Investigation of the Risk of Electromagnetic Security on Computer Systems
|
|
|
- Alyson Pitts
- 8 years ago
- Views:
Transcription
1 Investigation of the Risk of Electromagnetic Security on Computer Systems Changlin Zhou, Member, IACSIT, IEEE, Qun Yu, and Litao Wang Abstract Electromagnetic environmental effects (E3) and compromising emanations (CE) are two centrally important aspects of computer closely related to electromagnetic security. This paper investigates the electromagnetic compatibility (EMC) for functional safety and emission security on computer systems. Initially, the EMC security issues for the electromagnetic emission of computer systems as well as the susceptibility of tremendously increased critical circuits are presented. Then, impact of electromagnetic security in ubiquitous applications based on computer technology is discussed, which encompasses the damage of E3 and risk potential, CE security limits and experiment example of TEMPEST. Finally, the protection means of computer electromagnetic security are provided. The paper states the need for the guidelines on controlling EMC and the process of CE to achieve electromagnetic security of computer systems. Index Terms Electromagnetic compatibility (EMC), electromagnetic environmental effects (E3), compromising emanations (CE), functional safety, emission security, computer I. INTRODUCTION One of the important problems peculiar to computer systems is electromagnetic emission and immunity, as known as EMC for electromagnetic security [1], [2].All electronic technologies rely on computer systems which are being applied in very sensitive installations, and can suffer from degraded functionality, malfunctions and even permanent damage due to electromagnetic interference (EMI) [3], [4]. The computer systems may be commercial or industrial performance dependent on the correct operation, and may be military or government sensitivity where functional safety or even information security is at risk [5], [6]. As computer systems is increasingly used in safety-related applications, the real world risks of electromagnetic security are involved twofold [7].There are the relatively functional safety damage of disruption of computer system operations from external influences [8]. And, there are the emission security risks of sensitive information leaking out of the computer systems [9]. Consequently, with an increasing risk of electromagnetic security for computer systems architecture due to inadequate EMC can result in hazardous situations [10], [11]. Important issues of EMC-related functional safety and compromising emanations (CE) may be correctly addressed [12]-[14]. This paper is to raise the awareness of electromagnetic Manuscript received June 24, 2011; revised November 24, C. l. Zhou is with Zhengzhou Information Engineering University, Zhengzhou, , P.R. China ( Q. Yu and L. T. Wang are a Ph.D candidate at Zhengzhou Information Science and Technology Institute, Zheng zhou, P.R. China( fishes2009@126.com; tor.3769@163.com). security issues for computer systems and networks. It describes to achieve due diligence for functional safety, and introduces the comprehensive risk defending methodology to control CE for information security. II. ELECTROMAGNETIC SECURITY OF COMPUTER EMC is the scientific and engineering discipline of ensuring that electrical or electronic technologies not emitting high levels of EM energies that cause excessive EMI [1]. It is also concerned with ensuring that they do not suffer untoward EMI during operation. Achieving electromagnetic security and safety of computer systems means that risks due to EMC will remain no worse than tolerable over the anticipated lifetime. A. EMC Issues of Computer Systems The EMC of computer systems is the ability of system or networks to function satisfactorily in its Electromagnetic environment (EME) without introducing intolerable EMI to anything in that environment. Modern computers and other types of information equipment using microprocessors and IC devices appear to be vulnerable and sensitive to EMI. Following the scale down of the IC technology, the operating frequency has increased and the supply voltage has become lower, the EMC problems at computer systems level have recently risen in importance. The two major keywords in EMC issues are shown as Fig.1, and the characteristics of emissions and susceptibility must remain at least adequate. Susceptibility Eectromagnetic Interference Coupling Power PC Data lines Emission Eectromagnetic Information Security Network Fig. 1. EMC and security problem on computer systems. Computer systems susceptibility to EMI is becoming a major concern, with the multiplication of powerful electromagnetic sources such as mobile phones, high speed networks, wireless systems and intentional EMI (IEMI). High frequency wave and power pulse are received by the systems, which captures some energy that may flow to the interior, the board and finally to the component. As the supply voltages become lower, these devices manage various signals such as digital signal, communication protocol, external memory bus or external interrupt signal, which are potential paths to introduce EMI into inside circuits. The emission due to computer clock and system frequency is continuously increased, and may jeopardize the correct 93
2 behavior of other devices. The parasitic emission energy may be high enough to jeopardize the EMC of the whole electronic system. Finally, they cause damages on interior chips or some malfunction to systems. On the other hand, there are emission security risks of computer system for processing information. The EMC performance of computers could have implications for functional safety or security when these devices are used in communications systems and information equipments, safety-critical architecture or critical infrastructure. B. EMC for Security of Computer Systems The challenge of achieving EMC in the design of computer systems, particularly in the functional safety requirements and information processing security, has increased the needs for understanding, evaluating and improving the electromagnetic security performance of computer systems. Robust operation of complex systems and networks is essential for the computer deployed increasingly to monitor vital control and safety functions. Similar reliability standards are necessary in many other security appliances, ranging from nationality security to communications and even some consumer appliances. Safety functions are increasingly performed by integrated electronic systems, such as computer systems architecture and networks. These computer systems are designed in such a way as to prevent dangerous failures from occurring or to control such dangerous failures to a tolerable level of occurrence. Such dangerous failures may be the consequence of random or systematic hardware failures, software errors, human errors or environmental influences including electromagnetic disturbances and IEMI. With respect to EMC, the correct and safe operation of a computer system depends on the electromagnetic environment of intended use, the immunity level of the integrated system, mitigation measures applied, and the performance criteria applied. Emissions security includes conductive coupling such as power and network wires, and radiated coupling acts as an equivalent antenna and transmits undesired electromagnetic waves. Typical compromising emanation security problems appear due to undesired coupling of data wire and ribbon cables in direct and indirect emanations from computer display, and keyboards and network, when data is encoded with logic states transition and electromagnetic waves are eventually emitted. Electromagnetic emanations may interact with indirect emanations which induce new types of radiations. And these unintended emanations manifest themselves as modulations or inter-modulations or as carrier signals and their harmonics, and may have better propagation than direct emanations for information security. III. IMPACT OF ELECTROMAGNETIC SECURITY A. EMI Impact Analysis on Computer Systems EMI impact is about the hazard and risk associated with electrical and electromagnetic environments. The impact of electromagnetic is perhaps the best captured in the immunity limits to computer systems. The EMI coupling can occur either via antennas and sensors, denoted front-door coupling, or as back-door coupling, i.e. through imperfect shields or to cables. A basic decomposition of an EMI impact can be described as the schematic sketch as Fig.2. There are more than scientific curiosities to fuel the research of EMC. Fig. 2. Shown is a schematic decomposition of EMC impact The source (1.) is creating an electromagnetic field or a voltage and current transient which propagate along the coupling path (2.) The source can be categorized according to many characteristics, and mode of emission must be considered. The coupling path (2.) includes conduction as voltage and current propagating along a conductor, and radiation as electric and magnetic energy emitting into the space. The system exterior (3.) will highly influence the coupling of the energy to the system interior (4.) and finally interact with the response or impact of potential critical component in the system (5.). To reduce the impact of the affected system, the EMC is done by minimizing the transfer function between the source and the receiver. So to the typical computer systems, the disturbances source is expressed in the function of S( f, r, θ), which is figured by time variable frequency variable f, space variable r and orientation variable θ. Also the coupling way and target interfered response elements are expressed by C( f, r, θ) and R( f, r, θ). Then the EMC performance of the system can be assessed with inequation (1) when electromagnetic interference happens. S ( θ ) C( θ ) > R( θ ) where, the interference safety margin M can be given as an equation (2). M = R( θ) S( θ) C( θ) Obviously, M > 0 indicates a potential interference, M < 0 that is compatible with both work, M=0 that is in critical condition. Interference of the corresponding parameter is the EMC prediction equation based on the actual mathematical model for computer systems, combined with analysis of the equation and the corresponding solutions. Normally, -6 to -10 db for M is taken to be the safety factor, so resistance based on the actual evaluation results. It is expected to competently ensure a minimum margin M of the desired levels of safety risks. For higher safety integrity levels it may be necessary to have a higher compatibility level of confidence. Thus the susceptibility or immunity levels specified in EMC standard series may be sufficient for safety-related functions implemented. The computer system functional safety perspective on EMC must be addressed, and provide guidance for evaluating and designing to the appropriate requirements. (1) (2) 94
