Secure and simple authentication via mobile phone
|
|
|
- Tabitha Taylor
- 10 years ago
- Views:
Transcription
1 Mobile ID Secure and simple authentication via mobile phone Mobile ID provides your employees and customers with a convenient and secure way to login to applications and online portals. It also makes it easier than ever before to confirm and execute online transactions.
2 The mobile phone as key to the online world Mobile ID gives you, your employees and customers secure access to online applications and provides verifiable confirmation for all kinds of transactions. All the user needs is a mobile phone with one of the latest generation SIM cards available for all customers of Swisscom, Sunrise and Salt. Mobile ID can redeem hardware tokens, SMS and password solutions for accessing your solutions and raises the process to a uniquely simple and secure level. The simplicity of the Mobile ID for your employees or customers is matched by its straightforward and low-cost integration for you as a company or official body. We offer you a complete service package at clearly calculable monthly costs. «Mobile ID is a forwardlooking service with a promising future. It provides an ideal correlation between security, userfriendliness and functionality.» Reto Grubenmann, Director Risk Consulting, KPMG User Login and transaction with Mobile ID Application or portal Authentication Connection Mobile ID Service
3 A comprehensive service that caters to your needs Your applications and portals can be connected easily to the cloud-based Mobile ID Service via an interface. Integration does not require any software or specific Graphic User Interfaces (GUI). Mobile ID can also be seamlessly integrated into your login process via standard protocols such as SOAP or REST, RADIUS or SAML and is compatible with solutions such as Microsoft ADFS. Use the Mobile ID for: 1. Secure access to > Online portals > Cloud services > Mobile apps > VPN accesses > Remote workstations > CRM and ERP workflows The Service offers: > Rollout of the Mobile ID SIM cards to the users > Free choice and dynamic definition of the text displayed to the Mobile ID user > Comprehensive Selfcare portal with 24/7 telephone support and comprehensive help for replacement and life-cycle of the Mobile ID > SLA with guaranteed availability > Geo Location allows restricting access from undesirable countries 2. The straightforward confirmation of > Transactions, for example in the finance area > Various processes in the Business-to-Business environment > Expressions of will: activation of electronic signatures User Login and transaction with Mobile ID Business applications Remote workstations, VPN, B2B portals, CRM/ERP system, Intranet applications, etc. Consumer portals E-banking, e-health, e-shopping, Web portals, mobile apps, cloud services, extranet applications, etc. Government applications E-government, citizens portals
4 Advantages at a glance Simple and secure Mobile ID is the simple and secure solution for login and transaction confirmation. Mobile ID operates without the need for any software installation or app and can be used intuitively. Customer-friendly Mobile ID is user-friendly and meets the growing need for mobility. The service offers your customers an identical form of access for different portals and applications as well as detailed support via the Selfcare portal. Obvious Mobile ID is based on the mobile phone s SIM card which is contained permanently in the device and therefore available at all times. Affordable and quantifiable We assumes the cost-intensive processes such as logistics and user support. The associated costs are included in the clearly calculable costs per user. Standardised The Mobile ID authentication protocol is based on a widely-established technical standard which guarantees a high level of investment protection. Comprehensive We assumes all the costs for handling, processes and logistics as well as for investments in hardware or software for the integration of Mobile ID. Flexible Mobile ID is highly scalable, can be deployed for any number of users and works on all standard mobile phones. FAQ & Support Order Lifecycle User Activation PIN recovery
5 Mobile ID supports multi-channel strategies «Mobile ID is the clever answer to changing patterns of consumer behaviour, enabling users to login to the e-banking (e-finance) of PostFinance from anywhere and at any time.» Your customers can communicate with you via laptop or tablet, at the Point-of-Sale or by telephone and use the Mobile ID to authenticate their identity to you. The customer experience always remains the same, regardless of which channel of communication or device they use. With Mobile ID you are choosing an innovative method which is ideally suited for use on any channel. Fabian Kollros, Head of Marketing Services, PostFinance User Login and transaction with Mobile ID Laptop Tablet Mobile phone POS Telephone Access to the applications and portals of a multi-channel strategy
6 Successful and award-winning Recognition for technology: European Identity & Cloud Award 2012 The European Identity & Cloud Award is given in recognition of the best projects and initiatives covering the themes of «Identity & Access Management» and «Cloud Security». In 2012 Swisscom received the «Special Award Mobile Security» for its Mobile ID. Business Prize: Mobile Business Best Practice 2014 The jury of experts of the St. Gallen Mobile Business Forum presented Swisscom Mobile ID with the award for «Mobile Business Best Practice 2014». Mobile ID impressed the jury of the University of St. Gallen (HSG) as «the most innovative mobile business solution for customer loyalty». «Mobile ID gives us a powerful tool for user authentication with mobile devices. The cost to us is minimal and thanks to the intuitive use it enjoys a high level of user acceptance.» Tom Sprenger, CTO, AdNovum Mobile ID awarded top marks in PCtipp test In September 2014 the Swiss computer magazine PCtipp conducted a study of the security and convenience of the e-banking solutions of Switzerland s leading banks. Mobile ID from PostFinance was revealed as one of the two most impressive services. Four steps to a secure login: A portal login procedure using Mobile ID (example). Portal Login Do you want to login to the portal? Username Password Yes No 1 2 User starts the login to the chosen portal. Login via Mobile ID. User confirms request on the mobile phone.
7 Get started What does the implementation process look like? Advice & Offer Contract Integration Starting up Our specialists look forward to hearing from you. Once you have concluded the contract take advantage of the clearly calculable prices and low annual costs. We will connect your application to the Mobile ID service quickly and simply. We will equip your Mobile ID users and provide all the support and process services. Portal Login Username Password Do you want to login to the portal? Good to know Want to see how Mobile ID works and whether the solution is suitable for you? In that case simply put it to the Yes test and connect your application to the service. The costs will be minimal the one-off usage costs for the first year plus the costs per active user. No 1 2 User starts the login to the chosen portal. Login via Mobile ID. User confirms request on the mobile phone. Please enter your Mobile ID PIN You are successfully logged in. Connected! 3 4 User enters his/her Mobile ID PIN on the mobile phone. User access to the portal has been activated.
