Securing your SIP network with OpenSIPS Detection, prevention and control Vlad Paiu OpenSIPS Project Developer OpenSIPS Solutions
|
|
|
- Pierce Grant
- 7 years ago
- Views:
Transcription
1 Securing your SIP network with pensips Detection, prevention and control Vlad Paiu pensips Project Developer pensips Solutions
2 pen What is pensips GPL, pen Source project tens of contributers, community of thousands used from SMB to enterprises and grade-carriers SIP SIP RFC tens of SIP extensions SBC, trunking, billing, ITSP, router, call center S Server (registrar, proxy, LB, B2BUA, SIMPLE, NAT, apps) cps, 5K parallel calls, 1M subscribers Programmable and flexible (scripting with > 100 modules) pensips builds and glues SIP infrastructures.
3 Types of Attacks Passive attacks Make use of information from the SIP System Addressed by transport encryption ( signaling and media ) Active attacks Affect SIP systems operation Alter system resources
4 Active Attacks utside attacks riginated by non-local SIP entities Inside attacks riginated via local account on purpose or not Actual user or identity theft victim
5 utside Attacks
6 utside attacks - Floods Signature Detection Friendly scanner, etc Floods Pike module Check all UDP/TCP messages received Event interface automagically triggered Rate limit Ratelimit module Dynamic pipes Distributed
7 utside Attacks - Dictionary
8 utside Attacks - Dictionary Fail2ban is a sub-optimal solution!
9 utside Attacks - Dictionary www_authorize("","subscriber"); switch ($retcode) {; case -3: # stale nonce case -2: # invalid passwd case -1: # no such user xlog("failed Auth\n"); if ( cache_fetch("local","authf_$si",$avp(failed_no)) ) { if ( $(avp(failed_no){s.int}) >= 20 ) { xlog("script: SECURITY ALERT: 20 failed auth from $si\n"); send_reply("403","forbidden"); exit; } cache_add("local","authf_$si",1,60); } else { cache_store("local","authf_$si","1",60); } default: xlog("challenging\n"); www_challenge("", "0"); exit; break; };
10 utside Attacks - Fuzzing Malformed SIP packets sipmsg_validate() in sipmsgops module Check mandatory headers are present Check all header bodies Check SDP body
11 Inside Attacks
12 Inside attacks SIP Injection
13 Inside attacks SIP Injection if (loose_route()) { if ($DLG_status==NULL &&!match_dialog()) { xlog("unknown dialog. Might as well reject\n"); exit; } if (!validate_dialog()) { xlog("invalid in-dialog request\n"); fix_route_dialog(); } }
14 Inside attacks Register Poisoning
15 Inside attacks Register Poisoning $var(i) = 0; while( $(ct[$var(i)])!=null ) { $var(host) = $(ct[$varv(i)]{nameaddr.uri}{uri.host}); if ($var(host) == GWIP ) { xlog("security ALERT: $si registering $var(host)\n"); send_reply("476", "Contact Unacceptable ); exit; } $var(i) = $var(i) + 1; }
16 Inside attacks DNS poisoning User buys foobar.com and points DNS to GWIP
17 Inside attacks DNS poisoning modparam("drouting", "define_blacklist", 'gws= 0') dst_blacklist = media:{( udp, , 5060, "" )... if (!lookup("location","m")) { t_reply("404", "Not Found"); exit; } # make sure we do not route to gateways or media servers use_blacklist("gws"); use_blacklist( media );
18 Inside attacks Hijacked accounts Actual stolen accounts Weak passwords Badly configured phones Unchanged default passwords Exploits in the phone software Traffic is valid, does not look like an attack until the user starts complaining about the bill
19 Inside attacks Hijacked accounts Detect frauds as anomalies in user's dialing pattern. Patterns can be : Dynamic Use AI algs Learn from existing traffic Apply learned patterns Static - Pre-configured by the admin When you know the traffic pattern ( call-centers, etc )
20 Inside attacks Hijacked accounts Pattern for the volume of the calls Pattern for the daily schedule of the calls Pattern for the usual destination zones of the calls
21 Thank you for your attention You can find out more at Questions are welcome
Hosted PBX client or provider site? or how to manage PBX clouds with OpenSIPS
 Hosted PBX client or provider site? or how to manage PBX clouds with pensips Bogdan-Andrei Iancu Founder pensips Project pen What is pensips GPL, pen Source project tens of contributers, community of thousands
Hosted PBX client or provider site? or how to manage PBX clouds with pensips Bogdan-Andrei Iancu Founder pensips Project pen What is pensips GPL, pen Source project tens of contributers, community of thousands
The #1 Issue on VoIP, Fraud!
 Know your enemy Sun Tzu's The Art of War The #1 Issue on VoIP, Fraud! How to identify, prevent and reduce damages caused by fraud Flavio E. Goncalves About me Author of the book Building Telephony Systems
Know your enemy Sun Tzu's The Art of War The #1 Issue on VoIP, Fraud! How to identify, prevent and reduce damages caused by fraud Flavio E. Goncalves About me Author of the book Building Telephony Systems
nexvortex SIP Trunking Implementation & Planning Guide V1.5
 nexvortex SIP Trunking Implementation & Planning Guide V1.5 510 S PRING S TREET H ERNDON VA 20170 +1 855.639.8888 Introduction Welcome to nexvortex! This document is intended for nexvortex Customers and
nexvortex SIP Trunking Implementation & Planning Guide V1.5 510 S PRING S TREET H ERNDON VA 20170 +1 855.639.8888 Introduction Welcome to nexvortex! This document is intended for nexvortex Customers and
nexvortex Setup Guide
 nexvortex Setup Guide CUDATEL COMMUNICATION SERVER September 2012 510 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex
nexvortex Setup Guide CUDATEL COMMUNICATION SERVER September 2012 510 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex
BROADSOFT PARTNER CONFIGURATION GUIDE VEGASTREAM VEGA 100
 BROADSOFT PARTNER CONFIGURATION GUIDE VEGASTREAM VEGA 100 JULY 2005 Version 1.0 BroadWorks Guide Copyright Notice Copyright 2005 BroadSoft, Inc. All rights reserved. Any technical documentation that is
BROADSOFT PARTNER CONFIGURATION GUIDE VEGASTREAM VEGA 100 JULY 2005 Version 1.0 BroadWorks Guide Copyright Notice Copyright 2005 BroadSoft, Inc. All rights reserved. Any technical documentation that is
CompleteSBC: Getting Started Guide
 CompleteSBC: Getting Started Guide Default CompleteSBC Configuration CompleteSBC (SBC) is pre-configured to perform the following actions: registration caching limiting the number of concurrent calls via
CompleteSBC: Getting Started Guide Default CompleteSBC Configuration CompleteSBC (SBC) is pre-configured to perform the following actions: registration caching limiting the number of concurrent calls via