3 B. Risk Potential of Electromagnetic Effect The risk of E3 upon the operational capability of computer systems, and electromagnetic pulse (EMP), high power electromagnetic (HPEM) or IEMI sources is mostly considered in the victim system [2]. Computer is sensitive to exposure to EMP, as any cables running in and out of the equipment will behave very much like antennae, in effect guiding the high voltage transients into the system interior. Computers used in communications systems, and industrial control applications, and embedded in military equipment are all potentially vulnerable [5], [15]. There are several threat phenomena and effects that can take place and cause serious problems of interference or damage for computer systems. The different upset events can be classified according to risk assessment of IEMI or HPEM environments disturbance scale [16]. An alternate method, based on the variables threat level, consequence, and susceptibility of the computer systems and networks is suggested [17]. These three variables form a vulnerability vector in the variable space spanned which is shown as Fig.3. The scaling of these variables can be collectively be weighted and estimated by forming a numbered scale and grading. In a final assessment stage the values of all three quantities are concluded into the general risk potentials of the considered electromagnetic environment. TABLE I: THREAT LEVEL VARIABLES CLASSES CHARACTERIZATION Category Effect Description Value 0 No effects Functional safety <10V/m, <1kV 1 2 Cause disturbances Strong interference Interference, Wrong data Crash, State change Loss of function and 3 Mission kills data Destruction, Repair or 4 Physical damage replace 100V/m,10kV >1kV/m,100kV 10kV/m,1MV 100kV/m, 10MV TABLE II: CONSEQUENCE VARIABLES CLASS CHARACTERIZATION Category Description Lost Value 0 No connections any cable, battery supply <10% 1 Stationary computer hos mains power feed and data and wiring 10% 2 Computer systems architecture, platform and >25% connections local area network 3 Computer network, large associate platform and communication network 50% 4 Complex architecture, infrastructure and global information grid >80% Susceptibility. The susceptibility term expressed the computer systems to perform without degradation in the presence of an electromagnetic disturbance. Standard EMC susceptibility tests are made by subjecting the objects under test for disturbances and field levels for different situation and their corresponding upset events. Susceptibility terms can be estimated from susceptibility tests performed on subsystems or equipment either considered critical for the operation of the facility or easily accessible by an electromagnetic disturbance and standard EMC requirements as Table III. Fig. 3. Risk potential of radiated environments effects Threat level. The parameter threat level, where a high threat level characterizes a high risk, describes the ability of the HPEM environment to cause IEMI effects. The threat level is perhaps the aspect of an HPEM environment which has been mostly investigated and evaluated by the EMC community. In related publications attributes of the radiated field, i.e. amplitude (Epeak), far radiated voltage (r Epeak) and waveform characteristics, and the frequency range is from 100MHz to 10GHz. The threat level on computer systems can be represented by a threat vector as Table 1. Consequence. The consequence term is to investigate the number of existing connections in relation to the attacked computer systems, and a successful attack on a well connected system is often higher than one that is not connected. The criticality of these connections is of importance as a centralized system and larger grid infrastructure would collapse a great number of other systems would be directly affected. Loss of connections between systems could be a consequence of a successful IEMI attack. The consequence could be measured as lost connections and represented by a numbered scale and complication vector as Table II. TABLE III: SUSCEPTIBILITY VARIABLES CLASS CHARACTERIZATION Category Description Value 0 Highly sophisticated system, robust hardening strategies 1 No susceptibility 2 No sensitivity 3 4 Sensitivity, common equipment not hardened against HPEM Less than the level of immunity for common equipment IV. IMPACT OF EMANATIONS SECURITY Margin of at least 16.5 db of MNFS Margin of at least 6 db of MNFS MIL-STD-461F requirements Commercial EMC standard tests No commercial EMC tests Information leakage via electromagnetic emanation or emanations security (EMSEC) from computer systems is a well known security risk. An eavesdropper receiving electromagnetic emanations does not leave evidence of their activity, and the victim notices nothing, various countermeasures have been proposed for such TEMPEST problems. 95
4 A. Emission Security Limits for Computer Systems Emission limits and test procedures require its actual conformance standards for electromagnetic security of computer systems. Current means for such efforts could be the work that leads to the emission limits for EMC, to reduce the risk of information carrying emanations. The emissions limits therefore have to be based on an understanding of reasonable best-case assumptions of the minimal background noises that the eavesdropper faces even under good receiving conditions. One approach to designing an emission security standard is to provide an upper bound for the signal-to-noise ratio S/N that an eavesdropper could achieve. The major contributing factors be considered are shown in equation (3). EB Ga G p S / N = a a E f d w where E B is the maximum field strength that the test standard permits, B is the impulse bandwidth used in the tes ad is the free-space path loss, aw is the additional attenuation caused by building walls, Ga is the gain of the best directional antenna, Gp is the processing gain, E nb is the field strength of natural and man-made radio noises at the location of the eavesdropping antenna within a bandwidth B, fr is the noise factor of the eavesdropper receiver. Suggested emission limits require S/N < 0 db and use all of the just listed parameters in equation (3), and a result can be ended up with E B and E nb strength. It would be desirable if the suggested limits are verifiable with EMC measurement equipment. The EMC standard such as MIL-STD-461F provides in its requirement RE102 for mobile computer systems radiated electric limits field to those suggested here.the limits discussed here are aimed at products in which emission security is achieved by signal suppression and shielding and attenuation to be achieved protection standards. B. The Recovered Result from Electromagnetic Emission Computer systems can emit electromagnetic signals from which eavesdroppers may reconstruct processed data at some distance, known as TEMPEST issues on investigations of CE referring to national security information [10]. TEMPEST is often used broadly for the entire field of emission security for information systems from potential eavesdroppers and the ability to intercept and interpret those signals from other sources. In typical computer communication or data processing systems, undesired signal emanations will probably be detected when the equipment must be proven TEMPEST hazard-free. The most easily recognized CE is the RED (sensitive information) signal. This type of CE is generated as a carrier being usually amplitude or angle-modulated by the RED data signal. The mostly impulsive emanations of TEMPEST signals can be radiated into space or coupled into external conductors. The modulated spurious carrier and impulsive emanations with the operating computer can be seen on a line or through the air. Here is an example of TEMPEST information from computer systems, shown as Fig.4. The (a) is PC screen display word message, and the (b) is eavesdropper from a nb r (3) monitor at 10m distance. This result shows that we can monitor emanated electromagnetic signal corresponding to the screen image, and that the countermeasures are important and necessary. Fig. 4. Displaying the TEMPEST information. V. PREVENTION OF ELECTROMAGNETIC SECURITY The risk avoidance of a lack of proper function due to IEMI or HPEM and the lack of confidentiality due to EMSEC can be advanced level of the EM mitigation of the computer systems. An integral design guideline is needed to achieve an optimum cost-effective integration of technologies at the level of chip, board, cable, network, and systems architecture. A. EMC Design Guidelines for Functional Safety Traditional approaches to improving immunity include adding filtering and shielding to protect the electronic systems against IEMI. Specific design techniques or embedded software approaches may also be used. Focusing on the microcontroller world, part of the hardware problems due to EM susceptibility may be handled by using software solutions aiming at reinforcing the robustness of the embedded systems. The effectiveness of defensive software to protect computer systems against IEMI or HPEM disturbances is strongly dependent on the application and the threat level. And, in the case of more powerful disturbance, hardware-based recovery mechanisms and redundant storage of the most crucial system might help handle this type of interference. Four important EMC design guidelines to functional safety are often adopted to implement early in the computer design process. Firstly, minimize the loop areas associated with high frequency power and signal currents. The path of least impedance at high frequencies is generally the path of least inductance, and currents return as close as possible to the path of the outgoing curren which are generally the path that minimizes the loop area. Secondly, don t spli gap or cut the signal return plane. The thumb rule is to provide one solid plane for returning all signal currents. Thirdly, don t locate high speed circuitry between connectors as relatively efficient antennas can easily develop potential differences of mill volts. These voltages can drive currents onto attached cables causing a product to exceed radiated emissions requirements. Fourthly, control signal transition times which can cause signal integrity and thermal problems. The common methods use a logic family as fast as the application requires, put a resistor or a ferrite in series and a capacitor in parallel with a devices output. Some good design guidelines of circuit board layout generally offer good advice. A device on the board that communicates with a device off the board through a 96
