OpenID. Abendseminar «Innovative Alternativen zum Passwort» , Hotel Novotel, Zürich. Robert Ott OpenID Switzerland / Clavid AG
|
|
|
- Jesse Clark
- 8 years ago
- Views:
Transcription
1 OpenID Abendseminar «Innovative Alternativen zum Passwort» , Hotel Novotel, Zürich Robert Ott OpenID Switzerland / Clavid AG Information Security Society Switzerland 1
2 SECTION 1 OpenID > What is it? > How are we organized? > How does it work? > How to integrate? Page 2
3 OpenID - What is it? TO MANY PASSWORDS!!! Page 3
4 OpenID - What is it? > Internet SingleSignOn > Relatively Simple Protocol > User-Centric Identity Management > Internet Scalable > Free Choice of Identity Provider > No License Fee > Independent of Identification Methods > Non-Profit Organization Page 4
5 OpenID - How are we organized? OpenID Foundation (OIDF) - Non-Profit Organization Parent Organization of Local Chapters Trademark Protection egov Promotion Organization of Events (Summits) Members Facebook Google Microsoft IBM PayPal VeriSign Yahoo LexisNexis Page 5
6 OpenID - How are we organized? OpenID Switzerland (OIDCH) - Non-Profit Organization Official Local Chapter of OIDF Registered Association (Handelsregistereintrag) Organization of Local Events Geneva Conference 2010 with more than 200 attendees Members AXSionics Clavid Maret Consulting La Citadelle Electronique Private Members Page 6
7 OpenID - User Centric Identity Management Username Password TOMORROW? FUTURE TODAY? OpenID Provider Username Password Username Password Username Password Page 7
8 OpenID - How does it work? User Hans Muster (Domain: AUTHENTICATION Identity Provider hans.muster.iid.ch OpenID=hans.muster.iid.ch Identity URL e.g. hans.muster.iid.ch Enabled Service Page 8
9 OpenID - How does it work? User Hans Muster 3 4, 4a Identity Provider hans.muster.clavid.com 5 6 Caption 1. User enters OpenID 2. Discovery 3. Authentication 4. Approval 4a. Change Attributes 5. Send Attributes 6. Validation 1 Enabled Service 2 Identity URL Page 9
10 OpenID - How does it work? Step 1: Step 2: A user decides to use a personalized Internet Service supporting OpenID (e.g. local.ch). The user clicks on Login using OpenID and enters its OpenID (e.g. hans.muster.iid.ch). The requested Internet Service converts the OpenID into an URL ( and requests this URL in order to receive the Identity Provider of the user. Step 2a: In this example, the user has delegated its OpenID to the Identity Provider clavid.ch. Step 3: Step 4: The Identity Provider provides possible authentication methods for that specific user (in this case Password ). Having successfully authenticated, the next step (approval) is initiated. The user decides on the values of the requested attributes to be provided to the Internet Service. The Identity Provider usually provides user specific Personas (attribute templates) to assist the user in this approval process. Step 4a: At this point, the user may decide to change attribute values and store them on the Identity Provider for future approvals for that specific service. Thus, a user can automate future approvals for specific Internet Services. Step 5, 6: The attribute values are then signed and communicated from the Identity Provider to the Internet Service. The Internet Service validates the signature of the provided attributes and finally accepts the user to be authenticated. Page 10
11 OpenID - Login Procedure Page 11
12 OpenID Login Procedure with SREG Page 12
13 OpenID - Delegation <html> <head> <link rel="openid.server" href=" <link rel="openid2.provider" href=" <link rel="openid.delegate" href=" <link rel="openid2.local_id" href=" </head> <body> <h1>my Personal OpenID mydomain.ch</h1> </body> </html> Page 13
14 OpenID - How to Integrate? Assumptions concerning your current Site Users sign in with their username and password There is a form, where new users have to register Each user is identified by a unique ID in your database A settings page let users manage their account info Recipe Extend the database to map the OpenIDs to the user IDs Extend the registration page with an OpenID input field Extend the sign in page with an OpenID input field Extend the settings page to attach and detach openids Page 14
15 OpenID - How to Integrate? Ingredients A OpenID Consumer Library The Standard OpenID Logos An OpenID Provider to test your site with Page 15
16 OpenID - How to Integrate? OpenID Libraries Language Library C# DotNetOpenId, ExtremeSwank C++ Libopkele Java NetMesh InfoGrid LID, OpenID4Java, joid Perl Python Ruby PHP Coldfusion Apache 2 Net::OpenID, OpenID4Perl JanRain JanRain, Heraldry Jan Rain, Zend Framework OpenID Component, Saeven.net's JanRain Service Utility Class, Taral, Simple Class, sfopenidplugin, CakePHP, EasyOpenID, OpenID For PHP, AuthOpenID Snippet CFKit OpenID, CFOpenID, OpenID CFC mod_auth_openid Page 16
17 OpenID - International Identity Providers Username/Password Certificates Biometric OTP Page 17
18 Further Links: on OpenID OpenID Identity Providers can be found at: > > > > (Strong Authentication in Europe) Page 18
19 Danke für Ihre Aufmerksamkeit! Clavid AG Baarerstrasse 2 CH-6300 Zug Switzerland +41 (0) Phone +41 (0) Fax Information Security Society Switzerland ISSS2010XZ
Enabling Digital Identity. David Recordon Innovator for Advanced Products & Research
 Enabling Digital Identity David Recordon Innovator for Advanced Products & Research DC PHP Conference 2006 Overview + Web 2.0 + Identity so what? + Identity 2.0 + Competitive Overview + Digging into OpenID
Enabling Digital Identity David Recordon Innovator for Advanced Products & Research DC PHP Conference 2006 Overview + Web 2.0 + Identity so what? + Identity 2.0 + Competitive Overview + Digging into OpenID
OpenID Single Sign On and OAuth Data Access for Google Apps. Ryan Boyd @ryguyrg Dave Primmer May 2010
 OpenID Single Sign On and OAuth Data Access for Google Apps Ryan Boyd @ryguyrg Dave Primmer May 2010 Why? View live notes and questions about this session on Google Wave: http://bit.ly/magicwave Agenda
OpenID Single Sign On and OAuth Data Access for Google Apps Ryan Boyd @ryguyrg Dave Primmer May 2010 Why? View live notes and questions about this session on Google Wave: http://bit.ly/magicwave Agenda
Follow these easy instructions to list your business on the BEC Australia National Business Directory.
