Enabling Operational Use of RPKI via Internet Routing Registries
|
|
|
- Maurice Hunter
- 8 years ago
- Views:
Transcription
1 CYBER SECURITY DIVISION 2013 PRINCIPAL INVESTIGATORS Enabling Operational Use of RPKI via Internet Routing Registries Merit Network, Inc. Dr. Joe Adams 17 September 2013
2 Agenda Introduction Technical Approach Timeline & Deliverables Technology Transition Plan 2
3 Team Profile 3
4 Customer Need Advertised routes are currently held in Internet Routing Repositories (IRR). The Internet has had several incidents due to the lack of security in it's Border Gateway routing protocol (BGP) Large scale incidents include the AS7007 incident of 1997 and Pakistani Youtube hijack of 2008 Ongoing smaller scale incidents observed on a daily basis Resource Public Key Infrastructure (RPKI) is an initiative to make internet routing more secure through establishing trustworthy repositories of internet route advertisements. Applying trust to the IRR system is a natural fit to spread the adoption of RPKI to the broader Internet community. 4
5 Approach Existing Internet BGP Routing protocol lacks basic security We propose an incremental approach to improve and secure Internet routing configurations Rather than modifying protocols, we propose automating the generation of BGP filters which are supported by existing router capabilities 5
6 Technical Approach Extend the Routing Policy Specification Language to include RPKI attributes. Establish and operate a public RPKI validation cache. Modify registry software to allow searching on RPKI attributes. Augment existing tool sets to use the RPKI information being distributed via the IRRs. 66
7 Technical Approach The Internet Engineering Task Force has been working on improving Internet Routing Security through the Secure Inter-Domain Routing Working Group The working group has produced a base standard for securing routing called Resource Public Key Infrastructure (RPKI) Our approach is to modify existing databases (Internet Routing Registries) and tools to enable the use of this standard with existing toolsets employed by Internet Service Providers (ISPs). 7
8 Details Augment existing Routing Registry data with RPKI data to validate the information Update existing tools such as IRRToolSet to use this validation information when automating the generation of BGP filters Increase utilization of the tools by increasing the confidence in the information and also making the tools easier to use 8
9 Benefits The benefit of this approach is that it requires minimal modifications to existing tools It enables rapid deployment as it does not require the wholesale replacement of tools and potential hardware/firmware upgrades to routers It increases ISPs confidence as it does not require deployment of modifications which have seen limited testing in the real world 9
10 Benefits The IRR system and the Routing Assets Database (RADb) are used by the network operational community for routing policy specification and route configuration generation Allows for an easy to use mechanism to disseminate RPKI object information to large numbers of users via a familiar interface Integration of RPKI with default RADb configuration supports rapid adoption by the Internet community Creates production quality stable and supported validation cache as a community resource to support ongoing deployment and adoption of RPKI 10
11 Current Status 1 year funded effort for software development 4 deliverables: Extend RPSL for RPKI (mo 1-3) Create public validation cache (mo 4-6) Add RPKI searching to IRRD (mo 7-10) Augment IRR tool sets to use RPKI attributes (mo 11-12) 11
12 Next Steps RADb is already operational Establish a more trusted validation cache Move toward broader use of RPKI attributes Integrating RPKI attributes with commonly used tool sets 8/713 12
13 Contact Information Dr. Joe Adams Vice President of Research & Cyber Security Merit Network, Inc. (734) Larry Blunk Senior Research Engineer Merit Network, Inc. (734)
14 BAA Number CyberSecurity BAA Title: Enabling Operational Use of RPKI via Internet Routing Registries Offerer Name: Merit Network, Inc. Date: Other IRRs IRR System RADB RPKI Cache Validation Cache RIPE ARIN IRRD RPSL Attr: ROA-URI ROA-VALID APNIC RPKI Architecture Whois Query Interface Operational Community RADB Operational Capability Overall Performance Target: To enable the operational use of RPKI via Internet Routing Registries enhancing the security posture of the DHS and the Internet as a whole Benefits of RPKI Integration with the IRR System -The IRR system and RADB are used by the network operational community for routing policy specification and route configuration generation -Allows for an easy to use mechanism to disseminate RPKI object information to large numbers of users via a familiar interface -Integration of RPKI with default RADB configuration supports rapid adoption by the Internet community -Creates production quality stable and supported validation cache as a community resource to support ongoing deployment and adoption of RPKI Technical Approach Leverage the operational reach of the Routing Assets Database (RADB) to promote adoption of RPKI on a large scale -Develop RPSL extensions in the form of additional route attributes such as roa-valid or roa-uri that link the IRR with the RPKI architecture -Operate a production public RPKI validation cache as part of RADB -Develop and demonstrate RPKI support in IRR tools commonly used by the Internet community -Implement changes to IRRD software that forms the basis of the IRR system to implement support for RPKI validation lookups and responses to route queries Schedule, Costs, Deliverables, & Contact Info: Proposal Type: Type III Duration: 1 Oct Sep 2013 Deliverables & Schedule -Develop RPSL extensions for RPKI (mo 1-3) -Build/Operate Public Validation Cache (mo 4-6) -RPKI Support in RRD (mo 7-10) -Add RPKI Support to IRR Tools (mo 11 12) Technical POC Dr. Joe Adams 1000 Oakbrook Dr., Suite 200 Ann Arbor, MI (743) wjadams@merit.edu 14
BGP route monitoring. Mar, 25, 2008 Matsuzaki maz Yoshinobu <maz@telecom-isac.jp>, <maz@iij.ad.jp>
 BGP route monitoring Mar, 25, 2008 Matsuzaki maz Yoshinobu , 1 abstract BGP prefix hijack is a serious security issue in the internet, and these events have been widely
