SAP BusinessObjects GRC Access Control 10.0 New Feature Highlights and Initial Lessons Learned
|
|
|
- Briana Lane
- 10 years ago
- Views:
Transcription
1 SAP BusinessObjects GRC Access Control 10.0 New Feature Highlights and Initial Lessons Learned Executive Summary Organizations evaluating technology solutions to enhance their governance, risk and compliance (GRC) processes have an updated offering from SAP to consider: SAP BusinessObjects GRC Access Control version 10.0 (GRC 10.0). This product suite helps risk and compliance teams improve their ability to work with the business by managing risks and controls pervasively and within a single platform. In GRC 10.0, three cornerstone products Access Control (AC), Process Control (PC), and Risk Management (RM) are integrated, allowing for pervasive risk management across business processes and user access provisioning activities by improving key automated monitoring and risk reporting capabilities. The AC product simplifies the remediation and mitigation of segregation of duties (SoD) risk by integrating PC controls and functionality when managing and assigning compensating controls (both automated and manual). AC also allows central management of Firefighter IDs across multiple enterprise resource planning (ERP) systems, streamlines the temporary super-user access log review process by adding workflow capabilities, and enables business concepts within the role design and provisioning process. The PC product simplifies and enhances the process to define and set up automated monitoring of controls and workflow alerts, including monitoring of transactional records and configuration changes. The PC product also provides capabilities around content lifecycle management (CLM), which allows import and export of risk and control libraries across GRC environments. Lastly, the RM product brings risks and controls together by enhancing the integration with AC and PC into a single enterprise risk management platform that provides summarized views representing the different organizational risks and related automated, manual, and security controls from a business process perspective.
2 GRC 10.0 Key Highlights Individuals requesting access changes will experience many enhancements to the AC product in GRC 10.0, such as the ability to include multiple selection criteria in the user access request process (e.g., user group, personnel number, department, and organizational unit information). Additionally, super-users will be able to log their tasks prior to a Firefighter (troubleshooting) session, provide additional comments, and update the troubleshooting reason codes after a session has been completed. A process many companies used to complete manually now has been streamlined. In the past, s were sent to controllers notifying them to review Firefighter activity logs. Companies implemented manual processes (e.g., asking control owners to send an to confirm they had reviewed an activity log) to ensure logs were properly reviewed and documented. Now, in GRC 10.0, Firefighter log reviews can be integrated with workflow approval routes to confirm that Firefighter activity reviewers and approvers have completed their tasks. Furthermore, the GRC 10.0 suite offers multiple integration points between its key cornerstone products. For instance: The ability to mitigate SoD risks with automated or manual controls defined in the PC component. The ability to document and mitigate business process risks by monitoring access to critical business functions. Shared processes, data, and user interface across the GRC 10.0 suite. Key data such as business processes, organizations, and controls will be shared across the AC, PC and RM products. Each solution will run independently; however, in GRC 10.0, the control catalog only needs to be created once and then shared across the suite. What Has Changed? From a technical perspective, SAP has moved from Java programming language to the Advanced Business Application Programming (ABAP) platform, which enables consistent security and standardized configuration settings between GRC 10.0 products. This standardization allows centralized support across all components, and the solution s new platform improves change management processes by leveraging SAP s standard transport system, and background job scheduling and archiving features. As part of the migration to the ABAP platform, SAP has standardized the look and feel of each GRC solution component and further simplified the user experience by creating a single entry point. Another significant enhancement due to moving to the new ABAP platform is the ability to incorporate multistage and multipath (MSMP) workflow configuration into approval routings. This functionality allows for configuration of unlimited approval and review levels, and increased level of detail to define user access and remediation requests. Component names also have been updated to reflect functional processes. Risk Analysis and Remediation (RAR) is now Analyze and Manage Access Risk ; Compliant User Provisioning (CUP) is now referred to as Provision and Manage Users ; Enterprise Role Management (ERM) is now Design and Manage Roles ; and lastly, the Superuser Privilege Management (SPM) component is now defined as Centralized Emergency Access. Protiviti 2
3 Following are some of Protiviti s initial observations regarding the key changes and enhanced functionality of the different components that comprise the GRC 10.0 solution: Analyze and Manage Access Risk Users will experience increased flexibility in analyzing and reviewing SoD and sensitive access exception reports compared to previous versions of the solution. Key improvements include: Ability to filter, save reports and run multiple and custom risk analyses simultaneously; for instance, by user action (transaction code level) and permission (authorization object level, including activity, company code and plant), saving time on risk analysis reporting selection and setup. In previous versions, users could select only one option (i.e., by user action only) when executing a risk analysis. A risk analysis had to be rerun for each report type needed. Crystal Reports is now integrated in the GRC 10.0 solution, enabling report customization and the use of charts and graphs to represent risk analysis. Users also can save risk reports directly as PDF files. SoD simulations for role-level changes also can be expanded to show potential conflicts for all affected users of the role change(s).this is very useful for determining potential access risks when modifying transaction codes and authorization objects within a role. The ability to perform mass mitigation of SoD risks at the user or risk level will allow business users and control owners to experience increased productivity by reducing time spent on mitigating access risks. In previous versions of the GRC suite, mitigation only could be applied to one user across all systems (instead of a subset of systems). The GRC 10.0 solution allows mitigation of entire user populations and across all or subsets of systems, enabling a more efficient way to manage remediation. In addition, mitigating controls for SoD and sensitive access can be defined within the PC product and linked as tests to monitor access risks automatically. Centralized Emergency Access Super-user monitoring capabilities have been moved to a centralized environment on the GRC server and now can be connected to multiple target SAP instances (previously, Firefighter had to be installed and configured for each target system). This allows monitoring of emergency access from one GRC system and streamlining of the administration process. Additionally, GRC 10.0 provides the ability to manage Firefighter IDs by criticality level, resulting in enhanced workflow review and approval routing. Super-user compliance documentation capabilities also have been enhanced. More information is now captured in log files, and Firefighters have the ability to document unplanned activity while Firefighting. Control owners can then directly view the log report (reducing unnecessary clicks while researching Firefighter activity) and reviews can be managed via workflow, providing evidence that the review was completed. Protiviti 3
4 Provision and Manage Users User access provisioning within GRC 10.0 is now similar to directly provisioning an SAP user master record. The user access request form closely mirrors the user master record in SAP and includes fields such as license data, authorization groups, cost centers, accounting numbers, and time zones. Customized templates can be created for user requests to standardize and reduce time to create new requests. New functionality also allows management of role and access changes across multiple user groups. Additionally, the AC product includes some predelivered workflows for user access management; one significant enhancement is the ability to incorporate MSMP workflow configuration into user access approval routings. This functionality allows for unlimited review and approval levels related to user access requests. Design and Manage Roles Non-IT users, including finance, business process owners and compliance resources, can now have a business view to complete the process to review changes to security parameters by enabling a business role review. This review contains a mapping of technical roles (e.g., composite, single, derived roles) to business functions or functional positions. A new impact analysis feature also has been added to proactively assess the full impact of change requests by analyzing potential security issues associated with a role being updated. The role certification process has been enhanced, as well; it now allows role owners to periodically review and confirm role content (i.e., transaction codes) via workflow-driven certification processes. In addition, changes to roles can be tracked after the certification process has been completed, enabling an audit trail to monitor changes. GRC 10.0 Ramp-Up Case Study Protiviti helps organizations evaluate and implement GRC solutions. Recently, we assisted one of our clients an international service organization with more than 14,000 employees and 600 locations worldwide with a new implementation of SAP GRC Our client, which specializes in consulting, testing, certification and training, needed to implement a GRC solution to address significant security issues reported to its executive board by the external auditor in recent years. After evaluating several solutions, the client decided to take part in the GRC 10.0 ramp-up phase to take advantage of newly developed enhancements. The GRC system was installed in a virtual environment to ensure flexibility around sizing and take advantage of the opportunity to deploy other GRC product suite applications (i.e., PC and RM) in the future. The implementation process included technical installation of the solution, and configuration and deployment of the complete GRC AC 10.0 suite, including: Analyze and Manage Access Risk, Provision and Manage Users, Design and Manage Roles, and Centralized Emergency Access. Protiviti 4