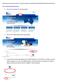 Follow these easy instructions to list your business on the BEC Australia National Business Directory. Go to www.becaustralia.org.au 1. Click on the Directory tab (see below) 2. Click on the Add listing
Follow these easy instructions to list your business on the BEC Australia National Business Directory. Go to www.becaustralia.org.au 1. Click on the Directory tab (see below) 2. Click on the Add listing
Social Application Guide
 Social Application Guide Version 2.2.0 Mar 2015 This document is intent to use for our following Magento Extensions Or any other cases it might help. Copyright 2015 LitExtension.com. All Rights Reserved
Social Application Guide Version 2.2.0 Mar 2015 This document is intent to use for our following Magento Extensions Or any other cases it might help. Copyright 2015 LitExtension.com. All Rights Reserved
Single Sign On. SSO & ID Management for Web and Mobile Applications
 Single Sign On and ID Management Single Sign On SSO & ID Management for Web and Mobile Applications Presenter: Manish Harsh Program Manager for Developer Marketing Platforms of NVIDIA (Visual Computing
Single Sign On and ID Management Single Sign On SSO & ID Management for Web and Mobile Applications Presenter: Manish Harsh Program Manager for Developer Marketing Platforms of NVIDIA (Visual Computing
Create your portal account, and connect to your medical records.
 Create your portal account, and connect to your medical records. Follow these steps if you have not received an email invitation to register. Any questions, please email us at patientportal@raleighmedicalgroup.com
Create your portal account, and connect to your medical records. Follow these steps if you have not received an email invitation to register. Any questions, please email us at patientportal@raleighmedicalgroup.com
Federated Identity Opportunities & Risks
 Federated Identity Opportunities & Risks Dominick Baier Former ERNW employee Security consultant at thinktecture application security in distributed systems identity management mostly Windows &.NET http://www.leastprivilege.com
Federated Identity Opportunities & Risks Dominick Baier Former ERNW employee Security consultant at thinktecture application security in distributed systems identity management mostly Windows &.NET http://www.leastprivilege.com
Analysis and Implementation of a SSO Solution for Several Web Portal
 Aalto University Bachelor s Thesis Analysis and Implementation of a SSO Solution for Several Web Portal Author: Xavi Magrinyà Supervisor: Professor Petri Vuorimaa A Thesis submitted in fulfilment of the
Aalto University Bachelor s Thesis Analysis and Implementation of a SSO Solution for Several Web Portal Author: Xavi Magrinyà Supervisor: Professor Petri Vuorimaa A Thesis submitted in fulfilment of the
Unified Access for Enterprise Users
 Unified Access for Enterprise Users Informational webinar Chinmay Meghani Liferay Portal Specialist Fulcrum Worldwide, Inc. Mehria Askaryar Business Development Manager Fulcrum Worldwide, Inc. Agenda Introduction
Unified Access for Enterprise Users Informational webinar Chinmay Meghani Liferay Portal Specialist Fulcrum Worldwide, Inc. Mehria Askaryar Business Development Manager Fulcrum Worldwide, Inc. Agenda Introduction
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
PingFederate. SSO Integration Overview
 PingFederate SSO Integration Overview 2006-2012 Ping Identity Corporation. All rights reserved. PingFederate SSO Integration Overview Version 6.6 January, 2012 Ping Identity Corporation 1001 17th Street,
PingFederate SSO Integration Overview 2006-2012 Ping Identity Corporation. All rights reserved. PingFederate SSO Integration Overview Version 6.6 January, 2012 Ping Identity Corporation 1001 17th Street,
Safewhere*Identify 3.4. Release Notes
 Safewhere*Identify 3.4 Release Notes Safewhere*identify is a new kind of user identification and administration service providing for externalized and seamless authentication and authorization across organizations.
Safewhere*Identify 3.4 Release Notes Safewhere*identify is a new kind of user identification and administration service providing for externalized and seamless authentication and authorization across organizations.
