Sales Pulse Research / Securosis. Information Security. Refresh / Upgrade Cycle for Network Security PANW, CSCO, FTNT
|
|
|
- Alexina McKinney
- 8 years ago
- Views:
Transcription
1 Sales Pulse Research / Securosis Information Security Refresh / Upgrade Cycle for Network Security PANW, CSCO, FTNT June 6,
2 Current Trends in This Report: ü Refresh / Upgrade Cycle for Network Security Vendor Views in This Report: ü PANW Very Strong Indications for Continued Growth, Watching for Upside from End Point, Possible Threat from Increased Competition ü FTNT Strong Indications for Continued Growth; Some Evidence of Progress in Large Enterprises ü CSCO Opportunity to Pick up the Pace and Disrupt This is the first report resulting from the partnership between Sales Pulse and Securosis. In this joint effort our goal is to provide our clients with a view of industry and vendor dynamics that results from depth of knowledge that Securosis brings from their industry backgrounds and work with end users and from Sales Pulse' on-going surveys and dialogue with VARs, integrators, and sales teams. In this report, Securosis has contributed subject matter expertise on the security market and end user requirements. Sales Pulse Research is solely responsible for opinions or expression of conviction regarding individual vendors. 2
3 Network Security (continued) Key Takeaways - The current upgrade cycle for network security is more than a typical product refresh. In addition to moving to faster hardware, and integrating more functionality, NGFWs provide multi-purpose platforms for new solutions that include anti-malware and threat detection. The depth of these new offerings greatly expands the Total Addressable Market (TAM). - Palo Alto has taken the lead in this next generation market and input suggests their continued leadership. We anticipate more challenging competitive responses as the market develops. For now, however, Palo Alto is executing well and best positioned in this large market. - Fortinet is executing well and showing some signs of improving their image in the enterprise and contending more with Palo Alto. Fortinet has the product strength to compete with Palo Alto. We are seeing signs that they are making renewed progress in the enterprise market. They appear to be gaining growing respect in the channel and just may break out of their traditional role and gain some of the luster that Palo Alto has. - Cisco is targeting security for accelerated growth and will likely succeed. Cisco is building on strong, but in some cases lagging technologies. They have been executing well with the technology they acquired with Sourcefire. Industry contacts believe that Marty Roesch is providing a strong vision. Even without great products the Cisco machine will achieve growth in this market. If they can execute well on the product side, Cisco may achieve their goal of growing their market share in security from ~7% to 20%. We will discuss where we think that share will come from. 3
4 Network Security Continued Network Technology Evaluation and Upgrade Cycle The security industry is benefitting from a long term upgrade cycle as organizations evaluate their network security/perimeter architecture driven by the need for next generation network security and that usually means a competitive bid (and possible displacement) of the incumbent. Giving up on Prevention We are observing the beginning of a budget shift away from ineffective prevention technologies to detecting and investigating attacks. We see organizations with mature security programs making this shift, but many others continue to focus on blocking attacks. Prevention is clearly still needed in the network organizations still need a firewall and IPS to enforce both positive (access control) and negative (attack) policies on their perimeters. They just need to be realistic about what they can block even shiny NGFW models. To Focus on Threat Detection So if many organizations have given up trying to block all attacks, what are they supposed to do? Spend tons of money on more appliances to detect attacks they missed at the perimeter, of course. RSAC featured a heavy focus on network-based threat detection including malware and breach detection, persistent threats and zero-day attacks. Threat detection technology is advancing. Analyzing network traffic patterns, profiling and baselining normal communications, and then looking for stuff that s not normal gives you a much better chance of finding compromised devices. What s new is the type of analysis possible with today s better analytics. Baselines aren t built only on Netflow records or DNS queries any more they can now incorporate very granular metadata from network traffic including identity, content, frequency of communication, and various other attributes. Over time, these aspects of detection will become integrated into network devices. Malware Sandboxes Demand for malware detection has been accelerating and is likely to see sustained growth. Vendors debate whether an on-premise approach versus a cloud-based approach to detonation is best. Both can be effective. And vendors are making a lot of noise about data center firewalls - basically just really fast segmentation devices. Some vendors describe this as micro-segmentation. It is another application of firewall technology that is increasing the TAM (Total Addressable Market), for security devices. 4
5 Network Security (continued) While Consolidating Functions Some big organizations still think they need separate devices for all their key functions. Pretty much all the network security players have technologies that allow authorized traffic and block attacks. Back when category names mattered, those functions were called firewalls and IPS respectively. But now everything is a next-generation firewall. But it does a lot more than a firewall. It also detonates malware (or integrates with a cloud service that does). And it looks for commandand-control traffic patterns. Product categories aside, regardless of whether a network security vendor started as a firewall player or with IPS (or both, thanks to the magic of acquisitions), they are all attacking the same real estate: what we call the network security gateway. And Looking for Automation Another hot topic that is ramping up in network security is automation, because managing hundreds of firewalls is complex and time consuming. At RSAC, there were a bunch of new startups showcasing new technologies that showed you how to use an alert from your SIEM or a bad IP address from your threat intelligence provider to make changes automatically on firewalls. Automating some of those rote functions of managing security devices can free up time to do more important and strategic things. In the Cloud At RSAC all the vendors discussed how their fancy 7-layer inspection technology is now available as a virtual machine. Of course unless they are old (like us), they won t remember that network security appliances happened because granular inspection and policy enforcement in software did not scale. Details, we know. But it is sometimes amusing when vendors position software-based network security as new and innovative. Inserting inspection points and bottlenecks in a cloud environment (public, private, or hybrid) breaks the whole cloud computing model. Effective cloud security takes a new approach, not just repositioning existing network security. There are some significant advantages that cloud architectures offer for separation of processes, users and data. Leveraging these advantages and mitigating a few disadvantages will take a new approach. More on that later. 5
6 Vendor Views Sales Pulse does not make buy or sell recommendations. We do express sentiment regarding current segment and vendor trends. The views below are our current views for the Information Security portion of business for these vendors. We are always monitoring for information that will change our views, primarily based upon field input. High Conviction Views Strong Growth: PANW, FTNT, GIMO, CUDA Positive Views Favorable Execution and Growth: PFPT, IMPV, QLYS, CYBR, RDWR, SPLK Cautious Views Signs of Possible Disruption: FEYE, VSCO, JNPR, NTCT, VDSI, SYMC, VMW, CHKP In Transition, Monitoring Execution: CSCO, FFIV, BLOX 6
7 Vendor Views PANW Very Strong Indications for Continued Growth, Watching for Upside from End Point, Possible Threat from Increased Competition - Palo Alto has done the best job of positioning as the next strategic security platform. They have a very strong brand and large distribution engine. Fortinet probably has a price / performance advantage, but is not nearly as proficient at selling to the enterprise. It s less about product capabilities and more about sales execution now, and Palo Alto is pretty good at sales execution. That has also favored Palo Alto and FireEye for advanced threat deals. The endpoint is the potential Achilles heel. Network security companies usually are poor at providing endpoint security, and the Cyvera technology they bought was raw and has needed a lot of work. - The company continues to aggressively expand their sales force with some recent hires coming from the storage market, EMC and NetApp in some markets. In this case Palo Alto appears to be hiring based upon success in competitive markets rather than security expertise. Key Issues: - We expect more aggressive responses by incumbent FW vendors who would like to make it harder for Palo Alto to take share. Although Cisco, Juniper and Check Point continue to try to show some progress so far there have been no significant improvements that we see as impacting Palo Alto s trajectory. We anticipate more moves this year by these vendors to shore up their position. Cisco has the greatest potential to improve their competitiveness through the introduction of a next gen platform. Fortinet is also working to step up their efforts against Palo Alto. In their case, they have a competitive platform but have some marketing challenges to overcome to have a greater impact in Palo Alto s core market. - Development of the Palo Alto s Traps, end point solution - as we will explore further in a separate report, the end point market is very large and ripe for change. Palo Alto and other vendors have introduced new and useful technology. No solutions are yet ready however to make major inroads into this market. Despite the fact that Palo Alto s initial success with Traps has been over stated, the end point market represents potential upside. 7
