Emulate virtual machines To avoid malware infections
|
|
|
- Frederick Gilbert
- 10 years ago
- Views:
Transcription
1 Emulate virtual machines To avoid malware infections Jordi Vázquez Aira Institut Obert of Catalonia (Barcelona, Spain) PAGE 1
2 Introduction The premise & Purposes The premise: If malware tries to avoid Virtual machines Why not try to emulate these environments? Purposes! Study the characteristics of VirtualBox! Specific drivers! Registry keys! VirtualBox Guest Additions Files! Know how the malware detects a virtual machine environment! Try to replicate these configurations on a physical computer PAGE 2
3 How does malware detect Virtual Machine? - Differences between Virtual machines and physical computers - Examples PAGE 3
4 Differences between VMs and physical computers Specific files with VirtualBox Guest Additions System32 VBoxDisp.dll VBoxHook.dll VBoxMRXNP.dll VBoxOGLarrayspu.dll VBoxOGLcrutil.dll VBoxOGLerrorspu.dll VBoxOGLfeedbackspu.dll VBoxOGLpackspu.dll VBoxoglpassthroughspu.dll VBoxTray.exe VBoxService.exe VBoxControl.exe Guest Additions folder VBoxDisp.dll VBoxDrvInst.exe VBoxVideo.inf VBoxVideo.sys VBoxControl.exe VBoxGuest.sys VBoxGuest.inf VBoxMouse.sys VBoxMouse.inf VBoxTray.exe VBoxWHQLFake.exe DIFxAPI.dll System32\Drivers VBoxMouse.sys VBoxGuest.sys VBoxSF.sys VBoxVideo.sys PAGE 4
5 Differences between VMs and physical computers Specific files with VirtualBox Guest Additions DRVSTORE\VBoxGuest_ED40339D 75DAC80DECCD6CCCDB8E202724F5321D VBoxControl.exe VBoxGuest.cat VBoxGuest.inf VBoxGuest.sys VBoxTray.exe DRVSTORE\VBOXVideo_5C9060E4 72F2B1E3E9D5353B27AF6B8DABF99D47 VBoxDisp.dll VBoxVideo.inf VBoxVideo.sys VBoxVideo.cat PAGE 5
6 Differences between VMs and physical computers Specific registry keys Folder Key Type Value HKLM\Software\Oracle\VirtualBox Guest Additions HKLM\Hardware\DEVICEMAP\Scsi\Scsi Port 0\ScSi Bus 0\Target Id 0\Logical Unit Id 0 HKLM\Hardware\DEVICEMAP\Scsi\Scsi Port 0\ScSi Bus 0\Target Id 1\Logical Unit Id 0 InstallDir REG_SZ Guest Additions folder Revision REG_SZ Revision number Version REG_SZ Version number VersionExt REG_SZ Version number Identifier REG_SZ VBOX HARDDISK Identifier REG_SZ VBOX CD-ROM HKLM\Hardware\DESCRIPTION\System SystemBiosVersion REG_MULTI_SZ VBOX -1 HKLM\Hardware\Acpi\DSDT\VBOX \VBOXBIOS\ VideoBiosVersion REG_MULTI_SZ Oracle VM VirtualBox Version (version number) REG_BINARY DSDT...VBOX VBOXBIOS...INTL PAGE 6
7 Differences between VMs and physical computers Specific registry keys Folder Key Type Value HKLM\System\CurrentControlSet\Services \Disk\Enum HKLM\System\CurrentControlSet\Services \VBoxGuest HKLM\System\CurrentControlSet\Services \VBoxGuest\Enum HKLM\System\CurrentControlSet\Services \VBoxMouse 0 REG_SZ IDE \DiskVBOX_HARDDISK 1.0 \ d DisplayName REG_SZ VirtualBox Guest Driver ImagePath REG_EXPAND_SZ system32\drivers \VBoxGuest.sys 0 REG_SZ PCI \VEN_80EE&DEV_CAFE&SUBS YS_ &REV_00\3&267a 616a&0&20 DisplayName REG_SZ VirtualBox Guest Mouse Service ImagePath REG_EXPAND_SZ system32\drivers \VBoxMouse.sys *These HKLM\System\CurrentControlSet\Services keys are in ControlSet001, ControlSet002 and CurrentControlSet 0 folders REG_SZ ACPI \VBoxMouse\Enum \PNP0F03\4&1d401fb5&0 PAGE 7
8 Differences between VMs and physical computers Specific registry keys Folder Key Type Value HKLM\System\CurrentControlSet\Enum\Ide \DiskVBOX_HARDDISK\ HKLM\System\CurrentControlSet\Enum\Ide \DiskVBOX_HARDDISK\ HKLM\System\CurrentControlSet\Services \VBoxService FriendlyName REG_SZ VBOX HARDDISK FriendlyName REG_SZ VBOX CD-ROM DisplayName REG_SZ VirtualBox Guest Aditions Service ImagePath REG_EXPAND_SZ system32\vboxservice.exe Description REG_SZ Manages VM runtime information and utilities for guest operating systems. ObjectName REG_SZ LocalSystem HKLM\System\CurrentControlSet\Services \VBoxService\Enum HKLM\System\CurrentControlSet\Services \VBoxSF 0 REG_SZ Root \LEGACY_VBOXSERVICE \0000 DisplayName REG_SZ VirtualBox Shared Folders *These keys are in ControlSet001, ControlSet002 and CurrentControlSet folders PAGE 8 ImagePath REG_EXPAND_SZ system32\drivers \VBoxSF.sys
9 Differences between VMs and physical computers Specific registry keys Folder Key Type Value HKLM\System\CurrentControlSet \Services\VBoxSF\Enum HKLM\System\CurrentControlSet \Services\VBoxSF \NetworkProvider HKLM\System\CurrentControlSet \Services\VBoxVideo HKLM\System\CurrentControlSet \Services\VBoxVideo\Device0 HKLM\System\CurrentControlSet \Services\VBoxVideo\Enum 0 REG_SZ Root\LEGACY_VBOXSF \0000 DeviceName REG_SZ \Device\VboxMinRdr Name REG_SZ VirtualBox Shared Folder ProviderPath REG_SZ %Systemroot% \System32\VBoxMRXNP.dll ImagePath REG_EXPAND_SZ system32\drivers \VBoxVideo.sys InstalledDisplayDrivers REG_MULTI_SZ VBoxDisp 0 REG_SZ PCI \VEN_80EE&DEV_BEEF&SUBS YS_ &REV_00\3&267a 616a&0&10 HKLM\System\CurrentControlSet Service REG_SZ Vbox Video *These \Services\VBoxVideo\Video keys are in ControlSet001, ControlSet002 and CurrentControlSet folders PAGE 9
10 Examples Trojan-spy.win32.Carberp Source: github.com/hzeroo/carberp/blob/master/source - absource/pro/all%20source/blackjoewhitejoe/source/vmdetect.cpp PAGE 10
11 Examples Usual methods to detect VMs Source: PAGE 11
12 Virtual Machine emulation Code structure Sample code PAGE 12
13 Virtual Machine emulation Code structure Import python libraries Create and modify registry keys Set up environment variables Create files Download libraries Register libraries PAGE 13
14 Virtual Machine emulation Sample code Full code available in: PAGE 14
15 Experimental results Themida Pafish Malware PAGE 15
16 Experimental results Themida PAGE 16
17 Experimental results Pafish Before After PAGE 17