5 connector should be located as close as possible to that connector. All off-board communication from a single device should be routed through the same connector. Active digital components should be selected that have maximum acceptable off-chip transition times. Critical signal traces should be buried between power or ground planes. A trace with a propagation delaying more than half the transition time of the signal it carries must have a matched termination. Signals with high-frequency content should not be routed beneath components used for board input and output (I/O). The length and the number of vias in high-frequency nets should be minimized. Connections should be made by using via adjacent to the power or ground pad of the component. Total computer systems architecture level guidelines for EM safety threats are based on two factors, which are general shielding of systems and filtering of I/O wiring. Metal shielding or thick concrete walls can achieve system protection. Protecting inputs and outputs is the main issue, and wires act as antennas special should be considered. The protections against IEMI and E3 are based on a breakthrough filtering technology. This filtering specifically protects the electronics against intentional aggressive signals produced by the EMP. The response time of the filtering technology is extremely short and energy absorption and shunting capabilities are extremely high. And the protection device continuously provides the rated voltage and current to the systems. B. TEMPEST Prevention Design Guidelines The prevention of TEMPEST problems can best be accomplished by being attentive to every stage of the computer systems design and development. And the most prevalent methods seem to be following RED/BLACK separation, shielding the equipmen filtering signals before they leave the facility, using proper grounding techniques, and using isolators on signal lines. RED/BLACK separation can reduce the RED possibilities of CE jumping on TEMPEST channels. Shielding keeps your signals inside an area, whether a computer case is any room. Filtering takes a set of signals in and usually only lets one signal out. Grounding or proper grounding with the path of least resistance for a conductor is to ground and not along the conductor away from your space. Due to the many ways that information is processed in equipmen there are many ways that CE can be generated. It is nearly impossible to completely prevent the generation of such CE. Therefore, the TEMPEST design objectives should keep the amplitude and frequency spectrum of CE as low as possible below the limi to prevent RED signals from coupling lines or circuits, and to prevent emanations from escaping from the systems through electromagnetic or acoustical radiation. And the whole defense in depth TEMPEST consideration is the design of equipment to meet TEMPEST requirements, the installation of infrastructure to maximize integrity, and the development of national security systems to utilize effective hardening strategies and hardware countermeasures. Additionally, computer systems architecture should be designed by using TEMPEST tested to verify compatible with CE requirements. Other security countermeasures can be against compromising emanations, such as low emission laptops, effective software protection technique and a suitable jamming scheme as countermeasures against eavesdropping [18], [19]. VI. CONCLUSION The important EMC problem related functional safety and emanations security to the computer systems architecture is electromagnetic security. The EME especially IEMI with the operation of equipment grows out of the electromagnetic effects on systems. Computer systems information leakage as TEMPEST problem may disclose emanations security from the sources which process plaintext and security data. There are some guidance to deal with EMC, to achieve electromagnetic security of computer architecture, and some defending methodology to control E3 damage and CE for information systems. A final note is that the implementation of comprehensive electromagnetic hardening would have a very interesting side effec which being a substantial reduction of the levels of electromagnetic security risk for computer and networking equipment. The means and methods have been outlined, as have some defensive measures in an area which is bound to attract significant funding in the near future work. REFERENCES [1] Requirements for the Control of Electromagnetic Interference Characteristics of Subsystems and Equipmen Department of Defense Interface Standard, MIL-STD-461F, December [2] Electromagnetic environmental effects requirements for systems, Department of Defense Interface Standard, MIL-STD-464C, December [3] AECTP 250: Electrical and Electromagnetic Environmental Conditions. Nato Letter of Promulgation. February [4] S. John, J. Foster, and E. Gjelde, Report of the Commission to Assess the Threat to the United States from Electromagnetic Pulse (EMP) Attack. USA Critical National Infrastructures. April [5] F. Sabath and H. Garbe, Risk potential of radiated HPEM environments, IEEE International Symposium on Electromagnetic Compatibility, Aug. 2009: [6] IET: Electromagnetic Compatibility for Functional Safety. The Institution of Engineering and Technology, [7] E. Keith Armstrong, EMC for Functional Safety: Applying Risk Management to EMC, Published by Kind Permission of the EMC Journal. [8] A. Ogunsola, and B. Jaekel, EMC and Functional Safety Requirements for Integrated Electronics Systems, IET International Conference on System Safety. 2008: 1-7. [9] G. Locke and D. Patrick. Gallagher, Information Security. Recommended Security Controls for Federal Information Systems and Organizations, NIST Special Publication [10] D. James. Heimberg, Emission Security: Reducing the emissions of Information Technology reduces the risk of information loss. White Paper Leverage Information Systems. April 6, [11] J. Cheryl. Roby, Policy on Wireless Communications: Protecting National Security Information. CNSSP No.17, May [12] W. A Radasky, Protection of commercial installations from the high-frequency electromagnetic threats of HEMP and IEMI using IEC standards, Asia-Pacific International Symposium on EMC, April 12-16, 2010: [13] ITU-T K.81: HPEM immunity guide for telecommunication systems, Telecommunication Standardization Sector of ITU, November [14] W. A. Radasky, Intentional Electromagnetic Interference (IEMI) and Its Impact on the U.S. Power Grid. Meta-R-323, January [15] M. Camp and H. Garbe, Susceptibility of personal computer systems to fast transient electromagnetic pulses, IEEE Trans. EMC, vol. 48, no. 4,pp , November
6 [16] D. Giri and F. Tesche, Classification of intentional electromagnetic environments (IEME), IEEE Trans. EMC, vol. 46, no. 3, pp August [17] D. Mansson. M. Backstrom, and R. Thottappillil, Classifying facilities with respect to Intentional EMI, IEEE International Symposium on EMC, 2009: [18] D. L. Zhu, P. He, and J. Q Zhang, Research of key problem of receiving and recovery of signal based on wide band receiver, 2010 International Conference on Internet Technology and Applications, [19] S. Yasunao and A. Yoshiharu, Jamming technique to prevent information leakage caused by unintentional emissions of PC video signals, IEEE International Symposium on EMC, 2010: Changlin Zhou (IEEE, IACSIT) was born in He received the B.S degree in physical electron from Zhengzhou University in 1983 and the M.S. degree in communications and information systems from Zhengzhou information engineering university in He is an associate professor at Zhengzhou Information Engineering University. His research interests include EMC, circuit & systems design, computer security, system reliability analysis. Qun Yu was born in He received the B.S degree and the M.S. degree in computer science and technology from Electric Engineering Institute in 2003 and 2007, respectively. He is a Ph.D candidate at Zhengzhou Information Science and Technology Institute. His research interests include electromagnetic protection, EMC Litao Wang was born in He received the M.S. degree in computer science and technology from Zhengzhou Information Science and Technology Institute in He is a Ph.D. candidate at Zhengzhou Information Science and Technology Institute. His research interests include information security, EMC. 98
EMC Standards: Standards of good EMC engineering
 Electromagnetic Compatibility (EMC) IEEE Definition Origin, control, and measurement of electromagnetic effects on electronic and biologic systems. IEEE EMC Society Areas of Interest EMC Standards: Standards
Electromagnetic Compatibility (EMC) IEEE Definition Origin, control, and measurement of electromagnetic effects on electronic and biologic systems. IEEE EMC Society Areas of Interest EMC Standards: Standards
Grounding Demystified
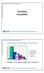 Grounding Demystified 3-1 Importance Of Grounding Techniques 45 40 35 30 25 20 15 10 5 0 Grounding 42% Case 22% Cable 18% Percent Used Filter 12% PCB 6% Grounding 42% Case Shield 22% Cable Shielding 18%
Grounding Demystified 3-1 Importance Of Grounding Techniques 45 40 35 30 25 20 15 10 5 0 Grounding 42% Case 22% Cable 18% Percent Used Filter 12% PCB 6% Grounding 42% Case Shield 22% Cable Shielding 18%
Harmonics and Noise in Photovoltaic (PV) Inverter and the Mitigation Strategies
 Soonwook Hong, Ph. D. Michael Zuercher Martinson Harmonics and Noise in Photovoltaic (PV) Inverter and the Mitigation Strategies 1. Introduction PV inverters use semiconductor devices to transform the
Soonwook Hong, Ph. D. Michael Zuercher Martinson Harmonics and Noise in Photovoltaic (PV) Inverter and the Mitigation Strategies 1. Introduction PV inverters use semiconductor devices to transform the
AVX EMI SOLUTIONS Ron Demcko, Fellow of AVX Corporation Chris Mello, Principal Engineer, AVX Corporation Brian Ward, Business Manager, AVX Corporation
 AVX EMI SOLUTIONS Ron Demcko, Fellow of AVX Corporation Chris Mello, Principal Engineer, AVX Corporation Brian Ward, Business Manager, AVX Corporation Abstract EMC compatibility is becoming a key design
AVX EMI SOLUTIONS Ron Demcko, Fellow of AVX Corporation Chris Mello, Principal Engineer, AVX Corporation Brian Ward, Business Manager, AVX Corporation Abstract EMC compatibility is becoming a key design
EMC STANDARDS STANDARDS AND STANDARD MAKING BODIES. International. International Electrotechnical Commission (IEC) http://www.iec.
 EMC STANDARDS The EMC standards that a particular electronic product must meet depend on the product application (commercial or military) and the country in which the product is to be used. These EMC regulatory
EMC STANDARDS The EMC standards that a particular electronic product must meet depend on the product application (commercial or military) and the country in which the product is to be used. These EMC regulatory
Nexus Technology Review -- Exhibit A
 Nexus Technology Review -- Exhibit A Background A. Types of DSL Lines DSL comes in many flavors: ADSL, ADSL2, ADSL2+, VDSL and VDSL2. Each DSL variant respectively operates up a higher frequency level.
Nexus Technology Review -- Exhibit A Background A. Types of DSL Lines DSL comes in many flavors: ADSL, ADSL2, ADSL2+, VDSL and VDSL2. Each DSL variant respectively operates up a higher frequency level.
Video eavesdropping- RF
 Security : Forensic Signal Analysis: MPHIL ACS 2009 Security : Forensic Signal Analysis Video eavesdropping- RF Y.K. Roland Tai 1. Introduction 2. History of TEMPEST 3. Type of RF leakages 4. Counter-measures.
Security : Forensic Signal Analysis: MPHIL ACS 2009 Security : Forensic Signal Analysis Video eavesdropping- RF Y.K. Roland Tai 1. Introduction 2. History of TEMPEST 3. Type of RF leakages 4. Counter-measures.