5 Project Scope In addition to the technical installation of AC, the project plan included: Workshops with key business process owners to adjust pre-delivered SoD risk levels (high, medium and low) to reflect the company s unique security risks Adjustment of SAP transactions included in the different SoD risk definitions and integrating custom SAP transactions into the customized SoD rule sets Integration and optimization of AC security administration and compliance processes by leveraging AC functionality, including SoD reporting with a customized rule set, workflow optimization, and compliance documentation Project management and coordination among executive management, IT and business teams, including checkpoints with auditors to obtain input regarding adjusted SoD risk levels, the workflow approval process, and related implementation documentation Support activities around the process to mitigate access risks, including: Training on GRC 10.0 functionality and best practices Access risk mitigation by leveraging mass mitigation functionality across multiple ERP components Role redesign performing SoD simulations for role-level changes to determine the impact of removing sensitive or conflicting transactions from SAP roles Initial Lessons Learned Our work in helping our client implement GRC 10.0 gave us many insights into the updated functionality of this enhanced solution. For instance: Known configuration of GRC AC 5.3 (via the configuration tabs) stayed consistent but has been moved into the Implementation Management Guide (IMG), accessed via the SPRO transaction (table maintenance programs). This new feature facilitates configuration; however, some additional time may be required to become familiar with the configuration settings and where they exist within the IMG. Decisions around front-end options should take into account current Basis resources and skills level, the existence of an SAP portal, and the possibility of integrating GRC 10.0 with the portal. GRC 10.0 provides three front-end options for end users: a. NetWeaver Business Client (NWBC) on client-side: This option requires the installation of the SAP Graphical User Interface (GUI) for logon; companies will need to consider the additional Basis skills needed for end user desktop management. b. NWBC on server-side: This option eliminates the need to install the SAP GUI on end user machines, centralizing NWBC administration. c. Portal: This option requires additional installation and configuration of a NetWeaver Java instance. This is an optional interface (used if client prefers accessing GRC via the SAP portal). For the front-end, our client chose to utilize option b, NWBC installed on the server-side, as no additional client software, Basis skills or portal functionality installation were required. Protiviti 5
6 Connectors to target systems need to be created only once for all GRC 10.0 functionality. In prior versions, connectors to target systems had to be created for each GRC component. The GRC system landscape, with its connections to two SAP ERP Central Component (ECC) landscapes (QA and Production), was established within a short period. Workflow functionality is much more flexible than in previous versions of GRC. Several approval scenarios, including multistage approvals, can be built leveraging MSMP workflow functionality (ERP-based). In addition, initiator routing conditions and approvers can be maintained using Business Rules Framework (BRF+), a business rule engine developed in ABAP. It is important to consider that this additional MSMP and BRF+ flexibility might require additional planning time and expert resources to help design and configure efficient approval routes. Standard and initial SoD analysis reports, which were based on GRC 10.0 pre-delivered SoD rules, were available within one week after technical implementation was complete. Reports with customized SoD risks ratings were made available within two weeks after initial setup was complete. Our client has successfully completed the technical setup and SoD risk matrix customization; they are now optimizing security administration processes. This includes the integration of GRC 10.0 functionality within security administration processes and internal controls requirements, as well as mitigation of security risks by assigning mitigating controls and redefining security to remove unnecessary access. Final Considerations If an organization plans to migrate, upgrade or implement GRC 10.0, common system implementation phases and tasks apply. Even though GRC solutions are not as broad as full ERP implementation or upgrade projects, planning, configuration, documentation, and testing are all steps that need to be considered, since it is very likely auditors will review implementation or migration/conversion documentation. Implementation and migration teams also should consider establishing a formal project management office (PMO) structure as part of the implementation team, which should play the role of driving the initiative to successful completion. The PMO s primary responsibilities should include consistent and effective status reporting, issue escalation and management, and should provide a governance structure responsible for integrating implementation tasks and deliverables with compliance and audit requirements. Below are the key GRC Access Control 10.0 implementation phases that should be considered: Risk Assessment: Companies without automated solutions to monitor SAP security risks should consider performing a security diagnostic to help identify key security issues, which will help drive the AC implementation plan. Diagnostics are very useful in identifying quick and easy security fixes that would have a great impact in mitigating security risks and optimizing security administration processes. This phase also will help determine implementation priorities and the need for potential security remediation. Protiviti 6
7 Implementation Planning: During this phase, a requirements analysis should be performed to determine how AC functionality can improve or solve current access issues. This phase should take into consideration process improvements, integration with current security administration and compliance processes and solutions, and technical requirements for the installation. Migration and/or Upgrade Preparation (for Companies Using Previous GRC Versions): This phase involves the technical aspects of upgrades and data migration, if previous GRC versions have been implemented or if non-sap GRC solutions are being replaced. During this phase, Basis resources should prepare the current GRC system to ensure no jobs are pending, open workflow requests are closed and completed, and users are disabled from the GRC application to prevent the creation of new access requests or triggering of jobs during the migration process. AC migration paths are as follows: GRC AC versions 4.0 (ABAP) or 5.3 (Java) can migrate data directly to version 10.0 GRC AC versions 5.2 or earlier will need to perform a technical upgrade to version 5.3 before migrating to version 10.0 Testing: This phase involves defining and documenting testing scripts, including validating expected process improvements. In an ideal scenario, testing scripts should be developed with input from key users who will utilize AC to create or approve access requests or assign mitigating controls. The testing phase should consider the following components: Technical: including system connections, job scheduling, archiving, and other baseline configuration settings Functional: including the sequence of tasks to perform a specific function (e.g., create a user, mitigate a security risk with an automated control, mass mitigation, or workflow approval paths) Integrated: including end-to-end testing scenarios, from when a user requests access through remediation or mitigation of potential security risks Configuration: During this phase, GRC master data, SoD rules and risks, mitigating controls, approval workflows and reports are set up. Go Live: In this phase, users are trained on process enhancements and compliance documentation is updated. Protiviti 7
8 About Protiviti Protiviti ( is a global business consulting and internal audit firm composed of experts specializing in risk, advisory and transaction services. We help solve problems in finance and transactions, operations, technology, litigation, governance, risk, and compliance. Our highly trained, results-oriented professionals provide a unique perspective on a wide range of critical business issues for clients in the Americas, Asia-Pacific, Europe and the Middle East. Protiviti has more than 60 locations worldwide and is a wholly owned subsidiary of Robert Half International Inc. (NYSE symbol: RHI). Founded in 1948, Robert Half International is a member of the S&P 500 index. As the world s leading provider of business software, SAP delivers products and services that enable enterprises of all sizes to improve their business operations. SAP facilitates a company s effort to manage risk and compliance while optimizing efficiency, strategy and growth with a single integrated financial management platform. Addressing business processes in more than 25 industries, SAP has maintained its role as the authority on business software. Protiviti and SAP are actively working together to help clients improve their capability in this important area by implementing and effectively utilizing the full SAP BusinessObjects suite of GRC and EPM solutions to enhance their integrated enterprisewide risk mitigation and compliance efforts. For more information, visit Technology/Managing%20Applications. Protiviti s Information Technology Effectiveness and Control Solutions We partner with chief information officers, chief financial officers and other executives to ensure their organizations maximize the return on information systems investments while at the same time minimizing their risks. Using strong IT governance to ensure alignment with business strategies, we drive excellence through the IT infrastructure and into the supporting applications, data analytics, and security. We also facilitate the selection and development of software, manage the risk of implementation, implement configurable controls on large ERP installations, and implement GRC software applications. For additional information about the issues reviewed in this white paper or Protiviti s services, please contact: Atlanta Aric Quinones Associate Director [email protected] Chicago Gordon Braun Director [email protected] Houston John Harrison Managing Director [email protected] Los Angeles Steve Cabello Managing Director [email protected] New York Carol Raimo Managing Director [email protected] San Francisco Ronan O Shea Managing Director [email protected] 2011 Protiviti Inc. An Equal Opportunity Employer. Protiviti is not licensed or registered as a public accounting firm and does not issue opinions on financial statements or offer attestation services.
