Content&Security RECOMMENDED(BEST(PRACTICES
|
|
|
- Vivien Stone
- 10 years ago
- Views:
Transcription
1 Content&Security RECOMMENDED(BEST(PRACTICES for(production(&(post(production(/(editorial( Version(16.2 MANAGEMENT(CONTROLS PERSONNEL(AND(RESOURCES(/(PRODUCTION(OFFICE ASSET(MANAGEMENT(/(CAMERA(MEDIA PHYSICAL(SECURITY IT(SECURITY TRAINING(AND(AWARENESS INCIDENT(MANAGEMENT(AND(RECOVERY(PLANNING EDITORIAL(/(DIGITAL(WORKFLOW SCRIPT(HANDLING( 1
2 INTRODUCTION( The(aim(of(this(framework(is(to(recommend(Best(Practices(for(securing(content(and(confidential(information(on[location( productions(and(the(post[production(editorial(spaces.( It(is(very(important(that(the(assessment(of(risks(in(these(areas(to(be(completely(without(interruption(to(the(creative(process,(and( should(not(interfere(with(the(operational(efficiencies(of(the(production(and(post(production(/(editorial(process. The(process(is(designed(to(encompass(all(stakeholders(in(the(Production(and(Post(Production(/(Editorial(process.(The(objective(is(to( promote(a(responsible(security(culture(on(commencement(of(the(project(and(to(introduce(a(structured(approach(when(determining( security(requirements During(the(projects(planning(phases(an(initial(assessment(against(the(Recommended(Best(Practices(will(be(completed(to(identify( any(potential(risks(that(need(consideration.((component(elements(for(content(protection(and(the(types(of(assets(to(be(protected( will(be(identified.(personnel(to(be(engaged(should(be(properly(briefed(in(advance(of(the(risk(assessment. An(assessment(report(will(be(submitted(to(the(project(management(team.(The(report(will(consider(the(relevant(controls(suggested( for(consideration(to(increase(security(and(mitigate(risk(of(loss(of(content(or(confidential(information(during(the(project(and(make( recommendation(on(implementation.(the(assessor(will(remain(available(to(assist(development(as(instructed. The(result(of(the(initial(assessment(will(be(documented(on(an(Assessor(Checklist((Appendix( A ).(Not(all(projects(will(require(every( Operational(Recommendation,(therefore(where(not(applicable(the(reason(will(be(recorded(within(the(Assessor(Checklist.( The(security(Recommended(Best(Practices(utilize(the(following(terms: Security:&The(preservation(of(confidential(intellectual(property(and(protection(of(media(related(assets,( against(all(threats,(whether(internal(or(external,(accidental(or(deliberate.( Recommendation:&&WHAT(to(do( Process&or&Procedure:&HOW(to(do(it( Role:&WHO(is(responsible(and/or(accountable(including(any(corresponding(competencies( Responsibility:&What(task/s(an(individual(is(accountable(for(in(accordance(with(any(policy(or(procedure Schedule:&WHEN(an(action(is(performed( 2
3 1 MANAGEMENT(CONTROLS 1.1 Documentation %&Produce&and&maintain&a&set&of&security&documents&or&work&instructions&for&content&and&site&security. %&Disseminate&security&related&requirements&to&all&persons&engaged&on&the&project.&Include&any&remote&locations&and&third&parties.&Set& out&specific&roles&and&responsibilities&for&security. %&Engage&and&promote&the&process&at&a&senior&management&level. %&Capture&signatures&of&acceptance&for&understanding&the&requirements&and&specific&roles&and&responsibilities. 1.2 Risk.Management %&Using&this&guideline&and&other&relevant&industry&best&practice&conduct&an&initial&review&of&activities.&Involve&management&and&key& stakeholders&to&identify&all&potential&security&related&risk. %&Engage&a&studio&or&producer&approved&third&party&to&assist&in&the&assessment&process&and&implementation&of&controls. %&Ensure&management&reviews&are&conducted&periodically&or&when&changes&in&content&related&activity&occur. 1.3 Compliance %&Review&procedures,&practices&and&implementation&to&ensure&ongoing&compliance&with&this&guideline&and&security&requirements. 3
4 2 2.1 PERSONNEL(AND(RESOURCES(/(PRODUCTION(OFFICE Personnel.and.Resources %&Appoint&an&individual&to&be&responsible&for&project&and&content&security. %&Ensure&they&have&suitable&skills,&capabilities&and&knowledge. %&Define&roles&and&responsibilities&for&content&security&and&asset&protection.&Document&them. %&Ensure&personnel&security&procedures&and&practices&are&implemented&and&that&they&are&understood&by&all&personnel. %&Appropriate&background&screening&will&be&conducted&where&required. %&Confidentiality&and&nonIdisclosure&agreements&should&have&been&signed&and&retained&prior&to&project&commencement.&These&should& be&maintained&for&changes&in&resources&for&the&projects&duration General.Guidelines %&All&General&Content&Security&Guidelines&listed&in&Section&8.1&below&also&apply&to&the&Production&Office,&as&well&as&all&members&of&the& crew&and&cast,&where&relevant. Production.Office %&Production&Office&is&responsible&for&secure&distribution&and&storage&all&startIup&paperwork&documents,&signed&agreements&and&other& confidential&production&documents. %&Any&assets&located&with&the&Production&Office,&especially&those&that&store&content&(camera&cards,&drives,&etc.)&or&other&confidential& Intellectual&Property&(scripts,&budgets)&should&be&securely&stored&in&areas&protected&by&security&camera&coverage,&with&limited&access,&as& determined&by&the&producers. %&Access&to&vaults,&safes,&or&locked&filing&cabinets&should&be&limited,&to&those&personnel&as&approved&by&the&producers. 4
5 2.4 Non;Disclosure.Agreements./.Social.Media.Awareness./.Etc. %&Production&Office&responsible&for&production&documents&to&be&signed&and&returned&by&all&production&hires,&including&NonIDisclosure& Agreements&(NDA),&Code&of&Ethics,&Social&Media&Awareness,&General&Content&Handling&Guidelines,&as&determined&by&the&producers&and& studio. %&All&crew&members,&background&extras,&day&players,&other&members&of&the&cast,&and&visitors&should&sign&agreements&to¬&photograph& or&otherwise&share&confidential&information&to&friends,&family,&coiworkers,&or&on&social&media&websites&or&apps.&&this&information& includes&but&is¬&limited&to,&set&locations,&plot&lines,&actors,&characters,&etc. %&Social&Media&websites&include&but&are¬&limited&to&Facebook,&Twitter,&Instagram,&Vine,&LinkedIn,&Pinterest,&Tumblr,&Vimeo,&Google+,& IMDB,&OnLocationVacations,&and&more.& Personal./.Mobile.Devices %&When¬&in&immediate&use,&personal&/&mobile&devices&such&as&iPads,&iPhones,&Android&phones,&laptops,&tablets,&setItop&computers,& that&store&sensitive&production&content,&or&other&confidential&intellectual&property&should&be&securely&stored,&protected&with&complex& passwords,&cable&locked,&and&have&remote&tracking&and&disabling&software&enabled,&and&stored&in&a&vault,&safe,&or&locked&filing&cabinet. Cloud.Storage./.Collaboration.Technologies %&Production&members&should&use&studio&approved&file&storage&and&collaboration&technologies,&instead&of&using&consumer&grade& solutions&(ie,&dropbox,&google&drive,&skydrive,&etc.,&for&storing&or&sharing&sensitive&files&and&content. %&Content&should&be&encrypted&at&rest. %&User&rights&should&have&the&ability&for&the&Admin&to&control&and&restrict&rights,&and&disable&access&remotely. %&Where&possible,&content&should&be&watermarked&and/or&spoiled&to&idenify&the&user. 5
6 2.7 Security.Systems %&Security&Cameras&should&be&utilized&at&key&entrances&and&exits,&as&well&as&areas&with&safe&/&vaults&/&locked&filing&cabinets&that&store& Audio/Visual&content&or&other&confidential&Intellectual&Property,&that&is&maintained&for&90&days.& %&Entrances&and&exits&should&be&alarmed,&and&remotely&monitored&by&either&a&trusted&third&party&security&company,&or&by&designated& members&of&the&production. %&Authorized&members&of&the&production&with&access&to&enter&Production&Office&after&hours&should&have&their&own&individual&access& code.&& %&Access&codes&should&be&changed&in&the&event&as&members&of&the&production&office&end&their&employment,&or&are&otherwise&discharged& from&the&production. 2.8 Change.Control %&Security&access&codes&and&system&passwords&should&be&changed&in&the&event&as&members&of&the&production&office&end&their& employment,&or&are&otherwise&discharged&from&the&production. %&Physicals&keys&should&also&be&collected,&and&locks&changed&on&areas&that&store&sensitive&content&and&confidential&Intellectual&Property. 2.9 On.Set.Visitation.Policy %&All&onIset&visitors&should&be&preIapproved&by&the&Producers,&should&have&signed&an&NDA&and&Social&Media&Policy. %&Further,&the&Production&Office&should&verbally&confirm&the&Social&Media&Policy&and&OnISet&Photography&Policy. %&Visitor&badges&should&be&issued,&then&returned&and&accounted&for&by&the&Production&Office&at&the&end&of&the&day. %&OnIset&visitors&should&be&escorted&to&and&from&the&set. %&All&Personal&/&Mobile&Devices&should&be&silenced,&powered&off,&or&stored&in&the&Production&Office&until&afterwards. Incident.Escalation %&All&members&of&a&production&should&be&aware&of&any&unfamiliar&person&on&set,&and¬ify&security&if&they&do¬&have&visible&Visitor&ID. %&Any&member&of&a&production&cast&or&crew&should&contact&security&if&they&witness&anyone&on&set&recording&video,&audio,&or&images&with& a&camera,&phone,&tablet,&or&other&recording&device. 6
