Delegate Resolver. Delegate Resolver? How it works. Priasoft
|
|
|
- Erica Parks
- 8 years ago
- Views:
Transcription
1 Delegate Resolver Priasoft Delegate Resolver? What is the Delegate Resolver? Priasoft provides a utility that can restore folder delegates in a user's mailbox and can restore Sendon-Behalf-Of rights. Outlook + Exchange provide a feature to allow a user to specific one or more other users that have permission to access a folder in their mailbox. Although this may not be a feature that is commonly used, when it is used it is often between VIPs and Executives and their assistants typically a very important group. The ability to restore delegate assignments quickly becomes a valuable feature. How it works The Delegate Resolver (DR) works by analyzing information collected during the migration of a mailbox. The DR is typically run automatically at the end of a migration batch (a list of mailboxes migrated with specific options). The Priasoft Mailbox Migration Manager (MMM) is responsible for the collection of the delegate information from the source mailbox and for storing the info in the target mailbox for later use by the DR. When the MMM is migrating a mailbox it enumerates all the visible folders for the user's mailbox. During that process, it reads all the delegated permissions on each folder, and stores similar information on the matching target folder for later use. Note that the MMM does not actually restore the permissions on the target folder, it merely places the recorded information from the source in a hidden property on the target folder. After a migration batch completes, the DR is started. The DR on startup first connects to a Domain Controller in the target environment and performs an LDAP search for mailboxes that have unresolved delegates. The DR is able to determine such by data placed on the target AD user accounts by the MMM. For each mailbox found to have unresolved delegates, the DR logs on to the mailbox and begins to enumerate the target mailbox's folders. For each folder, the previously recorded information about delegates is analyzed and a secondary search is performed. This secondary search is used to find users in the target environment that match each delegate that was collected during the migration. When a match is made, that user is restored as a delegate on the folder. PHONE WEB eriq@priasoft.com
2 2 To visualize this process, refer to the diagram below: Specifics As the diagram shows, the DR leverages information in Active Directory to determine which mailboxes to process. What is important to consider is that AD replication can impact the ability of the DR to find matching delegates and ultimately can affect whether or not a delegate can be restored. Active Directory Replication For instance, if Joe and his assistant are migrated and the Domain Controller upon which changes were made was in Site1, but the DR is connecting to a DC in Site2, the DR may not be able to find a match for some of Joe's assistant because the relevant changes that the DR is looking for have not replicated to the DC in Site2. You can always run the DR again after a migration has completed for such a case. Global Catalogs The DR uses GCs when it is searching for a matching delegate. As such, if the GC that the DR is using does not have matching information (again, possibly due to replication), the delegate will not be restored. However, the unmatched delegate will be looked at again the next time the DR runs.
3 3 Self Balancing This term is to highlight the fact that the DR looks at ALL unresolved delegates for ALL mailboxes that still have them, not just the last batch of mailboxes migrated. This means that if you migrate a user today that has a delegate, and you migrate the delegate tomorrow, the DR will be able to restore the relationship after tomorrow's migration. It is best from a user experience to try to identify groups of users that have delegate relationships and migrate them in the same batch, however sometimes such relationships are not easily discovered. In such cases, know that when the delegate is migrated, its relationship will be restored, even if there are many days between when the delegate and the related mailbox are migrated. Delegate Info It is important to understand the information collected about delegates in order to understand how delegates can fail to be restored. The MMM looks at the list of delegates on each source folder and collects specific information. It does that by using information provided solely by MAPI/Exchange. For each delegate, the display name, the rights, and one of 3 unique identifiers is collected. In Exchange, the Global Address List is a critical resource for nearly every activity. This is also true for delegate permissions on user's folders. The key identifier for objects in the GAL is the X500 address. This address is seen in Active Directory on the property legacyexchangedn. This is one of the 3 values that might be available to identify the delegate, and is the most common. When the MMM migrates a mailbox, the X500 address of the source mailbox is added to the target mailbox as an additional address. When the DR runs and finds an unresolved delegate, this is one of the values for which it searches. This search leverages a Global Catalog so that a delegate can exist anywhere in the target forest and still be restored. However, if the search does not find the value, the DR cannot restore that delegate. The reasons for the search not finding a match are few and most commonly are because the delegate has not yet been migrated. There are 2 other types of value that can exist to identify a delegate on a folder: the user account name or the SID. These other 2 value types only exist if the delegate's mail properties have been removed or if the user account has been deleted. A mail user in the Global Address List is associated with an AD user account. There is a property on a mail user that links an AD account to the address book entry. However, if the mailbox of a user were deleted (leaving only the user account), the link is broken. However, when a mailbox is deleted, no operation is performed to clean up any folders that the user had access to on any other user's mailbox. In truth, the user account is still listed with permission to a folder, however because the link is broken there is no X500 address for the delegate. What is left of the delegate is either the user account in the form of DOMAIN\username or the SID (see: Security Identifier) of the original object if the user account was deleted. In most cases these are seen as orphaned delegates, but Priasoft does not try to assume such. When a mailbox is migrated by MMM, in addition to the X500 address being copied, it copies the user account name and SID of the AD account that is associated with the source mailbox. These values are placed in the target mailbox's address list so that the DR can find the same. These additional values are seen on a target mailbox as: NTUSER:DOMAIN\username and NTSID:S (the series of zeros represent a long string of text that uniquely identifies the user account). Since each migrated mailbox will contain the X500 address, the NTUSER value, and the NTSID value of the original source object, the DR regardless of the value collected about a delegate will be able to find a match.
