2-FACTOR AUTHENTICATION WITH
|
|
|
- Jason Greer
- 9 years ago
- Views:
Transcription
1 2-FACTOR AUTHENTICATION WITH 2X JUNE 2014
2 Two-Factor Authentication and Authy What is Two-Factor Authentication? Two-Factor Authentication is a process involving two stages to verify the identity of someone trying to access services in a computer or in a network. It provides an extra layer of protection. Two-factor authentication is a simple feature that asks for more than just your password. It requires both something you know (like a password) and something you have (like your phone). After you enter your password, you ll get a second code sent to your phone, and only after you enter it will you get into your account. Think of it as entering a PIN number, then getting a retina scan, like you see in every spy movie ever made. It s simply added security for your online accounts. What is Authy? Authy is a third-party provider of a token-based authentication process. Authy can be used for a number of online applications like Gmail, Wordpress, Evernote and Facebook. Most of these applications involve a normal sign-in process (username and password) which is the first authentication. Authy provides the second authentication via mobile app, browser or SMS. Visit to learn more. Authy and has chosen Authy to provide it s Two-Factor Authentication process. Two-Factor Authentication is available for customers using Enterprise and is enabled by contacting your Transparency Concierge or [email protected]. Once enabled, the Administrator has complete control of which users are required to use two-factor authentication and when it will be enabled for each user. 2
3 Administrator (Admin) Assigning Two-Factor Authentication to new and existing users Two-Factor Authentication is enabled by the Firm or Client Admin on a per user basis. To enable or disable this feature, follow these steps: 1. After signing into, select the Enterprise/Administration toggle. 2. Select Users icon in the main menu. Assign to Existing User: Select a user. In that user s Overview section you will see a checkbox that says Require Two-Factor Auth. Checking the box will require this user to perform a few easy steps to configure their Two-Factor Authentication and then require their use of Two-Factor Authentication for all subsequent logins. To disable this feature, simply deselect the checkbox. Assign to New User: To enable Two-Factor Authentication for a new user, create a new user by selecting the icon. Fill out the new user s information and check the box that says Require Two-Factor Auth. Finally, click the Create User button. The new user now requires Two-Factor Authentication to sign into. To disable this feature for the user, follow the instructions for Existing Users and deselect the Require Two Factor Auth checkbox. 3
4 Users Signing into with Two-Factor Authentication If an Admin has enabled Two-Factor Authentication for your user account, you will see the following screens when you log into. Only the Admin can determine if you have this security feature. Go to page 7 to see the 2-Factor Authentication Sequence Diagram Log into by entering your username and password on the sign in page. 2. You will be prompted to enter your Authy credentials, which is your mobile number. 3. Clicking Enable initiates your Authy account. (You will not have to repeat this process again.) 3 4. If you have an Authy account, will be added to your list of applications and you can immediately access authentication tokens If you do NOT have an account with Authy, you will receive a text message containing a link to install the Authy App. The Authy App is available for the following mobile devices: ios, Android and Blackberry. A Google Chrome App is also available for desktop users at chrome.google. com/webstore. 7a 6. Once the Authy App is downloaded, follow the instructions to complete the set up of your account. (See pages 5 and 6 for more information about the Mobile and Chrome Apps.) 8 7. Once this process is completed, you must Verify your Authy Account by supplying an authentication token on the Website. Access this token via: a. SMS (by clicking the link located below the token input field). Doing this will send your authentication token via text message to your mobile device. 9 b. Authy s Mobile App c. Authy s Chrome App 8. Click Enable. 9. Now that your account is enabled, every time you log into, you will be required to provide an authentication token. 4
5 Users Using Authy Mobile App to create authentication tokens Download the application to your mobile device through the respective app store and perform the steps below: 1. Once downloaded, open the Authy App. You will be prompted to enter your phone number s country code, which is 1 for the United States, and your mobile phone number. 2. Then enter your address. 3. Choose to Get Account Verification via: Phone Call or SMS. 4. You will be prompted to Enter Your Registration PIN. 5. Select Don t Allow or OK to receive push notifications on your mobile device for Authy. 6. Once this process is complete you will notice that is visible in the App, and by selecting you will see the 7-digit verification code that expires and refreshes every 20 seconds. 7. Finally, use the Authentication Token provided when you sign into
6 Users Using Authy Chrome App to create authentication tokens In the Chrome browser, go to chrome.google.com/webstore. 2. Search the store for Authy and download it. 3. Once downloaded, open Chrome App Launcher. 4. Click on the Authy logo in your Chrome App Launcher. 5. You will be prompted to enter your country code and mobile number with a message underneath that states: Cellphone number should be the same you use for Authy on your mobile phone and all your other devices. Select OK. 6. You will be prompted to enter your to create a new account. 7. Select to have verification sent via SMS or Call. 8. You will be prompted to Enter Your Registration PIN that you receive via SMS. 9. You will now see the full Authy application, however you must register a mobile device. Before doing so select the Devices tab in the Chrome App and enable Multi-Device by checking the box. 10. Finally, use the Authentication Token provided when you sign into