18 Experimental results Net-Worm.Win32.Kolab.vw à Before Script Anti-debugging: The System registry key value:[hklm\system\controlset001\services\disk\enum] "0" Contains the strings: Vmware, Vbox, Virtual or QEMU It copied to the system folder Tries to detect if it s in a VM VM not detected VM detected The Original file is not deleted The original file self-destructs PAGE 18
19 Experimental results Net-Worm.Win32.Kolab.vw à After Script Anti-debugging: The System registry key value:[hklm\system\controlset001\services\disk\enum] "0" Contains the strings: Vmware, Vbox, Virtual or QEMU It copied to the system folder Tries to detect if it s in a VM VM not detected VM detected The Original file is not deleted The original file self-destructs PAGE 19
20 Conclusions Main findings Future lines of research PAGE 20
21 Conclusions Main findings and future lines of research Main findings! We can successfully simulate a virtual machine with a simple python script.! Most malware checks are in the Windows registry or files.! This technique should never be used individually. Future lines of research! Continue investigating virtual machines.! Try the script with more malware samples.! Investigate possible side-effects in a real environment. PAGE 21
22 Thank You Jordi Vázquez Aira Institut Obert of Catalonia (Barcelona, Spain) PAGE 22
A COMPARISON BETWEEN "ORACLE VM VIRTUALBOX" AND "VMWARE PLAYER" FROM A "LINUX" PERSPECTIVE
 A COMPARISON BETWEEN "ORACLE VM VIRTUALBOX" AND "VMWARE PLAYER" FROM A "LINUX" PERSPECTIVE SUMMARY: BASIC COMPARISON VIRTUAL HARD DRIVE ADAPTER DIFFERENCES VIRTUAL NETWORKING DIFFERENCES BASIC COMPARISON
A COMPARISON BETWEEN "ORACLE VM VIRTUALBOX" AND "VMWARE PLAYER" FROM A "LINUX" PERSPECTIVE SUMMARY: BASIC COMPARISON VIRTUAL HARD DRIVE ADAPTER DIFFERENCES VIRTUAL NETWORKING DIFFERENCES BASIC COMPARISON
Block Level Backups with EMC NetWorker
 Block Level Backups with EMC NetWorker David Stes email: [email protected] June 30, 2010 Abstract We discuss here image backup of Windows, Linux and other operating systems, without using a EMC NetWorker
Block Level Backups with EMC NetWorker David Stes email: [email protected] June 30, 2010 Abstract We discuss here image backup of Windows, Linux and other operating systems, without using a EMC NetWorker
Hypervisor Software and Virtual Machines. Professor Howard Burpee SMCC Computer Technology Dept.
 Hypervisor Software and Virtual Machines Learning Objectives Understand the common features of today s desktop virtualization products Select and implement a desktop virtualization option on a Linux, Mac,
Hypervisor Software and Virtual Machines Learning Objectives Understand the common features of today s desktop virtualization products Select and implement a desktop virtualization option on a Linux, Mac,
Creating a Linux Virtual Machine using Virtual Box
 A. Install Virtual Box: Creating a Linux Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer complete.
A. Install Virtual Box: Creating a Linux Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer complete.
Intelligent Video Analytics. Server Installation Guide. - Windows - Linux
 Intelligent Video Analytics Server Installation Guide - Windows - Linux 1) General Information... 2 2) Viasys on Windows PCs... 3 3) Viasys on Linux PCs... 7 4) Viasys Server Support Package... 10 Offices:
Intelligent Video Analytics Server Installation Guide - Windows - Linux 1) General Information... 2 2) Viasys on Windows PCs... 3 3) Viasys on Linux PCs... 7 4) Viasys Server Support Package... 10 Offices:
Creating a Windows XP Virtual Machine using Virtual Box
 A. Install Virtual Box: Creating a Windows XP Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer
A. Install Virtual Box: Creating a Windows XP Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer
Enterprise Cloud VM Image Import User Guide. Version 1.0
 Enterprise Cloud VM Image Import User Guide Version 1.0 Version History Issue Date Comments 1.0 2013/03/20 Initial version i Introduction 1) Purpose of this document: The purpose of this document is to
Enterprise Cloud VM Image Import User Guide Version 1.0 Version History Issue Date Comments 1.0 2013/03/20 Initial version i Introduction 1) Purpose of this document: The purpose of this document is to
In addition to their professional experience, students who attend this training should have technical knowledge in the following areas.
 6422A - Implementing and Managing Windows Server 2008 Hyper-V Course Number: 6422A Course Length: 3 Days Course Overview This three-day instructor-led course teaches students how to implement and manage
6422A - Implementing and Managing Windows Server 2008 Hyper-V Course Number: 6422A Course Length: 3 Days Course Overview This three-day instructor-led course teaches students how to implement and manage
Virtual Machines. Virtual Machines
 Virtual Machines Virtual Machines What is a virtual machine? Examples? Benefits? 1 Virtualization Creation of an isomorphism that maps a virtual guest system to a real host: Maps guest state S to host
Virtual Machines Virtual Machines What is a virtual machine? Examples? Benefits? 1 Virtualization Creation of an isomorphism that maps a virtual guest system to a real host: Maps guest state S to host
Using Keil software with Linux via VirtualBox
 Using Keil software with Linux via VirtualBox Introduction The Keil UVision software used to develop programs for ARM based microprocessor systems is designed to run on Microsoft Windows operating systems.
Using Keil software with Linux via VirtualBox Introduction The Keil UVision software used to develop programs for ARM based microprocessor systems is designed to run on Microsoft Windows operating systems.