Proactive Risk Management with SAP BusinessObjects
 Proactive Risk Management with SAP BusinessObjects Leveraging Technology to Gain Enterprise Transparency and Rapid Insight into Changing Business Conditions INTRODUCTION What is the totality of our enterprise
Proactive Risk Management with SAP BusinessObjects Leveraging Technology to Gain Enterprise Transparency and Rapid Insight into Changing Business Conditions INTRODUCTION What is the totality of our enterprise
Minimize Access Risk and Prevent Fraud With SAP Access Control
 SAP Solution in Detail SAP Solutions for Governance, Risk, and Compliance SAP Access Control Minimize Access Risk and Prevent Fraud With SAP Access Control Table of Contents 3 Quick Facts 4 The Access
SAP Solution in Detail SAP Solutions for Governance, Risk, and Compliance SAP Access Control Minimize Access Risk and Prevent Fraud With SAP Access Control Table of Contents 3 Quick Facts 4 The Access
Process Control Optimisation with SAP
 Process Control Optimisation with SAP The procure-to-pay cycle, which includes all activities from the procurement of goods and services to receiving invoices and paying vendors, is a basic business process.
Process Control Optimisation with SAP The procure-to-pay cycle, which includes all activities from the procurement of goods and services to receiving invoices and paying vendors, is a basic business process.
Overview of SAP BusinessObjects Risk Management 10.0
 Overview of SAP BusinessObjects Risk Management 10.0 Applies to: SAP BusinessObjects Risk Management 10.0, SAP NetWeaver 7.0, Enhancement Package 2. For more information, visit the Governance, Risk, and
Overview of SAP BusinessObjects Risk Management 10.0 Applies to: SAP BusinessObjects Risk Management 10.0, SAP NetWeaver 7.0, Enhancement Package 2. For more information, visit the Governance, Risk, and
Unlocking the Value of Continuous Monitoring and Control Automation Capabilities in SAP Process Control
 Unlocking the Value of Continuous Monitoring and Control Automation Capabilities in SAP Process Control Determining Where and How to Begin an Implementation Introduction Automation of controls is a key
Unlocking the Value of Continuous Monitoring and Control Automation Capabilities in SAP Process Control Determining Where and How to Begin an Implementation Introduction Automation of controls is a key
Security and Your SAP System When Working with Winshuttle Products
 Security and Your SAP System When Working with Winshuttle Products 2014 Winshuttle, LLC. All rights reserved. 2/14 www.winshuttle.com Background Companies running SAP systems are accustomed to configuring
Security and Your SAP System When Working with Winshuttle Products 2014 Winshuttle, LLC. All rights reserved. 2/14 www.winshuttle.com Background Companies running SAP systems are accustomed to configuring
How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions
 How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions Introduction This paper provides an overview of the integrated solution and a summary of implementation options
How to leverage SAP NetWeaver Identity Management and SAP Access Control combined solutions Introduction This paper provides an overview of the integrated solution and a summary of implementation options
Continuous Monitoring and Auditing: What is the difference? By John Verver, ACL Services Ltd.
 Continuous Monitoring and Auditing: What is the difference? By John Verver, ACL Services Ltd. Call them the twin peaks of continuity continuous auditing and continuous monitoring. There are certainly similarities
Continuous Monitoring and Auditing: What is the difference? By John Verver, ACL Services Ltd. Call them the twin peaks of continuity continuous auditing and continuous monitoring. There are certainly similarities
High Value Audits: An Update on Information Technology Auditing. Robert B. Hirth Jr., Managing Director
 High Value Audits: An Update on Information Technology Auditing Robert B. Hirth Jr., Managing Director The technology landscape and its impact on internal audit Technology is playing an ever-growing role
High Value Audits: An Update on Information Technology Auditing Robert B. Hirth Jr., Managing Director The technology landscape and its impact on internal audit Technology is playing an ever-growing role
AC 10.0 Centralized Emergency Access
 AC 10.0 Centralized Emergency Access Customer Solution Adoption June 2011 Version 2.0 Purpose of this document This document is a detailed guide on the emergency access capability of Access Control 10.0.
AC 10.0 Centralized Emergency Access Customer Solution Adoption June 2011 Version 2.0 Purpose of this document This document is a detailed guide on the emergency access capability of Access Control 10.0.