Registering the Digital Signature Certificate for Bank Officials
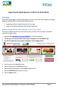 Registering the Digital Signature Certificate for Bank Officials Overview When Bank officials login to the MCA21 application for the first time, they need to register their Digital Signature Certificate
Registering the Digital Signature Certificate for Bank Officials Overview When Bank officials login to the MCA21 application for the first time, they need to register their Digital Signature Certificate
Digital Identity Management
 Digital Identity Management Roohul Halim Syed Atif Shaharyar Email: {rooha433, syesh740}@student.liu.se Supervisor: Anna Vapen, {annva@ida.liu.se} Project Report for Information Security Course Linköpings
Digital Identity Management Roohul Halim Syed Atif Shaharyar Email: {rooha433, syesh740}@student.liu.se Supervisor: Anna Vapen, {annva@ida.liu.se} Project Report for Information Security Course Linköpings
OpenLogin: PTA, SAML, and OAuth/OpenID
 OpenLogin: PTA, SAML, and OAuth/OpenID Ernie Turner Chris Fellows RightNow Technologies, Inc. Why should you care about these features? Why should you care about these features? Because users hate creating
OpenLogin: PTA, SAML, and OAuth/OpenID Ernie Turner Chris Fellows RightNow Technologies, Inc. Why should you care about these features? Why should you care about these features? Because users hate creating
shweclassifieds v 3.3 Php Classifieds Script (Joomla Extension) User Manual (Revision 2.0)
 shweclassifieds v 3.3 Php Classifieds Script (Joomla Extension) User Manual (Revision 2.0) Contents Installation Procedure... 4 What is in the zip file?... 4 Installing from Extension Manager... 6 Updating
shweclassifieds v 3.3 Php Classifieds Script (Joomla Extension) User Manual (Revision 2.0) Contents Installation Procedure... 4 What is in the zip file?... 4 Installing from Extension Manager... 6 Updating
PassKey Manager. Schoolwires Centricity
 Schoolwires Centricity Table of Contents Introduction... 1 What Provides... 1 What Does Not Provide... 1 Definitions for... 1 Manage PassKeys in Site Manager... 2 Access... 2 Create PassKeys... 2 Create
Schoolwires Centricity Table of Contents Introduction... 1 What Provides... 1 What Does Not Provide... 1 Definitions for... 1 Manage PassKeys in Site Manager... 2 Access... 2 Create PassKeys... 2 Create
Configuring IBM Cognos Controller 8 to use Single Sign- On
 Guideline Configuring IBM Cognos Controller 8 to use Single Sign- On Product(s): IBM Cognos Controller 8.2 Area of Interest: Security Configuring IBM Cognos Controller 8 to use Single Sign-On 2 Copyright
Guideline Configuring IBM Cognos Controller 8 to use Single Sign- On Product(s): IBM Cognos Controller 8.2 Area of Interest: Security Configuring IBM Cognos Controller 8 to use Single Sign-On 2 Copyright
External Authentication with WebCT. What We ll Discuss
 External Authentication with WebCT WebCT, Inc http://www.webct.com/ What We ll Discuss Introductions Terminology Authentication in WebCT External Authentication Custom Authentication Authorization in WebCT
External Authentication with WebCT WebCT, Inc http://www.webct.com/ What We ll Discuss Introductions Terminology Authentication in WebCT External Authentication Custom Authentication Authorization in WebCT
The Top 5 Federated Single Sign-On Scenarios
 The Top 5 Federated Single Sign-On Scenarios Table of Contents Executive Summary... 1 The Solution: Standards-Based Federation... 2 Service Provider Initiated SSO...3 Identity Provider Initiated SSO...3
The Top 5 Federated Single Sign-On Scenarios Table of Contents Executive Summary... 1 The Solution: Standards-Based Federation... 2 Service Provider Initiated SSO...3 Identity Provider Initiated SSO...3
Managed Services PKI 60-day Trial Quick Start Guide
 Entrust Managed Services PKI Managed Services PKI 60-day Trial Quick Start Guide Document issue: 3.0 Date of issue: Nov 2011 Copyright 2011 Entrust. All rights reserved. Entrust is a trademark or a registered
Entrust Managed Services PKI Managed Services PKI 60-day Trial Quick Start Guide Document issue: 3.0 Date of issue: Nov 2011 Copyright 2011 Entrust. All rights reserved. Entrust is a trademark or a registered
Criminal Justice Social Work Community of Practice Subscription, registration and login manual
 Criminal Justice Social Work Community of Practice Subscription, registration and login manual Version: concept 08102014 Introduction Before you can access the Criminal Justice Social Work - Community
Criminal Justice Social Work Community of Practice Subscription, registration and login manual Version: concept 08102014 Introduction Before you can access the Criminal Justice Social Work - Community
WebEx Integration to Outlook. User Guide
 WebEx Integration to Outlook User Guide 072310 Copyright 1997 2010 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are trademarks or
WebEx Integration to Outlook User Guide 072310 Copyright 1997 2010 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are trademarks or
Use Enterprise SSO as the Credential Server for Protected Sites
 Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Defender 5.7 - Token Deployment System Quick Start Guide
 Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Interoperate in Cloud with Federation
 Interoperate in Cloud with Federation - Leveraging federation standards can accelerate Cloud computing adoption by resolving vendor lock-in issues and facilitate On Demand business requirements Neha Mehrotra
Interoperate in Cloud with Federation - Leveraging federation standards can accelerate Cloud computing adoption by resolving vendor lock-in issues and facilitate On Demand business requirements Neha Mehrotra
Create a Room Block in the Hotel Center?
 Create a Room Block in the Hotel Center? To create a room block for an event in the Hotel Center, click on the Room Blocks tab Click on the button to get to the add room block page Revised 6/1/10 by SignUp4
Create a Room Block in the Hotel Center? To create a room block for an event in the Hotel Center, click on the Room Blocks tab Click on the button to get to the add room block page Revised 6/1/10 by SignUp4
INTEGRATION GUIDE. DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server
 INTEGRATION GUIDE DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
INTEGRATION GUIDE DIGIPASS Authentication for Google Apps using IDENTIKEY Federation Server Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document
YubiKey Authentication Module Design Guideline
 YubiKey Authentication Module Design Guideline Yubico Application Note Version 1.0 May 7, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company