7 2-Factor Authentication Sequence Diagram CAN BE DONE AT ANY TIME Download Authy App Create Account Login to Authy App added to Authy App Get Token (123) Must be same information Login to requires 2-Factor Authentication Enter Authy Credentials Verify Token LOG INTO VIEWABILL WITH Access 7
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication. Mobile App Activation
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
ONLINE ACCOUNTABILITY FOR EVERY DEVICE. Quick Reference Guide V1.0
 ONLINE ACCOUNTABILITY FOR EVERY DEVICE Quick Reference Guide V1.0 TABLE OF CONTENTS ACCOUNT SET UP Creating an X3watch account DOWNLOADING AND INSTALLING X3WATCH System Requirements How to install on a
ONLINE ACCOUNTABILITY FOR EVERY DEVICE Quick Reference Guide V1.0 TABLE OF CONTENTS ACCOUNT SET UP Creating an X3watch account DOWNLOADING AND INSTALLING X3WATCH System Requirements How to install on a
Remote Access End User Reference Guide for SHC Portal Access
 Remote Access End User Reference Guide for SHC Portal Access Version 2.0 6/7/2012 This remote access end user reference guide provides an overview of how to install Citrix receiver, which is a required
Remote Access End User Reference Guide for SHC Portal Access Version 2.0 6/7/2012 This remote access end user reference guide provides an overview of how to install Citrix receiver, which is a required
MDM User Guide June 2012
 June 2012 Sy mantec Corporation, 2012 Page 1 Purpose of Document This document provides a guide for users of App Center to set up and use Mobile Device Management (MDM) capabilities. MDM allows the App
June 2012 Sy mantec Corporation, 2012 Page 1 Purpose of Document This document provides a guide for users of App Center to set up and use Mobile Device Management (MDM) capabilities. MDM allows the App
Booth Gmail Configuration
 Student email is accessed via a Booth branded Gmail service. Student mailboxes will be accessed via Gmail. Configure Gmail Settings Before you connect Gmail to send and receive Booth Gmail on your mobile
Student email is accessed via a Booth branded Gmail service. Student mailboxes will be accessed via Gmail. Configure Gmail Settings Before you connect Gmail to send and receive Booth Gmail on your mobile
Defender 5.7 - Token Deployment System Quick Start Guide
 Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Two-Factor Authentication
 Two-Factor Authentication The two-factor authentication system provides an additional level of security when signing in to Ryerson web applications via Ryerson s Central Authentication Service. When you
Two-Factor Authentication The two-factor authentication system provides an additional level of security when signing in to Ryerson web applications via Ryerson s Central Authentication Service. When you
Two Factor Authentication - USER GUIDE
 Two Factor Authentication - USER GUIDE Two Factor Authentication (or 2FA) is a two step verification process that provides an extra layer of security for you when accessing your account within Online Services.
Two Factor Authentication - USER GUIDE Two Factor Authentication (or 2FA) is a two step verification process that provides an extra layer of security for you when accessing your account within Online Services.
Using the Educator Dashboard
 Reference Guide Using the Educator Dashboard What s Inside How to Create Accounts Get to Know the Educator Dashboard How to Manage Licenses and Create Educators How to Give Accommodations to Students First
Reference Guide Using the Educator Dashboard What s Inside How to Create Accounts Get to Know the Educator Dashboard How to Manage Licenses and Create Educators How to Give Accommodations to Students First
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
MCBDirect Corporate Logging on using a Soft Token
 MCBDirect Corporate Logging on using a Soft Token Document issue: 2.1 Date of issue: September 2014 Contents About Soft Token authentication... 3 Logging onto MCBDirect Corporate online banking... 4 Soft
MCBDirect Corporate Logging on using a Soft Token Document issue: 2.1 Date of issue: September 2014 Contents About Soft Token authentication... 3 Logging onto MCBDirect Corporate online banking... 4 Soft
Install and End User Reference Guide for Direct Access to Citrix Applications
 Install and End User Reference Guide for Direct Access to Citrix Applications Version 1.0 7/26/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a
Install and End User Reference Guide for Direct Access to Citrix Applications Version 1.0 7/26/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a
Installing Logos SSL Certificates on Mobile Devices
 Installing Logos SSL Certificates on Mobile Devices Phase 1: Obtain the SSL Certificate You can obtain the SSL certificate in one of 2 ways. Method 1 Download the SSL certificate from it.logostech.net
Installing Logos SSL Certificates on Mobile Devices Phase 1: Obtain the SSL Certificate You can obtain the SSL certificate in one of 2 ways. Method 1 Download the SSL certificate from it.logostech.net
ATTENTION: End users should take note that Main Line Health has not verified within a Citrix
 Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client
 SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
Two-Factor Authentication
 Two-Factor Authentication Two-Factor Authentication is an enhanced security feature for Payentry. It adds an extra layer of protection to ensure only authorized users can gain access to your data. In addition
Two-Factor Authentication Two-Factor Authentication is an enhanced security feature for Payentry. It adds an extra layer of protection to ensure only authorized users can gain access to your data. In addition
Step 1. Step 2. Open your browser and go to https://accounts.bestcare.org and you will be presented a logon screen show below.
 Manage your two-factor options through the accounts.bestcare.org website. This website is available internally and externally of the organization. Like other services, if you connect while external of
Manage your two-factor options through the accounts.bestcare.org website. This website is available internally and externally of the organization. Like other services, if you connect while external of
This document is not an offer, commitment, representation or warranty by AT&T and is subject to change.
