Connecting to the ODU Turing Cluster
|
|
|
- Edmund Gray
- 9 years ago
- Views:
Transcription
1 Connecting to the ODU Turing Cluster Section Terminology remote connection - This refers to a connection that is made over a network between two computers ssh - Secure Shell, a type of remote connection terminal - an application window, that accepts text commands username - In this document, when the term username is used, it is referring to a users MIDAS account user name (i.e. the part of your ODU address before symbol) password - In this document, when the term password is used, it is referring to a users MIDAS account password (i.e. the ODU account password) X window system (X11) - a set of software libraries and applications that allow images on a local or remote Linux/Unix computer, to be displayed {Note: The X window system is not the same thing as the Microsoft Windows set of operating systems.} Introduction to Remote Connections The Turing cluster runs a Linux operating system that allows users to remotely connect through a secure shell (ssh). The ssh connection can be created through a terminal window of a Linux/Unix based system (i.e. Macintosh OSX, Ubuntu, Oracle (historically Sun) Solaris, etc.). Microsoft Windows based systems; however, require the installation of additional software known as an application client to connect to the cluster. Information Technology Services - High Performance Computing Group 1 of 16
2 Microsoft Windows ssh connection clients There are several, widely available application clients that can be utilized on Microsoft Windows computers. This document will focus on the use of two popular packages. The first is X-Win32 which is a commercial application, and the second is PuTTY which is an open source package. Suggestions for remote clients on tablets and mobile devices will also be provided though these form factors are not recommended nor supported for intensive work sessions. X-Win32 for Microsoft Windows X-Win32 is a commercial application licensed by ODU, from the company StarNet. X-Win32 is a ssh and X11 emulator for Microsoft Windows based systems (i.e. Windows XP, Windows 7, Windows 8.1, etc.) The install files for X-Win32 is available through the ODU Software Services Catalog ( Once downloaded the package should be uncompressed (this can be done using a software package such as 7-zip ( zip.org)) and installed using the InstallXwin32.exe application. {Note: Improper installation of X-Win32 or direct installation of X-Win32 from the StarNet website will not include the ODU licensing information.} If the user is on the ODU network with reduced user privileges (i.e. a user is unable to install programs), a request to install the software can be made to the ITS group through the address [email protected]. Configuring X-Win32 1. After downloading and installing the X-win32 application from the ODU Software Services page ( do one of the following to open the application: a. Opening X-Config in Windows 7 i. Click the [Start] button ii. Select All Programs iii. Select X-Win iv. Select X-Config b. Opening X-Config in Windows 8 i. Open the Charm bar (put the mouse in the lower left hand corner until the icons appear) ii. Select Search (the magnifying glass icon) iii. Select Apps iv. Type X-Config in the search field v. Click the X-Config icon {Note: to add this application icon to the metrostart screen, right-click the X-Config icon and select Pin to Start } Information Technology Services - High Performance Computing Group 2 of 16
3 c. Opening X-Config in Windows 8.1 i. Open the Charm bar (put the mouse in the lower left hand corner until the icons appear) ii. Select Search (the magnifying glass icon) iii. Type X-Config in the search field iv. Click the X-Config icon {Note: to add this application icon to the metrostart screen, right-click the X-Config icon and select Pin to Start } Note: In both Microsoft Windows 8 and 8.1 the X-Config and X-Win32 application icons can be added to the Metro-styled Start menu by first searching for the icons, right-clicking the icon, and then selecting Pin to Start. Information Technology Services - High Performance Computing Group 3 of 16
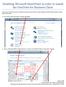
4 2. In the X-Win Configuration window, click the [Wizard] button. Information Technology Services - High Performance Computing Group 4 of 16
5 3. In the Connection Wizard - X - Config window, type Turing in the Name: field and select ssh as the Type:, then click [Next]. 4. In the Host: field type turing.hpc.odu.edu and the click [Next]. Information Technology Services - High Performance Computing Group 5 of 16
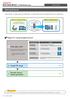
6 5. Enter your username (i.e. the part of your ODU address before symbol) and password (i.e. the ODU account password) in the corresponding fields and then click [Next]. 6. Select Linux and the commands /usr/bin/xterm -ls will automatically populate the Command: field; then click [Finish]. 7. The configuration of the X-Win32 connection to Turing is now completed. Information Technology Services - High Performance Computing Group 6 of 16
7 Connect using X-Win32 1. Open X-Win32 by using one of the following methods {Note: The difference between opening the X-Config versus the X-Win32 icons, is that X-Win32 attempts to automatically launch the last connection used}: a. Opening X-Win32 in Windows 7 i. Click the [Start] button ii. Select All Programs iii. Select X-Win iv. Select X-Config b. Opening X-Win32 in Windows 8 i. Open the Charm bar (put the mouse in the lower left hand corner until the icons appear) ii. Select Search (the magnifying glass icon) iii. Select Apps iv. Type X-Config in the search field v. Click the X-Config icon {Note: to add this application icon to the metrostart screen, right-click the X-Config icon and select Pin to Start } c. Opening X-Win32 in Windows 8.1 i. Open the Charm bar (put the mouse in the lower left hand corner until the icons appear) ii. Select Search (the magnifying glass icon) iii. Type X-Config in the search field iv. Click the X-Config icon {Note: to add this application icon to the metrostart screen, right-click the X-Config icon and select Pin to Start } Information Technology Services - High Performance Computing Group 7 of 16
