Protect Outbound Mail with DMARC
|
|
|
- Richard Mason
- 9 years ago
- Views:
Transcription
1 MDaemon Messaging Server How To Quick Start Guide Protect Outbound Mail with DMARC To protect outbound mail from your domain, you will need to create a DMARC record for your domain. We recommend carefully following an incremental deployment strategy, as outlined in this guide. What is DMARC and What Does It Do? DMARC (Domain-based Message Authentication, Reporting & Conformance) defines a scalable mechanism by which a mail sending organization can express domain level preferences for message validation, disposition, and reporting, and a mail receiving organization can use those preferences to improve mail handling. Why Should You Use DMARC? DMARC provides an easier way for recipients to validate the sender of the message, easier debugging and troubleshooting, and more consistent results for handling based on the results of SPF and DKIM lookups. How Does DMARC Work? When an inbound message is received, the receiving mail server performs SPF record lookups on the domain in the RFC5322 From field and DKIM lookups on the domain in the d=tag of the DKIM signature (when a message has been signed with DKIM). A message is considered to be in alignment with DMARC when: The organizational domain of the SPF authenticated RFC5321 Mail From command and the RFC5322 From field match. The message must pass SPF verification and the domain in the From: header must match the domain used to validate SPF (must exactly match for strict alignment, or must be a sub-domain for relaxed alignment)....and/or The organizational domain from the d= value of the DKIM record matches the domain taken from the RFC5322 From field (must exactly match for strict alignment, or must be a sub-domain for relaxed alignment), and the DKIM signature has been validated. If the message is not in alignment, then actions can be taken, such as placing the message in quarantine for review by the administrator. These actions are based on the p= tag in the DMARC record, and therefore, are chosen by the administrator of the sending domain. Additionally, aggregate reports can be sent to the domain administrator or another designated contact for all messages sent to a server claiming to be from your domain, and forensic reports can be sent for those messages that are considered to be unaligned. Aggregate reports are sent daily at midnight UTC. Forensic reports are sent immediately as incidents occur.
2 DMARC MDaemon Messaging Server How To Quick Start Guide Page 2 Creating DMARC Records Step 1 - Prerequisites 1. Create SPF or DKIM Records (or both) for your domain. DMARC requires that at least one of these record types be available, however, we recommend using both. In addition to creating these two records, messages should also be signed using DKIM. 2. Designate an account to receive aggregate reports from servers that receive messages claiming to be from your domain and specify the address these reports should be sent to. Step 2 - DMARC Record Format Here is a sample DMARC record: v=dmarc1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected]; pct=100 There are five parts (tags) to the above DMARC record - V, P, RUA, RUF, and PCT. These tags are defined below: 1. V= The protocol version of DMARC that is being used. EXAMPLE: v=dmarc1 2. P= The policy that you want to implement, such as p=none, p=quarantine, or p=reject. The p=tag tells receiving servers how you want them to handle mail that is considered unaligned. P=reject is not recommended. 3. RUA= Indicates that you want to receive DMARC aggregate reports from servers that receive messages claiming to be from your domain and specifies the address these reports should be sent to. EXAMPLE: rua=mailto:[email protected] 4. RUF= Indicates that you want to receive DMARC forensic reports from servers that receive unaligned messages claiming to be from your domain and specifies the address these reports should be sent to. EXAMPLE: ruf=mailto:[email protected] 5. PCT= The percentage of messages that should be handled based on the p= tag. In other words, if you have a policy of p=quarantine, then this indicates the percentage of s that will be quarantined when they are not in alignment. EXAMPLE: pct=100 The V and P tags are required in every DMARC record. Step 3 - Domain/Identifier Alignment You ll want to make sure all messages sent from your domain are in alignment with SPF and DKIM. 1. Look at the domain in the From field of sent messages. If you are using strict alignment anything other than an exact match of the domains for SPF and DKIM will be considered unaligned. If you are using relaxed alignment then subdomains are acceptable. There are many examples of DKIM and SPF records in strict and relaxed alignment under the Video Training section at 2. Compare the d= tag in the DKIM signature with the domain in the RFC5322 From field of the message. From: [email protected] DKIM-Signature: v=1; a=rsa-sha256; c=simple/relaxed; d=example.com; s=mail1; t= ; x= ; q=dns/ txt; h=received-spf:vbr-info:precedence:sender:from:to:subject:date:message-id:mime-version:content-type:thread- Index:Content-Language:Reply-To:List-ID:List-Post; bh=kiw5a0ukmcpokr+r4e9xsuzdrmx5xqtwl8ye/xkmpv 3. The DKIM signature must be valid, and the domains in the d= tag and the From header must match, depending on whether relaxed or strict alignment is being used, in order for the message to be in alignment. When relaxed alignment is used, subdomains are acceptable.
3 DMARC MDaemon Messaging Server How To Quick Start Guide Page 3 Deployment Strategy We recommend starting out in Monitor mode, then switching to Quarantine mode incrementally, as described below. Step 1 - Start in Monitor Mode When starting out, it s best to start with a policy of p=none and specify the address that will receive aggregate reports using the rua=tag. This address will receive daily aggregate reports of messages sent using your domain from servers that agree to send them. When you use p=none, no s claiming to be from your domain that are unaligned with DMARC will be deleted or quarantined. This allows you to monitor the results of your DMARC implementation so that legitimate s are not accidentally deleted or quarantined due to a misconfigured mail server or for other reasons. You can also request to receive a copy of the message headers from the actual message that is unaligned with DMARC by listing the ruf tag (if the reporting server provides it. Some servers only send the headers of the message in the report). You can do this now or later when you ve had a chance to get comfortable with the RUA (aggregate) reports. Some domains don t send the RUF (forensic) reports. Here is an example of a DMARC record with an RUF tag. v=dmarc1; p=none; rua=mailto:[email protected]; ruf=mailto:[email protected] Forensic reports are sent immediately, rather than on a schedule, and they may or may not include the message body. They should always include the message headers. Step 2 - Switch to Quarantine Mode After reviewing your forensic reports and correcting any issues found, you can tell mailbox providers to quarantine any spoofed or phishing s to the spam/junk folder. Use the p=quarantine tag in your DMARC record to tell others to quarantine unaligned mail from your domain. v=dmarc1; p=quarantine Step 3 - Increase Quarantine Percentages Incrementally Using the PCT=tag After you ve had time to monitor the aggregate reports, you can use the pct= tag to request that receiving mail servers only quarantine a small percentage of s from your domain that are unaligned. In the first example, we re requesting that receiving mail servers only quarantine 1% of unaligned messages. v=dmarc1; p=quarantine; rua=mailto:[email protected]; ruf=mailto:[email protected]; rf=afrf; pct=1 Then, after you ve had time to review additional reports and have corrected any issues found, you can gradually increase this percentage until you re comfortable enough to have receiving mail servers quarantine all unaligned messages from your domain. v=dmarc1; p=quarantine; rua=mailto:[email protected]; ruf=mailto:[email protected]; rf=afrf; pct=80 When you re ready to have receiving servers quarantine all unaligned messages from your domain, you can simply remove the pct=tag from your DMARC record. CAUTION: We do not recommend using p=reject mode. Using p=reject would increase the likelihood that legitimate messages sent from your domain are rejected in certain situations. It can also cause problems with mailing lists. Instead, use p=quarantine or p=none and review your DMARC reports so that you can make any changes necessary for messages from your domain to be in alignment with DMARC.
