24/7/365 Remote Computer Support
|
|
|
- Cameron Lindsey
- 8 years ago
- Views:
Transcription
1 24/7/365 Remote Computer Support
2 Program Overview
3 What is ACN Premium Technical Support? We are the premier provider of technical assistance for your computer and peripheral devices We deliver support 24/7/365 right from the convenience of your home Our technicians are all North American based and provide service to your computer via a secure remote log-in session You no longer have to bring your computer to a service center to receive support You don t have to invite a stranger into your home or business to receive support
4 Availability Available nationwide in the U.S and Canada, with the exception of Quebec*. Service offerings for residential customers as well as small businesses. Supported Devices PCs and Macs Home and small office networks (includes wireless) Peripherals: -PDAs and other mobile devices -MP3 players -Digital cameras -Printers -Fax machines -Scanners *Service is available in English only
5 Product Offerings
6 Residential Plans Basic Plus Remote Basic Plus Remote with Protect & Assist Basic Plus Remote with Backup & Assist Complete Remote Small Business Plans Business Basic Business Basic with Protect & Assist Business Basic with Backup & Assist Business Premier
7 Residential Plans
8 Basic Plus Remote 24/7/365 support for all your computer or tablet needs, including peripheral devices Maintenance, updates and software installation Removal of annoying pop-up messages and viruses to improve computer optimization Basic training on your computer and common third party software 1 year service agreement required Plans cover service for 1, up to 3, or up to 5 computers or tablets Minimum system requirements: Windows XP SP3, Windows Vista or Windows 7; Mac 10.4, 10.5 or 10.6 and a high speed Internet connection
9 Basic Plus with Protect & Assist Includes all features of Basic Plus Remote with the added security of antivirus software Installation of anti-virus software with 1-year license Automatic scans of system to help detect, block, and remove viruses, spyware, and adware Basic Plus with Backup & Assist Includes all features of Basic Plus Remote with complete automatic Mozy online backup of all files up to every hour Storage for files from the PC s internal hard drive Simple file recovery
10 Complete Remote 24/7/365 support for all your computer or tablets needs, including peripheral devices Maintenance, updates and software installation Removal of annoying pop-up messages and viruses to improve computer optimization Basic training on your computer and common third party software Includes anti-virus software Includes complete data backup from Mozy 1 year service agreement required Plans cover service for 1, up to 3, or up to 5 computers or tablets Minimum system requirements: Windows XP SP3, Windows Vista or Windows 7 and a high speed Internet connection
11 Small Business Plans
12 Business Basic 24/7/365 support for all your computer or tablet needs, including peripheral devices Maintenance, updates and software installation Removal of annoying pop-up messages and viruses to improve computer optimization Basic training on your computer and common third party software 1 year service agreement required Plans cover service for 1, up to 3, 5, 7 or 10 computers or tablets Minimum system requirements: Windows XP SP3, Windows Vista or Windows 7; Mac 10.4, 10.5 or 10.6 and a high speed Internet connection
13 Business Basic with Protect & Assist Includes all features of Business Basic with the added security of antivirus software Installation of anti-virus software with 1-year license Automatic scans of system to help detect, block, and remove viruses, spyware, and adware Business Basic with Backup & Assist Includes all features of Business Basic with complete automatic Mozy online backup of all files up to every hour Storage for files from the PC s internal hard drive Simple file recovery
14 Business Premier 24/7/365 support for all your computer or tablet needs, including peripheral devices Maintenance, updates and software installation Removal of annoying pop-up messages and viruses to improve computer optimization Basic training on your computer and common third party software Includes anti-virus software Includes complete data backup from Mozy 1 year service agreement required Plans cover service for 1, up to 3, 5, 7 or 10 computers or tablets Minimum system requirements: Windows XP SP3, Windows Vista or Windows 7 and a high speed Internet connection
15 Ordering
16 ORDERING YOUR ACN DIRECT ONLINE STORE
17 ORDERING SHOP NOW
18 ORDERING BUSINESS PLANS
19 ORDERING RESIDENTIAL PLANS
20 ORDERING RESIDENTIAL PLANS Complete Remote Plan Offering
21 Create An Account
ResNet Computer Consultant Job Description
 ResNet Computer Consultant Job Description Description: ResNet is the Internet Service Provider within the Residence Halls and Family and Graduate Housing at Montana State University. In addition to providing
ResNet Computer Consultant Job Description Description: ResNet is the Internet Service Provider within the Residence Halls and Family and Graduate Housing at Montana State University. In addition to providing
The I.T. Experience Service and Pricing List 2015
 The I.T. Experience Service and Pricing List 2015 Hourly Rates and Additional Services Residential Hourly Rate Hourly Rate All Services $59.00/hr. Business Hourly Rate Hourly Rate All Services $85.00/hr.
The I.T. Experience Service and Pricing List 2015 Hourly Rates and Additional Services Residential Hourly Rate Hourly Rate All Services $59.00/hr. Business Hourly Rate Hourly Rate All Services $85.00/hr.
