DATE: November 20, 2013 FILE: FTC Workshop: The Internet of Things -- Privacy and Security in a Connected World
|
|
|
- Cory McDaniel
- 8 years ago
- Views:
Transcription
1 MORRISON & FOERSTER LLP MEMORANDUM TO: FROM: ESPC D. Reed Freeman Jr. Libby Greismann DATE: November 20, 2013 FILE: RE: FTC Workshop: The Internet of Things -- Privacy and Security in a Connected World We write to provide you with a summary of the Federal Trade Commission ( FTC or Commission ) workshop entitled Internet of Things: Privacy and Security in a Connected World held November 19, The internet of things refers to a world in which machines can communicate with each other via the internet without human intervention. The FTC indicated in May 2013 that it would hold this workshop to explore the privacy implications of this rapidly emerging business model and how these implications weigh against possible societal benefits of the technology. The workshop consisted of a presentation on the technological landscape of the internet of things, remarks on contextual privacy, a keynote address from Vint Cerf, Vice President and Chief Internet Evangelist at Google, and four panel discussions. FTC staff moderated the panel discussions. Panel members consisted of industry representatives, private advocacy groups, and academics. EXECUTIVE SUMMARY In her introductory remarks, Chairwoman Ramirez: Identified three main challenges to consumer privacy presented by internetconnected devices: o Ability to collect vastly greater amounts of data that, when patched together, may present a full profile of our health, preferences, and identity; o Unexpected uses of data; and o Data at great risk, as devices connected to the internet are subject to hacking. In remarks prefacing the afternoon sessions, Commissioner Ohlhausen (a Republican):
2 Emphasized balancing efficiencies and benefits with protecting consumer privacy; and Stated that the FTC s approach will be to conduct policy R&D, educate consumers, and challenge any harms that do arise with traditional enforcement approaches. In closing remarks, director of the FTC s Bureau of Consumer Protection Jessica Rich: Noted that the next step for the FTC will be to issue a report about best practices; and Invited public comments through January 14 th, These were the only substantive pronouncements by the FTC at the workshop. However, questions asked by FTC staff moderators suggested they think the internet of things presents unique privacy and security threats that must be balanced against possible great societal benefits, and that traditional notice and consent frameworks will not be sufficient to inform consumers of how their personal data is being used. No questions were answered by FTC staff. In all four discussions, panelists disagreed over: Whether harms outweigh benefits in connecting devices to the internet o Industry representatives suggested that the benefit potential was huge, while privacy advocacy groups tended to weigh the harms more heavily. The degree of sensitivity of data that would be collected from these devices o Should consumers care about data collected in the aggregate and anonymously? o Should consumers worry about harmless data points such as energy consumption or fitness metrics? However, there was general agreement that: Consumers and vendors do not understand the implications of the datacollecting devices they are using. Internet of things policies should be technology-neutral. Transparency and consumer empowerment is key, as is implementing a privacy by design framework into connected devices. PRESENTATION: WHAT IS THE INTERNET OF THINGS? Keith Marzullo of the National Science Foundation began the workshop with a technical framing of the internet of things. Mr. Marzullo explained the three main categories of internet of things technology: 2
3 item identification based on RFID sensors applied to inert machines or objects embedded intelligence PRESENTATION: TRUST AND CONTEXT IN A CONNECTED WORLD Carolyn Nguyen of Microsoft spoke about the impact of the internet of things on the individual, specifically how it can assist individuals in making optimized and contextappropriate decisions. She emphasized that: For data driven ecosystems to be sustainable, the ecosystem must show that it is capable of earning individuals trust. This trust is gained by using data only for context-specific purposes where consumers gain the most value PANEL 1: THE SMART HOME This panel examined both the benefits of the increased connectivity of products and services for the home as well as the various associated privacy and security concerns. The panel also focused on what products are available, including smart meters for energy usage, smart appliances, and connected monitoring devices. Panelists were divided over the weight of the benefits conferred by the smart home Mike Beyerle of GE and Jeff Hagins of SmartThings believe that the smart home can provide significant convenience and value to the consumer. Lee Tien of the Electronic Frontier Foundation and Craig Heffner of Tactical Network Solutions were more skeptical, and were concerned about the vast amounts of data being collected about individuals personal lives. o Mr. Tien voiced concern over the fact that consumers are either unaware of real privacy issues, or have tendency to underestimate what can be done with this humdrum data. While panelists agreed that privacy and security risks are present, they pointed to different sources of these risks Craig Heffner pointed to the lack of financial incentives to make devices secure, and the fact that companies are cutting costs and hiring lower quality engineers Jeff Hagins noted that companies don t have all the skill sets they need to address security from top to bottom. PRESENTATION: KEYNOTE SPEAKER VINT CERF 3
4 Vint Cerf of Google gave a general overview of the internet of things environment, including the global implications, challenges and opportunities presented by this evolution. Mr. Cerf noted that: There is huge potential for global optimization of resource management, as well as potential health management, wellness, and educational improvements. Industry must continue to innovate on a global scale, while respecting privacy. PANEL 2: CONNECTED HEALTH AND FITNESS This panel examined both the benefits of the connected health and fitness devices and apps, as well as the various associated privacy and security concerns. The panel also focused on what products are available today or will soon be available, including glucose pumps for diabetics, FitBits (fitness monitoring wearable devices), and connected pillboxes. Panelists agreed that the data collected by these devices and apps is rich and highly personal Scott Peppet of the University of Colorado School of Law explained that the data coming off sensors is extremely high quality and can create a rich picture of the individual s personal lifestyle. Stan Crosley of Indiana University agreed, and emphasized that far more information about health is generated outside the walls of traditional healthcare today than within them. Panelists also agreed that traditional user notice and consent methods are highly unlikely to be effective Joseph Lorenzo Hall of the Center for Democracy and Technology stated that there is no practical way to have a consumer consent every time a device records something, as the device would simply not be practically useful. Jay Radcliffe of InGuardians, Inc suggested the industry come up with a new way to obtain consent, as nobody actually reads written privacy policies or manuals Scott Peppet stated that privacy policies leave important things out. Each panelist also provided his top security concern that doctors and consumers should be aware of as they decide whether to use these devices Panelists were concerned about lack of encryption, lack of consumer understanding of importance of security, and potentially unreliable data. PANEL 3: CONNECTED CARS This panel examined the emergence of smart cars and various integrated consumer-facing technologies, and the associated privacy and security concerns. Panelists focused on 4
