Secure Video Surveillance System (SVSS) for Unannounced Safeguards Inspections
|
|
|
- Giles Fowler
- 8 years ago
- Views:
Transcription
1 1 IAEA-CN-184/124 Secure Video Surveillance System (SVSS) for Unannounced Safeguards Inspections M. Pinkalla a, E. Galdoz b a Sandia National Laboratories Albuquerque, New Mexico USA b Brazilian-Argentine Agency for Accounting and Control of Nuclear Materials (ABACC) Rio de Janeiro, Brazil mnpinka@sandia.gov Abstract. The Secure Video Surveillance System (SVSS) is a collaborative effort between the U.S. Department of Energy (DOE), Sandia National Laboratories (SNL), and the Brazilian-Argentine Agency for Accounting and Control of Nuclear Materials (ABACC). The joint project addresses specific requirements of redundant surveillance systems installed in two South American nuclear facilities as a tool to support unannounced inspections conducted by ABACC and the International Atomic Energy Agency (IAEA). The surveillance covers the critical time (as much as a few hours) between the notification of an inspection and the access of inspectors to the location in facility where surveillance equipment is installed. ABACC and the IAEA currently use the EURATOM Multiple Optical Surveillance System (EMOSS). This outdated system is no longer available or supported by the manufacturer. The current EMOSS system has met the project objective; however, the lack of available replacement parts and system support has made this system unsustainable and has increased the risk of an inoperable system. A new system that utilizes current technology and is maintainable is required to replace the aging EMOSS system. ABACC intends to replace one of the existing ABACC EMOSS systems by the Secure Video Surveillance System. SVSS utilizes commercial off-the shelf (COTS) technologies for all individual components. Sandia National Laboratories supported the system design for SVSS to meet Safeguards requirements, i.e. tamper indication, data authentication, etc. The SVSS consists of two video surveillance cameras linked securely to a data collection unit. The collection unit is capable of retaining historical surveillance data for at least three hours with picture intervals as short as 1sec. Images in.jpg format are available to inspectors using various software review tools. SNL has delivered two SVSS systems for test and evaluation at the ABACC Safeguards Laboratory. An additional proto-type system remains at SNL for software and hardware testing. This paper will describe the capabilities of the new surveillance system, application and requirements, and the design approach. 1. Introduction The Brazilian-Argentine Agency for Accounting and Control of Nuclear Materials (ABACC) and the International Atomic Energy Agency (IAEA) perform safeguards verification activities at nuclear installations in Brazil and Argentina. In particular, ABACC and IAEA require surveillance measures to support unannounced inspections. Currently, the EMOSS (EURATOM Multi-camera Optical Surveillance System), developed by EURATOM for the IAEA, is the surveillance technology employed. The EMOSS is out-of-date and no longer manufactured, which has presented difficulties in purchasing spare parts and performing system maintenance. It is increasingly prone to failure. The ABACC therefore desires a replacement system, specifically designed to fulfill unannounced inspections requirements. The IAEA has been developing its next-generation surveillance system ( XCAM ), which eventually will replace existing safeguards surveillance systems. However, XCAM is not yet in production, and it is not known when new units would replace the EMOSS in South American facilities.
2 The ABACC and the U.S. Department of Energy (DOE) therefore agreed to develop a system suitable to replace the ABACC EMOSS units with current commercial off-the-shelf (COTS) technology customized to comply with the specific requirements for the unannounced inspection application. The solution would ensure data redundancy, confidence, and system reliability, with a relatively low cost for development, construction, operation, and maintenance. 2. Application Requirements The safeguards approach for unannounced inspections requires that a specific field of view be kept under surveillance from the time inspectors request access to the time they finally arrive at the area of interest. Any surveillance collected before the unannounced inspection request may not be disclosed to the inspectorate. The facility operator must ensure that inspectors can reach the inspection location within two hours after the inspection request; thus, the surveillance system should never retain more than the previous few hours of images. Whenever inspectors are able to gain access more quickly, all images acquired prior to the inspection request must not be visible to the inspector. The goal of the video surveillance system is to collect images in rapid succession to ensure the video detection of short-duration activities. ABACC requires a Picture Taking Interval (PTI) of one second between successive surveillance frames. The ABACC and IAEA inspectors may review the surveillance record either jointly or independently during unannounced inspections. All review activities must take place on site and no images may be removed from the facility. The surveillance system must therefore provide the inspector with all software tools necessary to obtain a safeguards conclusion prior to leaving the facility. In case of inconclusiveness or doubt, it must be possible to store the images on external media, kept under joint seal (ABACC, IAEA, and operator). SVSS acquires images from two independently-positioned cameras that transmit via wire links of arbitrary length to a collection unit for storage and review. The links must be protected using authentication measures to ensure that the inspector can trust the image data. In addition, the camera housings and collection unit must include tamper indication. To increase system reliability, images must also be retained as backup within the camera s flash memory. The backup images would only be needed to recover surveillance in the event of a collection unit or transmission failure. Administrative procedures would be necessary in this case so that the inspector was able to access only the images required. The system must operate on mains power provided by a secured facility electrical line. An uninterruptable power supply (UPS) within the tamper-indicating enclosure is required to protect against short-term loss of power. The UPS will further ensure that the cameras have priority to operate autonomously. 3. Design Approach The design utilizes commercial, off-the-shelf (COTS) components suitably integrated in a system that complies with the stated requirements. A number of cameras with different features could be used for the intended purpose. A Sony network camera was selected for this application because of its availability, reliability, performance characteristics, and operational experience. The camera is capable of acquiring and collecting images via Ethernet at a one second or shorter PTI. It is also capable of storing images locally on removable flash memory. The images acquired by the camera modules are transmitted (pushed) to a collection computer or server. The data transmission is handled by an Ethernet connection between each camera and the server. To ensure that the images stored in the server for review are authentic and generated by the actual and originally configured camera, the transmission is encapsulated inside a VPN (Virtual Private Network) tunnel, implemented with VPN hardware devices already approved for safeguards purposes. To confirm that no tampering has occurred in the system, the camera enclosures and server cabinet are