CS Hotline is a unique service made specially for Computer Repair Businesses CS Hotline stands for Computer Support Hotline and is part of Team 9
 CS Hotline is a unique service made specially for Computer Repair Businesses CS Hotline stands for Computer Support Hotline and is part of Team 9 Global Services. Serving more than 400 Business worldwide
CS Hotline is a unique service made specially for Computer Repair Businesses CS Hotline stands for Computer Support Hotline and is part of Team 9 Global Services. Serving more than 400 Business worldwide
Basic Virus Removal Steps
 Basic Virus Removal Steps The following are basic instructions on how to remove most virus and spyware that infect Windows XP/Vista computers. By providing these, we hope that users will be able to remove
Basic Virus Removal Steps The following are basic instructions on how to remove most virus and spyware that infect Windows XP/Vista computers. By providing these, we hope that users will be able to remove
Canada ACN Home Security
 Canada ACN Home Security Vivint 12.15.15 2 Security Statistics 1 home in 5 will suffer a burglary or fire incident in the next 6 years 1 home in 3 will have a medical emergency this year A burglary occurs
Canada ACN Home Security Vivint 12.15.15 2 Security Statistics 1 home in 5 will suffer a burglary or fire incident in the next 6 years 1 home in 3 will have a medical emergency this year A burglary occurs
Computer Repair Services
 Computer Repair Services PC and MAC Support Virus/Spyware/Malware removal Service Troubleshoot and Resolve Windows/OS X errors Diagnose Customer Desktop, Laptop Hardware Issues Install/Uninstall Software,
Computer Repair Services PC and MAC Support Virus/Spyware/Malware removal Service Troubleshoot and Resolve Windows/OS X errors Diagnose Customer Desktop, Laptop Hardware Issues Install/Uninstall Software,
Desktop or Laptop Diagnostic $49.99
 Desktop or Laptop Diagnostic $49.99 Important: For online service we need a high-speed internet connection and a working computer Expert Troubleshooting $49.99 On-Line, MSD Office On-Site Computer hardware
Desktop or Laptop Diagnostic $49.99 Important: For online service we need a high-speed internet connection and a working computer Expert Troubleshooting $49.99 On-Line, MSD Office On-Site Computer hardware
Business white paper. HP Business Helpdesk. System requirements and supported products
 Business white paper HP Business Helpdesk System requirements and supported products Minimum system requirements Operating System: Current Licensed Versions for Microsoft, Apple or Android, detailed in
Business white paper HP Business Helpdesk System requirements and supported products Minimum system requirements Operating System: Current Licensed Versions for Microsoft, Apple or Android, detailed in
Service Description: Dell On Call HelpDesk Service
 Service Description: On Call HelpDesk Service This Service Description is between you ( You or Customer ) and Canada Inc., (, Our or We ). The below services provide consumer customers with 24x7 telephone
Service Description: On Call HelpDesk Service This Service Description is between you ( You or Customer ) and Canada Inc., (, Our or We ). The below services provide consumer customers with 24x7 telephone
Contents. Hardware Configuration... 27 Uninstalling Shortcuts Black...29
 Contents Getting Started...1 Check your Computer meets the Minimum Requirements... 1 Ensure your Computer is Running in Normal Sized Fonts... 7 Ensure your Regional Settings are Correct... 9 Reboot your
Contents Getting Started...1 Check your Computer meets the Minimum Requirements... 1 Ensure your Computer is Running in Normal Sized Fonts... 7 Ensure your Regional Settings are Correct... 9 Reboot your
Before You Begin Installing Your Scanner
 Before You Begin Installing Your Scanner We recommend that you confirm the following before installing your scanner: MINIMUM SYSTEM REQUIREMENTS Review the following system and Internet requirements to
Before You Begin Installing Your Scanner We recommend that you confirm the following before installing your scanner: MINIMUM SYSTEM REQUIREMENTS Review the following system and Internet requirements to
Web-based Installation of Symantec AntiVirus
 College of Health and Social Welfare Technology Services Author: Ryan Stafford, IS Professional 3 Date: December 7, 2006 Web-based Installation of Symantec AntiVirus The University of Alaska Anchorage
College of Health and Social Welfare Technology Services Author: Ryan Stafford, IS Professional 3 Date: December 7, 2006 Web-based Installation of Symantec AntiVirus The University of Alaska Anchorage
Using Spy Sweeper for Windows Author: Jocelyn Kasamoto
 WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
QHR Accuro EMR IT Hardware Requirements
 QHR Accuro EMR IT Hardware Requirements Hardware Requirements for Accuro EMR Table of Contents Local Install Platform:... 3 Server Requirements:... 3 Workstation Requirements:... 4 Peripheral Requirements:...
QHR Accuro EMR IT Hardware Requirements Hardware Requirements for Accuro EMR Table of Contents Local Install Platform:... 3 Server Requirements:... 3 Workstation Requirements:... 4 Peripheral Requirements:...
Student Wireless Network Access Guide (Windows) v2.6 (21/09/2011)
 Student Wireless Network Access Guide (Windows) v2.6 (21/09/2011) To successfully connect the student wireless network your device must meet the following requirements: Windows XP with Service Pack 2,
Student Wireless Network Access Guide (Windows) v2.6 (21/09/2011) To successfully connect the student wireless network your device must meet the following requirements: Windows XP with Service Pack 2,
AT&T Internet Security Suite - powered by McAfee. Installation Guide (for Clean Machine with No Anti-Virus Installed)
 AT&T Internet Security Suite - powered by McAfee Installation Guide (for Clean Machine with No Anti-Virus Installed) Contents 2 Contents Introduction 3 Chapters 1. Start Download Manager...4 2. Select
AT&T Internet Security Suite - powered by McAfee Installation Guide (for Clean Machine with No Anti-Virus Installed) Contents 2 Contents Introduction 3 Chapters 1. Start Download Manager...4 2. Select
Hosted Solutions Effective June 19, 2014
 Hosted Solutions Effective June 19, 2014 I NF ORMA TION P ACKA GE TABLE OF CONTENTS TABLE OF CONTENTS... 2 ABOUT TSS... 3 ABOUT HOSTED SOLUTIONS... 4 COST SAVINGS... 4 SCALABILITY... 4 DATA PROTECTION...
Hosted Solutions Effective June 19, 2014 I NF ORMA TION P ACKA GE TABLE OF CONTENTS TABLE OF CONTENTS... 2 ABOUT TSS... 3 ABOUT HOSTED SOLUTIONS... 4 COST SAVINGS... 4 SCALABILITY... 4 DATA PROTECTION...