5 concerns related to data collection and existing vulnerabilities in the systems, including OnStar, remote access devices, and Event Data Recorders ( black boxes ). Panelists first discussed the benefits from connected cars Christopher Wolf, of the Future of Privacy Forum, named a host of benefits including: o Car can call first responders if driver is in accident, car can alert driver to hazardous road conditions or malfunctions, parents can track children s driving habits, etc. Panelists focused on differences between automobile industry and other connected industries Mr. Wolf explained that consumers are eager to see certain capabilities brought inside automobiles such as maps and personalized settings. Yoshi Kohno, of the University of Washington, noted that in the auto industry, unlike other industries, manufacturers are very aware and focused on security and privacy issues related to these technologies. Wayne Powell, of the Toyota Technical Center, emphasized that the fact that the car is physically moving down the road makes it a riskier environment if systems are hacked, as well as a challenge to provide consumers with data in a safe way. Moderator Karen Jagielski, of the FTC s Division of Privacy and Identity Protection, was particularly interested in the unique issues as to long-lasting ownership, and multiple owners, of automobiles. Most panelists were not concerned. Mr. Powell explained that when a car is sold to an individual, all off-board data from previous owner is gone as soon as accounts are closed, and cannot be retrieved. Mr. Nielsen also clarified that data derived for maintenance is collected only in the aggregate, and times out after 40 seconds. PANEL 4: PRIVACY AND SECURITY IN A CONNECTED WORLD In this panel, the moderators presented the panelists with four scenarios and asked them to discuss broader privacy and security issues raised by the internet of things, including best practices for managing privacy and security with new interconnected devices, and the incentives for designing products with privacy and security in mind. Scenario 1: At what point should small businesses begin to think about privacy? Panelists agreed that privacy should be considered as soon as the concept for the business is developed 5
6 o Michelle Chibba, of the Office of the Information and Privacy Commissioner of Ontario, suggested that small startups without IT infrastructure should collaborate and consult with other companies. She also supported data minimization as a way to promote security from the outset. Scenario 2: Do connected devices put consumers on notice that companies will collect private data? Panelists agreed that traditional notice and choice mechanisms are no longer sufficient for data collected from connected devices o Professor Calo emphasized the need to innovate around notice just as we do with other things in the industry He also expressed concern over the bait and switch scenario, where companies do not give consumers full disclosure regarding the monetization of their data o Drew Hickerson of Happtique and Dan Caprio of McKenna Long & Aldridge both saw a need for creation of some kind of standardization so that consumer know a product is trustworthy Suggested a seal of approval Scenario 3: What should vendors do when their connected device is breached? Panelists generally agreed again that security and breach protocol should have been built into the design There was slight disagreement over appropriate actions to take o Ms. Chibba suggested that the company shut down the system immediately o Mr. Rogers countered with the fact that shutting down the system is not often safest for the consumer for example, an internet-connected lock in a door should not be shut down to lock the consumer out or to unlock completely Scenario 4: If you were the FTC, what would you do next? Panelists focused on education and research before regulation or legislation o Mr. Jacobs believed that enforcement was appropriate, and the FTC is off to a good start with the TRENDnet investigation o Mr. Hickerson suggested that we continue to educate consumers and the industry and create partnerships with the industry as well as other agencies to avoid duplicative rulings o Ms. Chibba noted that the privacy by design framework is successful in Canada and could be in the United States as well 6
Senate Subcommittee Hearing and Report Regarding Online Advertising and Hidden Hazards to Consumer Security and Data Privacy
 MORRISON & FOERSTER LLP MEMORANDUM TO: FROM: ESPC Reed Freeman Patrick Bernhardt DATE: May 16, 2014 RE: Senate Subcommittee Hearing and Report Regarding Online Advertising and Hidden Hazards to Consumer
MORRISON & FOERSTER LLP MEMORANDUM TO: FROM: ESPC Reed Freeman Patrick Bernhardt DATE: May 16, 2014 RE: Senate Subcommittee Hearing and Report Regarding Online Advertising and Hidden Hazards to Consumer
Bios. Privacy & Security in a Connected World
 Privacy & Security in a Connected World Bios Michael Beyerle is the Marketing Manager for Innovation at GE Appliances. He has over 25 years of experience in engineering design, product management, and
Privacy & Security in a Connected World Bios Michael Beyerle is the Marketing Manager for Innovation at GE Appliances. He has over 25 years of experience in engineering design, product management, and
Privacy & Security in a Connected World
 Privacy & Security in a Connected World FTC Staff Report JANUARY 2015 FTC Staff Report January 2015 Table of Contents Executive Summary... i Background... 1 What is the Internet of Things?... 5 Benefits
Privacy & Security in a Connected World FTC Staff Report JANUARY 2015 FTC Staff Report January 2015 Table of Contents Executive Summary... i Background... 1 What is the Internet of Things?... 5 Benefits
Congress of the United States
 FRED UPTON, MICHIGAN CHAIRMAN FRANK PALLONE, JR., NEW JERSEY RANKING MEMBER ONE HUNDRED FOURTEENTH CONGRESS Congress of the United States House of Representatives COMMITTEE ON ENERGY AND COMMERCE 2125
FRED UPTON, MICHIGAN CHAIRMAN FRANK PALLONE, JR., NEW JERSEY RANKING MEMBER ONE HUNDRED FOURTEENTH CONGRESS Congress of the United States House of Representatives COMMITTEE ON ENERGY AND COMMERCE 2125
DAY 1 MONDAY, SEPT 28 2015
 MaRS Discovery District TORONTO, ON Sep 28 29, 2015 8:45 AM 9:15 AM 9:15 AM 10:00 AM 10:00 AM 11:00 AM DAY 1 MONDAY, SEPT 28 2015 OPENING KEYNOTE SPEAKER A Connected World with Intelligence 1-YEAR-LATER
MaRS Discovery District TORONTO, ON Sep 28 29, 2015 8:45 AM 9:15 AM 9:15 AM 10:00 AM 10:00 AM 11:00 AM DAY 1 MONDAY, SEPT 28 2015 OPENING KEYNOTE SPEAKER A Connected World with Intelligence 1-YEAR-LATER
BEFORE THE DEPARTMENT OF COMMERCE