nexvortex SIP Trunking
 nexvortex SIP Trunking January 2015 510 SPRING STREET HERNDON VA 20170 +1 855.639.8888 Copyright nexvortex 2014 This document is the exclusive property of nexvortex, Inc. and no part may be disclosed,
nexvortex SIP Trunking January 2015 510 SPRING STREET HERNDON VA 20170 +1 855.639.8888 Copyright nexvortex 2014 This document is the exclusive property of nexvortex, Inc. and no part may be disclosed,
OpenScape Business V2
 OpenScape Business V2 Tutorial Support of SIP Endpoints connected via the internet Version 2.1 Definitions HowTo An OpenScape Business HowTo describes the configuration of an OpenScape Business feature
OpenScape Business V2 Tutorial Support of SIP Endpoints connected via the internet Version 2.1 Definitions HowTo An OpenScape Business HowTo describes the configuration of an OpenScape Business feature
OpenScape Business V1
 OpenScape Business V1 Tutorial Support of SIP Endpoints connected via the internet Version 1.0.1 Definitions HowTo An OpenScape Business HowTo describes the configuration of an OpenScape Business feature
OpenScape Business V1 Tutorial Support of SIP Endpoints connected via the internet Version 1.0.1 Definitions HowTo An OpenScape Business HowTo describes the configuration of an OpenScape Business feature
nexvortex Setup Template
 nexvortex Setup Template ZULTYS, INC. April 2013 5 1 0 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex customers
nexvortex Setup Template ZULTYS, INC. April 2013 5 1 0 S P R I N G S T R E E T H E R N D O N V A 2 0 1 7 0 + 1 8 5 5. 6 3 9. 8 8 8 8 Introduction This document is intended only for nexvortex customers
OfficeMaster Gate (Virtual) Enterprise Session Border Controller for Microsoft Lync Server. Quick Start Guide
 OfficeMaster Gate (Virtual) Enterprise Session Border Controller for Microsoft Lync Server Quick Start Guide October 2013 Copyright and Legal Notice. All rights reserved. No part of this document may be
OfficeMaster Gate (Virtual) Enterprise Session Border Controller for Microsoft Lync Server Quick Start Guide October 2013 Copyright and Legal Notice. All rights reserved. No part of this document may be
Configuration Guide for connecting the Eircom Advantage 4800/1500/1200 PBXs to the Eircom SIP Voice platform.
 Configuration Guide for connecting the Eircom Advantage 4800/1500/1200 PBXs to the Eircom SIP Voice platform. 1 Contents Introduction.... 3 Installing the Applications Module... 4 Ordering a Licence for
Configuration Guide for connecting the Eircom Advantage 4800/1500/1200 PBXs to the Eircom SIP Voice platform. 1 Contents Introduction.... 3 Installing the Applications Module... 4 Ordering a Licence for
CS5008: Internet Computing
 CS5008: Internet Computing Lecture 22: Internet Security A. O Riordan, 2009, latest revision 2015 Internet Security When a computer connects to the Internet and begins communicating with others, it is
CS5008: Internet Computing Lecture 22: Internet Security A. O Riordan, 2009, latest revision 2015 Internet Security When a computer connects to the Internet and begins communicating with others, it is
AdvOSS Session Border Controller
 AdvOSS Session Border Controller Product Data Sheet Find latest copy of this document from http://www.advoss.com/pdf/advoss-sbc-productdatasheet.pdf Copyright AdvOSS.com, 2007-2011 All Rights Reserved
AdvOSS Session Border Controller Product Data Sheet Find latest copy of this document from http://www.advoss.com/pdf/advoss-sbc-productdatasheet.pdf Copyright AdvOSS.com, 2007-2011 All Rights Reserved
Wave SIP Trunk Configuration Guide FOR BROADVOX
 Wave SIP Trunk Configuration Guide FOR BROADVOX Last updated 1/7/2014 Contents Overview... 1 Special Notes... 1 Before you begin... 1 Required SIP trunk provisioning and configuration information... 1
Wave SIP Trunk Configuration Guide FOR BROADVOX Last updated 1/7/2014 Contents Overview... 1 Special Notes... 1 Before you begin... 1 Required SIP trunk provisioning and configuration information... 1
SIP Security Controllers. Product Overview
 SIP Security Controllers Product Overview Document Version: V1.1 Date: October 2008 1. Introduction UM Labs have developed a range of perimeter security gateways for VoIP and other applications running
SIP Security Controllers Product Overview Document Version: V1.1 Date: October 2008 1. Introduction UM Labs have developed a range of perimeter security gateways for VoIP and other applications running
Configuring a Mediatrix 500 / 600 Enterprise SIP Trunk SBC June 28, 2011
 Configuring a Mediatrix 500 / 600 Enterprise SIP Trunk SBC June 28, 2011 Proprietary 2011 Media5 Corporation Table of Contents Introduction... 3 Solution Overview... 3 Network Topology... 4 Network Configuration...
Configuring a Mediatrix 500 / 600 Enterprise SIP Trunk SBC June 28, 2011 Proprietary 2011 Media5 Corporation Table of Contents Introduction... 3 Solution Overview... 3 Network Topology... 4 Network Configuration...
WHITE PAPER. FortiWeb and the OWASP Top 10 Mitigating the most dangerous application security threats
 WHITE PAPER FortiWeb and the OWASP Top 10 PAGE 2 Introduction The Open Web Application Security project (OWASP) Top Ten provides a powerful awareness document for web application security. The OWASP Top
WHITE PAPER FortiWeb and the OWASP Top 10 PAGE 2 Introduction The Open Web Application Security project (OWASP) Top Ten provides a powerful awareness document for web application security. The OWASP Top
Security Considerations
 112 SIP Trunking VoIP endpoints and call agents such as CUCM and CUCMExpress also have facilities to control and mark packets. These can be used directly if the enterprise markings are the same as the
112 SIP Trunking VoIP endpoints and call agents such as CUCM and CUCMExpress also have facilities to control and mark packets. These can be used directly if the enterprise markings are the same as the
Configuring 3CX for Spitfire SIP Trunks
 Configuring 3CX for Spitfire SIP Trunks This document is a guideline for configuring Spitfire SIP trunks onto a 3CX which includes the settings required for Inbound DDI routing and Outbound CLI presentation.
Configuring 3CX for Spitfire SIP Trunks This document is a guideline for configuring Spitfire SIP trunks onto a 3CX which includes the settings required for Inbound DDI routing and Outbound CLI presentation.