Remote Access to Niagara Wheatfield s Computer Network
 Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
NETWORK SECURITY GUIDELINES
 NETWORK SECURITY GUIDELINES VIRUS PROTECTION STANDARDS All networked computers and networked laptop computers are protected by GST BOCES or district standard anti-virus protection software. The anti-virus
NETWORK SECURITY GUIDELINES VIRUS PROTECTION STANDARDS All networked computers and networked laptop computers are protected by GST BOCES or district standard anti-virus protection software. The anti-virus
Using XP Service Pack 2 with Cameleon
 1.1 What do I need to know about installing XP Service Pack 2 (XPSP2)? The Microsoft website has information about the service pack. Go to http://www.microsoft.com/windowsxp/sp2/default.mspx for more information
1.1 What do I need to know about installing XP Service Pack 2 (XPSP2)? The Microsoft website has information about the service pack. Go to http://www.microsoft.com/windowsxp/sp2/default.mspx for more information
REMOTE ACCESS SERVICE SUPPORT. ICR User Support Guide
 REMOTE ACCESS SERVICE SUPPORT ICR User Guide Question Answer/ What is supported Non-ICR computer access 1. What are the support hours for the remote access service? The IT Helpdesk service is available
REMOTE ACCESS SERVICE SUPPORT ICR User Guide Question Answer/ What is supported Non-ICR computer access 1. What are the support hours for the remote access service? The IT Helpdesk service is available
How not to lose your computer or your research. M.R. Muralidharan SERC IISc
 How not to lose your computer or your research M.R. Muralidharan SERC IISc The Battle has changed 08 Threat Landscape Shift 2004 Landscape Virus Threats are noisy & visible to everyone Threats are indiscriminate,
How not to lose your computer or your research M.R. Muralidharan SERC IISc The Battle has changed 08 Threat Landscape Shift 2004 Landscape Virus Threats are noisy & visible to everyone Threats are indiscriminate,
Lecture 6: Operating Systems and Utility Programs
 Lecture 6: Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
Lecture 6: Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
TECHNICAL VULNERABILITY & PATCH MANAGEMENT
 INFORMATION SECURITY POLICY TECHNICAL VULNERABILITY & PATCH MANAGEMENT ISO 27002 12.6.1 Author: Owner: Organisation: Document No: Chris Stone Ruskwig TruePersona Ltd SP-12.6.1 Version No: 1.1 Date: 1 st
INFORMATION SECURITY POLICY TECHNICAL VULNERABILITY & PATCH MANAGEMENT ISO 27002 12.6.1 Author: Owner: Organisation: Document No: Chris Stone Ruskwig TruePersona Ltd SP-12.6.1 Version No: 1.1 Date: 1 st
GTS Software Pty Ltd. Remote Desktop Services
 GTS Software Pty Ltd Remote Desktop Services Secure web access to GTS Software applications CONTENTS Overview... 2 What GTS can provide with Remote Desktop Services... 2 Main Features... 3 RD Web Access...
GTS Software Pty Ltd Remote Desktop Services Secure web access to GTS Software applications CONTENTS Overview... 2 What GTS can provide with Remote Desktop Services... 2 Main Features... 3 RD Web Access...
DIVISION OF ENGINEERING COMPUTING SERVICES DECS SERVICE DESK. Fall & Spring: Monday Thursday 8am to 9pm. Summer & Breaks:
 DECS Community IT Michigan State University College of Engineering DIVISION OF ENGINEERING COMPUTING SERVICES DECS SERVICE DESK For all questions and requests visit www.egr.msu.edu/decs or 1325EB, e mail
DECS Community IT Michigan State University College of Engineering DIVISION OF ENGINEERING COMPUTING SERVICES DECS SERVICE DESK For all questions and requests visit www.egr.msu.edu/decs or 1325EB, e mail
Sending Files to a Social Security Laptop
 Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
The Complete Plastic & Hand Surgery Electronic Office Solution
 The Complete Plastic & Hand Surgery Electronic Office Solution How IMS works IMS is a Client/Server application. This means that all your patients data is stored on a single computer designated as the
The Complete Plastic & Hand Surgery Electronic Office Solution How IMS works IMS is a Client/Server application. This means that all your patients data is stored on a single computer designated as the
How To Manage A Network Safely
 ICANWK303A Configure and administer a network operating system Release: 1 ICANWK303A Configure and administer a network operating system Modification History Release Release 1 Comments This Unit first
ICANWK303A Configure and administer a network operating system Release: 1 ICANWK303A Configure and administer a network operating system Modification History Release Release 1 Comments This Unit first
Information Technology Services. HelpDesk. Service Level Agreement (SLA) Effective November 13, 2012
 Information Technology Services HelpDesk Service Level Agreement (SLA) Effective November 13, 2012 Holy Family University IT Service Level Agreement Page 1 Holy Family University Information Technology
Information Technology Services HelpDesk Service Level Agreement (SLA) Effective November 13, 2012 Holy Family University IT Service Level Agreement Page 1 Holy Family University Information Technology
MedInformatix System Requirements
 MedInformatix System Requirements Acentec, Inc. A MedInformatix installation requires a workstation for each user who will access the system and a central server to store and process the data. A large
MedInformatix System Requirements Acentec, Inc. A MedInformatix installation requires a workstation for each user who will access the system and a central server to store and process the data. A large
Three steps to the best technology: 1. The Assessment 2. The Dialogue 3. The Recommendation
 Technology Assessment Checklist for Small Businesses A quick way to help your small-business customers get the best technology. Today's small-business owners want reliable technology that helps them do
Technology Assessment Checklist for Small Businesses A quick way to help your small-business customers get the best technology. Today's small-business owners want reliable technology that helps them do
Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9
 Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9 If you are not working from a Windows 7 or 8 computer, you will need to update: Windows XP to Service Pack 3 Windows Vista
Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9 If you are not working from a Windows 7 or 8 computer, you will need to update: Windows XP to Service Pack 3 Windows Vista
General Service Level Agreement
 General Service Level Agreement Pricing We offer an unlimited Break / Fix for each device. Cost is below. Server Management = $199 / month per server Network Management = $199 / month per company Desktop
General Service Level Agreement Pricing We offer an unlimited Break / Fix for each device. Cost is below. Server Management = $199 / month per server Network Management = $199 / month per company Desktop
BUSINESS SOFTWARE SOLUTIONS. Business Software Solutions Error Troubleshooting
 BUSINESS SOFTWARE SOLUTIONS Business Software Solutions Error Troubleshooting Contents Preventative Maintenance... 3 Backup Your BPA Software... 3 Posting Sales... 4 Anti-Virus/Anti-Spyware... 4 Index
BUSINESS SOFTWARE SOLUTIONS Business Software Solutions Error Troubleshooting Contents Preventative Maintenance... 3 Backup Your BPA Software... 3 Posting Sales... 4 Anti-Virus/Anti-Spyware... 4 Index
Accessing the SUNYIT wireless network for the first time
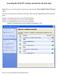 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Quarantine Network for Specialised Equipment.