 BEFORE THE DEPARTMENT OF COMMERCE NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION Request for Public Comments MULTISTAKEHOLDER PROCESS TO DEVELOP CONSUMER DATA PRIVACY CODES OF CONDUCT DOCKET#
BEFORE THE DEPARTMENT OF COMMERCE NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION Request for Public Comments MULTISTAKEHOLDER PROCESS TO DEVELOP CONSUMER DATA PRIVACY CODES OF CONDUCT DOCKET#
In the pursuit of becoming smart
 WHITE PAPER In the pursuit of becoming smart The business insight into Comarch IoT Platform Introduction Businesses around the world are seeking the direction for the future, trying to find the right solution
WHITE PAPER In the pursuit of becoming smart The business insight into Comarch IoT Platform Introduction Businesses around the world are seeking the direction for the future, trying to find the right solution
Connected Home Technologies. Part 1
 Connected Home Technologies Part 1 2 HSB Connected Home Technologies, Part 1 Since before the invention of the telephone, Hartford Steam Boiler has been monitoring trends in energy and technology that
Connected Home Technologies Part 1 2 HSB Connected Home Technologies, Part 1 Since before the invention of the telephone, Hartford Steam Boiler has been monitoring trends in energy and technology that
Interim Threat / Risk Assessment. Student E- Communications Outsourcing Project
 Interim Threat / Risk Assessment Student E- Communications Outsourcing Project Martin Loeffler Information Security, I+TS Creation Date: Version 1.0 June 24, 2010 Last Updated: Version 2.0 July 6, 2010
Interim Threat / Risk Assessment Student E- Communications Outsourcing Project Martin Loeffler Information Security, I+TS Creation Date: Version 1.0 June 24, 2010 Last Updated: Version 2.0 July 6, 2010
BEFORE THE UNITED STATES FEDERAL TRADE COMMISSION WASHINGTON, DC
 BEFORE THE UNITED STATES FEDERAL TRADE COMMISSION WASHINGTON, DC ) COMMENTS OF THE FUTURE OF PRIVACY FORUM ) ) RE: INTERNET OF THINGS, PROJECT NO. P135405 ) ) I. Introduction On November 19, 2013, the
BEFORE THE UNITED STATES FEDERAL TRADE COMMISSION WASHINGTON, DC ) COMMENTS OF THE FUTURE OF PRIVACY FORUM ) ) RE: INTERNET OF THINGS, PROJECT NO. P135405 ) ) I. Introduction On November 19, 2013, the
The Promise of Industrial Big Data
 The Promise of Industrial Big Data Big Data Real Time Analytics Katherine Butler 1 st Annual Digital Economy Congress San Diego, CA Nov 14 th 15 th, 2013 Individual vs. Ecosystem What Happened When 1B
The Promise of Industrial Big Data Big Data Real Time Analytics Katherine Butler 1 st Annual Digital Economy Congress San Diego, CA Nov 14 th 15 th, 2013 Individual vs. Ecosystem What Happened When 1B
Federal Trade Commission
 Federal Trade Commission The FTC s Privacy and Data Security Program: Where It Came From, Where It s Going Jessica Rich 1 Director, Bureau of Consumer Protection, FTC International Association of Privacy
Federal Trade Commission The FTC s Privacy and Data Security Program: Where It Came From, Where It s Going Jessica Rich 1 Director, Bureau of Consumer Protection, FTC International Association of Privacy
The Federal Trade Commission Data Collection Workshop - A Review
 G. ' ~. t" :;. The Internet Association The Honorable Donald Clark Office of the Secretary Federal Trade Commission Room H-113 (Annex E) 600 Pennsylvania Avenue, NW Washington, DC 20580 March 8, 2013 Re:
G. ' ~. t" :;. The Internet Association The Honorable Donald Clark Office of the Secretary Federal Trade Commission Room H-113 (Annex E) 600 Pennsylvania Avenue, NW Washington, DC 20580 March 8, 2013 Re:
NETWORK SECURITY, REIMAGINED FPO
 FPO NETWORK SECURITY, REIMAGINED by Derek Korte AS TENS OF BILLIONS OF NEW DEVICES GET CONNECTED, BUSINESS AND SOCIETY MUST RETHINK SECURITY, PRIVACY, AND OPPORTUNITY Illustration JUSTIN GABBARD Smart
FPO NETWORK SECURITY, REIMAGINED by Derek Korte AS TENS OF BILLIONS OF NEW DEVICES GET CONNECTED, BUSINESS AND SOCIETY MUST RETHINK SECURITY, PRIVACY, AND OPPORTUNITY Illustration JUSTIN GABBARD Smart
Inviting Data Hackers to Lunch Without Knowing it
 Reynolds and Reynolds Inviting Data Hackers to Lunch Without Knowing it And Getting Stuck with the Tab Bob Schaefer, Vice President of Data Services Reynolds and Reynolds Inviting Data Hackers to Lunch
Reynolds and Reynolds Inviting Data Hackers to Lunch Without Knowing it And Getting Stuck with the Tab Bob Schaefer, Vice President of Data Services Reynolds and Reynolds Inviting Data Hackers to Lunch
How To Understand The Power Of The Internet Of Things
 Next Internet Evolution: Getting Big Data insights from the Internet of Things Internet of things are fast becoming broadly accepted in the world of computing and they should be. Advances in Cloud computing,
Next Internet Evolution: Getting Big Data insights from the Internet of Things Internet of things are fast becoming broadly accepted in the world of computing and they should be. Advances in Cloud computing,
FWD. What the Internet of Things will mean for business
 Article 6: September 2014 Internet of Things This year the focus of business has shifted to the Internet of Things (IoT), the connection and sharing of information between objects, machines, people and
Article 6: September 2014 Internet of Things This year the focus of business has shifted to the Internet of Things (IoT), the connection and sharing of information between objects, machines, people and
Privacy Challenges in the Internet of Things (IoT) a European Perspective
 Privacy Challenges in the Internet of Things (IoT) a European Perspective Alicja Gniewek, PhD Student Interdisciplinary Centre for Security, Reliability and Trust Weicker Building, Université du Luxembourg
Privacy Challenges in the Internet of Things (IoT) a European Perspective Alicja Gniewek, PhD Student Interdisciplinary Centre for Security, Reliability and Trust Weicker Building, Université du Luxembourg
Removing barriers to Cloud Computing in Europe Open Workshop
 Removing barriers to Cloud Computing in Europe Open Workshop SMART 2011/0045 - Open workshop By David Bradshaw, Gabriella Cattaneo, Giuliana Folco, IDC Thursday May 10, 2012- Brussels Copyright IDC. Reproduction
Removing barriers to Cloud Computing in Europe Open Workshop SMART 2011/0045 - Open workshop By David Bradshaw, Gabriella Cattaneo, Giuliana Folco, IDC Thursday May 10, 2012- Brussels Copyright IDC. Reproduction
Buying Guide for Cloud Services
 BUYING GUIDE Buying Guide for Cloud Services Getting Started Welcome to the CompTIA Buying Guide for Cloud Services. If you are like most executives, buying technology often entails elements of excitement,
BUYING GUIDE Buying Guide for Cloud Services Getting Started Welcome to the CompTIA Buying Guide for Cloud Services. If you are like most executives, buying technology often entails elements of excitement,
Wearable Technology Evolution & Security: Grant Brown - Security Strategist Symantec
 Wearable Technology Evolution & Security: Grant Brown - Security Strategist Symantec 3.58 KM 12.11 KPH 493 Calories 114 BPM WEARABLE TECH EVOLUTION AND SECURITY GRANT BROWN SECURITY STRATEGIST @thegrantbrown
Wearable Technology Evolution & Security: Grant Brown - Security Strategist Symantec 3.58 KM 12.11 KPH 493 Calories 114 BPM WEARABLE TECH EVOLUTION AND SECURITY GRANT BROWN SECURITY STRATEGIST @thegrantbrown
The Internet of Things (IoT) Opportunities and Risks
 Session No. 744 The Internet of Things (IoT) Opportunities and Risks David Loomis, CSP Risk Specialist Chubb Group of Insurance Companies Brian Wohnsiedler, CSP Risk Specialist Chubb Group of Insurance