7 3 ASSET(MANAGEMENT(/(CAMERA(MEDIA Administrative.Controls %&Define&asset&management&roles,&responsibilities&and&handling&procedures&with&segregation&of&functions&where&necessary,&ensuring& security&measures&are&proportionate&to&risk. Asset.Controls %&Implement&an&effective&process&for&asset&management&and&tracking. %&This&should&be&capable&of&providing&an&auditable&chain&of&custody&for&content&related&assets&and&blank&media. %&Consider&the&use&of&a®ister&that&that&documents&the&time/date&of&creation/registration,¤t&location,&movement&and&final& destination&or&destruction&with&suitable&retained&records&should&they&be&required. 3.3.Asset.Receipt.and.Identification %&Ensure&that&all&content&related&assets&and&blank&media&received&are;&logged&into&the®ister,&uniquely&identified&and&securely&stored. 3.4.Secure.Asset.Storage.and.Reconciliation.Controls %&Provide&adequate&physical&storage&and&logical&controls&for&assets&when&left&unattended.&See&physical&and&IT&security§ions&for&more& detail.&implement&and&maintain&an&inventory&count&procedure&for&content&related&assets&and&blank&media. %&Where&possible&use&independent&personnel&to&conduct&checks&to&ensure&integrity&is&maintained. %&As&a&minimum&keep&records&for&the&duration&of&the&project. %&Report&and&investigate&discrepancies&and&consider&the&need&to&escalate¬ification&to&management&and&content&owners. 3.5.Asset.Re;call.Procedures %&Define&a&process&for&the&recall&of&content&related&assets&booked&out. %&Give&someone&the&responsibility&to&manage&the&asset®ister. %&Respond&immediately&and&investigate&any&failure&to&return&or&loss&of&any&asset. 7
8 Control.of.Blank.Media.Materials %&Treat&blank&media/blank&media&as&an&asset&as&it&can&be&used&to&remove&or&transfer&content&without&authority. %&It&should&be;&logged&onto&an&asset®ister,&identified&upon&receipt,&secured&and&handled&in&accordance&with&work&instructions.&Blank& media&other&than&that®istered&should&be&prohibited&from&site. %&Treat&blank&media&as&you&would&a&storage&device&by&implementing&checks&and&controls. Transportation.of.Assets %&Define&procedures&for&secure&transportation&of&content&related&assets&(tapes&drives&film&etc...),&ensuring&that&records&are&retained& within&the&asset®ister&and&that&any&3rd&parties&have&appropriate&insurances. %&Only&use&approved&and&appropriately&screened&members&of&production&staff,&runners&and&couriers. %&Document&the&process&for&any&Runners&and&Couriers&and&circulate&to&relevant&personnel. %&Consider&the&use&of&security&seals&and&encrypted&storage.&Implement&advance¬ification&processes&for&receipt&of&content.& %&Packaging&should&be&plain&and&non&descriptive&and&should¬&contain&title&or&sensitive&project&information..Destruction.and.Recycling %&Define&destruction&and&recycling&procedures&for&content&related&assets.&Document&destruction&and&keep&records&for&the&duration&of&the& project. Camera.Media.Handling %&The&Digital&Imaging&Technician&(D.I.T.)&should&ensure&that&camera&media&is&tracked&at&all×,&whether&it&is&on&set,&in&the&camera&truck,& production&office,&or&vendor&/&dailies&processing&lab. %&Camera&media&includes&but&is¬&limited&to&camera&cards,&hard&drives,&shuttle&drives,&&Compact&Flash&(CF)&drive,&SxS&card,&&SSD,&Codex& box,&"shoebox",&"media&vault",&cinestation,&tape,&disc,&san,<o,&or&recording&deck. %&Ensure&that&all&content&related&assets&and&blank&media&received&are;&logged&into&the®ister,&uniquely&identified&and&securely&stored. %&Camera&media&should&be&taken&from&camera&/&on&set&to&the&Camera&truck&for&backIup,&transfer,&and&storage&by&the&person&designated& by&digital&imaging&technician&(d.i.t.). 8
9 Camera.Media.Re;Use %&Camera&media&should&be&securely&stored&and&tracked&until&Post&Production&/&Editorial&has&viewed&dailies&and&camera&logs,&and& authorized&the&d.i.t.&to&wipe&and&prep&camera&media&for&reiuse. Shipping.Drives.to.Vendor %&AV&content&(dailies)&sent&out&to&dailies&vendor&should&be&stored&and&transported&on&shuttle&drives&that&are&encrypted&and&password& protected,&and&in&locked&case,&with&tamper&resistant&packaging,&with&the&driver&/&courier¬&having&access&to&the&key. %&Materials&should&be&packed&securely&using&plain&packaging,&nonIdescript&labeling&and&withhold&any&title/project&information.&& %&Shuttle&drives&sent&out&to&vendor&should&be&securely&held&and&returned&during&normal&production&shooting&hours Unauthorized.Back;Up.Copies %&No&unauthorized&backIup&copies&of&the&AV&content&(dailies)&should&be&made&without&approval&of&the&producers&/&studio Reconciliation.of.Camera.Media %&All&camera&media&should&be&reconciled&at&the&end&of&the&production,&and&all&AV&content&securely&deleted&prior&to&return&to&rental& company&or&for&asset&storage. Video.Assist.Cart %&Video&Assist&Cart&should&utilize&encrypted&and&password&protected&hard&drives. %&Video&Assist&Cart&should&be&secured&after&hours&inside&locked&equipment&truck,&with&cable&locks&to&secure&cart&and&hard&drives. %&At&end&of&production,&at&a&time&designated&by&the&producers,&all&AudioIVisual&content&should&be&securely&deleted&from&all&hard&drives,& and&the&hard&drives&wiped&and&reformatted. 9
10 3.15 On;Set.Streaming %&If&approved&for&onIset&streaming&of&dailies&footage,&content&should&first&be&ingested&from&the&camera&media&onto&a&local&server,&that&is& both&encrypted&and&password&protected. %&Dynamic&visible&user&name&burnIin&should&be&added&as&content&is&streamed&to&iPad&/&tablets. %&Files&should&be&transcoded&in&a&h.264&format&with&"Property&Of& "&and&other&appropriate&spoilers&burned&in&base&video. %&All&iPads&/&tablets&should&have&their&Unique&Device&ID&(UDID)®istered&in&advance,&with&client&app&installed&prior&to&set&visit,&with& active&ability&to&remotely&track,&lock,&and&wipe&devices.& %&Download&should&be&prohibited,&and&streaming&should&originate&from&a&private&WiFi&network&that&is&password&protected,&from&a&limited& range&wiifi&router. %&The&SSID&(Service&Set&Identifier)&should¬&be&broadcast,&preventing&the&name&of&the&private&WiFi&network&from&showing&up&on&a&scan. %&Dynamic&visible&user&name&burnIin&should&be&added&as&content&is&streamed&to&iPad&/&tablets. %&AudioIVisual&content&should&be&be&securely&deleted&from&hard&drives&once&the&content&is&securely&at&the&dailies&lab,&backed&up&to<O,& checkisum&verified,&and&deliverables&complete. %&The&cart&used&to&store,&transcode,&and&stream&AudioIVisual&content&should&be&secured&as&with&the&Video&Assist&Cart. 10
11 4 4.1 PHYSICAL(SECURITY Secure.Perimeters %&Define&within&a&security&plan,&what&physical&security&controls&are&in&place&and&how&these&are&monitored. %&Brief&staff&accordingly&on&a&need&to&know&basis. %&Apply&multiple&layers&of&protection&around&the&perimeter. %&Consider&use&of&CCTV,&automated&access&control,&key&controls,&visitor&procedures&and&perimeter&intruder&detection&systems&(PIDS). %&Utilize&existing&site&controls&wherever&possible&and&consider&the&need&for&physical&security&upgrades&prior&to&project&commencement. %&Where&third&party&controls&are&utilized&ensure&protocols&for&use&and&access&to&data&is&agreed&within&any&contract&or&a&written& agreement&prior&to&project&commencement.&consider&the&need&for&nondisclosure&or&confidentiality&agreements. 4.2 Securing.Internal.Areas %&Consider&the&sensitivity&of&production&activities&and&the&workflow. %&Create&secure&zones.&Physically&protect,&monitor&and&restrict&access&to&the&production&environment&and&all&storage&areas&as&necessary.& Do&this&on&a&basis&of&need&rather&than&convenience&to&reduce&risk. %&Identify&the&requirements&for&any&enhancement&or&increase&in&physical&security&where&content&is&to&be&created,&handled&or&stored. 4.3 Use.of.Guards %&Consider&the&value&of&deploying&guards&according&to&the&level&of&risk,&access&to&resources&and&the&availability&of&alternative&controls. %&Where&existing&facility&or&third&party&resources&are&used&ensure&security&requirements&for&third&parties&are&met,&including&NDA& nonidisclosure&and&suitable&back&ground&checks.& %&Review&and/or&create&suitable&assignment&instructions&maintain&and&check&agreed&activities&are&maintained. 11
12 4.4 Searches %&Define&a&search&policy&for&the&project %&Consider&the&roles&to&be&undertaken&and&the&locations&of&the&activity. %&Link&this&to&requirements&for&authorizing&and&prohibiting&storage&devices,&mobile&devices,&removable&media&and&blank&media&within&the& production&areas.&consider&the&need&for&permanent&and/or&random&searches. %&Implement&according&to&risk&and&activity. %&As&a&minimum&a&search&procedure& for&cause &(in&the&event&of&incident&or&suspected&unauthorized&act)&should&be&in&place CCTV %&Ensure&effective&deployment&of&CCTV&at&points&of&entry&and&egress&to&a&site&and&any&designated&internal&secure&areas. %&Consider&the&need&to&extend&coverage&where&content&is&handled&or&transferred&without&supervision&or&other&corroborative&control&such& as&searches. %&Define&or&integrate&local&procedures&for&CCTV.&Ensure&access&to&third&party&systems&is&agreed&and&that&images&are&retained&for&a& minimum&period&commensurate&to&the&activity&being&monitored&and&risk&to&content. %&Recommended&retention&periods&for&perimeter&controls&should&exceed&30&days&and&the&monitoring&of&internal&locations&should&be& extended. Access.Control.Key.Controls.and.Automated.Technology %&Ensure&effective&deployment&of&access&control&and/or&key&controls&at&points&of&entry&and&egress&to&a&site&and&any&designated&internal& secure&areas.& %&Define&or&integrate&local&procedures&for&access&control. %&Retain&automated&access&control&logs&for&the&duration&of&the&project. 4.7 Intruder.Detection.Systems.(Alarms) %&Ensure&effective&deployment&of&IDS&at&points&of&entry&and&egress&to&a&site&and&any&designated&internal&secure&areas.& %&Define&or&integrate&local&procedures&for&zoning&and&the&responsible&use&of&key&codes. %&Retain&access&activation&logs&for&the&project&duration. 12