 Quarantine Network for Specialised Equipment. Using Remote Desktop to get data in and out of the quarantine network V1.2 It is now possible to connect through a gateway or terminal server to PCs connected
Quarantine Network for Specialised Equipment. Using Remote Desktop to get data in and out of the quarantine network V1.2 It is now possible to connect through a gateway or terminal server to PCs connected
Audit4 Installation Requirements
 Audit4 version 8.1+ 2015 Copyright 2012 S4S Pty Ltd Audit4 Support Matrix 2015 The following table provides details on the operating system and database engine support for Audit4 as at March 2015. Operating
Audit4 version 8.1+ 2015 Copyright 2012 S4S Pty Ltd Audit4 Support Matrix 2015 The following table provides details on the operating system and database engine support for Audit4 as at March 2015. Operating
Item Minimum Required Recommended Notes
 Carestream Dental strongly adheres to compliance with Microsoft Windows operating systems and hardware compatibility (HCL), which can be found at www.microsoft.com/whdc/hcl/default.mspx. Only operating
Carestream Dental strongly adheres to compliance with Microsoft Windows operating systems and hardware compatibility (HCL), which can be found at www.microsoft.com/whdc/hcl/default.mspx. Only operating
Desktop Videoconferencing Guide
 Desktop Videoconferencing Guide A guide from the JANET Videoconferencing Service August 2010 Telephone: +44(0)131 650 4933 E-mail: vidconf@jvcs.ja.net Version: 1.9 12/08/2010 1 CONTENTS 1 HARDWARE & SOFTWARE
Desktop Videoconferencing Guide A guide from the JANET Videoconferencing Service August 2010 Telephone: +44(0)131 650 4933 E-mail: vidconf@jvcs.ja.net Version: 1.9 12/08/2010 1 CONTENTS 1 HARDWARE & SOFTWARE
CSG Windows Support Policy
 CSG Windows Support Policy This document describes the policies for service and support of computers running Microsoft Windows used by faculty and staff in the departments of Computer Science, Mathematics
CSG Windows Support Policy This document describes the policies for service and support of computers running Microsoft Windows used by faculty and staff in the departments of Computer Science, Mathematics
Click below for details about which Operating Systems work with UMT Plus and UMT Audit :
 Compatibility Grid for UMT Plus V18 and UMT Audit V3 Click below for details about which Operating Systems work with UMT Plus and UMT Audit : Windows Mobile OS Palm OS (also known as Garnet) Android OS
Compatibility Grid for UMT Plus V18 and UMT Audit V3 Click below for details about which Operating Systems work with UMT Plus and UMT Audit : Windows Mobile OS Palm OS (also known as Garnet) Android OS
Using Web Services for scanning on your network (Windows Vista SP2 or greater, Windows 7 and Windows 8)
 Using Web Services for scanning on your network (Windows Vista SP2 or greater, Windows 7 and Windows 8) The Web Services protocol allows Windows Vista (SP2 or greater), Windows 7 and Windows 8 users to
Using Web Services for scanning on your network (Windows Vista SP2 or greater, Windows 7 and Windows 8) The Web Services protocol allows Windows Vista (SP2 or greater), Windows 7 and Windows 8 users to
Introduction to Windows 7 (Brought to you by RMRoberts.com)
 Introduction to Windows 7 (Brought to you by RMRoberts.com) Note: Because of the number of screen captures needed to adequately explain this topic there have been some page breaks inserted to keep content
Introduction to Windows 7 (Brought to you by RMRoberts.com) Note: Because of the number of screen captures needed to adequately explain this topic there have been some page breaks inserted to keep content
The purpose of this document is to guide you through the installation and configuration of a new ShipGear installation.