Using the NetVanta 7100 Series
 MENU OK CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL 1 2
MENU OK CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL 1 2
Linux Network Security
 Linux Network Security Course ID SEC220 Course Description This extremely popular class focuses on network security, and makes an excellent companion class to the GL550: Host Security course. Protocols
Linux Network Security Course ID SEC220 Course Description This extremely popular class focuses on network security, and makes an excellent companion class to the GL550: Host Security course. Protocols
How to Configure the Cisco UC500 for use with Integra Telecom SIP Solutions
 How to Configure the Cisco UC500 for use with Integra Telecom SIP Solutions Overview: This document provides a reference for configuration of the Cisco UC500 IP PBX to connect to Integra Telecom SIP Trunks.
How to Configure the Cisco UC500 for use with Integra Telecom SIP Solutions Overview: This document provides a reference for configuration of the Cisco UC500 IP PBX to connect to Integra Telecom SIP Trunks.
SIP Trunk Configuration V/IPedge Feature Description 5/22/13
 SIP Trunk Configuration V/IPedge Feature Description 5/22/13 OVERVIEW Session Initiation Protocol (SIP) is an application layer protocol used for establishing sessions in an IP network. SIP trunks allow
SIP Trunk Configuration V/IPedge Feature Description 5/22/13 OVERVIEW Session Initiation Protocol (SIP) is an application layer protocol used for establishing sessions in an IP network. SIP trunks allow
Optional VBP-E at the Headquarters Location
 publicly whitelist/blacklist LAN/Subscriber-side GK address. Submit Default alias Optional VBP-E at the Headquarters Location As shown in the diagram above, you can choose to install a VBP-E to allow your
publicly whitelist/blacklist LAN/Subscriber-side GK address. Submit Default alias Optional VBP-E at the Headquarters Location As shown in the diagram above, you can choose to install a VBP-E to allow your
How to Configure the Allworx 6x, 24x and 48x for use with Integra Telecom SIP Solutions
 How to Configure the Allworx 6x, 24x and 48x for use with Integra Telecom SIP Solutions Overview: This document provides a reference for configuration of the Allworx 6x IP PBX to connect to Integra Telecom
How to Configure the Allworx 6x, 24x and 48x for use with Integra Telecom SIP Solutions Overview: This document provides a reference for configuration of the Allworx 6x IP PBX to connect to Integra Telecom
Application Note Startup Tool - Getting Started Guide
 Application Note Startup Tool - Getting Started Guide 1 April 2012 Startup Tool Table of Contents 1 INGATE STARTUP TOOL... 1 2 STARTUP TOOL INSTALLATION... 2 3 CONNECTING THE INGATE FIREWALL/SIPARATOR...
Application Note Startup Tool - Getting Started Guide 1 April 2012 Startup Tool Table of Contents 1 INGATE STARTUP TOOL... 1 2 STARTUP TOOL INSTALLATION... 2 3 CONNECTING THE INGATE FIREWALL/SIPARATOR...
Microbase OpenSIPs Summit 2015 Building an ITSP with OpenSIPs 2.1
 Microbase OpenSIPs Summit 2015 Building an ITSP with OpenSIPs 2.1 Antonis Psaras, Managing Partner, Microbase Microbase Microbase is a communications software developer and supplier, with a leading role
Microbase OpenSIPs Summit 2015 Building an ITSP with OpenSIPs 2.1 Antonis Psaras, Managing Partner, Microbase Microbase Microbase is a communications software developer and supplier, with a leading role
OpenSIPS clustering and balancing of media servers Bogdan-Andrei Iancu CEO Voice System Founder OpenSIPS Project
 pensips clustering and balancing of media servers Bogdan-Andrei Iancu CE Voice System Founder pensips Project The story nce upon a time there was a Switch and a PBX......there was pensips and Yate. The
pensips clustering and balancing of media servers Bogdan-Andrei Iancu CE Voice System Founder pensips Project The story nce upon a time there was a Switch and a PBX......there was pensips and Yate. The
20-CS-6053-00X Network Security Spring, 2014. An Introduction To. Network Security. Week 1. January 7
 20-CS-6053-00X Network Security Spring, 2014 An Introduction To Network Security Week 1 January 7 Attacks Criminal: fraud, scams, destruction; IP, ID, brand theft Privacy: surveillance, databases, traffic
20-CS-6053-00X Network Security Spring, 2014 An Introduction To Network Security Week 1 January 7 Attacks Criminal: fraud, scams, destruction; IP, ID, brand theft Privacy: surveillance, databases, traffic
Anat Bremler-Barr Ronit Halachmi-Bekel Jussi Kangasharju Interdisciplinary center Herzliya Darmstadt University of Technology
 Unregister Attack in SIP Anat Bremler-Barr Ronit Halachmi-Bekel Jussi Kangasharju Interdisciplinary center Herzliya Darmstadt University of Technology Unregister Attack We present a new VoIP Denial Of
Unregister Attack in SIP Anat Bremler-Barr Ronit Halachmi-Bekel Jussi Kangasharju Interdisciplinary center Herzliya Darmstadt University of Technology Unregister Attack We present a new VoIP Denial Of
The SIP School- 'Mitel Style'
 The SIP School- 'Mitel Style' Course Objectives This course will take delegates through the basics of SIP into some very technical areas and is suited to people who will be installing and supporting SIP
The SIP School- 'Mitel Style' Course Objectives This course will take delegates through the basics of SIP into some very technical areas and is suited to people who will be installing and supporting SIP
Customer Guide. BT Business - BT SIP Trunks. BT SIP Trunks: Firewall and LAN Guide. Issued by: BT Business Date 14.02.2012. Issue: v1.
