Intel Anti-Theft Service
|
|
|
- Andrew Lindsey
- 9 years ago
- Views:
Transcription
1 Intel Anti-Theft Service user guide Version 1.0
2 Contents Chapter 1: Quickstart... 4 Quickstart Requirements...4 Quickstart Procedure...4 Chapter 2: Introducing the Service... 6 Congratulations....6 Service Features....6 More About the Built-in Protection....6 Attach the Sticker to Your PC Secure Data Vault....7 Setting up Intel Anti-Theft Technology for Your PC....7 Chapter 3: Activating the Service Subscription Activation Site...8 Activating a First-Time Account...8 Enrolling a PC to the Service...10 Installing the PC-based software...12 Printing the Reference Screen Chapter 4: Using the Service Configuring the Service Installing Secure Data Vault...15 Locking Your PC Triggering the Lock/Theft Protection Mode...15 Viewing the History...16 Checking Status through the Notification Area Icon...17 Right-Clicking the Notification Area Icon...18 Using the Help Menu...18 Viewing Tooltips...18 Chapter 5: Using Secure Data Vault Opening Secure Data Vault Creating an Encrypted Container Closing Secure Data Vault...21 Recovering Secure Data Vault Information...21 Retrieving the Password for Secure Data Vault Contents
3 Chapter 6: Recovering Your PC Unlocking from the Web...24 Entering the Unlock Password...24 Retrieving the Unlock Password...25 Recovering the Service...25 Chapter 7: Suspending or Cancelling Service Suspending Service...26 Unsubscribing...27 Chapter 8: Contacting Customer Support Support Options...28 Planned Automated Phone Support...28 Chapter 9: FAQ Account Settings Theft Policy Settings...31 Secure Data Vault Unlock Password Appendix Installing Java* Runtime Environment v Glossary Contents
4 Chapter 1: Quickstart If you understand the technology and you are comfortable with the features of this Service, follow this quickstart to set up and configure the Intel Anti-Theft Service (referred to throughout as the Service ). If you d prefer more explanation with full details of the procedure, skip this quickstart and begin at Introducing the Service. Quickstart Requirements To enable the Service, you need: A valid address An Internet connection A PC equipped with Intel Anti-Theft Technology Some of the capable models are listed here: ATservice.intel.com Quickstart Procedure There are three basic steps to getting started: 1. Create an account 2. Enroll your PC 3. Create a Secure Data Vault container To create an account, 1. Go to ATservice.intel.com. 2. Click Create account. 3. Fill out the information requested on the form. 4. Follow the directions in the sent by the Service to finish creating an account. warning: Your PC is not protected until you enroll it into the Service. 4 Quickstart
5 To enroll your PC, 1. Go to ATservice.intel.com. 2. Log in to your account. 3. Click Enroll PC. 4. Follow the directions to download and install the Intel Anti-Theft Service programs. To create a Secure Data Vault container (if you chose to install Secure Data Vault), 1. Click Windows Start. 2. Click Secure Data Vault. 3. Create a new Secure Data Vault password and container. 4. Move files into the container and the program will automatically encrypt the files. To contact Intel Anti-Theft Service for additional questions, 1. Visit ATservice.intel.com. Click on Contact Us. 5 Quickstart
6 Chapter 2: Introducing the Service Congratulations Your selection of the Intel Anti-Theft Service is a positive step toward guarding against theft and ensuring your personal privacy. This manual explains how to take advantage of the built-in hardware features, software options, and service benefits. Note: We recommend that you complete the registration and activation process as soon as possible so that the powerful anti-theft capabilities in your new PC will be activated and ready for use. Service Features The Service lets you: Lock down your PC if it is lost or stolen so that no one can use it Create an encrypted folder (known as Secure Data Vault) on your PC where private files can be stored Note: Encryption converts data into a code to prevent unauthorized access. These features can t be used until you ve registered and activated your PC, so be sure to complete the activation process promptly. More About the Built-in Protection Your PC includes built-in hardware components, designed by Intel, that work with software and the Service to provide multiple levels of protection. Intel Anti-Theft Technology, available on select PCs featuring the 2nd generation Intel Core TM processor family, strengthens security by performing operations in protected areas in the PC s hardware. Hardware-enabled protection enhances protection. If your PC is lost or stolen, it can be automatically disabled and only you can turn it back on. It s like having a full-time security guard inside your PC. When suspicious activities are detected, the technology automatically locks down your PC. PC lockdown occurs if: Your PC is lost or stolen, and you notify the Service. The Service efficiently locks down your PC no matter where it is once notification has been received. You don t connect your PC to the Internet for a certain number of days (as set in the Service options). For example, if your PC is lost and the timer expires after several days without server synchronization across the Internet, the PC goes into lockdown mode. 6 Introducing the Service
7 You ll enjoy a greater degree of security and freedom with these strong PC protection features in place, and you ll reduce the risk of identity theft or having private information revealed. The Intel Anti-Theft Technology sticker on your PC can also be a strong deterrent to potential thieves, who recognize the obstacles presented by this multi-level security solution. Attach the Sticker to Your PC The bright yellow sticker serves notice to would-be thieves and hackers that your PC is protected with strong, hardware-based anti-theft technology. We recommend that you apply the sticker to a highly visible location on your PC, such as the top surface. You ll find the sticker included as part of the subscription details where your activation code is provided. Peel it free from the activation card and place it in a location where it will be easily noticed on your PC. Secure Data Vault Secure Data Vault is technology that creates a protected region on the hard disk drive of your PC where you can securely store sensitive information. This region is identified by its own assigned drive letter on your system, and it can be accessed only by supplying the password that you select. All data contained in Secure Data Vault is encrypted, so it cannot be read by anyone other than you. You can install this feature during the initial setup of the Service or at a later date. Setting up Intel Anti-Theft Service for Your PC You can control how the Service features work on your PC by setting certain options. Spend some time becoming familiar with these options by reading the descriptions in this guide. This will help you understand how to configure the Service to your personal preferences. The following chapter describes the activation, enrollment, and setup process for the Service. 7 Introducing the Service
8 Chapter 3: Activating the Service To activate the Intel Anti-Theft Service, you need: An Internet connection and a valid address The 25-character activation code you received in the Intel Anti-Theft Service package A PC that includes Intel Anti-Theft Technology (when you enroll be sure to use the PC that you purchased, rather than any other PC) To begin the activation process, 1. Log in to ATService.intel.com. The Welcome screen appears, described in the following section. Subscription Activation Site If this is the first time that you have logged into the subscription activation page, you must create an account and provide some information to start up the Service. Note: The subscription activation site relies on Java*. Refer to the Appendix if you need details on how to set up Java for your PC. This Appendix also provides information on browser compatibility and testing your PC for service compatibility. Note: If you already have an account, log in to the Web site using your existing username and password. Activating a First-time Account To create an account to use the Service, 1. From the Welcome page, click Activate your Account. The Account Set Up screen appears. 2. Enter the Activation Code found on the Activation Card inside the Intel Anti-Theft Service Package. 3. Enter the Address you want to use for communications with the Service. Retype the address in the box directly below to confirm it was entered correctly. Note: The address is used to complete the account setup. 8 Activating the Service
9 4. Create a login password to use when you access your account. Use numbers and a mix of uppercase and lowercase letters at least 8 characters in length to make the password harder to break. 5. Retype the login password to confirm the entry. 6. Enter the characters shown in the graphics box near the bottom of the left column. This box helps confirm that a person, not a computer program, is creating the account. 7. Select two security questions to answer from the options at the top of the right column. Your answers are used to confirm your identity during subsequent visits to this site. Choose questions that you readily know the answers to (so that you can easily remember the answers). Note: The visual indicator below the password box indicates the relative strength of the password that you re creating. A longer password using mnemonics rather than recognizable words is stronger. To activate support by phone service, using a PIN code that you supply, 1. Enter the 10-digit phone number that you want to use for phone support. If the number applies to a mobile phone, select the This is a mobile phone check box. 2. Create a PIN code that you want to use for identification. The combination of the phone number and PIN you provide will be used for phone support or for authentication. 3. Retype the same PIN code to confirm you entered it correctly. To create the account, 1. Review your entries on this form to be sure the information is correct. 2. Click the I Agree to Terms and Conditions link to read the legal details that apply to this account. If acceptable, select the check box to confirm your acceptance. 3. Click Create Account to register your account information. The Service account server sends an message to the address you provided in order to validate the address. 9 Activating the Service
10 5. Check your inbox for the message, and then click the link contained in the message Complete Account Setup to finalize the account setup. The program notifies you that the account setup has been completed and provides a login link to access your account. Enrolling a PC to the Service After you have successfully created an account and logged in, the home page appears. Each PC that is covered by this Service needs to be individually enrolled. You can enroll a maximum of 10 computers per account. You must perform this step using the same PC that is being enrolled in the Service. Once enrolled, your service settings can be managed from any computer. 6. Click the here link to access the login screen for your new account. 7. Enter the address and login password that you previously created. If you have forgotten the password, you can click the Forgot your password? link to recover your password. To recover the password, you ll need to answer the security questions that were entered earlier. To enroll your PC, 1. From the home page, click Enroll PC. A warning screen appears that describes the importance of not losing the Unlock Password for the PC. 8. Click Login to proceed. The Welcome screen for the Intel Anti-Theft Service appears. 2. Read the information on the screen, and then select the I understand this message check box and then click Continue with Enrollment. The first page of the PC enrollment wizard appears displaying the defined PC Settings. 10 Activating the Service