Installing Windows On A Macintosh Or Linux Using A Virtual Machine
 Installing Windows On A Macintosh Or Linux Using A Virtual Machine At Shaw Programs, the software we develop is made using Microsoft Access. As with all Microsoft Software it requires Windows in order
Installing Windows On A Macintosh Or Linux Using A Virtual Machine At Shaw Programs, the software we develop is made using Microsoft Access. As with all Microsoft Software it requires Windows in order
Installing Sun's VirtualBox on Windows XP and setting up an Ubuntu VM
 Installing Sun's VirtualBox on Windows XP and setting up an Ubuntu VM laptop will need to have 10GB of free space to install download the latest VirtualBox software from www.sun.com make sure you pick
Installing Sun's VirtualBox on Windows XP and setting up an Ubuntu VM laptop will need to have 10GB of free space to install download the latest VirtualBox software from www.sun.com make sure you pick
VIRTUAL NETWORKING WITH "WINDOWS VIRTUAL PC"
 VIRTUAL NETWORKING WITH "WINDOWS VIRTUAL PC" Summary: "Windows Virtual PC" provides four virtual networking configurations for the virtual machines of a "Windows 7" host computer: 1. a "Other" gateway/router
VIRTUAL NETWORKING WITH "WINDOWS VIRTUAL PC" Summary: "Windows Virtual PC" provides four virtual networking configurations for the virtual machines of a "Windows 7" host computer: 1. a "Other" gateway/router
Module I-7410 Advanced Linux FS-11 Part1: Virtualization with KVM
 Bern University of Applied Sciences Engineering and Information Technology Module I-7410 Advanced Linux FS-11 Part1: Virtualization with KVM By Franz Meyer Version 1.0 February 2011 Virtualization Architecture
Bern University of Applied Sciences Engineering and Information Technology Module I-7410 Advanced Linux FS-11 Part1: Virtualization with KVM By Franz Meyer Version 1.0 February 2011 Virtualization Architecture
IBM Tivoli Composite Application Manager for Microsoft Applications: Microsoft Hyper-V Server Agent Version 6.3.1 Fix Pack 2.
 IBM Tivoli Composite Application Manager for Microsoft Applications: Microsoft Hyper-V Server Agent Version 6.3.1 Fix Pack 2 Reference IBM Tivoli Composite Application Manager for Microsoft Applications:
IBM Tivoli Composite Application Manager for Microsoft Applications: Microsoft Hyper-V Server Agent Version 6.3.1 Fix Pack 2 Reference IBM Tivoli Composite Application Manager for Microsoft Applications:
Installing & Using KVM with Virtual Machine Manager COSC 495
 Installing & Using KVM with Virtual Machine Manager COSC 495 1 Abstract:. There are many different hypervisors and virtualization software available for use. One commonly use hypervisor in the Linux system
Installing & Using KVM with Virtual Machine Manager COSC 495 1 Abstract:. There are many different hypervisors and virtualization software available for use. One commonly use hypervisor in the Linux system
Recommended Solutions for Installing Symantec Endpoint Protection 12.1.x in Shared and PvD Virtual Machines
 Recommended Solutions for Installing Symantec Endpoint Protection 12.1.x in Shared and PvD Virtual Machines Applicability When Symantec Endpoint Protection (SEP 12.1.x is installed in a virtual machine
Recommended Solutions for Installing Symantec Endpoint Protection 12.1.x in Shared and PvD Virtual Machines Applicability When Symantec Endpoint Protection (SEP 12.1.x is installed in a virtual machine
Virtualization and Other Tricks.
 Virtualization and Other Tricks. Pavel Parízek, Tomáš Kalibera, Peter Libič DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz CHARLES UNIVERSITY PRAGUE Faculty of Mathematics and
Virtualization and Other Tricks. Pavel Parízek, Tomáš Kalibera, Peter Libič DEPARTMENT OF DISTRIBUTED AND DEPENDABLE SYSTEMS http://d3s.mff.cuni.cz CHARLES UNIVERSITY PRAGUE Faculty of Mathematics and
VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED.
 VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED. Starting Vmware Workstation Go to the start menu and start the VMware Workstation program. *If you are using
VMWare Workstation 11 Installation MICROSOFT WINDOWS SERVER 2008 R2 STANDARD ENTERPRISE ED. Starting Vmware Workstation Go to the start menu and start the VMware Workstation program. *If you are using
AFACT Cloud Computing Working Group. Chia Hung Kao Institute for Information Industry
 AFACT Cloud Computing Working Group Chia Hung Kao Institute for Information Industry 1 Outline CAKE (Cloud Appliance Kernel Environment) by III Migration to Cloud Open Virtualization Format Collaboration
AFACT Cloud Computing Working Group Chia Hung Kao Institute for Information Industry 1 Outline CAKE (Cloud Appliance Kernel Environment) by III Migration to Cloud Open Virtualization Format Collaboration
NAS 249 Virtual Machine Configuration with VirtualBox
 NAS 249 Virtual Machine Configuration with VirtualBox Configure and run Virtual Machines on ASUSTOR Portal with VirtualBox A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you
NAS 249 Virtual Machine Configuration with VirtualBox Configure and run Virtual Machines on ASUSTOR Portal with VirtualBox A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you
These instructions were tested on OS X 10.9.4. Earlier or later versions may have slight or major differences in how things work and appear.
 These instructions were tested on OS X 10.9.4. Earlier or later versions may have slight or major differences in how things work and appear. PART ONE VBOX INSTALL AND FILE STAGING You will be given a location
These instructions were tested on OS X 10.9.4. Earlier or later versions may have slight or major differences in how things work and appear. PART ONE VBOX INSTALL AND FILE STAGING You will be given a location
FROM A "WINDOWS" PERSPECTIVE
 VIRTUAL NETWORKING WITH "Oracle VM VirtualBox" FROM A "WINDOWS" PERSPECTIVE Summary: "VMware Player" provides five virtual networking configurations for the virtual machines of a Windows host computer:
VIRTUAL NETWORKING WITH "Oracle VM VirtualBox" FROM A "WINDOWS" PERSPECTIVE Summary: "VMware Player" provides five virtual networking configurations for the virtual machines of a Windows host computer:
How to Install Multiple Monitoring Agents on a Microsoft Operating System. Version StoneGate Firewall/VPN 2.6 and SMC 3.2
 How to Install Multiple Monitoring Agents on a Microsoft Operating System Version StoneGate Firewall/VPN 2.6 and SMC 3.2 INTRODUCTION This document provides detailed instructions for installing multiple
How to Install Multiple Monitoring Agents on a Microsoft Operating System Version StoneGate Firewall/VPN 2.6 and SMC 3.2 INTRODUCTION This document provides detailed instructions for installing multiple
IOS110. Virtualization 5/27/2014 1
 IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
Retrospect 7.7 User s Guide Addendum
 Retrospect 7.7 User s Guide Addendum 2011 Retrospect, Inc. All rights reserved. Retrospect 7.7 Users Guide Addendum, first edition. Use of this product (the Software ) is subject to acceptance of the license
Retrospect 7.7 User s Guide Addendum 2011 Retrospect, Inc. All rights reserved. Retrospect 7.7 Users Guide Addendum, first edition. Use of this product (the Software ) is subject to acceptance of the license
Virtualised MikroTik
 Virtualised MikroTik MikroTik in a Virtualised Hardware Environment Speaker: Tom Smyth CTO Wireless Connect Ltd. Event: MUM Krackow Feb 2008 http://wirelessconnect.eu/ Copyright 2008 1 Objectives Understand
Virtualised MikroTik MikroTik in a Virtualised Hardware Environment Speaker: Tom Smyth CTO Wireless Connect Ltd. Event: MUM Krackow Feb 2008 http://wirelessconnect.eu/ Copyright 2008 1 Objectives Understand
How to use the VMware Workstation / Player to create an ISaGRAF (Ver. 3.55) development environment?