BUSINESS-DRIVEN, COMPLIANT IDENTITY MANAGEMENT USING SAP NetWeaver IDENTITY MANAGEMENT
 Solution in Detail NetWeaver BUSINESS-DRIVEN, COMPLIANT IDENTITY MANAGEMENT USING NetWeaver IDENTITY MANAGEMENT Identity management today presents organizations with a host of challenges. System landscapes
Solution in Detail NetWeaver BUSINESS-DRIVEN, COMPLIANT IDENTITY MANAGEMENT USING NetWeaver IDENTITY MANAGEMENT Identity management today presents organizations with a host of challenges. System landscapes
Business-Driven, Compliant Identity Management
 Solution in Detail NetWeaver NetWeaver Identity Business-Driven, Compliant Identity Using NetWeaver Identity Managing users in heterogeneous IT landscapes presents many challenges for organizations. System
Solution in Detail NetWeaver NetWeaver Identity Business-Driven, Compliant Identity Using NetWeaver Identity Managing users in heterogeneous IT landscapes presents many challenges for organizations. System
SAP Standard for Security
 SAP Standard for E2E Solution Operations Document Version: 1.0 2014-12-12 SAP Solution Manager 7.1 Typographic Conventions Type Style Example Description Words or characters quoted from the screen. These
SAP Standard for E2E Solution Operations Document Version: 1.0 2014-12-12 SAP Solution Manager 7.1 Typographic Conventions Type Style Example Description Words or characters quoted from the screen. These
Business-Driven, Compliant Identity Management
 SAP Solution in Detail SAP NetWeaver SAP Identity Management Business-Driven, Compliant Identity Management Table of Contents 3 Quick Facts 4 Business Challenges: Managing Costs, Process Change, and Compliance
SAP Solution in Detail SAP NetWeaver SAP Identity Management Business-Driven, Compliant Identity Management Table of Contents 3 Quick Facts 4 Business Challenges: Managing Costs, Process Change, and Compliance
Moving Forward with IT Governance and COBIT
 Moving Forward with IT Governance and COBIT Los Angeles ISACA COBIT User Group Tuesday 27, March 2007 IT GRC Questions from the CIO Today s discussion focuses on the typical challenges facing the CIO around
Moving Forward with IT Governance and COBIT Los Angeles ISACA COBIT User Group Tuesday 27, March 2007 IT GRC Questions from the CIO Today s discussion focuses on the typical challenges facing the CIO around
AC 10.0 Customizing Workflows for Access Management
 AC 10.0 Customizing Workflows for Access Management Customer Solution Adoption June 2011 Version 2.0 Purpose of this document This document allows implementation consultants and administrators to setup
AC 10.0 Customizing Workflows for Access Management Customer Solution Adoption June 2011 Version 2.0 Purpose of this document This document allows implementation consultants and administrators to setup
IT Service Continuity Management PinkVERIFY
 -11-G-001 General Criteria Does the tool use ITIL 2011 Edition process terms and align to ITIL 2011 Edition workflows and process integrations? -11-G-002 Does the tool have security controls in place to
-11-G-001 General Criteria Does the tool use ITIL 2011 Edition process terms and align to ITIL 2011 Edition workflows and process integrations? -11-G-002 Does the tool have security controls in place to
Best Practices Report
 Overview As an IT leader within your organization, you face new challenges every day from managing user requirements and operational needs to the burden of IT Compliance. Developing a strong IT general
Overview As an IT leader within your organization, you face new challenges every day from managing user requirements and operational needs to the burden of IT Compliance. Developing a strong IT general
PRECANT CONSULTING PRIVATE LIMITED. Sales Office: No. 17, Inhwa Business Centre, IRIS Tech Park, Gurgaon.
 PRECANT CONSULTING PRIVATE LIMITED Sales Office: No. 17, Inhwa Business Centre, IRIS Tech Park, Gurgaon. Development Center: D-77, Sector 63, Noida-201301. Phone +91 120 4313630 (India) Mobile +91 91 9910210572,
PRECANT CONSULTING PRIVATE LIMITED Sales Office: No. 17, Inhwa Business Centre, IRIS Tech Park, Gurgaon. Development Center: D-77, Sector 63, Noida-201301. Phone +91 120 4313630 (India) Mobile +91 91 9910210572,
How To Get A Tech Startup To Comply With Regulations
 Agile Technology Controls for Startups a Contradiction in Terms or a Real Opportunity? Implementing Dynamic, Flexible and Continuously Optimized IT General Controls POWERFUL INSIGHTS Issue It s not a secret
Agile Technology Controls for Startups a Contradiction in Terms or a Real Opportunity? Implementing Dynamic, Flexible and Continuously Optimized IT General Controls POWERFUL INSIGHTS Issue It s not a secret
Designing NetSuite ERP Application Security Leveraging Fastpath Assure Access Monitoring Solutions
 Designing NetSuite ERP Application Security Leveraging Fastpath Assure Access Monitoring Solutions Introduction Defining NetSuite security requirements in the early phase of an implementation, upgrade
Designing NetSuite ERP Application Security Leveraging Fastpath Assure Access Monitoring Solutions Introduction Defining NetSuite security requirements in the early phase of an implementation, upgrade
Solution Manager: What Is It & What Can It Do for Your Business? A Solution Overview written by Ken Asher, Sr. SAP Architect
 Solution Manager: What Is It & What Can It Do for Your Business? A Solution Overview written by Ken Asher, Sr. SAP Architect Are you considering implementing additional functionality within Solution Manager?
Solution Manager: What Is It & What Can It Do for Your Business? A Solution Overview written by Ken Asher, Sr. SAP Architect Are you considering implementing additional functionality within Solution Manager?
Manage and Control Access Risk and Assess Its Financial Impact
 SAP Brief Extensions SAP Access Violation Management by Greenlight Objectives Manage and Control Access Risk and Assess Its Financial Impact Make access control decisions based on business impact Make
SAP Brief Extensions SAP Access Violation Management by Greenlight Objectives Manage and Control Access Risk and Assess Its Financial Impact Make access control decisions based on business impact Make
SAP Change Control - One Integrated Process to Manage Software Solution Deployments SAP AG
 SAP Change Control - One Integrated Process to Manage Software Solution Deployments SAP AG Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase
SAP Change Control - One Integrated Process to Manage Software Solution Deployments SAP AG Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase
Introducing SAP s Landscape and Data Center Innovation Platform. Phil Jackson SAP Solution Engineer
 Introducing SAP s Landscape and Data Center Innovation Platform Phil Jackson SAP Solution Engineer CIO challenges Business Agility & Innovation Business Continuity Cost Containment Hybrid On-premise, Virtual
Introducing SAP s Landscape and Data Center Innovation Platform Phil Jackson SAP Solution Engineer CIO challenges Business Agility & Innovation Business Continuity Cost Containment Hybrid On-premise, Virtual
Application Management Services (AMS)
 Contents 1. AMS : An Overview 2. AMS : Models 3. Delivery Organization 4. Processes & Tools 5. Transition Methodology 6. Pricing Application Management Services (AMS) Enterprise Application Services Capability
Contents 1. AMS : An Overview 2. AMS : Models 3. Delivery Organization 4. Processes & Tools 5. Transition Methodology 6. Pricing Application Management Services (AMS) Enterprise Application Services Capability
Application Control Effectiveness for SAP. December 2007
 Application Control Effectiveness for SAP December 2007 Meeting Objectives Application Control Effectiveness Compliance at a glance Trends and challenges Technology issues Application Control Business
Application Control Effectiveness for SAP December 2007 Meeting Objectives Application Control Effectiveness Compliance at a glance Trends and challenges Technology issues Application Control Business
..making process automation a business priority..