YubiKey Authentication Module Design Guideline Yubico Application Note Version 1.0 May 7, 2012 Introduction Disclaimer Yubico is the leading provider of simple, open online identity protection. The company
INTEGRATION GUIDE. General Radius Config
 INTEGRATION GUIDE General Radius Config Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data Security assumes no
INTEGRATION GUIDE General Radius Config Disclaimer Disclaimer of Warranties and Limitation of Liabilities All information contained in this document is provided 'as is'; VASCO Data Security assumes no
Hosted Email Security 2.0 Quick Start Guide
 Hosted Email Security 2.0 Quick Start Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Hosted Email Security 2.0 Quick Start Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
IMPLEMENTATION GUIDE. API Service. More Power to You. May 2008. For more information, please contact support@zedo.com
 IMPLEMENTATION GUIDE API Service More Power to You May 2008 For more information, please contact support@zedo.com Implementation Guide ZEDO API Service Disclaimer This Implementation Guide is for informational
IMPLEMENTATION GUIDE API Service More Power to You May 2008 For more information, please contact support@zedo.com Implementation Guide ZEDO API Service Disclaimer This Implementation Guide is for informational
Web Publishing (Ch. 11.4)
 Web Publishing (Ch. 11.4) Web publishing is the process of uploading web pages to a web server. Web server For a web page to be placed onto the Internet, it needs to be stored on a computer with the following
Web Publishing (Ch. 11.4) Web publishing is the process of uploading web pages to a web server. Web server For a web page to be placed onto the Internet, it needs to be stored on a computer with the following
Add in Guide for Microsoft Dynamics CRM May 2012
 Add in Guide for Microsoft Dynamics CRM May 2012 Microsoft Dynamics CRM Addin Guide This document will guide you through configuration of the Microsoft Dynamics CRM addin. Microsoft Dynamics CRM is a bit
Add in Guide for Microsoft Dynamics CRM May 2012 Microsoft Dynamics CRM Addin Guide This document will guide you through configuration of the Microsoft Dynamics CRM addin. Microsoft Dynamics CRM is a bit
Web Hosting Features. Small Office Premium. Small Office. Basic Premium. Enterprise. Basic. General
 General Basic Basic Small Office Small Office Enterprise Enterprise RAID Web Storage 200 MB 1.5 MB 3 GB 6 GB 12 GB 42 GB Web Transfer Limit 36 GB 192 GB 288 GB 480 GB 960 GB 1200 GB Mail boxes 0 23 30
General Basic Basic Small Office Small Office Enterprise Enterprise RAID Web Storage 200 MB 1.5 MB 3 GB 6 GB 12 GB 42 GB Web Transfer Limit 36 GB 192 GB 288 GB 480 GB 960 GB 1200 GB Mail boxes 0 23 30
Hosted Email Security Quick Start Guide
 Hosted Email Security Quick Start Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Hosted Email Security Quick Start Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
A trusted identity management system is not only essential for ensuring your customers safety and confidence.
 A trusted identity management system is not only essential for ensuring your customers safety and confidence. With the new EU legislation, high protection of personal data has become a pressing need. Side
A trusted identity management system is not only essential for ensuring your customers safety and confidence. With the new EU legislation, high protection of personal data has become a pressing need. Side
> GET IT HERE < WhoIsByinvitationonlystep4 WhoIsDirectory Domain Names, Websites, Hosting - User Review --> Click Here
 Cheapest website building and hosting, web and email hosting reviews. > GET IT HERE < WhoIsByinvitationonlystep4 WhoIsDirectory Domain Names, Websites, Hosting - User Review --> Click Here Professional
Cheapest website building and hosting, web and email hosting reviews. > GET IT HERE < WhoIsByinvitationonlystep4 WhoIsDirectory Domain Names, Websites, Hosting - User Review --> Click Here Professional
Dell One Identity Cloud Access Manager 8.0.1 - How to Develop OpenID Connect Apps
 Dell One Identity Cloud Access Manager 8.0.1 - How to Develop OpenID Connect Apps May 2015 This guide includes: What is OAuth v2.0? What is OpenID Connect? Example: Providing OpenID Connect SSO to a Salesforce.com
Dell One Identity Cloud Access Manager 8.0.1 - How to Develop OpenID Connect Apps May 2015 This guide includes: What is OAuth v2.0? What is OpenID Connect? Example: Providing OpenID Connect SSO to a Salesforce.com
Using Remote Desktop with No-IP
 Page 1 of 6 Lost Password? Sign-up Now!. com Support : Guides and Tips : Remote Access : Using Remote Desktop with No-IP Overview The use of Microsoft's Remote Desktop Connection to access another computer
Page 1 of 6 Lost Password? Sign-up Now!. com Support : Guides and Tips : Remote Access : Using Remote Desktop with No-IP Overview The use of Microsoft's Remote Desktop Connection to access another computer
Login with Amazon. Getting Started Guide for Websites. Version 1.0
 Login with Amazon Getting Started Guide for Websites Version 1.0 Login with Amazon: Getting Started Guide for Websites Copyright 2016 Amazon Services, LLC or its affiliates. All rights reserved. Amazon
Login with Amazon Getting Started Guide for Websites Version 1.0 Login with Amazon: Getting Started Guide for Websites Copyright 2016 Amazon Services, LLC or its affiliates. All rights reserved. Amazon
Privacy and Security Advantages of Social Login. White Paper
 Privacy and Security Advantages of Social Login White Paper User Management Platform for the Social Web white paper Privacy and Security Advantages of Third-Party Authentication The practice of implementing
Privacy and Security Advantages of Social Login White Paper User Management Platform for the Social Web white paper Privacy and Security Advantages of Third-Party Authentication The practice of implementing
OpenID & Strong Authentication
 OpenID & Strong Authentication CTST 2009: Emerging Technology D14: Smart Cards, Tokens & Digital Identity May 5, 2009 Brian Kelly Vice President TrustBearer Labs Simplify Multi-factor authentication can
OpenID & Strong Authentication CTST 2009: Emerging Technology D14: Smart Cards, Tokens & Digital Identity May 5, 2009 Brian Kelly Vice President TrustBearer Labs Simplify Multi-factor authentication can
How to Use Google Cloud Print
 1 The machine is compatible with Google Cloud Print (Google Cloud Print is a service provided by Google Inc.). By using Google Cloud Print, you can print from anywhere with applications or services supporting