White Paper: Electrical Ground Rules
 Acromag, Incorporated 30765 S Wixom Rd, Wixom, MI 48393 USA Tel: 248-295-0880 Fax: 248-624-9234 www.acromag.com White Paper: Electrical Ground Rules Best Practices for Grounding Your Electrical Equipment
Acromag, Incorporated 30765 S Wixom Rd, Wixom, MI 48393 USA Tel: 248-295-0880 Fax: 248-624-9234 www.acromag.com White Paper: Electrical Ground Rules Best Practices for Grounding Your Electrical Equipment
Application Note AN:005. FPA Printed Circuit Board Layout Guidelines. Introduction Contents. The Importance of Board Layout
 FPA Printed Circuit Board Layout Guidelines By Paul Yeaman Principal Product Line Engineer V I Chip Strategic Accounts Introduction Contents Page Introduction 1 The Importance of 1 Board Layout Low DC
FPA Printed Circuit Board Layout Guidelines By Paul Yeaman Principal Product Line Engineer V I Chip Strategic Accounts Introduction Contents Page Introduction 1 The Importance of 1 Board Layout Low DC
Electromagnetic Compatibility Considerations for Switching Power Supplies
 Electromagnetic Compatibility Considerations Characterization of the EMI problem requires understanding the interference source Switching power supplies generate Electromagnetic Interference (EMI) by virtue
Electromagnetic Compatibility Considerations Characterization of the EMI problem requires understanding the interference source Switching power supplies generate Electromagnetic Interference (EMI) by virtue
Common Mode Choke Filtering Improves CMRR in Ethernet Transformer Applications. Application Note. June 2011
 Common Mode Choke Filtering Improves CMRR in Ethernet Transformer Applications June 2011 Application Note Common mode chokes provide an effective EMI filtering solution for Ethernet transformer applications.
Common Mode Choke Filtering Improves CMRR in Ethernet Transformer Applications June 2011 Application Note Common mode chokes provide an effective EMI filtering solution for Ethernet transformer applications.
SECTION 2 TECHNICAL DESCRIPTION OF BPL SYSTEMS
 SECTION 2 TECHNICAL DESCRIPTION OF SYSTEMS 2.1 INTRODUCTION Access equipment consists of injectors (also known as concentrators), repeaters, and extractors. injectors are tied to the backbone via fiber
SECTION 2 TECHNICAL DESCRIPTION OF SYSTEMS 2.1 INTRODUCTION Access equipment consists of injectors (also known as concentrators), repeaters, and extractors. injectors are tied to the backbone via fiber
USB 3.0* Radio Frequency Interference Impact on 2.4 GHz Wireless Devices
 USB 3.0* Radio Frequency Interference Impact on 2.4 GHz Wireless Devices White Paper April 2012 Document: 327216-001 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE,
USB 3.0* Radio Frequency Interference Impact on 2.4 GHz Wireless Devices White Paper April 2012 Document: 327216-001 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE,
Simulation and Design of Printed Circuit Boards Utilizing Novel Embedded Capacitance Material
 Simulation and Design of Printed Circuit Boards Utilizing Novel Embedded Capacitance Material Yu Xuequan, Yan Hang, Zhang Gezi, Wang Haisan Huawei Technologies Co., Ltd Lujiazui Subpark, Pudong Software
Simulation and Design of Printed Circuit Boards Utilizing Novel Embedded Capacitance Material Yu Xuequan, Yan Hang, Zhang Gezi, Wang Haisan Huawei Technologies Co., Ltd Lujiazui Subpark, Pudong Software
CONDUCTED EMISSION MEASUREMENT OF A CELL PHONE PROCESSOR MODULE
 Progress In Electromagnetics esearch C, Vol. 42, 191 203, 2013 CONDUCTED EMISSION MEASUEMENT OF A CELL PHONE POCESSO MODULE Fayu Wan *, Junxiang Ge, and Mengxiang Qu Nanjing University of Information Science
Progress In Electromagnetics esearch C, Vol. 42, 191 203, 2013 CONDUCTED EMISSION MEASUEMENT OF A CELL PHONE POCESSO MODULE Fayu Wan *, Junxiang Ge, and Mengxiang Qu Nanjing University of Information Science
Analysis of Immunity by RF Wireless Communication Signals
 64 PIERS Proceedings, Guangzhou, China, August 25 28, 2014 Analysis of Immunity by RF Wireless Communication Signals Hongsik Keum 1, Jungyu Yang 2, and Heung-Gyoon Ryu 3 1 EletroMagneticwave Technology
64 PIERS Proceedings, Guangzhou, China, August 25 28, 2014 Analysis of Immunity by RF Wireless Communication Signals Hongsik Keum 1, Jungyu Yang 2, and Heung-Gyoon Ryu 3 1 EletroMagneticwave Technology
30 In Compliance October 2014 www.incompliancemag.com
 30 In Compliance October 2014 www.incompliancemag.com Medical Devices in a Wireless World BY IVAYLO TANKOV While wireless technology is now an integral component of a wide variety of manufactured products,
30 In Compliance October 2014 www.incompliancemag.com Medical Devices in a Wireless World BY IVAYLO TANKOV While wireless technology is now an integral component of a wide variety of manufactured products,
Radiated emission measurement of a cell phone processor module using TEM cell
 , pp.48-53 http://dx.doi.org/10.14257/astl.2013.28.09 Radiated emission measurement of a cell phone processor module using TEM cell Fayu Wan 1,2*, Qi Liu 3, Jian Shen 3, Jin Wang 3 and Nigel Linge 4 1
, pp.48-53 http://dx.doi.org/10.14257/astl.2013.28.09 Radiated emission measurement of a cell phone processor module using TEM cell Fayu Wan 1,2*, Qi Liu 3, Jian Shen 3, Jin Wang 3 and Nigel Linge 4 1
1+1 PROTECTION WITHOUT RELAYS USING IDT82V2044/48/48L & IDT82V2054/58/58L HITLESS PROTECTION SWITCHING
 1+1 PROTECTION WITHOUT RELAYS USING IDT82V2044/48/48L & IDT82V2054/58/58L APPLICATION NOTE AN-357 1.0 INTRODUCTION In today's highly competitive market, high quality of service, QOS, and reliability is
1+1 PROTECTION WITHOUT RELAYS USING IDT82V2044/48/48L & IDT82V2054/58/58L APPLICATION NOTE AN-357 1.0 INTRODUCTION In today's highly competitive market, high quality of service, QOS, and reliability is
UNDERSTANDING AND CONTROLLING COMMON-MODE EMISSIONS IN HIGH-POWER ELECTRONICS
 Page 1 UNDERSTANDING AND CONTROLLING COMMON-MODE EMISSIONS IN HIGH-POWER ELECTRONICS By Henry Ott Consultants Livingston, NJ 07039 (973) 992-1793 www.hottconsultants.com hott@ieee.org Page 2 THE BASIC
Page 1 UNDERSTANDING AND CONTROLLING COMMON-MODE EMISSIONS IN HIGH-POWER ELECTRONICS By Henry Ott Consultants Livingston, NJ 07039 (973) 992-1793 www.hottconsultants.com hott@ieee.org Page 2 THE BASIC
with Component Rating A Simple Perspective
 Cat-6A UTP and Shielded with Component Rating A Simple Perspective Asef Baddar RCDD, DCD Sr. Technical Manager Leviton Middle East Category Specifications Agenda Terminology International & North America
Cat-6A UTP and Shielded with Component Rating A Simple Perspective Asef Baddar RCDD, DCD Sr. Technical Manager Leviton Middle East Category Specifications Agenda Terminology International & North America
Radiated Emission and Susceptibility
 Radiated Emission and Susceptibility Tzong-Lin Wu, Ph.D. EMC Lab Department of Electrical Engineering National Taiwan University Differential-Mode v.s. Common-mode Currents 1 Differential-Mode v.s. Common-mode
Radiated Emission and Susceptibility Tzong-Lin Wu, Ph.D. EMC Lab Department of Electrical Engineering National Taiwan University Differential-Mode v.s. Common-mode Currents 1 Differential-Mode v.s. Common-mode
Current Probes, More Useful Than You Think
 Current Probes, More Useful Than You Think Training and design help in most areas of Electrical Engineering Copyright 1998 Institute of Electrical and Electronics Engineers. Reprinted from the IEEE 1998
Current Probes, More Useful Than You Think Training and design help in most areas of Electrical Engineering Copyright 1998 Institute of Electrical and Electronics Engineers. Reprinted from the IEEE 1998
11. High-Speed Differential Interfaces in Cyclone II Devices
 11. High-Speed Differential Interfaces in Cyclone II Devices CII51011-2.2 Introduction From high-speed backplane applications to high-end switch boxes, low-voltage differential signaling (LVDS) is the
11. High-Speed Differential Interfaces in Cyclone II Devices CII51011-2.2 Introduction From high-speed backplane applications to high-end switch boxes, low-voltage differential signaling (LVDS) is the
Interfacing electrification and system reliability. Earthing of AC and DC railways 4,10,13
 Interfacing electrification and system reliability Roger White Professional Head of Electrification and Plant Rail Abstract Integration is the term given to ensuring that the different elements of an electrified
Interfacing electrification and system reliability Roger White Professional Head of Electrification and Plant Rail Abstract Integration is the term given to ensuring that the different elements of an electrified
