IHS Emergency Department Dashboard
|
|
|
- Toby O’Neal’
- 10 years ago
- Views:
Transcription
1 RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS Emergency Department Dashboard (BEDD) Version 1.0 Office of Information Technology Division of Information Resource Management Albuquerque, New Mexico
2 Document Revision History Date of Location of Revision Change Revision June 2012 GDIT First Draft GDIT Final Version ii Document Revision History
3 Table of Contents 1.0 Introduction Getting Started Initial EDD Configuration Log on to the EDD Application Open the Manager Page Add a Room Setup and Configure Options Screen Timeout (in seconds) Operate Dashboard Stand Alone Use more than 1 Clinic Show Daily Summary on Dashboard Print Med Rec Worksheet Print Patient Routing Sheet Print Arm Band Show Used Room Show Provider Show Nurse Show Consult Use Auto Note Use Comm Board Print Triage Report upon Save Switch EHR Patient on Edit Reg Column on Main Display Typical Workflow Admit Patient via AMER Triage Patient and Triage Actions Assign a Patient to a Room Update Additional ED Data Injury Information Visit Information Additional Notes Discharge Remove the Patient from the Room Discharge Patient Discharge Reporting ED Dashboard Reporting Appendix A: Available Reports A.1 ERS Admission Summary A.2 Central Log A.3 Check-In Summary by Hour iii Table of Contents
4 A.4 Length of Stay by Triage Acuity A.5 Discharge Activity by Hour A.6 Room Utilization Appendix B: Rules of Behavior B.1 All RPMS Users B.1.1 Access B.1.2 Information Accessibility B.1.3 Accountability B.1.4 Confidentiality B.1.5 Integrity B.1.6 System Logon B.1.7 Passwords B.1.8 Backups B.1.9 Reporting B.1.10 Session Timeouts B.1.11 Hardware B.1.12 Awareness B.1.13 Remote Access B.2 RPMS Developers B.3 Privileged Users Acronym List Contact Information iv Table of Contents
5 Preface The purpose of this manual is to provide the user with the information required to use the IHS Emergency Department Dashboard (EDD). v Preface
6 1.0 Introduction The EDD is a tool that electronically enables facilities to run and manage their emergency and or urgent care clinics. It is dependent on the RPMS Emergency Room System (ERS) in the AMER namespace. EDD is built on the ERS foundation to enhance patient flow and provider communication. EDD can be set up to operate as a standalone icon on the staff computer or can be accessed from within the Resource and Patient Management System (RPMS) Electronic Health Record (EHR) application. EDD gets its data and updates from one of four ways: ERS Dashboard Edit EHR data A combination of all three. 1 Introduction
7 2.0 Getting Started Before using the EDD application, it must be set up to meet the needs of the user s site with respect to clinic information, and how the application will behave while admitting, processing and discharging patients. 2.1 Initial EDD Configuration Someone with EDD Manager Access as described in the BEDD Installation Guide is required to set up bed locations, site information, and other settings before the application is used Log on to the EDD Application 1. Do one of the following: Double-click the EDD icon on the desktop Click the Emergency Department Dashboard tab in EHR Figure 2-1: EDD logon dialog Note: If accessing EDD via the EHR, you may not see the EDD logon dialog because the system already recognizes you as having logged on. 2. Type your RPMS Access Code and Verify Code in the appropriate fields (Figure 2-1). 3. Click Login to display the Main EDD page (Figure 2-2). 2 Getting Started
8 Figure 2-2: Main EDD page with Manager button highlighted Open the Manager Page At the Main EDD page, click Manager. The Manager page opens with the Room Setup pane displayed (Figure 2-3). Note: At initial setup, rooms are not yet defined; consequently, the Room Setup pane will be empty. Figure 2-3: Manager page, Room Setup pane 3 Getting Started
9 2.1.3 Add a Room To add a room: 1. Type the room name in the Room Name field in the Edit Room Info area near the bottom of the page. 2. Set Status to Active. 3. Set Occupied to No. 4. Press Save. The Message from webpage dialog displays (Figure 2-4). Figure 2-4: Room Setup pane: adding a room 5. Click OK to dismiss the dialog. When adding or changing a room, its status can be set to No Longer Used or Temporarily Unavailable. Also, selecting Yes under Occupied will prevent any patient from being assigned to an otherwise Active room. 2.2 Setup and Configure Options To access the setup and configure options: 1. Click Setup on the menu bar at the top of the page to display the ED Dashboard Setup pane (Figure 2-5). 4 Getting Started
10 Figure 2-5: Manager page, ED Dashboard Setup pane 2. Select the SiteName of the site to be edited. The corresponding row in the table is highlighted (Figure 2-6) and the current setup configuration displays in the ED Dashboard System Setup panel. Figure 2-6: ED Dashboard Setup panel, Red Lake Hospital row selected 5 Getting Started
11 Note: Site data is automatically populated with INSTITUTION file (#4) entries identified by the MEDICAL CENTER DIVISION file (#40.8), and new sites can only be added by clinic or hospital management. If the appropriate sites are not displaying, please contact the RPMS system administrator for this installation. 3. Edit the various fields in the Dashboard System Setup panel. The following subsections describe the changes in the EDD produced by each field. 4. Click Save to save all changes Screen Timeout (in seconds) This value affects how often pages are refreshed or timed out when logged in to the EDD application Operate Dashboard Stand Alone Not implemented Use more than 1 Clinic Display the Clinic column on the dashboard in the Check-In, Triaged, Room Management, and Pending Documentation sections (Figure 2-7). Figure 2-7: EDD, Clinic column Show Daily Summary on Dashboard Not implemented 6 Getting Started
12 2.2.5 Print Med Rec Worksheet Print to screen as part of AMER Admission (Figure 2-8). Select printer for PATIENT MEDICATION WORKSHEET... DEVICE: HOME// VT PRINTED ON 06/21/ :31 PAGE: 1 ***ALERT*** PATIENT COPY *** PATIENT COPY *** ALERT *** RED LAKE HOSPITAL PATIENT MEDICATION RECONCILIATION PATIENT APPOINTMENT: 06/21/ :30 LOCATION: URGENT CARE PATIENT NAME: PATIENT,DEMO1 SEX: MALE CHART #: DOB: 03/25/2011 *************************************************************************** Figure 2-8: AMER Admission excerpt for Med Rec Worksheet print Print Patient Routing Sheet Print to screen as part of AMER Admission (Figure 2-9). Do you want to PRINT a routing slip? YES// FILE ROOM PRINTER: UC WALKINS// 0 VT Right Margin: 80// FACILITY: RED LAKE HOSPITAL PAGE 1 OUTPATIENT ROUTING SLIP **Confidential Patient Data** PATIENT,DEMO1 HRCN: DOB: 03/25/2011 PO BOX 196 ALBERTA, MINNESOTA APPT DT: 6/21/2012@14:30 **CURRENT APPOINTMENTS** TIME CLINIC LOCATION PHONE 2:30 PM WI URGENT CARE URGENT CARE DATE PRINTED: Jun 21, 2012@14:31:04 Requested by: PROVIDER,DEMO Figure 2-9: AMER ADMISSION excerpt for Print Patient Routing Sheet 7 Getting Started
13 2.2.7 Print Arm Band Print to screen as part of AMER Admission (Figure 2-10). Enter number of labels to print: (0-50): 4// LABEL PRINTER: ERL// 0 VT Right Margin: 80// M PATIENT,DEMO1 03/25/11 BLACKDUCK M PATIENT,DEMO1 03/25/11 BLACKDUCK M PATIENT,DEMO1 03/25/11 BLACKDUCK M PATIENT,DEMO1 03/25/11 BLACKDUCK Figure 2-10: AMER Admission excerpt for Print Arm Band Show Used Room Not Implemented Show Provider Display the Provider column on the dashboard in the Triaged, Room Management, and Pending Documentation sections (Figure 2-11). Figure 2-11: EDD, Provider column 8 Getting Started
14 Show Nurse Display the Nurse column on the dashboard in the Triaged, Room Management, and Pending Documentation sections (Figure 2-12). Figure 2-12: EDD, Nurse column Show Consult Display the Consult column on the dashboard in the Triaged, Room Management, and Pending Documentation sections (Figure 2-13). Figure 2-13: EDD, Consult column 9 Getting Started
15 Use Auto Note Auto-updates the notes field when Trg Page (Triage Page), Rm Page (Room Page), or Obsv (Patient Observed) options are checked for a patient on the dashboard in the Check-In, Triaged, Room Management, or Pending Documentation sections. Figure 2-14, Figure 2-15, and Figure 2-16 show the sequence of Trg Page being used to page for triage. Figure 2-14: Clicking Trg Page in the Action column Figure 2-15: Message from webpage dialog indicating a Triage Page was requested Figure 2-16: Info column containing the Triage Page note Use Comm Board Not Implemented Print Triage Report upon Save Not Implemented 10 Getting Started
16 Switch EHR Patient on Edit If this box is checked and the EDD is being used within EHR, whenever a patient is edited on the dashboard, the EHR patient and visit will automatically switch to the patient and visit being edited in the dashboard. If the box is not checked, the switch will not occur. Note: This setting only applies when in EHR mode. When utilizing standalone mode, the patient/visit will not switch upon a patient edit Reg Column on Main Display The Reg column on the EDD indicates if the patient s registration file was updated on the current date: If any change was made to the patient s registration file, the Reg column displays Yes on a white background (Figure 2-17). Figure 2-17: EDD, Reg column value Yes If no change was made to the patient s registration file, the Reg column displays No on a yellow background (Figure 2-18). Figure 2-18: EDD, Reg column value No Additionally, a check is performed on the patient s AG Tribe of Membership field (AG page 2). If the tribe is NON-INDIAN BENEFICIARY, NoBens is attached as a suffix to the value in the Reg column (Figure 2-19). Figure 2-19:EDD, Non-Indian Beneficiary Indicator NoBens 11 Getting Started
17 3.0 Typical Workflow This section outlines a typical workflow for using the EDD. Be advised that some of these steps may be different for a given site. Admit a patient via the RPMS AMER ADMISSION option, which will register the patient on the dashboard (in the Check-In section). Triage the patient which moves the patient into the Triaged section of the dashboard. Assign the patient to a room. Update various informational visit pages: Injury General visit information ED Consult Information Procedure information Diagnosis information Remove the patient from the room. Discharge the patient. 3.1 Admit Patient via AMER In order to list a patient in the EDD the patient must first be admitted to the ED using the RPMS AMER ADMISSION menu option (Figure 3-1). Select OPTION NAME: AMER 1 AMER ACTIVE PATIENTS List Patients Currently Admitted to ER 2 AMER ADMISSION Admit to Emergency Room 3 AMER AUDIT REPORT ER VISIT AUDITING LOG REPORTS 4 AMER BATCH Batch Mode ER Admission/Discharge 5 AMER CANNED ER System Pre-Defined Reports Press <RETURN> to see more, '^' to exit this list, OR CHOOSE 1-5: 2 AMER ADMISSION Admit to Emergency Room Admit to Emergency Room ER SYSTEM Ver 3.0: ADMISSION TO EMERGENCY ROOM ^ = back up ^^ = quit Questions preceded by a '*' are MANDATORY. Enter '??' to see choices. ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Enter the patient's NAME or LOCAL CHART NUMBER: TEST,PA 1 TEST,PATIENT EIGHT <A> M XXX-XX-4958 RLHO TEST,PATIENT FIVE F XXX-XX-9957 RLHO TEST,PATIENT FOUR <A> M XXX-XX-5661 RLHO TEST,PATIENT ONE <A> M XXX-XX-3333 RLHO T TEST,PATIENT SEVEN M XXX-XX-8583 RLHO ENTER '^' TO STOP, OR CHOOSE 1-5: 5 TEST,PATIENT SEVEN M XXX-XX-8583 RLHO Typical Workflow