13 Check.Visitor.ID %&Security&guards&should&be&cognizant&of&all&visitors&on&or&near&the&set,&and&should&make&sure&they&have&proper&visitor&badge& identification.&&the&producers&should&have&a&clearly&defined&search&policy&for&the&project. Key.Assets./.Props./.Costumes./.Equipment %&Areas&holding&key&assets&such&as&props,&costumes,&equipment,&computers,&or&other&valuable&assets&should&consider&use&of&CCTV,& automated&access&control,&key&controls,&visitor&procedures&and&perimeter&intruder&detection&systems&(pids).& %&Utilize&existing&site&controls&wherever&possible&and&consider&the&need&for&physical&security&upgrades&prior&to&project&commencement Camera.Truck %&Camera&truck&should&secure&all&devices&used&to&store&or&process&AudioIVisual&content,&including&a&safe&or&locking&vault&to&store&camera& media,&hard&drives,&laptops,&or&any&other&device&used&to&store&or&process&audioivisual&content. %&Camera&truck&should&be&kept&in&a&secure&location,&locked,&and&where&possible&with&alarm&and&security&camera&coverage. 13
14 5 5.1 IT(SECURITY Information.Security %&Define&and&develop&IT&security&plans.&Prior&to&project&commencement&consider&and&assess&the&need&for&the&following&controls:&&&&& %&Control&of&authorized&and&prohibited&devices&and&software %&Inventory&requirements&for&authorized&devices&and&software %&The&secure&configuration&and&segregated&use&of&hardware&and&software&on&production&networks %&Basic&requirements&for&vulnerability&assessment,&malware&controls&and&application/software&security&updates %&Public&facing&boundary&defenses&to&include&properly&managed&firewalls,&DMZ&and&Intrusion&detection %&Secure&server&and&device&configuration %&Logical&and&physical&segregation&for&production&networks %&Securely&engineered&networks&and&end&point&security&controls&for&all&devices&handling&content %&Wireless&router&and&device&controls %&Network&access&controls&to&include&port,&protocol&and&restricted/controlled&access&to&services %&Securely&managed&administration&of&production&networks %&Managed,&monitored&and&controlled&logical&user&access&to&content&within&production&networks %&Logging&enabled,&monitored&and&securely&stored %&Process&for&incident&response&and&the&capture&of&evidence"&&&&&& 5.2 Acceptable.Use %&Define&the&acceptable&use&for&IT&systems&and&devices;&include&use&of&the&production&network,&authorized&use&of&devices&and&restrictions& on&access&to&web&based&services.&capture&individual s&acceptance&of&policy. 5.3 System.Administrator.and.Elevated.Privilege.User.Accounts %&Authorize&and&define&requirements&for&the&administration&of&production&networks.&Prevent&the&use&of&administrator&accounts&for& noniadministrative&functions.&log&and&retain&details&of&administrator&actions&for&the&duration&of&the&project. 14
15 5.4 System.Basic.User.Accounts %&Consider&the&level&of&access&required&to&content&and&restrict&access&to&production&networks&accordingly.&Use&a&policy&of&authorized&and& need&to&have&only.&restrict&file&access&and&sharing&using&appropriate&configuration&controls. 5.5 Password.Management %&Define&a&Strong&Password&policy&for&all&devices&and&workstations&containing&or&accessing&media&content:&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& %&At&least&eight&characters&long %&Does¬&contain&any&user&name,&real&name,&nickname,&company&name&or&identifiable&number. %&Is&unique&and¬&used&elsewhere. %&Does¬&contain&a&single&complete&word. %&Contains&one&from&each&of&the&following&four&categories;&Upper&Case,&Lower&Case,&Number,&Character&Changes&should&be&significantly& different&from&previous&passwords. %&Password&changes&should&be&made&every&30&days.&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& %&Devices&should&be&set&to&auto&log&out&after&five&minutes. 5.6 Authorizing.Third;party.Access.to.IT.Systems %&Define&thirdIparty&access&policy&and&procedures.&Only&approved&devices&should&be&connected&to&networks&or&devices&where&media& content&is&stored&or&accessed. 5.7 Removable.Media %&Include&authorized&removable&media&within&an&approved&device®ister. %&If&possible&identify&approved&devices&using&hologram&or&other&nonIdescriptive&marking. %&Prohibit&the&use&and&possession&of&nonIapproved&devices&where&content&is&handled,&created&or&stored. %&Use&end&point&security&software&and/or&disable&ports&and&peripheral&device&writers&at&source&to&prevent&unauthorized&connection&of& noniapproved&devices.&treat&blank&media&as&a&removable&media&asset&and&place&it&on&a®ister.&control&access&and&use.&complete& inventory&checks. 15
16 5.8 Mobile.Device.Management %&Establish,&implement&and&maintain&a&mobile&device&acceptable&use&policy. %&Complete&an&approved&device®ister&recording&authorization&to&possess&devices&where&content&is&handled,&created&or&stored. %&Where&personal&items&capable&of&content&transfer&or&storage&are&permitted&into&production&areas&this&should&be&authorized&by& management,&documented&and&monitored. %&Persons&authorized&to&carry&personal&items&of&this&nature&should&be&advised&of&the&risk&and&consequences&of&unauthorized&use&of&the& device&and&that&they&may&be&subject&to&search&and&additional&checks&and&controls Wireless.Networks %&Define&a&wireless&network&policy&to&include&acceptable&use. %&Deny&the&use&of&wireless&on&production&networks. %&Implement&strong&user&and&password&authentication&for&Staff&and&any&guest&networks.&Implement&encryption&WPA2&minimum& standard. %&Prohibit&the&transfer&of&feature&content&via&wireless&networks. Environmental.Security.Controls %&Physically&secure&server&locations&monitor&and&restrict&access. %&Physically&secure&systems&and&hardware&to&prevent&misuse&and&configure&so&as&to&prevent&any&circumvention&of&secure&connections Network.Monitoring %&Establish&how&network&traffic&is&to&be&monitored&retain&event&logs&for&the&project&duration Access.Controls &%&Establish&policy&and&process&to&identify&and&control&access&using&secure&configuration&and&authentication Remote.Access %&Establish&policy&and&process&to&identify&and&control&remote&access&requirements&using&dual&factor&authentication&for&VPN&or&equivalent. 16
17 5.14 Change.Management %&Appoint&an&administrator&responsible&for&policy&and&process&to&manage&changes 5.15 System.Documentation %&Document&and&maintain&a&basic&network&diagram Networks %&Securely&configure&and&segregate&internal&and&external&networks.&Isolate&content&networks&from&noIproduction&networks %&Establish&policy&and&processes&for&all&file&transfer&and&encryption&technologies.& %&Only&use&studio&approved&hardware&and&software&for&content&transfer.& %&Apply&secure&configuration&and&administration&controls. %&Retain&log&files&for&all&content&tranfers. %&Content&within&all&data&storage&locations&should&be&kept&physically&secure&when&unattended. %&Use&approved&hardware&for&storage&systems&and&segregate&where&possible. %&Use&approved&encryption&methods&for&transfer&and&storage.& %&As&a&minimum&use&AES&128&Bit&Encryption File.Transfer.Management.and.Data.Storage Firewall.Management %&Correctly&configure&firewalls&to&deny&untrusted&incoming&traffic. %&Implement&firewall&rules&to&deny&all&outbound&traffic&by&default. %&Control&and&monitor&outbound&traffic&using&secure&configuration&controls&to&prevent&loss&of&data/content&and&protect&network& integrity. %&Review&configuration®ularly&during&the&project. Vulnerability.Management %&An&antiIvirus&policy&shall&be&documented&and&implemented. %&Servers&and&workstations&are&protected. %&Implement&a&patching®ime&for&servers,&workstations&and&security&barriers. 17
18 6 6.1 TRAINING(AND(AWARENESS Training.and.Awareness.Needs %&Establish&antiIpiracy&and&security&awareness&briefings. %&Record&details&of&persons&completing&the&awareness&package.& %&On&projects&of&a&long&duration&refresh&awareness&during&key&phases&of&production&(ie,&after&the&Director's&Cut&or&Picture&Lock). 6.2 Kick;Off.Meetings %&Include&a&Content&Security&discussion&at&key&Production&and&PostIProduction&kickIoff&meetings,&to&make&key&members&of&the& production&team&aware&of&risks,&and&studio&expectations,&for&protecting&the&intellectual&property&and&audioivisual&content. 6.3 Start;Up.Paperwork %&Producers&and&Production&Office&responsible&for&requiring&all&cast&and&crew&members&to&sign&agreements&to¬&photograph&or& otherwise&share&confidential&information&to&friends,&family,&coiworkers,&or&on&social&media&websites&or&apps.&& %&This&information&includes&but&is¬&limited&to,&set&locations,&plot&lines,&actors,&characters,&etc.&&&&&&& 18