 To log in to Premier Online Care as a Corporate Responsibility User (CRU), you first need to register for a Premier account. This guide walks you through the steps of registering yourself using a PIN that
To log in to Premier Online Care as a Corporate Responsibility User (CRU), you first need to register for a Premier account. This guide walks you through the steps of registering yourself using a PIN that
Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are.
 Two Factor Authentication Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are. For example, one method currently utilized within
Two Factor Authentication Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are. For example, one method currently utilized within
Brainloop Secure Dataroom Version 8.30. QR Code Scanner Apps for ios Version 1.1 and for Android
 Brainloop Secure Dataroom Version 8.30 QR Code Scanner Apps for ios Version 1.1 and for Android Quick Guide Brainloop Secure Dataroom Version 8.30 Copyright Brainloop AG, 2004-2015. All rights reserved.
Brainloop Secure Dataroom Version 8.30 QR Code Scanner Apps for ios Version 1.1 and for Android Quick Guide Brainloop Secure Dataroom Version 8.30 Copyright Brainloop AG, 2004-2015. All rights reserved.
Establishing two-factor authentication with Cyberoam UTM appliances and HOTPin authentication server from Celestix Networks
 Establishing two-factor authentication with Cyberoam UTM appliances and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks
Establishing two-factor authentication with Cyberoam UTM appliances and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks
AWS Account Management Guidance
 AWS Account Management Guidance Introduction Security is a top priority at AWS. Every service that is offered is tightly controlled and adheres to a strict security standard. This is evident in the security
AWS Account Management Guidance Introduction Security is a top priority at AWS. Every service that is offered is tightly controlled and adheres to a strict security standard. This is evident in the security
Online Statements. About this guide. Important information
 Online Statements About this guide This guide shows you how to: View online statements, including CommBiz Activity Statements (Billing summaries) and online statements for Transaction Accounts, Credit
Online Statements About this guide This guide shows you how to: View online statements, including CommBiz Activity Statements (Billing summaries) and online statements for Transaction Accounts, Credit
Remote Desktop Web Access. Using Remote Desktop Web Access
 Remote Desktop Web Access What is RD Web Access? RD Web Access is a Computer Science service that allows you to access department software and machines from your Windows or OS X computer, both on and off
Remote Desktop Web Access What is RD Web Access? RD Web Access is a Computer Science service that allows you to access department software and machines from your Windows or OS X computer, both on and off
Install MS Office 365 on your Android mobile device
 Install MS Office 365 on your Android mobile device IT Documentation Team, March 2015 This factsheet contains instructions for installing the Office Mobile for Android phone and Office for Android tablet
Install MS Office 365 on your Android mobile device IT Documentation Team, March 2015 This factsheet contains instructions for installing the Office Mobile for Android phone and Office for Android tablet
Google 2 factor authentication User Guide
 Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
BlackBerry Universal Device Service. Demo Access. AUTHOR: System4u
 Demo Access AUTHOR: System4u BlackBerry Universal Device Service Revisions Date Version Description Author June 26 th 2012 1.0 Roman Přikryl September 25 th 2012 1.5 Revision Roman Přikryl October 5 th
Demo Access AUTHOR: System4u BlackBerry Universal Device Service Revisions Date Version Description Author June 26 th 2012 1.0 Roman Přikryl September 25 th 2012 1.5 Revision Roman Přikryl October 5 th
Establishing two-factor authentication with Barracuda NG Firewall and HOTPin authentication server from Celestix Networks
 Establishing two-factor authentication with Barracuda NG Firewall and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks EMEA
Establishing two-factor authentication with Barracuda NG Firewall and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks EMEA
UP L18 Enhanced MDM and Updated Email Protection Hands-On Lab
 UP L18 Enhanced MDM and Updated Email Protection Hands-On Lab Description The Symantec App Center platform continues to expand it s offering with new enhanced support for native agent based device management
UP L18 Enhanced MDM and Updated Email Protection Hands-On Lab Description The Symantec App Center platform continues to expand it s offering with new enhanced support for native agent based device management
Preparing your Domain to transfer from Go Daddy
 Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
Preparing your Domain to transfer from Go Daddy Before you can transfer a domain: Getting Started Disable domain privacy. If the privacy service forwards incoming email, check the ʻforward toʼ contact
DUO SECURITY CISCO VPN USER GUIDE 1/27/2016
 DUO SECURITY CISCO VPN USER GUIDE 1/27/2016 CONTENTS Enrolling Your Devices... 2 Install Cisco AnyConnect VPN Client... 6 Connecting to a PC with Microsoft Remote Desktop... 8 Disconnecting the AnyConnect
DUO SECURITY CISCO VPN USER GUIDE 1/27/2016 CONTENTS Enrolling Your Devices... 2 Install Cisco AnyConnect VPN Client... 6 Connecting to a PC with Microsoft Remote Desktop... 8 Disconnecting the AnyConnect
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
OneLogin Integration User Guide
 OneLogin Integration User Guide Table of Contents OneLogin Account Setup... 2 Create Account with OneLogin... 2 Setup Application with OneLogin... 2 Setup Required in OneLogin: SSO and AD Connector...