3 sealed using Agency approved seals to permit independent access of only one agency (IAEA or ABACC) during inspections. The cabinet selected to enclose the server computer is a two compartment Hoffman enclosure, accessed by independent doors. The bottom door is sealed with a passive metallic seal intended for access to the main system components for maintenance purposes only. The top door is sealed with an electronic seal (VACOSS or EOSS), which allows the inspector to access the server computer during a surveillance review by using the supplied keyboard and monitor. The collection computer is an industrial PC running standard software for storage and review of the images, based on the storage requirements. Specific software operates on the server to maintain at least three hours of data, yet permits an inspector to review at most two hours of the most recently recorded data. The software also downloads the jpeg-format images from the camera(s) and converts the images into an AVI file for playback review during the inspection activities. In the event of a system failure, it is possible for an inspector to retrieve the images directly from the local removable flash memory in the camera for manual safeguards review. Safeguards technical data are also recorded on the system. System logs are continuously updated with information about any abnormality that may have occurred during the period between two consecutive inspections, e.g., dropped images, camera or server housing tamper events, high temperature alerts, etc. Inspectors can review these events in the system logs to assess the reliability and performance of the system. A UPS provides uninterruptable power to the system to ensure that a power outage does not cause an interruption of the surveillance process. The UPS is designed to provide power to the system continuously. If the power outage persists, the UPS will initiate shutdown of all hardware components except for the cameras, which will use the remaining battery power for image collection. Critical components are powered in a redundant configuration. Multiple DC power supplies provide power to the components. The cameras operate from parallel power sources; a DC power supply and a DC power converter. The DC power supply is powered directly from the facility mains power. If that fails, the DC power converter begins tapping power directly from the batteries of the UPS system. This will maximize camera operation during a power outage by utilizing the available battery power after UPS system switches off. The photograph in figure 1 shows the prototype cabinet with the inspector door opened and the closed cameras housings on top. The diagrams in figures 2 and 3 show the main components of the system and their interconnection. 4. Software Approach The system is designed using a client server model, where the cameras act as clients producing images and the server receives and stores the images pushed periodically by the client s cameras. A two-layer software platform operates in the server computer: -based layer receives and stores the images in the server hard disk. Images older than the time limit are removed at this level. System status events are also processed and recorded in this layer. -based layer operates as an interface to the inspector, and allows the image review. Both operating systems run on the same computer, by using virtualization software to share resources. The Linux operating system hosts the applications that comprise the SVSS software. Linux was chosen due to the availability of quality open-source software tools. These tools allowed the SVSS software to integrate off the shelf capabilities to meet the design and application requirements. State of health, event logging, construction of the dual image AVI file, and ftp server for camera image collection were capabilities obtained by the addition of open-source software. Custom Perl scripts were used as the integration glue code to allow the separate applications to act together as a system. All the software tools are accessible through the Windows side web browser. The Windows operating system is the user interface used by the inspector to access the SVSS software and
4 run the video review application. Currently, a standard utility is used to play AVI video files. An AVI file is created upon the receipt of a request for inspection. The inspection must fall within appropriate time constraints and is restricted to the period under surveillance only. The software will take the images stored and generate the AVI file. The Windows operating system also offers flexibility to run future applications. It is foreseen that software specifically designed for safeguards review of surveillance will be used, such as GARS, which can be modified to handle the images generated by SVSS cameras. Figure 1: Picture of SVSS Figure 2: Functional diagram of the camera modules
5 Tamper-protected enclosure Air Vent Flat Screen Monitor S1 Door Switch (Operations) Panel mounted to separate Inspector Review from Equipment & Service functions Keyboard/Mouse Inspector Review Fan Equipment and Service 12VDC to Cameras Data Collection Unit Hard Drive Fan Temp Sensor S1 S2 220VAC IN Diodes VPN I/O Device All external DC power and network cables to be inside flexible conduit DC to DC Converter To VPN, I/O and Switch To Fan and Camera VPN To Fan and Camera VPN Ethernet Switch To Monitor 220VAC S2 Door Switch (Maintenance) To Camera VPN devices ~ 5 minutes back-up ~ 6 hours back-up ~ 5 minutes back-up Battery UPS (220VAC) 220VAC IN Air Vent Figure 3: Functional diagram of cabinet
6 5. Conclusions The joint DOE/SNL-ABACC project has successfully assembled two SVSS units that have been delivered to ABACC, as well as an initial prototype unit kept at SNL. The systems have been set up for ongoing testing and evaluation. ABACC will decide if, when and where to deploy each of the delivered units. SNL will continue working with ABACC as required to support the system application. Utilizing commercially available, industrial grade components succeeded in producing a particular solution for this specific Safeguards application. The main advantage to the commercial equipment is availability and sustainability. Employing modular commercial components that are available worldwide allows for efficient maintenance necessitated by failures or upgrades. The software development and testing cycles of the project dealt successfully with various unforeseen challenges to the system integration. Software interdependencies, performance of individual components, and communications protocols presented occasional difficulties requiring special development attention. The extensive testing was therefore a critically important aspect of the project, and ultimately provides the necessary confidence in the system to both acquire and report safeguards information reliably. Acknowledgments Sandia is a multi-program laboratory operated by Sandia Corporation, a Lockheed Martin Company, for the United States Department of Energy under contract DE-AC04-94AL85000.
Secure Video Surveillance System (SVSS) for Unannounced Safeguards Inspections
 Secure Video Surveillance System (SVSS) for Unannounced Safeguards Inspections Abstract Richard L. Lucero, Jack C. Bartberger, Diana Eichert 1, Mark Pinkalla, George Baldwin Sandia National Laboratories
Secure Video Surveillance System (SVSS) for Unannounced Safeguards Inspections Abstract Richard L. Lucero, Jack C. Bartberger, Diana Eichert 1, Mark Pinkalla, George Baldwin Sandia National Laboratories
NGSS. Evolutionary Safeguards Surveillance. Nuclear measurement solutions for safety and security. NUCLEAR MEASUREMENTS BUSINESS UNIT OF AREVA NAS
 Nuclear measurement solutions for safety and security. NAS DCM-C5 Camera NAS Reader UPS NGSS Evolutionary Safeguards Surveillance NUCLEAR MEASUREMENTS BUSINESS UNIT OF AREVA NGSS The NGSS is a modular,
Nuclear measurement solutions for safety and security. NAS DCM-C5 Camera NAS Reader UPS NGSS Evolutionary Safeguards Surveillance NUCLEAR MEASUREMENTS BUSINESS UNIT OF AREVA NGSS The NGSS is a modular,
F2F Storage Facility Monitoring System and Software Integration
 F2F Storage Facility Monitoring System and Software Integration Igor Bondar, Mikhail Osipov, Egor Terushev, Dmitry Pazhin, Boris Barkanov, Anatoly Amelichev All-Russian Scientific Research Institute of
F2F Storage Facility Monitoring System and Software Integration Igor Bondar, Mikhail Osipov, Egor Terushev, Dmitry Pazhin, Boris Barkanov, Anatoly Amelichev All-Russian Scientific Research Institute of
NGSS Data Consolidator (DC)
 NGSS Data Consolidator (DC) The Data Consolidator (DC) facilitates system configuration, monitors network status, and supervises long-term data storage and remote data transmission. The DC consists of
NGSS Data Consolidator (DC) The Data Consolidator (DC) facilitates system configuration, monitors network status, and supervises long-term data storage and remote data transmission. The DC consists of
