Domain Name Forensics: A Systematic Approach to Investigating an Internet Presence
|
|
|
- Gloria Marsh
- 10 years ago
- Views:
Transcription
1 Domain Name Forensics: A Systematic Approach to Investigating an Internet Presence by Bruce J. Nikkel [email protected] Originally published by Elsevier in Digital Investigation The International Journal of Digital Forensics and Incident Response Vol. 1, No. 4 (doi: /j.diin ) August 1, 2005 Abstract Over the last few years the typical Internet presence has become a crowded outsourcing arrangement of multiple organizations dividing up the complexity of maintaining various parts of an infrastructure. Finding the parties responsible for the different infrastructure areas has become time consuming and error prone. This paper presents a systematic approach to investigating a complex Internet presence, including collecting, time-stamping, packaging, preserving, and presenting evidence. It is geared towards the network forensics practitioner. Keywords: Digital Forensics, Network Forensics, Domain Name Investigation, Domain Name Forensics, DNS Investigation, Website Investigation 1
2 Contents 1 Introduction 3 2 Advantages of Complexity 3 3 Identifying Points of Responsibility Domain Name Registrars Domain Name Registrants DNS Server Owners Regional Internet Registries Network Owners Web Server Owners Server Owners Upstream ISP Telecommunications Carriers Routes and AS owners Other Responsible Parties The next generation, IPv Collecting and Preserving the Evidence Preparing for the Investigation Investigating the Domain Registry and Registrant Investigating the DNS Owners Investigating the IP Network Owners Investigating the Reverse DNS Investigating the Webserver Owner Investigating the Upstream ISPs Investigating the Routing Information Investigating the Physical Location Investigating the Owners Finding Additional Information Packaging and Preserving the Evidence 16 6 Presenting the Evidence 17 7 Conclusion and Future Work 17 2
3 1 Introduction Tools such as whois or nslookup have traditionally provided a quick and simple method of investigating who is behind a particular Internet site. Unfortunately, the number of involved parties playing a role in maintaining an Internet presence has increased dramatically over the past few years making it more difficult for an investigator to identify those responsible for a site or it s infrastructure. A typical modern Internet presence has become a crowded outsourcing arrangement of multiple organizations dividing up the complexity of maintaining various parts of an infrastructure. Today there are often separate organizations managing the DNS, the IP network, and the various other server system platforms ( , web, application, and database servers, etc.). Servers are physically co-located, websites are virtually hosted, and other critical infrastructure components are sub-contracted out. Even the previously centralized role of Network Solutions Inc. 1 has turned into a large competitive market of registrars. What used to be a trivial investigative task has now become time consuming and error prone. A more systematic approach is needed which identifies the various responsible parties in an orderly manner and treats the information gathered as evidence. A method for collecting, time-stamping, packaging, preserving, and presenting this evidence is needed. This paper outlines some simple procedures for achieving this goal. 2 Advantages of Complexity In spite of the issues just mentioned, the additional complexity brings some interesting benefits for investigators. Having critical infrastructure spread across multiple parties can, in some cases, help investigators overcome legal jurisdiction hurdles, as well as solve issues regarding anonymity. Illegal activity done using Internet infrastructure residing outside a local jurisdiction has always been difficult to bring under control. But with more parties involved, the chances of having a piece of critical infrastructure residing within a region s legal jurisdiction are increased. This could provide investigators with additional sources of evidence, or even opportunities to disable a site. 1 Once the sole registrar for.com,.net, and.edu 3
4 The privacy and protection offered by anonymity is continuously misused by criminals to hide their identities from law enforcement and other investigative bodies. The more parties involved in the existence of an Internet presence, the more difficult it becomes for an entity to remain completely anonymous. Each outsourced party may have a certain amount of information about the anonymous entity (billing, registration, physical location, etc.). Piecing this information together could assist in the identification of the anonymous entity. 3 Identifying Points of Responsibility In order to systematically proceed with an investigation, we need to identify the major parties responsible for maintaining an Internet presence. This section outlines the major responsible parties involved, identifies information each party may be able to provide, and identifies the capability they have to disable an Internet presence (if legally or ethically compelled to do so). 3.1 Domain Name Registrars Before a domain name is recognized, it must be registered with the registrar of a Top Level Domain (TLD). Most countries centrally manage registrations to their own Country Code TLDs (for example.uk or.ch). Generic TLDs (for example.com or.org) are managed by independent registrars (for example Network Solutions Inc, or Register.com). Among other things, the registrar is responsible for maintaining contact information and name server information for registered domains under its control. A registrar also has the ability to deactivate or delete domain names under its responsibility. 3.2 Domain Name Registrants The domain name registrants are those parties responsible for registering and maintaining a domain name. This typically includes the registrant, an administrative contact, a technical contact, and possibly a billing contact. These domain owners have the ability to deactivate their domain or to modify the information specifying the DNS servers and contacts. 3.3 DNS Server Owners Name server owners control the DNS zones which resolve IP addresses and domain names. Maintaining DNS servers for a domain can be done by anyone, anywhere on the Internet (for example, a remote ISP, the registrar, dynamic DNS hosters, etc.). The DNS server owners can provide information about other hosts within the same domain or IP range. The DNS server 4
5 owners also have the ability to modify or disable DNS resolution for domains under their control. 3.4 Regional Internet Registries Control of the Internet Protocol (IP) address space has been delegated to four Regional Internet Registries (RIRs). In general, regional delegation is as follows[4]: ARIN for North America and sub-saharan Africa LACNIC for South America and the Caribbean Islands APNIC for the Asia/Pacific region RIPE for Europe, the middle east, northern Africa and central Asia A newcomer, AfriNIC, may manage address space for the African continent in the future. These RIRs further delegate IP ranges to Local Internet Registries (LIRs) and National Internet Registries (NIRs) within a region. Internet Registries provide information about who is responsible for a particular IP range. 3.5 Network Owners Network owners are those parties responsible for managing a particular IP network. They typically handle things like routing, link-layer connectivity and possibly reverse DNS lookups for a network. They can provide information about network topologies, physical links (including geographic location), and contact information for further delegated subnets. They have the ability to monitor Internet traffic and the possibility to provide access logs for dial-up connections. The owner of a network has the ability to disconnect subnets from the Internet either physically or by removing the relevant routing information. 3.6 Web Server Owners Web server owners are responsible for providing a platform for storing and serving web content. They are responsible for the system administration of the server operating system and the web serving software. They may also be responsible for the server hardware (but not necessarily). These machines may be located at a remote site, or co-located at a central location together with other servers. The web server owner may be able to provide information about the people responsible for the web content, including file transfer logs or content management access. They may be able to provide HTTP access logs of the site including downloaded files. They even have the ability to provide investigative access to restricted areas of a site. The 5
6 web server owner is able to shutdown a website, redirect it elsewhere, or modify/remove content contained on the site Server Owners service can be broken down into two basic parts, which may or may not be owned by the same party. Sending servers 2 forward or deliver to other servers or mailboxes. Servers which store delivered provide access to mailboxes via the POP or IMAP protocols, and may provide a web front-end as well. server owners can provide logs of both incoming and outgoing traffic, and may provide investigative access to mailboxes. server owners are also in a position to monitor message activity for investigative purposes. The server owners also have the ability to reject to/from a particular domain. 3.8 Upstream ISP Large ISPs and commercial networks are connected to each other through peering agreements at Internet Exchanges (IXs), Network Access Points (NAPs), or Metropolitan Area Exchanges (MAEs). These larger entities often provide bandwidth to smaller ISPs. Sometimes information about a site can be found by examining the surrounding ISPs. These upstream ISPs may also have the ability to monitor or block traffic to or from an attached site. 3.9 Telecommunications Carriers The local telecommunications carriers are responsible for the last mile of physical connectivity. They maintain the physical link between a site and the ISP s nearest point of presence. This could be a leased line, frame relay connection, or some other link layer technology. Home and small business connections may also have ADSL or cable connections. The carrier will be able to provide information about the physical location of a site. It may also have information about other network links at that physical location. The telecommunications carrier is able to disconnect a site from an ISP Routes and AS owners In the distant past a single routing table was maintained for every network on the entire Internet. Internet routing has evolved considerably since then and today[2] uses Autonomous Systems (AS) which exchange routing information with peers using the Border Gateway Protocol (BGP 3 ). Each AS 2 properly referred to as Message Transfer Agents or MTAs 3 Currently BGP version 4 6