 The purpose of this document is to guide you through the installation and configuration of a new ShipGear installation. Following is an overview of sections in this document: Section A Installing ShipGear
The purpose of this document is to guide you through the installation and configuration of a new ShipGear installation. Following is an overview of sections in this document: Section A Installing ShipGear
Get Connected! How to Configure Your Computer for MITnet. Red Hat Enterprise Linux Mac OS X Windows XP Professional, Vista
 Get Connected! How to Configure Your Computer for MITnet Red Hat Enterprise Linux Mac OS X Windows XP Professional, Vista 2008 Massachusetts Institute of Technology Table of Contents Introduction...3 About
Get Connected! How to Configure Your Computer for MITnet Red Hat Enterprise Linux Mac OS X Windows XP Professional, Vista 2008 Massachusetts Institute of Technology Table of Contents Introduction...3 About
Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library
 Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library Why should you be concerned? There are over 1 million known computer viruses. An unprotected computer on the
Essentials of PC Security: Central Library Tech Center Evansville Vanderburgh Public Library Why should you be concerned? There are over 1 million known computer viruses. An unprotected computer on the
Activatiecode voor NovaBackup Professional voor 3 pc. Omschrijving NovaBACKUP Professional 14.1
 Talen English Korte omschrijving Activatiecode voor NovaBackup Professional voor 3 pc. Omschrijving NovaBACKUP Professional 14.1 Windows Backup Software for Laptops, PCs, and Workstations Easy to install,
Talen English Korte omschrijving Activatiecode voor NovaBackup Professional voor 3 pc. Omschrijving NovaBACKUP Professional 14.1 Windows Backup Software for Laptops, PCs, and Workstations Easy to install,
CradlePoint Solution Success Stories
 CradlePoint Solution Success Stories Retail National Retail Tire Company and Franchiser IMPLEMENTATION: CradlePoint has partnered with a national retail tire company during their redesign of their front
CradlePoint Solution Success Stories Retail National Retail Tire Company and Franchiser IMPLEMENTATION: CradlePoint has partnered with a national retail tire company during their redesign of their front
Chapter 7A. Functions of Operating Systems. Types of Operating Systems. Operating System Basics
 Chapter 7A Operating System Basics Functions of Operating Provide a user interface Run programs Manage hardware devices Organized file storage 2 Types of Operating Real-time operating system Very fast
Chapter 7A Operating System Basics Functions of Operating Provide a user interface Run programs Manage hardware devices Organized file storage 2 Types of Operating Real-time operating system Very fast
San Jacinto College District Information Technology Services Desktop Support Guidelines
 Our goal at (ITS) is to provide the highest level of technical support and customer service to all San Jacinto College students and employees. We are constantly striving to provide a secure and efficient
Our goal at (ITS) is to provide the highest level of technical support and customer service to all San Jacinto College students and employees. We are constantly striving to provide a secure and efficient
Determining Your Computer Resources
 Determining Your Computer Resources There are a number of computer components that must meet certain requirements in order for your computer to perform effectively. This document explains how to check
Determining Your Computer Resources There are a number of computer components that must meet certain requirements in order for your computer to perform effectively. This document explains how to check
Access Control & Surveillance. Business Phone Systems. Data Storage & Recovery. Managed IT Services
 Designed by Business Phone Systems Managed IT Services Access Control & Surveillance Data Storage & Recovery FOR MORE INFORMATION, CONTACT TCT TODAY: Toll free 1.800.800.7806 454 Moore Lane, Suite 4 &
Designed by Business Phone Systems Managed IT Services Access Control & Surveillance Data Storage & Recovery FOR MORE INFORMATION, CONTACT TCT TODAY: Toll free 1.800.800.7806 454 Moore Lane, Suite 4 &
Before you start your SKE course:
 Before you start your SKE course: We are looking forward to supporting you in your studies with us. As you know the course is entirely delivered online. In preparation, we just need to check with you about
Before you start your SKE course: We are looking forward to supporting you in your studies with us. As you know the course is entirely delivered online. In preparation, we just need to check with you about
Point OS. Point OS is a windows based software which will work on most computers
 Point OS Point OS is a full featured restaurant point of sale system designed for Fine Dining, Full Service Restaurants, Quick Service Restaurants, Bars and Clubs. Point OS is a windows based software
Point OS Point OS is a full featured restaurant point of sale system designed for Fine Dining, Full Service Restaurants, Quick Service Restaurants, Bars and Clubs. Point OS is a windows based software
HELP DESK C D M S F I R S T. C O M ADVANTAGES TECHNICAL HELP DESK CHARACTÉRISTICS CHARACTERISTICS. Always there to help you
 TECHNICAL HELP DESK CHARACTÉRISTICS HELP DESK Always there to help you With the emergence of specialized technologies such as network remote access, Virtualization, Intranets and Extranets, wireless networks,
TECHNICAL HELP DESK CHARACTÉRISTICS HELP DESK Always there to help you With the emergence of specialized technologies such as network remote access, Virtualization, Intranets and Extranets, wireless networks,
Mobile Solutions. Mobile Solutions RFID AIDC. auto ID. mobility. labeling. data collec tion. software development
 Mobile Solutions Mobile Solutions RFID mobility AIDC data collec tion auto ID W L A N labeling software development w i r e l e s s BRINGING STABILITY TO MOBILITY Organizations go to great lengths to create
Mobile Solutions Mobile Solutions RFID mobility AIDC data collec tion auto ID W L A N labeling software development w i r e l e s s BRINGING STABILITY TO MOBILITY Organizations go to great lengths to create
Hardware Requirements
 Hardware Requirements This guide details the critical points of installing the IntraVet software from specific technology requirements to explicit hardware recommendations. communication organization practice
Hardware Requirements This guide details the critical points of installing the IntraVet software from specific technology requirements to explicit hardware recommendations. communication organization practice
Residential Service Offerings
 Affordable Technology Support For Your Home Residential Service Offerings Comtex Technologies Co. (317) 409-4592 Fax (317) 926-5975 Email: sales@comtex.us SERVING THE INDIANAPOLIS, IN AREA SINCE 2000 Now
Affordable Technology Support For Your Home Residential Service Offerings Comtex Technologies Co. (317) 409-4592 Fax (317) 926-5975 Email: sales@comtex.us SERVING THE INDIANAPOLIS, IN AREA SINCE 2000 Now
What you need to know to keep your computer safe on the Internet
 What you need to know to keep your computer safe on the Internet Tip 1: Always install Operating System updates The most important steps for any computer user is to always install updates, especially security
What you need to know to keep your computer safe on the Internet Tip 1: Always install Operating System updates The most important steps for any computer user is to always install updates, especially security
RSS Cloud Solution COMMON QUESTIONS