4 4 Usage In most cases, usage of the Delegate Resolver is automatic. Its execution starts automatically after a batch of users completes a migration. However, there are times when it may be necessary or desirable to run the DR manually, such as when there is a delay in AD replication. The following will explain how to do such. To run the DR manually, execute its shortcut from the Priasoft start menu folder: Start -> Priasoft -> Mailbox Migration Manager -> Tools -> Mailbox Delegates Update Processor Target DC This should be a Domain Controller in the target environment. In most cases this should be the same target DC that was used by MMM. Username, User Domain These should be the username and domain of an account in the target domain, the same domain for which the Target DC supports. The account should have sufficient permission to query AD and to make changes to target AD user accounts. It is typical to use a Domain Admin account for this purpose. Ideally, you should use the same account that was used by the MMM for the same Target DC. Password The password for the username Save as InfoPackage This button is used to save the above details to a secure file for reuse. Load InfoPackage This button is used to load a saved InfoPackage. Note that an InfoPackage is automatically saved with each migration batch. If you need to run the DR at some time after a migration has already completed, you can use this option to load the same parameters that were used for the migration batch. The file will be located in the root of the batch folder. Batch folders are located in c:\programdata\priasoft and are named by date and timestamp. The file will have an extension of *.drpkg.
5 5 Troubleshooting The DR rarely has issues but sometimes a delegate that existed on a source folder will not be restored on a target folder. The DR creates logs in the windows event log system. These logs can be reviewed to analyze the activity performed and to determine why a delegate might not have been restored. The DR must be able to logon to user mailboxes with system privileges. It is important to understand that the account that is used to launch the DR must have appropriate permissions. The account used in the dialog when the tool is run manually is only used to access Active Directory that account has no interaction with access to users' mailboxes. Always ensure that the account used to logon to the migration host has sufficient MAPI/Exchange permissions.
NYSeMail Office 365 Administration Guide for Agencies
 NYSeMail Office 365 Administration Guide for Agencies Office 365 Overview... 34 What is included... 34 Software Requirements... 34 Message Limits... 34 Provisioning... 34 Archive and Retention Policy...
NYSeMail Office 365 Administration Guide for Agencies Office 365 Overview... 34 What is included... 34 Software Requirements... 34 Message Limits... 34 Provisioning... 34 Archive and Retention Policy...
Windows Server 2003 Logon Scripts Paul Flynn
 Creating logon scripts You can use logon scripts to assign tasks that will be performed when a user logs on to a particular computer. The scripts can carry out operating system commands, set system environment
Creating logon scripts You can use logon scripts to assign tasks that will be performed when a user logs on to a particular computer. The scripts can carry out operating system commands, set system environment
Integrating LANGuardian with Active Directory
 Integrating LANGuardian with Active Directory 01 February 2012 This document describes how to integrate LANGuardian with Microsoft Windows Server and Active Directory. Overview With the optional Identity
Integrating LANGuardian with Active Directory 01 February 2012 This document describes how to integrate LANGuardian with Microsoft Windows Server and Active Directory. Overview With the optional Identity
FuseMail- Exchange ControlPanel Admin Guide Feb.27-14 V1.0. Exchange ControlPanel Administration Guide
 Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
Cisco TelePresence Management Suite Extension for Microsoft Exchange
 Cisco TelePresence Management Suite Extension for Microsoft Exchange Installation Guide Software version 2.3 D14846.03 August 2013 Contents Introduction 4 End user guidance 4 Server requirements 5 Exchange
Cisco TelePresence Management Suite Extension for Microsoft Exchange Installation Guide Software version 2.3 D14846.03 August 2013 Contents Introduction 4 End user guidance 4 Server requirements 5 Exchange
For details for obtaining this later version; see the Known issues & Limitations, section at the end of this document.
 Note: This is the version of Entourage which comes as part of the Microsoft Office 2008 for Mac suite. Microsoft has now released Entourage 2008 Web Services Edition, in our testing this later version
Note: This is the version of Entourage which comes as part of the Microsoft Office 2008 for Mac suite. Microsoft has now released Entourage 2008 Web Services Edition, in our testing this later version
GALSYNC V7.0. Manual. NETsec. NETsec GmbH & Co.KG Schillingsstrasse 117 DE - 52355 Düren. 01. June 2016
 GALSYNC V7.0 Manual NETsec 01. June 2016 NETsec GmbH & Co.KG Schillingsstrasse 117 DE - 52355 Düren Introduction... 9 What are the principles?... 9 Versions... 9 Compatibility... 11 Recommendations (Do
GALSYNC V7.0 Manual NETsec 01. June 2016 NETsec GmbH & Co.KG Schillingsstrasse 117 DE - 52355 Düren Introduction... 9 What are the principles?... 9 Versions... 9 Compatibility... 11 Recommendations (Do
CMT Self-Service Archive Migrator 1.2. Comprehensive User Guide
 CMT Self-Service Archive Migrator 1.2 Comprehensive User Guide January 2015 Contents Section 1. Overview... 3 Section 2. End User Workstation Requirements... 3 Section 3. Self-Service Archive Migration
CMT Self-Service Archive Migrator 1.2 Comprehensive User Guide January 2015 Contents Section 1. Overview... 3 Section 2. End User Workstation Requirements... 3 Section 3. Self-Service Archive Migration
Information Systems Services. Configuring Entourage 2008 to connect to the University s Exchange service Version 2.2 February 2009
 Information Systems Services Configuring Entourage 2008 to connect to the University s Exchange service Configuring Entourage 2008 to connect to the University s Exchange service Contents Contents... 2
Information Systems Services Configuring Entourage 2008 to connect to the University s Exchange service Configuring Entourage 2008 to connect to the University s Exchange service Contents Contents... 2
T his feature is add-on service available to Enterprise accounts.