18 ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ *Date and time of admission to ER: NOW// No Pending Appointments (JUN 21, ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ *Presenting complaint: PAIN ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ********************************************************************** Date of Last Registration Update: MAR 19, 2012 Additional Registration Information: ********************************************************************** Want to Edit this Registration Record? NO// ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ *Visit type: UNSCHEDULED// ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ *Was this patient transferred from another facility? NO// ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ *Mode of transport to the ER: PRIVATE VEHICLE/WALK IN// Want to print PCC+ forms? Yes// (Yes) Encounter form: Request to print PCC+ forms cancelled! Enter number of labels to print: (0-50): 4// LABEL PRINTER: ERL// 0 VT Right Margin: 80// M TEST,PATIENT SEVEN 01/07/01 PONEMAH M TEST,PATIENT SEVEN 01/07/01 PONEMAH M TEST,PATIENT SEVEN 01/07/01 PONEMAH M TEST,PATIENT SEVEN 01/07/01 PONEMAH Do you want to PRINT a routing slip? YES// FILE ROOM PRINTER: UC WALKINS// 0 VT Right Margin: 80// FACILITY: RED LAKE HOSPITAL PAGE 1 OUTPATIENT ROUTING SLIP **Confidential Patient Data** TEST,PATIENT SEVEN HRCN: Typical Workflow
19 DOB: 01/07/ TH STREET ALBERTA, MINNESOTA APPT DT: **CURRENT APPOINTMENTS** TIME CLINIC LOCATION PHONE 3:42 PM WI URGENT CARE URGENT CARE DATE PRINTED: Jun 21, Requested by: ADAM,SITE Setting data for Dashboard... Select printer for PATIENT MEDICATION WORKSHEET... DEVICE: HOME// VT PRINTED ON 06/21/ :43 PAGE: 1 ***ALERT*** PATIENT COPY *** PATIENT COPY *** ALERT *** RED LAKE HOSPITAL PATIENT MEDICATION RECONCILIATION PATIENT APPOINTMENT: 06/21/ :42 LOCATION: URGENT CARE PATIENT NAME: TEST,PATIENT SEVEN SEX: MALE CHART #: DOB: 01/07/2001 ****************************************************************************** ALLERGIES: Allergies Unknown No Medications Found ****************************************************************************** I am unsure of any outside medications and/or over the counter medications and dosages. I will bring my medications on my next visit. ****************************************************************************** Enter RETURN to continue or '^' to exit: PRINTED ON 06/21/ :43 PAGE: 2 ***ALERT*** PATIENT COPY *** PATIENT COPY *** ALERT *** RED LAKE HOSPITAL PATIENT MEDICATION RECONCILIATION PATIENT APPOINTMENT: 06/21/ :42 LOCATION: URGENT CARE PATIENT NAME: TEST,PATIENT SEVEN SEX: MALE CHART #: DOB: 01/07/2001 OUTSIDE MEDICATIONS Patient: Please list any outside medications not received at any RED LAKE HOSPITAL Pharmacy 14 Typical Workflow
20 Enter RETURN to continue or '^' to exit: PRINTED ON 06/21/ :43 PAGE: 3 ***ALERT*** PATIENT COPY *** PATIENT COPY *** ALERT *** RED LAKE HOSPITAL PATIENT MEDICATION RECONCILIATION PATIENT APPOINTMENT: 06/21/ :42 LOCATION: URGENT CARE PATIENT NAME: TEST,PATIENT SEVEN SEX: MALE CHART #: DOB: 01/07/2001 ****************************************************************************** OVER THE COUNTER MEDICATIONS Patient: Please list any OVER the Counter Medications PRINTED ON 06/21/ :43 PAGE: 4 ***ALERT*** PATIENT COPY *** PATIENT COPY *** ALERT *** RED LAKE HOSPITAL PATIENT MEDICATION RECONCILIATION PATIENT APPOINTMENT: 06/21/ :42 LOCATION: URGENT CARE PATIENT NAME: TEST,PATIENT SEVEN SEX: MALE CHART #: DOB: 01/07/2001 ****************************************************************************** NEW/CHANGE MEDICATIONS Enter RETURN to continue or '^' to exit: Select printer for PATIENT ROUTING SLIP... DEVICE: HOME// VT RED LAKE HOSPITAL PATIENT ROUTING SLIP - PRINTED: 06/21/ :43 ***ALERT - THIS PAPER CONTAINS YOUR ELIGIBILITY*** PATIENT NAME: TEST,PATIENT SEVEN SEX: MALE 15 Typical Workflow
21 CHART #: DOB: 01/07/2001 ELIGIBILITY: CHS & DIRECT ******************************************************************************* Other Information / Instructions: ******************************************************************************* Departments for Patient to visit today: (Patient: Please check in at any indicated department) Return to Clinic Today Yes No ***Note to Surgery Patient: You must go to all indicated departments TODAY, or your surgery may be cancelled! Lab Imaging Tribal Health Prog. Testing Ctr Imaging Pharmacy Respiratory Therapy Cardiology Medisaw BC Orientation Admissions Behavioral Health ***Note to nurses: For pre-op patient, please complete the following: Surgery Date: Diagnosis: Surgeon: Procedure: LOS: ******************************************************************************* Follow-Up Return to Clinic in: Days Weeks Months PRN Appointment date/time: For: 15 mins 20 mins 30 mins 40 mins 60 mins With: Purpose of appt: Other instructions: Other Appointments Needed: ******************************************************************************* PATIENT: TEST,PATIENT SEVEN Was seen in clinic today. Should not work or attend school from to Should be excused from Phys Ed from to Signature: Date: Select printer for Patient WristBand/Embossed Card... PATIENT REGISTRATION RED LAKE HOSPITAL 16 Typical Workflow
22 Print an EMBOSSED CARD *** NOTE: IF YOU EDIT A PATIENT AND SEE THEIR NAME IN REVERSE VIDEO *** *** WITH '(RHI)' BLINKING NEXT TO IT, IT MEANS THEY HAVE RESTRICTED *** *** HEALTH INFORMATION *** How many copies of the EMBOSSED CARD do you want? (1-5) 1// DEVICE: HOME// VT < RED LAKE HO (114449) XXX-XX-8583 TEST,PATIENT SEVEN JAN 07, > ER admission data collection is now complete. Thank you. Figure 3-1: AMER Admission Note: All three configurable label options were printed, as the site setup options Print Med Rec Worksheet, Print Patient Routing Sheet, and Print Arm Band were checked as described in Section 2.2. The patient now appears in the EDD in the Check-In section as seen in Figure 3-2. Figure 3-2: Patient in Check-In status 17 Typical Workflow
23 3.2 Triage Patient and Triage Actions Add triage information before or after assigning the admitted patient to a room. Figure 3-3: EDD showing name of patient for whom triage information will be added To add triage information: 1. Click the patient s name in the Patient (gender) column. The Patient Edit page (Figure 3-4) displays. Figure 3-4: Patient Edit page 18 Typical Workflow
24 2. Enter triage information into the Admission Information section of the Patient Edit page which includes Presenting Complaint, Initial Acuity, Triaged (date and time), Triage Nurse, and Clinic Type (Figure 3-5). Figure 3-5: Patient Edit page, Admission Information section 3. Click Save/Close. The patient s listing will move to the Triaged section of the EDD (Figure 3-6). Figure 3-6: EDD showing patient listing moved to the Triaged section Actions such as Room Page, Observation, and Triage Report can now be performed for the patient listed in the Triaged section (Figure 3-7). 19 Typical Workflow
25 Figure 3-7: Triaged section, available Actions If the Use Auto Note site setting in Section is selected, choosing from the available Actions will automatically post a note in the Info column. Room Page: To post a note stating that the patient was paged for a room: 1. Select Rm Page. A Message from webpage dialog (Figure 3-8) displays. Figure 3-8: Message from webpage dialog 2. Click OK to dismiss the dialog. The Room Page note (Figure 3-9) appears in the Info column of the Triaged section. Figure 3-9: Room Page note in the Info column Observation: To post a note stating that the patient was observed, select Obsv. 20 Typical Workflow
26 Triage Report: To display a triage report for the patient: 1. Select TrgRpt. The Triage Report (Figure 3-10) displays. Figure 3-10: BEDD ED Triage Report 2. When finished with the report, click the Return to ED Tracking Board link on the upper left of the triage report. 3.3 Assign a Patient to a Room To assign a patient to a room: 1. Click the patient s name on the EDD. The Edit Patient page (Figure 3-4) displays. 2. In the Room Information section (Figure 3-11): Figure 3-11: Edit Patient page, Room Information section a. Select the Primary Nurse from the drop-down list. b. Select from the Available Rooms to update the Room Assignment. c. Click Save/Close. The patient now appears in the Room Management section of the EDD (Figure 3-12). 21 Typical Workflow
27 Figure 3-12: EDD, Patient moved to Room Management section 3.4 Update Additional ED Data Additional informational elements can be entered and tracked via the EDD. These include injury, general visit, consult, and procedure and diagnosis information. To access any of these elements, click the Patient name wherever it appears on the EDD to open the Patient Edit page. Note: A dialog indicating that a Save will be performed displays when moving between sections and adding data to the various injury, general visit, consult, and procedure and diagnosis sections Injury Information Indicate that the visit was caused by an injury by using the options available in the Injury Information section of the Patient Edit page (Figure 3-13): Figure 3-13 : Injury Information section of Patient Edit page 1. Select Yes at Was this visit caused by an injury? 2. Click Add Injury Information to display the confirmation dialog. 3. Click OK to display the Injury Worksheet (Figure 3-14) or click Cancel to end the process. 22 Typical Workflow
28 Figure 3-14: Injury Worksheet page Required fields have an asterisk by the label: Town/Village where injury occurred Date and time of injury Cause Setting (in which the injury occurred) 23 Typical Workflow
29 3.4.2 Visit Information General visit information is entered in the Visit Information section of the Patient Edit page (Figure 3-15). Figure 3-15: Visit Information section of the Patient Edit page Admissions Information As appropriate, complete the following fields: Seen by Admitting Physician (date and time field) Decision to Admit Time (date and time field) Admitting Physician (dropdown list) ED Consults Click ED Consult Information to display the ED Consult Worksheet (Figure 3-16). Fields preceded with an asterisk (*) are required entries. Multiple consults can be entered. Figure 3-16: ED Consult Worksheet 24 Typical Workflow
30 ED Procedures Click Procedure Information to display the ED Procedure Worksheet (Figure 3-17). Fields preceded with an asterisk (*) are required entries. Multiple consults can be entered. Figure 3-17: ED Procedure Worksheet Diagnosis Click Diagnosis Information to display the ED Diagnosis Worksheet (Figure 3-18). Fields preceded with an asterisk (*) are required entries. At least one entry must be listed as a primary diagnosis. Multiple consults can be entered. Figure 3-18: ED Diagnosis Worksheet Note: A diagnosis is required. If no diagnosis entry is on file for the visit, the entry.9999 UNCODED DIAGNOSIS is automatically entered. The user must complete the Diagnosis Narrative and save the entry. 25 Typical Workflow
31 3.4.3 Additional Notes Add additional notes on the Patient Edit page by typing in the General Information/Notes section (Figure 3-19) and clicking Save/Close. Figure 3-19: General Information/Notes section of the Patient Edit page 3.5 Discharge Remove the Patient from the Room Optionally, the patient may be removed from the room prior to actual discharge in order to free up the room for another patient. This step is completely optional if the patient is being discharged, as the patient would otherwise be removed from the room in the course of performing the discharge step. To remove a patient from the room: 1. Scroll to the Room Information section (Figure 3-20) of the Patient Edit page. 2. Select Remove from Room. 3. Click Save/Close. Figure 3-20: Room Information section, Patient Edit page 26 Typical Workflow
