Market Guide for Network Sandboxing
|
|
|
- Daniela Norman
- 9 years ago
- Views:
Transcription
1 G Market Guide for Network Sandboxing Published: 2 March 2015 Analyst(s): Lawrence Orans, Jeremy D'Hoinne Choosing a network sandboxing solution is challenging due to the wide array of options available from established security vendors and new entrants. This market guide will help network security managers understand the range of sandboxing technology and deployment options. Key Findings The market for network sandboxing consists of three categories: (1) stand-alone (solutions that have no dependencies on existing security infrastructure); (2) sandboxing as a feature of firewalls, intrusion prevention systems (IPSs) and unified threat management (UTM) devices; and (3) sandboxing as a feature of secure Web gateways and/or secure gateways. The number of sandboxing vendors has grown quickly due to low barriers to entry and high demand. Several vendors have licensed sandboxing technology from OEM providers, and some have added very basic sandboxing capabilities. The network sandboxing market is far from mature, and solutions vary widely in functionality (for example, the types of objects that can be analyzed), efficacy and pricing. Recommendations Security leaders: Implement sandboxing technology if you need to improve perimeter-based inbound malware detection capabilities. Evaluate sandboxing-as-a-feature options from your strategic security vendors. Evaluate one or more network sandboxing solutions in the stand-alone category. These sandboxes are implemented independently of other security products and services. Maximize the breadth of sandboxing coverage allowed by your budget by implementing solutions that analyze a broad set of suspicious objects (for example, executables, files and Web objects) and monitor both Web and channels.
2 Market Definition Network-based sandboxing is a proven technique for detecting malware and targeted attacks. Network sandboxes monitor network traffic for suspicious objects and automatically submit them to the sandbox environment, where they are analyzed and assigned malware probability scores and severity ratings. In "Five Styles of Advanced Threat Defense," Gartner referred to network sandboxing as "payload analysis." Here, we use the more popular "sandbox" term. Sandboxing technology has been used for years by malware researchers at security companies and even in some large enterprises that are highly security conscious. Traditionally, using a sandbox has been an intensive effort requiring advanced skills. The malware researcher manually submits a suspicious object into the sandbox and analyzes it before flagging it as malware or not. By adding automated features to sandboxing technology (automatically submitting suspicious objects and automatically generating alerts), FireEye became instrumental in moving sandboxing from research labs into enterprise datacenters, a transformation that began around Today, many vendors sell sandboxing either as a stand-alone product or as a feature of other security solutions. Several vendors of advanced threat defense solutions that use other primary technologies for detecting threats, such as network protocol analysis, network forensics and some endpoint solutions, use sandboxing technology to further enhance the efficacy of their solutions, although they do not sell sandboxing as a separate feature (see Note 1). Market Direction The market for network sandboxing consists of these three categories: Stand-alone These solutions are implemented independently of other security products. No prerequisite products are required. Firewall/IPS/UTM Sandboxing is an optional feature of an existing network security product. It is commonly implemented in the cloud, with customers paying an annual subscription for the sandboxing service. For example, Palo Alto Networks' fee-based WildFire service charges a 20% premium for each firewall that contributes suspicious objects to the service (it also offers a more limited version free of charge). If the cost of the firewall is $100,000, customers pay $20,000 per year for this firewall to utilize the WildFire service (multiple firewalls can utilize WildFire, but customers must purchase a license for each firewall that submits objects to WildFire). Other vendors in this category have similar pricing models. Check Point is an exception, since its pricing model is based on the number of files submitted to the cloud infrastructure. Some vendors in this category offer on-premises appliances instead of a cloud-based service, primarily to address privacy concerns, and some vendors offer both on-premises and cloud-based options. Secure Web Gateway (SWG)/Secure Gateway (SEG) Sandboxing is offered as an optional feature of these content-centric solutions. The pricing models and the deployment options, cloud-based or on-premises solutions, are similar to the category above. Page 2 of 9 Gartner, Inc. G
3 Two factors account for network sandboxing emerging as the most popular "style" (see "Five Styles of Advanced Threat Defense"). The rapid growth of FireEye FY14 revenue growth of 163% (see Note 2) combined with aggressive marketing campaigns, has contributed heavily to the interest in sandboxing solutions. However, FireEye's solutions are expensive, and this has opened the door for many competitors to enter the market. This research identifies nearly 20 vendors offering sandboxing products/services. There is a low barrier to entry for traditional security vendors to add sandboxing as a feature to other products and services, because vendors can license technology from an OEM provider (two examples are Joe Security and Lastline) or build their own using open-source code. To date, most of the challenges to FireEye's dominance have come from the less expensive cloudbased services of the firewall vendors. However, Gartner expects serious challenges from key vendors in the secure Web gateway market in 2015 and 2016, particularly as Blue Coat and Zscaler ramp up their go-to-market plans. Market Analysis Several factors distinguish sandboxing solutions. The concept of "feeding content to the sandbox" represents an important architectural difference. Figure 1 shows the three main options for feeding suspicious objects to a sandbox. The integrated sensor approach (Option A) is where the feeding sensor and the sandbox are integrated in one appliance. With this approach, the sandbox "feeds" itself. The distributed sensor approach is where the feeding sensors are distributed, and they feed a centralized sandbox. Depending on the implementation, the feeding sensors could be firewalls, IPSs, UTM devices, SWGs, SEGs or dedicated sensors. Some solutions enable endpoints to feed suspicious objects to the sandbox. In Option C, the sandbox is in the cloud and is managed by the vendor. An alternative implementation for a centralized sandbox is for an enterprise to implement a local appliance-based sandbox in one of its own data centers. (Option B). Gartner, Inc. G Page 3 of 9
4 Figure 1. Sandboxing Deployment Options Source: Gartner (March 2015) The following sections analyze the three segments of the sandboxing market: Stand-Alone Stand-alone sandboxes are implemented independently of other security products. Unlike solutions where sandboxing is a feature of other security products (for example, firewall, IPS, UTM, SWG, SEG), no prerequisite products are required to implement a stand-alone sandbox. Stand-alone sandboxes can use an integrated sensor like FireEye or Trend Micro or distributed sensors like Cyphort or Lastline. In both scenarios, the sandboxes are designed to "feed" themselves without dependency on other security products. A drawback to the stand-alone approach is the requirement to add new equipment, feeding sensors, to the network. The integrated feeding sensor approach is more expensive, especially for distributed enterprises with many Internet egress points, whereas the distributed feeding sensor approach is typically less expensive, because of the centralized sandbox analysis environment. Sample Vendors: AhnLab; Cyphort; FireEye; HP; Lastline; Trend Micro; Websense Page 4 of 9 Gartner, Inc. G