An extended EMC study of an electrical powertrain for transportation systems
 European Association for the Development of Renewable Energies, Environment and Power Quality (EA4EPQ) International Conference on Renewable Energies and Power Quality (ICREPQ 12) Santiago de Compostela
European Association for the Development of Renewable Energies, Environment and Power Quality (EA4EPQ) International Conference on Renewable Energies and Power Quality (ICREPQ 12) Santiago de Compostela
Current Probes. User Manual
 Current Probes User Manual ETS-Lindgren L.P. reserves the right to make changes to any product described herein in order to improve function, design, or for any other reason. Nothing contained herein shall
Current Probes User Manual ETS-Lindgren L.P. reserves the right to make changes to any product described herein in order to improve function, design, or for any other reason. Nothing contained herein shall
EMC countermeasures for High-Speed Differential Interfaces
 TDK EMC Technology Practice Section EMC countermeasures for High-Speed Differential Interfaces How Do Common Mode Filters Suppress EMI in Differential Transmission Circuits? TDK Corporation Application
TDK EMC Technology Practice Section EMC countermeasures for High-Speed Differential Interfaces How Do Common Mode Filters Suppress EMI in Differential Transmission Circuits? TDK Corporation Application
PCB Design Conference - East Keynote Address EMC ASPECTS OF FUTURE HIGH SPEED DIGITAL DESIGNS
 OOOO1 PCB Design Conference - East Keynote Address September 12, 2000 EMC ASPECTS OF FUTURE HIGH SPEED DIGITAL DESIGNS By Henry Ott Consultants Livingston, NJ 07039 (973) 992-1793 www.hottconsultants.com
OOOO1 PCB Design Conference - East Keynote Address September 12, 2000 EMC ASPECTS OF FUTURE HIGH SPEED DIGITAL DESIGNS By Henry Ott Consultants Livingston, NJ 07039 (973) 992-1793 www.hottconsultants.com
Electromagnetic Pulse: Effects on the U.S. Power Grid
 Executive Summary The nation s power grid is vulnerable to the effects of an electromagnetic pulse (EMP), a sudden burst of electromagnetic radiation resulting from a natural or man-made event. EMP events
Executive Summary The nation s power grid is vulnerable to the effects of an electromagnetic pulse (EMP), a sudden burst of electromagnetic radiation resulting from a natural or man-made event. EMP events
PCB Radiation Mechanisms: Using Component-Level Measurements to
 Radiation Directly from PCB Structures PCB Radiation Mechanisms: Using Component-Level Measurements to Determine System-Level Radiated Emissions Signal or component voltage appears between two good antenna
Radiation Directly from PCB Structures PCB Radiation Mechanisms: Using Component-Level Measurements to Determine System-Level Radiated Emissions Signal or component voltage appears between two good antenna
LVDS Technology Solves Typical EMI Problems Associated with Cell Phone Cameras and Displays
 AN-5059 Fairchild Semiconductor Application Note May 2005 Revised May 2005 LVDS Technology Solves Typical EMI Problems Associated with Cell Phone Cameras and Displays Differential technologies such as
AN-5059 Fairchild Semiconductor Application Note May 2005 Revised May 2005 LVDS Technology Solves Typical EMI Problems Associated with Cell Phone Cameras and Displays Differential technologies such as
Application Note: Spread Spectrum Oscillators Reduce EMI for High Speed Digital Systems
 Application Note: Spread Spectrum Oscillators Reduce EMI for High Speed Digital Systems Introduction to Electro-magnetic Interference Design engineers seek to minimize harmful interference between components,
Application Note: Spread Spectrum Oscillators Reduce EMI for High Speed Digital Systems Introduction to Electro-magnetic Interference Design engineers seek to minimize harmful interference between components,
Time and Frequency Domain Analysis for Right Angle Corners on Printed Circuit Board Traces
 Time and Frequency Domain Analysis for Right Angle Corners on Printed Circuit Board Traces Mark I. Montrose Montrose Compliance Services 2353 Mission Glen Dr. Santa Clara, CA 95051-1214 Abstract: For years,
Time and Frequency Domain Analysis for Right Angle Corners on Printed Circuit Board Traces Mark I. Montrose Montrose Compliance Services 2353 Mission Glen Dr. Santa Clara, CA 95051-1214 Abstract: For years,
C ellular telephones increasingly use digital
 J Am Acad Audiol 12 : 309-314 (2001) Hearing Aid and Cellular Telephone Compatibility : Working Toward Solutions H. Stephen Berger* Abstract The ability of hearing aid wearers to use cellular telephones
J Am Acad Audiol 12 : 309-314 (2001) Hearing Aid and Cellular Telephone Compatibility : Working Toward Solutions H. Stephen Berger* Abstract The ability of hearing aid wearers to use cellular telephones
Case Study Competition 2013. Be an engineer of the future! Innovating cars using the latest instrumentation!
 Case Study Competition 2013 Be an engineer of the future! Innovating cars using the latest instrumentation! The scenario You are engineers working on a project team that is tasked with the development
Case Study Competition 2013 Be an engineer of the future! Innovating cars using the latest instrumentation! The scenario You are engineers working on a project team that is tasked with the development
Verizon NEBS TM Compliance: Data Center Equipment NEBS Requirements Verizon Technical Purchasing Requirements VZ.TPR.9703 Issue 2, March 2012
 Verizon NEBS TM Compliance: Data Center Equipment NEBS Requirements Verizon Technical Purchasing Requirements VZ.TPR.9703 Issue 2, March 2012 CHANGE CONTROL RECORD: Version Date Action* Reason for Revision
Verizon NEBS TM Compliance: Data Center Equipment NEBS Requirements Verizon Technical Purchasing Requirements VZ.TPR.9703 Issue 2, March 2012 CHANGE CONTROL RECORD: Version Date Action* Reason for Revision
AND9015. A Solution for Peak EMI Reduction with Spread Spectrum Clock Generators APPLICATION NOTE. Prepared by: Apps Team, BIDC ON Semiconductor
 A Solution for Peak EMI Reduction with Spread Spectrum Clock Generators Prepared by: Apps Team, BIDC ON Semiconductor APPLICATION NOTE Introduction This application note will outline Spread Spectrum Clock
A Solution for Peak EMI Reduction with Spread Spectrum Clock Generators Prepared by: Apps Team, BIDC ON Semiconductor APPLICATION NOTE Introduction This application note will outline Spread Spectrum Clock
Amplifier for Small Magnetic and Electric Wideband Receiving Antennas (model AAA-1B)
 Amplifier for Small Magnetic and Electric Wideband Receiving Antennas (model AAA-1B) 1. Description and Specifications Contents 1.1 Description 1.2 1.2 Specifications 1.3 1.3 Tested parameters in production
Amplifier for Small Magnetic and Electric Wideband Receiving Antennas (model AAA-1B) 1. Description and Specifications Contents 1.1 Description 1.2 1.2 Specifications 1.3 1.3 Tested parameters in production
PL-277x Series SuperSpeed USB 3.0 SATA Bridge Controllers PCB Layout Guide
 Application Note PL-277x Series SuperSpeed USB 3.0 SATA Bridge Controllers PCB Layout Guide Introduction This document explains how to design a PCB with Prolific PL-277x SuperSpeed USB 3.0 SATA Bridge
Application Note PL-277x Series SuperSpeed USB 3.0 SATA Bridge Controllers PCB Layout Guide Introduction This document explains how to design a PCB with Prolific PL-277x SuperSpeed USB 3.0 SATA Bridge
Application Note, Rev.1.0, September 2008 TLE8366. Application Information. Automotive Power
 Application Note, Rev.1.0, September 2008 TLE8366 Automotive Power Table of Contents 1 Abstract...3 2 Introduction...3 3 Dimensioning the Output and Input Filter...4 3.1 Theory...4 3.2 Output Filter Capacitor(s)
Application Note, Rev.1.0, September 2008 TLE8366 Automotive Power Table of Contents 1 Abstract...3 2 Introduction...3 3 Dimensioning the Output and Input Filter...4 3.1 Theory...4 3.2 Output Filter Capacitor(s)
EECC694 - Shaaban. Transmission Channel
 The Physical Layer: Data Transmission Basics Encode data as energy at the data (information) source and transmit the encoded energy using transmitter hardware: Possible Energy Forms: Electrical, light,
The Physical Layer: Data Transmission Basics Encode data as energy at the data (information) source and transmit the encoded energy using transmitter hardware: Possible Energy Forms: Electrical, light,
AP24026. Microcontroller. EMC Design Guidelines for Microcontroller Board Layout. Microcontrollers. Application Note, V 3.