OneLogin Integration User Guide Table of Contents OneLogin Account Setup... 2 Create Account with OneLogin... 2 Setup Application with OneLogin... 2 Setup Required in OneLogin: SSO and AD Connector...
Instructions on accessing your journal s content on your new app
 Instructions on accessing your journal s content on your new app There are three main methods to access content on your journal app depending on how you normally view your journal online. 1. Do you normally
Instructions on accessing your journal s content on your new app There are three main methods to access content on your journal app depending on how you normally view your journal online. 1. Do you normally
Self-Service Portal Registering, downloading & activating a soft token
 Self-Service Portal Registering, downloading & activating a soft token Document issue: 3.2 Date of issue: September 2014 Contents Introduction... 3 About two-factor authentication... 3 About egrid authentication...
Self-Service Portal Registering, downloading & activating a soft token Document issue: 3.2 Date of issue: September 2014 Contents Introduction... 3 About two-factor authentication... 3 About egrid authentication...
QUICK INSTALLATION GUIDE ACTIVATE
 ACTIVATE ACTIVATE ACTIVATE 1. Activate the business cloud A. Service Activation: You will receive a confirmation e-mail within 2 hours maximum BASE business Cloud: Notification/Notificatie B. Go to https://cdashboard.
ACTIVATE ACTIVATE ACTIVATE 1. Activate the business cloud A. Service Activation: You will receive a confirmation e-mail within 2 hours maximum BASE business Cloud: Notification/Notificatie B. Go to https://cdashboard.
Getting Started. Getting Started with Time Warner Cable Business Class. Voice Manager. A Guide for Administrators and Users
 Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Downloading the GAIG Annuity App. Log In Screen. Home Page
 Downloading the GAIG Annuity App ios users: https://itunes.apple.com/us/app/gaig-annuity/id925743711?ls=1&mt=8 Android users: https://play.google.com/store/apps/details?id=com.gaig.annuity.app.mobile.android.agent
Downloading the GAIG Annuity App ios users: https://itunes.apple.com/us/app/gaig-annuity/id925743711?ls=1&mt=8 Android users: https://play.google.com/store/apps/details?id=com.gaig.annuity.app.mobile.android.agent
Business Banking Customer Login Experience for Enhanced Login Security
 Business Banking Customer Login Experience for Enhanced Login Security User credentials uniquely identify each person who uses the banking platform. The intent of authentication is unequivocal verification
Business Banking Customer Login Experience for Enhanced Login Security User credentials uniquely identify each person who uses the banking platform. The intent of authentication is unequivocal verification
Setting Up and Accessing VPN
 Setting Up and Accessing VPN Instructions for establishing remote access to the URMC network for PC or Mac Duo Two-Factor Authentication If you have already enrolled and setup Duo Two-Factor Authentication
Setting Up and Accessing VPN Instructions for establishing remote access to the URMC network for PC or Mac Duo Two-Factor Authentication If you have already enrolled and setup Duo Two-Factor Authentication
User Guide for eduroam
 User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
How To Get A Certificate From Digicert On A Pc Or Mac Or Mac (For Pc Or Ipa) On A Mac Or Ipad (For Mac) On Pc Or Pc Or Pb (For Ipa Or Mac) For Free
 DigiCert User Guide Version 3.7 Contents 1 User Management... 7 1.1 Roles and Account Access... 7 1.1.1 Administrator Role... 7 1.1.2 User Role... 7 1.1.3 CS Verified User... 7 1.1.4 EV Verified User...
DigiCert User Guide Version 3.7 Contents 1 User Management... 7 1.1 Roles and Account Access... 7 1.1.1 Administrator Role... 7 1.1.2 User Role... 7 1.1.3 CS Verified User... 7 1.1.4 EV Verified User...