5 Firewall/IPS/UTM All solutions in this category utilize the distributed feeding sensor approach. Implementations are usually cost-effective and easy to deploy, particularly when the feeding sensors (firewalls, IPSs or UTM appliances) are already in place. These devices only need to be configured to "feed" the centralized sandbox. As noted in the Market Direction section, it's common for vendors to offer sandboxing analysis as a cloud service (for example, Palo Alto WildFire, Check Point Threat Emulation, Fortinet FortiSandbox). These vendors and others also offer an on-premises appliance as an alternative model to a cloud-based service. The sandboxing features of firewalls, IPSs and UTM appliances focus on file-based analysis. They are less effective in detecting Web-based exploits, which require the analysis of Web objects, such as JavaScript and HTML. Parsing these objects negatively impacts performance on firewalls, IPSs and UTM devices, which is why many customers disable the feature or do limited (headers only) parsing. Because these solutions use the distributed sensor approach (Figure 1, Options B and C), bandwidth limitations may restrict the number of objects that they can send to a centralized sandbox. By design, they cannot flood a WAN link with a heavy load of suspicious objects, because the extra traffic may negatively impact network performance. This is especially true for small branches with more limited bandwidth than larger locations. Intellectual property and privacy concerns apply only to cloud-based sandboxes, which are a common offering among firewall, IPS and UTM vendors. Enterprises that are highly security conscious often choose appliance-based sandboxes over cloud-based sandboxes due to confidentiality concerns related to cloud services. The ability to terminate and decrypt SSL traffic is an advanced capability that is commonly found in firewalls, IPSs and UTM devices. These solutions have an advantage over those stand-alone sandboxing solutions that do not support the termination and inspection of SSL traffic. However, the performance hit from enabling SSL decryption discourages many organizations from enabling this feature (see "Security Leaders Must Address Threats From Rising SSL Traffic"). Sample Vendors: Barracuda Networks; Check Point Software; Palo Alto Networks; Fortinet; Intel Security-McAfee; WatchGuard Secure Web Gateway/Secure Gateway Similar to the FW/IPS/UTM category, SWG and SEG vendors utilize the distributed feeding sensor approach to submit objects to a centralized sandbox. Many vendors that offer SWGs and SEGs have added sandboxing as an optional feature to both solutions. This is a cost-effective approach that enables malware detection across and Web channels. The bandwidth limitation issues and the concerns about intellectual property and privacy that were noted in the FW/IPS/UTM section above also apply to sandboxing as a feature of SWG/SEG Gartner, Inc. G Page 5 of 9
6 solutions. Also, many SWGs support SSL termination, thereby enabling greater visibility into network traffic, although the performance impact on the SWG varies widely. Sample Vendors: SWG and SEG (shared sandbox approach) Intel Security-McAfee, Trend Micro; Websense. SWG Blue Coat; ContentKeeper Technologies, iboss Network Security; Zscaler. SEG Proofpoint. Note: FireEye offers a sandboxing appliance and a cloud-based service to analyze attachments, but it does not offer a SEG. HP and Trend Micro also offer a sandboxing appliance to analyze attachments. Technical Evaluation Guidelines The quality of sandboxing solutions varies widely. Critical capabilities include: The ability to analyze a broad range of suspicious objects The most basic sandboxes offer a very limited set of file types that can be analyzed (executables, DDL objects, sometimes PDFs). More advanced sandboxes include the ability to analyze other common files such as Microsoft Office documents, Java, Flash and other file types. The most advanced sandboxes are able to detect Web exploits by analyzing more Web objects, such as JavaScript and HTML elements. Static analysis and other prefiltering techniques Many technologies use prefiltering techniques to minimize the number of objects that are fed to the sandbox for further analysis. These techniques include static analysis, antivirus engines, reputation feeds and other approaches to identify malware without requiring a sandbox analysis. Suspicious objects that cannot be identified via prefiltering are analyzed in the sandbox. Prefiltering is an important factor in determining the rate of false positives and false negatives. Comprehensive operating system and application stack It is important to detect malware that has been fine-tuned to run only in a specific targeted environment. Comprehensive approaches include regional versions of Windows operating systems (for example, a Chinese version), full Microsoft Office software (not just a Word document reader) and a variety of minor and major versions of the software used to open the suspicious files. Anti-evasion technologies These are necessary to counter malware that attempts to detect the presence of a sandbox environment. An example is the use of customized hypervisors, which make it more difficult for malware to detect that it is running in a sandbox environment. A common characteristic of advanced malware is to look for the presence of a hypervisor, which may be a signal that the code is executing in a sandbox. Customized hypervisors are harder to detect and, therefore, harder to evade. However, there is a trade-off to customized hypervisors they may restrict the sandbox to running a generic version of a desktop environment instead of the enterprise's "gold" desktop image. Page 6 of 9 Gartner, Inc. G
7 The rate at which objects can be analyzed in the sandbox This is an important indicator of scalability. One way to measure scalability is to compare the number of objects that the sandbox can analyze per hour. Another important aspect to evaluate is how the sandboxing engine behaves when its queue is full. A combination of virtualization-based and emulation-based sandboxing analysis In the virtualization-based approach, suspicious objects are analyzed while executing in a virtualized operating system environment. The emulation approach uses a software layer that imitates (part of) an application, OS or hardware platform. An emulator translates, for example, API calls and machine instructions to another platform. Solutions that combine virtualization and emulation sandboxing capture the benefits of both approaches. Contextual information about the malware or targeted attack Context is important because it can help incident responders determine whether or not malware represents a targeted attack or consumer-grade malware. Information that reveals if the attack was aimed at a specific industry vertical or the motivation of the threat actors is highly valuable. Integration with forensics tools Because sandboxing analyzes malware in a simulated environment, integrating with forensics tools is valuable for confirming the impact to the enterprise's true environment. Integration with endpoint forensics tools and/or network forensics tools (for example, packet capture) enables security teams to shorten the incident response window. Market Recommendations If your organization is budget-constrained or looking for a quick path to add sandboxing, first evaluate adding sandboxing as a feature from one of your current security vendors. Assess the sandboxing capabilities of your firewall, IPS or UTM solutions and do the same for your SWG and SEG. It's likely that this approach will be the most cost-effective option, because it utilizes existing infrastructure to feed suspicious objects to the sandbox. If budget permits, or when targeted malware is identified as a high risk, evaluate stand-alone sandboxing solutions. This is likely to be the most expensive option, because it requires the addition of feeding sensors to the network. Stand-alone sandboxes typically include more advanced functionality (more of the critical capabilities outlined in the Market Analysis section) than the sandboxing-as-a-feature capabilities that have been added to firewalls, UTM devices and SWGs, although this is not always the case. The increased cost should come with recognized additional benefits such as higher detection rates and a lower number of false positives. Gartner Recommended Reading Some documents may not be available as part of your current Gartner subscription. "Five Styles of Advanced Threat Defense" Gartner, Inc. G Page 7 of 9