8 We look forward to hearing from you. Sunrise: Salt: Swisscom:
Swisscom Mobile ID: Enabling an Ecosystem for Secure Mobile Authentication
 Swisscom Mobile ID: Enabling an Ecosystem for Secure Mobile Authentication The GSMA represents the interests of mobile operators worldwide. Spanning more than 220 countries, the GSMA unites nearly 800
Swisscom Mobile ID: Enabling an Ecosystem for Secure Mobile Authentication The GSMA represents the interests of mobile operators worldwide. Spanning more than 220 countries, the GSMA unites nearly 800
Authentication Solutions VERSATILE AND INNOVATIVE AUTHENTICATION SOLUTIONS TO SECURE AND ENABLE YOUR BUSINESS
 Authentication Solutions VERSATILE AND INNOVATIVE AUTHENTICATION SOLUTIONS TO SECURE AND ENABLE YOUR BUSINESS SafeNet Strong Authentication and Transaction Verification Solutions The Upward Spiral of Cybercrime
Authentication Solutions VERSATILE AND INNOVATIVE AUTHENTICATION SOLUTIONS TO SECURE AND ENABLE YOUR BUSINESS SafeNet Strong Authentication and Transaction Verification Solutions The Upward Spiral of Cybercrime
TABLE OF CONTENTS. Introduction 3 OTP SMS Two-Factor Authentication 5 Technical Overview 9 Features 10 Benefits 11 About MobiWeb 12 Quality 13
 TABLE OF CONTENTS Introduction 3 OTP SMS Two-Factor Authentication 5 Technical Overview 9 Features 10 Benefits 11 About MobiWeb 12 Quality 13 Introduction Our world is more Mobile now than ever. In 2013
TABLE OF CONTENTS Introduction 3 OTP SMS Two-Factor Authentication 5 Technical Overview 9 Features 10 Benefits 11 About MobiWeb 12 Quality 13 Introduction Our world is more Mobile now than ever. In 2013
Authentication Solutions. Versatile And Innovative Authentication Solutions To Secure And Enable Your Business
 Authentication Solutions Versatile And Innovative Authentication Solutions To Secure And Enable Your Business SafeNet Strong Authentication and Transaction Verification Solutions The Upward Spiral of Cybercrime
Authentication Solutions Versatile And Innovative Authentication Solutions To Secure And Enable Your Business SafeNet Strong Authentication and Transaction Verification Solutions The Upward Spiral of Cybercrime
Mobility, Security and Trusted Identities: It s Right In The Palm of Your Hands. Ian Wills Country Manager, Entrust Datacard
 Mobility, Security and Trusted Identities: It s Right In The Palm of Your Hands Ian Wills Country Manager, Entrust Datacard WHO IS ENTRUST DATACARD? 2 Entrust DataCard Datacard Corporation. Corporation.
Mobility, Security and Trusted Identities: It s Right In The Palm of Your Hands Ian Wills Country Manager, Entrust Datacard WHO IS ENTRUST DATACARD? 2 Entrust DataCard Datacard Corporation. Corporation.
Nevis Secure Web Interaction
 Nevis Secure Web Interaction Your Challenges Role-based Access Control End-to-End Security End-to-End Audit Trail Data Protection Delegated Administration Unauthorized Access Access Collaboration User
Nevis Secure Web Interaction Your Challenges Role-based Access Control End-to-End Security End-to-End Audit Trail Data Protection Delegated Administration Unauthorized Access Access Collaboration User
p@$5w0rd??_ 300% increase 280 MILLION 65% re-use passwords $22 per helpdesk call Passwords can no longer protect you
 Freja is an innovative solution to one of the biggest problems in the Internet era: How do you securely manage identities, access and credentials for a large number of users without costs going haywire?
Freja is an innovative solution to one of the biggest problems in the Internet era: How do you securely manage identities, access and credentials for a large number of users without costs going haywire?
NCSU SSO. Case Study
 NCSU SSO Case Study 2 2 NCSU Project Requirements and Goals NCSU Operating Environment Provide support for a number Apps and Programs Different vendors have their authentication databases End users must
NCSU SSO Case Study 2 2 NCSU Project Requirements and Goals NCSU Operating Environment Provide support for a number Apps and Programs Different vendors have their authentication databases End users must
Cybersecurity and Secure Authentication with SAP Single Sign-On
 Solution in Detail SAP NetWeaver SAP Single Sign-On Cybersecurity and Secure Authentication with SAP Single Sign-On Table of Contents 3 Quick Facts 4 Remember One Password Only 6 Log In Once to Handle
Solution in Detail SAP NetWeaver SAP Single Sign-On Cybersecurity and Secure Authentication with SAP Single Sign-On Table of Contents 3 Quick Facts 4 Remember One Password Only 6 Log In Once to Handle
WHITE PAPER SETTING UP AND USING ESTATE MASTER ON THE CLOUD INTRODUCTION
 WHITE PAPER SETTING UP AND USING ESTATE MASTER ON THE CLOUD INTRODUCTION Cloud Computing can provide great flexibility for the Estate Master user. You can access your feasibilities, manage you projects
WHITE PAPER SETTING UP AND USING ESTATE MASTER ON THE CLOUD INTRODUCTION Cloud Computing can provide great flexibility for the Estate Master user. You can access your feasibilities, manage you projects
WHITEPAPER. SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS
 WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
WHITEPAPER SECUREAUTH 2-FACTOR AS A SERVICE 2FaaS EXECUTIVE OVERVIEW 2-Factor as a Service (2FaaS) is a 100% cloud-hosted authentication solution that offers flexible security without compromising user
TrustedX - PKI Authentication. Whitepaper
 TrustedX - PKI Authentication Whitepaper CONTENTS Introduction... 3 1... 4 Use Scenarios... 5 Operation... 5 Architecture and Integration... 6 SAML and OAuth 7 RESTful Web Services 8 Monitoring and Auditing...
