THE OPEN UNIVERSITY OF TANZANIA
|
|
|
- Charlotte Long
- 10 years ago
- Views:
Transcription
1 THE OPEN UNIVERSITY OF TANZANIA Institute of Educational and Management Technologies COURSE OUTLINES FOR DIPLOMA IN COMPUTER SCIENCE 2 nd YEAR (NTA LEVEL 6) SEMESTER I 06101: Advanced Website Design Gather user requirements Identify techniques use to collect requirements Analyse the requirement Design the system Identify webpage development tools Identify web languages Describe platforms used to design WebPages Analyse webpage development tools Describe Web Development phases Plan a Website Design website. Design web contents. Develop Website Test website. Upload website. Maintain website.
2 Create page layout Describe page layout Examine page layout Create page layout Develop website using HTML and CSS Define HTML and CSS. Understand the structure of HTML and CSS. Describe the version of CSS and HTML Describe types of CSS Develop website using HTML and CSS Identify web standards Define web standards List web standard Describe the functions of web standards Write good quality content Describe the features of quality web contents Describe the standard web content Create web content Use Web Content Management Systems (CMS) to create and manage website Define web Content Management Systems. Understand the role of web content management system Describe different web Content Management Systems Choose appropriate content management systems Create web page using Content Management Systems Enhanced web interactivity with JavaScript Define JavaScript Describe JavaScript Syntax Use JavaScript in the HTML documents
3 Register website Domain Name Describe domain name. Describe domain name systems. Choose appropriate domain name Host a Website Describe web hosting. Describe the web hosting plan. Choose web hosting plan Upload and Download a Website Describe Upload and Download. Identify different uploading technologies. Identify requirements for uploading. Upload a website. Download a website. Identify and correct errors during uploading and downloading a website Identify language standards available in web server Observe files naming standard Examine the web server space and the uploading file Analyze website traffic and statistics Describe web traffic and statistics. Differentiate between web traffic and web statistics. Describe web analytics and stats tools Analyze types of contents Collect feedback from users Analyse the importance of user feedback Identify user feedback methods Analyse user feedback Conduct usability testing Identify tools Organise usability test team
4 Analyse usability Conduct compatibility and accessibility testing Testing multiple and common used browses Examine compatibility test Conduct compatibility and accessibility testing Log in remotely Create an account Set system user privilege Identify secure login client Make changes to website Identify changes Collect information Identify rules on making changes Market the site on the web Conduct marketing research Identify tools for marketing website Implement the results Examine copyright laws Describe copyright laws Identify copyright laws Describe the need for copyright laws Identify web system attacks Describe web systems threats. Identify type of web system attacks. Identify the techniques to secure website Create strong authentication and access control Generate passwords Generate access keys Secure passwords
5 Apply URL filtering Describe URL filtering Describe the role URL filtering Apply URL filtering Deploy spyware tools Describe spyware Install spyware tool Configure spyware tools Deploy antivirus scanning Install antivirus Configure antivirus Update antivirus Identify web system vulnerabilities. Describe website vulnerability. Identify website vulnerability scanning tools. Use website vulnerability scanning tools. Optimize website for search engine Describe a Search Engine. Describe a Search Engine Optimization (SEO). Identify features of a search engine. Optimize site for search engine. Prevent website from Hackers. Describe the term Hacking. Describe techniques used by website hackers Identify techniques and tools to prevent website hackers
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Performing a Web Application Security Assessment
 IBM Software Group Performing a Web Application Security Assessment 2007 IBM Corporation Coordinate the Time of the Audit Set up a time window with the application owner Inform your security team Inform
IBM Software Group Performing a Web Application Security Assessment 2007 IBM Corporation Coordinate the Time of the Audit Set up a time window with the application owner Inform your security team Inform
Web Design and Development I a.k.a. Fundamentals of Web Design and Development
 CompuScholar, Inc. Alignment to South Carolina Web Design and Development I Standards South Carolina Course Details: Course Name: Web Design and Development I a.k.a. Fundamentals of Web Design and Development
CompuScholar, Inc. Alignment to South Carolina Web Design and Development I Standards South Carolina Course Details: Course Name: Web Design and Development I a.k.a. Fundamentals of Web Design and Development
Net2 Anywhere - Installation
 Net2 Anywhere - Installation What is Net2 Anywhere? Net2 Anywhere is a range of services that use the internet to provide additional features for your Net2 access control system. Our secure web server
Net2 Anywhere - Installation What is Net2 Anywhere? Net2 Anywhere is a range of services that use the internet to provide additional features for your Net2 access control system. Our secure web server
ABB s approach concerning IS Security for Automation Systems
 ABB s approach concerning IS Security for Automation Systems Copyright 2006 ABB. All rights reserved. Stefan Kubik [email protected] The problem Most manufacturing facilities are more connected (and
ABB s approach concerning IS Security for Automation Systems Copyright 2006 ABB. All rights reserved. Stefan Kubik [email protected] The problem Most manufacturing facilities are more connected (and
Managing Qualys Scanners
 Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Developing ASP.NET MVC 4 Web Applications MOC 20486
 Developing ASP.NET MVC 4 Web Applications MOC 20486 Course Outline Module 1: Exploring ASP.NET MVC 4 The goal of this module is to outline to the students the components of the Microsoft Web Technologies
Developing ASP.NET MVC 4 Web Applications MOC 20486 Course Outline Module 1: Exploring ASP.NET MVC 4 The goal of this module is to outline to the students the components of the Microsoft Web Technologies
Administering the Web Server (IIS) Role of Windows Server
 Course 10972B: Administering the Web Server (IIS) Role of Windows Server Page 1 of 7 Administering the Web Server (IIS) Role of Windows Server Course 10972B: 4 days; Instructor-Led Introduction This course
Course 10972B: Administering the Web Server (IIS) Role of Windows Server Page 1 of 7 Administering the Web Server (IIS) Role of Windows Server Course 10972B: 4 days; Instructor-Led Introduction This course
WEB DEVELOPMENT IA & IB (893 & 894)
 DESCRIPTION Web Development is a course designed to guide students in a project-based environment in the development of up-to-date concepts and skills that are used in the development of today s websites.
