CISO Certified Information Security Officer in Small and Medium Enterprises
|
|
|
- Timothy James
- 10 years ago
- Views:
Transcription
1 CISO Certified Information Security Officer in Small and Medium Enterprises This project has been funded with support from the European Commission. This publication [communication] reflects the views only of the author, and the Commission cannot be held responsible for any use which may be made of the information contained therein. TRANSFER OF INNOVATION, LEONARDO DA VINCI LIFELONG LEARNING PROGRAMME LLP-LDV-TOI PL1-LEO Sectors EA35 and EA37
2 1 The learning environment The learning environment, which is available in all partnership languages, provides authorized users with access to materials that have been organized in each teaching unit, each designed on the basis of the model devised by the European partnership, to address and provide the necessary support to develop skills relating to various information security issues. The teaching units have been linked to the offices of a typical, virtual company (Back Office, Front Office, Information Security Room and Information Technology Room). Here, users can acquire knowledge and receive technical information by using the online media products developed on the basis of the model described below, and can also download documents, complete exercises and ask the expert questions. Audio-visual support and self-assessment tests allow users to learn in a quick, flexible, intuitive and efficient way. All you need are access credentials (username and password) that CONFORM S.c.a.r.l. issues.
3 2 The Model The learning environment created for the CISO project is a direct expression of the application of the competence based model, designed to facilitate and promote a system to manage and develop people based on skills, by identifying, maintaining and developing what people know, what they know how to do and how they do it. The application of the competence based model allowed the partners to adapt the Competence Dictionary of the Security Manager to national reference contexts of the CISO project partnership and to respective linguistic terminology. The dictionary contains the names, e-competences, work processes, description and break down of knowledge, operational skills and behaviour, in order to govern the basic and specialist skills required to undertake business activities to expected performance levels. The Competence Dictionary, which can be accessed from the Information Security Room of the CISO learning environment, constitutes a strategic map of the vocational skills of the Information Security Manager, divided into knowledge and skills. The definition of their levels of exercise has been defined in line with those defined by the European e-competence Framework, structured in four dimensions: Dimension 1: definition of the 5 areas of e-competence (Plan, Build, Run, Enable and Manage) that reflect the processes and main subprocesses of the ICT market. Dimension 2: identification and description of a set of reference e-competences
4 3 Dimension 3: skills levels for each competence, articulated in levels of expertise from e-1 to e-5, in relation to the EQF - European Qualifications Framework levels 3 to 8, as shown in the following table: e-cf Level Correlated EQF Level* e-5 8 e-4 7 e-3 6 e-2 4 e 5 e-1 3 * levels 1 and 2 of the EQF are not relevant in this context Dimension 4: detailed examples of knowledge and fundamental abilities that refer to the contents of the e-competence. The dictionary has become the reference guide first for processing and after for delivery of the training course and, thus, the learning environment to increase the effectiveness of learning at individual and collective level, using the full potential of new technologies, to lead to teaching/learning processes with high levels of interactivity. To promote the direct involvement of the direct target audience, animations were made and translated into the different partnership languages. These can be seen in the different teaching units. The animations are an opportunity for learning in sitù to which learners can relate, triggering a virtuous cycle of analysis, reflection, criticism and internalization in virtue of the lifelong e-learning model that promotes sedimented, conscious learning that can favour the systematic adoption for learners of the professional conduct and correlated procedural, operational and technical measures using an organizational, methodological and pedagogical rationale.
5 4 Each teaching unit also contains various opportunities for self-evaluation and assessment, where learners can test the skills they have acquired and reflect on the content and the information conveyed by animations. Front Office: Worksheet IT Room: Test In addition, the model particularly emphasis the development of the cognitive dimension of learning, offering users the possibility to access a variety of resources and educational tools (glossaries, guidelines, checklists, posters) that aim to develop, disseminate and maintain over time the key knowledge to perform well in the project target sector, standardize language, theoretical references, methodological principles, operational requirements, behavioural measures in a lifelong e-learning perspective.
6 5 The offices The learning environment is divided into four virtual offices: Front Office, Back Office, Information Security Office, Information Technology Room, where authorised users can access materials containing further information and the teaching units, by clicking on sensitive objects (computers, shelves, folders, etc.). Front Office Back Office IS Office (Information Security Office) IT Room (Information Technology Room) Here follows a short presentation of the contents of each room
7 6 The offices Front Office The Front Office provides an initial introduction to information security, its management and an overview of the measures to be taken to protect data: the aim is to raise awareness and stimulate interest in information security. Authorized users can consult a series of training materials and information about international rules on the matter and the aims of good information security policy. The Front Office contains the first unit, which can be accessed from the home tab. Here users can access the following teaching and support materials: Animations - Security Incident: what can happen in a company if you do not pay due attention to information security? - Too Late Show: interview with an expert on information security, Mrs Safe, to understand just how important it is to protect company data. Exercise Passing the floor to users: you will be asked to identify company guidelines on information security with particular reference to secure passwords, attacks from computer viruses and clean desktop policies. Glossary List of key terms used in the teaching units. Users will be able to test and assess the definitions of individual terms by degree of complexity: beginner, intermediate, advanced. Evaluation Tests Users can check the skills they have acquired by answering simple multiple choice questions: Basic level: 15 questions Intermediate level: 27 questions Advanced Level: 30 questions
8 7 The offices Back Office The Back Office is dedicated to information security issues as regards human resources management as a risk factor, to training needs and opportunities, to planning of security manage strategies and risk analysis. Authorized users can consult a series of training and information materials, including a useful checklist to be used for risk analysis and guidance on how to keep up-to-date in the field of data protection. From the Back Office you can access the teaching units, within which enabled users can access the following teaching and support materials: Animations - Data protection - Part 1: a security incident provides an opportunity to reflect on the policies to be applied for effective risk analysis. - Data protection - Part 2: Mrs Safe, an information security expert describes the risks associated with the lack of data protection. Exercise Passing the floor to users: Users will be asked to explain how they would act in the situation presented in the first animation. What measures would be adopted? In what way? And by whom? Poster Activating an awareness campaign is proposed to stimulate interest and promote knowledge on information security. Posters can be used and downloaded from the environment. Game A miniature business game: users are presented with a typical situation, with data and reference values and asked to test themselves in determining the value of a resource. At the end of the game a series of considerations are provided and they can see the correct solution.