TrustedX - PKI Authentication Whitepaper CONTENTS Introduction... 3 1... 4 Use Scenarios... 5 Operation... 5 Architecture and Integration... 6 SAML and OAuth 7 RESTful Web Services 8 Monitoring and Auditing...
Remote Access End User Reference Guide for SHC Portal Access
 Remote Access End User Reference Guide for SHC Portal Access Version 2.0 6/7/2012 This remote access end user reference guide provides an overview of how to install Citrix receiver, which is a required
Remote Access End User Reference Guide for SHC Portal Access Version 2.0 6/7/2012 This remote access end user reference guide provides an overview of how to install Citrix receiver, which is a required
Hosted Contact Centre. Driving a more flexible customer service experience. Making technology easy and enjoyable
 Hosted Contact Centre Driving a more flexible customer service experience Making technology easy and enjoyable Page 2 Making technology easy and enjoyable Your contact centre is critical to the success
Hosted Contact Centre Driving a more flexible customer service experience Making technology easy and enjoyable Page 2 Making technology easy and enjoyable Your contact centre is critical to the success
API-Security Gateway Dirk Krafzig
 API-Security Gateway Dirk Krafzig Intro Digital transformation accelerates application integration needs Dramatically increasing number of integration points Speed Security Industrial robustness Increasing
API-Security Gateway Dirk Krafzig Intro Digital transformation accelerates application integration needs Dramatically increasing number of integration points Speed Security Industrial robustness Increasing
Intel Identity Protection Technology (IPT)
 Intel Identity Protection Technology (IPT) Enabling improved user-friendly strong authentication in VASCO's latest generation solutions June 2013 Steve Davies Solution Architect Intel Corporation 1 Copyright
Intel Identity Protection Technology (IPT) Enabling improved user-friendly strong authentication in VASCO's latest generation solutions June 2013 Steve Davies Solution Architect Intel Corporation 1 Copyright
EasyConnect. Any application - Any device - Anywhere. Faster, Simpler & Safer Networks
 EasyConnect Any application - Any device - Anywhere As cloud computing and mobile devices continue to reshape the way people work, workforces are becoming increasingly mobile. In order to remain competitive,
EasyConnect Any application - Any device - Anywhere As cloud computing and mobile devices continue to reshape the way people work, workforces are becoming increasingly mobile. In order to remain competitive,
Frequently Asked Questions Aerohive ID Manager
 Frequently Asked Questions Aerohive ID Manager About the Product... 1 Ordering FAQs... 4 Product Strategy... 6 About the Product 1. What is ID Manager? ID Manager is Aerohive s new cloud-based guest management
Frequently Asked Questions Aerohive ID Manager About the Product... 1 Ordering FAQs... 4 Product Strategy... 6 About the Product 1. What is ID Manager? ID Manager is Aerohive s new cloud-based guest management
REDCENTRIC N3 SECURE REMOTE ACCESS SERVICE DEFINITION. SD045 V4.1 Issue Date 04 07 2014. Page 1 Public
 REDCENTRIC N3 SECURE REMOTE ACCESS SERVICE DEFINITION SD045 V4.1 Issue Date 04 07 2014 Page 1 Public 1) SERVICE OVERVIEW 1.1) SERVICE OVERVIEW Redcentric s N3 Secure Remote Access (N3-SRA) Service offers
REDCENTRIC N3 SECURE REMOTE ACCESS SERVICE DEFINITION SD045 V4.1 Issue Date 04 07 2014 Page 1 Public 1) SERVICE OVERVIEW 1.1) SERVICE OVERVIEW Redcentric s N3 Secure Remote Access (N3-SRA) Service offers
Strong Authentication for Secure VPN Access
 Strong Authentication for Secure VPN Access Solving the Challenge of Simple and Secure Remote Access W H I T E P A P E R EXECUTIVE SUMMARY In today s competitive and efficiency-driven climate, organizations
Strong Authentication for Secure VPN Access Solving the Challenge of Simple and Secure Remote Access W H I T E P A P E R EXECUTIVE SUMMARY In today s competitive and efficiency-driven climate, organizations
Proposal Document TitleDocument Version 1.0 TitleDocument
 G-Cloud - Strong Authentication Service - Service Definition Proposal Document Author TitleDocument Version 1.0 TitleDocument Document publication date - 02/12/2014 Title Document Classification - Public
G-Cloud - Strong Authentication Service - Service Definition Proposal Document Author TitleDocument Version 1.0 TitleDocument Document publication date - 02/12/2014 Title Document Classification - Public
Digital Marketplace - G-Cloud
 Digital Marketplace - G-Cloud SharePoint Services Core offer 22 services in this area: 1. SharePoint Forms SharePoint comes with out-of-the-box web-based forms that allow for data to be captured for your
Digital Marketplace - G-Cloud SharePoint Services Core offer 22 services in this area: 1. SharePoint Forms SharePoint comes with out-of-the-box web-based forms that allow for data to be captured for your
SECUREAUTH IDP AND OFFICE 365
 WHITEPAPER SECUREAUTH IDP AND OFFICE 365 STRONG AUTHENTICATION AND SINGLE SIGN-ON FOR THE CLOUD-BASED OFFICE SUITE EXECUTIVE OVERVIEW As more and more enterprises move to the cloud, it makes sense that
WHITEPAPER SECUREAUTH IDP AND OFFICE 365 STRONG AUTHENTICATION AND SINGLE SIGN-ON FOR THE CLOUD-BASED OFFICE SUITE EXECUTIVE OVERVIEW As more and more enterprises move to the cloud, it makes sense that
Secure Your Enterprise with Usher Mobile Identity
 Secure Your Enterprise with Usher Mobile Identity Yong Qiao, Vice President of Software Engineering & Chief Security Architect, MicroStrategy Agenda Introduction to Usher Unlock the enterprise Dematerialize
Secure Your Enterprise with Usher Mobile Identity Yong Qiao, Vice President of Software Engineering & Chief Security Architect, MicroStrategy Agenda Introduction to Usher Unlock the enterprise Dematerialize
Cloud Computing and Government Services August 2013 Serdar Yümlü SAMPAŞ Information & Communication Systems
 eenviper White Paper #4 Cloud Computing and Government Services August 2013 Serdar Yümlü SAMPAŞ Information & Communication Systems 1 Executive Summary Cloud computing could revolutionise public services
eenviper White Paper #4 Cloud Computing and Government Services August 2013 Serdar Yümlü SAMPAŞ Information & Communication Systems 1 Executive Summary Cloud computing could revolutionise public services
HOTPin Integration Guide: Google Apps with Active Directory Federated Services
 HOTPin Integration Guide: Google Apps with Active Directory Federated Services Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as