AN INFORMATION MANAGEMENT SYSTEM FOR A SPENT NUCLEAR FUEL INTERIM STORAGE FACILITY
 AN INFORMATION MANAGEMENT SYSTEM FOR A SPENT NUCLEAR FUEL INTERIM STORAGE FACILITY Karl Horak 1, Todd Giles 1, Hong-Nian Jow 2, Robert Finch 1, Hsien-Lang Chiu 3 1 Sandia National Laboratories, P.O. Box
AN INFORMATION MANAGEMENT SYSTEM FOR A SPENT NUCLEAR FUEL INTERIM STORAGE FACILITY Karl Horak 1, Todd Giles 1, Hong-Nian Jow 2, Robert Finch 1, Hsien-Lang Chiu 3 1 Sandia National Laboratories, P.O. Box
Impact of Power-over-Ethernet (PoE) on Industrial-based Networking
 Ethernet-based communication, Transmission Control Protocol/Internet Protocol (TCP/IP), is emerging at all levels of the mass communications market. The introduction of Power-over- Ethernet (PoE) is poised
Ethernet-based communication, Transmission Control Protocol/Internet Protocol (TCP/IP), is emerging at all levels of the mass communications market. The introduction of Power-over- Ethernet (PoE) is poised
Fire Alarm System Monitoring - CAN/ULC-S561-03
 Fire Alarm System Monitoring - CAN/ULC-S561-03 Brian McBain ULC Regulatory Services May 4, 2011 Copyright 1995-2007 Underwriters' Laboratories of Canada. All rights reserved. No portion of this material
Fire Alarm System Monitoring - CAN/ULC-S561-03 Brian McBain ULC Regulatory Services May 4, 2011 Copyright 1995-2007 Underwriters' Laboratories of Canada. All rights reserved. No portion of this material
Temperature & Humidity SMS Alert Controller
 Temperature & Humidity Alert Controller METERS 3 simple steps starting the unit: Insert the SIM card Plug in the sensors connectors Connect the AC power cord. Specifications: AC 90~260V Auto Select Internal
Temperature & Humidity Alert Controller METERS 3 simple steps starting the unit: Insert the SIM card Plug in the sensors connectors Connect the AC power cord. Specifications: AC 90~260V Auto Select Internal
Use of electronic seals and remote data transmission to increase the efficiency of safeguards applied in a static Plutonium store
 Use of electronic seals and remote data transmission to increase the efficiency of safeguards applied in a static Plutonium store L. Persson 1, S. Synetos 1, A. Ozols 1, K. Ruuska 1, R. Leslie 2, H. Du
Use of electronic seals and remote data transmission to increase the efficiency of safeguards applied in a static Plutonium store L. Persson 1, S. Synetos 1, A. Ozols 1, K. Ruuska 1, R. Leslie 2, H. Du
Elements of Physical Security Systems II: Intrusion Detection, Alarm Communication and Assessment, Delay, and Response
 Elements of Physical Security Systems II: Intrusion Detection, Alarm Communication and Assessment, Delay, and Response International Biological Threat Reduction Department Sandia National Laboratories
Elements of Physical Security Systems II: Intrusion Detection, Alarm Communication and Assessment, Delay, and Response International Biological Threat Reduction Department Sandia National Laboratories
Amcrest 960H DVR Quick Start Guide
 Amcrest 960H DVR Quick Start Guide Welcome Thank you for purchasing our Amcrest 960H DVR! This quick start guide will help you become familiar with our DVR in a very short time. Before installation and
Amcrest 960H DVR Quick Start Guide Welcome Thank you for purchasing our Amcrest 960H DVR! This quick start guide will help you become familiar with our DVR in a very short time. Before installation and
Technical Overview CM-16 Climate Monitor. Get yours direct at: 01491 410913 www.theclimate.co.uk
 Technical Overview CM-16 Climate Monitor Get yours direct at: 01491 410913 www.theclimate.co.uk Need a lot of remote sensors in a rack mount? The CM-16 has web access, graphing, and alarm alerts sent by
Technical Overview CM-16 Climate Monitor Get yours direct at: 01491 410913 www.theclimate.co.uk Need a lot of remote sensors in a rack mount? The CM-16 has web access, graphing, and alarm alerts sent by
Security & Surveillance Cabling Systems
 Security & Surveillance Cabling Systems Security and Surveillance Cabling Systems The video security industry is growing and ever-changing, offering a wealth of opportunity for today s security professionals.
Security & Surveillance Cabling Systems Security and Surveillance Cabling Systems The video security industry is growing and ever-changing, offering a wealth of opportunity for today s security professionals.
Temperature@lert WiFi Edition
 Temperature@lert WiFi Edition Affordable WiFi temperature and humidity monitoring to protect your most critical assets Single or Dual Sensor Configurations available Overview Temperature@lert WiFi Edition
Temperature@lert WiFi Edition Affordable WiFi temperature and humidity monitoring to protect your most critical assets Single or Dual Sensor Configurations available Overview Temperature@lert WiFi Edition
Bosch Access Professional Edition 3.0 Access Control Module Certification Evaluation Made by Milestone 12-15-2014
 Bosch Access Professional Edition 3.0 Access Control Module Certification Evaluation Made by Milestone 12-15-2014 Bosch - Milestone Certified Solution Summary document 1 Table of Contents Products Tested
Bosch Access Professional Edition 3.0 Access Control Module Certification Evaluation Made by Milestone 12-15-2014 Bosch - Milestone Certified Solution Summary document 1 Table of Contents Products Tested
Executive Summary. Technical Description
 Executive Summary The Cellwatch system is built using modules. The majority of the system is constructed with Data Collection Modules (DCMs). The DCMs are optically linked to Control Units (CUs) that in
Executive Summary The Cellwatch system is built using modules. The majority of the system is constructed with Data Collection Modules (DCMs). The DCMs are optically linked to Control Units (CUs) that in
Wired / Wireless / PoE. CMOS Internet Camera ICA-107 / ICA-107W / ICA-107P. Quick Installation Guide
 Wired / Wireless / PoE CMOS Internet Camera ICA-107 / ICA-107W / ICA-107P Quick Installation Guide Table of Contents 1. Package Contents... 3 2. System Requirements... 4 3. Outlook... 5 Front panel of
Wired / Wireless / PoE CMOS Internet Camera ICA-107 / ICA-107W / ICA-107P Quick Installation Guide Table of Contents 1. Package Contents... 3 2. System Requirements... 4 3. Outlook... 5 Front panel of
Addendum #2 Contract UK-11-13
 Addendum #2 Contract UK-11-13 Utilities Kingston Purchase and Replacement of Switchgear at Kingston Hydro Substation MS11 March 25, 2011 Delivered to: All RFP recipients Total number of pages: Nine (9)
Addendum #2 Contract UK-11-13 Utilities Kingston Purchase and Replacement of Switchgear at Kingston Hydro Substation MS11 March 25, 2011 Delivered to: All RFP recipients Total number of pages: Nine (9)
SCADA and Monitoring for Solar Energy Plant
 SCADA and Monitoring for Solar Energy Plant Segment: Industry Country: Thailand Author: Ranon Satitpanyapan Products: NI LabVIEW with LabVIEW Real-Time Module crio Real-Time controller 8 slot with 16 current
SCADA and Monitoring for Solar Energy Plant Segment: Industry Country: Thailand Author: Ranon Satitpanyapan Products: NI LabVIEW with LabVIEW Real-Time Module crio Real-Time controller 8 slot with 16 current
DIVISION 28 ELECTRONIC SAFETY AND SECURITY SECTION 28 13 00 SECURITY AND ACCESS CONTROL SYSTEM
 DIVISION 28 ELECTRONIC SAFETY AND SECURITY PART 1 GENERAL 1.01 DESCRIPTION A. Division 28 Contractor shall extend a complete Matrix Systems Access Control System as shown on the Drawings and as specified
DIVISION 28 ELECTRONIC SAFETY AND SECURITY PART 1 GENERAL 1.01 DESCRIPTION A. Division 28 Contractor shall extend a complete Matrix Systems Access Control System as shown on the Drawings and as specified
ReadyNAS OS 6 Desktop Storage Systems
 ReadyNAS OS 6 Desktop Storage Systems Hardware Manual Models: ReadyNAS 102 ReadyNAS 104 ReadyNAS 312 ReadyNAS 314 ReadyNAS 316 ReadyNAS 516 ReadyNAS 716X EDA 500 October 2013 202-11206-04 350 East Plumeria
ReadyNAS OS 6 Desktop Storage Systems Hardware Manual Models: ReadyNAS 102 ReadyNAS 104 ReadyNAS 312 ReadyNAS 314 ReadyNAS 316 ReadyNAS 516 ReadyNAS 716X EDA 500 October 2013 202-11206-04 350 East Plumeria
Access control designed simply for you
 TruPortal Access control designed simply for you QUICK START GUIDE Introduction TruPortal access control solutions have been engineered and designed to install quickly and easily right out of the box.