Session No. 744 The Internet of Things (IoT) Opportunities and Risks David Loomis, CSP Risk Specialist Chubb Group of Insurance Companies Brian Wohnsiedler, CSP Risk Specialist Chubb Group of Insurance
Bring Your Own Internet of Things: BYO IoT
 SESSION ID: CSV F02 Bring Your Own Internet of Things: BYO IoT Carsten Eiram Chief Research Officer Risk Based Security @carsteneiram Jake Kouns CISO Risk Based Security @jkouns Agenda What is IoT? What
SESSION ID: CSV F02 Bring Your Own Internet of Things: BYO IoT Carsten Eiram Chief Research Officer Risk Based Security @carsteneiram Jake Kouns CISO Risk Based Security @jkouns Agenda What is IoT? What
Federal Trade Commission
 Federal Trade Commission Consumer Protection Challenges and Priorities for 2014 Jessica Rich 1 Director, Bureau of Consumer Protection, FTC Consumer Federation of America 2014 Consumer Assembly March 21,
Federal Trade Commission Consumer Protection Challenges and Priorities for 2014 Jessica Rich 1 Director, Bureau of Consumer Protection, FTC Consumer Federation of America 2014 Consumer Assembly March 21,
Staying Out of Trouble: Key Privacy, Data Security, and Advertising Mistakes That Can Put You in the Enforcement Crosshairs
 Staying Out of Trouble: Key Privacy, Data Security, and Advertising Mistakes That Can Put You in the Enforcement Crosshairs April 1, 2015 Reed Freeman Heather Zachary Overview Current State of the Market
Staying Out of Trouble: Key Privacy, Data Security, and Advertising Mistakes That Can Put You in the Enforcement Crosshairs April 1, 2015 Reed Freeman Heather Zachary Overview Current State of the Market
Cyber Security: Exploring the Human Element
 Cyber Security: Exploring the Human Element Summary of Proceedings Cyber Security: Exploring the Human Element Institute of Homeland Security Solutions March 8, 2011 National Press Club Introduction A
Cyber Security: Exploring the Human Element Summary of Proceedings Cyber Security: Exploring the Human Element Institute of Homeland Security Solutions March 8, 2011 National Press Club Introduction A
Written Submission to the Canadian Council of Insurance Regulators Credit Scoring Working Group
 Written Submission to the Canadian Council of Insurance Regulators Credit Scoring Working Group Monday, August 8, 2011 The Co-operators is pleased to provide comments to CCIR s issues paper Use of Credit
Written Submission to the Canadian Council of Insurance Regulators Credit Scoring Working Group Monday, August 8, 2011 The Co-operators is pleased to provide comments to CCIR s issues paper Use of Credit
Seizing Opportunity: Good Privacy Practices for Developing Mobile Apps
 Seizing Opportunity: Good Privacy Practices for Developing Mobile Apps 1 2 Introduction Canada s privacy laws require all businesses to balance innovation and entrepreneurialism with effective privacy
Seizing Opportunity: Good Privacy Practices for Developing Mobile Apps 1 2 Introduction Canada s privacy laws require all businesses to balance innovation and entrepreneurialism with effective privacy
The Challenges of Securing the Internet of Things (IoT) at Scale
 The Challenges of Securing the Internet of Things (IoT) at Scale Ulf Lindqvist, Ph.D. Program Director, SRI International Chair, IEEE Computer Society s Technical Committee on Security and Privacy Vice
The Challenges of Securing the Internet of Things (IoT) at Scale Ulf Lindqvist, Ph.D. Program Director, SRI International Chair, IEEE Computer Society s Technical Committee on Security and Privacy Vice
A WIDER SHARING ECOSYSTEM. The pivotal role of data in transport solutions
 A WIDER SHARING ECOSYSTEM The pivotal role of data in transport solutions October 2015 A MARKET ON THE MOVE CONTENTS 3 TRANSPORT TRENDS 4 THE ROAD AHEAD 5 TRANSPARENCY LEADS TO TRUST 6 DATA LOCATION AND
A WIDER SHARING ECOSYSTEM The pivotal role of data in transport solutions October 2015 A MARKET ON THE MOVE CONTENTS 3 TRANSPORT TRENDS 4 THE ROAD AHEAD 5 TRANSPARENCY LEADS TO TRUST 6 DATA LOCATION AND
The Canadian Realities of Big Data and Business Analytics. Utsav Arora February 12, 2014
 The Canadian Realities of Big Data and Business Analytics Utsav Arora February 12, 2014 Things to think about for today How Important is Big Data for me? Why do I need to implement Big Data and Analytics
The Canadian Realities of Big Data and Business Analytics Utsav Arora February 12, 2014 Things to think about for today How Important is Big Data for me? Why do I need to implement Big Data and Analytics
Securing the Growth of IoT and M2M
 Securing the Growth of IoT and M2M Svetlana Grant, Director, Future IoT Networks Connected Living Programme, GSMA 9 September 2015 Connected Living - Mobilising the Internet of Things GSMA VISION 2020
Securing the Growth of IoT and M2M Svetlana Grant, Director, Future IoT Networks Connected Living Programme, GSMA 9 September 2015 Connected Living - Mobilising the Internet of Things GSMA VISION 2020
MES and Industrial Internet
 October 7, 2014 MES and Industrial Internet Jan Snoeij Board Member, MESA International Principal Consultant, CGI Do you know MESA? Agenda Introduction Internet of Things Big Data Smart Factory or Smart
October 7, 2014 MES and Industrial Internet Jan Snoeij Board Member, MESA International Principal Consultant, CGI Do you know MESA? Agenda Introduction Internet of Things Big Data Smart Factory or Smart
Where Do You Draw the Creepy Line? Privacy, Big Data Analytics and the Internet of Things
 Where Do You Draw the Creepy Line? Privacy, Big Data Analytics and the Internet of Things aisa.org.a u aisa.org.a u Rebecca Herold, CEO The Privacy Professor 1 rebeccaherold@rebeccaherold.com Agenda Technology
Where Do You Draw the Creepy Line? Privacy, Big Data Analytics and the Internet of Things aisa.org.a u aisa.org.a u Rebecca Herold, CEO The Privacy Professor 1 rebeccaherold@rebeccaherold.com Agenda Technology
Alberta Private Passenger Usage Based Insurance (UBI) Implementation Process Consultation The Co-operators January 30, 2015
 Alberta Private Passenger Usage Based Insurance (UBI) Implementation Process Consultation The Co-operators January 30, 2015 Friday, January 30, 2015 Mr. Mark Prefontaine Superintendent of Insurance 402
Alberta Private Passenger Usage Based Insurance (UBI) Implementation Process Consultation The Co-operators January 30, 2015 Friday, January 30, 2015 Mr. Mark Prefontaine Superintendent of Insurance 402
Federal Trade Commission
 Federal Trade Commission Exploring Privacy A Roundtable Series Berkeley, CA Remarks of David Vladeck, 1 Director FTC Bureau of Consumer Protection, January 28, 2010 It is great to be here in California.
Federal Trade Commission Exploring Privacy A Roundtable Series Berkeley, CA Remarks of David Vladeck, 1 Director FTC Bureau of Consumer Protection, January 28, 2010 It is great to be here in California.
Digital Insurance Era: Stretch Your Boundaries
 Accenture Technology Vision for Insurance 2015 Digital Insurance Era: Stretch Your Boundaries EXECUTIVE SUMMARY INTRODUCTION A new We Economy is bringing change to the insurance industry whether carriers
Accenture Technology Vision for Insurance 2015 Digital Insurance Era: Stretch Your Boundaries EXECUTIVE SUMMARY INTRODUCTION A new We Economy is bringing change to the insurance industry whether carriers
PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION. Protecting Personal Consumer Information from Cyber Attacks and Data Breaches.
 PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION on Protecting Personal Consumer Information from Cyber Attacks and Data Breaches Before the COMMITTEE ON COMMERCE, SCIENCE, AND TRANSPORTATION UNITED
PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION on Protecting Personal Consumer Information from Cyber Attacks and Data Breaches Before the COMMITTEE ON COMMERCE, SCIENCE, AND TRANSPORTATION UNITED
30 BILLION RISKS AND REWARDS OF CONNECTED DEVICES THE INTERNET OF THINGS CYBER LANDSCAPE TODAY
 RISKS AND REWARDS OF CONNECTED DEVICES THE HIDDEN INTERNET OF THINGS ISACA 2015 IT RISK / REWARD BAROMETER The Internet of Things paints a vision of a carefree, seamlessly connected world where interconnected
RISKS AND REWARDS OF CONNECTED DEVICES THE HIDDEN INTERNET OF THINGS ISACA 2015 IT RISK / REWARD BAROMETER The Internet of Things paints a vision of a carefree, seamlessly connected world where interconnected
Security in Internet-Connected Building Automation and Energy Management Systems
 Security in Internet-Connected Building Automation and Energy Management Systems Executive Summary Thermostats, lights, meters, and sensors are joining the Internet of Things, increasing the power and
Security in Internet-Connected Building Automation and Energy Management Systems Executive Summary Thermostats, lights, meters, and sensors are joining the Internet of Things, increasing the power and
The Internet of Things From a User Perspective: Enhancing user experience in networks with multiple devices
 The Internet of Things From a User Perspective: Enhancing user experience in networks with multiple devices Helena Holmström Olsson Malmö University Helena Holmström Olsson About me: Professor, Computer
The Internet of Things From a User Perspective: Enhancing user experience in networks with multiple devices Helena Holmström Olsson Malmö University Helena Holmström Olsson About me: Professor, Computer
INTRODUCTION. IoT AND IP STRATEGIES
 INTRODUCTION At first, the Internet of Things (IoT) may seem like an idea straight out of science fiction. However, on closer consideration, we realize that the process of connecting everyday electronic
INTRODUCTION At first, the Internet of Things (IoT) may seem like an idea straight out of science fiction. However, on closer consideration, we realize that the process of connecting everyday electronic
The Internet of Things. Suzanne Bell (Wilson Sonsini Goodrich & Rosati) Tracy Shapiro (Wilson Sonsini Goodrich & Rosati) Vineet Shahani (Nest Labs)
 The Internet of Things Suzanne Bell (Wilson Sonsini Goodrich & Rosati) Tracy Shapiro (Wilson Sonsini Goodrich & Rosati) Vineet Shahani (Nest Labs) 1 Defining the Internet of Things There have been prior
The Internet of Things Suzanne Bell (Wilson Sonsini Goodrich & Rosati) Tracy Shapiro (Wilson Sonsini Goodrich & Rosati) Vineet Shahani (Nest Labs) 1 Defining the Internet of Things There have been prior
Application Alley. Smart Wireless Sensing. WE MATTER WE CONNECT - Smart Home Security PARTNER SOLVE DELIVER
 PARTNER SOLVE DELIVER Smart Wireless Sensing Advanced Electronic Components Bring Smart Home Security Features Alive With the advent of smart technology, integrating wireless/connected functionality and
PARTNER SOLVE DELIVER Smart Wireless Sensing Advanced Electronic Components Bring Smart Home Security Features Alive With the advent of smart technology, integrating wireless/connected functionality and
Cross-border Cloud Computing: The State / International Tax Debate
 NAVIGATING STATE TAXATION IN A GLOBAL BUSINESS ENVIRONMENT Cross-border Cloud Computing: The State / International Tax Debate Carolynn S. Iafrate Kranz Industry Sales Tax Solutions Jim Nason Deloitte Tax
NAVIGATING STATE TAXATION IN A GLOBAL BUSINESS ENVIRONMENT Cross-border Cloud Computing: The State / International Tax Debate Carolynn S. Iafrate Kranz Industry Sales Tax Solutions Jim Nason Deloitte Tax
Data Breach Notifications. Submission by the Australian Communications Consumer Action Network to the Attorney General s Department
 Data Breach Notifications Submission by the Australian Communications Consumer Action Network to the Attorney General s Department November 2012 About ACCAN The Australian Communications Consumer Action
Data Breach Notifications Submission by the Australian Communications Consumer Action Network to the Attorney General s Department November 2012 About ACCAN The Australian Communications Consumer Action
Enabling Integrated Care
 Enabling Integrated Care Harnessing personal health systems for better outcomes across the care continuum Briefing Note for a SmartPersonalHealth Workshop WoHIT, Thursday 18 March 2010, 13:00-17:00, Barcelona
Enabling Integrated Care Harnessing personal health systems for better outcomes across the care continuum Briefing Note for a SmartPersonalHealth Workshop WoHIT, Thursday 18 March 2010, 13:00-17:00, Barcelona
The Internet of Things Risks and Challenges
 The Internet of Things Risks and Challenges Providing the insight that enables our customers to make informed business decisions. Antony Price 03rd March 2015 Contents Internet of Things - The next threat
The Internet of Things Risks and Challenges Providing the insight that enables our customers to make informed business decisions. Antony Price 03rd March 2015 Contents Internet of Things - The next threat
ALM Virtual Corporate Counsel Managing Cybersecurity Risks and Mitigating Data Breach Damage
 ALM Virtual Corporate Counsel Managing Cybersecurity Risks and Mitigating Data Breach Damage VENABLE LLP Attorneys at Law Washington, DC/New York/San Francisco/Los Angeles/Baltimore/Virginia/Delaware November
ALM Virtual Corporate Counsel Managing Cybersecurity Risks and Mitigating Data Breach Damage VENABLE LLP Attorneys at Law Washington, DC/New York/San Francisco/Los Angeles/Baltimore/Virginia/Delaware November
Risks and Rewards of the Internet of Things. Findings From ISACA s 2013 IT Risk/Reward Barometer
 Risks and Rewards of the Internet of Things Findings From ISACA s 2013 IT Risk/Reward Barometer The world is increasingly being populated by connected devices that collect and share information over the
Risks and Rewards of the Internet of Things Findings From ISACA s 2013 IT Risk/Reward Barometer The world is increasingly being populated by connected devices that collect and share information over the
Federal Trade Commission
 Federal Trade Commission Introductory Remarks to Follow the Lead: An FTC Workshop on Lead Generation Jessica Rich Director, Bureau of Consumer Protection, FTC Washington, D.C. October 30, 2015 Good morning.
Federal Trade Commission Introductory Remarks to Follow the Lead: An FTC Workshop on Lead Generation Jessica Rich Director, Bureau of Consumer Protection, FTC Washington, D.C. October 30, 2015 Good morning.
Shared Infrastructure: What and Where is Collaboration Needed to Build the SM Platform?