 ..making process automation a business priority.. Why do our customers run promentawebflow TM? It provides a solution platform to drive SAP process automation Enable the web based automation of any SAP
..making process automation a business priority.. Why do our customers run promentawebflow TM? It provides a solution platform to drive SAP process automation Enable the web based automation of any SAP
COMPLIANCE MANAGEMENT SOLUTIONS THOMSON REUTERS ACCELUS COMPLIANCE MANAGEMENT SOLUTIONS
 THOMSON REUTERS ACCELUS COMPLIANCE MANAGEMENT SOLUTIONS THOMSON REUTERS ACCELUS Our solutions dynamically connect business transactions, strategy, and operations to the ever-changing regulatory environment,
THOMSON REUTERS ACCELUS COMPLIANCE MANAGEMENT SOLUTIONS THOMSON REUTERS ACCELUS Our solutions dynamically connect business transactions, strategy, and operations to the ever-changing regulatory environment,
How Accenture is taking SAP NetWeaver Identity Management to the next level. Kristian Lehment, SAP AG Matthew Pecorelli, Accenture
 How Accenture is taking SAP NetWeaver Identity Management to the next level Kristian Lehment, SAP AG Matthew Pecorelli, Accenture In This Session You will receive an overview of the functionality that
How Accenture is taking SAP NetWeaver Identity Management to the next level Kristian Lehment, SAP AG Matthew Pecorelli, Accenture In This Session You will receive an overview of the functionality that
ERP Implementation Risk: Identifying, Monitoring and Remediating Issues Throughout the Project to Ensure Success
 ERP Implementation Risk: Identifying, Monitoring and Remediating Issues Throughout the Project to Ensure Success Introduction From hardware and software implementation to support services, organizations
ERP Implementation Risk: Identifying, Monitoring and Remediating Issues Throughout the Project to Ensure Success Introduction From hardware and software implementation to support services, organizations
Fraud Prevention and Detection in a Manufacturing Environment
 Fraud Prevention and Detection in a Manufacturing Environment Introduction The Association of Certified Fraud Examiners (ACFE) estimated in its 2008 Report to the Nation on Occupational Fraud and Abuse
Fraud Prevention and Detection in a Manufacturing Environment Introduction The Association of Certified Fraud Examiners (ACFE) estimated in its 2008 Report to the Nation on Occupational Fraud and Abuse
theguard! SmartChange Intelligent SAP change management think big, change SMART!
 theguard! SmartChange Intelligent SAP change management think big, change SMART! theguard! SmartChange theguard! SmartChange takes an intelligent SAP change management approach. It provides maximum automation,
theguard! SmartChange Intelligent SAP change management think big, change SMART! theguard! SmartChange theguard! SmartChange takes an intelligent SAP change management approach. It provides maximum automation,
SAP GRC Superuser Privilege Management
 SAP GRC Superuser Privilège Management September 26, 2007 English SAP GRC Superuser Privilege Management Business Scenario Script for Discovery System version 3 SAP AG Neurottstr. 16 69190 Walldorf Germany
SAP GRC Superuser Privilège Management September 26, 2007 English SAP GRC Superuser Privilege Management Business Scenario Script for Discovery System version 3 SAP AG Neurottstr. 16 69190 Walldorf Germany
Compliance & SAP Security. Secure SAP applications based on state-of-the-art user & system concepts. Driving value with IT
 Compliance & SAP Security Secure SAP applications based on state-of-the-art user & system concepts Driving value with IT BO Access Control Authorization Workflow Central User Management Encryption Data
Compliance & SAP Security Secure SAP applications based on state-of-the-art user & system concepts Driving value with IT BO Access Control Authorization Workflow Central User Management Encryption Data
EIM264 Flexible Governance Govern Your Own Objects in SAP Master Data Governance
 EIM264 Flexible Governance Govern Your Own Objects in SAP Master Data Governance Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase decision.
EIM264 Flexible Governance Govern Your Own Objects in SAP Master Data Governance Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase decision.
Expert Tips To Simplify And Automate Your User Access Request Process David Denson PwC
 Expert Tips To Simplify And Automate Your User Access Request Process David Denson PwC IN THIS SESSION In this session, we will discuss effective strategies that have been utilized at other implementations
Expert Tips To Simplify And Automate Your User Access Request Process David Denson PwC IN THIS SESSION In this session, we will discuss effective strategies that have been utilized at other implementations
Designing SAP Application Security Leveraging SAP Access Monitoring Solutions During SAP Implementations, Upgrades or Security Redesign Projects
 Designing SAP Application Security Leveraging SAP Access Monitoring Solutions During SAP Implementations, Upgrades or Security Redesign Projects Introduction DEFINING SAP SECURITY REQUIREMENTS IN THE EARLY
Designing SAP Application Security Leveraging SAP Access Monitoring Solutions During SAP Implementations, Upgrades or Security Redesign Projects Introduction DEFINING SAP SECURITY REQUIREMENTS IN THE EARLY
Reduce Audit Time Using Automation, By Example. Jay Gohil Senior Manager
 Reduce Audit Time Using Automation, By Example Jay Gohil Senior Manager Today s Session Speaker Bio: Jay Gohil, Protiviti Jay is a Senior Manager in the ERP Services practice in Atlanta. In the past seven
Reduce Audit Time Using Automation, By Example Jay Gohil Senior Manager Today s Session Speaker Bio: Jay Gohil, Protiviti Jay is a Senior Manager in the ERP Services practice in Atlanta. In the past seven
effective performance monitoring in SAP environments
 WHITE PAPER September 2012 effective performance monitoring in SAP environments Key challenges and how CA Nimsoft Monitor helps address them agility made possible table of contents executive summary 3
WHITE PAPER September 2012 effective performance monitoring in SAP environments Key challenges and how CA Nimsoft Monitor helps address them agility made possible table of contents executive summary 3
ORACLE APPLICATION ACCESS CONTROLS GOVERNOR FOR PEOPLESOFT
 ORACLE APPLICATION ACCESS CONTROLS GOVERNOR FOR PEOPLESOFT KEY FEATURES Continuously monitors application users access from high-level ERP roles and permissions to detailed access points 550 + Delivered,
ORACLE APPLICATION ACCESS CONTROLS GOVERNOR FOR PEOPLESOFT KEY FEATURES Continuously monitors application users access from high-level ERP roles and permissions to detailed access points 550 + Delivered,