7 has an AS Number (ASN) with the associated contact information available by querying whois databases. An AS has the ability to filter routing information entering or leaving the AS Other Responsible Parties There are many other possible places to investigate an Internet presence. So far we have identified the most common parties involved at the infrastructure level. Other potential investigative points include such areas as: content management or publishing services web design companies distributed web caching services SSL Certificate Authorities application and database back-end providers other hosts on the same network segment or same domain name other parties mentioned or linked in the website s content All of these areas could provide an investigator with useful information or assistance in disabling a site or finding the identities of people behind it The next generation, IPv6 The original IP protocol (version 4) has worked well for a number of years, but it is not without its problems. The next generation, IP version 6 was designed to fix a number of shortcomings in scalability and security which haunt the current Internet. The IPv6 Internet already exists and is growing (it is already common to see IPv6 name servers appearing in DNS lookups). In the future this will also be territory which will need to be part of every investigation. Fortunately, the methods outlined here will transfer easily to this new network layer, since it is conceptually similar to IPv4. 4 Collecting and Preserving the Evidence This next section shows a practical investigation of an Internet presence. We start with only one piece of information: the website name. From this, we systematically do whois and DNS lookups to uncover the responsible parties. Investigating a modern Internet presence can generate a lot of query data, so it is imperative to save everything in an organized manner and to keep a record of the work that was done. 7
8 4.1 Preparing for the Investigation The data we collect is evidence. The record of all our activity shows the procedures used to acquire the evidence. From this evidence, we will generate a report outlining the various points of responsibility together with contact information. It should be possible for an independent investigator to verify the contents of the report from the evidence collected. For our investigation we will use a command line shell to systematically pipe collected evidence into an organized set of files. The example procedure shown is from a generic Unix shell, but it will also work on Linux, Mac OSX, and Windows shells (for Windows, additional tools may need to be installed separately). There are certain forensic advantages to collecting evidence with a command line instead of GUI or online Web interfaces: Each file containing evidence has a system generated time-stamp showing the exact time of evidence collection. Collected evidence is transferred from the collection tools directly to the files without human intervention 4 The Whois and DNS server names are explicitly defined and logged, showing that the evidence was collected from authoritative sources. A complete transcript log of the evidence collection procedure is available for scrutiny. The example site we will be investigating is [3] We begin by creating and entering our evidence directory and recording our session: $ mkdir evidence $ cd evidence $ script record.txt The Unix script command will keep a record of everything we see or type (including control characters). The file record.txt is the raw transcript of our investigation and will be included together with the rest of the evidence we will collect. Throughout this document we will be using Unix redirection ( > ) to pipe evidential data into files. The first character of the file name denotes the content (W=Whois, N=Nslookup, T=Traceroute). These files may be read with standard Unix tools such as cat or more, etc. Do not edit or modify these files. Doing so will update the modification time-stamp, causing the time of evidence collection to be lost. 4 Human errors from graphical interactions such as copying and pasting are eliminated. 8
9 The Network Time Protocol[8] (NTP) can keep the system time accurate to a few tens of milliseconds. To show that our investigative machine is properly time synchronized[7], we use the ntpq command to save the time synchronization status 5 : $ ntpq -p > timesync.txt Every file we create will have system time-stamps which we will later preserve when we package the evidence. Since we are collecting evidence snapshots of things which will change over time, accurately time-stamping the moment of evidence collection is important. At this point we can start writing our report which will be updated as we proceed with the investigation. To begin the report, state the time and date as seen with the unix date command: $ date Also state in the report that the investigative machine had the correct time and date when the investigation took place. If website content is of evidential value, now would be a good time to acquire it. Proper acquisition of remote websites is outside the scope of this paper, but may be addressed in future work. We now move on to getting the information about the various parties involved. 4.2 Investigating the Domain Registry and Registrant We will need to do a number of whois lookups, but first, we need to know which whois servers to use. The initial whois information can be found at the Internet Assigned Numbers Authority (IANA). A summary is provided here: For.com,.net, and.edu domains, queries to whois.internic.net will refer us to the appropriate independent registrar s whois server. For.org domains, we use whois.pir.org Databases for other generic TLDs (gtlds) such as.biz or.info, can be found at Databases for country code TLDs (cctlds) such as.ch or.uk can be found at 5 If NTP synchronization is not an option, the rdate command could be used 9
10 Using whois 6, we look up example.com using whois.internic.net. Since this is a.com domain, it is not managed by a central registrar and the query will point us to the managing registrar s whois server. We save the registrar information as follows: $ whois -h whois.internic.net example.com > W_DomainRegistry.txt From this, we will get the name of the registrar, a link to their website, and their whois server. The registrar is one of our points of responsibility. We note the registrar s name and website in our report under the heading Domain Name Registry. For example.com, the registrar s whois server is whois.iana.org. Using this server, we do another whois lookup of the domain name: $ whois -h whois.iana.org example.com > W_DomainOwner.txt Here we find the traditional whois database info about the registrant, technical, admin, and billing contacts. If they are shown, these contacts are all potential points of responsibility. We note these contacts in our report under the heading Domain Owners. A word of caution: The registrars are under no obligation to verify the quality if this information. It could be falsified, anonymized, or registered by a proxy service. 4.3 Investigating the DNS Owners The last whois query also gave us a list of the name servers. Anyone controlling the DNS servers is a potential point of responsibility. We therefore do whois lookups on the name server s domain name(s) and save them as evidence. For example.com the name server s domain name was ianaservers.net: $ whois -h whois.internic.net iana-servers.net # find registrar $ whois -h whois.register.com iana-servers.net > W_DNSserver.txt We note the names of the name server contacts in our report under the heading DNS Server Owners 4.4 Investigating the IP Network Owners Now that we know who controls the domain s whois data and name servers, we move on to finding out more about the owners of the IP address. For this we use the traditional nslookup tool 7. 6 The whois client used in this paper is a simple traditional whois client without any special query features 7 dig is a more modern replacement, but not all systems include it by default 10
11 $ nslookup a.iana-servers.net > N_Website.txt Note how we used the domain s name server (a.iana-servers.net) which was found in previous whois lookups. This ensures the data we receive is authoritative[1]. A thorough investigation would include additional nslookups against each name server to reveal any inconsistencies. We now have the IP address which will help us find information about the network owners. The whois server used depends on the geographic region of the IP range, and will be one of the four Regional Internet Registries: whois.arin.net (North America/Sub-Sahara Africa) whois.ripe.net (Europe/Mid-East/Central Asia/North Africa) whois.apnic.net (Asia/Pacific) whois.lacnic.net (South America/Caribbean) If you don t know the region, then try all four. Here we guess that it is in North America: $ whois -h whois.arin.net > W_IPaddress.txt Local Internet Registries (LIRs) and National Internet Registries (NIRs) may also have additional whois servers with more information specific to smaller IP networks[4]. Any contact information found from the Internet Registry whois lookups, we record in our report under the heading Network Owners. We also include the names of the Internet Registries (RIR, LIR or NIR) where the IP range exists. 4.5 Investigating the Reverse DNS There is still more info we can find about potential network owners. This is done by querying for the Start Of Authority (SOA) resource records of the in-addr.arpa address. The SOA Resource Record (RR) provides us with the authoritative name server for a zone, that is, the name server with the best data out of all the name servers listed. The SOA RR also gives us the address of the person responsible for that data (this address is somewhat obscured, the first dot in the mail addr field is ). 11