9 8 The offices Information Security Room The Information Security Room is the Security Manager s Office, the head of security in the company and concerns information security strategies to define security policies and guidelines. In this section authorized users can access a set of training materials and information on the following topics: Control measures Company Security Monitoring Types of verification Updates In the Information Security Room you can access the teaching units where enabled users can find the following teaching and support materials: Animations - Black Friday - A Black Friday: what consequences could a company face if it does not have specific information security guidelines and policies? In this animation we will see an example. Test Users participate in a fun quiz show and can practice their new skills by answering simple multiple choice questions. - Interview: the company takes on Mrs Safe, an information security consultant, and asks her for a few tips for careful data protection management. Exercise Passing the floor to users: users can explain how they would have behaved in a situation like the one shown in the first animation. What organizational measures should be taken? How should you involve staff? Which aspects should be tackled? From the Information Security Office you can access the Information Security Manager Competency Dictionary
10 9 The offices Information Technology Room The Information Technology Room is the server room, where issues relating to information security within a company are tackled: the use of firewalls, antivirus, back-up systems, operating systems, etc. Authorised users can access documents on company measures at human and technical level. Inside the Information Technology Room, you can also access the teaching unit that allows you to see the following teaching and support materials: Animations - What a mess!: once again, a security incident prompts users to reflect on the importance of creating back-up copies and defining emergency measures. - Copies of back-up: Mrs Safe, the information security expert, explains the reasons that should prompt a company to implement protective measures and create Exercise Passing the floor to users: users will be prompted to specify how a company should behave in making back-up copies, dealing with data loss and preparing a Business Continuity plan. Evaluation Test Users can practice their new skills and consolidate the information received on back-up copies responding to twenty simple multiple choice questions. Glossary List of key terms used in the teaching unit. Users will be able to test and verify the definitions of individual terms, arranged by degree of complexity: beginner, intermediate, advanced.
11 CONFORM Consulenza Formazione e Management S.c.a.r.l. Collina Liguorini Centro Direzionale BdC - Avellino tel: /06/50 fax: [email protected] sito:
Instructions for Registering for a Miradi Account & Installing Miradi Software
 Instructions for Registering for a Miradi Account & Installing Miradi Software www.miradi.org/download Version: March 2015 Introduction The following slides guide users through the process for registering
Instructions for Registering for a Miradi Account & Installing Miradi Software www.miradi.org/download Version: March 2015 Introduction The following slides guide users through the process for registering
Connecting to securevirtual Workspace
 Connecting to securevirtual Workspace The following document provides information on connecting to securevirtual Workspace. This Document includes: Connecting Using Remote Desktop Connection (RDC) Connecting
Connecting to securevirtual Workspace The following document provides information on connecting to securevirtual Workspace. This Document includes: Connecting Using Remote Desktop Connection (RDC) Connecting
METHODOLOGY FOR ASSESSMENT OF NON-FORMAL AND INFORMAL LEARNING ACHIEVEMENTS IN A STUDY PROCESS
 TIMA-Balt Leonardo da Vinci programme project TRANSFER OF INNOVATIVE METHODOLOGY FOR ASSESSMENT OF VET TEACHERS PRIOR LEARNING LLP-LdV-TOI-2007-LT-0004 Contents: Introduction I. Principles II. Prerequisites
TIMA-Balt Leonardo da Vinci programme project TRANSFER OF INNOVATIVE METHODOLOGY FOR ASSESSMENT OF VET TEACHERS PRIOR LEARNING LLP-LdV-TOI-2007-LT-0004 Contents: Introduction I. Principles II. Prerequisites
EMR Link Server Interface Installation
 EMR Link Server Interface Installation Version 1.0 ** INTRODUCTION ** If you would like assistance with installation, please contact our preferred support provider at [email protected], or call
EMR Link Server Interface Installation Version 1.0 ** INTRODUCTION ** If you would like assistance with installation, please contact our preferred support provider at [email protected], or call
Coillte IT has recently upgraded the Remote Access Solution to a new platform.
 Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
Overview Coillte IT has recently upgraded the Remote Access Solution to a new platform. This document explains how to gain access to the Coillte network using your home computer through the new Remote
Internet Security Awareness Program in Georgia funded by ISOC Community Grants Programme
 Internet Security Awareness Program in Georgia funded by ISOC Community Grants Programme Final Report July, 2011 Prepared by David Tabatadze Project Coordinator [email protected] Project Overview With the internet
Internet Security Awareness Program in Georgia funded by ISOC Community Grants Programme Final Report July, 2011 Prepared by David Tabatadze Project Coordinator [email protected] Project Overview With the internet
Cyber Essentials Questionnaire
 Cyber Essentials Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a business enabler rather than a core deliverable.
Cyber Essentials Questionnaire Introduction The Cyber Essentials scheme is recommended for organisations looking for a base level Cyber security test where IT is a business enabler rather than a core deliverable.
Preface No changes of substance have been made in the Framework, Introduction or the IESs.