4 DMARC MDaemon Messaging Server How To Quick Start Guide Page 4 Verifying DMARC Records for Inbound Mail The following steps explain how to configure MDaemon to verify DMARC records for inbound mail. Step 1 - Enabling DMARC Verification in MDaemon To enable DMARC verification in MDaemon, navigate to Security Security Settings Sender Authentication DMARC Verification, and check the first box Enable DMARC Verification and Reporting. [Figure 1-1] As part of the DMARC verification process, MDaemon will first use SPF and/ or DKIM to validate each message. Each message must pass at least one of these two methods in order to be in alignment for purposes of DMARC. If the message is aligned, then it will proceed normally through the rest of MDaemon s delivery and filtering processes. If the message fails both DKIM and SPF, however, then the fate of the message is determined by a combination of the domain s DMARC policy and how you have configured MDaemon to deal with those messages. Figure 4-1 MDaemon then performs a DMARC DNS query on the domain found in the RFC 5322 From: field of each incoming message to determine whether or not the domain uses DMARC. If a DMARC DNS record is found, MDaemon will scan this record for its DMARC policy. Step 2 - If the Message Fails DKIM and/or SPF Verification Figure Policy p=none - If a message fails DKIM and SPF verification and the DMARC domain has a policy of p=none then no punitive action will be taken and normal message processing will continue. 2. Policy p=quarantine - When a domain has a restrictive policy of p=quarantine MDaemon can optionally filter unaligned messages automatically to the receiving user s Junk folder. MDaemon will also insert a fail policy header, such as: X-MDDMARC-Fail-policy: quarantine 3. Policy p=reject - When a domain has a restrictive policy of p=reject, and MDaemon has been configured to honor the p=reject tag when DMARC produces a FAIL result, unaligned messages will be rejected and the SMTP session will be terminated. If the option to honor p=reject is disabled, then instead of rejecting the message, MDaemaon can accept the message and insert an X-MDDMARC-Fail-policy: reject header into the message. You can then use the Content Filter to perform actions based on the presence of those headers, such as sending the message to a specific folder for further review. [Figure 4-2] Figure 4-3 You can optionally route all unaligned messages to the user s Junk folder. [Figure 4-3] NOTE [for items 2 and 3 above]: be careful when enabling the option to route unaligned messages to the user s Junk folder because if users are using POP, they won t have access to this junk folder. They would need to be using IMAP (Outlook Connector included), ActiveSync, or WorldClient. When this is enabled, MDaemon will ask if it should create an IMAP filter rule for all users to route DMARC failed messages to the Junk folder.
5 DMARC MDaemon Messaging Server How To Quick Start Guide Page 5 NOTE: If you ve enabled the option to Honor a policy of p=reject when DMARC produces a FAIL result, messages will not be routed to the junk folder because the SMTP sessions will be terminated. Step 3 - Exceptions You can optionally skip DMARC verification for messages from authenticated sessions or trusted IPs. You can also optionally cache DMARC records for faster processing. [Figure 5-1] Step 4 - Reporting Figure Aggregate - Check the box to allow MDaemon to send DMARC aggregate reports to domains that include an RUA= entry in their DMARC records. If no RUA entry exists, then the domain is not requesting these reports. With this option enabled, MDaemon will send aggregate reports to the address defined in the rua= entry of the public DMARC record of the sending domain. [Figure 5-2] 2. Forensic/Failure - Check the box to have MDaemon submit failure reports to domains that contain the ruf= entry in their public DMARC records. [Figure 5-2] DMARC Settings Figure 5-2 The DMARC Settings screen contains various options for including certain information in DMARC reports, logging DMARC DNS records, and updating the Public Suffix file used by MDaemon for DMARC. Step 1 - DKIM Canonicalized Headers are Included in DMARC Failure Reports When this option is enabled, DKIM headers of messages that failed DKIM verification will be included in the DMARC failure reports that are sent to the domains that request them. [Figure 5-3] Use this with caution: This header information may include the message subject, which may contain sensitive information. Figure 5-3 Step 2 - DKIM Canonicalized Body is Included in DMARC Failure Reports When this option is enabled, the body of the failed message will be included in the DMARC failure report to the domain that requested it. NOTE: The above options are useful for debugging, however, they do reveal content when sending failure reports.