32 The patient will now appear in the Pending Documentation section of the dashboard (Figure 3-21). Figure 3-21 : EDD; Patient moved to Pending Documentation section Discharge Patient On the Patient Edit page, click Discharge. The EDD will validate that required information has been entered before proceeding with the discharge: If any information is missing, one or more dialogs will display (Figure 3-22). Figure 3-22: Message from webpage dialog; Primary Diagnosis Code is Required 27 Typical Workflow
33 If no additional data is needed, the Patient Discharge page (Figure 3-23) displays. Figure 3-23: Patient Discharge page To discharge the patient: 1. Enter disposition information in the various fields of the Disposition Information section (Figure 3-24) of the Patient Discharge page. Mandatory entries are indicated with an asterisk (*) preceding the label. Figure 3-24: Disposition Information section; Patient Discharge page 2. Click Complete Discharge. A confirmation dialog (Figure 3-25) displays. 28 Typical Workflow
34 Figure 3-25: Message from webpage dialog, Complete Discharge? confirmation 3. Click OK. The patient is removed from EDD and AMER (Figure 3-26). Figure 3-26: Patient removed from EDD and AMER Discharge Reporting To display a list of discharges by date at the EDD: 1. Click Discharges at the top of the dashboard (Figure 3-27). Figure 3-27: EDD; Manager button 29 Typical Workflow
35 The Emergency Department DISCHARGES page (Figure 3-28) displays. Figure 3-28: Emergency Department DISCHARGES page 2. Select the date range to report on using the Discharge From Date and Discharge To Date fields. 3. Click Show. Matching discharge records are displayed in the list (Figure 3-29). Figure 3-29: Example list of Discharges by date range 3.6 ED Dashboard Reporting A number of management reports can be generated, provided the user has access to the Manager page. To run a report, starting at the EDD main page: 1. Click Manager at the main EDD page (Figure 2-2). 2. Select Reports from the menu bar. The ERS/BEDD Reports page (Figure 3-30) displays. 30 Typical Workflow
36 Figure 3-30: ERS/BEDD Reports page 3. Locate the report in the list and: a. Type the beginning date in that report s Enter the Beginning Date field. b. Type the ending date in that report s Enter the Ending Date field. c. Click Run Report for that report. The requested report is displayed. Appendix A: contains samples of available reports. 4. To return to the Manager page, click the hyperlink in the upper right corner of any report. 31 Typical Workflow
37 Appendix A: Available Reports A.1 ERS Admission Summary A.2 Central Log 32 Available Reports
38 A.3 Check-In Summary by Hour A.4 Length of Stay by Triage Acuity A.5 Discharge Activity by Hour A.6 Room Utilization 33 Available Reports
39 Appendix B: Rules of Behavior The Resource and Patient Management (RPMS) system is a United States Department of Health and Human Services (HHS), Indian Health Service (IHS) information system that is FOR OFFICIAL USE ONLY. The RPMS system is subject to monitoring; therefore, no expectation of privacy shall be assumed. Individuals found performing unauthorized activities are subject to disciplinary action including criminal prosecution. All users (Contractors and IHS Employees) of RPMS will be provided a copy of the Rules of Behavior (RoB) and must acknowledge that they have received and read them prior to being granted access to a RPMS system, in accordance IHS policy. For a listing of general ROB for all users, see the most recent edition of IHS General User Security Handbook (SOP 06-11a). For a listing of system administrators/managers rules, see the most recent edition of the IHS Technical and Managerial Handbook (SOP 06-11b). Both documents are available at this IHS Web site: The ROB listed in the following sections are specific to RPMS. B.1 All RPMS Users In addition to these rules, each application may include additional RoBs that may be defined within the documentation of that application (e.g., Dental, Pharmacy). B.1.1 Access RPMS users shall Only use data for which you have been granted authorization. Only give information to personnel who have access authority and have a need to know. Always verify a caller s identification and job purpose with your supervisor or the entity provided as employer before providing any type of information system access, sensitive information, or nonpublic agency information. Be aware that personal use of information resources is authorized on a limited basis within the provisions Indian Health Manual Part 8, Information Resources Management, Chapter 6, Limited Personal Use of Information Technology Resources. 34 Rules of Behavior
40 RPMS users shall not Retrieve information for someone who does not have authority to access the information. Access, research, or change any user account, file, directory, table, or record not required to perform their official duties. Store sensitive files on a PC hard drive, or portable devices or media, if access to the PC or files cannot be physically or technically limited. Exceed their authorized access limits in RPMS by changing information or searching databases beyond the responsibilities of their jobs or by divulging information to anyone not authorized to know that information. B.1.2 Information Accessibility RPMS shall restrict access to information based on the type and identity of the user. However, regardless of the type of user, access shall be restricted to the minimum level necessary to perform the job. RPMS users shall Access only those documents they created and those other documents to which they have a valid need-to-know and to which they have specifically granted access through an RPMS application based on their menus (job roles), keys, and FileMan access codes. Some users may be afforded additional privileges based on the functions they perform, such as system administrator or application administrator. Acquire a written preauthorization in accordance with IHS polices and procedures prior to interconnection to or transferring data from RPMS. B.1.3 Accountability RPMS users shall Behave in an ethical, technically proficient, informed, and trustworthy manner. Log out of the system whenever they leave the vicinity of their personal computers (PCs). Be alert to threats and vulnerabilities in the security of the system. Report all security incidents to their local Information System Security Officer (ISSO) Differentiate tasks and functions to ensure that no one person has sole access to or control over important resources. Protect all sensitive data entrusted to them as part of their government employment. 35 Rules of Behavior
41 Abide by all Department and Agency policies and procedures and guidelines related to ethics, conduct, behavior, and information technology (IT) information processes. B.1.4 B.1.5 Confidentiality RPMS users shall Be aware of the sensitivity of electronic and hard copy information, and protect it accordingly. Store hard copy reports/storage media containing confidential information in a locked room or cabinet. Erase sensitive data on storage media prior to reusing or disposing of the media. Protect all RPMS terminals from public viewing at all times. Abide by all Health Insurance Portability and Accountability Act (HIPAA) regulations to ensure patient confidentiality. RPMS users shall not Allow confidential information to remain on the PC screen when someone who is not authorized to that data is in the vicinity. Store sensitive files on a portable device or media without encrypting. Integrity RPMS users shall Protect their systems against viruses and similar malicious programs. Observe all software license agreements. Follow industry standard procedures for maintaining and managing RPMS hardware, operating system software, application software, and/or database software and database tables. Comply with all copyright regulations and license agreements associated with RPMS software. RPMS users shall not Violate federal copyright laws. Install or use unauthorized software within the system libraries or folders. Use freeware, shareware, or public domain software on/with the system without their manager s written permission and without scanning it for viruses first. 36 Rules of Behavior
42 B.1.6 B.1.7 System Logon RPMS users shall Have a unique User Identification/Account name and password. Be granted access based on authenticating the account name and password entered. Be locked out of an account after five successive failed login attempts within a specified time period (e.g., one hour). Passwords RPMS users shall Change passwords a minimum of every 90 days. Create passwords with a minimum of eight characters. If the system allows, use a combination of alpha-numeric characters for passwords, with at least one uppercase letter, one lower case letter, and one number. It is recommended, if possible, that a special character also be used in the password. Change vendor-supplied passwords immediately. Protect passwords by committing them to memory or store them in a safe place (do not store passwords in login scripts or batch files). Change passwords immediately if password has been seen, guessed, or otherwise compromised, and report the compromise or suspected compromise to their ISSO. Keep user identifications (IDs) and passwords confidential. RPMS users shall not Use common words found in any dictionary as a password. Use obvious readable passwords or passwords that incorporate personal data elements (e.g., user s name, date of birth, address, telephone number, or social security number; names of children or spouses; favorite band, sports team, or automobile; or other personal attributes). Share passwords/ids with anyone or accept the use of another s password/id, even if offered. Reuse passwords. A new password must contain no more than five characters per eight characters from the previous password. Post passwords. Keep a password list in an obvious place, such as under keyboards, in desk drawers, or in any other location where it might be disclosed. 37 Rules of Behavior
43 Give a password out over the phone. B.1.8 B.1.9 Backups RPMS users shall Plan for contingencies such as physical disasters, loss of processing, and disclosure of information by preparing alternate work strategies and system recovery mechanisms. Make backups of systems and files on a regular, defined basis. If possible, store backups away from the system in a secure environment. Reporting RPMS users shall Contact and inform their ISSO that they have identified an IT security incident and begin the reporting process by providing an IT Incident Reporting Form regarding this incident. Report security incidents as detailed in the IHS Incident Handling Guide (SOP 05-03). RPMS users shall not Assume that someone else has already reported an incident. The risk of an incident going unreported far outweighs the possibility that an incident gets reported more than once. B.1.10 Session Timeouts RPMS system implements system-based timeouts that back users out of a prompt after no more than 5 minutes of inactivity. RPMS users shall Utilize a screen saver with password protection set to suspend operations at no greater than 10 minutes of inactivity. This will prevent inappropriate access and viewing of any material displayed on the screen after some period of inactivity. B.1.11 Hardware RPMS users shall Avoid placing system equipment near obvious environmental hazards (e.g., water pipes). Keep an inventory of all system equipment. 38 Rules of Behavior