1 The machine is compatible with Google Cloud Print (Google Cloud Print is a service provided by Google Inc.). By using Google Cloud Print, you can print from anywhere with applications or services supporting
SHODAN for Penetration Testers. Michael theprez98 Schearer
 SHODAN for Penetration Testers Michael theprez98 Schearer SHODAN for Penetration Testers What is SHODAN? Basic Operations Penetration Testing Case Study 1: Cisco Devices Case Study 2: Default Passwords
SHODAN for Penetration Testers Michael theprez98 Schearer SHODAN for Penetration Testers What is SHODAN? Basic Operations Penetration Testing Case Study 1: Cisco Devices Case Study 2: Default Passwords
PayPal By PayDollar. Setup Guide
 PayPal By PayDollar Setup Guide (Leave Blank Intentionally) PayDollar By PayPal Setup Guide Page 1 Copyright Information AsiaPay (HK) Limited Room 1702, 17/F K. Wah Centre 191 Java Road Hong Kong. Telephone
PayPal By PayDollar Setup Guide (Leave Blank Intentionally) PayDollar By PayPal Setup Guide Page 1 Copyright Information AsiaPay (HK) Limited Room 1702, 17/F K. Wah Centre 191 Java Road Hong Kong. Telephone
MIT Tech Talk, May 2013 Justin Richer, The MITRE Corporation
 MIT Tech Talk, May 2013 Justin Richer, The MITRE Corporation Approved for Public Release Distribution Unlimited 13-1871 2013 The MITRE Corporation All Rights Reserved } OpenID Connect and OAuth2 protocol
MIT Tech Talk, May 2013 Justin Richer, The MITRE Corporation Approved for Public Release Distribution Unlimited 13-1871 2013 The MITRE Corporation All Rights Reserved } OpenID Connect and OAuth2 protocol
Linux VPS with cpanel. Getting Started Guide
 Linux VPS with cpanel Getting Started Guide First Edition October 2010 Table of Contents Introduction...1 cpanel Documentation...1 Accessing your Server...2 cpanel Users...2 WHM Interface...3 cpanel Interface...3
Linux VPS with cpanel Getting Started Guide First Edition October 2010 Table of Contents Introduction...1 cpanel Documentation...1 Accessing your Server...2 cpanel Users...2 WHM Interface...3 cpanel Interface...3
EDINBURGH UNIVERSITY PRESS LIBRARIAN ADMINISTRATION USER GUIDE http://www.euppublishing.com
 EDINBURGH UNIVERSITY PRESS LIBRARIAN ADMINISTRATION USER GUIDE http://www.euppublishing.com Journal Subscription Activation... 1 1. Register as an Individual User... 1 2. Subscription Confirmation Email...
EDINBURGH UNIVERSITY PRESS LIBRARIAN ADMINISTRATION USER GUIDE http://www.euppublishing.com Journal Subscription Activation... 1 1. Register as an Individual User... 1 2. Subscription Confirmation Email...
Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive
 Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
Using Microsoft Windows Authentication for Microsoft SQL Server Connections in Data Archive 2014 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
2X SecureRemoteDesktop. Version 1.1
 2X SecureRemoteDesktop Version 1.1 Website: www.2x.com Email: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious
2X SecureRemoteDesktop Version 1.1 Website: www.2x.com Email: info@2x.com Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious
PingFederate. Identity Menu Builder. User Guide. Version 1.0
 Identity Menu Builder Version 1.0 User Guide 2011 Ping Identity Corporation. All rights reserved. Identity Menu Builder User Guide Version 1.0 April, 2011 Ping Identity Corporation 1099 18th Street, Suite
Identity Menu Builder Version 1.0 User Guide 2011 Ping Identity Corporation. All rights reserved. Identity Menu Builder User Guide Version 1.0 April, 2011 Ping Identity Corporation 1099 18th Street, Suite
How To Use Salesforce Identity Features
 Identity Implementation Guide Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
Identity Implementation Guide Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of
plonesocial.auth.rpx Documentation
 plonesocial.auth.rpx Documentation Release 0.9 Carsten Rebbien August 14, 2014 Contents 1 Tutorial 3 1.1 Install plonesocial.auth.rpx in Plone................................... 3 1.2 Creating an account
plonesocial.auth.rpx Documentation Release 0.9 Carsten Rebbien August 14, 2014 Contents 1 Tutorial 3 1.1 Install plonesocial.auth.rpx in Plone................................... 3 1.2 Creating an account
OpenID Connect 1.0 for Enterprise
 OpenID Connect 1.0 for Enterprise By Paul Madsen Executive Overview In order to meet the challenges presented by the use of mobile apps and cloud services in the enterprise, a new generation of identity
OpenID Connect 1.0 for Enterprise By Paul Madsen Executive Overview In order to meet the challenges presented by the use of mobile apps and cloud services in the enterprise, a new generation of identity
Cisco ASA Adaptive Security Appliance Single Sign-On: Solution Brief
 Guide Cisco ASA Adaptive Security Appliance Single Sign-On: Solution Brief October 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 21 Contents
Guide Cisco ASA Adaptive Security Appliance Single Sign-On: Solution Brief October 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 21 Contents
ClickView Digital Signage User Manual
 ClickView Digital Signage User Manual Table of Contents 1. What is ClickView Digital Signage?... 3 2. Where do I find ClickView Digital Signage?... 3 2.1. To find ClickView Digital Signage... 3 3. How
ClickView Digital Signage User Manual Table of Contents 1. What is ClickView Digital Signage?... 3 2. Where do I find ClickView Digital Signage?... 3 2.1. To find ClickView Digital Signage... 3 3. How
a media development and design company Please give us a general overview of your business and the services/products you offer.
 Client Name: Date: Strategy and Design Please give us a general overview of your business and the services/products you offer. What are the main reasons why you want to develop or redesign your website?
Client Name: Date: Strategy and Design Please give us a general overview of your business and the services/products you offer. What are the main reasons why you want to develop or redesign your website?
Note that if at any time during the setup process you are asked to login, click either Cancel or Work Offline depending upon the prompt.
 USC Marshall School of Business Academic Information Services Configuring Outlook 2010 RPC Over HTTP Protocol For Windows 7 Home Computers or Wireless Laptops The steps in this document cover how to configure
USC Marshall School of Business Academic Information Services Configuring Outlook 2010 RPC Over HTTP Protocol For Windows 7 Home Computers or Wireless Laptops The steps in this document cover how to configure
Welcome to ECBuzz.com! Please go through this document carefully to make the experience of owning and using a website an enjoyable one.