8 "Designing an Adaptive Security Architecture for Protection From Advanced Attacks" "Magic Quadrant for Secure Gateways" "Magic Quadrant for Secure Web Gateways" "Magic Quadrant for Enterprise Network Firewalls" "Malware Protection Systems for Detecting Malicious Code in the Network" "Fight Network Security Evasion via Wider Testing, Refined Monitoring and Vigilant Patching" Note 1 Solutions That Embed Sandboxing Technology Some solutions use sandboxing technology to complement their primary malware and advanced threat detection techniques. For example, Fidelis Cybersecurity Solutions (Fidelis XPS) and Cisco (Sourcefire Advanced Malware Protection) use this approach. Sandboxing capability is included in the core product offering for both vendors. Cisco offers a sandbox appliance known as AMP Threat Grid (available since January 2015). Because suspicious objects are not automatically fed to AMP Threat Grid by other Cisco products, it does not meet Gartner's definition of a network sandbox. At the time of this writing, suspicious files must be fed manually to the AMP Threat Grid appliance, but Cisco's road map includes plans to automate the feeding of suspicious objects to the appliance. Note 2 Factors Contributing to FireEye's Revenue Growth Network sandboxes are the flagship solutions offered by FireEye, but other products (for example, endpoint security), support services and professional services also contributed to its revenue growth. Page 8 of 9 Gartner, Inc. G
9 GARTNER HEADQUARTERS Corporate Headquarters 56 Top Gallant Road Stamford, CT USA Regional Headquarters AUSTRALIA BRAZIL JAPAN UNITED KINGDOM For a complete list of worldwide locations, visit Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without Gartner s prior written permission. If you are authorized to access this publication, your use of it is subject to the Usage Guidelines for Gartner Services posted on gartner.com. The information contained in this publication has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information and shall have no liability for errors, omissions or inadequacies in such information. This publication consists of the opinions of Gartner s research organization and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice. Although Gartner research may include a discussion of related legal issues, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner is a public company, and its shareholders may include firms and funds that have financial interests in entities covered in Gartner research. Gartner s Board of Directors may include senior managers of these firms or funds. Gartner research is produced independently by its research organization without input or influence from these firms, funds or their managers. For further information on the independence and integrity of Gartner research, see Guiding Principles on Independence and Objectivity. Gartner, Inc. G Page 9 of 9
The Cyber Threat Landscape
 The Cyber Threat Landscape Oliver Rochford Research Director Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without
The Cyber Threat Landscape Oliver Rochford Research Director Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without
Realize That Big Security Data Is Not Big Security Nor Big Intelligence
 G00245789 Realize That Big Security Data Is Not Big Security Nor Big Intelligence Published: 19 April 2013 Analyst(s): Joseph Feiman Security intelligence's ultimate objective, enterprise protection, is
G00245789 Realize That Big Security Data Is Not Big Security Nor Big Intelligence Published: 19 April 2013 Analyst(s): Joseph Feiman Security intelligence's ultimate objective, enterprise protection, is
you us MSSP are a Managed Security Service Provider looking to offer Advanced Malware Protection Services
 MSSP you us are a Managed Security Service Provider looking to offer Advanced Malware Protection Services Lastline is the only company with 10+ years of academic research focused on detecting advanced
MSSP you us are a Managed Security Service Provider looking to offer Advanced Malware Protection Services Lastline is the only company with 10+ years of academic research focused on detecting advanced
MSSP Advanced Threat Protection Service
 SOLUTION BRIEF SOLUTION BRIEF: MSSP ADVANCED THREAT PROTECTION SERVICE MSSP Advanced Threat Protection Service Fortinet Empowers MSSP Delivery of Complete ATP Managed Security Service The Need For ATP
SOLUTION BRIEF SOLUTION BRIEF: MSSP ADVANCED THREAT PROTECTION SERVICE MSSP Advanced Threat Protection Service Fortinet Empowers MSSP Delivery of Complete ATP Managed Security Service The Need For ATP
Next Generation Firewalls and Sandboxing
 Next Generation Firewalls and Sandboxing Joe Hughes, Director www.servicetech.co.uk Summary What is a Next Generation Firewall (NGFW)? Threat evolution Features Deployment Best practices What is Sandboxing?
Next Generation Firewalls and Sandboxing Joe Hughes, Director www.servicetech.co.uk Summary What is a Next Generation Firewall (NGFW)? Threat evolution Features Deployment Best practices What is Sandboxing?
Next-Generation Firewalls: CEO, Miercom
 Next-Generation Firewalls: Results from the Lab Robert Smithers Robert Smithers CEO, Miercom Agenda Participating i Vendors and Products How We Did It Categories of Products Tested About the Technology
Next-Generation Firewalls: Results from the Lab Robert Smithers Robert Smithers CEO, Miercom Agenda Participating i Vendors and Products How We Did It Categories of Products Tested About the Technology
SourceFireNext-Generation IPS
 D Ů V Ě Ř U J T E S I L N Ý M SourceFireNext-Generation IPS Petr Salač CCNP Security, CCNP, CICSP, CCSI #33835 [email protected] Our Customers Biggest Security Challenges Maintaining security posture
D Ů V Ě Ř U J T E S I L N Ý M SourceFireNext-Generation IPS Petr Salač CCNP Security, CCNP, CICSP, CCSI #33835 [email protected] Our Customers Biggest Security Challenges Maintaining security posture
Guest Speaker. Michael Sutton Chief Information Security Officer Zscaler, Inc.
 Guest Speaker Michael Sutton Chief Information Security Officer Zscaler, Inc. Michael Sutton has dedicated his career to conducting leadingedge security research, building world-class security teams and
Guest Speaker Michael Sutton Chief Information Security Officer Zscaler, Inc. Michael Sutton has dedicated his career to conducting leadingedge security research, building world-class security teams and
WildFire. Preparing for Modern Network Attacks
 WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
WildFire WildFire automatically protects your networks from new and customized malware across a wide range of applications, including malware hidden within SSL-encrypted traffic. WildFire easily extends
Survey Analysis: Adoption of Cloud ERP, 2013 Through 2023
 G00261104 Survey Analysis: Adoption of Cloud ERP, 2013 Through 2023 Published: 24 January 2014 Analyst(s): Nigel Rayner This Gartner Research Circle survey conducted in September 2013 shows that some organizations
G00261104 Survey Analysis: Adoption of Cloud ERP, 2013 Through 2023 Published: 24 January 2014 Analyst(s): Nigel Rayner This Gartner Research Circle survey conducted in September 2013 shows that some organizations
NGFWs will be most effective when working in conjunction with other layers of security controls.
