End to End Defense against Rootkits in Cloud Environment. Design- Part 2
|
|
|
- Lucinda Harmon
- 8 years ago
- Views:
Transcription
1 End to End Defense against Rootkits in Cloud Environment Design- Part 2 Sachin Shetty Associate Professor Electrical and Computer Engineering Director, Cybersecurity Laboratory Tennessee State University
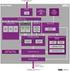
2 RootKitDet- Scalability In order to monitor multiple guest OSes simultaneously, we expands our system into a scalable architecture For each guest OS, we generate related meta-data of the kernel in advance, which includes: (1) system.map which contains names and locations of the kernel symbols, (2) checksum of the kernel code which is used to detect modifications to the running kernel code, (3) definitions of important data structures that might be referred to by the rootkits or during recovery, (4) type information of important global variables and dynamically allocated objects and their relationship in the kernel.
3 RootkitDet: Scalable Architecture Guest OS 1 Kernel... Guest OS n Kernel VMM Dector Analyzer & Recoverer Conductor Registered kernel and modules RootkitDet Rootkit profiles
4 RootKitDet: Scalability Our system takes advantages of the kernel s meta-data to detect kernel-level rootkits and perform recovery. Besides, only one kernel s meta-data is necessary if all of the guest OSes are using the same kernel Furthermore, several guest OSes can also runs on the same hypervisor if the hypervisor supports multiple guest OSes.
5 RootkitDet: Detection Procedure Challenges Under some particular conditions, inconsistency between the executable regions and loaded modules may occur in the kernel of guest OSes, which causes a false positive in detection procedure 1. Case 1: When a module is loading, the kernel allocates another executable region for its initialization code, which is released immediately after the initialization code is executed. The temporary existence of initialization code of a module may cause a false positive. We confirm the detection of rootkits only when the detector continuously reports rootkits 3 times.
6 RootkitDet: Detection Procedure Challenges Case 2: When a module is unloaded, the kernel doesn t release related regions until the total size reaches a threshold. The lazy clean-up may also cause false positive. We require a subtle modification to the kernel source code to release all free regions once a module is unloaded. This modification doesn t affect the efficiency of the kernel because unloading modules happens rarely in general.
7 RootkitDet: Detection Procedure Challenges Case 3: Unused space usually exists below the code of a module because of the pagealigned allocation of memory. As far as we know, the kernel doesn t clear the memory regions allocated for modules before loading modules into them. As a result, the unused space may contain nonzero data, which cause a false positive in detection procedure 2. To eliminate this kind of false positive, we require a subtle modification to the kernel source code to clear the last page of memory regions allocated for modules.
8 RootkitDet: Detection Procedure Challenges The code of a module varies with the relocation address of the module when it is loaded into the kernel. We can t compute checksums of modules in detection procedure 3 because the original object files of modules are not required when the detector computes checksums in our system. To reduce the work of the detector, the original checksums of modules are provided by the conductor The detector computes current checksums of legitimate code respectively, and compares them with original checksums. Any mismatch means modifications to the legitimate code.
9 RootkitDet: Detection Procedure Detection procedures are performed periodically instead of being triggered like Patagonix Rootkits that are erased immediately after execution are out the scope of the system, RootkitDet focuses only on the kernel space instead of the space of all processes. Overhead of periodical detection is small. Unused space of modules should be checked lthough the pages are already legitimate to be executed. RootkitDet more flexible to adjust periods of detection procedures.
10 RootkitDet: Diagnosis To categorize the detected rootkit, we investigate well known typical rootkits according to the intentions that rootkits achieve and the tactics that rootkits adopt. For each typical rootkit, we generate a profile to describe its tactic to achieve its intention as well as modified data structures and objects that we should recover.
11 RootkitDet: Diagnosis Generate profiles of typical rootkits manually due to the following reasons. First, rootkits may achieve different intentions together, and understanding the intentions and related tactics of rootkits requires manual effort. Second, data structures and objects that are accessed in the same tactic might subtly vary with the kernel version. Third, rootkits may implement the same tactic in different ways.
12 RootkitDet: Diagnosis To apply the profiles of known rootkits during diagnosis, we translate the profiles into ones that coordinate with the kernel running in the guest OS monitored by our system. Then the profiles of known rootkits are ready to categorize the detected rootkit. Categorization is done by matching certain characteristic information (collected from the detected rootkit) against the set of pre-generated profiles.
13 RootkitDet: Diagnosis RootkitDet system performs static analysis on the code of rootkit to collect characteristic information. The characteristic information is divided into two groups. One group is the control flow information. Usually, a rootkit calls to some kernel functions to achieve its intentions, which we name external function call s. The other group is the global variables and dynamically allocated data structures accessed by the rootkit. In general, to access special data structure maintained by the kernel, the rootkit has to find it starting from a global variable and tracking down according to the relationship among different data structures.
14 RootkitDet: Diagnosis A global variable is actually a kernel symbol and usually accessed by its address which is constant. The characteristic information collected through static analysis is binary. RootkitDet system translates the characteristi information according to the meta-data of the kernel. Translated information is then used to categorize the detected rootkit.
15 RootkitDet: Diagnosis We extract the characteristic information of the rootkit through static analysis. We focus on external function calls and memory access during static analysis instead of the control flow of the code. Determine the values of CPU registers during static analysis. We create a static machine with a special CPU and stack to execute the code of rootkit statically.
16 RootkitDet: Diagnosis First, we use a pair < val, flags> to represent the value of a register, in which val represents the value while flags indicates validation of each byte of val. We update the pair instead of the value of registers when we execute instructions. Second, when an instruction involves read of memory other than the stack, we update val by the value of the memory and set flags by a value indicating val totally valid. Finally, some instructions load hard-coded immediate values into registers.
17 RootkitDet: Diagnosis In that case, we also update the flags of the target register according to the size of immediate value and the instruction type. In consequence, the values of registers that we can determine during static analysis are independent of execution environments. In most cases, we can determine the external function calls and accesses to global variables of the kernel, which we can use to infer the behavior of the suspicious code
18 RootkitDet: Diagnosis Example binary code snippet(middle), with its associated C snippet(left) and associated output of static analysis
19 RootkitDet: Recovery RootkitDet attempts to recover the infected kernel according to the profile of the rootkit. Data structures and objects that are modified by the rootkit are described in the profile of the rootkit. Combined with the meta-data of the kernel, recovery driven profile is derived from the profile of the rootkit. Recovery-driven profile describes how to locate the modified data structures and objects and how to recover them.