DESCRIPTION Web Development is a course designed to guide students in a project-based environment in the development of up-to-date concepts and skills that are used in the development of today s websites.
Internet Security Protecting Your Business. Hayden Johnston & Rik Perry WYSCOM
 Internet Security Protecting Your Business Hayden Johnston & Rik Perry WYSCOM Introduction Protecting Your Network Securing Your Information Standards & Best Practices Tools & Options Into The Future Creating
Internet Security Protecting Your Business Hayden Johnston & Rik Perry WYSCOM Introduction Protecting Your Network Securing Your Information Standards & Best Practices Tools & Options Into The Future Creating
Sophos for Microsoft SharePoint startup guide
 Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
The purpose of this report is to educate our prospective clients about capabilities of Hackers Locked.
 This sample report is published with prior consent of our client in view of the fact that the current release of this web application is three major releases ahead in its life cycle. Issues pointed out
This sample report is published with prior consent of our client in view of the fact that the current release of this web application is three major releases ahead in its life cycle. Issues pointed out
Cisco Advanced Services for Network Security
 Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Roars. Sudaworld. M+1.408.622.9642 Esales.usa@ roarsinc.com W www.roarsinc.com. Roars Technologies Pvt. Ltd. Escalon, Sunnyvale, California, USA 94085
 Technologies Pvt. Ltd. Sudaworld Technologies Pvt. Ltd. REQUIREMENT OVERVIEW The project is to build a dynamic CMS responsive website, The Client is looking for a video and articles based blogging website
Technologies Pvt. Ltd. Sudaworld Technologies Pvt. Ltd. REQUIREMENT OVERVIEW The project is to build a dynamic CMS responsive website, The Client is looking for a video and articles based blogging website
1352 Blue Oaks Blvd. Suite 180 Roseville, CA 95678 (916) 771-5318 www.arroyoc.com. Arroyo Consulting Dynamic Website Storyboard
 Arroyo Consulting Dynamic Website Storyboard Arroyo Consulting dynamic website storyboard Arroyo Consultings goal with a dynamic website is to provide our clients with a TOOL to administer the dynamic
Arroyo Consulting Dynamic Website Storyboard Arroyo Consulting dynamic website storyboard Arroyo Consultings goal with a dynamic website is to provide our clients with a TOOL to administer the dynamic
Portal Recipient Guide
 Portal Recipient Guide Lindenhouse Software Limited 2015 Contents 1 Introduction... 4 2 Account Activation... 4 3 Forgotten Password... 9 4 Document signing... 12 5 Authenticating your Device & Browser...
Portal Recipient Guide Lindenhouse Software Limited 2015 Contents 1 Introduction... 4 2 Account Activation... 4 3 Forgotten Password... 9 4 Document signing... 12 5 Authenticating your Device & Browser...
Developing ASP.NET MVC 4 Web Applications
 Course M20486 5 Day(s) 30:00 Hours Developing ASP.NET MVC 4 Web Applications Introduction In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5 tools
Course M20486 5 Day(s) 30:00 Hours Developing ASP.NET MVC 4 Web Applications Introduction In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5 tools
TEAL: Transparent Email Archiving Library
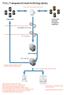 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
BlackShield ID Agent for Remote Web Workplace
 Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
HoneyBOT User Guide A Windows based honeypot solution
 HoneyBOT User Guide A Windows based honeypot solution Visit our website at http://www.atomicsoftwaresolutions.com/ Table of Contents What is a Honeypot?...2 How HoneyBOT Works...2 Secure the HoneyBOT Computer...3
HoneyBOT User Guide A Windows based honeypot solution Visit our website at http://www.atomicsoftwaresolutions.com/ Table of Contents What is a Honeypot?...2 How HoneyBOT Works...2 Secure the HoneyBOT Computer...3
EBOX Digital Content Management System (CMS) User Guide For Site Owners & Administrators
 EBOX Digital Content Management System (CMS) User Guide For Site Owners & Administrators Version 1.0 Last Updated on 15 th October 2011 Table of Contents Introduction... 3 File Manager... 5 Site Log...