8 PANW (continued): Current outlook: - At this time we see no disruption in sight to Palo Alto s strong execution and growth. Palo Alto has continued to build on the lead they established with their solution set and marketing of their next generation security platform. The few execution issues we have seen (i.e. initially misguided telecom sales effort) have been overcome by their favorable overall execution and the benefit of very good market timing. Palo Alto has a large addressable market that is going through a major technology evaluation and refresh. - Some have recently suggested that we are approaching a peak in the firewall refresh cycle. As discussed in our section on Network Security, the current market evolution is not only based upon the move to NGFW, but the deployment of technologies for malware detection and threat intelligence. The addition of this much needed functionality is increasing the TAM for the Network Security Gateway to the benefit of vendors who have been aggressive in adding these solutions to their next generation platforms. - Palo Alto continues to receive the highest score for growth in our quarterly surveys. On-going dialogue with VARs, SIs, and other field contacts in this market indicates continued strength for Palo Alto. 8
9 FTNT Strong Indications for Continued Growth; Some Evidence of Progress in Large Enterprises - Fortinet is executing well in their traditional markets - SMB (where their UTM approach is efficient in cost and resources), Distributed Enterprise (where their very low cost edge UTM is unmatched in price / performance / functionality) and in large, managed service provider data centers (where the high performance / low latency of their ASIC based architecture is needed). They have picked up some new channels after Sourcefire was acquired by Cisco. They also continue to build their sales and marketing organizations in an effort to accelerate their growth. - Fortinet's gets high marks for keeping up with an aggressive product roadmap. The company displays the engineering approach of their CEO as well as his lack of marketing focus. Some criticize them for having too broad of a product set (includes WiFi, cameras, and a few other misc products that provide very little revenue and arguably distract from their security focus). But they execute very well on their security product roadmap so this does not seem to be a big concern. - Fortinet does well in head to head tests when the focus is on price / performance against Palo Alto and others, although their management software is not as strong, especially for large environments. It appears that Fortinet s slower growth vs. Palo Alto has helped them realize the importance of marketing. Over the past year they have been investing much more heavily in expanding sales and marketing. Feedback is that they have hired some very capable marketing people. - Fortinet has shown that they may be accelerating in the large enterprise market with some impressive wins in the past few quarters. Current outlook: - Based upon ongoing feedback we believe Fortinet will continue to grow faster than the market because of their strong execution in the three markets we discussed. We believe they are benefitting from the pickup in hiring they have done over the past three quarters. We also expect their OPEX to remain fairly high because they appear committed to continue to hire in their attempt to catch up to Palo Alto s growth rate. - In very recent discussions we are hearing that some VARs are growing frustrated with the difficulty they are having representing Palo Alto because of their hot stature in the market. Although this is generally a positive indication for Palo Alto, a number of the VARs we have spoken with have decided to put more effort into selling Fortinet. In revisiting Fortinet some have commented on their surprise at the advantages of Fortinet s solutions. The new attention of some capable VARs along with Fortinet s strong platform and improved marketing could be an added boost for Fortinet. As always we will be monitoring for additional signs of progress. 9
10 CSCO Opportunity to Pick up the Pace and Disrupt - Recent comments made by Cisco s CEO and CFO disclaim interest in FireEye, but affirm expectations for future acquisitions in the security market. As the largest vendor in the security market Cisco has the potential to pick up their pace of growth and possibility disrupt some some current hot vendors including Palo Alto, Fortinet and FireEye. With mediocre execution Cisco can continue to pick up their pace of growth in the security market. To disrupt they need to execute on an aggressive product roadmap, something that has always proven to be difficult for large organizations. - Still a share loser in FW market - Cisco has a relatively large share in the fragmented security market. In the firewall segment they remain a net share loser in a growing market as their aging ASA FW has been targeted for replacement by competitors, most notably Palo Alto and Fortinet. In their most recent quarter Cisco has shown renewed growth in security based upon strong execution with products acquired via Sourcefire. Sourcefire has provided a leading IPS solution as well as strong anti-malware and end point technology. Although some end users, especially mid-size, are consolidating traditional FW and IPS functionality in next generation platforms there are still many organizations who keep these functions separate. Cisco/Sourcefire has a strong IPS solution and Cisco s sales force has been ramping up in their ability to sell it. - Opportunity for acceleration - Cisco is competing more effectively as their Sourcefire technology permeates through the ASA hardware. They most recently added Sourcefire IPS capabilities via a co-processor in the ASA platform. Although not a strong performer, this upgrade has added functionality and is effective in environments where performance is not a constraint. They remain vulnerable in evaluations and head to head tests against competitors where performance is a major consideration. We believe that Cisco has been working very hard on a new product set that will leverage legacy ASA functionality and Sourcefire IPS and other advanced features in a true next generation platform. If they execute well and deliver a competitive solution in the near future, they have the opportunity to protect their base, take advantage of strong security budgets and realize stronger revenue growth. As a strategic supplier to their large customer base, they also have the opportunity to consolidate other security functions in response to CIOs who would rather reduce their number of suppliers vs. chase all the point products that they are now using to meet the ever increasing number of security threats. The key question is when Cisco may introduce a next generation platform and how competitive it will be. Marty Roesch, former founder and CEO of Sourcefire, who now leads Cisco s security group is highly regarded and believed to provide the right vision and leadership for Cisco s efforts. We believe that delivering a next generation hardware is easier now then in the past. Platforms from Cavium and Netronome provide very high performance and rich software for performing packet inspection and the basic functions of security. The Cisco / Sourcefire product is currently based on the Netronome processor and that would seem to offer 10
11 CSCO (continued): one path to a very competitive next gen platform. ASA software provides legacy FW features and Sourcefire has leading IPS functionality. With all these building blocks how hard could it be to deliver a solution set that will go head to head with Palo Alto, Fortinet, Dell,. Apparently product development is harder than it looks. - Some Thoughts on Acquisitions - In recent articles Palo Alto, Fortinet, Check Point, FireEye, F5, Imperva, and others have been named as potential acquisition targets by Cisco. We believe that Cisco will make multiple acquisitions in the security segment but likely smaller companies with technology they can leverage with their large sales engine. Many of the companies named have solutions that overlap with Cisco s ASA / Sourcefire technology discussed above where we believe Cisco is still committed to their own development efforts. The security market offers many choices in terms of problems to solve and there has been a proliferation of early stage security companies with innovative solutions. Cisco has recently made small acquisitions in security including Neohapsis (Dec 2014, Security advisory services) and Threat Grid (June 2014, Threat intelligence and malware analysis). We expect more of these types of acquisitions, especially in the services area where Cisco needs to add resources that will be difficult to achieve organically. Two other areas where Cisco may get more aggressive are in the end point market and analytics. These are both large markets that are ripe for new solutions (more about that in a future report). There are numerous private companies, and a few public in analytics, that would accelerate their efforts. It is also possible that Cisco may go after public players like Imperva or CyberArk, where there is little overlap with their current technology, (although in Privileged Identity Management Xceedium may be a better choice). Current Outlook: - In summary, we believe that Cisco is determined to accelerate their growth in the security market. We have no doubt that they are working hard at internal development and at acquisitions and we expect to see the results of both as this year progresses. With mediocre execution they can at least see improved growth, with strong execution they can disrupt a number of today s hot vendors. It promises to be an interesting year and we will be watching closely and collecting input from our network of industry professionals to help us understand the dynamics and impact that Cisco s moves will have on the market and vendors. 11