20 RootkitDet: Recovery: Control Data Expected values of the control data are locations of kernel functions. Data structures and objects maintained by the kernel can always be found tracking down from some global variable. Address of global variables are constant and can be found in the meta-data of the kernel. Recovery-driven profile for control data describes the tracking path from the global variable to the object containing the control data.
21 RootkitDet: Recovery: Control Data For example, a rootkit may overwrite the pointers of functions registered with the virtual file system layer by the pseudo random number generator (PRNG) to disable the PRNG [17]. The pointers of functions registered by the PRNG are stored in structures random fops and urandom fops, which are located in the object devlist, a list of memory devices that is a global variable. Recovery-driven profile for the functions registered by PRNG contains the address of devlist, offsets of random fops and urandom fops in devlist as well as the real addresses of the functions registered by the PRNG.
22 RootkitDet: Recovery: Non Control Data Non-control data is different because the original values are either lost forever or not easy to calculate. Non-control data is different in the way to locate the related data structures or objects. For example, a rootkit hides a process by removing related item from the pid hash table. Then we can t find the process tracking down from the pid hash table. The only way to find the process is tracking down from init task and checking each process whether it is not linked into the pid hash table.
23 RootkitDet: Recovery: Non Control Data As a result, the recovery-driven profile for non-control data describes how to restore the broken links or resolve violations of invariants as well as the tracking path from the global variable to the object containing the non-control data. If the original value of a non-control data are lost forever, we can not recover it. For example, we can not recover the entropy pool of PRNG if it is zeroed by a rootkit
24 RootkitDet: Design Requirements Scalable. RootkitDet should support detection of kernel-level rootkits on multi- VMs, Low overhead. Performance is critical in cloud environment because the cost a cloud user should pay depends on the resources that he consumes. Easy to adopt. Xen[23] and KVM[12] are both used to create VMs in the cloud, It should be easy to deploy RootkitDet system in the cloud base on both Xen and KVM.
25 RootkitDet: Detection Method Procedure 1 - Detect whether extra executable regions exist in the kernel space. Procedure 2 - Detect whether some code resides in unused spaces of modules. Procedure 3 - Detect whether the code of kernel or modules are modified. We can conclude that kernel-level rootkits exist if and only if any of the procedures above comes true. The only precondition is that the NX feature is enabled.
26 RootkitDet: Detection Method As we know, the kernel runs in a VM, so this precondition only depends on the settings of the physical machine and the kernel in the VM can not change it. In addition, we only read some registers and memory of the VM in all of the three procedures. We neither monitor the execution of the VM nor keep watch on some registers or memory of the VM. As a consequence, the overhead of this detection method is pretty low
27 RootKitDet Design Summary RootkitDet system consists of one conductor and multiple detectors. Conductor runs on the host OS as a user space process. Communicates with all of the detectors through IPC. Sends detection commands to the detectors, and receives responses back. If rootkits are detected, it raises alert. Detector detects kernel-level rootkits in a VM by reading its registers and memory. In order to conveniently access the VM s registers and memory, the detector is integrated into the qemu-kvm hypervisor
28 RootKitDet Design Summary Registration procedures Registration of kernel Registration of loadable kernel modules (LKMs) Detection procedures Detect extra executable regions in kernel space Detect code residing in unused space of LKMs Detect malicious modifications to legitimate code Challenges Inconsistency of executable regions when LKM is unloaded Kernel frees unused virtual memory area in a lazy manner Module s code is variable due to the relocation Relocation address and symbols of itself Symbols of main kernel, even other modules
29 RootKitDet Design Summary Static analysis Characteristic information of detected rootkits External function calls Global variables and dynamically allocated objects accessed by the code Categorization Profiles of known rootkits The tactic adopted by the rootkit to achieve its intention Data structures that are modified according to its tactic Detail the profiles Translate symbols into addresses according to the running kernel
30 RootKitDet Design Summary Recovery-driven profile Derived from the profile of the rootkit and meta-data of the running kernel Recovery of control data Expected values are constant and known Tracking down from some global variable Recovery of non-control data Expected values can be inferred if logical relations among non-control data and other objects in the kernel
End to End Defense against Rootkits in Cloud Environment Sachin Shetty
 End to End Defense against Rootkits in Cloud Environment Sachin Shetty Associate Professor Electrical and Computer Engineering Director, Cybersecurity Laboratory Tennessee State University Tennessee State
End to End Defense against Rootkits in Cloud Environment Sachin Shetty Associate Professor Electrical and Computer Engineering Director, Cybersecurity Laboratory Tennessee State University Tennessee State
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtual Machine Security
 Virtual Machine Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/ 1 Operating System Quandary Q: What is the primary goal
Virtual Machine Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/ 1 Operating System Quandary Q: What is the primary goal
Cloud Defense. Kevin Hall Cyber Security Technology Department 4/17/2012. Sandia National Laboratories SAND 2012-2581C
 4/17/2012 Cloud Defense Kevin Hall Cyber Security Technology Department Sandia National Laboratories SAND 2012-2581C Sandia National Laboratories is a multi program laboratory managed and operated by Sandia
4/17/2012 Cloud Defense Kevin Hall Cyber Security Technology Department Sandia National Laboratories SAND 2012-2581C Sandia National Laboratories is a multi program laboratory managed and operated by Sandia
Microkernels, virtualization, exokernels. Tutorial 1 CSC469
 Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Rootkit Detection on Virtual Machines through Deep Information Extraction at Hypervisor-level
 Rootkit Detection on Virtual Machines through Deep Information Extraction at Hypervisor-level Xiongwei Xie Department of SIS UNC Charlotte Charlotte, NC 28223 Email: xxie2@uncc.edu Weichao Wang Department
Rootkit Detection on Virtual Machines through Deep Information Extraction at Hypervisor-level Xiongwei Xie Department of SIS UNC Charlotte Charlotte, NC 28223 Email: xxie2@uncc.edu Weichao Wang Department
Data Centers and Cloud Computing
 Data Centers and Cloud Computing CS377 Guest Lecture Tian Guo 1 Data Centers and Cloud Computing Intro. to Data centers Virtualization Basics Intro. to Cloud Computing Case Study: Amazon EC2 2 Data Centers
Data Centers and Cloud Computing CS377 Guest Lecture Tian Guo 1 Data Centers and Cloud Computing Intro. to Data centers Virtualization Basics Intro. to Cloud Computing Case Study: Amazon EC2 2 Data Centers