Establishing two-factor authentication with Check Point and HOTPin authentication server from Celestix Networks
 Establishing two-factor authentication with Check Point and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks EMEA Celestix
Establishing two-factor authentication with Check Point and HOTPin authentication server from Celestix Networks Contact Information www.celestix.com Celestix Networks USA Celestix Networks EMEA Celestix
Contents First Time Setup... 2 Setting up the Legal Vault Client (KiteDrive)... 3 Setting up the KiteDrive Outlook Plugin... 10 Using the Legal Vault
 Contents First Time Setup... 2 Setting up the Legal Vault Client (KiteDrive)... 3 Setting up the KiteDrive Outlook Plugin... 10 Using the Legal Vault Outlook Plugin... 13 Using KiteDrive to Send Large
Contents First Time Setup... 2 Setting up the Legal Vault Client (KiteDrive)... 3 Setting up the KiteDrive Outlook Plugin... 10 Using the Legal Vault Outlook Plugin... 13 Using KiteDrive to Send Large
Recommended Browser Setting for MySBU Portal
 The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
Technology Services Group Procedures. IH Anywhere guide. 0 P a g e
 VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
Medstar Health Dell Services
 Medstar Health Dell Services Non Medstar Device Citrix Connectivity Guide October 2012 Sean Kaminski Dell Services System Admin Consultant 1 Table of Contents Overview...3 What is Citrix and why do I need
Medstar Health Dell Services Non Medstar Device Citrix Connectivity Guide October 2012 Sean Kaminski Dell Services System Admin Consultant 1 Table of Contents Overview...3 What is Citrix and why do I need
Comodo Mobile Device Manager Software Version 3.0
 Comodo Mobile Device Manager Software Version 3.0 CMDM Cloud Portal Setup Guide Guide Version 3.0.010515 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Mobile Device Manager - Cloud
Comodo Mobile Device Manager Software Version 3.0 CMDM Cloud Portal Setup Guide Guide Version 3.0.010515 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Mobile Device Manager - Cloud
Mobile Iron User Guide
 2015 Mobile Iron User Guide Information technology Sparrow Health System 9/1/2015 Contents...0 Introduction...2 Changes to your Mobile Device...2 Self Service Portal...3 Registering your new device...4
2015 Mobile Iron User Guide Information technology Sparrow Health System 9/1/2015 Contents...0 Introduction...2 Changes to your Mobile Device...2 Self Service Portal...3 Registering your new device...4
Employee Active Directory Self-Service Quick Setup Guide
 Employee Active Directory Self-Service Quick Setup Guide (V2.0) Last update: 11/5/2014 Copyright 2014 InfraDog Inc. All rights reserved Corporate Phone: +1 (416) 473-4096, Fax: +1 (888) 863-3936, Email:
Employee Active Directory Self-Service Quick Setup Guide (V2.0) Last update: 11/5/2014 Copyright 2014 InfraDog Inc. All rights reserved Corporate Phone: +1 (416) 473-4096, Fax: +1 (888) 863-3936, Email:
BOTTOM UP THINKING EMAIL SETUP INSTRUCTIONS. Unique businesses require unique solutions CLIENT GUIDE
 BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
The University of Texas Rio Grande Valley. Network Security. Create a Virtual Private. Network (VPN) Connection. Network Security How-to:
 Create a Virtual Private Network (VPN) Connection 1 Virtual Private Network (VPN) The VPN service provides secure (encrypted) off-campus connection to access University resources. Use VPN to access Oracle
Create a Virtual Private Network (VPN) Connection 1 Virtual Private Network (VPN) The VPN service provides secure (encrypted) off-campus connection to access University resources. Use VPN to access Oracle
Active Directory Integration for Greentree
 App Number: 010044 Active Directory Integration for Greentree Last Updated 14 th February 2013 Powered by: AppsForGreentree.com 2013 1 Table of Contents Features... 3 Options... 3 Important Notes... 3
App Number: 010044 Active Directory Integration for Greentree Last Updated 14 th February 2013 Powered by: AppsForGreentree.com 2013 1 Table of Contents Features... 3 Options... 3 Important Notes... 3
ACCESSING YOUR E-MAIL ON A MOBILE DEVICE
 ACCESSING YOUR E-MAIL ON A MOBILE DEVICE ACCESSING YOUR E-MAIL ON A MOBILE DEVICE You can access your USC e-mail on the following mobile devices: Android BlackBerry BlackBerry 10 iphone /ipod Touch /ipad
ACCESSING YOUR E-MAIL ON A MOBILE DEVICE ACCESSING YOUR E-MAIL ON A MOBILE DEVICE You can access your USC e-mail on the following mobile devices: Android BlackBerry BlackBerry 10 iphone /ipod Touch /ipad
Remote Access Services Microsoft Windows - Installation Guide
 Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
OFFICE 365 SELF- CONFIGURATION GUIDE
 IT HELPDESK, REPUBLIC POLYTECHNIC OFFICE 365 SELF- CONFIGURATION GUIDE Version 7.0 IT Helpdesk 6-30-2015 0 TABLE OF CONTENTS Things to note before proceeding with this guide:... 1 Office 365 ProPlus Installation
IT HELPDESK, REPUBLIC POLYTECHNIC OFFICE 365 SELF- CONFIGURATION GUIDE Version 7.0 IT Helpdesk 6-30-2015 0 TABLE OF CONTENTS Things to note before proceeding with this guide:... 1 Office 365 ProPlus Installation
PRACTICE LINK. Getting Started. version 1.0.x. Digita Support: 08450 180 909 Digita Sales: 08450 180 907 digita.com
 PRACTICE LINK Getting Started version 1.0.x Digita Support: 08450 180 909 Digita Sales: 08450 180 907 digita.com TL 28615 (11/17/14) Copyright Information Text copyright 2010 2014 by Thomson Reuters. All