12 The.arpa (Address and Routing Parameter Area) domain is a special domain used for Internet infrastructure[10]. The few sub-domains are under the responsibility of the Internet Architecture Board (IAB). The in-addr.arpa domain is of interest to us, because it provides us with information about Internet addresses (ip6.arpa is the IPv6 equivalent). Specifically, the in-addr.arpa domain tells us which name servers will provide us with reverse lookups of an IP network. Performing an in-addr.arpa query can be a bit tricky. It involves reversing the order of the IP network address and adding it to the in-addr.arpa domain. A thorough explanation of this can be found in DNS and BIND [1]. To illustrate, we perform this query on the network containing $ nslookup -type=soa in-addr.arpa > N_inaddrarpa.txt Note how is the first three octets of the webserver s IP address ( ), but reversed. This is intentional and part of how DNS works[1]. A thorough investigation would include additional nslookups against each name server to reveal inconsistencies. Record the address in the report and do a whois lookup of the server domain in the origin field, as well as any other name server domains. These are all potential points of responsibility and should be noted under the heading Network Owners. Since example.com s name server domain (for the in-addr.arpa zone) is icann.org, we use whois.pir.org to perform the query: $ whois -h whois.pir.org icann.org > W_IPDNSserver.txt 4.6 Investigating the Webserver Owner If the website is being virtually hosted[5], the IP address may resolve to something other than itself, possibly revealing the owner of the machine. We can find the Fully Qualified Domain Name (FQDN) of the machine by doing a reverse lookup on the IP address. A word of caution: be careful when trusting DNS lookups of IP addresses. Anyone controlling address resolution for a particular IP range can arbitrarily assign any host or domain name to those IP addresses. This is an easy method for malicious network owners to frame other people or mislead investigators. Using the a.iana-servers.net name server found in previous queries, we lookup the FQDN behind the IP address: $ nslookup a.iana-servers.net > N_IPaddress.txt 12
13 If it is not the same as the website, we do a whois lookup on the FQDN and save it as evidence, it may be the web server owner: $ whois -h whois.internic.net examplehoster.com # find registrar $ whois -h whois.godaddy.com examplehoster.com > W_Webserver.txt Here examplehoster.com and whois.godaddy.com were just used to show the procedure. The site s IP address actually resolves back to itself correctly, indicating that the web server owner is probably already identified in a previous whois query. Either way, we make a note of the results in our report under the heading Web Server Owners since this is a potential point of responsibility. 4.7 Investigating the Upstream ISPs We now try to find some information about adjacent networks using traceroute. This may take some time since some firewalls will silently drop certain ICMP traffic along the way, causing timeouts and gaps in the trace: $ traceroute > T_FromMyISP.txt The data collected here will give us some addresses of upstream ISP routers to which the site is attached. It could also give us some clues as to the geographic region of the site. The last hops in the traceroute could be a potential points of responsibility. We do a whois lookup of alter.net (seen in our traceroute) and make a note in our report under Upstream ISPs. $ whois -h whois.internic.net alter.net # find registrar $ whois -h whois.networksolutions.com alter.net > W_UpstreamISP.txt 4.8 Investigating the Routing Information Another useful way to find information about the upstream providers is to analyze an IP s routing information. This will tell us the Autonomous System Number to which the site belongs, as well as contact information for that ASN. To find this, we look to the Internet Routing Registry ( The IRR maintains a list of routing registries which provide information about routes and routing policies[11][12] which can be queried with the standard whois command. While the IRR has a large list of routing registries, Merit Network Inc. ( has attempted to mirror most of them. We query their whois server with s IP address as follows: $ whois -h whois.radb.net > W_IRR.txt 13
14 Here we see various bits of information, including the size of the block and the ASN to which the IP address belongs. Once we know the AS number, we can find out more by querying the Regional Internet Registry servers. The AS Numbers allocated to the RIRs can be found at IANA: Not all whois servers use the same syntax for AS queries, but here are some examples: whois -h whois.arin.net a 11 whois -h whois.ripe.net AS559 whois -h whois.lacnic.net whois -h whois.apnic.net AS23552 Using whois.arin.net (identified at IANA), we query for AS where s IP address belongs: $ whois -h whois.arin.net a > W_AS.txt We record any contact information in our report under the heading AS Owners For this procedure was fairly simple and straight forward. Other IP addresses may be more difficult to investigate, possibly requiring additional whois lookups at local routing registries. A detailed analysis of Internet routing investigation is outside the scope of this paper, but may be covered in future work. 4.9 Investigating the Physical Location The physical location of a site is also of importance. If the ISP and general location of a site is known, it may be possible to determine the telecommunications carrier responsible for the lower layer network connections (leased lines, frame-relay, etc.). In smaller countries there is often a single carrier which manages the last mile communications links for the entire country. If the country of origin is known, the carrier may also be known, and should be added to the report as a potential point of responsibility under the heading Telecommunications Carrier. Another possibility of determining the physical location of a site is to examine the type of ISP. If the site is using a co-location provider, then the server will be physically located at the ISP. In this case, the investigated site s geographical address is the same as the ISP. 14
15 4.10 Investigating the Owners servers can also be interesting information for a case. Investigating the owners of a domain s servers is just applying more of the same techniques as we ve previously used. First, we ll query for the domain s mx (Mail Exchanger) resource records using an authoritative server: $ nslookup -type=mx example.com a.iana-servers.net > N_MXServer.txt This will typically include a list of mail servers and backup mail relays which are accepting on behalf of a domain 8. The owners of these machines are potential points of responsibility for the suspect domain s traffic. A whois lookup of each mail server s domain should be saved as evidence and the contacts noted in the report under the heading Server Owners Finding Additional Information Whois databases can be used for more than just domain name and IP address queries. As we saw with ASNs, searching can also be done with other keywords. Depending on the whois database used, searches for Names, Addresses, NIC handles, etc. can be queried. Check with the whois database for more information on creating queries. For example: $ whois -h whois.networksolutions.com help $ whois -h whois.ripe.net help Other DNS Resource Records could also be queried for information. For example, RR s which may be of interest (if they exist) could be the Canonical Name (CNAME), the Responsible Person (RP) or Host Info (HINFO). For more information on other RR s used, see [13]. The investigation that we have just completed is somewhat simplified. There may be large numbers of servers providing redundant DNS, Web, or services for a site. These are all potential points of responsibility and each one should be analyzed for inclusion in the report. In such cases, we simply number the files as follows: $ whois -h networksolutions.com domaina.com > W_MXserver1.txt $ whois -h networksolutions.com domainb.com > W_MXserver2.txt $ whois -h networksolutions.com domainc.com > W_MXserver3.txt $ whois -h networksolutions.com domaind.com > W_MXserver4.txt and so on... 8 example.com is a poor example here, since it has no mx records (probably for good reason) 15
16 Exhaustively collecting all this information will generate a lot of data, but the procedure outlined here will keep the process organized and manageable. 5 Packaging and Preserving the Evidence Once we are satisfied that our collection of evidence is complete, we need to package it in a simple format that can be distributed to people who may need it for reference. We also need to include a method to ensure the evidence has not been altered. Before we do this, we exit the script program and leave the directory. Then we package the collected evidence using the Unix tar command: $ exit $ cd.. $ tar cvf evidence.tar evidence The tar command will create a single file which can be opened with most modern unpacking programs (like winzip). This command will also package any sub-directories that may have been created (like recursive downloads of websites). Tar will also preserve the file modification time-stamps of our evidence files (the time of collection in this procedure), and preserve the Unix user-id of the investigator who created the files 9 The final step in packaging our evidence is to make a cryptographic hash of the tar file. This hash needs to be kept separately for the purpose of verifying that the evidence integrity has been maintained. This is done as follows 10 : $ md5sum evidence.tar > evidence.md5 if you have no md5sum command, but you have openssl: $ openssl md5 evidence.tar > evidence.md5 The evidence.md5 file should be included with the report, and also stored separately in a safe place. If a particular investigator needs to sign off on the evidence collection, a PGP signature of the hash or the tar file could also be taken. 9 This entire investigation can be done without root privileges. 10 md5sum and the MD5 alogrithm are used in these examples but there are many other tools and algorithms available. 16