Virtual Hosting & Virtual Machines
 & Virtual Machines Coleman Kane Coleman.Kane@ge.com September 2, 2014 Cyber Defense Overview / Machines 1 / 17 Similar to the network partitioning schemes described previously, there exist a menu of options
& Virtual Machines Coleman Kane Coleman.Kane@ge.com September 2, 2014 Cyber Defense Overview / Machines 1 / 17 Similar to the network partitioning schemes described previously, there exist a menu of options
How To Stop A Malicious Process From Running On A Hypervisor
 Hypervisor-Based Systems for Malware Detection and Prevention Yoshihiro Oyama ( 大 山 恵 弘 ) The University of Electro-Communications ( 電 気 通 信 大 学 ), Tokyo, Japan This Talk I introduce two hypervisor-based
Hypervisor-Based Systems for Malware Detection and Prevention Yoshihiro Oyama ( 大 山 恵 弘 ) The University of Electro-Communications ( 電 気 通 信 大 学 ), Tokyo, Japan This Talk I introduce two hypervisor-based
Run-Time Deep Virtual Machine Introspection & Its Applications
 Run-Time Deep Virtual Machine Introspection & Its Applications Jennia Hizver Computer Science Department Stony Brook University, NY, USA Tzi-cker Chiueh Cloud Computing Center Industrial Technology Research
Run-Time Deep Virtual Machine Introspection & Its Applications Jennia Hizver Computer Science Department Stony Brook University, NY, USA Tzi-cker Chiueh Cloud Computing Center Industrial Technology Research
High-Availability Using Open Source Software
 High-Availability Using Open Source Software Luka Perkov Iskon Internet, Zagreb, Croatia Nikola Pavković Ruđer Bošković Institute Bijenička cesta Zagreb, Croatia Juraj Petrović Faculty of Electrical Engineering
High-Availability Using Open Source Software Luka Perkov Iskon Internet, Zagreb, Croatia Nikola Pavković Ruđer Bošković Institute Bijenička cesta Zagreb, Croatia Juraj Petrović Faculty of Electrical Engineering
A Hypervisor IPS based on Hardware assisted Virtualization Technology
 A Hypervisor IPS based on Hardware assisted Virtualization Technology 1. Introduction Junichi Murakami (murakami@fourteenforty.jp) Fourteenforty Research Institute, Inc. Recently malware has become more
A Hypervisor IPS based on Hardware assisted Virtualization Technology 1. Introduction Junichi Murakami (murakami@fourteenforty.jp) Fourteenforty Research Institute, Inc. Recently malware has become more
The Benefits of POWER7+ and PowerVM over Intel and an x86 Hypervisor
 The Benefits of POWER7+ and PowerVM over Intel and an x86 Hypervisor Howard Anglin rhbear@us.ibm.com IBM Competitive Project Office May 2013 Abstract...3 Virtualization and Why It Is Important...3 Resiliency
The Benefits of POWER7+ and PowerVM over Intel and an x86 Hypervisor Howard Anglin rhbear@us.ibm.com IBM Competitive Project Office May 2013 Abstract...3 Virtualization and Why It Is Important...3 Resiliency
Intel s Virtualization Extensions (VT-x) So you want to build a hypervisor?
 Intel s Virtualization Extensions (VT-x) So you want to build a hypervisor? Mr. Jacob Torrey February 26, 2014 Dartmouth College 153 Brooks Road, Rome, NY 315.336.3306 http://ainfosec.com @JacobTorrey
Intel s Virtualization Extensions (VT-x) So you want to build a hypervisor? Mr. Jacob Torrey February 26, 2014 Dartmouth College 153 Brooks Road, Rome, NY 315.336.3306 http://ainfosec.com @JacobTorrey
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Virtual Computing and VMWare. Module 4
 Virtual Computing and VMWare Module 4 Virtual Computing Cyber Defense program depends on virtual computing We will use it for hands-on learning Cyber defense competition will be hosted on a virtual computing
Virtual Computing and VMWare Module 4 Virtual Computing Cyber Defense program depends on virtual computing We will use it for hands-on learning Cyber defense competition will be hosted on a virtual computing
Dynamic Load Balancing of Virtual Machines using QEMU-KVM
 Dynamic Load Balancing of Virtual Machines using QEMU-KVM Akshay Chandak Krishnakant Jaju Technology, College of Engineering, Pune. Maharashtra, India. Akshay Kanfade Pushkar Lohiya Technology, College
Dynamic Load Balancing of Virtual Machines using QEMU-KVM Akshay Chandak Krishnakant Jaju Technology, College of Engineering, Pune. Maharashtra, India. Akshay Kanfade Pushkar Lohiya Technology, College
Windows Server Virtualization & The Windows Hypervisor
 Windows Server Virtualization & The Windows Hypervisor Brandon Baker Lead Security Engineer Windows Kernel Team Microsoft Corporation Agenda - Windows Server Virtualization (WSV) Why a hypervisor? Quick
Windows Server Virtualization & The Windows Hypervisor Brandon Baker Lead Security Engineer Windows Kernel Team Microsoft Corporation Agenda - Windows Server Virtualization (WSV) Why a hypervisor? Quick
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR
 GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
Analysis of the Linux Audit System 1
 Analysis of the Linux Audit System 1 Authors Bruno Morisson, MSc (Royal Holloway, 2014) Stephen Wolthusen, ISG, Royal Holloway Overview Audit mechanisms on an operating system (OS) record relevant system
Analysis of the Linux Audit System 1 Authors Bruno Morisson, MSc (Royal Holloway, 2014) Stephen Wolthusen, ISG, Royal Holloway Overview Audit mechanisms on an operating system (OS) record relevant system
www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009
 SEE-GRID-SCI Virtualization and Grid Computing with XEN www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009 Milan Potocnik University
SEE-GRID-SCI Virtualization and Grid Computing with XEN www.see-grid-sci.eu Regional SEE-GRID-SCI Training for Site Administrators Institute of Physics Belgrade March 5-6, 2009 Milan Potocnik University
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines
 Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
QEMU-KVM + D-System Monitor Setup Manual
 DEOS-FY2014-QK-02E 2013-2014 Japan Science and Technology Agency QEMU-KVM + D-System Monitor Setup Manual Version E1.2 2014/02/01 Edited by DEOS R&D Center DEOS Project JST-CREST Research Area Dependable
DEOS-FY2014-QK-02E 2013-2014 Japan Science and Technology Agency QEMU-KVM + D-System Monitor Setup Manual Version E1.2 2014/02/01 Edited by DEOS R&D Center DEOS Project JST-CREST Research Area Dependable
Intro to Virtualization
 Cloud@Ceid Seminars Intro to Virtualization Christos Alexakos Computer Engineer, MSc, PhD C. Sysadmin at Pattern Recognition Lab 1 st Seminar 19/3/2014 Contents What is virtualization How it works Hypervisor
Cloud@Ceid Seminars Intro to Virtualization Christos Alexakos Computer Engineer, MSc, PhD C. Sysadmin at Pattern Recognition Lab 1 st Seminar 19/3/2014 Contents What is virtualization How it works Hypervisor
Chapter 5 Cloud Resource Virtualization
 Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Computer Science. About PaaS Security. Donghoon Kim Henry E. Schaffer Mladen A. Vouk
 About PaaS Security Donghoon Kim Henry E. Schaffer Mladen A. Vouk North Carolina State University, USA May 21, 2015 @ ICACON 2015 Outline Introduction Background Contribution PaaS Vulnerabilities and Countermeasures
About PaaS Security Donghoon Kim Henry E. Schaffer Mladen A. Vouk North Carolina State University, USA May 21, 2015 @ ICACON 2015 Outline Introduction Background Contribution PaaS Vulnerabilities and Countermeasures
Windows Server 2008 R2 Hyper-V Live Migration
 Windows Server 2008 R2 Hyper-V Live Migration Table of Contents Overview of Windows Server 2008 R2 Hyper-V Features... 3 Dynamic VM storage... 3 Enhanced Processor Support... 3 Enhanced Networking Support...