44 Keep records of maintenance/repairs performed on system equipment. RPMS users shall not Eat or drink near system equipment. B.1.12 Awareness RPMS users shall Participate in organization-wide security training as required. Read and adhere to security information pertaining to system hardware and software. Take the annual information security awareness. Read all applicable RPMS manuals for the applications used in their jobs. B.1.13 Remote Access Each subscriber organization establishes its own policies for determining which employees may work at home or in other remote workplace locations. Any remote work arrangement should include policies that Are in writing. Provide authentication of the remote user through the use of ID and password or other acceptable technical means. Outline the work requirements and the security safeguards and procedures the employee is expected to follow. Ensure adequate storage of files, removal, and nonrecovery of temporary files created in processing sensitive data, virus protection, and intrusion detection, and provide physical security for government equipment and sensitive data. Establish mechanisms to back up data created and/or stored at alternate work locations. Remote RPMS users shall Remotely access RPMS through a virtual private network (VPN) whenever possible. Use of direct dial in access must be justified and approved in writing and its use secured in accordance with industry best practices or government procedures. Remote RPMS users shall not Disable any encryption established for network, internet, and Web browser communications. 39 Rules of Behavior
45 B.2 RPMS Developers RPMS developers shall Always be mindful of protecting the confidentiality, availability, and integrity of RPMS when writing or revising code. Always follow the IHS RPMS Programming Standards and Conventions (SAC) when developing for RPMS. Only access information or code within the namespaces for which they have been assigned as part of their duties. Remember that all RPMS code is the property of the U.S. Government, not the developer. Not access live production systems without obtaining appropriate written access, and shall only retain that access for the shortest period possible to accomplish the task that requires the access. Observe separation of duties policies and procedures to the fullest extent possible. Document or comment all changes to any RPMS software at the time the change or update is made. Documentation shall include the programmer s initials, date of change, and reason for the change. Use checksums or other integrity mechanism when releasing their certified applications to assure the integrity of the routines within their RPMS applications. Follow industry best standards for systems they are assigned to develop or maintain, and abide by all Department and Agency policies and procedures. Document and implement security processes whenever available. RPMS developers shall not Write any code that adversely impacts RPMS, such as backdoor access, Easter eggs, time bombs, or any other malicious code or make inappropriate comments within the code, manuals, or help frames. Grant any user or system administrator access to RPMS unless proper documentation is provided. Release any sensitive agency or patient information. B.3 Privileged Users Personnel who have significant access to processes and data in RPMS, such as, system security administrators, systems administrators, and database administrators, have added responsibilities to ensure the secure operation of RPMS. 40 Rules of Behavior
46 Privileged RPMS users shall Verify that any user requesting access to any RPMS system has completed the appropriate access request forms. Ensure that government personnel and contractor personnel understand and comply with license requirements. End users, supervisors, and functional managers are ultimately responsible for this compliance. Advise the system owner on matters concerning information technology security. Assist the system owner in developing security plans, risk assessments, and supporting documentation for the certification and accreditation process. Ensure that any changes to RPMS that affect contingency and disaster recovery plans are conveyed to the person responsible for maintaining continuity of operations plans. Ensure that adequate physical and administrative safeguards are operational within their areas of responsibility and that access to information and data is restricted to authorized personnel on a need-to-know basis. Verify that users have received appropriate security training before allowing access to RPMS. Implement applicable security access procedures and mechanisms, incorporate appropriate levels of system auditing, and review audit logs. Document and investigate known or suspected security incidents or violations and report them to the ISSO, Chief Information Security Officer (CISO), and systems owner. Protect the supervisor, superuser, or system administrator passwords. Avoid instances where the same individual has responsibility for several functions (i.e., transaction entry and transaction approval). Watch for unscheduled, unusual, and unauthorized programs. Help train system users on the appropriate use and security of the system. Establish protective controls to ensure the accountability, integrity, confidentiality, and availability of the system. Replace passwords when a compromise is suspected. Delete user accounts as quickly as possible from the time that the user is no longer authorized system. Passwords forgotten by their owner should be replaced, not reissued. Terminate user accounts when a user transfers or has been terminated. If the user has authority to grant authorizations to others, review these other authorizations. Retrieve any devices used to gain access to the system or equipment. Cancel logon IDs and passwords, and delete or reassign related active and backup files. 41 Rules of Behavior
47 Use a suspend program to prevent an unauthorized user from logging on with the current user's ID if the system is left on and unattended. Verify the identity of the user when resetting passwords. This can be done either in person or having the user answer a question that can be compared to one in the administrator s database. Shall follow industry best standards for systems they are assigned to, and abide by all Department and Agency policies and procedures. Privileged RPMS users shall not Access any files, records, systems, etc., that are not explicitly needed to perform their duties Grant any user or system administrator access to RPMS unless proper documentation is provided. Release any sensitive agency or patient information. 42 Rules of Behavior
48 Acronym List EDD EHR ERS IHS RPMS Emergency Department Dashboard Electronic Health Record Emergency Room System Indian Health Service Resource and Patient Management System 43 Acronym List
49 Contact Information If you have any questions or comments regarding this distribution, please contact the OIT Help Desk (IHS). Phone: (505) or (888) (toll free) Fax: (505) Web: Contact Information
RESOURCE AND PATIENT MANAGEMENT SYSTEM. Drug Accountability (PSA) GUI Invoice Upload Program Installation and Configuration Guide
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Drug Accountability (PSA) GUI Invoice Upload Program Installation and Configuration Guide Version 1.0 Office of Information Technology (OIT) Division of Information
RESOURCE AND PATIENT MANAGEMENT SYSTEM Drug Accountability (PSA) GUI Invoice Upload Program Installation and Configuration Guide Version 1.0 Office of Information Technology (OIT) Division of Information
Practice Management Application Suite
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BPRM) Version 3.0 Office of Information Technology Division of Information Technology Table of Contents 1.0 Introduction...1
RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BPRM) Version 3.0 Office of Information Technology Division of Information Technology Table of Contents 1.0 Introduction...1
IHS Emergency Department Dashboard
 RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS Emergency Department Dashboard (BEDD) Version 1.0 Office of Information Technology Division of Information Resource Management Albuquerque, New Mexico Table of
RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS Emergency Department Dashboard (BEDD) Version 1.0 Office of Information Technology Division of Information Resource Management Albuquerque, New Mexico Table of
Behavioral Health System
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Behavioral Health System (AMH) Version 4.0 Patch 6 Office of Information Technology Division of Information Technology Table of Contents 1.0 Objective #1: Introduction
RESOURCE AND PATIENT MANAGEMENT SYSTEM Behavioral Health System (AMH) Version 4.0 Patch 6 Office of Information Technology Division of Information Technology Table of Contents 1.0 Objective #1: Introduction
Personal Health Record
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Personal Health Record (BPHR) Personal Health Record Web Portal Administrator Manual Version 2.0 Office of Information Technology (OIT) Division of Information Resource
RESOURCE AND PATIENT MANAGEMENT SYSTEM Personal Health Record (BPHR) Personal Health Record Web Portal Administrator Manual Version 2.0 Office of Information Technology (OIT) Division of Information Resource
IHS USER SECURITY AUDIT
 RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS USER SECURITY AUDIT (BUSA) Version 1.0 Office of Information Technology Division of Information Technology Albuquerque, New Mexico Table of Contents 1.0 Release
RESOURCE AND PATIENT MANAGEMENT SYSTEM IHS USER SECURITY AUDIT (BUSA) Version 1.0 Office of Information Technology Division of Information Technology Albuquerque, New Mexico Table of Contents 1.0 Release
Clinical Scheduling for Windows
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Clinical Scheduling for Windows (BSDX) Version 3.0 Office of Information Technology (OIT) Albuquerque, New Mexico Preface Security This manual contains the installation
RESOURCE AND PATIENT MANAGEMENT SYSTEM Clinical Scheduling for Windows (BSDX) Version 3.0 Office of Information Technology (OIT) Albuquerque, New Mexico Preface Security This manual contains the installation
U.S. Department of the Interior's Federal Information Systems Security Awareness Online Course
 U.S. Department of the Interior's Federal Information Systems Security Awareness Online Course Rules of Behavior Before you print your certificate of completion, please read the following Rules of Behavior
U.S. Department of the Interior's Federal Information Systems Security Awareness Online Course Rules of Behavior Before you print your certificate of completion, please read the following Rules of Behavior
MCCG PowerChart. Message Center Complete Manual. Hold the Ctrl key down & then left click on a link below to navigate to it:
 Hold the Ctrl key down & then left click on a link below to navigate to it: Table of Contents Overview of the Message Center Message Center Basics Working with the Message Journal Working with Documents
Hold the Ctrl key down & then left click on a link below to navigate to it: Table of Contents Overview of the Message Center Message Center Basics Working with the Message Journal Working with Documents
EMR DOCUMENTATION LYNX. Instructor Script
 EMR DOCUMENTATION LYNX Instructor Script Table of Contents TABLE OF CONTENTS INFORMATION SECURITY AND CONFIDENTIALITY... 4 OVERVIEW... 5 LEARNING OBJECTIVES... 5 TIPS AND TRICKS... 5 SOLUTION ICONS...