PRACTICE LINK Getting Started version 1.0.x Digita Support: 08450 180 909 Digita Sales: 08450 180 907 digita.com TL 28615 (11/17/14) Copyright Information Text copyright 2010 2014 by Thomson Reuters. All
NextGen Setup Guide First-time Workstation Setup & Logging In
 This guide will help you get setup on NextGen for the first time you log onto a City or SBC computer. It will also help if you are a first-time user and need to create your password. I. Setting up Desktop
This guide will help you get setup on NextGen for the first time you log onto a City or SBC computer. It will also help if you are a first-time user and need to create your password. I. Setting up Desktop
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Enrollment Process for Android Devices
 1 Enrollment Process for Android Devices Introduction:... 2 Pre-requisites:... 2 Via SMS:... 2 Via Email:... 11 Self Service:... 19 2 Introduction: This is a brief guide to enrolling an android device
1 Enrollment Process for Android Devices Introduction:... 2 Pre-requisites:... 2 Via SMS:... 2 Via Email:... 11 Self Service:... 19 2 Introduction: This is a brief guide to enrolling an android device
Student BYOD - Olathe Public Schools
 Student BYOD - Olathe Public Schools Connecting a Personally-Owned Device to the District s Wireless Network Students may attach ONE personal electronic device to the Olathe Public Schools wireless network
Student BYOD - Olathe Public Schools Connecting a Personally-Owned Device to the District s Wireless Network Students may attach ONE personal electronic device to the Olathe Public Schools wireless network
WHAT IS VIRTUAL DESKTOP? WHAT YOU NEED LOG IN TO VIRTUAL DESKTOP SET UP CITRIX RECEIVER REMOTE ACCESS GUIDE
 WHAT IS VIRTUAL DESKTOP? Virtual Desktop is an online environment that allows you to access NSF applications and a virtual desktop that mimics a Windows 7 environment. You can use Virtual Desktop to use
WHAT IS VIRTUAL DESKTOP? Virtual Desktop is an online environment that allows you to access NSF applications and a virtual desktop that mimics a Windows 7 environment. You can use Virtual Desktop to use
Accessing Citrix on a MAC using OS X (Mountain Lion and Newer)
 These instructions are specifically designed for OS X Mountain Lion and Mavericks. Earlier versions of the OS will require a different installation. These instructions assume that there are no Java, Citrix
These instructions are specifically designed for OS X Mountain Lion and Mavericks. Earlier versions of the OS will require a different installation. These instructions assume that there are no Java, Citrix
Electronic Questionnaires for Investigations Processing (e-qip)
 January 2016 Electronic Questionnaires for Investigations Processing (e-qip) Login Instructions for first-time users OR users that have had their accounts reset Step 1 Access the e-qip Login screen at
January 2016 Electronic Questionnaires for Investigations Processing (e-qip) Login Instructions for first-time users OR users that have had their accounts reset Step 1 Access the e-qip Login screen at
Using the owncloud Android App
 Using the owncloud Android App Accessing your files on your owncloud server via the Web interface is easy and convenient, as you can use any Web browser on any operating system without installing special
Using the owncloud Android App Accessing your files on your owncloud server via the Web interface is easy and convenient, as you can use any Web browser on any operating system without installing special
VMware Identity Manager Administration
 VMware Identity Manager Administration VMware Identity Manager 2.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware Identity Manager Administration VMware Identity Manager 2.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Your guide to the HSBC Digital Security Device. HSBC Bank USA, N.A. 2015 All rights reserved.
 Your guide to the HSBC Digital Security Device HSBC Bank USA, N.A. 2015 All rights reserved. 1 Welcome to the next step in the evolution of online security Protecting your money and personal information
Your guide to the HSBC Digital Security Device HSBC Bank USA, N.A. 2015 All rights reserved. 1 Welcome to the next step in the evolution of online security Protecting your money and personal information
Wharf T&T. iwatch 2012 Mobile Apps User Guide (ios / Android)
 Wharf T&T iwatch 2012 Mobile Apps User Guide (ios / Android) 1 Table of Contents 1. iwatch... 3 1.1 Application download and login... 3 2. imonitor... 4 2.1 imonitor Setup Procedures (First-time user)...
Wharf T&T iwatch 2012 Mobile Apps User Guide (ios / Android) 1 Table of Contents 1. iwatch... 3 1.1 Application download and login... 3 2. imonitor... 4 2.1 imonitor Setup Procedures (First-time user)...
Connecting to the University Wireless Network
 Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Flexible Identity. OTP software tokens guide. Multi-Factor Authentication. version 1.0
 Flexible Identity Multi-Factor Authentication OTP software tokens guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services 2 of
Flexible Identity Multi-Factor Authentication OTP software tokens guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services 2 of
B&SC Office 365 Email
 B&SC Office 365 Email Microsoft Office 365 In its continuous efforts to provide the highest quality student experience, Bryant & Stratton College is giving students access to a new tool for accessing email.
B&SC Office 365 Email Microsoft Office 365 In its continuous efforts to provide the highest quality student experience, Bryant & Stratton College is giving students access to a new tool for accessing email.