 Microcontroller Application Note, V 3.0, April 2005 AP24026 for Microcontroller Board Layout Microcontrollers Never stop thinking. TriCore Revision History: 2005-04 V 3.0 Previous Version: 2001-04 Page
Microcontroller Application Note, V 3.0, April 2005 AP24026 for Microcontroller Board Layout Microcontrollers Never stop thinking. TriCore Revision History: 2005-04 V 3.0 Previous Version: 2001-04 Page
Design of Bidirectional Coupling Circuit for Broadband Power-Line Communications
 Journal of Electromagnetic Analysis and Applications, 2012, 4, 162-166 http://dx.doi.org/10.4236/jemaa.2012.44021 Published Online April 2012 (http://www.scirp.org/journal/jemaa) Design of Bidirectional
Journal of Electromagnetic Analysis and Applications, 2012, 4, 162-166 http://dx.doi.org/10.4236/jemaa.2012.44021 Published Online April 2012 (http://www.scirp.org/journal/jemaa) Design of Bidirectional
is the power reference: Specifically, power in db is represented by the following equation, where P0 P db = 10 log 10
 RF Basics - Part 1 This is the first article in the multi-part series on RF Basics. We start the series by reviewing some basic RF concepts: Decibels (db), Antenna Gain, Free-space RF Propagation, RF Attenuation,
RF Basics - Part 1 This is the first article in the multi-part series on RF Basics. We start the series by reviewing some basic RF concepts: Decibels (db), Antenna Gain, Free-space RF Propagation, RF Attenuation,
A NEAR FIELD INJECTION MODEL FOR SUSCEPTIBILITY PREDICTION IN INTEGRATED CIRCUITS
 ICONIC 2007 St. Louis, MO, USA June 27-29, 2007 A NEAR FIELD INJECTION MODEL FOR SUSCEPTIBILITY PREDICTION IN INTEGRATED CIRCUITS Ali Alaeldine 12, Alexandre Boyer 3, Richard Perdriau 1, Sonia Ben Dhia
ICONIC 2007 St. Louis, MO, USA June 27-29, 2007 A NEAR FIELD INJECTION MODEL FOR SUSCEPTIBILITY PREDICTION IN INTEGRATED CIRCUITS Ali Alaeldine 12, Alexandre Boyer 3, Richard Perdriau 1, Sonia Ben Dhia
EMC Basics. Speaker : Alain Lafuente. Alain.lafuente@we-online.com
 EMC Basics Speaker : lain Lafuente lain.lafuente@we-online.com WHT IS EMC? 2 CE Marking With the formation of the single European market, standardization was required to remove technical barriers to trade.
EMC Basics Speaker : lain Lafuente lain.lafuente@we-online.com WHT IS EMC? 2 CE Marking With the formation of the single European market, standardization was required to remove technical barriers to trade.
Coordination of Telecommunications Surge Protective Devices in Countries with Unstable AC Power
 App Notes ~ Outdoor Power System Design and Cost Considerations 1 Authors Peter Nystrom President TSi Power Corp. Coordination of Telecommunications Surge Protective Devices in Countries with Unstable
App Notes ~ Outdoor Power System Design and Cost Considerations 1 Authors Peter Nystrom President TSi Power Corp. Coordination of Telecommunications Surge Protective Devices in Countries with Unstable
EMC-conform development of a Tablet-PC
 EMC-conform development of a Tablet-PC January 21, 2014 Johannes Biner Electrosuisse Montena EMC Bernstrasste 93 CH - 3006 Bern Tel. +41 79 256 21 55 Johannes.biner@montenaemc.ch www.montenaemc.ch Programm
EMC-conform development of a Tablet-PC January 21, 2014 Johannes Biner Electrosuisse Montena EMC Bernstrasste 93 CH - 3006 Bern Tel. +41 79 256 21 55 Johannes.biner@montenaemc.ch www.montenaemc.ch Programm
Power surges can also be generated by equipment in your facility such as:
 Power Quality Surge Suppressors What is Surge Protection A surge suppressor can be the first and best defense against the instant or gradual destruction of electrical equipment. Compared to the replacement
Power Quality Surge Suppressors What is Surge Protection A surge suppressor can be the first and best defense against the instant or gradual destruction of electrical equipment. Compared to the replacement
AN1200.04. Application Note: FCC Regulations for ISM Band Devices: 902-928 MHz. FCC Regulations for ISM Band Devices: 902-928 MHz
 AN1200.04 Application Note: FCC Regulations for ISM Band Devices: Copyright Semtech 2006 1 of 15 www.semtech.com 1 Table of Contents 1 Table of Contents...2 1.1 Index of Figures...2 1.2 Index of Tables...2
AN1200.04 Application Note: FCC Regulations for ISM Band Devices: Copyright Semtech 2006 1 of 15 www.semtech.com 1 Table of Contents 1 Table of Contents...2 1.1 Index of Figures...2 1.2 Index of Tables...2
Module 11: Conducted Emissions
 Module 11: Conducted Emissions 11.1 Overview The term conducted emissions refers to the mechanism that enables electromagnetic energy to be created in an electronic device and coupled to its AC power cord.
Module 11: Conducted Emissions 11.1 Overview The term conducted emissions refers to the mechanism that enables electromagnetic energy to be created in an electronic device and coupled to its AC power cord.
DDX 7000 & 8003. Digital Partial Discharge Detectors FEATURES APPLICATIONS
 DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
W a d i a D i g i t a l
 Wadia Decoding Computer Overview A Definition What is a Decoding Computer? The Wadia Decoding Computer is a small form factor digital-to-analog converter with digital pre-amplifier capabilities. It is
Wadia Decoding Computer Overview A Definition What is a Decoding Computer? The Wadia Decoding Computer is a small form factor digital-to-analog converter with digital pre-amplifier capabilities. It is
Clamp Filters that Suppress Emission Noise Provide Immunity Against Surge Noise
 TDK EMC Technology Product Section Clamp Filters that Suppress Emission Noise Provide Immunity Against Surge Noise TDK Shonai Corporation Satoru Saito Reduce Emission Noise from Cables Even if an electronic
TDK EMC Technology Product Section Clamp Filters that Suppress Emission Noise Provide Immunity Against Surge Noise TDK Shonai Corporation Satoru Saito Reduce Emission Noise from Cables Even if an electronic
DCS - Data Center Shielding. Protection against espionage, electronic attacks and interception. www.rz-products.com
 DCS - Protection against espionage, electronic attacks and interception www.rz-products.com DCS - Protect the capital of your company The protection of data and IT infrastructures is no longer related
DCS - Protection against espionage, electronic attacks and interception www.rz-products.com DCS - Protect the capital of your company The protection of data and IT infrastructures is no longer related
Pre-Compliance Test Method for Radiated Emissions of Automotive Components Using Scattering Parameter Transfer Functions
 PreCompliance Test Method for Radiated Emissions of Automotive Components Using Scattering Parameter Transfer Functions D. Schneider 1*, S. Tenbohlen 1, W. Köhler 1 1 Institute of Power Transmission and
PreCompliance Test Method for Radiated Emissions of Automotive Components Using Scattering Parameter Transfer Functions D. Schneider 1*, S. Tenbohlen 1, W. Köhler 1 1 Institute of Power Transmission and
Electromagnetic (EMI) shielding
 Electromagnetic (EMI) shielding 1.1. The mechanism of Electromagnetic Interference (EMI) The definition of EMC The council of the European Union defines EMC in Article 4 of their "council directive on
Electromagnetic (EMI) shielding 1.1. The mechanism of Electromagnetic Interference (EMI) The definition of EMC The council of the European Union defines EMC in Article 4 of their "council directive on
This application note is written for a reader that is familiar with Ethernet hardware design.
 AN18.6 SMSC Ethernet Physical Layer Layout Guidelines 1 Introduction 1.1 Audience 1.2 Overview SMSC Ethernet products are highly-integrated devices designed for 10 or 100 Mbps Ethernet systems. They are
AN18.6 SMSC Ethernet Physical Layer Layout Guidelines 1 Introduction 1.1 Audience 1.2 Overview SMSC Ethernet products are highly-integrated devices designed for 10 or 100 Mbps Ethernet systems. They are
RX-AM4SF Receiver. Pin-out. Connections
 RX-AM4SF Receiver The super-heterodyne receiver RX-AM4SF can provide a RSSI output indicating the amplitude of the received signal: this output can be used to create a field-strength meter capable to indicate
RX-AM4SF Receiver The super-heterodyne receiver RX-AM4SF can provide a RSSI output indicating the amplitude of the received signal: this output can be used to create a field-strength meter capable to indicate
EMI in Electric Vehicles
 EMI in Electric Vehicles S. Guttowski, S. Weber, E. Hoene, W. John, H. Reichl Fraunhofer Institute for Reliability and Microintegration Gustav-Meyer-Allee 25, 13355 Berlin, Germany Phone: ++49(0)3046403144,
EMI in Electric Vehicles S. Guttowski, S. Weber, E. Hoene, W. John, H. Reichl Fraunhofer Institute for Reliability and Microintegration Gustav-Meyer-Allee 25, 13355 Berlin, Germany Phone: ++49(0)3046403144,
Ultra Wideband Signal Impact on IEEE802.11b Network Performance
 Ultra Wideband Signal Impact on IEEE802.11b Network Performance Matti Hämäläinen 1, Jani Saloranta 1, Juha-Pekka Mäkelä 1, Tero Patana 2, Ian Oppermann 1 1 Centre for Wireless Communications (CWC), University