Windows Server 2008 R2 Hyper-V Live Migration Table of Contents Overview of Windows Server 2008 R2 Hyper-V Features... 3 Dynamic VM storage... 3 Enhanced Processor Support... 3 Enhanced Networking Support...
Cloud Computing #6 - Virtualization
 Cloud Computing #6 - Virtualization Main source: Smith & Nair, Virtual Machines, Morgan Kaufmann, 2005 Today What do we mean by virtualization? Why is it important to cloud? What is the penalty? Current
Cloud Computing #6 - Virtualization Main source: Smith & Nair, Virtual Machines, Morgan Kaufmann, 2005 Today What do we mean by virtualization? Why is it important to cloud? What is the penalty? Current
The Xen of Virtualization
 The Xen of Virtualization Assignment for CLC-MIRI Amin Khan Universitat Politècnica de Catalunya March 4, 2013 Amin Khan (UPC) Xen Hypervisor March 4, 2013 1 / 19 Outline 1 Introduction 2 Architecture
The Xen of Virtualization Assignment for CLC-MIRI Amin Khan Universitat Politècnica de Catalunya March 4, 2013 Amin Khan (UPC) Xen Hypervisor March 4, 2013 1 / 19 Outline 1 Introduction 2 Architecture
Practical Protection of Kernel Integrity for Commodity OS from Untrusted Extensions
 Practical Protection of Kernel Integrity for Commodity OS from Untrusted Extensions Xi Xiong The Pennsylvania State University xixiong@cse.psu.edu Donghai Tian The Pennsylvania State University Beijing
Practical Protection of Kernel Integrity for Commodity OS from Untrusted Extensions Xi Xiong The Pennsylvania State University xixiong@cse.psu.edu Donghai Tian The Pennsylvania State University Beijing
ProMoX: A Protocol Stack Monitoring Framework
 ProMoX: A Protocol Stack Monitoring Framework Elias Weingärtner, Christoph Terwelp, Klaus Wehrle Distributed Systems Group Chair of Computer Science IV RWTH Aachen University http://ds.cs.rwth-aachen.de
ProMoX: A Protocol Stack Monitoring Framework Elias Weingärtner, Christoph Terwelp, Klaus Wehrle Distributed Systems Group Chair of Computer Science IV RWTH Aachen University http://ds.cs.rwth-aachen.de
Windows Server 2008 R2 Hyper-V Live Migration
 Windows Server 2008 R2 Hyper-V Live Migration White Paper Published: August 09 This is a preliminary document and may be changed substantially prior to final commercial release of the software described
Windows Server 2008 R2 Hyper-V Live Migration White Paper Published: August 09 This is a preliminary document and may be changed substantially prior to final commercial release of the software described
Virtualization. Pradipta De pradipta.de@sunykorea.ac.kr
 Virtualization Pradipta De pradipta.de@sunykorea.ac.kr Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Virtualization Pradipta De pradipta.de@sunykorea.ac.kr Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
McAfee Deep Safe. Security beyond the OS. Kai-Ping Seidenschnur Senior Security Engineer. October 16, 2012
 McAfee Deep Safe Security beyond the OS Kai-Ping Seidenschnur Senior Security Engineer October 16, 2012 Intel/McAfee Initiatives: epo Deep Command and Deep Defender McAfee epo Deep Command Security Management
McAfee Deep Safe Security beyond the OS Kai-Ping Seidenschnur Senior Security Engineer October 16, 2012 Intel/McAfee Initiatives: epo Deep Command and Deep Defender McAfee epo Deep Command Security Management
IOS110. Virtualization 5/27/2014 1
 IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
Virtualization Technologies (ENCS 691K Chapter 3)
 Virtualization Technologies (ENCS 691K Chapter 3) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ The Key Technologies on Which Cloud Computing
Virtualization Technologies (ENCS 691K Chapter 3) Roch Glitho, PhD Associate Professor and Canada Research Chair My URL - http://users.encs.concordia.ca/~glitho/ The Key Technologies on Which Cloud Computing
Virtualization and cloud computing monitoring
 Virtualization and cloud computing monitoring Virtualization and cloud computing monitoring OpenOffice/PDF Version 1º Edition, 14 February 2011 Artica Soluciones Tecnológicas 2005 2011 1 MONITORING AMAZON
Virtualization and cloud computing monitoring Virtualization and cloud computing monitoring OpenOffice/PDF Version 1º Edition, 14 February 2011 Artica Soluciones Tecnológicas 2005 2011 1 MONITORING AMAZON
Introduction to Virtualization & KVM
 Introduction to Virtualization & KVM By Zahra Moezkarimi ICT Research Institute Software Platform Laboratory Outline Virtualization History Overview Advantages and Limitations Types of virtualization Virtualization
Introduction to Virtualization & KVM By Zahra Moezkarimi ICT Research Institute Software Platform Laboratory Outline Virtualization History Overview Advantages and Limitations Types of virtualization Virtualization
Virtual Machine Monitors. Dr. Marc E. Fiuczynski Research Scholar Princeton University
 Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtualization. Jukka K. Nurminen 23.9.2015
 Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Virtualization Jukka K. Nurminen 23.9.2015 Virtualization Virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms,
Transparent Monitoring of a Process Self in a Virtual Environment
 Transparent Monitoring of a Process Self in a Virtual Environment PhD Lunchtime Seminar Università di Pisa 24 Giugno 2008 Outline Background Process Self Attacks Against the Self Dynamic and Static Analysis
Transparent Monitoring of a Process Self in a Virtual Environment PhD Lunchtime Seminar Università di Pisa 24 Giugno 2008 Outline Background Process Self Attacks Against the Self Dynamic and Static Analysis
OPEN SOURCE VIRTUALIZATION TRENDS. SYAMSUL ANUAR ABD NASIR Warix Technologies / Fedora Community Malaysia
 OPEN SOURCE VIRTUALIZATION TRENDS SYAMSUL ANUAR ABD NASIR Warix Technologies / Fedora Community Malaysia WHAT I WILL BE TALKING ON? Introduction to Virtualization Full Virtualization, Para Virtualization
