Internet Routing Registry (IRR) APNIC Tutorial in APNIC35 February 27, 2013, Singapore.
|
|
|
- Lynne Crawford
- 7 years ago
- Views:
Transcription
1 Internet Routing Registry (IRR) APNIC Tutorial in APNIC35 February 27, 2013, Singapore.
2 Introduction Presenter Nurul Islam Roman Senior Training Specialist Specialties: Routing & Switching MPLS, IPv6 DNS/DNSSEC Internet Resource Management Network Security
3 What is a Routing Registry? A repository (database) of Internet routing policy information Autonomous Systems exchanges routing information via BGP Exterior routing decisions are based on policy based rules However BGP does not provides a mechanism to publish/ communicate the policies themselves RR provides this functionality Routing policy information is expressed in a series of objects
4 What is a Routing Registry? Global Internet Routing Registry database Uses RPSL Stability and consistency of routing network operators share information Both public and private databases These databases are independent but some exchange data only register your data in one database
5 What is a Routing Registry? RIPE ARIN, ArcStar, FGC, Verio, Bconnex, Optus, Telstra,... RADB CW APNIC Connect IRR = APNIC RR + RIPE DB + RADB + C&W + ARIN +
6 Routing Registry Objects Route, aut-num, inet-rtr, peering-set, AS-set, rtr-set, filterset Each object has its own purpose Together express routing policies More details covered later
7 What is Routing Policy? Description of the routing relationship between autonomous systems Who are my BGP peers? Customer, peers, upstream What routes are: Originated by each neighbour? Imported from each neighbour? Exported to each neighbour? Preferred when multiple routes exist? What to do if no route exists? What routes to aggregate?
8 Representation of Routing Policy AS1 AS2 NET1 NET2 In order for traffic to flow from NET2 to NET1 between AS1 and AS2: AS1 has to announce NET1 to AS2 via BGP And AS2 has to accept this information and use it Resulting in packet flow from NET2 to NET1
9 Representation of Routing Policy (cont.) AS1 AS2 NET1 NET2 In order for traffic to flow towards from NET1 to NET2: AS2 must announce NET2 to AS1 And AS1 has to accept this information and use it Resulting in packet flow from NET 1 to NET2
10 RPSL Routing Policy Specification Language Object oriented language Based on RIPE-181 Structured whois objects Higher level of abstraction than access lists Describes things interesting to routing policy: Routes, AS Numbers Relationships between BGP peers Management responsibility Relevant RFCs Routing Policy Specification Language Routing Policy System Security Using RPSL in Practice RFC 2622 RFC 2725 RFC 2650
11 Routing Policy - Examples Basic concept AS 1 AS 2 action pref - the lower the value, the preferred the route aut-num: AS1 import: from AS2 action pref= 100; accept AS2 export: to AS2 announce AS1 aut-num: AS2 import: from AS1 action pref=100; accept AS1 export: to AS1 announce AS2
12 Routing Policy - Examples AS 123 AS4 AS5 AS5 More complex example AS10 AS4 gives transit to AS5, AS10 AS4 gives local routes to AS123
13 Routing Policy - Examples AS 123 AS4 AS5 AS5 aut-num: AS4 import: from AS123 action pref=100; accept AS123 import: from AS5 action pref=100; accept AS5 import: from AS10 action pref=100; accept AS10 export: to AS123 announce AS4 export: to AS5 announce AS4 AS10 export: to AS10 announce AS4 AS5 Not a path AS10
14 Routing Policy - Examples AS123 transit traffic over link2 AS4 AS6 link3 private link1 More complex example AS4 and AS6 private link1 AS4 and AS123 main transit link2 backup all traffic over link1 and link3 in event of link2 failure
15 Routing Policy - Examples AS123 transit traffic over link2 AS4 AS representation AS6 link3 private link1 aut-num: AS4 import: from AS123 action pref=100; accept ANY full routing received import: from AS6 action pref=50; accept AS6 import: from AS6 action pref=200; accept ANY export: to AS6 announce AS4 export: to AS123 announce AS4 higher cost for backup route
16 APNIC Database and the IRR
17 APNIC Database & the IRR APNIC whois Database Two databases in one Public Network Management Database whois info about networks & contact persons IP addresses, AS numbers etc Routing Registry contains routing information routing policy, routes, filters, peers etc. APNIC RR is part of the global IRR
18 Integration of Whois and IRR Integrated APNIC Whois Database & Internet Routing Registry IP, ASNs, reverse domains, contacts, maintainers etc inetnum, aut-num, domain, person, role, maintainer APNIC Whois IRR Internet resources & routing information routes, routing policy, filters, peers etc route, aut-num, as-set, inet-rtr, peering-set etc.
19 IRR Objects route Specifies interas routes aut-num Represents an AS. Used to describe external routing policy inet-rtr Represents a router peering-set Defines a set of peerings route-set Defines a set of routes as-set Defines a set of aut-num objects rtr-set Defines a set of routers filter-set Defines a set of routes that are matched by its filter
20 Using the Routing Registry
21 IRRToolSet Set of tools developed for using the Internet Routing Registry (IRR) Work with Internet routing policies These policies are stored in IRR in the Routing Policy Specification Language (RPSL) The goal of the IRRToolSet is to make routing information more convenient and useful for network engineers Tools for automated router configuration, Routing policy analysis On-going maintenance etc.
22 IRRToolSet Now maintained by ISC: Download: ftp://ftp.isc.org/isc/irrtoolset/ Installation needs: lex, yacc and C++ compiler
23 Use of RPSL - RtConfig RtConfig v4 part of IRRToolSet Reads policy from IRR (aut-num, route & -set objects) and generates router configuration vendor specific: Cisco, Bay's BCC, Juniper's Junos and Gated/RSd Creates route-map and AS path filters Can also create ingress / egress filters (documentation says Cisco only)
24 Why use IRR and RtConfig? Benefits of RtConfig Avoid filter errors (typos) Expertise encoded in the tools that generate the policy rather than engineer configuring peering session Filters consistent with documented policy (need to get policy correct though)
25 Using RPSL in practice
26 Common Peering Policies Internet AS AS45192 private peer upstream private peer AS17821 downstream AS45192 is your upstream provider AS is a private peer Your AS is AS17821
27 How to write this in Aut-num aut-num: AS17821 remarks: AS45192 is your upstream provider import: from AS45192 action pref=100; accept ANY export: to AS45192 announce AS17821 remarks: AS is a private peer import: from AS action pref=20; accept AS export: to AS announce AS17821
28 Common Peering Policies Internet AS AS45192 upstream low upstream high downstream AS17821 downstream AS45192 is your preferred upstream provider AS is your backup upstream provider Your AS is AS17821