19 7 7.1 INCIDENT(MANAGEMENT(AND(RECOVERY(PLANNING Incident.Management.and.Recovery.Planning %&Establish&a&process&for&reporting&and&responding&to&a&security&incident&Establish&a&basic&continuity&and&recovery&plan %&Review&effectiveness %&Record&details&of&persons&completing&the&awareness&package.& 7.2 Geographic.Separation %&All&AudioIVideo&Content,&including&dailies,&rough&cuts,&and&VFX&shots,&should&have&backIup&copies,&with&geographic&separation&of& original&version&and&backiups. %&A&backIup©&of&all&Edit&Decision&Lists&(EDL)&from&editorial&(Avid,&Final&Cut&Pro)&should&be&maintained&at&all×,&for&retrieval&and& restoration&of&project. 19
20 8 8.1 EDITORIAL(/(DIGITAL(WORKFLOW General.Guidelines The&following&requirements&outline&the&fundamental&guidelines&has&been&developed&for&safeguarding&the&content&handled&during& Production&and&Post&Production.&The&Post&Production&workflow&and&content&created&during&this&phase&are&unique&and&the&controls&for& protecting&this&material&have&been&specifically&put&in&place&for&it.& a b c Closed&Set:&Maintain&a& closed&set &environment.&if&people&do¬&need&to&have&visibility/access&to&content,&they&should¬&be& permitted&in&areas&where&content&is&handled.&if&people&will&have&visibility/access&to&content,&they&should&sign&the&applicable&noni disclosure&agreement&(nda).& Complex&Passwords:&Use&complex&passwords&for&all&systems,&programs&and&devices&that&require&a&password.&Complex& passwords&are&at&least&8&characters,&consisting&of&upperi&and&lowericase&letters,&numbers&and&symbols.&an&example&is:& P@ran0iD.&Passwords&should¬&be&shared.&Passwords&should&be&changed&at&the&start&of&every&show.& Restrict&Internet&Access:&Internet&access&is&never&allowed&on&any&systems&handling&and/or&storing&content.&You&should&unplug& Internet&cables&and/or&disable&wireless&access&on&Production&Networks. d e Encrypt&Data&:&If&thumb&drives&or&external&hardIdrives&are&used,&they&should&be,&at&minimum&AES&128Ibit,&encrypted&and& securely&stored&when¬&in&use.&complex&passwords/phrases&are&required&and&should&be&sent&separate&from&the&device.& Physical&Security:&Areas&where&content&is&stored&or&handled&should&be&kept&as&physically&secure&as&possible.&This&requires&doors& to&be&locked&when&staff&is¬&present,&physical&materials&to&be&locked&in&safes/cabinets/vaults,&and&if&possible&security&camera& and&swipe&card&systems&installed&covering&sensitive&areas.& 20
21 8.1 f g h General.Guidelines.Continued Secure&Electronic&Transfers:&All&electronic&transfers&should&be&conducted&via&studio&approved&transfer&technology&(Aspera,& Signiant,&Sohonet,&etc.).&Content&may&never&be&sent&over& &or&uploaded&to&a&system&that&has¬&been&approved&(e.g.& YouSendIt,&FTP,&AIM,&etc.).&If&a&vendor&requests&to&use&an&alternate&system,&Content&Security&should&be&contacted&to&have&these& systems&reviewed.& Secure&Physical&Deliveries:&All&materials&being&sent&physically&(e.g.&tapes,&drives,&film,&etc.)&should&be&sent&using&a&production& employee,&studio&employee&or&an&approved&courier/freight&service.&materials&should&be&packed&securely&using&plain&packaging,& nonidescript&labeling&and&withhold&any&title/project&information.& Appropriate&Spoilage:&Unless&otherwise&approved&by&the&studio,&"turnIover&copies"&should&have&unique&spoilage&specific&to&the& recipient.& i j Approved&Vendors:&If&requested&by&the&studio,&the&production&shall&endeavor&to&use&only&vendors&who&the&studio&has&conducted& security&reviews&and&approved&vendor&to&handle&content. Principle&of&Least&Privilege:&Do¬&send&content&to&people&who&do¬&absolutely&require&content.&Content&will&only&be&provided& to&persons&absolutely&requiring&access&to&our&materials.&when&content&is&provided,&it&should&follow&the&above&guidelines&for& delivery,&spoilage&and&handling.& 21
22 8.2 Digital.Workflow The&Producers,&Post&Production&Supervisor,&and&the&Digital&Imaging&Technician&(D.I.T.)&should&create&a&detailed&Digital&Workflow,&to&be& approved&by&the&studio,&to&include&the&following&areas: & %&Method&of&Digital&Acquisition&(camera,&camera&media) %&Processing&of&dailies&On&Set&vs.&Near&Set&vs&Lab %&Application&of&color&correction&/&Look&Up&Tables&(LUTs)& %&Ingesting&AudioIVideo&content&to&local&SAN&or&hard&drive&for&creating&deliverables %&CheckIsum&verifications %&Transcoding&to&dailies&and&editorial&media&specs %&Syncing&of&audio&and&video %&Digital&or&physical&delivery&to&studio&executives,&editorial&or&VFX %&BackIup&copies&to<O&or&other&formats %&Additional&checkIsum&verification&of&SAN&or&hard&drive&to<O&or&other&format %&Archival&backIup©&with&geographic&separation %&Process&for&how&long&to&hold&camera&media&for&reIuse %&Determine&who&authorizes&wiping&of&media&for&reIuse&after&editorial&and&camera&department&review&content&against&camera&reports 8.3 Burn;ins./.Spoilers./.Watermarking %&BurnIins&/&spoilers&/&watermarking&should&be&used&to&the&highest°ree&possible&without&frustrating&the&intended&business&purpose. %&Only&use&studio&approved&solutions&for&sending,&receiving,&viewing,&collaborating,&or&transforming&content. %&Apply&unique&markings&and&make&identification&specific&to&the&recipient. %&Show&the&name&of&the&facility/company,&recipient&initials&and&Dub&date. %&Use&assigned&project&alias&to&label&media. %&Consider&the&need&to&deIsaturate&media&intended&for&vendor&dissemination. %&Consider&the&need&to&physically&secure&media&such&as&DVD&and&tape&before&distribution.&(See§ion&3.7)& %&Do¬&leave&physical&media&unattended&at&any&time.&(See§ion&3.7) 22
23 8.4 Online.Screeners./.Media %&Only&use&studio&approved&delivery&applications. %&Login&credentials&are&specific&to&the&recipient&and&are¬&to&be&shared&under&any&circumstance %&Pre&approved&burnIins&should&be&applied.&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& %&Download&facility&should&be&approved&by&studio. 8.5 Vendor.Duplication %&Editorial&and&studio&should&be&responsible&for&media&output&during&post&production. %&For&media&that&has&bespoke&technical&requirements&use&studio&preIapproved&vendors&only. %&Such&content&is&considered&high&security&and&can&only&be&approved&by&studio&authorized&staff&or&their&designees 8.6 Screenings %&Do¬&send&clear&media&without&ADVANCE&approval&of&studio&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& %&Media&burnIins&are&mandatory&unless&authorized. %&Editing&room&staff&should&be&present&and&will&be&responsible&for&the&handling&and&transport&security&of&content&to&prevent&unauthorized& duplication,&transmission&or&access. %&Should&screening&of&clear&content&be&required,&the&studio&approved&screening&room&should&be&used. 8.7 Editing.Rooms. %&Editing&Systems&should&be&configured&to&prohibit&internet&access.&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&&& %&All&drives&should&be&scanned&for&viruses&and&malware&prior&to&attaching&to&storage&devices&or&ingesting&content&onto&production& network %&Content&should&be&transferred&from&a¢ralized&data&I/O&(input/output)&station&(using&approved&encrypted&transfer&technology),&and& securely&deleted&from&the&station&once&delivery&has&been&confirmed. %&Devices&used&for&eImail&or&other&access&to&the&internet&should&never&contain&user&names&or&passwords&for&systems&with&access&to& content,&and&should¬&be&used&to&download,&transfer,&receive,&or&otherwise&access&sensitive&content. %&Production&network&storage&devices&(Isilon,&ISIS,&SAN,&Xtore,&etc.)&should&be&kept&in&well&ventilated&and&temperature&controlled& environments,&with&cctv&coverage&where&possible,&with&keycard&access&where&possible,&and&locked&when¬&under&immediate& supervision&of&the&editorial&staff. 23
24 9 9.1 SCRIPT(HANDLING Development.&.Pre;Production %&Scripts&should&be&distributed&digitally&via&an&access&control&system,&unless&a&physical©&is&otherwise&approved&by&the&Producer. %&All&Scripts&should&be&watermarked&with&recipient s&name. %&Digital&Script&security&settings&should&prevent&printing&/©ing&/&forwarding. %&Digital&Scripts&should&be&set&to& expire &and&autoidelete&from&recipient&devices&after&a&time&frame&determined&by&producer. %&Physical&scripts&should&never&be&unattended,&should&be&kept&locked&up&unless&in&immediate&use,&and&shredded&or&returned&to&the& Producer&after&an&agreed&upon&timeframe. %&Scripts&should&be&distributed&only&to&the&intended&recipient. %&Scripts&at&table&reads&will&be&watermarked,&signed&for,&collected&afterwards,&and&either&shredded&or&locked&away&securely&at&discretion& of&the&producer. %&All&elements&of&the&script&including&storyline,&locations,&characters,&props,&dialogue,&etc.,&are&covered&under&NonIDisclosure& Agreements,&and&should¬&be&discussed&with&anyone&outside&the&relevant&members&of&the&production&(unless&authorized&by&the& Producer),&including&friends,&relatives,&and&all&Social&Media&outlets. 9.2 Production.(Scripts.&.Sides) %&Scripts&&&Sides&should&be&distributed&digitally&via&access&control&system,&unless&physical&copies&are&otherwise&approved&by&the&Producer. %&All&Scripts&&&Sides&should&be&watermarked&with&recipient s&name %&Digital&Script&&&Sides&security&settings&should&be&set&to&prevent&printing&/©ing&/&forwarding. %&Digital&Scripts&&&Sides&should&be&set&to& expire &and&autoidelete&from&recipient&devices&after&a&time&frame&determined&by&producer. %&Physical&Scripts&&&Sides&should&never&be&unattended,&should&be&kept&locked&up&unless&in&immediate&use,&and&collected&at&the&end&of&the& day&to&be&either&shredded&or&locked&away&securely,&at&discretion&of&the&producer. %&Scripts&should&be&distributed&only&to&the&intended&recipient. 24