 Customer Guide BT Business - BT SIP Trunks BT SIP Trunks: Firewall and LAN Guide Issue: v1.3 1 Contents 1 Overview 3 2 Firewalls 3 3 Recommendations 4 4 Ports 5 5 Warning & Disclaimer 5 Issue: v1.3 2 1
Customer Guide BT Business - BT SIP Trunks BT SIP Trunks: Firewall and LAN Guide Issue: v1.3 1 Contents 1 Overview 3 2 Firewalls 3 3 Recommendations 4 4 Ports 5 5 Warning & Disclaimer 5 Issue: v1.3 2 1
Voice Over IP and Firewalls
 Introduction Voice Over IP and Firewalls By Mark Collier Chief Technology Officer SecureLogix Corporation mark.collier@securelogix.com Use of Voice Over IP (VoIP) in enterprises is becoming more and more
Introduction Voice Over IP and Firewalls By Mark Collier Chief Technology Officer SecureLogix Corporation mark.collier@securelogix.com Use of Voice Over IP (VoIP) in enterprises is becoming more and more
Application Note Configuring the Synapse SB67070 SIP Gateway for Broadvox GO! SIP Trunking
 Configuring the Synapse SB67070 SIP Gateway for Broadvox GO! SIP Trunking 2012 Advanced American Telephones. All Rights Reserved. AT&T and the AT&T logo are trademarks of AT&T Intellectual Property licensed
Configuring the Synapse SB67070 SIP Gateway for Broadvox GO! SIP Trunking 2012 Advanced American Telephones. All Rights Reserved. AT&T and the AT&T logo are trademarks of AT&T Intellectual Property licensed
ADTRAN SBC and Avaya IP Office PBX SIP Trunk Interoperability
 6AOSSG001-42B March 2014 Interoperability Guide ADTRAN SBC and Avaya IP Office PBX SIP Trunk Interoperability This guide describes an example configuration used in testing the interoperability of an ADTRAN
6AOSSG001-42B March 2014 Interoperability Guide ADTRAN SBC and Avaya IP Office PBX SIP Trunk Interoperability This guide describes an example configuration used in testing the interoperability of an ADTRAN
21.4 Network Address Translation (NAT) 21.4.1 NAT concept
 21.4 Network Address Translation (NAT) This section explains Network Address Translation (NAT). NAT is also known as IP masquerading. It provides a mapping between internal IP addresses and officially
21.4 Network Address Translation (NAT) This section explains Network Address Translation (NAT). NAT is also known as IP masquerading. It provides a mapping between internal IP addresses and officially
OpenScape Business V2
 OpenScape Business V2 Tutorial System Device@Home Configuration Version 1.1 Table of Contents 1. Configuration Overview 4 1.1. Network Scenario Description: 4 1.2. Configuration Steps 5 1.2.1. Overview
OpenScape Business V2 Tutorial System Device@Home Configuration Version 1.1 Table of Contents 1. Configuration Overview 4 1.1. Network Scenario Description: 4 1.2. Configuration Steps 5 1.2.1. Overview
IP Ports and Protocols used by H.323 Devices
 IP Ports and Protocols used by H.323 Devices Overview: The purpose of this paper is to explain in greater detail the IP Ports and Protocols used by H.323 devices during Video Conferences. This is essential
IP Ports and Protocols used by H.323 Devices Overview: The purpose of this paper is to explain in greater detail the IP Ports and Protocols used by H.323 devices during Video Conferences. This is essential
OpenSER the open SIP Server. Bogdan-Andrei Iancu CEO Voice System Co-Founder OpenSER Project
 penser the open SIP Server Bogdan-Andrei Iancu CE Voice System Co-Founder penser Project About penser verview penser is an open source, GPLed SIP server with High scalability (up to thousands of calls
penser the open SIP Server Bogdan-Andrei Iancu CE Voice System Co-Founder penser Project About penser verview penser is an open source, GPLed SIP server with High scalability (up to thousands of calls
White paper. SIP An introduction
 White paper An introduction Table of contents 1 Introducing 3 2 How does it work? 3 3 Inside a normal call 4 4 DTMF sending commands in sip calls 6 5 Complex environments and higher security 6 6 Summary
White paper An introduction Table of contents 1 Introducing 3 2 How does it work? 3 3 Inside a normal call 4 4 DTMF sending commands in sip calls 6 5 Complex environments and higher security 6 6 Summary
Vega 100G and Vega 200G Gamma Config Guide
 Vega 100G and Vega 200G Gamma Config Guide This document aims to go through the steps necessary to configure the Vega SBC to be used with a Gamma SIP Trunk. When a SIP trunk is provisioned by Gamma a list
Vega 100G and Vega 200G Gamma Config Guide This document aims to go through the steps necessary to configure the Vega SBC to be used with a Gamma SIP Trunk. When a SIP trunk is provisioned by Gamma a list
Setup Reference guide for PBX to SBC interconnection
 Setup Reference guide for PBX to SBC interconnection Method of connection by "LAN interface only" i.e. SBC is placed behind the Perimeter Router / Fire-wall. Panasonic PBX (KX-TDE, NCP series), Media5
Setup Reference guide for PBX to SBC interconnection Method of connection by "LAN interface only" i.e. SBC is placed behind the Perimeter Router / Fire-wall. Panasonic PBX (KX-TDE, NCP series), Media5
SIP Trunk Configuration Guide. using
 SIP Trunk Configuration Guide using www.cbeyond.net 1-877-441-9783 The information contained in this document is specific to setting up SIP connections between Vertical SBX IP 320 and Cbeyond. If you require
SIP Trunk Configuration Guide using www.cbeyond.net 1-877-441-9783 The information contained in this document is specific to setting up SIP connections between Vertical SBX IP 320 and Cbeyond. If you require
ThinkTel. IN - 13024 Date : May 2013 Product: ShoreTel Ingate ThinkTel System version: ShoreTel 13.x
 ThinkTel Innovation Network App Note IN - 13024 Date : May 2013 Product: ShoreTel Ingate ThinkTel System version: ShoreTel 13.x ShoreTel, Ingate & ThinkTel for SIP Trunking SIP Trunking allows the use
ThinkTel Innovation Network App Note IN - 13024 Date : May 2013 Product: ShoreTel Ingate ThinkTel System version: ShoreTel 13.x ShoreTel, Ingate & ThinkTel for SIP Trunking SIP Trunking allows the use
MODELLING OF INTELLIGENCE IN INTERNET TELEPHONE SYSTEM
 MODELLING OF INTELLIGENCE IN INTERNET TELEPHONE SYSTEM Evelina Nicolova Pencheva, Vessela Liubomirova Georgieva Department of telecommunications, Technical University of Sofia, 7 Kliment Ohridski St.,
MODELLING OF INTELLIGENCE IN INTERNET TELEPHONE SYSTEM Evelina Nicolova Pencheva, Vessela Liubomirova Georgieva Department of telecommunications, Technical University of Sofia, 7 Kliment Ohridski St.,
Voice over IP Security
 Voice over IP Security Patrick Park Cisco Press Cisco Press 800 East 96th Street Indianapolis, Indiana 46240 USA vii Contents Introduction xvii Part I VoIP Security Fundamentals 3 Chapter 1 Working with
Voice over IP Security Patrick Park Cisco Press Cisco Press 800 East 96th Street Indianapolis, Indiana 46240 USA vii Contents Introduction xvii Part I VoIP Security Fundamentals 3 Chapter 1 Working with
The VoIP Vulnerability Scanner
 SiVuS (SiP Vulnerability Scanner) The VoIP Vulnerability Scanner User Guide v1.07 www.vopsecurity.org Contents 1 INTRODUCTION... 3 2 SIVUS FEATURES AND FUNCTIONALITY... 4 3 INSTALLATION... 5 4 OPERATION...