12 Sales Pulse Universe of Coverage in Security Segment A10 Networks Barracuda Check Point Software Cisco Citrix CyberArk F5 FireEye Fortinet Gigamon HP IBM Imperva Infoblox Intel Security Juniper Networks MobileIron Netscout / Arbor Palo Alto Networks Proofpoint Qualys Radware Splunk Symantec Trend Micro Varonis Vasco VMware Private and early stage companies including: Blue Coat Dell Gemalto / SafeNet Bit9 + Carbon Black ForeScout Tenable Network Security Netronome Websense Bromium Invincea Tanium Open Peak LightCyber Dumballa Vectra Networks Okta There are many, many more private companies entering the security market, some that we are familiar with and others less so. We are always happy to discuss other vendors and reach out to our network of industry contacts to get feedback that may be helpful to clients. 12
13 Additional Topics in This Series of Reports: In this and following reports, we discuss our views of the information security market with a focus on current trends, anticipating disruption and monitoring the market for change. Examples of topics we will explore include: ü Growing Budgets for Information Security ü Refresh / Upgrade Cycle for Network Security Acceleration of Anti-malware, Remediation Application Security Endpoint Security A Very Large Market Segment Ripe for Disruption Infection Point for Identity and Access Management Security Management and the Growth of Analytics Cloud Security Fundamental Change vs. Cloud Washing. Security as a Service Response of the Large Incumbents (Cisco, Symantec, Intel, Juniper, to Share Erosion and Change) We offer our current views and will update on an on-going basis based upon input from VARs, SIs, End Users with insight into competitive market dynamics, share shift and evaluation of the size of the TAM for various segments. 13
14 Copyright 2015, Sales Pulse Research, LLC All rights reserved. Important Disclosures: Facts and the other informalon contained in this report have been obtained from public sources considered reliable but are not guaranteed in any way. No independent confirmalon of the truth, correctness or accuracy of the informalon presented has been made by Sales Pulse Research, LLC. This report is published solely for informalon purposes and is not an offer to buy or sell or a solicitalon of an offer to buy or sell any security or derivalve. Sales Pulse Research, LLC accepts no responsibility for any loss or damage suffered by any person or enlty as a result of any such person's or enlty's reliance on the informalon presented in this report. Opinions and eslmates expressed herein consltute judgments as of the date appearing on the report and are subject to change without nolce. Employees of Sales Pulse Research, LLC may from Lme to Lme acquire, hold or sell a posilon in the securiles menloned herein in this report. All of the recommendalons and views about the securiles and companies in this report accurately reflect the personal views of the analyst(s) of Sales Pulse Research, LLC. No part of analyst's compensalon was, is, or will be directly or indirectly related to the specific recommendalons or views expressed by the research analyst. No part of this document may be copied, photocopied, or duplicated in any form or other means redistributed or quoted without the prior wri\en consent of Sales Pulse Research, LLC. The informalon contained herein has been obtained from sources believed reliable but is it not necessarily complete and accuracy is not guaranteed. ConfidenLality NoLce: This transmi\al is a confidenlal communicalon or may otherwise be privileged or confidenlal. If you are not the intended recipient, you are hereby nolfied that you have received this transmi\al in error and that any review, disseminalon, distribulon or copying of this transmi\al is strictly prohibited. If you have received this communicalon in error, please nolfy the sender immediately by reply and delete this message and all its a\achments, if any. 14
15 Addendum 15
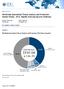
16 Technology Blankblank Trends Rating Change Since Fall Survey +.1 Survey Results The graphic on this page is from our March survey. The column on the far right compares recent results with our survey from last fall. The question asked our field contacts for their estimate of growth for each vendor on a scale of 1 5. We will mention our typical disclaimer, that we do not usual find the greatest value in numerical results. They do sometimes provide clues however, along with the comments and anecdotes to help us better understand the market. A few takeaways from these results: Results for all vendors in the security segment indicated growth (above the 3.0 level). Although our field contacts are an optimistic group by nature, this is the highest aggregate level we have seen for any segment and correlates with other bullish indicators for security spending. No surprise that indications for Palo Alto are the strongest of any vendor - consistent with input that we have received over the past year as well as published reports showing rapid new account gains and growing deal sizes. Both CyberArk and Proofpoint saw somewhat notable ratings increases. These increases correlate well with comments we have heard from VARs regarding the acceleration of their businesses. Indications for other vendors are discussed in the vendor section of this and upcoming reports
17 Supplemental Information: Sales Pulse Research Update Notes Archive - Bloomberg Terminal Function PLSR Sales Pulse Research Update Notes Archive ( Contact SPR for PW Securosis - Research Library ( Securosis Blog ( Both Sales Pulse and Securosis have a history of working hard to keep marketing hype to a minimum, reports concise and focusing on what we know and believe to be the best way to offer value to our clients. We are always happy to discuss areas of specific interest in more detail and work collaboratively with clients on targeted projects. 17
18 Sales Pulse Research In addition to coverage of the Cyber Security market Sales Pulse provides research on technology market segments that includes Cloud, Data Center / Virtualization, WLAN, Big Data and Analytics, Storage, Telecommunications, Enterprise Networking, Optical Networking, SaaS, XaaS, Network Management, Application Acceleration/Optimization, and Unified Communications and Collaboration. Contacts: Tom Morphis Sales Pulse Research, LLC (404) tom@salespulse.net Steve Thompson Sales Pulse Research, LLC steve@salespulse.net 18
The Cyber Threat Landscape
 The Cyber Threat Landscape Oliver Rochford Research Director Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without
The Cyber Threat Landscape Oliver Rochford Research Director Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without
Requirements When Considering a Next- Generation Firewall
 White Paper Requirements When Considering a Next- Generation Firewall What You Will Learn The checklist provided in this document details six must-have capabilities to look for when evaluating a nextgeneration
White Paper Requirements When Considering a Next- Generation Firewall What You Will Learn The checklist provided in this document details six must-have capabilities to look for when evaluating a nextgeneration
Software Defined Networking Moving Towards Mainstream
 Electronics Banking Research August 2012 Software Defined Networking Moving Towards Mainstream Key Takeaways: Edited by Kirk Bloede Software Defined Networking (SDN) has emerged as a promising new approach
Electronics Banking Research August 2012 Software Defined Networking Moving Towards Mainstream Key Takeaways: Edited by Kirk Bloede Software Defined Networking (SDN) has emerged as a promising new approach
2012 North American Enterprise Firewalls Market Penetration Leadership Award
 2012 2012 North American Enterprise Firewalls Market Penetration Leadership Award 2012 Frost & Sullivan 1 We Accelerate Growth Market Penetration Leadership Award Enterprise Firewalls North America, 2012
2012 2012 North American Enterprise Firewalls Market Penetration Leadership Award 2012 Frost & Sullivan 1 We Accelerate Growth Market Penetration Leadership Award Enterprise Firewalls North America, 2012
Braindumps.700-295.50.QA
 Braindumps.700-295.50.QA Number: 700-295 Passing Score: 800 Time Limit: 120 min File Version: 6.0 http://www.gratisexam.com/ Comprehensive, easy and to the point study material made it possible for me
Braindumps.700-295.50.QA Number: 700-295 Passing Score: 800 Time Limit: 120 min File Version: 6.0 http://www.gratisexam.com/ Comprehensive, easy and to the point study material made it possible for me
Market Guide for Network Sandboxing
 G00271317 Market Guide for Network Sandboxing Published: 2 March 2015 Analyst(s): Lawrence Orans, Jeremy D'Hoinne Choosing a network sandboxing solution is challenging due to the wide array of options
G00271317 Market Guide for Network Sandboxing Published: 2 March 2015 Analyst(s): Lawrence Orans, Jeremy D'Hoinne Choosing a network sandboxing solution is challenging due to the wide array of options
IT Security Q1 2016. Investment Banking. Market Challenges Slow Near-Term Activity in IT Security. Highlights from RSA Conference.