OPEN SOURCE VIRTUALIZATION TRENDS SYAMSUL ANUAR ABD NASIR Warix Technologies / Fedora Community Malaysia WHAT I WILL BE TALKING ON? Introduction to Virtualization Full Virtualization, Para Virtualization
Security on cloud storage and IaaS
 Security on cloud storage and IaaS at Taiwan-Japan Workshop 2012/Nov/27 http://www.jst.go.jp/sicp/ws2012_nsc.html Kuniyasu Suzaki (RISEC) National Institute of Advanced Industrial Science and Technology
Security on cloud storage and IaaS at Taiwan-Japan Workshop 2012/Nov/27 http://www.jst.go.jp/sicp/ws2012_nsc.html Kuniyasu Suzaki (RISEC) National Institute of Advanced Industrial Science and Technology
Rackspace Cloud Databases and Container-based Virtualization
 Rackspace Cloud Databases and Container-based Virtualization August 2012 J.R. Arredondo @jrarredondo Page 1 of 6 INTRODUCTION When Rackspace set out to build the Cloud Databases product, we asked many
Rackspace Cloud Databases and Container-based Virtualization August 2012 J.R. Arredondo @jrarredondo Page 1 of 6 INTRODUCTION When Rackspace set out to build the Cloud Databases product, we asked many
Basics of Virtualisation
 Basics of Virtualisation Volker Büge Institut für Experimentelle Kernphysik Universität Karlsruhe Die Kooperation von The x86 Architecture Why do we need virtualisation? x86 based operating systems are
Basics of Virtualisation Volker Büge Institut für Experimentelle Kernphysik Universität Karlsruhe Die Kooperation von The x86 Architecture Why do we need virtualisation? x86 based operating systems are
Network virtualization in AutoI
 Network virtualization in AutoI and ResumeNet Future Internet Cluster meeting March, Sophia Antipolis Andreas Fischer, Andreas Berl, Alex Galis, Hermann de Meer Network Virtualization Network virtualization
Network virtualization in AutoI and ResumeNet Future Internet Cluster meeting March, Sophia Antipolis Andreas Fischer, Andreas Berl, Alex Galis, Hermann de Meer Network Virtualization Network virtualization
VIRTUALIZATION INTROSPECTION SYSTEM ON KVM-BASED CLOUD COMPUTING PLATFORMS. 100356010@nccu.edu.tw Advisor: yuf@nccu.edu.tw Software Security Lab.
 VIRTUALIZATION INTROSPECTION SYSTEM ON KVM-BASED CLOUD COMPUTING PLATFORMS 100356010@nccu.edu.tw Advisor: yuf@nccu.edu.tw Software Security Lab. Motivation The era of cloud computing Motivation In the
VIRTUALIZATION INTROSPECTION SYSTEM ON KVM-BASED CLOUD COMPUTING PLATFORMS 100356010@nccu.edu.tw Advisor: yuf@nccu.edu.tw Software Security Lab. Motivation The era of cloud computing Motivation In the
Making a Smooth Transition to a Hybrid Cloud with Microsoft Cloud OS
 Making a Smooth Transition to a Hybrid Cloud with Microsoft Cloud OS Transitioning from today s highly virtualized data center environments to a true cloud environment requires solutions that let companies
Making a Smooth Transition to a Hybrid Cloud with Microsoft Cloud OS Transitioning from today s highly virtualized data center environments to a true cloud environment requires solutions that let companies
How do Users and Processes interact with the Operating System? Services for Processes. OS Structure with Services. Services for the OS Itself
 How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
How do Users and Processes interact with the Operating System? Users interact indirectly through a collection of system programs that make up the operating system interface. The interface could be: A GUI,
Oracle VM Server Recovery Guide. Version 8.2
 Oracle VM Server Recovery Guide Version 8.2 Oracle VM Server for x86 Recovery Guide The purpose of this document is to provide the steps necessary to perform system recovery of an Oracle VM Server for
Oracle VM Server Recovery Guide Version 8.2 Oracle VM Server for x86 Recovery Guide The purpose of this document is to provide the steps necessary to perform system recovery of an Oracle VM Server for
Virtualization System Vulnerability Discovery Framework. Speaker: Qinghao Tang Title:360 Marvel Team Leader
 Virtualization System Vulnerability Discovery Framework Speaker: Qinghao Tang Title:360 Marvel Team Leader 1 360 Marvel Team Established in May 2015, the first professional could computing and virtualization
Virtualization System Vulnerability Discovery Framework Speaker: Qinghao Tang Title:360 Marvel Team Leader 1 360 Marvel Team Established in May 2015, the first professional could computing and virtualization
Introduction to Windows Azure Cloud Computing Futures Group, Microsoft Research Roger Barga, Jared Jackson,Nelson Araujo, Dennis Gannon, Wei Lu, and
 Introduction to Windows Azure Cloud Computing Futures Group, Microsoft Research Roger Barga, Jared Jackson,Nelson Araujo, Dennis Gannon, Wei Lu, and Jaliya Ekanayake Range in size from edge facilities
Introduction to Windows Azure Cloud Computing Futures Group, Microsoft Research Roger Barga, Jared Jackson,Nelson Araujo, Dennis Gannon, Wei Lu, and Jaliya Ekanayake Range in size from edge facilities
Effects of Memory Randomization, Sanitization and Page Cache on Memory Deduplication
 Effects of Memory Randomization, Sanitization and Page Cache on Memory Deduplication Kuniyasu Suzaki, Kengo Iijima, Toshiki Yagi, Cyrille Artho Research Institute for Secure Systems EuroSec 2012 at Bern,
Effects of Memory Randomization, Sanitization and Page Cache on Memory Deduplication Kuniyasu Suzaki, Kengo Iijima, Toshiki Yagi, Cyrille Artho Research Institute for Secure Systems EuroSec 2012 at Bern,
Attacking Hypervisors via Firmware and Hardware
 Attacking Hypervisors via Firmware and Hardware Alex Matrosov (@matrosov), Mikhail Gorobets, Oleksandr Bazhaniuk (@ABazhaniuk), Andrew Furtak, Yuriy Bulygin (@c7zero) Advanced Threat Research Agenda Hypervisor
Attacking Hypervisors via Firmware and Hardware Alex Matrosov (@matrosov), Mikhail Gorobets, Oleksandr Bazhaniuk (@ABazhaniuk), Andrew Furtak, Yuriy Bulygin (@c7zero) Advanced Threat Research Agenda Hypervisor