TruPortal Access control designed simply for you QUICK START GUIDE Introduction TruPortal access control solutions have been engineered and designed to install quickly and easily right out of the box.
A&E Specifications RoadRunner Video Surveillance Systems for School Transportation Applications
 RoadRunner Video Surveillance Systems for School Transportation Applications A. Digital Video Recorder (DVR) System: 1. The system shall be provided in compatible and interchangeable formats that support
RoadRunner Video Surveillance Systems for School Transportation Applications A. Digital Video Recorder (DVR) System: 1. The system shall be provided in compatible and interchangeable formats that support
Security Systems Intrusion Alarm
 Dufferin-Peel Catholic District School Board STANDARD TEXT GUIDELINE FOR Security Systems for SECONDARY AND ELEMENTARY SCHOOLS Prepared by the Plant Department With Assistance from Vision Dynamics Formatted
Dufferin-Peel Catholic District School Board STANDARD TEXT GUIDELINE FOR Security Systems for SECONDARY AND ELEMENTARY SCHOOLS Prepared by the Plant Department With Assistance from Vision Dynamics Formatted
Data Sheet Fujitsu CELVIN NAS Server QR802 Storage
 Data Sheet Fujitsu CELVIN NAS Server QR802 Storage Powerful 4-Drive NAS Rack Solution Ì» Ú««ÝÛÔÊ Ò backup options and SAN (Storage Area Network) integration for SMB customers - enabling centralized data
Data Sheet Fujitsu CELVIN NAS Server QR802 Storage Powerful 4-Drive NAS Rack Solution Ì» Ú««ÝÛÔÊ Ò backup options and SAN (Storage Area Network) integration for SMB customers - enabling centralized data
 Controller 5000GL Controller 5000GL provides flexible system architecture with options of GBUS and LOCAL BUS communications to field devices, to meet a wide range of site requirements. GGBUS L LOCAL BUS
Controller 5000GL Controller 5000GL provides flexible system architecture with options of GBUS and LOCAL BUS communications to field devices, to meet a wide range of site requirements. GGBUS L LOCAL BUS
System i and System p. Customer service, support, and troubleshooting
 System i and System p Customer service, support, and troubleshooting System i and System p Customer service, support, and troubleshooting Note Before using this information and the product it supports,
System i and System p Customer service, support, and troubleshooting System i and System p Customer service, support, and troubleshooting Note Before using this information and the product it supports,
Hosted Testing and Grading
 Hosted Testing and Grading Technical White Paper July 2014 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or
Hosted Testing and Grading Technical White Paper July 2014 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or
integrated lights-out in the ProLiant BL p-class system
 hp industry standard servers august 2002 integrated lights-out in the ProLiant BL p-class system technology brief table of contents executive summary 2 introduction 2 management processor architectures
hp industry standard servers august 2002 integrated lights-out in the ProLiant BL p-class system technology brief table of contents executive summary 2 introduction 2 management processor architectures
Smart Anytime, Safe Anywhere. Climax Home Portal Platform. Envisage and Enable a Connected Future
 Smart Anytime, Safe Anywhere Climax Home Portal Platform Envisage and Enable a Connected Future Climax Home Portal Platform An IP/GPRS-Based Solution to Deliver Smart Home and Mobile Control Services Reliable
Smart Anytime, Safe Anywhere Climax Home Portal Platform Envisage and Enable a Connected Future Climax Home Portal Platform An IP/GPRS-Based Solution to Deliver Smart Home and Mobile Control Services Reliable
CalMod Design-Build Electrification Services
 SECTION 28 16 00 INTRUSION DETECTION SYSTEM PART 1 - GENERAL 1.1 DESCRIPTION A. This section describes the detailed technical requirements for the Intrusion Detection System (IDS), where the Contractor
SECTION 28 16 00 INTRUSION DETECTION SYSTEM PART 1 - GENERAL 1.1 DESCRIPTION A. This section describes the detailed technical requirements for the Intrusion Detection System (IDS), where the Contractor
Using RAID Admin and Disk Utility
 Using RAID Admin and Disk Utility Xserve RAID Includes instructions for creating RAID arrays and monitoring Xserve RAID systems K Apple Computer, Inc. 2003 Apple Computer, Inc. All rights reserved. Under
Using RAID Admin and Disk Utility Xserve RAID Includes instructions for creating RAID arrays and monitoring Xserve RAID systems K Apple Computer, Inc. 2003 Apple Computer, Inc. All rights reserved. Under
Quick Start Guide. RV 120W Wireless-N VPN Firewall. Cisco Small Business
 Quick Start Guide Cisco Small Business RV 120W Wireless-N VPN Firewall Package Contents Wireless-N VPN Firewall Ethernet Cable Power Adapter Quick Start Guide Documentation and Software on CD-ROM Welcome
Quick Start Guide Cisco Small Business RV 120W Wireless-N VPN Firewall Package Contents Wireless-N VPN Firewall Ethernet Cable Power Adapter Quick Start Guide Documentation and Software on CD-ROM Welcome
- Monitoring Array: a seismic or infrasound array, including from 1(4) to 20 Remote Elements (RE) and one Central Recording Facility (CRF).