 Smart Manufacturing Forum Shared Infrastructure: What and Where is Collaboration Needed to Build the SM Platform? 10:45-11:45am panel discussion Moderator: John Bernaden, Vice Chair, Smart Manufacturing
Smart Manufacturing Forum Shared Infrastructure: What and Where is Collaboration Needed to Build the SM Platform? 10:45-11:45am panel discussion Moderator: John Bernaden, Vice Chair, Smart Manufacturing
IoT Service Transformation
 IoT Service Transformation John Carrington VP, Marketing & Strategy October 28, 2015 Agenda Service Trends and Transformation Connected Products and IoT Intersection of IoT and Services Connected Service
IoT Service Transformation John Carrington VP, Marketing & Strategy October 28, 2015 Agenda Service Trends and Transformation Connected Products and IoT Intersection of IoT and Services Connected Service
Online Interest-Based Advertising: The Road Traveled and the Road Ahead
 Online Interest-Based Advertising: The Road Traveled and the Road Ahead Genie Barton VP & Director, Online Interest-Based Advertising Program Advertising Self-Regulatory Council (ASRC)/ Council of Better
Online Interest-Based Advertising: The Road Traveled and the Road Ahead Genie Barton VP & Director, Online Interest-Based Advertising Program Advertising Self-Regulatory Council (ASRC)/ Council of Better
Cyber Risk in Healthcare AOHC, 3 June 2015
 Cyber Risk in Healthcare AOHC, 3 June 2015 Kopiha Nathan, Senior Healthcare Risk Management and Data Specialist James Penafiel, Underwriting Supervisor, Insurance Operations CFPC Conflict of Interest -
Cyber Risk in Healthcare AOHC, 3 June 2015 Kopiha Nathan, Senior Healthcare Risk Management and Data Specialist James Penafiel, Underwriting Supervisor, Insurance Operations CFPC Conflict of Interest -
FTC Consumer Protection Priorities In 2015
 Portfolio Media. Inc. 860 Broadway, 6th Floor New York, NY 10003 www.law360.com Phone: +1 646 783 7100 Fax: +1 646 783 7161 customerservice@law360.com FTC Consumer Protection Priorities In 2015 Law360,
Portfolio Media. Inc. 860 Broadway, 6th Floor New York, NY 10003 www.law360.com Phone: +1 646 783 7100 Fax: +1 646 783 7161 customerservice@law360.com FTC Consumer Protection Priorities In 2015 Law360,
Security & Privacy Strategies for Expanded Communities. Deven McGraw Partner Manatt, Phelps & Phillips LLP
 Security & Privacy Strategies for Expanded Communities Deven McGraw Partner Manatt, Phelps & Phillips LLP 1 Key Challenges in Community Data Sharing Patient-mediated data sharing Sharing data with companies
Security & Privacy Strategies for Expanded Communities Deven McGraw Partner Manatt, Phelps & Phillips LLP 1 Key Challenges in Community Data Sharing Patient-mediated data sharing Sharing data with companies
Internet of Things and insurance. Paris, March 24h, 2015
 Internet of Things and insurance Paris, March 4h, 0 Think Tank on Aggregators - 04 The "IoT Insurance" Think Tank was conducted with participating European insurers between November 04 and February 0 8
Internet of Things and insurance Paris, March 4h, 0 Think Tank on Aggregators - 04 The "IoT Insurance" Think Tank was conducted with participating European insurers between November 04 and February 0 8
BYOD: Bring Your Own Device Advantage, Liability or Both?
 BYOD: Bring Your Own Device Advantage, Liability or Both? S S Scott Summers Laura B. Grubbs Dinsmore & Shohl Louisville, KY The BYOD to Work Movement Dual-Use Devices: used for both personal and company
BYOD: Bring Your Own Device Advantage, Liability or Both? S S Scott Summers Laura B. Grubbs Dinsmore & Shohl Louisville, KY The BYOD to Work Movement Dual-Use Devices: used for both personal and company
Decrypting the Security Risk Assessment (SRA) Requirement for Meaningful Use
 Click to edit Master title style Decrypting the Security Risk Assessment (SRA) Requirement for Meaningful Use Andy Petrovich, MHSA, MPH M-CEITA / Altarum Institute April 8, 2015 4/8/2015 1 1 Who is M-CEITA?
Click to edit Master title style Decrypting the Security Risk Assessment (SRA) Requirement for Meaningful Use Andy Petrovich, MHSA, MPH M-CEITA / Altarum Institute April 8, 2015 4/8/2015 1 1 Who is M-CEITA?
An Introduction to the Internet of Things (IoT)
 An Introduction to the Internet of Things (IoT) Part 1. of The IoT Series November 2013 Lopez Research LLC 2269 Chestnut Street #202 San Francisco, CA 94123 T (866) 849-5750 E sales@lopezresearch.com W
An Introduction to the Internet of Things (IoT) Part 1. of The IoT Series November 2013 Lopez Research LLC 2269 Chestnut Street #202 San Francisco, CA 94123 T (866) 849-5750 E sales@lopezresearch.com W
Before the AmCham EU Transatlantic Conference (Mar. 3, 2011), available at http://useu.usmission.gov/kennard_amchameu_030311.html.
 One Year Later: Privacy and Data Security in a World of Big Data, the Internet of Things, and Global Data Flows Keynote Address Before the USCIB/BIAC/OECD Conference on Promoting Inclusive Growth in the
One Year Later: Privacy and Data Security in a World of Big Data, the Internet of Things, and Global Data Flows Keynote Address Before the USCIB/BIAC/OECD Conference on Promoting Inclusive Growth in the
A COALFIRE PERSPECTIVE. Moving to the Cloud. NCHELP Spring Convention Panel May 2012
 A COALFIRE PERSPECTIVE Moving to the Cloud A Summary of Considerations for Implementing Cloud Migration Plans into New Business Platforms NCHELP Spring Convention Panel May 2012 DALLAS DENVER LOS ANGELES
A COALFIRE PERSPECTIVE Moving to the Cloud A Summary of Considerations for Implementing Cloud Migration Plans into New Business Platforms NCHELP Spring Convention Panel May 2012 DALLAS DENVER LOS ANGELES
Creating an IoT Ecosystem through scenarios
 Creating an IoT Ecosystem through scenarios IEEE Internet of Things Initiative Hendrik Berndt, Scenarios Track Chair IoT Week Lisbon, June 17 th, 2015 1 16/06/15 An IoT Definition! The Internet of Things
Creating an IoT Ecosystem through scenarios IEEE Internet of Things Initiative Hendrik Berndt, Scenarios Track Chair IoT Week Lisbon, June 17 th, 2015 1 16/06/15 An IoT Definition! The Internet of Things
The Facility Manager s Guide to IoT in Meeting Spaces. An AVI-SPL White Paper. www.avispl.com (+01).866.559.8197
 The Facility Manager s Guide to IoT in Meeting Spaces An AVI-SPL White Paper www.avispl.com (+01).866.559.8197 1 The Facility Manager s Guide to IoT in Meeting Spaces (+01).866.559.8197 www.avispl.com
The Facility Manager s Guide to IoT in Meeting Spaces An AVI-SPL White Paper www.avispl.com (+01).866.559.8197 1 The Facility Manager s Guide to IoT in Meeting Spaces (+01).866.559.8197 www.avispl.com
PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION. Protecting Consumer Information: Can Data Breaches Be Prevented? Before the
 PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION on Protecting Consumer Information: Can Data Breaches Be Prevented? Before the COMMITTEE ON ENERGY AND COMMERCE SUBCOMMITTEE ON COMMERCE, MANUFACTURING,
PREPARED STATEMENT OF THE FEDERAL TRADE COMMISSION on Protecting Consumer Information: Can Data Breaches Be Prevented? Before the COMMITTEE ON ENERGY AND COMMERCE SUBCOMMITTEE ON COMMERCE, MANUFACTURING,
Industrial Automation. A Manufacturing Revolution in Automotive and Industrial Equipment
 Industrial Automation A Manufacturing Revolution in Automotive and Industrial Equipment 1 Automated production, integrated end-to-end: transparent, reliable, predictable and efficient. That s the promise
Industrial Automation A Manufacturing Revolution in Automotive and Industrial Equipment 1 Automated production, integrated end-to-end: transparent, reliable, predictable and efficient. That s the promise
Developing the edge or scaling the core through corporate venturing Internet of Things. Daan Witteveen
 Developing the edge or scaling the core through corporate venturing Internet of Things Daan Witteveen Global M2M Connections (billion) The Global IOT Market is expected to see a forecasted to grow at a
