User s Guide VERSION 1.2 User s Guide VERSION 1.2 InternetSafety.com, Inc 3979 South Main Street Suite 230 Acworth, GA 30101 Phone 678 384 5300 Fax 678 384 5299 1 Table of
Internet Filtering Appliance User s Guide VERSION 1.2 User s Guide VERSION 1.2 InternetSafety.com, Inc 3979 South Main Street Suite 230 Acworth, GA 30101 Phone 678 384 5300 Fax 678 384 5299 1 Table of
Valmeyer Community Unit School District #3 Acceptable Use Of Computers and Networks
 Valmeyer Community Unit School District #3 Acceptable Use Of Computers and Networks The Valmeyer Community Unit School District #3 Board of Education supports the use of the Internet and other computer
Valmeyer Community Unit School District #3 Acceptable Use Of Computers and Networks The Valmeyer Community Unit School District #3 Board of Education supports the use of the Internet and other computer
Haddon Township School District Acceptable Use of Information and Communication Technology for Students
 Haddon Township School District Acceptable Use of Information and Communication Technology for Students Please read the following carefully before signing the Acceptable Use Policy for Students Agreement.
Haddon Township School District Acceptable Use of Information and Communication Technology for Students Please read the following carefully before signing the Acceptable Use Policy for Students Agreement.
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.8 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.8 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
MEMORANDUM INFORMATION TECHNOLOGY SERVICES DEPARTMENT
 MEMORANDUM INFORMATION TECHNOLOGY SERVICES DEPARTMENT TO: John Phillips, City Manager Number: 04-020 SUBJECT: Computer Network, Internet and E-Mail Access Policy Date: 9/903 Attached is copy of the Information
MEMORANDUM INFORMATION TECHNOLOGY SERVICES DEPARTMENT TO: John Phillips, City Manager Number: 04-020 SUBJECT: Computer Network, Internet and E-Mail Access Policy Date: 9/903 Attached is copy of the Information
INFORMATION GOVERNANCE POLICY: NETWORK SECURITY
 INFORMATION GOVERNANCE POLICY: NETWORK SECURITY Original Approved by: Policy and Procedure Ratification Sub-group on 23 October 2007 Version 1.2 Approved by: Information Governance Group Approval Date:
INFORMATION GOVERNANCE POLICY: NETWORK SECURITY Original Approved by: Policy and Procedure Ratification Sub-group on 23 October 2007 Version 1.2 Approved by: Information Governance Group Approval Date:
Basic Computer Security Part 2
 Basic Computer Security Part 2 Presenter David Schaefer, MBA OCC Manager of Desktop Support Adjunct Security Instructor: Walsh College, Oakland Community College, Lawrence Technology University Welcome
Basic Computer Security Part 2 Presenter David Schaefer, MBA OCC Manager of Desktop Support Adjunct Security Instructor: Walsh College, Oakland Community College, Lawrence Technology University Welcome
Welcome. Thank you for choosing Cogeco High Speed Internet.
 Welcome Welcome Thank you for choosing Cogeco High Speed Internet. Welcome to the endless range of possibilities available to you with your new High Speed Internet service. When it comes to speed, you
Welcome Welcome Thank you for choosing Cogeco High Speed Internet. Welcome to the endless range of possibilities available to you with your new High Speed Internet service. When it comes to speed, you
We have opted to implement a modified Bring Your Own Device (BYOD) program at the high school level.