Seagate Access for Personal Cloud User Manual
 Seagate Access for Personal Cloud User Manual 2015 Seagate Technology LLC. All rights reserved. Seagate, Seagate Technology, the Wave logo, and FreeAgent are trademarks or registered trademarks of Seagate
Seagate Access for Personal Cloud User Manual 2015 Seagate Technology LLC. All rights reserved. Seagate, Seagate Technology, the Wave logo, and FreeAgent are trademarks or registered trademarks of Seagate
Configuration Guide. BES12 Cloud
 Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
NetIQ Advanced Authentication Framework
 NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
NetIQ Advanced Authentication Framework Security Officer Guide Version 5.2.0 1 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 Authenticators Management 4 Card 8 Email OTP
Using the Jive for ios App
 Using the Jive for ios App TOC 2 Contents App Overview...3 System Requirements... 4 Release Notes...5 Which Version Am I Using?... 6 Connecting to Your Community... 11 Getting Started...12 Using Your Inbox...13
Using the Jive for ios App TOC 2 Contents App Overview...3 System Requirements... 4 Release Notes...5 Which Version Am I Using?... 6 Connecting to Your Community... 11 Getting Started...12 Using Your Inbox...13
How to Remotely Access the C&CDHB Network from a Personal Device
 How to Remotely Access the C&CDHB Network from a Personal Device 13/09/2012 Contents Installing the Citrix Receiver for Windows PCs... 2 Installing the Citrix Receiver for Mac OS X... 6 Installing the
How to Remotely Access the C&CDHB Network from a Personal Device 13/09/2012 Contents Installing the Citrix Receiver for Windows PCs... 2 Installing the Citrix Receiver for Mac OS X... 6 Installing the
YubiKey & OATH- TOTP Verification
 YubiKey & OATH- TOTP Verification February 7, 2014 YubiKey & OATH-TOTP Verification 2014 Yubico. All rights reserved. Page 1 of 11 Introduction Disclaimer Yubico is the leading provider of simple, open
YubiKey & OATH- TOTP Verification February 7, 2014 YubiKey & OATH-TOTP Verification 2014 Yubico. All rights reserved. Page 1 of 11 Introduction Disclaimer Yubico is the leading provider of simple, open
How To Use Salesforce Identity Features
 Identity Implementation Guide Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Identity Implementation Guide Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Connecting With Lifesize Cloud
 There are several different ways to connect to a Lifesize Cloud video conference meeting. This guide will provide you instructions for each way. Ways to Join a Lifesize Cloud Video Conference After getting
There are several different ways to connect to a Lifesize Cloud video conference meeting. This guide will provide you instructions for each way. Ways to Join a Lifesize Cloud Video Conference After getting
Coillte IT has recently upgraded the Remote Access Solution to a new platform.
 Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
Single Sign-On Portal User Reference (Okta Cloud SSO)
 Single Sign-On Portal User Reference (Okta Cloud SSO) Contents Okta Single Sign-on Portal... 3 Initial account creation and configuration... 3 First time manual login to the Okta Single Sign-on Portal...
Single Sign-On Portal User Reference (Okta Cloud SSO) Contents Okta Single Sign-on Portal... 3 Initial account creation and configuration... 3 First time manual login to the Okta Single Sign-on Portal...
Mobile Online Banking
 Mobile Online Banking User Guide Table of Contents Enrolling Through Traditional Online Banking, pg. 2 Enrolling Using Your Mobile Device, pg. 4 Login Screen, pg. 7 Locations, pg. 7 Mobile Browser View,
Mobile Online Banking User Guide Table of Contents Enrolling Through Traditional Online Banking, pg. 2 Enrolling Using Your Mobile Device, pg. 4 Login Screen, pg. 7 Locations, pg. 7 Mobile Browser View,
Advanced Configuration Steps
 Advanced Configuration Steps After you have downloaded a trial, you can perform the following from the Setup menu in the MaaS360 portal: Configure additional services Configure device enrollment settings
Advanced Configuration Steps After you have downloaded a trial, you can perform the following from the Setup menu in the MaaS360 portal: Configure additional services Configure device enrollment settings
LIBRARY MEMBER USER GUIDE
 LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account... 2 Part 2) How to checkout a magazine issue... 4 Part 3) How to download and use Zinio Reader 4... 8 a) For your PC... 8 b)
LIBRARY MEMBER USER GUIDE CONTENTS PAGE Part 1) How to create a new account... 2 Part 2) How to checkout a magazine issue... 4 Part 3) How to download and use Zinio Reader 4... 8 a) For your PC... 8 b)
Multi-Factor Authentication Job Aide
 To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
WatchDox for Mac User Guide
 WatchDox for Mac User Guide Version 2.3.0 Confidentiality This document contains confidential material that is proprietary to WatchDox. The information and ideas herein may not be disclosed to any unauthorized
WatchDox for Mac User Guide Version 2.3.0 Confidentiality This document contains confidential material that is proprietary to WatchDox. The information and ideas herein may not be disclosed to any unauthorized
Building a BYOD Program Using the Casper Suite. Technical Paper Casper Suite v9.4 or Later 17 September 2014
 Building a BYOD Program Using the Casper Suite Technical Paper Casper Suite v9.4 or Later 17 September 2014 JAMF Software, LLC 2014 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts
Building a BYOD Program Using the Casper Suite Technical Paper Casper Suite v9.4 or Later 17 September 2014 JAMF Software, LLC 2014 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts
Digital Storage Options MAKING ROOM IN THE CLOUD
 Digital Storage Options MAKING ROOM IN THE CLOUD Today s Objectives Download and start using Microsoft 365 and more specifically, OneDrive Digital Storage: Personally Speaking Dropbox As many accounts
Digital Storage Options MAKING ROOM IN THE CLOUD Today s Objectives Download and start using Microsoft 365 and more specifically, OneDrive Digital Storage: Personally Speaking Dropbox As many accounts
McAfee Directory Services Connector extension
 Getting Started Guide Revision A McAfee Directory Services Connector extension For use with epolicy Orchestrator 4.6.1 through 5.0 COPYRIGHT Copyright 2013 McAfee, Inc. Do not copy without permission.