Ultra Wideband Signal Impact on IEEE802.11b Network Performance Matti Hämäläinen 1, Jani Saloranta 1, Juha-Pekka Mäkelä 1, Tero Patana 2, Ian Oppermann 1 1 Centre for Wireless Communications (CWC), University
Conducted EMI filter design for SMPS
 Conducted EMI filter design for Jukka-Pekka Sjöroos Helsinki University of Technology Power Electronics Laboratory Conducted EMI filter design for Introduction EMI in Common Mode(CM noise Differential
Conducted EMI filter design for Jukka-Pekka Sjöroos Helsinki University of Technology Power Electronics Laboratory Conducted EMI filter design for Introduction EMI in Common Mode(CM noise Differential
AND8229/D. An Introduction to Transient Voltage Suppression Devices APPLICATION NOTE
 An Introduction to Transient Voltage Suppression Devices Prepared by: Jim Lepkowski ON Semiconductor APPLICATION NOTE INTRODUCTION Transient Voltage Suppression (TVS) protection devices such as shielded
An Introduction to Transient Voltage Suppression Devices Prepared by: Jim Lepkowski ON Semiconductor APPLICATION NOTE INTRODUCTION Transient Voltage Suppression (TVS) protection devices such as shielded
Digital C4I Interoperability: The EM Protection Issue
 Digital C4I Interoperability: The EM Protection Issue Robert Pfeffer U.S. Army Nuclear and Chemical Agency ATTN: ATNA-NU (R. Pfeffer) 7150 Heller Loop Suite 101 Springfield, VA 22150-3198 Abstract In this
Digital C4I Interoperability: The EM Protection Issue Robert Pfeffer U.S. Army Nuclear and Chemical Agency ATTN: ATNA-NU (R. Pfeffer) 7150 Heller Loop Suite 101 Springfield, VA 22150-3198 Abstract In this
FM Radio Transmitter & Receiver Modules
 FM Radio Transmitter & Receiver Modules T5 / R5 Features MINIATURE SIL PACKAGE FULLY SHIELDED DATA RATES UP TO 128KBITS/S RANGE UPTO 300 METRES SINGLE SUPPLY VOLTAGE INDUSTRY PIN COMPATIBLE QFMT5-434 TEMP
FM Radio Transmitter & Receiver Modules T5 / R5 Features MINIATURE SIL PACKAGE FULLY SHIELDED DATA RATES UP TO 128KBITS/S RANGE UPTO 300 METRES SINGLE SUPPLY VOLTAGE INDUSTRY PIN COMPATIBLE QFMT5-434 TEMP
Department of Electrical and Computer Engineering Ben-Gurion University of the Negev. LAB 1 - Introduction to USRP
 Department of Electrical and Computer Engineering Ben-Gurion University of the Negev LAB 1 - Introduction to USRP - 1-1 Introduction In this lab you will use software reconfigurable RF hardware from National
Department of Electrical and Computer Engineering Ben-Gurion University of the Negev LAB 1 - Introduction to USRP - 1-1 Introduction In this lab you will use software reconfigurable RF hardware from National
Title: Low EMI Spread Spectrum Clock Oscillators
 Title: Low EMI oscillators Date: March 3, 24 TN No.: TN-2 Page 1 of 1 Background Title: Low EMI Spread Spectrum Clock Oscillators Traditional ways of dealing with EMI (Electronic Magnetic Interference)
Title: Low EMI oscillators Date: March 3, 24 TN No.: TN-2 Page 1 of 1 Background Title: Low EMI Spread Spectrum Clock Oscillators Traditional ways of dealing with EMI (Electronic Magnetic Interference)
Shielding Effectiveness Test Method. Harbour s LL, SB, and SS Coaxial Cables. Designs for Improved Shielding Effectiveness
 Shielding Effectiveness Test Method Harbour s LL, SB, and SS Coaxial Cables Designs for Improved Shielding Effectiveness Harbour Industries 4744 Shelburne Road Shelburne Vermont 05482 USA 802-985-3311
Shielding Effectiveness Test Method Harbour s LL, SB, and SS Coaxial Cables Designs for Improved Shielding Effectiveness Harbour Industries 4744 Shelburne Road Shelburne Vermont 05482 USA 802-985-3311
Technical Article MS-2443
 . MS-2443 Safeguard Your RS-485 Communication Networks from Harmful EMC Events by James Scanlon, Senior Evaluation Engineer, Analog Devices, Inc., and Koenraad Rutgers, Senior Field Applications Engineer,
. MS-2443 Safeguard Your RS-485 Communication Networks from Harmful EMC Events by James Scanlon, Senior Evaluation Engineer, Analog Devices, Inc., and Koenraad Rutgers, Senior Field Applications Engineer,
Developments in Point of Load Regulation
 Developments in Point of Load Regulation By Paul Greenland VP of Marketing, Power Management Group, Point of load regulation has been used in electronic systems for many years especially when the load
Developments in Point of Load Regulation By Paul Greenland VP of Marketing, Power Management Group, Point of load regulation has been used in electronic systems for many years especially when the load
WHITEPAPER. Cable and Connector for Hiperface dsl motor drive applications
 WHITEPAPER Cable and Connector for Hiperface dsl motor drive applications information for cable manufacturers Version 02 Content Information for cable manufacturers...3 Communication...3 Crosstalk & shielding...3
WHITEPAPER Cable and Connector for Hiperface dsl motor drive applications information for cable manufacturers Version 02 Content Information for cable manufacturers...3 Communication...3 Crosstalk & shielding...3
X2Y Solution for Decoupling Printed Circuit Boards
 Summary As printed circuit board s (PCB) power distribution systems (PDS) gain in complexity (i.e. multiple voltages and lower voltages levels) the sensitivity to transients and noise voltage is becoming
Summary As printed circuit board s (PCB) power distribution systems (PDS) gain in complexity (i.e. multiple voltages and lower voltages levels) the sensitivity to transients and noise voltage is becoming
AN-837 APPLICATION NOTE
 APPLICATION NOTE One Technology Way P.O. Box 916 Norwood, MA 262-916, U.S.A. Tel: 781.329.47 Fax: 781.461.3113 www.analog.com DDS-Based Clock Jitter Performance vs. DAC Reconstruction Filter Performance
APPLICATION NOTE One Technology Way P.O. Box 916 Norwood, MA 262-916, U.S.A. Tel: 781.329.47 Fax: 781.461.3113 www.analog.com DDS-Based Clock Jitter Performance vs. DAC Reconstruction Filter Performance
Compliance with TIS and TRP Requirements
 White Paper Compliance with TIS and TRP Requirements This document describes the issues related to meeting Total Isotropic Sensitivity and Total Radiated Power requirements for cellular products. May 2006
White Paper Compliance with TIS and TRP Requirements This document describes the issues related to meeting Total Isotropic Sensitivity and Total Radiated Power requirements for cellular products. May 2006
Application Note SAW-Components
 Application Note SAW-Components Principles of SAWR-stabilized oscillators and transmitters. App: Note #1 This application note describes the physical principle of SAW-stabilized oscillator. Oscillator
Application Note SAW-Components Principles of SAWR-stabilized oscillators and transmitters. App: Note #1 This application note describes the physical principle of SAW-stabilized oscillator. Oscillator
Application of transient pulses on power supply cables by using commercial of the shelf components
 Adv. Radio Sci., 8, 183 188, 2010 doi:10.5194/ars-8-183-2010 Author(s) 2010. CC Attribution 3.0 License. Advances in Radio Science Application of transient pulses on power supply cables by using commercial
Adv. Radio Sci., 8, 183 188, 2010 doi:10.5194/ars-8-183-2010 Author(s) 2010. CC Attribution 3.0 License. Advances in Radio Science Application of transient pulses on power supply cables by using commercial
Computer Aided Design of Home Medical Alert System
 Computer Aided Design of Home Medical Alert System Submitted to The Engineering Honors Committee 119 Hitchcock Hall College of Engineering The Ohio State University Columbus, Ohio 43210 By Pei Chen Kan
Computer Aided Design of Home Medical Alert System Submitted to The Engineering Honors Committee 119 Hitchcock Hall College of Engineering The Ohio State University Columbus, Ohio 43210 By Pei Chen Kan
On One Approach to Scientific CAD/CAE Software Developing Process
 ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 9 On One Approach to Scientific CAD/CAE Software Developing Process George Sergia 1, Alexander Demurov 2, George Petrosyan 3, Roman Jobava 4 1 Exact and
ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 9 On One Approach to Scientific CAD/CAE Software Developing Process George Sergia 1, Alexander Demurov 2, George Petrosyan 3, Roman Jobava 4 1 Exact and
Article from Micrel. A new approach to the challenge of powering cellular M2M modems By Anthony Pele Senior Field Applications Engineer, Micrel
 Article from Micrel A new approach to the challenge of powering cellular M2M modems By Anthony Pele Senior Field Applications Engineer, Micrel www.micrel.com Industrial applications for machine-to-machine
Article from Micrel A new approach to the challenge of powering cellular M2M modems By Anthony Pele Senior Field Applications Engineer, Micrel www.micrel.com Industrial applications for machine-to-machine
Reducing EMI and Improving Signal Integrity Using Spread Spectrum Clocking
 Reducing EMI and Improving Signal Integrity Using Spread Spectrum Clocking Electromagnetic interference (EMI), once the exclusive concern of equipment designers working with high-speed signals, is no longer