 SAML Single Sign-On T his feature is add-on service available to Enterprise accounts. Are you already using an Identity Provider (IdP) to manage logins and access to the various systems your users need
SAML Single Sign-On T his feature is add-on service available to Enterprise accounts. Are you already using an Identity Provider (IdP) to manage logins and access to the various systems your users need
State of Michigan Data Exchange Gateway. Web-Interface Users Guide 12-07-2009
 State of Michigan Data Exchange Gateway Web-Interface Users Guide 12-07-2009 Page 1 of 21 Revision History: Revision # Date Author Change: 1 8-14-2009 Mattingly Original Release 1.1 8-31-2009 MM Pgs 4,
State of Michigan Data Exchange Gateway Web-Interface Users Guide 12-07-2009 Page 1 of 21 Revision History: Revision # Date Author Change: 1 8-14-2009 Mattingly Original Release 1.1 8-31-2009 MM Pgs 4,
Cisco TelePresence Management Suite Extension for Microsoft Exchange
 Cisco TelePresence Management Suite Extension for Microsoft Exchange Installation Guide D14846.01 June 2011 Software version 2.3 Contents Introduction 5 End user guidance 5 Server requirements 6 Exchange
Cisco TelePresence Management Suite Extension for Microsoft Exchange Installation Guide D14846.01 June 2011 Software version 2.3 Contents Introduction 5 End user guidance 5 Server requirements 6 Exchange
Frequently Asked Questions
 Frequently Asked Questions Priasoft Migration Suite for Exchange Table of Contents Q: Can Priasoft pre-stage or trickle or synchronize mailbox data to the target environment?... 2 Q: How does Priasoft
Frequently Asked Questions Priasoft Migration Suite for Exchange Table of Contents Q: Can Priasoft pre-stage or trickle or synchronize mailbox data to the target environment?... 2 Q: How does Priasoft
How to Install the Active Directory Domain Services (AD DS) Role in Windows Server 2008 R2 and Promote a Server to a Domain Controller
 How to Install the Active Directory Domain Services (AD DS) Role in Windows Server 2008 R2 and Promote a Server to a Domain Controller I am not responsible for your actions or their outcomes, in any way,
How to Install the Active Directory Domain Services (AD DS) Role in Windows Server 2008 R2 and Promote a Server to a Domain Controller I am not responsible for your actions or their outcomes, in any way,
Symantec Enterprise Vault
 Symantec Enterprise Vault Guide for Microsoft Outlook 2003/2007 Users 10.0 Light Outlook Add-In Symantec Enterprise Vault: Guide for Microsoft Outlook 2003/2007 Users The software described in this book
Symantec Enterprise Vault Guide for Microsoft Outlook 2003/2007 Users 10.0 Light Outlook Add-In Symantec Enterprise Vault: Guide for Microsoft Outlook 2003/2007 Users The software described in this book
Windows Mail POP Instructions - Bloomsburg University Students
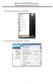 1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
Service Manager Dashboard
 Service Manager Service Manager Our Service Manager is part of the ExchangeDefender support portal as a central hub of control for ordering and managing the majority of our services. Once you log into
Service Manager Service Manager Our Service Manager is part of the ExchangeDefender support portal as a central hub of control for ordering and managing the majority of our services. Once you log into
Click Studios. Passwordstate. Installation Instructions
 Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Symantec Enterprise Vault
 Symantec Enterprise Vault Guide for Microsoft Outlook 2010 Users 9.0 Contents Chapter 1 Enterprise Vault options and mailbox icons Enterprise Vault options and toolbar buttons Enterprise Vault Outlook
Symantec Enterprise Vault Guide for Microsoft Outlook 2010 Users 9.0 Contents Chapter 1 Enterprise Vault options and mailbox icons Enterprise Vault options and toolbar buttons Enterprise Vault Outlook
Nevepoint Access Manager 1.2 BETA Documentation
 Nevepoint Access Manager 1.2 BETA Documentation Table of Contents Installation...3 Locating the Installation Wizard URL...3 Step 1: Configure the Administrator...4 Step 2: Connecting to Primary Connector...4
Nevepoint Access Manager 1.2 BETA Documentation Table of Contents Installation...3 Locating the Installation Wizard URL...3 Step 1: Configure the Administrator...4 Step 2: Connecting to Primary Connector...4
CISNTWK-492e. Microsoft Exchange Server 2003 Administration. Chapter Five Managing Addresses
 CISNTWK-492e Microsoft Exchange Server 2003 Administration Chapter Five Managing Addresses 1 Objectives Understand and create the different types of address lists that are used within Exchange Server 2003
CISNTWK-492e Microsoft Exchange Server 2003 Administration Chapter Five Managing Addresses 1 Objectives Understand and create the different types of address lists that are used within Exchange Server 2003
Setting Up a Backup Domain Controller
 Setting Up a Backup Domain Controller June 27, 2012 Copyright 2012 by World Class CAD, LLC. All Rights Reserved. A Backup Domain Controller After setting up a primary domain controller, we will want to
Setting Up a Backup Domain Controller June 27, 2012 Copyright 2012 by World Class CAD, LLC. All Rights Reserved. A Backup Domain Controller After setting up a primary domain controller, we will want to
OpenProtocols Connector for Microsoft Outlook Version 2.00 ARPDev Pty. Ltd. Overview. Features. Requirements
 OpenProtocols Connector for Microsoft Outlook Version 2.00 ARPDev Pty. Ltd Overview This guide describes the installation and functionality of the OpenProtocols for Microsoft Outlook. The OpenProtocols
OpenProtocols Connector for Microsoft Outlook Version 2.00 ARPDev Pty. Ltd Overview This guide describes the installation and functionality of the OpenProtocols for Microsoft Outlook. The OpenProtocols
Managing Identities in Outlook Express
 Managing Identities in Outlook Express Managing Identities in Outlook Express 4 Introduction 4 Creating a Outlook Express Identity 4 Managing Outlook Express Identities 4 Switching Outlook Express Identities
Managing Identities in Outlook Express Managing Identities in Outlook Express 4 Introduction 4 Creating a Outlook Express Identity 4 Managing Outlook Express Identities 4 Switching Outlook Express Identities
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Active Directory Manager Pro 5.0.0.0 New Features
 Active Directory Manager Pro 5.0.0.0 New Features General Information: info@cionsystems.com Online Support: support@cionsystems.com CionSystems Inc. 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
Active Directory Manager Pro 5.0.0.0 New Features General Information: info@cionsystems.com Online Support: support@cionsystems.com CionSystems Inc. 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
Global Image Management System For epad-vision. User Manual Version 1.10
 Global Image Management System For epad-vision User Manual Version 1.10 May 27, 2015 Global Image Management System www.epadlink.com 1 Contents 1. Introduction 3 2. Initial Setup Requirements 3 3. GIMS-Server
Global Image Management System For epad-vision User Manual Version 1.10 May 27, 2015 Global Image Management System www.epadlink.com 1 Contents 1. Introduction 3 2. Initial Setup Requirements 3 3. GIMS-Server
Migrating Exchange Server to Office 365
 Migrating Exchange Server to Office 365 By: Brien M. Posey CONTENTS Domain Verification... 3 IMAP Migration... 4 Cut Over and Staged Migration Prep Work... 5 Cut Over Migrations... 6 Staged Migration...