EBOX Digital Content Management System (CMS) User Guide For Site Owners & Administrators Version 1.0 Last Updated on 15 th October 2011 Table of Contents Introduction... 3 File Manager... 5 Site Log...
Pearl Echo Installation Checklist
 Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Symantec Endpoint Protection Analyzer Report
 Symantec Endpoint Protection Analyzer Report For Symantec Customer Table of Contents Statement of Confidentiality... 3 1. Introduction... 4 2. Environmental Analysis Overview... 5 2.1 Findings Overview...
Symantec Endpoint Protection Analyzer Report For Symantec Customer Table of Contents Statement of Confidentiality... 3 1. Introduction... 4 2. Environmental Analysis Overview... 5 2.1 Findings Overview...
Administering the Web Server (IIS) Role of Windows Server 10972B; 5 Days
 Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Administering the Web Server (IIS) Role of Windows Server 10972B; 5 Days
Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Administering the Web Server (IIS) Role of Windows Server 10972B; 5 Days
$920+ GST Paid Annually. e-commerce Website Hosting Service HOSTING:: WHAT YOU GET WORDPRESS:: THEME + PLUG-IN UPDATES
 e-commerce Website Hosting Service HOSTING:: WHAT YOU GET Where you host your website is an extremely important decision to make, if you choose simply on price, you may be making a huge mistake. We encourage
e-commerce Website Hosting Service HOSTING:: WHAT YOU GET Where you host your website is an extremely important decision to make, if you choose simply on price, you may be making a huge mistake. We encourage
Livezilla How to Install on Shared Hosting http://www.jonathanmanning.com By: Jon Manning
 Livezilla How to Install on Shared Hosting By: Jon Manning This is an easy to follow tutorial on how to install Livezilla 3.2.0.2 live chat program on a linux shared hosting server using cpanel, linux
Livezilla How to Install on Shared Hosting By: Jon Manning This is an easy to follow tutorial on how to install Livezilla 3.2.0.2 live chat program on a linux shared hosting server using cpanel, linux
Penetration Testing in Romania
 Penetration Testing in Romania Adrian Furtunǎ, Ph.D. 11 October 2011 Romanian IT&C Security Forum Agenda About penetration testing Examples Q & A 2 What is penetration testing? Method for evaluating the
Penetration Testing in Romania Adrian Furtunǎ, Ph.D. 11 October 2011 Romanian IT&C Security Forum Agenda About penetration testing Examples Q & A 2 What is penetration testing? Method for evaluating the
PROPOSED SOLUTIONS FOR THE DESIGN & DEVELOPMENT OF COUPON WEBSITE
 PROPOSED SOLUTIONS FOR THE DESIGN & DEVELOPMENT OF COUPON WEBSITE Proposed Framework: PHP5.0, Jquery, Json, Javascript, Ajax; MySQL will be used as back-end database; Div based HTML/CSS for browser compatibility;
PROPOSED SOLUTIONS FOR THE DESIGN & DEVELOPMENT OF COUPON WEBSITE Proposed Framework: PHP5.0, Jquery, Json, Javascript, Ajax; MySQL will be used as back-end database; Div based HTML/CSS for browser compatibility;
Protecting Your Network Against Risky SSL Traffic ABSTRACT
 Protecting Your Network Against Risky SSL Traffic ABSTRACT Every day more and more Web traffic traverses the Internet in a form that is illegible to eavesdroppers. This traffic is encrypted with Secure
Protecting Your Network Against Risky SSL Traffic ABSTRACT Every day more and more Web traffic traverses the Internet in a form that is illegible to eavesdroppers. This traffic is encrypted with Secure
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
BlackShield ID Agent for Terminal Services Web and Remote Desktop Web
 Agent for Terminal Services Web and Remote Desktop Web 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication
Agent for Terminal Services Web and Remote Desktop Web 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication
Web Development I & II*
 Web Development I & II* Career Cluster Information Technology Course Code 10161 Prerequisite(s) Computer Applications Introduction to Information Technology (recommended) Computer Information Technology
Web Development I & II* Career Cluster Information Technology Course Code 10161 Prerequisite(s) Computer Applications Introduction to Information Technology (recommended) Computer Information Technology
Developing ASP.NET MVC 4 Web Applications Course 20486A; 5 Days, Instructor-led
 Developing ASP.NET MVC 4 Web Applications Course 20486A; 5 Days, Instructor-led Course Description In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5
Developing ASP.NET MVC 4 Web Applications Course 20486A; 5 Days, Instructor-led Course Description In this course, students will learn to develop advanced ASP.NET MVC applications using.net Framework 4.5
MatriXay WEB Application Vulnerability Scanner V 5.0. 1. Overview. (DAS- WEBScan ) - - - - - The best WEB application assessment tool
 MatriXay DAS-WEBScan MatriXay WEB Application Vulnerability Scanner V 5.0 (DAS- WEBScan ) - - - - - The best WEB application assessment tool 1. Overview MatriXay DAS- Webscan is a specific application
MatriXay DAS-WEBScan MatriXay WEB Application Vulnerability Scanner V 5.0 (DAS- WEBScan ) - - - - - The best WEB application assessment tool 1. Overview MatriXay DAS- Webscan is a specific application
Cyber Essentials Questionnaire
 Cyber Essentials Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a business enabler rather than a core deliverable.