6 DMARC MDaemon Messaging Server How To Quick Start Guide Page 6 Step 3 - Replace Reserved IPs in DMARC Reports with X.X.X.X This option is enabled by default to conceal reserved IPs in DMARC reports. Reserved IPs may include *, *.*, 10.*.*.*, and /12. [Figure 6-1] Step 4 - Automatically Update Public Suffix File if It s Older Than This Many Days DMARC uses a public suffix file to reliably determine the proper domains to query for DMARC DNS records. By default, this file is updated when it s more than 15 days old. You can change this setting if you d like to update this file more or less often. [Figure 6-2] Figure 6-1 Click on Update public suffix file now to have MDaemon immediately update the suffix file at the URL specified. Summary DMARC takes the guesswork out of determining what to do with messages that did not originate from the domain specified in the From field of the message. When a message fails DKIM and SPF lookups, DMARC allows domain administrators to tell receiving mail server administrators or mailbox providers what to do with the message, such as accept, quarantine, or reject the message. Forensic and aggregate reports allow domain administrators to see how, when and where their domain is being abused. Figure 6-2 For a more technical, more thorough explanation of DMARC, including many examples of aligned and unaligned messages, you can view the complete lesson at , Ltd. MDaemon, WorldClient, RelayFax, and Alt-N are trademarks of, Ltd. All trademarks are property of their respective owners
This user guide provides guidelines and recommendations for setting up your business s domain authentication to improve your deliverability rating.
 BLUEHORNET USER GUIDE EMAIL AUTHENTICATION AND DOMAIN MONITORING TOOLS This user guide provides guidelines and recommendations for setting up your business s domain authentication to improve your deliverability
BLUEHORNET USER GUIDE EMAIL AUTHENTICATION AND DOMAIN MONITORING TOOLS This user guide provides guidelines and recommendations for setting up your business s domain authentication to improve your deliverability
Configuring MDaemon for Centralized Spam Blocking and Filtering
 Configuring MDaemon for Centralized Spam Blocking and Filtering Alt-N Technologies, Ltd 2201 East Lamar Blvd, Suite 270 Arlington, TX 76006 (817) 525-2005 http://www.altn.com July 26, 2004 Contents A Centralized
Configuring MDaemon for Centralized Spam Blocking and Filtering Alt-N Technologies, Ltd 2201 East Lamar Blvd, Suite 270 Arlington, TX 76006 (817) 525-2005 http://www.altn.com July 26, 2004 Contents A Centralized
THE DMARC GUIDE. Understanding DMARC for Securing Email
 THE DMARC GUIDE Understanding DMARC for Securing Email The History - Introduction Email despite its importance, ubiquity, and staying power has never been secure. Prior attempts at security have failed
THE DMARC GUIDE Understanding DMARC for Securing Email The History - Introduction Email despite its importance, ubiquity, and staying power has never been secure. Prior attempts at security have failed
Email AntiSpam. Administrator Guide and Spam Manager Deployment Guide
 Email AntiSpam Administrator Guide and Spam Manager Deployment Guide AntiSpam Administration and Spam Manager Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec
Email AntiSpam Administrator Guide and Spam Manager Deployment Guide AntiSpam Administration and Spam Manager Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec
Curbing Email Threats & Spear Phishing The Promise & Results with DMARC
 SESSION ID: TECH-W03 Curbing Email Threats & Spear Phishing The Promise & Results with DMARC MODERATOR: Craig Spiezle Executive Director & President Online Trust Alliance @otalliance PANELISTS: Pat Peterson
SESSION ID: TECH-W03 Curbing Email Threats & Spear Phishing The Promise & Results with DMARC MODERATOR: Craig Spiezle Executive Director & President Online Trust Alliance @otalliance PANELISTS: Pat Peterson
2014-10-07. Email security
 Email security Simple Mail Transfer Protocol First defined in RFC821 (1982), later updated in RFC 2821 (2001) and most recently in RFC5321 (Oct 2008) Communication involves two hosts SMTP Client SMTP Server
Email security Simple Mail Transfer Protocol First defined in RFC821 (1982), later updated in RFC 2821 (2001) and most recently in RFC5321 (Oct 2008) Communication involves two hosts SMTP Client SMTP Server
Sender Authentication Technology Deployment and Authentication Identifiers
 2. Sender Authentication Technology Deployment and Authentication Identifiers In this report we will present an overview of spam trends for week 14 through week 26 of 2012. The ratio of spam has dropped
2. Sender Authentication Technology Deployment and Authentication Identifiers In this report we will present an overview of spam trends for week 14 through week 26 of 2012. The ratio of spam has dropped
Using MailStore to Archive MDaemon Email
 Using MailStore to Archive MDaemon Email This guide details how to archive all inbound and outbound email using MailStore, as well as archiving any emails currently found in the users accounts in MDaemon.
Using MailStore to Archive MDaemon Email This guide details how to archive all inbound and outbound email using MailStore, as well as archiving any emails currently found in the users accounts in MDaemon.
DKIM last chance for mail service? TFMC2 01/2006
 DKIM last chance for mail service? TFMC2 01/2006 Mail service status More and more spam, fishing, spoofing, virus More and more energy in spam fighting More and more messages lost because : Imperfect automatic
DKIM last chance for mail service? TFMC2 01/2006 Mail service status More and more spam, fishing, spoofing, virus More and more energy in spam fighting More and more messages lost because : Imperfect automatic
Implementing MDaemon as an Email Security Gateway to Exchange Server
 Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
MDaemon Vs. Microsoft Exchange Server 2013 Standard
 Comparison Guide Vs. The following chart is a side-by-side feature comparison of and. Flex Licensing Maximum Accounts Unlimited Unlimited SMTP, POP3, DomainPOP, and MultiPOP POP3 & SMTP Only SSL / TLS
Comparison Guide Vs. The following chart is a side-by-side feature comparison of and. Flex Licensing Maximum Accounts Unlimited Unlimited SMTP, POP3, DomainPOP, and MultiPOP POP3 & SMTP Only SSL / TLS
POP3 Connector for Exchange - Configuration
 Eclarsys PopGrabber POP3 Connector for Exchange - Configuration PopGrabber is an excellent replacement for the POP3 connector included in Windows SBS 2000 and 2003. It also works, of course, with Exchange
Eclarsys PopGrabber POP3 Connector for Exchange - Configuration PopGrabber is an excellent replacement for the POP3 connector included in Windows SBS 2000 and 2003. It also works, of course, with Exchange
EFFECTIVE SPAM FILTERING WITH MDAEMON
 EFFECTIVE SPAM FILTERING WITH MDAEMON Introduction The following guide provides a recommended method for increasing the overall effectiveness of MDaemon s spam filter to reduce the level of spam received
EFFECTIVE SPAM FILTERING WITH MDAEMON Introduction The following guide provides a recommended method for increasing the overall effectiveness of MDaemon s spam filter to reduce the level of spam received
DomainKeys Identified Mail DKIM authenticates senders, message content
 DomainKeys Identified Mail DKIM authenticates senders, message content Alt-N Technologies, Ltd. 2201 East Lamar Blvd, Suite 270 Arlington, Texas 76006 Phone: (817) 525-2005 Fax: (817) 525-2019 http://www.altn.com/
DomainKeys Identified Mail DKIM authenticates senders, message content Alt-N Technologies, Ltd. 2201 East Lamar Blvd, Suite 270 Arlington, Texas 76006 Phone: (817) 525-2005 Fax: (817) 525-2019 http://www.altn.com/
Using The Outlook Connector Client
 Outlook Connector for MDaemon How To Quick Start Guide Using The Outlook Connector Client When Outlook Connector is installed on the MDaemon server, the Outlook Connector client, which is installed on
Outlook Connector for MDaemon How To Quick Start Guide Using The Outlook Connector Client When Outlook Connector is installed on the MDaemon server, the Outlook Connector client, which is installed on
Collax Mail Server. Howto. This howto describes the setup of a Collax server as mail server.
 Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Internet Standards. Sam Silberman, Constant Contact
 Internet Standards Sam Silberman, Constant Contact What are Standards? World without Standards We live in a connected world Topics DMARC (Indirect flows) Security/Privacy TLS over SMTP End-to-end encryption
Internet Standards Sam Silberman, Constant Contact What are Standards? World without Standards We live in a connected world Topics DMARC (Indirect flows) Security/Privacy TLS over SMTP End-to-end encryption
Install and Configure RelayFax
 RelayFax Network Fax Manager How To Quick Start Guide Install and Configure RelayFax Welcome to RelayFax Network Fax Manager. This guide is designed to help you quickly install and start using your RelayFax.
RelayFax Network Fax Manager How To Quick Start Guide Install and Configure RelayFax Welcome to RelayFax Network Fax Manager. This guide is designed to help you quickly install and start using your RelayFax.
Intercept Anti-Spam Quick Start Guide
 Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Exchange Online Protection In-Depth
 Exchange Online Protection In-Depth Mike Crowley Baseline Technologies Session Agenda Introduction to EOP Administration DMARC, SPF & DKIM Advanced Threat Protection EOP Deployment Tips Introduction to
Exchange Online Protection In-Depth Mike Crowley Baseline Technologies Session Agenda Introduction to EOP Administration DMARC, SPF & DKIM Advanced Threat Protection EOP Deployment Tips Introduction to
Domains Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc.
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
From SPAMfighter SMTP Anti Spam Server to SPAMfighter Mail Gateway
 From SPAMfighter SMTP Anti Spam Server to SPAMfighter Mail Gateway This guide will assist you in going from the SPAMfighter SMTP Anti Spam Server to the SPAMfighter Mail Gateway. It is strongly advised
From SPAMfighter SMTP Anti Spam Server to SPAMfighter Mail Gateway This guide will assist you in going from the SPAMfighter SMTP Anti Spam Server to the SPAMfighter Mail Gateway. It is strongly advised
Features by Version. MDaemon Messaging Server Feature Guide. Alt-N Technologies
 MDaemon Messaging Server Feature Guide Features by Version The following chart shows what version of MDaemon that new features where introduced in. CalDAV Support 15.5 Do Not Disturb 15.5 Email Encryption
MDaemon Messaging Server Feature Guide Features by Version The following chart shows what version of MDaemon that new features where introduced in. CalDAV Support 15.5 Do Not Disturb 15.5 Email Encryption
Email Quick-Start Guide
 For TradeMark Media s email system Thank you for choosing TradeMark Media for your email hosting. You ve made a wise choice. TradeMark Media offers comprehensive spam and virus protection, POP3 and WebMail
For TradeMark Media s email system Thank you for choosing TradeMark Media for your email hosting. You ve made a wise choice. TradeMark Media offers comprehensive spam and virus protection, POP3 and WebMail
Reliable & Secure Email. Professional, Dependable, Complete Easy to Learn, Use and Grow
 Reliable & Secure Email Professional, Dependable, Complete Easy to Learn, Use and Grow About this Presentation Summarizes primary purposes of email, plus the needs of email providers and users. Introduces
Reliable & Secure Email Professional, Dependable, Complete Easy to Learn, Use and Grow About this Presentation Summarizes primary purposes of email, plus the needs of email providers and users. Introduces
Protect your brand from phishing emails by implementing DMARC 1
 Protect your brand from phishing emails by implementing DMARC 1 Message from the Certified Senders Alliance supported by AOL, Microsoft and Google In the following article we want to clarify why marketers
Protect your brand from phishing emails by implementing DMARC 1 Message from the Certified Senders Alliance supported by AOL, Microsoft and Google In the following article we want to clarify why marketers
Anti-Phishing Best Practices for ISPs and Mailbox Providers
 Anti-Phishing Best Practices for ISPs and Mailbox Providers Version 2.01, June 2015 A document jointly produced by the Messaging, Malware and Mobile Anti-Abuse Working Group (M 3 AAWG) and the Anti-Phishing
Anti-Phishing Best Practices for ISPs and Mailbox Providers Version 2.01, June 2015 A document jointly produced by the Messaging, Malware and Mobile Anti-Abuse Working Group (M 3 AAWG) and the Anti-Phishing
How to set up a multifunction device or application to send email using Office 365
 How to set up a multifunction device or application to send email using Office 365 Exchange Online 232 out of 424 rated this helpful Applies to: Exchange Online Topic Last Modified: 2015 10 14 You can
How to set up a multifunction device or application to send email using Office 365 Exchange Online 232 out of 424 rated this helpful Applies to: Exchange Online Topic Last Modified: 2015 10 14 You can
MailGuard and Microsoft Exchange 2007
 MailGuard and Microsoft Exchange 2007 Contents: Introduction - The purpose of this document. Protecting OUTBOUND email - Send your outbound email through MailGuard. MailGuard and Sender Policy Framework
MailGuard and Microsoft Exchange 2007 Contents: Introduction - The purpose of this document. Protecting OUTBOUND email - Send your outbound email through MailGuard. MailGuard and Sender Policy Framework