HOTPin Integration Guide: Google Apps with Active Directory Federated Services Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as
SalesForce SSO with Active Directory Federated Services (ADFS) v2.0 Authenticating Users Using SecurAccess Server by SecurEnvoy
 SalesForce SSO with Active Directory Federated Services (ADFS) v2.0 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House
SalesForce SSO with Active Directory Federated Services (ADFS) v2.0 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House
Guide to Evaluating Multi-Factor Authentication Solutions
 Guide to Evaluating Multi-Factor Authentication Solutions PhoneFactor, Inc. 7301 West 129th Street Overland Park, KS 66213 1-877-No-Token / 1-877-668-6536 www.phonefactor.com Guide to Evaluating Multi-Factor
Guide to Evaluating Multi-Factor Authentication Solutions PhoneFactor, Inc. 7301 West 129th Street Overland Park, KS 66213 1-877-No-Token / 1-877-668-6536 www.phonefactor.com Guide to Evaluating Multi-Factor
Flexible Identity Federation
 Flexible Identity Federation Quick start guide version 1.0.1 Publication history Date Description Revision 2015.09.23 initial release 1.0.0 2015.12.11 minor updates 1.0.1 Copyright Orange Business Services
Flexible Identity Federation Quick start guide version 1.0.1 Publication history Date Description Revision 2015.09.23 initial release 1.0.0 2015.12.11 minor updates 1.0.1 Copyright Orange Business Services
COLLEAGUES. CLIENTS. CONNECTED. CLOUD.
 COLLEAGUES. CLIENTS. CONNECTED. CLOUD. THOMSON REUTERS Simplifying your life with powerful, integrated and innovative solutions. The Tax & Accounting business of Thomson Reuters provides the profession
COLLEAGUES. CLIENTS. CONNECTED. CLOUD. THOMSON REUTERS Simplifying your life with powerful, integrated and innovative solutions. The Tax & Accounting business of Thomson Reuters provides the profession
iii. You will not be able to access their iocbc account without a valid OTP token from 1 Nov 2012 onward.
 Login using One-Time Password (OTP) i. You can continue to login without the OTP from now till 31 October 2012 so long as you have not activated your token via the iocbc Online platform. ii. Once you have
Login using One-Time Password (OTP) i. You can continue to login without the OTP from now till 31 October 2012 so long as you have not activated your token via the iocbc Online platform. ii. Once you have
INTEGRATION GUIDE. DIGIPASS Authentication for Juniper SSL-VPN
 INTEGRATION GUIDE DIGIPASS Authentication for Juniper SSL-VPN Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data
INTEGRATION GUIDE DIGIPASS Authentication for Juniper SSL-VPN Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data
Enhancing productivity, enabling. Success. Sage CRM
 Enhancing productivity, enabling Success. Sage CRM Customer Relationship Management Customer Relationship Management (CRM) is far more than just a software application. It is a business solution that gives
Enhancing productivity, enabling Success. Sage CRM Customer Relationship Management Customer Relationship Management (CRM) is far more than just a software application. It is a business solution that gives
Securing e-government Web Portal Access Using Enhanced Two Factor Authentication
 Securing e-government Web Portal Access Using Enhanced Two Factor Authentication Ahmed Arara 1, El-Bahlul Emhemed Fgee 2, and Hamdi Ahmed Jaber 3 Abstract This paper suggests an advanced two-factor authentication
Securing e-government Web Portal Access Using Enhanced Two Factor Authentication Ahmed Arara 1, El-Bahlul Emhemed Fgee 2, and Hamdi Ahmed Jaber 3 Abstract This paper suggests an advanced two-factor authentication
epass OTP Authentication System White Paper
 Authentication System White Paper Directory 1. Overview...3 2. Principle of Authentication...4 3. Authentication System...6 4. Features...7 5. Technical Guideline...8 6. Typical Application...9 1. Overview
Authentication System White Paper Directory 1. Overview...3 2. Principle of Authentication...4 3. Authentication System...6 4. Features...7 5. Technical Guideline...8 6. Typical Application...9 1. Overview
Windows and MAC User Handbook Remote and Secure Connection Version 1.01 09/19/2013. User Handbook
 Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
WHITEPAPER SECUREAUTH AND CAC HSPD-12 AUTHENTICATION TO WEB, NETWORK, AND CLOUD RESOURCES
 WHITEPAPER SECUREAUTH AND CAC HSPD-12 AUTHENTICATION TO WEB, NETWORK, AND CLOUD RESOURCES Executive Overview U.S. Federal mandates dictates that personal with defense related initiatives must prove access
WHITEPAPER SECUREAUTH AND CAC HSPD-12 AUTHENTICATION TO WEB, NETWORK, AND CLOUD RESOURCES Executive Overview U.S. Federal mandates dictates that personal with defense related initiatives must prove access
Intel Identity Protection Technology Enabling improved user-friendly strong authentication in VASCO's latest generation solutions
 Intel Identity Protection Technology Enabling improved user-friendly strong authentication in VASCO's latest generation solutions June 2013 Dirk Roziers Market Manager PC Client Services Intel Corporation
Intel Identity Protection Technology Enabling improved user-friendly strong authentication in VASCO's latest generation solutions June 2013 Dirk Roziers Market Manager PC Client Services Intel Corporation
WatchGuard SSL 2.0 New Features
 WatchGuard SSL 2.0 New Features For Secure Remote Access, Identity Management, and Network Access Control Introduction WatchGuard SSL 2.0 unifies identity and access management capabilities, with features
WatchGuard SSL 2.0 New Features For Secure Remote Access, Identity Management, and Network Access Control Introduction WatchGuard SSL 2.0 unifies identity and access management capabilities, with features
Contactless Solutions
 Contactless Solutions Extends Windows Authentication ACCESS secure. Contactless Solutions Add contactless logical access control to your physical access control system w Three-component solution (Prox
Contactless Solutions Extends Windows Authentication ACCESS secure. Contactless Solutions Add contactless logical access control to your physical access control system w Three-component solution (Prox
Dell SonicWALL and SecurEnvoy Integration Guide. Authenticating Users Using SecurAccess Server by SecurEnvoy
 Dell SonicWALL and SecurEnvoy Integration Guide Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale
Dell SonicWALL and SecurEnvoy Integration Guide Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale
Move your business into the Cloud with one single, easy step.