EMR DOCUMENTATION LYNX Instructor Script Table of Contents TABLE OF CONTENTS INFORMATION SECURITY AND CONFIDENTIALITY... 4 OVERVIEW... 5 LEARNING OBJECTIVES... 5 TIPS AND TRICKS... 5 SOLUTION ICONS...
Getting Started. Getting Started with Time Warner Cable Business Class. Voice Manager. A Guide for Administrators and Users
 Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Estate Agents Authority
 INFORMATION SECURITY AND PRIVACY PROTECTION POLICY AND GUIDELINES FOR ESTATE AGENTS Estate Agents Authority The contents of this document remain the property of, and may not be reproduced in whole or in
INFORMATION SECURITY AND PRIVACY PROTECTION POLICY AND GUIDELINES FOR ESTATE AGENTS Estate Agents Authority The contents of this document remain the property of, and may not be reproduced in whole or in
Resource Online User Guide JUNE 2013
 Resource Online User Guide JUNE 2013 CHASE PAYMENTECH SOLUTIONS MAKES NO WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, WITH REGARD TO THIS MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
Resource Online User Guide JUNE 2013 CHASE PAYMENTECH SOLUTIONS MAKES NO WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, WITH REGARD TO THIS MATERIAL, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES
Optum Patient Portal. 70 Royal Little Drive. Providence, RI 02904. Copyright 2002-2013 Optum. All rights reserved. Updated: 3/7/13
 Optum Patient Portal 70 Royal Little Drive Providence, RI 02904 Copyright 2002-2013 Optum. All rights reserved. Updated: 3/7/13 Table of Contents 1 Patient Portal Activation...1 1.1 Pre-register a Patient...1
Optum Patient Portal 70 Royal Little Drive Providence, RI 02904 Copyright 2002-2013 Optum. All rights reserved. Updated: 3/7/13 Table of Contents 1 Patient Portal Activation...1 1.1 Pre-register a Patient...1
eopf Release E Administrator Training Manual
 eopf Release E Administrator Training Manual i The United States Office Of Personnel Management eopf Administrator Training Manual for eopf v5 eopf Version 4.1, July 2007, March 2008, March 2009; eopf
eopf Release E Administrator Training Manual i The United States Office Of Personnel Management eopf Administrator Training Manual for eopf v5 eopf Version 4.1, July 2007, March 2008, March 2009; eopf
SUNY DOWNSTATE MEDICAL CENTER. Hospital Information Systems. Laboratory Information System. Cerner Millenium Pathnet
 SUNY DOWNSTATE MEDICAL CENTER Hospital Information Systems Laboratory Information System Cerner Millenium Pathnet June 2005 HOSPITAL INFORMATION SYSTEMS Cerner L.I.S. Reference Guide 2002, 2005 Maryam
SUNY DOWNSTATE MEDICAL CENTER Hospital Information Systems Laboratory Information System Cerner Millenium Pathnet June 2005 HOSPITAL INFORMATION SYSTEMS Cerner L.I.S. Reference Guide 2002, 2005 Maryam
User Manual for Web. Help Desk Authority 9.0
 User Manual for Web Help Desk Authority 9.0 2011ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic logo and Point,Click,Done! are trademarks and registered trademarks of ScriptLogic
User Manual for Web Help Desk Authority 9.0 2011ScriptLogic Corporation ALL RIGHTS RESERVED. ScriptLogic, the ScriptLogic logo and Point,Click,Done! are trademarks and registered trademarks of ScriptLogic
SIGN Surgical Database Training Manual
 Manual In addition to using the Online Surgical Database for single case entry, you can also use the Offline Data Entry Tool (ODET) to enter each case offline and then upload a batch of cases to the online
Manual In addition to using the Online Surgical Database for single case entry, you can also use the Offline Data Entry Tool (ODET) to enter each case offline and then upload a batch of cases to the online
Information Security
 Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA)
 UNIVERSITY OF PITTSBURGH POLICY SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA) DATE: March 18, 2005 I. SCOPE This
UNIVERSITY OF PITTSBURGH POLICY SUBJECT: SECURITY OF ELECTRONIC MEDICAL RECORDS COMPLIANCE WITH THE HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT OF 1996 (HIPAA) DATE: March 18, 2005 I. SCOPE This
Soarian Clinicals Training Manual. For Current Nursing Staff Migrating From Siemens NetAccess to Soarian Clinicals
 Soarian Clinicals Training Manual For Current Nursing Staff Migrating From Siemens NetAccess to Soarian Clinicals Prepared By: Amelia Griggs Information Management Siemens Health Services at Holy Redeemer
Soarian Clinicals Training Manual For Current Nursing Staff Migrating From Siemens NetAccess to Soarian Clinicals Prepared By: Amelia Griggs Information Management Siemens Health Services at Holy Redeemer
Sunrise Clinical Manager (SCM) View-Only Training
 Sunrise Clinical Manager (SCM) View-Only Training General Use Guide UK Hosp, Staff Education July 06 1 Logging on to SCM At the desktop, double click on the Sunrise Clinical Manager icon. OR At the bottom
Sunrise Clinical Manager (SCM) View-Only Training General Use Guide UK Hosp, Staff Education July 06 1 Logging on to SCM At the desktop, double click on the Sunrise Clinical Manager icon. OR At the bottom
Remote Access Agreement
 Purpose: The purpose of this agreement is to define standards, procedures, and restrictions for connecting to Wayne Public Schools internal network(s) from external hosts (e.g., your home computer) via
Purpose: The purpose of this agreement is to define standards, procedures, and restrictions for connecting to Wayne Public Schools internal network(s) from external hosts (e.g., your home computer) via
ETS. Major Field Tests. Proctor Administrator Manual
 ETS Major Field Tests Proctor Administrator Manual Updated: December 2010 Table of Contents Contents 1.0 WELCOME... 1 1.1 INTRODUCTION... 1 1.2 SYSTEM REQUIREMENTS AND SETTING-UP STUDENT WORKSTATIONS...
ETS Major Field Tests Proctor Administrator Manual Updated: December 2010 Table of Contents Contents 1.0 WELCOME... 1 1.1 INTRODUCTION... 1 1.2 SYSTEM REQUIREMENTS AND SETTING-UP STUDENT WORKSTATIONS...
Affiliated Provider Billing/Coding
 Affiliated Provider Billing/Coding ED BILLING USING FIRSTNET Table of Contents Affiliated Provider ED Billing...2 icentra FirstNet...2 Accessing FirstNet...2 To access FirstNet:...2 Checking In as a Provider...2
Affiliated Provider Billing/Coding ED BILLING USING FIRSTNET Table of Contents Affiliated Provider ED Billing...2 icentra FirstNet...2 Accessing FirstNet...2 To access FirstNet:...2 Checking In as a Provider...2
HIPAA Information Security Overview
 HIPAA Information Security Overview Security Overview HIPAA Security Regulations establish safeguards for protected health information (PHI) in electronic format. The security rules apply to PHI that is
HIPAA Information Security Overview Security Overview HIPAA Security Regulations establish safeguards for protected health information (PHI) in electronic format. The security rules apply to PHI that is
DAISY 4.2. New features. Electronic prescribing with erx Integrated credit card processing with DAISY InCharge
 DAISY 4.2 New features Electronic prescribing with erx Integrated credit card processing with DAISY InCharge DAISY 4.2 Update Release Notes 1 What s New in DAISY 4.2... 1 New Features... 1 Other Enhancements
DAISY 4.2 New features Electronic prescribing with erx Integrated credit card processing with DAISY InCharge DAISY 4.2 Update Release Notes 1 What s New in DAISY 4.2... 1 New Features... 1 Other Enhancements
HIPAA Security Training Manual
 HIPAA Security Training Manual The final HIPAA Security Rule for Montrose Memorial Hospital went into effect in February 2005. The Security Rule includes 3 categories of compliance; Administrative Safeguards,
HIPAA Security Training Manual The final HIPAA Security Rule for Montrose Memorial Hospital went into effect in February 2005. The Security Rule includes 3 categories of compliance; Administrative Safeguards,
Practice Management Application Suite
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BPRM) Version 3.0 Office of Information Technology Division of Information Technology Table of Contents 1.0 Introduction...
RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BPRM) Version 3.0 Office of Information Technology Division of Information Technology Table of Contents 1.0 Introduction...
End User Configuration
 CHAPTER114 The window in Cisco Unified Communications Manager Administration allows the administrator to add, search, display, and maintain information about Cisco Unified Communications Manager end users.
CHAPTER114 The window in Cisco Unified Communications Manager Administration allows the administrator to add, search, display, and maintain information about Cisco Unified Communications Manager end users.
PHYSICIAN USER EMR QUICK REFERENCE MANUAL
 PHYSICIAN USER EMR QUICK REFERENCE MANUAL Epower 4/30/2012 Table of Contents Accessing the system. 3 User Identification Area.. 3 Viewing ED Activity. 4 Accessing patient charts. 4 Documentation Processes.
PHYSICIAN USER EMR QUICK REFERENCE MANUAL Epower 4/30/2012 Table of Contents Accessing the system. 3 User Identification Area.. 3 Viewing ED Activity. 4 Accessing patient charts. 4 Documentation Processes.
May 2015 VERSION 02. Capacity Management Quick Reference Guide
 May 2015 VERSION 02 Capacity Management Quick Reference Guide Table of Contents Capacity Management Background... 1 Superuser Role... 1 Gadget Summary and Functionality... 2 Patient List... 2 Discharge
May 2015 VERSION 02 Capacity Management Quick Reference Guide Table of Contents Capacity Management Background... 1 Superuser Role... 1 Gadget Summary and Functionality... 2 Patient List... 2 Discharge
PowerSchool Parent Portal User Guide. PowerSchool 7.x Student Information System
 PowerSchool 7.x Student Information System Released December 2011 Document Owner: Documentation Services This edition applies to Release 7.1 of the [product name] software and to all subsequent releases
PowerSchool 7.x Student Information System Released December 2011 Document Owner: Documentation Services This edition applies to Release 7.1 of the [product name] software and to all subsequent releases
Practice Management Application Suite
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BPRM) Version 3.0 Office of Information Technology (OIT) Division of Information Technology Table of Contents 1.0 Introduction...
RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BPRM) Version 3.0 Office of Information Technology (OIT) Division of Information Technology Table of Contents 1.0 Introduction...
Individuals Authorized Access to the CMS Computer Services (IACS) User Guide for the Help Desk
 Individuals Authorized Access to the CMS Computer Services (IACS) User Guide for the Help Desk Document Version 5.0 Document No.: IACS.UG.5.0 Contract No.: HHSM-500-2007-00024I Prepared for: Centers for
Individuals Authorized Access to the CMS Computer Services (IACS) User Guide for the Help Desk Document Version 5.0 Document No.: IACS.UG.5.0 Contract No.: HHSM-500-2007-00024I Prepared for: Centers for
ITS ebilling. User s Training Manual
 ITS ebilling User s Training Manual Version 1.0 November 3, 2008 Page 1 of 85 Table of Contents ebilling Training URL --------------------------------------------------------------------------- 3 ebilling
ITS ebilling User s Training Manual Version 1.0 November 3, 2008 Page 1 of 85 Table of Contents ebilling Training URL --------------------------------------------------------------------------- 3 ebilling
Institution/Department Administrator Manual
 ETS Major Field Tests Institution/Department Administrator Manual Updated: December 2010 Table of Contents 1.0 WELCOME... 1 1.1 INTRODUCTION... 1 1.2 COMPUTER HARDWARE AND SOFTWARE REQUIREMENTS... 1 2.0
ETS Major Field Tests Institution/Department Administrator Manual Updated: December 2010 Table of Contents 1.0 WELCOME... 1 1.1 INTRODUCTION... 1 1.2 COMPUTER HARDWARE AND SOFTWARE REQUIREMENTS... 1 2.0
NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT
 NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT INSTRUCTION GUIDE For Natural Person Credit Unions NCUA 10200 (REV 4) Table of Contents A. Introduction...
NATIONAL CREDIT UNION ADMINISTRATION CREDIT UNION ONLINE: CREDIT UNION PROFILE AND 5300 CALL REPORT INSTRUCTION GUIDE For Natural Person Credit Unions NCUA 10200 (REV 4) Table of Contents A. Introduction...
Contact Manager and Document Tracking. CampusVue Student User Guide
 Contact Manager and Document Tracking CampusVue Student User Guide Campus Management Corporation Web Site http://www.campusmanagement.com/ E-mail Information: Support: E-mail form on Web site [email protected]
Contact Manager and Document Tracking CampusVue Student User Guide Campus Management Corporation Web Site http://www.campusmanagement.com/ E-mail Information: Support: E-mail form on Web site [email protected]
Getting Started. Business Link. User Name Rules. Hardware/Software Requirements. Password Rules
 Getting Started User Name Rules All user names must: Be unique. Be between six and 40 characters in length. Notes: It is recommended that user names consist only of alphanumeric characters (A-Z, 0-9).
Getting Started User Name Rules All user names must: Be unique. Be between six and 40 characters in length. Notes: It is recommended that user names consist only of alphanumeric characters (A-Z, 0-9).
SCM Training For Nursing Staff
 SCM Training For Nursing Staff UK Hosp, Staff Education August 06 1 Resources and Help Support Center: 323-8586 Useful Web Sites Learning Center Web page http://www.mc.uky.edu/learningcenter ICIS Web page
SCM Training For Nursing Staff UK Hosp, Staff Education August 06 1 Resources and Help Support Center: 323-8586 Useful Web Sites Learning Center Web page http://www.mc.uky.edu/learningcenter ICIS Web page
AT&T Voice DNA User Guide
 AT&T Voice DNA User Guide Page 1 Table of Contents GET STARTED... 4 Log In... 5 About the User Dashboard... 9 Manage Personal Profile... 15 Manage Messages... 17 View and Use Call Logs... 22 Search the
AT&T Voice DNA User Guide Page 1 Table of Contents GET STARTED... 4 Log In... 5 About the User Dashboard... 9 Manage Personal Profile... 15 Manage Messages... 17 View and Use Call Logs... 22 Search the
PowerChart Cerner Millennium System
 PowerChart Cerner Millennium System Non-Physician Training Manual Clinical Information System Team MCG Health, Inc. 1120 15 th Street Augusta, Georgia 30912 Version 3 Table of Contents 1. About the PowerChart
PowerChart Cerner Millennium System Non-Physician Training Manual Clinical Information System Team MCG Health, Inc. 1120 15 th Street Augusta, Georgia 30912 Version 3 Table of Contents 1. About the PowerChart
NETWORK PRINT MONITOR User Guide
 NETWORK PRINT MONITOR User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
NETWORK PRINT MONITOR User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
The United States Office Of Personnel Management eopf System Administrator Training Manual for eopf Version 4.0.