Reducing EMI and Improving Signal Integrity Using Spread Spectrum Clocking Electromagnetic interference (EMI), once the exclusive concern of equipment designers working with high-speed signals, is no longer
How To Understand And Understand The Power Of A Cdma/Ds System
 CDMA Technology : Pr. Dr. W. Skupin www.htwg-konstanz.de Pr. S. Flament www.greyc.fr/user/99 On line Course on CDMA Technology CDMA Technology : Introduction to Spread Spectrum Technology CDMA / DS : Principle
CDMA Technology : Pr. Dr. W. Skupin www.htwg-konstanz.de Pr. S. Flament www.greyc.fr/user/99 On line Course on CDMA Technology CDMA Technology : Introduction to Spread Spectrum Technology CDMA / DS : Principle
DDX 7000 & 8003. Digital Partial Discharge Detectors FEATURES APPLICATIONS
 DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
EMOSAFE EN-100. Network Isolators for PCB assembly 1 GENERAL DESCRIPTION. Product Data Sheet ENGLISH
 ENGLISH EMOSAFE EN-100 Product Data Sheet Network Isolators for PCB assembly November 2013 1 GENERAL DESCRIPTION The EMOSAFE EN-100 Network Isolator interrupts all galvanically conducting connections (conductors
ENGLISH EMOSAFE EN-100 Product Data Sheet Network Isolators for PCB assembly November 2013 1 GENERAL DESCRIPTION The EMOSAFE EN-100 Network Isolator interrupts all galvanically conducting connections (conductors
ILB, ILBB Ferrite Beads
 ILB, ILBB Ferrite Beads Electro-Magnetic Interference and Electro-Magnetic Compatibility (EMI/EMC) avid B. Fancher Inductive Products ivision INTROUCTION Manufacturers of electrical and electronic equipment
ILB, ILBB Ferrite Beads Electro-Magnetic Interference and Electro-Magnetic Compatibility (EMI/EMC) avid B. Fancher Inductive Products ivision INTROUCTION Manufacturers of electrical and electronic equipment
IEEE Electromagnetic Compatibility Standards (Active & Archive) Collection: VuSpec
 IEEE Electromagnetic Compatibility Standards (Active & Archive) Collection: VuSpec This value-packed VuSpec CD-ROM represents the most complete resource available for professional engineers looking for
IEEE Electromagnetic Compatibility Standards (Active & Archive) Collection: VuSpec This value-packed VuSpec CD-ROM represents the most complete resource available for professional engineers looking for
The Effect of Network Cabling on Bit Error Rate Performance. By Paul Kish NORDX/CDT
 The Effect of Network Cabling on Bit Error Rate Performance By Paul Kish NORDX/CDT Table of Contents Introduction... 2 Probability of Causing Errors... 3 Noise Sources Contributing to Errors... 4 Bit Error
The Effect of Network Cabling on Bit Error Rate Performance By Paul Kish NORDX/CDT Table of Contents Introduction... 2 Probability of Causing Errors... 3 Noise Sources Contributing to Errors... 4 Bit Error
High Frequency Power Quality
 High Frequency Power Quality Dr. Ing. Jos Knockaert, MSc jos.knockaert@ugent.be CE-ABLE Seminar 21st June 2016-1 Project: TETRA HFPQ funded by Dec 2014 Nov 2016 Main goals: - How to measure? - What are
High Frequency Power Quality Dr. Ing. Jos Knockaert, MSc jos.knockaert@ugent.be CE-ABLE Seminar 21st June 2016-1 Project: TETRA HFPQ funded by Dec 2014 Nov 2016 Main goals: - How to measure? - What are
ST Series POWER SUPPLIES USER INSTRUCTIONS
 Introduction These instructions detail the installation and operation requirements for the ST20 & ST35 power supplies. These have been designed for operation in RV s providing a DC power system, with optional
Introduction These instructions detail the installation and operation requirements for the ST20 & ST35 power supplies. These have been designed for operation in RV s providing a DC power system, with optional
A Beginners Guide to EMC. Presented by Andy Lawson Technical Supervisor, Industry EMC, TÜV SÜD Product Service
 A Beginners Guide to EMC Presented by Andy Lawson Technical Supervisor, Industry EMC, TÜV SÜD Product Service EMC Issues In The Real World What Actually is EMC? EMC Standards and Legislation The Need For
A Beginners Guide to EMC Presented by Andy Lawson Technical Supervisor, Industry EMC, TÜV SÜD Product Service EMC Issues In The Real World What Actually is EMC? EMC Standards and Legislation The Need For
Maximizing Receiver Dynamic Range for Spectrum Monitoring
 Home Maximizing Receiver Dynamic Range for Spectrum Monitoring Brian Avenell, National Instruments Corp., Austin, TX October 15, 2012 As consumers continue to demand more data wirelessly through mobile
Home Maximizing Receiver Dynamic Range for Spectrum Monitoring Brian Avenell, National Instruments Corp., Austin, TX October 15, 2012 As consumers continue to demand more data wirelessly through mobile
APPLICATION NOTE. RF System Architecture Considerations ATAN0014. Description
 APPLICATION NOTE RF System Architecture Considerations ATAN0014 Description Highly integrated and advanced radio designs available today, such as the Atmel ATA5830 transceiver and Atmel ATA5780 receiver,
APPLICATION NOTE RF System Architecture Considerations ATAN0014 Description Highly integrated and advanced radio designs available today, such as the Atmel ATA5830 transceiver and Atmel ATA5780 receiver,
A. Jraifi, R. A. Laamara, A. Belhaj, and E. H. Saidi Lab/UFR-groupe Canal Propagation Radio PHE, Faculté des Sciences, Rabat, Morocco
 Progress In Electromagnetics Research C, Vol. 12, 15 25, 2010 A PROPOSAL SOLUTION FOR INTERFERENCE INTER-OPERATORS A. Jraifi, R. A. Laamara, A. Belhaj, and E. H. Saidi Lab/UFR-groupe Canal Propagation
Progress In Electromagnetics Research C, Vol. 12, 15 25, 2010 A PROPOSAL SOLUTION FOR INTERFERENCE INTER-OPERATORS A. Jraifi, R. A. Laamara, A. Belhaj, and E. H. Saidi Lab/UFR-groupe Canal Propagation
MOBILE SYSTEM FOR DIAGNOSIS OF HIGH VOLTAGE CABLES (132KV/220KV) VLF-200 HVCD
 MOBILE SYSTEM FOR DIAGNOSIS OF HIGH VOLTAGE CABLES (132KV/220KV) VLF-200 HVCD VERY LOW FREQUENCY (VLF) - PARTIAL DISCHARGES AND TANGENT DELTA HV/EHV POWER CABLES DIAGNOSTIC AND ON-SITE FIELD TESTING WITH
MOBILE SYSTEM FOR DIAGNOSIS OF HIGH VOLTAGE CABLES (132KV/220KV) VLF-200 HVCD VERY LOW FREQUENCY (VLF) - PARTIAL DISCHARGES AND TANGENT DELTA HV/EHV POWER CABLES DIAGNOSTIC AND ON-SITE FIELD TESTING WITH
IEC and CISPR Standards
 IEC and CISPR Standards With thanks to Gideon Wiid, PhD student, and Paul van der Merwe EE Eng, 2 May, 2007 EMC Definition: Electromagnetic compatibility itself is defined as [1]: "the ability of an equipment
IEC and CISPR Standards With thanks to Gideon Wiid, PhD student, and Paul van der Merwe EE Eng, 2 May, 2007 EMC Definition: Electromagnetic compatibility itself is defined as [1]: "the ability of an equipment
Evaluating AC Current Sensor Options for Power Delivery Systems
 Evaluating AC Current Sensor Options for Power Delivery Systems State-of-the-art isolated ac current sensors based on CMOS technology can increase efficiency, performance and reliability compared to legacy
Evaluating AC Current Sensor Options for Power Delivery Systems State-of-the-art isolated ac current sensors based on CMOS technology can increase efficiency, performance and reliability compared to legacy
An Ethernet Cable Discharge Event (CDE) Test and Measurement System
 An Ethernet Cable Discharge Event (CDE) Test and Measurement System Wei Huang, Jerry Tichenor ESDEMC Technology LLC Rolla, MO, USA whuang@esdemc.com Abstract A Cable Discharge Event (CDE) is an electrostatic
An Ethernet Cable Discharge Event (CDE) Test and Measurement System Wei Huang, Jerry Tichenor ESDEMC Technology LLC Rolla, MO, USA whuang@esdemc.com Abstract A Cable Discharge Event (CDE) is an electrostatic
MEASUREMENT UNCERTAINTY IN VECTOR NETWORK ANALYZER
 MEASUREMENT UNCERTAINTY IN VECTOR NETWORK ANALYZER W. Li, J. Vandewege Department of Information Technology (INTEC) University of Gent, St.Pietersnieuwstaat 41, B-9000, Gent, Belgium Abstract: Precision
MEASUREMENT UNCERTAINTY IN VECTOR NETWORK ANALYZER W. Li, J. Vandewege Department of Information Technology (INTEC) University of Gent, St.Pietersnieuwstaat 41, B-9000, Gent, Belgium Abstract: Precision
GigaSPEED X10D Solution How
 SYSTIMAX Solutions GigaSPEED X10D Solution How White Paper June 2009 www.commscope.com Contents Modal Decomposition Modeling and the Revolutionary 1 SYSTIMAX GigaSPEED X10D Performance MDM An Introduction
SYSTIMAX Solutions GigaSPEED X10D Solution How White Paper June 2009 www.commscope.com Contents Modal Decomposition Modeling and the Revolutionary 1 SYSTIMAX GigaSPEED X10D Performance MDM An Introduction
Design and Certification of ASH Radio Systems for Japan
 Design and Certification of ASH Radio Systems for Japan RFM s second-generation ASH radio hybrids are being used in a wide variety of applications in Japan, operating under the Japanese BIJAKU radio regulations.
Design and Certification of ASH Radio Systems for Japan RFM s second-generation ASH radio hybrids are being used in a wide variety of applications in Japan, operating under the Japanese BIJAKU radio regulations.