 International Accounting Education Standards Board International Federation of Accountants 545 Fifth Avenue, 14th Floor New York, New York 10017 USA E-mail: [email protected] Website: http://www.ifac.org
International Accounting Education Standards Board International Federation of Accountants 545 Fifth Avenue, 14th Floor New York, New York 10017 USA E-mail: [email protected] Website: http://www.ifac.org
Grant Proposal Outline
 Once you ve completed your brainstorming worksheet, it is time to start crafting your proposal responses. Follow the prompts in this worksheet to prepare the answers you will need when it comes time to
Once you ve completed your brainstorming worksheet, it is time to start crafting your proposal responses. Follow the prompts in this worksheet to prepare the answers you will need when it comes time to
CREDENTIAL MANAGER IN WINDOWS 7
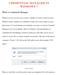 CREDENTIAL MANAGER IN WINDOWS 7 What is Credential Manager Whenever we try to access some resource, whether it is local or remote resource, Windows always validates our credentials to make sure we have
CREDENTIAL MANAGER IN WINDOWS 7 What is Credential Manager Whenever we try to access some resource, whether it is local or remote resource, Windows always validates our credentials to make sure we have
Honours Degree (top-up) Computing Abbreviated Programme Specification Containing Both Core + Supplementary Information
 Honours Degree (top-up) Computing Abbreviated Programme Specification Containing Both Core + Supplementary Information 1 Awarding Institution / body: Lancaster University 2a Teaching institution: University
Honours Degree (top-up) Computing Abbreviated Programme Specification Containing Both Core + Supplementary Information 1 Awarding Institution / body: Lancaster University 2a Teaching institution: University
The following qualifications have had changes made to them to be implemented in 2011.
 CHANGES TO VARIOUS FGASA QUALIFICATIONS The following qualifications have had changes made to them to be implemented in 2011. FGASA Level 1 Nature guide FGASA Level 2 Nature guide FGASA Back-up & Trails
CHANGES TO VARIOUS FGASA QUALIFICATIONS The following qualifications have had changes made to them to be implemented in 2011. FGASA Level 1 Nature guide FGASA Level 2 Nature guide FGASA Back-up & Trails
Translator. Group Central South Consortium Joint Education Service. Learning and Innovation Network for Schools. Division. Section - Sub Section -
 Translator Group Central South Consortium Joint Education Service Division Learning and Innovation Network for Schools Section - Sub Section - Post Title Translator Vision Post Number 12581 Grade Grade
Translator Group Central South Consortium Joint Education Service Division Learning and Innovation Network for Schools Section - Sub Section - Post Title Translator Vision Post Number 12581 Grade Grade
Internet basics 2.3 Protecting your computer
 Basics Use this document with the glossary Beginner s guide to Internet basics 2.3 Protecting your computer How can I protect my computer? This activity will show you how to protect your computer from
Basics Use this document with the glossary Beginner s guide to Internet basics 2.3 Protecting your computer How can I protect my computer? This activity will show you how to protect your computer from
Information Technology Engineers Examination. Information Security Specialist Examination. (Level 4) Syllabus
 Information Technology Engineers Examination Information Security Specialist Examination (Level 4) Syllabus Details of Knowledge and Skills Required for the Information Technology Engineers Examination
Information Technology Engineers Examination Information Security Specialist Examination (Level 4) Syllabus Details of Knowledge and Skills Required for the Information Technology Engineers Examination
HWS Virtual Private Network Configuration and Setup Mac OS X 12/19/2006
 The VPN connection supports mainly access to the HWS network drives, not streaming audio/video or downloading large amounts of data. Contents Before Connecting via VPN Before setting up a Virtual Private
The VPN connection supports mainly access to the HWS network drives, not streaming audio/video or downloading large amounts of data. Contents Before Connecting via VPN Before setting up a Virtual Private
Guide: Using Citrix for Home/ Office
 Guide: Using Citrix for Home/ Office Contents Important information about disconnecting from Citrix 1 How to access Citrix Site 2 How to install Citrix Receiver for Home/ Personal Device (ipad, android
Guide: Using Citrix for Home/ Office Contents Important information about disconnecting from Citrix 1 How to access Citrix Site 2 How to install Citrix Receiver for Home/ Personal Device (ipad, android
Please apply to the DIOS Helpdesk (see Information and communication at the end of this document) for further assistance.
 Student manual FSW Secure Access Portal Faculty of Social and Behavioural Sciences FSW Secure Access Portal The FSW Secure Access Portal (short: Portal) provides safe access from outside to the Faculty
Student manual FSW Secure Access Portal Faculty of Social and Behavioural Sciences FSW Secure Access Portal The FSW Secure Access Portal (short: Portal) provides safe access from outside to the Faculty
Small businesses: What you need to know about cyber security
 Small businesses: What you need to know about cyber security March 2015 Contents page What you need to know about cyber security... 3 Why you need to know about cyber security... 4 Getting the basics right...
Small businesses: What you need to know about cyber security March 2015 Contents page What you need to know about cyber security... 3 Why you need to know about cyber security... 4 Getting the basics right...