Migrating Exchange Server to Office 365 By: Brien M. Posey CONTENTS Domain Verification... 3 IMAP Migration... 4 Cut Over and Staged Migration Prep Work... 5 Cut Over Migrations... 6 Staged Migration...
Managing User Accounts
 Managing User Accounts This chapter includes the following sections: Configuring Local Users, page 1 Active Directory, page 2 Viewing User Sessions, page 6 Configuring Local Users Before You Begin You
Managing User Accounts This chapter includes the following sections: Configuring Local Users, page 1 Active Directory, page 2 Viewing User Sessions, page 6 Configuring Local Users Before You Begin You
Unity 7.x Event Log Errors
 Unity 7.x Event Log Errors Document ID: 112073 Contents Introduction Prerequisites Requirements Components Used Conventions Problem Cisco Unity Phrase Server Error Messages Unity 7.0(2) MWI Issues 1 2
Unity 7.x Event Log Errors Document ID: 112073 Contents Introduction Prerequisites Requirements Components Used Conventions Problem Cisco Unity Phrase Server Error Messages Unity 7.0(2) MWI Issues 1 2
Sophos Mobile Control as a Service Startup guide. Product version: 3.5
 Sophos Mobile Control as a Service Startup guide Product version: 3.5 Document date: August 2013 Contents 1 About this guide...3 2 What are the key steps?...4 3 First login...5 4 Change your administrator
Sophos Mobile Control as a Service Startup guide Product version: 3.5 Document date: August 2013 Contents 1 About this guide...3 2 What are the key steps?...4 3 First login...5 4 Change your administrator
Upgrading User-ID. Tech Note PAN-OS 4.1. 2011, Palo Alto Networks, Inc.
 Upgrading User-ID Tech Note PAN-OS 4.1 Revision B 2011, Palo Alto Networks, Inc. Overview PAN-OS 4.1 introduces significant improvements in the User-ID feature by adding support for multiple user directories,
Upgrading User-ID Tech Note PAN-OS 4.1 Revision B 2011, Palo Alto Networks, Inc. Overview PAN-OS 4.1 introduces significant improvements in the User-ID feature by adding support for multiple user directories,
How To Take Advantage Of Active Directory Support In Groupwise 2014
 White Paper Collaboration Taking Advantage of Active Directory Support in GroupWise 2014 Flexibility and interoperability have always been hallmarks for Novell. That s why it should be no surprise that
White Paper Collaboration Taking Advantage of Active Directory Support in GroupWise 2014 Flexibility and interoperability have always been hallmarks for Novell. That s why it should be no surprise that
User Guide. Version R91. English
 AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
UNIFIED COMMUNICATIONS POST-MIGRATION INSTRUCTIONS
 UNIFIED COMMUNICATIONS POST-MIGRATION INSTRUCTIONS (PURPOSE): The purpose of this document is to prepare the email user for post email migration activities to ensure a successful email migration with no
UNIFIED COMMUNICATIONS POST-MIGRATION INSTRUCTIONS (PURPOSE): The purpose of this document is to prepare the email user for post email migration activities to ensure a successful email migration with no
MailEnable Connector for Microsoft Outlook
 MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
Quality Center LDAP Guide
 Information Services Quality Assurance Quality Center LDAP Guide Version 1.0 Lightweight Directory Access Protocol( LDAP) authentication facilitates single sign on by synchronizing Quality Center (QC)
Information Services Quality Assurance Quality Center LDAP Guide Version 1.0 Lightweight Directory Access Protocol( LDAP) authentication facilitates single sign on by synchronizing Quality Center (QC)
Table of Contents. Page 3
 Welcome to Exchange Mail Customer Full Name Your e-mail is now being delivered and stored on the new Exchange server. Your new e-mail address is @rit.edu. This is the e-mail address that you should give
Welcome to Exchange Mail Customer Full Name Your e-mail is now being delivered and stored on the new Exchange server. Your new e-mail address is @rit.edu. This is the e-mail address that you should give
Smart Card Authentication. Administrator's Guide
 Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
NETWRIX ACCOUNT LOCKOUT EXAMINER
 NETWRIX ACCOUNT LOCKOUT EXAMINER ADMINISTRATOR S GUIDE Product Version: 4.1 July 2014. Legal Notice The information in this publication is furnished for information use only, and does not constitute a
NETWRIX ACCOUNT LOCKOUT EXAMINER ADMINISTRATOR S GUIDE Product Version: 4.1 July 2014. Legal Notice The information in this publication is furnished for information use only, and does not constitute a
NetWrix Account Lockout Examiner Version 4.0 Administrator Guide
 NetWrix Account Lockout Examiner Version 4.0 Administrator Guide Table of Contents Concepts... 1 Product Architecture... 1 Product Settings... 2 List of Managed Domains and Domain Controllers... 2 Email
NetWrix Account Lockout Examiner Version 4.0 Administrator Guide Table of Contents Concepts... 1 Product Architecture... 1 Product Settings... 2 List of Managed Domains and Domain Controllers... 2 Email
Avaya Modular Messaging Microsoft Outlook Client Release 5.2
 Avaya Modular Messaging Microsoft Outlook Client Release 5.2 Important: Instructions in this guide are applicable only if your message store is the Avaya Message Storage Server (MSS) or Microsoft Exchange
Avaya Modular Messaging Microsoft Outlook Client Release 5.2 Important: Instructions in this guide are applicable only if your message store is the Avaya Message Storage Server (MSS) or Microsoft Exchange
Printer Connection Manager
 IT DIRECT Printer Connection Manager Information Technology Direct Limited PO Box 33-1406 Auckland NZ Table of Contents OVERVIEW...2 SETUP INSTRUCTIONS:...3 INSTALLATION...5 Install with New Settings.xml
IT DIRECT Printer Connection Manager Information Technology Direct Limited PO Box 33-1406 Auckland NZ Table of Contents OVERVIEW...2 SETUP INSTRUCTIONS:...3 INSTALLATION...5 Install with New Settings.xml
Dell Active Administrator 8.0
 What s new in Dell Active Administrator 8.0 January 2016 Dell Active Administrator 8.0 is the upcoming release of Dell Software's complete solution for managing Microsoft Active Directory security auditing,
What s new in Dell Active Administrator 8.0 January 2016 Dell Active Administrator 8.0 is the upcoming release of Dell Software's complete solution for managing Microsoft Active Directory security auditing,
Objectives. At the end of this chapter students should be able to:
 NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
Inteset Secure Lockdown ver. 2.0
 Inteset Secure Lockdown ver. 2.0 for Windows XP, 7, 8, 10 Administrator Guide Table of Contents Administrative Tools and Procedures... 3 Automatic Password Generation... 3 Application Installation Guard
Inteset Secure Lockdown ver. 2.0 for Windows XP, 7, 8, 10 Administrator Guide Table of Contents Administrative Tools and Procedures... 3 Automatic Password Generation... 3 Application Installation Guard
Information Clicking the blue I next to each account will present you with connection and download information.