Cyber Essentials Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a business enabler rather than a core deliverable.
10972B: Administering the Web Server (IIS) Role of Windows Server
 10972B: Administering the Web Server (IIS) Role of Windows Server Course Details Course Code: Duration: Notes: 10972B 5 days This course syllabus should be used to determine whether the course is appropriate
10972B: Administering the Web Server (IIS) Role of Windows Server Course Details Course Code: Duration: Notes: 10972B 5 days This course syllabus should be used to determine whether the course is appropriate
WordPress Security Scan Configuration
 WordPress Security Scan Configuration To configure the - WordPress Security Scan - plugin in your WordPress driven Blog, login to WordPress as administrator, by simply entering the url_of_your_website/wp-admin
WordPress Security Scan Configuration To configure the - WordPress Security Scan - plugin in your WordPress driven Blog, login to WordPress as administrator, by simply entering the url_of_your_website/wp-admin
Putting Web Threat Protection and Content Filtering in the Cloud
 Putting Web Threat Protection and Content Filtering in the Cloud Why secure web gateways belong in the cloud and not on appliances Contents The Cloud Can Lower Costs Can It Improve Security Too?. 1 The
Putting Web Threat Protection and Content Filtering in the Cloud Why secure web gateways belong in the cloud and not on appliances Contents The Cloud Can Lower Costs Can It Improve Security Too?. 1 The
FileMaker Server 12. FileMaker Server Help
 FileMaker Server 12 FileMaker Server Help 2010-2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc.
FileMaker Server 12 FileMaker Server Help 2010-2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark of FileMaker, Inc.
Citrix EdgeSight for NetScaler Rapid Deployment Guide
 Citrix EdgeSight for NetScaler Rapid Deployment Guide Citrix EdgeSight for NetScaler 2.1 This document provides step by step instructions for preparing the environment for EdgeSight for NetScaler installation,
Citrix EdgeSight for NetScaler Rapid Deployment Guide Citrix EdgeSight for NetScaler 2.1 This document provides step by step instructions for preparing the environment for EdgeSight for NetScaler installation,
Unit 3 Research Project. Eddie S. Jackson. Kaplan University. IT540: Management of Information Security. Kenneth L. Flick, Ph.D.
 Running head: UNIT 3 RESEARCH PROJECT 1 Unit 3 Research Project Eddie S. Jackson Kaplan University IT540: Management of Information Security Kenneth L. Flick, Ph.D. 10/07/2014 UNIT 3 RESEARCH PROJECT 2
Running head: UNIT 3 RESEARCH PROJECT 1 Unit 3 Research Project Eddie S. Jackson Kaplan University IT540: Management of Information Security Kenneth L. Flick, Ph.D. 10/07/2014 UNIT 3 RESEARCH PROJECT 2
ClickDimensions Quick Start Guide For Microsoft Dynamics CRM 2011. 9/1/2011 ClickDimensions
 ClickDimensions Quick Start Guide For Microsoft Dynamics CRM 2011 9/1/2011 ClickDimensions Online Training Resources This guide will explain how to register for and use a ClickDimensions Marketing Automation
ClickDimensions Quick Start Guide For Microsoft Dynamics CRM 2011 9/1/2011 ClickDimensions Online Training Resources This guide will explain how to register for and use a ClickDimensions Marketing Automation
CONTENTS. PCI DSS Compliance Guide
 CONTENTS PCI DSS COMPLIANCE FOR YOUR WEBSITE BUILD AND MAINTAIN A SECURE NETWORK AND SYSTEMS Requirement 1: Install and maintain a firewall configuration to protect cardholder data Requirement 2: Do not
CONTENTS PCI DSS COMPLIANCE FOR YOUR WEBSITE BUILD AND MAINTAIN A SECURE NETWORK AND SYSTEMS Requirement 1: Install and maintain a firewall configuration to protect cardholder data Requirement 2: Do not
Fax User Guide 07/31/2014 USER GUIDE
 Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Programming Fundamentals of Web Applications Course 10958A; 5 Days
 Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Programming Fundamentals of Web Applications Course 10958A; 5 Days Course
Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Programming Fundamentals of Web Applications Course 10958A; 5 Days Course
IndusGuard Web Application Firewall Test Drive User Registration