Developing the edge or scaling the core through corporate venturing Internet of Things Daan Witteveen Global M2M Connections (billion) The Global IOT Market is expected to see a forecasted to grow at a
Hyper-connectivity and Artificial Intelligence
 Hyper-connectivity and Artificial Intelligence How hyper-connectivity changes AI through contextual computing Chuan (Coby) M 04/03/15 Description of Major Sections Background Artificial intelligence (AI)
Hyper-connectivity and Artificial Intelligence How hyper-connectivity changes AI through contextual computing Chuan (Coby) M 04/03/15 Description of Major Sections Background Artificial intelligence (AI)
Comments on the Online Trust Alliance s Proposed Internet of Things Best Practices Framework. September 14, 2015
 Comments on the Online Trust Alliance s Proposed Internet of Things Best Practices Framework September, 05 Recently, the Online Trust Alliance (OTA) published a request for comments on their Internet of
Comments on the Online Trust Alliance s Proposed Internet of Things Best Practices Framework September, 05 Recently, the Online Trust Alliance (OTA) published a request for comments on their Internet of
Privacy by Design. Ian Brown, Prof. of Information Security and Privacy Oxford Internet Institute, University of Oxford @IanBrownOII
 Privacy by Design Ian Brown, Prof. of Information Security and Privacy Oxford Internet Institute, University of Oxford @IanBrownOII Privacy by Design principles 1. Proactive not Reactive; Preventative
Privacy by Design Ian Brown, Prof. of Information Security and Privacy Oxford Internet Institute, University of Oxford @IanBrownOII Privacy by Design principles 1. Proactive not Reactive; Preventative
Data Privacy & Security: Essential Questions Every Business Must Ask
 Data Privacy & Security: Essential Questions Every Business Must Ask Presented by: Riddell Williams P.S. Riddell Williams P.S. May 6, 2015 #4841-4703-9779 Innocent? 2 Overview 3 basic questions every business
Data Privacy & Security: Essential Questions Every Business Must Ask Presented by: Riddell Williams P.S. Riddell Williams P.S. May 6, 2015 #4841-4703-9779 Innocent? 2 Overview 3 basic questions every business
Dr. Peter Sargious Medical Director of Chronic Disease with Alberta Health Services, Calgary, AB
 On September 18 th, we held our webinar, the online Chronic Disease Self- Management Program A good choice for Canada? We weren t able to answer all the questions from attendees, so we asked our panelists
On September 18 th, we held our webinar, the online Chronic Disease Self- Management Program A good choice for Canada? We weren t able to answer all the questions from attendees, so we asked our panelists
Working Lunch The Future of Responsible Big Data
 Working Lunch The Future of Responsible Big Data 3 March 2015 Washington, DC FOLLOW US ON linkedin.com/company/centre-for-information-policy-leadership FOLLOW US ON TWITTER @THE_CIPL Working Lunch The
Working Lunch The Future of Responsible Big Data 3 March 2015 Washington, DC FOLLOW US ON linkedin.com/company/centre-for-information-policy-leadership FOLLOW US ON TWITTER @THE_CIPL Working Lunch The
Security and the Internet of Things
 Security and the Internet of Things Joe Sanford 1. Abstract More and more smart devices are being introduced to the market, allowing end-users to have more of the devices they use every day to be connected
Security and the Internet of Things Joe Sanford 1. Abstract More and more smart devices are being introduced to the market, allowing end-users to have more of the devices they use every day to be connected
The Internet of Everything
 The Internet of Everything Turning Big Data into BIG Opportunity (Everything you need to know about the Internet of Everything) Imagine never making another grocery list because the connected fridge sends
The Internet of Everything Turning Big Data into BIG Opportunity (Everything you need to know about the Internet of Everything) Imagine never making another grocery list because the connected fridge sends
Secure and Reliable Data Exchange with IoT Devices. Vinny Sakore & Amit Trivedi February 29, 2016
 Secure and Reliable Data Exchange with IoT Devices Vinny Sakore & Amit Trivedi February 29, 2016 Mobile and Internet of Things (IoT) Security Risk With IoT Technology Nepal Earthquake (April 25, 2015)
Secure and Reliable Data Exchange with IoT Devices Vinny Sakore & Amit Trivedi February 29, 2016 Mobile and Internet of Things (IoT) Security Risk With IoT Technology Nepal Earthquake (April 25, 2015)
The problem of cloud data governance
 The problem of cloud data governance Vasilis Tountopoulos, Athens Technology Center S.A. (ATC) CSP EU Forum 2014 - Thursday, 22 nd May, 2014 Focus on data protection in the cloud Why data governance in
The problem of cloud data governance Vasilis Tountopoulos, Athens Technology Center S.A. (ATC) CSP EU Forum 2014 - Thursday, 22 nd May, 2014 Focus on data protection in the cloud Why data governance in
OT PRODUCTS AND SOLUTIONS MACHINE TO MACHINE
 OT PRODUCTS AND SOLUTIONS MACHINE TO MACHINE MACHINE-TO-MACHINE ENABLE AND SECURE A CONNECTED LIFE DRIVEN BY GOVERNMENT REGULATIONS, COMPANY AND CONSUMER NEEDS, PRODUCTS ARE TRANSFORMED INTO INTELLIGENT,
OT PRODUCTS AND SOLUTIONS MACHINE TO MACHINE MACHINE-TO-MACHINE ENABLE AND SECURE A CONNECTED LIFE DRIVEN BY GOVERNMENT REGULATIONS, COMPANY AND CONSUMER NEEDS, PRODUCTS ARE TRANSFORMED INTO INTELLIGENT,
Internet of Things From Idea to Scale
 PRG Symposium Internet of Things From Idea to Scale September 12, 2014 alex.blanter@atkearney.com @AlexBlanter You are here today because you are interested in the Internet of Things and so is everybody
PRG Symposium Internet of Things From Idea to Scale September 12, 2014 alex.blanter@atkearney.com @AlexBlanter You are here today because you are interested in the Internet of Things and so is everybody
internet of things Patrick Pax Business Development Manager Chris Geary Innovation Manager
 internet of things Patrick Pax Business Development Manager Chris Geary Innovation Manager agenda 1 2 3 4 internet of things moving into main stream uncover new opportunities in your business call for
internet of things Patrick Pax Business Development Manager Chris Geary Innovation Manager agenda 1 2 3 4 internet of things moving into main stream uncover new opportunities in your business call for
BIG DATA AND INSURANCE SYMPOSIUM
 BIG DATA AND INSURANCE SYMPOSIUM ATTORNEY GENERAL GEORGE JEPSEN UNIVERSITY OF CONNECTICUT SCHOOL OF LAW APRIL 3, 2014 (REVISED FOR PUBLICATION) *** This Article reproduces the keynote address delivered
BIG DATA AND INSURANCE SYMPOSIUM ATTORNEY GENERAL GEORGE JEPSEN UNIVERSITY OF CONNECTICUT SCHOOL OF LAW APRIL 3, 2014 (REVISED FOR PUBLICATION) *** This Article reproduces the keynote address delivered
Before the Department of Energy Washington, D.C. 20585 ) ) ) ) ) ) NBP RFI: Data Access, Third Party Use, and Privacy
 Before the Department of Energy Washington, D.C. 20585 In the Matter of Implementing the National Broadband Plan by Empowering Consumers and the Smart Grid: Data Access, Third Party Use, and Privacy )
Before the Department of Energy Washington, D.C. 20585 In the Matter of Implementing the National Broadband Plan by Empowering Consumers and the Smart Grid: Data Access, Third Party Use, and Privacy )
1. Understanding Big Data
 Big Data and its Real Impact on Your Security & Privacy Framework: A Pragmatic Overview Erik Luysterborg Partner, Deloitte EMEA Data Protection & Privacy leader Prague, SCCE, March 22 nd 2016 1. 2016 Deloitte
Big Data and its Real Impact on Your Security & Privacy Framework: A Pragmatic Overview Erik Luysterborg Partner, Deloitte EMEA Data Protection & Privacy leader Prague, SCCE, March 22 nd 2016 1. 2016 Deloitte
Start your adventure with SMART HOME.