17 6 Presenting the Evidence Our report so far has consisted almost entirely of contact information. For every potential point of responsibility we have identified names, phone numbers, fax numbers, and physical addresses, and website names. Without going into too much technical detail, we have created a report during the course of the investigation that non-technical staff can use within the context of their roles (legal staff, for example). The information in the report can be independently verified based on the data in the evidence.tar file. The integrity of the evidence.tar file can be verified with the evidence.md5 file (a copy of which should be kept separately in a safe place). 7 Conclusion and Future Work This paper organizes the investigation of an Internet presence. It outlines the forensic analysis of domain names and IP networks and has completed the following: Defined the points of responsibility related to an Internet presence. Systematically collected and time-stamped the evidence which identifies these parties. Saved and packaged the evidence in an organized manner. Created a cryptographic hash of the evidence to ensure integrity is preserved. Created a verifiable report presenting the contact information found in the evidence. Several areas were touched upon in this paper where future work could be done. The area of remote website acquisition for investigative purposes needs to be addressed. The forensic analysis of IP routing (including the core routing protocols) would be useful. Network forensics relating to IPv6 also needs to be analyzed in more depth. References [1] Paul Albitz and Cricket Liu. DNS and BIND, 3rd Ed. 1998, O Reilly & Associates 17
18 [2] Bassam Halabi. Internet Routing Architectures, Cisco Press, 1997, New Riders Publishing [3] RFC2606 allows example.com to be used for documentation and testing. RFC Reserved Top Level DNS Names, 1999 [4] RIRs are listed at Follow the links for more info about NIRs and LIRs [5] Virtual hosting allows multiple websites to be served from a single IP address. See section of RFC Hypertext Transfer Protocol HTTP/1.1, 1999 [6] This was a simple example using a class C address. For information on Classless networks see RFC Classless Inter-Domain Routing (CIDR): an Address Assignment and Aggregation Strategy, 1993 [7] For information on time synchronizing a machine using NTP servers see [8] RFC Network Time Protocol (Version 3) Specification, Implementation, 1992 [9] RFC A Border Gateway Protocol 4 (BGP-4), 1995 [10] RFC Management Guidelines & Operational Requirements for the Address and Routing Parameter Area Domain ( arpa ), 2001 [11] RFC-2622: Routing Policy Specification Language, 1999 [12] RFC-2650: Using RPSL in Practice, 1999 [13] RFC New DNS RR Definitions,
19 Document History Aug-Oct 2004: Created original article Oct 14, 2004: Submitted to Elsevier Dec 14, 2004: Published in Digital Investigation Journal April 27,2005: Minor corrections. Changed examples to use md5sum instead of md5 August 1,2005 Added table of contents and document history 19
How to use the UNIX commands for incident handling. June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan
 How to use the UNIX commands for incident handling June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan Agenda Training Environment Commands for incident handling network
How to use the UNIX commands for incident handling June 12, 2013 Koichiro (Sparky) Komiyama Sam Sasaki JPCERT Coordination Center, Japan Agenda Training Environment Commands for incident handling network
Glossary of Technical Terms Related to IPv6
 AAAA Record An AAAA record stores a 128-bit Internet Protocol version 6 (IPv6) address, which does not fit the standard A record format. For example, 2007:0db6:85a3:0000:0000:6a2e:0371:7234 is a valid
AAAA Record An AAAA record stores a 128-bit Internet Protocol version 6 (IPv6) address, which does not fit the standard A record format. For example, 2007:0db6:85a3:0000:0000:6a2e:0371:7234 is a valid
Part I - Gathering WHOIS Information
 Part I - Gathering WHOIS Information Exercise 1: command-line WHOIS queries: in the following exercise you will use a Linux system to perform WHOIS lookups from a command-line. This requires outbound TCP
Part I - Gathering WHOIS Information Exercise 1: command-line WHOIS queries: in the following exercise you will use a Linux system to perform WHOIS lookups from a command-line. This requires outbound TCP
APNIC IPv6 Deployment
 APNIC IPv6 Deployment Ulaanbaatar, Mongolia 19 October 2015 Issue Date: Revision: Overview Deployment motivation Network deployment IPv6 Services deployment IPv6 Anycast service IPv6 Cloud service Summary
APNIC IPv6 Deployment Ulaanbaatar, Mongolia 19 October 2015 Issue Date: Revision: Overview Deployment motivation Network deployment IPv6 Services deployment IPv6 Anycast service IPv6 Cloud service Summary
The IANA Functions. An Introduction to the Internet Assigned Numbers Authority (IANA) Functions
 The IANA Functions An Introduction to the Internet Assigned Numbers Authority (IANA) Functions Contents SECTION 1: INTRODUCTION 4 SECTION 2: POLICY, STAKEHOLDERS AND STEWARDSHIP IMPLEMENTATION 6 SECTION
The IANA Functions An Introduction to the Internet Assigned Numbers Authority (IANA) Functions Contents SECTION 1: INTRODUCTION 4 SECTION 2: POLICY, STAKEHOLDERS AND STEWARDSHIP IMPLEMENTATION 6 SECTION
Topic 1: Internet Architecture & Addressing
 Topic 1: Internet Architecture & Addressing Objectives Understand the general architecture of Internet Identify the main actors in the Internet architecture Identify the main organizations implied in Internet
Topic 1: Internet Architecture & Addressing Objectives Understand the general architecture of Internet Identify the main actors in the Internet architecture Identify the main organizations implied in Internet
Distributed Systems. 09. Naming. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 09. Naming Paul Krzyzanowski Rutgers University Fall 2015 October 7, 2015 2014-2015 Paul Krzyzanowski 1 Naming things Naming: map names to objects Helps with using, sharing, and communicating
Distributed Systems 09. Naming Paul Krzyzanowski Rutgers University Fall 2015 October 7, 2015 2014-2015 Paul Krzyzanowski 1 Naming things Naming: map names to objects Helps with using, sharing, and communicating
THE MASTER LIST OF DNS TERMINOLOGY. v 2.0
 THE MASTER LIST OF DNS TERMINOLOGY v 2.0 DNS can be hard to understand and if you re unfamiliar with the terminology, learning more about DNS can seem as daunting as learning a new language. To help people
THE MASTER LIST OF DNS TERMINOLOGY v 2.0 DNS can be hard to understand and if you re unfamiliar with the terminology, learning more about DNS can seem as daunting as learning a new language. To help people
DNS and BIND Primer. Pete Nesbitt pete @ linux1.ca. April 2012
 DNS and BIND Primer Pete Nesbitt pete @ linux1.ca April 2012 1 When we access the Internet we typically do so by accessing systems using a somewhat meaningful hostname often in the form of a web based
DNS and BIND Primer Pete Nesbitt pete @ linux1.ca April 2012 1 When we access the Internet we typically do so by accessing systems using a somewhat meaningful hostname often in the form of a web based
Internet Structure and Organization
 Internet Structure and Organization Resources management and allocation [email protected] Introduction What s the Internet? Why organizations / bodies are needed? Define protocol specifications Agree
Internet Structure and Organization Resources management and allocation [email protected] Introduction What s the Internet? Why organizations / bodies are needed? Define protocol specifications Agree
What's inside the cloud?!
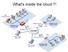 What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
THE MASTER LIST OF DNS TERMINOLOGY. First Edition
 THE MASTER LIST OF DNS TERMINOLOGY First Edition DNS can be hard to understand and if you re unfamiliar with the terminology, learning more about DNS can seem as daunting as learning a new language. To
THE MASTER LIST OF DNS TERMINOLOGY First Edition DNS can be hard to understand and if you re unfamiliar with the terminology, learning more about DNS can seem as daunting as learning a new language. To
DNS Root NameServers
 DNS Root NameServers An Overview Dr. Farid Farahmand Updated: 9/24/12 Who- is- Who! Over half million networks are connected to the Internet 5 billion users by 2015! Network numbers are managed by ICANN
DNS Root NameServers An Overview Dr. Farid Farahmand Updated: 9/24/12 Who- is- Who! Over half million networks are connected to the Internet 5 billion users by 2015! Network numbers are managed by ICANN
DOMAIN AND EMAIL GLOSSARY The phrases and terms you may encounter, when registering a domain name
 DOMAIN AND EMAIL GLOSSARY The phrases and terms you may encounter, when registering a domain name Don t know your Registrar from your Registry? No idea what a Name server actually does? Well, don t worry.
DOMAIN AND EMAIL GLOSSARY The phrases and terms you may encounter, when registering a domain name Don t know your Registrar from your Registry? No idea what a Name server actually does? Well, don t worry.
Introduction to The Internet. ISP/IXP Workshops
 Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Networking Domain Name System
 System i Networking Domain Name System Version 6 Release 1 System i Networking Domain Name System Version 6 Release 1 Note Before using this information and the product it supports, read the information
System i Networking Domain Name System Version 6 Release 1 System i Networking Domain Name System Version 6 Release 1 Note Before using this information and the product it supports, read the information
The Internet Introductory material.