 The Cloud Desktop For Business Unify Your Business IT Experience Move your business into the Cloud with one single, easy step. Secure all your apps & data in one place. What is OS33 Cloud Desktop for Business?
The Cloud Desktop For Business Unify Your Business IT Experience Move your business into the Cloud with one single, easy step. Secure all your apps & data in one place. What is OS33 Cloud Desktop for Business?
Beyond passwords: Protect the mobile enterprise with smarter security solutions
 IBM Software Thought Leadership White Paper September 2013 Beyond passwords: Protect the mobile enterprise with smarter security solutions Prevent fraud and improve the user experience with an adaptive
IBM Software Thought Leadership White Paper September 2013 Beyond passwords: Protect the mobile enterprise with smarter security solutions Prevent fraud and improve the user experience with an adaptive
How To Use Saml 2.0 Single Sign On With Qualysguard
 QualysGuard SAML 2.0 Single Sign-On Technical Brief Introduction Qualys provides its customer the option to use SAML 2.0 Single Sign On (SSO) authentication with their QualysGuard subscription. When implemented,
QualysGuard SAML 2.0 Single Sign-On Technical Brief Introduction Qualys provides its customer the option to use SAML 2.0 Single Sign On (SSO) authentication with their QualysGuard subscription. When implemented,
External authentication with Astaro AG Astaro Security Gateway UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy
 External authentication with Astaro AG Astaro Security Gateway UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010
External authentication with Astaro AG Astaro Security Gateway UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010
Authentication Solutions
 Authentication Solutions simplicity security freedom connection and protection on the move Business is going mobile. Today s agile organisations need to give their key people access to all their information
Authentication Solutions simplicity security freedom connection and protection on the move Business is going mobile. Today s agile organisations need to give their key people access to all their information
PostFiles. The file sharing and synchronization solution dedicated to professionals. www.oodrive.com
 PostFiles The file sharing and synchronization solution dedicated to professionals www.oodrive.com Share all file types, regardless of size or format. Synchronize and read files across several devices.
PostFiles The file sharing and synchronization solution dedicated to professionals www.oodrive.com Share all file types, regardless of size or format. Synchronize and read files across several devices.
Enhancing Productivity. Enabling Success. Sage CRM
 Enhancing Productivity. Enabling Success. Sage CRM Customer Relationship Management Customer Relationship Management (CRM) is far more than just a software application. It is a business solution that gives
Enhancing Productivity. Enabling Success. Sage CRM Customer Relationship Management Customer Relationship Management (CRM) is far more than just a software application. It is a business solution that gives
BENEFITS OF MOBILE DEVICE MANAGEMENT
 BENEFITS OF MOBILE DEVICE MANAGEMENT White Paper 2013 SUMMARY OVERVIEW This white paper outlines the benefits of Mobile Device Management in different use cases. SyncShield is a Mobile Device Management
BENEFITS OF MOBILE DEVICE MANAGEMENT White Paper 2013 SUMMARY OVERVIEW This white paper outlines the benefits of Mobile Device Management in different use cases. SyncShield is a Mobile Device Management
Why MobilityGuard OneGate?
 Any Scenario for Access Just One Solution Why MobilityGuard OneGate? Scenarios 1 Access from Anywhere 2 Strongly Identify Your Users 3 No more Post-IT notes with Single Sign-On 4 Three Click Access Administration
Any Scenario for Access Just One Solution Why MobilityGuard OneGate? Scenarios 1 Access from Anywhere 2 Strongly Identify Your Users 3 No more Post-IT notes with Single Sign-On 4 Three Click Access Administration
POS software: Microsoft Dynamics - Point of Sale FAQ
 POS software: Microsoft Dynamics - Point of Sale FAQ Q: I only have one retail store. I'd like to use a computer and software, but don't know if Microsoft Dynamics Point of Sale is a good fit. A: Point
POS software: Microsoft Dynamics - Point of Sale FAQ Q: I only have one retail store. I'd like to use a computer and software, but don't know if Microsoft Dynamics Point of Sale is a good fit. A: Point
DIS VPN Service Client Documentation
 DIS VPN Service Client Documentation Background ------------------------------------------------------------------------------------------------ 1 Downloading the Client ---------------------------------------------------------------------------------
DIS VPN Service Client Documentation Background ------------------------------------------------------------------------------------------------ 1 Downloading the Client ---------------------------------------------------------------------------------
nexus Hybrid Access Gateway
 Product Sheet nexus Hybrid Access Gateway nexus Hybrid Access Gateway nexus Hybrid Access Gateway uses the inherent simplicity of virtual appliances to create matchless security, even beyond the boundaries
Product Sheet nexus Hybrid Access Gateway nexus Hybrid Access Gateway nexus Hybrid Access Gateway uses the inherent simplicity of virtual appliances to create matchless security, even beyond the boundaries
WHITEPAPER SECURITY APPROACHES AND SECURITY TECHNOLOGIES IN INTEGRATION CLOUD
 WHITEPAPER SECURITY APPROACHES AND SECURITY TECHNOLOGIES IN INTEGRATION CLOUD TABLE OF CONTENTS 1 In this whitepaper... 3 2 User security... 4 2.1 Authentication... 4 2.2 Authorization & Access Control...