 Author Janice Hong Version 1.0.0 Date Mar. 2014 Page 1/56 How to use the VMware Workstation / Player to create an ISaGRAF (Ver. 3.55) development environment? Application Note The 32-bit operating system
Author Janice Hong Version 1.0.0 Date Mar. 2014 Page 1/56 How to use the VMware Workstation / Player to create an ISaGRAF (Ver. 3.55) development environment? Application Note The 32-bit operating system
Running Windows 8 on top of Android with KVM. 21 October 2013. Zhi Wang, Jun Nakajima, Jack Ren
 Running Windows 8 on top of Android with KVM 21 October 2013 Zhi Wang, Jun Nakajima, Jack Ren Legal Disclaimer INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS
Running Windows 8 on top of Android with KVM 21 October 2013 Zhi Wang, Jun Nakajima, Jack Ren Legal Disclaimer INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS
Virtual Hosting & Virtual Machines
 & Virtual Machines Coleman Kane [email protected] September 2, 2014 Cyber Defense Overview / Machines 1 / 17 Similar to the network partitioning schemes described previously, there exist a menu of options
& Virtual Machines Coleman Kane [email protected] September 2, 2014 Cyber Defense Overview / Machines 1 / 17 Similar to the network partitioning schemes described previously, there exist a menu of options
EXPLORING LINUX KERNEL: THE EASY WAY!
 EXPLORING LINUX KERNEL: THE EASY WAY! By: Ahmed Bilal Numan 1 PROBLEM Explore linux kernel TCP/IP stack Solution Try to understand relative kernel code Available text Run kernel in virtualized environment
EXPLORING LINUX KERNEL: THE EASY WAY! By: Ahmed Bilal Numan 1 PROBLEM Explore linux kernel TCP/IP stack Solution Try to understand relative kernel code Available text Run kernel in virtualized environment
Monitor and Secure Linux System with Open Source Tripwire
 Cyber Forensics Laboratory 1 Monitor and Secure Linux System with Open Source Tripwire Copyright c 2012 Hui Li, Michael McGinty and Xinwen Fu, University of Massachusetts Lowell Permission is granted to
Cyber Forensics Laboratory 1 Monitor and Secure Linux System with Open Source Tripwire Copyright c 2012 Hui Li, Michael McGinty and Xinwen Fu, University of Massachusetts Lowell Permission is granted to
Onboarding VMs to Cisco OpenStack Private Cloud
 White Paper Onboarding VMs to Cisco OpenStack Private Cloud This white paper will explain the process for exporting existing virtual machines from either VMware vsphere or AWS EC2 into Cisco OpenStack
White Paper Onboarding VMs to Cisco OpenStack Private Cloud This white paper will explain the process for exporting existing virtual machines from either VMware vsphere or AWS EC2 into Cisco OpenStack
AKIPS Network Monitor Installation, Configuration & Upgrade Guide Version 16. AKIPS Pty Ltd
 AKIPS Network Monitor Installation, Configuration & Upgrade Guide Version 16 AKIPS Pty Ltd July 5, 2016 1 Copyright Copyright 2015 AKIPS Holdings Pty Ltd. All rights reserved worldwide. No part of this
AKIPS Network Monitor Installation, Configuration & Upgrade Guide Version 16 AKIPS Pty Ltd July 5, 2016 1 Copyright Copyright 2015 AKIPS Holdings Pty Ltd. All rights reserved worldwide. No part of this
Uses for Virtual Machines. Virtual Machines. There are several uses for virtual machines:
 Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Developing Microsoft Azure Solutions
 Course 20532A: Developing Microsoft Azure Solutions Page 1 of 7 Developing Microsoft Azure Solutions Course 20532A: 4 days; Instructor-Led Introduction This course is intended for students who have experience
Course 20532A: Developing Microsoft Azure Solutions Page 1 of 7 Developing Microsoft Azure Solutions Course 20532A: 4 days; Instructor-Led Introduction This course is intended for students who have experience
Developing Microsoft Azure Solutions 20532A; 5 days
 Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Developing Microsoft Azure Solutions 20532A; 5 days Course Description This
Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Developing Microsoft Azure Solutions 20532A; 5 days Course Description This
Converting Linux and Windows Physical and Virtual Machines to Oracle VM Virtual Machines. An Oracle Technical White Paper December 2008
 Converting Linux and Windows Physical and Virtual Machines to Oracle VM Virtual Machines An Oracle Technical White Paper December 2008 Converting Linux and Windows Physical and Virtual Machines to Oracle
Converting Linux and Windows Physical and Virtual Machines to Oracle VM Virtual Machines An Oracle Technical White Paper December 2008 Converting Linux and Windows Physical and Virtual Machines to Oracle
Guest Operating System. Installation Guide
 Guest Operating System Installation Guide VMware, Inc. 3145 Porter Drive Palo Alto, CA 94304 www.vmware.com Please note that you will always find the most up-to-date technical documentation on our Web
Guest Operating System Installation Guide VMware, Inc. 3145 Porter Drive Palo Alto, CA 94304 www.vmware.com Please note that you will always find the most up-to-date technical documentation on our Web
Accessing RCS IBM Console in Windows Using Linux Virtual Machine
 Accessing RCS IBM Console in Windows Using Linux Virtual Machine For Graphics Simulation Experiment, Real Time Applications, ECSE 4760 Quan Wang Department of ECSE, Rensselaer Polytechnic Institute March,
Accessing RCS IBM Console in Windows Using Linux Virtual Machine For Graphics Simulation Experiment, Real Time Applications, ECSE 4760 Quan Wang Department of ECSE, Rensselaer Polytechnic Institute March,
Installation of Winisis on Windows 8 (64 bits) using Oracle Virtual Box Ernesto Spinak 15/07/2013
 Installation of Winisis on Windows 8 (64 bits) using Oracle Virtual Box Ernesto Spinak 15/07/2013 Introduction Winisis is a Windows application that uses program libraries for 16 and 32-bit systems, so
Installation of Winisis on Windows 8 (64 bits) using Oracle Virtual Box Ernesto Spinak 15/07/2013 Introduction Winisis is a Windows application that uses program libraries for 16 and 32-bit systems, so
Professional Xen Visualization
 Professional Xen Visualization William von Hagen WILEY Wiley Publishing, Inc. Acknowledgments Introduction ix xix Chapter 1: Overview of Virtualization : 1 What Is Virtualization? 2 Application Virtualization