 IndusGuard Web Application Firewall Test Drive User Registration Document Version 1.0 24/06/2015 Confidentiality INDUSFACE HAS PREPARED THIS DOCUMENT FOR INTERNAL PURPOSE. NEITHER THIS DOCUMENT NOR ITS
IndusGuard Web Application Firewall Test Drive User Registration Document Version 1.0 24/06/2015 Confidentiality INDUSFACE HAS PREPARED THIS DOCUMENT FOR INTERNAL PURPOSE. NEITHER THIS DOCUMENT NOR ITS
Web Security School Final Exam
 Web Security School Final Exam By Michael Cobb 1.) Which of the following services is not required to run a Windows server solely configured to run IIS and publish a Web site on the Internet? a. IIS Admin
Web Security School Final Exam By Michael Cobb 1.) Which of the following services is not required to run a Windows server solely configured to run IIS and publish a Web site on the Internet? a. IIS Admin
Installation and configuration guide
 Installation and Configuration Guide Installation and configuration guide Adding X-Forwarded-For support to Forward and Reverse Proxy TMG Servers Published: May 2010 Applies to: Winfrasoft X-Forwarded-For
Installation and Configuration Guide Installation and configuration guide Adding X-Forwarded-For support to Forward and Reverse Proxy TMG Servers Published: May 2010 Applies to: Winfrasoft X-Forwarded-For
CA Service Desk Manager - Mobile Enabler 2.0
 This Document is aimed at providing information about the (CA SDM) Mobile Enabler and mobile capabilities that is typically not available in the product documentation. This is a living document and will
This Document is aimed at providing information about the (CA SDM) Mobile Enabler and mobile capabilities that is typically not available in the product documentation. This is a living document and will
Using Microsoft Expression Web to Upload Your Site
 Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
This course provides students with the knowledge and skills to develop ASP.NET MVC 4 web applications.
 20486B: Developing ASP.NET MVC 4 Web Applications Course Overview This course provides students with the knowledge and skills to develop ASP.NET MVC 4 web applications. Course Introduction Course Introduction
20486B: Developing ASP.NET MVC 4 Web Applications Course Overview This course provides students with the knowledge and skills to develop ASP.NET MVC 4 web applications. Course Introduction Course Introduction
Installation and configuration guide
 Installation and Configuration Guide Installation and configuration guide Adding X-Username support to Forward and Reverse Proxy TMG Servers Published: December 2010 Applies to: Winfrasoft X-Username for
Installation and Configuration Guide Installation and configuration guide Adding X-Username support to Forward and Reverse Proxy TMG Servers Published: December 2010 Applies to: Winfrasoft X-Username for
Maldives Pension Administration Office Republic of Maldives
 A. Background Maldives Pension Administration Office Republic of Maldives Pension and Social Protection Administration Project IDA Credit.: 4611-MV Date: 01 June 2014 Design and Development of the CMDA
A. Background Maldives Pension Administration Office Republic of Maldives Pension and Social Protection Administration Project IDA Credit.: 4611-MV Date: 01 June 2014 Design and Development of the CMDA
IBM Connections Cloud Security
 IBM Connections White Paper September 2014 IBM Connections Cloud Security 2 IBM Connections Cloud Security Contents 3 Introduction 4 Security-rich Infrastructure 6 Policy Enforcement Points Provide Application
IBM Connections White Paper September 2014 IBM Connections Cloud Security 2 IBM Connections Cloud Security Contents 3 Introduction 4 Security-rich Infrastructure 6 Policy Enforcement Points Provide Application
How To Control Vcloud Air From A Microsoft Vcloud 1.1.1 (Vcloud)
 SOC 1 Control Objectives/Activities Matrix goes to great lengths to ensure the security and availability of vcloud Air services. In this effort, we have undergone a variety of industry standard audits,
SOC 1 Control Objectives/Activities Matrix goes to great lengths to ensure the security and availability of vcloud Air services. In this effort, we have undergone a variety of industry standard audits,
Job Ready Assessment Blueprint. Web Design. Test Code: 2750 / Version: 01. Copyright 2011. All Rights Reserved.