Accessing the SUNYIT wireless network for the first time
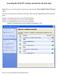 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
PGCert/PGDip/MA Education PGDip/Masters in Teaching and Learning (MTL) Programme Specifications
 PGCert/PGDip/MA Education PGDip/Masters in Teaching and Learning (MTL) Programme Specifications Faculty of Education, Law and Social Sciences School of Education December 2011 Programme Specification PG
PGCert/PGDip/MA Education PGDip/Masters in Teaching and Learning (MTL) Programme Specifications Faculty of Education, Law and Social Sciences School of Education December 2011 Programme Specification PG
Birmingham City University Faculty of Computing, Engineering and the Built Environment. Undergraduate Programme. Programme Specification
 Birmingham City University Faculty of Computing, Engineering and the Built Environment Undergraduate Programme BSc (Hons) Digital Media Technology Date of Course Approval/Review Version Number Version
Birmingham City University Faculty of Computing, Engineering and the Built Environment Undergraduate Programme BSc (Hons) Digital Media Technology Date of Course Approval/Review Version Number Version
extranet.airproducts.com Windows XP Client Configuration
 extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
Document Number: SOP/RAD/SEHSCT/007 Page 1 of 17 Version 2.0
 Standard Operating Procedures (SOPs) Research and Development Office Title of SOP: Computerised Systems for Clinical Trials SOP Number: 7 Version Number: 2.0 Supercedes: 1.0 Effective date: August 2013
Standard Operating Procedures (SOPs) Research and Development Office Title of SOP: Computerised Systems for Clinical Trials SOP Number: 7 Version Number: 2.0 Supercedes: 1.0 Effective date: August 2013
Accessing TP SSL VPN
 Accessing TP SSL VPN This guide describes the steps to install, connect and disconnect the SSL VPN for remote access to TP intranet systems using personal notebooks. A. Installing the SSL VPN client Junos
Accessing TP SSL VPN This guide describes the steps to install, connect and disconnect the SSL VPN for remote access to TP intranet systems using personal notebooks. A. Installing the SSL VPN client Junos
my.airproducts.com Windows Vista Client Configuration
 my.airproducts.com Windows Vista Client Configuration To successfully connect to the Air Products my.airproducts.com website, the client computer needs to have the following three pieces of software installed
my.airproducts.com Windows Vista Client Configuration To successfully connect to the Air Products my.airproducts.com website, the client computer needs to have the following three pieces of software installed
You may have been given a download link on your trial software email. Use this link to download the software.
 BackupVault / Attix5 Server Quickstart Guide This document takes about 5 minutes to read and will show you how to: Download the software Install the Attix5 Professional Backup software Backup your files
BackupVault / Attix5 Server Quickstart Guide This document takes about 5 minutes to read and will show you how to: Download the software Install the Attix5 Professional Backup software Backup your files
Fujitsu Group s Information Security
 Fujitsu Group s Information Under the corporate governance system, the Fujitsu Group promotes appropriate information management and information usage according to Group rules, as part of risk management.
Fujitsu Group s Information Under the corporate governance system, the Fujitsu Group promotes appropriate information management and information usage according to Group rules, as part of risk management.
THE EDINBURGH NAPIER UNIVERSITY WINDOWS VIRTUAL PRIVATE NETWORK (VPN) GUIDE FOR MAC USERS
 THE EDINBURGH NAPIER UNIVERSITY WINDOWS VIRTUAL PRIVATE NETWORK (VPN) GUIDE FOR MAC USERS INTRODUCTION... 2 WHAT SERVICES CAN I ACCESS USING THE VPN?... 2 WHAT ARE THE REQUIREMENTS OF THE VPN SERVICE?...
THE EDINBURGH NAPIER UNIVERSITY WINDOWS VIRTUAL PRIVATE NETWORK (VPN) GUIDE FOR MAC USERS INTRODUCTION... 2 WHAT SERVICES CAN I ACCESS USING THE VPN?... 2 WHAT ARE THE REQUIREMENTS OF THE VPN SERVICE?...
Schools CPD Online General User Guide Contents
 Schools CPD Online General User Guide Contents New user?...2 Access the Site...6 Managing your account in My CPD...8 Searching for events...14 Making a Booking on an Event...20 Tracking events you are
Schools CPD Online General User Guide Contents New user?...2 Access the Site...6 Managing your account in My CPD...8 Searching for events...14 Making a Booking on an Event...20 Tracking events you are
Course overview. CompTIA A+ Certification (Exam 220 902) Official Study Guide (G188eng verdraft)
 Overview This 5-day course is intended for those wishing to qualify with. A+ is a foundation-level certification designed for IT professionals with around 1 year's experience whose job role is focused
Overview This 5-day course is intended for those wishing to qualify with. A+ is a foundation-level certification designed for IT professionals with around 1 year's experience whose job role is focused
National 5 Health Sector: Skills for Work Course Specification
 National 5 Health Sector: Skills for Work Course Specification Valid from August 2013 This edition: August 2013, version 2.0 This specification may be reproduced in whole or in part for educational purposes
National 5 Health Sector: Skills for Work Course Specification Valid from August 2013 This edition: August 2013, version 2.0 This specification may be reproduced in whole or in part for educational purposes
THE WEB-BASED CORE COMPETENCY PROFILE ASSESSMENT TOOL Colleen S. Post and Micheline L. Brunett*
 INTERNATIONAL PUBLIC PROCUREMENT CONFERENCE PROCEEDINGS 21-23 September 2006 THE WEB-BASED CORE COMPETENCY PROFILE ASSESSMENT TOOL Colleen S. Post and Micheline L. Brunett* ABSTRACT. The Professional Development
INTERNATIONAL PUBLIC PROCUREMENT CONFERENCE PROCEEDINGS 21-23 September 2006 THE WEB-BASED CORE COMPETENCY PROFILE ASSESSMENT TOOL Colleen S. Post and Micheline L. Brunett* ABSTRACT. The Professional Development
...1 CITRIX REMOTE ACCESS WINDOWS 7...1 TABLE OF CONTENTS...1 ADDING CITRIX.AKERMAN.COM AS A TRUSTED SITE TO INTERNET EXPLORER 8.0...