25 9.3 Personal./.Mobile.Device.Policy %&Personal&/&Mobile&Devices&include&Pads,&Tablets,&Laptops,&MacBooks,&iPhones,&Android&Phones&SetItop&computers,&and&other&such& devices&that&store&content&or&other&confidential&intellectual&property& %&When¬&in&immediate&use,&these&devices&should&be&securely&stored,&protected&with&complex&passwords,&cable&locked,&and&have& remote&tracking&and&disabling&software&enabled,&and/or&stored&in&a&vault,&safe,&or&locked&filing&cabinet. %&Personal&/&Mobile&Devices&should&be&configured&with&a&complex&password&where&possible,&with&minimum&4Idigit&nonIconsecutive&and& nonirepeating&pin&#&where&applicable. %&Personal&/&Mobile&Devices&should&be&configured&to&lockIout&after&5&unsuccessful&logIin&attempts. %&Personal&/&Mobile&Devices&should&be&set&to&track&/&lock&/&delete&contents&remotely. %&Personal&/&Mobile&Devices&backIup&data&should&be&encrypted. %&MacBooks&and&PC's&should&enable&FileVault&/&FileVault2&security&settings&or&other&technology&as&approved&by&the&Producers&or&the& Studio. 25
ป งบประมาณ พ.ศ.๒๕๕๘ ( ๑ ต ลาคม ๒๕๕๗ ถ ง 30 ก นยายน ๒๕๕๘ ) สร ปผลปร มาณงานพ สด การจ ดซ อ/จ าง/เช า ในรอบเด อนพฤศจ กายน ๒๕๕๗ ส าน กงานท ด นจ งหว ดเช
 ๑ ท ชม ๐๐๒๐.๑.๓/ ลว. ๗ พฤศจ กายน ๒๕๕๗ ๒๐,๐๐๐ ตกลงราคา เร อง รายงานขอจ ดซ อว สด น าม นเช อเพล งและหล อล น สาขาแม แตง รถยนต ย ห อโตโยต า ทะเบ ยน ฮก-๔๑๖๔ กทม จากบร ษ ทส ข มเซอร ว ส จ าก ด ๒ ท ชม ๐๐๒๐.๑.๓/
๑ ท ชม ๐๐๒๐.๑.๓/ ลว. ๗ พฤศจ กายน ๒๕๕๗ ๒๐,๐๐๐ ตกลงราคา เร อง รายงานขอจ ดซ อว สด น าม นเช อเพล งและหล อล น สาขาแม แตง รถยนต ย ห อโตโยต า ทะเบ ยน ฮก-๔๑๖๔ กทม จากบร ษ ทส ข มเซอร ว ส จ าก ด ๒ ท ชม ๐๐๒๐.๑.๓/
Connecting Windows Vista to DragonFly3
 ConnectingWindowsVistatoDragonFly3 Thefollowinginstructionswillguideyouthroughthesetupprocessforconnectinga MicrosoftWindowsVistacomputertotheDrexelDragonFly3wirelessnetwork. PLEASENOTE:Dell,Hewlett Packard,Compaq,Lenovo,IBMandsomeotherlaptop
ConnectingWindowsVistatoDragonFly3 Thefollowinginstructionswillguideyouthroughthesetupprocessforconnectinga MicrosoftWindowsVistacomputertotheDrexelDragonFly3wirelessnetwork. PLEASENOTE:Dell,Hewlett Packard,Compaq,Lenovo,IBMandsomeotherlaptop
Cybersecurity!Evaluations!
 CybersecurityEvaluations https://www.cybersecdefense.com @cybersecdefense 13720JetportCommerceParkway STE13 Ft.Myers,FL33913 COPYRIGHT 2015,CybersecurityDefenseSolutions,LLC ALLRIGHTSRESERVED CybersecurityEvaluationsVOverview
CybersecurityEvaluations https://www.cybersecdefense.com @cybersecdefense 13720JetportCommerceParkway STE13 Ft.Myers,FL33913 COPYRIGHT 2015,CybersecurityDefenseSolutions,LLC ALLRIGHTSRESERVED CybersecurityEvaluationsVOverview
ENTERPRISE SECURITY RISK MANAGEMENT: A HOLISTIC APPROACH TO SECURITY OVERVIEW AND BACKGROUND DEFINITION OF ESRM
 ENTERPRISE SECURITY RISK MANAGEMENT: A HOLISTIC APPROACH TO SECURITY OVERVIEW AND BACKGROUND Organizations are continuously exposed to a host of evolving threats which create a multitude of security risks.
ENTERPRISE SECURITY RISK MANAGEMENT: A HOLISTIC APPROACH TO SECURITY OVERVIEW AND BACKGROUND Organizations are continuously exposed to a host of evolving threats which create a multitude of security risks.
1 Introduction 2. 2 Document Disclaimer 2
 Important: We take great care to ensure that all parties understand and appreciate the respective responsibilities relating to an infrastructure-as-a-service or self-managed environment. This document
Important: We take great care to ensure that all parties understand and appreciate the respective responsibilities relating to an infrastructure-as-a-service or self-managed environment. This document
Responsibility Matrix
 Akamai Technologies Inc. Responsibility Matrix PCI-DSS 3.0 Requirement 12.8.2 Table of Contents Purpose... 2 Overview... 2 Disclaimer... 2 Responsibility Matrix... 3 Purpose Akamai provides below a detailed
Akamai Technologies Inc. Responsibility Matrix PCI-DSS 3.0 Requirement 12.8.2 Table of Contents Purpose... 2 Overview... 2 Disclaimer... 2 Responsibility Matrix... 3 Purpose Akamai provides below a detailed
! PRIVATE!PAGES! DRUPAL!7!WEB!CONTENT!MANAGEMENT!
 UNIVERSITY*OF*CALGARY InformationTechnologies PRIVATEPAGES DRUPAL7WEBCONTENTMANAGEMENT September2015 TableofContents FirstSteps...1 AddingaPrivatePage...2 AccessControl...4 PrivatePages Drupal7WebContentManagement
UNIVERSITY*OF*CALGARY InformationTechnologies PRIVATEPAGES DRUPAL7WEBCONTENTMANAGEMENT September2015 TableofContents FirstSteps...1 AddingaPrivatePage...2 AccessControl...4 PrivatePages Drupal7WebContentManagement
BYOD Policies: A Litigation Perspective
 General Counsel Panel Reveals the Real Deal BYOD Policies: A Litigation Perspective By Andrew Hinkes Reprinted with Permission BYOD Policies: A Litigation Perspective By Andrew Hinkes Bring-your-own-device
General Counsel Panel Reveals the Real Deal BYOD Policies: A Litigation Perspective By Andrew Hinkes Reprinted with Permission BYOD Policies: A Litigation Perspective By Andrew Hinkes Bring-your-own-device
Standard: PCI Data Security Standard (PCI DSS) Version: 1.0 Date: August 2014. Information Supplement: Best Practices for Maintaining
 Standard: PCI Data Security Standard (PCI DSS) Version: 1.0 Date: August 2014 Author: Best Practices for Maintaining PCI DSS Compliance Special Interest Group PCI Security Standards Council Information
Standard: PCI Data Security Standard (PCI DSS) Version: 1.0 Date: August 2014 Author: Best Practices for Maintaining PCI DSS Compliance Special Interest Group PCI Security Standards Council Information
Release 1. BSBPMG415A Apply project risk-management techniques
 Release 1 BSBPMG415A Apply project risk-management techniques BSBPMG415A Apply project risk-management techniques Modification History Release Release 1 Comments This version first released with BSB07
Release 1 BSBPMG415A Apply project risk-management techniques BSBPMG415A Apply project risk-management techniques Modification History Release Release 1 Comments This version first released with BSB07
5. Graduate Degrees Awarded AY 2007-2011. (Table 9) Graduate School/Department AY 2010 AY 2011 AY 2007 AY 2008 AY 2009. Note. Graduate Department of
 5. s Awarded -2011 School/Department School of Theology School of Humanities Theology Philosophy Aesthetics Psychology Education Master s 18 15 11 11 10 9 6 6 13 11 1 1 3 1 3 1 3 1 2 4 1 0 0 0 1 Master
5. s Awarded -2011 School/Department School of Theology School of Humanities Theology Philosophy Aesthetics Psychology Education Master s 18 15 11 11 10 9 6 6 13 11 1 1 3 1 3 1 3 1 2 4 1 0 0 0 1 Master
Secure Email Actions for Email Recipients
 Secure Email Actions for Email Recipients Actions for Email Recipients The recipient cannot forward encrypted email outside the secure system. Each email will only be available to the recipient for 30
Secure Email Actions for Email Recipients Actions for Email Recipients The recipient cannot forward encrypted email outside the secure system. Each email will only be available to the recipient for 30
Remote Control Invitations Invite Someone to Control your Computer
 Invite Someone to Control your Computer Table of contents: - Glossary - Installation Process - Inviting Someone to Control your Computer About NSN Connect and this document NSN Connect has been developed
Invite Someone to Control your Computer Table of contents: - Glossary - Installation Process - Inviting Someone to Control your Computer About NSN Connect and this document NSN Connect has been developed
Unleashing the power of secure, real-time collaboration
 Unleashing the power of secure, real-time collaboration Cisco WebEx web conferencing security White Paper 1 2010 Cisco and/or its affiliates. All rights reserved. Introduction Enabling real-time collaboration
Unleashing the power of secure, real-time collaboration Cisco WebEx web conferencing security White Paper 1 2010 Cisco and/or its affiliates. All rights reserved. Introduction Enabling real-time collaboration
How Cisco IT Controls Building Security over the Enterprise WAN
 How Cisco IT Controls Building Security over the Enterprise WAN Centrally managed IP-based building security system saves costs and improves safety and responsiveness. Cisco IT Case Study / Security and
How Cisco IT Controls Building Security over the Enterprise WAN Centrally managed IP-based building security system saves costs and improves safety and responsiveness. Cisco IT Case Study / Security and
EMAIL: How to setup Outlook and Outlook Web Access (OWA) to give a send receipt and a read receipt (Options)
 EMAIL: How to setup Outlook and Outlook Web Access (OWA) to give a send receipt and a read receipt (Options) Versions: Outlook 2003 and OWA 2003 Purpose: To show how a user can setup an email message such
EMAIL: How to setup Outlook and Outlook Web Access (OWA) to give a send receipt and a read receipt (Options) Versions: Outlook 2003 and OWA 2003 Purpose: To show how a user can setup an email message such
Q: How do I log in to my account?