 Sales call: 90116 90305 Sales email: sales@ecbuzz.com Support email: support@ecbuzz.com Welcome to ECBuzz.com! Please go through this document carefully to make the experience of owning and using a website
Sales call: 90116 90305 Sales email: sales@ecbuzz.com Support email: support@ecbuzz.com Welcome to ECBuzz.com! Please go through this document carefully to make the experience of owning and using a website
HTTP Mutual authentication and Web security
 HTTP Mutual authentication and Web security Yutaka OIWA SAAG, IETF 80 Prague Web security Its importance no need to say Transaction security (credit card, PayPal etc.) User data privacy Most online consumer
HTTP Mutual authentication and Web security Yutaka OIWA SAAG, IETF 80 Prague Web security Its importance no need to say Transaction security (credit card, PayPal etc.) User data privacy Most online consumer
Web Meetings through VPN. Note: Conductor means person leading the meeting. Table of Contents. Instant Web Meetings with VPN (Conductor)...
 Table of Contents Instant Web Meetings with VPN (Conductor)...2 How to Set Up a Scheduled Web Meeting with VPN (Conductor)...6 How to Set Up a Support Web Meeting with GVSU VPN Service (Conductor)...15
Table of Contents Instant Web Meetings with VPN (Conductor)...2 How to Set Up a Scheduled Web Meeting with VPN (Conductor)...6 How to Set Up a Support Web Meeting with GVSU VPN Service (Conductor)...15
Online shopping store
 Online shopping store 1. Research projects: A physical shop can only serves the people locally. An online shopping store can resolve the geometrical boundary faced by the physical shop. It has other advantages,
Online shopping store 1. Research projects: A physical shop can only serves the people locally. An online shopping store can resolve the geometrical boundary faced by the physical shop. It has other advantages,
TYPO3 6.x Enterprise Web CMS
 An Acira Group Whitepaper April 2013 TYPO3 6.x Enterprise Web CMS A cloud ready open source web platform with enterprise systems integration Executive Summary TYPO3 separates content from design and function,
An Acira Group Whitepaper April 2013 TYPO3 6.x Enterprise Web CMS A cloud ready open source web platform with enterprise systems integration Executive Summary TYPO3 separates content from design and function,
Work with PassKey Manager
 Work with PassKey Manager Trademark Notice Blackboard, the Blackboard logos, and the unique trade dress of Blackboard are the trademarks, service marks, trade dress and logos of Blackboard, Inc. All other
Work with PassKey Manager Trademark Notice Blackboard, the Blackboard logos, and the unique trade dress of Blackboard are the trademarks, service marks, trade dress and logos of Blackboard, Inc. All other
Exhibitor Services User Guide
 Exhibitor Services User Guide For Exhibitors CONTENTS Login and overview... 2 Profile... 3 Logo... 4 Products... 4 How does my company information appear in the mobile app?... 5 LEADS Users... 6 Qualifying
Exhibitor Services User Guide For Exhibitors CONTENTS Login and overview... 2 Profile... 3 Logo... 4 Products... 4 How does my company information appear in the mobile app?... 5 LEADS Users... 6 Qualifying
Tableau Server Trusted Authentication
 Tableau Server Trusted Authentication When you embed Tableau Server views into webpages, everyone who visits the page must be a licensed user on Tableau Server. When users visit the page they will be prompted
Tableau Server Trusted Authentication When you embed Tableau Server views into webpages, everyone who visits the page must be a licensed user on Tableau Server. When users visit the page they will be prompted
Beyond The Web Drupal Meets The Desktop (And Mobile) Justin Miller Code Sorcery Workshop, LLC http://codesorcery.net/dcdc
 Beyond The Web Drupal Meets The Desktop (And Mobile) Justin Miller Code Sorcery Workshop, LLC http://codesorcery.net/dcdc Introduction Personal introduction Format & conventions for this talk Assume familiarity
Beyond The Web Drupal Meets The Desktop (And Mobile) Justin Miller Code Sorcery Workshop, LLC http://codesorcery.net/dcdc Introduction Personal introduction Format & conventions for this talk Assume familiarity
EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL
 EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL The following manual will outline the configuration and setup for email access by any staff member. There are multiple ways to configure this
EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL The following manual will outline the configuration and setup for email access by any staff member. There are multiple ways to configure this
WebEx Integration to Lotus Notes. Users Guide
 WebEx Integration to Lotus Notes Users Guide 072310 Copyright 1997 2010 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are trademarks
WebEx Integration to Lotus Notes Users Guide 072310 Copyright 1997 2010 Cisco and/or its affiliates. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are trademarks
Identity Implementation Guide
 Identity Implementation Guide Version 37.0, Summer 16 @salesforcedocs Last updated: May 26, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com,
Identity Implementation Guide Version 37.0, Summer 16 @salesforcedocs Last updated: May 26, 2016 Copyright 2000 2016 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com,
Shibboleth Development and Support Services. OpenID and SAML. Fiona Culloch, EDINA. EuroCAMP, Stockholm, 7 May 2008
 OpenID and SAML Fiona Culloch, EDINA EuroCAMP, Stockholm, 7 May 2008 What is OpenID for? In principle, an OpenID is a universal username, valid across multiple, unrelated services E.g., I have fculloch.protectnetwork.org
OpenID and SAML Fiona Culloch, EDINA EuroCAMP, Stockholm, 7 May 2008 What is OpenID for? In principle, an OpenID is a universal username, valid across multiple, unrelated services E.g., I have fculloch.protectnetwork.org
Multi-Factor Authentication Job Aide
 To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
CRM to Exchange Synchronization
 CRM to Exchange Synchronization Product Registration Instructions VERSION 2.0 DATE PREPARED: 1/1/2013 DEVELOPMENT: BRITE GLOBAL, INC. 2012 Brite Global, Incorporated. All rights reserved. The information
CRM to Exchange Synchronization Product Registration Instructions VERSION 2.0 DATE PREPARED: 1/1/2013 DEVELOPMENT: BRITE GLOBAL, INC. 2012 Brite Global, Incorporated. All rights reserved. The information
SAP Cloud Identity Service Document Version: 1.0 2014-09-01. SAP Cloud Identity Service
 Document Version: 1.0 2014-09-01 Content 1....4 1.1 Release s....4 1.2 Product Overview....8 Product Details.... 9 Supported Browser Versions....10 Supported Languages....12 1.3 Getting Started....13 1.4
Document Version: 1.0 2014-09-01 Content 1....4 1.1 Release s....4 1.2 Product Overview....8 Product Details.... 9 Supported Browser Versions....10 Supported Languages....12 1.3 Getting Started....13 1.4
PowerTerm WebConnect. Integration Instructions with Juniper SSL VPN
 PowerTerm WebConnect Integration Instructions with Juniper SSL VPN Version 2.2 May 17, 2009 Notice This document is subject to the following conditions and restrictions: The proprietary information belongs
PowerTerm WebConnect Integration Instructions with Juniper SSL VPN Version 2.2 May 17, 2009 Notice This document is subject to the following conditions and restrictions: The proprietary information belongs
SCADA Security. Enabling Integrated Windows Authentication For CitectSCADA Web Client. Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.