 TABLE OF CONTENTS...1 CITRIX REMOTE ACCESS WINDOWS 7...1 TABLE OF CONTENTS...1 ADDING CITRIX.AKERMAN.COM AS A TRUSTED SITE TO INTERNET EXPLORER 8.0...2 INSTALLING THE ENDPOINT ANALYSIS...4 LOGGING OFF
TABLE OF CONTENTS...1 CITRIX REMOTE ACCESS WINDOWS 7...1 TABLE OF CONTENTS...1 ADDING CITRIX.AKERMAN.COM AS A TRUSTED SITE TO INTERNET EXPLORER 8.0...2 INSTALLING THE ENDPOINT ANALYSIS...4 LOGGING OFF
User Guide Online Backup
 User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
Cyber Essentials Scheme
 Cyber Essentials Scheme Requirements for basic technical protection from cyber attacks June 2014 December 2013 Contents Contents... 2 Introduction... 3 Who should use this document?... 3 What can these
Cyber Essentials Scheme Requirements for basic technical protection from cyber attacks June 2014 December 2013 Contents Contents... 2 Introduction... 3 Who should use this document?... 3 What can these
Yale Software Library http://www.yale.edu/software/
 e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, [email protected] Remote Desktop General overview With Remote Desktop, you get full access
e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, [email protected] Remote Desktop General overview With Remote Desktop, you get full access
PROGRAMME SPECIFICATION. BA (Hons) International Business Management
 PROGRAMME SPECIFICATION BA (Hons) International Business Management 1. Awarding institution / body Cardiff Metropolitan University 2. Teaching institution International University College 3. Programme
PROGRAMME SPECIFICATION BA (Hons) International Business Management 1. Awarding institution / body Cardiff Metropolitan University 2. Teaching institution International University College 3. Programme
Elluminate Live! Access Guide. Page 1 of 7
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
Step-by-Step Guide to Securing Windows XP Professional with Service Pack 2 in Small and Medium Businesses
 Step-by-Step Guide to Securing Windows XP Professional with Service Pack 2 in Small and Medium Businesses 2004 Microsoft Corporation. All rights reserved. This document is for informational purposes only.
Step-by-Step Guide to Securing Windows XP Professional with Service Pack 2 in Small and Medium Businesses 2004 Microsoft Corporation. All rights reserved. This document is for informational purposes only.
Online Banking Security Guide Internet-based version
 Online Banking Security Guide Internet-based version Contents Introduction to the Security Guide... 2 Security Guide... 2 Using the internet securely... 2 Security solutions in Online Banking... 3 What
Online Banking Security Guide Internet-based version Contents Introduction to the Security Guide... 2 Security Guide... 2 Using the internet securely... 2 Security solutions in Online Banking... 3 What
Please note that after installation, you can configure the backup, but no backup files will be created until the Server / PC has been restarted.
 How to Configure Shadow Protect and Image Manager with our Cloud Service This guide will walk you through installation of Shadow Protect (SP) and Image Manager (IM), ready to send Offsite to our Cloud
How to Configure Shadow Protect and Image Manager with our Cloud Service This guide will walk you through installation of Shadow Protect (SP) and Image Manager (IM), ready to send Offsite to our Cloud
Money and shopping 8.1 Online banking. Beginner s guide to. Wider interests
 Wider interests Use this document with the glossary Beginner s guide to Money and shopping 8.1 Online banking This activity will help you register to bank online and get you started with your online banking
Wider interests Use this document with the glossary Beginner s guide to Money and shopping 8.1 Online banking This activity will help you register to bank online and get you started with your online banking
How to Install a Network-Licensed Version of IBM SPSS Statistics 19
 How to Install a Network-Licensed Version of IBM SPSS Statistics 19 Important: IBM SPSS Statistics 19 requires either Windows XP Professional or later. IBM SPSS Statistics 19 installs from a DVD and your
How to Install a Network-Licensed Version of IBM SPSS Statistics 19 Important: IBM SPSS Statistics 19 requires either Windows XP Professional or later. IBM SPSS Statistics 19 installs from a DVD and your
User Management Tool 1.5
 User Management Tool 1.5 2014-12-08 23:32:23 UTC 2014 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents User Management Tool 1.5... 3 ShareFile User Management
User Management Tool 1.5 2014-12-08 23:32:23 UTC 2014 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents User Management Tool 1.5... 3 ShareFile User Management
Virtual Training Centers of the I*Teach Project - Continuous learning
 Virtual Training Centers of the I*Teach Project - Continuous learning Malgorzata Miranowicz, Adam Mickiewicz University, Poznan, Poland, [email protected] Gabriella Dodero, Free University of Bozen-Bolzano,
Virtual Training Centers of the I*Teach Project - Continuous learning Malgorzata Miranowicz, Adam Mickiewicz University, Poznan, Poland, [email protected] Gabriella Dodero, Free University of Bozen-Bolzano,
SYLLABUS. Cambridge O Level. Second Language Urdu. For examination in June and November 2016. Cambridge Secondary 2. www.theallpapers.
 SYLLABUS Cambridge O Level Second Language Urdu 3248 For examination in June and November 2016 Cambridge Secondary 2 Changes to syllabus for 2016 This syllabus has been updated, but there are no significant
SYLLABUS Cambridge O Level Second Language Urdu 3248 For examination in June and November 2016 Cambridge Secondary 2 Changes to syllabus for 2016 This syllabus has been updated, but there are no significant
Introduction... 2. Requesting a VPN Account... 2. Accessing the Citrix Access Gateway (CAG)... 3. Tips and Tricks... 9
 NWI Research VPN Basics Table of Contents Introduction... 2 Requesting a VPN Account... 2 Accessing the Citrix Access Gateway (CAG)... 3 Tips and Tricks... 9 Back up Your Favorites and Desktop Folders
NWI Research VPN Basics Table of Contents Introduction... 2 Requesting a VPN Account... 2 Accessing the Citrix Access Gateway (CAG)... 3 Tips and Tricks... 9 Back up Your Favorites and Desktop Folders
POSTGRADUATE PROGRAMME SPECIFICATION
 POSTGRADUATE PROGRAMME SPECIFICATION Programme Title: Awarding Body: Teaching Institution: Masters of Business Administration International (MBA International) Staffordshire University Staffordshire University
POSTGRADUATE PROGRAMME SPECIFICATION Programme Title: Awarding Body: Teaching Institution: Masters of Business Administration International (MBA International) Staffordshire University Staffordshire University
Follow these steps to configure Outlook Express to access your Staffmail email account:
 Windows Instructions (This documentation is based on Outlook Express version 6). Outlook Express is no longer a recommended email client as it can cause unnecessary network traffic and server overload.