 Research Publication Date: 12 October 2009 ID Number: G00171540 Defining the Next-Generation Firewall John Pescatore, Greg Young Firewalls need to evolve to be more proactive in blocking new threats, such
Research Publication Date: 12 October 2009 ID Number: G00171540 Defining the Next-Generation Firewall John Pescatore, Greg Young Firewalls need to evolve to be more proactive in blocking new threats, such
How To Sell Security Products To A Network Security Company
 Market Segment Definitions Author Joshua Mittler Overview In addition to product testing, NSS Labs quantitatively evaluates market size for each of the product categories tested. NSS provides metrics that
Market Segment Definitions Author Joshua Mittler Overview In addition to product testing, NSS Labs quantitatively evaluates market size for each of the product categories tested. NSS provides metrics that
Sourcefire Solutions Overview Security for the Real World. SEE everything in your environment. LEARN by applying security intelligence to data
 SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
How To Protect Your Network From Intrusions From A Malicious Computer (Malware) With A Microsoft Network Security Platform)
 McAfee Security: Intrusion Prevention System REV: 0.1.1 (July 2011) 1 Contents 1. McAfee Network Security Platform...3 2. McAfee Host Intrusion Prevention for Server...4 2.1 Network IPS...4 2.2 Workload
McAfee Security: Intrusion Prevention System REV: 0.1.1 (July 2011) 1 Contents 1. McAfee Network Security Platform...3 2. McAfee Host Intrusion Prevention for Server...4 2.1 Network IPS...4 2.2 Workload
What's a Digital Marketing Platform? What Isn't?
 G00252512 What's a Digital Marketing Platform? What Isn't? Published: 26 June 2013 Analyst(s): Jake Sorofman, Andrew Frank, Bill Gassman, Adam Sarner, Mike McGuire The rise of digital marketing has amplified
G00252512 What's a Digital Marketing Platform? What Isn't? Published: 26 June 2013 Analyst(s): Jake Sorofman, Andrew Frank, Bill Gassman, Adam Sarner, Mike McGuire The rise of digital marketing has amplified
FROM PRODUCT TO PLATFORM
 FROM PRODUCT TO PLATFORM DATA EQUIPMENT 2016 Mikkel Bossen Agenda Today s Challenges Data Growth, SSL encryption, Application Growth & SaaS What s hiding in under the surface? Legacy Security is that really
FROM PRODUCT TO PLATFORM DATA EQUIPMENT 2016 Mikkel Bossen Agenda Today s Challenges Data Growth, SSL encryption, Application Growth & SaaS What s hiding in under the surface? Legacy Security is that really
Cloud IaaS: Security Considerations
 G00210095 Cloud IaaS: Security Considerations Published: 7 March 2011 Analyst(s): Lydia Leong, Neil MacDonald Ensuring adherence to your organization's security and compliance requirements is one of the
G00210095 Cloud IaaS: Security Considerations Published: 7 March 2011 Analyst(s): Lydia Leong, Neil MacDonald Ensuring adherence to your organization's security and compliance requirements is one of the
Cisco ASA and Cloud Web Security: Best-in-Class Network Security Combined with Best-in-Class Web Security
 White Paper Cisco ASA and Cloud Web Security: Best-in-Class Network Security Combined with Best-in-Class Web Security Introduction Organizations that want to harness the power of the web must deal with
White Paper Cisco ASA and Cloud Web Security: Best-in-Class Network Security Combined with Best-in-Class Web Security Introduction Organizations that want to harness the power of the web must deal with
Organizations Must Employ Effective Data Security Strategies
 Research Publication Date: 30 August 2005 ID Number: G00123639 Organizations Must Employ Effective Data Security Strategies Rich Mogull Organizations can best protect data through a hierarchical data security
Research Publication Date: 30 August 2005 ID Number: G00123639 Organizations Must Employ Effective Data Security Strategies Rich Mogull Organizations can best protect data through a hierarchical data security
REVOLUTIONIZING ADVANCED THREAT PROTECTION
 REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
Selecting a Mobile App Development Vendor
 G00246304 Selecting a Mobile App Development Vendor Published: 27 December 2012 Analyst(s): Ken Parmelee Ensuring that mobile app development vendors meet requirements and are viable requires an understanding
G00246304 Selecting a Mobile App Development Vendor Published: 27 December 2012 Analyst(s): Ken Parmelee Ensuring that mobile app development vendors meet requirements and are viable requires an understanding
Braindumps.700-295.50.QA
 Braindumps.700-295.50.QA Number: 700-295 Passing Score: 800 Time Limit: 120 min File Version: 6.0 http://www.gratisexam.com/ Comprehensive, easy and to the point study material made it possible for me
Braindumps.700-295.50.QA Number: 700-295 Passing Score: 800 Time Limit: 120 min File Version: 6.0 http://www.gratisexam.com/ Comprehensive, easy and to the point study material made it possible for me
Unified Security, ATP and more
 SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
Cisco Security Intelligence Operations
 Operations Operations of 1 Operations Operations of Today s organizations require security solutions that accurately detect threats, provide holistic protection, and continually adapt to a rapidly evolving,
Operations Operations of 1 Operations Operations of Today s organizations require security solutions that accurately detect threats, provide holistic protection, and continually adapt to a rapidly evolving,
Agenda Overview for Social Marketing, 2015
 G00270737 Agenda Overview for Social Marketing, 2015 Published: 19 December 2014 Analyst(s): Julie Hopkins Social marketing programs are maturing; executives increasingly expect ROI to follow social marketing
G00270737 Agenda Overview for Social Marketing, 2015 Published: 19 December 2014 Analyst(s): Julie Hopkins Social marketing programs are maturing; executives increasingly expect ROI to follow social marketing
Agenda Overview for Digital Commerce, 2015
 G00270685 Agenda Overview for Digital Commerce, 2015 Published: 18 December 2014 Analyst(s): Jennifer Polk Marketing is making a greater impact on, and taking more responsibility for, digital commerce.
G00270685 Agenda Overview for Digital Commerce, 2015 Published: 18 December 2014 Analyst(s): Jennifer Polk Marketing is making a greater impact on, and taking more responsibility for, digital commerce.