RCL: Software Prototype
 Business Continuity as a Service ICT FP7-609828 RCL: Software Prototype D3.2.1 June 2014 Document Information Scheduled delivery 30.06.2014 Actual delivery 30.06.2014 Version 1.0 Responsible Partner IBM
Business Continuity as a Service ICT FP7-609828 RCL: Software Prototype D3.2.1 June 2014 Document Information Scheduled delivery 30.06.2014 Actual delivery 30.06.2014 Version 1.0 Responsible Partner IBM
Cloud Computing. Up until now
 Cloud Computing Lecture 11 Virtualization 2011-2012 Up until now Introduction. Definition of Cloud Computing Grid Computing Content Distribution Networks Map Reduce Cycle-Sharing 1 Process Virtual Machines
Cloud Computing Lecture 11 Virtualization 2011-2012 Up until now Introduction. Definition of Cloud Computing Grid Computing Content Distribution Networks Map Reduce Cycle-Sharing 1 Process Virtual Machines
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
Virtualization: Know your options on Ubuntu. Nick Barcet. Ubuntu Server Product Manager nick.barcet@canonical.com
 Virtualization: Know your options on Ubuntu Nick Barcet Ubuntu Server Product Manager nick.barcet@canonical.com Agenda Defi nitions Host virtualization tools Desktop virtualization tools Ubuntu as a guest
Virtualization: Know your options on Ubuntu Nick Barcet Ubuntu Server Product Manager nick.barcet@canonical.com Agenda Defi nitions Host virtualization tools Desktop virtualization tools Ubuntu as a guest
FRONT FLYLEAF PAGE. This page has been intentionally left blank
 FRONT FLYLEAF PAGE This page has been intentionally left blank Abstract The research performed under this publication will combine virtualization technology with current kernel debugging techniques to
FRONT FLYLEAF PAGE This page has been intentionally left blank Abstract The research performed under this publication will combine virtualization technology with current kernel debugging techniques to
Chapter 14 Virtual Machines
 Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Virtual Servers. Virtual machines. Virtualization. Design of IBM s VM. Virtual machine systems can give everyone the OS (and hardware) that they want.
 Virtual machines Virtual machine systems can give everyone the OS (and hardware) that they want. IBM s VM provided an exact copy of the hardware to the user. Virtual Servers Virtual machines are very widespread.
Virtual machines Virtual machine systems can give everyone the OS (and hardware) that they want. IBM s VM provided an exact copy of the hardware to the user. Virtual Servers Virtual machines are very widespread.
2) Xen Hypervisor 3) UEC
 5. Implementation Implementation of the trust model requires first preparing a test bed. It is a cloud computing environment that is required as the first step towards the implementation. Various tools
5. Implementation Implementation of the trust model requires first preparing a test bed. It is a cloud computing environment that is required as the first step towards the implementation. Various tools
matasano Hardware Virtualization Rootkits Dino A. Dai Zovi
 Hardware Virtualization Rootkits Dino A. Dai Zovi Agenda Introductions Virtualization (Software and Hardware) Intel VT-x (aka Vanderpool ) VM Rootkits Implementing a VT-x based Rootkit Detecting Hardware-VM
Hardware Virtualization Rootkits Dino A. Dai Zovi Agenda Introductions Virtualization (Software and Hardware) Intel VT-x (aka Vanderpool ) VM Rootkits Implementing a VT-x based Rootkit Detecting Hardware-VM
Enterprise-Class Virtualization with Open Source Technologies
 Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Secure In-VM Monitoring Using Hardware Virtualization
 Secure In-VM Monitoring Using Hardware Virtualization Monirul Sharif Georgia Institute of Technology Atlanta, GA, USA msharif@cc.gatech.edu Wenke Lee Georgia Institute of Technology Atlanta, GA, USA wenke@cc.gatech.edu
Secure In-VM Monitoring Using Hardware Virtualization Monirul Sharif Georgia Institute of Technology Atlanta, GA, USA msharif@cc.gatech.edu Wenke Lee Georgia Institute of Technology Atlanta, GA, USA wenke@cc.gatech.edu
Soft-Timer Driven Transient Kernel Control Flow Attacks and Defense
 Soft-Timer Driven Transient Kernel Control Flow Attacks and Defense Jinpeng Wei, Bryan D. Payne, Jonathon Giffin, Calton Pu Georgia Institute of Technology Annual Computer Security Applications Conference
Soft-Timer Driven Transient Kernel Control Flow Attacks and Defense Jinpeng Wei, Bryan D. Payne, Jonathon Giffin, Calton Pu Georgia Institute of Technology Annual Computer Security Applications Conference
The MIPS architecture and virtualization
 The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
Virtual Private Systems for FreeBSD
 Virtual Private Systems for FreeBSD Klaus P. Ohrhallinger 06. June 2010 Abstract Virtual Private Systems for FreeBSD (VPS) is a novel virtualization implementation which is based on the operating system
Virtual Private Systems for FreeBSD Klaus P. Ohrhallinger 06. June 2010 Abstract Virtual Private Systems for FreeBSD (VPS) is a novel virtualization implementation which is based on the operating system
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies
 Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer kklemperer@blackboard.com Agenda Session Length:
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer kklemperer@blackboard.com Agenda Session Length:
Technology Insight Series
 Evaluating Storage Technologies for Virtual Server Environments Russ Fellows June, 2010 Technology Insight Series Evaluator Group Copyright 2010 Evaluator Group, Inc. All rights reserved Executive Summary
Evaluating Storage Technologies for Virtual Server Environments Russ Fellows June, 2010 Technology Insight Series Evaluator Group Copyright 2010 Evaluator Group, Inc. All rights reserved Executive Summary