 RSS Cloud Solution COMMON QUESTIONS 1 Services... 3 Connectivity... 5 Support... 6 Implementation... 7 Security... 8 Applications... 9 Backups... 9 Email... 10 Contact... 11 2 Services What is included
RSS Cloud Solution COMMON QUESTIONS 1 Services... 3 Connectivity... 5 Support... 6 Implementation... 7 Security... 8 Applications... 9 Backups... 9 Email... 10 Contact... 11 2 Services What is included
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013
 Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
Greenway Medical Technologies PrimeSuite Integrated EHR, PM and Interoperability Solution
 Greenway Medical Technologies PrimeSuite Integrated EHR, PM and Interoperability Solution Technical Review and Hardware/Software Requirements Contents Technical Review Application Architecture Application
Greenway Medical Technologies PrimeSuite Integrated EHR, PM and Interoperability Solution Technical Review and Hardware/Software Requirements Contents Technical Review Application Architecture Application
Compulink Advantage Cloud sm Software Installation, Configuration, and Performance Guide for Windows
 Compulink Advantage Cloud sm Software Installation, Configuration, and Performance Guide for Windows Compulink Business Systems, Inc. 2645 Townsgate Road, Suite 200 Westlake Village, CA 91361 2013 Compulink
Compulink Advantage Cloud sm Software Installation, Configuration, and Performance Guide for Windows Compulink Business Systems, Inc. 2645 Townsgate Road, Suite 200 Westlake Village, CA 91361 2013 Compulink
Remote Desktop Part II. AHS Computing
 Remote Desktop Part II AHS Computing Overview How to become connected at home How to be secure when connecting from home Hazards of home computing How to work from home Troubleshooting issues from home
Remote Desktop Part II AHS Computing Overview How to become connected at home How to be secure when connecting from home Hazards of home computing How to work from home Troubleshooting issues from home
VRD for Windows User guide
 VRD for Windows User guide es/15865771_3 Table of contents Item Headings Page 1. VRD - key points to note... 1 2. First time user to VRD... 2 3. Returning user to VRD... 2 4. Using VRD for Windows... 2
VRD for Windows User guide es/15865771_3 Table of contents Item Headings Page 1. VRD - key points to note... 1 2. First time user to VRD... 2 3. Returning user to VRD... 2 4. Using VRD for Windows... 2
VPS Hosting. The Guide to Bet Angel VPS. Getting started with Bet Angel VPS. Revised August 2013. Page 1
 The Guide to Bet Angel VPS Getting started with Bet Angel VPS Revised August 2013 Page 1 Contents VPS Hosting Connecting to a Windows Server for the first time... 3 1 Ensuring that your Server has been
The Guide to Bet Angel VPS Getting started with Bet Angel VPS Revised August 2013 Page 1 Contents VPS Hosting Connecting to a Windows Server for the first time... 3 1 Ensuring that your Server has been
INFORMATION TECHNOLOGY TECHNICIAN I/II
 INFORMATION TECHNOLOGY TECHNICIAN I/II CITY OF HAYWARD DEFINITION To perform responsible technical duties related to computer hardware and software customer support; provide project support for new and
INFORMATION TECHNOLOGY TECHNICIAN I/II CITY OF HAYWARD DEFINITION To perform responsible technical duties related to computer hardware and software customer support; provide project support for new and
STEP 1: INSTALLING WINDOWS DEFENDER
 Office of Information Technology Secure your Windows XP Computer for Use on AU s Network Every member of the AU community has a shared responsibility for the safekeeping of our computer network. Since
Office of Information Technology Secure your Windows XP Computer for Use on AU s Network Every member of the AU community has a shared responsibility for the safekeeping of our computer network. Since
Coillte IT has recently upgraded the Remote Access Solution to a new platform.
 Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
IT Support & Maintenance Contract
 IT Support & Maintenance Contract This document has been produced by STOCK IT Ltd, www.stockit.co.uk, an IT company offering technology advice & support for small businesses. Company Registration No: 9060944
IT Support & Maintenance Contract This document has been produced by STOCK IT Ltd, www.stockit.co.uk, an IT company offering technology advice & support for small businesses. Company Registration No: 9060944
Installing the Panini Universal Scanner Driver
 Installing the Panini Universal Scanner Driver The following steps should be followed for installation of a Panini scanner. The user installing the scanner on his/her PC should have local administrative
Installing the Panini Universal Scanner Driver The following steps should be followed for installation of a Panini scanner. The user installing the scanner on his/her PC should have local administrative
NETGEAR genie Apps. User Manual. 350 East Plumeria Drive San Jose, CA 95134 USA. August 2012 202-10933-04 v1.0
 User Manual 350 East Plumeria Drive San Jose, CA 95134 USA August 2012 202-10933-04 v1.0 Support Thank you for choosing NETGEAR. To register your product, get the latest product updates, get support online,
User Manual 350 East Plumeria Drive San Jose, CA 95134 USA August 2012 202-10933-04 v1.0 Support Thank you for choosing NETGEAR. To register your product, get the latest product updates, get support online,
Information Technology Mission Statement. Information Technology Goals
 Ionia County Information Technology Strategic Plan 2008-2013 Table of Contents Information Technology Mission 3 Information Technology Goals 3 Current Network Overview 4-5 Information Technology Focus
Ionia County Information Technology Strategic Plan 2008-2013 Table of Contents Information Technology Mission 3 Information Technology Goals 3 Current Network Overview 4-5 Information Technology Focus
Mary Immaculate. ICT Services. ICT Helpdesk. User Guide
 Mary Immaculate ICT Services ICT Helpdesk User Guide Table of Contents 1. Introduction 3 2. How To Log A Call With The ICT Helpdesk 3 2.1 Email 3 2.2 Phone 3 2.3 Voicemail 3 2.4 Web Self Service Option
Mary Immaculate ICT Services ICT Helpdesk User Guide Table of Contents 1. Introduction 3 2. How To Log A Call With The ICT Helpdesk 3 2.1 Email 3 2.2 Phone 3 2.3 Voicemail 3 2.4 Web Self Service Option
Kaseya IT Automation Framework
 Kaseya Kaseya IT Automation Framework An Integrated solution designed for reducing complexity while increasing productivity for IT Professionals and Managed Service Providers. The powerful, web-based automation
Kaseya Kaseya IT Automation Framework An Integrated solution designed for reducing complexity while increasing productivity for IT Professionals and Managed Service Providers. The powerful, web-based automation
VPN Network Access. Principles and Restrictions
 BBG VPN WINDOWS CLIENT INSTALLATION PROCEDURES Page 1 of 11 Principles and Restrictions VPN Network Access High Speed access via broadband Internet connections is available for the Agency network resources
BBG VPN WINDOWS CLIENT INSTALLATION PROCEDURES Page 1 of 11 Principles and Restrictions VPN Network Access High Speed access via broadband Internet connections is available for the Agency network resources
REQUEST FOR PROPOSALS INFORMATION TECHNOLOGY SUPPORT SERVICES. Bid Packets are Due:
 REQUEST FOR PROPOSALS INFORMATION TECHNOLOGY SUPPORT SERVICES Issue Date: Friday, March 15 th, 2013 Closing Date: Monday, April 15 th, 2013 University City District is requesting proposals from qualified,
REQUEST FOR PROPOSALS INFORMATION TECHNOLOGY SUPPORT SERVICES Issue Date: Friday, March 15 th, 2013 Closing Date: Monday, April 15 th, 2013 University City District is requesting proposals from qualified,
THE. solution. STORe it. SHARE it.