8 2. Select the Connections tab within the X-Win Configuration window 3. Select the Turing connection 4. Click the [Launch] button 5. A terminal window will open with a cursor blinking next to a prompt similar to [username@turing1 ~]$. That means you have successfully logged into the Turing cluster. Information Technology Services - High Performance Computing Group 8 of 16
9 Note: If either the username or password are incorrect, inactive, or not entered during the configuration of the connection, you will be prompted to enter/re-enter your username and/or password before you receive a terminal window. If unable to log into the cluster please submit an ITS Helpdesk request by ing [email protected]. Information Technology Services - High Performance Computing Group 9 of 16
10 Exiting/Closing the connection 1. Type exit into the window, and then press [Enter] 2. Press [OK] in the X-Win Configuration window Information Technology Services - High Performance Computing Group 10 of 16
11 PuTTY for Microsoft Windows (No native X11 Support) PuTTY is an open source application written and maintained primarily by Mr. Simon Tatham. The unique characteristic about PuTTY is that no administrative rights are necessary to run the application. The application putty.exe is a stand-alone executable file that can be downloaded from There are however, two caveats when compared with X-Win32. The first is that PuTTY does not have an included (native) X11 component, which means only a text based terminal connection is available. The second caveat is if you would like to have traditional icons added to the Start/Metro Menu of Windows, the full PuTTY application package should be installed. That means that if the user has reduced privileges (i.e. a user is unable to install programs), a request to install the software must be made to the ITS group through the address [email protected]. Configuring PuTTY.exe 1. After downloading the PuTTY.exe application from the official PuTTY website ( double-click on the putty icon to open the program. {Note: When PuTTY is opened the first time after downloaded, the system may display a warning about opening the downloaded application. Select Yes to continue.} 2. In the PuTTY Configuration window select Session from the Category tree. 3. In the Host Name (or IP address) field, type turing.hpc.odu.edu Information Technology Services - High Performance Computing Group 11 of 16
12 4. In the Saved Sessions field type the name Turing and press [Save]. Information Technology Services - High Performance Computing Group 12 of 16
13 Connect using PuTTY.exe 1. Open PuTTY using the icon. 2. In the PuTTY Configuration window select Session from the Category tree. 3. Click Turing in the Saved Sessions area, then click [Load]. 4. Click the [Open] button at the bottom of the window. 5. If this is the first time connecting to the Turing cluster, a window will open asking to add the server's host key to the registry. Select [Yes]. Information Technology Services - High Performance Computing Group 13 of 16
14 6. In the turing.hpc.odu.edu - PuTTY window, where it asks login as:, type your username (i.e. the part of your ODU address before symbol) and press [Enter] 7. In the turing.hpc.odu.edu - PuTTY window, where it asks [email protected] s password:, type your password (i.e. the ODU account password) and press [Enter] {Note: You will not see anything change on the screen as you type your password}. Information Technology Services - High Performance Computing Group 14 of 16
15 8. At this point you will see a cursor blinking next to a prompt similar to [username@turing1 ~]$. That means you have successfully logged into the Turing cluster. Exiting/Closing the connection 1. Type exit into the window, and then press [Enter] Information Technology Services - High Performance Computing Group 15 of 16
16 Information Technology Services - High Performance Computing Group 16 of 16
Citrix Client Install Instructions
 Citrix Client Install Instructions If you are using Citrix remotely, Information Technology Services recommends updating Citrix client to the newest version available online. You must be an administrator
Citrix Client Install Instructions If you are using Citrix remotely, Information Technology Services recommends updating Citrix client to the newest version available online. You must be an administrator
Virtual Office Remote Installation Guide
 Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
OFFICE 365 SELF- CONFIGURATION GUIDE
 IT HELPDESK, REPUBLIC POLYTECHNIC OFFICE 365 SELF- CONFIGURATION GUIDE Version 7.0 IT Helpdesk 6-30-2015 0 TABLE OF CONTENTS Things to note before proceeding with this guide:... 1 Office 365 ProPlus Installation
IT HELPDESK, REPUBLIC POLYTECHNIC OFFICE 365 SELF- CONFIGURATION GUIDE Version 7.0 IT Helpdesk 6-30-2015 0 TABLE OF CONTENTS Things to note before proceeding with this guide:... 1 Office 365 ProPlus Installation
Miami University RedHawk Cluster Connecting to the Cluster Using Windows
 Miami University RedHawk Cluster Connecting to the Cluster Using Windows The RedHawk cluster is a general purpose research computing resource available to support the research community at Miami University.
Miami University RedHawk Cluster Connecting to the Cluster Using Windows The RedHawk cluster is a general purpose research computing resource available to support the research community at Miami University.
Macs are not directly compatible with Noetix.