x86 ISA Modifications to support Virtual Machines
 x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
Cloud Computing CS 15-319
 Cloud Computing CS 15-319 Virtualization Case Studies : Xen and VMware Lecture 20 Majd F. Sakr, Mohammad Hammoud and Suhail Rehman 1 Today Last session Resource Virtualization Today s session Virtualization
Cloud Computing CS 15-319 Virtualization Case Studies : Xen and VMware Lecture 20 Majd F. Sakr, Mohammad Hammoud and Suhail Rehman 1 Today Last session Resource Virtualization Today s session Virtualization
Lecture 2 Cloud Computing & Virtualization. Cloud Application Development (SE808, School of Software, Sun Yat-Sen University) Yabo (Arber) Xu
 Lecture 2 Cloud Computing & Virtualization Cloud Application Development (SE808, School of Software, Sun Yat-Sen University) Yabo (Arber) Xu Outline Introduction to Virtualization The Major Approaches
Lecture 2 Cloud Computing & Virtualization Cloud Application Development (SE808, School of Software, Sun Yat-Sen University) Yabo (Arber) Xu Outline Introduction to Virtualization The Major Approaches
Distributed Systems. Virtualization. Paul Krzyzanowski pxk@cs.rutgers.edu
 Distributed Systems Virtualization Paul Krzyzanowski pxk@cs.rutgers.edu Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Distributed Systems Virtualization Paul Krzyzanowski pxk@cs.rutgers.edu Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Virtual Machines and Security Paola Stone Martinez East Carolina University November, 2013.
 Virtual Machines and Security Paola Stone Martinez East Carolina University November, 2013. Keywords: virtualization, virtual machine, security. 1. Virtualization The rapid growth of technologies, nowadays,
Virtual Machines and Security Paola Stone Martinez East Carolina University November, 2013. Keywords: virtualization, virtual machine, security. 1. Virtualization The rapid growth of technologies, nowadays,
Security Model for VM in Cloud
 Security Model for VM in Cloud 1 Venkataramana.Kanaparti, 2 Naveen Kumar R, 3 Rajani.S, 4 Padmavathamma M, 5 Anitha.C 1,2,3,5 Research Scholars, 4Research Supervisor 1,2,3,4,5 Dept. of Computer Science,
Security Model for VM in Cloud 1 Venkataramana.Kanaparti, 2 Naveen Kumar R, 3 Rajani.S, 4 Padmavathamma M, 5 Anitha.C 1,2,3,5 Research Scholars, 4Research Supervisor 1,2,3,4,5 Dept. of Computer Science,
Week Overview. Installing Linux Linux on your Desktop Virtualization Basic Linux system administration
 ULI101 Week 06b Week Overview Installing Linux Linux on your Desktop Virtualization Basic Linux system administration Installing Linux Standalone installation Linux is the only OS on the computer Any existing
ULI101 Week 06b Week Overview Installing Linux Linux on your Desktop Virtualization Basic Linux system administration Installing Linux Standalone installation Linux is the only OS on the computer Any existing
Analysis on Virtualization Technologies in Cloud
 Analysis on Virtualization Technologies in Cloud 1 V RaviTeja Kanakala, V.Krishna Reddy, K.Thirupathi Rao 1 Research Scholar, Department of CSE, KL University, Vaddeswaram, India I. Abstract Virtualization
Analysis on Virtualization Technologies in Cloud 1 V RaviTeja Kanakala, V.Krishna Reddy, K.Thirupathi Rao 1 Research Scholar, Department of CSE, KL University, Vaddeswaram, India I. Abstract Virtualization
A block based storage model for remote online backups in a trust no one environment
 A block based storage model for remote online backups in a trust no one environment http://www.duplicati.com/ Kenneth Skovhede (author, kenneth@duplicati.com) René Stach (editor, rene@duplicati.com) Abstract
A block based storage model for remote online backups in a trust no one environment http://www.duplicati.com/ Kenneth Skovhede (author, kenneth@duplicati.com) René Stach (editor, rene@duplicati.com) Abstract
How To Create A Cloud Based System For Aaas (Networking)
 1 3.1 IaaS Definition IaaS: Infrastructure as a Service Through the internet, provide IT server, storage, computing power and other infrastructure capacity to the end users and the service fee based on
1 3.1 IaaS Definition IaaS: Infrastructure as a Service Through the internet, provide IT server, storage, computing power and other infrastructure capacity to the end users and the service fee based on
System Virtual Machines
 System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
Securely Isolating Malicious OS Kernel Modules Using Hardware Virtualization Support
 Journal of Computational Information Systems 9: 13 (2013) 5403 5410 Available at http://www.jofcis.com Securely Isolating Malicious OS Kernel Modules Using Hardware Virtualization Support Zhixian CHEN
Journal of Computational Information Systems 9: 13 (2013) 5403 5410 Available at http://www.jofcis.com Securely Isolating Malicious OS Kernel Modules Using Hardware Virtualization Support Zhixian CHEN
Server and Storage Virtualization. Virtualization. Overview. 5 Reasons to Virtualize
 Server and Storage Virtualization. Overview Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu These slides and audio/video recordings of this class lecture are at:
Server and Storage Virtualization. Overview Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu These slides and audio/video recordings of this class lecture are at:
International Journal of Computer & Organization Trends Volume20 Number1 May 2015
 Performance Analysis of Various Guest Operating Systems on Ubuntu 14.04 Prof. (Dr.) Viabhakar Pathak 1, Pramod Kumar Ram 2 1 Computer Science and Engineering, Arya College of Engineering, Jaipur, India.
Performance Analysis of Various Guest Operating Systems on Ubuntu 14.04 Prof. (Dr.) Viabhakar Pathak 1, Pramod Kumar Ram 2 1 Computer Science and Engineering, Arya College of Engineering, Jaipur, India.