MDaemon configuration recommendations for dealing with spam related issues
 Web: Introduction MDaemon configuration recommendations for dealing with spam related issues Without a doubt, our most common support queries these days fall into one of the following groups:- 1. Why did
Web: Introduction MDaemon configuration recommendations for dealing with spam related issues Without a doubt, our most common support queries these days fall into one of the following groups:- 1. Why did
Email Quick Reference. Administrator Guide
 Email Quick Reference Administrator Guide Email Services Quick Reference Documentation version: 1.0 Legal Notice Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec
Email Quick Reference Administrator Guide Email Services Quick Reference Documentation version: 1.0 Legal Notice Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Frequently Asked Questions for New Electric Mail Administrators 1 Domain Setup/Administration
 Frequently Asked Questions for New Electric Mail Administrators 1 Domain Setup/Administration 1.1 How do I access the records of the domain(s) that I administer? To access the domains you administer, you
Frequently Asked Questions for New Electric Mail Administrators 1 Domain Setup/Administration 1.1 How do I access the records of the domain(s) that I administer? To access the domains you administer, you
SCORECARD EMAIL MARKETING. Find Out How Much You Are Really Getting Out of Your Email Marketing
 EMAIL MARKETING SCORECARD Find Out How Much You Are Really Getting Out of Your Email Marketing This guide is designed to help you self-assess your email sending activities. There are two ways to render
EMAIL MARKETING SCORECARD Find Out How Much You Are Really Getting Out of Your Email Marketing This guide is designed to help you self-assess your email sending activities. There are two ways to render
MOC 5047B: Intro to Installing & Managing Microsoft Exchange Server 2007 SP1
 MOC 5047B: Intro to Installing & Managing Microsoft Exchange Server 2007 SP1 Course Number: 5047B Course Length: 3 Days Certification Exam This course will help you prepare for the following Microsoft
MOC 5047B: Intro to Installing & Managing Microsoft Exchange Server 2007 SP1 Course Number: 5047B Course Length: 3 Days Certification Exam This course will help you prepare for the following Microsoft
Before you begin with an Exchange 2010 hybrid deployment... 3. Sign up for Office 365 for an Exchange 2010 hybrid deployment... 10
 Contents Before you begin with an Exchange 2010 hybrid deployment... 3 Sign up for Office 365 for an Exchange 2010 hybrid deployment... 10 Verify prerequisites with an Exchange 2010 hybrid deployment...
Contents Before you begin with an Exchange 2010 hybrid deployment... 3 Sign up for Office 365 for an Exchange 2010 hybrid deployment... 10 Verify prerequisites with an Exchange 2010 hybrid deployment...
Outlook Connector. Version 2 User Manual. client-side plugin. Collaborate Using Outlook. Version 2.0.0
 Outlook Connector client-side plugin Collaborate Using Outlook Version 2 User Manual Version 2.0.0 2003-2005 Alt-N Technologies. All rights reserved. MDaemon, WorldClient, and RelayFax are registered trademarks
Outlook Connector client-side plugin Collaborate Using Outlook Version 2 User Manual Version 2.0.0 2003-2005 Alt-N Technologies. All rights reserved. MDaemon, WorldClient, and RelayFax are registered trademarks
Setting up Microsoft Office 365
 Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Sonian Getting Started Guide October 2008
 Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Deployment Guide. For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php
 Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS. v.109
 K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS v.109 1 The Exchange environment is an important entry point by which a threat or security risk can enter into a network. K7 Mail Security is a complete
K7 Mail Security FOR MICROSOFT EXCHANGE SERVERS v.109 1 The Exchange environment is an important entry point by which a threat or security risk can enter into a network. K7 Mail Security is a complete
Dell SonicWALL Hosted Email Security. Administration Guide
 Dell SonicWALL Hosted Email Security 2015 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software
Dell SonicWALL Hosted Email Security 2015 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software
Windows Mail POP Instructions - Bloomsburg University Students
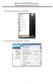 1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Anti-Spam Configuration in Outlook 2003 INDEX. Webmail settings Page 2. Client settings Page 6. Creation date 12.12.06 Version 1.2
 Anti-Spam Configuration in Outlook 2003 INDEX Webmail settings Page 2 Client settings Page 6 Creation date 12.12.06 Version 1.2 Webmail settings In this section, you will learn how to activate and configure
Anti-Spam Configuration in Outlook 2003 INDEX Webmail settings Page 2 Client settings Page 6 Creation date 12.12.06 Version 1.2 Webmail settings In this section, you will learn how to activate and configure
Objective This howto demonstrates and explains the different mechanisms for fending off unwanted spam e-mail.