11 3. Confirm that the Activation Code you received in the Intel Anti-Theft Service package correctly displays in the PC Details section. This code is automatically filled in for the first PC you enroll in the account. 4. Select a nickname for the PC that will make it easy to identify (for example, Joe s computer or Dad s computer ). 5. Create an Unlock Password of at least eight numbers. This will be the password used to reactivate your PC following a lockdown event (for example, if the PC is lost and then returned to you). 6. Retype the Unlock Password to confirm it is correct. 7. Enter the number of days before the Auto Lock is engaged. The range is 3 to 30 days. If you have not logged into the Internet after the number of days you specify, your PC will automatically go into lockdown. Once in lockdown mode, the PC cannot be used until you enter the Unlock Password. Refer to the section Recovering Your PC for more details about how to use the Unlock Password. Note: You can optionally enter a Locked PC message. The maximum message length is 50 characters. This message will appear as the first screen when a PC is in lockdown mode. For example, you might enter instructions for someone to contact you if your PC is located: If found, [email protected]. Keep in mind that any information that you enter here will be visible to someone who has stolen your PC. 8. Click Next to accept the entries on this page. Secure Data Vault provides an encrypted area on your PC s hard disk where confidential files can be securely stored. You can choose whether or not to create Secure Data Vault. Secure Data Vault lets you create containers, which display on your PC as drives identified by letters. When a drive is unlocked, you can freely move files in and out of this drive whenever you are using the PC, but if the PC is locked down all of the information in the containers is protected by encryption. To install Secure Data Vault, 1. Select the Install Secure Data Vault Drive on my PC check box. 2. Click Next to proceed to the next screen. Secure Data Vault will be installed on your PC after downloading the PC-based software in the next step. 11 Activating the Service
12 Installing the PC-based Software The Service PC-based software that is installed depends on the selections you make while enrolling your PC. The Services to be downloaded are displayed in the Install window as shown. To download the PC-based software, 1. Verify that the items that appear in the Install window are correct. If Secure Data Vault does not appear and you want to install it, click Back to return to the previous screen. You can also choose to install Secure Data Vault at a later time. 2. Click Download Now to download the selected services. A progress bar indicates the download is taking place. When complete, the License Agreement, the first page of the Intel Anti-Theft Service Setup Wizard, appears. 3. Use the arrow keys to scroll the License Agreement text and review. To agree to the terms, click Next to continue. The Select Installation Folder dialog box that appears shows the target folder for the installation. You can select a different folder using the Browse button. 4. Click Next to confirm your selections. 5. In most cases, you will want to select the Install Updates Automatically option. You can choose to receive the Service prompt for software upgrades, automatically upgrade the software whenever a new version is available, or take no upgrade action at all. 6. In the Confirm Installation dialog box that appears, click Next again to continue with the installation. A progress bar shows how the installation is proceeding. 7. When the installation is complete, click Next to continue. The Intel Anti-Theft Service Upgrade Policy screen appears. 12 Activating the Service
13 8. Select the appropriate upgrade policy and click Next. The Installation Complete dialog box appears, indicating that the software has been successfully installed on your PC. This activates the Service. 9. Click Close. Printing the Reference Screen When you have finished the installation, the Service displays a summary screen that lists important information that applies to your account. We recommend you print this screen and keep it in a safe location. It includes password details, the original Activation Code, your unlock password, and other details that are essential for using the features of the Service. 13 Activating the Service
14 Chapter 4: Using the Service Whether you have one PC or several enrolled in the Service, it is always easy to log on, check the current status of your enrolled PCs, make changes to passwords, view recent activities, and change the settings that apply to lockdown. When you log on to the Service, the initial screen displays the list of PCs that are currently enrolled. To change settings or view status, click the name of any of the PCs shown in this list. Configuring the Service To configure the PC settings, 1. In the PC Settings list, click the PC Nickname of the PC you would like to configure. If you enrolled only one PC, only one PC will be visible in the list. On the Settings tab for the selected PC, you can view and change the current settings for Auto Lock Timer and Locked Message. You can also change or retrieve your Unlock Password or retrieve your Secure Data Vault Password. 2. Make any necessary changes to the settings that are shown. For more details about an option, click the help symbol (?) next to the setting. 3. When you have finished changing the settings, click Save to confirm the changes and store the new values. These changes will be in effect the next time your PC synchronizes with the Service. 14 Using the Service
15 Installing Secure Data Vault Drive If you did not previously install the feature for Secure Data Vault on your PC, you can select the Install Secure Data Vault Drive on my PC check box to perform the installation from the settings page. If you select the check box to install Secure Data Vault, you should also assign a password for it. The first time you run Secure Data Vault you will need to create a password, and this information will be sent to the Service. You can return to this settings tab at any time retrieve your password if you forget it. Locking Your PC When you turn on a PC that is enrolled in the subscription service, that PC automatically communicates or synchronizes with the Service server while it is connected to the Internet. This connection confirms that all is well and that no lockdown requests have been received (by phone or Web). If the lock or theft protection mode for the PC is activated, one cannot go farther than the initial screen where the Unlock Password is required. Triggering the Lock/Theft Protection Mode Locking Your PC Automatically The PC goes into a lockdown state if there has been no communication to the Service server within a number of days (as specified by the Auto Lock Timer setting). You can set the number of days allowed before this action takes place by going to the Settings page. Note: Internet access is required to complete the Service server synchronizations. For example, if your PC is lost during travel on an airline and is sent to lost and found, after the set number of days passes without a network connection, it will lock down. If you set the lockdown value at 4 days, if the PC is powered up on day 5, it will be in lockdown mode. Requesting Lock PC Mode To lock down a PC, 1. From the Service home page, click the name of the selected PC. The values that apply to that PC display on a tabbed dialog box. 2. Click the Lock/Unlock PC tab. The Lock/Unlock PC dialog box appears. 3. Click the red Lock PC button. A dialog box appears asking to confirm the lockdown state. Tip: To strengthen the security protection, configure your PC so that the WLAN connection can be completed before Microsoft Windows* starts. This allows the contact with the Service server to be made (and any recent changes to the settings to be implemented). 15 Using the Service
16 4. Click Confirm to lock your PC. The dialog box confirms the PC is locked. The lock request will be delivered to the PC the next time your PC synchronizes with the server. Note: You can also lock down your PC by phone. Refer to Getting Automated Phone Support for details. Viewing the History The Service maintains a history of activities relating to each enrolled PC. You can check this history at any time to see what activities have taken place. To view the PC history, 1. From the Service home page, click the name of the selected PC. The values that apply to that PC are shown on a tabbed dialog box. 2. Click the History tab. The Service history for the selected PC appears. The date for each individual event is shown, as well as the IP address from which the event was initiated. 3. When you have finished viewing the events, click Close to return to the previous dialog box. 16 Using the Service
17 Checking Status through the Notification Area Icon When the PC-based software for the Service has been installed on your PC, an icon appears in the Windows notification area (at the far right of the taskbar). This icon changes to reflect current status and to provide security-related notifications. The following table describes the range of notifications and the icons in use. Icon Icon state Notification Action Red Indicates that less than 24 hours remain before server contact is needed. Log on to the Internet within the 24-hour window to avoid having the system lock. Pop-up balloon Appears once each hour, counting down the time before the PC automatically locks up. When less than 45 minutes remain, the balloon pops up every 15 minutes. Log on to the Internet within the time specified to avoid having the system lock. Gray Indicates the Service is currently suspended. No action needed. Missing icon Default icon If no icon is visible in the system tray, the PC has been unsubscribed from the Service. Indicates the Service is enabled and monitoring conditions. Re-enroll if service is needed. No action needed. Note: The notification area icon may not be visible. Click the up arrow to view the visible icons. 17 Using the Service
18 Right-Clicking the Notification Area Icon If you right-click the notification area icon for the client application, you can access a menu that controls these options: Open Secure Data Vault (if closed) or Close Secure Data Vault (if open). Provides access to password-protected encrypted containers that you have created with the Secure Data Vault feature. Synchronize Settings with Server. Forces synchronization with the Service server to check status and update settings. Software Update Settings. Lets you select the manner in which updates are handled. Options include Install Updates Automatically, Notify Me When an Update is Available, and Don t Automatically Check for Updates. The command Check Now when selected immediately performs the check for updates. Show EULA. Displays the End User License Agreement. Server Synchronization Status. Indicates the current details related to the server synchronization operations. About. Provides information about the Service client application. Exit. The Service client application exits and the icon disappears from the tray. The client and system tray icon are again available the next time the PC boots. Using the Help Menu You can obtain help when logged in to the Service by clicking the Help button near the top of the main screen. The Help window that appears offers answers to common questions and provides concise procedures for tasks such as creating a user account and enrolling a new PC. Viewing Tooltips Many of the options displayed in the Service screens use tooltips to provide a quick description of a field or feature. To view tooltips, let the cursor hover over an item for two or three seconds and, if a tip is available, a pop-up description will appear. 18 Using the Service
19 Chapter 5: Using Secure Data Vault If you installed Secure Data Vault either when you initially set up your Service and enrolled your PC or at a later date you can create a protected area on your hard disk that is passwordprotected and encrypted. Secure Data Vault offers additional protection for any private or sensitive information stored on your PC. When the Secure Data Vault option has been installed, you can create an encrypted container, which appears as a drive on your PC mapped to a letter that you assign to it (for example, drive E). When you start Secure Data Vault for the first time, you will need to create a password and the encrypted data can be accessed only if the password is supplied. Note: We strongly recommend that you regularly back up the files in your Secure Data Vault using your favorite backup utility. You can also back up the entire encrypted container, but the container is typically large and could require a significant amount of time and space for the back-up process. Information in this backup will have the same encryption and password protection as the encrypted container that you created on your hard disk. If your PC is stolen or lost, you can recover the information from the backup using the data recovery tool. Opening Secure Data Vault When Secure Data Vault is open, you can create containers and copy files into them. When the vault is closed, the files are encrypted and cannot be viewed unless the correct password is provided. To open Secure Data Vault, 1. Locate the application for Secure Data Vault on your Start Menu and click its icon. 2. If you have not already created a password to access Secure Data Vault, the program will ask you to create one at this time. Enter the password you want to use and confirm this entry in the next field. Click OK to continue. 19 Using Secure Data Vault