 Service Manager Our Service Manager is part of the ExchangeDefender support portal as a central hub of control for ordering and managing the majority of our services. Once you log into our support portal
Service Manager Our Service Manager is part of the ExchangeDefender support portal as a central hub of control for ordering and managing the majority of our services. Once you log into our support portal
Active Directory Restoration
 Active Directory Restoration This document outlines the steps required to recover an Active Directory Infrastructure, running on Windows 2003 R2 Server Standard. The scope of this document covers the scenario
Active Directory Restoration This document outlines the steps required to recover an Active Directory Infrastructure, running on Windows 2003 R2 Server Standard. The scope of this document covers the scenario
Email Client configuration and migration Guide Setting up Thunderbird 3.1
 Email Client configuration and migration Guide Setting up Thunderbird 3.1 1. Open Mozilla Thunderbird. : 1. On the Edit menu, click Account Settings. 2. On the Account Settings page, under Account Actions,
Email Client configuration and migration Guide Setting up Thunderbird 3.1 1. Open Mozilla Thunderbird. : 1. On the Edit menu, click Account Settings. 2. On the Account Settings page, under Account Actions,
VMware Identity Manager Administration
 VMware Identity Manager Administration VMware Identity Manager 2.6 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware Identity Manager Administration VMware Identity Manager 2.6 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Microsoft Virtual Labs. Active Directory New User Interface
 Microsoft Virtual Labs Active Directory New User Interface 2 Active Directory New User Interface Table of Contents Active Directory New User Interface... 3 Exercise 1 User Management and Saved Queries...4
Microsoft Virtual Labs Active Directory New User Interface 2 Active Directory New User Interface Table of Contents Active Directory New User Interface... 3 Exercise 1 User Management and Saved Queries...4
RDS Online Backup Suite v5.1 Brick-Level Exchange Backup
 Version 5.1.0.5 May 2006 1 Introduction...3 2 How To - Backup Individual Emails...3 2.1 Granting Full Mailbox Access Privileges...3 2.1.1 For one specific mailbox...3 2.1.2 For mailboxes located within
Version 5.1.0.5 May 2006 1 Introduction...3 2 How To - Backup Individual Emails...3 2.1 Granting Full Mailbox Access Privileges...3 2.1.1 For one specific mailbox...3 2.1.2 For mailboxes located within
Rentavault Online Backup. MS Exchange Mail Level Backup
 Version 5.1 May 2006 1 Introduction... 3 2 How To - Backup Individual Emails... 3 2.1 Granting Full Mailbox Access Privileges... 3 2.1.1 For one specific mailbox... 3 2.1.2 For mailboxes located within
Version 5.1 May 2006 1 Introduction... 3 2 How To - Backup Individual Emails... 3 2.1 Granting Full Mailbox Access Privileges... 3 2.1.1 For one specific mailbox... 3 2.1.2 For mailboxes located within
Lepide Exchange Recovery Manager
 Configuration Guide Lepide Exchange Recovery Manager Lepide Software Private Limited, All Rights Reserved This User Guide and documentation is copyright of Lepide Software Private Limited, with all rights
Configuration Guide Lepide Exchange Recovery Manager Lepide Software Private Limited, All Rights Reserved This User Guide and documentation is copyright of Lepide Software Private Limited, with all rights
FirstClass FAQ's An item is missing from my FirstClass desktop
 FirstClass FAQ's An item is missing from my FirstClass desktop Deleted item: If you put a item on your desktop, you can delete it. To determine what kind of item (conference-original, conference-alias,
FirstClass FAQ's An item is missing from my FirstClass desktop Deleted item: If you put a item on your desktop, you can delete it. To determine what kind of item (conference-original, conference-alias,
Configuring Controller 8.2 to use Active Directory authentication
 Proven Practice Configuring Controller 8.2 to use Active Directory authentication Product(s): Controller 8.2 Area of Interest: Infrastructure Configuring Controller 8.2 to use Active Directory authentication
Proven Practice Configuring Controller 8.2 to use Active Directory authentication Product(s): Controller 8.2 Area of Interest: Infrastructure Configuring Controller 8.2 to use Active Directory authentication
Using Logon Agent for Transparent User Identification
 Using Logon Agent for Transparent User Identification Websense Logon Agent (also called Authentication Server) identifies users in real time, as they log on to domains. Logon Agent works with the Websense
Using Logon Agent for Transparent User Identification Websense Logon Agent (also called Authentication Server) identifies users in real time, as they log on to domains. Logon Agent works with the Websense
Windows 7 Hard Disk Recovery
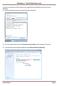 In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
Click Studios. Passwordstate. Installation Instructions
 Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Application Note. ShoreTel 9: Active Directory Integration. Integration checklist. AN-10233 June 2009
 Application Note AN-10233 June 2009 ShoreTel 9: Active Directory Integration This application note outlines the configuration required to prepare a customer s Microsoft Active Directory environment for
Application Note AN-10233 June 2009 ShoreTel 9: Active Directory Integration This application note outlines the configuration required to prepare a customer s Microsoft Active Directory environment for
CTERA Agent Sync Edition for Windows
 Quick Walkthrough CTERA Agent Sync Edition for Windows November 2012 Version 3.2 2012, CTERA Networks. All rights reserved. 1 Install CTERA Agent for Windows Tip For more detailed information, refer to
Quick Walkthrough CTERA Agent Sync Edition for Windows November 2012 Version 3.2 2012, CTERA Networks. All rights reserved. 1 Install CTERA Agent for Windows Tip For more detailed information, refer to
Enterprise Vault Instructions for Saving Items from an archive restored to a secondary mailbox in Microsoft Outlook
 Enterprise Vault Instructions for Saving Items from an archive restored to a secondary mailbox in Microsoft Outlook The following instructions were created using Microsoft Outlook 2013 on a Windows 7 computer.