Windows Instructions (This documentation is based on Outlook Express version 6). Outlook Express is no longer a recommended email client as it can cause unnecessary network traffic and server overload.
PROGRAMME SPECIFICATION
 MANCHESTER METROPOLITAN UNIVERSITY PS/1 PROGRAMME SPECIFICATION Basic Programme Details 1 Programme title Foundation Degrees in Business 2 Mode(s) and duration Full Time / Part Time - 2 years 3 Awarding
MANCHESTER METROPOLITAN UNIVERSITY PS/1 PROGRAMME SPECIFICATION Basic Programme Details 1 Programme title Foundation Degrees in Business 2 Mode(s) and duration Full Time / Part Time - 2 years 3 Awarding
JOB DESCRIPTION. Head of Learning and Standards. Salary grade: Management Scale 2 + 1
 JOB DESCRIPTION Job Title: Responsible to: Head of Learning and Standards Director of Faculty Salary grade: Management Scale 2 + 1 Hours per week: 21.6 hours per week Main Purpose of the Role 1. To manage
JOB DESCRIPTION Job Title: Responsible to: Head of Learning and Standards Director of Faculty Salary grade: Management Scale 2 + 1 Hours per week: 21.6 hours per week Main Purpose of the Role 1. To manage
PROGRAMME SPECIFICATION
 Programme Specification Section 1: Basic Data Awarding institution/body Teaching institution Faculty responsible for programme University of the West of England University of the West of England Faculty
Programme Specification Section 1: Basic Data Awarding institution/body Teaching institution Faculty responsible for programme University of the West of England University of the West of England Faculty
account multiple solutions
 Start Guide Salary Payments for Sage VIP Payroll & HR 1 Our easy to use guide will get you up and running in no time! Sage Pay allows you to seamlessly transfer your salary payments from Sage VIP Payroll
Start Guide Salary Payments for Sage VIP Payroll & HR 1 Our easy to use guide will get you up and running in no time! Sage Pay allows you to seamlessly transfer your salary payments from Sage VIP Payroll
Quality Assurance in Higher Education
 III.4.7 Decision-making structures Good practices in decision-making suggest: Strong feeling of identity, commitment and responsibility Recognition based on performance criteria Awareness to improve quality
III.4.7 Decision-making structures Good practices in decision-making suggest: Strong feeling of identity, commitment and responsibility Recognition based on performance criteria Awareness to improve quality
STUDY VISITS FOR EDUCATION AND VOCATIONAL TRAINING SPECIALISTS AND DECISION-MAKERS
 Brussels, 31.01.2012 (LLP/NA/DIR/2012/004 Annex-1) STUDY VISITS FOR EDUCATION AND VOCATIONAL TRAINING SPECIALISTS AND DECISION-MAKERS PROGRAMME ANNOUNCEMENT FOR STUDY VISITS IN THE 2012-2013 ACADEMIC YEAR
Brussels, 31.01.2012 (LLP/NA/DIR/2012/004 Annex-1) STUDY VISITS FOR EDUCATION AND VOCATIONAL TRAINING SPECIALISTS AND DECISION-MAKERS PROGRAMME ANNOUNCEMENT FOR STUDY VISITS IN THE 2012-2013 ACADEMIC YEAR
Certificate and Diplomas in ICT Professional Competence (4520-01/02/03/04)
 Certificate and Diplomas in ICT Professional Competence (4520-01/02/03/04) Levels 1-4 unit handbook for centres www.cityandguilds.com July 2011 Version 1.2 (May 2012) About City & Guilds As the UK s leading
Certificate and Diplomas in ICT Professional Competence (4520-01/02/03/04) Levels 1-4 unit handbook for centres www.cityandguilds.com July 2011 Version 1.2 (May 2012) About City & Guilds As the UK s leading
English Language Services
 FROM English Language Services AT A GLANCE work in oz The Work in Oz series explores the world of work through the eyes of Australian workers. The resources include audio and video recordings and learning
FROM English Language Services AT A GLANCE work in oz The Work in Oz series explores the world of work through the eyes of Australian workers. The resources include audio and video recordings and learning
T141 Computer Systems Technician MTCU Code 50505 Program Learning Outcomes
 T141 Computer Systems Technician MTCU Code 50505 Program Learning Outcomes Synopsis of the Vocational Learning Outcomes * The graduate has reliably demonstrated the ability to 1. analyze and resolve information
T141 Computer Systems Technician MTCU Code 50505 Program Learning Outcomes Synopsis of the Vocational Learning Outcomes * The graduate has reliably demonstrated the ability to 1. analyze and resolve information
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Calday Grange Grammar School PERSON SPECIFICATION: TEACHER
 Qualifications 1. Qualified teacher status. a) Commitment to continuing professional development activities Professional Attributes 1. Have high expectations of young people including a commitment to ensuring
Qualifications 1. Qualified teacher status. a) Commitment to continuing professional development activities Professional Attributes 1. Have high expectations of young people including a commitment to ensuring
Using TS-ACCESS for Remote Desktop Access
 Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Elluminate Live! Access Guide. Page 1 of 7
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
Office of elearning & Innovation
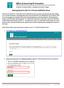 Getting Started with Tri-C Private SoftChalk Cloud Welcome to Private Tri-C SoftChalk Cloud! SoftChalk Cloud is an award winning software that enables you to create interactive web pages that can be incorporated
Getting Started with Tri-C Private SoftChalk Cloud Welcome to Private Tri-C SoftChalk Cloud! SoftChalk Cloud is an award winning software that enables you to create interactive web pages that can be incorporated
Connecting to Remote Desktop Windows Users
 Connecting to Remote Desktop Windows Users How to log into the College Network from Home 1. Start the Remote Desktop Connection For Windows XP, Vista and Windows 7 this is found at:- Star t > All Programs
Connecting to Remote Desktop Windows Users How to log into the College Network from Home 1. Start the Remote Desktop Connection For Windows XP, Vista and Windows 7 this is found at:- Star t > All Programs
RAPID BROADBAND INSTALLATION RAPID BROADBAND SUPPORT CONTACT DETAILS. [email protected] AND TROUBLESHOOTING GUIDE. Email: Tel: 076 6708787
 RAPID BROADBAND INSTALLATION AND TROUBLESHOOTING GUIDE RAPID BROADBAND SUPPORT CONTACT DETAILS Email: [email protected] Tel: 076 6708787 January 2008 1 INTERNET CONNECTION TROUBLESHOOTING GUIDE
RAPID BROADBAND INSTALLATION AND TROUBLESHOOTING GUIDE RAPID BROADBAND SUPPORT CONTACT DETAILS Email: [email protected] Tel: 076 6708787 January 2008 1 INTERNET CONNECTION TROUBLESHOOTING GUIDE
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT
 NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT INSTRUCTION GUIDE For Natural Person Credit Unions NCUA 10200 (REV 4) Table of Contents A. Introduction...
NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT INSTRUCTION GUIDE For Natural Person Credit Unions NCUA 10200 (REV 4) Table of Contents A. Introduction...
Online Document Management Software
 Online Document Management Software We recommend using BOX.NET for this purpose. What is box.net used for in our process: 1. For the client to scan, store, retrieve the documents that needs to be processed
Online Document Management Software We recommend using BOX.NET for this purpose. What is box.net used for in our process: 1. For the client to scan, store, retrieve the documents that needs to be processed
Lecturer in Psychology and Anthropology. A C 20,899-30,948 per annum, pro rata. Head of Sixth Form/ Director of Academic Studies
 Post number: K139 Closing date: 10.00 pm, Sunday 20 th May 2012 Interview date: 28 th May 2012 We are committed to ensuring all individuals are valued and work in a safe environment, promoting the ethos
Post number: K139 Closing date: 10.00 pm, Sunday 20 th May 2012 Interview date: 28 th May 2012 We are committed to ensuring all individuals are valued and work in a safe environment, promoting the ethos
The Standards for Registration: mandatory requirements for Registration with the General Teaching Council for Scotland December 2012
 DRIVING FORWARD PROFESSIONAL STANDARDS FOR TEACHERS The Standards for Registration: mandatory requirements for Registration with the General Teaching Council for Scotland December 2012 Contents Page The
DRIVING FORWARD PROFESSIONAL STANDARDS FOR TEACHERS The Standards for Registration: mandatory requirements for Registration with the General Teaching Council for Scotland December 2012 Contents Page The
BTEC. Edexcel Level 4 BTEC Higher Nationals in Business. Issue 2. September 2004. Edexcel Level 4 BTEC Higher Nationals. Guidance and units.
 BTEC Edexcel Level 4 BTEC Higher Nationals in Business Issue 2 September 2004 Guidance and units Edexcel Level 4 BTEC Higher Nationals Business London Qualifications is one of the leading examining and
BTEC Edexcel Level 4 BTEC Higher Nationals in Business Issue 2 September 2004 Guidance and units Edexcel Level 4 BTEC Higher Nationals Business London Qualifications is one of the leading examining and
How Do I Map a Haas Drive?
 How Do I Map a Haas Drive? Enterprise Computing & Service Management If you are a student, faculty, or staff member at Haas you have shares on the network that you can access both here and at home. Usually
How Do I Map a Haas Drive? Enterprise Computing & Service Management If you are a student, faculty, or staff member at Haas you have shares on the network that you can access both here and at home. Usually
QUALIFICATION HANDBOOK
 QUALIFICATION HANDBOOK Level 2 Extended Certificate in Health Informatics (7450-12) February 2012 Version 1.0 Qualification at a glance Subject area City & Guilds number 7450 Health Informatics Age group
QUALIFICATION HANDBOOK Level 2 Extended Certificate in Health Informatics (7450-12) February 2012 Version 1.0 Qualification at a glance Subject area City & Guilds number 7450 Health Informatics Age group
ABERDARE COMMUNITY SCHOOL
 ABERDARE COMMUNITY SCHOOL IT Security Policy Drafted June 2014 Revised on....... Mrs. S. Davies (Headteacher) Mr. A. Maddox (Chair of Interim Governing Body) IT SECURITY POLICY Review This policy has been
ABERDARE COMMUNITY SCHOOL IT Security Policy Drafted June 2014 Revised on....... Mrs. S. Davies (Headteacher) Mr. A. Maddox (Chair of Interim Governing Body) IT SECURITY POLICY Review This policy has been
(this is being worked on)
 Sault College VPN Access for MAC OS X Introduction This document will describe how to obtain, install and configure the Cisco VPN Client software for MAC OS X. The Cisco CVN Client software will enable
Sault College VPN Access for MAC OS X Introduction This document will describe how to obtain, install and configure the Cisco VPN Client software for MAC OS X. The Cisco CVN Client software will enable
Bucks PSN. Export & Import BLP Mail Mailbox to and from Outlook Data File (.pst) Version 1.0
 Bucks PSN Export & Import BLP Mail Mailbox to and from Outlook Data File (.pst) Version 1.0 Updata Infrastructure Ltd Page 2 of 4 Overview The purpose of this Guide is to provide detailed step by step
Bucks PSN Export & Import BLP Mail Mailbox to and from Outlook Data File (.pst) Version 1.0 Updata Infrastructure Ltd Page 2 of 4 Overview The purpose of this Guide is to provide detailed step by step
PROGRAMME SPECIFICATION. Foundation Degree (Working with Children: Education and Well-Being) Foundation Degree / Foundation Certificate
 PROGRAMME SPECIFICATION Foundation Degree (Working with Children: Education and Well-Being) Awarding institution: Institute of Education, University of London Teaching institution: Institute of Education,
PROGRAMME SPECIFICATION Foundation Degree (Working with Children: Education and Well-Being) Awarding institution: Institute of Education, University of London Teaching institution: Institute of Education,
HND Hospitality Management GG26 16. Course Tutor Guide. October 2012. Version: 02 (October 2015)
 HND Hospitality Management GG26 16 Course Tutor Guide October 2012 Version: 02 (October 2015) History of changes It is anticipated that changes will take place during the life of the qualification, and