20 3. If you have already created a password, each time you begin to open Secure Data Vault, the program requires that you enter it. In the Login to Secure Data Vault dialog box, type the password, and then click Login. 4. In the window that appears, select the name of To create a new encrypted container, 1. Select the application for Secure Data Vault from the Start Menu on your PC. 2. From the main window, select New. The Create New Encrypted Container dialog box appears. the container that you want to open. Click the Open icon to make the container, associated with the drive letter you assigned, available for use. If you haven t yet created any containers, the next section explains how to do so. Creating an Encrypted Container You can create as many containers as you want within Secure Data Vault. 3. Create a name for the new container and designate a folder in which to store it. By default, the encrypted container is stored in your My Documents folder on drive C. Use the Browse button to select a different folder anywhere on your system. 4. Specify a size for the container in the Size entry field. Make sure that you leave adequate space on your disk drive for other applications and normal operations. Note: If you choose to back up the entire container, the size of the container will determine the time and space that the backup will take. To expedite backup time and to save space, you can back up your files instead of the entire container. A large container typically requires a significant amount of time and space to backup. 5. In the Assign drive letter field, specify the letter drive you want to use. 6. Click Create to name and create the encrypted container. The drive that you assigned to the container and the status will be shown in the window for Secure Data Vault. 20 Using Secure Data Vault
21 Closing Secure Data Vault To close Secure Data Vault, 1. Once you re done using Secure Data Vault and you ve finished copying files in or out of containers, select any open containers that you d like to close from the displayed list. 2. Click the Close icon to close and lock the selected container. 3. Click the Logout icon to exit from the application for Secure Data Vault. Recovering Secure Data Vault Information If your PC is lost, stolen, or suffers a hard disk drive failure, you can recover the data stored in your Secure Data Vault if you have a backup file available. 7. While the status of the container is Open, you can move files in and out of it as you would with any disk drive using those Microsoft Windows tools that are most convenient. Files are encrypted from the time they are moved into the vault. 8. Click the Close icon to return the vault to password protection. 9. Click the Logout icon to exit from the application. To restore Secure Data Vault on a replacement PC 1. On your replacement PC, restore the data backup of the Secure Data Vault encrypted container to the My Documents folder. 2. Log in to the Service, and then click the Maintenance tab. Note: You can include the path for each Secure Data Vault encrypted container in your regular backup operations, but the entire container will be backed up. This should be the path where Secure Data Vault was originally created (for example: C:\User\Administrator\Documents\ SDVContainers). The data contained in the backup will also be encrypted, and it can be recovered using the recovery procedure described in the following section. 3. Click Download Tool to download the data recovery tool for Secure Data Vault. 4. When the download is complete, double-click the tool to open it. If you ve restored the container files to My Documents, the recovery program will automatically recognize and register them. 21 Using Secure Data Vault
22 5. Open any of the displayed containers and copy the recovered content to any appropriate location on your hard drive or other media. If your replacement PC includes Intel Anti-Theft Technology capabilities and you have service time remaining, you can optionally enroll the PC in the Service at this time. To restore Secure Data Vault onto your PC following hard disk replacement, 1. Complete the installation of the new hard disk drive or operating system upgrade. 2. Restore the data backup of an encrypted container made by Secure Data Vault to the My Documents folder on your PC. 3. Log in to the Service and reinstall Secure Data Vault for your PC. 4. When the software has been installed, open the Secure Data Vault application. Your encrypted container files that have been copied to the My Documents folder are visible and ready to access. If your PC has been repaired, had changes to its motherboard, or had the BIOS re-flashed (causing the PC to become un-enrolled), the system may be returned in a suspended state. When you resume the Service, we recommend that you change your password. To restore Secure Data Vault on your PC after a repair, 1. Restore the data backup of the container made by Secure Data Vault to the My Documents folder on your PC. 2. Log in to the Service, and then open the Maintenance tab for the selected PC. 3. Click Download Tool to download the data recovery tool for Secure Data Vault. 4. When the download is complete, double-click the tool to open it. If you ve restored the container files to the My Documents folder, the recovery program will automatically recognize and register them. 5. Open any of the displayed containers and copy the recovered content to any appropriate location on your hard drive or other media. 22 Using Secure Data Vault
23 Retrieving the Password for Secure Data Vault If you lose or forget the password to Secure Data Vault, you can retrieve it as long as your Service subscription is active. To retrieve the password for Secure Data Vault, 1. Log in to the Service and then click the PC Nickname for the selected PC (on which Secure Data Vault is stored). 2. Click Retrieve Password. A message containing a link is sent to your current address. 3. Open the message, and then click the link provided. 4. Answer the security questions on the screen that appears. The program then lets you view the current password. Note: You can change the password for Secure Data Vault by selecting the Change Password check box at the time you log in to Secure Data Vault. The program will provide a second field to confirm the newly entered password. The next time the client application synchronizes with the Service, this new password will be stored on the server. You can then retrieve it whenever necessary using the preceding procedure. Note: If your subscription is not active, your Secure Data Vault is in read-only mode and you cannot recover your password. For more details, refer to Chapter 7: Suspending or Cancelling Service. 23 Using Secure Data Vault
24 Chapter 6: Recovering Your PC If your PC is lost or stolen, it can be locked in one of three ways: By logging into the Service and using the Lock PC command By the PC failing to connect with the Service for the set number of days in the Auto Lock timer By issuing a Lock PC command by phone using Customer Support Unlocking from the Web If your locked PC is recovered, you can return it to normal operation by first setting the PC to unlock on the Web and then entering the Unlock Password on the locked PC. To unlock the PC on the Web, 1. Log in to the Service, and then click the name of the selected PC. The values that apply to that PC are shown on a tabbed dialog box. 2. From the Lock/Unlock PC tab, click Unlock PC. 3. Click Close to exit the tab. 4. The next time the specified PC communicates with the Service, it will be unlocked for your use. Entering the Unlock Password To enter the Unlock Password, 1. Turn on your PC. If the PC has been locked, a screen will appear from the BIOS that requests the recovery passphrase, such as the following: 2. Enter 1 (to use a passphrase). 3. Enter the passphrase (your Unlock Password). If the password is correct, the PC completes the startup process. 24 Recovering Your PC
25 Retrieving the Unlock Password If you forget the Unlock Password, you can retrieve it from the Service. To retrieve the Unlock Password for an enrolled PC 1. Log in to the Service, and then click the name of the selected PC. The values that apply to that PC are shown on a tabbed dialog box. 2. From the Settings tab, click Retrieve Password (to the right of the Unlock Password check box). 3. A message with a link is sent to your registered address. Click the link and then answer the security questions. 4. The Service displays your Unlock Password. Click OK to return to the previous screen. Recovering the Service In certain situations, your subscription to the Service may be current, but you may not be able to access it because of disk drive corruption, a hard disk change, or other system changes. To continue using the Service, you will need to log in and reinstall the necessary software. To recover the Service, 1. Log in to the Service at ATService.intel.com using your current password. 2. Click Help. 3. Click Reinstall Intel Anti-Theft Service on an enrolled PC. 25 Recovering Your PC
26 Chapter 7: Suspending or Cancelling Service Depending on circumstances, you may want to temporarily suspend the Service. For example, if you take your PC in for service, you don t want it to lock while being repaired. In such cases, you can use the Suspend feature to temporarily discontinue service and then use Resume when you return to re-activate the anti-theft coverage. You can also choose to unsubscribe, which cancels service for the PC. If you unsubscribe a PC from the Service, you will have to re-enroll it before protection will be available again. Note: While suspended, your PC does not respond to automatic lockdowns or lock requests. As an alternative to suspending services, you can extend the number of days as part of the Automatic Lock Time settings beyond the anticipated period of PC inactivity. To operate from Suspend Mode, 1. Starting from Shutdown or Hibernate mode, the PC will show the following: Suspending Service To suspend service, 1. Log in to the Service, and then click the name of the PC that you want to suspend. 2. Click the Suspend tab. 3. Click the Suspend button. The Service asks security questions before continuing. The Service suspension takes place the next time the PC-based software synchronizes with the Service. Note: Changes made on the Suspend tab are not applied on your PC until after synchronization with the Service server. To synchronize immediately, right-click the Intel Anti-Theft Service icon and click Synchronize Settings with Server. 2. Type n, and then press Enter. The PC will resume normal operation. To resume service, 1. Log in to the Service, and then click the name of the PC for which you want service resumed. 2. Click the Suspend tab. 3. Click the Resume button. The Service is resumed and the timers for the automatic lockdown settings that you have specified begin counting once more. 26 Suspending or Cancelling Service
27 Unsubscribing You can cancel your subscription at any time. Unsubscribing turns off the theft protection features for your PC. To unsubscribe from the Service, 1. Log in to the Service, and then click the name of the selected PC. The values that apply to that PC are shown on a tabbed dialog box. 2. Click the Suspend tab. 3. To cancel the subscription service, click Unsubscribe and then answer the security questions that appear. 4. Confirm this change in the dialog box that appears. You can re-activate the Service subscription by supplying the original Activation Code within the time limit of your original subscription period. If you unsubscribe, files that you have stored in Secure Data Vault will still be protected, but without hardware security. We recommend that you move your secure data out of Secure Data Vault to another location before you unsubscribe. Note: Changes made on the Suspend tab, including Unsubscribe, are not applied on your PC until after the next synchronization with the Service server. To synchronize immediately, right-click the Intel Anti- Theft Service icon and click Synchronize Settings with Server. 27 Suspending or Cancelling Service