 Q1 2016 Investment Banking Market Challenges Slow Near-Term Activity in IT Security IT Security In This Report Highlights from RSA Conference IPO activity slows as valuations decline Volatility delays
Q1 2016 Investment Banking Market Challenges Slow Near-Term Activity in IT Security IT Security In This Report Highlights from RSA Conference IPO activity slows as valuations decline Volatility delays
Next-Generation Firewalls: CEO, Miercom
 Next-Generation Firewalls: Results from the Lab Robert Smithers Robert Smithers CEO, Miercom Agenda Participating i Vendors and Products How We Did It Categories of Products Tested About the Technology
Next-Generation Firewalls: Results from the Lab Robert Smithers Robert Smithers CEO, Miercom Agenda Participating i Vendors and Products How We Did It Categories of Products Tested About the Technology
Seven Requirements for Hybrid Web Delivery Getting the best of both on-premises and SaaS
 Seven Requirements for Hybrid Web Delivery Getting the best of both on-premises and SaaS Traditionally, IT risk management has balanced security investment and the impact of the threat, allowing each business
Seven Requirements for Hybrid Web Delivery Getting the best of both on-premises and SaaS Traditionally, IT risk management has balanced security investment and the impact of the threat, allowing each business
The Evolution of the Enterprise And Enterprise Security
 The Evolution of the Enterprise And Enterprise Security Introduction Today's enterprise is evolving rapidly, with new technologies such as consumer-grade mobile devices, internet-based applications and
The Evolution of the Enterprise And Enterprise Security Introduction Today's enterprise is evolving rapidly, with new technologies such as consumer-grade mobile devices, internet-based applications and
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL
 CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
Achieving Actionable Situational Awareness... McAfee ESM. Ad Quist, Sales Engineer NEEUR
 Achieving Actionable Situational Awareness... McAfee ESM Ad Quist, Sales Engineer NEEUR The Old SECURITY Model Is BROKEN 2 Advanced Targeted Attacks The Reality ADVANCED TARGETED ATTACKS COMPROMISE TO
Achieving Actionable Situational Awareness... McAfee ESM Ad Quist, Sales Engineer NEEUR The Old SECURITY Model Is BROKEN 2 Advanced Targeted Attacks The Reality ADVANCED TARGETED ATTACKS COMPROMISE TO
Addressing APTs and Modern Malware with Security Intelligence Date: September 2013 Author: Jon Oltsik, Senior Principal Analyst
 ESG Brief Addressing APTs and Modern Malware with Security Intelligence Date: September 2013 Author: Jon Oltsik, Senior Principal Analyst Abstract: APTs first came on the scene in 2010, creating a wave
ESG Brief Addressing APTs and Modern Malware with Security Intelligence Date: September 2013 Author: Jon Oltsik, Senior Principal Analyst Abstract: APTs first came on the scene in 2010, creating a wave
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T W o r l d w i d e W e b S e c u r i t y 2 0 1 1-2 0 1 5 F o r e c a s t a n d 2 0 1
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T W o r l d w i d e W e b S e c u r i t y 2 0 1 1-2 0 1 5 F o r e c a s t a n d 2 0 1
SPR update 3-23-15: Highlights from the Enterprise Connect Conference (SONS, MSFT, PLT, AUDC, EGHT, SHOR, BSFT, RNG, IRI, PLCM, CSCO, SMT)
 SPR update 3-23-15: Highlights from the Enterprise Connect Conference (SONS, MSFT, PLT, AUDC, EGHT, SHOR, BSFT, RNG, IRI, PLCM, CSCO, SMT) Enterprise Connect: Vendors Fighting for Growth As Budgets Shrink
SPR update 3-23-15: Highlights from the Enterprise Connect Conference (SONS, MSFT, PLT, AUDC, EGHT, SHOR, BSFT, RNG, IRI, PLCM, CSCO, SMT) Enterprise Connect: Vendors Fighting for Growth As Budgets Shrink
Advanced Threat Detection: Necessary but Not Sufficient The First Installment in the Blinded By the Hype Series
 Advanced Threat Detection: Necessary but Not Sufficient The First Installment in the Blinded By the Hype Series Whitepaper Advanced Threat Detection: Necessary but Not Sufficient 2 Executive Summary Promotion
Advanced Threat Detection: Necessary but Not Sufficient The First Installment in the Blinded By the Hype Series Whitepaper Advanced Threat Detection: Necessary but Not Sufficient 2 Executive Summary Promotion
Securing Your Business with DNS Servers That Protect Themselves
 Summary: The Infoblox DNS security product portfolio mitigates attacks on DNS/DHCP servers by intelligently recognizing various attack types and dropping attack traffic while responding only to legitimate
Summary: The Infoblox DNS security product portfolio mitigates attacks on DNS/DHCP servers by intelligently recognizing various attack types and dropping attack traffic while responding only to legitimate
How to Choose the Right Security Information and Event Management (SIEM) Solution
 How to Choose the Right Security Information and Event Management (SIEM) Solution John Burnham Director, Strategic Communications and Analyst Relations IBM Security Chris Meenan Director, Security Intelligence
How to Choose the Right Security Information and Event Management (SIEM) Solution John Burnham Director, Strategic Communications and Analyst Relations IBM Security Chris Meenan Director, Security Intelligence
REMOVING THE BARRIERS FOR DATA CENTRE AUTOMATION
 REMOVING THE BARRIERS FOR DATA CENTRE AUTOMATION The modern data centre has ever-increasing demands for throughput and performance, and the security infrastructure required to protect and segment the network
REMOVING THE BARRIERS FOR DATA CENTRE AUTOMATION The modern data centre has ever-increasing demands for throughput and performance, and the security infrastructure required to protect and segment the network
INSERT COMPANY LOGO HERE
 INSERT COMPANY LOGO HERE 2014 Frost & Sullivan 1 We Accelerate Growth Technology Innovation Leadership Award Network Security Global, 2014 Frost & Sullivan s Global Research Platform Frost & Sullivan is
INSERT COMPANY LOGO HERE 2014 Frost & Sullivan 1 We Accelerate Growth Technology Innovation Leadership Award Network Security Global, 2014 Frost & Sullivan s Global Research Platform Frost & Sullivan is
The Benefits of an Integrated Approach to Security in the Cloud
 The Benefits of an Integrated Approach to Security in the Cloud Judith Hurwitz President and CEO Marcia Kaufman COO and Principal Analyst Daniel Kirsch Senior Analyst Sponsored by IBM Introduction The
The Benefits of an Integrated Approach to Security in the Cloud Judith Hurwitz President and CEO Marcia Kaufman COO and Principal Analyst Daniel Kirsch Senior Analyst Sponsored by IBM Introduction The
Weekly Valuation Update & Metrics Review Big Data & Cyber Security Firms Ended: Friday, November 14, 2014
 Weekly Valuation Update & Metrics Review Big Data & Cyber Security Firms Ended: Friday, November 14, 2014 Michael S. Lewis, CFA Managing Director msl@thesilverlinegroup.com (703) 424-1969 Michael J. Smith,
Weekly Valuation Update & Metrics Review Big Data & Cyber Security Firms Ended: Friday, November 14, 2014 Michael S. Lewis, CFA Managing Director msl@thesilverlinegroup.com (703) 424-1969 Michael J. Smith,
Agenda. 3 2012, Palo Alto Networks. Confidential and Proprietary.
 Agenda Evolution of the cyber threat How the cyber threat develops Why traditional systems are failing Need move to application controls Need for automation 3 2012, Palo Alto Networks. Confidential and
Agenda Evolution of the cyber threat How the cyber threat develops Why traditional systems are failing Need move to application controls Need for automation 3 2012, Palo Alto Networks. Confidential and
How To Buy Nitro Security
 McAfee Acquires NitroSecurity McAfee announced that it has closed the acquisition of privately owned NitroSecurity. 1. Who is NitroSecurity? What do they do? NitroSecurity develops high-performance security
McAfee Acquires NitroSecurity McAfee announced that it has closed the acquisition of privately owned NitroSecurity. 1. Who is NitroSecurity? What do they do? NitroSecurity develops high-performance security
SSL Performance Problems
 ANALYST BRIEF SSL Performance Problems SIGNIFICANT SSL PERFORMANCE LOSS LEAVES MUCH ROOM FOR IMPROVEMENT Author John W. Pirc Overview In early 2013, NSS Labs released the results of its Next Generation
ANALYST BRIEF SSL Performance Problems SIGNIFICANT SSL PERFORMANCE LOSS LEAVES MUCH ROOM FOR IMPROVEMENT Author John W. Pirc Overview In early 2013, NSS Labs released the results of its Next Generation
Sourcefire Solutions Overview Security for the Real World. SEE everything in your environment. LEARN by applying security intelligence to data
 SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
Unified Security, ATP and more
 SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
Joshua Beeman University Information Security Officer October 17, 2011
 Joshua Beeman University Information Security Officer October 17, 2011 1 June, 2011- NPTF Security Presentation on FY 12 InfoSec goals: Two Factor Authentication Levels of Assurance Shibboleth InCommon
Joshua Beeman University Information Security Officer October 17, 2011 1 June, 2011- NPTF Security Presentation on FY 12 InfoSec goals: Two Factor Authentication Levels of Assurance Shibboleth InCommon
Trends in Zero-Day Kernel Exploits and Protection 2015
 Trends in Zero-Day Kernel Exploits and Protection 2015 Overview of Key Protection Technologies and Their Limitations in Dealing With Zero-Day Kernel Attacks Executive Summary Legacy security solutions
Trends in Zero-Day Kernel Exploits and Protection 2015 Overview of Key Protection Technologies and Their Limitations in Dealing With Zero-Day Kernel Attacks Executive Summary Legacy security solutions
CyberArk Privileged Threat Analytics. Solution Brief
 CyberArk Privileged Threat Analytics Solution Brief Table of Contents The New Security Battleground: Inside Your Network...3 Privileged Account Security...3 CyberArk Privileged Threat Analytics : Detect
CyberArk Privileged Threat Analytics Solution Brief Table of Contents The New Security Battleground: Inside Your Network...3 Privileged Account Security...3 CyberArk Privileged Threat Analytics : Detect
Securing your IOT journey and beyond. Alvin Rodrigues Market Development Director South East Asia and Hong Kong. What is the internet of things?