 Collax Spam Filter Howto This howto describes the configuration of the spam filter on a Collax server. Requirements Collax Business Server Collax Groupware Suite Collax Security Gateway Collax Platform
Collax Spam Filter Howto This howto describes the configuration of the spam filter on a Collax server. Requirements Collax Business Server Collax Groupware Suite Collax Security Gateway Collax Platform
SonicWALL Email Security Quick Start Guide. Version 4.6
 SonicWALL Email Security Quick Start Guide Version 4.6 Quick Start Guide - Introduction This document guides you through the most basic steps to set up and administer SonicWALL Email Security. For more
SonicWALL Email Security Quick Start Guide Version 4.6 Quick Start Guide - Introduction This document guides you through the most basic steps to set up and administer SonicWALL Email Security. For more
The What, Why, and How of Email Authentication
 The What, Why, and How of Email Authentication by Ellen Siegel: Director of Technology and Standards, Constant Contact There has been much discussion lately in the media, in blogs, and at trade conferences
The What, Why, and How of Email Authentication by Ellen Siegel: Director of Technology and Standards, Constant Contact There has been much discussion lately in the media, in blogs, and at trade conferences
Frequently Asked Questions
 Frequently Asked Questions Table of Contents DNS Settings... 3 MX record... 3 SPF record... 3 Configuring Outbound... 3 Smart host configuration for Exchange 2003... 3 Smart host configuration for Exchange
Frequently Asked Questions Table of Contents DNS Settings... 3 MX record... 3 SPF record... 3 Configuring Outbound... 3 Smart host configuration for Exchange 2003... 3 Smart host configuration for Exchange
Barracuda Spam Firewall
 Barracuda Spam Firewall Overview The Barracuda Spam Firewall is a network appliance that scans every piece of email our organization receives. Its main purposes are to reduce the amount of spam we receive
Barracuda Spam Firewall Overview The Barracuda Spam Firewall is a network appliance that scans every piece of email our organization receives. Its main purposes are to reduce the amount of spam we receive
SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide
 SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide One of the typical usage cases for NowSMS is as an E-Mail to SMS & MMS Gateway. E-Mail users can send an SMS or MMS message by sending an e-mail
SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide One of the typical usage cases for NowSMS is as an E-Mail to SMS & MMS Gateway. E-Mail users can send an SMS or MMS message by sending an e-mail
DMARC and your.bank Domain. September 2015 v
 DMARC and your.bank Domain September 2015 v EMAIL MAKES IT EASY FOR CRIMINALS TO REACH YOUR CUSTOMERS USING YOUR BRAND Phishing and brand abuse erode consumer trust Attacks cause lasting brand damage Fallout
DMARC and your.bank Domain September 2015 v EMAIL MAKES IT EASY FOR CRIMINALS TO REACH YOUR CUSTOMERS USING YOUR BRAND Phishing and brand abuse erode consumer trust Attacks cause lasting brand damage Fallout
SMTP Email Settings. Magento Extension User Guide. Official extension page: SMTP Email Settings. User Guide: SMTP Email Settings
 SMTP Email Settings Magento Extension User Guide Official extension page: SMTP Email Settings Page 1 Table of contents: 1. General Settings. 3 2. SMTP Configuration.. 5 3. Log Clearing Settings. 6 4. Sent
SMTP Email Settings Magento Extension User Guide Official extension page: SMTP Email Settings Page 1 Table of contents: 1. General Settings. 3 2. SMTP Configuration.. 5 3. Log Clearing Settings. 6 4. Sent
Mimecast Services for Outlook (MSO4)
 Mimecast Services for Outlook (MSO4) End User Quick Start Guide for Outlook 2010/2013 Mimecast Services for Outlook (MSO 4) is a software application that integrates with your Microsoft Outlook. Once installed,
Mimecast Services for Outlook (MSO4) End User Quick Start Guide for Outlook 2010/2013 Mimecast Services for Outlook (MSO 4) is a software application that integrates with your Microsoft Outlook. Once installed,
eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide
 eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide This guide is designed to help the administrator configure the eprism Intercept Anti-Spam engine to provide a strong spam protection
eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide This guide is designed to help the administrator configure the eprism Intercept Anti-Spam engine to provide a strong spam protection
INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS)
 Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v15.5.0 ONWARDS) This document provides an installation and configuration guide for MDaemon Messaging Server along with
SESA Securing Email with Cisco Email Security Appliance Parts 1 and 2
 Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Office 365 Exchange Online Protection Administration Guide
 Chapter 10 Office 365 Exchange Online Protection Administration Guide Office 365 version 2013 is a suite of software products: Software as a Service (SaaS). Customers can purchase Office 365 in many ways,
Chapter 10 Office 365 Exchange Online Protection Administration Guide Office 365 version 2013 is a suite of software products: Software as a Service (SaaS). Customers can purchase Office 365 in many ways,
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Cloud Services. Email Anti-Spam. Admin Guide
 Cloud Services Email Anti-Spam Admin Guide 10/23/2014 CONTENTS Introduction to Anti- Spam... 4 About Anti- Spam... 4 Locating the Anti- Spam Pages in the Portal... 5 Anti- Spam Best Practice Settings...
Cloud Services Email Anti-Spam Admin Guide 10/23/2014 CONTENTS Introduction to Anti- Spam... 4 About Anti- Spam... 4 Locating the Anti- Spam Pages in the Portal... 5 Anti- Spam Best Practice Settings...
Comprehensive Anti-Spam Service
 Comprehensive Anti-Spam Service Chapter 1: Document Scope This document describes how to implement and manage the Comprehensive Anti-Spam Service. This document contains the following sections: Comprehensive
Comprehensive Anti-Spam Service Chapter 1: Document Scope This document describes how to implement and manage the Comprehensive Anti-Spam Service. This document contains the following sections: Comprehensive
Email Services Deployment. Administrator Guide
 Email Services Deployment Administrator Guide Email Services Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the
Email Services Deployment Administrator Guide Email Services Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the
English Translation of SecurityGateway for Exchange/SMTP Servers
 Testing: Alt N Technologies SecurityGateway by Sandra Lucifora Administrators spend a considerable amount of their time on the job on eliminating unwanted messages. Viruses, Phishing, and Spoofing pose
Testing: Alt N Technologies SecurityGateway by Sandra Lucifora Administrators spend a considerable amount of their time on the job on eliminating unwanted messages. Viruses, Phishing, and Spoofing pose
Hosted CanIt. Roaring Penguin Software Inc. 26 April 2011
 Hosted CanIt Roaring Penguin Software Inc. 26 April 2011 1 1 Introduction Thank you for selecting Hosted CanIt. This document explains how Hosted CanIt works and how you should configure your network to
Hosted CanIt Roaring Penguin Software Inc. 26 April 2011 1 1 Introduction Thank you for selecting Hosted CanIt. This document explains how Hosted CanIt works and how you should configure your network to
Before you begin with an Exchange 2010 hybrid deployment... 3. Sign up for Office 365 for an Exchange 2010 hybrid deployment... 10
 Contents Before you begin with an Exchange 2010 hybrid deployment... 3 Sign up for Office 365 for an Exchange 2010 hybrid deployment... 10 Verify prerequisites with an Exchange 2010 hybrid deployment...