Enterprise Vault Instructions for Saving Items from an archive restored to a secondary mailbox in Microsoft Outlook The following instructions were created using Microsoft Outlook 2013 on a Windows 7 computer.
User Guide. SysMan Utilities. By Sysgem AG
 SysMan Utilities User Guide By Sysgem AG Sysgem is a trademark of Sysgem AG. Other brands and products are registered trademarks of their respective holders. 2013 Sysgem AG, Lavaterstr. 45, CH-8002 Zürich,
SysMan Utilities User Guide By Sysgem AG Sysgem is a trademark of Sysgem AG. Other brands and products are registered trademarks of their respective holders. 2013 Sysgem AG, Lavaterstr. 45, CH-8002 Zürich,
OneNet Cloud Services
 OneNet Cloud Services Documentation OneNet Limited Distribution Page 1 of 19 Contents Summary... 3 Logging into Control Panel... 4 Microsoft Cloud Services Management... 6 Creating a new user (applies
OneNet Cloud Services Documentation OneNet Limited Distribution Page 1 of 19 Contents Summary... 3 Logging into Control Panel... 4 Microsoft Cloud Services Management... 6 Creating a new user (applies
Introduction. Creating an Archive file TO CREATE AN ARCHIVE FOLDER ON YOUR H: SPACE: Guide to Outlook 2010: Archiving email http://www.lse.ac.
 Guide to Outlook 2010: Archiving email http://www.lse.ac.uk/imt Contents > Creating an Archive file, Working with archived mail, Archiving email using drag and drop, Delete Archived Mail Messages, Compact
Guide to Outlook 2010: Archiving email http://www.lse.ac.uk/imt Contents > Creating an Archive file, Working with archived mail, Archiving email using drag and drop, Delete Archived Mail Messages, Compact
Using MailStore to Archive MDaemon Email
 Using MailStore to Archive MDaemon Email This guide details how to archive all inbound and outbound email using MailStore, as well as archiving any emails currently found in the users accounts in MDaemon.
Using MailStore to Archive MDaemon Email This guide details how to archive all inbound and outbound email using MailStore, as well as archiving any emails currently found in the users accounts in MDaemon.
All Tech Notes and KBCD documents and software are provided "as is" without warranty of any kind. See the Terms of Use for more information.
 Tech Note 115 Overview of the InTouch 7.0 Windows NT Services All Tech Notes and KBCD documents and software are provided "as is" without warranty of any kind. See the Terms of Use for more information.
Tech Note 115 Overview of the InTouch 7.0 Windows NT Services All Tech Notes and KBCD documents and software are provided "as is" without warranty of any kind. See the Terms of Use for more information.
Asset Track Getting Started Guide. An Introduction to Asset Track
 Asset Track Getting Started Guide An Introduction to Asset Track Contents Introducing Asset Track... 3 Overview... 3 A Quick Start... 6 Quick Start Option 1... 6 Getting to Configuration... 7 Changing
Asset Track Getting Started Guide An Introduction to Asset Track Contents Introducing Asset Track... 3 Overview... 3 A Quick Start... 6 Quick Start Option 1... 6 Getting to Configuration... 7 Changing
Configuring, Customizing, and Troubleshooting Outlook Express
 3 Configuring, Customizing, and Troubleshooting Outlook Express............................................... Terms you ll need to understand: Outlook Express Newsgroups Address book Email Preview pane
3 Configuring, Customizing, and Troubleshooting Outlook Express............................................... Terms you ll need to understand: Outlook Express Newsgroups Address book Email Preview pane
EPM Performance Suite Profitability Administration & Security Guide
 BusinessObjects XI R2 11.20 EPM Performance Suite Profitability Administration & Security Guide BusinessObjects XI R2 11.20 Windows Patents Trademarks Copyright Third-party Contributors Business Objects
BusinessObjects XI R2 11.20 EPM Performance Suite Profitability Administration & Security Guide BusinessObjects XI R2 11.20 Windows Patents Trademarks Copyright Third-party Contributors Business Objects
Public Folder Migrations
 Public Folder Migrations Microsoft Free tools vs Priasoft Introduction Many times when an Exchange migration project starts, a discussion about Public Folders arises. This document will attempt to define
Public Folder Migrations Microsoft Free tools vs Priasoft Introduction Many times when an Exchange migration project starts, a discussion about Public Folders arises. This document will attempt to define
Ultimus and Microsoft Active Directory
 Ultimus and Microsoft Active Directory May 2004 Ultimus, Incorporated 15200 Weston Parkway, Suite 106 Cary, North Carolina 27513 Phone: (919) 678-0900 Fax: (919) 678-0901 E-mail: documents@ultimus.com
Ultimus and Microsoft Active Directory May 2004 Ultimus, Incorporated 15200 Weston Parkway, Suite 106 Cary, North Carolina 27513 Phone: (919) 678-0900 Fax: (919) 678-0901 E-mail: documents@ultimus.com
Table of Contents. Changing Your Password in Windows NT p. 1. Changing Your Password in Alpha Connection.. pp. 1-3
 Table of Contents Changing Your Password in Windows NT p. 1 Changing Your Password in Alpha Connection.. pp. 1-3 Not Able to Get Outlook Express Mail Because Alpha Connection Password Expires... pp. 3-4
Table of Contents Changing Your Password in Windows NT p. 1 Changing Your Password in Alpha Connection.. pp. 1-3 Not Able to Get Outlook Express Mail Because Alpha Connection Password Expires... pp. 3-4
Databoks Remote Backup. MS Exchange Mail Level Backup
 Version 5.1 May 2006 Table of Content 1 Introduction... 3 2 How To - Backup Individual Emails... 3 2.1 Granting Full Mailbox Access Privileges... 3 2.1.1 For one specific mailbox... 3 2.1.2 For mailboxes
Version 5.1 May 2006 Table of Content 1 Introduction... 3 2 How To - Backup Individual Emails... 3 2.1 Granting Full Mailbox Access Privileges... 3 2.1.1 For one specific mailbox... 3 2.1.2 For mailboxes
Domain Controller Failover When Using Active Directory
 Domain Controller Failover When Using Active Directory Domain Controller Failover When Using Active Directory published January 2002 NSI and Double-Take are registered trademarks of Network Specialists,
Domain Controller Failover When Using Active Directory Domain Controller Failover When Using Active Directory published January 2002 NSI and Double-Take are registered trademarks of Network Specialists,