BGP route monitoring Mar, 25, 2008 Matsuzaki maz Yoshinobu , 1 abstract BGP prefix hijack is a serious security issue in the internet, and these events have been widely
Introduction to RPSL. TorIX Meeting, September 2004 Joe Abley, jabley@isc.org
 Introduction to RPSL TorIX Meeting, September 2004 Joe Abley, jabley@isc.org Agenda Some handwaving about why any of this is actually useful Architectural overview Incredibly brief history lesson Brief
Introduction to RPSL TorIX Meeting, September 2004 Joe Abley, jabley@isc.org Agenda Some handwaving about why any of this is actually useful Architectural overview Incredibly brief history lesson Brief
ARIN Online Users Forum
 ARIN Online Users Forum Overview Purpose and Players Brief overview of how ARIN sets priorities Usage statistics Review of the ARIN Online user survey Discussion of: ACSP suggestions on changes to ARIN
ARIN Online Users Forum Overview Purpose and Players Brief overview of how ARIN sets priorities Usage statistics Review of the ARIN Online user survey Discussion of: ACSP suggestions on changes to ARIN
BGP Routing. Course Description. Students Will Learn. Target Audience. Hands-On
 Hands-On Course Description This Hands-On course on (Border Gateway Protocol), from the basics of how it works through to advanced issues such as route reflectors, policy, filtering, route selection and
Hands-On Course Description This Hands-On course on (Border Gateway Protocol), from the basics of how it works through to advanced issues such as route reflectors, policy, filtering, route selection and
Resource Certification. Alex Band Product Manager
 Resource Certification Alex Band Product Manager The RIPE NCC involvement in RPKI The authority on who is the registered holder of an Internet Number Resource in our region IPv4 and IPv6 Address Blocks
Resource Certification Alex Band Product Manager The RIPE NCC involvement in RPKI The authority on who is the registered holder of an Internet Number Resource in our region IPv4 and IPv6 Address Blocks
Internet routing registries (IRRs), data governance and security
 Internet routing registries (IRRs), data governance and security Brenden Kuerbis and Milton Mueller School of Public Policy Georgia Institute of Technology, United States Introduction Supply and use of
Internet routing registries (IRRs), data governance and security Brenden Kuerbis and Milton Mueller School of Public Policy Georgia Institute of Technology, United States Introduction Supply and use of
OPPORTUNITIES AND CHALLENGES IN CYBERSECURITY
 ASIA-PACIFIC TELECOMMUNITY 5th APT CYBERSECURITY FORUM (CSF-5) 26-28 May 2014, Ulaanbaatar, Mongolia Document CSF-5/INP-13 19 May 2014 Mr. Adli Wahid, APNIC OPPORTUNITIES AND CHALLENGES IN CYBERSECURITY
ASIA-PACIFIC TELECOMMUNITY 5th APT CYBERSECURITY FORUM (CSF-5) 26-28 May 2014, Ulaanbaatar, Mongolia Document CSF-5/INP-13 19 May 2014 Mr. Adli Wahid, APNIC OPPORTUNITIES AND CHALLENGES IN CYBERSECURITY
Fireware How To Dynamic Routing
 Fireware How To Dynamic Routing How do I configure my Firebox to use BGP? Introduction A routing protocol is the language a router speaks with other routers to share information about the status of network
Fireware How To Dynamic Routing How do I configure my Firebox to use BGP? Introduction A routing protocol is the language a router speaks with other routers to share information about the status of network
Internet Operations and the RIRs
 Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Internet Operations and the RIRs Overview ARIN and the Regional Internet Registry (RIR) System IP Number Resources, DNS and Routing IP Address Management Whois ARIN and the RIR System About ARIN One of
Global Infrastructure Security and IPv6 Implications. Larry J. Blunk Fall 2004 Internet2 Member Meeting September 29, 2004
 Global Infrastructure Security and IPv6 Implications Larry J. Blunk Fall 2004 Internet2 Member Meeting September 29, 2004 1 Defining GlobGg infbasfrusrfee Internet Global Infrastructure consists of core
Global Infrastructure Security and IPv6 Implications Larry J. Blunk Fall 2004 Internet2 Member Meeting September 29, 2004 1 Defining GlobGg infbasfrusrfee Internet Global Infrastructure consists of core
Implementing IPv6 at ARIN Matt Ryanczak
 Implementing IPv6 at ARIN Matt Ryanczak ARIN began implementing IPv6 in 2003 and finished enabling most systems and services in 2008. Today all new networks and services are designed with IPv6 in mind.
Implementing IPv6 at ARIN Matt Ryanczak ARIN began implementing IPv6 in 2003 and finished enabling most systems and services in 2008. Today all new networks and services are designed with IPv6 in mind.
Description: Objective: Upon completing this course, the learner will be able to meet these overall objectives:
 Course: Building Cisco Service Provider Next-Generation Networks, Part 2 Duration: 5 Day Hands-On Lab & Lecture Course Price: $ 3,750.00 Learning Credits: 38 Description: The Building Cisco Service Provider
Course: Building Cisco Service Provider Next-Generation Networks, Part 2 Duration: 5 Day Hands-On Lab & Lecture Course Price: $ 3,750.00 Learning Credits: 38 Description: The Building Cisco Service Provider
Tools and Techniques for the Analysis of Large Scale BGP Datasets. Manish Karir, Larry Blunk (Merit) Dion Blazakis, John Baras (UMd)
 Tools and Techniques for the Analysis of Large Scale BGP Datasets Manish Karir, Larry Blunk (Merit) Dion Blazakis, John Baras (UMd) The Problem Large amounts of data are now, or soon will be available:
Tools and Techniques for the Analysis of Large Scale BGP Datasets Manish Karir, Larry Blunk (Merit) Dion Blazakis, John Baras (UMd) The Problem Large amounts of data are now, or soon will be available:
National Initiative for Cybersecurity Education
 THE NICE VISION National Initiative for Cybersecurity Education a national campaign to promote cybersecurity awareness and digital literacy from our boardrooms to our classrooms, and to build a digital
THE NICE VISION National Initiative for Cybersecurity Education a national campaign to promote cybersecurity awareness and digital literacy from our boardrooms to our classrooms, and to build a digital
ISP Case Study. UUNET UK (1997) ISP/IXP Workshops. ISP/IXP Workshops. 1999, Cisco Systems, Inc.