 Securing your IOT journey and beyond Alvin Rodrigues Market Development Director South East Asia and Hong Kong 1 What is the internet of things? 2 1 Imagine if Meeting @ 9am 5 mins later Meeting delayed
Securing your IOT journey and beyond Alvin Rodrigues Market Development Director South East Asia and Hong Kong 1 What is the internet of things? 2 1 Imagine if Meeting @ 9am 5 mins later Meeting delayed
SourceFireNext-Generation IPS
 D Ů V Ě Ř U J T E S I L N Ý M SourceFireNext-Generation IPS Petr Salač CCNP Security, CCNP, CICSP, CCSI #33835 petr.salac@alefnula.com Our Customers Biggest Security Challenges Maintaining security posture
D Ů V Ě Ř U J T E S I L N Ý M SourceFireNext-Generation IPS Petr Salač CCNP Security, CCNP, CICSP, CCSI #33835 petr.salac@alefnula.com Our Customers Biggest Security Challenges Maintaining security posture
Next Generation Enterprise Network Security Platform
 Next Generation Enterprise Network Security Platform November 2014 Lyndon Clough - Territory Sales Manager Derran Guinan Systems Engineer Agenda The Palo Alto Networks story Today s Threat Landscape The
Next Generation Enterprise Network Security Platform November 2014 Lyndon Clough - Territory Sales Manager Derran Guinan Systems Engineer Agenda The Palo Alto Networks story Today s Threat Landscape The
Cisco Cloud Web Security
 Data Sheet Today s highly connected and fast-moving world is filled with complex and sophisticated web security threats. Cisco delivers the strong protection, complete control, and investment value that
Data Sheet Today s highly connected and fast-moving world is filled with complex and sophisticated web security threats. Cisco delivers the strong protection, complete control, and investment value that
The Advanced Attack Challenge. Creating a Government Private Threat Intelligence Cloud
 The Advanced Attack Challenge Creating a Government Private Threat Intelligence Cloud The Advanced Attack Challenge One of the most prominent and advanced threats to government networks is advanced delivery
The Advanced Attack Challenge Creating a Government Private Threat Intelligence Cloud The Advanced Attack Challenge One of the most prominent and advanced threats to government networks is advanced delivery
2012 North American Managed Security Service Providers Growth Leadership Award
 2011 South African Data Centre Green Excellence Award in Technology Innovation Cybernest 2012 2012 North American Managed Security Service Providers Growth Leadership Award 2011 Frost & Sullivan 1 We Accelerate
2011 South African Data Centre Green Excellence Award in Technology Innovation Cybernest 2012 2012 North American Managed Security Service Providers Growth Leadership Award 2011 Frost & Sullivan 1 We Accelerate
KEYW uses acquired Sensage technology to form Hexis Cyber Solutions
 KEYW uses acquired Sensage technology to form Hexis Cyber Solutions Analyst: Javvad Malik 13 Nov, 2013 In the virtual arms race, attack tools and techniques get shared among a wide range of actors with
KEYW uses acquired Sensage technology to form Hexis Cyber Solutions Analyst: Javvad Malik 13 Nov, 2013 In the virtual arms race, attack tools and techniques get shared among a wide range of actors with
Sophos Acquires Cyberoam
 Sophos Acquires Cyberoam Frequently Asked Questions Table of Contents FAQ... 2 What is Sophos announcing?... 2 Who is Cyberoam?... 2 Why is Sophos acquiring Cyberoam?... 2 Why is Sophos acquiring Cyberoam
Sophos Acquires Cyberoam Frequently Asked Questions Table of Contents FAQ... 2 What is Sophos announcing?... 2 Who is Cyberoam?... 2 Why is Sophos acquiring Cyberoam?... 2 Why is Sophos acquiring Cyberoam
you us MSSP are a Managed Security Service Provider looking to offer Advanced Malware Protection Services
 MSSP you us are a Managed Security Service Provider looking to offer Advanced Malware Protection Services Lastline is the only company with 10+ years of academic research focused on detecting advanced
MSSP you us are a Managed Security Service Provider looking to offer Advanced Malware Protection Services Lastline is the only company with 10+ years of academic research focused on detecting advanced
CASE STUDY. NEXON ASIA PACIFIC Nexon Securely Onboards 25 Cloud Customers in Only Eight Months
 CASE STUDY NEXON ASIA PACIFIC PAGE 1 Nexon Asia Pacific is a Managed Security Service Provider (MSSP) that delivers infrastructure and software to provide secure connectivity and productivity applications,
CASE STUDY NEXON ASIA PACIFIC PAGE 1 Nexon Asia Pacific is a Managed Security Service Provider (MSSP) that delivers infrastructure and software to provide secure connectivity and productivity applications,
Cloud Computing. Exclusive Research from
 2014 Cloud Computing Exclusive Research from Cloud Computing Continues to Make Inroads Companies are expanding their use of cloud as they work through implementation and organizational challenges Cloud
2014 Cloud Computing Exclusive Research from Cloud Computing Continues to Make Inroads Companies are expanding their use of cloud as they work through implementation and organizational challenges Cloud
Scott Lucas: I m Scott Lucas. I m the Director of Product Marketing for the Branch Solutions Business Unit.