29 How to write this in Aut-num aut-num: AS17821 remarks: AS45192 is your preferred upstream provider import: from AS45192 action pref=100; accept ANY export: to AS45192 announce AS17821 remarks: AS is your backup upstream provider import: from AS action pref=200; accept ANY export: to AS action aspath.prepend (AS17821, AS17821); announce AS17821 remarks: Optional extra import line to prefer direct remarks: connection to AS from AS17821 import: from AS action pref=20; accept AS131107
30 Common Peering Policies Internet AS AS45192 upstream upstream downstream AS17821 downstream AS45192 is your upstream provider AS is your upstream provider Your AS is AS17821
31 How to write this in Aut-num aut-num: AS17821 remarks: AS45192 is your upstream provider import: from AS45192 action pref=100; accept ANY export: to AS45192 announce AS17821 remarks: AS is your upstream provider import: from AS action pref=100; accept ANY export: to AS announce AS remarks: the pref is optional here
32 Common Peering Policies Internet AS AS45192 transit upstream transit AS17821 downstream AS45192 is your upstream provider AS gives you transit AND you give AS transit as well Your AS is AS17821
33 How to write this in Aut-num aut-num: AS17821 remarks: AS45192 is your upstream provider import: from AS45192 action pref=100; accept ANY export: to AS45192 announce AS17821 remarks: AS is your transit provider import: from AS action pref=100; accept ANY export: to AS announce ANY remarks: the pref is optional here
34 Common Peering Policies Internet ISP (Transit provider) Customer AS 1 AS 2 AS 3 AS 4 AS 5 Peering policies of an AS Registered in an aut-num object
35 Common Peering Policies Policy for AS3 in the AS2 aut-num object aut-num: as-name: dsescr: import: import: export: export: admin-c: tech-c: mtn-by: changed: AS2 SAMPLE-NET Sample AS from AS1 accept ANY from AS3 accept <^AS3+$> to AS3 announce ANY to AS1 announce AS2 AS3 CW89-AP CW89-AP MAINT-SAMPLE-AP
36 Filter List- Regular Expression Like Unix regular expressions. Match one character * Match any number of preceding expression + Match at least one of preceding expression ^ Beginning of line $ End of line \ Escape a regular expression character _ Beginning, end, white-space, brace Or () Brackets to contain expression [] Brackets to contain number ranges
37 ISP Customer Transit Provider Policies Policy for AS3 and AS4 in the AS2 aut-num object aut-num: import: import: import: export: export: export: AS2 from AS1 accept ANY from AS3 accept <^AS3+$> from AS4 accept <^AS4+$> to AS3 announce ANY to AS4 announce ANY to AS1 announce AS2 AS3 AS4
38 AS-set Object Describe the customers of AS2 as-set: members: changed: source: AS2:AS-CUSTOMERS AS3 AS4 APNIC
39 New Initiative RIRs have been developing a new service for their members APNIC has now launched Resource Certification for the AP region Improves the security of inter-domain routing and augmenting the information published in the APNIC Whois Database 39
40 Terminology Resource holders include: Regional Internet Registries (RIRs) Local Internet Registries (LIRs) Internet Service Providers (ISPs) End-user organizations Internet resources are: IPv4 and IPv6 address blocks Autonomous System (AS) numbers 40
41 Resource Certification Benefits Routing information corresponds to properly delegated address resources Resource Certification gives resource holders proof that they hold certain resources Resource holders can attest to those resources when distributing them 41
42 Benefits (Cont.) Resource users can 'sign' information with a digital signature, which essentially 'freezes' that information Any effort to alter that information results in the signature being invalidated Only resource holders with a properly delegated 'right of use' can generate a signature 42
43 Benefits (cont.) Routing advertisements are made with the explicit agreement of the current 'right of use' holder of the addresses being advertised. 43
44 What is RPKI? Designed to secure the Internet's routing infrastructure Only the legitimate holder can advertise their prefix to the Internet Prevent those incidence of route hijacking (sometime by mistake)
45 How It Works? Initially each RIR issued a selfsigned trust anchors to the address they received from IANA Contains all resources from a single trust anchor managed by the RIR It was irrespective of their source
46 How It Works? RPKI Validation: Distributed Repository AFRINIC IANA APNIC LACNIC RIPE NCC ARIN Validation Tool (rcynic/bbn) BIG LIR validated cache
47 How It Works? RPKI Validation: RPKI-RTR protocol validated cache RPKI RTR PROTOCOL BGP Decision Process router bgp bgp log-neighbor-changes bgp rpki server tcp port refresh 60 How does it look in BGP table then?
48 BGP Table RPKI Validation: RPKI-RTR protocol router1#sh bgp ipv4 unicast BGP table version is 45, local router ID is Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale, m multipath, b backup-path, x best-external, f RT-Filter, a additional-path Origin codes: i - IGP, e - EGP,? - incomplete RPKI validation codes: V valid, I invalid, N Not found Network Next Hop Metric LocPrf Weight Path V i *> N / e *> V / i *> I / i *> V / i *> N / i *> N / i Use route-map to accept RPKI validated route route-map validity-0 match rpki-unknown set metric 50 route-map validity-1 match rpki-invalid set metric 25 route-map validity-2 set metric 100 route-map validity-0 match rpki-invalid drop route-map validity-1 match rpki-not-found set localpref 50 // Valid defaults to 100
49 What Is The New Challenge? Inter RIR transfer process is implemented now It requires an efficient way to reflect the changes to an RIR s resource holding Without revoking and reissuing the affected RIR trust anchor The split anchor model allows more granular updates, affecting only the certification path that covers the transferred resources
50 New Split Anchor Model APNIC has published five new self-signed certificates One for those address space given by IANA for this region Four for other self-signed certificates for resource acquired from each other RIR
51 What Changes For Operational Network? Organizations that RPKI origin validation on their router software need to make updates to their routing configuration If you already have the APNIC trust anchor you should refresh this with the complete new set of five Take note of any required configuration changes in your software
52 Find More.. APNIC to Upgrade to Split Trust Anchor RPKI: Resource Public Key Infrastructure (RPKI) FAQ: rpki/ Resource certification
53 Current Stage of ResCert Origin validation code is engineering now, could deploy in next few years but requires production RPKI Path validation is still research Filter validation is still research 53