 ISP Case Study UUNET UK (1997) ISP/IXP Workshops ISP/IXP Workshops 1999, Cisco Systems, Inc. 1 Acknowledgements Thanks are due to UUNET UK for allowing the use of their configuration information and network
ISP Case Study UUNET UK (1997) ISP/IXP Workshops ISP/IXP Workshops 1999, Cisco Systems, Inc. 1 Acknowledgements Thanks are due to UUNET UK for allowing the use of their configuration information and network
BGP. 1. Internet Routing
 BGP 1. Internet Routing (C) Herbert Haas 2005/03/11 1 Internet Routing Interior Gateway Protocols (IGPs) not suitable for Inter-ISP routing Technical metrics only No policy features Inter-ISP routing is
BGP 1. Internet Routing (C) Herbert Haas 2005/03/11 1 Internet Routing Interior Gateway Protocols (IGPs) not suitable for Inter-ISP routing Technical metrics only No policy features Inter-ISP routing is
RPKI Tutorial. Certification. Goals. Current Practices in Filtering
 RPKI Tutorial MENOG 10, Dubai UAE Marco Hogewoning Trainer Goals Explain where it started Learn what resources certificates are Learn how to request a certificate Learn how to create a Route Origin Authorization
RPKI Tutorial MENOG 10, Dubai UAE Marco Hogewoning Trainer Goals Explain where it started Learn what resources certificates are Learn how to request a certificate Learn how to create a Route Origin Authorization
A Link Load Balancing Solution for Multi-Homed Networks
 A Link Load Balancing Solution for Multi-Homed Networks Overview An increasing number of enterprises are using the Internet for delivering mission-critical content and applications. By maintaining only
A Link Load Balancing Solution for Multi-Homed Networks Overview An increasing number of enterprises are using the Internet for delivering mission-critical content and applications. By maintaining only
BT Internet Connect Global - Annex to the General Service Schedule
 1. Definitions The following definitions apply, in addition to those in the General Terms and Conditions and the General Services Schedule. ARP means Address Resolution Protocol. Border Gateway Protocol
1. Definitions The following definitions apply, in addition to those in the General Terms and Conditions and the General Services Schedule. ARP means Address Resolution Protocol. Border Gateway Protocol
Inter-domain Routing. Outline. Border Gateway Protocol
 Inter-domain Routing Outline Border Gateway Protocol Internet Structure Original idea Backbone service provider Consumer ISP Large corporation Consumer ISP Small corporation Consumer ISP Consumer ISP Small
Inter-domain Routing Outline Border Gateway Protocol Internet Structure Original idea Backbone service provider Consumer ISP Large corporation Consumer ISP Small corporation Consumer ISP Consumer ISP Small
Global Network Mobility NANOG 31
 Ben Abarbanel cbbrouting@boeing.com Global Network Mobility NANOG 31 Implementing Global Network Mobility What is Connexion by Boeing? Summary of the problem Network and Service Challenges BGP as a mobility
Ben Abarbanel cbbrouting@boeing.com Global Network Mobility NANOG 31 Implementing Global Network Mobility What is Connexion by Boeing? Summary of the problem Network and Service Challenges BGP as a mobility
Cyber Security Defense Services Portfolio Development Status. February 2016
 Cyber Security Defense Services Portfolio Development Status February 2016 1 Agenda Merit s Six Strategic Thrusts Merit s current security offerings Member feedback Mission and vision statement for this
Cyber Security Defense Services Portfolio Development Status February 2016 1 Agenda Merit s Six Strategic Thrusts Merit s current security offerings Member feedback Mission and vision statement for this
The ISP Column A monthly column on things Internet. Securing BGP with BGPsec. Introduction
 The ISP Column A monthly column on things Internet July 2011 Geoff Huston Randy Bush Securing BGP with BGPsec Introduction For many years the Internet's fundamental elements names and addresses were the
The ISP Column A monthly column on things Internet July 2011 Geoff Huston Randy Bush Securing BGP with BGPsec Introduction For many years the Internet's fundamental elements names and addresses were the
Multihoming and Multi-path Routing. CS 7260 Nick Feamster January 29. 2007
 Multihoming and Multi-path Routing CS 7260 Nick Feamster January 29. 2007 Today s Topic IP-Based Multihoming What is it? What problem is it solving? (Why multihome?) How is it implemented today (in IP)?
Multihoming and Multi-path Routing CS 7260 Nick Feamster January 29. 2007 Today s Topic IP-Based Multihoming What is it? What problem is it solving? (Why multihome?) How is it implemented today (in IP)?
Layer Four Traceroute (and related tools) A modern, flexible path-discovery solution with advanced features for network (reverse) engineers
 Layer Four Traceroute (and related tools) A modern, flexible path-discovery solution with advanced features for network (reverse) engineers So, what is path discovery and why is it important? Path discovery
Layer Four Traceroute (and related tools) A modern, flexible path-discovery solution with advanced features for network (reverse) engineers So, what is path discovery and why is it important? Path discovery
Research and Educational Networking Information Analysis and Sharing Center (REN-ISAC)
 Research and Educational Networking Information Analysis and Sharing Center (REN-ISAC) Doug Pearson Director, REN-ISAC ren-isac@iu.edu Copyright Trustees of Indiana University 2003. Permission is granted
Research and Educational Networking Information Analysis and Sharing Center (REN-ISAC) Doug Pearson Director, REN-ISAC ren-isac@iu.edu Copyright Trustees of Indiana University 2003. Permission is granted
Network Infrastructure Under Siege
 Network Infrastructure Under Siege Char Sample Security Engineer, CERT Information Security Decisions TechTarget Disclaimer Standard Disclaimer - This talk represents the opinions and research of the presenter
Network Infrastructure Under Siege Char Sample Security Engineer, CERT Information Security Decisions TechTarget Disclaimer Standard Disclaimer - This talk represents the opinions and research of the presenter
Bell Aliant. Business Internet Border Gateway Protocol Policy and Features Guidelines
 Bell Aliant Business Internet Border Gateway Protocol Policy and Features Guidelines Effective 05/30/2006, Updated 1/30/2015 BGP Policy and Features Guidelines 1 Bell Aliant BGP Features Bell Aliant offers
Bell Aliant Business Internet Border Gateway Protocol Policy and Features Guidelines Effective 05/30/2006, Updated 1/30/2015 BGP Policy and Features Guidelines 1 Bell Aliant BGP Features Bell Aliant offers
CISCO INFORMATION TECHNOLOGY AT WORK CASE STUDY: CISCO IOS NETFLOW TECHNOLOGY
 CISCO INFORMATION TECHNOLOGY AT WORK CASE STUDY: CISCO IOS NETFLOW TECHNOLOGY CISCO INFORMATION TECHNOLOGY SEPTEMBER 2004 1 Overview Challenge To troubleshoot capacity and quality problems and to understand
CISCO INFORMATION TECHNOLOGY AT WORK CASE STUDY: CISCO IOS NETFLOW TECHNOLOGY CISCO INFORMATION TECHNOLOGY SEPTEMBER 2004 1 Overview Challenge To troubleshoot capacity and quality problems and to understand
Network Level Multihoming and BGP Challenges
 Network Level Multihoming and BGP Challenges Li Jia Helsinki University of Technology jili@cc.hut.fi Abstract Multihoming has been traditionally employed by enterprises and ISPs to improve network connectivity.
Network Level Multihoming and BGP Challenges Li Jia Helsinki University of Technology jili@cc.hut.fi Abstract Multihoming has been traditionally employed by enterprises and ISPs to improve network connectivity.