How to Migrate to MailEnable using the Migration Console
 How to Migrate to MailEnable using the Migration Console Contents 1. OVERVIEW... 2 2. MAILENABLE MIGRATION CONSOLE... 2 3. SELECT THE MIGRATION APPROACH... 2 Server Migration... 2 Domain Migration... 3
How to Migrate to MailEnable using the Migration Console Contents 1. OVERVIEW... 2 2. MAILENABLE MIGRATION CONSOLE... 2 3. SELECT THE MIGRATION APPROACH... 2 Server Migration... 2 Domain Migration... 3
Manage Public Folder Permissions
 Control CASE STUDY Panel Connecting Your Business. Anywhere. Manage Public Folder Permissions 2012 Apptix, Inc. Public folders are an optional service available to all Apptix hosted Exchange customers.
Control CASE STUDY Panel Connecting Your Business. Anywhere. Manage Public Folder Permissions 2012 Apptix, Inc. Public folders are an optional service available to all Apptix hosted Exchange customers.
Websense Support Webinar: Questions and Answers
 Websense Support Webinar: Questions and Answers Configuring Websense Web Security v7 with Your Directory Service Can updating to Native Mode from Active Directory (AD) Mixed Mode affect transparent user
Websense Support Webinar: Questions and Answers Configuring Websense Web Security v7 with Your Directory Service Can updating to Native Mode from Active Directory (AD) Mixed Mode affect transparent user
Avalanche Site Edition
 Avalanche Site Edition Version 4.8 avse ug 48 20090325 Revised 03/20/2009 ii Copyright 2008 by Wavelink Corporation All rights reserved. Wavelink Corporation 6985 South Union Park Avenue, Suite 335 Midvale,
Avalanche Site Edition Version 4.8 avse ug 48 20090325 Revised 03/20/2009 ii Copyright 2008 by Wavelink Corporation All rights reserved. Wavelink Corporation 6985 South Union Park Avenue, Suite 335 Midvale,
Video Administration Backup and Restore Procedures
 CHAPTER 12 Video Administration Backup and Restore Procedures This chapter provides procedures for backing up and restoring the Video Administration database and configuration files. See the following
CHAPTER 12 Video Administration Backup and Restore Procedures This chapter provides procedures for backing up and restoring the Video Administration database and configuration files. See the following
Customer admin guide. UC Management Centre
 Customer admin guide UC Management Centre June 2013 Contents 1. Introduction 1.1 Logging into the UC Management Centre 1.2 Language Options 1.3 Navigating Around the UC Management Centre 4 4 5 5 2. Customers
Customer admin guide UC Management Centre June 2013 Contents 1. Introduction 1.1 Logging into the UC Management Centre 1.2 Language Options 1.3 Navigating Around the UC Management Centre 4 4 5 5 2. Customers
Windows Server 2012 Directory Partition Containers- A Walk Through
 Windows Server 2012 Directory Partition Containers- A Walk Through Introduction: Active Directory Users and Computers form a centralized management console to manage User objects, computer objects, Groups,
Windows Server 2012 Directory Partition Containers- A Walk Through Introduction: Active Directory Users and Computers form a centralized management console to manage User objects, computer objects, Groups,
Restructuring Active Directory Domains Within a Forest
 C H A P T E R 1 2 Restructuring Active Directory Domains Within a Forest Restructuring Active Directory directory service domains within a forest with the goal of reducing the number of domains allows
C H A P T E R 1 2 Restructuring Active Directory Domains Within a Forest Restructuring Active Directory directory service domains within a forest with the goal of reducing the number of domains allows
ScriptLogic Active Administrator. VERSION 6 Installation Guide
 ScriptLogic Active Administrator VERSION 6 Installation Guide ACTIVE ADMINISTRATOR 6.0 INSTALLATION GUIDE II Copyright 2011 ScriptLogic Corporation. All Rights Reserved. This publication is protected by
ScriptLogic Active Administrator VERSION 6 Installation Guide ACTIVE ADMINISTRATOR 6.0 INSTALLATION GUIDE II Copyright 2011 ScriptLogic Corporation. All Rights Reserved. This publication is protected by
1 EDI Source EDI/HQ. Troubleshooting Licensing Issues. for Microsoft Windows 7 and Microsoft Windows 2008 Server
 1 EDI Source EDI/HQ Troubleshooting Licensing Issues for Microsoft Windows 7 and Microsoft Windows 2008 Server 1 Overview This document is meant to provide support for updating a software license for EDI/HQ
1 EDI Source EDI/HQ Troubleshooting Licensing Issues for Microsoft Windows 7 and Microsoft Windows 2008 Server 1 Overview This document is meant to provide support for updating a software license for EDI/HQ
Collaboration Technology Support Center Microsoft Collaboration Brief
 Collaboration Technology Support Center Microsoft Collaboration Brief September 2005 HOW TO INTEGRATE MICROSOFT EXCHANGE SERVER INTO SAP ENTERPRISE PORTAL Authors Robert Draken, Solution Architect, Comma
Collaboration Technology Support Center Microsoft Collaboration Brief September 2005 HOW TO INTEGRATE MICROSOFT EXCHANGE SERVER INTO SAP ENTERPRISE PORTAL Authors Robert Draken, Solution Architect, Comma
Solcon Online Backup. MS Exchange Mail Level Backup
 Version 5.2 Augustus 2007 Table of Content 1 Introduction... 2 2 How To - Backup Individual Emails... 2 2.1 Granting Full Mailbox Access Privileges... 3 2.1.1 For one specific mailbox...... 3 2.1.2 For
Version 5.2 Augustus 2007 Table of Content 1 Introduction... 2 2 How To - Backup Individual Emails... 2 2.1 Granting Full Mailbox Access Privileges... 3 2.1.1 For one specific mailbox...... 3 2.1.2 For
Coveo Platform 7.0. Microsoft Active Directory Connector Guide
 Coveo Platform 7.0 Microsoft Active Directory Connector Guide Notice The content in this document represents the current view of Coveo as of the date of publication. Because Coveo continually responds
Coveo Platform 7.0 Microsoft Active Directory Connector Guide Notice The content in this document represents the current view of Coveo as of the date of publication. Because Coveo continually responds
Facilities and Safety How-To Guide: Accessing and Using Your UCF Webmail Account
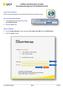 Launch Internet Explorer Click on the Internet Explorer icon at the bottom left of the computer screen. Go to the UCF Webmail Website 1. In the address bar at the top of the screen, type webmail.ucf.edu.