54 MyAPNIC Home Page
55 Resources Management
56 Activate Certification
57 Service Activated
58 Create Route Origin Authorization
59 Name ROA
60 Add Resources
61 Add Resources
62 Add AS
63 Advanced Management
64 Route Origin Authorization (ROA)
65 ROA Collection Management
66 Add ROA Collection
67 Add ROA Collection
68 Add ROA Collection
69 Add/Remove Resources
70 View & Update Collections
71 Download Certificate
72 Download Certificate
73 Questions?
74 Thank you! J
BGP Attributes and Path Selection
 BGP Attributes and Path Selection ISP Workshops Last updated 29 th March 2015 1 BGP Attributes BGP s policy tool kit 2 What Is an Attribute?... Next Hop AS Path MED...... p Part of a BGP Update p Describes
BGP Attributes and Path Selection ISP Workshops Last updated 29 th March 2015 1 BGP Attributes BGP s policy tool kit 2 What Is an Attribute?... Next Hop AS Path MED...... p Part of a BGP Update p Describes
APNIC elearning: BGP Attributes
 APNIC elearning: BGP Attributes Contact: training@apnic.net erou04_v1.0 Overview BGP Attributes Well-known and Optional Attributes AS Path AS Loop Detection ibgp and ebgp Next Hop Next Hop Best Practice
APNIC elearning: BGP Attributes Contact: training@apnic.net erou04_v1.0 Overview BGP Attributes Well-known and Optional Attributes AS Path AS Loop Detection ibgp and ebgp Next Hop Next Hop Best Practice
Enabling Operational Use of RPKI via Internet Routing Registries
 CYBER SECURITY DIVISION 2013 PRINCIPAL INVESTIGATORS Enabling Operational Use of RPKI via Internet Routing Registries Merit Network, Inc. Dr. Joe Adams 17 September 2013 Agenda Introduction Technical Approach
CYBER SECURITY DIVISION 2013 PRINCIPAL INVESTIGATORS Enabling Operational Use of RPKI via Internet Routing Registries Merit Network, Inc. Dr. Joe Adams 17 September 2013 Agenda Introduction Technical Approach
RPKI Tutorial. Certification. Goals. Current Practices in Filtering
 RPKI Tutorial MENOG 10, Dubai UAE Marco Hogewoning Trainer Goals Explain where it started Learn what resources certificates are Learn how to request a certificate Learn how to create a Route Origin Authorization
RPKI Tutorial MENOG 10, Dubai UAE Marco Hogewoning Trainer Goals Explain where it started Learn what resources certificates are Learn how to request a certificate Learn how to create a Route Origin Authorization
Resource Certification. Alex Band Product Manager
 Resource Certification Alex Band Product Manager The RIPE NCC involvement in RPKI The authority on who is the registered holder of an Internet Number Resource in our region IPv4 and IPv6 Address Blocks
Resource Certification Alex Band Product Manager The RIPE NCC involvement in RPKI The authority on who is the registered holder of an Internet Number Resource in our region IPv4 and IPv6 Address Blocks
APNIC elearning: BGP Basics. Contact: training@apnic.net. erou03_v1.0
 erou03_v1.0 APNIC elearning: BGP Basics Contact: training@apnic.net Overview What is BGP? BGP Features Path Vector Routing Protocol Peering and Transit BGP General Operation BGP Terminology BGP Attributes
erou03_v1.0 APNIC elearning: BGP Basics Contact: training@apnic.net Overview What is BGP? BGP Features Path Vector Routing Protocol Peering and Transit BGP General Operation BGP Terminology BGP Attributes
Introduction to RPSL. TorIX Meeting, September 2004 Joe Abley, jabley@isc.org
 Introduction to RPSL TorIX Meeting, September 2004 Joe Abley, jabley@isc.org Agenda Some handwaving about why any of this is actually useful Architectural overview Incredibly brief history lesson Brief
Introduction to RPSL TorIX Meeting, September 2004 Joe Abley, jabley@isc.org Agenda Some handwaving about why any of this is actually useful Architectural overview Incredibly brief history lesson Brief
BGP1 Multihoming and Traffic Engineering
 83950 Telecommunications Laboratory Course BGP1 BGP1 Multihoming and Traffic Engineering date & time student # name 1 2 bgp-tyo.tex,v 1.11 2005/04/18 14:09:14 ams Exp 1/17 Part I Home Assignment 1 General
83950 Telecommunications Laboratory Course BGP1 BGP1 Multihoming and Traffic Engineering date & time student # name 1 2 bgp-tyo.tex,v 1.11 2005/04/18 14:09:14 ams Exp 1/17 Part I Home Assignment 1 General
RIPE Whois Database Query Reference Manual
 RIPE Whois Database Query Reference Manual João Luis Silva Damas Andrei Robachevsky Denis Walker Document ID: ripe-358 Date: October 2005 Partly Obsoletes: ripe-252 Abstract This document describes how
RIPE Whois Database Query Reference Manual João Luis Silva Damas Andrei Robachevsky Denis Walker Document ID: ripe-358 Date: October 2005 Partly Obsoletes: ripe-252 Abstract This document describes how
Routing Security Training Course
 Routing Security Training Course Exercise Booklet November 2015 Introduction Your database objects For your convenience we have already created some objects in the RIPE TEST Database. You can use these
Routing Security Training Course Exercise Booklet November 2015 Introduction Your database objects For your convenience we have already created some objects in the RIPE TEST Database. You can use these
A PKI For IDR Public Key Infrastructure and Number Resource Certification
 A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
Understanding Route Aggregation in BGP
 Understanding Route Aggregation in BGP Document ID: 5441 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Aggregate Without the as set Argument Aggregate with
Understanding Route Aggregation in BGP Document ID: 5441 Contents Introduction Prerequisites Requirements Components Used Conventions Network Diagram Aggregate Without the as set Argument Aggregate with
BGP Operations and Security. Training Course
 BGP Operations and Security Training Course Training Services RIPE NCC April 2016 Schedule 09:00-09:30 11:00-11:15 13:00-14:00 15:30-15:45 17:30 Coffee, Tea Break Lunch Break End BGP Operations and Security
BGP Operations and Security Training Course Training Services RIPE NCC April 2016 Schedule 09:00-09:30 11:00-11:15 13:00-14:00 15:30-15:45 17:30 Coffee, Tea Break Lunch Break End BGP Operations and Security
APNIC Trial of Certification of IP Addresses and ASes
 APNIC Trial of Certification of IP Addresses and ASes RIPE 51 11 October 2005 Geoff Huston 1 Address and Routing Security What we have today is a relatively insecure system that is vulnerable to various
APNIC Trial of Certification of IP Addresses and ASes RIPE 51 11 October 2005 Geoff Huston 1 Address and Routing Security What we have today is a relatively insecure system that is vulnerable to various
BGP. 1. Internet Routing
 BGP 1. Internet Routing (C) Herbert Haas 2005/03/11 1 Internet Routing Interior Gateway Protocols (IGPs) not suitable for Inter-ISP routing Technical metrics only No policy features Inter-ISP routing is
BGP 1. Internet Routing (C) Herbert Haas 2005/03/11 1 Internet Routing Interior Gateway Protocols (IGPs) not suitable for Inter-ISP routing Technical metrics only No policy features Inter-ISP routing is
RIPE Network Coordination Centre RIPE NCC LIR Tutorial
 RIPE NCC LIR Tutorial Alex Band, RIPE NCC The Internet Registry (IR) system Getting resources RIPE Database 2 What is an LIR? Local Internet Registry - responsible for obtaining, distributing and registering
RIPE NCC LIR Tutorial Alex Band, RIPE NCC The Internet Registry (IR) system Getting resources RIPE Database 2 What is an LIR? Local Internet Registry - responsible for obtaining, distributing and registering
How To Import Ipv4 From Global To Global On Cisco Vrf.Net (Vf) On A Vf-Net (Virtual Private Network) On Ipv2 (Vfs) On An Ipv3 (Vv
 BGP Support for IP Prefix Import from Global Table into a VRF Table The BGP Support for IP Prefix Import from Global Table into a VRF Table feature introduces the capability to import IPv4 unicast prefixes
BGP Support for IP Prefix Import from Global Table into a VRF Table The BGP Support for IP Prefix Import from Global Table into a VRF Table feature introduces the capability to import IPv4 unicast prefixes
basic BGP in Huawei CLI
 basic BGP in Huawei CLI BGP stands for Border Gateway Protocol. It is widely used among Internet Service Providers to make core routing decisions on the Internet. The current BGP version is BGP-4 defined
basic BGP in Huawei CLI BGP stands for Border Gateway Protocol. It is widely used among Internet Service Providers to make core routing decisions on the Internet. The current BGP version is BGP-4 defined