Actions and Recommendations (A/R) Summary
 Actions and Recommendations (A/R) Summary Priority I: A National Cyberspace Security Response System A/R 1-1: DHS will create a single point-ofcontact for the federal government s interaction with industry
Actions and Recommendations (A/R) Summary Priority I: A National Cyberspace Security Response System A/R 1-1: DHS will create a single point-ofcontact for the federal government s interaction with industry
Address Scheme Planning for an ISP backbone Network
 Address Scheme Planning for an ISP backbone Network Philip Smith Consulting Engineering, Office of the CTO Version 0.1 (draft) LIST OF FIGURES 2 INTRODUCTION 3 BACKGROUND 3 BUSINESS MODEL 3 ADDRESS PLAN
Address Scheme Planning for an ISP backbone Network Philip Smith Consulting Engineering, Office of the CTO Version 0.1 (draft) LIST OF FIGURES 2 INTRODUCTION 3 BACKGROUND 3 BUSINESS MODEL 3 ADDRESS PLAN
How To Stop A Malicious Dns Attack On A Domain Name Server (Dns) From Being Spoofed (Dnt) On A Network (Networking) On An Ip Address (Ip Address) On Your Ip Address On A Pc Or Ip Address
 DNS Amplification Are YOU Part of the Problem? (RIPE66 Dublin, Ireland - May 13, 2013) Merike Kaeo Security Evangelist, Internet Identity merike@internetidentity.com INTRO Statistics on DNS Amplification
DNS Amplification Are YOU Part of the Problem? (RIPE66 Dublin, Ireland - May 13, 2013) Merike Kaeo Security Evangelist, Internet Identity merike@internetidentity.com INTRO Statistics on DNS Amplification
A PKI For IDR Public Key Infrastructure and Number Resource Certification
 A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
A PKI For IDR Public Key Infrastructure and Number Resource Certification AUSCERT 2006 Geoff Huston Research Scientist APNIC If You wanted to be Bad on the Internet And you wanted to: Hijack a site Inspect
ISP Systems Design. ISP Workshops. Last updated 24 April 2013
 ISP Systems Design ISP Workshops Last updated 24 April 2013 1 Agenda p DNS Server placement p Mail Server placement p News Server placement p Services network design p Services Network Security 2 ISP Services
ISP Systems Design ISP Workshops Last updated 24 April 2013 1 Agenda p DNS Server placement p Mail Server placement p News Server placement p Services network design p Services Network Security 2 ISP Services
Click here to submit your resume
 To be considered for positions with SE Solutions candidates must be clearable to a Top Secret level. A current Secret clearance or higher is preferred. US citizenship is required. All positions are full
To be considered for positions with SE Solutions candidates must be clearable to a Top Secret level. A current Secret clearance or higher is preferred. US citizenship is required. All positions are full
Measurement Study on the Internet reachability. 3.1 Introduction. 3. Internet Backbone
 3. Measurement Study on the Internet reachability Internet reachability can be assessed using control-plane and data-plane measurements. However, there are biases in the results of these two measurement
3. Measurement Study on the Internet reachability Internet reachability can be assessed using control-plane and data-plane measurements. However, there are biases in the results of these two measurement
Towards a Next- Generation Inter-domain Routing Protocol. L. Subramanian, M. Caesar, C.T. Ee, M. Handley, Z. Mao, S. Shenker, and I.
 Towards a Next- Generation Inter-domain Routing Protocol L. Subramanian, M. Caesar, C.T. Ee, M. Handley, Z. Mao, S. Shenker, and I. Stoica Routing 1999 Internet Map Coloured by ISP Source: Bill Cheswick,
Towards a Next- Generation Inter-domain Routing Protocol L. Subramanian, M. Caesar, C.T. Ee, M. Handley, Z. Mao, S. Shenker, and I. Stoica Routing 1999 Internet Map Coloured by ISP Source: Bill Cheswick,
Detecting BGP hijacks in 2014
 Detecting BGP hijacks in 2014 Guillaume Valadon & Nicolas Vivet Agence nationale de la sécurité des systèmes d information http://www.ssi.gouv.fr/en NSC - November 21th, 2014 ANSSI - Detecting BGP hijacks
Detecting BGP hijacks in 2014 Guillaume Valadon & Nicolas Vivet Agence nationale de la sécurité des systèmes d information http://www.ssi.gouv.fr/en NSC - November 21th, 2014 ANSSI - Detecting BGP hijacks
Firewall-on-Demand. GRNET s approach to advanced network security services management via bgp flow-spec and NETCONF. Leonidas Poulopoulos
 Firewall-on-Demand GRNET s approach to advanced network security services management via bgp flow-spec and NETCONF Leonidas Poulopoulos 1 leopoul@nocgrnetgr 1 NOC/Greek Research and Technology Network
Firewall-on-Demand GRNET s approach to advanced network security services management via bgp flow-spec and NETCONF Leonidas Poulopoulos 1 leopoul@nocgrnetgr 1 NOC/Greek Research and Technology Network
IPv4 Address Trading Using Resource Certificate
 Journal of Information Processing Systems, Vol.6, No.1, March 2010 DOI : 10.3745/JIPS.2010.6.1.107 IPv4 Address Trading Using Resource Certificate Cheol-Soon Park*, Jae-Cheol Ryou** and Yong-Tae Park***
Journal of Information Processing Systems, Vol.6, No.1, March 2010 DOI : 10.3745/JIPS.2010.6.1.107 IPv4 Address Trading Using Resource Certificate Cheol-Soon Park*, Jae-Cheol Ryou** and Yong-Tae Park***
Internet Addresses (You should read Chapter 4 in Forouzan)
 Internet Addresses (You should read Chapter 4 in Forouzan) IP Address is 32 Bits Long Conceptually the address is the pair (NETID, HOSTID) Addresses are assigned by the internet company for assignment
Internet Addresses (You should read Chapter 4 in Forouzan) IP Address is 32 Bits Long Conceptually the address is the pair (NETID, HOSTID) Addresses are assigned by the internet company for assignment
Monitoring BGP and Route Leaks using OpenBMP and Apache Kafka
 Monitoring BGP and Route Leaks using OpenBMP and Apache Kafka Tim Evens (tievens@cisco.com) NANOG-65 Traditional Method: VTY (cli/netconf/xml) Data is polled instead of pushed (not real-time) Large queries
Monitoring BGP and Route Leaks using OpenBMP and Apache Kafka Tim Evens (tievens@cisco.com) NANOG-65 Traditional Method: VTY (cli/netconf/xml) Data is polled instead of pushed (not real-time) Large queries
LAN TCP/IP and DHCP Setup
 CHAPTER 2 LAN TCP/IP and DHCP Setup 2.1 Introduction In this chapter, we will explain in more detail the LAN TCP/IP and DHCP Setup. 2.2 LAN IP Network Configuration In the Vigor 2900 router, there are
CHAPTER 2 LAN TCP/IP and DHCP Setup 2.1 Introduction In this chapter, we will explain in more detail the LAN TCP/IP and DHCP Setup. 2.2 LAN IP Network Configuration In the Vigor 2900 router, there are
Novel Systems. Extensible Networks
 Novel Systems Active Networks Denali Extensible Networks Observations Creating/disseminating standards hard Prototyping/research Incremental deployment Computation may be cheap compared to communication
Novel Systems Active Networks Denali Extensible Networks Observations Creating/disseminating standards hard Prototyping/research Incremental deployment Computation may be cheap compared to communication
Coveo Platform 7.0. Microsoft Active Directory Connector Guide
 Coveo Platform 7.0 Microsoft Active Directory Connector Guide Notice The content in this document represents the current view of Coveo as of the date of publication. Because Coveo continually responds
Coveo Platform 7.0 Microsoft Active Directory Connector Guide Notice The content in this document represents the current view of Coveo as of the date of publication. Because Coveo continually responds
What's inside the cloud?!