WHITEPAPER SECURITY APPROACHES AND SECURITY TECHNOLOGIES IN INTEGRATION CLOUD TABLE OF CONTENTS 1 In this whitepaper... 3 2 User security... 4 2.1 Authentication... 4 2.2 Authorization & Access Control...
QUICK INSTALLATION GUIDE ACTIVATE
 ACTIVATE ACTIVATE ACTIVATE 1. Activate the business cloud A. Service Activation: You will receive a confirmation e-mail within 2 hours maximum BASE business Cloud: Notification/Notificatie B. Go to https://cdashboard.
ACTIVATE ACTIVATE ACTIVATE 1. Activate the business cloud A. Service Activation: You will receive a confirmation e-mail within 2 hours maximum BASE business Cloud: Notification/Notificatie B. Go to https://cdashboard.
YOUR SECURE ONLINE VAULT. DSWISS AG BADENERSTRASSE 281 CH-8003 ZURICH [email protected] +41 44 515 11 11 www.securesafe.com
 YOUR SECURE ONLINE VAULT DSWISS AG BADENERSTRASSE 281 CH-8003 ZURICH [email protected] +41 44 515 11 11 www.securesafe.com SECURESAFE PRIVACY MANIFESTO We have embedded privacy directly into the design
YOUR SECURE ONLINE VAULT DSWISS AG BADENERSTRASSE 281 CH-8003 ZURICH [email protected] +41 44 515 11 11 www.securesafe.com SECURESAFE PRIVACY MANIFESTO We have embedded privacy directly into the design
Ensuring the Security of Your Company s Data & Identities. a best practices guide
 a best practices guide Ensuring the Security of Your Company s Data & Identities Symplified 1600 Pearl Street, Suite 200» Boulder, CO, 80302» www.symplified.com» @Symplified Safe and Secure Identity Management
a best practices guide Ensuring the Security of Your Company s Data & Identities Symplified 1600 Pearl Street, Suite 200» Boulder, CO, 80302» www.symplified.com» @Symplified Safe and Secure Identity Management
External authentication with Fortinet Fortigate UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy
 External authentication with Fortinet Fortigate UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External authentication with Fortinet Fortigate UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
Entrust IdentityGuard Comprehensive
 Entrust IdentityGuard Comprehensive Entrust IdentityGuard Comprehensive is a five-day, hands-on overview of Entrust Course participants will gain experience planning, installing and configuring Entrust
Entrust IdentityGuard Comprehensive Entrust IdentityGuard Comprehensive is a five-day, hands-on overview of Entrust Course participants will gain experience planning, installing and configuring Entrust
How to login with the RSA Token?
 How to login with the RSA Token? How does the RSA Token work? To log on to your online trading account, you need to enter your existing username and password as usual, followed by the unique security code
How to login with the RSA Token? How does the RSA Token work? To log on to your online trading account, you need to enter your existing username and password as usual, followed by the unique security code
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
UNILY FOR SHAREPOINT ONLINE
 The World s Largest SharePoint Product and Resource Directory UNILY FOR SHAREPOINT ONLINE A superior 5 star product. SharePoint Online has never looked better Product Reviewed by Ron Charity January 2015
The World s Largest SharePoint Product and Resource Directory UNILY FOR SHAREPOINT ONLINE A superior 5 star product. SharePoint Online has never looked better Product Reviewed by Ron Charity January 2015
ACCESSING MICROSOFT OFFICE 365 FREE STUDENT RESOURCES
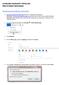 ACCESSING MICROSOFT OFFICE 365 FREE STUDENT RESOURCES Download and Installation instructions 1. Go here and sign into Office 365 with your username and password. Username: [email protected]
ACCESSING MICROSOFT OFFICE 365 FREE STUDENT RESOURCES Download and Installation instructions 1. Go here and sign into Office 365 with your username and password. Username: [email protected]
The Top 5 Federated Single Sign-On Scenarios
 The Top 5 Federated Single Sign-On Scenarios Table of Contents Executive Summary... 1 The Solution: Standards-Based Federation... 2 Service Provider Initiated SSO...3 Identity Provider Initiated SSO...3
The Top 5 Federated Single Sign-On Scenarios Table of Contents Executive Summary... 1 The Solution: Standards-Based Federation... 2 Service Provider Initiated SSO...3 Identity Provider Initiated SSO...3
GoToMyPC reviewer s guide
 GoToMyPC reviewer s guide Citrix GoToMyPC reviewer s guide Thank you for evaluating Citrix GoToMyPC. This guide will introduce you to the current GoToMyPC functionality and help you effectively evaluate
GoToMyPC reviewer s guide Citrix GoToMyPC reviewer s guide Thank you for evaluating Citrix GoToMyPC. This guide will introduce you to the current GoToMyPC functionality and help you effectively evaluate
External Authentication with Windows 2003 Server with Routing and Remote Access service Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Windows 2003 Server with Routing and Remote Access service Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845
External Authentication with Windows 2003 Server with Routing and Remote Access service Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845
How To Integrate Watchguard Xtm With Secur Access With Watchguard And Safepower 2Factor Authentication On A Watchguard 2T (V2) On A 2Tv 2Tm (V1.2) With A 2F
 External Authentication with Watchguard XTM Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington Business Park
External Authentication with Watchguard XTM Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington Business Park
Swisscom Mobile Device Services Quick Start Guide: Set-up Remote Management basic. Mobile Device Services Februar 2014
 Swisscom Mobile Device Services Quick Start Guide: Set-up Remote Management basic Mobile Device Services Februar 2014 Contents 2 Login «Welcome to Swisscom MDS» First steps Step 1: Installing the MDM certificate
Swisscom Mobile Device Services Quick Start Guide: Set-up Remote Management basic Mobile Device Services Februar 2014 Contents 2 Login «Welcome to Swisscom MDS» First steps Step 1: Installing the MDM certificate
Nomad Vault: a 100% secure virtual private network accessible via thumb drive
 Nomad Vault: a 100% secure virtual private network accessible via thumb drive Nomad Vault: securely save, share and transfer your data, anywhere you go How can you prevent losing everything when your laptop
Nomad Vault: a 100% secure virtual private network accessible via thumb drive Nomad Vault: securely save, share and transfer your data, anywhere you go How can you prevent losing everything when your laptop
Collaboration solutions for midsized businesses Buyer s guide
 Collaboration solutions for midsized businesses Buyer s guide Increase productivity by improving collaboration across and beyond your business. Give employees access to the information, people and resources
Collaboration solutions for midsized businesses Buyer s guide Increase productivity by improving collaboration across and beyond your business. Give employees access to the information, people and resources
Single Sign On. SSO & ID Management for Web and Mobile Applications
 Single Sign On and ID Management Single Sign On SSO & ID Management for Web and Mobile Applications Presenter: Manish Harsh Program Manager for Developer Marketing Platforms of NVIDIA (Visual Computing
Single Sign On and ID Management Single Sign On SSO & ID Management for Web and Mobile Applications Presenter: Manish Harsh Program Manager for Developer Marketing Platforms of NVIDIA (Visual Computing
Endpoint Protection Small Business Edition 2013?