 Those that use Macintosh computers to access Noetix cannot directly access Noetix through http://www.sandiego.edu/noetix. If one is on a Mac and goes to Noetix directly in a web browser, the page is likely
Those that use Macintosh computers to access Noetix cannot directly access Noetix through http://www.sandiego.edu/noetix. If one is on a Mac and goes to Noetix directly in a web browser, the page is likely
Using SSH Secure Shell Client for FTP
 Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using Remote Web Workplace Version 1.01
 Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
BRIC VPN Setup Instructions
 BRIC VPN Setup Instructions Change Your VPN Password 1. Go to https://fw-ats.bric.msu.edu/. Note: You will receive a message about the certificate not being valid; go ahead and accept it. 2. Login with
BRIC VPN Setup Instructions Change Your VPN Password 1. Go to https://fw-ats.bric.msu.edu/. Note: You will receive a message about the certificate not being valid; go ahead and accept it. 2. Login with
Dial Up Config & Connecting Instructions with Graphics
 Dial Up Config & Connecting Instructions with Graphics Dial Up Config & Connecting Below are the Basic Manual Configurations Connecting to the Internet for the following operating systems: Windows 2000
Dial Up Config & Connecting Instructions with Graphics Dial Up Config & Connecting Below are the Basic Manual Configurations Connecting to the Internet for the following operating systems: Windows 2000
Adafruit's Raspberry Pi Lesson 5. Using a Console Cable
 Adafruit's Raspberry Pi Lesson 5. Using a Console Cable Created by Simon Monk Last updated on 2014-09-15 12:00:13 PM EDT Guide Contents Guide Contents Overview You Will Need Part Software Installation
Adafruit's Raspberry Pi Lesson 5. Using a Console Cable Created by Simon Monk Last updated on 2014-09-15 12:00:13 PM EDT Guide Contents Guide Contents Overview You Will Need Part Software Installation
Hallpass Instructions for Connecting to Mac with a Mac
 Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Sophos UTM. Remote Access via SSL Configuring Remote Client
 Sophos UTM Remote Access via SSL Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
Sophos UTM Remote Access via SSL Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website
 Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Sophos UTM. Remote Access via PPTP Configuring Remote Client
 Sophos UTM Remote Access via PPTP Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
Sophos UTM Remote Access via PPTP Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
Using Remote Desktop with the Cisco AnyConnect VPN Client in Windows Vista
 Using Remote Desktop with the Cisco AnyConnect VPN Client in Windows Vista 1. In order to use Remote Desktop and the VPN client, users must first complete the Blackboard Remote Users training course and
Using Remote Desktop with the Cisco AnyConnect VPN Client in Windows Vista 1. In order to use Remote Desktop and the VPN client, users must first complete the Blackboard Remote Users training course and
Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.5
 Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.5 Objectives Part 1: Configure CCP Access for Routers Enable HTTP/HTTPS server. Create a user account with privilege level 15.
Configuring Devices for Use with Cisco Configuration Professional (CCP) 2.5 Objectives Part 1: Configure CCP Access for Routers Enable HTTP/HTTPS server. Create a user account with privilege level 15.
Xopero Backup Build your private cloud backup environment. Getting started
 Xopero Backup Build your private cloud backup environment Getting started 07.05.2015 List of contents Introduction... 2 Get Management Center... 2 Setup Xopero to work... 3 Change the admin password...
Xopero Backup Build your private cloud backup environment Getting started 07.05.2015 List of contents Introduction... 2 Get Management Center... 2 Setup Xopero to work... 3 Change the admin password...
OCS Virtual image. User guide. Version: 1.3.1 Viking Edition
 OCS Virtual image User guide Version: 1.3.1 Viking Edition Publication date: 30/12/2012 Table of Contents 1. Introduction... 2 2. The OCS virtualized environment composition... 2 3. What do you need?...
OCS Virtual image User guide Version: 1.3.1 Viking Edition Publication date: 30/12/2012 Table of Contents 1. Introduction... 2 2. The OCS virtualized environment composition... 2 3. What do you need?...
How to Configure Outlook 2010 E-mail Client for Exchange
 LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8)
 INFORMATION SYSTEMS SERVICE NETWORKS AND COMMUNICATIONS SECTOR VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8) ΥΠΣ ΕΔ/50 November 2012 A. INSTALLATION
INFORMATION SYSTEMS SERVICE NETWORKS AND COMMUNICATIONS SECTOR VPN Remote Access Installation and Configuration Guide Operating System: Windows (XP, Vista, 7 and 8) ΥΠΣ ΕΔ/50 November 2012 A. INSTALLATION
Connecting to HomeRun over the Web
 (o HomeRun Integrated Clinical and Financial Homecare Software Connecting to HomeRun over the Web White Oak Systems, LLC 8 Research Parkway Wallingford, CT 06492 Phone: 866-679-7702 [email protected]
(o HomeRun Integrated Clinical and Financial Homecare Software Connecting to HomeRun over the Web White Oak Systems, LLC 8 Research Parkway Wallingford, CT 06492 Phone: 866-679-7702 [email protected]
