Discussion Session 9. CS/ECE 552 Ramkumar Ravi 26 Mar 2012
|
|
|
- Malcolm Cox
- 9 years ago
- Views:
Transcription
1 Discussion Session 9 CS/ECE 55 Ramkumar Ravi 6 Mar CS/ECE 55, Spring
2 Mark your calendar IMPORTANT DATES TODAY 4/ Spring break 4/ HW5 due 4/ Project Demo HW5 discussion Error in mem_system_randbench.v (will be corrected and uploaded in course webpage) Other test-bench modules look OK Modification to problem 5 Discussion of a sample state-machine and show sample code (if time permits)
3 Problems and 4 Cache Parameters SIZE = total amount of cache data storage, in bytes BLOCKSIZE = total number of bytes in a single ASSOC = associativity, i.e., # of lines in a set Equation for # of cache lines in cache = size / size Equation for # of sets in cache = size / (size * associativity) You may need this for few of the problems in this HW
4 Address Fields Tag field is compared to the (s) of the ed cache line(s). If it matches, is there (hit). If it doesn t match, is not there (miss). Used to look up a set, whose lines contain one or more memory s. (The # of lines per set is the associativity.) Once a is found, the selects a particular byte or word of data in the.
5 Address Fields (cont.) Widths of address fields (# bits) # bits = log (# sets) # bits = log ( size) # bits = # bits # bits Assuming -bit addresses
6 Example of cache operation Example: Processor accesses a 56-byte direct-mapped cache, which has -byte lines, with the following sequence of addresses. Show contents of the cache after each access. Count # of hits and # of replacements. # bits = log (# sets) = log (8) = # bits = log ( size) = log ( bytes) = 5 # bits = total # address bits # bits # bits = bits bits 5 bits = 4 Thus, the top 6 nibbles (4 bits) of address form the and lower nibbles (8 bits) of address form the and fields.
7 Example address sequence Address (hex) Tag (hex) Index & bits (binary) xff4e xbeef5c xff4e xff4e8 x78 x8e x64 x55c x544 Index (decimal) Comment
8 Analysis of results follows next Address (hex) Tag (hex) Index & bits (binary) Index (decimal) Comment xff4e xff4 7 Miss xbeef5c xbeef Miss xff4e xff4 7 Hit xff4e8 xff4 7 Hit x78 x Miss x8e x8 7 Miss+Replace x64 x Hit x55c x5 Miss+Replace x544 x5 Hit
9 FF4 7 Data FF4 FF4 BEEF FF4 FF Get from memory (slow)
10 BEEF Data BEEF FF4 FF4 BEEF FF4 FF Get from memory (slow)
11 FF4 7 Data BEEF FF4 FF4 BEEF FF4 FF
12 FF4 7 Data BEEF FF4 FF4 BEEF FF4 FF
13 Data BEEF FF4 FF4 BEEF FF4 FF Get from memory (slow)
14 Data BEEF 8 FF4 FF4 BEEF FF4 FF Get from Memory (slow)
15 BEEF 8 Data FF4 BEEF FF4 FF
16 BEEF 8 Data FF4 BEEF FF4 FF Get from memory (slow)
17 Data 5 8 FF4 BEEF FF4 FF
18 Set-Associative Example Example: Processor accesses a 56-byte -way set-associative cache, which has line size of bytes, with the following sequence of addresses. Show contents of cache after each access. Count # of hits and # of replacements. # bits = log (# sets) = log (4) = # bits = log ( size) = log ( bytes) = 5 # bits = total # address bits # bits # bits = bits bits 5 bits = 5
19 Address (hex) Tag (hex) Index & bits (binary) Index (decimal) Comment xff4e xfe8 Miss xbeef5c x7dde Miss x78 x Miss xff4e xfe8 Hit x78 x Hit x8e x47 Miss/Replace x64 x Hit
20 FE8 5 FE8 Data not shown for convenience
21 DDE 7DDE 5 FE8 Data not shown for convenience
22 DDE 5 FE8 Data not shown for convenience
23 FE8 7DDE 5 FE8 Data not shown for convenience
24 DDE 5 FE8 Data not shown for convenience
25 DDE 47 5 FE8 Data not shown for convenience
26 DDE 5 47 Data not shown for convenience
27 PROBLEM 5 Total cache storage (capacity) (64-byte s) * (5 sets) * (# of ways) Total number of bits Tag size = 4 bits - # bits - # bits Block size = valid + dirty + LRU + + data
28 PROBLEMS and Sample FSM presentation Understanding the requirements of the problem
Outline. Cache Parameters. Lecture 5 Cache Operation
 Lecture Cache Operation ECE / Fall Edward F. Gehringer Based on notes by Drs. Eric Rotenberg & Tom Conte of NCSU Outline Review of cache parameters Example of operation of a direct-mapped cache. Example
Lecture Cache Operation ECE / Fall Edward F. Gehringer Based on notes by Drs. Eric Rotenberg & Tom Conte of NCSU Outline Review of cache parameters Example of operation of a direct-mapped cache. Example
The Quest for Speed - Memory. Cache Memory. A Solution: Memory Hierarchy. Memory Hierarchy
 The Quest for Speed - Memory Cache Memory CSE 4, Spring 25 Computer Systems http://www.cs.washington.edu/4 If all memory accesses (IF/lw/sw) accessed main memory, programs would run 20 times slower And
The Quest for Speed - Memory Cache Memory CSE 4, Spring 25 Computer Systems http://www.cs.washington.edu/4 If all memory accesses (IF/lw/sw) accessed main memory, programs would run 20 times slower And
We r e going to play Final (exam) Jeopardy! "Answers:" "Questions:" - 1 -
 . (0 pts) We re going to play Final (exam) Jeopardy! Associate the following answers with the appropriate question. (You are given the "answers": Pick the "question" that goes best with each "answer".)
. (0 pts) We re going to play Final (exam) Jeopardy! Associate the following answers with the appropriate question. (You are given the "answers": Pick the "question" that goes best with each "answer".)