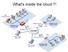 What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
What's inside the cloud?! Initial Arpanet Initial Arpanet Interface Message Processors - DDP-516 mini-computers - 24 Kbyte of Core memory - Store-and-forward packet switching - Predecessors of present
APNIC Trial of Certification of IP Addresses and ASes
 APNIC Trial of Certification of IP Addresses and ASes RIPE 51 11 October 2005 Geoff Huston 1 Address and Routing Security What we have today is a relatively insecure system that is vulnerable to various
APNIC Trial of Certification of IP Addresses and ASes RIPE 51 11 October 2005 Geoff Huston 1 Address and Routing Security What we have today is a relatively insecure system that is vulnerable to various
Secure routing: State-of-the-art deployment and impact on network resilience
 Secure Routing July 10 Secure routing: State-of-the-art deployment and impact on network resilience About ENISA: The European Network and Information Security Agency (ENISA) is an EU agency created to
Secure Routing July 10 Secure routing: State-of-the-art deployment and impact on network resilience About ENISA: The European Network and Information Security Agency (ENISA) is an EU agency created to
BGP (Border Gateway Protocol)
 BGP (Border Gateway Protocol) Document revision 1.2 (Thu Mar 04 19:34:34 GMT 2004) This document applies to V2.8 Table of Contents Table of Contents General Information Summary Specifications Related Documents
BGP (Border Gateway Protocol) Document revision 1.2 (Thu Mar 04 19:34:34 GMT 2004) This document applies to V2.8 Table of Contents Table of Contents General Information Summary Specifications Related Documents
Recent Progress in Routing Standardization An IETF update for UKNOF 23
 Recent Progress in Routing Standardization An IETF update for UKNOF 23 Old Dog Consulting Adrian Farrel adrian@olddog.co.uk afarrel@juniper.net IETF Routing Area Director Daniel King daniel@olddog.co.uk
Recent Progress in Routing Standardization An IETF update for UKNOF 23 Old Dog Consulting Adrian Farrel adrian@olddog.co.uk afarrel@juniper.net IETF Routing Area Director Daniel King daniel@olddog.co.uk
Exterior Gateway Protocols (BGP)
 Exterior Gateway Protocols (BGP) Internet Structure Large ISP Large ISP Stub Dial-Up ISP Small ISP Stub Stub Stub Autonomous Systems (AS) Internet is not a single network! The Internet is a collection
Exterior Gateway Protocols (BGP) Internet Structure Large ISP Large ISP Stub Dial-Up ISP Small ISP Stub Stub Stub Autonomous Systems (AS) Internet is not a single network! The Internet is a collection
BGP FORGOTTEN BUT USEFUL FEATURES. Piotr Wojciechowski (CCIE #25543)
 BGP FORGOTTEN BUT USEFUL FEATURES Piotr Wojciechowski (CCIE #25543) ABOUT ME Senior Network Engineer MSO at VeriFone Inc. Previously Network Solutions Architect at one of top polish IT integrators CCIE
BGP FORGOTTEN BUT USEFUL FEATURES Piotr Wojciechowski (CCIE #25543) ABOUT ME Senior Network Engineer MSO at VeriFone Inc. Previously Network Solutions Architect at one of top polish IT integrators CCIE
How to Integrate NERC s Requirements in an Ongoing Automation and Integration Project Framework
 How to Integrate NERC s Requirements in an Ongoing Automation and Integration Project Framework Jacques Benoit, Cooper Power Systems Inc., Energy Automations Solutions - Cybectec Robert O Reilly, Cooper
How to Integrate NERC s Requirements in an Ongoing Automation and Integration Project Framework Jacques Benoit, Cooper Power Systems Inc., Energy Automations Solutions - Cybectec Robert O Reilly, Cooper
DDoS Overview and Incident Response Guide. July 2014
 DDoS Overview and Incident Response Guide July 2014 Contents 1. Target Audience... 2 2. Introduction... 2 3. The Growing DDoS Problem... 2 4. DDoS Attack Categories... 4 5. DDoS Mitigation... 5 1 1. Target
DDoS Overview and Incident Response Guide July 2014 Contents 1. Target Audience... 2 2. Introduction... 2 3. The Growing DDoS Problem... 2 4. DDoS Attack Categories... 4 5. DDoS Mitigation... 5 1 1. Target
BGP Security The Human Threat
 BGP Security The Human Threat RIPE / Amsterdam 2011.05.02 Randy Bush 2011.05.02 The Human Threat 1 Assume RPKI Cert/IANA CA 98.128.0.0/16 SIA Cert/RIPE CA CA CA Cert/ARIN Cert/APNIC 98.128.0.0/20
BGP Security The Human Threat RIPE / Amsterdam 2011.05.02 Randy Bush 2011.05.02 The Human Threat 1 Assume RPKI Cert/IANA CA 98.128.0.0/16 SIA Cert/RIPE CA CA CA Cert/ARIN Cert/APNIC 98.128.0.0/20
Global Network Mobility RIPE 48
 John Bender Don Bowman cbbrouting@boeing.com Global Network Mobility RIPE 48 Implementing Network Mobility Summary What is Connexion by Boeing? Network and Service Challenges BGP as a mobility solution
John Bender Don Bowman cbbrouting@boeing.com Global Network Mobility RIPE 48 Implementing Network Mobility Summary What is Connexion by Boeing? Network and Service Challenges BGP as a mobility solution
Outline. Outline. Outline
 Network Forensics: Network Prefix Scott Hand September 30 th, 2011 1 What is network forensics? 2 What areas will we focus on today? Basics Some Techniques What is it? OS fingerprinting aims to gather
Network Forensics: Network Prefix Scott Hand September 30 th, 2011 1 What is network forensics? 2 What areas will we focus on today? Basics Some Techniques What is it? OS fingerprinting aims to gather
HOW TO PREVENT DDOS ATTACKS IN A SERVICE PROVIDER ENVIRONMENT
 HOW TO PREVENT DDOS ATTACKS IN A SERVICE PROVIDER ENVIRONMENT The frequency and sophistication of Distributed Denial of Service attacks (DDoS) on the Internet are rapidly increasing. Most of the earliest
HOW TO PREVENT DDOS ATTACKS IN A SERVICE PROVIDER ENVIRONMENT The frequency and sophistication of Distributed Denial of Service attacks (DDoS) on the Internet are rapidly increasing. Most of the earliest
How To Load Balance On A Bgg On A Network With A Network (Networking) On A Pc Or Ipa On A Computer Or Ipad On A 2G Network On A Microsoft Ipa (Netnet) On An Ip
 Globally Distributed Content (Using BGP to Take Over the World) Horms (Simon Horman) horms@vergenet.net November 2001 http://supersparrow.org/ 1 Introduction Electronic content is becoming increasingly
Globally Distributed Content (Using BGP to Take Over the World) Horms (Simon Horman) horms@vergenet.net November 2001 http://supersparrow.org/ 1 Introduction Electronic content is becoming increasingly
DoS-resistant Internet - progress. Bob Briscoe Jun 2005
 DoS-resistant Internet - progress Bob Briscoe Jun 2005 BT activity Research 2020 Communications Architecture project DoS-resistant Internet Architecture task Network Security project BGP security control
DoS-resistant Internet - progress Bob Briscoe Jun 2005 BT activity Research 2020 Communications Architecture project DoS-resistant Internet Architecture task Network Security project BGP security control
IP Routing Configuring Static Routes
 11 IP Routing Configuring Static Routes Contents Overview..................................................... 11-3 IP Addressing.............................................. 11-3 Networks.................................................