Rethinking IT and IT Security Strategies in an Era of Advanced Attacks, Cloud and Consumerization
 Rethinking IT and IT Security Strategies in an Era of Advanced Attacks, Cloud and Consumerization Neil MacDonald VP and Gartner Fellow Gartner Information Security, Privacy and Risk Research Twitter @nmacdona
Rethinking IT and IT Security Strategies in an Era of Advanced Attacks, Cloud and Consumerization Neil MacDonald VP and Gartner Fellow Gartner Information Security, Privacy and Risk Research Twitter @nmacdona
SOLUTION BRIEF. Next Generation APT Defense for Healthcare
 SOLUTION BRIEF Next Generation APT Defense for Healthcare Overview Next Generation APT Defense for Healthcare Healthcare records with patients personally identifiable information (PII) combined with their
SOLUTION BRIEF Next Generation APT Defense for Healthcare Overview Next Generation APT Defense for Healthcare Healthcare records with patients personally identifiable information (PII) combined with their
Blind as a Bat? Supporting Packet Decryption for Security Scanning
 Sponsored by VSS Monitoring Blind as a Bat? Supporting Packet Decryption for Security Scanning November 2012 A SANS Whitepaper Written by: Dave Shackleford Options for SSL Inspection Page 2 Implementing
Sponsored by VSS Monitoring Blind as a Bat? Supporting Packet Decryption for Security Scanning November 2012 A SANS Whitepaper Written by: Dave Shackleford Options for SSL Inspection Page 2 Implementing
Guideline on Firewall
 CMSGu2014-02 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Firewall National Computer Board Mauritius Version 1.0 June
CMSGu2014-02 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Firewall National Computer Board Mauritius Version 1.0 June
McAfee Network Security Platform
 McAfee Network Security Platform Next Generation Network Security Youssef AGHARMINE, Network Security, McAfee Network is THE Security Battleground Who is behind the data breaches? 81% some form of hacking
McAfee Network Security Platform Next Generation Network Security Youssef AGHARMINE, Network Security, McAfee Network is THE Security Battleground Who is behind the data breaches? 81% some form of hacking
Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses
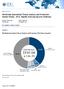 Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE
Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE
Fighting Advanced Threats
 Fighting Advanced Threats With FortiOS 5 Introduction In recent years, cybercriminals have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
Fighting Advanced Threats With FortiOS 5 Introduction In recent years, cybercriminals have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
Protection Against Advanced Persistent Threats
 Protection Against Advanced Persistent Threats Peter Mesjar Systems Engineer, CCIE 17428 October 2014 Agenda Modern Threats Advanced Malware Protection Solution Why Cisco? Cisco Public 2 The Problem are
Protection Against Advanced Persistent Threats Peter Mesjar Systems Engineer, CCIE 17428 October 2014 Agenda Modern Threats Advanced Malware Protection Solution Why Cisco? Cisco Public 2 The Problem are
Comprehensive real-time protection against Advanced Threats and data theft
 TRITON AP-WEB Comprehensive real-time protection against Advanced Threats and data theft Your business and its data are under constant attack. Traditional security solutions no longer provide sufficient
TRITON AP-WEB Comprehensive real-time protection against Advanced Threats and data theft Your business and its data are under constant attack. Traditional security solutions no longer provide sufficient
A New Approach to Assessing Advanced Threat Solutions
 A New Approach to Assessing Advanced Threat Solutions December 4, 2014 A New Approach to Assessing Advanced Threat Solutions How Well Does Your Advanced Threat Solution Work? The cyber threats facing enterprises
A New Approach to Assessing Advanced Threat Solutions December 4, 2014 A New Approach to Assessing Advanced Threat Solutions How Well Does Your Advanced Threat Solution Work? The cyber threats facing enterprises
Cloud Security Primer MALICIOUS NETWORK COMMUNICATIONS: WHAT ARE YOU OVERLOOKING?
 A Cloud Security Primer : WHAT ARE YOU OVERLOOKING? LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed
A Cloud Security Primer : WHAT ARE YOU OVERLOOKING? LEGAL DISCLAIMER The information provided herein is for general information and educational purposes only. It is not intended and should not be construed
The Cisco ASA 5500 as a Superior Firewall Solution
 The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
Five Steps For Securing The Data Center: Why Traditional Security May Not Work
 White Paper Five Steps For Securing The Data Center: Why Traditional Security May Not Work What You Will Learn Data center administrators face a significant challenge: They need to secure the data center
White Paper Five Steps For Securing The Data Center: Why Traditional Security May Not Work What You Will Learn Data center administrators face a significant challenge: They need to secure the data center
High Performance NGFW Extended
 High Performance NGFW Extended Enrique Millán Country Manager Colombia [email protected] 1 Copyright 2013 Fortinet Inc. All rights reserved. D I S C L A I M E R This document contains confidential material
High Performance NGFW Extended Enrique Millán Country Manager Colombia [email protected] 1 Copyright 2013 Fortinet Inc. All rights reserved. D I S C L A I M E R This document contains confidential material
The Hillstone and Trend Micro Joint Solution
 The Hillstone and Trend Micro Joint Solution Advanced Threat Defense Platform Overview Hillstone and Trend Micro offer a joint solution the Advanced Threat Defense Platform by integrating the industry
The Hillstone and Trend Micro Joint Solution Advanced Threat Defense Platform Overview Hillstone and Trend Micro offer a joint solution the Advanced Threat Defense Platform by integrating the industry
WEBSENSE TRITON SOLUTIONS
 WEBSENSE TRITON SOLUTIONS INNOVATIVE SECURITY FOR WEB, EMAIL, DATA AND MOBILE TRITON STOPS MORE THREATS. WE CAN PROVE IT. PROTECTION AS ADVANCED AND DYNAMIC AS THE THREATS THEMSELVES The security threats
WEBSENSE TRITON SOLUTIONS INNOVATIVE SECURITY FOR WEB, EMAIL, DATA AND MOBILE TRITON STOPS MORE THREATS. WE CAN PROVE IT. PROTECTION AS ADVANCED AND DYNAMIC AS THE THREATS THEMSELVES The security threats
Cisco Cloud Web Security
 Data Sheet Today s highly connected and fast-moving world is filled with complex and sophisticated web security threats. Cisco delivers the strong protection, complete control, and investment value that
Data Sheet Today s highly connected and fast-moving world is filled with complex and sophisticated web security threats. Cisco delivers the strong protection, complete control, and investment value that
SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION
 SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION How ThreatBLADES add real-time threat scanning and alerting to the Analytics Platform INTRODUCTION: analytics solutions have become an essential weapon
SECURITY ANALYTICS MOVES TO REAL-TIME PROTECTION How ThreatBLADES add real-time threat scanning and alerting to the Analytics Platform INTRODUCTION: analytics solutions have become an essential weapon
Agenda Overview for Customer Experience, 2015
 G00270544 Agenda Overview for Customer Experience, 2015 Published: 22 December 2014 Analyst(s): Jake Sorofman Customer experience has emerged as a top priority for marketers. This overview summarizes how
G00270544 Agenda Overview for Customer Experience, 2015 Published: 22 December 2014 Analyst(s): Jake Sorofman Customer experience has emerged as a top priority for marketers. This overview summarizes how
Check Point Positions
 Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
By John Pirc. THREAT DETECTION HAS moved beyond signature-based firewalls EDITOR S DESK SECURITY 7 AWARD WINNERS ENHANCED THREAT DETECTION
 THE NEXT (FRONT) TIER IN SECURITY When conventional security falls short, breach detection systems and other tier 2 technologies can bolster your network s defenses. By John Pirc THREAT HAS moved beyond
THE NEXT (FRONT) TIER IN SECURITY When conventional security falls short, breach detection systems and other tier 2 technologies can bolster your network s defenses. By John Pirc THREAT HAS moved beyond
White Paper. Advantage FireEye. Debunking the Myth of Sandbox Security
 White Paper Advantage FireEye Debunking the Myth of Sandbox Security White Paper Contents The Myth of Sandbox Security 3 Commercial sandbox evasion 3 Lack of multi-flow analysis and exploit detection 3
White Paper Advantage FireEye Debunking the Myth of Sandbox Security White Paper Contents The Myth of Sandbox Security 3 Commercial sandbox evasion 3 Lack of multi-flow analysis and exploit detection 3
Comprehensive Advanced Threat Defense
 1 Comprehensive Advanced Threat Defense June 2014 PAGE 1 PAGE 1 1 INTRODUCTION The hot topic in the information security industry these days is Advanced Threat Defense (ATD). There are many definitions,
1 Comprehensive Advanced Threat Defense June 2014 PAGE 1 PAGE 1 1 INTRODUCTION The hot topic in the information security industry these days is Advanced Threat Defense (ATD). There are many definitions,
How To Protect Your Network From Attack From A Virus And Attack From Your Network (D-Link)
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering
Next Generation Enterprise Network Security Platform
 Next Generation Enterprise Network Security Platform November 2014 Lyndon Clough - Territory Sales Manager Derran Guinan Systems Engineer Agenda The Palo Alto Networks story Today s Threat Landscape The
Next Generation Enterprise Network Security Platform November 2014 Lyndon Clough - Territory Sales Manager Derran Guinan Systems Engineer Agenda The Palo Alto Networks story Today s Threat Landscape The
Analyzing HTTP/HTTPS Traffic Logs
 Advanced Threat Protection Automatic Traffic Log Analysis APTs, advanced malware and zero-day attacks are designed to evade conventional perimeter security defenses. Today, there is wide agreement that
Advanced Threat Protection Automatic Traffic Log Analysis APTs, advanced malware and zero-day attacks are designed to evade conventional perimeter security defenses. Today, there is wide agreement that
Symantec Advanced Threat Protection: Network
 Symantec Advanced Threat Protection: Network DR150218C April 2015 Miercom www.miercom.com Contents 1.0 Executive Summary... 3 2.0 Overview... 4 2.1 Products Tested... 4 2.2. Malware Samples... 5 3.0 How
Symantec Advanced Threat Protection: Network DR150218C April 2015 Miercom www.miercom.com Contents 1.0 Executive Summary... 3 2.0 Overview... 4 2.1 Products Tested... 4 2.2. Malware Samples... 5 3.0 How
Palo Alto Networks. October 6
 Palo Alto Networks October 6 Agenda Malware Trends by the numbers Protect Locally Share Globally Delivery methods 21.5% ~14% OF MALWARE HAS BEEN DELIVERED OVER APPS OTHER THAN WEB AND EMAIL IN 2015 8.2%
Palo Alto Networks October 6 Agenda Malware Trends by the numbers Protect Locally Share Globally Delivery methods 21.5% ~14% OF MALWARE HAS BEEN DELIVERED OVER APPS OTHER THAN WEB AND EMAIL IN 2015 8.2%
Secure Web Gateways Buyer s Guide >
 White Paper Secure Web Gateways Buyer s Guide > (Abbreviated Version) The web is the number one source for malware distribution. With more than 2 million 1 new pages added every day and 10,000 new malicious
White Paper Secure Web Gateways Buyer s Guide > (Abbreviated Version) The web is the number one source for malware distribution. With more than 2 million 1 new pages added every day and 10,000 new malicious
Stop advanced targeted attacks, identify high risk users and control Insider Threats
 TRITON AP-EMAIL Stop advanced targeted attacks, identify high risk users and control Insider Threats From socially engineered lures to targeted phishing, most large cyberattacks begin with email. As these
TRITON AP-EMAIL Stop advanced targeted attacks, identify high risk users and control Insider Threats From socially engineered lures to targeted phishing, most large cyberattacks begin with email. As these
Magic Quadrant for Secure Web Gateways
 G00262738 Magic Quadrant for Secure Web Gateways Published: 23 June 2014 Analyst(s): Lawrence Orans, Peter Firstbrook The SWG market is evolving rapidly as vendors respond to the mobility trend and the
G00262738 Magic Quadrant for Secure Web Gateways Published: 23 June 2014 Analyst(s): Lawrence Orans, Peter Firstbrook The SWG market is evolving rapidly as vendors respond to the mobility trend and the
TRITON AP-WEB COMPREHENSIVE REAL-TIME PROTECTION AGAINST ADVANCED THREATS & DATA THEFT
 TRITON AP-WEB COMPREHENSIVE REAL-TIME PROTECTION AGAINST ADVANCED THREATS & DATA THEFT TRITON AP-WEB COMPREHENSIVE REAL-TIME PROTECTION AGAINST ADVANCED THREATS AND DATA THEFT Your business and its data
TRITON AP-WEB COMPREHENSIVE REAL-TIME PROTECTION AGAINST ADVANCED THREATS & DATA THEFT TRITON AP-WEB COMPREHENSIVE REAL-TIME PROTECTION AGAINST ADVANCED THREATS AND DATA THEFT Your business and its data
Data in the Cloud: The Changing Nature of Managing Data Delivery
 Research Publication Date: 1 March 2011 ID Number: G00210129 Data in the Cloud: The Changing Nature of Managing Data Delivery Eric Thoo Extendible data integration strategies and capabilities will play
Research Publication Date: 1 March 2011 ID Number: G00210129 Data in the Cloud: The Changing Nature of Managing Data Delivery Eric Thoo Extendible data integration strategies and capabilities will play