 Attention 7-12 parents and students: Last year we had the opportunity to pilot a 1:1 Chromebook program in grades 7-8. During this program, we were able to assess the impact providing each student with
Attention 7-12 parents and students: Last year we had the opportunity to pilot a 1:1 Chromebook program in grades 7-8. During this program, we were able to assess the impact providing each student with
Small Business Server Part 2
 Small Business Server Part 2 Presented by : Robert Crane BE MBA MCP [email protected] Computer Information Agency http://www.ciaops.com Agenda Week 1 What is SBS / Setup Week 2 Using & configuring SBS
Small Business Server Part 2 Presented by : Robert Crane BE MBA MCP [email protected] Computer Information Agency http://www.ciaops.com Agenda Week 1 What is SBS / Setup Week 2 Using & configuring SBS
Network Security Policy: Best Practices White Paper
 Security Policy: Best Practices White Paper Document ID: 13601 Introduction Preparation Create Usage Policy Statements Conduct a Risk Analysis Establish a Security Team Structure Prevention Approving Security
Security Policy: Best Practices White Paper Document ID: 13601 Introduction Preparation Create Usage Policy Statements Conduct a Risk Analysis Establish a Security Team Structure Prevention Approving Security
Marion County School District Computer Acceptable Use Policy
 Marion County School District Computer Acceptable Use Policy The Marion County School District (MCSD) offers currently enrolled students, faculty and staff access to the school computer network through
Marion County School District Computer Acceptable Use Policy The Marion County School District (MCSD) offers currently enrolled students, faculty and staff access to the school computer network through
INSTITUTIONAL COMPLIANCE REQUIREMENTS PUBLIC LAW 110-315
 INSTITUTIONAL COMPLIANCE REQUIREMENTS PUBLIC LAW 110-315 The Digital Millennium Copyright Act (DMCA) and Peer-to-Peer File Sharing Policy Copying, distributing, and downloading copyrighted materials, including
INSTITUTIONAL COMPLIANCE REQUIREMENTS PUBLIC LAW 110-315 The Digital Millennium Copyright Act (DMCA) and Peer-to-Peer File Sharing Policy Copying, distributing, and downloading copyrighted materials, including
Getting Connected. Student Technology Services
 Getting Connected Student Technology Services 2015-2016 Contents Welcome 3 Your Computer 4 Network Services 5 Network Assistance 6 Emergency Notification 8 Labs and Printing 9 Student Technology Store
Getting Connected Student Technology Services 2015-2016 Contents Welcome 3 Your Computer 4 Network Services 5 Network Assistance 6 Emergency Notification 8 Labs and Printing 9 Student Technology Store
PROTECT YOUR COMPUTER AND YOUR PRIVACY!
 PROTECT YOUR COMPUTER AND YOUR PRIVACY! Fraud comes in many shapes simple: the loss of both money protecting your computer and Take action and get peace of and sizes, but the outcome is and time. That
PROTECT YOUR COMPUTER AND YOUR PRIVACY! Fraud comes in many shapes simple: the loss of both money protecting your computer and Take action and get peace of and sizes, but the outcome is and time. That
Computer Security Maintenance Information and Self-Check Activities
 Computer Security Maintenance Information and Self-Check Activities Overview Unlike what many people think, computers are not designed to be maintenance free. Just like cars they need routine maintenance.
Computer Security Maintenance Information and Self-Check Activities Overview Unlike what many people think, computers are not designed to be maintenance free. Just like cars they need routine maintenance.
WELCOME TO VERIZON HIGH SPEED INTERNET FOR BUSINESS
 WELCOME TO VERIZON HIGH SPEED INTERNET FOR BUSINESS For a better online experience, start here today. YOUR GUIDE TO INSTALLING AND USING VERIZON HIGH SPEED INTERNET. Congratulations on choosing Verizon
WELCOME TO VERIZON HIGH SPEED INTERNET FOR BUSINESS For a better online experience, start here today. YOUR GUIDE TO INSTALLING AND USING VERIZON HIGH SPEED INTERNET. Congratulations on choosing Verizon
[Acceptable Use Policy]
![[Acceptable Use Policy] [Acceptable Use Policy]](/thumbs/27/9982233.jpg) South College Computer Code of Ethics [Acceptable Use Policy] Introduction Freedom of expression and an open environment to pursue scholarly inquiry and for sharing of information are encouraged, supported,
South College Computer Code of Ethics [Acceptable Use Policy] Introduction Freedom of expression and an open environment to pursue scholarly inquiry and for sharing of information are encouraged, supported,