SAP Solution in Detail SAP NetWeaver SAP NetWeaver Identity Management. Business-Driven, Compliant Identity Management
 Solution in Detail NetWeaver Business-Driven, Compliant Identity Table of Contents 3 Quick Facts 4 Business Challenges Identity for the User Lifecycle 5 The Solution Supporting a Heterogeneous IT Landscape
Solution in Detail NetWeaver Business-Driven, Compliant Identity Table of Contents 3 Quick Facts 4 Business Challenges Identity for the User Lifecycle 5 The Solution Supporting a Heterogeneous IT Landscape
Identity and Access Management Integration with PowerBroker. Providing Complete Visibility and Auditing of Identities
 Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Enterprise Information Management Services Managing Your Company Data Along Its Lifecycle
 SAP Solution in Detail SAP Services Enterprise Information Management Enterprise Information Management Services Managing Your Company Data Along Its Lifecycle Table of Contents 3 Quick Facts 4 Key Services
SAP Solution in Detail SAP Services Enterprise Information Management Enterprise Information Management Services Managing Your Company Data Along Its Lifecycle Table of Contents 3 Quick Facts 4 Key Services
Smart Operations Management Suite
 Lifecycle Services for Syncade Operations Smart Operations Management Suite Service Data Sheet Lifecycle Services for Syncade Operations Smart Operations Management Suite Offering the Right Service at
Lifecycle Services for Syncade Operations Smart Operations Management Suite Service Data Sheet Lifecycle Services for Syncade Operations Smart Operations Management Suite Offering the Right Service at
Frequently Asked Questions
 Table of contents 1. Agent Technology...3 1.1. Has the Knoa agent been tested with standard set of services on the PC?... 3 1.2. Do users need to do anything to activate the Agent?...3 1.3. Does the Knoa
Table of contents 1. Agent Technology...3 1.1. Has the Knoa agent been tested with standard set of services on the PC?... 3 1.2. Do users need to do anything to activate the Agent?...3 1.3. Does the Knoa
How To Ensure Financial Compliance
 Evolving from Financial Compliance to Next Generation GRC Gary Prince Principal Solution Specialist - GRC Agenda Business Challenges Oracle s Leadership in Governance, Risk and Compliance Solution Overview
Evolving from Financial Compliance to Next Generation GRC Gary Prince Principal Solution Specialist - GRC Agenda Business Challenges Oracle s Leadership in Governance, Risk and Compliance Solution Overview
SAP Project Portfolio Monitoring Rapid- Deployment Solution: Software Requirements
 SAP Portfolio and Project Management 5.0 July 2013 English SAP Project Portfolio Monitoring Rapid- Deployment Solution: SAP AG Dietmar-Hopp-Allee 16 69190 Walldorf Germany Copyright 2013 SAP AG or an SAP
SAP Portfolio and Project Management 5.0 July 2013 English SAP Project Portfolio Monitoring Rapid- Deployment Solution: SAP AG Dietmar-Hopp-Allee 16 69190 Walldorf Germany Copyright 2013 SAP AG or an SAP
Fixed Scope Offering for Implementation of Sales Cloud & Sales Cloud Integration With GTS Property Extensions
 Fixed Scope Offering for Implementation of Sales Cloud & Sales Cloud Integration With GTS Property Extensions Today s Business Challenges Adopt leading CRM practices and stream line processes Take advantage
Fixed Scope Offering for Implementation of Sales Cloud & Sales Cloud Integration With GTS Property Extensions Today s Business Challenges Adopt leading CRM practices and stream line processes Take advantage
Audit Compliance and Internal Audit Analysis for Dynamics
 Fastpath Audit Compliance and Internal Audit Analysis for Dynamics: Better Audit Results with a Reliable, Repeatable Process using Fastpath Fastpath 11107 Aurora Ave. Urbandale, IA 50322 (515) 276-1779
Fastpath Audit Compliance and Internal Audit Analysis for Dynamics: Better Audit Results with a Reliable, Repeatable Process using Fastpath Fastpath 11107 Aurora Ave. Urbandale, IA 50322 (515) 276-1779
Capital Projects and Construction: Building in Risk Management and Project Controls
 Capital Projects and Construction: Building in Risk Management and Project Controls Making Every Dollar Count The global economic crisis sparked by the subprime mortgage debacle, the collapse of the securitized
Capital Projects and Construction: Building in Risk Management and Project Controls Making Every Dollar Count The global economic crisis sparked by the subprime mortgage debacle, the collapse of the securitized
rating of 5 out 5 stars
 SPM User Guide Contents Aegify comprehensive benefits... 2 Security Posture Assessment workflow... 3 Scanner Management... 3 Upload external scan output... 6 Reports - Views... 6 View Individual Security
SPM User Guide Contents Aegify comprehensive benefits... 2 Security Posture Assessment workflow... 3 Scanner Management... 3 Upload external scan output... 6 Reports - Views... 6 View Individual Security
Security management White paper. Develop effective user management to demonstrate compliance efforts and achieve business value.
 Security management White paper Develop effective user management to demonstrate compliance efforts and achieve business value. September 2008 2 Contents 2 Overview 3 Understand the challenges of user
Security management White paper Develop effective user management to demonstrate compliance efforts and achieve business value. September 2008 2 Contents 2 Overview 3 Understand the challenges of user
Maximizing your SAP ERP
 950 Tower Lane, Suite 750 Foster City, CA 94404 650.341.3310 phone 650.341.3610 fax www.guixt.com Maximizing your SAP ERP Desktop Suite GuiXT Portal Suite Web UI Suite Mobile Suite Offline Suite Developer
950 Tower Lane, Suite 750 Foster City, CA 94404 650.341.3310 phone 650.341.3610 fax www.guixt.com Maximizing your SAP ERP Desktop Suite GuiXT Portal Suite Web UI Suite Mobile Suite Offline Suite Developer
VBLOCK SOLUTION FOR SAP APPLICATION SERVER ELASTICITY
 Vblock Solution for SAP Application Server Elasticity Table of Contents www.vce.com VBLOCK SOLUTION FOR SAP APPLICATION SERVER ELASTICITY Version 2.0 February 2013 1 Copyright 2013 VCE Company, LLC. All
Vblock Solution for SAP Application Server Elasticity Table of Contents www.vce.com VBLOCK SOLUTION FOR SAP APPLICATION SERVER ELASTICITY Version 2.0 February 2013 1 Copyright 2013 VCE Company, LLC. All
How To Manage Work Mode On An It Calendar On An Apa System
 SAP Solution Manager 7.1 Technical Administration Work Center Setup Q2, 2011 Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase decision.
SAP Solution Manager 7.1 Technical Administration Work Center Setup Q2, 2011 Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase decision.