Launch Internet Explorer Click on the Internet Explorer icon at the bottom left of the computer screen. Go to the UCF Webmail Website 1. In the address bar at the top of the screen, type webmail.ucf.edu.
Help. F-Secure Online Backup
 Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
PineApp Surf-SeCure Quick
 PineApp Surf-SeCure Quick Installation Guide September 2010 WEB BASED INSTALLATION SURF-SECURE AS PROXY 1. Once logged in, set the appliance s clock: a. Click on the Edit link under Time-Zone section.
PineApp Surf-SeCure Quick Installation Guide September 2010 WEB BASED INSTALLATION SURF-SECURE AS PROXY 1. Once logged in, set the appliance s clock: a. Click on the Edit link under Time-Zone section.
HYPERION SYSTEM 9 N-TIER INSTALLATION GUIDE MASTER DATA MANAGEMENT RELEASE 9.2
 HYPERION SYSTEM 9 MASTER DATA MANAGEMENT RELEASE 9.2 N-TIER INSTALLATION GUIDE P/N: DM90192000 Copyright 2005-2006 Hyperion Solutions Corporation. All rights reserved. Hyperion, the Hyperion logo, and
HYPERION SYSTEM 9 MASTER DATA MANAGEMENT RELEASE 9.2 N-TIER INSTALLATION GUIDE P/N: DM90192000 Copyright 2005-2006 Hyperion Solutions Corporation. All rights reserved. Hyperion, the Hyperion logo, and
BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005
 BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005 PLEASE NOTE: The contents of this publication, and any associated documentation provided to you, must not be disclosed to any third party without
BIGPOND ONLINE STORAGE USER GUIDE Issue 1.1.0-18 August 2005 PLEASE NOTE: The contents of this publication, and any associated documentation provided to you, must not be disclosed to any third party without
Multi-Forest Exchange Consolidations
 Multi-Forest Exchange Consolidations Mindset and Best Practices - Priasoft Multi-Forest Migration? Why discuss a Multi-Forest Migration? In many larger organizations there exists a state where users, data,
Multi-Forest Exchange Consolidations Mindset and Best Practices - Priasoft Multi-Forest Migration? Why discuss a Multi-Forest Migration? In many larger organizations there exists a state where users, data,
Freshservice Discovery Probe User Guide
 Freshservice Discovery Probe User Guide 1. What is Freshservice Discovery Probe? 1.1 What details does Probe fetch? 1.2 How does Probe fetch the information? 2. What are the minimum system requirements
Freshservice Discovery Probe User Guide 1. What is Freshservice Discovery Probe? 1.1 What details does Probe fetch? 1.2 How does Probe fetch the information? 2. What are the minimum system requirements
Module 1: Introduction to Active Directory Infrastructure
 Module 1: Introduction to Active Directory Infrastructure Contents Overview 1 Lesson: The Architecture of Active Directory 2 Lesson: How Active Directory Works 10 Lesson: Examining Active Directory 19
Module 1: Introduction to Active Directory Infrastructure Contents Overview 1 Lesson: The Architecture of Active Directory 2 Lesson: How Active Directory Works 10 Lesson: Examining Active Directory 19
Cisco WebEx Mail Administrator's Guide
 Cisco WebEx Mail Administrator's Guide Copyright 1997-2009 Cisco Systems, Inc. and/or its affiliated entities. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are
Cisco WebEx Mail Administrator's Guide Copyright 1997-2009 Cisco Systems, Inc. and/or its affiliated entities. All rights reserved. WEBEX, CISCO, Cisco WebEx, the CISCO logo, and the Cisco WebEx logo are
Getting Started with the DCHR Service Desk. District Service Management Program
 Getting Started with the DCHR Service Desk District Service Management Program October 30, 2008 Contacting the District Service Management Group You can access the District Service Management group s website
Getting Started with the DCHR Service Desk District Service Management Program October 30, 2008 Contacting the District Service Management Group You can access the District Service Management group s website
Attention: This is an old version of the GALsync Upgrade Instructions, which was published for GALsync 5.1.
 Attention: This is an old version of the GALsync Upgrade Instructions, which was published for GALsync 5.1. The current documentation for GALsync is available for download here: http://www.netsec.de/en/products/galsync/documentation.html
Attention: This is an old version of the GALsync Upgrade Instructions, which was published for GALsync 5.1. The current documentation for GALsync is available for download here: http://www.netsec.de/en/products/galsync/documentation.html
Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de Exchange 2003 - User, groups, distribution list and contact management with Windows 2003 Active
Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de Exchange 2003 - User, groups, distribution list and contact management with Windows 2003 Active