Professional Xen Visualization William von Hagen WILEY Wiley Publishing, Inc. Acknowledgments Introduction ix xix Chapter 1: Overview of Virtualization : 1 What Is Virtualization? 2 Application Virtualization
Machine Edition USB Hardware License Key did not get recognize inside Virtual Machine
 Machine Edition USB Hardware License Key did not get recognize inside Virtual Machine A virtual machine (VM) is a software implementation of a machine (i.e. a computer) that executes programs like a physical
Machine Edition USB Hardware License Key did not get recognize inside Virtual Machine A virtual machine (VM) is a software implementation of a machine (i.e. a computer) that executes programs like a physical
Advanced Server Virtualization: Vmware and Microsoft Platforms in the Virtual Data Center
 Advanced Server Virtualization: Vmware and Microsoft Platforms in the Virtual Data Center Marshall, David ISBN-13: 9780849339318 Table of Contents BASIC CONCEPTS Introduction to Server Virtualization Overview
Advanced Server Virtualization: Vmware and Microsoft Platforms in the Virtual Data Center Marshall, David ISBN-13: 9780849339318 Table of Contents BASIC CONCEPTS Introduction to Server Virtualization Overview
Using VMware Workstation
 VMware Workstation 10 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
VMware Workstation 10 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
CopyKittens Attack Group
 CopyKittens Attack Group Version 1.0 23/11/2015 All Rights Reserved To Minerva Labs LTD and ClearSky Cyber Security, 2015 Contents Executive Summary... 3 The Group Attack Cycle... 4 Step One Spear Phishing...
CopyKittens Attack Group Version 1.0 23/11/2015 All Rights Reserved To Minerva Labs LTD and ClearSky Cyber Security, 2015 Contents Executive Summary... 3 The Group Attack Cycle... 4 Step One Spear Phishing...
Virtualization. Types of Interfaces
 Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Building a Penetration Testing Virtual Computer Laboratory
 Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
[VADP OVERVIEW FOR NETBACKUP]
![[VADP OVERVIEW FOR NETBACKUP] [VADP OVERVIEW FOR NETBACKUP]](/thumbs/39/18644205.jpg) 2013 Ram Nagalla [VADP OVERVIEW FOR NETBACKUP] Understanding the concept of VADP backup in Netbackup and brief description about the different configuration scenarios. Index 1) Overview. 2 2) Compatibility
2013 Ram Nagalla [VADP OVERVIEW FOR NETBACKUP] Understanding the concept of VADP backup in Netbackup and brief description about the different configuration scenarios. Index 1) Overview. 2 2) Compatibility
ClearPass Policy Manager 6.3
 ClearPass Policy Manager 6.3 Tech Note: Installing or Upgrading on a Virtual Machine This document describes the procedures for installing and upgrading ClearPass Policy Manager 6.3 on a Virtual Machine.
ClearPass Policy Manager 6.3 Tech Note: Installing or Upgrading on a Virtual Machine This document describes the procedures for installing and upgrading ClearPass Policy Manager 6.3 on a Virtual Machine.
Comparing Free Virtualization Products
 A S P E I T Tr a i n i n g Comparing Free Virtualization Products A WHITE PAPER PREPARED FOR ASPE BY TONY UNGRUHE www.aspe-it.com toll-free: 877-800-5221 Comparing Free Virtualization Products In this
A S P E I T Tr a i n i n g Comparing Free Virtualization Products A WHITE PAPER PREPARED FOR ASPE BY TONY UNGRUHE www.aspe-it.com toll-free: 877-800-5221 Comparing Free Virtualization Products In this
How to Install Windows on Xen TM 3.0
 How to Install Windows on Xen TM 3.0 A XenSource Technical Note for the Windows 2003 Server Introduction This note describes how to install Windows 2003 Server on Xen. It provides an overview of the Linux
How to Install Windows on Xen TM 3.0 A XenSource Technical Note for the Windows 2003 Server Introduction This note describes how to install Windows 2003 Server on Xen. It provides an overview of the Linux
Course 20532B: Developing Microsoft Azure Solutions
 Course 20532B: Developing Microsoft Solutions Five Days, Instructor-Led About this Course This course is intended for students who have experience building vertically scaled applications. Students should
Course 20532B: Developing Microsoft Solutions Five Days, Instructor-Led About this Course This course is intended for students who have experience building vertically scaled applications. Students should
JobScheduler Installation by Copying
 JobScheduler - Job Execution and Scheduling System JobScheduler Installation by Copying Deployment of multiple JobSchedulers on distributed servers by copying a template JobScheduler March 2015 March 2015
JobScheduler - Job Execution and Scheduling System JobScheduler Installation by Copying Deployment of multiple JobSchedulers on distributed servers by copying a template JobScheduler March 2015 March 2015
The Tor VM Project. Installing the Build Environment & Building Tor VM. Copyright 2008 - The Tor Project, Inc. Authors: Martin Peck and Kyle Williams
 The Tor VM Project Installing the Build Environment & Building Tor VM Authors: Martin Peck and Kyle Williams Table of Contents 1. Introduction and disclaimer 2. Creating the virtualization build environment
The Tor VM Project Installing the Build Environment & Building Tor VM Authors: Martin Peck and Kyle Williams Table of Contents 1. Introduction and disclaimer 2. Creating the virtualization build environment
A Comparison of VMware and {Virtual Server}
 A Comparison of VMware and {Virtual Server} Kurt Lamoreaux Consultant, MCSE, VCP Computer Networking and Consulting Services A Funny Thing Happened on the Way to HP World 2004 Call for speakers at the
A Comparison of VMware and {Virtual Server} Kurt Lamoreaux Consultant, MCSE, VCP Computer Networking and Consulting Services A Funny Thing Happened on the Way to HP World 2004 Call for speakers at the
INSTALLATION GUIDE El Jefe 2.1 Document version: June 2014
 INSTALLATION GUIDE El Jefe 2.1 Document version: June 2014 Contents 1 Goal of this Document...3 2 Introduction...3 3 Installation...4 3.1 El Jefe 2.1 Installation on Ubuntu 13.04 LTS...4 3.2 El Jefe 2.1
INSTALLATION GUIDE El Jefe 2.1 Document version: June 2014 Contents 1 Goal of this Document...3 2 Introduction...3 3 Installation...4 3.1 El Jefe 2.1 Installation on Ubuntu 13.04 LTS...4 3.2 El Jefe 2.1
WINDOWS LOGGING CHEAT SHEET - Win 7/Win 2008 or later