 Page 1 of 30 Page 2 of 30 1. Basic terminology - Monitoring Array: a seismic or infrasound array, including from 1(4) to 20 Remote Elements (RE) and one Central Recording Facility (CRF). - Remote Element:
Page 1 of 30 Page 2 of 30 1. Basic terminology - Monitoring Array: a seismic or infrasound array, including from 1(4) to 20 Remote Elements (RE) and one Central Recording Facility (CRF). - Remote Element:
Vess. Architectural & Engineering Specifications For Video Surveillance. A2200 Series. www.promise.com. Version: 1.2 Feb, 2013
 Vess A2200 Series Architectural & Engineering Specifications Version: 1.2 Feb, 2013 www.promise.com Copyright 2013 Promise Technology, Inc. All Rights Reserved. No part of this document may be reproduced
Vess A2200 Series Architectural & Engineering Specifications Version: 1.2 Feb, 2013 www.promise.com Copyright 2013 Promise Technology, Inc. All Rights Reserved. No part of this document may be reproduced
Universal Network Access Policy
 Universal Network Access Policy Purpose Poynton Workmens Club makes extensive use of network ed Information Technology resources to support its research and administration functions and provides a variety
Universal Network Access Policy Purpose Poynton Workmens Club makes extensive use of network ed Information Technology resources to support its research and administration functions and provides a variety
Chapter 1 Introduction
 Chapter 1 Introduction The ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN connects your local area network (LAN) to the Internet through one or two external broadband access devices such as cable
Chapter 1 Introduction The ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN connects your local area network (LAN) to the Internet through one or two external broadband access devices such as cable
Redundant Gigabit Backbone Adds Speed and Reliability to Industrial Networks
 Adds Speed and Reliability to Industrial Networks by Harry Hsiao, MOXA Product Manager harry.hsiao@moxa.com Introduction Gigabit network applications are becoming more and more popular in the modern networking
Adds Speed and Reliability to Industrial Networks by Harry Hsiao, MOXA Product Manager harry.hsiao@moxa.com Introduction Gigabit network applications are becoming more and more popular in the modern networking
Intel Server Component Extended Warranty: Selling Guide
 Intel Server Component Extended Warranty: Selling Guide Platform Collaboration and Systems Division Data Center Group Intel Corporation January 2015 Contents Extended Warranty overview Ordering and Registering
Intel Server Component Extended Warranty: Selling Guide Platform Collaboration and Systems Division Data Center Group Intel Corporation January 2015 Contents Extended Warranty overview Ordering and Registering
securityprobe 5E Standard
 securityprobe 5E Standard securityprobe 5E Standard Monitor the physical environment and receive alerts of any disturbances, such as unauthorized intruders, security breaches, high temperatures, smoke,
securityprobe 5E Standard securityprobe 5E Standard Monitor the physical environment and receive alerts of any disturbances, such as unauthorized intruders, security breaches, high temperatures, smoke,
Middleborough Police Electronic Security Narrative
 Middleborough Police Electronic Security Narrative 1. PURPOSE The purpose of this document is to define specific security, access control and surveillance requirements for the exterior and interior of
Middleborough Police Electronic Security Narrative 1. PURPOSE The purpose of this document is to define specific security, access control and surveillance requirements for the exterior and interior of
Advanced Transportation Management Systems
 Advanced Transportation Management Systems Summary Many Department of Transportation agencies are looking for cost-saving ways to improve the efficiencies of roadways without making actual surface improvements
Advanced Transportation Management Systems Summary Many Department of Transportation agencies are looking for cost-saving ways to improve the efficiencies of roadways without making actual surface improvements
The All-in-One Support Solution. Easy & Secure. Secure Advisor
 The All-in-One Support Solution. Easy & Secure. Secure Advisor Secure Advisor - A Perfect Solution for Online Support Fast and easy remote support from anywhere Problems that often sound complicated on
The All-in-One Support Solution. Easy & Secure. Secure Advisor Secure Advisor - A Perfect Solution for Online Support Fast and easy remote support from anywhere Problems that often sound complicated on
2. DESIGN REQUIREMENTS
 2. DESIGN REQUIREMENTS The Smart Lock Security system will give the user the ability to control his or her door lock from the convenience of texting from the user s cell phone. The device can be controlled
2. DESIGN REQUIREMENTS The Smart Lock Security system will give the user the ability to control his or her door lock from the convenience of texting from the user s cell phone. The device can be controlled
Cisco Physical Access Manager
 Data Sheet Cisco Physical Access Manager 1.4.1 Cisco Physical Access Manager is the management application for the Cisco Physical Access Control solution. Cisco Physical Access Manager (Figure 1) is used
Data Sheet Cisco Physical Access Manager 1.4.1 Cisco Physical Access Manager is the management application for the Cisco Physical Access Control solution. Cisco Physical Access Manager (Figure 1) is used
NETWORK ENABLED EQUIPMENT MONITOR
 NETWORK ENABLED EQUIPMENT MONITOR Remotely Monitor Sensors over the Internet Connect Sensors to the Web to Remotely Monitor Equipment, Processes or Other Applications A Complete, Easy to Deploy, Stand-Alone
NETWORK ENABLED EQUIPMENT MONITOR Remotely Monitor Sensors over the Internet Connect Sensors to the Web to Remotely Monitor Equipment, Processes or Other Applications A Complete, Easy to Deploy, Stand-Alone
SNMP Web card. User s Manual. Management Software for Uninterruptible Power Supply Systems
 SNMP Web card User s Manual Management Software for Uninterruptible Power Supply Systems Table of Contents 1. Overview... 3 1.1 Introduction... 3 1.2 Features... 3 1.3 Overlook... 3 1.4 Installation and
SNMP Web card User s Manual Management Software for Uninterruptible Power Supply Systems Table of Contents 1. Overview... 3 1.1 Introduction... 3 1.2 Features... 3 1.3 Overlook... 3 1.4 Installation and
MAXIMIZING YOUR DATA CENTER INFRASTRUCTURE: CENTRALIZED MANAGEMENT AND WIRE-FREE ENVIRONMENTAL MONITORING
 MAXIMIZING YOUR DATA CENTER INFRASTRUCTURE: CENTRALIZED MANAGEMENT AND WIRE-FREE Chris C. Gaskins Vice President of Product Development RF Code, Inc. AUGUST 2010 Shawn Griggs Director of Product Management
MAXIMIZING YOUR DATA CENTER INFRASTRUCTURE: CENTRALIZED MANAGEMENT AND WIRE-FREE Chris C. Gaskins Vice President of Product Development RF Code, Inc. AUGUST 2010 Shawn Griggs Director of Product Management
FVSU-33201301 REPAIR & UPGRADE FIBER OPTIC 280000-1 SECTION 280000 FIRE ALARM SYSTEM CONNECTIVITY
 FVSU-33201301 REPAIR & UPGRADE FIBER OPTIC 280000-1 SECTION 280000 FIRE ALARM SYSTEM CONNECTIVITY PART 1 - GENERAL 1.1 SUMMARY A. Section Includes: 1. Fire-alarm control unit. 2. Addressable interface
FVSU-33201301 REPAIR & UPGRADE FIBER OPTIC 280000-1 SECTION 280000 FIRE ALARM SYSTEM CONNECTIVITY PART 1 - GENERAL 1.1 SUMMARY A. Section Includes: 1. Fire-alarm control unit. 2. Addressable interface
Recommended Tools and Supplies: Small Flat Blade Screwdriver, 35mm x 7.5mm DIN Rail. Qwik Install
 TPDIN-Monitor-WEB Web Based Monitor and Control Remote Power Stations Backup Power Systems Solar Systems Wind Powered Systems Industrial Sense & Control Process Automation Congratulations! on your purchase
TPDIN-Monitor-WEB Web Based Monitor and Control Remote Power Stations Backup Power Systems Solar Systems Wind Powered Systems Industrial Sense & Control Process Automation Congratulations! on your purchase
WIRELESS INSTRUMENTATION TECHNOLOGY
 BS&B WIRELESS, L.L.C. BS&B WIRELESS, L.L.C. WIRELESS INSTRUMENTATION TECHNOLOGY Printed February 2004 BS&B WIRELESS, L.L.C. 7422-B East 46th Place, Tulsa, OK74145 Phone: 918-622-5950 Fax: 918-665-3904
BS&B WIRELESS, L.L.C. BS&B WIRELESS, L.L.C. WIRELESS INSTRUMENTATION TECHNOLOGY Printed February 2004 BS&B WIRELESS, L.L.C. 7422-B East 46th Place, Tulsa, OK74145 Phone: 918-622-5950 Fax: 918-665-3904
112 Linton House 164-180 Union Street London SE1 0LH T: 020 7960 5111 F: 020 7960 5100
 112 Linton House 164-180 Union Street London SE1 0LH T: 020 7960 5111 F: 020 7960 5100 Our dedicated servers offer outstanding performance for even the most demanding of websites with the low monthly fee.
112 Linton House 164-180 Union Street London SE1 0LH T: 020 7960 5111 F: 020 7960 5100 Our dedicated servers offer outstanding performance for even the most demanding of websites with the low monthly fee.