Base Conversion written by Cathy Saxton
 Base Conversion written by Cathy Saxton 1. Base 10 In base 10, the digits, from right to left, specify the 1 s, 10 s, 100 s, 1000 s, etc. These are powers of 10 (10 x ): 10 0 = 1, 10 1 = 10, 10 2 = 100,
Base Conversion written by Cathy Saxton 1. Base 10 In base 10, the digits, from right to left, specify the 1 s, 10 s, 100 s, 1000 s, etc. These are powers of 10 (10 x ): 10 0 = 1, 10 1 = 10, 10 2 = 100,
Table 1 below is a complete list of MPTH commands with descriptions. Table 1 : MPTH Commands. Command Name Code Setting Value Description
 MPTH: Commands Table 1 below is a complete list of MPTH commands with descriptions. Note: Commands are three bytes long, Command Start Byte (default is 128), Command Code, Setting value. Table 1 : MPTH
MPTH: Commands Table 1 below is a complete list of MPTH commands with descriptions. Note: Commands are three bytes long, Command Start Byte (default is 128), Command Code, Setting value. Table 1 : MPTH
Counting in base 10, 2 and 16
 Counting in base 10, 2 and 16 1. Binary Numbers A super-important fact: (Nearly all) Computers store all information in the form of binary numbers. Numbers, characters, images, music files --- all of these
Counting in base 10, 2 and 16 1. Binary Numbers A super-important fact: (Nearly all) Computers store all information in the form of binary numbers. Numbers, characters, images, music files --- all of these
Useful Number Systems
 Useful Number Systems Decimal Base = 10 Digit Set = {0, 1, 2, 3, 4, 5, 6, 7, 8, 9} Binary Base = 2 Digit Set = {0, 1} Octal Base = 8 = 2 3 Digit Set = {0, 1, 2, 3, 4, 5, 6, 7} Hexadecimal Base = 16 = 2
Useful Number Systems Decimal Base = 10 Digit Set = {0, 1, 2, 3, 4, 5, 6, 7, 8, 9} Binary Base = 2 Digit Set = {0, 1} Octal Base = 8 = 2 3 Digit Set = {0, 1, 2, 3, 4, 5, 6, 7} Hexadecimal Base = 16 = 2
Board Notes on Virtual Memory
 Board Notes on Virtual Memory Part A: Why Virtual Memory? - Letʼs user program size exceed the size of the physical address space - Supports protection o Donʼt know which program might share memory at
Board Notes on Virtual Memory Part A: Why Virtual Memory? - Letʼs user program size exceed the size of the physical address space - Supports protection o Donʼt know which program might share memory at
CS101 Lecture 11: Number Systems and Binary Numbers. Aaron Stevens 14 February 2011
 CS101 Lecture 11: Number Systems and Binary Numbers Aaron Stevens 14 February 2011 1 2 1 3!!! MATH WARNING!!! TODAY S LECTURE CONTAINS TRACE AMOUNTS OF ARITHMETIC AND ALGEBRA PLEASE BE ADVISED THAT CALCULTORS
CS101 Lecture 11: Number Systems and Binary Numbers Aaron Stevens 14 February 2011 1 2 1 3!!! MATH WARNING!!! TODAY S LECTURE CONTAINS TRACE AMOUNTS OF ARITHMETIC AND ALGEBRA PLEASE BE ADVISED THAT CALCULTORS
Outlook 2003/2007 NK2 File Format and Developer Guidelines
 Outlook 2003/2007 NK2 File Format and Developer Guidelines This post explains how Microsoft Office Outlook 2007 interacts with the nickname cache file, also known as the.nk2 file. The.nk2 file is where
Outlook 2003/2007 NK2 File Format and Developer Guidelines This post explains how Microsoft Office Outlook 2007 interacts with the nickname cache file, also known as the.nk2 file. The.nk2 file is where
The Big Picture. Cache Memory CSE 675.02. Memory Hierarchy (1/3) Disk
 The Big Picture Cache Memory CSE 5.2 Computer Processor Memory (active) (passive) Control (where ( brain ) programs, Datapath data live ( brawn ) when running) Devices Input Output Keyboard, Mouse Disk,
The Big Picture Cache Memory CSE 5.2 Computer Processor Memory (active) (passive) Control (where ( brain ) programs, Datapath data live ( brawn ) when running) Devices Input Output Keyboard, Mouse Disk,
CS201: Architecture and Assembly Language
 CS201: Architecture and Assembly Language Lecture Three Brendan Burns CS201: Lecture Three p.1/27 Arithmetic for computers Previously we saw how we could represent unsigned numbers in binary and how binary
CS201: Architecture and Assembly Language Lecture Three Brendan Burns CS201: Lecture Three p.1/27 Arithmetic for computers Previously we saw how we could represent unsigned numbers in binary and how binary
GW-7552 PRIFIBUS/MODBUS GATEWAY
 GW-7552 PRIFIBUS/MODBUS GATEWAY Quick Start User Guide 1. Introduction This manual introduces the GW-7552's basic setting and operating quickly, the user can refer to the user manual in the ICP DAS companion
GW-7552 PRIFIBUS/MODBUS GATEWAY Quick Start User Guide 1. Introduction This manual introduces the GW-7552's basic setting and operating quickly, the user can refer to the user manual in the ICP DAS companion
Decimal to Binary Conversion
 Decimal to Binary Conversion A tool that makes the conversion of decimal values to binary values simple is the following table. The first row is created by counting right to left from one to eight, for
Decimal to Binary Conversion A tool that makes the conversion of decimal values to binary values simple is the following table. The first row is created by counting right to left from one to eight, for
1. Give the 16 bit signed (twos complement) representation of the following decimal numbers, and convert to hexadecimal:
 Exercises 1 - number representations Questions 1. Give the 16 bit signed (twos complement) representation of the following decimal numbers, and convert to hexadecimal: (a) 3012 (b) - 435 2. For each of
Exercises 1 - number representations Questions 1. Give the 16 bit signed (twos complement) representation of the following decimal numbers, and convert to hexadecimal: (a) 3012 (b) - 435 2. For each of
Technical Support Bulletin Nr.18 Modbus Tips
 Technical Support Bulletin Nr.18 Modbus Tips Contents! Definitions! Implemented commands! Examples of commands or frames! Calculating the logical area! Reading a signed variable! Example of commands supported
Technical Support Bulletin Nr.18 Modbus Tips Contents! Definitions! Implemented commands! Examples of commands or frames! Calculating the logical area! Reading a signed variable! Example of commands supported
18-548/15-548 Associativity 9/16/98. 7 Associativity. 18-548/15-548 Memory System Architecture Philip Koopman September 16, 1998
 7 Associativity 18-548/15-548 Memory System Architecture Philip Koopman September 16, 1998 Required Reading: Cragon pg. 166-174 Assignments By next class read about data management policies: Cragon 2.2.4-2.2.6,
7 Associativity 18-548/15-548 Memory System Architecture Philip Koopman September 16, 1998 Required Reading: Cragon pg. 166-174 Assignments By next class read about data management policies: Cragon 2.2.4-2.2.6,
ELEG3924 Microprocessor Ch.7 Programming In C
 Department of Electrical Engineering University of Arkansas ELEG3924 Microprocessor Ch.7 Programming In C Dr. Jingxian Wu [email protected] OUTLINE 2 Data types and time delay I/O programming and Logic operations
Department of Electrical Engineering University of Arkansas ELEG3924 Microprocessor Ch.7 Programming In C Dr. Jingxian Wu [email protected] OUTLINE 2 Data types and time delay I/O programming and Logic operations
ACR122 NFC Contactless Smart Card Reader
 Datenblatt / Specifications ACR122 NFC Contactless Smart Card Reader Table of Contents 1. Introduction... 3 1.1. USB Interface... 3 2. Implementation... 4 2.1. Smart Card Reader Interface Overview... 5
Datenblatt / Specifications ACR122 NFC Contactless Smart Card Reader Table of Contents 1. Introduction... 3 1.1. USB Interface... 3 2. Implementation... 4 2.1. Smart Card Reader Interface Overview... 5
Homework # 2. Solutions. 4.1 What are the differences among sequential access, direct access, and random access?