Contents Before you begin with an Exchange 2010 hybrid deployment... 3 Sign up for Office 365 for an Exchange 2010 hybrid deployment... 10 Verify prerequisites with an Exchange 2010 hybrid deployment...
INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v9.5.0 ONWARDS)
 Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v9.5.0 ONWARDS) This document is designed to provide a quick installation and configuration guide for MDaemon along
Web: Overview INSTALLATION AND CONFIGURATION GUIDE (THIS DOCUMENT RELATES TO MDAEMON v9.5.0 ONWARDS) This document is designed to provide a quick installation and configuration guide for MDaemon along
IBM Express Managed Security Services for Email Security. Anti-Spam Administrator s Guide. Version 5.32
 IBM Express Managed Security Services for Email Security Anti-Spam Administrator s Guide Version 5.32 Table of Contents 1. Service overview... 3 1.1 Welcome... 3 1.2 Anti-Spam (AS) features... 3 1.3 How
IBM Express Managed Security Services for Email Security Anti-Spam Administrator s Guide Version 5.32 Table of Contents 1. Service overview... 3 1.1 Welcome... 3 1.2 Anti-Spam (AS) features... 3 1.3 How
MailStore Server 7 Documentation
 MailStore Server 7 Documentation 2012 MailStore Software GmbH 11. May 2012 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
MailStore Server 7 Documentation 2012 MailStore Software GmbH 11. May 2012 Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners.
GFI MailEssentials 12. Manual. By GFI Software
 GFI MailEssentials 12 Manual By GFI Software http://www.gfi.com Email: [email protected] Information in this document is subject to change without notice. Companies, names, and data used in examples herein
GFI MailEssentials 12 Manual By GFI Software http://www.gfi.com Email: [email protected] Information in this document is subject to change without notice. Companies, names, and data used in examples herein
Paladin Computers Privacy Policy Last Updated on April 26, 2006
 Paladin Computers Privacy Policy Last Updated on April 26, 2006 At Paladin Computers ( Service Provider ), we respect our Users and Clients right to privacy with regards to the use of their email and our
Paladin Computers Privacy Policy Last Updated on April 26, 2006 At Paladin Computers ( Service Provider ), we respect our Users and Clients right to privacy with regards to the use of their email and our
Outlook Express POP Instructions - Bloomsburg University Students
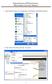 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Configuration Guide for Exchange 2003, 2007 and 2010
 Configuration Guide for Exchange 2003, 2007 and 2010 Table of Contents Exchange 2013... 2 Configuring Outbound Smart Host... 2 Configure Access Restriction to Prevent DoS Attacks... 2 Exchange 2007/2010...
Configuration Guide for Exchange 2003, 2007 and 2010 Table of Contents Exchange 2013... 2 Configuring Outbound Smart Host... 2 Configure Access Restriction to Prevent DoS Attacks... 2 Exchange 2007/2010...
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter explains the procedure on how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter explains the procedure on how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in
How to configure Incoming Email Enabled Libraries in MOSS2007 RTM using Exchange 2007 in an Active Directory Domain.
 How to configure Incoming Email Enabled Libraries in MOSS2007 RTM using Exchange 2007 in an Active Directory Domain. By Steve Smith, MVP SharePoint Portal Server, MCT Combined Knowledge www.combined-knowledge.com
How to configure Incoming Email Enabled Libraries in MOSS2007 RTM using Exchange 2007 in an Active Directory Domain. By Steve Smith, MVP SharePoint Portal Server, MCT Combined Knowledge www.combined-knowledge.com
eprism Enterprise Tech Notes
 eprism Enterprise Tech Notes Utilizing Microsoft Active Directory for eprism s Directory Services Context eprism can integrate with an existing LDAP (Lightweight Directory Access Protocol) directory for
eprism Enterprise Tech Notes Utilizing Microsoft Active Directory for eprism s Directory Services Context eprism can integrate with an existing LDAP (Lightweight Directory Access Protocol) directory for
Managing Junk Mail. About the Junk Mail Filter
 Managing Junk Mail Outlook can filter out certain types of messages and send them to a separate folder to keep your Inbox from being cluttered with junk mail. Outlook can also disable links in suspicious
Managing Junk Mail Outlook can filter out certain types of messages and send them to a separate folder to keep your Inbox from being cluttered with junk mail. Outlook can also disable links in suspicious
PANDA CLOUD EMAIL PROTECTION 3.3.0 / Administrator s Manual / 1
 PANDA CLOUD EMAIL PROTECTION 3.3.0 / Administrator s Manual / 1 Contents 1 INTRODUCTION TO PANDA CLOUD EMAIL PROTECTION... 5 1.1 WHAT IS PANDA CLOUD EMAIL PROTECTION?... 5 1.2 FUNCTIONALITIES... 5 2 PANDA
PANDA CLOUD EMAIL PROTECTION 3.3.0 / Administrator s Manual / 1 Contents 1 INTRODUCTION TO PANDA CLOUD EMAIL PROTECTION... 5 1.1 WHAT IS PANDA CLOUD EMAIL PROTECTION?... 5 1.2 FUNCTIONALITIES... 5 2 PANDA
IRMACS E-Mail Setup. Your IRMACS e-mail is available internally by the IMAP protocol. The server settings used are:
 IRMACS E-Mail Setup General Information This document covers both the default Apple OSX mail client and the installed Mozilla s Thunderbird mail client. If you are comfortable setting up your own mail
IRMACS E-Mail Setup General Information This document covers both the default Apple OSX mail client and the installed Mozilla s Thunderbird mail client. If you are comfortable setting up your own mail
IMF Tune Opens Exchange to Any Anti-Spam Filter
 Page 1 of 8 IMF Tune Opens Exchange to Any Anti-Spam Filter September 23, 2005 10 th July 2007 Update Include updates for configuration steps in IMF Tune v3.0. IMF Tune enables any anti-spam filter to
Page 1 of 8 IMF Tune Opens Exchange to Any Anti-Spam Filter September 23, 2005 10 th July 2007 Update Include updates for configuration steps in IMF Tune v3.0. IMF Tune enables any anti-spam filter to
WaveWare Technologies, Inc. We Deliver Information at the Speed of Light
 WaveWare Technologies, Inc. We Deliver Information at the Speed of Light Enterprise Messaging Software WaveWare Enterprise SMTP Email Server How-to Send an Email to a Pager Please Note This How to Guide
WaveWare Technologies, Inc. We Deliver Information at the Speed of Light Enterprise Messaging Software WaveWare Enterprise SMTP Email Server How-to Send an Email to a Pager Please Note This How to Guide
CHAPTER 1 Exploring Mobile Devices with IMail 1
 Contents CHAPTER 1 Exploring Mobile Devices with IMail 1 CHAPTER 2 Windows Mobile... 2 Configuring Microsoft Exchange ActiveSync... 2 Setting up Mail Account... 8 CHAPTER 3 BlackBerry... 13 Configuring
Contents CHAPTER 1 Exploring Mobile Devices with IMail 1 CHAPTER 2 Windows Mobile... 2 Configuring Microsoft Exchange ActiveSync... 2 Setting up Mail Account... 8 CHAPTER 3 BlackBerry... 13 Configuring
Microsoft Exchange Server 2007, Upgrade from Exchange 2000/2003 (3938. 3938/5049/5050) Course KC3065 5 Days OVERVIEW COURSE OBJECTIVES AUDIENCE
 Microsoft Exchange, Upgrade from Exchange 2000/2003 COURSE OVERVIEW This instructor-led course offers Microsoft Exchange Server administrators with the skills they need to manage a Microsoft Exchange infrastructure.