28 Chapter 8: Contacting Customer Support Support Options If you need answers to questions not covered in this manual, or you would like to configure your PC (such as locking your PC) with the help of an agent, visit the ATservice.intel.com site and click Support/Contact Us. The options provided let you: 1. questions about the Service or provide feedback 2. Chat with a live agent (during certain hours) 3. Call Customer Support. Individual phone numbers for each country or region are listed on the site, ATservice.intel.com. To talk to a service representative, 1. Call the phone number for your country or region. A full list of current numbers appears on the ATservice.intel.com site. Click Support/ Contact Us to find the appropriate number. 2. Enter the phone number that you provided when you enrolled your PC. 3. Enter the 4-digit PIN code that you created at that time. 4. Select Talk to Agent from the options given. 5. Explain the nature of your request to the service representative. Note: If you have multiple PCs, you must first select the correct PC to continue. Several other functions are available by phone, including Lock, PC Status, Retrieve Login Password, and Talk to Agent. Follow the voice prompts to access the services that you need. Planned Automated Phone Support To obtain automated phone-based support (when available), 1. Call the phone number for your country or region. A full list of current numbers appears on the ATservice.intel.com site. Click Support/Contact Us to find the appropriate number. 2. Enter the phone number that you provided when you enrolled your PC. 3. Enter the 4-digit PIN code that you created at that time. 4. Follow the voice prompts. Note: Automated phone support is currently not available. To lock your PC or perform other functions using your phone, call Customer Support. Individual phone numbers for each country are listed on the site, ATservice.intel.com. Note: You will receive support from the retailer from whom you purchased the PC. They will have their own privacy guidelines. 28 Contacting Customer Support
29 Chapter 9: FAQ What is Intel Anti-Theft Service? The Service helps consumers protect their PC and data from theft. This Service uses Intel Anti- Theft Technology (Intel AT) as a foundation and provides added security built into the chipset. Additionally, this service lets you use an optional feature called Secure Data Vault on your PC where private files can be encrypted and stored. What is Intel Anti-Theft Technology? Intel AT locks down your PC if it s lost or stolen and helps secure sensitive information stored on the PC s hard drive. Intel AT has these benefits: Built-in protection for added peace of mind: This technology is built into Intel s chips so reformatting or replacing the hard drive will not defeat the lock. Easy to disable the PC locally or remotely when lost: Lock down your PC if it is lost or stolen. A locked PC cannot be used by a thief, but can be easily unlocked by its owner. PC theft deterrence: The Intel AT sticker warns thieves that the PC has added protection. This can help in deterring theft. How is privacy protected for the enrollment and account information? All user information is stored in encrypted form on the Service server. Does the Service include recovery of a lost or stolen PC? The Service does not provide recovery of lost or stolen PCs. Guaranteed PC recovery is not feasible, so the Service focuses on deterring theft and then disabling stolen PCs and protecting their data. Your customized lock message may make it possible for someone to return your PC. Account Settings Why do I have to create an account? You must create an account to use the Service to control security, validate your identity, and assist in performing lock and unlock procedures. The activation code is used to create an account. Who can see my account information? Only the valid account holder and customer support representatives for the Service can view account information. Users must log in to the Service Web site to view information about any PCs that have been enrolled in the Service. Additional information about the current account settings appears in the Account Settings window on the Web site, which can be accessed by answering the authentication questions (based on the information supplied initially by the user). How is my account information used? Account information such as your address is used by the Service to notify you of relevant information about your enrolled PC. The phone number that you provide when registering is used for identification when you contact the call center. 29 Frequently Asked Questions
30 How is my address used? Your address is the basic means for communication with the Service. Messages are generated to the address you provide to confirm and validate certain operations, such as resetting your account password, retrieving a password, providing warnings about missed synchronizations with the server, issuing service expiration notices, and so on. How can I change my address? To change your address, log in to the Service, select Account Settings, and answer the authentication questions to gain access. You can change your address on the screen that appears. What is the Login Password? The Login Password controls access to your Service account. You must supply this password each time you visit the Web site. How do I change my Login Password? To change your login password, click the Account Settings button on the home page and answer the authentication questions to gain access. You can make the changes in the window that appears. You can also reset the password using the Forgot Password option on the home page of the Web site. The Service sends a message to your registered address. When you receive the message, follow the link contained in it to complete the password reset process. You will need to answer authentication questions to confirm the reset. How are my Login Password and Unlock Password different? The Login Password gives you access to log in to the Service. The Unlock Password is used only in situations where your PC is locked down and you want to unlock it (for example, if the Auto Lock Timer is triggered after the set number of days, which would lock down the PC). An additional password that applies to Secure Data Vault is also kept available for retrieval on the site. How do I choose a strong Login Password? A strong login password consists of: At least 8 characters One or more numerals An uppercase and lowercase character A special character The password does not start with a question mark (?) or exclamation mark (!), or 3 repeating characters at the beginning When you first create your Login Password, a graphic gauge below the password entry box dynamically shows the strength of the password as you add characters. What are Authentication Questions? Authentication questions are combinations of questions and answers that you define as a user when you register. They provide extra security whenever you are accessing or changing sensitive information within your account. We recommend that you memorize the answers to the questions and keep them secret to maintain the security of your account. Why do I have to register my phone number? Your registered 10-digit phone number is used for identification when obtaining customer support. Which phone number should I register? I have many. We recommend that you use a mobile phone if you have one. Otherwise, use a phone number where you are frequently available. 30 Frequently Asked Questions
31 What is the PIN code? The PIN code is used for getting support during an Interactive Voice Response session. The PIN must consist of four digits. I already have an account. Can I add a new PC to it? Any current subscriber with a valid account can add up to 10 PCs as long as an activation code is available for each enrolled PC. To add a PC to your account, log into your account, and use the Enroll PC button on the Service home page. Theft Policy Settings What does the term Auto Lock Timer mean? Each day that a PC does not communicate with the Service server counts as one day toward automatic lockdown, based on the Auto Lock Timer value that has been set. For example, if the timer value is set to 10 days and your PC doesn t communicate with the server on the Internet for 6 days, the notification area icon will notify you that 4 days until automatic lock remain. You can use your Unlock Password if your PC is locked down inadvertently. What does Locked PC Message mean? The Locked PC Message that you specify when enrolling a PC gets displayed by the BIOS if the PC has been locked down and someone tries to start it. What is Unlock Password? Use the Unlock Password to gain access to a PC that has been locked down. This password is set during the PC enrollment process. How do I change my Unlock Password? To change the Unlock Password, log in to the Service, and then go to the Settings tab. Click the Change button to enter a new password. I forgot my Unlock Password. How can I retrieve it? To retrieve your Unlock Password, log in to the Service, and then go to the Settings tab. Click the Retrieve Password button to enter a new password. The Service generates an message containing a link. Click the link to complete the process, which includes answering authentication questions to validate your identity. The Unlock Password is displayed for two minutes. You can also recover your Unlock Password by contacting the Interactive Voice Response support line. Secure Data Vault What is Secure Data Vault? Secure Data Vault is a data protection service that lets you create an encrypted container on your PC s hard drive where sensitive files can be protected and stored. Can I add Secure Data Vault later? Yes. To add Secure Data Vault to your enrolled PC, go to the Settings tab and select the Install Secure Data Vault Drive on my PC check box. When you click the Save button, the Service installs Secure Data Vault on your PC. Does Secure Data Vault protect all the data on my PC? No. Secure Data Vault protects only the files that are copied to it. How does it prevent others from seeing my data? The encrypted data stored in Secure Data Vault can be accessed and decrypted only by supplying a password. Only an authenticated user can access the files stored in the vault. 31 Frequently Asked Questions
32 What kind of files or data should I store here? Secure Data Vault can be used to store any kind of files or documents that you want to protect from unauthorized viewing. This might include bank or credit card information, passwords for other accounts, personal information that might be used for identity theft, or anything you would like to encrypt. Unlock Password How do I lock a lost or stolen PC? To lock a lost or stolen PC, log in to the Service, go to the Lock/Unlock PC tab for the enrolled PC, and click the Lock button. Following the next synchronization with the server (if someone tries to start up the PC), the PC will be locked by the Service. You can also use Interactive Voice Response support to lock a PC. How do I unlock a PC? Turn on the PC and enter the Unlock Password on the BIOS screen that appears. Then, log in to the Service, go to the Lock/Unlock PC tab for the enrolled PC, and click the Unlock button. Following the next synchronization with the server, the PC will be unlocked by the Service. If you forget to perform this step, the server will lock down the PC the next time it synchronizes with it. How do I suspend or resume the Service? To suspend service, log in to the Service, and then click the name of the PC that you want to suspend. Click the Suspend tab, and then click the Suspend button. While suspended, your PC does not respond to automatic lockdowns or lock requests. Note that you will need to answer the security questions to suspend service. To resume service, log in to the Service, and then click the name of the PC for which you want to resume service. Click the Resume tab, and then click the Resume button. How do I view the history for an enrolled PC? To view the Service history for a PC, log in to the Service, select an enrolled PC, and click the History tab. The last 50 events related to this PC will be displayed. How do I unsubscribe a PC from the Service? Log in to the Service, and then click the name of the selected PC. Click the Suspend tab. Click the Unsubscribe button in the dialog box that appears. The next time the server synchronizes with the PC, the PC subscription will be terminated. Note that you will need to answer the security questions to unsubscribe from the Service. 32 Frequently Asked Questions