Simple Multihoming. ISP/IXP Workshops
 Simple Multihoming ISP/IXP Workshops 1 Why Multihome? Redundancy One connection to internet means the network is dependent on: Local router (configuration, software, hardware) WAN media (physical failure,
Simple Multihoming ISP/IXP Workshops 1 Why Multihome? Redundancy One connection to internet means the network is dependent on: Local router (configuration, software, hardware) WAN media (physical failure,
BGP FORGOTTEN BUT USEFUL FEATURES. Piotr Wojciechowski (CCIE #25543)
 BGP FORGOTTEN BUT USEFUL FEATURES Piotr Wojciechowski (CCIE #25543) ABOUT ME Senior Network Engineer MSO at VeriFone Inc. Previously Network Solutions Architect at one of top polish IT integrators CCIE
BGP FORGOTTEN BUT USEFUL FEATURES Piotr Wojciechowski (CCIE #25543) ABOUT ME Senior Network Engineer MSO at VeriFone Inc. Previously Network Solutions Architect at one of top polish IT integrators CCIE
BGP Multihoming Techniques
 BGP Multihoming Techniques Philip Smith , Oakland 2001, Cisco Systems, Inc. All rights reserved. 1 Presentation Slides Available on NANOG Web site www.nanog.org/mtg-0110/smith.html Available
BGP Multihoming Techniques Philip Smith , Oakland 2001, Cisco Systems, Inc. All rights reserved. 1 Presentation Slides Available on NANOG Web site www.nanog.org/mtg-0110/smith.html Available
APNIC Internet Resource Management (IRM) Tutorial. Petaling Jaya, Malaysia 24 February 2014
 APNIC Internet Resource Management (IRM) Tutorial Petaling Jaya, Malaysia 24 February 2014 Presenter Sheryl Hermoso (Shane) Training Officer, APNIC Sheryl has had various roles as a Network and Systems
APNIC Internet Resource Management (IRM) Tutorial Petaling Jaya, Malaysia 24 February 2014 Presenter Sheryl Hermoso (Shane) Training Officer, APNIC Sheryl has had various roles as a Network and Systems
Internet Operations and the RIRs
 Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Fireware How To Dynamic Routing
 Fireware How To Dynamic Routing How do I configure my Firebox to use BGP? Introduction A routing protocol is the language a router speaks with other routers to share information about the status of network
Fireware How To Dynamic Routing How do I configure my Firebox to use BGP? Introduction A routing protocol is the language a router speaks with other routers to share information about the status of network
BGP Terminology, Concepts, and Operation. Chapter 6 2007 2010, Cisco Systems, Inc. All rights reserved. Cisco Public
 BGP Terminology, Concepts, and Operation 1 IGP versus EGP Interior gateway protocol (IGP) A routing protocol operating within an Autonomous System (AS). RIP, OSPF, and EIGRP are IGPs. Exterior gateway
BGP Terminology, Concepts, and Operation 1 IGP versus EGP Interior gateway protocol (IGP) A routing protocol operating within an Autonomous System (AS). RIP, OSPF, and EIGRP are IGPs. Exterior gateway
How To Get An Ipv6 Allocation On Ipv4 (Ipv4) From Ipv5) From The Ipvripe Ncc (Ip6) From A Ipvv6 Ipv2 (Ip4) To Ip
 What s hot at the RIPE NCC PLNOG6, March 2011 Sandra Brás Trainer, RIPE NCC sbras@ripe.net Hot topics - overview The registry system IPv4 depletion IPv6 policy update Independent resources 2 The five RIRs
What s hot at the RIPE NCC PLNOG6, March 2011 Sandra Brás Trainer, RIPE NCC sbras@ripe.net Hot topics - overview The registry system IPv4 depletion IPv6 policy update Independent resources 2 The five RIRs
BGP Multihoming Techniques
 BGP Multihoming Techniques Philip Smith PacNOG 2 Workshop Apia, Samoa 18-24 June 2006 PacNOG 2 Workshops 1 BGP Multihoming Techniques Why Multihome? Definition & Options Preparing the Network
BGP Multihoming Techniques Philip Smith PacNOG 2 Workshop Apia, Samoa 18-24 June 2006 PacNOG 2 Workshops 1 BGP Multihoming Techniques Why Multihome? Definition & Options Preparing the Network
BGP Multihoming Techniques
 BGP Multihoming Techniques Philip Smith , Seoul, South Korea August 2003 1 Presentation Slides Available on ftp://ftp-eng.cisco.com/pfs/seminars/ 2 Preliminaries Presentation has many configuration
BGP Multihoming Techniques Philip Smith , Seoul, South Korea August 2003 1 Presentation Slides Available on ftp://ftp-eng.cisco.com/pfs/seminars/ 2 Preliminaries Presentation has many configuration
Introduction to The Internet. ISP/IXP Workshops
 Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Introduction to The Internet ISP/IXP Workshops 1 Introduction to the Internet Topologies and Definitions IP Addressing Internet Hierarchy Gluing it all together 2 Topologies and Definitions What does all
Simple Multihoming. ISP Workshops. Last updated 30 th March 2015
 Simple Multihoming ISP Workshops Last updated 30 th March 2015 1 Why Multihome? p Redundancy n One connection to internet means the network is dependent on: p Local router (configuration, software, hardware)
Simple Multihoming ISP Workshops Last updated 30 th March 2015 1 Why Multihome? p Redundancy n One connection to internet means the network is dependent on: p Local router (configuration, software, hardware)
Application Note. Failover through BGP route health injection
 Application Note Document version: v1.2 Last update: 8th November 2013 Purpose This application note aims to describe how to build a high available platform using BGP routing protocol to choose the best
Application Note Document version: v1.2 Last update: 8th November 2013 Purpose This application note aims to describe how to build a high available platform using BGP routing protocol to choose the best
Introduction to Routing
 Introduction to Routing How traffic flows on the Internet Philip Smith pfs@cisco.com RIPE NCC Regional Meeting, Moscow, 16-18 18 June 2004 1 Abstract Presentation introduces some of the terminologies used,
Introduction to Routing How traffic flows on the Internet Philip Smith pfs@cisco.com RIPE NCC Regional Meeting, Moscow, 16-18 18 June 2004 1 Abstract Presentation introduces some of the terminologies used,
IPv6 and IPv4 Update from the RIPE NCC. Sandra Brás, Ferenc Csorba
 IPv6 and IPv4 Update from the RIPE NCC Sandra Brás, Ferenc Csorba RIPE NCC IPv6 Kongress - Frankfurt 22 May 2014 Schedule IPv6 Kongress 2 RIPE/RIPE NCC. Who are we? IPv4 exhaustion IPv4 transfers IPv6
IPv6 and IPv4 Update from the RIPE NCC Sandra Brás, Ferenc Csorba RIPE NCC IPv6 Kongress - Frankfurt 22 May 2014 Schedule IPv6 Kongress 2 RIPE/RIPE NCC. Who are we? IPv4 exhaustion IPv4 transfers IPv6
Dove siamo? Architecture of Dynamic Routing
 Dove siamo? Algoritmi di routing Protocolli di routing» Intra dominio (IGP)» Inter dominio (EGP) Le slides relative a questo argomenti sono tratte da Interdomain Routing and The Border Gateway Protocol
Dove siamo? Algoritmi di routing Protocolli di routing» Intra dominio (IGP)» Inter dominio (EGP) Le slides relative a questo argomenti sono tratte da Interdomain Routing and The Border Gateway Protocol
Using Resource Certificates Progress Report on the Trial of Resource Certification
 Using Resource Certificates Progress Report on the Trial of Resource Certification October 2006 Geoff Huston Chief Scientist APNIC From the PPML Mailing List 2006-3 ("Capturing Originations in Templates")
Using Resource Certificates Progress Report on the Trial of Resource Certification October 2006 Geoff Huston Chief Scientist APNIC From the PPML Mailing List 2006-3 ("Capturing Originations in Templates")
The ISP Column A monthly column on things Internet. Securing BGP with BGPsec. Introduction
 The ISP Column A monthly column on things Internet July 2011 Geoff Huston Randy Bush Securing BGP with BGPsec Introduction For many years the Internet's fundamental elements names and addresses were the
The ISP Column A monthly column on things Internet July 2011 Geoff Huston Randy Bush Securing BGP with BGPsec Introduction For many years the Internet's fundamental elements names and addresses were the
Inter-domain Routing. Outline. Border Gateway Protocol
 Inter-domain Routing Outline Border Gateway Protocol Internet Structure Original idea Backbone service provider Consumer ISP Large corporation Consumer ISP Small corporation Consumer ISP Consumer ISP Small
Inter-domain Routing Outline Border Gateway Protocol Internet Structure Original idea Backbone service provider Consumer ISP Large corporation Consumer ISP Small corporation Consumer ISP Consumer ISP Small