Microsoft Exchange, Upgrade from Exchange 2000/2003 COURSE OVERVIEW This instructor-led course offers Microsoft Exchange Server administrators with the skills they need to manage a Microsoft Exchange infrastructure.
Configuration Task 3: (Optional) As part of configuration, you can deploy rules. For more information, see "Deploy Inbox Rules" below.
 Configure the E-mail Router After the E-mail Router has been installed, you can configure several aspects of it. Some of these configuration tasks are mandatory. Others are optional in that you use them
Configure the E-mail Router After the E-mail Router has been installed, you can configure several aspects of it. Some of these configuration tasks are mandatory. Others are optional in that you use them
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Rich Web Mail Quick Guide
 February 09 Rich Web Mail Quick Guide Version 1.3 Table of Contents 1 Purpose... 3 2 Quick Start Web Mail Overview... 3 2.1 Primary Email Features... 3 2.1.1 Report as Spam Feature Description...3 2.1.2
February 09 Rich Web Mail Quick Guide Version 1.3 Table of Contents 1 Purpose... 3 2 Quick Start Web Mail Overview... 3 2.1 Primary Email Features... 3 2.1.1 Report as Spam Feature Description...3 2.1.2
Outlook Connector Installation & Configuration groupwaresolution.net Hosted MS Exchange Alternative On Linux
 Outlook Connector Installation & Configuration groupwaresolution.net Hosted MS Exchange Alternative On Linux Page 1 of 5 DOWNLOAD Please download the connector installer msi file and save it to your computer.
Outlook Connector Installation & Configuration groupwaresolution.net Hosted MS Exchange Alternative On Linux Page 1 of 5 DOWNLOAD Please download the connector installer msi file and save it to your computer.
EXCHANGE ONLINE PROTECTION SPAM OVERVIEW. Tech Tips, Tricks and Tools by MessageOps
 EXCHANGE ONLINE PROTECTION SPAM OVERVIEW Tech Tips, Tricks and Tools by MessageOps TABLE OF CONTENTS: OVERVIEW AND DOCUMENT INTENTION..3 TRANSPORT RULES..... 4 CONTENT FILTER... 12 MALWARE FILTER......15
EXCHANGE ONLINE PROTECTION SPAM OVERVIEW Tech Tips, Tricks and Tools by MessageOps TABLE OF CONTENTS: OVERVIEW AND DOCUMENT INTENTION..3 TRANSPORT RULES..... 4 CONTENT FILTER... 12 MALWARE FILTER......15
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010
 10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
MailEnable Connector for Microsoft Outlook
 MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
Lesson Plans Configuring Exchange Server 2007
 Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
11/23/2015 Step by Step Guide for. Exchange Server 2016. MS Messaging Solution. Md Shaifullah Mozide Palash OVIWIN
 11/23/2015 Step by Step Guide for Exchange Server 2016 MS Messaging Solution Md Shaifullah Mozide Palash OVIWIN Table of Contents 1. Operating System Support for Exchange Server 2016... 2 2. Active Directory
11/23/2015 Step by Step Guide for Exchange Server 2016 MS Messaging Solution Md Shaifullah Mozide Palash OVIWIN Table of Contents 1. Operating System Support for Exchange Server 2016... 2 2. Active Directory
Panda Cloud Email Protection
 Panda Cloud Email Protection 1. Introduction a) What is spam? Spam is the term used to describe unsolicited messages or messages sent from unknown senders. They are usually sent in large (even massive)
Panda Cloud Email Protection 1. Introduction a) What is spam? Spam is the term used to describe unsolicited messages or messages sent from unknown senders. They are usually sent in large (even massive)
GFI MailEssentials Online Archive Configuration and usage
 GFI MailEssentials Online Archive Configuration and usage Contents Retention policies 3 Message tagging 4 Access rights 5 Journaling 5 Accessing archived messages 7 Archive search / Viewing archived messages
GFI MailEssentials Online Archive Configuration and usage Contents Retention policies 3 Message tagging 4 Access rights 5 Journaling 5 Accessing archived messages 7 Archive search / Viewing archived messages
Setup Guide for Exchange Server
 Setup Guide for Exchange Server Table of Contents Overview... 1 A. Exchange Server 2007/2010 Inbound Mail... 2 B. Exchange Server 2007/2010 Outbound Mail (optional)... 8 C. Exchange Server 2003/2000 Inbound
Setup Guide for Exchange Server Table of Contents Overview... 1 A. Exchange Server 2007/2010 Inbound Mail... 2 B. Exchange Server 2007/2010 Outbound Mail (optional)... 8 C. Exchange Server 2003/2000 Inbound