 Job Ready Assessment Blueprint Web Design Test Code: 2750 / Version: 01 Copyright 2011. All Rights Reserved. General Assessment Information Blueprint Contents General Assessment Information Written Assessment
Job Ready Assessment Blueprint Web Design Test Code: 2750 / Version: 01 Copyright 2011. All Rights Reserved. General Assessment Information Blueprint Contents General Assessment Information Written Assessment
K7 Business Lite User Manual
 K7 Business Lite User Manual About the Admin Console The Admin Console is a centralized web-based management console. The web console is accessible through any modern web browser from any computer on the
K7 Business Lite User Manual About the Admin Console The Admin Console is a centralized web-based management console. The web console is accessible through any modern web browser from any computer on the
IBM QRadar Security Intelligence April 2013
 IBM QRadar Security Intelligence April 2013 1 2012 IBM Corporation Today s Challenges 2 Organizations Need an Intelligent View into Their Security Posture 3 What is Security Intelligence? Security Intelligence
IBM QRadar Security Intelligence April 2013 1 2012 IBM Corporation Today s Challenges 2 Organizations Need an Intelligent View into Their Security Posture 3 What is Security Intelligence? Security Intelligence
Hacking the WordpressEcosystem
 Hacking the WordpressEcosystem About Me Dan Catalin VASILE Information Security Consultant Researcher / Writer / Presenter OWASP Romania Board Member Online presence http://www.pentest.ro [email protected]/
Hacking the WordpressEcosystem About Me Dan Catalin VASILE Information Security Consultant Researcher / Writer / Presenter OWASP Romania Board Member Online presence http://www.pentest.ro [email protected]/
ONLINE RECONNAISSANCE
 ONLINE RECONNAISSANCE HOW YOUR INTERNET PROFILE CAN BE USED AGAINST YOU May 2013 Most people and organisations put information about themselves on the web. Companies advertise their work and achievements
ONLINE RECONNAISSANCE HOW YOUR INTERNET PROFILE CAN BE USED AGAINST YOU May 2013 Most people and organisations put information about themselves on the web. Companies advertise their work and achievements
About the Canon Mobile Scanning MEAP Application
 About the Canon Mobile Scanning MEAP Application Canon Mobile Scanning MEAP Application (referred to as "this product" hereafter) is a MEAP application that supports receiving data scanned by an imagerunner
About the Canon Mobile Scanning MEAP Application Canon Mobile Scanning MEAP Application (referred to as "this product" hereafter) is a MEAP application that supports receiving data scanned by an imagerunner
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
CRYPTUS DIPLOMA IN IT SECURITY
 CRYPTUS DIPLOMA IN IT SECURITY 6 MONTHS OF TRAINING ON ETHICAL HACKING & INFORMATION SECURITY COURSE NAME: CRYPTUS 6 MONTHS DIPLOMA IN IT SECURITY Course Description This is the Ethical hacking & Information
CRYPTUS DIPLOMA IN IT SECURITY 6 MONTHS OF TRAINING ON ETHICAL HACKING & INFORMATION SECURITY COURSE NAME: CRYPTUS 6 MONTHS DIPLOMA IN IT SECURITY Course Description This is the Ethical hacking & Information
FileMaker Server 10 Help
 FileMaker Server 10 Help 2007-2009 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker, the file folder logo, Bento and the Bento logo
FileMaker Server 10 Help 2007-2009 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker, the file folder logo, Bento and the Bento logo
New Systems and Services Security Guidance
 New Systems and Services Security Guidance Version Version Number Date Author Type of modification / Notes 0.1 29/05/2012 Donna Waymouth First draft 0.2 21/06/2012 Donna Waymouth Update re certificates
New Systems and Services Security Guidance Version Version Number Date Author Type of modification / Notes 0.1 29/05/2012 Donna Waymouth First draft 0.2 21/06/2012 Donna Waymouth Update re certificates
Recon and Mapping Tools and Exploitation Tools in SamuraiWTF Report section Nick Robbins
 Recon and Mapping Tools and Exploitation Tools in SamuraiWTF Report section Nick Robbins During initial stages of penetration testing it is essential to build a strong information foundation before you
Recon and Mapping Tools and Exploitation Tools in SamuraiWTF Report section Nick Robbins During initial stages of penetration testing it is essential to build a strong information foundation before you
Six Common Factors to Consider When selecting a CMS
 By Akshaya Ray, Technical Support Leader, Revize Software Systems When you create a search on the Internet you will find many web content management solutions (also referred to as a CMS content management