1. Open Thunderbird. If the Import Wizard window opens, select Don t import anything and click Next and go to step 3.
 Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
Thunderbird The changes that need to be made in the email programs will be the following: Incoming mail server: newmail.one-eleven.net Outgoing mail server (SMTP): newmail.one-eleven.net You will also
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link:
 TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
Email Client Configuration Guide
 Email Client Configuration Guide Table of Contents Email Configuration...3 Email settings...3 IMAP...3 POP...3 SMTP...3 Process Overview...5 Account set up wizards...5 Anatomy of an email address...5 Why
Email Client Configuration Guide Table of Contents Email Configuration...3 Email settings...3 IMAP...3 POP...3 SMTP...3 Process Overview...5 Account set up wizards...5 Anatomy of an email address...5 Why
How to set up Outlook Anywhere on your home system
 How to set up Outlook Anywhere on your home system The Outlook Anywhere feature for Microsoft Exchange Server 2007 allows Microsoft Office Outlook 2007 and Outlook 2003 users to connect to their Outlook
How to set up Outlook Anywhere on your home system The Outlook Anywhere feature for Microsoft Exchange Server 2007 allows Microsoft Office Outlook 2007 and Outlook 2003 users to connect to their Outlook
Contents. VPN Instructions. VPN Instructions... 1
 VPN Instructions Contents VPN Instructions... 1 Download & Install Check Point VPN Software... 2 Connect to FPUA by VPN... 6 Connect to Your Computer... 8 Determine Your Machine Type... 10 Identify 32-bit
VPN Instructions Contents VPN Instructions... 1 Download & Install Check Point VPN Software... 2 Connect to FPUA by VPN... 6 Connect to Your Computer... 8 Determine Your Machine Type... 10 Identify 32-bit
How to Install the Cisco AnyConnect VPN Client. Installing Cisco AnyConnect VPN Client on Windows with the Chrome Browser (Recommended)
 How to Install the Cisco AnyConnect VPN Client Instructions for Windows (Chrome Browser - Recommended) Instructions for Windows (Internet Explorer with Java) Instructions for Mac OS (Chrome Browser) Installing
How to Install the Cisco AnyConnect VPN Client Instructions for Windows (Chrome Browser - Recommended) Instructions for Windows (Internet Explorer with Java) Instructions for Mac OS (Chrome Browser) Installing
Setting up Email in Outlook Express
 Setting up Email in Outlook Express If you have more than one email account but need to use a single computer to access them, then Outlook Express can help. To begin, open Outlook Express by double-clicking
Setting up Email in Outlook Express If you have more than one email account but need to use a single computer to access them, then Outlook Express can help. To begin, open Outlook Express by double-clicking
Remote Access VPN SSL VPN Access via Internet Explorer
 The following instructions will allow you to access your company network remotely, via your Internet Explorer web browser. 1. Launch Internet Explorer and choose Internet Options from the Tools menu. 2.
The following instructions will allow you to access your company network remotely, via your Internet Explorer web browser. 1. Launch Internet Explorer and choose Internet Options from the Tools menu. 2.
KSC Remote Access Solution
 KSC Remote Access Solution Step 1 Pulse Client Install/Configuration Installing the Pulse Client on a PC Installing the Pulse Client on a MAC Step 2 Using Remote Desktop to Access Remote Resources How
KSC Remote Access Solution Step 1 Pulse Client Install/Configuration Installing the Pulse Client on a PC Installing the Pulse Client on a MAC Step 2 Using Remote Desktop to Access Remote Resources How
Lab 8.3.3b Configuring a Remote Router Using SSH
 Lab 8.3.3b Configuring a Remote Router Using SSH Objectives Use SDM to configure a router to accept SSH connections. Configure SSH client software on a PC. Establish a connection to a Cisco ISR using SSH
Lab 8.3.3b Configuring a Remote Router Using SSH Objectives Use SDM to configure a router to accept SSH connections. Configure SSH client software on a PC. Establish a connection to a Cisco ISR using SSH
Getting the most out of your new Aalto workstation An Aalto IT guide for personnel migrating to the new Aalto workstation environment
 Getting the most out of your new Aalto workstation An Aalto IT guide for personnel migrating to the new Aalto workstation environment What services do I use with the old TKK password, and what do I use
Getting the most out of your new Aalto workstation An Aalto IT guide for personnel migrating to the new Aalto workstation environment What services do I use with the old TKK password, and what do I use
Remote Desktop Instructions for the Remote PC Running Windows Vista
 USC Marshall School of Business Academic Information Services Remote Desktop Instructions for the Remote PC Running Windows Vista Remote Desktop allows you to access the files and programs on a computer
USC Marshall School of Business Academic Information Services Remote Desktop Instructions for the Remote PC Running Windows Vista Remote Desktop allows you to access the files and programs on a computer
Remote Access - Mac OS X
 Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Job Aid: Creating Additional Remote Access Logins
 This job aid describes the steps required to add an additional remote access login to the Avaya S8300, S8500, and S8700 Series Media Servers. These logins may be used to establish a Point to Point Protocol
This job aid describes the steps required to add an additional remote access login to the Avaya S8300, S8500, and S8700 Series Media Servers. These logins may be used to establish a Point to Point Protocol
How do I use Citrix Staff Remote Desktop
 How do I use Citrix Staff Remote Desktop September 2014 Initial Log On In order to login into the new Citrix system, you need to go to the following web address. https://remotets.tees.ac.uk/ Be sure to
How do I use Citrix Staff Remote Desktop September 2014 Initial Log On In order to login into the new Citrix system, you need to go to the following web address. https://remotets.tees.ac.uk/ Be sure to
How to Use Remote Access Using Internet Explorer
 Introduction Welcome to the Mount s Remote Access service. The following documentation is intended to assist first time or active users with connecting, authenticating and properly logging out of Remote
Introduction Welcome to the Mount s Remote Access service. The following documentation is intended to assist first time or active users with connecting, authenticating and properly logging out of Remote
SSH and Basic Commands
 SSH and Basic Commands In this tutorial we'll introduce you to SSH - a tool that allows you to send remote commands to your Web server - and show you some simple UNIX commands to help you manage your website.