 ECE337 / CS341, Fall 2005 Introduction to Computer Architecture and Organization Instructor: Victor Manuel Murray Herrera Date assigned: 09/19/05, 05:00 PM Due back: 09/30/05, 8:00 AM Homework # 2 Solutions
ECE337 / CS341, Fall 2005 Introduction to Computer Architecture and Organization Instructor: Victor Manuel Murray Herrera Date assigned: 09/19/05, 05:00 PM Due back: 09/30/05, 8:00 AM Homework # 2 Solutions
CS 61C: Great Ideas in Computer Architecture Virtual Memory Cont.
 CS 61C: Great Ideas in Computer Architecture Virtual Memory Cont. Instructors: Vladimir Stojanovic & Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/ 1 Bare 5-Stage Pipeline Physical Address PC Inst.
CS 61C: Great Ideas in Computer Architecture Virtual Memory Cont. Instructors: Vladimir Stojanovic & Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/ 1 Bare 5-Stage Pipeline Physical Address PC Inst.
Memory ICS 233. Computer Architecture and Assembly Language Prof. Muhamed Mudawar
 Memory ICS 233 Computer Architecture and Assembly Language Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline Random
Memory ICS 233 Computer Architecture and Assembly Language Prof. Muhamed Mudawar College of Computer Sciences and Engineering King Fahd University of Petroleum and Minerals Presentation Outline Random
Chapter 7 Lab - Decimal, Binary, Octal, Hexadecimal Numbering Systems
 Chapter 7 Lab - Decimal, Binary, Octal, Hexadecimal Numbering Systems This assignment is designed to familiarize you with different numbering systems, specifically: binary, octal, hexadecimal (and decimal)
Chapter 7 Lab - Decimal, Binary, Octal, Hexadecimal Numbering Systems This assignment is designed to familiarize you with different numbering systems, specifically: binary, octal, hexadecimal (and decimal)
Computer Architecture
 Cache Memory Gábor Horváth 2016. április 27. Budapest associate professor BUTE Dept. Of Networked Systems and Services [email protected] It is the memory,... The memory is a serious bottleneck of Neumann
Cache Memory Gábor Horváth 2016. április 27. Budapest associate professor BUTE Dept. Of Networked Systems and Services [email protected] It is the memory,... The memory is a serious bottleneck of Neumann
Experiment # 9. Clock generator circuits & Counters. Eng. Waleed Y. Mousa
 Experiment # 9 Clock generator circuits & Counters Eng. Waleed Y. Mousa 1. Objectives: 1. Understanding the principles and construction of Clock generator. 2. To be familiar with clock pulse generation
Experiment # 9 Clock generator circuits & Counters Eng. Waleed Y. Mousa 1. Objectives: 1. Understanding the principles and construction of Clock generator. 2. To be familiar with clock pulse generation
Number of bits needed to address hosts 8
 Advanced Subnetting Example 1: Your ISP has assigned you a Class C network address of 198.47.212.0. You have 3 networks in your company with the largest containing 134 hosts. You need to figure out if
Advanced Subnetting Example 1: Your ISP has assigned you a Class C network address of 198.47.212.0. You have 3 networks in your company with the largest containing 134 hosts. You need to figure out if
WIZnet S2E (Serial-to-Ethernet) Device s Configuration Tool Programming Guide
 WIZnet S2E (Serial-to-Ethernet) Device s Configuration Tool Programming Guide Rev 0.2 This document describes how to make your own Configuration Tool for WIZ100SR, WIZ105SR and WIZ110SR of WIZnet. And
WIZnet S2E (Serial-to-Ethernet) Device s Configuration Tool Programming Guide Rev 0.2 This document describes how to make your own Configuration Tool for WIZ100SR, WIZ105SR and WIZ110SR of WIZnet. And
Internet Addresses (You should read Chapter 4 in Forouzan)
 Internet Addresses (You should read Chapter 4 in Forouzan) IP Address is 32 Bits Long Conceptually the address is the pair (NETID, HOSTID) Addresses are assigned by the internet company for assignment
Internet Addresses (You should read Chapter 4 in Forouzan) IP Address is 32 Bits Long Conceptually the address is the pair (NETID, HOSTID) Addresses are assigned by the internet company for assignment
Binary Representation
 Binary Representation The basis of all digital data is binary representation. Binary - means two 1, 0 True, False Hot, Cold On, Off We must tbe able to handle more than just values for real world problems
Binary Representation The basis of all digital data is binary representation. Binary - means two 1, 0 True, False Hot, Cold On, Off We must tbe able to handle more than just values for real world problems
Fingerprint Based Biometric Attendance System
 Fingerprint Based Biometric Attendance System Team Members Vaibhav Shukla Ali Kazmi Amit Waghmare Ravi Ranka Email Id [email protected] [email protected] Contact Numbers 8097031667 9167689265
Fingerprint Based Biometric Attendance System Team Members Vaibhav Shukla Ali Kazmi Amit Waghmare Ravi Ranka Email Id [email protected] [email protected] Contact Numbers 8097031667 9167689265
Nemo 96HD/HD+ MODBUS
 18/12/12 Pagina 1 di 28 MULTIFUNCTION FIRMWARE 2.30 Nemo 96HD/HD+ MODBUS COMMUNICATION PROTOCOL CONTENTS 1.0 ABSTRACT 2.0 DATA MESSAGE DESCRIPTION 2.1 Parameters description 2.2 Data format 2.3 Description
18/12/12 Pagina 1 di 28 MULTIFUNCTION FIRMWARE 2.30 Nemo 96HD/HD+ MODBUS COMMUNICATION PROTOCOL CONTENTS 1.0 ABSTRACT 2.0 DATA MESSAGE DESCRIPTION 2.1 Parameters description 2.2 Data format 2.3 Description
Lecture 2. Binary and Hexadecimal Numbers
 Lecture 2 Binary and Hexadecimal Numbers Purpose: Review binary and hexadecimal number representations Convert directly from one base to another base Review addition and subtraction in binary representations
Lecture 2 Binary and Hexadecimal Numbers Purpose: Review binary and hexadecimal number representations Convert directly from one base to another base Review addition and subtraction in binary representations
Counters. Present State Next State A B A B 0 0 0 1 0 1 1 0 1 0 1 1 1 1 0 0
 ounter ounters ounters are a specific type of sequential circuit. Like registers, the state, or the flip-flop values themselves, serves as the output. The output value increases by one on each clock cycle.