SiVuS (SiP Vulnerability Scanner) The VoIP Vulnerability Scanner User Guide v1.07 www.vopsecurity.org Contents 1 INTRODUCTION... 3 2 SIVUS FEATURES AND FUNCTIONALITY... 4 3 INSTALLATION... 5 4 OPERATION...
Transcoding and Call Centers with OpenSIPS Bogdan-Andrei Iancu Founder OpenSIPS Project OpenSIPS Solutions
 Transcoding and Call Centers with pensips Bogdan-Andrei Iancu Founder pensips Project pensips Solutions August 6-8 pensips 1.10 and more- ClueCon 2013 Chicago,US About pensips August 6-8 pensips 1.10 and
Transcoding and Call Centers with pensips Bogdan-Andrei Iancu Founder pensips Project pensips Solutions August 6-8 pensips 1.10 and more- ClueCon 2013 Chicago,US About pensips August 6-8 pensips 1.10 and
Basic Vulnerability Issues for SIP Security
 Introduction Basic Vulnerability Issues for SIP Security By Mark Collier Chief Technology Officer SecureLogix Corporation mark.collier@securelogix.com The Session Initiation Protocol (SIP) is the future
Introduction Basic Vulnerability Issues for SIP Security By Mark Collier Chief Technology Officer SecureLogix Corporation mark.collier@securelogix.com The Session Initiation Protocol (SIP) is the future
Time Warner ITSP Setup Guide
 October 14 Time Warner ITSP Setup Guide Author: Zultys Technical Support This configuration guide was created to assist knowledgeable vendors with configuring the Zultys MX Phone System with Time Warner
October 14 Time Warner ITSP Setup Guide Author: Zultys Technical Support This configuration guide was created to assist knowledgeable vendors with configuring the Zultys MX Phone System with Time Warner
ThinkTel ITSP with Registration Setup Quick Start Guide
 January 13 ThinkTel ITSP with Registration Setup Quick Start Guide Author: Zultys Technical Support This configuration guide was created to assist knowledgeable vendors with configuring the Zultys MX Phone
January 13 ThinkTel ITSP with Registration Setup Quick Start Guide Author: Zultys Technical Support This configuration guide was created to assist knowledgeable vendors with configuring the Zultys MX Phone
Configuration of the Intertex IX78 E-SBC with IP-PBXs and Telia SIP Trunking Services
 2010-03-07 Configuration of the Intertex IX78 E-SBC with IP-PBXs and Telia SIP Trunking Services For the IX78 ADSL T8 GW2 model with Telia SIP-anslutning using Telia Bredband Företag or Telia ProLane Table
2010-03-07 Configuration of the Intertex IX78 E-SBC with IP-PBXs and Telia SIP Trunking Services For the IX78 ADSL T8 GW2 model with Telia SIP-anslutning using Telia Bredband Företag or Telia ProLane Table
Abstract. Avaya Solution & Interoperability Test Lab
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring SIP Trunking between the Verizon Business VoIP Service with IP Trunking and Avaya Communication Manager Branch Edition Issue
Avaya Solution & Interoperability Test Lab Application Notes for Configuring SIP Trunking between the Verizon Business VoIP Service with IP Trunking and Avaya Communication Manager Branch Edition Issue
Arbor s Solution for ISP
 Arbor s Solution for ISP Recent Attack Cases DDoS is an Exploding & Evolving Trend More Attack Motivations Geopolitical Burma taken offline by DDOS attack Protests Extortion Visa, PayPal, and MasterCard
Arbor s Solution for ISP Recent Attack Cases DDoS is an Exploding & Evolving Trend More Attack Motivations Geopolitical Burma taken offline by DDOS attack Protests Extortion Visa, PayPal, and MasterCard
FLX UC1000/1500 Registering with Siemens HiPath 4000 & OpenScape Voice Server
 Technical Note FLX UC1000/1500 Registering with Siemens HiPath 4000 & OpenScape Voice Date: February 1, 2016 This technical note gives a detailed description on how to register a Revolabs FLX UC1000/1500
Technical Note FLX UC1000/1500 Registering with Siemens HiPath 4000 & OpenScape Voice Date: February 1, 2016 This technical note gives a detailed description on how to register a Revolabs FLX UC1000/1500
Setup Reference Guide for KX-TDE/NCP to SBC SIP Trunking
 Setup Reference Guide for KX-TDE/NCP to SBC SIP Trunking Method of connection by "WAN Global IP address directly" (i.e. SBC is the Perimeter Router device.) Panasonic IP-PBX (KX-TDE/NCP Version6 series),
Setup Reference Guide for KX-TDE/NCP to SBC SIP Trunking Method of connection by "WAN Global IP address directly" (i.e. SBC is the Perimeter Router device.) Panasonic IP-PBX (KX-TDE/NCP Version6 series),
Knowledgebase Solution
 Knowledgebase Solution Updated: 2/27/2014 Configuring an EdgeMarc for SIP trunking with an IP PBX This document describes the steps needed to configure an IP PBX behind the EdgeMarc which is pointing to
Knowledgebase Solution Updated: 2/27/2014 Configuring an EdgeMarc for SIP trunking with an IP PBX This document describes the steps needed to configure an IP PBX behind the EdgeMarc which is pointing to
CREATE A CUSTOMER... 2 SIP TRUNK ACCOUNTS...
 Contents CREATE A CUSTOMER... 2 SIP TRUNK ACCOUNTS... 3 CREATE THE MAIN SIP TRUNK ACCOUNT... 3 SETUP THE SIP TRUNK ACCOUNT... 4 EXTRA DIDS... 7 HOW TO..... 9 BILL FOR THE SIP TRUNKING SERVICE... 9 LIMIT
Contents CREATE A CUSTOMER... 2 SIP TRUNK ACCOUNTS... 3 CREATE THE MAIN SIP TRUNK ACCOUNT... 3 SETUP THE SIP TRUNK ACCOUNT... 4 EXTRA DIDS... 7 HOW TO..... 9 BILL FOR THE SIP TRUNKING SERVICE... 9 LIMIT
How To Understand The Purpose Of A Sip Aware Firewall/Alg (Sip) With An Alg (Sip) And An Algen (S Ip) (Alg) (Siph) (Network) (Ip) (Lib
 NetVanta Unified Communications Technical Note The Purpose of a SIP-Aware Firewall/ALG Introduction This technical note will explore the purpose of a Session Initiation Protocol (SIP)-aware firewall/application
NetVanta Unified Communications Technical Note The Purpose of a SIP-Aware Firewall/ALG Introduction This technical note will explore the purpose of a Session Initiation Protocol (SIP)-aware firewall/application
Recommended IP Telephony Architecture
 Report Number: I332-009R-2006 Recommended IP Telephony Architecture Systems and Network Attack Center (SNAC) Updated: 1 May 2006 Version 1.0 SNAC.Guides@nsa.gov This Page Intentionally Left Blank ii Warnings
Report Number: I332-009R-2006 Recommended IP Telephony Architecture Systems and Network Attack Center (SNAC) Updated: 1 May 2006 Version 1.0 SNAC.Guides@nsa.gov This Page Intentionally Left Blank ii Warnings
Direct IP Calls. Quick IP Call Mode
 Unicorn3112 Tips Direct IP Calls...1 Quick IP Call Mode...1 PSTN Pass Through...2 VoIP-to-PSTN Calls...2 PSTN-to-VoIP Calls...3 Route Calls to PSTN...4 Forward Calls to PSTN...4 Forward Calls to VoIP...4
Unicorn3112 Tips Direct IP Calls...1 Quick IP Call Mode...1 PSTN Pass Through...2 VoIP-to-PSTN Calls...2 PSTN-to-VoIP Calls...3 Route Calls to PSTN...4 Forward Calls to PSTN...4 Forward Calls to VoIP...4
OpenScape Business V2
 OpenScape Business V2 Tutorial VoIP Interfaces Version 1.0 Definitions HowTo An OpenScape Business HowTo describes the configuration of an OpenScape Business feature within the OpenScape Business administration.