11 IP Routing Configuring Static Routes Contents Overview..................................................... 11-3 IP Addressing.............................................. 11-3 Networks.................................................
Information security versus network security in the Internet as critical infrastructure Security of Internet and Critical Infrastructures: European
 Information security versus network security in the Internet as critical infrastructure Security of Internet and Critical Infrastructures: European Experiences, Rome, 13 June 2011 Objectives Describe information
Information security versus network security in the Internet as critical infrastructure Security of Internet and Critical Infrastructures: European Experiences, Rome, 13 June 2011 Objectives Describe information
Interdomain Routing. Project Report
 Interdomain Routing Project Report Network Infrastructure improvement proposal To Company A Team 4: Zhang Li Bin Yang Md. Safiqul Islam Saurabh Arora Network Infrastructure Improvement Interdomain routing
Interdomain Routing Project Report Network Infrastructure improvement proposal To Company A Team 4: Zhang Li Bin Yang Md. Safiqul Islam Saurabh Arora Network Infrastructure Improvement Interdomain routing
Measuring IPv6 Deployment. Geoff Huston APNIC December 2009
 Measuring IPv6 Deployment Geoff Huston APNIC December 2009 IPv4 address exhaustion Total Address Count Adver0sed Count IANA Pool Unadver0sed Count IPv4 address exhaustion The model of address consumption
Measuring IPv6 Deployment Geoff Huston APNIC December 2009 IPv4 address exhaustion Total Address Count Adver0sed Count IANA Pool Unadver0sed Count IPv4 address exhaustion The model of address consumption
Routing Security Training Course
 Routing Security Training Course Exercise Booklet November 2015 Introduction Your database objects For your convenience we have already created some objects in the RIPE TEST Database. You can use these
Routing Security Training Course Exercise Booklet November 2015 Introduction Your database objects For your convenience we have already created some objects in the RIPE TEST Database. You can use these
70-642 R4: Configuring Windows Server 2008 Network Infrastructure
 70-642 R4: Configuring Windows Server 2008 Network Infrastructure Course Introduction Chapter 01 - Understanding and Configuring IP Lesson: Introducing the OSI Model Understanding the Network Layers OSI
70-642 R4: Configuring Windows Server 2008 Network Infrastructure Course Introduction Chapter 01 - Understanding and Configuring IP Lesson: Introducing the OSI Model Understanding the Network Layers OSI
Collective responsibility for security and resilience of the global routing system
 Collective responsibility for security and resilience of the global routing system Andrei Robachevsky www.internetsociety.org Let us look at the problem first BGP is based on trust
Collective responsibility for security and resilience of the global routing system Andrei Robachevsky www.internetsociety.org Let us look at the problem first BGP is based on trust
IPv6, Perspective from small to medium ISP
 IPv6, Perspective from small to medium ISP April 13 th, 2010 INET Conference, Hong Kong Christian Dwinantyo Overview Some myths and facts about IPv6 Implementation Strategy Before you begin Case study:
IPv6, Perspective from small to medium ISP April 13 th, 2010 INET Conference, Hong Kong Christian Dwinantyo Overview Some myths and facts about IPv6 Implementation Strategy Before you begin Case study:
Guide to DDoS Attacks December 2014 Authored by: Lee Myers, SOC Analyst
 INTEGRATED INTELLIGENCE CENTER Technical White Paper William F. Pelgrin, CIS President and CEO Guide to DDoS Attacks December 2014 Authored by: Lee Myers, SOC Analyst This Center for Internet Security
INTEGRATED INTELLIGENCE CENTER Technical White Paper William F. Pelgrin, CIS President and CEO Guide to DDoS Attacks December 2014 Authored by: Lee Myers, SOC Analyst This Center for Internet Security
How close are we sticking to the transition script? How well are we doing with IPv6 deployment?
 The ISP Column A monthly column on things Internet April 2008 Geoff Huston & George Michaelson IPv6 Deployment: Just where are we? I suppose we all know the plot by now. Back in the early 1990's it was
The ISP Column A monthly column on things Internet April 2008 Geoff Huston & George Michaelson IPv6 Deployment: Just where are we? I suppose we all know the plot by now. Back in the early 1990's it was
Networking Basics for Automation Engineers
 Networking Basics for Automation Engineers Page 1 of 10 mac-solutions.co.uk v1.0 Oct 2014 1. What is Transmission Control Protocol/Internet Protocol (TCP/IP)------------------------------------------------------------
Networking Basics for Automation Engineers Page 1 of 10 mac-solutions.co.uk v1.0 Oct 2014 1. What is Transmission Control Protocol/Internet Protocol (TCP/IP)------------------------------------------------------------
Update from the RIPE NCC
 RIPE Network Coordination Centre Update from the RIPE NCC RIPE 59, 5-9 October, Lisbon http://www.ripe.net 1 Member Services - New LIR Setup - Billing Customer Services - Administrative and LIR Portal
RIPE Network Coordination Centre Update from the RIPE NCC RIPE 59, 5-9 October, Lisbon http://www.ripe.net 1 Member Services - New LIR Setup - Billing Customer Services - Administrative and LIR Portal
Border Gateway Protocol BGP4 (2)
 Border Gateway Protocol BGP4 (2) Professor Richard Harris School of Engineering and Advanced Technology (SEAT) Presentation Outline Border Gateway Protocol - Continued Computer Networks - 1/2 Learning
Border Gateway Protocol BGP4 (2) Professor Richard Harris School of Engineering and Advanced Technology (SEAT) Presentation Outline Border Gateway Protocol - Continued Computer Networks - 1/2 Learning
Practical BGP Security: Architecture, Techniques and Tools
 renesys WHITE PAPER Practical BGP Security: Architecture, Techniques and Tools Laris Benkis A practical approach to identify weaknesses and highlight strategies for the detection of internetwork failures
renesys WHITE PAPER Practical BGP Security: Architecture, Techniques and Tools Laris Benkis A practical approach to identify weaknesses and highlight strategies for the detection of internetwork failures
The ISP Column A monthly column on things Internet. Leaking Routes. March 2012 Geoff Huston. Its happened again.