 FAQ Contents How do I log in to my account? How do I claim my invoices? Where is my invoice? Where can I view my statement & tracking history? What if I accidentally claimed an invoice that s not mine?
FAQ Contents How do I log in to my account? How do I claim my invoices? Where is my invoice? Where can I view my statement & tracking history? What if I accidentally claimed an invoice that s not mine?
Managing BlackBerry Enterprise Service 10 version 10.2
 Managing BlackBerry Enterprise Service 10 version 10.2 Course details Course code 726-08882-123 Approximate duration Labs 3 days Labs are included in this course Course overview This course explains how
Managing BlackBerry Enterprise Service 10 version 10.2 Course details Course code 726-08882-123 Approximate duration Labs 3 days Labs are included in this course Course overview This course explains how
Configuring Role-Based Access Control
 5 CHAPTER This chapter describes how to configure role-based access control (RBAC) on the Cisco Application Control Engine (ACE) module. This chapter contains the following sections: Information About
5 CHAPTER This chapter describes how to configure role-based access control (RBAC) on the Cisco Application Control Engine (ACE) module. This chapter contains the following sections: Information About
Email Encryption. Instructions for sending and retrieving an encrypted email:
 (Effective 9/11/15) Email Encryption Instructions for sending and retrieving an encrypted email: PRIMARY METHOD to encrypt messages: Email encryption is used by specifying subject line tags. [secure] {secure}
(Effective 9/11/15) Email Encryption Instructions for sending and retrieving an encrypted email: PRIMARY METHOD to encrypt messages: Email encryption is used by specifying subject line tags. [secure] {secure}
EPIC EMR Research Coordination Staff Creating a Research (Non Chargeable) Encounter
 EPIC EMR Research Coordination Staff Creating a Research (Non Chargeable) Encounter When placing a research related order without a scheduled visit, Research Coordinators need to create a separate encounter.
EPIC EMR Research Coordination Staff Creating a Research (Non Chargeable) Encounter When placing a research related order without a scheduled visit, Research Coordinators need to create a separate encounter.
The service will notify subscribers when the following changes are made to a licensee s record:
 Minnesota Board of Nursing Auto Verification Service The Minnesota Board of Nursing s Auto Verification service enables subscribers to get information about the status of any registered nurse or licensed
Minnesota Board of Nursing Auto Verification Service The Minnesota Board of Nursing s Auto Verification service enables subscribers to get information about the status of any registered nurse or licensed
10/28/2013. Partners Zixmail Web Portal. Provider Training. Let s Get Started!
 Partners Zixmail Web Portal Provider Training Let s Get Started! 1 Setting Up Your Partners Zixmail Web Portal There are two methods to begin this process. Option #1 Use the link on the Partners Provider
Partners Zixmail Web Portal Provider Training Let s Get Started! 1 Setting Up Your Partners Zixmail Web Portal There are two methods to begin this process. Option #1 Use the link on the Partners Provider
Secure File Transfer Guest User Guide Updated: 5/8/14
 Secure File Transfer Guest User Guide Updated: 5/8/14 TABLE OF CONTENTS INTRODUCTION... 3 ACCESS SECURE FILE TRANSFER TOOL... 3 REGISTRATION... 4 SELF REGISTERING... 4 REGISTER VIA AN INVITATION SENT BY
Secure File Transfer Guest User Guide Updated: 5/8/14 TABLE OF CONTENTS INTRODUCTION... 3 ACCESS SECURE FILE TRANSFER TOOL... 3 REGISTRATION... 4 SELF REGISTERING... 4 REGISTER VIA AN INVITATION SENT BY
Web Conferencing: Unleash the Power of Secure, Real-Time Collaboration
 White Paper Web Conferencing: Unleash the Power of Secure, Real-Time Collaboration This paper focuses on security information for Cisco WebEx Meeting Center, Cisco WebEx Training Center, Cisco WebEx Support
White Paper Web Conferencing: Unleash the Power of Secure, Real-Time Collaboration This paper focuses on security information for Cisco WebEx Meeting Center, Cisco WebEx Training Center, Cisco WebEx Support
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Distributing Surveys
 Distributing Surveys Provided by Technology Across the Curriculum (TAC) Distributing Surveys Anonymously 1 Qualtrics is a powerful survey tool. Once you have created your survey you will need to decide
Distributing Surveys Provided by Technology Across the Curriculum (TAC) Distributing Surveys Anonymously 1 Qualtrics is a powerful survey tool. Once you have created your survey you will need to decide
SQL Server 2005 Advanced settings
 SQL Server 2005 Advanced settings Setting maximum memory use for SQL Server 2005 NOTE: By default SQL Server 2005 Express has a limitation of 2GB memory use. Set a limitation in memory use First: Open
SQL Server 2005 Advanced settings Setting maximum memory use for SQL Server 2005 NOTE: By default SQL Server 2005 Express has a limitation of 2GB memory use. Set a limitation in memory use First: Open
Recognition of Prior Learning (RPL) BSB41515 Certificate IV in Project Management Practice
 Recognition of Prior Learning (RPL) BSB41515 Certificate IV in Project Management Practice What is RPL? RPL recognises that you may already have the skills and knowledge needed to meet national competency
Recognition of Prior Learning (RPL) BSB41515 Certificate IV in Project Management Practice What is RPL? RPL recognises that you may already have the skills and knowledge needed to meet national competency
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies
 Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
ONLINE BILL PAY QUICK REFERENCE GUIDE
 Thank you for enrolling in the DiCarlo Food Service On-line Payment Program. By enrolling in this service, you will have the ability to: Bullet Receive an email notification when your bill is ready Securely
Thank you for enrolling in the DiCarlo Food Service On-line Payment Program. By enrolling in this service, you will have the ability to: Bullet Receive an email notification when your bill is ready Securely
Cisco Advanced Services for Network Security
 Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Customer Ad Proofing Portal
 Customer Ad Proofing Portal User Guide The Day Publishing Company - Customer Ad Proofing Portal 2 Introduction The customer ad proofing portal allows advertising customers to view electronic proofs and
Customer Ad Proofing Portal User Guide The Day Publishing Company - Customer Ad Proofing Portal 2 Introduction The customer ad proofing portal allows advertising customers to view electronic proofs and
Secure E-Mail Management Guide. June 2008
 Secure E-Mail Management Guide June 2008 What are Paychex Secure Messages? To enhance the security of client and vendor data, Paychex created the Paychex Secure E-mail Message Center, a Web site hosted
Secure E-Mail Management Guide June 2008 What are Paychex Secure Messages? To enhance the security of client and vendor data, Paychex created the Paychex Secure E-mail Message Center, a Web site hosted
BEING MOBILE WITH WINDOWS 8.1
 www.realdolmen.com BEING MOBILE WITH WINDOWS 8.1 OCTOBER 28, 2014 SLIDE 1 SPEAKERS INTRO #Name: D Hoker Gino #Function: Technology Expert #Email: [email protected] #Twitter: @GinoDH #Blog: #Mobile:
www.realdolmen.com BEING MOBILE WITH WINDOWS 8.1 OCTOBER 28, 2014 SLIDE 1 SPEAKERS INTRO #Name: D Hoker Gino #Function: Technology Expert #Email: [email protected] #Twitter: @GinoDH #Blog: #Mobile:
Keystone Enterprise Backup
 Keystone Enterprise Backup Table of Contents 1 Introduction... 3 2 Recommendations... 3 3 MSSQL... 3 3.1 Example MSSQL 2012 Backup... 4 3.1.1 To Create a Maintenance Plan... 4 4 Standard Volume Structure...
Keystone Enterprise Backup Table of Contents 1 Introduction... 3 2 Recommendations... 3 3 MSSQL... 3 3.1 Example MSSQL 2012 Backup... 4 3.1.1 To Create a Maintenance Plan... 4 4 Standard Volume Structure...