 Juniper Networks Next Generation Security for a Cybercrime World Lior Cohen Principal Solutions Architect Scott Lucas Director of Product Marketing, Branch Solutions Service Layer Technologies Business
Juniper Networks Next Generation Security for a Cybercrime World Lior Cohen Principal Solutions Architect Scott Lucas Director of Product Marketing, Branch Solutions Service Layer Technologies Business
Zak Khan Director, Advanced Cyber Defence
 Securing your data, intellectual property and intangible assets from cybercrime Zak Khan Director, Advanced Cyber Defence Agenda (16 + optional video) Introduction (2) Context Global Trends Strategic Impacts
Securing your data, intellectual property and intangible assets from cybercrime Zak Khan Director, Advanced Cyber Defence Agenda (16 + optional video) Introduction (2) Context Global Trends Strategic Impacts
SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION
 SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION How ThreatBLADES add real-time threat scanning and alerting to the Analytics Platform INTRODUCTION: analytics solutions have become an essential weapon
SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION How ThreatBLADES add real-time threat scanning and alerting to the Analytics Platform INTRODUCTION: analytics solutions have become an essential weapon
Firms Turn To Next- Generation Firewalls To Tackle Evolving IT Threats
 A Custom Technology Adoption Profile Commissioned By Fortinet April 2014 1 Firms Turn To Next- Generation Firewalls To Tackle Evolving IT Threats Introduction With the advancement of technology, IT security
A Custom Technology Adoption Profile Commissioned By Fortinet April 2014 1 Firms Turn To Next- Generation Firewalls To Tackle Evolving IT Threats Introduction With the advancement of technology, IT security
Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats
 Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats Executive Summary Palo Alto Networks strategic partnership with Splunk brings the power of our next generation
Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats Executive Summary Palo Alto Networks strategic partnership with Splunk brings the power of our next generation
Achieve Deeper Network Security
 Achieve Deeper Network Security Dell Next-Generation Firewalls Abstract Next-generation firewalls (NGFWs) have taken the world by storm, revolutionizing network security as we once knew it. Yet in order
Achieve Deeper Network Security Dell Next-Generation Firewalls Abstract Next-generation firewalls (NGFWs) have taken the world by storm, revolutionizing network security as we once knew it. Yet in order
Analysis of the Global Security Information and Event Management (SIEM) and Log Management (LM) Market All Information Becomes Actionable
 Analysis of the Global Security Information and Event Management (SIEM) and Log Management (LM) Market All Information Becomes Actionable April 2015 1 List of Exhibits Chart Slide Number Executive Summary
Analysis of the Global Security Information and Event Management (SIEM) and Log Management (LM) Market All Information Becomes Actionable April 2015 1 List of Exhibits Chart Slide Number Executive Summary
The 2014 Next Generation Firewall Challenge
 Network World and Robin Layland present The 2014 Next Generation Firewall Challenge Guide to Understanding and Choosing a Next Generation Firewall to Combat Today's Threats 2014 The 2014 Next Generation
Network World and Robin Layland present The 2014 Next Generation Firewall Challenge Guide to Understanding and Choosing a Next Generation Firewall to Combat Today's Threats 2014 The 2014 Next Generation
REVOLUTIONIZING ADVANCED THREAT PROTECTION
 REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
EXTENDING NETWORK SECURITY: TAKING A THREAT CENTRIC APPROACH TO SECURITY
 EXTENDING NETWORK SECURITY: TAKING A THREAT CENTRIC APPROACH TO SECURITY Dean Frye Sourcefire Session ID: SEC-W05 Session Classification: Intermediate Industrialisation of Threat Factories Goal: Glory,
EXTENDING NETWORK SECURITY: TAKING A THREAT CENTRIC APPROACH TO SECURITY Dean Frye Sourcefire Session ID: SEC-W05 Session Classification: Intermediate Industrialisation of Threat Factories Goal: Glory,
Trustwave blocks Web-borne malware - guaranteed, or your money back
 Trustwave blocks Web-borne malware - guaranteed, or your money back Analyst: Adrian Sanabria 16 Jul, 2014 Today, Trustwave makes a bold announcement a zero malware guarantee. The anti-malware market has
Trustwave blocks Web-borne malware - guaranteed, or your money back Analyst: Adrian Sanabria 16 Jul, 2014 Today, Trustwave makes a bold announcement a zero malware guarantee. The anti-malware market has
Next Generation Security Strategies. Marc Sarrias Regional Sales Manager msarrias@paloaltonetworks.com
 Next Generation Security Strategies Marc Sarrias Regional Sales Manager msarrias@paloaltonetworks.com IT Ever-Evolving Challenges & Constraints Support IT Initiatives Minimize Business Risks from Cybersecurity
Next Generation Security Strategies Marc Sarrias Regional Sales Manager msarrias@paloaltonetworks.com IT Ever-Evolving Challenges & Constraints Support IT Initiatives Minimize Business Risks from Cybersecurity
Technology Blueprint. Protect Your Email Servers. Guard the data and availability that enable business-critical communications
 Technology Blueprint Protect Your Email Servers Guard the data and availability that enable business-critical communications LEVEL 1 2 3 4 5 SECURITY CONNECTED REFERENCE ARCHITECTURE LEVEL 1 2 4 5 3 Security
Technology Blueprint Protect Your Email Servers Guard the data and availability that enable business-critical communications LEVEL 1 2 3 4 5 SECURITY CONNECTED REFERENCE ARCHITECTURE LEVEL 1 2 4 5 3 Security
CLOUD & Managed Security Services
 CLOUD & Managed Security Services INFOCOM Security April 1 st 2015, Athens, Greece Angeliki Philippopoulou, MSEE, MBA Regional Sales Manager Copyright Fortinet Inc. All rights reserved. Agenda A few words
CLOUD & Managed Security Services INFOCOM Security April 1 st 2015, Athens, Greece Angeliki Philippopoulou, MSEE, MBA Regional Sales Manager Copyright Fortinet Inc. All rights reserved. Agenda A few words
Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses
 Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE
Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE
What is SIEM? Security Information and Event Management. Comes in a software format or as an appliance.
 Ross Spooner Cyber Security for Government Conference 6 August 2013 What is SIEM? Security Information and Event Management Centralised security log management Long term storage, analysis and reporting
Ross Spooner Cyber Security for Government Conference 6 August 2013 What is SIEM? Security Information and Event Management Centralised security log management Long term storage, analysis and reporting
A Closer Look At The Second Largest Cybersecurity M&A Transaction In History
 1 acquires A Closer Look At The Second Largest Cybersecurity M&A Transaction In History Advisors & Dealmakers In Cybersecurity. Momentum Partners, LLC Advise. Network. Invest. Symantec Acquires Blue Coat
1 acquires A Closer Look At The Second Largest Cybersecurity M&A Transaction In History Advisors & Dealmakers In Cybersecurity. Momentum Partners, LLC Advise. Network. Invest. Symantec Acquires Blue Coat
InfoTrack for Unified Communications
 InfoTrack for Unified Communications Impact of Microsoft Lync on the Enterprise Voice Market 2014 June 2014 A T3i Group Market Intelligence Program Focused on Unified Communications Enterprise and SMB
InfoTrack for Unified Communications Impact of Microsoft Lync on the Enterprise Voice Market 2014 June 2014 A T3i Group Market Intelligence Program Focused on Unified Communications Enterprise and SMB
2016 Firewall Management Trends Report
 2016 Firewall Management Trends Report A survey of trends in firewall use and satisfaction with firewall management JANUARY 2016 Copyright 2016 Skybox Security, Inc. All rights reserved. Skybox is a trademark
2016 Firewall Management Trends Report A survey of trends in firewall use and satisfaction with firewall management JANUARY 2016 Copyright 2016 Skybox Security, Inc. All rights reserved. Skybox is a trademark
CaaS Think as a bad guy Petr Hněvkovský, CISA, CISSP HP Enterprise Security
 CaaS Think as a bad guy Petr Hněvkovský, CISA, CISSP HP Enterprise Security 1 Copyright 2014 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.
CaaS Think as a bad guy Petr Hněvkovský, CISA, CISSP HP Enterprise Security 1 Copyright 2014 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice.
CASE STUDY. RHEINLAND VERSICHERUNGSGRUPPE Who Ensures Security for The Insurers? RHEINLAND VERSICHERUNGSGRUPPE Who Ensures Security for The Insurers?
 CASE STUDY RHEINLAND VERSICHERUNGSGRUPPE PAGE 1 RheinLand Versicherungsgruppe (RheinLand Insurance Group) is the holding company for several insurance companies. Established in 1880, it operates RheinLand
CASE STUDY RHEINLAND VERSICHERUNGSGRUPPE PAGE 1 RheinLand Versicherungsgruppe (RheinLand Insurance Group) is the holding company for several insurance companies. Established in 1880, it operates RheinLand
Unlock the full potential of data centre virtualisation with micro-segmentation. Making software-defined security (SDS) work for your data centre
 Unlock the full potential of data centre virtualisation with micro-segmentation Making software-defined security (SDS) work for your data centre Contents 1 Making software-defined security (SDS) work for
Unlock the full potential of data centre virtualisation with micro-segmentation Making software-defined security (SDS) work for your data centre Contents 1 Making software-defined security (SDS) work for
Security 2014 and Beyond: An Evolving Threat Environment in a Mobile, Cloud, and Virtual World
 Security 2014 and Beyond: An Evolving Threat Environment in a Mobile, Cloud, and Virtual World December 2013 Joel P. Fishbein, Jr BMO Capital Markets Corp. joel.fishbein@bmo.com (212) 885-4159 Brett Fodero
Security 2014 and Beyond: An Evolving Threat Environment in a Mobile, Cloud, and Virtual World December 2013 Joel P. Fishbein, Jr BMO Capital Markets Corp. joel.fishbein@bmo.com (212) 885-4159 Brett Fodero
WildFire. Preparing for Modern Network Attacks
 WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
Response to Questions CML 15-018 Managed Information Security
 Response to Questions CML 15-018 Managed Information Security 1. What are the most critical aspects that need to be provided for this RFP, in light of the comment that multiple awards might be provided?