ounter ounters ounters are a specific type of sequential circuit. Like registers, the state, or the flip-flop values themselves, serves as the output. The output value increases by one on each clock cycle.
Numbering Systems. InThisAppendix...
 G InThisAppendix... Introduction Binary Numbering System Hexadecimal Numbering System Octal Numbering System Binary Coded Decimal (BCD) Numbering System Real (Floating Point) Numbering System BCD/Binary/Decimal/Hex/Octal
G InThisAppendix... Introduction Binary Numbering System Hexadecimal Numbering System Octal Numbering System Binary Coded Decimal (BCD) Numbering System Real (Floating Point) Numbering System BCD/Binary/Decimal/Hex/Octal
SRF08 Ultra sonic range finder Technical Specification
 SRF08 Ultra sonic range finder Technical Specification Communication with the SRF08 ultrasonic rangefinder is via the I2C bus. This is available on popular controllers such as the OOPic and Stamp BS2p,
SRF08 Ultra sonic range finder Technical Specification Communication with the SRF08 ultrasonic rangefinder is via the I2C bus. This is available on popular controllers such as the OOPic and Stamp BS2p,
Machine Architecture and Number Systems. Major Computer Components. Schematic Diagram of a Computer. The CPU. The Bus. Main Memory.
 1 Topics Machine Architecture and Number Systems Major Computer Components Bits, Bytes, and Words The Decimal Number System The Binary Number System Converting from Decimal to Binary Major Computer Components
1 Topics Machine Architecture and Number Systems Major Computer Components Bits, Bytes, and Words The Decimal Number System The Binary Number System Converting from Decimal to Binary Major Computer Components
Dualog Connection Suite Hardware and Software Requirements
 Dualog Connection Suite Hardware and Software Requirements Author Kristian Olsen Date 29.Mar 2012 Description Revision Number 2.0 Environmental requirements and recommendations running Dualog Connection
Dualog Connection Suite Hardware and Software Requirements Author Kristian Olsen Date 29.Mar 2012 Description Revision Number 2.0 Environmental requirements and recommendations running Dualog Connection
Memory is implemented as an array of electronic switches
 Memory Structure Memory is implemented as an array of electronic switches Each switch can be in one of two states 0 or 1, on or off, true or false, purple or gold, sitting or standing BInary digits (bits)
Memory Structure Memory is implemented as an array of electronic switches Each switch can be in one of two states 0 or 1, on or off, true or false, purple or gold, sitting or standing BInary digits (bits)
Chapter 5 Instructor's Manual
 The Essentials of Computer Organization and Architecture Linda Null and Julia Lobur Jones and Bartlett Publishers, 2003 Chapter 5 Instructor's Manual Chapter Objectives Chapter 5, A Closer Look at Instruction
The Essentials of Computer Organization and Architecture Linda Null and Julia Lobur Jones and Bartlett Publishers, 2003 Chapter 5 Instructor's Manual Chapter Objectives Chapter 5, A Closer Look at Instruction
ENGG*44200 Real Time System Design Lab3 Implement VoIP on ARM Outline
 ENGG*44200 Real Time System Design Lab3 Implement VoIP on ARM 1 Outline Features of VoIP IP Communication Device Examples Phone Protocol of the Lab 2 VoIP Voice Calls are transmitted over Packet Switched
ENGG*44200 Real Time System Design Lab3 Implement VoIP on ARM 1 Outline Features of VoIP IP Communication Device Examples Phone Protocol of the Lab 2 VoIP Voice Calls are transmitted over Packet Switched
UM0853 User manual. 1 Introduction. M24LRxx application software user guide
 User manual M24LRxx application software user guide 1 Introduction The purpose of this user manual is to teach how to use the M24LRxx tool kit with the M24LRxx_Application_Software. It describes the M24LRxx_Application_Software
User manual M24LRxx application software user guide 1 Introduction The purpose of this user manual is to teach how to use the M24LRxx tool kit with the M24LRxx_Application_Software. It describes the M24LRxx_Application_Software
x10* CP290 HOME CONTROL INTERFACE PROGRAMMING GUIDE FOR ADVANCED PROGRAMMERS
 x10* CP290 HOME CONTROL INTERFACE PROGRAMMING GUIDE FOR ADVANCED PROGRAMMERS 1 TABLE OF CONTENTS 3. Introduction. 6. Programming. 7. RS-232 connections. a. Byte format. 9. Download Base Housecode. IO.
x10* CP290 HOME CONTROL INTERFACE PROGRAMMING GUIDE FOR ADVANCED PROGRAMMERS 1 TABLE OF CONTENTS 3. Introduction. 6. Programming. 7. RS-232 connections. a. Byte format. 9. Download Base Housecode. IO.