 The United States Office Of Personnel Management eopf System Administrator Training Manual for eopf Version 4.0. Copyright 1994-2007 by Northrop Grumman. All rights reserved. Northrop Grumman, the Northrop
The United States Office Of Personnel Management eopf System Administrator Training Manual for eopf Version 4.0. Copyright 1994-2007 by Northrop Grumman. All rights reserved. Northrop Grumman, the Northrop
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
Contact Center Administrator Guide
 ServicePattern Version 3.6 Revision SP36-CCADM-41855 Bright Pattern, Inc. 1111 Bayhill Drive, Suite 275, San Bruno, CA 94066 Phone: +1 (650) 529.4099 Fax: +1 (415) 480.1782 www.brightpattern.com 2010-2014
ServicePattern Version 3.6 Revision SP36-CCADM-41855 Bright Pattern, Inc. 1111 Bayhill Drive, Suite 275, San Bruno, CA 94066 Phone: +1 (650) 529.4099 Fax: +1 (415) 480.1782 www.brightpattern.com 2010-2014
Inpatient Cerner Navigation and Documentation For Nursing Students
 Inpatient Cerner Navigation and Documentation For Nursing Students Audience Note: Purpose: Objectives: Cerner PowerChart training is for all students in the following inpatient areas Med/Surg, OSNO, Oncology,
Inpatient Cerner Navigation and Documentation For Nursing Students Audience Note: Purpose: Objectives: Cerner PowerChart training is for all students in the following inpatient areas Med/Surg, OSNO, Oncology,
Basic ebusiness Banking User Guide
 Basic ebusiness Banking User Guide 1 Welcome: Welcome to Chemical Bank s ebusiness Banking system. With ebusiness Banking, you can access your accounts 24-hours a day, seven days a week; anywhere an Internet
Basic ebusiness Banking User Guide 1 Welcome: Welcome to Chemical Bank s ebusiness Banking system. With ebusiness Banking, you can access your accounts 24-hours a day, seven days a week; anywhere an Internet
B. WORKING WITH SCHEDULES...6 1. Daily Schedule... 6 2. Clinical Toolbar...7 3. Personalize...8 4. Multiple Provider Schedules...8
 A. OVERVIEW OF JUP EMR...2 1. Logging in and Logging out...2 2. Vertical Toolbar...3 3. Horizontal Toolbar...3 4. Site Selector VTB...4 5. Locking the Session...5 6. Toolplace...5 B. WORKING WITH SCHEDULES...6
A. OVERVIEW OF JUP EMR...2 1. Logging in and Logging out...2 2. Vertical Toolbar...3 3. Horizontal Toolbar...3 4. Site Selector VTB...4 5. Locking the Session...5 6. Toolplace...5 B. WORKING WITH SCHEDULES...6
Provider Electronic Solutions Software User s Guide
 Vermont Title XIX Provider Electronic Solutions Software User s Guide HP ENTERPRISE SERVICES 312 HURRICANE LANE, STE 101 PO BOX 888 WILLISTON VT 05495 Table of Contents 1 Introduction... 2 1.1 Provider
Vermont Title XIX Provider Electronic Solutions Software User s Guide HP ENTERPRISE SERVICES 312 HURRICANE LANE, STE 101 PO BOX 888 WILLISTON VT 05495 Table of Contents 1 Introduction... 2 1.1 Provider
Information Security Policy September 2009 Newman University IT Services. Information Security Policy
 Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Contents 1. Statement 1.1 Introduction 1.2 Objectives 1.3 Scope and Policy Structure 1.4 Risk Assessment and Management 1.5 Responsibilities for Information Security 2. Compliance 3. HR Security 3.1 Terms
Network and Workstation Acceptable Use Policy
 CONTENT: Introduction Purpose Policy / Procedure References INTRODUCTION Information Technology services including, staff, workstations, peripherals and network infrastructures are an integral part of
CONTENT: Introduction Purpose Policy / Procedure References INTRODUCTION Information Technology services including, staff, workstations, peripherals and network infrastructures are an integral part of
HIPAA Privacy and Security. Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012
 HIPAA Privacy and Security Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012 Goals and Objectives Course Goal: To introduce the staff of Munson Healthcare to the concepts
HIPAA Privacy and Security Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012 Goals and Objectives Course Goal: To introduce the staff of Munson Healthcare to the concepts
CSOS Certificate Support Guide. Version: 1.1 Published: October 1, 2006 Publisher: CSOS Certification Authority
 Version: 1.1 Published: October 1, 2006 Publisher: CSOS Certification Authority Document Revision History Version # Revision Sections Summary of Changes Initials Date Affected 1.0 4/27/2006 All Version
Version: 1.1 Published: October 1, 2006 Publisher: CSOS Certification Authority Document Revision History Version # Revision Sections Summary of Changes Initials Date Affected 1.0 4/27/2006 All Version
Procedure Title: TennDent HIPAA Security Awareness and Training
 Procedure Title: TennDent HIPAA Security Awareness and Training Number: TD-QMP-P-7011 Subject: Security Awareness and Training Primary Department: TennDent Effective Date of Procedure: 9/23/2011 Secondary
Procedure Title: TennDent HIPAA Security Awareness and Training Number: TD-QMP-P-7011 Subject: Security Awareness and Training Primary Department: TennDent Effective Date of Procedure: 9/23/2011 Secondary
The United States Office Of Personnel Management eopf Human Resources Specialist Training Manual for eopf Version 4.0.
 The United States Office Of Personnel Management eopf Human Resources Specialist Training Manual for eopf Version 4.0. Copyright 1994-2007 by Northrop Grumman. All rights reserved. Northrop Grumman, the
The United States Office Of Personnel Management eopf Human Resources Specialist Training Manual for eopf Version 4.0. Copyright 1994-2007 by Northrop Grumman. All rights reserved. Northrop Grumman, the
Sunrise Acute Care (SAC) Module 1 New Provider Basic Course
 Sunrise Acute Care (SAC) Module 1 New Provider Basic Course May 2013 Sunrise Acute Care Training Consists of 5 modules To gain access to Acute Care you will need to: Complete all 5 modules Pass the Acute
Sunrise Acute Care (SAC) Module 1 New Provider Basic Course May 2013 Sunrise Acute Care Training Consists of 5 modules To gain access to Acute Care you will need to: Complete all 5 modules Pass the Acute
Cox Business Premium Online Backup USER'S GUIDE. Cox Business VERSION 1.0
 Cox Business Premium Online Backup USER'S GUIDE Cox Business VERSION 1.0 Table of Contents ABOUT THIS GUIDE... 4 DOWNLOADING COX BUSINESS PREMIUM ONLINE BACKUP... 5 INSTALLING COX BUSINESS PREMIUM ONLINE
Cox Business Premium Online Backup USER'S GUIDE Cox Business VERSION 1.0 Table of Contents ABOUT THIS GUIDE... 4 DOWNLOADING COX BUSINESS PREMIUM ONLINE BACKUP... 5 INSTALLING COX BUSINESS PREMIUM ONLINE
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access
 Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Quick Reference Guide SoftPhone for Windows 7
 Introduction Quick Reference Guide SoftPhone for Windows 7 SoftPhone is software that allows you to use your NASA phone number from your NASA-issued computer to place or/and receive calls. You can also
Introduction Quick Reference Guide SoftPhone for Windows 7 SoftPhone is software that allows you to use your NASA phone number from your NASA-issued computer to place or/and receive calls. You can also
Strategic Asset Tracking System User Guide
 Strategic Asset Tracking System User Guide Contents 1 Overview 2 Web Application 2.1 Logging In 2.2 Navigation 2.3 Assets 2.3.1 Favorites 2.3.3 Purchasing 2.3.4 User Fields 2.3.5 History 2.3.6 Import Data
Strategic Asset Tracking System User Guide Contents 1 Overview 2 Web Application 2.1 Logging In 2.2 Navigation 2.3 Assets 2.3.1 Favorites 2.3.3 Purchasing 2.3.4 User Fields 2.3.5 History 2.3.6 Import Data
DarwiNet Client Level
 DarwiNet Client Level Table Of Contents Welcome to the Help area for your online payroll system.... 1 Getting Started... 3 Welcome to the Help area for your online payroll system.... 3 Logging In... 4
DarwiNet Client Level Table Of Contents Welcome to the Help area for your online payroll system.... 1 Getting Started... 3 Welcome to the Help area for your online payroll system.... 3 Logging In... 4
Management Tools Quiz Answers
 Management Tools Quiz Answers 70 Royal Little Drive Providence, RI 02904 Copyright 2002-2010 Ingenix. All rights reserved. General Navigation and Help 1) How do you send messages within CareTracker? a)
Management Tools Quiz Answers 70 Royal Little Drive Providence, RI 02904 Copyright 2002-2010 Ingenix. All rights reserved. General Navigation and Help 1) How do you send messages within CareTracker? a)
Getting Started with IntelleView POS Administrator Software
 Getting Started with IntelleView POS Administrator Software Administrator s Guide for Software Version 1.2 About this Guide This administrator s guide explains how to start using your IntelleView POS (IntelleView)
Getting Started with IntelleView POS Administrator Software Administrator s Guide for Software Version 1.2 About this Guide This administrator s guide explains how to start using your IntelleView POS (IntelleView)
Nursing Home Facility Implementation Overview
 DrConnect Improved Communication; Improved Care Nursing Home Facility Implementation Overview clevelandclinic.org/drconnect Cleveland Clinic 1995-2013. All Rights Reserved. Table of Contents Table of Contents...2
DrConnect Improved Communication; Improved Care Nursing Home Facility Implementation Overview clevelandclinic.org/drconnect Cleveland Clinic 1995-2013. All Rights Reserved. Table of Contents Table of Contents...2
MacScan. MacScan User Guide. Detect, Isolate and Remove Spyware
 MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
Table of Contents. Overview of the TEA Login Application... 1. Features... 1. Roles in Obtaining Application Access... 1. Approval Process...
 TEAL Help Table of Contents Overview of the TEA Login Application... 1 Features... 1 Roles in Obtaining Application Access... 1 Approval Process... 2 Processing an Application Request... 4 The Process
TEAL Help Table of Contents Overview of the TEA Login Application... 1 Features... 1 Roles in Obtaining Application Access... 1 Approval Process... 2 Processing an Application Request... 4 The Process
Critical Care EEG Database Public Edition. User Manual
 Critical Care EEG Database Public Edition User Manual v. 9/25/2015 Table of Contents Overview... 2 Installation... 2 Basic Structure 2 Installing the Files 3 Connecting to Data 4 Configuration... 4 System
Critical Care EEG Database Public Edition User Manual v. 9/25/2015 Table of Contents Overview... 2 Installation... 2 Basic Structure 2 Installing the Files 3 Connecting to Data 4 Configuration... 4 System
CareAware Capacity Management - Patient Flow Patient List Gadget
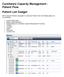 CareAware Capacity Management - Patient Flow Patient List Gadget When using the Patient List gadget in CareAware Patient Flow, the following tasks can be completed: Launch PowerChart Modify Patient Attributes
CareAware Capacity Management - Patient Flow Patient List Gadget When using the Patient List gadget in CareAware Patient Flow, the following tasks can be completed: Launch PowerChart Modify Patient Attributes
VanillaSoft. Administrator s Manual
 VanillaSoft Administrator s Manual Copyright 2009 VanillaSoft Inc. Contents Contents Overview... 5 This Manual...5 Sections...5 Conventions and Terminology...5 VanillaSoft...6 Basics...6 Logging In...7
VanillaSoft Administrator s Manual Copyright 2009 VanillaSoft Inc. Contents Contents Overview... 5 This Manual...5 Sections...5 Conventions and Terminology...5 VanillaSoft...6 Basics...6 Logging In...7
National Government Services Connex Quick Steps
 National Government Services Connex Quick Steps Table of Contents Table of Contents... 1 Detailed Setup Instructions... 3 Detailed setup instructions for new Connex users are available by going to http://www.ngsmedicare.com
National Government Services Connex Quick Steps Table of Contents Table of Contents... 1 Detailed Setup Instructions... 3 Detailed setup instructions for new Connex users are available by going to http://www.ngsmedicare.com
Practice Management Application Suite
 RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BMW) Version 2.0 Office of Information Technology Division of Information Technology Albuquerque, New Mexico Table of Contents
RESOURCE AND PATIENT MANAGEMENT SYSTEM Practice Management Application Suite (BMW) Version 2.0 Office of Information Technology Division of Information Technology Albuquerque, New Mexico Table of Contents
EMR DOCUMENTATION LYNX. Instructor Script
 EMR DOCUMENTATION LYNX Instructor Script 1 Table of Contents Table of Contents INFORMATION SECURITY AND CONFIDENTIALITY... 4 OVERVIEW... 5 LEARNING OBJECTIVES... 5 AUDIENCE... 5 SIGNING ON... 6 KH ED
EMR DOCUMENTATION LYNX Instructor Script 1 Table of Contents Table of Contents INFORMATION SECURITY AND CONFIDENTIALITY... 4 OVERVIEW... 5 LEARNING OBJECTIVES... 5 AUDIENCE... 5 SIGNING ON... 6 KH ED
ScriptLogic File System Auditor User Guide
 ScriptLogic File System Auditor User Guide FILE SYSTEM AUDITOR I 2005 by ScriptLogic Corporation All rights reserved. This publication is protected by copyright and all rights are reserved by ScriptLogic
ScriptLogic File System Auditor User Guide FILE SYSTEM AUDITOR I 2005 by ScriptLogic Corporation All rights reserved. This publication is protected by copyright and all rights are reserved by ScriptLogic
Data Management Policies. Sage ERP Online
 Sage ERP Online Sage ERP Online Table of Contents 1.0 Server Backup and Restore Policy... 3 1.1 Objectives... 3 1.2 Scope... 3 1.3 Responsibilities... 3 1.4 Policy... 4 1.5 Policy Violation... 5 1.6 Communication...