 The ISP Column A monthly column on things Internet March 2012 Geoff Huston Leaking Routes Its happened again. We've just had yet another major routing leak, this time bringing down the Internet for most
The ISP Column A monthly column on things Internet March 2012 Geoff Huston Leaking Routes Its happened again. We've just had yet another major routing leak, this time bringing down the Internet for most
Policy-Based AS Path Verification with Enhanced Comparison Algorithm to Prevent 1-Hop AS Path Hijacking in Real Time
 , pp.11-22 http://dx.doi.org/10.14257/ijmue.2016.11.1.02 Policy-Based AS Path Verification with Enhanced Comparison Algorithm to Prevent 1-Hop AS Path Hijacking in Real Time Je-Kuk Yun 1 and Jin-Hee Song
, pp.11-22 http://dx.doi.org/10.14257/ijmue.2016.11.1.02 Policy-Based AS Path Verification with Enhanced Comparison Algorithm to Prevent 1-Hop AS Path Hijacking in Real Time Je-Kuk Yun 1 and Jin-Hee Song
BGP Operations and Security. Training Course
 BGP Operations and Security Training Course Training Services RIPE NCC April 2016 Schedule 09:00-09:30 11:00-11:15 13:00-14:00 15:30-15:45 17:30 Coffee, Tea Break Lunch Break End BGP Operations and Security
BGP Operations and Security Training Course Training Services RIPE NCC April 2016 Schedule 09:00-09:30 11:00-11:15 13:00-14:00 15:30-15:45 17:30 Coffee, Tea Break Lunch Break End BGP Operations and Security
Planning the transition to IPv6
 Planning the transition to IPv6 An Allstream White Paper 1 Table of contents Why transition now? 1 Transition mechanisms 2 Transition phases 2 IPv6 transition challenges 3 Taking advantage of IPv6 benefits
Planning the transition to IPv6 An Allstream White Paper 1 Table of contents Why transition now? 1 Transition mechanisms 2 Transition phases 2 IPv6 transition challenges 3 Taking advantage of IPv6 benefits
RIPE Whois Database Query Reference Manual
 RIPE Whois Database Query Reference Manual João Luis Silva Damas Andrei Robachevsky Denis Walker Document ID: ripe-358 Date: October 2005 Partly Obsoletes: ripe-252 Abstract This document describes how
RIPE Whois Database Query Reference Manual João Luis Silva Damas Andrei Robachevsky Denis Walker Document ID: ripe-358 Date: October 2005 Partly Obsoletes: ripe-252 Abstract This document describes how
How NOC manages and controls inter-domain traffic? 5 th tf-noc meeting, Dubrovnik nino.ciurleo@garr.it
 How NOC manages and controls inter-domain traffic? 5 th tf-noc meeting, Dubrovnik nino.ciurleo@garr.it Agenda Inter-domain traffic: o how does NOC monitor and control it? Common case as example: new BGP
How NOC manages and controls inter-domain traffic? 5 th tf-noc meeting, Dubrovnik nino.ciurleo@garr.it Agenda Inter-domain traffic: o how does NOC monitor and control it? Common case as example: new BGP
INOC-DBA Hotline Phone System
 INOC-DBA Hotline Phone System RIPE 49 BoF Presentation edited after the BoF to reflect key discussions September 2004 Gaurab Raj Upadhaya gaurab@lahai.com INOC-DBA Operator, Packet Clearing House What
INOC-DBA Hotline Phone System RIPE 49 BoF Presentation edited after the BoF to reflect key discussions September 2004 Gaurab Raj Upadhaya gaurab@lahai.com INOC-DBA Operator, Packet Clearing House What
Customized BGP Route Selection Using BGP/MPLS VPNs
 Customized BGP Route Selection Using BGP/MPLS VPNs Laurent Vanbever Université catholique de Louvain, BE!"#$%&'()"&*%+%$,#-./#+"0&(*% Pierre Francois (UCLouvain, BE), Olivier Bonaventure (UCLouvain, BE)
Customized BGP Route Selection Using BGP/MPLS VPNs Laurent Vanbever Université catholique de Louvain, BE!"#$%&'()"&*%+%$,#-./#+"0&(*% Pierre Francois (UCLouvain, BE), Olivier Bonaventure (UCLouvain, BE)
APNIC Plans and Budget - Review
 APNIC 2015 Activity Plan and Budget APNIC 2015 Activity Plan and Budget Table of Contents Introduction... 3 Notes on the Plan... 4 Executive Summary... 5 Operating Expenditure 2015... 5 APNIC 2015 Activity
APNIC 2015 Activity Plan and Budget APNIC 2015 Activity Plan and Budget Table of Contents Introduction... 3 Notes on the Plan... 4 Executive Summary... 5 Operating Expenditure 2015... 5 APNIC 2015 Activity
NSA/DHS Centers of Academic Excellence for Information Assurance/Cyber Defense
 NSA/DHS Centers of Academic Excellence for Information Assurance/Cyber Defense Cyber Investigations Data Management Systems Security Data Security Analysis Digital Forensics Health Care Security Industrial
NSA/DHS Centers of Academic Excellence for Information Assurance/Cyber Defense Cyber Investigations Data Management Systems Security Data Security Analysis Digital Forensics Health Care Security Industrial
Hi-BGP: A Lightweight Hijack-proof Inter-domain Routing Protocol
 1 Hi-BGP: A Lightweight Hijack-proof Inter-domain Routing Protocol Jian Qiu and Lixin Gao Department of ECE, University of Massachusetts, Amherst, MA 01002 jqiu@ecs.umass.edu, lgao@ecs.umass.edu Abstract
1 Hi-BGP: A Lightweight Hijack-proof Inter-domain Routing Protocol Jian Qiu and Lixin Gao Department of ECE, University of Massachusetts, Amherst, MA 01002 jqiu@ecs.umass.edu, lgao@ecs.umass.edu Abstract
Networks 3. 2015 University of Stirling CSCU9B1 Essential Skills for the Information Age. Content
 Networks 3 Lecture Networks 3/Slide 1 Content What is a communications protocol? Network protocols TCP/IP High-level protocols Firewalls Network addresses Host name IP address Domain name system (DNS)
Networks 3 Lecture Networks 3/Slide 1 Content What is a communications protocol? Network protocols TCP/IP High-level protocols Firewalls Network addresses Host name IP address Domain name system (DNS)
Department of Veteran Affairs. Fred Catoe Office of Cyber and Information Security AAIP Project Manager March 2004
 Department of Veteran Affairs Fred Catoe Office of Cyber and Information Security AAIP Project Manager March 2004 Background Smart Cards are a subset of a larger Authentication and Authorization Infrastructure
Department of Veteran Affairs Fred Catoe Office of Cyber and Information Security AAIP Project Manager March 2004 Background Smart Cards are a subset of a larger Authentication and Authorization Infrastructure
Understanding Route Redistribution & Filtering
 Understanding Route Redistribution & Filtering When to Redistribute and Filter PAN-OS 5.0 Revision B 2013, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Route Redistribution......