Introduction to The Internet
 Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
Introduction to The Internet ISP Workshops Last updated 5 September 2014 1 Introduction to the Internet p Topologies and Definitions p IP Addressing p Internet Hierarchy p Gluing it all together 2 Topologies
BGP Best Path Selection Algorithm
 BGP Best Path Selection Algorithm Document ID: 13753 Contents Introduction Prerequisites Requirements Components Used Conventions Why Routers Ignore Paths How the Best Path Algorithm Works Example: BGP
BGP Best Path Selection Algorithm Document ID: 13753 Contents Introduction Prerequisites Requirements Components Used Conventions Why Routers Ignore Paths How the Best Path Algorithm Works Example: BGP
DD2491 p1 2008. Inter-domain routing and BGP part I Olof Hagsand KTH/CSC
 DD2491 p1 2008 Inter-domain routing and BGP part I Olof Hagsand KTH/CSC Inter-domain routing The objective of inter-domain routing is to bind together all the thousands of independent IP networks that
DD2491 p1 2008 Inter-domain routing and BGP part I Olof Hagsand KTH/CSC Inter-domain routing The objective of inter-domain routing is to bind together all the thousands of independent IP networks that
BGP Multihoming Techniques. Philip Smith <philip@apnic.net> APRICOT 2013 Singapore 19 th February 1 st March 2013
 BGP Multihoming Techniques Philip Smith APRICOT 2013 Singapore 19 th February 1 st March 2013 Presentation Slides p Will be available on n http://thyme.apnic.net/ftp/seminars/ APRICOT2013-Multihoming.pdf
BGP Multihoming Techniques Philip Smith APRICOT 2013 Singapore 19 th February 1 st March 2013 Presentation Slides p Will be available on n http://thyme.apnic.net/ftp/seminars/ APRICOT2013-Multihoming.pdf
Detecting BGP hijacks in 2014
 Detecting BGP hijacks in 2014 Guillaume Valadon & Nicolas Vivet Agence nationale de la sécurité des systèmes d information http://www.ssi.gouv.fr/en NSC - November 21th, 2014 ANSSI - Detecting BGP hijacks
Detecting BGP hijacks in 2014 Guillaume Valadon & Nicolas Vivet Agence nationale de la sécurité des systèmes d information http://www.ssi.gouv.fr/en NSC - November 21th, 2014 ANSSI - Detecting BGP hijacks
IPv6 Addressing. ISP Training Workshops
 IPv6 Addressing ISP Training Workshops 1 Where to get IPv6 addresses p Your upstream ISP p Africa n AfriNIC http://www.afrinic.net p Asia and the Pacific n APNIC http://www.apnic.net p North America n
IPv6 Addressing ISP Training Workshops 1 Where to get IPv6 addresses p Your upstream ISP p Africa n AfriNIC http://www.afrinic.net p Asia and the Pacific n APNIC http://www.apnic.net p North America n
BGP Techniques for Internet Service Providers
 BGP Techniques for Internet Service Providers Philip Smith AfNOG 2011 Dar Es Salaam, Tanzania 5 June 2011 AfNOG 2011 1 Presentation Slides Will be available on ftp://ftp-eng.cisco.com /pfs/seminars/afnog2011-bgp-techniques.pdf
BGP Techniques for Internet Service Providers Philip Smith AfNOG 2011 Dar Es Salaam, Tanzania 5 June 2011 AfNOG 2011 1 Presentation Slides Will be available on ftp://ftp-eng.cisco.com /pfs/seminars/afnog2011-bgp-techniques.pdf
Address Scheme Planning for an ISP backbone Network
 Address Scheme Planning for an ISP backbone Network Philip Smith Consulting Engineering, Office of the CTO Version 0.1 (draft) LIST OF FIGURES 2 INTRODUCTION 3 BACKGROUND 3 BUSINESS MODEL 3 ADDRESS PLAN
Address Scheme Planning for an ISP backbone Network Philip Smith Consulting Engineering, Office of the CTO Version 0.1 (draft) LIST OF FIGURES 2 INTRODUCTION 3 BACKGROUND 3 BUSINESS MODEL 3 ADDRESS PLAN
Internet Structure and Organization
 Internet Structure and Organization Resources management and allocation Bernard.Tuy@renater.fr Introduction What s the Internet? Why organizations / bodies are needed? Define protocol specifications Agree
Internet Structure and Organization Resources management and allocation Bernard.Tuy@renater.fr Introduction What s the Internet? Why organizations / bodies are needed? Define protocol specifications Agree
BGP Basics. BGP Uses TCP 179 ibgp - BGP Peers in the same AS ebgp - BGP Peers in different AS's. 64512-65535 Private BGP ASN. BGP Router Processes
 BGP Basics BGPv4 - RFC 4271 - IPv6 support Path vector routing protocol EGP Routing between AS'es Classless Transit Area - Area used to reach other areas. Requires full routing table (no default routes).
BGP Basics BGPv4 - RFC 4271 - IPv6 support Path vector routing protocol EGP Routing between AS'es Classless Transit Area - Area used to reach other areas. Requires full routing table (no default routes).
DD2491 p1 2008. Load balancing BGP. Johan Nicklasson KTHNOC/NADA
 DD2491 p1 2008 Load balancing BGP Johan Nicklasson KTHNOC/NADA Dual home When do you need to be dual homed? How should you be dual homed? Same provider. Different providers. What do you need to have in
DD2491 p1 2008 Load balancing BGP Johan Nicklasson KTHNOC/NADA Dual home When do you need to be dual homed? How should you be dual homed? Same provider. Different providers. What do you need to have in
Exterior Gateway Protocols (BGP)
 Exterior Gateway Protocols (BGP) Internet Structure Large ISP Large ISP Stub Dial-Up ISP Small ISP Stub Stub Stub Autonomous Systems (AS) Internet is not a single network! The Internet is a collection
Exterior Gateway Protocols (BGP) Internet Structure Large ISP Large ISP Stub Dial-Up ISP Small ISP Stub Stub Stub Autonomous Systems (AS) Internet is not a single network! The Internet is a collection
IAB IPv6 Multi-Homing BOF. Jason Schiller Senior Internet Network Engineer IP Core Infrastructure Engineering UUNET / MCI
 IAB IPv6 Multi-Homing BOF Jason Schiller Senior Internet Network Engineer IP Core Infrastructure Engineering UUNET / MCI Multi-homing Problems Inbound to the destination traffic engineering is needed Current
IAB IPv6 Multi-Homing BOF Jason Schiller Senior Internet Network Engineer IP Core Infrastructure Engineering UUNET / MCI Multi-homing Problems Inbound to the destination traffic engineering is needed Current
BGP Multihoming Techniques
 BGP Multihoming Techniques Philip Smith NANOG 41 14th - 16th October 2007 Albuquerque, New Mexico 1 Presentation Slides Available on ftp://ftp-eng.cisco.com /pfs/seminars/nanog41-multihoming.pdf
BGP Multihoming Techniques Philip Smith NANOG 41 14th - 16th October 2007 Albuquerque, New Mexico 1 Presentation Slides Available on ftp://ftp-eng.cisco.com /pfs/seminars/nanog41-multihoming.pdf
IPv6 Address Planning
 eip604_v1.0 APNIC elearning: IPv6 Address Planning Contact: training@apnic.net Overview Where to Get IPv6 Addresses Addressing Plans ISP Infrastructure Addressing Plans Customer Example Address Plan Addressing
eip604_v1.0 APNIC elearning: IPv6 Address Planning Contact: training@apnic.net Overview Where to Get IPv6 Addresses Addressing Plans ISP Infrastructure Addressing Plans Customer Example Address Plan Addressing
BGP Routing. Course Description. Students Will Learn. Target Audience. Hands-On
 Hands-On Course Description This Hands-On course on (Border Gateway Protocol), from the basics of how it works through to advanced issues such as route reflectors, policy, filtering, route selection and
Hands-On Course Description This Hands-On course on (Border Gateway Protocol), from the basics of how it works through to advanced issues such as route reflectors, policy, filtering, route selection and
IPv6 and 4-byte ASN Update
 IPv6 and 4-byte ASN Update Philip Smith PacNOG 8 Pohnpei, FSM 22nd-27th November 2010 1 IPv6 Update 2 2004 Today Resurgence in demand for IPv4 address space 5% address space still unallocated
IPv6 and 4-byte ASN Update Philip Smith PacNOG 8 Pohnpei, FSM 22nd-27th November 2010 1 IPv6 Update 2 2004 Today Resurgence in demand for IPv4 address space 5% address space still unallocated
Measuring IPv6 Deployment. Geoff Huston APNIC December 2009
 Measuring IPv6 Deployment Geoff Huston APNIC December 2009 IPv4 address exhaustion Total Address Count Adver0sed Count IANA Pool Unadver0sed Count IPv4 address exhaustion The model of address consumption
Measuring IPv6 Deployment Geoff Huston APNIC December 2009 IPv4 address exhaustion Total Address Count Adver0sed Count IANA Pool Unadver0sed Count IPv4 address exhaustion The model of address consumption
What's inside the cloud?!