Solution Guide Parallels Virtualization for Linux
 Solution Guide Parallels Virtualization for Linux Overview Created in 1991, Linux was designed to be UNIX-compatible software that was composed entirely of open source or free software components. Linux
Solution Guide Parallels Virtualization for Linux Overview Created in 1991, Linux was designed to be UNIX-compatible software that was composed entirely of open source or free software components. Linux
KVM: A Hypervisor for All Seasons. Avi Kivity avi@qumranet.com
 KVM: A Hypervisor for All Seasons Avi Kivity avi@qumranet.com November 2007 Virtualization Simulation of computer system in software Components Processor: register state, instructions, exceptions Memory
KVM: A Hypervisor for All Seasons Avi Kivity avi@qumranet.com November 2007 Virtualization Simulation of computer system in software Components Processor: register state, instructions, exceptions Memory
StACC: St Andrews Cloud Computing Co laboratory. A Performance Comparison of Clouds. Amazon EC2 and Ubuntu Enterprise Cloud
 StACC: St Andrews Cloud Computing Co laboratory A Performance Comparison of Clouds Amazon EC2 and Ubuntu Enterprise Cloud Jonathan S Ward StACC (pronounced like 'stack') is a research collaboration launched
StACC: St Andrews Cloud Computing Co laboratory A Performance Comparison of Clouds Amazon EC2 and Ubuntu Enterprise Cloud Jonathan S Ward StACC (pronounced like 'stack') is a research collaboration launched
Management of VMware ESXi. on HP ProLiant Servers
 Management of VMware ESXi on W H I T E P A P E R Table of Contents Introduction................................................................ 3 HP Systems Insight Manager.................................................
Management of VMware ESXi on W H I T E P A P E R Table of Contents Introduction................................................................ 3 HP Systems Insight Manager.................................................
Compromise-as-a-Service
 ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg 3/31/14 Compromise-as-a-Service Our PleAZURE Felix Wilhelm & Matthias Luft {fwilhelm, mluft}@ernw.de ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg Agenda
ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg 3/31/14 Compromise-as-a-Service Our PleAZURE Felix Wilhelm & Matthias Luft {fwilhelm, mluft}@ernw.de ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg Agenda
Distributed System Monitoring and Failure Diagnosis using Cooperative Virtual Backdoors
 Distributed System Monitoring and Failure Diagnosis using Cooperative Virtual Backdoors Benoit Boissinot E.N.S Lyon directed by Christine Morin IRISA/INRIA Rennes Liviu Iftode Rutgers University Phenix
Distributed System Monitoring and Failure Diagnosis using Cooperative Virtual Backdoors Benoit Boissinot E.N.S Lyon directed by Christine Morin IRISA/INRIA Rennes Liviu Iftode Rutgers University Phenix
Security Management of Cloud-Native Applications. Presented By: Rohit Sharma MSc in Dependable Software Systems (DESEM)
 Security Management of Cloud-Native Applications Presented By: Rohit Sharma MSc in Dependable Software Systems (DESEM) 1 Outline Context State-of-the-Art Design Patterns Threats to cloud systems Security
Security Management of Cloud-Native Applications Presented By: Rohit Sharma MSc in Dependable Software Systems (DESEM) 1 Outline Context State-of-the-Art Design Patterns Threats to cloud systems Security
Last Class: OS and Computer Architecture. Last Class: OS and Computer Architecture
 Last Class: OS and Computer Architecture System bus Network card CPU, memory, I/O devices, network card, system bus Lecture 3, page 1 Last Class: OS and Computer Architecture OS Service Protection Interrupts
Last Class: OS and Computer Architecture System bus Network card CPU, memory, I/O devices, network card, system bus Lecture 3, page 1 Last Class: OS and Computer Architecture OS Service Protection Interrupts
HRG Assessment: Stratus everrun Enterprise
 HRG Assessment: Stratus everrun Enterprise Today IT executive decision makers and their technology recommenders are faced with escalating demands for more effective technology based solutions while at
HRG Assessment: Stratus everrun Enterprise Today IT executive decision makers and their technology recommenders are faced with escalating demands for more effective technology based solutions while at
Distributed and Cloud Computing
 Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Hypervisors. Introduction. Introduction. Introduction. Introduction. Introduction. Credits:
 Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
In-Guest Monitoring With Microsoft System Center
 In-Guest Monitoring With Microsoft System Center 2 Introduction to In-Guest Monitoring As organizations incorporate virtualization into their IT infrastructures, they have access to new capabilities that
In-Guest Monitoring With Microsoft System Center 2 Introduction to In-Guest Monitoring As organizations incorporate virtualization into their IT infrastructures, they have access to new capabilities that
RCL: Design and Open Specification
 ICT FP7-609828 RCL: Design and Open Specification D3.1.1 March 2014 _D3.1.1_RCLDesignAndOpenSpecification_v1.0 Document Information Scheduled delivery Actual delivery Version Responsible Partner 31.03.2014
ICT FP7-609828 RCL: Design and Open Specification D3.1.1 March 2014 _D3.1.1_RCLDesignAndOpenSpecification_v1.0 Document Information Scheduled delivery Actual delivery Version Responsible Partner 31.03.2014
Secure Cloud Computing: The Monitoring Perspective
 Secure Cloud Computing: The Monitoring Perspective Peng Liu Penn State University 1 Cloud Computing is Less about Computer Design More about Use of Computing (UoC) CPU, OS, VMM, PL, Parallel computing
Secure Cloud Computing: The Monitoring Perspective Peng Liu Penn State University 1 Cloud Computing is Less about Computer Design More about Use of Computing (UoC) CPU, OS, VMM, PL, Parallel computing
Tom Eastep Linuxfest NW April 26-27, 2008 Bellingham, Washington
 Tom Eastep Linuxfest NW April 26-27, 2008 Bellingham, Washington 1. Introduction to Virtualization Techniques 2. Pros and Cons 3. Where does KVM fit in 4. QEMU-kvm 5. Creating a virtual disk 6. Installing
Tom Eastep Linuxfest NW April 26-27, 2008 Bellingham, Washington 1. Introduction to Virtualization Techniques 2. Pros and Cons 3. Where does KVM fit in 4. QEMU-kvm 5. Creating a virtual disk 6. Installing
Exploiting the x86 Architecture to Derive Virtual Machine State Information
 2010 Fourth International Conference on Emerging Security Information, Systems and Technologies Exploiting the x86 Architecture to Derive Virtual Machine State Information Jonas Pfoh, Christian Schneider,
2010 Fourth International Conference on Emerging Security Information, Systems and Technologies Exploiting the x86 Architecture to Derive Virtual Machine State Information Jonas Pfoh, Christian Schneider,