OpenScape Business V2 Tutorial VoIP Interfaces Version 1.0 Definitions HowTo An OpenScape Business HowTo describes the configuration of an OpenScape Business feature within the OpenScape Business administration.
Bria iphone Edition User Guide
 Bria iphone Edition User Guide CounterPath Corporation CounterPath Corporation Suite 300, One Bentall Centre 505 Burrard Street, Box 95 Vancouver, BC V7X 1M3 Tel: 604.320.3344 sales@counterpath.com www.counterpath.com
Bria iphone Edition User Guide CounterPath Corporation CounterPath Corporation Suite 300, One Bentall Centre 505 Burrard Street, Box 95 Vancouver, BC V7X 1M3 Tel: 604.320.3344 sales@counterpath.com www.counterpath.com
Voice over IP Fundamentals
 Voice over IP Fundamentals Duration: 5 Days Course Code: GK3277 Overview: The aim of this course is for delegates to gain essential data networking and Voice over IP (VoIP) knowledge in a single, week-long
Voice over IP Fundamentals Duration: 5 Days Course Code: GK3277 Overview: The aim of this course is for delegates to gain essential data networking and Voice over IP (VoIP) knowledge in a single, week-long
Recommendations for secure deployment of an IP-PBX
 Internet Telephony Services Providers Association Recommendations for secure deployment of an IP-PBX Version 2 November 2013 Contact: admin@itspa.org.uk Contents Introduction... 3 Health Warning!... 3
Internet Telephony Services Providers Association Recommendations for secure deployment of an IP-PBX Version 2 November 2013 Contact: admin@itspa.org.uk Contents Introduction... 3 Health Warning!... 3
6.40A AudioCodes Mediant 800 MSBG
 AudioCodes Mediant 800 MSBG Page 1 of 66 6.40A AudioCodes Mediant 800 MSBG 1. Important Notes Check the SIP 3 rd Party Validation Website for current validation status. The SIP 3 rd party Validation Website
AudioCodes Mediant 800 MSBG Page 1 of 66 6.40A AudioCodes Mediant 800 MSBG 1. Important Notes Check the SIP 3 rd Party Validation Website for current validation status. The SIP 3 rd party Validation Website
OpenSIPS networking the VoIP
 pensips networking the VoIP Bogdan-Andrei Iancu CE Voice System Founder pensips Project What is pensips pensips is an open source, GPLed SIP server with High scalability (up to thousands of calls per second
pensips networking the VoIP Bogdan-Andrei Iancu CE Voice System Founder pensips Project What is pensips pensips is an open source, GPLed SIP server with High scalability (up to thousands of calls per second
SIP Trunk Bridge Fundamentals Avaya Communication Server 1000
 SIP Trunk Bridge Fundamentals Avaya Communication Server 1000 Release 7.6 NN43001-143 Issue 03.01 March 2013 2013 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure
SIP Trunk Bridge Fundamentals Avaya Communication Server 1000 Release 7.6 NN43001-143 Issue 03.01 March 2013 2013 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure
Application Security Testing
 Tstsec - Version: 1 09 July 2016 Application Security Testing Application Security Testing Tstsec - Version: 1 4 days Course Description: We are living in a world of data and communication, in which the
Tstsec - Version: 1 09 July 2016 Application Security Testing Application Security Testing Tstsec - Version: 1 4 days Course Description: We are living in a world of data and communication, in which the
Comparing Session Border Controllers to Firewalls with SIP Application Layer Gateways in Enterprise Voice over IP and Unified Communications Scenarios
 An Oracle White Paper June 2013 Comparing Session Border Controllers to Firewalls with SIP Application Layer Gateways in Enterprise Voice over IP and Unified Communications Scenarios Introduction Voice
An Oracle White Paper June 2013 Comparing Session Border Controllers to Firewalls with SIP Application Layer Gateways in Enterprise Voice over IP and Unified Communications Scenarios Introduction Voice
Configuring the Synapse SB67070 SIP Gateway from AT&T for Clearfly SIP Trunking. January 2013
 Configuring the Synapse SB67070 SIP Gateway from AT&T for Clearfly SIP Trunking January 2013 1 Introduction This guide was created to assist Synapse partners with configuring the Synapse SB67070 SIP Gateway
Configuring the Synapse SB67070 SIP Gateway from AT&T for Clearfly SIP Trunking January 2013 1 Introduction This guide was created to assist Synapse partners with configuring the Synapse SB67070 SIP Gateway
Configuration Notes 0217
 PBX Remote Line Extension using Mediatrix 1104 and 1204 Introduction... 2 Application Scenario... 2 Running the Unit Manager Network (UMN) Software... 3 Configuring the Mediatrix 1104... 6 Configuring
PBX Remote Line Extension using Mediatrix 1104 and 1204 Introduction... 2 Application Scenario... 2 Running the Unit Manager Network (UMN) Software... 3 Configuring the Mediatrix 1104... 6 Configuring
Virtual private network. Network security protocols VPN VPN. Instead of a dedicated data link Packets securely sent over a shared network Internet VPN
 Virtual private network Network security protocols COMP347 2006 Len Hamey Instead of a dedicated data link Packets securely sent over a shared network Internet VPN Public internet Security protocol encrypts
Virtual private network Network security protocols COMP347 2006 Len Hamey Instead of a dedicated data link Packets securely sent over a shared network Internet VPN Public internet Security protocol encrypts
Network Security and Firewall 1
 Department/program: Networking Course Code: CPT 224 Contact Hours: 96 Subject/Course WEB Access & Network Security: Theoretical: 2 Hours/week Year Two Semester: Two Prerequisite: NET304 Practical: 4 Hours/week
Department/program: Networking Course Code: CPT 224 Contact Hours: 96 Subject/Course WEB Access & Network Security: Theoretical: 2 Hours/week Year Two Semester: Two Prerequisite: NET304 Practical: 4 Hours/week
Setup Reference Guide for KX-NS1000 to SBC SIP Trunking