HND Hospitality Management GG26 16 Course Tutor Guide October 2012 Version: 02 (October 2015) History of changes It is anticipated that changes will take place during the life of the qualification, and
THE HUMAN COMPONENT OF CYBER SECURITY
 cybersecurity.thalesgroup.com.au People, with their preference to minimise their own inconvenience, their predictability, apathy and general naivety about the potential impacts of their actions, are the
cybersecurity.thalesgroup.com.au People, with their preference to minimise their own inconvenience, their predictability, apathy and general naivety about the potential impacts of their actions, are the
POSTGRADUATE PROGRAMME SPECIFICATION
 POSTGRADUATE PROGRAMME SPECIFICATION Programme Title: Awarding Body: Teaching Institution: Final Awards: MSc International Accounting and Financial Management Staffordshire University Staffordshire University
POSTGRADUATE PROGRAMME SPECIFICATION Programme Title: Awarding Body: Teaching Institution: Final Awards: MSc International Accounting and Financial Management Staffordshire University Staffordshire University
Integrating Trend Micro OfficeScan 10 EventTracker v7.x
 Integrating Trend Micro OfficeScan 10 EventTracker v7.x Publication Date: August 26, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide will help you in
Integrating Trend Micro OfficeScan 10 EventTracker v7.x Publication Date: August 26, 2015 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide will help you in
Course Guide March 2015. Employability. Self Employment. IT and Technology. Changing Gears Level 2 8 Days
 Course Guide March 2015 Employability Changing Gears Level 2 8 Days Our most popular employability course, that s being delivered in Job Centres across Cornwall. Changing Gears is designed to give learners
Course Guide March 2015 Employability Changing Gears Level 2 8 Days Our most popular employability course, that s being delivered in Job Centres across Cornwall. Changing Gears is designed to give learners
Client Installation Guide. Version 6.0 SP1
 Client Installation Guide Version 6.0 SP1 2013 Pitney Bowes Software Inc. All rights reserved. This document may contain confidential and proprietary information belonging to Pitney Bowes Inc. and/or its
Client Installation Guide Version 6.0 SP1 2013 Pitney Bowes Software Inc. All rights reserved. This document may contain confidential and proprietary information belonging to Pitney Bowes Inc. and/or its
Network Setup Instructions
 Network Setup Instructions This document provides technical details for setting up the Elite Salon & Spa Management program in a network environment. If you have any questions, please contact our Technical
Network Setup Instructions This document provides technical details for setting up the Elite Salon & Spa Management program in a network environment. If you have any questions, please contact our Technical
EQF CODE EQF. European Competence Profiles in e-content Professions. http://www.ubique.org/eqfcode
 EQF CODE EQF European Competence Profiles in e-content Professions http://www.ubique.org/eqfcode European Competence Profiles in e-content Professions This project has been funded with support from the
EQF CODE EQF European Competence Profiles in e-content Professions http://www.ubique.org/eqfcode European Competence Profiles in e-content Professions This project has been funded with support from the
Cyber Safety Workshop from CyberSmart! Online PD N/A
 1. Creativity and Innovation Students demonstrate creative thinking, construct knowledge, and develop innovative products and processes using technology. Students: a. apply existing knowledge to generate
1. Creativity and Innovation Students demonstrate creative thinking, construct knowledge, and develop innovative products and processes using technology. Students: a. apply existing knowledge to generate
Galveston College Wireless Network Users Setup Guide Version 1.0
 Galveston College Wireless Network Users Setup Guide Version 1.0 TABLE OF CONTENT 1 DOCUMENT CONTROL RECORD... 3 2 ISSUE AND AMENDMENT RECORD... 3 3 GENERAL... 3 3.1 INTRODUCTION...3 3.2 OBJECTIVE... 3
Galveston College Wireless Network Users Setup Guide Version 1.0 TABLE OF CONTENT 1 DOCUMENT CONTROL RECORD... 3 2 ISSUE AND AMENDMENT RECORD... 3 3 GENERAL... 3 3.1 INTRODUCTION...3 3.2 OBJECTIVE... 3
ITIL Operations Support Analysis (OSA) Certification Program - 5 Days
 ITIL Operations Support Analysis (OSA) Certification Program - 5 Days Program Overview ITIL is a set of best practices guidance that has become a worldwide-adopted framework for Information Technology
ITIL Operations Support Analysis (OSA) Certification Program - 5 Days Program Overview ITIL is a set of best practices guidance that has become a worldwide-adopted framework for Information Technology
Connecting to the Staff Desktop Service
 Connecting to the Staff Desktop Service Access your programs and files just like you were in the office Get Setup The first step to use our Remote Connection service is to check that you have the free
Connecting to the Staff Desktop Service Access your programs and files just like you were in the office Get Setup The first step to use our Remote Connection service is to check that you have the free