Computer Organization and Architecture. Characteristics of Memory Systems. Chapter 4 Cache Memory. Location CPU Registers and control unit memory
 Computer Organization and Architecture Chapter 4 Cache Memory Characteristics of Memory Systems Note: Appendix 4A will not be covered in class, but the material is interesting reading and may be used in
Computer Organization and Architecture Chapter 4 Cache Memory Characteristics of Memory Systems Note: Appendix 4A will not be covered in class, but the material is interesting reading and may be used in
Section 1.4 Place Value Systems of Numeration in Other Bases
 Section.4 Place Value Systems of Numeration in Other Bases Other Bases The Hindu-Arabic system that is used in most of the world today is a positional value system with a base of ten. The simplest reason
Section.4 Place Value Systems of Numeration in Other Bases Other Bases The Hindu-Arabic system that is used in most of the world today is a positional value system with a base of ten. The simplest reason
14.1 Rent-or-buy problem
 CS787: Advanced Algorithms Lecture 14: Online algorithms We now shift focus to a different kind of algorithmic problem where we need to perform some optimization without knowing the input in advance. Algorithms
CS787: Advanced Algorithms Lecture 14: Online algorithms We now shift focus to a different kind of algorithmic problem where we need to perform some optimization without knowing the input in advance. Algorithms
Binary, Hexadecimal, Octal, and BCD Numbers
 23CH_PHCalter_TMSETE_949118 23/2/2007 1:37 PM Page 1 Binary, Hexadecimal, Octal, and BCD Numbers OBJECTIVES When you have completed this chapter, you should be able to: Convert between binary and decimal
23CH_PHCalter_TMSETE_949118 23/2/2007 1:37 PM Page 1 Binary, Hexadecimal, Octal, and BCD Numbers OBJECTIVES When you have completed this chapter, you should be able to: Convert between binary and decimal
Lab 17: Building a 4-Digit 7-Segment LED Decoder
 Phys2303 L.A. Bumm [Nexys 1.1.2] Lab 17 (p1) Lab 17: Building a 4-Digit 7-Segment LED Decoder In this lab your will make 4 test circuits, the 4-digit 7-segment decoder, and demonstration circuit using
Phys2303 L.A. Bumm [Nexys 1.1.2] Lab 17 (p1) Lab 17: Building a 4-Digit 7-Segment LED Decoder In this lab your will make 4 test circuits, the 4-digit 7-segment decoder, and demonstration circuit using
Lecture 11: Number Systems
 Lecture 11: Number Systems Numeric Data Fixed point Integers (12, 345, 20567 etc) Real fractions (23.45, 23., 0.145 etc.) Floating point such as 23. 45 e 12 Basically an exponent representation Any number
Lecture 11: Number Systems Numeric Data Fixed point Integers (12, 345, 20567 etc) Real fractions (23.45, 23., 0.145 etc.) Floating point such as 23. 45 e 12 Basically an exponent representation Any number
Lecture 17: Virtual Memory II. Goals of virtual memory
 Lecture 17: Virtual Memory II Last Lecture: Introduction to virtual memory Today Review and continue virtual memory discussion Lecture 17 1 Goals of virtual memory Make it appear as if each process has:
Lecture 17: Virtual Memory II Last Lecture: Introduction to virtual memory Today Review and continue virtual memory discussion Lecture 17 1 Goals of virtual memory Make it appear as if each process has:
SYMETRIX SOLUTIONS: TECH TIP August 2015
 String Output Modules The purpose of this document is to provide an understanding of operation and configuration of the two different String Output modules available within SymNet Composer. The two different
String Output Modules The purpose of this document is to provide an understanding of operation and configuration of the two different String Output modules available within SymNet Composer. The two different
6 3 4 9 = 6 10 + 3 10 + 4 10 + 9 10
 Lesson The Binary Number System. Why Binary? The number system that you are familiar with, that you use every day, is the decimal number system, also commonly referred to as the base- system. When you
Lesson The Binary Number System. Why Binary? The number system that you are familiar with, that you use every day, is the decimal number system, also commonly referred to as the base- system. When you
ISOBUS Task Controller Workshop. Presented by Andy Beck / Hans Nissen John Deere
 ISOBUS Task Controller Workshop Presented by Andy Beck / Hans Nissen John Deere 1 Agenda Welcome Introductions ISO11783 Overview Part 6: Virtual Terminal Part 10: Task Controller Part 11: Data Dictionary
ISOBUS Task Controller Workshop Presented by Andy Beck / Hans Nissen John Deere 1 Agenda Welcome Introductions ISO11783 Overview Part 6: Virtual Terminal Part 10: Task Controller Part 11: Data Dictionary
Caml Virtual Machine File & data formats Document version: 1.4 http://cadmium.x9c.fr
 Caml Virtual Machine File & data formats Document version: 1.4 http://cadmium.x9c.fr Copyright c 2007-2010 Xavier Clerc [email protected] Released under the LGPL version 3 February 6, 2010 Abstract: This
Caml Virtual Machine File & data formats Document version: 1.4 http://cadmium.x9c.fr Copyright c 2007-2010 Xavier Clerc [email protected] Released under the LGPL version 3 February 6, 2010 Abstract: This
Let s put together a Manual Processor
 Lecture 14 Let s put together a Manual Processor Hardware Lecture 14 Slide 1 The processor Inside every computer there is at least one processor which can take an instruction, some operands and produce
Lecture 14 Let s put together a Manual Processor Hardware Lecture 14 Slide 1 The processor Inside every computer there is at least one processor which can take an instruction, some operands and produce
Instruction Set Architecture (ISA)
 Instruction Set Architecture (ISA) * Instruction set architecture of a machine fills the semantic gap between the user and the machine. * ISA serves as the starting point for the design of a new machine
Instruction Set Architecture (ISA) * Instruction set architecture of a machine fills the semantic gap between the user and the machine. * ISA serves as the starting point for the design of a new machine