Getting Started Guide Revision A McAfee Directory Services Connector extension For use with epolicy Orchestrator 4.6.1 through 5.0 COPYRIGHT Copyright 2013 McAfee, Inc. Do not copy without permission.
Welcome to the Opus Bank Mobile Banking App User Guide
 Welcome to the Opus Bank Mobile Banking App User Guide 1.855.678.7226 [email protected] www.opusbank.com Table of Contents Enroll in Mobile Banking & Install App... 3 Login to Personal Online
Welcome to the Opus Bank Mobile Banking App User Guide 1.855.678.7226 [email protected] www.opusbank.com Table of Contents Enroll in Mobile Banking & Install App... 3 Login to Personal Online
Connecting With Lifesize Cloud
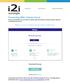 There are several different ways to connect to a Lifesize Cloud video conference meeting. This guide will provide you instructions for each way. Ways to Join a Lifesize Cloud Video Conference After getting
There are several different ways to connect to a Lifesize Cloud video conference meeting. This guide will provide you instructions for each way. Ways to Join a Lifesize Cloud Video Conference After getting
Integrating ConnectWise Service Desk Ticketing with the Cisco OnPlus Portal
 Integrating ConnectWise Service Desk Ticketing with the Cisco OnPlus Portal This Application Note explains how to configure ConnectWise PSA (Professional Service Automation) application settings and Cisco
Integrating ConnectWise Service Desk Ticketing with the Cisco OnPlus Portal This Application Note explains how to configure ConnectWise PSA (Professional Service Automation) application settings and Cisco
Zoho CRM and Google Apps Synchronization
 Zoho CRM and Google Apps Synchronization Table of Contents End User Integration Points 1. Contacts 2. Calendar 3. Email 4. Tasks 5. Docs 3 6 8 11 12 Domain-Wide Points of Integration 1. Authentication
Zoho CRM and Google Apps Synchronization Table of Contents End User Integration Points 1. Contacts 2. Calendar 3. Email 4. Tasks 5. Docs 3 6 8 11 12 Domain-Wide Points of Integration 1. Authentication
Configuring an Email Client to Connect to CASS Mail Servers
 Configuring an Email Client to Connect to CASS Mail Servers Table of Contents Introduction... 2 Webmail... 2 Settings... 2 Forwarding... 2 Email Client Configuration... 3 Outlook 2003... 3 Outlook 2007...
Configuring an Email Client to Connect to CASS Mail Servers Table of Contents Introduction... 2 Webmail... 2 Settings... 2 Forwarding... 2 Email Client Configuration... 3 Outlook 2003... 3 Outlook 2007...
Posting Job Orders. mindscope Staffing and Recruiting Software www.mindscope.com
 Posting Job Orders CURA Technical Support Email: [email protected] Phone: 1.888.322.2362 x 555 Posting Job Orders Page 1 Table of Contents Posting Jobs Orders... 2 Posting Jobs on Your Website...
Posting Job Orders CURA Technical Support Email: [email protected] Phone: 1.888.322.2362 x 555 Posting Job Orders Page 1 Table of Contents Posting Jobs Orders... 2 Posting Jobs on Your Website...
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources (DUO)
 Akin Gump Strauss Hauer & Feld LLP Remote Access Resources (DUO) Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2015 Akin Gump Strauss Hauer & Feld LLP Check Point
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources (DUO) Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2015 Akin Gump Strauss Hauer & Feld LLP Check Point
How do I use Citrix Staff Remote Desktop
 How do I use Citrix Staff Remote Desktop September 2014 Initial Log On In order to login into the new Citrix system, you need to go to the following web address. https://remotets.tees.ac.uk/ Be sure to
How do I use Citrix Staff Remote Desktop September 2014 Initial Log On In order to login into the new Citrix system, you need to go to the following web address. https://remotets.tees.ac.uk/ Be sure to
How To Send Mail From A Macbook Access To A Pc Or Ipad With A Password Protected Email Address (Monroe Access) On A Pc (For Macbook) Or Ipa (For Ipa) On Pc Or Macbook (For
 Email client settings: Incoming Mail (IMAP) Server requires SSL: Outgoing Mail (SMTP) Server requires TLS or SSL: Account Name: Email Address: Password: imap.gmail.com Use SSL: Yes Port: 993 smtp.gmail.com
Email client settings: Incoming Mail (IMAP) Server requires SSL: Outgoing Mail (SMTP) Server requires TLS or SSL: Account Name: Email Address: Password: imap.gmail.com Use SSL: Yes Port: 993 smtp.gmail.com
Getting Started. with VitalSource Bookshelf. How to Access your ebooks Using VitalSource Bookshelf
 Getting Started with VitalSource Bookshelf How to Access your ebooks Using VitalSource Bookshelf Table of Contents Step 1: Accessing VitalSource Bookshelf Online... 1 Step 2: Configuring Your Account for
Getting Started with VitalSource Bookshelf How to Access your ebooks Using VitalSource Bookshelf Table of Contents Step 1: Accessing VitalSource Bookshelf Online... 1 Step 2: Configuring Your Account for