By Akshaya Ray, Technical Support Leader, Revize Software Systems When you create a search on the Internet you will find many web content management solutions (also referred to as a CMS content management
Creating Stronger, Safer, Web Facing Code. JPL IT Security Mary Rivera June 17, 2011
 Creating Stronger, Safer, Web Facing Code JPL IT Security Mary Rivera June 17, 2011 Agenda Evolving Threats Operating System Application User Generated Content JPL s Application Security Program Securing
Creating Stronger, Safer, Web Facing Code JPL IT Security Mary Rivera June 17, 2011 Agenda Evolving Threats Operating System Application User Generated Content JPL s Application Security Program Securing
MONTHLY WEBSITE MAINTENANCE PACKAGES
 MONTHLY WEBSITE MAINTENANCE PACKAGES The security and maintenance of your website is serious business, and what you don t know can certainly hurt you. A hacked or spamvertised site can wreak havoc on search
MONTHLY WEBSITE MAINTENANCE PACKAGES The security and maintenance of your website is serious business, and what you don t know can certainly hurt you. A hacked or spamvertised site can wreak havoc on search
Configuring Single Sign-on from the VMware Identity Manager Service to WebEx
 Configuring Single Sign-on from the VMware Identity Manager Service to WebEx VMware Identity Manager SEPTEMBER 2015 V 2 Configuring Single Sign-On from VMware Identity Manager to WebEx Table of Contents
Configuring Single Sign-on from the VMware Identity Manager Service to WebEx VMware Identity Manager SEPTEMBER 2015 V 2 Configuring Single Sign-On from VMware Identity Manager to WebEx Table of Contents
1. Introduction. 2. Web Application. 3. Components. 4. Common Vulnerabilities. 5. Improving security in Web applications
 1. Introduction 2. Web Application 3. Components 4. Common Vulnerabilities 5. Improving security in Web applications 2 What does World Wide Web security mean? Webmasters=> confidence that their site won
1. Introduction 2. Web Application 3. Components 4. Common Vulnerabilities 5. Improving security in Web applications 2 What does World Wide Web security mean? Webmasters=> confidence that their site won
WEB PROTECTION. Features SECURITY OF INFORMATION TECHNOLOGIES
 WEB PROTECTION Features SECURITY OF INFORMATION TECHNOLOGIES The web today has become an indispensable tool for running a business, and is as such a favorite attack vector for hackers. Injecting malicious
WEB PROTECTION Features SECURITY OF INFORMATION TECHNOLOGIES The web today has become an indispensable tool for running a business, and is as such a favorite attack vector for hackers. Injecting malicious
www.nuvox.net, enter the administrator user name and password for that domain.
 Page 1 of 7 Cute_FTP Server Names and Authentication Before connecting to an FTP site you need three pieces of information: the server name or the site you are connecting to and a user name and password.
Page 1 of 7 Cute_FTP Server Names and Authentication Before connecting to an FTP site you need three pieces of information: the server name or the site you are connecting to and a user name and password.
NTT Web Hosting Service [User Manual]
![NTT Web Hosting Service [User Manual] NTT Web Hosting Service [User Manual]](/thumbs/24/4009182.jpg) User Version 0.11 August 22, 2014 NTT Web Hosting Service [User Manual] Presented By: OAM Linux A NTT Communications (Thailand) CO., LTD. Table of Contents NTT Web Hosting Service [User Manual] 1 General...
User Version 0.11 August 22, 2014 NTT Web Hosting Service [User Manual] Presented By: OAM Linux A NTT Communications (Thailand) CO., LTD. Table of Contents NTT Web Hosting Service [User Manual] 1 General...
Security and Compliance Suite
 Security and Compliance Suite Quick Tour The Qualys user interface is easy-to-use with powerful Web 2.0 capabilities featuring interactive dashboards, actionable menus and workflows, context-based interactions
Security and Compliance Suite Quick Tour The Qualys user interface is easy-to-use with powerful Web 2.0 capabilities featuring interactive dashboards, actionable menus and workflows, context-based interactions
Compliance series Guide to meeting requirements of the UK Government Cyber Essentials Scheme
 Compliance series Guide to meeting requirements of the UK Government Cyber Essentials Scheme avecto.com Contents Introduction to the scheme 2 Boundary firewalls and internet gateways 3 Secure configuration
Compliance series Guide to meeting requirements of the UK Government Cyber Essentials Scheme avecto.com Contents Introduction to the scheme 2 Boundary firewalls and internet gateways 3 Secure configuration
The PA-4000 Series can add visibility and control into your network for webmail applications to stop incoming threats and limit uploaded data.