 The Internet Introductory material. An overview lecture that covers Internet related topics, including a definition of the Internet, an overview of its history and growth, and standardization and naming.
The Internet Introductory material. An overview lecture that covers Internet related topics, including a definition of the Internet, an overview of its history and growth, and standardization and naming.
Networking Domain Name System
 System i Networking Domain Name System Version 5 Release 4 System i Networking Domain Name System Version 5 Release 4 Note Before using this information and the product it supports, read the information
System i Networking Domain Name System Version 5 Release 4 System i Networking Domain Name System Version 5 Release 4 Note Before using this information and the product it supports, read the information
Introduction to The Internet
 Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
HTG XROADS NETWORKS. Network Appliance How To Guide: EdgeDNS. How To Guide
 HTG X XROADS NETWORKS Network Appliance How To Guide: EdgeDNS How To Guide V 3. 2 E D G E N E T W O R K A P P L I A N C E How To Guide EdgeDNS XRoads Networks 17165 Von Karman Suite 112 888-9-XROADS V
HTG X XROADS NETWORKS Network Appliance How To Guide: EdgeDNS How To Guide V 3. 2 E D G E N E T W O R K A P P L I A N C E How To Guide EdgeDNS XRoads Networks 17165 Von Karman Suite 112 888-9-XROADS V
The Use of DNS Resource Records
 International Journal of Advances in Electrical and Electronics Engineering 230 Available online at www.ijaeee.com & www.sestindia.org/volume-ijaeee/ ISSN: 2319-1112 Simar Preet Singh Systems Engineer,
International Journal of Advances in Electrical and Electronics Engineering 230 Available online at www.ijaeee.com & www.sestindia.org/volume-ijaeee/ ISSN: 2319-1112 Simar Preet Singh Systems Engineer,
1. LAB SNIFFING LAB ID: 10
 H E R A LAB ID: 10 SNIFFING Sniffing in a switched network ARP Poisoning Analyzing a network traffic Extracting files from a network trace Stealing credentials Mapping/exploring network resources 1. LAB
H E R A LAB ID: 10 SNIFFING Sniffing in a switched network ARP Poisoning Analyzing a network traffic Extracting files from a network trace Stealing credentials Mapping/exploring network resources 1. LAB
Ref: A. Leon Garcia and I. Widjaja, Communication Networks, 2 nd Ed. McGraw Hill, 2006 Latest update of this lecture was on 16 10 2010
 IPv4 Addressing There are several non-profit organizations in the world that have the authority for assigning IP addresses to institutions that need access to the Internet. These organizations are (for
IPv4 Addressing There are several non-profit organizations in the world that have the authority for assigning IP addresses to institutions that need access to the Internet. These organizations are (for
Appendix D: Configuring Firewalls and Network Address Translation
 Appendix D: Configuring Firewalls and Network Address Translation The configuration information in this appendix will help the network administrator plan and configure the network architecture for Everserve.
Appendix D: Configuring Firewalls and Network Address Translation The configuration information in this appendix will help the network administrator plan and configure the network architecture for Everserve.
Securing an Internet Name Server
 Securing an Internet Name Server Cricket Liu [email protected] Securing an Internet Name Server Name servers exposed to the Internet are subject to a wide variety of attacks: Attacks against the name
Securing an Internet Name Server Cricket Liu [email protected] Securing an Internet Name Server Name servers exposed to the Internet are subject to a wide variety of attacks: Attacks against the name
The Domain Name System
 DNS " This is the means by which we can convert names like news.bbc.co.uk into IP addresses like 212.59.226.30 " Purely for the benefit of human users: we can remember numbers (e.g., telephone numbers),
DNS " This is the means by which we can convert names like news.bbc.co.uk into IP addresses like 212.59.226.30 " Purely for the benefit of human users: we can remember numbers (e.g., telephone numbers),
How to Add Domains and DNS Records
 How to Add Domains and DNS Records Configure the Barracuda NextGen X-Series Firewall to be the authoritative DNS server for your domains or subdomains to take advantage of Split DNS or dead link detection.
How to Add Domains and DNS Records Configure the Barracuda NextGen X-Series Firewall to be the authoritative DNS server for your domains or subdomains to take advantage of Split DNS or dead link detection.
The Internet. On October 24, 1995, the FNC unanimously passed a resolution defining the term Internet.
 The Internet Introductory material. An overview lecture that covers Internet related topics, including a definition of the Internet, an overview of its history and growth, and standardization and naming.
The Internet Introductory material. An overview lecture that covers Internet related topics, including a definition of the Internet, an overview of its history and growth, and standardization and naming.
Copyright International Business Machines Corporation 2001. All rights reserved. US Government Users Restricted Rights Use, duplication or disclosure
 iseries DNS iseries DNS Copyright International Business Machines Corporation 2001. All rights reserved. US Government Users Restricted Rights Use, duplication or disclosure restricted by GSA ADP Schedule
iseries DNS iseries DNS Copyright International Business Machines Corporation 2001. All rights reserved. US Government Users Restricted Rights Use, duplication or disclosure restricted by GSA ADP Schedule
Domain Name System 2015-04-28 17:49:44 UTC. 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement
 Domain Name System 2015-04-28 17:49:44 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Domain Name System... 4 Domain Name System... 5 How DNS Works
Domain Name System 2015-04-28 17:49:44 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Domain Name System... 4 Domain Name System... 5 How DNS Works
How To Guide Edge Network Appliance How To Guide:
 How To Guide Edge Network Appliance How To Guide: ActiveDNS v 4.01 Edge Network Appliance How To Guide: ActiveDNS 2007 XRoads Networks 17165 Von Karman, Suite 112 888-9-XROADS v 4.01 updated 09/11/07 Table
How To Guide Edge Network Appliance How To Guide: ActiveDNS v 4.01 Edge Network Appliance How To Guide: ActiveDNS 2007 XRoads Networks 17165 Von Karman, Suite 112 888-9-XROADS v 4.01 updated 09/11/07 Table
Oracle Communications Internet Name and Address Management
 Oracle Communications Internet Name and Address Management IP Name and Address Service Guide Release 6.1.5 E26653-02 December 2012 Oracle Communications Internet Name and Address Management IP Name and
Oracle Communications Internet Name and Address Management IP Name and Address Service Guide Release 6.1.5 E26653-02 December 2012 Oracle Communications Internet Name and Address Management IP Name and
Internet Operations and the RIRs
 Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Networking Domain Name System
 IBM i Networking Domain Name System Version 7.2 IBM i Networking Domain Name System Version 7.2 Note Before using this information and the product it supports, read the information in Notices on page
IBM i Networking Domain Name System Version 7.2 IBM i Networking Domain Name System Version 7.2 Note Before using this information and the product it supports, read the information in Notices on page
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Internet Security [1] VU 184.216. Engin Kirda [email protected]
![Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at](/thumbs/33/15826620.jpg) Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
IP Addressing A Simplified Tutorial
 Application Note IP Addressing A Simplified Tutorial July 2002 COMPAS ID 92962 Avaya Labs 1 All information in this document is subject to change without notice. Although the information is believed to