FIRST TIME HOMEBUYERS PROGRAM GUIDELINES (for Market Rate Units) Last Revised October 3, 2013
 FIRST TIME HOMEBUYERS PROGRAM GUIDELINES (for Market Rate Units) Last Revised October 3, 2013 I. Applicant Eligibility a. The total household income can be no greater than 120% of area median, adjusted
FIRST TIME HOMEBUYERS PROGRAM GUIDELINES (for Market Rate Units) Last Revised October 3, 2013 I. Applicant Eligibility a. The total household income can be no greater than 120% of area median, adjusted
Your guide to a virtual office
 Your guide to a virtual office how does it work? where can you get one? how much will it cost? find out more inside Why go virtual? To help project a professional image for your business To support you
Your guide to a virtual office how does it work? where can you get one? how much will it cost? find out more inside Why go virtual? To help project a professional image for your business To support you
Email Security Enhancements 3/9/15
 Email Security Enhancements 3/9/15 CU Recovery and The Loan Service Center recently implemented security enhancements to our email system. This feature allows emails containing sensitive data to be securely
Email Security Enhancements 3/9/15 CU Recovery and The Loan Service Center recently implemented security enhancements to our email system. This feature allows emails containing sensitive data to be securely
CMIPS II and You: New Timesheets & Payroll Processing for IHSS Providers
 CMIPS II and You: New Timesheets & Payroll Processing for IHSS Providers What does CMIPS II mean to IHSS Providers? The Case Management Information and Payrolling System II (CMIPS II) is the new computer
CMIPS II and You: New Timesheets & Payroll Processing for IHSS Providers What does CMIPS II mean to IHSS Providers? The Case Management Information and Payrolling System II (CMIPS II) is the new computer
As close to perfection. development and production. Modular data center
 As close to perfection development and production Modular data center August 2014 What is GreenMDC modular data center? Basically it is the modular design construction which is realized by the principle
As close to perfection development and production Modular data center August 2014 What is GreenMDC modular data center? Basically it is the modular design construction which is realized by the principle
P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems
 Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Appendix M. Change Management QUESTIONS
 Appendix M Change Management Change management is the process by which changes are introduced into the information technology (IT) environment. The change management process facilitates the migration of
Appendix M Change Management Change management is the process by which changes are introduced into the information technology (IT) environment. The change management process facilitates the migration of
SEC External Guide for Using the E-mail Encryption Solution
 Securities and Exchange Commission Office of Information Technology SEC External Guide for Using the E-mail Encryption Solution The Securities and Exchange Commission National Exam Program Hotline (202)551-3925
Securities and Exchange Commission Office of Information Technology SEC External Guide for Using the E-mail Encryption Solution The Securities and Exchange Commission National Exam Program Hotline (202)551-3925
How to Share Your Desktop or a Large Sized File
 How to Share Your Desktop or a Large Sized File White Paper LogMeIn (LMI) Customer Use Procedure - October 2013 Before going over the procedure steps, let s quickly state the basic two functions available
How to Share Your Desktop or a Large Sized File White Paper LogMeIn (LMI) Customer Use Procedure - October 2013 Before going over the procedure steps, let s quickly state the basic two functions available
This brief, published April 2014, replaces a previous version published December 2012. Changes include the following:
 Volume Licensing brief Multiplexing Client Step-up licenses Access License (CAL) requirements This brief applies to all Microsoft Volume Licensing programs. Table of Contents Summary... 1 What s New in
Volume Licensing brief Multiplexing Client Step-up licenses Access License (CAL) requirements This brief applies to all Microsoft Volume Licensing programs. Table of Contents Summary... 1 What s New in
IT-Security at Karlsruhe Institute of Technology Introduction. Andreas Lorenz. www.kit.edu STEINBUCH CENTRE FOR COMPUTING - SCC
 IT-Security at Karlsruhe Institute of Technology Introduction Andreas Lorenz STEINBUCH CENTRE FOR COMPUTING - SCC KIT University of the State of Baden-Württemberg and National Laboratory of the Helmholtz
IT-Security at Karlsruhe Institute of Technology Introduction Andreas Lorenz STEINBUCH CENTRE FOR COMPUTING - SCC KIT University of the State of Baden-Württemberg and National Laboratory of the Helmholtz
Communication Manager Drip Library. Drip Campaign Management
 Communication Manager Drip Library Drip Campaign Management In Communication Manager, Drip Library - start a new drip or suspend a drip; track statistics. Head office users can create drip campaigns and
Communication Manager Drip Library Drip Campaign Management In Communication Manager, Drip Library - start a new drip or suspend a drip; track statistics. Head office users can create drip campaigns and
Using Adobe Connect with CDCI By Shannon Stern & Brendan Donaghey
 UsingAdobeConnectwithCDCI ByShannonStern&BrendanDonaghey Thisdocumentservesasastep by stepguideforsettingup,creating,andrunninga webinarusingtheplatformadobeconnect. TableofContents SectionI:SettingUpaMeeting
UsingAdobeConnectwithCDCI ByShannonStern&BrendanDonaghey Thisdocumentservesasastep by stepguideforsettingup,creating,andrunninga webinarusingtheplatformadobeconnect. TableofContents SectionI:SettingUpaMeeting
How to Send an Encrypted Email via KDADS' Outlook Client or Outlook Web Application
 How to Send an Encrypted Email via KDADS' Outlook Client or Outlook Web Application In order to ensure Personal Health Information (PHI) and Personally Identifiable Information (PII) is protected, KDADS
How to Send an Encrypted Email via KDADS' Outlook Client or Outlook Web Application In order to ensure Personal Health Information (PHI) and Personally Identifiable Information (PII) is protected, KDADS
SMS Holdings Email Retention Policy: Overview. January 2, 2013
 SMS Holdings Email Retention Policy: Overview January 2, 2013 1 Disclaimer: The Email Retention Policy applies to all employees of SMS Holdings and its subsidiaries who have been issued an SMS Holdings
SMS Holdings Email Retention Policy: Overview January 2, 2013 1 Disclaimer: The Email Retention Policy applies to all employees of SMS Holdings and its subsidiaries who have been issued an SMS Holdings
How to... Send and Receive Files with DropBox
 How to... Send and Receive Files with DropBox Overview The Cornell DropBox is a secure method for transferring files to the people you specify. Files are encrypted during transport. DropBox can also be
How to... Send and Receive Files with DropBox Overview The Cornell DropBox is a secure method for transferring files to the people you specify. Files are encrypted during transport. DropBox can also be
Integration of QMS, SMS,
 Integration of QMS, SMS, WMO/QM Task Team, 4th Meeting 20.-22. January 2015 / Gerold Fletzer DIESER TEXT DIENT DER NAVIGATION Since last meeting the world has changed: 2015 we are facing ISO 9001:2015
Integration of QMS, SMS, WMO/QM Task Team, 4th Meeting 20.-22. January 2015 / Gerold Fletzer DIESER TEXT DIENT DER NAVIGATION Since last meeting the world has changed: 2015 we are facing ISO 9001:2015
Design History S4 AGDDHOL202 20/07/15 12/08/15 13/11/15 $360.50 Design Studio S5 AGDDSOL301 20/07/15 12/08/15 13/11/15 $1,030.00
 Advanced Diploma of Graphic Design CUV60411 Online Course s 2012, 2013 & 2014 October 2012, January 2013, March 2013, July 2013, October 2013, January 2014, March 2014 & July 2014 Intakes Design Studio
Advanced Diploma of Graphic Design CUV60411 Online Course s 2012, 2013 & 2014 October 2012, January 2013, March 2013, July 2013, October 2013, January 2014, March 2014 & July 2014 Intakes Design Studio
Using the PeaceHealth Secure E-mail System
 1 PeaceHealth is using a Secure E-mail System that allows for secure E-mail communications between individuals with a PeaceHealth E-mail address and individuals with E-mail addresses outside the PeaceHealth
1 PeaceHealth is using a Secure E-mail System that allows for secure E-mail communications between individuals with a PeaceHealth E-mail address and individuals with E-mail addresses outside the PeaceHealth
Sharing files and folders by inviting people
 The documents and folders you store in OneDrive for Business are private until you decide to share them. When you share documents and folders, you can decide whether to let people edit or just view them.
The documents and folders you store in OneDrive for Business are private until you decide to share them. When you share documents and folders, you can decide whether to let people edit or just view them.
Novar Database Mail Setup Guidelines
 Database Mail Setup Guidelines August 2015 Delivering the Moment Publication Information 2015 Imagine Communications Corp. Proprietary and Confidential. Imagine Communications considers this document and
Database Mail Setup Guidelines August 2015 Delivering the Moment Publication Information 2015 Imagine Communications Corp. Proprietary and Confidential. Imagine Communications considers this document and
Training module 2 Installing VMware View
 Training module 2 Installing VMware View In this second module we ll install VMware View for an End User Computing environment. We ll install all necessary parts such as VMware View Connection Server and
Training module 2 Installing VMware View In this second module we ll install VMware View for an End User Computing environment. We ll install all necessary parts such as VMware View Connection Server and
FDIC Secure Email Procedures for External Users April 23, 2010
 FDIC Secure Email Procedures for External Users April 23, 2010 This document contains information proprietary to the Federal Deposit Insurance Corporation. Table of Contents 1. Introduction...2 2. Receiving
FDIC Secure Email Procedures for External Users April 23, 2010 This document contains information proprietary to the Federal Deposit Insurance Corporation. Table of Contents 1. Introduction...2 2. Receiving
How To Encrypt An Email From A Cell Phone To A Pc Or Ipad (For A Partner) With A Cisco Email Encryption Solution (For Partners)
 New PHI & PII E-mail Encryption Solution (Partner Notification) In a continuing effort to utilize the advantages of email security while at the same time protecting clients private information, the Department
New PHI & PII E-mail Encryption Solution (Partner Notification) In a continuing effort to utilize the advantages of email security while at the same time protecting clients private information, the Department
Omnicast Migration Guide 5.2. Click here for the most recent version of this document.