DMZ Virtualization Using VMware vsphere 4 and the Cisco Nexus 1000V Virtual Switch
 DMZ Virtualization Using VMware vsphere 4 and the Cisco Nexus 1000V Virtual Switch What You Will Learn A demilitarized zone (DMZ) is a separate network located in the neutral zone between a private (inside)
DMZ Virtualization Using VMware vsphere 4 and the Cisco Nexus 1000V Virtual Switch What You Will Learn A demilitarized zone (DMZ) is a separate network located in the neutral zone between a private (inside)
Achieve Deeper Network Security
 Achieve Deeper Network Security Dell Next-Generation Firewalls Abstract Next-generation firewalls (NGFWs) have taken the world by storm, revolutionizing network security as we once knew it. Yet in order
Achieve Deeper Network Security Dell Next-Generation Firewalls Abstract Next-generation firewalls (NGFWs) have taken the world by storm, revolutionizing network security as we once knew it. Yet in order
Securing BYOD With Network Access Control, a Case Study
 Securing BYOD With Network Access Control, a Case Study 29 August 2012 ID:G00226207 Analyst(s): Lawrence Orans VIEW SUMMARY This Case Study highlights how an organization utilized NAC and mobile device
Securing BYOD With Network Access Control, a Case Study 29 August 2012 ID:G00226207 Analyst(s): Lawrence Orans VIEW SUMMARY This Case Study highlights how an organization utilized NAC and mobile device
Achieve Deeper Network Security and Application Control
 Achieve Deeper Network Security and Application Control Dell Next-Generation Firewalls Abstract Next-generation firewalls (NGFWs) have emerged to revolutionize network security as we once knew it. Yet
Achieve Deeper Network Security and Application Control Dell Next-Generation Firewalls Abstract Next-generation firewalls (NGFWs) have emerged to revolutionize network security as we once knew it. Yet
Next-Generation Firewalls: Critical to SMB Network Security
 Next-Generation Firewalls: Critical to SMB Network Security Next-Generation Firewalls provide dramatic improvements in protection versus traditional firewalls, particularly in dealing with today s more
Next-Generation Firewalls: Critical to SMB Network Security Next-Generation Firewalls provide dramatic improvements in protection versus traditional firewalls, particularly in dealing with today s more
Agenda Overview for Emerging Marketing Technology and Trends, 2015
 G00270688 Agenda Overview for Emerging Marketing Technology and Trends, 2015 Published: 18 December 2014 Analyst(s): Andrew Frank The best digital marketers exploit emerging trends and technologies to
G00270688 Agenda Overview for Emerging Marketing Technology and Trends, 2015 Published: 18 December 2014 Analyst(s): Andrew Frank The best digital marketers exploit emerging trends and technologies to
Solution Path: Threats and Vulnerabilities
 Solution Path: Threats and Vulnerabilities Published: 24 January 2012 Burton IT1 Research G00226331 Analyst(s): Dan Blum This solution path helps Gartner clients develop a strategy and program for managing
Solution Path: Threats and Vulnerabilities Published: 24 January 2012 Burton IT1 Research G00226331 Analyst(s): Dan Blum This solution path helps Gartner clients develop a strategy and program for managing
Seven Requirements for Hybrid Web Delivery Getting the best of both on-premises and SaaS
 Seven Requirements for Hybrid Web Delivery Getting the best of both on-premises and SaaS Traditionally, IT risk management has balanced security investment and the impact of the threat, allowing each business
Seven Requirements for Hybrid Web Delivery Getting the best of both on-premises and SaaS Traditionally, IT risk management has balanced security investment and the impact of the threat, allowing each business
Cloud, SDN and the Evolution of
 Cloud, SDN and the Evolution of Enterprise Networks Neil Rickard Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form
Cloud, SDN and the Evolution of Enterprise Networks Neil Rickard Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form
How Lastline Has Better Breach Detection Capabilities. By David Strom December 2014 [email protected]
 How Lastline Has Better Breach Detection Capabilities By David Strom December 2014 [email protected] The Internet is a nasty place, and getting nastier. Current breach detection products using traditional
How Lastline Has Better Breach Detection Capabilities By David Strom December 2014 [email protected] The Internet is a nasty place, and getting nastier. Current breach detection products using traditional
NetDefend Firewall UTM Services
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering (WCF) for superior
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering (WCF) for superior
The Need for Intelligent Network Security: Adapting IPS for today s Threats
 The Need for Intelligent Network Security: Adapting IPS for today s Threats James Tucker Security Engineer Sourcefire Nordics A Bit of History It started with passive IDS. Burglar alarm for the network
The Need for Intelligent Network Security: Adapting IPS for today s Threats James Tucker Security Engineer Sourcefire Nordics A Bit of History It started with passive IDS. Burglar alarm for the network
HOW TO PROTECT YOUR VIRTUAL DESKTOPS AND SERVERS? Security for Virtual and Cloud Environments
 HOW TO PROTECT YOUR VIRTUAL DESKTOPS AND SERVERS? Security for Virtual and Cloud Environments OVERVIEW This document explains the functionality of Security for Virtual and Cloud Environments (SVCE) - what
HOW TO PROTECT YOUR VIRTUAL DESKTOPS AND SERVERS? Security for Virtual and Cloud Environments OVERVIEW This document explains the functionality of Security for Virtual and Cloud Environments (SVCE) - what
Securing Virtual Applications and Servers
 White Paper Securing Virtual Applications and Servers Overview Security concerns are the most often cited obstacle to application virtualization and adoption of cloud-computing models. Merely replicating
White Paper Securing Virtual Applications and Servers Overview Security concerns are the most often cited obstacle to application virtualization and adoption of cloud-computing models. Merely replicating
Emerging PC Life Cycle Configuration Management Vendors
 Research Publication Date: 20 January 2011 ID Number: G00209766 Emerging PC Life Cycle Configuration Management Vendors Terrence Cosgrove Although the PC configuration life cycle management (PCCLM) market
Research Publication Date: 20 January 2011 ID Number: G00209766 Emerging PC Life Cycle Configuration Management Vendors Terrence Cosgrove Although the PC configuration life cycle management (PCCLM) market
Agenda Overview for Multichannel Marketing, 2015
 G00271717 Agenda Overview for Multichannel Marketing, 2015 Published: 19 December 2014 Analyst(s): Adam Sarner, Jennifer S. Beck Multichannel marketing is where content and context meet and where brand