 THE small business solution THE HP Storageworks X510 Data Vault STORe it. SECURE it. SHARE it. T H E H P S t o r a g e w o r k s X 51 0 D a t a V a u l t data protection just got less puzzling If, like
THE small business solution THE HP Storageworks X510 Data Vault STORe it. SECURE it. SHARE it. T H E H P S t o r a g e w o r k s X 51 0 D a t a V a u l t data protection just got less puzzling If, like
Server must be connected to the internet via high-speed internet connection.
 Server Based System Requirements Database Server Component / Number of users 1-10 Users 11-25 Users 28-50 Users Processor Recommended 4 Cores 6 Cores 8 Cores Processor Minimum 2 Cores 4 Cores 6 Cores Memory
Server Based System Requirements Database Server Component / Number of users 1-10 Users 11-25 Users 28-50 Users Processor Recommended 4 Cores 6 Cores 8 Cores Processor Minimum 2 Cores 4 Cores 6 Cores Memory
GETTING STARTED WITH A COMPUTER SYSTEM FACTSHEET
 FACTSHEET When setting up a small business there can be many areas of uncertainty, but getting your IT or computer systems right and connected does not need to be one of them. If your company is either
FACTSHEET When setting up a small business there can be many areas of uncertainty, but getting your IT or computer systems right and connected does not need to be one of them. If your company is either
Service Description: Solution Station HelpDesk Service
 Dell Services Service Description: Solution Station HelpDesk Service Service Overview Service Provider. Dell Marketing L.P. ( Dell ), One Dell Way, Round Rock, Texas 78682. Terms and Conditions. Dell is
Dell Services Service Description: Solution Station HelpDesk Service Service Overview Service Provider. Dell Marketing L.P. ( Dell ), One Dell Way, Round Rock, Texas 78682. Terms and Conditions. Dell is
Service Level Agreement
 Service Level Agreement Occupational Studies Administration Occupational Studies Computer Lab Contract Date 1/25/2005 to 12/31/2005 SLA Contract and Responsible Parties This Service Level Agreement is
Service Level Agreement Occupational Studies Administration Occupational Studies Computer Lab Contract Date 1/25/2005 to 12/31/2005 SLA Contract and Responsible Parties This Service Level Agreement is
TECHNOLOGY BRIEF: CA THREAT MANAGER. Protecting Endpoint Systems Using Threat Management Solutions
 TECHNOLOGY BRIEF: CA THREAT MANAGER Protecting Endpoint Systems Using Threat Management Solutions Table of Contents Executive Summary SECTION 1: CHALLENGE 2 Issues Surrounding Multiple Threat Vectors SECTION
TECHNOLOGY BRIEF: CA THREAT MANAGER Protecting Endpoint Systems Using Threat Management Solutions Table of Contents Executive Summary SECTION 1: CHALLENGE 2 Issues Surrounding Multiple Threat Vectors SECTION
Softline VIP Payroll System Requirements v2.9a January 2010
 i Softline VIP Payroll System Requirements v2.9a January 2010 Table of Contents Introduction... 1 Assumptions... 1 Standalone Requirements... 2 Note:Peer-to-peer Network Installations... 2 Peer-to-peer
i Softline VIP Payroll System Requirements v2.9a January 2010 Table of Contents Introduction... 1 Assumptions... 1 Standalone Requirements... 2 Note:Peer-to-peer Network Installations... 2 Peer-to-peer
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Setting up for Adobe Connect meetings
 Setting up for Adobe Connect meetings When preparing to lead a live lecture or meeting, you probably ensure that your meeting room and materials are ready before your participants arrive. You run through
Setting up for Adobe Connect meetings When preparing to lead a live lecture or meeting, you probably ensure that your meeting room and materials are ready before your participants arrive. You run through
INSTALLATION MINIMUM REQUIREMENTS. Visit us on the Web www.docstar.com
 INSTALLATION MINIMUM REQUIREMENTS Visit us on the Web www.docstar.com Clients This section details minimum requirements for client workstations that use. Workstation (Scan) Windows 7 (32/64 bit); Windows
INSTALLATION MINIMUM REQUIREMENTS Visit us on the Web www.docstar.com Clients This section details minimum requirements for client workstations that use. Workstation (Scan) Windows 7 (32/64 bit); Windows
Anti- Virus Protection Get real-time protection against viruses, worms, Trojans and rootkits.