33 Appendix Installing Java* Runtime Environment v6 The Service requires that Java* Run Time Environment (JRE) version 6 be installed for Web pages to be viewed properly. If JRE v6 is not installed you may see a blank screen when trying to access a page or the following dialog box may appear in your browser window. In most cases, Java will already be installed and enabled for your browser, but if you receive a message that Java is needed to continue, complete the installation in the following manner. To install JRE v6 in Internet Explorer* 1. Click the Windows Start button, and then click Internet Explorer. The browser window appears. 2. Access the Java.com Web site. 3. Click the Free Java Download button. The File Download Security Warning appears. 4. Click Run to continue. The installer provides more details about the software. 5. Click Run to confirm. The Welcome to Java dialog box appears. 6. Click Install to proceed with the installation. A progress bar tracks the downloading and installation of the software. 7. After the installation has finished, restart the computer to enroll in Intel Anti-Theft Service. With Java installed, you should have full access to all pages on the Service site. Checking Browser Compatibility The Service works with the following browser: Microsoft Internet Explorer version 8 33 Appendix
34 Glossary Account Password. When you first create your Service account, you assign a password to control access to it through the Service Web site. Protect this password carefully, since it is the primary means of locking and unlocking your PC and setting the options that apply to your account. BIOS (Basic Input/Output System). A program stored within your PC that controls startup operations and configures the PC for use by the operating system. If your PC is locked down by the Service, the complete startup operation can t proceed unless the Unlock PC password is provided, preventing a thief from loading the operating system to access the files on your PC. Encryption. A process by which data in a computer is concealed for security by means of a code or cipher. The encrypted data becomes unreadable unless a key is supplied to access it (which can be tied to a password or other means of authenticating a user s identity). Encrypted Container. A protected area on your hard disk drive that you create using Secure Data Vault. To your PC, the area looks like a normal drive with a drive letter but the information within it is encrypted and protected by a password. Intel Anti-Theft Technology. Security features built into select 2nd generation Intel Core processor family products that can protect sensitive data by blocking the boot process at startup. Secure Data Vault. Technology that creates a protected area on a computer that can be used to store personal information in an encrypted format. Secure Data Vault password. The password you create when you make a Secure Data Vault using the PC-based software installed on your PC. This password, which controls access to the encrypted data, is also stored on the server of the Service so that you can log in and access it, if needed. Server Synchronization. A scheduled communication exchange between the PC and the Service that compares settings, evaluates current conditions, and determines whether the PC should be locked for security reasons. Unlock Password. A password that you create through the Service that must be supplied to access a PC that has been locked down for protection. This password should be carefully stored in a place where it can t be stolen and where it is available if the PC is locked. If you lose it, your PC may be unrecoverable. 34 Glossary
35 35
36 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. UNLESS OTHERWISE AGREED IN WRITING BY INTEL, THE INTEL PRODUCTS ARE NOT DESIGNED NOR INTENDED FOR ANY APPLICATION IN WHICH THE FAILURE OF THE INTEL PRODUCT COULD CREATE A SITUATION WHERE PERSONAL INJURY OR DEATH MAY OCCUR. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked reserved or undefined. Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. The information here is subject to change without notice. Do not finalize a design with this information. The products described in this document may contain design defects or errors known as errata which may cause the product to deviate from published specifications. Current characterized errata are available on request. Contact your local Intel sales office or your distributor to obtain the latest specifications and before placing your product order. Copies of documents that have an order number and are referenced in this document, or other Intel literature, may be obtained by calling , or go to: Intel Anti-Theft Technology (Intel AT): No system can provide absolute security under all conditions. Intel AT requires an enabled chipset, BIOS, firmware, software, and a subscription with a capable Service Provider such as Intel Anti-Theft Service. Consult your system manufacturer for availability and functionality. Intel assumes no liability for lost or stolen data and/or systems or any other damages resulting thereof. For more information, visit If your system is enrolled in the Intel Anti-Theft Service (the Service ), you must regularly connect your enrolled computer system to the Internet so that it can synchronize with the Service s system server. Lack of regular synchronization with the Service s system server can lead to your enrolled computer system being locked down which will require you to use your unlock password to unlock your computer system. Copyright 2011 Intel Corporation. All rights reserved. Intel Corporation, 2200 Mission College Blvd., Santa Clara, CA 95054, USA. Intel, the Intel logo, and Intel Anti-Theft Technology, and Intel Core are trademarks of Intel Corporation in the US and other countries. These materials are provided through ATservice.intel.com as a service to its customers and may be used for informational purposes only. Intel Anti-Theft Service is a service provided by Intel Corporation and/or its subsidiaries. *Other names and brands may be claimed as the property of others. 0911/JKO/MESH 36
Personal Vault. User Guide
 Personal Vault User Guide i Contents McAfee Personal Vault 3 Personal Vault features... 4 Getting started... 5 Using McAfee Personal Vault... 6 The First-Use wizard: Step 1... 8 The First-Use wizard:
Personal Vault User Guide i Contents McAfee Personal Vault 3 Personal Vault features... 4 Getting started... 5 Using McAfee Personal Vault... 6 The First-Use wizard: Step 1... 8 The First-Use wizard:
User Guide. Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved.
 Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved. Table of Contents Getting Started... 4 New Features... 4 System Requirements... 4 Configuring Microsoft Internet Explorer... 4 Configuring
Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved. Table of Contents Getting Started... 4 New Features... 4 System Requirements... 4 Configuring Microsoft Internet Explorer... 4 Configuring
NovaBACKUP. Storage Server. NovaStor / May 2011
 NovaBACKUP Storage Server NovaStor / May 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
NovaBACKUP Storage Server NovaStor / May 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
PaymentNet Federal Card Solutions Cardholder FAQs
 PaymentNet Federal Card Solutions It s easy to find the answers to your questions about PaymentNet! June 2014 Frequently Asked Questions First Time Login How do I obtain my login information?... 2 How
PaymentNet Federal Card Solutions It s easy to find the answers to your questions about PaymentNet! June 2014 Frequently Asked Questions First Time Login How do I obtain my login information?... 2 How
Online Sharing User Manual
 Online Sharing User Manual June 13, 2007 If discrepancies between this document and Online Sharing are discovered, please contact [email protected]. Copyrights and Proprietary Notices The information
Online Sharing User Manual June 13, 2007 If discrepancies between this document and Online Sharing are discovered, please contact [email protected]. Copyrights and Proprietary Notices The information
Xythos on Demand Quick Start Guide For Xythos Drive
 Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005
 BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005 PLEASE NOTE: The contents of this publication, and any associated documentation provided to you, must not be disclosed to any third party without
BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005 PLEASE NOTE: The contents of this publication, and any associated documentation provided to you, must not be disclosed to any third party without
Expertcity, Inc. GoToMyPC User s Guide. GoToMyPC User s Guide. Version 3.0
 GoToMyPC User s Guide Version 3.0 Expertcity, Inc 2002 Expertcity, Inc. All Rights Reserved. 5385 Hollister Avenue Santa Barbara, CA 93111 Voice: 805.690.6400 Fax: 805.690.6471 Contents Getting Started...
GoToMyPC User s Guide Version 3.0 Expertcity, Inc 2002 Expertcity, Inc. All Rights Reserved. 5385 Hollister Avenue Santa Barbara, CA 93111 Voice: 805.690.6400 Fax: 805.690.6471 Contents Getting Started...
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Seagate Manager. User Guide. For Use With Your FreeAgent TM Drive. Seagate Manager User Guide for Use With Your FreeAgent Drive 1
 Seagate Manager User Guide For Use With Your FreeAgent TM Drive Seagate Manager User Guide for Use With Your FreeAgent Drive 1 Seagate Manager User Guide for Use With Your FreeAgent Drive Revision 1 2008
Seagate Manager User Guide For Use With Your FreeAgent TM Drive Seagate Manager User Guide for Use With Your FreeAgent Drive 1 Seagate Manager User Guide for Use With Your FreeAgent Drive Revision 1 2008
McAfee Endpoint Encryption 7.0 Users Guide and FAQ
 McAfee Endpoint Encryption 7.0 Users Guide and FAQ Table of Contents Introduction... 1 Installation... 1 Boot-Up/Login... 1 Encryption Status... 3 Notes for Encryption... 4 Changing Your Password... 4
McAfee Endpoint Encryption 7.0 Users Guide and FAQ Table of Contents Introduction... 1 Installation... 1 Boot-Up/Login... 1 Encryption Status... 3 Notes for Encryption... 4 Changing Your Password... 4
User Guide. Active Online Backup - Secure, automatic protection
 Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Active Online Backup - Secure, automatic protection 1. Quick Setup... 1 2. Backup Selecting Folders and Files... 2 3. Backup - Changing Selected Folders and Files... 3 4. Checking on Your Backups... 4
Windows XP Pro: Basics 1
 NORTHWEST MISSOURI STATE UNIVERSITY ONLINE USER S GUIDE 2004 Windows XP Pro: Basics 1 Getting on the Northwest Network Getting on the Northwest network is easy with a university-provided PC, which has
NORTHWEST MISSOURI STATE UNIVERSITY ONLINE USER S GUIDE 2004 Windows XP Pro: Basics 1 Getting on the Northwest Network Getting on the Northwest network is easy with a university-provided PC, which has
2. To encrypt the drive for future use, click Yes (Fig 1, 2). This will start the encryption process.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
CTERA Agent for Windows
 User Guide CTERA Agent for Windows May 2012 Version 3.1 Copyright 2009-2012 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Windows May 2012 Version 3.1 Copyright 2009-2012 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
Vodafone PC SMS 2010. (Software version 4.7.1) User Manual
 Vodafone PC SMS 2010 (Software version 4.7.1) User Manual July 19, 2010 Table of contents 1. Introduction...4 1.1 System Requirements... 4 1.2 Reply-to-Inbox... 4 1.3 What s new?... 4 2. Installation...6
Vodafone PC SMS 2010 (Software version 4.7.1) User Manual July 19, 2010 Table of contents 1. Introduction...4 1.1 System Requirements... 4 1.2 Reply-to-Inbox... 4 1.3 What s new?... 4 2. Installation...6
U.S. Bank Secure Mail
 U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
ASUS WebStorage Client-based for Windows [Advanced] User Manual
![ASUS WebStorage Client-based for Windows [Advanced] User Manual ASUS WebStorage Client-based for Windows [Advanced] User Manual](/thumbs/40/21159954.jpg) ASUS WebStorage Client-based for Windows [Advanced] User Manual 1 Welcome to ASUS WebStorage, your personal cloud space Our function panel will help you better understand ASUS WebStorage services. The
ASUS WebStorage Client-based for Windows [Advanced] User Manual 1 Welcome to ASUS WebStorage, your personal cloud space Our function panel will help you better understand ASUS WebStorage services. The
Help. F-Secure Online Backup
 Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry GO!Enterprise MDM Version 4.11.x GO!Enterprise MDM for BlackBerry 1 Table of Contents GO!Enterprise MDM for
GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry GO!Enterprise MDM Version 4.11.x GO!Enterprise MDM for BlackBerry 1 Table of Contents GO!Enterprise MDM for
Kansas City Scout. Subscriber s Guide. Version 1.0
 Kansas City Scout Subscriber s Guide Version 1.0 November 15, 2010 TABLE OF CONTENTS 1 INTRODUCTION... 1-1 1.1 Overview... 1-1 2 SYSTEM DESCRIPTION... 2-1 2.1 System Overview... 2-1 2.1.1 Information Services...