SSH and Basic Commands In this tutorial we'll introduce you to SSH - a tool that allows you to send remote commands to your Web server - and show you some simple UNIX commands to help you manage your website.
ATTENTION: End users should take note that Main Line Health has not verified within a Citrix
 Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
EMBnet Norway User introduction pack (instructions and services overview) George Magklaras Head Systems Engineer Version 3.
 EMBnet Norway User introduction pack (instructions and services overview) George Magklaras Head Systems Engineer Version 3.2 (February 2008) How to connect a Windows workstation to the EMBnet servers using
EMBnet Norway User introduction pack (instructions and services overview) George Magklaras Head Systems Engineer Version 3.2 (February 2008) How to connect a Windows workstation to the EMBnet servers using
Configuring VPN Using Windows XP
 Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
WatchDox for Mac User Guide
 WatchDox for Mac User Guide Version 2.3.0 Confidentiality This document contains confidential material that is proprietary to WatchDox. The information and ideas herein may not be disclosed to any unauthorized
WatchDox for Mac User Guide Version 2.3.0 Confidentiality This document contains confidential material that is proprietary to WatchDox. The information and ideas herein may not be disclosed to any unauthorized
Setting up a VPN connection Windows XP
 Setting up a VPN connection Windows XP 1. Open Control Panel. 2. Click on Network and Internet Connections. 3. Click on Create a connection to the network at your workplace. 4. Select Virtual Private Network
Setting up a VPN connection Windows XP 1. Open Control Panel. 2. Click on Network and Internet Connections. 3. Click on Create a connection to the network at your workplace. 4. Select Virtual Private Network
Adafruit's Raspberry Pi Lesson 5. Using a Console Cable
 Adafruit's Raspberry Pi Lesson 5. Using a Console Cable Created by Simon Monk Last updated on 2016-04-12 08:03:49 PM EDT Guide Contents Guide Contents Overview You Will Need Part Software Installation
Adafruit's Raspberry Pi Lesson 5. Using a Console Cable Created by Simon Monk Last updated on 2016-04-12 08:03:49 PM EDT Guide Contents Guide Contents Overview You Will Need Part Software Installation
Net 2. NetApp Electronic Library. User Guide for Net 2 Client Version 6.0a
 Net 2 NetApp Electronic Library User Guide for Net 2 Client Version 6.0a Table of Contents 1 INTRODUCTION AND KEY FEATURES... 3 SOME OF THE KEY FEATURES INCLUDE:... 3 INSTALLATION PREREQUISITES:... 3 2
Net 2 NetApp Electronic Library User Guide for Net 2 Client Version 6.0a Table of Contents 1 INTRODUCTION AND KEY FEATURES... 3 SOME OF THE KEY FEATURES INCLUDE:... 3 INSTALLATION PREREQUISITES:... 3 2
FAQs. OneDrive for Business?
 Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Lab 8: Configuring Backups
 CompTIA Security+ Lab Series Lab 8: Configuring Backups CompTIA Security+ Domain 2 - Compliance and Operational Security Objective 2.7: Execute disaster recovery plans and procedures Document Version:
CompTIA Security+ Lab Series Lab 8: Configuring Backups CompTIA Security+ Domain 2 - Compliance and Operational Security Objective 2.7: Execute disaster recovery plans and procedures Document Version:
Installing Remote Desktop Connection
 SETTING UP YOUR REMOTE DESKTOP This section will assist you in setting you Remote Desktop Connection. This will allow you to create an icon for easy access to your virtual desktop. DISCLAIMER: All images
SETTING UP YOUR REMOTE DESKTOP This section will assist you in setting you Remote Desktop Connection. This will allow you to create an icon for easy access to your virtual desktop. DISCLAIMER: All images
CruzNet Secure Set-Up Instructions for Windows Vista
 CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
Passport installation Windows 8 + Firefox
 Passport installation Windows 8 + Firefox OS Version Windows 8 System Type 32-bit and 64-bit Browser name & version Firefox 23 Before you begin Check you have Anti Virus software installed on your computer
Passport installation Windows 8 + Firefox OS Version Windows 8 System Type 32-bit and 64-bit Browser name & version Firefox 23 Before you begin Check you have Anti Virus software installed on your computer
Quick Reference Guide: Business Mail
 : Business Mail TABLE OF CONTENTS GENERAL INFORMATION...2 DETAILED STEPS ON CONFIGURING WINDOWS FOR E-MAIL...2 Set-up For Microsoft Outlook Express...7 Set-up Of Microsoft Outlook On Windows XP...9 PROBLEMS
: Business Mail TABLE OF CONTENTS GENERAL INFORMATION...2 DETAILED STEPS ON CONFIGURING WINDOWS FOR E-MAIL...2 Set-up For Microsoft Outlook Express...7 Set-up Of Microsoft Outlook On Windows XP...9 PROBLEMS
Remote Desktop Solution, (RDS), replacing CITRIX Home Access
 Remote Desktop Solution, (RDS), replacing CITRIX Home Access RDS Applications on a Computer Overview RDS has replaced citrix for remote access at home for College staff and pupils. This does not replace
Remote Desktop Solution, (RDS), replacing CITRIX Home Access RDS Applications on a Computer Overview RDS has replaced citrix for remote access at home for College staff and pupils. This does not replace
User guide. Business Email
 User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
Installing the Virtual Desktop Application (MAC)
 Installing the Virtual Desktop Application (MAC) The folowing instructions will guide you through the process of installing the components necessary to connect in to the NEL B Virtual Desktop environment