Sage ERP Online Sage ERP Online Table of Contents 1.0 Server Backup and Restore Policy... 3 1.1 Objectives... 3 1.2 Scope... 3 1.3 Responsibilities... 3 1.4 Policy... 4 1.5 Policy Violation... 5 1.6 Communication...
End User Training Guide
 End User Training Guide October 2013 2005-2013 ExpenseWire LLC. All rights reserved. 1 expensewire.com Use of this user documentation is subject to the terms and conditions of the applicable End- User
End User Training Guide October 2013 2005-2013 ExpenseWire LLC. All rights reserved. 1 expensewire.com Use of this user documentation is subject to the terms and conditions of the applicable End- User
MHC CareMail User Guide
 MHC CareMail User Guide Get Started with MHC CareMail Secure Communications Version 1.7 Table of Contents About MHC CareMail Communications... 4 Getting Started with... 5 Your MHC CareMail Account... 5
MHC CareMail User Guide Get Started with MHC CareMail Secure Communications Version 1.7 Table of Contents About MHC CareMail Communications... 4 Getting Started with... 5 Your MHC CareMail Account... 5
3 Easy Steps to Get Started
 Quick Start Guide Contents 1. What is icafe Manager?... 4 1.1. Server... 4 1.2. Client Terminal... 4 2. Downloading, Registering & Activating Cafe Code... 5 2.1. Downloading icafe Manager:... 5 2.2. Registering
Quick Start Guide Contents 1. What is icafe Manager?... 4 1.1. Server... 4 1.2. Client Terminal... 4 2. Downloading, Registering & Activating Cafe Code... 5 2.1. Downloading icafe Manager:... 5 2.2. Registering
Department of Homeland Security Management Directive System MD Number: 4900 INDIVIDUAL USE AND OPERATION OF DHS INFORMATION SYSTEMS/ COMPUTERS
 Department of Homeland Security Management Directive System MD Number: 4900 INDIVIDUAL USE AND OPERATION OF DHS INFORMATION SYSTEMS/ COMPUTERS 1. Purpose This directive establishes the Department of Homeland
Department of Homeland Security Management Directive System MD Number: 4900 INDIVIDUAL USE AND OPERATION OF DHS INFORMATION SYSTEMS/ COMPUTERS 1. Purpose This directive establishes the Department of Homeland
BounceBack User Guide
 Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
Table Of Contents 1. Table of Contents... 2 2. 1-0 Introduction... 3 2.1 1-0: Introduction... 4 2.2 1-1: BounceBack Software Overview... 6 3. 2-0 Navigating the BounceBack Control Center... 9 3.1 2-0:
2. _General Help and Technical Support
 1. _Welcome Welcome to Business Internet Banking. Our online service is available 06:00 AM ET 12:00 AM (Midnight) ET, seven days a week, so you and your employees can manage your business banking accounts
1. _Welcome Welcome to Business Internet Banking. Our online service is available 06:00 AM ET 12:00 AM (Midnight) ET, seven days a week, so you and your employees can manage your business banking accounts
Provider Services Portal (PSP) Enrollment & Functionality Manual Provider Services Portal (PSP) Enrollment & Functionality Manual
 Provider Services Portal (PSP) Enrollment & Functionality Manual 1 Table of Contents PSP Website Home page... 3 PSP Enrollment... 3 E-Authentication Identity Proofing... 3 User Password Security and Protection...
Provider Services Portal (PSP) Enrollment & Functionality Manual 1 Table of Contents PSP Website Home page... 3 PSP Enrollment... 3 E-Authentication Identity Proofing... 3 User Password Security and Protection...
HIPAA Security. 2 Security Standards: Administrative Safeguards. Security Topics
 HIPAA Security SERIES Security Topics 1. Security 101 for Covered Entities 5. 2. Security Standards - Organizational, Security Policies Standards & Procedures, - Administrative and Documentation Safeguards
HIPAA Security SERIES Security Topics 1. Security 101 for Covered Entities 5. 2. Security Standards - Organizational, Security Policies Standards & Procedures, - Administrative and Documentation Safeguards
TOPS v3.2.1 Calendar/Scheduler User Guide. By TOPS Software, LLC Clearwater, Florida
 TOPS v3.2.1 Calendar/Scheduler User Guide By TOPS Software, LLC Clearwater, Florida Document History Version Edition Date Document Software Trademark Copyright First Edition Second Edition 02 2007 09-2007
TOPS v3.2.1 Calendar/Scheduler User Guide By TOPS Software, LLC Clearwater, Florida Document History Version Edition Date Document Software Trademark Copyright First Edition Second Edition 02 2007 09-2007
Contact Center Administrator Guide
 ServicePattern Version 3.7 Revision SP37-CCADM-42059 Bright Pattern, Inc. 1111 Bayhill Drive, Suite 275, San Bruno, CA 94066 Phone: +1 (650) 529.4099 Fax: +1 (415) 480.1782 www.brightpattern.com 2010-2015
ServicePattern Version 3.7 Revision SP37-CCADM-42059 Bright Pattern, Inc. 1111 Bayhill Drive, Suite 275, San Bruno, CA 94066 Phone: +1 (650) 529.4099 Fax: +1 (415) 480.1782 www.brightpattern.com 2010-2015
Transitioning from TurningPoint 5 to TurningPoint Cloud - LMS 1
 Transitioning from TurningPoint 5 to TurningPoint Cloud - LMS 1 A Turning Account is a unique identifier that is used to tie together all software accounts and response devices. A Turning Account is required
Transitioning from TurningPoint 5 to TurningPoint Cloud - LMS 1 A Turning Account is a unique identifier that is used to tie together all software accounts and response devices. A Turning Account is required
UniCom with Office Communicator and Live Meeting. Quick Start Guide
 UniCom with Office Communicator and Live Meeting Quick Start Guide Table of Contents Understanding UniCom and Office Communicator... 1 What is UniCom?... 1 What Is Office Communicator?... 1 Who Can Use
UniCom with Office Communicator and Live Meeting Quick Start Guide Table of Contents Understanding UniCom and Office Communicator... 1 What is UniCom?... 1 What Is Office Communicator?... 1 Who Can Use
EXPRESSPATH PROVIDER PORTAL USER GUIDE AUGUST 2013
 EXPRESSPATH PROVIDER PORTAL USER GUIDE AUGUST 2013 2013-2020 Express Scripts, Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic
EXPRESSPATH PROVIDER PORTAL USER GUIDE AUGUST 2013 2013-2020 Express Scripts, Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic
How To Use Swol On Pcode (For Athletes)
 101 Tosca Drive Stoughton, MA 02072 USA (Phone) 781.297-2034 (FAX) 781.297-2039 (Web) www.csmisolutions.com SportsWareOnLine User Manual SportsWare and SportsWareOnLine are trademarks of Computer Sports
101 Tosca Drive Stoughton, MA 02072 USA (Phone) 781.297-2034 (FAX) 781.297-2039 (Web) www.csmisolutions.com SportsWareOnLine User Manual SportsWare and SportsWareOnLine are trademarks of Computer Sports
enicq 5 System Administrator s Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Our website Internet Banking
 Our website Internet Banking A safe and efficient way of accessing your People s Choice Credit Union accounts, paying bills and transferring money. 1 Contents 1. Security, system requirements and cookies...3
Our website Internet Banking A safe and efficient way of accessing your People s Choice Credit Union accounts, paying bills and transferring money. 1 Contents 1. Security, system requirements and cookies...3
PROPHIX Reporting What is PROPHIX?
 ALA Financial System PROPHIX Reporting What is PROPHIX? ALA s Financial System upgrade is comprised of three new software solutions: 1. Bill Payment Process (BPP), a Microsoft SharePoint web-based platform
ALA Financial System PROPHIX Reporting What is PROPHIX? ALA s Financial System upgrade is comprised of three new software solutions: 1. Bill Payment Process (BPP), a Microsoft SharePoint web-based platform
Kaspersky Password Manager USER GUIDE
 Kaspersky Password Manager USER GUIDE Dear User! Thank you for choosing our product. We hope that this documentation helps you in your work and provides answers you may need. Any type of reproduction or
Kaspersky Password Manager USER GUIDE Dear User! Thank you for choosing our product. We hope that this documentation helps you in your work and provides answers you may need. Any type of reproduction or