 This Windows Logging Cheat Sheet is intended to help you get started setting up basic and necessary Windows Audit Policy and Logging. By no means is this list extensive; but it does include some very common
This Windows Logging Cheat Sheet is intended to help you get started setting up basic and necessary Windows Audit Policy and Logging. By no means is this list extensive; but it does include some very common
Introduction to Virtualization
 Høgskolen i Telemark Telemark University College Department of Electrical Engineering, Information Technology and Cybernetics Introduction to Virtualization Hans- Petter Halvorsen, 2013.11.27 Faculty of
Høgskolen i Telemark Telemark University College Department of Electrical Engineering, Information Technology and Cybernetics Introduction to Virtualization Hans- Petter Halvorsen, 2013.11.27 Faculty of
Course Outline: Course 6331: Deploying and Managing Microsoft System Center Virtual Machine Manager Learning Method: Instructor-led Classroom Learning
 Course Outline: Course 6331: Deploying and Managing Microsoft System Center Virtual Machine Manager Learning Method: Instructor-led Classroom Learning Duration: 3.00 Day(s)/ 24 hrs Overview: This three-day
Course Outline: Course 6331: Deploying and Managing Microsoft System Center Virtual Machine Manager Learning Method: Instructor-led Classroom Learning Duration: 3.00 Day(s)/ 24 hrs Overview: This three-day
Before we can talk about virtualization security, we need to delineate the differences between the
 1 Before we can talk about virtualization security, we need to delineate the differences between the terms virtualization and cloud. Virtualization, at its core, is the ability to emulate hardware via
1 Before we can talk about virtualization security, we need to delineate the differences between the terms virtualization and cloud. Virtualization, at its core, is the ability to emulate hardware via
APPLICATION NOTE. How to build pylon applications for ARM
 APPLICATION NOTE Version: 01 Language: 000 (English) Release Date: 31 January 2014 Application Note Table of Contents 1 Introduction... 2 2 Steps... 2 1 Introduction This document explains how pylon applications
APPLICATION NOTE Version: 01 Language: 000 (English) Release Date: 31 January 2014 Application Note Table of Contents 1 Introduction... 2 2 Steps... 2 1 Introduction This document explains how pylon applications
Operating Systems Virtualization mechanisms
 Operating Systems Virtualization mechanisms René Serral-Gracià Xavier Martorell-Bofill 1 1 Universitat Politècnica de Catalunya (UPC) May 26, 2014 Contents 1 Introduction 2 Hardware Virtualization mechanisms
Operating Systems Virtualization mechanisms René Serral-Gracià Xavier Martorell-Bofill 1 1 Universitat Politècnica de Catalunya (UPC) May 26, 2014 Contents 1 Introduction 2 Hardware Virtualization mechanisms
Virtualization System Vulnerability Discovery Framework. Speaker: Qinghao Tang Title:360 Marvel Team Leader
 Virtualization System Vulnerability Discovery Framework Speaker: Qinghao Tang Title:360 Marvel Team Leader 1 360 Marvel Team Established in May 2015, the first professional could computing and virtualization
Virtualization System Vulnerability Discovery Framework Speaker: Qinghao Tang Title:360 Marvel Team Leader 1 360 Marvel Team Established in May 2015, the first professional could computing and virtualization
70-271. Supporting Users and Troubleshooting a Microsoft Windows XP Operating System Q&A. DEMO Version
 Supporting Users and Troubleshooting a Microsoft Windows XP Operating System Q&A DEMO Version Copyright (c) 2007 Chinatag LLC. All rights reserved. Important Note Please Read Carefully For demonstration
Supporting Users and Troubleshooting a Microsoft Windows XP Operating System Q&A DEMO Version Copyright (c) 2007 Chinatag LLC. All rights reserved. Important Note Please Read Carefully For demonstration
Download Virtualization Software Download a Linux-based OS Creating a Virtual Machine using VirtualBox: VM name
 Download Virtualization Software You will first need to download and install a virtualization product. This will allow you to create a virtual machine which you can install a Linux distribution on. I recommend
Download Virtualization Software You will first need to download and install a virtualization product. This will allow you to create a virtual machine which you can install a Linux distribution on. I recommend
How To Protect Your Data From Being Damaged On Vsphere Vdp Vdpa Vdpo Vdprod (Vmware) Vsphera Vdpower Vdpl (Vmos) Vdper (Vmom
 VMware vsphere Data Protection 6.0 Maciej Kot Senior Systems Engineer VMware Overview vsphere Data Protection Overview Data protection for VMs and applications Agent-less VM backup and restore Agents for
VMware vsphere Data Protection 6.0 Maciej Kot Senior Systems Engineer VMware Overview vsphere Data Protection Overview Data protection for VMs and applications Agent-less VM backup and restore Agents for
HP Operations Orchestration Software
 HP Operations Orchestration Software Software Version: 9.00 Microsoft Hyper-V Integration Guide Document Release Date: June 2010 Software Release Date: June 2010 Legal Notices Warranty The only warranties
HP Operations Orchestration Software Software Version: 9.00 Microsoft Hyper-V Integration Guide Document Release Date: June 2010 Software Release Date: June 2010 Legal Notices Warranty The only warranties
How to troubleshoot MS DTC firewall issues
 Page 1 of 5 Article ID: 306843 - Last Review: October 29, 2007 - Revision: 5.3 How to troubleshoot MS DTC firewall issues Retired KB Content Disclaimer This article was previously published under Q306843
Page 1 of 5 Article ID: 306843 - Last Review: October 29, 2007 - Revision: 5.3 How to troubleshoot MS DTC firewall issues Retired KB Content Disclaimer This article was previously published under Q306843
Intelligent Laptop Virtualization No compromises for IT or end users. VMware Mirage [email protected]
 Intelligent Laptop Virtualization No compromises for IT or end users VMware Mirage [email protected] Little video to start with... The Problem with Laptops Windows XP support is expiring
Intelligent Laptop Virtualization No compromises for IT or end users VMware Mirage [email protected] Little video to start with... The Problem with Laptops Windows XP support is expiring