 Controlling Webmail Tech Note Overview Webmail interfaces are widespread and available from search providers (Yahoo, Google), software vendors (Microsoft s Hotmail), social networking sites (Myspace, Facebook),
Controlling Webmail Tech Note Overview Webmail interfaces are widespread and available from search providers (Yahoo, Google), software vendors (Microsoft s Hotmail), social networking sites (Myspace, Facebook),
Network Assessment. Prepared For: Prospect Or Customer Prepared By: Your Company Name
 Network Assessment Prepared For: Prospect Or Customer Prepared By: Your Company Name Environment Risk and Issue Score Issue Review Next Steps Agenda Environment - Overview Domain Domain Controllers 4 Number
Network Assessment Prepared For: Prospect Or Customer Prepared By: Your Company Name Environment Risk and Issue Score Issue Review Next Steps Agenda Environment - Overview Domain Domain Controllers 4 Number
WompMobile Technical FAQ
 WompMobile Technical FAQ What are the technical benefits of WompMobile? The mobile site has the same exact URL as the desktop website. The mobile site automatically and instantly syncs with the desktop
WompMobile Technical FAQ What are the technical benefits of WompMobile? The mobile site has the same exact URL as the desktop website. The mobile site automatically and instantly syncs with the desktop
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
HOW TO SILENTLY INSTALL CLOUD LINK REMOTELY WITHOUT SUPERVISION
 HOW TO SILENTLY INSTALL CLOUD LINK REMOTELY WITHOUT SUPERVISION Version 1.1 / Last updated November 2012 INTRODUCTION The Cloud Link for Windows client software is packaged as an MSI (Microsoft Installer)
HOW TO SILENTLY INSTALL CLOUD LINK REMOTELY WITHOUT SUPERVISION Version 1.1 / Last updated November 2012 INTRODUCTION The Cloud Link for Windows client software is packaged as an MSI (Microsoft Installer)
Cybersecurity Health Check At A Glance
 This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
Montefiore Portal Quick Reference Guide
 Montefiore Portal Quick Reference Guide Montefiore s remote portal allows users to securely access Windows applications, file shares, internal web applications, and more. To use the Portal, you must already
Montefiore Portal Quick Reference Guide Montefiore s remote portal allows users to securely access Windows applications, file shares, internal web applications, and more. To use the Portal, you must already
MyCompany Professional Web Developer Certification Examination Specification
 MyCompany Professional Web Developer Certification Examination Specification Introduction This is a sample of an exam specification and is not representative of any actual exam specification. The exam
MyCompany Professional Web Developer Certification Examination Specification Introduction This is a sample of an exam specification and is not representative of any actual exam specification. The exam
INFORMATION GOVERNANCE POLICY: NETWORK SECURITY
 INFORMATION GOVERNANCE POLICY: NETWORK SECURITY Original Approved by: Policy and Procedure Ratification Sub-group on 23 October 2007 Version 1.2 Approved by: Information Governance Group Approval Date:
INFORMATION GOVERNANCE POLICY: NETWORK SECURITY Original Approved by: Policy and Procedure Ratification Sub-group on 23 October 2007 Version 1.2 Approved by: Information Governance Group Approval Date:
Enterprise-Grade Security from the Cloud
 Datasheet Website Security Enterprise-Grade Security from the Cloud Unmatched web application security experience, enhanced by real-time big data analytics, enables Incapsula to provide best-of-breed security
Datasheet Website Security Enterprise-Grade Security from the Cloud Unmatched web application security experience, enhanced by real-time big data analytics, enables Incapsula to provide best-of-breed security
Analysis of SQL injection prevention using a proxy server
 Computer Science Honours 2005 Project Proposal Analysis of SQL injection prevention using a proxy server By David Rowe Supervisor: Barry Irwin Department of Computer
Computer Science Honours 2005 Project Proposal Analysis of SQL injection prevention using a proxy server By David Rowe Supervisor: Barry Irwin Department of Computer
A Manager s Guide to Unified Threat Management and Next-Gen Firewalls
 A Manager s Guide to Unified Threat Management and Next-Gen Firewalls Key factors to justify and evaluate UTM and NGFW systems By Udo Kerst, Director Product Management, Network Security and Barbara Hudson,
A Manager s Guide to Unified Threat Management and Next-Gen Firewalls Key factors to justify and evaluate UTM and NGFW systems By Udo Kerst, Director Product Management, Network Security and Barbara Hudson,
Strong Authentication for Microsoft TS Web / RD Web
 Strong Authentication for Microsoft TS Web / RD Web with Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright Copyright 2011. CRYPTOCard
Strong Authentication for Microsoft TS Web / RD Web with Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright Copyright 2011. CRYPTOCard
Work with PassKey Manager
 Work with PassKey Manager Trademark Notice Blackboard, the Blackboard logos, and the unique trade dress of Blackboard are the trademarks, service marks, trade dress and logos of Blackboard, Inc. All other
Work with PassKey Manager Trademark Notice Blackboard, the Blackboard logos, and the unique trade dress of Blackboard are the trademarks, service marks, trade dress and logos of Blackboard, Inc. All other
Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive
 Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
NTP Software File Auditor for Windows Edition
 NTP Software File Auditor for Windows Edition An NTP Software Installation Guide Abstract This guide provides a short introduction to installation and initial configuration of NTP Software File Auditor
NTP Software File Auditor for Windows Edition An NTP Software Installation Guide Abstract This guide provides a short introduction to installation and initial configuration of NTP Software File Auditor
WEBSITE REDESIGN PROCESS Project Plan Overview: DRAFT Updated 1/26/12 A> DEFINITION AND PLANNING
 WEBSITE REDESIGN PROCESS Project Plan Overview: DRAFT Updated 1/26/12 A> DEFINITION AND PLANNING B> SITE STRUCTURE AND CONTENT C> VISUAL DESIGN D> SITE DEVELOPMENT E> TESTING F> LAUNCH AND POST LAUNCH
WEBSITE REDESIGN PROCESS Project Plan Overview: DRAFT Updated 1/26/12 A> DEFINITION AND PLANNING B> SITE STRUCTURE AND CONTENT C> VISUAL DESIGN D> SITE DEVELOPMENT E> TESTING F> LAUNCH AND POST LAUNCH