Application Note IP Addressing A Simplified Tutorial July 2002 COMPAS ID 92962 Avaya Labs 1 All information in this document is subject to change without notice. Although the information is believed to
Terminology. Internet Addressing System
 Terminology A local area network (LAN) is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. The defining characteristics
Terminology A local area network (LAN) is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. The defining characteristics
Domain Name Server. Training Division National Informatics Centre New Delhi
 Domain Name Server Training Division National Informatics Centre New Delhi Domain Name Service (DNS) I. History of DNS II. DNS structure and its components III. Functioning of DNS IV. Possible Configurations
Domain Name Server Training Division National Informatics Centre New Delhi Domain Name Service (DNS) I. History of DNS II. DNS structure and its components III. Functioning of DNS IV. Possible Configurations
Lab - Mapping the Internet
 Objectives Part 1: Test Network Connectivity Using Ping Part 2: Trace a Route to a Remote Server Using Windows Tracert Part 3: Trace a Route to a Remote Server Using Web-Based and Software Tools Part 4:
Objectives Part 1: Test Network Connectivity Using Ping Part 2: Trace a Route to a Remote Server Using Windows Tracert Part 3: Trace a Route to a Remote Server Using Web-Based and Software Tools Part 4:
Section 1 Overview... 4. Section 2 Home... 5
 ecogent User Guide 2012 Cogent Communications, Inc. All rights reserved. Every effort has been made to ensure that the information in this User Guide is accurate. Information in this document is subject
ecogent User Guide 2012 Cogent Communications, Inc. All rights reserved. Every effort has been made to ensure that the information in this User Guide is accurate. Information in this document is subject
THE DOMAIN NAME SYSTEM DNS
 Announcements THE DOMAIN NAME SYSTEM DNS Internet Protocols CSC / ECE 573 Fall, 2005 N. C. State University copyright 2005 Douglas S. Reeves 2 Today s Lecture I. Names vs. Addresses II. III. IV. The Namespace
Announcements THE DOMAIN NAME SYSTEM DNS Internet Protocols CSC / ECE 573 Fall, 2005 N. C. State University copyright 2005 Douglas S. Reeves 2 Today s Lecture I. Names vs. Addresses II. III. IV. The Namespace
Parallels Plesk Panel 11 for your Linux server
 Getting Started Guide Parallels Plesk Panel 11 for your Linux server Getting Started Guide Page 1 Getting Started Guide: Parallels Plesk Panel 11, Linux Server Version 1.1 (11.1.2012) Copyright 2012. All
Getting Started Guide Parallels Plesk Panel 11 for your Linux server Getting Started Guide Page 1 Getting Started Guide: Parallels Plesk Panel 11, Linux Server Version 1.1 (11.1.2012) Copyright 2012. All
Use Domain Name System and IP Version 6
 Use Domain Name System and IP Version 6 What You Will Learn The introduction of IP Version 6 (IPv6) into an enterprise environment requires some changes both in the provisioned Domain Name System (DNS)
Use Domain Name System and IP Version 6 What You Will Learn The introduction of IP Version 6 (IPv6) into an enterprise environment requires some changes both in the provisioned Domain Name System (DNS)
ECE 4321 Computer Networks. Network Programming
 ECE 4321 Computer Networks Network Programming Name Space System.Net Domain Name System (DNS) To resolve computer naming Host database is split up and distributed among multiple systems on the Internet
ECE 4321 Computer Networks Network Programming Name Space System.Net Domain Name System (DNS) To resolve computer naming Host database is split up and distributed among multiple systems on the Internet
Enterprise Architecture Office Resource Document Design Note - Domain Name System (DNS)
 Date: 8/27/2012 Enterprise Architecture Office Resource Document Design Note - Domain Name System (DNS) Table of Contents 1 Overview...2 1.1 Other Resources...2 1.1.1 State of Minnesota Standards and Guidelines...2
Date: 8/27/2012 Enterprise Architecture Office Resource Document Design Note - Domain Name System (DNS) Table of Contents 1 Overview...2 1.1 Other Resources...2 1.1.1 State of Minnesota Standards and Guidelines...2
DNS Appliance Architecture: Domain Name System Best Practices
 WHITEPAPER DNS Appliance Architecture: Domain Name System Best Practices A Practical Look at Deploying DNS Appliances in the Network to Increase Simplicity, Security & Scalability Cricket Liu, Chief Infrastructure
WHITEPAPER DNS Appliance Architecture: Domain Name System Best Practices A Practical Look at Deploying DNS Appliances in the Network to Increase Simplicity, Security & Scalability Cricket Liu, Chief Infrastructure
Decoding DNS data. Using DNS traffic analysis to identify cyber security threats, server misconfigurations and software bugs
 Decoding DNS data Using DNS traffic analysis to identify cyber security threats, server misconfigurations and software bugs The Domain Name System (DNS) is a core component of the Internet infrastructure,
Decoding DNS data Using DNS traffic analysis to identify cyber security threats, server misconfigurations and software bugs The Domain Name System (DNS) is a core component of the Internet infrastructure,
Lecture 2 CS 3311. An example of a middleware service: DNS Domain Name System
 Lecture 2 CS 3311 An example of a middleware service: DNS Domain Name System The problem Networked computers have names and IP addresses. Applications use names; IP uses for routing purposes IP addresses.
Lecture 2 CS 3311 An example of a middleware service: DNS Domain Name System The problem Networked computers have names and IP addresses. Applications use names; IP uses for routing purposes IP addresses.
FAQ (Frequently Asked Questions)
 FAQ (Frequently Asked Questions) Specific Questions about Afilias Managed DNS What is the Afilias DNS network? How long has Afilias been working within the DNS market? What are the names of the Afilias
FAQ (Frequently Asked Questions) Specific Questions about Afilias Managed DNS What is the Afilias DNS network? How long has Afilias been working within the DNS market? What are the names of the Afilias
what s in a name? taking a deeper look at the domain name system mike boylan penn state mac admins conference
 what s in a name? taking a deeper look at the domain name system mike boylan penn state mac admins conference whoami work for robert morris university, pittsburgh, pa primarily mac and voip admin @mboylan
what s in a name? taking a deeper look at the domain name system mike boylan penn state mac admins conference whoami work for robert morris university, pittsburgh, pa primarily mac and voip admin @mboylan
The Environment Surrounding DNS. 3.1 The Latest DNS Trends. 3. Technology Trends
 3. The Environment Surrounding DNS DNS is used in many applications, serving as an important Internet service. Here we discuss name collision issues that have arisen with recent TLD additions, and examine
3. The Environment Surrounding DNS DNS is used in many applications, serving as an important Internet service. Here we discuss name collision issues that have arisen with recent TLD additions, and examine
256 4 = 4,294,967,296 ten billion. 256 16 = 18,446,744,073,709,551,616 ten quintillion. IP Addressing. IPv4 Address Classes
 IP Addressing With the exception of multicast addresses, Internet addresses consist of a network portion and a host portion. The network portion identifies a logical network to which the address refers,
IP Addressing With the exception of multicast addresses, Internet addresses consist of a network portion and a host portion. The network portion identifies a logical network to which the address refers,
Basic DNS Course. Module 1. DNS Theory. Ron Aitchison ZYTRAX, Inc. Page 1 of 24
 Basic DNS Course Module 1 Ron Aitchison ZYTRAX, Inc. Page 1 of 24 The following are the slides used in this Module of the course. Some but not all slides have additional notes that you may find useful.
Basic DNS Course Module 1 Ron Aitchison ZYTRAX, Inc. Page 1 of 24 The following are the slides used in this Module of the course. Some but not all slides have additional notes that you may find useful.