 SecureIT Plus PC Security To learn more about Security Coverage s suite of security features, select from the Quick Links that follow. This document can also be printed, or saved to your desktop and used
SecureIT Plus PC Security To learn more about Security Coverage s suite of security features, select from the Quick Links that follow. This document can also be printed, or saved to your desktop and used
IT Decisions for Small Business
 IT Decisions for Small Business The most frequently asked questions and answers By Keith Powell and Chris Brandow, Invision Partners Computing technology has become a necessary business tool, and there
IT Decisions for Small Business The most frequently asked questions and answers By Keith Powell and Chris Brandow, Invision Partners Computing technology has become a necessary business tool, and there
Online Backup Plus Frequently Asked Questions
 Online Backup Plus Frequently Asked Questions 1 INSTALLATION 1.1 Who installs the Redstor Online Backup Plus service? 1.2 How does the installed client connect to Redstor s Cloud Platform? 1.3 On which
Online Backup Plus Frequently Asked Questions 1 INSTALLATION 1.1 Who installs the Redstor Online Backup Plus service? 1.2 How does the installed client connect to Redstor s Cloud Platform? 1.3 On which
Spyware. Michael Glenn Technology Management Michael.Glenn@Qwest.com. 2004 Qwest Communications International Inc.
 Spyware Michael Glenn Technology Management Michael.Glenn@Qwest.com Agenda Security Fundamentals Current Issues Spyware Definitions Overlaps of Threats Best Practices What Service Providers are Doing References
Spyware Michael Glenn Technology Management Michael.Glenn@Qwest.com Agenda Security Fundamentals Current Issues Spyware Definitions Overlaps of Threats Best Practices What Service Providers are Doing References
SOFTDENT Practice Management Software v14.0 System Requirements. Server. Workstation (without digital imaging)
 SoftDent software strongly adheres to compliance with MICROSOFT WINDOWS operating systems and hardware compatibility. Only operating systems and hardware listed below have been fully tested and certified
SoftDent software strongly adheres to compliance with MICROSOFT WINDOWS operating systems and hardware compatibility. Only operating systems and hardware listed below have been fully tested and certified
Tech Brief. Enterprise Secure and Scalable Enforcement of Microsoft s Network Access Protection in Mobile Networks
 Tech Brief Enterprise Secure and Scalable Enforcement of Microsoft s Network Access Protection in Mobile Networks Introduction In today s era of increasing mobile computing, one of the greatest challenges
Tech Brief Enterprise Secure and Scalable Enforcement of Microsoft s Network Access Protection in Mobile Networks Introduction In today s era of increasing mobile computing, one of the greatest challenges
Welcome To VIRTUAL WITHOUT THE VIRTUAL TM. imvp Setup Guide for Windows. imvp with RDP Lab Setup Guide For Windows 1
 Welcome To VIRTUAL WITHOUT THE VIRTUAL TM imvp Setup Guide for Windows imvp with RDP Lab Setup Guide For Windows 1 The imvp Team is here for you If you have any questions during the imvp setup process,
Welcome To VIRTUAL WITHOUT THE VIRTUAL TM imvp Setup Guide for Windows imvp with RDP Lab Setup Guide For Windows 1 The imvp Team is here for you If you have any questions during the imvp setup process,
ReadyNAS OS 6.2. Reviewer s Guide
 ReadyNAS OS 6.2 Reviewer s Guide Table of Contents NETGEAR Contact Info... 3 Product Category... 3 Overview... 3 What s New in 6.2... 5 Quick Setup Instructions... 10 Adding Files and Folders to the ReadyNAS...
ReadyNAS OS 6.2 Reviewer s Guide Table of Contents NETGEAR Contact Info... 3 Product Category... 3 Overview... 3 What s New in 6.2... 5 Quick Setup Instructions... 10 Adding Files and Folders to the ReadyNAS...
System Environment Specifications Network, PC, Peripheral & Server Requirements
 Allscripts MyWay 8.6 System Environment Specifications Network, PC, Peripheral & Server Requirements NETWORK REQUIREMENTS An Internet Protocol (TCP/IP) network is required between Allscripts MyWay clients
Allscripts MyWay 8.6 System Environment Specifications Network, PC, Peripheral & Server Requirements NETWORK REQUIREMENTS An Internet Protocol (TCP/IP) network is required between Allscripts MyWay clients
User Guide Max Secure Recovery CD/USB creation
 User Guide Max Secure Recovery CD/USB creation This user guide describes how you can go about creating an emergency bootable Max Secure Recovery CD / USB. You can boot from this CD/USB into a Windows environment
User Guide Max Secure Recovery CD/USB creation This user guide describes how you can go about creating an emergency bootable Max Secure Recovery CD / USB. You can boot from this CD/USB into a Windows environment
SSL VPN Service. Once you have installed the AnyConnect Secure Mobility Client, this document is available by clicking on the Help icon on the client.
 Contents Introduction... 2 Prepare Work PC for Remote Desktop... 4 Add VPN url as a Trusted Site in Internet Explorer... 5 VPN Client Installation... 5 Starting the VPN Application... 6 Connect to Work
Contents Introduction... 2 Prepare Work PC for Remote Desktop... 4 Add VPN url as a Trusted Site in Internet Explorer... 5 VPN Client Installation... 5 Starting the VPN Application... 6 Connect to Work
Lakeview Community Schools Computer Network Managed Services Proposal July 1, 2010 to June 30, 2013
 Lakeview Community Schools Computer Network Managed Services Proposal July 1, 2010 to June 30, 2013 Lakeview Community Schools is requesting proposals for Network, Servers, PCs and Printers Administrative
Lakeview Community Schools Computer Network Managed Services Proposal July 1, 2010 to June 30, 2013 Lakeview Community Schools is requesting proposals for Network, Servers, PCs and Printers Administrative