TrueAlarm Fire Alarm Systems
 TrueAlarm Systems UL, ULC, CSFM Listed; FM Approved* Network Annunciators; es Features Provides a dedicated local area network (LAN) for connection of a TrueSite workstation server to remote clients: es
TrueAlarm Systems UL, ULC, CSFM Listed; FM Approved* Network Annunciators; es Features Provides a dedicated local area network (LAN) for connection of a TrueSite workstation server to remote clients: es
DORMA MODEL PS-406BB POWER SUPPLY INSTALLATION INSTRUCTIONS
 Features: INSTALLATION Install in accordance with NFPA 70. DORMA MODEL PS-406BB POWER SUPPLY INSTALLATION INSTRUCTIONS Up to 1.95 Amps Load Capacity Class 2 Rated Outputs Overload, Over Voltage, and Short
Features: INSTALLATION Install in accordance with NFPA 70. DORMA MODEL PS-406BB POWER SUPPLY INSTALLATION INSTRUCTIONS Up to 1.95 Amps Load Capacity Class 2 Rated Outputs Overload, Over Voltage, and Short
38. ACCESS CONTROL AND ELECTRONIC SECURITY SYSTEM
 38. ACCESS CONTROL AND ELECTRONIC SECURITY SYSTEM 38.1 GENERAL Scope Modification and extension of the existing CDU Cardax security system and CCTV System including: Cardax (FT 3000 series) Access control
38. ACCESS CONTROL AND ELECTRONIC SECURITY SYSTEM 38.1 GENERAL Scope Modification and extension of the existing CDU Cardax security system and CCTV System including: Cardax (FT 3000 series) Access control
ABB PSPS Erich Steinmann; Generator control-2013
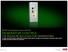 ABB PSPS Erich Steinmann; Generator control-2013 GENERATOR CONTROL THE MODULAR SOLUTION FOR GENERATORS To make sure that power is efficiently converted into electric energy, it is necessary to supervise
ABB PSPS Erich Steinmann; Generator control-2013 GENERATOR CONTROL THE MODULAR SOLUTION FOR GENERATORS To make sure that power is efficiently converted into electric energy, it is necessary to supervise
AKCess Pro Server Management Software
 Management Software v.100.00x takes the best from IP Video Monitoring Software and is the first to combine it with Environmental / Security Sensor and Access Control equipment in one centralized management
Management Software v.100.00x takes the best from IP Video Monitoring Software and is the first to combine it with Environmental / Security Sensor and Access Control equipment in one centralized management
Integrated Building Management and Security System. Building Automation & Security. www.coba-group.com
 Integrated Building Management and Security System Building Automation & Security www.coba-group.com INTEGRATED BUILDING MANAGEMENT AND SECURITY SYSTEM INDEX 1 GENERAL... 3 1.1 SYSTEM INTEGRATION... 3
Integrated Building Management and Security System Building Automation & Security www.coba-group.com INTEGRATED BUILDING MANAGEMENT AND SECURITY SYSTEM INDEX 1 GENERAL... 3 1.1 SYSTEM INTEGRATION... 3
Powerful Dedicated Servers
 Powerful Dedicated Servers Our dedicated servers offer outstanding performance for even the most demanding of websites with the latest Intel & Dell technology combining unparalleled server specification,
Powerful Dedicated Servers Our dedicated servers offer outstanding performance for even the most demanding of websites with the latest Intel & Dell technology combining unparalleled server specification,
Tk20 Network Infrastructure
 Tk20 Network Infrastructure Tk20 Network Infrastructure Table of Contents Overview... 4 Physical Layout... 4 Air Conditioning:... 4 Backup Power:... 4 Personnel Security:... 4 Fire Prevention and Suppression:...
Tk20 Network Infrastructure Tk20 Network Infrastructure Table of Contents Overview... 4 Physical Layout... 4 Air Conditioning:... 4 Backup Power:... 4 Personnel Security:... 4 Fire Prevention and Suppression:...
SAN Conceptual and Design Basics
 TECHNICAL NOTE VMware Infrastructure 3 SAN Conceptual and Design Basics VMware ESX Server can be used in conjunction with a SAN (storage area network), a specialized high speed network that connects computer
TECHNICAL NOTE VMware Infrastructure 3 SAN Conceptual and Design Basics VMware ESX Server can be used in conjunction with a SAN (storage area network), a specialized high speed network that connects computer
IP Video Surveillance
 IP Video Surveillance Solutions and Services Wireless IP PDA Administration Wireless Access Point Viewer Remote Control IP Video Server IP Network Alarm Management Video Recording Analog Video Server Access
IP Video Surveillance Solutions and Services Wireless IP PDA Administration Wireless Access Point Viewer Remote Control IP Video Server IP Network Alarm Management Video Recording Analog Video Server Access
Generic Procurement Specification for a. Video Vehicle Detection System. For Road Traffic Applications
 Generic Procurement Specification for a Video Vehicle Detection System For Road Traffic Applications The Autoscope ENCORE video vehicle detection system meets the attached specifications. 1 of 7 683-10493M-0311
Generic Procurement Specification for a Video Vehicle Detection System For Road Traffic Applications The Autoscope ENCORE video vehicle detection system meets the attached specifications. 1 of 7 683-10493M-0311
Domonial, le Sucre. Easy to Use Intruder Detection Systems
 Domonial, le Sucre Easy to Use Intruder Detection Systems Domonial Brief description With over a million installed sites, Domonial is one of the most popular remotely monitored wireless security systems
Domonial, le Sucre Easy to Use Intruder Detection Systems Domonial Brief description With over a million installed sites, Domonial is one of the most popular remotely monitored wireless security systems
PRI (T1/E1) Call Recorder User Manual Rev 1.0 (December 2013)
 PRI (T1/E1) Call Recorder User Manual Rev 1.0 (December 2013) 1. Call Recording Architecture Overview PRI Call recording solution consists of two major components: Passive T1/E1 Tap Adapter and server
PRI (T1/E1) Call Recorder User Manual Rev 1.0 (December 2013) 1. Call Recording Architecture Overview PRI Call recording solution consists of two major components: Passive T1/E1 Tap Adapter and server
securityserver Unparalleled management and detection of security, environmental, and disaster control resources.