Installing the Virtual Desktop Application (MAC) The folowing instructions will guide you through the process of installing the components necessary to connect in to the NEL B Virtual Desktop environment
How to connect to the University of Exeter VPN service
 How to connect to the University of Exeter VPN service *****Important Part of the process of using the VPN service involves the automatic download and installation of Juniper Network Connect software,
How to connect to the University of Exeter VPN service *****Important Part of the process of using the VPN service involves the automatic download and installation of Juniper Network Connect software,
Passport Installation. Windows 8 + Internet Explorer 10
 Passport Installation Windows 8 + Internet Explorer 10 OS Version Windows 8 System Type 32bit and 64bit Browser Name & version Internet Explorer 10 Before you begin Make sure you have Anti Virus software
Passport Installation Windows 8 + Internet Explorer 10 OS Version Windows 8 System Type 32bit and 64bit Browser Name & version Internet Explorer 10 Before you begin Make sure you have Anti Virus software
Remote Access: Internet Explorer
 Introduction: Welcome to the MSVU Remote Access service. The following documentation is intended to assist first time or active users with connecting, authenticating and properly logging out of Remote
Introduction: Welcome to the MSVU Remote Access service. The following documentation is intended to assist first time or active users with connecting, authenticating and properly logging out of Remote
Citrix Remote Access Work Instructions
 Work Instructions Version 1.0 15 January 2010 InTACT Shared Services Centre ACT Department of Treasury Quality Management System Service Management Tools Contents Introduction... 3 Purpose... 3 Scope...
Work Instructions Version 1.0 15 January 2010 InTACT Shared Services Centre ACT Department of Treasury Quality Management System Service Management Tools Contents Introduction... 3 Purpose... 3 Scope...
Download and Install the Citrix Receiver for Mac/Linux
 Download and Install the Citrix Receiver for Mac/Linux NOTE: WOW can only be used with Internet Explorer for Windows. To accommodate WOW customers using Mac or Linux computers, a Citrix solution was developed
Download and Install the Citrix Receiver for Mac/Linux NOTE: WOW can only be used with Internet Explorer for Windows. To accommodate WOW customers using Mac or Linux computers, a Citrix solution was developed
Using SSH Secure File Transfer to Upload Files to Banner
 Using SSH Secure File Transfer to Upload Files to Banner Several Banner processes, including GLP2LMP (Create PopSelect Using File), require you to upload files from your own computer to the computer system
Using SSH Secure File Transfer to Upload Files to Banner Several Banner processes, including GLP2LMP (Create PopSelect Using File), require you to upload files from your own computer to the computer system
BUSINESS CLASS POP3 E-MAIL END USER GUIDE TIME WARNER CABLE BUSINESS SERVICES VERSION 1.0, RELEASE 1.2
 BUSINESS CLASS POP3 E-MAIL END USER GUIDE TIME WARNER CABLE BUSINESS SERVICES VERSION 1.0, RELEASE 1.2 Table of Contents MANAGING E-MAIL ACCOUNTS... 3 GENERIC CONFIGURATION INSTRUCTIONS... 3 POP mail...
BUSINESS CLASS POP3 E-MAIL END USER GUIDE TIME WARNER CABLE BUSINESS SERVICES VERSION 1.0, RELEASE 1.2 Table of Contents MANAGING E-MAIL ACCOUNTS... 3 GENERIC CONFIGURATION INSTRUCTIONS... 3 POP mail...
How to Connect to Berkeley College Virtual Lab Using Windows
 How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
Passport Installation. Windows XP + Internet Explorer 8
 Passport Installation Windows XP + Internet Explorer 8 OS Version Windows XP System Type 32bit or 64bit Browser & version Internet Explorer 8 Before you begin.. Make sure you have Anti Virus software installed
Passport Installation Windows XP + Internet Explorer 8 OS Version Windows XP System Type 32bit or 64bit Browser & version Internet Explorer 8 Before you begin.. Make sure you have Anti Virus software installed
OpenVPN over SSH tunneling
 Step 1: What you'll need before starting OpenVPN over SSH tunneling You're going to need a couple of things in order to create an SSH tunnel that you can use as a SOCKS 5 proxy for tunneling OpenVPN or
Step 1: What you'll need before starting OpenVPN over SSH tunneling You're going to need a couple of things in order to create an SSH tunnel that you can use as a SOCKS 5 proxy for tunneling OpenVPN or
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources
 Akin Gump Strauss Hauer & Feld LLP Remote Access Resources Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2013 Akin Gump Strauss Hauer & Feld LLP Checkpoint VPN (Firm
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2013 Akin Gump Strauss Hauer & Feld LLP Checkpoint VPN (Firm
SSL VPN Support Guide
 P a g e 1 SSL VPN Support Guide Revision date: 5/4/10 P a g e 2 Table of Contents Before calling the Support Desk..pg 3 What the Support Desk can assist users with. pg 4 Instructions for PC users (Internet
P a g e 1 SSL VPN Support Guide Revision date: 5/4/10 P a g e 2 Table of Contents Before calling the Support Desk..pg 3 What the Support Desk can assist users with. pg 4 Instructions for PC users (Internet
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP with Service Pack 2 Your wireless card must support 802.1x, AES, and WPA2. Windows XP with service pack 2, it is recommended
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP with Service Pack 2 Your wireless card must support 802.1x, AES, and WPA2. Windows XP with service pack 2, it is recommended
FAQs. OneDrive for Business?
 Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
IMAP and SMTP Setup in Email Clients
 IMAP and SMTP Setup in Email Clients Configuring an Email Client for IMAP Configuring an Email Client for the SMTP Server Overview Internet Message Access Protocol (IMAP), or a remote connection through
IMAP and SMTP Setup in Email Clients Configuring an Email Client for IMAP Configuring an Email Client for the SMTP Server Overview Internet Message Access Protocol (IMAP), or a remote connection through
Remote Desktop Services
 Remote Desktop Services AMERICAN INSTITUTES FOR RESEARCH AIR REMOTE DESKTOP SERVICES (RDS) GUIDE Overview Welcome to AIR Remote Desktop Services! AIR Remote Desktop Services can be accessed from a Windows
Remote Desktop Services AMERICAN INSTITUTES FOR RESEARCH AIR REMOTE DESKTOP SERVICES (RDS) GUIDE Overview Welcome to AIR Remote Desktop Services! AIR Remote Desktop Services can be accessed from a Windows
NAS 109 Using NAS with Linux
 NAS 109 Using NAS with Linux Access the files on your NAS using Linux A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Use Linux to access files on
NAS 109 Using NAS with Linux Access the files on your NAS using Linux A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Use Linux to access files on
NAS 208 WebDAV A Secure File Sharing Alternative to FTP
 NAS 208 WebDAV A Secure File Sharing Alternative to FTP Connect to your NAS via WebDAV A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Have a basic
NAS 208 WebDAV A Secure File Sharing Alternative to FTP Connect to your NAS via WebDAV A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Have a basic
Internet Explorer 7 for Windows XP: Obtaining MIT Certificates
 Internet Explorer 7 for Windows XP: Obtaining MIT Certificates Overview In order to use secure web services at MIT, you will need to obtain two types of MIT web certificates: MIT Certificate Authority
Internet Explorer 7 for Windows XP: Obtaining MIT Certificates Overview In order to use secure web services at MIT, you will need to obtain two types of MIT web certificates: MIT Certificate Authority
QUANTIFY INSTALLATION GUIDE
 QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
All existing accounts will be listed. 2. Click Add and select Mail to add a new E-mail account (see Figure 2). Figure 1. Figure 2
 Microsoft Outlook Express 5.x, 6.0 This section describes how to configure Outlook Express to access POP E-mail. 1. Click Tools and select Accounts from the pull-down menu (see Figure 1). Figure 1 All
Microsoft Outlook Express 5.x, 6.0 This section describes how to configure Outlook Express to access POP E-mail. 1. Click Tools and select Accounts from the pull-down menu (see Figure 1). Figure 1 All
How to remotely access your Virtual Desktop from outside the college using VMware View Client. How to guide
 How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
How to use SURA in three simple steps:
 How to use SURA in three simple steps: Most of SURA s functionality can be accessed through these three steps. 1) Download SURA to your computer Go to the SU Downloads page to obtain the SURA utility.
How to use SURA in three simple steps: Most of SURA s functionality can be accessed through these three steps. 1) Download SURA to your computer Go to the SU Downloads page to obtain the SURA utility.
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems
 SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems What is SSH?: SSH is an application that protects the TCP/IP connections between two computers. The software
SSH Secure Client (Telnet & SFTP) Installing & Using SSH Secure Shell for Windows Operation Systems What is SSH?: SSH is an application that protects the TCP/IP connections between two computers. The software
MODEM AND DIAL-UP. Installation/Configuration (Windows 95/98/Me/NT/2000/XP)
 MODEM AND DIAL-UP Installation/Configuration (Windows 95/98/Me/NT/2000/XP) Iridium Satellite LLC 1 February 22, 2006 --------------------------------------------------------------------------------------------------------------------------------------------TABLE
MODEM AND DIAL-UP Installation/Configuration (Windows 95/98/Me/NT/2000/XP) Iridium Satellite LLC 1 February 22, 2006 --------------------------------------------------------------------------------------------------------------------------------------------TABLE
Patching the Windows 2000 Server Operating System on S8100 Media Servers, IP600 Communications Servers, & DEFNITY ONE Communications Systems
 Patching the Windows 2000 Server Operating System on S8100 Media Servers, IP600 Communications Servers, & DEFNITY ONE Communications Systems Abstract This document provides guidance on how to apply Microsoft
Patching the Windows 2000 Server Operating System on S8100 Media Servers, IP600 Communications Servers, & DEFNITY ONE Communications Systems Abstract This document provides guidance on how to apply Microsoft
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client
 Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Remote Access Using The New York Eye & Ear Infirmary of Mount Sinai Secure Web VPN
 Remote Access Using The New York Eye & Ear Infirmary of Mount Sinai Secure Web VPN OVERVIEW The New York Eye & Ear Infirmary of Mount Sinai Remote Access (VPN) home page allows remote access to the Infirmary
Remote Access Using The New York Eye & Ear Infirmary of Mount Sinai Secure Web VPN OVERVIEW The New York Eye & Ear Infirmary of Mount Sinai Remote Access (VPN) home page allows remote access to the Infirmary
Connecting and Setting Up Your Laptop Computer
 CHAPTER 3 Connecting and Setting Up Your Laptop Computer This chapter explains how to connect your laptop to the Cisco Unified MeetingPlace system and how to set up your laptop so that you can use HyperTerminal.