 Setup Reference Guide for KX-NS1000 to SBC SIP Trunking Method of connection by "WAN Global IP address directly" (i.e. SBC is the Perimeter Router device.) Panasonic IP-PBX (KX-NS1000 Version2 series),
Setup Reference Guide for KX-NS1000 to SBC SIP Trunking Method of connection by "WAN Global IP address directly" (i.e. SBC is the Perimeter Router device.) Panasonic IP-PBX (KX-NS1000 Version2 series),
SIP Trunking using Optimum Business Sip Trunk Adaptor and the Zultys MX250 IP PBX
 SIP Trunking using Optimum Business Sip Trunk Adaptor and the Zultys MX250 IP PBX Table of Contents Goal 3 Prerequisites 3 Zultys MX250 Configuration 4 Network Settings 4 Phone Registration and Assignment
SIP Trunking using Optimum Business Sip Trunk Adaptor and the Zultys MX250 IP PBX Table of Contents Goal 3 Prerequisites 3 Zultys MX250 Configuration 4 Network Settings 4 Phone Registration and Assignment
Integrating Citrix EasyCall Gateway with SwyxWare
 Integrating Citrix EasyCall Gateway with SwyxWare The EasyCall Gateway has been tested for interoperability with Swyx SwyxWare, versions 6.12 and 6.20. These integration tests were done by using EasyCall
Integrating Citrix EasyCall Gateway with SwyxWare The EasyCall Gateway has been tested for interoperability with Swyx SwyxWare, versions 6.12 and 6.20. These integration tests were done by using EasyCall
Chapter 5 Customizing Your Network Settings
 Chapter 5 Customizing Your Network Settings This chapter describes how to configure advanced networking features of the RangeMax NEXT Wireless Router WNR834B, including LAN, WAN, and routing settings.
Chapter 5 Customizing Your Network Settings This chapter describes how to configure advanced networking features of the RangeMax NEXT Wireless Router WNR834B, including LAN, WAN, and routing settings.
Technical Publications
 January 09 babytel ITSP Setup Author: Zultys Technical Support This document covers how to set up a babytel account. For ITSP Accounts ALG is required. For further information on ALG please refer to the
January 09 babytel ITSP Setup Author: Zultys Technical Support This document covers how to set up a babytel account. For ITSP Accounts ALG is required. For further information on ALG please refer to the
ZULTYS. Optimum Business Trunking and the Zultys MX250 IP PBX Configuration Guide
 ZULTYS Optimum Business Trunking and the Zultys MX250 IP PBX Configuration Guide ZULTYS Table of Contents 1. Overview 2. SIP Trunk Adaptor Set-up Instructions 3. Additional Set-up Information 4. International
ZULTYS Optimum Business Trunking and the Zultys MX250 IP PBX Configuration Guide ZULTYS Table of Contents 1. Overview 2. SIP Trunk Adaptor Set-up Instructions 3. Additional Set-up Information 4. International
Conducting an IP Telephony Security Assessment
 Conducting an IP Telephony Security Assessment Mark D. Collier Chief Technology Officer mark.collier@securelogix.com www.securelogix.com Presentation Outline Ground rules and scope Discovery Security policy
Conducting an IP Telephony Security Assessment Mark D. Collier Chief Technology Officer mark.collier@securelogix.com www.securelogix.com Presentation Outline Ground rules and scope Discovery Security policy
CSCE 465 Computer & Network Security
 CSCE 465 Computer & Network Security Instructor: Dr. Guofei Gu http://courses.cse.tamu.edu/guofei/csce465/ Firewall 1 Basic firewall concept Roadmap Filtering firewall Proxy firewall Network Address Translation
CSCE 465 Computer & Network Security Instructor: Dr. Guofei Gu http://courses.cse.tamu.edu/guofei/csce465/ Firewall 1 Basic firewall concept Roadmap Filtering firewall Proxy firewall Network Address Translation
ADTRAN SBC and Cisco Unified Call Manager SIP Trunk Interoperability
 6AOSSG0004-42A April 2013 Interoperability Guide ADTRAN SBC and Cisco Unified Call Manager SIP Trunk Interoperability This guide describes an example configuration used in testing the interoperability
6AOSSG0004-42A April 2013 Interoperability Guide ADTRAN SBC and Cisco Unified Call Manager SIP Trunk Interoperability This guide describes an example configuration used in testing the interoperability
Firewalls P+S Linux Router & Firewall 2013
 Firewalls P+S Linux Router & Firewall 2013 Firewall Techniques What is a firewall? A firewall is a hardware or software device which is configured to permit, deny, or proxy data through a computer network
Firewalls P+S Linux Router & Firewall 2013 Firewall Techniques What is a firewall? A firewall is a hardware or software device which is configured to permit, deny, or proxy data through a computer network
Presenter. Zane Ryan. Director Dot Force zane.ryan@dotforce.co.uk www.dotforce.co.uk
 Presenter Zane Ryan Director Dot Force zane.ryan@dotforce.co.uk www.dotforce.co.uk Ingate Systems Headquarters in Stockholm, Sweden North American subsidiary in New Hampshire Long Island, New York San
Presenter Zane Ryan Director Dot Force zane.ryan@dotforce.co.uk www.dotforce.co.uk Ingate Systems Headquarters in Stockholm, Sweden North American subsidiary in New Hampshire Long Island, New York San
Date 10/04/2012 TB Number TB - 12004 VoIP Security Threat Reminder
 VOIP SECURITY THREAT REMINDER Bulletin Authorisation Detail Author Andrew Kenyon Authorisation Wilf Wood Date 10/04/2012 TB Number TB - 12004 Description VoIP Security Threat Reminder Summary Please use
VOIP SECURITY THREAT REMINDER Bulletin Authorisation Detail Author Andrew Kenyon Authorisation Wilf Wood Date 10/04/2012 TB Number TB - 12004 Description VoIP Security Threat Reminder Summary Please use
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address
 Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
Deployment of TLS support with Open SIP Express Router
 Deployment of TLS support with Open SIP Express Router The aim of this guide is to describe how to implement the TLS support on a proxy OpenSER (http://www.openser.org/). TLS is an optional part of the