Getting started with DfuSe USB device firmware upgrade STMicroelectronics extension
 User manual Getting started with DfuSe USB device firmware upgrade STMicroelectronics extension Introduction This document describes the demonstration user interface that was developed to illustrate use
User manual Getting started with DfuSe USB device firmware upgrade STMicroelectronics extension Introduction This document describes the demonstration user interface that was developed to illustrate use
plc numbers - 13.1 Encoded values; BCD and ASCII Error detection; parity, gray code and checksums
 plc numbers - 3. Topics: Number bases; binary, octal, decimal, hexadecimal Binary calculations; s compliments, addition, subtraction and Boolean operations Encoded values; BCD and ASCII Error detection;
plc numbers - 3. Topics: Number bases; binary, octal, decimal, hexadecimal Binary calculations; s compliments, addition, subtraction and Boolean operations Encoded values; BCD and ASCII Error detection;
The Hexadecimal Number System and Memory Addressing
 APPENDIX C The Hexadecimal Number System and Memory Addressing U nderstanding the number system and the coding system that computers use to store data and communicate with each other is fundamental to
APPENDIX C The Hexadecimal Number System and Memory Addressing U nderstanding the number system and the coding system that computers use to store data and communicate with each other is fundamental to
Today. Binary addition Representing negative numbers. Andrew H. Fagg: Embedded Real- Time Systems: Binary Arithmetic
 Today Binary addition Representing negative numbers 2 Binary Addition Consider the following binary numbers: 0 0 1 0 0 1 1 0 0 0 1 0 1 0 1 1 How do we add these numbers? 3 Binary Addition 0 0 1 0 0 1 1
Today Binary addition Representing negative numbers 2 Binary Addition Consider the following binary numbers: 0 0 1 0 0 1 1 0 0 0 1 0 1 0 1 1 How do we add these numbers? 3 Binary Addition 0 0 1 0 0 1 1
361 Computer Architecture Lecture 14: Cache Memory
 1 361 Computer Architecture Lecture 14 Memory cache.1 The Motivation for s Memory System Processor DRAM Motivation Large memories (DRAM) are slow Small memories (SRAM) are fast Make the average access
1 361 Computer Architecture Lecture 14 Memory cache.1 The Motivation for s Memory System Processor DRAM Motivation Large memories (DRAM) are slow Small memories (SRAM) are fast Make the average access
Absolute Backdoor Revisited. Vitaliy Kamlyuk, Kaspersky Lab Sergey Belov, Kaspersky Lab Anibal Sacco, Cubica Labs
 Absolute Backdoor Revisited Vitaliy Kamlyuk, Kaspersky Lab Sergey Belov, Kaspersky Lab Anibal Sacco, Cubica Labs BlackHat, Las Vegas August, 2014 What is Computrace? Computrace is an Anti-Theft software
Absolute Backdoor Revisited Vitaliy Kamlyuk, Kaspersky Lab Sergey Belov, Kaspersky Lab Anibal Sacco, Cubica Labs BlackHat, Las Vegas August, 2014 What is Computrace? Computrace is an Anti-Theft software
isppac-powr1220at8 I 2 C Hardware Verification Utility User s Guide
 November 2005 Introduction Application Note AN6067 The isppac -POWR1220AT8 device from Lattice is a full-featured second-generation Power Manager chip. As part of its feature set, this device supports
November 2005 Introduction Application Note AN6067 The isppac -POWR1220AT8 device from Lattice is a full-featured second-generation Power Manager chip. As part of its feature set, this device supports
FREE TV AUSTRALIA OPERATIONAL PRACTICE OP42
 Page 1 of 6 1. SCOPE Free TV Australia Operational Practice OP42 describes the technical/operational practices associated with their distribution to and subsequent monitoring and transmission by broadcasters
Page 1 of 6 1. SCOPE Free TV Australia Operational Practice OP42 describes the technical/operational practices associated with their distribution to and subsequent monitoring and transmission by broadcasters
Consult protocol, Nissan Technical egroup, Issue 6
 Consult protocol, Nissan Technical egroup, Issue 6 1. Electrical and Signaling protocol 1.1. Consult terminal or PC communications is via three wire bus. TX, RX and Async Clock. 1.2. TX data to ECU level
Consult protocol, Nissan Technical egroup, Issue 6 1. Electrical and Signaling protocol 1.1. Consult terminal or PC communications is via three wire bus. TX, RX and Async Clock. 1.2. TX data to ECU level
MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b3 CONTENTS
 MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b3 CONTENTS 1 Introduction... 2 1.1 Scope of this document... 2 2 Abbreviations... 2 3 Context... 3 4 General description... 3 4.1 Protocol description...
MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b3 CONTENTS 1 Introduction... 2 1.1 Scope of this document... 2 2 Abbreviations... 2 3 Context... 3 4 General description... 3 4.1 Protocol description...
BCD (ASCII) Arithmetic. Where and Why is BCD used? Packed BCD, ASCII, Unpacked BCD. BCD Adjustment Instructions AAA. Example
 BCD (ASCII) Arithmetic We will first look at unpacked BCD which means strings that look like '4567'. Bytes then look like 34h 35h 36h 37h OR: 04h 05h 06h 07h x86 processors also have instructions for packed
BCD (ASCII) Arithmetic We will first look at unpacked BCD which means strings that look like '4567'. Bytes then look like 34h 35h 36h 37h OR: 04h 05h 06h 07h x86 processors also have instructions for packed
The Orca Chip... Heart of IBM s RISC System/6000 Value Servers
 The Orca Chip... Heart of IBM s RISC System/6000 Value Servers Ravi Arimilli IBM RISC System/6000 Division 1 Agenda. Server Background. Cache Heirarchy Performance Study. RS/6000 Value Server System Structure.
The Orca Chip... Heart of IBM s RISC System/6000 Value Servers Ravi Arimilli IBM RISC System/6000 Division 1 Agenda. Server Background. Cache Heirarchy Performance Study. RS/6000 Value Server System Structure.
UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering. EEC180B Lab 7: MISP Processor Design Spring 1995
 UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering EEC180B Lab 7: MISP Processor Design Spring 1995 Objective: In this lab, you will complete the design of the MISP processor,
UNIVERSITY OF CALIFORNIA, DAVIS Department of Electrical and Computer Engineering EEC180B Lab 7: MISP Processor Design Spring 1995 Objective: In this lab, you will complete the design of the MISP processor,
MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b CONTENTS
 MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b CONTENTS 1 Introduction... 2 1.1 Scope of this document... 2 2 Abbreviations... 2 3 Context... 3 4 General description... 3 4.1 Protocol description... 3
MODBUS APPLICATION PROTOCOL SPECIFICATION V1.1b CONTENTS 1 Introduction... 2 1.1 Scope of this document... 2 2 Abbreviations... 2 3 Context... 3 4 General description... 3 4.1 Protocol description... 3
USB Simply Buffered (USB) Mass Storage Class Bulk-Only Transport
 USB Simply Buffered (USB) ass Storage Class Bulk-Only Transport Copyright 2007. Shakthi Kannan. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation
USB Simply Buffered (USB) ass Storage Class Bulk-Only Transport Copyright 2007. Shakthi Kannan. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation
2011, The McGraw-Hill Companies, Inc. Chapter 3
 Chapter 3 3.1 Decimal System The radix or base of a number system determines the total number of different symbols or digits used by that system. The decimal system has a base of 10 with the digits 0 through
Chapter 3 3.1 Decimal System The radix or base of a number system determines the total number of different symbols or digits used by that system. The decimal system has a base of 10 with the digits 0 through
Byte Ordering of Multibyte Data Items
 Byte Ordering of Multibyte Data Items Most Significant Byte (MSB) Least Significant Byte (LSB) Big Endian Byte Addresses +0 +1 +2 +3 +4 +5 +6 +7 VALUE (8-byte) Least Significant Byte (LSB) Most Significant
Byte Ordering of Multibyte Data Items Most Significant Byte (MSB) Least Significant Byte (LSB) Big Endian Byte Addresses +0 +1 +2 +3 +4 +5 +6 +7 VALUE (8-byte) Least Significant Byte (LSB) Most Significant
Traditional IBM Mainframe Operating Principles
 C H A P T E R 1 7 Traditional IBM Mainframe Operating Principles WHEN YOU FINISH READING THIS CHAPTER YOU SHOULD BE ABLE TO: Distinguish between an absolute address and a relative address. Briefly explain
C H A P T E R 1 7 Traditional IBM Mainframe Operating Principles WHEN YOU FINISH READING THIS CHAPTER YOU SHOULD BE ABLE TO: Distinguish between an absolute address and a relative address. Briefly explain
Application Note. Introduction AN2471/D 3/2003. PC Master Software Communication Protocol Specification
 Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
Chapter 1 Computer System Overview
 Operating Systems: Internals and Design Principles Chapter 1 Computer System Overview Eighth Edition By William Stallings Operating System Exploits the hardware resources of one or more processors Provides
Operating Systems: Internals and Design Principles Chapter 1 Computer System Overview Eighth Edition By William Stallings Operating System Exploits the hardware resources of one or more processors Provides
A Predictive Model for Cache-Based Side Channels in Multicore and Multithreaded Microprocessors
 A Predictive Model for Cache-Based Side Channels in Multicore and Multithreaded Microprocessors Leonid Domnitser, Nael Abu-Ghazaleh and Dmitry Ponomarev Department of Computer Science SUNY-Binghamton {lenny,
A Predictive Model for Cache-Based Side Channels in Multicore and Multithreaded Microprocessors Leonid Domnitser, Nael Abu-Ghazaleh and Dmitry Ponomarev Department of Computer Science SUNY-Binghamton {lenny,
Bluetooth HID Profile
 RN-WIFLYCR-UM-.01 RN-HID-UM Bluetooth HID Profile 2012 Roving Networks. All rights reserved. Version 1.0r 1/17/2012 USER MANUAL www.rovingnetworks.com 1 OVERVIEW Roving Networks Bluetooth modules support
RN-WIFLYCR-UM-.01 RN-HID-UM Bluetooth HID Profile 2012 Roving Networks. All rights reserved. Version 1.0r 1/17/2012 USER MANUAL www.rovingnetworks.com 1 OVERVIEW Roving Networks Bluetooth modules support
3. Convert a number from one number system to another
 3. Convert a number from one number system to another Conversion between number bases: Hexa (16) Decimal (10) Binary (2) Octal (8) More Interest Way we need conversion? We need decimal system for real
3. Convert a number from one number system to another Conversion between number bases: Hexa (16) Decimal (10) Binary (2) Octal (8) More Interest Way we need conversion? We need decimal system for real
APP INVENTOR. Test Review
 APP INVENTOR Test Review Main Concepts App Inventor Lists Creating Random Numbers Variables Searching and Sorting Data Linear Search Binary Search Selection Sort Quick Sort Abstraction Modulus Division
APP INVENTOR Test Review Main Concepts App Inventor Lists Creating Random Numbers Variables Searching and Sorting Data Linear Search Binary Search Selection Sort Quick Sort Abstraction Modulus Division
PROGRAMMABLE LOGIC CONTROLLERS Unit code: A/601/1625 QCF level: 4 Credit value: 15 TUTORIAL OUTCOME 2 Part 1
 UNIT 22: PROGRAMMABLE LOGIC CONTROLLERS Unit code: A/601/1625 QCF level: 4 Credit value: 15 TUTORIAL OUTCOME 2 Part 1 This work covers part of outcome 2 of the Edexcel standard module. The material is
UNIT 22: PROGRAMMABLE LOGIC CONTROLLERS Unit code: A/601/1625 QCF level: 4 Credit value: 15 TUTORIAL OUTCOME 2 Part 1 This work covers part of outcome 2 of the Edexcel standard module. The material is
CPU Organisation and Operation
 CPU Organisation and Operation The Fetch-Execute Cycle The operation of the CPU 1 is usually described in terms of the Fetch-Execute cycle. 2 Fetch-Execute Cycle Fetch the Instruction Increment the Program
CPU Organisation and Operation The Fetch-Execute Cycle The operation of the CPU 1 is usually described in terms of the Fetch-Execute cycle. 2 Fetch-Execute Cycle Fetch the Instruction Increment the Program
SUBNETS, CIDR, AND CLASSLESS ADDRESSING
 Announcements SUBNETS, CIDR, AND CLASSLESS ADDRESSING Internet Protocols CSC / ECE 573 Fall, 005 No office hours tomorrow (Wednesday) out of town No class on Thursday Fall break! Midterm exam next Tuesday!
Announcements SUBNETS, CIDR, AND CLASSLESS ADDRESSING Internet Protocols CSC / ECE 573 Fall, 005 No office hours tomorrow (Wednesday) out of town No class on Thursday Fall break! Midterm exam next Tuesday!