What s New Guide: Version 5.6
 What s New Guide: Version 5.6 A QUEST SOFTWARE COMPANY 1. 8 0 0. 4 2 4. 9 4 1 1 w w w. s c r i p t l o g i c. c o m WHAT S NEW IN ACTIVE ADMINISTRATOR 5.6? Contents...3 Active Administrator Product Overview...3
What s New Guide: Version 5.6 A QUEST SOFTWARE COMPANY 1. 8 0 0. 4 2 4. 9 4 1 1 w w w. s c r i p t l o g i c. c o m WHAT S NEW IN ACTIVE ADMINISTRATOR 5.6? Contents...3 Active Administrator Product Overview...3
How To Use Ibm Tivoli Monitoring Software
 Monitor and manage critical resources and metrics across disparate platforms from a single console IBM Tivoli Monitoring Highlights Help improve uptime and shorten Help optimize IT service delivery by
Monitor and manage critical resources and metrics across disparate platforms from a single console IBM Tivoli Monitoring Highlights Help improve uptime and shorten Help optimize IT service delivery by
Security Information & Event Management A Best Practices Approach
 Security Information & Event Management A Best Practices Approach Implementing a best-of-class IT compliance framework using iservice help desk and EventSentry monitoring software A white paper written
Security Information & Event Management A Best Practices Approach Implementing a best-of-class IT compliance framework using iservice help desk and EventSentry monitoring software A white paper written
Governance, Risk & Compliance for Public Sector
 Governance, Risk & Compliance for Public Sector Steve Hagner EMEA GRC Solution Sales From egovernment to Oracle igovernment Increase Efficiency and Transparency Oracle igovernment
Governance, Risk & Compliance for Public Sector Steve Hagner EMEA GRC Solution Sales From egovernment to Oracle igovernment Increase Efficiency and Transparency Oracle igovernment
State of Oregon. State of Oregon 1
 State of Oregon State of Oregon 1 Table of Contents 1. Introduction...1 2. Information Asset Management...2 3. Communication Operations...7 3.3 Workstation Management... 7 3.9 Log management... 11 4. Information
State of Oregon State of Oregon 1 Table of Contents 1. Introduction...1 2. Information Asset Management...2 3. Communication Operations...7 3.3 Workstation Management... 7 3.9 Log management... 11 4. Information
Bank Account Management(J77_US)
 Test Script SAP S/4HANA November 2015 PUBLIC Content 1 Purpose of the Document....5 1.1 Purpose of Bank Account Management.... 5 2 Prerequisites.... 6 2.1 System Access....6 2.2 Roles....6 2.3 Master Data,
Test Script SAP S/4HANA November 2015 PUBLIC Content 1 Purpose of the Document....5 1.1 Purpose of Bank Account Management.... 5 2 Prerequisites.... 6 2.1 System Access....6 2.2 Roles....6 2.3 Master Data,
IT Service Management by SAP Africa (ITSM) Dirk Smit ALM Engagement Manager
 IT Service Management by SAP Africa (ITSM) Dirk Smit ALM Engagement Manager Optimize IT Operations Process Support Business Goals CIO CEO/CFO Reliable Business Support Changes to improve IT services are
IT Service Management by SAP Africa (ITSM) Dirk Smit ALM Engagement Manager Optimize IT Operations Process Support Business Goals CIO CEO/CFO Reliable Business Support Changes to improve IT services are
Overview. Microsoft Office Enterprise Project Management Solution. In this article
 Microsoft Office Enterprise Project Management Solution Overview Applies to: Microsoft Office Project 2007 Project Server 2007 In this article Manage and control all types of work Improve visibility and
Microsoft Office Enterprise Project Management Solution Overview Applies to: Microsoft Office Project 2007 Project Server 2007 In this article Manage and control all types of work Improve visibility and
SAP Archiving and SAP Document Access
 SAP Solution in Detail SAP ERP SAP Archiving and SAP Document Access Streamline the Process of Upgrading SAP ERP The process of upgrading to the SAP ERP 6.0 application can be streamlined by using archiving
SAP Solution in Detail SAP ERP SAP Archiving and SAP Document Access Streamline the Process of Upgrading SAP ERP The process of upgrading to the SAP ERP 6.0 application can be streamlined by using archiving
SAP NetWeaver Information Lifecycle Management
 SAP NetWeaver Information Lifecycle Management What s New in Release 7.03 and Future Direction June 2012 SAP NetWeaver Information Lifecycle Management Information lifecycle management Retention management
SAP NetWeaver Information Lifecycle Management What s New in Release 7.03 and Future Direction June 2012 SAP NetWeaver Information Lifecycle Management Information lifecycle management Retention management
Financial Close Optimization: Five Steps for Identifying and Resolving Systems and Process Inefficiencies
 Financial Close Optimization: Five Steps for Identifying and Resolving Systems and Process Inefficiencies Introduction A recent survey by the Institute of Management Accountants found that financial closing
Financial Close Optimization: Five Steps for Identifying and Resolving Systems and Process Inefficiencies Introduction A recent survey by the Institute of Management Accountants found that financial closing
Dell Active Administrator 8.0
 What s new in Dell Active Administrator 8.0 January 2016 Dell Active Administrator 8.0 is the upcoming release of Dell Software's complete solution for managing Microsoft Active Directory security auditing,
What s new in Dell Active Administrator 8.0 January 2016 Dell Active Administrator 8.0 is the upcoming release of Dell Software's complete solution for managing Microsoft Active Directory security auditing,
Organizational IT Concepts and SAP Solution Manager. General IT operations and service concepts with SAP Solution Manager. Driving value with IT
 Organizational IT Concepts and SAP Solution Manager General IT operations and service concepts with SAP Solution Manager Driving value with IT How SAP customers can benefit from REALTECH s Solution Manager
Organizational IT Concepts and SAP Solution Manager General IT operations and service concepts with SAP Solution Manager Driving value with IT How SAP customers can benefit from REALTECH s Solution Manager
Intelligent Inventory and Professional License Management
 Intelligent Inventory and Professional License Management RayVentory is part of RaySuite. Smarter Software and Hardware Inventory Top Benefits Various collection methods Agent-based and agentless inventory
Intelligent Inventory and Professional License Management RayVentory is part of RaySuite. Smarter Software and Hardware Inventory Top Benefits Various collection methods Agent-based and agentless inventory
Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid clouds.
 ENTERPRISE MONITORING & LIFECYCLE MANAGEMENT Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
ENTERPRISE MONITORING & LIFECYCLE MANAGEMENT Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
EMC DOCUMENTUM XCP Accelerate the development of custom content-enabled solutions to support case management
 EMC DOCUMENTUM XCP Accelerate the development of custom content-enabled solutions to support case management ESSENTIALS For IT: Accelerate the application lifecycle and decrease deployment complexity Eliminate
EMC DOCUMENTUM XCP Accelerate the development of custom content-enabled solutions to support case management ESSENTIALS For IT: Accelerate the application lifecycle and decrease deployment complexity Eliminate
SAP Standard for Data Volume Management
 SAP Standard for E2E Solution Operations Document Version: 1.0 2014-12-12 SAP Solution Manager 7.1 Typographic Conventions Type Style Example Description Words or characters quoted from the screen. These
SAP Standard for E2E Solution Operations Document Version: 1.0 2014-12-12 SAP Solution Manager 7.1 Typographic Conventions Type Style Example Description Words or characters quoted from the screen. These
SAP Learning Hub: Learning Rooms. List of available and upcoming learning rooms as of March 2015