Deployment of TLS support with Open SIP Express Router The aim of this guide is to describe how to implement the TLS support on a proxy OpenSER (http://www.openser.org/). TLS is an optional part of the
Configuring Sonus SBC 1000/2000. with. Rogers Business Solution (RBS) SIP Trunking Service. Application Note
 Configuring Sonus SBC 1000/2000 with Rogers Business Solution (RBS) SIP Trunking Service Application Note Last Updated: March 2014 Copyright 2014, Sonus Networks, Inc. All rights reserved. This document
Configuring Sonus SBC 1000/2000 with Rogers Business Solution (RBS) SIP Trunking Service Application Note Last Updated: March 2014 Copyright 2014, Sonus Networks, Inc. All rights reserved. This document
Dos & DDoS Attack Signatures (note supplied by Steve Tonkovich of CAPTUS NETWORKS)
 Dos & DDoS Attack Signatures (note supplied by Steve Tonkovich of CAPTUS NETWORKS) Signature based IDS systems use these fingerprints to verify that an attack is taking place. The problem with this method
Dos & DDoS Attack Signatures (note supplied by Steve Tonkovich of CAPTUS NETWORKS) Signature based IDS systems use these fingerprints to verify that an attack is taking place. The problem with this method
NetVanta 7100 Exercise Service Provider SIP Trunk
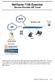 NetVanta 7100 Exercise Service Provider SIP Trunk PSTN NetVanta 7100 FXS 0/1 x2001 SIP Eth 0/0 x2004 SIP Server 172.23.102.87 Hosted by x2003 www.voxitas.com In this exercise, you will create a SIP trunk
NetVanta 7100 Exercise Service Provider SIP Trunk PSTN NetVanta 7100 FXS 0/1 x2001 SIP Eth 0/0 x2004 SIP Server 172.23.102.87 Hosted by x2003 www.voxitas.com In this exercise, you will create a SIP trunk
DSX. DSX SIP Setup. April 22, 2011 Issue 1.04. NEC Corporation of America 4 Forest Parkway, Shelton, CT 06484
 DSX DSX SIP Setup April 22, 2011 Issue 1.04 NEC Corporation of America 4 Forest Parkway, Shelton, CT 06484 Copyright 2011 NEC Corporation of America 6535 N. State Highway 161 Irving, TX 75039-2402 Communications
DSX DSX SIP Setup April 22, 2011 Issue 1.04 NEC Corporation of America 4 Forest Parkway, Shelton, CT 06484 Copyright 2011 NEC Corporation of America 6535 N. State Highway 161 Irving, TX 75039-2402 Communications
Digi Connect WAN Application Guide Using the Digi Connect WAN and Digi Connect VPN with a Wireless Router/Access Point
 Scenario Digi Connect WAN Application Guide Using the Digi Connect WAN and Digi Connect VPN with a Wireless Router/Access Point Digi Connect WAN and Digi Connect VPN are used for primary remote site connectivity.
Scenario Digi Connect WAN Application Guide Using the Digi Connect WAN and Digi Connect VPN with a Wireless Router/Access Point Digi Connect WAN and Digi Connect VPN are used for primary remote site connectivity.
SIP Trunking using the EdgeMarc Network Services Gateway and the Mitel 3300 ICP IP-PBX
 June 26th, 2014 SIP Trunking using the EdgeMarc Network Services Gateway and the Mitel 3300 ICP IP-PBX Page 1 of 30 Table of Contents 1 Overview... 3 2 Prerequisites... 3 3 Network Topology... 4 4 Description
June 26th, 2014 SIP Trunking using the EdgeMarc Network Services Gateway and the Mitel 3300 ICP IP-PBX Page 1 of 30 Table of Contents 1 Overview... 3 2 Prerequisites... 3 3 Network Topology... 4 4 Description
This Lecture. The Internet and Sockets. The Start 1969. If everyone just sends a small packet of data, they can all use the line at the same.
 This Lecture The Internet and Sockets Computer Security Tom Chothia How the Internet works. Some History TCP/IP Some useful network tools: Nmap, WireShark Some common attacks: The attacker controls the
This Lecture The Internet and Sockets Computer Security Tom Chothia How the Internet works. Some History TCP/IP Some useful network tools: Nmap, WireShark Some common attacks: The attacker controls the
ITSPA. Recommendations for secure deployment of an IP-PBX. Public. Node4 Limited Richard Buxton 31/05/2011
 ITSPA Recommendations for secure deployment of an IP-PBX Public Node4 Limited Richard Buxton 31/05/2011 Recommendations for secure deployment of an IP-PBX Node4 are members of the Internet Telephony Service
ITSPA Recommendations for secure deployment of an IP-PBX Public Node4 Limited Richard Buxton 31/05/2011 Recommendations for secure deployment of an IP-PBX Node4 are members of the Internet Telephony Service
ShoreTel, Ingate & Broadvox for SIP Trunking
 I n n o v a t i o n N e t w o r k A p p N o t e IN- 13056 Date : Sept, 2013 Product: ShoreTel Ingate Broadvox System version: ShoreTel 13.x ShoreTel, Ingate & Broadvox for SIP Trunking SIP Trunking allows
I n n o v a t i o n N e t w o r k A p p N o t e IN- 13056 Date : Sept, 2013 Product: ShoreTel Ingate Broadvox System version: ShoreTel 13.x ShoreTel, Ingate & Broadvox for SIP Trunking SIP Trunking allows
VOIP NETWORK CONFIGURATION GUIDE RELEASE 6.10
 TALKSWITCH DOCUMENTATION VOIP NETWORK CONFIGURATION GUIDE RELEASE 6.10 CT.TS005.002606 ANSWERS WITH INTELLIGENCE INTRODUCTION About this guide This guide will help you plan and configure a TalkSwitch system
TALKSWITCH DOCUMENTATION VOIP NETWORK CONFIGURATION GUIDE RELEASE 6.10 CT.TS005.002606 ANSWERS WITH INTELLIGENCE INTRODUCTION About this guide This guide will help you plan and configure a TalkSwitch system
Watson Networks. Carrier / Service Provider Guide. 445 Dexter Avenue - Suite 2050 Montgomery, Alabama 36104 WatsonNetworks.com
 WATSON NETWORKS Watson Networks Carrier / Service Provider Guide (855) 381-5700 24/7 Network Operations Center & Client Service Center 445 Dexter Avenue - Suite 2050 Montgomery, Alabama 36104 WatsonNetworks.com
WATSON NETWORKS Watson Networks Carrier / Service Provider Guide (855) 381-5700 24/7 Network Operations Center & Client Service Center 445 Dexter Avenue - Suite 2050 Montgomery, Alabama 36104 WatsonNetworks.com