v7.8.2 Release Notes for Websense Content Gateway
 v7.8.2 Release Notes for Websense Content Gateway Topic 60086 Web Security Gateway and Gateway Anywhere 12-Mar-2014 These Release Notes are an introduction to Websense Content Gateway version 7.8.2. New
v7.8.2 Release Notes for Websense Content Gateway Topic 60086 Web Security Gateway and Gateway Anywhere 12-Mar-2014 These Release Notes are an introduction to Websense Content Gateway version 7.8.2. New
DNS and email issues in connecting UNINET-ZA to the Internet
 DNS and email issues in connecting UNINET-ZA to the Internet Alan Barrett November 2011 Abstract This article describes some of the activities and configuration relating to the Domain Name System (DNS)
DNS and email issues in connecting UNINET-ZA to the Internet Alan Barrett November 2011 Abstract This article describes some of the activities and configuration relating to the Domain Name System (DNS)
Computer Networks: DNS a2acks CS 1951e - Computer Systems Security: Principles and Prac>ce. Domain Name System
 Computer Networks: DNS a2acks CS 1951e - Computer Systems Security: Principles and Prac>ce 18/02/15 Networks: DNS attacks 1 Domain Name System The domain name system (DNS) is an applica>on- layer protocol
Computer Networks: DNS a2acks CS 1951e - Computer Systems Security: Principles and Prac>ce 18/02/15 Networks: DNS attacks 1 Domain Name System The domain name system (DNS) is an applica>on- layer protocol
How to Configure the Windows DNS Server
 Windows 2003 How to Configure the Windows DNS Server How to Configure the Windows DNS Server Objective This document demonstrates how to configure domains and record on the Windows 2003 DNS Server. Windows
Windows 2003 How to Configure the Windows DNS Server How to Configure the Windows DNS Server Objective This document demonstrates how to configure domains and record on the Windows 2003 DNS Server. Windows
EECS 489 Winter 2010 Midterm Exam
 EECS 489 Winter 2010 Midterm Exam Name: This is an open-book, open-resources exam. Explain or show your work for each question. Your grade will be severely deducted if you don t show your work, even if
EECS 489 Winter 2010 Midterm Exam Name: This is an open-book, open-resources exam. Explain or show your work for each question. Your grade will be severely deducted if you don t show your work, even if
How To Load Balance On A Bgg On A Network With A Network (Networking) On A Pc Or Ipa On A Computer Or Ipad On A 2G Network On A Microsoft Ipa (Netnet) On An Ip
 Globally Distributed Content (Using BGP to Take Over the World) Horms (Simon Horman) [email protected] November 2001 http://supersparrow.org/ 1 Introduction Electronic content is becoming increasingly
Globally Distributed Content (Using BGP to Take Over the World) Horms (Simon Horman) [email protected] November 2001 http://supersparrow.org/ 1 Introduction Electronic content is becoming increasingly
ISP Systems Design. ISP Workshops. Last updated 24 April 2013
 ISP Systems Design ISP Workshops Last updated 24 April 2013 1 Agenda p DNS Server placement p Mail Server placement p News Server placement p Services network design p Services Network Security 2 ISP Services
ISP Systems Design ISP Workshops Last updated 24 April 2013 1 Agenda p DNS Server placement p Mail Server placement p News Server placement p Services network design p Services Network Security 2 ISP Services
DNS. The Root Name Servers. DNS Hierarchy. Computer System Security and Management SMD139. Root name server. .se name server. .
 Computer System Security and Management SMD139 Lecture 5: Domain Name System Peter A. Jonsson DNS Translation of Hostnames to IP addresses Hierarchical distributed database DNS Hierarchy The Root Name
Computer System Security and Management SMD139 Lecture 5: Domain Name System Peter A. Jonsson DNS Translation of Hostnames to IP addresses Hierarchical distributed database DNS Hierarchy The Root Name
Project 4: IP over DNS Due: 11:59 PM, Dec 14, 2015
 CS168 Computer Networks Jannotti Project 4: IP over DNS Due: 11:59 PM, Dec 14, 2015 Contents 1 Introduction 1 2 Components 1 2.1 Creating the tunnel..................................... 2 2.2 Using the
CS168 Computer Networks Jannotti Project 4: IP over DNS Due: 11:59 PM, Dec 14, 2015 Contents 1 Introduction 1 2 Components 1 2.1 Creating the tunnel..................................... 2 2.2 Using the
F5 and Infoblox DNS Integrated Architecture Offering a Complete Scalable, Secure DNS Solution
 F5 and Infoblox DNS Integrated Architecture Offering a Complete Scalable, Secure DNS Solution As market leaders in the application delivery market and DNS, DHCP, and IP Address Management (DDI) market
F5 and Infoblox DNS Integrated Architecture Offering a Complete Scalable, Secure DNS Solution As market leaders in the application delivery market and DNS, DHCP, and IP Address Management (DDI) market
Application Protocols in the TCP/IP Reference Model
 Application Protocols in the TCP/IP Reference Model File Transfer E-Mail Network Management WWW Virtual Terminal Name Service File Transfer HTTP FTP Telnet SMTP DNS SNMP TFTP Internet protocols TCP UDP
Application Protocols in the TCP/IP Reference Model File Transfer E-Mail Network Management WWW Virtual Terminal Name Service File Transfer HTTP FTP Telnet SMTP DNS SNMP TFTP Internet protocols TCP UDP
Application Protocols in the TCP/IP Reference Model. Application Protocols in the TCP/IP Reference Model. DNS - Concept. DNS - Domain Name System
 Application Protocols in the TCP/IP Reference Model Application Protocols in the TCP/IP Reference Model File Transfer E-Mail Network Management Protocols of the application layer are common communication
Application Protocols in the TCP/IP Reference Model Application Protocols in the TCP/IP Reference Model File Transfer E-Mail Network Management Protocols of the application layer are common communication
3. The Domain Name Service
 3. The Domain Name Service n Overview and high level design n Typical operation and the role of caching n Contents of DNS Resource Records n Basic message formats n Configuring/updating Resource Records
3. The Domain Name Service n Overview and high level design n Typical operation and the role of caching n Contents of DNS Resource Records n Basic message formats n Configuring/updating Resource Records
1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet
 Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
IPv6 support in the DNS
 IPv6 support in the DNS How important is the DNS? Getting the IP address of the remote endpoint is necessary for every communication between TCP/IP applications Humans are unable to memorize millions of
IPv6 support in the DNS How important is the DNS? Getting the IP address of the remote endpoint is necessary for every communication between TCP/IP applications Humans are unable to memorize millions of
Technical Note. ISP Protection against BlackListing. FORTIMAIL Deployment for Outbound Spam Filtering. Rev 2.2
 Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
IPv6 Support in the DNS. Workshop Name Workshop Location, Date
 IPv6 Support in the DNS Workshop Name Workshop Location, Date Agenda How important is the DNS? DNS Resource Lookup DNS Extensions for IPv6 Lookups in an IPv6-aware DNS Tree About Required IPv6 Glue in
IPv6 Support in the DNS Workshop Name Workshop Location, Date Agenda How important is the DNS? DNS Resource Lookup DNS Extensions for IPv6 Lookups in an IPv6-aware DNS Tree About Required IPv6 Glue in
Network Working Group. Category: Best Current Practice S. Bradner Harvard University M. Patton Consultant July 1997
 Network Working Group Request for Comments: 2182 BCP: 16 Category: Best Current Practice R. Elz University of Melbourne R. Bush RGnet, Inc. S. Bradner Harvard University M. Patton Consultant July 1997
Network Working Group Request for Comments: 2182 BCP: 16 Category: Best Current Practice R. Elz University of Melbourne R. Bush RGnet, Inc. S. Bradner Harvard University M. Patton Consultant July 1997
Public-Root Name Server Operational Requirements
 Public-Root Name Server Operational Requirements Published January the 17 th, 2005 Status of this Document This document provides information to the Public-Root and Internet technical community. This document
Public-Root Name Server Operational Requirements Published January the 17 th, 2005 Status of this Document This document provides information to the Public-Root and Internet technical community. This document
Lesson Plans Managing a Windows 2003 Network Infrastructure
 Lesson Plans Managing a Windows 2003 Network Infrastructure (Exam 70-291) Table of Contents Course Overview... 2 Section 0.1: Introduction... 3 Section 1.1: Client Configuration... 4 Section 1.2: IP Addressing...
Lesson Plans Managing a Windows 2003 Network Infrastructure (Exam 70-291) Table of Contents Course Overview... 2 Section 0.1: Introduction... 3 Section 1.1: Client Configuration... 4 Section 1.2: IP Addressing...
The Domain Name System: An Integral Part of the Internet. By Keiko Ishioka
 The Domain Name System: An Integral Part of the Internet By Keiko Ishioka The Domain Name System (otherwise known as the Domain Name Server system) (DNS) is a distributed database that is accessed by anyone
The Domain Name System: An Integral Part of the Internet By Keiko Ishioka The Domain Name System (otherwise known as the Domain Name Server system) (DNS) is a distributed database that is accessed by anyone
DNS Domain Name System
 Domain Name System DNS Domain Name System The domain name system is usually used to translate a host name into an IP address Domain names comprise a hierarchy so that names are unique, yet easy to remember.
Domain Name System DNS Domain Name System The domain name system is usually used to translate a host name into an IP address Domain names comprise a hierarchy so that names are unique, yet easy to remember.