CIT 668: System Architecture
 CIT 668: System Architecture Cloud Security Topics 1. The Same Old Security Problems 2. Virtualization Security 3. New Security Issues and Threat Model 4. Data Security 5. Amazon Cloud Security Data Loss
CIT 668: System Architecture Cloud Security Topics 1. The Same Old Security Problems 2. Virtualization Security 3. New Security Issues and Threat Model 4. Data Security 5. Amazon Cloud Security Data Loss
SOFTWARE INSTALLATION INSTRUCTIONS
 AUDITGARD LGA Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS Implementation Package The AuditGard Software implementation package includes: 707013 AuditGard Software Install CD 42145 Programming/Audit
AUDITGARD LGA Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS Implementation Package The AuditGard Software implementation package includes: 707013 AuditGard Software Install CD 42145 Programming/Audit
ArCycle vmbackup. for VMware/Hyper-V. User Guide
 ArCycle vmbackup for VMware/Hyper-V User Guide 2 Copyright Copyright ArCycle Software, Ltd., 2011-2014. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system,
ArCycle vmbackup for VMware/Hyper-V User Guide 2 Copyright Copyright ArCycle Software, Ltd., 2011-2014. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system,
Deploying Red Hat Enterprise Virtualization On Tintri VMstore Systems Best Practices Guide
 TECHNICAL WHITE PAPER Deploying Red Hat Enterprise Virtualization On Tintri VMstore Systems Best Practices Guide www.tintri.com Contents Intended Audience... 4 Introduction... 4 Consolidated List of Practices...
TECHNICAL WHITE PAPER Deploying Red Hat Enterprise Virtualization On Tintri VMstore Systems Best Practices Guide www.tintri.com Contents Intended Audience... 4 Introduction... 4 Consolidated List of Practices...
Virtual Machines. www.viplavkambli.com
 1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
The safer, easier way to help you pass any IT exams. Exam : 070-659. TS: Windows Server 2008 R2, Server Virtualization. Title : Version : Demo 1 / 7
 Exam : 070-659 Title : TS: Windows Server 2008 R2, Server Virtualization Version : Demo 1 / 7 1.You install Windows Server 2008 R2 Enterprise on a new physical server. You need to prepare the server to
Exam : 070-659 Title : TS: Windows Server 2008 R2, Server Virtualization Version : Demo 1 / 7 1.You install Windows Server 2008 R2 Enterprise on a new physical server. You need to prepare the server to
Skip the But it Works on My Machine Excuse with Vagrant
 Skip the Excuse with Vagrant Ohio LinuxFest 2015 Outline 1 2 3 4 Agenda 1 2 3 4 JVM and Big Data Developer Stylophile Coffee aficionado [email protected] @jbeard6 http://josephbeard.net Agenda 1
Skip the Excuse with Vagrant Ohio LinuxFest 2015 Outline 1 2 3 4 Agenda 1 2 3 4 JVM and Big Data Developer Stylophile Coffee aficionado [email protected] @jbeard6 http://josephbeard.net Agenda 1
Course 6331A: Deploying and Managing Microsoft System Center Virtual Machine Manager
 Course 6331A: Deploying and Managing Microsoft System Center Virtual Machine Manager Length: 3 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology: Microsoft System Center Virtual
Course 6331A: Deploying and Managing Microsoft System Center Virtual Machine Manager Length: 3 Days Language(s): English Audience(s): IT Professionals Level: 300 Technology: Microsoft System Center Virtual
How to Backup and Restore a VM using Veeam
 How to Backup and Restore a VM using Veeam Table of Contents Introduction... 3 Assumptions... 3 Add ESXi Server... 4 Backup a VM... 6 Restore Full VM... 12 Appendix A: Install Veeam Backup & Replication
How to Backup and Restore a VM using Veeam Table of Contents Introduction... 3 Assumptions... 3 Add ESXi Server... 4 Backup a VM... 6 Restore Full VM... 12 Appendix A: Install Veeam Backup & Replication
Table of Contents Introduction and System Requirements 9 Installing VMware Server 35
 Table of Contents Introduction and System Requirements 9 VMware Server: Product Overview 10 Features in VMware Server 11 Support for 64-bit Guest Operating Systems 11 Two-Way Virtual SMP (Experimental
Table of Contents Introduction and System Requirements 9 VMware Server: Product Overview 10 Features in VMware Server 11 Support for 64-bit Guest Operating Systems 11 Two-Way Virtual SMP (Experimental
Date: December 2009 Version: 1.0. How Does Xen Work?
 Date: December 2009 Version: 1.0 How Does Xen Work? Table of Contents Executive Summary... 3 Xen Environment Components... 3 Xen Hypervisor... 3... 4 Domain U... 4 Domain Management and Control... 6 Xend...
Date: December 2009 Version: 1.0 How Does Xen Work? Table of Contents Executive Summary... 3 Xen Environment Components... 3 Xen Hypervisor... 3... 4 Domain U... 4 Domain Management and Control... 6 Xend...
The Art of Virtualization with Free Software
 Master on Free Software 2009/2010 {mvidal,jfcastro}@libresoft.es GSyC/Libresoft URJC April 24th, 2010 (cc) 2010. Some rights reserved. This work is licensed under a Creative Commons Attribution-Share Alike
Master on Free Software 2009/2010 {mvidal,jfcastro}@libresoft.es GSyC/Libresoft URJC April 24th, 2010 (cc) 2010. Some rights reserved. This work is licensed under a Creative Commons Attribution-Share Alike
RUNNING vtvax FOR WINDOWS
 RUNNING vtvax FOR WINDOWS IN A AVT / Vere Technologies TECHNICAL NOTE AVT/Vere Technical Note: Running vtvax for Windows in a Virtual Machine Environment Document Revision 1.1 (September, 2015) 2015 Vere
RUNNING vtvax FOR WINDOWS IN A AVT / Vere Technologies TECHNICAL NOTE AVT/Vere Technical Note: Running vtvax for Windows in a Virtual Machine Environment Document Revision 1.1 (September, 2015) 2015 Vere
Introduction to KVM. By Sheng-wei Lee [email protected] #20110929
 Introduction to KVM By Sheng-wei Lee [email protected] #20110929 Hypervisor - KVM virt-manager Outline Libvirt Migration How to install KVM. Bridged Networking Virsh How to new a VM How to adjust the setting
Introduction to KVM By Sheng-wei Lee [email protected] #20110929 Hypervisor - KVM virt-manager Outline Libvirt Migration How to install KVM. Bridged Networking Virsh How to new a VM How to adjust the setting
Application Note. Example of user log on Magelis HMI with XB5S5B2L2 biometric switch. Advanced Technical Support - Brazil. Version: 1.