Kansas City Scout Subscriber s Guide Version 1.0 November 15, 2010 TABLE OF CONTENTS 1 INTRODUCTION... 1-1 1.1 Overview... 1-1 2 SYSTEM DESCRIPTION... 2-1 2.1 System Overview... 2-1 2.1.1 Information Services...
Getting Started with WebEx Access Anywhere
 Getting Started with WebEx Access Anywhere This guide provides basic instructions to help you start using WebEx Access Anywhere quickly. This guide assumes that you have a user account on your meeting
Getting Started with WebEx Access Anywhere This guide provides basic instructions to help you start using WebEx Access Anywhere quickly. This guide assumes that you have a user account on your meeting
User Guide. CTERA Agent. August 2011 Version 3.0
 User Guide CTERA Agent August 2011 Version 3.0 Copyright 2009-2011 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written permission
User Guide CTERA Agent August 2011 Version 3.0 Copyright 2009-2011 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written permission
ScoMIS Encryption Service
 Introduction This guide explains how to install the ScoMIS Encryption Service Software onto a laptop computer. There are three stages to the installation which should be completed in order. The installation
Introduction This guide explains how to install the ScoMIS Encryption Service Software onto a laptop computer. There are three stages to the installation which should be completed in order. The installation
Kaspersky Password Manager
 Kaspersky Password Manager User Guide Dear User, Thank you for choosing our product. We hope that you will find this documentation useful and that it will provide answers to most questions that may arise.
Kaspersky Password Manager User Guide Dear User, Thank you for choosing our product. We hope that you will find this documentation useful and that it will provide answers to most questions that may arise.
Encrypt USB Drive to Protect Data
 Encrypt USB Drive to Protect Data Enable BitLocker on USB Flash Drives to Protect Data Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external
Encrypt USB Drive to Protect Data Enable BitLocker on USB Flash Drives to Protect Data Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external
Only smart people read the manual.
 Only smart people read the manual. Contents Getting Started... 1 Installing the FreeAgent Tools... 1 Using the FreeAgent Tools Icons... 9 Using the System Tray Icon... 10 Disconnecting the FreeAgent Drive...
Only smart people read the manual. Contents Getting Started... 1 Installing the FreeAgent Tools... 1 Using the FreeAgent Tools Icons... 9 Using the System Tray Icon... 10 Disconnecting the FreeAgent Drive...
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216
 Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Getting Started. Getting Started with Time Warner Cable Business Class. Voice Manager. A Guide for Administrators and Users
 Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
VMware Horizon FLEX User Guide
 Horizon FLEX 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8)
 BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
BitLocker to Go: Encryption for personal USB flash drives (Windows 7 and 8) Encryption is an effective method of protecting data stored on portable devices such as USB flash drives and external hard drives.
2 Main window...7. 3 Backing up to Acronis Online Storage...9 3.1 Log in to the online storage... 9 3.2 Computer selection...10
 User's Guide Table of contents 1 General information...3 1.1 What is Acronis True Image Online?... 3 1.2 System requirements... 3 1.3 Acronis True Image Online installation and startup... 3 1.4 Subscription
User's Guide Table of contents 1 General information...3 1.1 What is Acronis True Image Online?... 3 1.2 System requirements... 3 1.3 Acronis True Image Online installation and startup... 3 1.4 Subscription
QBalance.com. We make QuickBooks work for you. Call Toll-Free: (800) 216-0763. Congratulations! You are using the best accounting software available!
 QBalance.com We make QuickBooks work for you CPA Call Toll-Free: (800) 216-0763 Congratulations! You are using the best accounting software available! But: you may be one of the 75% of all QuickBooks installations
QBalance.com We make QuickBooks work for you CPA Call Toll-Free: (800) 216-0763 Congratulations! You are using the best accounting software available! But: you may be one of the 75% of all QuickBooks installations
Kaspersky Password Manager USER GUIDE
 Kaspersky Password Manager USER GUIDE Dear User! Thank you for choosing our product. We hope that this documentation helps you in your work and provides answers you may need. Any type of reproduction or
Kaspersky Password Manager USER GUIDE Dear User! Thank you for choosing our product. We hope that this documentation helps you in your work and provides answers you may need. Any type of reproduction or
Stellar Phoenix Exchange Server Backup
 Stellar Phoenix Exchange Server Backup Version 1.0 Installation Guide Introduction This is the first release of Stellar Phoenix Exchange Server Backup tool documentation. The contents will be updated periodically
Stellar Phoenix Exchange Server Backup Version 1.0 Installation Guide Introduction This is the first release of Stellar Phoenix Exchange Server Backup tool documentation. The contents will be updated periodically
How To Backup Your Computer With A Remote Drive Client On A Pc Or Macbook Or Macintosh (For Macintosh) On A Macbook (For Pc Or Ipa) On An Uniden (For Ipa Or Mac Macbook) On
 Remote Drive PC Client software User Guide -Page 1 of 27- PRIVACY, SECURITY AND PROPRIETARY RIGHTS NOTICE: The Remote Drive PC Client software is third party software that you can use to upload your files
Remote Drive PC Client software User Guide -Page 1 of 27- PRIVACY, SECURITY AND PROPRIETARY RIGHTS NOTICE: The Remote Drive PC Client software is third party software that you can use to upload your files
User s Guide For Department of Facility Services
 Doc s File Server User s Guide For Department of Facility Services For Ver : 7.2.88.1020 Rev : 1_05-27-2011 Created by : Elliott Jeyaseelan 2 Table of Contents SERVER LOGIN & AUTHENTICATION REQUIREMENTS
Doc s File Server User s Guide For Department of Facility Services For Ver : 7.2.88.1020 Rev : 1_05-27-2011 Created by : Elliott Jeyaseelan 2 Table of Contents SERVER LOGIN & AUTHENTICATION REQUIREMENTS
3 Backing up to Acronis Online Storage... 10 3.1 Log in to the online storage...10 3.2 Computer selection...11
 User's Guide Table of contents 1 General information...3 1.1 What is Acronis True Image Online?... 3 1.2 System requirements... 3 1.3 Acronis True Image Online installation and startup... 4 1.4 Subscription
User's Guide Table of contents 1 General information...3 1.1 What is Acronis True Image Online?... 3 1.2 System requirements... 3 1.3 Acronis True Image Online installation and startup... 4 1.4 Subscription
User guide. Business Email
 User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
GoldKey Software. User s Manual. Revision 7.12. WideBand Corporation www.goldkey.com. Copyright 2007-2014 WideBand Corporation. All Rights Reserved.
 GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
Getting Started With Citrix ShareFile
 Guide Getting Started With Citrix ShareFile Learn the basics of your ShareFile account. Plus, get the answers to some of our most frequently asked how-to questions. ShareFile.com Welcome to ShareFile!
Guide Getting Started With Citrix ShareFile Learn the basics of your ShareFile account. Plus, get the answers to some of our most frequently asked how-to questions. ShareFile.com Welcome to ShareFile!
Setting Up and Using the Funambol Outlook Plug-in v7
 Setting Up and Using the Funambol Outlook Plug-in v7 Contents Introduction.......................................... 2 Requirements for Plug-In Use........................... 2 Installing the Funambol
Setting Up and Using the Funambol Outlook Plug-in v7 Contents Introduction.......................................... 2 Requirements for Plug-In Use........................... 2 Installing the Funambol
Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7
 Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7 Description This hands-on lab session covers the hard drive encryption technologies from PGP. Students will administer a typical Whole Disk Encryption
Symantec PGP Whole Disk Encryption Hands-On Lab V 3.7 Description This hands-on lab session covers the hard drive encryption technologies from PGP. Students will administer a typical Whole Disk Encryption
BounceBack User Guide
 Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
CTERA Agent for Mac OS-X
 User Guide CTERA Agent for Mac OS-X June 2014 Version 4.1 Copyright 2009-2014 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Mac OS-X June 2014 Version 4.1 Copyright 2009-2014 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
Carry it Easy. User Guide
 Carry it Easy User Guide User Manual Version 3.2 2004-2010 CoSoSys Ltd. Carry it Easy User Manual Table of Contents Table of Contents... I 1. Introduction... 1 2. System Requirements... 1 3. Installation...