 Enabling Integrated Windows Authentication For CitectSCADA Web Client Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.xx Summary: What is the difference between Basic Authentication and Windows
Enabling Integrated Windows Authentication For CitectSCADA Web Client Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.xx Summary: What is the difference between Basic Authentication and Windows
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
AskCody Connect Connect your Outlook or AD to AskCody s solutions seamlessly. Everything included!
 AskCody Connect Connect your Outlook or AD to AskCody s solutions seamlessly. Everything included! Integrate the solutions from AskCody with your existing calendar system and create a complete, dynamic
AskCody Connect Connect your Outlook or AD to AskCody s solutions seamlessly. Everything included! Integrate the solutions from AskCody with your existing calendar system and create a complete, dynamic
How to Implement the X.509 Certificate Based Single Sign-On Solution with SAP Netweaver Single Sign-On
 How to Implement the X.509 Certificate Based Single Sign-On Solution with SAP Netweaver Single Sign-On How to implement the X.509 certificate based Single Sign-On solution from SAP Page 2 of 34 How to
How to Implement the X.509 Certificate Based Single Sign-On Solution with SAP Netweaver Single Sign-On How to implement the X.509 certificate based Single Sign-On solution from SAP Page 2 of 34 How to
Administration Guide. BlackBerry Enterprise Service 12. Version 12.0
 Administration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2015-01-16 SWD-20150116150104141 Contents Introduction... 9 About this guide...10 What is BES12?...11 Key features of BES12...
Administration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2015-01-16 SWD-20150116150104141 Contents Introduction... 9 About this guide...10 What is BES12?...11 Key features of BES12...
From centralized to single sign on
 The LemonLDAP::NG project Abstract LemonLDAP::NG is a modular WebSSO (Web Single Sign On) software based on Apache::Session modules. It simplifies the build of a protected area with a few changes in the
The LemonLDAP::NG project Abstract LemonLDAP::NG is a modular WebSSO (Web Single Sign On) software based on Apache::Session modules. It simplifies the build of a protected area with a few changes in the
Cloud-based Identity and Access Control for Diagnostic Imaging Systems
 Cloud-based Identity and Access Control for Diagnostic Imaging Systems Weina Ma and Kamran Sartipi Department of Electrical, Computer and Software Engineering University of Ontario Institute of Technology
Cloud-based Identity and Access Control for Diagnostic Imaging Systems Weina Ma and Kamran Sartipi Department of Electrical, Computer and Software Engineering University of Ontario Institute of Technology
HOW TO USE THE ACCESS CODE. Adding Members to Your Group Using the Access Code
 HOW TO USE THE ACCESS CODE Adding Members to Your Group Using the Access Code New group members (your personnel) may be added to your group by any of these options: - Manually, using either the Add Members
HOW TO USE THE ACCESS CODE Adding Members to Your Group Using the Access Code New group members (your personnel) may be added to your group by any of these options: - Manually, using either the Add Members
My Sage Pay User Manual
 My Sage Pay User Manual Page 1 of 32 Contents 01. About this guide..4 02. Getting started.4 Online help Accessing My Sage Pay Test Servers Live Servers The Administrator account Creating user accounts
My Sage Pay User Manual Page 1 of 32 Contents 01. About this guide..4 02. Getting started.4 Online help Accessing My Sage Pay Test Servers Live Servers The Administrator account Creating user accounts
Identity Management in Liferay Overview and Best Practices. Liferay Portal 6.0 EE
 Identity Management in Liferay Overview and Best Practices Liferay Portal 6.0 EE Table of Contents Introduction... 1 IDENTITY MANAGEMENT HYGIENE... 1 Where Liferay Fits In... 2 How Liferay Authentication
Identity Management in Liferay Overview and Best Practices Liferay Portal 6.0 EE Table of Contents Introduction... 1 IDENTITY MANAGEMENT HYGIENE... 1 Where Liferay Fits In... 2 How Liferay Authentication
How to Configure Active Directory based User Authentication
 How to Configure Active Directory based User Authentication You Must Have: Microsoft server with Active Directory configured. Windows 2000 Server is configured as Active Directory server in this example.
How to Configure Active Directory based User Authentication You Must Have: Microsoft server with Active Directory configured. Windows 2000 Server is configured as Active Directory server in this example.