 securityserver Unparalleled management and detection of security, environmental, and disaster control resources. Map cameras & sensors in server rooms or buildings in cities AKCP securityserver puts you
securityserver Unparalleled management and detection of security, environmental, and disaster control resources. Map cameras & sensors in server rooms or buildings in cities AKCP securityserver puts you
DISASTER RECOVERY. Omniture Disaster Plan. June 2, 2008 Version 2.0
 DISASTER RECOVERY Omniture Disaster Plan June 2, 2008 Version 2.0 CHAPTER 1 1 Disaster Recovery Plan Overview In the event that one of our data collection environments are unavailable due to an event,
DISASTER RECOVERY Omniture Disaster Plan June 2, 2008 Version 2.0 CHAPTER 1 1 Disaster Recovery Plan Overview In the event that one of our data collection environments are unavailable due to an event,
DS-9500NI-ST Series NVR. Technical Specification
 DS-9500NI-ST Series NVR Technical Specification Notices The information in this documentation is subject to change without notice and does not represent any commitment on behalf of HIKVISION. HIKVISION
DS-9500NI-ST Series NVR Technical Specification Notices The information in this documentation is subject to change without notice and does not represent any commitment on behalf of HIKVISION. HIKVISION
Terms of Reference Microsoft Exchange and Domain Controller/ AD implementation
 Terms of Reference Microsoft Exchange and Domain Controller/ AD implementation Overview Maldivian Red Crescent will implement it s first Microsoft Exchange server and replace it s current Domain Controller
Terms of Reference Microsoft Exchange and Domain Controller/ AD implementation Overview Maldivian Red Crescent will implement it s first Microsoft Exchange server and replace it s current Domain Controller
Domus, the connected home
 Domus, the connected home Amazouz Ali, Bar Alexandre, Benoist Hugues, Gwinner Charles, Hamidi Nassim, Mahboub Mohamed, Mounsif Badr, Plane Benjamin {aamazouz, abar, hbenoist, cgwinner, nhamidi, mmahboub,
Domus, the connected home Amazouz Ali, Bar Alexandre, Benoist Hugues, Gwinner Charles, Hamidi Nassim, Mahboub Mohamed, Mounsif Badr, Plane Benjamin {aamazouz, abar, hbenoist, cgwinner, nhamidi, mmahboub,
Overview. Alarm console supports simultaneous viewing of both live and recorded video when alarm events are selected
 Niagara Security Overview Niagara Security by Tridium, is an open, web-based security management solution that allows you to manage and monitor your facility anytime, anywhere. Built on Tridium s Niagara
Niagara Security Overview Niagara Security by Tridium, is an open, web-based security management solution that allows you to manage and monitor your facility anytime, anywhere. Built on Tridium s Niagara
Redundancy in enterprise storage networks using dual-domain SAS configurations
 Redundancy in enterprise storage networks using dual-domain SAS configurations technology brief Abstract... 2 Introduction... 2 Why dual-domain SAS is important... 2 Single SAS domain... 3 Dual-domain
Redundancy in enterprise storage networks using dual-domain SAS configurations technology brief Abstract... 2 Introduction... 2 Why dual-domain SAS is important... 2 Single SAS domain... 3 Dual-domain
out of this world guide to: POWERFUL DEDICATED SERVERS
 out of this world guide to: POWERFUL DEDICATED SERVERS Our dedicated servers offer outstanding performance for even the most demanding of websites with the latest Intel & Dell technology combining unparalleled
out of this world guide to: POWERFUL DEDICATED SERVERS Our dedicated servers offer outstanding performance for even the most demanding of websites with the latest Intel & Dell technology combining unparalleled
Who is Watching You? Video Conferencing Security
 Who is Watching You? Video Conferencing Security Navid Jam Member of Technical Staff March 1, 2007 SAND# 2007-1115C Computer and Network Security Security Systems and Technology Video Conference and Collaborative
Who is Watching You? Video Conferencing Security Navid Jam Member of Technical Staff March 1, 2007 SAND# 2007-1115C Computer and Network Security Security Systems and Technology Video Conference and Collaborative
Temperature Alert. LAN-based Temperature and Humidity Data Logger
 Temperature Alert LAN-based Temperature and Humidity Data Logger LAN-based Temperature and Humidity Monitoring - Supports Simultaneous WiFi and Hardwired Interfaces -20 C to +60 C (-4 F to +140 F) Standard
Temperature Alert LAN-based Temperature and Humidity Data Logger LAN-based Temperature and Humidity Monitoring - Supports Simultaneous WiFi and Hardwired Interfaces -20 C to +60 C (-4 F to +140 F) Standard
Vess A2000 Series HA Surveillance with Milestone XProtect VMS Version 1.0
 Vess A2000 Series HA Surveillance with Milestone XProtect VMS Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Purpose 1 Scope 1 Audience 1 What is High Availability?
Vess A2000 Series HA Surveillance with Milestone XProtect VMS Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Purpose 1 Scope 1 Audience 1 What is High Availability?
Question Shall the Tender include installation of the central server application on a redundant server?
 s and answers regarding the Invitation for Tender for a national gamma monitoring system in Sweden s and answers published 2008-07-07 Will alternative tenders from the same Tenderer be considered? No,
s and answers regarding the Invitation for Tender for a national gamma monitoring system in Sweden s and answers published 2008-07-07 Will alternative tenders from the same Tenderer be considered? No,
WISE-4000 Series. WISE IoT Wireless I/O Modules
 WISE-4000 Series WISE IoT Wireless I/O Modules Bring Everything into World of the IoT WISE IoT Ethernet I/O Architecture Public Cloud App Big Data New WISE DNA Data Center Smart Configure File-based Cloud
WISE-4000 Series WISE IoT Wireless I/O Modules Bring Everything into World of the IoT WISE IoT Ethernet I/O Architecture Public Cloud App Big Data New WISE DNA Data Center Smart Configure File-based Cloud
SOLARCARE SERIES PRODUCT AND APPLICATION GUIDE
 SOLARCARE SERIES PRODUCT AND APPLICATION GUIDE for solar energy management LEATEC Delivering Solutions for Energy Management SOLAR ENERGY DATA CENTER BUILDING 4 to8 String Monitoring with 0.% Accuracy
SOLARCARE SERIES PRODUCT AND APPLICATION GUIDE for solar energy management LEATEC Delivering Solutions for Energy Management SOLAR ENERGY DATA CENTER BUILDING 4 to8 String Monitoring with 0.% Accuracy
Power over Ethernet technology for industrial Ethernet networks
 Power over Ethernet technology for industrial Ethernet networks Introduction Ethernet networking has grown beyond office and home usage to become a very successful protocol suite used in many industrial
Power over Ethernet technology for industrial Ethernet networks Introduction Ethernet networking has grown beyond office and home usage to become a very successful protocol suite used in many industrial
RAS Associates, Inc. Systems Development Proposal. Scott Klarman. March 15, 2009
 Systems Development Proposal Scott Klarman March 15, 2009 Systems Development Proposal Page 2 Planning Objective: RAS Associates will be working to acquire a second location in Detroit to add to their
Systems Development Proposal Scott Klarman March 15, 2009 Systems Development Proposal Page 2 Planning Objective: RAS Associates will be working to acquire a second location in Detroit to add to their
4-CH Hybrid Digital Video Recorder
 4-CH Hybrid Digital Video Recorder Key Features Hardware Embedded, highly-reliable standalone HDVR Supports 4-ch BNC connectors Supports dual local display (VGA and HDMI) Supports 3.5" SATA x 1 HDD Supports
4-CH Hybrid Digital Video Recorder Key Features Hardware Embedded, highly-reliable standalone HDVR Supports 4-ch BNC connectors Supports dual local display (VGA and HDMI) Supports 3.5" SATA x 1 HDD Supports
CenterMind G+ Smart and Proactive Environment Monitoring
 CenterMind G+ Smart and Proactive Environment Monitoring Smart and Proactive Environment Monitoring real-time visibility into the state of your computer room or data center environment, 24/7 RiT CenterMind