 Start your adventure with SMART HOME. Your home can be smarter than you think. Explore the benefits of home automation with FIBARO STARTER KIT. Five intelligent devices together with Home Center Lite will
Start your adventure with SMART HOME. Your home can be smarter than you think. Explore the benefits of home automation with FIBARO STARTER KIT. Five intelligent devices together with Home Center Lite will
What is Quantified Self (QS)?
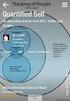 Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
CSR Breach Reporting Service Frequently Asked Questions
 CSR Breach Reporting Service Frequently Asked Questions Quick and Complete Reporting is Critical after Data Loss Why do businesses need this service? If organizations don t have this service, what could
CSR Breach Reporting Service Frequently Asked Questions Quick and Complete Reporting is Critical after Data Loss Why do businesses need this service? If organizations don t have this service, what could
Privacy Impact Assessment. For. Non-GFE for Remote Access. Date: May 26, 2015. Point of Contact and Author: Michael Gray michael.gray@ed.
 For Non-GFE for Remote Access Date: May 26, 2015 Point of Contact and Author: Michael Gray michael.gray@ed.gov System Owner: Allen Hill allen.hill@ed.gov Office of the Chief Information Officer (OCIO)
For Non-GFE for Remote Access Date: May 26, 2015 Point of Contact and Author: Michael Gray michael.gray@ed.gov System Owner: Allen Hill allen.hill@ed.gov Office of the Chief Information Officer (OCIO)
COMMUNIQUÉ ON PRINCIPLES FOR INTERNET POLICY-MAKING OECD HIGH LEVEL MEETING ON THE INTERNET ECONOMY,
 COMMUNIQUÉ ON PRINCIPLES FOR INTERNET POLICY-MAKING OECD HIGH LEVEL MEETING ON THE INTERNET ECONOMY, 28-29 JUNE 2011 The Seoul Declaration on the Future of the Internet Economy adopted at the 2008 OECD
COMMUNIQUÉ ON PRINCIPLES FOR INTERNET POLICY-MAKING OECD HIGH LEVEL MEETING ON THE INTERNET ECONOMY, 28-29 JUNE 2011 The Seoul Declaration on the Future of the Internet Economy adopted at the 2008 OECD
Smart Grid Security: Ground Zero for Cyber Security. June 2, 2010 at 12:51 PM by Larry Karisny
 Smart Grid Security: Ground Zero for Cyber Security June 2, 2010 at 12:51 PM by Larry Karisny It was pretty amazing to see the amount of people involved in Conductivity Week in Santa Clara California last
Smart Grid Security: Ground Zero for Cyber Security June 2, 2010 at 12:51 PM by Larry Karisny It was pretty amazing to see the amount of people involved in Conductivity Week in Santa Clara California last
Big data companies beware: the FTC plans to boost enforcement in your industry
 AUGUST 29, 2013 Big data companies beware: the FTC plans to boost enforcement in your industry By Linn Foster Freedman and Kathryn M. Sylvia On August 19, 2013, at the Technology Policy Institute s Annual
AUGUST 29, 2013 Big data companies beware: the FTC plans to boost enforcement in your industry By Linn Foster Freedman and Kathryn M. Sylvia On August 19, 2013, at the Technology Policy Institute s Annual
Personal Information Management Services:
 Personal Information Management Services: A Market Poised to Disrupt A snapshot of developments in Personal Data Stores and Personal Information Management Services A briefing from Ctrl-Shift November
Personal Information Management Services: A Market Poised to Disrupt A snapshot of developments in Personal Data Stores and Personal Information Management Services A briefing from Ctrl-Shift November
IDENTITY THEFT AND DATA BREACH CONFERENCE 2016
 IDENTITY THEFT AND DATA BREACH CONFERENCE 2016 Day 1 Thursday January 28, 2016 INTERNATIONAL DATA PRIVACY DAY 7:30am 8:30am Registration 8:30am 9:00am Opening Remarks Conference Chair Kevin M. Scott, President
IDENTITY THEFT AND DATA BREACH CONFERENCE 2016 Day 1 Thursday January 28, 2016 INTERNATIONAL DATA PRIVACY DAY 7:30am 8:30am Registration 8:30am 9:00am Opening Remarks Conference Chair Kevin M. Scott, President
Security in Vehicle Networks
 Security in Vehicle Networks Armin Happel, Christof Ebert Stuttgart, 17. March 2015 V1.1 2015-04-28 Introduction Vector Consulting Services supports clients worldwide in improving their product development
Security in Vehicle Networks Armin Happel, Christof Ebert Stuttgart, 17. March 2015 V1.1 2015-04-28 Introduction Vector Consulting Services supports clients worldwide in improving their product development
The Social Impact of Open Data
 United States of America Federal Trade Commission The Social Impact of Open Data Remarks of Maureen K. Ohlhausen 1 Commissioner, Federal Trade Commission Center for Data Innovation The Social Impact of
United States of America Federal Trade Commission The Social Impact of Open Data Remarks of Maureen K. Ohlhausen 1 Commissioner, Federal Trade Commission Center for Data Innovation The Social Impact of
Opinion and recommendations on challenges raised by biometric developments
 Opinion and recommendations on challenges raised by biometric developments Position paper for the Science and Technology Committee (House of Commons) Participation to the inquiry on Current and future
Opinion and recommendations on challenges raised by biometric developments Position paper for the Science and Technology Committee (House of Commons) Participation to the inquiry on Current and future
UNITED STATES OF AMERICA FEDERAL TRADE COMMISSION
 UNITED STATES OF AMERICA FEDERAL TRADE COMMISSION 122 3095 COMMISSIONERS: Edith Ramirez, Chairwoman Julie Brill Maureen K. Ohlhausen Joshua D. Wright In the Matter of GMR TRANSCRIPTION SERVICES, INC.,
UNITED STATES OF AMERICA FEDERAL TRADE COMMISSION 122 3095 COMMISSIONERS: Edith Ramirez, Chairwoman Julie Brill Maureen K. Ohlhausen Joshua D. Wright In the Matter of GMR TRANSCRIPTION SERVICES, INC.,
Workshop Discussion Notes: Data Supply Chains
 Workshop Discussion Notes: Data Supply Chains The Social, Cultural & Ethical Dimensions of Big Data March 17, 2014 - New York, NY http://www.datasociety.net/initiatives/2014-0317/ This document was produced
Workshop Discussion Notes: Data Supply Chains The Social, Cultural & Ethical Dimensions of Big Data March 17, 2014 - New York, NY http://www.datasociety.net/initiatives/2014-0317/ This document was produced
Smart City Live! 9-10 May 2016, Nice
 Monday, May 9, 2016 Smart City Live! 9-10 May 2016, Nice Draft agenda as of November 20, 2015 SMART LIVING SMART CITY SERVICES 9:00 AM CASE STUDY: Developing Smart Energy communities Understanding the
Monday, May 9, 2016 Smart City Live! 9-10 May 2016, Nice Draft agenda as of November 20, 2015 SMART LIVING SMART CITY SERVICES 9:00 AM CASE STUDY: Developing Smart Energy communities Understanding the