 Symantec Endpoint Protection Small Business Edition 2013 Customer FAQ FAQ: Endpoint Security What is Symantec Endpoint Protection Small Business Edition 2013? is a new solution that offers simple, fast,
Symantec Endpoint Protection Small Business Edition 2013 Customer FAQ FAQ: Endpoint Security What is Symantec Endpoint Protection Small Business Edition 2013? is a new solution that offers simple, fast,
Workspot Configuration Guide for the Cisco Adaptive Security Appliance
 Workspot Configuration Guide for the Cisco Adaptive Security Appliance Workspot, Inc. 1/27/2015 Cisco ASA and Workspot Overview The Cisco Adaptive Security Appliance (ASA) provides organizations with secure,
Workspot Configuration Guide for the Cisco Adaptive Security Appliance Workspot, Inc. 1/27/2015 Cisco ASA and Workspot Overview The Cisco Adaptive Security Appliance (ASA) provides organizations with secure,
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client
 SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
Security Upgrade FAQs
 Security Upgrade FAQs Your online security is important to us. Soon, we ll be upgrading your online banking experience to include a new security service, which is known in the online security industry
Security Upgrade FAQs Your online security is important to us. Soon, we ll be upgrading your online banking experience to include a new security service, which is known in the online security industry
LDAP Authentication Configuration Appendix
 1 Overview LDAP Authentication Configuration Appendix Blackboard s authentication technology is considered a focal point in the company s ability to provide true enterprise software. Natively, the Blackboard
1 Overview LDAP Authentication Configuration Appendix Blackboard s authentication technology is considered a focal point in the company s ability to provide true enterprise software. Natively, the Blackboard
RSA SecurID Two-factor Authentication
 RSA SecurID Two-factor Authentication Today, we live in an era where data is the lifeblood of a company. Now, security risks are more pressing as attackers have broadened their targets beyond financial
RSA SecurID Two-factor Authentication Today, we live in an era where data is the lifeblood of a company. Now, security risks are more pressing as attackers have broadened their targets beyond financial
WHITEPAPER. 13 Questions You Must Ask When Integrating Office 365 With Active Directory
 WHITEPAPER 13 Questions You Must Ask When Integrating Office 365 With Active Directory Many organizations have begun their push to the cloud with a handful of applications. Microsoft s Office 365 offering
WHITEPAPER 13 Questions You Must Ask When Integrating Office 365 With Active Directory Many organizations have begun their push to the cloud with a handful of applications. Microsoft s Office 365 offering
Axway API Portal. Putting APIs first for your developer ecosystem
 Axway API Portal Putting APIs first for your developer ecosystem To fully embrace an API-first strategy, it s no longer enough to simply develop and deploy APIs. Organizations need broad API management
Axway API Portal Putting APIs first for your developer ecosystem To fully embrace an API-first strategy, it s no longer enough to simply develop and deploy APIs. Organizations need broad API management
Server Virtualization Cloud Partner Training Series
 Server Virtualization Cloud Partner Training Series August 2015 Agenda What is it? Benefits Industry Landscape Evolve is Different How we can help you $ucceed Who is a fit? Who is a challenge? Key Questions
Server Virtualization Cloud Partner Training Series August 2015 Agenda What is it? Benefits Industry Landscape Evolve is Different How we can help you $ucceed Who is a fit? Who is a challenge? Key Questions
The Security Behind Sticky Password
 The Security Behind Sticky Password Technical White Paper version 3, September 16th, 2015 Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and
The Security Behind Sticky Password Technical White Paper version 3, September 16th, 2015 Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and
ONE INTEGRATED PLATFORM FOR ALL YOUR PRINT, SCAN AND DEVICE MANAGEMENT. uniflow canon.com.au/business
 ONE INTEGRATED PLATFORM FOR ALL YOUR PRINT, SCAN AND DEVICE MANAGEMENT uniflow canon.com.au/business INTEGRATED, PRODUCTIVE CONTROL OF PRINTING, COPYING SCANNING, AND FAXING uniflow is an integrated print
ONE INTEGRATED PLATFORM FOR ALL YOUR PRINT, SCAN AND DEVICE MANAGEMENT uniflow canon.com.au/business INTEGRATED, PRODUCTIVE CONTROL OF PRINTING, COPYING SCANNING, AND FAXING uniflow is an integrated print
VMware Horizon DaaS: Desktop as a Cloud Service (DaaS)
 VMware Horizon DaaS: Desktop as a Cloud Service (DaaS) 1 43% of workforce using 3+ devices 74% of employees use consumer technologies, due to a lack of alternatives from IT 2010 The year the number of
VMware Horizon DaaS: Desktop as a Cloud Service (DaaS) 1 43% of workforce using 3+ devices 74% of employees use consumer technologies, due to a lack of alternatives from IT 2010 The year the number of
Signicat white paper. Signicat Solutions. This document introduces the Signicat solutions for digital identities and electronic signatures 2015-08