 Application Note Example of user log on Magelis HMI with XB5S5B2L2 biometric switch. Version: 1.0 Advanced Technical Support - Brazil Technical Specifications Hardware: Firmware: HMIGTO4310 XB5S5B2L2 Software:
Application Note Example of user log on Magelis HMI with XB5S5B2L2 biometric switch. Version: 1.0 Advanced Technical Support - Brazil Technical Specifications Hardware: Firmware: HMIGTO4310 XB5S5B2L2 Software:
Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine
 Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine Version 3.0 Please note: This appliance is for testing and educational purposes only; it is unsupported and not
Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine Version 3.0 Please note: This appliance is for testing and educational purposes only; it is unsupported and not
Running vtserver in a Virtual Machine Environment. Technical Note. 2015 by AVTware
 Running vtserver in a Virtual Machine Environment Technical Note 2015 by AVTware Table of Contents 1. Scope... 3 1.1. Introduction... 3 2. General Virtual Machine Considerations... 4 2.1. The Virtualization
Running vtserver in a Virtual Machine Environment Technical Note 2015 by AVTware Table of Contents 1. Scope... 3 1.1. Introduction... 3 2. General Virtual Machine Considerations... 4 2.1. The Virtualization
Linux Development Environment Description Based on VirtualBox Structure
 Linux Development Environment Description Based on VirtualBox Structure V1.0 1 VirtualBox is open source virtual machine software. It mainly has three advantages: (1) Free (2) compact (3) powerful. At
Linux Development Environment Description Based on VirtualBox Structure V1.0 1 VirtualBox is open source virtual machine software. It mainly has three advantages: (1) Free (2) compact (3) powerful. At
SECTION 3 - INSTALLATION
 SECTION 3 - INTRODUCTION This section explains how to install the Strategic Enterprise Management Application Programming Interface (semapi) software and how to use the ICICONF.EXE program to configure
SECTION 3 - INTRODUCTION This section explains how to install the Strategic Enterprise Management Application Programming Interface (semapi) software and how to use the ICICONF.EXE program to configure
Installing Ubuntu. Obtaining files required
 Installing Ubuntu Historically, Linux has required its own private space on your hard disk. Achieving this required making some fairly fundamental alterations to the files on your hard disk that could
Installing Ubuntu Historically, Linux has required its own private space on your hard disk. Achieving this required making some fairly fundamental alterations to the files on your hard disk that could
Capability VMware Hyper-V
 Capability VMware Hyper-V Host File System Management Virtual Disk Image Format Integration Tools / Drivers Connect LUN directly to VM from SAN VMFS (Virtual Machine File System) VMware allows you to extend
Capability VMware Hyper-V Host File System Management Virtual Disk Image Format Integration Tools / Drivers Connect LUN directly to VM from SAN VMFS (Virtual Machine File System) VMware allows you to extend
Eaton NetWatch NetWatch installation and configuration guide VMware ESX 3 Virtual architecture
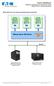 Eaton NetWatch NetWatch installation and configuration guide VMware ESX 3 Virtual architecture VMware ESX server host and guest operating systems architecture Virtual/ Guest OS 1 (Windows) Applications,
Eaton NetWatch NetWatch installation and configuration guide VMware ESX 3 Virtual architecture VMware ESX server host and guest operating systems architecture Virtual/ Guest OS 1 (Windows) Applications,
COMBOGARDPRO. 39E Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS
 COMBOGARDPRO 39E Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS IMPLEMENTATION PACKAGE The ComboGard Pro Software implementation package includes: 707012 ComboGard Pro Software Install
COMBOGARDPRO 39E Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS IMPLEMENTATION PACKAGE The ComboGard Pro Software implementation package includes: 707012 ComboGard Pro Software Install
Software SIParator / Firewall
 Orientation and Installation Guide for the Ingate SBC and E-SBC Software SIParator / Firewall for Virtual x86 Machines For the Ingate Software SIParators using software release 5.0.6 or later Revision
Orientation and Installation Guide for the Ingate SBC and E-SBC Software SIParator / Firewall for Virtual x86 Machines For the Ingate Software SIParators using software release 5.0.6 or later Revision
Windows Azure and private cloud
 Windows Azure and private cloud Joe Chou Senior Program Manager China Cloud Innovation Center Customer Advisory Team Microsoft Asia-Pacific Research and Development Group 1 Agenda Cloud Computing Fundamentals
Windows Azure and private cloud Joe Chou Senior Program Manager China Cloud Innovation Center Customer Advisory Team Microsoft Asia-Pacific Research and Development Group 1 Agenda Cloud Computing Fundamentals
Backup and Recovery for Microsoft Hyper-V Using Best Practices Planning. Brien M. Posey
 Backup and Recovery for Microsoft Hyper-V Using Best Practices Planning Brien M. Posey Introduction There usually isn t anything overly complicated about backing up a physical datacenter. While it s true
Backup and Recovery for Microsoft Hyper-V Using Best Practices Planning Brien M. Posey Introduction There usually isn t anything overly complicated about backing up a physical datacenter. While it s true
Analysis of Virtualization Tools and Techniques
 Analysis of Virtualization Tools and Techniques Mrs. Kavita S. 1, Mrs. Dakshyani G. 2, Mrs. Kiruthika 3 Assistant Professor, Department of Computer Engineering, FCRIT, Vashi, Navi Mumbai, India 1,2 Associate
Analysis of Virtualization Tools and Techniques Mrs. Kavita S. 1, Mrs. Dakshyani G. 2, Mrs. Kiruthika 3 Assistant Professor, Department of Computer Engineering, FCRIT, Vashi, Navi Mumbai, India 1,2 Associate
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE
 MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
vsphere Replication for Disaster Recovery to Cloud
 vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
vsphere Replication for Disaster Recovery to Cloud vsphere Replication 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