CS:APP Chapter 4 Computer Architecture. Wrap-Up. William J. Taffe Plymouth State University. using the slides of
 CS:APP Chapter 4 Computer Architecture Wrap-Up William J. Taffe Plymouth State University using the slides of Randal E. Bryant Carnegie Mellon University Overview Wrap-Up of PIPE Design Performance analysis
CS:APP Chapter 4 Computer Architecture Wrap-Up William J. Taffe Plymouth State University using the slides of Randal E. Bryant Carnegie Mellon University Overview Wrap-Up of PIPE Design Performance analysis
Hacking cars in the style of Stuxnet
 Hacking cars in the style of Stuxnet András Szijj 1, Levente Buttyán 1, Zsolt Szalay 2 1 CrySyS Lab, Department of Networked Systems and Services 2 Department of Automobiles and Vehicle Manufacturing Budapest
Hacking cars in the style of Stuxnet András Szijj 1, Levente Buttyán 1, Zsolt Szalay 2 1 CrySyS Lab, Department of Networked Systems and Services 2 Department of Automobiles and Vehicle Manufacturing Budapest
Dolphin In-Circuit programming Updating Firmware in the field
 Dolphin In-Circuit programming Updating Firmware in the field 1 Introduction In systems e.g. gateways, where an external microcontroller is connected to a Dolphin based product like a TCM300 it might be
Dolphin In-Circuit programming Updating Firmware in the field 1 Introduction In systems e.g. gateways, where an external microcontroller is connected to a Dolphin based product like a TCM300 it might be
Application Programming Interface
 Application Programming Interface Advanced Card Systems Ltd. Website: www.acs.com.hk Email: [email protected] CONTENTS Introduction 4 Features 4 USB interface 4 Contact and Contactless interface handling
Application Programming Interface Advanced Card Systems Ltd. Website: www.acs.com.hk Email: [email protected] CONTENTS Introduction 4 Features 4 USB interface 4 Contact and Contactless interface handling
IBM Emulation Mode Printer Commands
 IBM Emulation Mode Printer Commands Section 3 This section provides a detailed description of IBM emulation mode commands you can use with your printer. Control Codes Control codes are one-character printer
IBM Emulation Mode Printer Commands Section 3 This section provides a detailed description of IBM emulation mode commands you can use with your printer. Control Codes Control codes are one-character printer
Life Cycle of a Memory Request. Ring Example: 2 requests for lock 17
 Life Cycle of a Memory Request (1) Use AQR or AQW to place address in AQ (2) If A[31]==0, check for hit in DCache Ring (3) Read Hit: place cache word in RQ; Write Hit: replace cache word with WQ RDDest/RDreturn
Life Cycle of a Memory Request (1) Use AQR or AQW to place address in AQ (2) If A[31]==0, check for hit in DCache Ring (3) Read Hit: place cache word in RQ; Write Hit: replace cache word with WQ RDDest/RDreturn
CS/COE1541: Introduction to Computer Architecture. Memory hierarchy. Sangyeun Cho. Computer Science Department University of Pittsburgh
 CS/COE1541: Introduction to Computer Architecture Memory hierarchy Sangyeun Cho Computer Science Department CPU clock rate Apple II MOS 6502 (1975) 1~2MHz Original IBM PC (1981) Intel 8080 4.77MHz Intel
CS/COE1541: Introduction to Computer Architecture Memory hierarchy Sangyeun Cho Computer Science Department CPU clock rate Apple II MOS 6502 (1975) 1~2MHz Original IBM PC (1981) Intel 8080 4.77MHz Intel
Memory Management Simulation Interactive Lab
 Memory Management Simulation Interactive Lab The purpose of this lab is to help you to understand deadlock. We will use a MOSS simulator for this. The instructions for this lab are for a computer running
Memory Management Simulation Interactive Lab The purpose of this lab is to help you to understand deadlock. We will use a MOSS simulator for this. The instructions for this lab are for a computer running
Solution for Homework 2
 Solution for Homework 2 Problem 1 a. What is the minimum number of bits that are required to uniquely represent the characters of English alphabet? (Consider upper case characters alone) The number of
Solution for Homework 2 Problem 1 a. What is the minimum number of bits that are required to uniquely represent the characters of English alphabet? (Consider upper case characters alone) The number of
Mifare DESFire Specification
 Mifare DESFire Specification Version 1.0 29 th September 2009 Revision History Version Date Author Description of Changes 1.0 29/09/09 O McLaughlin Ratified by LASSeO 0.2 28/07/09 O McLaughlin Minor changes
Mifare DESFire Specification Version 1.0 29 th September 2009 Revision History Version Date Author Description of Changes 1.0 29/09/09 O McLaughlin Ratified by LASSeO 0.2 28/07/09 O McLaughlin Minor changes
Section 29. Real-Time Clock and Calendar (RTCC)
 Section 29. Real-Time Clock and Calendar (RTCC) HIGHLIGHTS This section of the manual contains the following topics: 29.1 Introduction... 29-2 29.2 Status and Control Registers... 29-3 29.3 Modes of Operation...
Section 29. Real-Time Clock and Calendar (RTCC) HIGHLIGHTS This section of the manual contains the following topics: 29.1 Introduction... 29-2 29.2 Status and Control Registers... 29-3 29.3 Modes of Operation...
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide
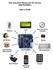 Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Data Acquisition Module with I2C interface «I2C-FLEXEL» User s Guide Sensors LCD Real Time Clock/ Calendar DC Motors Buzzer LED dimming Relay control I2C-FLEXEL PS2 Keyboards Servo Motors IR Remote Control
Chapter 4: Computer Codes
 Slide 1/30 Learning Objectives In this chapter you will learn about: Computer data Computer codes: representation of data in binary Most commonly used computer codes Collating sequence 36 Slide 2/30 Data
Slide 1/30 Learning Objectives In this chapter you will learn about: Computer data Computer codes: representation of data in binary Most commonly used computer codes Collating sequence 36 Slide 2/30 Data
Addressing The problem. When & Where do we encounter Data? The concept of addressing data' in computations. The implications for our machine design(s)
 Addressing The problem Objectives:- When & Where do we encounter Data? The concept of addressing data' in computations The implications for our machine design(s) Introducing the stack-machine concept Slide
Addressing The problem Objectives:- When & Where do we encounter Data? The concept of addressing data' in computations The implications for our machine design(s) Introducing the stack-machine concept Slide