 Signicat white paper Signicat Solutions This document introduces the Signicat solutions for digital identities and electronic signatures 2015-08 Version 1.1 2015-08-20 Disclaimer Please note that this
Signicat white paper Signicat Solutions This document introduces the Signicat solutions for digital identities and electronic signatures 2015-08 Version 1.1 2015-08-20 Disclaimer Please note that this
Global M2M Platform vodacom.co.za/business
 Vodacom Global M2M Global M2M Platform vodacom.co.za/business Vodacom Global M2M Opening up the potential for a new range of smart M2M services Vodacom Global M2M Services are designed to help you accelerate
Vodacom Global M2M Global M2M Platform vodacom.co.za/business Vodacom Global M2M Opening up the potential for a new range of smart M2M services Vodacom Global M2M Services are designed to help you accelerate
How to Use YourPrintCloud Wireless Printing for Xerox Copiers & Printers. revised 30 Jan 2015 1
 How to Use YourPrintCloud Wireless Printing for Xerox Copiers & Printers revised 30 Jan 2015 1 WIRELESS PRINTING SMARTPHONES YourPrintCloud Mobile smartphone apps support PDF s, Microsoft Word, PowerPoint,
How to Use YourPrintCloud Wireless Printing for Xerox Copiers & Printers revised 30 Jan 2015 1 WIRELESS PRINTING SMARTPHONES YourPrintCloud Mobile smartphone apps support PDF s, Microsoft Word, PowerPoint,
The Who, What, When, Where and Why of IAM Bob Bentley
 The Who, What, When, Where and Why of IAM Bob Bentley Product Management Director October 2014 It s a Jungle Out There IAM is more than just provisioning user accounts and managing access to web pages
The Who, What, When, Where and Why of IAM Bob Bentley Product Management Director October 2014 It s a Jungle Out There IAM is more than just provisioning user accounts and managing access to web pages
Enterprise Security Management CheckPoint SecuRemote VPN v4.0 for pcanywhere
 Enterprise Security Management CheckPoint SecuRemote VPN v4.0 for pcanywhere White Paper 7KH#&KDOOHQJH Virtual Private Networks (VPNs) provides a powerful means of protecting the privacy and integrity
Enterprise Security Management CheckPoint SecuRemote VPN v4.0 for pcanywhere White Paper 7KH#&KDOOHQJH Virtual Private Networks (VPNs) provides a powerful means of protecting the privacy and integrity
University of Strathclyde: Information Services Directorate Operational Plan for 2014/15
 University of Strathclyde: Information Services Directorate Operational Plan for 2014/15 Enabling the future: transforming our information systems and technology 2014/15 2014/2015 CONTENTS 1 DRIVERS, STRATEGIC
University of Strathclyde: Information Services Directorate Operational Plan for 2014/15 Enabling the future: transforming our information systems and technology 2014/15 2014/2015 CONTENTS 1 DRIVERS, STRATEGIC
Department of Supply & Services (CIMS) RSA Web Express User Guide v1.2
 Department of Supply & Services (CIMS) RSA Web Express User Guide v1.2 Created: May 22, 2008 Updated: April 23, 2009 The RSA Web Express web express web site automates functions required to deploy hardware
Department of Supply & Services (CIMS) RSA Web Express User Guide v1.2 Created: May 22, 2008 Updated: April 23, 2009 The RSA Web Express web express web site automates functions required to deploy hardware
White Paper What is Noah Mobile?
 NoahMobile Documentation White Paper What is Noah Mobile? Noah Mobile, a new service included with Noah System 4.5, lets you work with your patients on mobile devices such Android tablets and IPads! With
NoahMobile Documentation White Paper What is Noah Mobile? Noah Mobile, a new service included with Noah System 4.5, lets you work with your patients on mobile devices such Android tablets and IPads! With
BYOD. and Mobile Device Security. Shirley Erp, CISSP CISA November 28, 2012
 BYOD and Mobile Device Security Shirley Erp, CISSP CISA November 28, 2012 Session is currently being recorded, and will be available on our website at http://www.utsystem.edu/compliance/swcacademy.html.
BYOD and Mobile Device Security Shirley Erp, CISSP CISA November 28, 2012 Session is currently being recorded, and will be available on our website at http://www.utsystem.edu/compliance/swcacademy.html.
Secure WiFi Access in Schools and Educational Institutions. WPA2 / 802.1X and Captive Portal based Access Security
 Secure WiFi Access in Schools and Educational Institutions WPA2 / 802.1X and Captive Portal based Access Security Cloudessa, Inc. Palo Alto, CA July 2013 Overview The accelerated use of technology in the
Secure WiFi Access in Schools and Educational Institutions WPA2 / 802.1X and Captive Portal based Access Security Cloudessa, Inc. Palo Alto, CA July 2013 Overview The accelerated use of technology in the
Out-of-Band Multi-Factor Authentication Cloud Services Whitepaper
 Out-of-Band Multi-Factor Authentication Cloud Services Whitepaper StrikeForce Technologies, Inc. 1090 King Georges Post Rd. Edison, NJ 08837, USA Tel: 732 661-9641 Fax: 732 661-9647 http://www.sftnj.com
Out-of-Band Multi-Factor Authentication Cloud Services Whitepaper StrikeForce Technologies, Inc. 1090 King Georges Post Rd. Edison, NJ 08837, USA Tel: 732 661-9641 Fax: 732 661-9647 http://www.sftnj.com