Response to Questions CML 15-018 Managed Information Security 1. What are the most critical aspects that need to be provided for this RFP, in light of the comment that multiple awards might be provided?
Session 9: Changing Paradigms and Challenges Tools for Space Systems Cyber Situational Awareness
 Session 9: Changing Paradigms and Challenges Tools for Space Systems Cyber Situational Awareness Wayne A. Wheeler The Aerospace Corporation GSAW 2015, Los Angeles, CA, March 2015 Agenda Emerging cyber
Session 9: Changing Paradigms and Challenges Tools for Space Systems Cyber Situational Awareness Wayne A. Wheeler The Aerospace Corporation GSAW 2015, Los Angeles, CA, March 2015 Agenda Emerging cyber
2013 Frost & Sullivan Asia Pacific ICT Awards Network Security Vendor of the Year
 2013 Frost & Sullivan Asia Pacific ICT Awards Network Security Vendor of the Year 2013 Frost & Sullivan Asia Pacific Network Security Vendor of the Year Frost & Sullivan s Global Research Platform Frost
2013 Frost & Sullivan Asia Pacific ICT Awards Network Security Vendor of the Year 2013 Frost & Sullivan Asia Pacific Network Security Vendor of the Year Frost & Sullivan s Global Research Platform Frost
See what cloud can do for you.
 See what cloud can do for you. Uncomplicating cloud business Table of contents Introduction 3 Why cloud is relevant for your business? 4 What is changing? 4 Why organizations are moving to cloud 5 What
See what cloud can do for you. Uncomplicating cloud business Table of contents Introduction 3 Why cloud is relevant for your business? 4 What is changing? 4 Why organizations are moving to cloud 5 What
FROM PRODUCT TO PLATFORM
 FROM PRODUCT TO PLATFORM DATA EQUIPMENT 2016 Mikkel Bossen Agenda Today s Challenges Data Growth, SSL encryption, Application Growth & SaaS What s hiding in under the surface? Legacy Security is that really
FROM PRODUCT TO PLATFORM DATA EQUIPMENT 2016 Mikkel Bossen Agenda Today s Challenges Data Growth, SSL encryption, Application Growth & SaaS What s hiding in under the surface? Legacy Security is that really
Assessing the Business Value of the Secured Datacenter
 IDC SOLUTION BRIEF Assessing the Business Value of the Secured Datacenter Sponsored by: Cisco Pete Lindstrom Matthew Marden December 2014 Richard L. Villars OVERVIEW The world of IT is in the midst of
IDC SOLUTION BRIEF Assessing the Business Value of the Secured Datacenter Sponsored by: Cisco Pete Lindstrom Matthew Marden December 2014 Richard L. Villars OVERVIEW The world of IT is in the midst of
Breach Found. Did It Hurt?
 ANALYST BRIEF Breach Found. Did It Hurt? INCIDENT RESPONSE PART 2: A PROCESS FOR ASSESSING LOSS Authors Christopher Morales, Jason Pappalexis Overview Malware infections impact every organization. Many
ANALYST BRIEF Breach Found. Did It Hurt? INCIDENT RESPONSE PART 2: A PROCESS FOR ASSESSING LOSS Authors Christopher Morales, Jason Pappalexis Overview Malware infections impact every organization. Many
IBM QRadar Security Intelligence April 2013
 IBM QRadar Security Intelligence April 2013 1 2012 IBM Corporation Today s Challenges 2 Organizations Need an Intelligent View into Their Security Posture 3 What is Security Intelligence? Security Intelligence
IBM QRadar Security Intelligence April 2013 1 2012 IBM Corporation Today s Challenges 2 Organizations Need an Intelligent View into Their Security Posture 3 What is Security Intelligence? Security Intelligence
The Growing Need for Real-time and Actionable Security Intelligence Date: February 2014 Author: Jon Oltsik, Senior Principal Analyst
 ESG Brief The Growing Need for Real-time and Actionable Security Intelligence Date: February 2014 Author: Jon Oltsik, Senior Principal Analyst Abstract: ESG data indicates that many enterprise organizations
ESG Brief The Growing Need for Real-time and Actionable Security Intelligence Date: February 2014 Author: Jon Oltsik, Senior Principal Analyst Abstract: ESG data indicates that many enterprise organizations
2013 Trends to Watch: Cloud Services
 2013 Trends to Watch: Cloud Services The debate on cloud services place in enterprise IT is over Reference Code: IT019 003114 Publication Date: 25 Oct 2012 Author: John Madden SUMMARY Catalyst The debate
2013 Trends to Watch: Cloud Services The debate on cloud services place in enterprise IT is over Reference Code: IT019 003114 Publication Date: 25 Oct 2012 Author: John Madden SUMMARY Catalyst The debate
Content Security: Protect Your Network with Five Must-Haves
 White Paper Content Security: Protect Your Network with Five Must-Haves What You Will Learn The continually evolving threat landscape is what makes the discovery of threats more relevant than defense as
White Paper Content Security: Protect Your Network with Five Must-Haves What You Will Learn The continually evolving threat landscape is what makes the discovery of threats more relevant than defense as
Close the security gap with a unified approach. Detect, block and remediate risks faster with end-to-end visibility of the security cycle
 Close the security gap with a unified approach Detect, block and remediate risks faster with end-to-end visibility of the security cycle Events are not correlated. Tools are not integrated. Teams are not
Close the security gap with a unified approach Detect, block and remediate risks faster with end-to-end visibility of the security cycle Events are not correlated. Tools are not integrated. Teams are not
BEST PRACTICES RESEARCH
 2013 Frost & Sullivan 1 We Accelerate Growth Market Leadership Award Vulnerability Management Global, 2013 Frost & Sullivan s Global Research Platform Frost & Sullivan is in its 50th year of business with
2013 Frost & Sullivan 1 We Accelerate Growth Market Leadership Award Vulnerability Management Global, 2013 Frost & Sullivan s Global Research Platform Frost & Sullivan is in its 50th year of business with
The Dirty Secret Behind the UTM: What Security Vendors Don t Want You to Know
 The Dirty Secret Behind the UTM: What Security Vendors Don t Want You to Know I n t r o d u c t i o n Until the late 1990s, network security threats were predominantly written by programmers seeking notoriety,
The Dirty Secret Behind the UTM: What Security Vendors Don t Want You to Know I n t r o d u c t i o n Until the late 1990s, network security threats were predominantly written by programmers seeking notoriety,
Q1 Labs Corporate Overview
 Q1 Labs Corporate Overview The Security Intelligence Leader Who we are: Innovative Security Intelligence software company One of the largest and most successful SIEM vendors Leader in Gartner 2011, 2010,
Q1 Labs Corporate Overview The Security Intelligence Leader Who we are: Innovative Security Intelligence software company One of the largest and most successful SIEM vendors Leader in Gartner 2011, 2010,
Private Cloud for the Enterprise: Platform ISF
 Private Cloud for the Enterprise: Platform ISF A Neovise Vendor Perspective Report 2009 Neovise, LLC. All Rights Reserved. Background Cloud computing is a model for enabling convenient, on-demand network
Private Cloud for the Enterprise: Platform ISF A Neovise Vendor Perspective Report 2009 Neovise, LLC. All Rights Reserved. Background Cloud computing is a model for enabling convenient, on-demand network
Next-Generation Firewalls: Critical to SMB Network Security
 Next-Generation Firewalls: Critical to SMB Network Security Next-Generation Firewalls provide dramatic improvements in protection versus traditional firewalls, particularly in dealing with today s more
Next-Generation Firewalls: Critical to SMB Network Security Next-Generation Firewalls provide dramatic improvements in protection versus traditional firewalls, particularly in dealing with today s more
REPORT Perimeter Security Defenses. State of Perimeter Security Defenses, Time to Think Different?