 SAP Learning Hub: Learning Rooms List of available and upcoming learning rooms as of March 2015 Learning Rooms Learning Rooms are expert-moderated social learning components within SAP Learning Hub. They
SAP Learning Hub: Learning Rooms List of available and upcoming learning rooms as of March 2015 Learning Rooms Learning Rooms are expert-moderated social learning components within SAP Learning Hub. They
WHITE PAPER. iet ITSM Enables Enhanced Service Management
 iet ITSM Enables Enhanced Service Management iet ITSM Enables Enhanced Service Management Need for IT Service Management The focus within the vast majority of large and medium-size companies has shifted
iet ITSM Enables Enhanced Service Management iet ITSM Enables Enhanced Service Management Need for IT Service Management The focus within the vast majority of large and medium-size companies has shifted
How To Use Sap Business Objects For Microsoft (For Microsoft) For Microsoft (For Pax) For Pax (For Sap) For Spera) For A Business Intelligence (Bio) Solution
 SAP BusinessObjects FOR MICROSOFT ENVIRONMENTS MAKE BETTER DECISIONS TODAY SAP Solution Brief SAP BusinessObjects Business Intelligence Solutions SAP BusinessObjects FOR MICROSOFT ENVIRONMENTS SAP BusinessObjects
SAP BusinessObjects FOR MICROSOFT ENVIRONMENTS MAKE BETTER DECISIONS TODAY SAP Solution Brief SAP BusinessObjects Business Intelligence Solutions SAP BusinessObjects FOR MICROSOFT ENVIRONMENTS SAP BusinessObjects
WebLearning SAP Best Practice CD-ROM Courseware and e-library Titles. SAP Best Practices for Business Intelligence and Warehouse - BW
 WebLearning SAP Best Practice CD-ROM Courseware and e-library Titles SAP Best Practices for Business Intelligence and Warehouse - BW SAP Best Practices for Business Intelligence support the fast and smooth
WebLearning SAP Best Practice CD-ROM Courseware and e-library Titles SAP Best Practices for Business Intelligence and Warehouse - BW SAP Best Practices for Business Intelligence support the fast and smooth
Extending The Value of SAP with the SAP BusinessObjects Business Intelligence Platform Product Integration Roadmap
 Extending The Value of SAP with the SAP BusinessObjects Business Intelligence Platform Product Integration Roadmap Naomi Tomioka Phipps Principal Solution Advisor Business User South East Asia 22 nd April,
Extending The Value of SAP with the SAP BusinessObjects Business Intelligence Platform Product Integration Roadmap Naomi Tomioka Phipps Principal Solution Advisor Business User South East Asia 22 nd April,
Vistara Lifecycle Management
 Vistara Lifecycle Management Solution Brief Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
Vistara Lifecycle Management Solution Brief Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
My Inbox in SAP Fiori Simplifying Workflow for End Users
 My Inbox in SAP Fiori Simplifying Workflow for End Users Benjamin Notheis, Product Manager BPM, SAP SE ASUG Annual Conference, May 2015 Session Code: BT1072 Public Enterprise Architecture Data Modeling
My Inbox in SAP Fiori Simplifying Workflow for End Users Benjamin Notheis, Product Manager BPM, SAP SE ASUG Annual Conference, May 2015 Session Code: BT1072 Public Enterprise Architecture Data Modeling
How To Create A Help Desk For A System Center System Manager
 System Center Service Manager Vision and Planned Capabilities Microsoft Corporation Published: April 2008 Executive Summary The Service Desk function is the primary point of contact between end users and
System Center Service Manager Vision and Planned Capabilities Microsoft Corporation Published: April 2008 Executive Summary The Service Desk function is the primary point of contact between end users and
What makes SAP SRM 7.01 impressive? Rakesh Singh, GyanSys Inc. Naveen Rajan, GyanSys Inc.
 What makes SAP SRM 7.01 impressive? Rakesh Singh, GyanSys Inc. Naveen Rajan, GyanSys Inc. ] [ Agenda GyanSys Brief Overview SRM 7.01 New Features 7.01 Case Study [ GyanSys Brief Overview Offices Global
What makes SAP SRM 7.01 impressive? Rakesh Singh, GyanSys Inc. Naveen Rajan, GyanSys Inc. ] [ Agenda GyanSys Brief Overview SRM 7.01 New Features 7.01 Case Study [ GyanSys Brief Overview Offices Global
VOLUME 4, NUMBER 1, JANUARY 2006. Alloy Navigator 5: Robust New Service Management Solution Slated for Release
 Directions VOLUME 4, NUMBER 1, JANUARY 2006 Welcome to Directions Welcome to the January 2006 issue of Directions, Alloy Software s online customer newsletter. Let us know any topics you want to read about,
Directions VOLUME 4, NUMBER 1, JANUARY 2006 Welcome to Directions Welcome to the January 2006 issue of Directions, Alloy Software s online customer newsletter. Let us know any topics you want to read about,
Enterprise Content Management (ECM) Strategies
 Enterprise Content (ECM) Strategies Randy Hans Senior Solutions Consultant Open Text Corporation February 19, 2009 SAP 2009 / Page 1 [email protected] Agenda Open Text & SAP Business Challenges Open Text
Enterprise Content (ECM) Strategies Randy Hans Senior Solutions Consultant Open Text Corporation February 19, 2009 SAP 2009 / Page 1 [email protected] Agenda Open Text & SAP Business Challenges Open Text
The Power of Risk, Compliance & Security Management in SAP S/4HANA
 The Power of Risk, Compliance & Security Management in SAP S/4HANA OUR AGENDA Key Learnings Observations on Risk & Compliance Management Current State Current Challenges The SAP GRC and Security Solution
The Power of Risk, Compliance & Security Management in SAP S/4HANA OUR AGENDA Key Learnings Observations on Risk & Compliance Management Current State Current Challenges The SAP GRC and Security Solution
1) Go to the following URL: https://myitservices.nus.edu.sg/arsys/ 2) Login with your NUS account and password.
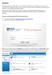 Introduction: Computer Centre has a wide range of service offering to all NUS users. Through an easy-to-use selfservice IT Service Request Portal, selected services are exposed to NUS Community to facilitate
Introduction: Computer Centre has a wide range of service offering to all NUS users. Through an easy-to-use selfservice IT Service Request Portal, selected services are exposed to NUS Community to facilitate
How To Use The Sap Process Control Application
 SAP Solution in Detail SAP Solutions for Governance, Risk, and Compliance SAP Process Control Ensure Effective Controls and Ongoing Compliance Table of Contents 3 Quick Facts 4 Focus Your Resources on
SAP Solution in Detail SAP Solutions for Governance, Risk, and Compliance SAP Process Control Ensure Effective Controls and Ongoing Compliance Table of Contents 3 Quick Facts 4 Focus Your Resources on
Dell One Identity Manager Scalability and Performance
 Dell One Identity Manager Scalability and Performance Scale up and out to ensure simple, effective governance for users. Abstract For years, organizations have had to be able to support user communities
Dell One Identity Manager Scalability and Performance Scale up and out to ensure simple, effective governance for users. Abstract For years, organizations have had to be able to support user communities
SAP ERP FINANCIALS ENABLING FINANCIAL EXCELLENCE. SAP Solution Overview SAP Business Suite
 SAP Solution Overview SAP Business Suite SAP ERP FINANCIALS ENABLING FINANCIAL EXCELLENCE ESSENTIAL ENTERPRISE BUSINESS STRATEGY PROVIDING A SOLID FOUNDATION FOR ENTERPRISE FINANCIAL MANAGEMENT 2 Even
SAP Solution Overview SAP Business Suite SAP ERP FINANCIALS ENABLING FINANCIAL EXCELLENCE ESSENTIAL ENTERPRISE BUSINESS STRATEGY PROVIDING A SOLID FOUNDATION FOR ENTERPRISE FINANCIAL MANAGEMENT 2 Even
Cisco Network Optimization Service
 Service Data Sheet Cisco Network Optimization Service Optimize your network for borderless business evolution and innovation using Cisco expertise and leading practices. New Expanded Smart Analytics Offerings
Service Data Sheet Cisco Network Optimization Service Optimize your network for borderless business evolution and innovation using Cisco expertise and leading practices. New Expanded Smart Analytics Offerings