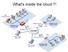 What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
Tutorial: Options for Blackhole and Discard Routing. Joseph M. Soricelli Wayne Gustavus NANOG 32, Reston, Virginia
 Tutorial: Options for Blackhole and Discard Routing Joseph M. Soricelli Wayne Gustavus NANOG 32, Reston, Virginia Caveats and Assumptions The views presented here are those of the authors and they do not
Tutorial: Options for Blackhole and Discard Routing Joseph M. Soricelli Wayne Gustavus NANOG 32, Reston, Virginia Caveats and Assumptions The views presented here are those of the authors and they do not
ISP Case Study. UUNET UK (1997) ISP/IXP Workshops. ISP/IXP Workshops. 1999, Cisco Systems, Inc.
 ISP Case Study UUNET UK (1997) ISP/IXP Workshops ISP/IXP Workshops 1999, Cisco Systems, Inc. 1 Acknowledgements Thanks are due to UUNET UK for allowing the use of their configuration information and network
ISP Case Study UUNET UK (1997) ISP/IXP Workshops ISP/IXP Workshops 1999, Cisco Systems, Inc. 1 Acknowledgements Thanks are due to UUNET UK for allowing the use of their configuration information and network
Claudio Jeker. RIPE 41 Meeting Amsterdam, 15. January 2002. oppermann@pipeline.ch. jeker@n-r-g.com. Using BGP topology information for DNS RR sorting
 BGPDNS Using BGP topology information for DNS RR sorting a scalable way of multi-homing André Oppermann oppermann@pipeline.ch Claudio Jeker jeker@n-r-g.com RIPE 41 Meeting Amsterdam, 15. January 2002 What
BGPDNS Using BGP topology information for DNS RR sorting a scalable way of multi-homing André Oppermann oppermann@pipeline.ch Claudio Jeker jeker@n-r-g.com RIPE 41 Meeting Amsterdam, 15. January 2002 What
Internet inter-as routing: BGP
 Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means to: 1. Obtain subnet reachability information from neighboring ASs. 2. Propagate the reachability
Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means to: 1. Obtain subnet reachability information from neighboring ASs. 2. Propagate the reachability
Border Gateway Protocol BGP4 (2)
 Border Gateway Protocol BGP4 (2) Professor Richard Harris School of Engineering and Advanced Technology (SEAT) Presentation Outline Border Gateway Protocol - Continued Computer Networks - 1/2 Learning
Border Gateway Protocol BGP4 (2) Professor Richard Harris School of Engineering and Advanced Technology (SEAT) Presentation Outline Border Gateway Protocol - Continued Computer Networks - 1/2 Learning
HP Networking BGP and MPLS technology training
 Course overview HP Networking BGP and MPLS technology training (HL046_00429577) The HP Networking BGP and MPLS technology training provides networking professionals the knowledge necessary for designing,
Course overview HP Networking BGP and MPLS technology training (HL046_00429577) The HP Networking BGP and MPLS technology training provides networking professionals the knowledge necessary for designing,
IPE Database Features
 RIPE Database Software Recent Changes Shane Kerr, RIPE NCC shane@ripe.net APNIC 18, September 2004 RIPE Database Software: Recent Changes Page 1 of 7 X.509 Support Added As part of the Improved Secure
RIPE Database Software Recent Changes Shane Kerr, RIPE NCC shane@ripe.net APNIC 18, September 2004 RIPE Database Software: Recent Changes Page 1 of 7 X.509 Support Added As part of the Improved Secure
BGP and Traffic Engineering with Akamai. Caglar Dabanoglu Akamai Technologies AfPIF 2015, Maputo, August 25th
 BGP and Traffic Engineering with Akamai Caglar Dabanoglu Akamai Technologies AfPIF 2015, Maputo, August 25th AGENDA Akamai Intelligent Platform Peering with Akamai Traffic Engineering Summary Q&A The Akamai
BGP and Traffic Engineering with Akamai Caglar Dabanoglu Akamai Technologies AfPIF 2015, Maputo, August 25th AGENDA Akamai Intelligent Platform Peering with Akamai Traffic Engineering Summary Q&A The Akamai
Internet Bodies. Bernard.Tuy@renater.fr
 Internet Bodies Bernard.Tuy@renater.fr Agenda Names, Acronyms in the Internet IETF organisation IESG, IAB, ISOC ICANN & IANA Standardisation process Standardisation compliance Internet Registries Requesting
Internet Bodies Bernard.Tuy@renater.fr Agenda Names, Acronyms in the Internet IETF organisation IESG, IAB, ISOC ICANN & IANA Standardisation process Standardisation compliance Internet Registries Requesting
BGP Multihoming Techniques
 BGP Multihoming Techniques Philip Smith SANOG 12 6th-14th August 2008 Kathmandu 1 Presentation Slides Available on ftp://ftp-eng.cisco.com /pfs/seminars/sanog12-multihoming.pdf And on the
BGP Multihoming Techniques Philip Smith SANOG 12 6th-14th August 2008 Kathmandu 1 Presentation Slides Available on ftp://ftp-eng.cisco.com /pfs/seminars/sanog12-multihoming.pdf And on the
APNIC elearning: Requesting IP Address
 APNIC elearning: Requesting IP Address 19 AUG 2015 01:00 PM AEST Brisbane (UTC+10) Issue Date: 07 July 2015 Revision: 2.0 Introduction Presenter Sheryl Hermoso Training Officer sheryl@apnic.net Specialties:
APNIC elearning: Requesting IP Address 19 AUG 2015 01:00 PM AEST Brisbane (UTC+10) Issue Date: 07 July 2015 Revision: 2.0 Introduction Presenter Sheryl Hermoso Training Officer sheryl@apnic.net Specialties:
How To Understand Bg
 Table of Contents BGP Case Studies...1 BGP4 Case Studies Section 1...3 Contents...3 Introduction...3 How Does BGP Work?...3 ebgp and ibgp...3 Enabling BGP Routing...4 Forming BGP Neighbors...4 BGP and
Table of Contents BGP Case Studies...1 BGP4 Case Studies Section 1...3 Contents...3 Introduction...3 How Does BGP Work?...3 ebgp and ibgp...3 Enabling BGP Routing...4 Forming BGP Neighbors...4 BGP and
BGP Multihoming Techniques
 BGP Multihoming Techniques Philip Smith 26th July - 4th August 2006 Karachi 1 Presentation Slides Available on ftp://ftp-eng.cisco.com /pfs/seminars/sanog8-multihoming.pdf And on the SANOG8
BGP Multihoming Techniques Philip Smith 26th July - 4th August 2006 Karachi 1 Presentation Slides Available on ftp://ftp-eng.cisco.com /pfs/seminars/sanog8-multihoming.pdf And on the SANOG8
Network Level Multihoming and BGP Challenges
 Network Level Multihoming and BGP Challenges Li Jia Helsinki University of Technology jili@cc.hut.fi Abstract Multihoming has been traditionally employed by enterprises and ISPs to improve network connectivity.