G00271717 Agenda Overview for Multichannel Marketing, 2015 Published: 19 December 2014 Analyst(s): Adam Sarner, Jennifer S. Beck Multichannel marketing is where content and context meet and where brand
NAC Strategies for Supporting BYOD Environments
 G00226204 NAC Strategies for Supporting BYOD Environments Published: 22 December 2011 Analyst(s): Lawrence Orans, John Pescatore Network access control (NAC) will be a key element in a flexible approach
G00226204 NAC Strategies for Supporting BYOD Environments Published: 22 December 2011 Analyst(s): Lawrence Orans, John Pescatore Network access control (NAC) will be a key element in a flexible approach
Symantec Protection Suite Add-On for Hosted Email and Web Security
 Symantec Protection Suite Add-On for Hosted Email and Web Security Overview Your employees are exchanging information over email and the Web nearly every minute of every business day. These essential communication
Symantec Protection Suite Add-On for Hosted Email and Web Security Overview Your employees are exchanging information over email and the Web nearly every minute of every business day. These essential communication
Agenda Overview for Marketing Management, 2015
 G00270720 Agenda Overview for Marketing Management, 2015 Published: 18 December 2014 Analyst(s): Richard Fouts Increased participation in strategic business decisions and an evolving organization put new
G00270720 Agenda Overview for Marketing Management, 2015 Published: 18 December 2014 Analyst(s): Richard Fouts Increased participation in strategic business decisions and an evolving organization put new
Advantages of Managed Security Services
 Advantages of Managed Security Services Cloud services via MPLS networks for high security at low cost Get Started Now: 877.611.6342 to learn more. www.megapath.com Executive Summary Protecting Your Network
Advantages of Managed Security Services Cloud services via MPLS networks for high security at low cost Get Started Now: 877.611.6342 to learn more. www.megapath.com Executive Summary Protecting Your Network
OVERVIEW. Enterprise Security Solutions
 Enterprise Security Solutions OVERVIEW For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an everevolving IT threat landscape. It s how we got to be the world s
Enterprise Security Solutions OVERVIEW For more than 25 years, Trend Micro has innovated constantly to keep our customers ahead of an everevolving IT threat landscape. It s how we got to be the world s
KSÖ-SICHERHEITSKONGRESS 2015
 KSÖ-SICHERHEITSKONGRESS 2015 Wachstum durch digitale Standortsicherung. Chancen und Herausforderungen auf dem Weg zu einem cyber-sicheren Österreich. Adapting IT Security to Digital Business Jeremy D'Hoinne
KSÖ-SICHERHEITSKONGRESS 2015 Wachstum durch digitale Standortsicherung. Chancen und Herausforderungen auf dem Weg zu einem cyber-sicheren Österreich. Adapting IT Security to Digital Business Jeremy D'Hoinne
The Advanced Attack Challenge. Creating a Government Private Threat Intelligence Cloud
 The Advanced Attack Challenge Creating a Government Private Threat Intelligence Cloud The Advanced Attack Challenge One of the most prominent and advanced threats to government networks is advanced delivery
The Advanced Attack Challenge Creating a Government Private Threat Intelligence Cloud The Advanced Attack Challenge One of the most prominent and advanced threats to government networks is advanced delivery
Lab Testing Summary Report
 Lab Testing Summary Report February 14 Report 132B Product Category: Web Security Gateway Vendor Tested: Key findings and conclusions: security appliance exhibits best rate to date, 91.3%, for classifying
Lab Testing Summary Report February 14 Report 132B Product Category: Web Security Gateway Vendor Tested: Key findings and conclusions: security appliance exhibits best rate to date, 91.3%, for classifying
Content Security: Protect Your Network with Five Must-Haves
 White Paper Content Security: Protect Your Network with Five Must-Haves What You Will Learn The continually evolving threat landscape is what makes the discovery of threats more relevant than defense as
White Paper Content Security: Protect Your Network with Five Must-Haves What You Will Learn The continually evolving threat landscape is what makes the discovery of threats more relevant than defense as
Top 10 Technology Trends, 2013: Cloud Computing and Hybrid IT Drive Future IT Models
 G00237716 Top 10 Technology Trends, 2013: Cloud Computing and Hybrid IT Drive Future IT Models Published: 6 February 2013 Analyst(s): David W. Cearley, Donna Scott, Joe Skorupa, Thomas J. Bittman Cloud
G00237716 Top 10 Technology Trends, 2013: Cloud Computing and Hybrid IT Drive Future IT Models Published: 6 February 2013 Analyst(s): David W. Cearley, Donna Scott, Joe Skorupa, Thomas J. Bittman Cloud
Magic Quadrant for Secure Web Gateways
 Magic Quadrant for Secure Web Gateways 28 May 2015 ID:G00267241 Analyst(s): Lawrence Orans, Peter Firstbrook VIEW SUMMARY The market for SWG solutions is still dominated by traditional on premises appliances.
Magic Quadrant for Secure Web Gateways 28 May 2015 ID:G00267241 Analyst(s): Lawrence Orans, Peter Firstbrook VIEW SUMMARY The market for SWG solutions is still dominated by traditional on premises appliances.
CIO Update: The Gartner Firewall Magic Quadrant for 2H02
 IGG-09252002-03 R. Stiennon Article 25 September 2002 CIO Update: The Gartner Firewall Magic Quadrant for 2H02 In presenting its latest Firewall Magic Quadrant, Gartner discusses how the firewall market
IGG-09252002-03 R. Stiennon Article 25 September 2002 CIO Update: The Gartner Firewall Magic Quadrant for 2H02 In presenting its latest Firewall Magic Quadrant, Gartner discusses how the firewall market
Securing and Optimizing the Next Generation Branch Office
 Securing and Optimizing the Next Generation Branch Office 1 Global Organizations Current state of affairs 3 Globally distributed enterprises rely on the WAN for day to day operations to stay competitive
Securing and Optimizing the Next Generation Branch Office 1 Global Organizations Current state of affairs 3 Globally distributed enterprises rely on the WAN for day to day operations to stay competitive
Content-ID. Content-ID enables customers to apply policies to inspect and control content traversing the network.
 Content-ID Content-ID enables customers to apply policies to inspect and control content traversing the network. Malware & Vulnerability Research 0-day Malware and Exploits from WildFire Industry Collaboration
Content-ID Content-ID enables customers to apply policies to inspect and control content traversing the network. Malware & Vulnerability Research 0-day Malware and Exploits from WildFire Industry Collaboration