Carry it Easy User Guide User Manual Version 3.2 2004-2010 CoSoSys Ltd. Carry it Easy User Manual Table of Contents Table of Contents... I 1. Introduction... 1 2. System Requirements... 1 3. Installation...
User s Manual. Transcend JetFlash SecureDrive. Contents
 User s Manual Transcend JetFlash SecureDrive Thank you for purchasing Transcend s USB Flash drive with built-in 256-bit AES encryption security. JetFlash SecureDrive helps you safeguard data by creating
User s Manual Transcend JetFlash SecureDrive Thank you for purchasing Transcend s USB Flash drive with built-in 256-bit AES encryption security. JetFlash SecureDrive helps you safeguard data by creating
SafeGuard Enterprise Web Helpdesk. Product version: 6 Document date: February 2012
 SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
Premier Installation 2013.1 Guide for SQL Server Administrators
 for Depreciation, Tracking, Planning, and Reporting Premier Installation 2013.1 Guide for SQL Server Administrators Premier Installation Guide Version 2013.1 Contents Chapter 1. Introduction Supported
for Depreciation, Tracking, Planning, and Reporting Premier Installation 2013.1 Guide for SQL Server Administrators Premier Installation Guide Version 2013.1 Contents Chapter 1. Introduction Supported
Field Manager Mobile Worker User Guide for RIM BlackBerry 1
 Vodafone Field Manager Mobile Worker User Guide for RIM BlackBerry APPLICATION REQUIREMENTS Supported devices listed here o http://support.vodafonefieldmanager.com Application requires 600 KB of application
Vodafone Field Manager Mobile Worker User Guide for RIM BlackBerry APPLICATION REQUIREMENTS Supported devices listed here o http://support.vodafonefieldmanager.com Application requires 600 KB of application
HP ProtectTools User Guide
 HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
SingTel PowerON Desktop Backup
 SingTel PowerON Desktop Backup User Manual Copyright 2011 F-Secure Corporation. All rights reserved. SingTel PowerON Desktop Backup Table of Contents 1. SingTel PowerON Desktop Backup Help... 1 1.1. What
SingTel PowerON Desktop Backup User Manual Copyright 2011 F-Secure Corporation. All rights reserved. SingTel PowerON Desktop Backup Table of Contents 1. SingTel PowerON Desktop Backup Help... 1 1.1. What
University of Rochester Sophos SafeGuard Encryption for Windows Support Guide
 Sophos SafeGuard Encryption for Windows Support Guide University Information Technology Security & Policy September 15, 2015 Version Date Modification 1.0 September 15, 2015 Initial guide 1.1 1.2 1.3 1.4
Sophos SafeGuard Encryption for Windows Support Guide University Information Technology Security & Policy September 15, 2015 Version Date Modification 1.0 September 15, 2015 Initial guide 1.1 1.2 1.3 1.4
Sendspace Wizard Desktop Tool Step-By-Step Guide
 Sendspace Wizard Desktop Tool Step-By-Step Guide Copyright 2007 by sendspace.com This publication is designed to provide accurate and authoritative information for users of sendspace, the easy big file
Sendspace Wizard Desktop Tool Step-By-Step Guide Copyright 2007 by sendspace.com This publication is designed to provide accurate and authoritative information for users of sendspace, the easy big file
Arkay Remote Data Backup Client Quick Start Guide
 Arkay Remote Data Backup Client Quick Start Guide Version 6.1.56.27 September 2005 Quick Start Guide It's easy to get started with Arkay Remote Data Backup and Recovery Service. To start using Arkay Remote
Arkay Remote Data Backup Client Quick Start Guide Version 6.1.56.27 September 2005 Quick Start Guide It's easy to get started with Arkay Remote Data Backup and Recovery Service. To start using Arkay Remote
HP External Hard Disk Drive Backup Solution by Seagate User Guide. November 2004 (First Edition) Part Number 373652-001
 HP External Hard Disk Drive Backup Solution by Seagate User Guide November 2004 (First Edition) Part Number 373652-001 Copyright 2004 Hewlett-Packard Development Company, L.P. The information contained
HP External Hard Disk Drive Backup Solution by Seagate User Guide November 2004 (First Edition) Part Number 373652-001 Copyright 2004 Hewlett-Packard Development Company, L.P. The information contained
Frequently Asked Questions: Cisco Jabber 9.x for Android
 Frequently Asked Questions Frequently Asked Questions: Cisco Jabber 9.x for Android Frequently Asked Questions (FAQs) 2 Setup 2 Basics 4 Connectivity 8 Calls 9 Contacts and Directory Search 14 Voicemail
Frequently Asked Questions Frequently Asked Questions: Cisco Jabber 9.x for Android Frequently Asked Questions (FAQs) 2 Setup 2 Basics 4 Connectivity 8 Calls 9 Contacts and Directory Search 14 Voicemail
Using SSH Secure Shell Client for FTP
 Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Time Matters and Billing Matters Administration Guide
 Time Matters and Billing Matters Administration Guide Version 14.1 2015 LexisNexis. All rights reserved. Copyright and Trademark LexisNexis, Lexis, and the Knowledge Burst logo are registered trademarks
Time Matters and Billing Matters Administration Guide Version 14.1 2015 LexisNexis. All rights reserved. Copyright and Trademark LexisNexis, Lexis, and the Knowledge Burst logo are registered trademarks
Motion Computing Tablet PC
 Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Introduction 1-1 Installing FAS 500 Asset Accounting the First Time 2-1 Installing FAS 500 Asset Accounting: Upgrading from a Prior Version 3-1
 Contents 1. Introduction 1-1 Supported Operating Environments................ 1-1 System Requirements............................. 1-2 Security Requirements........................ 1-3 Installing Server
Contents 1. Introduction 1-1 Supported Operating Environments................ 1-1 System Requirements............................. 1-2 Security Requirements........................ 1-3 Installing Server
SafeGuard Enterprise Web Helpdesk. Product version: 6.1
 SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
Frequently Asked Questions for logging in to Online Banking
 Frequently Asked Questions for logging in to Online Banking Why don t I recognize any of the phone numbers on the Secure Code page? I can t remember my password; can I reset it myself? I know I have the
Frequently Asked Questions for logging in to Online Banking Why don t I recognize any of the phone numbers on the Secure Code page? I can t remember my password; can I reset it myself? I know I have the
Exchange 2010. Outlook Profile/POP/IMAP/SMTP Setup Guide
 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide Document Revision Date: Nov. 13, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Introduction... 1 Exchange 2010 Outlook
Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide Document Revision Date: Nov. 13, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Introduction... 1 Exchange 2010 Outlook
HP ProtectTools for Small Business Security Software, Version 5.10. User Guide
 HP ProtectTools for Small Business Security Software, Version 5.10 User Guide Copyright 2010 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.
HP ProtectTools for Small Business Security Software, Version 5.10 User Guide Copyright 2010 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.
TM Online Storage: StorageSync
 TM Online Storage: StorageSync 1 Part A: Backup Your Profile 1: How to download and install StorageSync? Where to download StorageSync? You may download StorageSync from your e-storage account. Please
TM Online Storage: StorageSync 1 Part A: Backup Your Profile 1: How to download and install StorageSync? Where to download StorageSync? You may download StorageSync from your e-storage account. Please
ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference. May 2016
 ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference May 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference May 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
SafeGuard Enterprise Web Helpdesk
 SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SOS SO S O n O lin n e lin e Bac Ba kup cku ck p u USER MANUAL
 SOS Online Backup USER MANUAL HOW TO INSTALL THE SOFTWARE 1. Download the software from the website: http://www.sosonlinebackup.com/download_the_software.htm 2. Click Run to install when promoted, or alternatively,
SOS Online Backup USER MANUAL HOW TO INSTALL THE SOFTWARE 1. Download the software from the website: http://www.sosonlinebackup.com/download_the_software.htm 2. Click Run to install when promoted, or alternatively,
User Guide Win7Zilla
 User Guide Win7Zilla Table of contents Section 1: Installation... 3 1.1 System Requirements... 3 1.2 Software Installation... 3 1.3 Uninstalling Win7Zilla software... 3 Section 2: Navigation... 4 2.1 Main
User Guide Win7Zilla Table of contents Section 1: Installation... 3 1.1 System Requirements... 3 1.2 Software Installation... 3 1.3 Uninstalling Win7Zilla software... 3 Section 2: Navigation... 4 2.1 Main
Using an Edline Gradebook. EGP Teacher Guide
 Using an Edline Gradebook EGP Teacher Guide Table of Contents Introduction...3 Setup...3 Get the Gradebook Web Plugin... 3 Using Your Web Gradebook... 4 Using the Web Gradebook on a Shared Computer...
Using an Edline Gradebook EGP Teacher Guide Table of Contents Introduction...3 Setup...3 Get the Gradebook Web Plugin... 3 Using Your Web Gradebook... 4 Using the Web Gradebook on a Shared Computer...