CHAPTER 3 Connecting and Setting Up Your Laptop Computer This chapter explains how to connect your laptop to the Cisco Unified MeetingPlace system and how to set up your laptop so that you can use HyperTerminal.
Steps for using MagicConnect
 Getting Started Getting Started MagicConnect is a remote access service that allows you safe remote access to a target device from your remote device. What is a remote device? It is a Windows device, iphone/ipad,
Getting Started Getting Started MagicConnect is a remote access service that allows you safe remote access to a target device from your remote device. What is a remote device? It is a Windows device, iphone/ipad,
Setting up Remote Desktop
 Setting up Remote Desktop Terminology: Host PC the computer you want to access remotely; the destination Client PC the computer you are actually using to access another PC; the source IP Address the numerical
Setting up Remote Desktop Terminology: Host PC the computer you want to access remotely; the destination Client PC the computer you are actually using to access another PC; the source IP Address the numerical
VCL Access. VCL provides access to Linux and Windows 7 Virtual Machines. Users will only see those images that they are authorized to access.
 What is VCL? VCL (Virtual Computer Lab) is a service running on servers in IIT s datacenter that enables users to schedule and connect to virtual desktops running specific academic software applications
What is VCL? VCL (Virtual Computer Lab) is a service running on servers in IIT s datacenter that enables users to schedule and connect to virtual desktops running specific academic software applications
Easy Setup Guide for the Sony Network Camera
 -878-191-11 (1) Easy Setup Guide for the Sony Network Camera For setup, a computer running the Microsoft Windows Operating System is required. For monitoring camera images, Microsoft Internet Explorer
-878-191-11 (1) Easy Setup Guide for the Sony Network Camera For setup, a computer running the Microsoft Windows Operating System is required. For monitoring camera images, Microsoft Internet Explorer
Driver Upgrade Instructions
 Driver Upgrade Instructions Table of Content Installing updated drivers in Microsoft Windows 2 Uninstall Procedure 2 Uninstall Procedure for Windows 7 3 Install Procedure 4 Installing updated drivers in
Driver Upgrade Instructions Table of Content Installing updated drivers in Microsoft Windows 2 Uninstall Procedure 2 Uninstall Procedure for Windows 7 3 Install Procedure 4 Installing updated drivers in
CompleteView Admin Console Users Guide. Version 3.0.0 Revised: 02/15/2008
 CompleteView Admin Console Users Guide Version 3.0.0 Revised: 02/15/2008 Table Of Contents Configuration... 3 Starting the Admin Console... 3 Adding a Server... 4 Monitoring Server Status... 6 Menus...
CompleteView Admin Console Users Guide Version 3.0.0 Revised: 02/15/2008 Table Of Contents Configuration... 3 Starting the Admin Console... 3 Adding a Server... 4 Monitoring Server Status... 6 Menus...
educ Office 365 email: Remove & create new Outlook profile
 Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Yale Software Library http://www.yale.edu/software/
 e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, [email protected] Remote Desktop General overview With Remote Desktop, you get full access
e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, [email protected] Remote Desktop General overview With Remote Desktop, you get full access
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using Virtual Machines
 Using Virtual Machines We will use VMs in CIT 130 so that you can access both a Windows 7 and a Linux machine. You will be able to access these from on and off campus (off campus access will require that
Using Virtual Machines We will use VMs in CIT 130 so that you can access both a Windows 7 and a Linux machine. You will be able to access these from on and off campus (off campus access will require that
How do I find the Wireless Security Information in Windows XP, Vista, 7, 8 or 8.1?
 Description of Problem 100000025093 How do I find the Wireless Security Information in Windows XP, Vista, 7, 8 or 8.1? Description of Solution 200000032138 These steps may help you locate your wireless
Description of Problem 100000025093 How do I find the Wireless Security Information in Windows XP, Vista, 7, 8 or 8.1? Description of Solution 200000032138 These steps may help you locate your wireless
Adafruit's Raspberry Pi Lesson 6. Using SSH
 Adafruit's Raspberry Pi Lesson 6. Using SSH Created by Simon Monk Last updated on 2015-04-09 03:47:50 PM EDT Guide Contents Guide Contents Overview Enabling SSH Using SSH on a Mac or Linux SSH under Windows
Adafruit's Raspberry Pi Lesson 6. Using SSH Created by Simon Monk Last updated on 2015-04-09 03:47:50 PM EDT Guide Contents Guide Contents Overview Enabling SSH Using SSH on a Mac or Linux SSH under Windows
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
The initial set up takes a few steps, but then each time you want to connect it is just a two set process.
 Remote Access to your Desktop using VPN Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from
Remote Access to your Desktop using VPN Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from