 REPORT Perimeter Security Defenses State of Perimeter Security Defenses, Time to Think Different? Table of Contents Introduction 3 Key Findings 4 Implications 6 REPORT State of Perimeter Security Defenses
REPORT Perimeter Security Defenses State of Perimeter Security Defenses, Time to Think Different? Table of Contents Introduction 3 Key Findings 4 Implications 6 REPORT State of Perimeter Security Defenses
Mobile Security Challenge Emerges Smart IT Leaders Evaluating Pervasive Security Options
 Mobile Security Challenge Emerges Smart IT Leaders Evaluating Pervasive Security Options By Robin Gareiss Executive Vice President and Founder, Nemertes Research Executive Summary As more employees bring
Mobile Security Challenge Emerges Smart IT Leaders Evaluating Pervasive Security Options By Robin Gareiss Executive Vice President and Founder, Nemertes Research Executive Summary As more employees bring
Virtualization Essentials
 Virtualization Essentials Table of Contents Introduction What is Virtualization?.... 3 How Does Virtualization Work?... 4 Chapter 1 Delivering Real Business Benefits.... 5 Reduced Complexity....5 Dramatically
Virtualization Essentials Table of Contents Introduction What is Virtualization?.... 3 How Does Virtualization Work?... 4 Chapter 1 Delivering Real Business Benefits.... 5 Reduced Complexity....5 Dramatically
Ovum Decision Matrix: Selecting a Global Telco Managed Security Services Provider
 Ovum Decision Matrix: Selecting a Global Telco Managed Security Services Provider Moving from network-centric security to the broader IT security suite Reference Code: TE007-000800 Publication Date: 17
Ovum Decision Matrix: Selecting a Global Telco Managed Security Services Provider Moving from network-centric security to the broader IT security suite Reference Code: TE007-000800 Publication Date: 17
Ty Miller. Director, Threat Intelligence Pty Ltd
 Ty Miller Director, Threat Intelligence Pty Ltd Security Specialist Creator of Threat Analytics CREST Tech Lead, Assessor, Board of Directors Trained likes of FBI, US DoD, US Mil, International Govt agencies,
Ty Miller Director, Threat Intelligence Pty Ltd Security Specialist Creator of Threat Analytics CREST Tech Lead, Assessor, Board of Directors Trained likes of FBI, US DoD, US Mil, International Govt agencies,
CREATING PACKAGED IP FOR BUSINESS ANALYTICS PROJECTS
 CREATING PACKAGED IP FOR BUSINESS ANALYTICS PROJECTS A PERSPECTIVE FOR SYSTEMS INTEGRATORS Sponsored by Microsoft Corporation 1/ What is Packaged IP? Categorizing the Options 2/ Why Offer Packaged IP?
CREATING PACKAGED IP FOR BUSINESS ANALYTICS PROJECTS A PERSPECTIVE FOR SYSTEMS INTEGRATORS Sponsored by Microsoft Corporation 1/ What is Packaged IP? Categorizing the Options 2/ Why Offer Packaged IP?
Utilizing Security Ratings for Enterprise IT Risk Mitigation Date: June 2014 Author: Jon Oltsik, Senior Principal Analyst
 ESG Brief Utilizing Security Ratings for Enterprise IT Risk Mitigation Date: June 2014 Author: Jon Oltsik, Senior Principal Analyst Abstract: What do large enterprises need in order to address increasingly
ESG Brief Utilizing Security Ratings for Enterprise IT Risk Mitigation Date: June 2014 Author: Jon Oltsik, Senior Principal Analyst Abstract: What do large enterprises need in order to address increasingly
Support the Era of the App with End-to-End Network and Application Performance Visibility
 Support the Era of the App with End-to-End Network and Application Performance Visibility Traditional Performance Management Is Not Enough The realities of the modern IT landscape are daunting. Your business-critical
Support the Era of the App with End-to-End Network and Application Performance Visibility Traditional Performance Management Is Not Enough The realities of the modern IT landscape are daunting. Your business-critical
Bricata Next Generation Intrusion Prevention System A New, Evolved Breed of Threat Mitigation
 Bricata Next Generation Intrusion Prevention System A New, Evolved Breed of Threat Mitigation Iain Davison Chief Technology Officer Bricata, LLC WWW.BRICATA.COM The Need for Multi-Threaded, Multi-Core
Bricata Next Generation Intrusion Prevention System A New, Evolved Breed of Threat Mitigation Iain Davison Chief Technology Officer Bricata, LLC WWW.BRICATA.COM The Need for Multi-Threaded, Multi-Core
Changing the Enterprise Security Landscape
 Changing the Enterprise Security Landscape Petr Hněvkovský Presales Consultant, ArcSight EMEA HP Enterprise Security Products 2012 Hewlett-Packard Development Company, L.P. The information contained herein
Changing the Enterprise Security Landscape Petr Hněvkovský Presales Consultant, ArcSight EMEA HP Enterprise Security Products 2012 Hewlett-Packard Development Company, L.P. The information contained herein
Next Generation Firewalls and Sandboxing
 Next Generation Firewalls and Sandboxing Joe Hughes, Director www.servicetech.co.uk Summary What is a Next Generation Firewall (NGFW)? Threat evolution Features Deployment Best practices What is Sandboxing?
Next Generation Firewalls and Sandboxing Joe Hughes, Director www.servicetech.co.uk Summary What is a Next Generation Firewall (NGFW)? Threat evolution Features Deployment Best practices What is Sandboxing?
Tufin Orchestration Suite
 Tufin Orchestration Suite Security Policy Orchestration across Physical Networks & Hybrid Cloud Environments The Network Security Challenge In today s world, enterprises face considerably more network
Tufin Orchestration Suite Security Policy Orchestration across Physical Networks & Hybrid Cloud Environments The Network Security Challenge In today s world, enterprises face considerably more network
While you are waiting for our webinar to begin, you might be interested in the downloads on the Attachment tab:
 While you are waiting for our webinar to begin, you might be interested in the downloads on the Attachment tab: A copy of today s presentation and our Upcoming webinars Information on how to dial in if
While you are waiting for our webinar to begin, you might be interested in the downloads on the Attachment tab: A copy of today s presentation and our Upcoming webinars Information on how to dial in if
McAfee Network Security Platform
 McAfee Network Security Platform Next Generation Network Security Youssef AGHARMINE, Network Security, McAfee Network is THE Security Battleground Who is behind the data breaches? 81% some form of hacking
McAfee Network Security Platform Next Generation Network Security Youssef AGHARMINE, Network Security, McAfee Network is THE Security Battleground Who is behind the data breaches? 81% some form of hacking
Stop advanced targeted attacks, identify high risk users and control Insider Threats
 TRITON AP-EMAIL Stop advanced targeted attacks, identify high risk users and control Insider Threats From socially engineered lures to targeted phishing, most large cyberattacks begin with email. As these
TRITON AP-EMAIL Stop advanced targeted attacks, identify high risk users and control Insider Threats From socially engineered lures to targeted phishing, most large cyberattacks begin with email. As these
Ipanema Technologies: A True Synergy Between WAN Optimization and Application Performance Management
 Ipanema Technologies: A True Synergy Between WAN Optimization and Application Performance Management Introduction When WAN optimization technologies were first introduced to the market, solution providers
Ipanema Technologies: A True Synergy Between WAN Optimization and Application Performance Management Introduction When WAN optimization technologies were first introduced to the market, solution providers
Cisco Security Strategy Update Integrated Threat Defense. Oct 28, 2015
 Cisco Security Strategy Update Integrated Threat Defense Oct 28, 2015 Breaches are the New Normal FDA Wards of Security Flaw in Infusion Pump Cisco Confidential Cisco s Covers the Threat-Centric Entire
Cisco Security Strategy Update Integrated Threat Defense Oct 28, 2015 Breaches are the New Normal FDA Wards of Security Flaw in Infusion Pump Cisco Confidential Cisco s Covers the Threat-Centric Entire