Understanding Route Redistribution & Filtering When to Redistribute and Filter PAN-OS 5.0 Revision B 2013, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Route Redistribution......
ALTO and Content Delivery Networks dra7- penno- alto- cdn
 ALTO and Content Delivery Networks dra7- penno- alto- cdn Stefano Previdi, sprevidi@cisco.com Richard Alimi, ralimi@google.com Jan Medved, jmedved@juniper.net Reinaldo Penno, rpenno@juniper.net Richard
ALTO and Content Delivery Networks dra7- penno- alto- cdn Stefano Previdi, sprevidi@cisco.com Richard Alimi, ralimi@google.com Jan Medved, jmedved@juniper.net Reinaldo Penno, rpenno@juniper.net Richard
7 Homeland. ty Grant Program HOMELAND SECURITY GRANT PROGRAM. Fiscal Year 2008
 U.S. D EPARTMENT OF H OMELAND S ECURITY 7 Homeland Fiscal Year 2008 HOMELAND SECURITY GRANT PROGRAM ty Grant Program SUPPLEMENTAL RESOURCE: CYBER SECURITY GUIDANCE uidelines and Application Kit (October
U.S. D EPARTMENT OF H OMELAND S ECURITY 7 Homeland Fiscal Year 2008 HOMELAND SECURITY GRANT PROGRAM ty Grant Program SUPPLEMENTAL RESOURCE: CYBER SECURITY GUIDANCE uidelines and Application Kit (October
BGP as an IGP for Carrier/Enterprise Networks
 BGP as an IGP for Carrier/Enterprise Networks Presented by: Kevin Myers, SENIOR NETWORK ENGINEER IP ArchiTECHS MANAGED SERVICES Background Kevin Myers 15 + years in IT/Network Engineering Designed and
BGP as an IGP for Carrier/Enterprise Networks Presented by: Kevin Myers, SENIOR NETWORK ENGINEER IP ArchiTECHS MANAGED SERVICES Background Kevin Myers 15 + years in IT/Network Engineering Designed and
NOS for Network Support (903)
 NOS for Network Support (903) November 2014 V1.1 NOS Reference ESKITP903301 ESKITP903401 ESKITP903501 ESKITP903601 NOS Title Assist with Installation, Implementation and Handover of Network Infrastructure
NOS for Network Support (903) November 2014 V1.1 NOS Reference ESKITP903301 ESKITP903401 ESKITP903501 ESKITP903601 NOS Title Assist with Installation, Implementation and Handover of Network Infrastructure
CSC458 Lecture 6. Homework #1 Grades. Inter-domain Routing IP Addressing. Administrivia. Midterm will Cover Following Topics
 CSC458 Lecture 6 Inter-domain Routing IP Addressing Stefan Saroiu http://www.cs.toronto.edu/syslab/courses/csc458 University of Toronto at Mississauga Homework #1 Grades Fraction of Students 100 80 60
CSC458 Lecture 6 Inter-domain Routing IP Addressing Stefan Saroiu http://www.cs.toronto.edu/syslab/courses/csc458 University of Toronto at Mississauga Homework #1 Grades Fraction of Students 100 80 60
Understanding Large Internet Service Provider Backbone Networks
 Understanding Large Internet Service Provider Backbone Networks Joel M. Gottlieb IP Network Management & Performance Department AT&T Labs Research Florham Park, New Jersey joel@research.att.com Purpose
Understanding Large Internet Service Provider Backbone Networks Joel M. Gottlieb IP Network Management & Performance Department AT&T Labs Research Florham Park, New Jersey joel@research.att.com Purpose
Customer Managed Connectivity - Milan
 Customer Managed Connectivity - Milan Service and Technical Description December 2015 Version 1 Table of Contents 1.0 Document Scope 3 1.1 1.2 1.3 1.4 Structure of this document 3 Version History 3 Use
Customer Managed Connectivity - Milan Service and Technical Description December 2015 Version 1 Table of Contents 1.0 Document Scope 3 1.1 1.2 1.3 1.4 Structure of this document 3 Version History 3 Use
The Cloud and IPv6 Company IPv6 and Cloud
 The Cloud and IPv6 Company IPv6 and Cloud Ciprian Popoviciu Shixiong Shang Agenda The IPv6 and Cloud Story IPv6 and OpenStack Overview IPv6 and OpenStack Case Study Conclusion 2 A Little Bit About Us (
The Cloud and IPv6 Company IPv6 and Cloud Ciprian Popoviciu Shixiong Shang Agenda The IPv6 and Cloud Story IPv6 and OpenStack Overview IPv6 and OpenStack Case Study Conclusion 2 A Little Bit About Us (
Secure Border Gateway Protocol (S-BGP) Real World Performance and Deployment Issues
 Secure Border Gateway Protocol (S-BGP) Real World Performance and Deployment Issues Stephen Kent, Charles Lynn, Joanne Mikkelson, and Karen Seo BBN Technologies Abstract The Border Gateway Protocol (BGP),
Secure Border Gateway Protocol (S-BGP) Real World Performance and Deployment Issues Stephen Kent, Charles Lynn, Joanne Mikkelson, and Karen Seo BBN Technologies Abstract The Border Gateway Protocol (BGP),
TABLE OF CONTENTS. Section 5 IPv6... 5-1 5.1 Introduction... 5-1 5.2 Definitions... 5-1 5.3 DoD IPv6 Profile... 5-3 5.3.1 Product Requirements...
 , Table of Contents TABLE OF CONTENTS SECTION PAGE IPv6... 5-1 5.1 Introduction... 5-1 5.2 Definitions... 5-1 5.3 DoD IPv6 Profile... 5-3 5.3.1 Product Requirements... 5-4 i , List of Figures LIST OF FIGURES
, Table of Contents TABLE OF CONTENTS SECTION PAGE IPv6... 5-1 5.1 Introduction... 5-1 5.2 Definitions... 5-1 5.3 DoD IPv6 Profile... 5-3 5.3.1 Product Requirements... 5-4 i , List of Figures LIST OF FIGURES