Configuring and Integrating JMX
 Configuring and Integrating JMX The Basics of JMX 3 JConsole 3 Adding a JMX Component Monitor to SAM 6 This document includes basic information about JMX and its role with SolarWinds SAM 2 Configuring
Configuring and Integrating JMX The Basics of JMX 3 JConsole 3 Adding a JMX Component Monitor to SAM 6 This document includes basic information about JMX and its role with SolarWinds SAM 2 Configuring
Enabling Kerberos SSO in IBM Cognos Express on Windows Server 2008
 Enabling Kerberos SSO in IBM Cognos Express on Windows Server 2008 Nature of Document: Guideline Product(s): IBM Cognos Express Area of Interest: Infrastructure 2 Copyright and Trademarks Licensed Materials
Enabling Kerberos SSO in IBM Cognos Express on Windows Server 2008 Nature of Document: Guideline Product(s): IBM Cognos Express Area of Interest: Infrastructure 2 Copyright and Trademarks Licensed Materials
CLAIMS-BASED IDENTITY FOR WINDOWS
 CLAIMS-BASED IDENTITY FOR WINDOWS TECHNOLOGIES AND SCENARIOS DAVID CHAPPELL FEBRUARY 2011 SPONSORED BY MICROSOFT CORPORATION CONTENTS Understanding Claims-Based Identity... 3 The Problem: Working with
CLAIMS-BASED IDENTITY FOR WINDOWS TECHNOLOGIES AND SCENARIOS DAVID CHAPPELL FEBRUARY 2011 SPONSORED BY MICROSOFT CORPORATION CONTENTS Understanding Claims-Based Identity... 3 The Problem: Working with
Infoshare ediscovery Portal Registration Guide
 Infoshare ediscovery Portal Registration Guide Camden County Prosecutor s Office 330 Mac Lane, Keasbey, N.J. 08832 (732) 346-0200 www.infoshare.com www.infoshare.com Page 1 1. REGISTRATION: Open a browser
Infoshare ediscovery Portal Registration Guide Camden County Prosecutor s Office 330 Mac Lane, Keasbey, N.J. 08832 (732) 346-0200 www.infoshare.com www.infoshare.com Page 1 1. REGISTRATION: Open a browser
Cloud federation. Prelude to Hybrid Clouds. CHEP 2015 Okinawa, Japan. Marek Denis CERN Geneva, Switzerland
 Cloud federation CHEP 2015 Okinawa, Japan Prelude to Hybrid Clouds Marek Denis CERN Geneva, Switzerland Basic definitions OpenStack: An Open Source Cloud Managing System which allows implementors to: --
Cloud federation CHEP 2015 Okinawa, Japan Prelude to Hybrid Clouds Marek Denis CERN Geneva, Switzerland Basic definitions OpenStack: An Open Source Cloud Managing System which allows implementors to: --
BEST WEB PROGRAMMING LANGUAGES TO LEARN ON YOUR OWN TIME
 BEST WEB PROGRAMMING LANGUAGES TO LEARN ON YOUR OWN TIME System Analysis and Design S.Mohammad Taheri S.Hamed Moghimi Fall 92 1 CHOOSE A PROGRAMMING LANGUAGE FOR THE PROJECT 2 CHOOSE A PROGRAMMING LANGUAGE
BEST WEB PROGRAMMING LANGUAGES TO LEARN ON YOUR OWN TIME System Analysis and Design S.Mohammad Taheri S.Hamed Moghimi Fall 92 1 CHOOSE A PROGRAMMING LANGUAGE FOR THE PROJECT 2 CHOOSE A PROGRAMMING LANGUAGE
CIC ASHRAE Meeting Registration Online Training Session
 Go to the ASHRAE website http://www.indyashrae.org Click on the member area login button. Type in your chapter ID and password; chapter ID is your ASHRAE Society membership number. The password is eggplant,
Go to the ASHRAE website http://www.indyashrae.org Click on the member area login button. Type in your chapter ID and password; chapter ID is your ASHRAE Society membership number. The password is eggplant,
CHARTER BUSINESS CUSTOM HOSTING MIGRATION INSTRUCTIONS
 1. Go to https://cp.charter-business.net 2. Enter the username that was provided to you in the letter and/or email you received from Charter Business. 3. Enter your password by entering the letters Ch
1. Go to https://cp.charter-business.net 2. Enter the username that was provided to you in the letter and/or email you received from Charter Business. 3. Enter your password by entering the letters Ch
Connecting Users with Identity as a Service
 Ping Identity has demonstrated support for multiple workforce and external identity use cases, as well as strong service provider support. Gregg Kreizman Gartner 1 Connecting Users with Identity as a Service
Ping Identity has demonstrated support for multiple workforce and external identity use cases, as well as strong service provider support. Gregg Kreizman Gartner 1 Connecting Users with Identity as a Service
Designing Service-Oriented Tools
 Designing Service-Oriented Tools for HPC Account Management and Reporting Adam G. Carlyle Robert D. French William A. Renaud ORNL is managed by UT-Battelle for the US Department of Energy Projects: OLCF
Designing Service-Oriented Tools for HPC Account Management and Reporting Adam G. Carlyle Robert D. French William A. Renaud ORNL is managed by UT-Battelle for the US Department of Energy Projects: OLCF
Customer Tips. Configuring Color Access on the WorkCentre 7328/7335/7345 using Windows Active Directory. for the user. Overview
 Xerox Multifunction Devices Customer Tips February 13, 2008 This document applies to the stated Xerox products. It is assumed that your device is equipped with the appropriate option(s) to support the
Xerox Multifunction Devices Customer Tips February 13, 2008 This document applies to the stated Xerox products. It is assumed that your device is equipped with the appropriate option(s) to support the
Project specification for suncoastreoholdings.com. Version 1.0
 Project specification for suncoastreoholdings.com Version 1.0 This document lists the list of major functionality that this website will offer on its first version. 10/2/2012 Table of Contents Introduction...
Project specification for suncoastreoholdings.com Version 1.0 This document lists the list of major functionality that this website will offer on its first version. 10/2/2012 Table of Contents Introduction...
A Guide to New Features in Propalms OneGate 4.0
 A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