Internet Bodies. [email protected]
 Internet Bodies [email protected] Agenda Names, Acronyms in the Internet IETF organisation IESG, IAB, ISOC ICANN & IANA Standardisation process Standardisation compliance Internet Registries Requesting
Internet Bodies [email protected] Agenda Names, Acronyms in the Internet IETF organisation IESG, IAB, ISOC ICANN & IANA Standardisation process Standardisation compliance Internet Registries Requesting
Domain Name System (DNS) RFC 1034 RFC 1035 http://www.ietf.org
 Domain Name System (DNS) RFC 1034 RFC 1035 http://www.ietf.org TCP/IP Protocol Suite Application Layer DHCP DNS SNMP HTTP SMTP POP Transport Layer UDP TCP ICMP IGMP Network Layer IP Link Layer ARP ARP
Domain Name System (DNS) RFC 1034 RFC 1035 http://www.ietf.org TCP/IP Protocol Suite Application Layer DHCP DNS SNMP HTTP SMTP POP Transport Layer UDP TCP ICMP IGMP Network Layer IP Link Layer ARP ARP
OpenSRS Email Service DNS Configuration Guide
 OpenSRS Email Service DNS Configuration Guide September 18, 2008 Table of Contents DNS Configuration...3 Types of DNS records...3 Email Exchange (MX) records...3 Canonical Name (CNAME) records...4 Example
OpenSRS Email Service DNS Configuration Guide September 18, 2008 Table of Contents DNS Configuration...3 Types of DNS records...3 Email Exchange (MX) records...3 Canonical Name (CNAME) records...4 Example
Guidance for Preparing Domain Name Orders, Seizures & Takedowns
 Guidance for Preparing Domain Name Orders, Seizures & Takedowns Abstract This thought paper offers guidance for anyone who prepares an order that seeks to seize or take down domain names. Its purpose is
Guidance for Preparing Domain Name Orders, Seizures & Takedowns Abstract This thought paper offers guidance for anyone who prepares an order that seeks to seize or take down domain names. Its purpose is
Introduction to Network Operating Systems
 As mentioned earlier, different layers of the protocol stack use different kinds of addresses. We can now see that the Transport Layer (TCP) uses port addresses to route data to the correct process, the
As mentioned earlier, different layers of the protocol stack use different kinds of addresses. We can now see that the Transport Layer (TCP) uses port addresses to route data to the correct process, the
DNS. Computer Networks. Seminar 12
 DNS Computer Networks Seminar 12 DNS Introduction (Domain Name System) Naming system used in Internet Translate domain names to IP addresses and back Communication works on UDP (port 53), large requests/responses
DNS Computer Networks Seminar 12 DNS Introduction (Domain Name System) Naming system used in Internet Translate domain names to IP addresses and back Communication works on UDP (port 53), large requests/responses
shortcut Tap into learning NOW! Visit www.informit.com/shortcuts for a complete list of Short Cuts. Your Short Cut to Knowledge
 shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
DNS & IPv6. Agenda 4/14/2009. MENOG4, 8-9 April 2009. Raed Al-Fayez SaudiNIC CITC [email protected], www.nic.net.sa. DNS & IPv6.
 DNS & IPv6 MENOG4, 8-9 April 2009 Raed Al-Fayez SaudiNIC CITC [email protected], www.nic.net.sa Agenda DNS & IPv6 Introduction What s next? SaudiNIC & IPv6 About SaudiNIC How a cctld Registry supports
DNS & IPv6 MENOG4, 8-9 April 2009 Raed Al-Fayez SaudiNIC CITC [email protected], www.nic.net.sa Agenda DNS & IPv6 Introduction What s next? SaudiNIC & IPv6 About SaudiNIC How a cctld Registry supports
Module 2. Configuring and Troubleshooting DNS. Contents:
 Configuring and Troubleshooting DNS 2-1 Module 2 Configuring and Troubleshooting DNS Contents: Lesson 1: Installing the DNS Server Role 2-3 Lesson 2: Configuring the DNS Server Role 2-9 Lesson 3: Configuring
Configuring and Troubleshooting DNS 2-1 Module 2 Configuring and Troubleshooting DNS Contents: Lesson 1: Installing the DNS Server Role 2-3 Lesson 2: Configuring the DNS Server Role 2-9 Lesson 3: Configuring
OVERVIEW OF THE DNS AND GLOSSARY OF TERMS
 PROTECT YOUR BUSINESS D-Zone Anycast DNS Service OVERVIEW OF THE DNS AND GLOSSARY OF TERMS 1 PROTECT YOUR BUSINESS OVERVIEW OF THE DNS AND GLOSSARY OF TERMS The DNS is a technology that most IT managers
PROTECT YOUR BUSINESS D-Zone Anycast DNS Service OVERVIEW OF THE DNS AND GLOSSARY OF TERMS 1 PROTECT YOUR BUSINESS OVERVIEW OF THE DNS AND GLOSSARY OF TERMS The DNS is a technology that most IT managers
Subnetting and Network Management Omer F. Rana. Networks and Data Communications 1
 Subnetting and Network Management Omer F. Rana Networks and Data Communications 1 Subnetting Subnetting is an important concept in establishing TCP/IP based networks important in integrating small Local
Subnetting and Network Management Omer F. Rana Networks and Data Communications 1 Subnetting Subnetting is an important concept in establishing TCP/IP based networks important in integrating small Local
Local DNS Attack Lab. 1 Lab Overview. 2 Lab Environment. SEED Labs Local DNS Attack Lab 1
 SEED Labs Local DNS Attack Lab 1 Local DNS Attack Lab Copyright c 2006 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation s Course,
SEED Labs Local DNS Attack Lab 1 Local DNS Attack Lab Copyright c 2006 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation s Course,
Computer Networks: Domain Name System
 Computer Networks: Domain Name System Domain Name System The domain name system (DNS) is an application-layer protocol for mapping domain names to IP addresses DNS www.example.com 208.77.188.166 http://www.example.com
Computer Networks: Domain Name System Domain Name System The domain name system (DNS) is an application-layer protocol for mapping domain names to IP addresses DNS www.example.com 208.77.188.166 http://www.example.com
Introduction to the Domain Name System
 CHAPTER 14 The Domain Name System (DNS) handles the growing number of Internet users. DNS translates names, such as www.cisco.com, into IP addresses, such as 192.168.40.0 (or the more extended IPv6 addresses),
CHAPTER 14 The Domain Name System (DNS) handles the growing number of Internet users. DNS translates names, such as www.cisco.com, into IP addresses, such as 192.168.40.0 (or the more extended IPv6 addresses),
Connecting with Computer Science, 2e. Chapter 5 The Internet
 Connecting with Computer Science, 2e Chapter 5 The Internet Objectives In this chapter you will: Learn what the Internet really is Become familiar with the architecture of the Internet Become familiar
Connecting with Computer Science, 2e Chapter 5 The Internet Objectives In this chapter you will: Learn what the Internet really is Become familiar with the architecture of the Internet Become familiar
DEERFIELD.COM. DNS2Go Update API. DNS2Go Update API
 DEERFIELD.COM DNS2Go Update API DNS2Go Update API DEERFIELD.COM PRODUCT DOCUMENTATION DNS2Go Update API Deerfield.com 4241 Old U.S. 27 South Gaylord, MI 49686 Phone 989.732.8856 Email [email protected]
DEERFIELD.COM DNS2Go Update API DNS2Go Update API DEERFIELD.COM PRODUCT DOCUMENTATION DNS2Go Update API Deerfield.com 4241 Old U.S. 27 South Gaylord, MI 49686 Phone 989.732.8856 Email [email protected]
Lightweight DNS for Multipurpose and Multifunctional Devices
 IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.12, December 2013 71 Lightweight DNS for Multipurpose and Multifunctional Devices Yogesh A. Wagh 1, Prashant A. Dhangar
IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.12, December 2013 71 Lightweight DNS for Multipurpose and Multifunctional Devices Yogesh A. Wagh 1, Prashant A. Dhangar
BGP. 1. Internet Routing
 BGP 1. Internet Routing (C) Herbert Haas 2005/03/11 1 Internet Routing Interior Gateway Protocols (IGPs) not suitable for Inter-ISP routing Technical metrics only No policy features Inter-ISP routing is
BGP 1. Internet Routing (C) Herbert Haas 2005/03/11 1 Internet Routing Interior Gateway Protocols (IGPs) not suitable for Inter-ISP routing Technical metrics only No policy features Inter-ISP routing is
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