Enterprise Asset Management System
 Enterprise Asset Management System in the Agile Enterprise Asset Management System AgileAssets Inc. Agile Enterprise Asset Management System EAM, Version 1.2, 10/16/09. 2008 AgileAssets Inc. Copyrighted
Enterprise Asset Management System in the Agile Enterprise Asset Management System AgileAssets Inc. Agile Enterprise Asset Management System EAM, Version 1.2, 10/16/09. 2008 AgileAssets Inc. Copyrighted
Banner Frequently Asked Questions (FAQs)
 Banner Frequently Asked Questions (FAQs) How do I install Java?...1 Banner prompts me to download and install Java. Is this OK?....1 What Java version should I use?...2 How do I check what version of Java
Banner Frequently Asked Questions (FAQs) How do I install Java?...1 Banner prompts me to download and install Java. Is this OK?....1 What Java version should I use?...2 How do I check what version of Java
CTERA Agent for Linux
 User Guide CTERA Agent for Linux September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Linux September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
How to test and debug an ASP.NET application
 Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
CTERA Agent for Mac OS-X
 User Guide CTERA Agent for Mac OS-X September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without
User Guide CTERA Agent for Mac OS-X September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without
User Guide. Digital Signature
 User Guide Digital Signature ENTRUST ESP 9..2 Document version: 2.2 Publication date: January 2014 This guide is the exclusive property of Notarius Inc. All reproduction, printing or distribution of this
User Guide Digital Signature ENTRUST ESP 9..2 Document version: 2.2 Publication date: January 2014 This guide is the exclusive property of Notarius Inc. All reproduction, printing or distribution of this
Secure Email Recipient Guide
 Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Table of Contents. OpenDrive Drive 2. Installation 4 Standard Installation Unattended Installation
 User Guide for OpenDrive Application v1.6.0.4 for MS Windows Platform 20150430 April 2015 Table of Contents Installation 4 Standard Installation Unattended Installation Installation (cont.) 5 Unattended
User Guide for OpenDrive Application v1.6.0.4 for MS Windows Platform 20150430 April 2015 Table of Contents Installation 4 Standard Installation Unattended Installation Installation (cont.) 5 Unattended
HP Client Security. Getting Started
 HP Client Security Getting Started Copyright 2013 Hewlett-Packard Development Company, L.P. Bluetooth is a trademark owned by its proprietor and used by Hewlett-Packard Company under license. Intel is
HP Client Security Getting Started Copyright 2013 Hewlett-Packard Development Company, L.P. Bluetooth is a trademark owned by its proprietor and used by Hewlett-Packard Company under license. Intel is
Table of Contents. Rebit 5 Help
 Rebit 5 Help i Rebit 5 Help Table of Contents Getting Started... 1 Making the First Recovery Point... 1 Don't Forget to Create a Recovery Media... 1 Changing Backup Settings... 1 What Does Rebit 5 Do?...
Rebit 5 Help i Rebit 5 Help Table of Contents Getting Started... 1 Making the First Recovery Point... 1 Don't Forget to Create a Recovery Media... 1 Changing Backup Settings... 1 What Does Rebit 5 Do?...
NATIONAL BANK s MasterCard SecureCode / Verified by VISA Service - Questions and Answers
 Learn more about MasterCard SecureCode / Verified by VISA service of NATIONAL BANK. You can use the links below to jump to specific topics, or scroll down the page to read the full list of questions and
Learn more about MasterCard SecureCode / Verified by VISA service of NATIONAL BANK. You can use the links below to jump to specific topics, or scroll down the page to read the full list of questions and
Getting Started and Administration
 AUGUST 2015 Microsoft Volume Licensing Service Center Getting Started and Administration 2 Microsoft Volume Licensing Service Center: Getting Started and Administration Table of contents Microsoft Volume
AUGUST 2015 Microsoft Volume Licensing Service Center Getting Started and Administration 2 Microsoft Volume Licensing Service Center: Getting Started and Administration Table of contents Microsoft Volume
IsItUp Quick Start Manual
 IsItUp - When you need to know the status of your network Taro Software Inc. Website: www.tarosoft.com Telephone: 703-405-4697 Postal address: 8829 110th Lane, Seminole Fl, 33772 Electronic mail: [email protected]
IsItUp - When you need to know the status of your network Taro Software Inc. Website: www.tarosoft.com Telephone: 703-405-4697 Postal address: 8829 110th Lane, Seminole Fl, 33772 Electronic mail: [email protected]
USB Flash Memory TransMemory-EX II TM
 USB Flash Memory TransMemory-EX II TM Security Software User Manual TOSHIBA Corporation Semiconductor & Storage Products Company Contents Chapter 1: Introduction... 2 Chapter 2: System Requirements...
USB Flash Memory TransMemory-EX II TM Security Software User Manual TOSHIBA Corporation Semiconductor & Storage Products Company Contents Chapter 1: Introduction... 2 Chapter 2: System Requirements...
Table of Contents. Table of Contents
 Table of Contents Setup Instructions... 1 Step 1: Download the Required Components... 1 Step 2: Install and Run the Online Backup Module... 3 Step 3: Sign-Up to the Online Backup Service... 4 Step 4: Configure
Table of Contents Setup Instructions... 1 Step 1: Download the Required Components... 1 Step 2: Install and Run the Online Backup Module... 3 Step 3: Sign-Up to the Online Backup Service... 4 Step 4: Configure
Pendragon Forms Industrial
 Pendragon Forms Industrial Version 7 Installation & Reference Guide for Android Devices Contents What Is Pendragon Forms Industrial?... 2 Installing Pendragon Forms Industrial... 2 Installing Pendragon
Pendragon Forms Industrial Version 7 Installation & Reference Guide for Android Devices Contents What Is Pendragon Forms Industrial?... 2 Installing Pendragon Forms Industrial... 2 Installing Pendragon
AT&T Voice DNA User Guide
 AT&T Voice DNA User Guide Page 1 Table of Contents GET STARTED... 4 Log In... 5 About the User Dashboard... 9 Manage Personal Profile... 15 Manage Messages... 17 View and Use Call Logs... 22 Search the
AT&T Voice DNA User Guide Page 1 Table of Contents GET STARTED... 4 Log In... 5 About the User Dashboard... 9 Manage Personal Profile... 15 Manage Messages... 17 View and Use Call Logs... 22 Search the
IT Quick Reference Guides Using Windows 7
 IT Quick Reference Guides Using Windows 7 Windows Guides This sheet covers many of the basic commands for using the Windows 7 operating system. WELCOME TO WINDOWS 7 After you log into your machine, the
IT Quick Reference Guides Using Windows 7 Windows Guides This sheet covers many of the basic commands for using the Windows 7 operating system. WELCOME TO WINDOWS 7 After you log into your machine, the
Using MioNet. 2006 Senvid Inc. User Manual Version 1.07
 Using MioNet Copyright 2006 by Senvid, Inc. All rights reserved. 2445 Faber Place, Suite 200, Palo Alto, CA 94303 Voice: (650) 354-3613 Fax: (650) 354-8890 1 COPYRIGHT NOTICE No part of this publication
Using MioNet Copyright 2006 by Senvid, Inc. All rights reserved. 2445 Faber Place, Suite 200, Palo Alto, CA 94303 Voice: (650) 354-3613 Fax: (650) 354-8890 1 COPYRIGHT NOTICE No part of this publication
mybullard Personal Control Panel User Guide
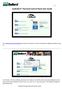 Page 1 mybullard Personal Control Panel User Guide Go to www.bullard.com/mybullard and click on the setup file in order to download the mybullard installer to your PC. Your browser / anti-virus software
Page 1 mybullard Personal Control Panel User Guide Go to www.bullard.com/mybullard and click on the setup file in order to download the mybullard installer to your PC. Your browser / anti-virus software
User Guide. IntraLinks Courier Plug-in for Microsoft Outlook
 IntraLinks Courier Plug-in for Microsoft Outlook User Guide Copyright 2012 IntraLinks, Inc. Version 3.2 September 2012 IntraLinks 24/7/365 support US: 212 543 7800 UK: +44 (0) 20 7623 8500 See IntraLinks
IntraLinks Courier Plug-in for Microsoft Outlook User Guide Copyright 2012 IntraLinks, Inc. Version 3.2 September 2012 IntraLinks 24/7/365 support US: 212 543 7800 UK: +44 (0) 20 7623 8500 See IntraLinks
WD SmartWare Software
 WD SmartWare Software User Manual Version 1.6.x Backup Software WD SmartWare Software User Manual, Version 1.6.x WD Service and Support Should you encounter any problem, please give us an opportunity to
WD SmartWare Software User Manual Version 1.6.x Backup Software WD SmartWare Software User Manual, Version 1.6.x WD Service and Support Should you encounter any problem, please give us an opportunity to
Upgrading from Windows XP to Windows 7
 We highly recommend that you print this tutorial. Your PC will restart during the Windows 7 installation process, so having a printed copy will help you follow the steps if you're unable to return to this
We highly recommend that you print this tutorial. Your PC will restart during the Windows 7 installation process, so having a printed copy will help you follow the steps if you're unable to return to this
Upgrading from Call Center Reporting to Reporting for Contact Center. BCM Contact Center
 Upgrading from Call Center Reporting to Reporting for Contact Center BCM Contact Center Document Number: NN40010-400 Document Status: Standard Document Version: 02.00 Date: June 2006 Copyright Nortel Networks
Upgrading from Call Center Reporting to Reporting for Contact Center BCM Contact Center Document Number: NN40010-400 Document Status: Standard Document Version: 02.00 Date: June 2006 Copyright Nortel Networks
Setting Up and Using the Funambol Outlook Sync Client v8.0
 Setting Up and Using the Funambol Outlook Sync Client v8.0 Contents Introduction.......................................... 2 Requirements........................................ 2 Installing the Funambol
Setting Up and Using the Funambol Outlook Sync Client v8.0 Contents Introduction.......................................... 2 Requirements........................................ 2 Installing the Funambol
BULLGUARD BAckUp GUIDE
 BULLGUARD backup GUIDE CONTENTS BullGuard Backup introduction page 3 Installing BullGuard Backup page 6 Uninstalling BullGuard Backup page 11 Registering BullGuard Backup: creating an account page 12 Running
BULLGUARD backup GUIDE CONTENTS BullGuard Backup introduction page 3 Installing BullGuard Backup page 6 Uninstalling BullGuard Backup page 11 Registering BullGuard Backup: creating an account page 12 Running
Team Foundation Server 2013 Installation Guide
 Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day [email protected] v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day [email protected] v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link:
 TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