 Omnicast Migration Guide 5.2 Click here for the most recent version of this document. Copyright notice 2015 Genetec Inc. All rights reserved. Genetec Inc. distributes this document with software that includes
Omnicast Migration Guide 5.2 Click here for the most recent version of this document. Copyright notice 2015 Genetec Inc. All rights reserved. Genetec Inc. distributes this document with software that includes
TECHNOLOGY ROLE MANAGEMENT SOFTWARE TOOLS TRAINING AVAILABLE ASSIGNED TO
 EducationTechnologyServices TECHNOLOGYROLES/CONTACTSWORKSHEET CorporateFunctionswillbeenteredintheSAPPA30screen.Thisinfotypeisusedtotrackemployeeswhoareperformingtechnologytasks/functionsatyoursite. TECHNOLOGYROLE
EducationTechnologyServices TECHNOLOGYROLES/CONTACTSWORKSHEET CorporateFunctionswillbeenteredintheSAPPA30screen.Thisinfotypeisusedtotrackemployeeswhoareperformingtechnologytasks/functionsatyoursite. TECHNOLOGYROLE
Role-BasedAccessControl
 Role-BasedAccessControl Proceedingsof15thNationalComputerSecurityConference,1992 NationalInstituteofStandardsandTechnology DavidFerraioloandRichardKuhn Gaithersburg,Maryland20899 Reprintedfrom thatrelianceondacastheprincipalmethodofaccesscontrolisunfoundedandinappropriateformanycommercialandciviliangovernmentorganizations.thepapeitaryapplications,discretionaryaccesscontrols(dac)areoftenperceivedasmeeting
Role-BasedAccessControl Proceedingsof15thNationalComputerSecurityConference,1992 NationalInstituteofStandardsandTechnology DavidFerraioloandRichardKuhn Gaithersburg,Maryland20899 Reprintedfrom thatrelianceondacastheprincipalmethodofaccesscontrolisunfoundedandinappropriateformanycommercialandciviliangovernmentorganizations.thepapeitaryapplications,discretionaryaccesscontrols(dac)areoftenperceivedasmeeting
 1 Attack Top Attackers Report, Top Targets Report, Top Protocol Used by Attack Report, Top Attacks Report, Top Internal Attackers Report, Top External Attackers Report, Top Internal Targets Report, Top
1 Attack Top Attackers Report, Top Targets Report, Top Protocol Used by Attack Report, Top Attacks Report, Top Internal Attackers Report, Top External Attackers Report, Top Internal Targets Report, Top
CDUfiles User Guide. Chapter 1: Accessing your data with CDUfiles. Sign In. CDUfiles User Guide Page 1. Here are the first steps to using CDUfiles.
 CDUfiles User Guide Chapter 1: Accessing your data with CDUfiles Here are the first steps to using CDUfiles. Sign In Open your web browser and enter cdufiles.cdu.edu.au or Note: Use cdufiles.egnyte.com
CDUfiles User Guide Chapter 1: Accessing your data with CDUfiles Here are the first steps to using CDUfiles. Sign In Open your web browser and enter cdufiles.cdu.edu.au or Note: Use cdufiles.egnyte.com
GRS Advantage Website User Reference Guide
 GRS Advantage Website User Reference Guide This document describes how to use the GRS Advantage Website. Table of Contents GRS Advantage Website... 2 Accessing the Website... 2 Requesting Access to the
GRS Advantage Website User Reference Guide This document describes how to use the GRS Advantage Website. Table of Contents GRS Advantage Website... 2 Accessing the Website... 2 Requesting Access to the
MSGCU SECURE MESSAGE CENTER
 MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
CRAISS Online status reports
 CRAISS Online status reports Index 1. Guidance and procedure 1. Status report for one shipment 2. Status report for several shipments with same recipient 2. Status selection 3. Time period for status reports
CRAISS Online status reports Index 1. Guidance and procedure 1. Status report for one shipment 2. Status report for several shipments with same recipient 2. Status selection 3. Time period for status reports
Active Directory Rights Management Services integration (AD RMS)
 MOSS Information Rights Management Ashish Bahuguna [email protected] Active Directory Rights Management Services integration (AD RMS) Agenda AD RMS Overview AD RMS Architecture Components MOSS
MOSS Information Rights Management Ashish Bahuguna [email protected] Active Directory Rights Management Services integration (AD RMS) Agenda AD RMS Overview AD RMS Architecture Components MOSS
(Formerly FM 19-30) Headquarters, Department of the Army
 ÿþýüûúùøü (Formerly FM 19-30) Headquarters, Department of the Army DISTRIBUTION RESTRICTION: Approved for public release; distribution is unlimited. *FM 3-19.30 Field Manual No. 3-19.30 Headquarters Department
ÿþýüûúùøü (Formerly FM 19-30) Headquarters, Department of the Army DISTRIBUTION RESTRICTION: Approved for public release; distribution is unlimited. *FM 3-19.30 Field Manual No. 3-19.30 Headquarters Department
Subject Access Request Form
 Subject Access Request Form Please refer to the explanatory notes for help completing this form. If you are seeking personal information about yourself please complete Sections 1-4. If you are giving permission
Subject Access Request Form Please refer to the explanatory notes for help completing this form. If you are seeking personal information about yourself please complete Sections 1-4. If you are giving permission
USC Marshall School of Business ShareFile_With_Outlook_Client_v2.docx 6/12/13 1 of 9
 About ShareFile When you wish to send someone a file or need a file from someone else, your best option is to use ShareFile. It not only provides increased security by automatically encrypting files but
About ShareFile When you wish to send someone a file or need a file from someone else, your best option is to use ShareFile. It not only provides increased security by automatically encrypting files but
Fiber Optic Transport Services
 Fiber Optic Transport Services Maxcom Corporation www.maxcomcorp.com Professional Services Guide What our Company Does: Maxcom Corporation is a manufacturer of fiber optic * transport and conversion equipment
Fiber Optic Transport Services Maxcom Corporation www.maxcomcorp.com Professional Services Guide What our Company Does: Maxcom Corporation is a manufacturer of fiber optic * transport and conversion equipment
Practice Name: Brief overview of your intended scope of practice at Anna Jaques Hospital:
 Medical Staff Application for Initial Appointment Supplemental Page Introduction (to be presented to the Credential Committee): Practice Name: Brief overview of your intended scope of practice at Anna
Medical Staff Application for Initial Appointment Supplemental Page Introduction (to be presented to the Credential Committee): Practice Name: Brief overview of your intended scope of practice at Anna
Business Process Flowchart. Supplier Management. Packet Description. MAGIC Roles. MAGIC Flows. Help or Questions
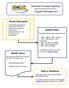 Business Process Flowchart Supplier Management Packet Description The Supplier Management Packet describes how to handle errors, updates to attributes and organizational structures, and user account management.
Business Process Flowchart Supplier Management Packet Description The Supplier Management Packet describes how to handle errors, updates to attributes and organizational structures, and user account management.
Milestone XProtect Corporate 3.1 Step-by-Step Guide How to Back Up and Restore the System Configuration
 Milestone XProtect Corporate 3.1 Step-by-Step Guide How to Back Up and Restore the System Configuration This document describes backup and restoration on the same XProtect Corporate Management Server.
Milestone XProtect Corporate 3.1 Step-by-Step Guide How to Back Up and Restore the System Configuration This document describes backup and restoration on the same XProtect Corporate Management Server.
Harrisburg)South)Middle)School) Bring)Your)Own)Device))
 HarrisburgSouthMiddleSchool BringYourOwnDevice BringYourOwnDevice TableofContents Attachment1:BYODPurposeandGuidelines Attachment2:BYODFAQ s(bringyourowndevice/frequentlyaskedquestions Attachment3:TechnologyAcceptableUsePoliceParent/StudentAgreementsignLoffForm
HarrisburgSouthMiddleSchool BringYourOwnDevice BringYourOwnDevice TableofContents Attachment1:BYODPurposeandGuidelines Attachment2:BYODFAQ s(bringyourowndevice/frequentlyaskedquestions Attachment3:TechnologyAcceptableUsePoliceParent/StudentAgreementsignLoffForm
Using the Filex File Distribution System
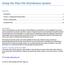 Using the Filex File Distribution System Contents Introduction... 1 Section 1: Creating and Sharing Folders... 1 Section 2: Sharing Files... 6 Important notes... 10 Introduction Filex is a file distribution
Using the Filex File Distribution System Contents Introduction... 1 Section 1: Creating and Sharing Folders... 1 Section 2: Sharing Files... 6 Important notes... 10 Introduction Filex is a file distribution
Table of Contents. CHAPTER 1 About This Guide... 9. CHAPTER 2 Introduction... 11. CHAPTER 3 Database Backup and Restoration... 15
 Table of Contents CHAPTER 1 About This Guide......................... 9 The Installation Guides....................................... 10 CHAPTER 2 Introduction............................ 11 Required
Table of Contents CHAPTER 1 About This Guide......................... 9 The Installation Guides....................................... 10 CHAPTER 2 Introduction............................ 11 Required
Penetration Test Methodology on Information-Security Product Utilizing the Virtualization Technology
 Penetration Test Methodology on Information-Security Product Utilizing the Virtualization Technology JungDae Kim ([email protected]) ByongKi Park ([email protected]) CONTENTS 1 Background Information 2 Vulnerability
Penetration Test Methodology on Information-Security Product Utilizing the Virtualization Technology JungDae Kim ([email protected]) ByongKi Park ([email protected]) CONTENTS 1 Background Information 2 Vulnerability
1.0 Doors.Net Database Backup Microsoft SQL Server 2005 Studio Express
 This procedure describes a backup process for Doors.NET databases using Microsoft SQL Server 2005 Studio Express. This is typically installed with Doors.NET. If a different version of Microsoft SQL Server
This procedure describes a backup process for Doors.NET databases using Microsoft SQL Server 2005 Studio Express. This is typically installed with Doors.NET. If a different version of Microsoft SQL Server
Patch Management. Is it recommended to patch an Industrial Automation Control System and, if so, why? Siemens AG 2012. All Rights Reserved.
 Patch Management Is it recommended to patch an Industrial Automation Control System and, if so, why? Facts Most of the computer components of modern Industrial Automation Control System are based on standard
Patch Management Is it recommended to patch an Industrial Automation Control System and, if so, why? Facts Most of the computer components of modern Industrial Automation Control System are based on standard