Network Level Multihoming and BGP Challenges Li Jia Helsinki University of Technology jili@cc.hut.fi Abstract Multihoming has been traditionally employed by enterprises and ISPs to improve network connectivity.
Routing in Small Networks. Internet Routing Overview. Agenda. Routing in Large Networks
 Routing in Small Networks Internet Routing Overview AS, IGP,, BGP in small networks distance vector or link state protocols like RIP or OSPF can be used for dynamic routing it is possible that every router
Routing in Small Networks Internet Routing Overview AS, IGP,, BGP in small networks distance vector or link state protocols like RIP or OSPF can be used for dynamic routing it is possible that every router
Components of Routing Table Growth
 Components of Routing Table Growth Harsha Narayan (U. of California, San Diego) Joint work with Ramesh Govindan (U. of Southern California) and George Varghese (U. of California, San Diego) 1 The Goal
Components of Routing Table Growth Harsha Narayan (U. of California, San Diego) Joint work with Ramesh Govindan (U. of Southern California) and George Varghese (U. of California, San Diego) 1 The Goal
MANTICORE: Providing Users with a Logical IP Network Service
 MANTICORE: Providing Users with a Logical IP Network Service Victor Reijs (HEAnet) MANTICORE Partners (self funded project): Agenda MANTICORE vision MANTICORE-I implementation Infrastructure as a Service
MANTICORE: Providing Users with a Logical IP Network Service Victor Reijs (HEAnet) MANTICORE Partners (self funded project): Agenda MANTICORE vision MANTICORE-I implementation Infrastructure as a Service
Chapter 49 Border Gateway Protocol version 4 (BGP-4)
 Chapter 49 Border Gateway Protocol version 4 (BGP-4) Introduction... 1-3 Overview of BGP-4... 1-3 BGP Operation... 1-5 BGP Attributes... 1-6 BGP Route Selection... 1-8 Classless Inter-domain Routing (CIDR)
Chapter 49 Border Gateway Protocol version 4 (BGP-4) Introduction... 1-3 Overview of BGP-4... 1-3 BGP Operation... 1-5 BGP Attributes... 1-6 BGP Route Selection... 1-8 Classless Inter-domain Routing (CIDR)
Topic 1: Internet Architecture & Addressing
 Topic 1: Internet Architecture & Addressing Objectives Understand the general architecture of Internet Identify the main actors in the Internet architecture Identify the main organizations implied in Internet
Topic 1: Internet Architecture & Addressing Objectives Understand the general architecture of Internet Identify the main actors in the Internet architecture Identify the main organizations implied in Internet
Firewall-on-Demand. GRNET s approach to advanced network security services management via bgp flow-spec and NETCONF. Leonidas Poulopoulos
 Firewall-on-Demand GRNET s approach to advanced network security services management via bgp flow-spec and NETCONF Leonidas Poulopoulos 1 leopoul@nocgrnetgr 1 NOC/Greek Research and Technology Network
Firewall-on-Demand GRNET s approach to advanced network security services management via bgp flow-spec and NETCONF Leonidas Poulopoulos 1 leopoul@nocgrnetgr 1 NOC/Greek Research and Technology Network
netkit lab bgp: multi-homed Università degli Studi Roma Tre Dipartimento di Informatica e Automazione Computer Networks Research Group
 Università degli Studi Roma Tre Dipartimento di Informatica e Automazione Computer Networks Research Group netkit lab bgp: multi-homed Version Author(s) E-mail Web Description 2.0 G. Di Battista, M. Patrignani,
Università degli Studi Roma Tre Dipartimento di Informatica e Automazione Computer Networks Research Group netkit lab bgp: multi-homed Version Author(s) E-mail Web Description 2.0 G. Di Battista, M. Patrignani,
s@lm@n Juniper Exam JN0-343 Juniper Networks Certified Internet Specialist (JNCIS-ENT) Version: 10.1 [ Total Questions: 498 ]
![s@lm@n Juniper Exam JN0-343 Juniper Networks Certified Internet Specialist (JNCIS-ENT) Version: 10.1 [ Total Questions: 498 ] s@lm@n Juniper Exam JN0-343 Juniper Networks Certified Internet Specialist (JNCIS-ENT) Version: 10.1 [ Total Questions: 498 ]](/thumbs/39/18985711.jpg) s@lm@n Juniper Exam JN0-343 Juniper Networks Certified Internet Specialist (JNCIS-ENT) Version: 10.1 [ Total Questions: 498 ] Topic 1, Volume A Question No : 1 - (Topic 1) How much overhead does the GRE
s@lm@n Juniper Exam JN0-343 Juniper Networks Certified Internet Specialist (JNCIS-ENT) Version: 10.1 [ Total Questions: 498 ] Topic 1, Volume A Question No : 1 - (Topic 1) How much overhead does the GRE
BGP Techniques for Internet Service Providers
 BGP Techniques for Internet Service Providers Philip Smith MENOG 2 19-21 November 2007 Doha, Qatar 1 Presentation Slides Will be available on ftp://ftp-eng.cisco.com /pfs/seminars/menog2-bgp-techniques.pdf
BGP Techniques for Internet Service Providers Philip Smith MENOG 2 19-21 November 2007 Doha, Qatar 1 Presentation Slides Will be available on ftp://ftp-eng.cisco.com /pfs/seminars/menog2-bgp-techniques.pdf
Multihoming and Multi-path Routing. CS 7260 Nick Feamster January 29. 2007
 Multihoming and Multi-path Routing CS 7260 Nick Feamster January 29. 2007 Today s Topic IP-Based Multihoming What is it? What problem is it solving? (Why multihome?) How is it implemented today (in IP)?
Multihoming and Multi-path Routing CS 7260 Nick Feamster January 29. 2007 Today s Topic IP-Based Multihoming What is it? What problem is it solving? (Why multihome?) How is it implemented today (in IP)?