CenterMind G+ Smart and Proactive Environment Monitoring Smart and Proactive Environment Monitoring real-time visibility into the state of your computer room or data center environment, 24/7 RiT CenterMind
NETWORK MANAGEMENT SOLUTIONS
 N E T S M A R T NETWORK MANAGEMENT SOLUTIONS UNIFY YOUR NETWORK As new and legacy services coexist to support a widening variety of customers, network support presents more technical challenges. This complex,
N E T S M A R T NETWORK MANAGEMENT SOLUTIONS UNIFY YOUR NETWORK As new and legacy services coexist to support a widening variety of customers, network support presents more technical challenges. This complex,
Foglight Experience Monitor and Foglight Experience Viewer
 Foglight Experience Monitor and Foglight Experience Viewer Quest Software, Inc. April 2008 Using the Dell Remote Access Controller Copyright Quest Software, Inc. 2008. All rights reserved. This guide contains
Foglight Experience Monitor and Foglight Experience Viewer Quest Software, Inc. April 2008 Using the Dell Remote Access Controller Copyright Quest Software, Inc. 2008. All rights reserved. This guide contains
Web: www.stp.hu; www.logipix.eu; www.walkdvr.com
 StP Technical Development Ltd. version: 1 Contact: Address: 11-13. Késmárk st., 1158 Budapest, Hungary Phone: +36 1 410-0556; +36 20 480-5933 Fax: +36 1 414-0913 E-mail: info@stp.hu Technical support:
StP Technical Development Ltd. version: 1 Contact: Address: 11-13. Késmárk st., 1158 Budapest, Hungary Phone: +36 1 410-0556; +36 20 480-5933 Fax: +36 1 414-0913 E-mail: info@stp.hu Technical support:
Reducing operating costs of telecom base stations with remote management
 Reducing operating costs of telecom base stations with remote management Whitepaper How remote management can be used to cut operating expenses of existing telecom infrastructure. HMS Industrial Networks
Reducing operating costs of telecom base stations with remote management Whitepaper How remote management can be used to cut operating expenses of existing telecom infrastructure. HMS Industrial Networks
Blackboard Collaborate Web Conferencing Hosted Environment Technical Infrastructure and Security
 Overview Blackboard Collaborate Web Conferencing Hosted Environment Technical Infrastructure and Security Blackboard Collaborate web conferencing is available in a hosted environment and this document
Overview Blackboard Collaborate Web Conferencing Hosted Environment Technical Infrastructure and Security Blackboard Collaborate web conferencing is available in a hosted environment and this document
Ambient Temperature In Range Probe X
 List of Events This section lists all events that are written to the Event Log. Some of these events can be configured through the Configuring Events to Take Actions page, and these are listed in the first
List of Events This section lists all events that are written to the Event Log. Some of these events can be configured through the Configuring Events to Take Actions page, and these are listed in the first
Synology Disaster Recovery Deployment Guide Document ID
 Document ID Syno_UsersGuide_DisasterRecovery_20111114 Table of Contents Chapter 1: Dual Server Disaster Recovery Plan Back up Primary Server's Configurations... 5 Synchronize Data between Primary and Backup
Document ID Syno_UsersGuide_DisasterRecovery_20111114 Table of Contents Chapter 1: Dual Server Disaster Recovery Plan Back up Primary Server's Configurations... 5 Synchronize Data between Primary and Backup
Remote Services. Managing Open Systems with Remote Services
 Remote Services Managing Open Systems with Remote Services Reduce costs and mitigate risk with secure remote services As control systems move from proprietary technology to open systems, there is greater
Remote Services Managing Open Systems with Remote Services Reduce costs and mitigate risk with secure remote services As control systems move from proprietary technology to open systems, there is greater
Hardware and Software Upgrade for the Solution Measurement and Monitor System at Rokkasho Reprocessing
 Hardware and Software Upgrade for the Solution Measurement and Monitor System at Rokkasho Reprocessing R. Plenteda a, A. Alessandrello a, M. Frankl a, W. Deringer a, M. Lang a, M. Cronholm a, K. Baird
Hardware and Software Upgrade for the Solution Measurement and Monitor System at Rokkasho Reprocessing R. Plenteda a, A. Alessandrello a, M. Frankl a, W. Deringer a, M. Lang a, M. Cronholm a, K. Baird
LAB FORWARD. WITH PROService REMOTE SERVICE APPLICATION. Frequently Asked Questions
 LAB FORWARD WITH PROService REMOTE SERVICE APPLICATION Frequently Asked Questions MORE WAYS TO INCREASE UPTIME AND IMPROVE PRODUCTIVITY. GENERAL INFORMATION Q: What is PROService? A: PROService is Beckman
LAB FORWARD WITH PROService REMOTE SERVICE APPLICATION Frequently Asked Questions MORE WAYS TO INCREASE UPTIME AND IMPROVE PRODUCTIVITY. GENERAL INFORMATION Q: What is PROService? A: PROService is Beckman
How To Backup Your Hard Drive With Pros 4 Technology Online Backup
 Pros 4 Technology Online Backup Features Introduction Computers are the default storage medium for most businesses and virtually all home users. Because portable media is quickly becoming an outdated and
Pros 4 Technology Online Backup Features Introduction Computers are the default storage medium for most businesses and virtually all home users. Because portable media is quickly becoming an outdated and
Understanding the Pros and Cons of Combination Networks 7. Acknowledgments Introduction. Establishing the Numbers of Clients and Servers 4
 Mac OS X System Administration GUY HART-DAVIS Mc Graw Hill New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Acknowledgments Introduction,
Mac OS X System Administration GUY HART-DAVIS Mc Graw Hill New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Acknowledgments Introduction,
Compact Monitoring Technology your environmental monitoring solution
 Compact Monitoring Technology your environmental monitoring solution Monitor your GxP environmental parameters and cut your validation costs. Solutions for Life Science and Hospitals www.siemens.com/cmt
Compact Monitoring Technology your environmental monitoring solution Monitor your GxP environmental parameters and cut your validation costs. Solutions for Life Science and Hospitals www.siemens.com/cmt
Stratusphere Solutions
 Stratusphere Solutions Deployment Best Practices Guide Introduction This guide has been authored by experts at Liquidware Labs in order to provide a baseline as well as recommendations for a best practices
Stratusphere Solutions Deployment Best Practices Guide Introduction This guide has been authored by experts at Liquidware Labs in order to provide a baseline as well as recommendations for a best practices
KANGAROO MOBILE DESKTOP USER GUIDE
 KANGAROO MOBILE DESKTOP USER GUIDE Copyright InFocus Corporation., 2015. All rights reserved. This document contains information proprietary to InFocus Corporation, hereinafter InFocus. Use or disclosure
KANGAROO MOBILE DESKTOP USER GUIDE Copyright InFocus Corporation., 2015. All rights reserved. This document contains information proprietary to InFocus Corporation, hereinafter InFocus. Use or disclosure
How To Secure Your Computer With Libreware Libreroview 2.5.2.2 (Windows) And Libreros (Windows 2) (Windows 3.5) (For Windows) (Powerpoint) (Networking)
 Addressing Embedded Security in LabVIEW RIO Systems Carlos Pazos Product Marketing Manager Embedded Software Why Care About Security? 3 Why care about Security? Why Care About Industrial Security? 4 Stuxnet
Addressing Embedded Security in LabVIEW RIO Systems Carlos Pazos Product Marketing Manager Embedded Software Why Care About Security? 3 Why care about Security? Why Care About Industrial Security? 4 Stuxnet
Guest Room Controls & Monitoring System. Integrated Solution for Hotels Southern Countries. www.lonix.com
 Guest Room Controls & Monitoring System Integrated Solution for Hotels Southern Countries www.lonix.com GUEST ROOM CONTROLS & MONITORING SYSTEM INDEX 1 GENERAL... 3 1.1 SYSTEM INTEGRATION... 3 1.2 USER
Guest Room Controls & Monitoring System Integrated Solution for Hotels Southern Countries www.lonix.com GUEST ROOM CONTROLS & MONITORING SYSTEM INDEX 1 GENERAL... 3 1.1 SYSTEM INTEGRATION... 3 1.2 USER