OPPORTUNITIES AND CHALLENGES IN CYBERSECURITY
 ASIA-PACIFIC TELECOMMUNITY 5th APT CYBERSECURITY FORUM (CSF-5) 26-28 May 2014, Ulaanbaatar, Mongolia Document CSF-5/INP-13 19 May 2014 Mr. Adli Wahid, APNIC OPPORTUNITIES AND CHALLENGES IN CYBERSECURITY
ASIA-PACIFIC TELECOMMUNITY 5th APT CYBERSECURITY FORUM (CSF-5) 26-28 May 2014, Ulaanbaatar, Mongolia Document CSF-5/INP-13 19 May 2014 Mr. Adli Wahid, APNIC OPPORTUNITIES AND CHALLENGES IN CYBERSECURITY
Internet inter-as routing: BGP
 Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means to: 1. Obtain subnet reachability information from neighboring ASs. 2. Propagate the reachability
Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means to: 1. Obtain subnet reachability information from neighboring ASs. 2. Propagate the reachability
Collective responsibility for security and resilience of the global routing system
 Collective responsibility for security and resilience of the global routing system Andrei Robachevsky www.internetsociety.org Let us look at the problem first BGP is based on trust
Collective responsibility for security and resilience of the global routing system Andrei Robachevsky www.internetsociety.org Let us look at the problem first BGP is based on trust
Strategies to Protect Against Distributed Denial of Service (DDoS) Attacks
 Strategies to Protect Against Distributed Denial of Service (DDoS) Attacks Document ID: 13634 Contents Introduction Understanding the Basics of DDoS Attacks Characteristics of Common Programs Used to Facilitate
Strategies to Protect Against Distributed Denial of Service (DDoS) Attacks Document ID: 13634 Contents Introduction Understanding the Basics of DDoS Attacks Characteristics of Common Programs Used to Facilitate
Load balancing and traffic control in BGP
 DD2491 p2 2011 Load balancing and traffic control in BGP Olof Hagsand KTH CSC 1 Issues in load balancing Load balancing: spread traffic on several paths instead of a single. Why? Use resources better Can
DD2491 p2 2011 Load balancing and traffic control in BGP Olof Hagsand KTH CSC 1 Issues in load balancing Load balancing: spread traffic on several paths instead of a single. Why? Use resources better Can
Netflow Overview. PacNOG 6 Nadi, Fiji
 Netflow Overview PacNOG 6 Nadi, Fiji Agenda Netflow What it is and how it works Uses and Applications Vendor Configurations/ Implementation Cisco and Juniper Flow-tools Architectural issues Software, tools
Netflow Overview PacNOG 6 Nadi, Fiji Agenda Netflow What it is and how it works Uses and Applications Vendor Configurations/ Implementation Cisco and Juniper Flow-tools Architectural issues Software, tools
Internet Firewall CSIS 4222. Packet Filtering. Internet Firewall. Examples. Spring 2011 CSIS 4222. net15 1. Routers can implement packet filtering
 Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
Internet Firewall CSIS 4222 A combination of hardware and software that isolates an organization s internal network from the Internet at large Ch 27: Internet Routing Ch 30: Packet filtering & firewalls
Ref: A. Leon Garcia and I. Widjaja, Communication Networks, 2 nd Ed. McGraw Hill, 2006 Latest update of this lecture was on 16 10 2010
 IPv4 Addressing There are several non-profit organizations in the world that have the authority for assigning IP addresses to institutions that need access to the Internet. These organizations are (for
IPv4 Addressing There are several non-profit organizations in the world that have the authority for assigning IP addresses to institutions that need access to the Internet. These organizations are (for
Border Gateway Protocol (BGP)
 Border Gateway Protocol (BGP) Petr Grygárek rek 1 Role of Autonomous Systems on the Internet 2 Autonomous systems Not possible to maintain complete Internet topology information on all routers big database,
Border Gateway Protocol (BGP) Petr Grygárek rek 1 Role of Autonomous Systems on the Internet 2 Autonomous systems Not possible to maintain complete Internet topology information on all routers big database,
Community tools to fight against DDoS
 Community tools to fight against DDoS Fakrul Alam Senior Training Officer SANOG 27 & APNIC Regional Meeting, Kathmandu, Nepal 25 Jan - 01 Feb, 2016 Issue Date: Revision: 26-12-2015 1.3 DDoS Denial of Service
Community tools to fight against DDoS Fakrul Alam Senior Training Officer SANOG 27 & APNIC Regional Meeting, Kathmandu, Nepal 25 Jan - 01 Feb, 2016 Issue Date: Revision: 26-12-2015 1.3 DDoS Denial of Service
Internet Routing Protocols Lecture 04 BGP Continued
 Internet Routing Protocols Lecture 04 BGP Continued Advanced Systems Topics Lent Term, 008 Timothy G. Griffin Computer Lab Cambridge UK Two Types of BGP Sessions AS External Neighbor (EBGP) in a different
Internet Routing Protocols Lecture 04 BGP Continued Advanced Systems Topics Lent Term, 008 Timothy G. Griffin Computer Lab Cambridge UK Two Types of BGP Sessions AS External Neighbor (EBGP) in a different
BGP and Traffic Engineering with Akamai. Christian Kaufmann Akamai Technologies MENOG 14
 BGP and Traffic Engineering with Akamai Christian Kaufmann Akamai Technologies MENOG 14 The Akamai Intelligent Platform The world s largest on-demand, distributed computing platform delivers all forms
BGP and Traffic Engineering with Akamai Christian Kaufmann Akamai Technologies MENOG 14 The Akamai Intelligent Platform The world s largest on-demand, distributed computing platform delivers all forms
Transitioning to BGP. ISP Workshops. Last updated 24 April 2013
 Transitioning to BGP ISP Workshops Last updated 24 April 2013 1 Scaling the network How to get out of carrying all prefixes in IGP 2 Why use BGP rather than IGP? p IGP has Limitations: n The more routing
Transitioning to BGP ISP Workshops Last updated 24 April 2013 1 Scaling the network How to get out of carrying all prefixes in IGP 2 Why use BGP rather than IGP? p IGP has Limitations: n The more routing
Lecture 18: Border Gateway Protocol"
 Lecture 18: Border Gateway Protocol" CSE 123: Computer Networks Alex C. Snoeren HW 3 due Wednesday! Some figures courtesy Mike Freedman Lecture 18 Overview" Path-vector Routing Allows scalable, informed
Lecture 18: Border Gateway Protocol" CSE 123: Computer Networks Alex C. Snoeren HW 3 due Wednesday! Some figures courtesy Mike Freedman Lecture 18 Overview" Path-vector Routing Allows scalable, informed
Cisco IOS Flexible NetFlow Technology
 Cisco IOS Flexible NetFlow Technology Last Updated: December 2008 The Challenge: The ability to characterize IP traffic and understand the origin, the traffic destination, the time of day, the application
Cisco IOS Flexible NetFlow Technology Last Updated: December 2008 The Challenge: The ability to characterize IP traffic and understand the origin, the traffic destination, the time of day, the application
Multihomed BGP Configurations
 Multihomed BGP Configurations lvaro Retana Cisco IOS Deployment and Scalability 1 genda General Considerations Multihomed Networks Best Current Practices 2 The Basics General Considerations 3 General Considerations
Multihomed BGP Configurations lvaro Retana Cisco IOS Deployment and Scalability 1 genda General Considerations Multihomed Networks Best Current Practices 2 The Basics General Considerations 3 General Considerations
LIR Handbook. January 2012 RIPE NETWORK COORDINATION CENTRE
 LIR Handbook January 2012 RIPE NETWORK COORDINATION CENTRE 2 Most Important Definitions at a Glance I just want some IP addresses. What should I do?... p5 IPv4 Address Space Exhaustion...Preface... p12
LIR Handbook January 2012 RIPE NETWORK COORDINATION CENTRE 2 Most Important Definitions at a Glance I just want some IP addresses. What should I do?... p5 IPv4 Address Space Exhaustion...Preface... p12
BGP Techniques for Internet Service Providers
 BGP Techniques for Internet Service Providers Philip Smith NANOG 50 3-6 October 2010 Atlanta, GA 1 Presentation Slides Will be available on ftp://ftp-eng.cisco.com /pfs/seminars/nanog50-bgp-techniques.pdf
BGP Techniques for Internet Service Providers Philip Smith NANOG 50 3-6 October 2010 Atlanta, GA 1 Presentation Slides Will be available on ftp://ftp-eng.cisco.com /pfs/seminars/nanog50-bgp-techniques.pdf
BGP Multihoming Techniques. Philip Smith <philip@apnic.net> APRICOT 2012 21 st February 2 nd March 2012 New Delhi
 BGP Multihoming Techniques Philip Smith APRICOT 2012 21 st February 2 nd March 2012 New Delhi Presentation Slides p Available on n http://thyme.apnic.net/ftp/seminars/ APRICOT2012-BGP-Multihoming.pdf
BGP Multihoming Techniques Philip Smith APRICOT 2012 21 st February 2 nd March 2012 New Delhi Presentation Slides p Available on n http://thyme.apnic.net/ftp/seminars/ APRICOT2012-BGP-Multihoming.pdf
IPv6 over MPLS VPN. Contents. Prerequisites. Document ID: 112085. Requirements
 IPv6 over MPLS VPN Document ID: 112085 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram VRF Configuration Multiprotocol BGP (MP BGP) Configuration
IPv6 over MPLS VPN Document ID: 112085 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram VRF Configuration Multiprotocol BGP (MP BGP) Configuration
