Role-BasedAccessControl
|
|
|
- Jonah Day
- 8 years ago
- Views:
Transcription
1 Role-BasedAccessControl Proceedingsof15thNationalComputerSecurityConference,1992 NationalInstituteofStandardsandTechnology DavidFerraioloandRichardKuhn Gaithersburg,Maryland20899 Reprintedfrom thatrelianceondacastheprincipalmethodofaccesscontrolisunfoundedandinappropriateformanycommercialandciviliangovernmentorganizations.thepapeitaryapplications,discretionaryaccesscontrols(dac)areoftenperceivedasmeeting thesecurityprocessingneedsofindustryandciviliangovernment.thispaperargues WhileMandatoryAccessControls(MAC)areappropriateformultilevelsecuremil- Abstract describesatypeofnon-discretionaryaccesscontrol-role-basedaccesscontrol(rbac) 1Introduction TheU.S.governmenthasbeeninvolvedindevelopingsecuritytechnologyforcomputerand communicationssystemsforsometime.althoughadvanceshavebeengreat,itisgenerally perceivedthatthecurrentstateofsecuritytechnologyhas,tosomeextentfailedtoaddress -thatismorecentraltothesecureprocessingneedsofnon-militarysystemsthendac. theneedsofall.[1],[2]thisisespeciallytrueoforganizationsoutsidethedepartmentof Defense(DoD).[3] outofresearchanddevelopmenteortsonthepartofthedodoveraperiodoftwenty plusyears.todaythebestknownu.s.computersecuritystandardisthetrustedcomputer exclusivelyderived,engineeredandrationalizedbasedondodsecuritypolicy,createdto SystemEvaluationCriteria(TCSEC[4]).Itcontainssecurityfeaturesandassurances, information.theresultisacollectionofsecurityproductsthatdonotfullyaddresssecurity meetonemajorsecurityobjective-preventingtheunauthorizedobservationofclassied Thecurrentsetofsecuritycriteria,criteriainterpretations,andguidelineshasgrown securitymechanismshavebeenpartiallysuccessfulinpromotingsecuritysolutionsoutside issuesastheypertaintounclassiedsensitiveprocessingenvironments.althoughexisting ofamoreappropriatesetofcontrols. ofthedod[2],inmanyinstancesthesecontrolsarelessthenperfect,andareusedinlieu 1
2 (DAC)andMandatoryAccessControls(MAC).SincetheTCSEC'sappearanceinDecember (RBAC),thatcanbemoreappropriateandcentraltothesecureprocessingneedswithin of1983,dacrequirementshavebeenperceivedasbeingtechnicallycorrectforcommercial andciviliangovernmentsecurityneeds,aswellasforsingle-levelmilitarysystems.macis premiseofthispaperisthatthereexistsacontrol,referredtoasrole-basedaccesscontrol usedformulti-levelsecuremilitarysystems,butitsuseinotherapplicationsisrare.the TheTCSECspeciestwotypesofaccesscontrols:DiscretionaryAccessControls needsofcommercialandciviliangovernmentorganizations.itisapparentthatsignicant Recently,considerableattentionhasbeenpaidtoresearchingandaddressingthesecurity industryandciviliangovernmentthanthatofdac,althoughtheneedfordacwillcontinue andbroadsweepingsecurityrequirementsexistoutsidethedepartmentofdefense.[2], toexist. 2AspectsofSecurityPolicies impact.likedodagencies,civiliangovernmentandcommercialrmsareverymuchconcernedwithprotectingthecondentialityofinformation.thisincludestheprotectionoclosure,ortheftofcorporateresourcescoulddisruptanorganization'soperationsandhave immediate,seriousnancial,legal,humansafety,personalprivacyandpubliccondence datanetworksaremajorconcernsthroughoutallsectors.thecorruption,unauthorizeddis- [5],[6]Civiliangovernmentandcorporationsalsorelyheavilyoninformationprocessing ments.theintegrity,availability,andcondentialityofkeysoftwaresystems,databases,and systemstomeettheirindividualoperational,nancial,andinformationtechnologyrequirevelopmenttechniques.butmanyoftheseorganizationshaveevengreaterconcernforintegrity.[1curitythancondentiality.integrityisparticularlyrelevanttosuchapplicationsasfunds transfer,clinicalmedicine,environmentalresearch,airtraccontrol,andavionics.theimportanceofintegrityconcernsindefensesystemshasalsobeenstudiedinrecentyears.[7], privateorganizations.anorganizationalmeaningofsecuritycannotbepresupposed.each Withinindustryandciviliangovernment,integritydealswithbroaderissuesofse- personneldata,marketingplans,productannouncements,formulas,manufacturingandde- [8]Awidegamutofsecuritypoliciesandneedsexistwithinciviliangovernmentand traditionalmacanddaccontrols. organizationhasuniquesecurityrequirements,manyofwhicharediculttomeetusing mechanismthatpermitssystemuserstoallowordisallowotherusersaccesstoobjects undertheircontrol: groupstowhichtheybelong.thecontrolsarediscretionaryinthesensethat Ameansofrestrictingaccesstoobjectsbasedontheidentityofsubjectsand/or AsdenedintheTCSECandcommonlyimplemented,DACisanaccesscontrol 2
3 revokeaccesstoanyoftheobjectsundertheircontrolwithouttheintercessionofasystem asubjectwithacertainaccesspermissioniscapableofpassingthatpermission administrator. belefttothediscretionoftheindividualusers.adacmechanismallowsuserstograntor (perhapsindirectly)ontoanyothersubject(unlessrestrainedbymandatory accesscontrol).[4] areallowedaccess.fortheseorganizations,thecorporationoragencyistheactual\owner" ofsystemobjectsaswellastheprogramsthatprocessit.controlisoftenbasedonemployee Inmanyorganizations,theendusersdonot\own"theinformationforwhichthey DAC,asthenameimplies,permitsthegrantingandrevokingofaccessprivilegesto includedoctor,nurse,clinician,andpharmacist.rolesinabankincludeteller,loanocer, aspartofanorganization.thisincludesthespecicationofduties,responsibilities,and qualications.forexample,therolesanindividualassociatedwithahospitalcanassume functionsratherthandataownership. andaccountant.rolescanalsoapplytomilitarysystems;forexample,targetanalyst, situationanalyst,andtracanalystarecommonrolesintacticalsystems.arolebased accesscontrol(rbac)policybasesaccesscontroldecisionsonthefunctionsauserisallowed Accesscontroldecisionsareoftendeterminedbytherolesindividualuserstakeon toperformwithinanorganization.theuserscannotpassaccesspermissionsontoother forprivacyassociatedwiththediagnosisofailments,treatmentofdisease,andtheadministeringofmedicinewithahospital.tosupportsuchpolicies,acapabilitytocentrallycontrol andmaintainaccessrightsisrequired.thesecurityadministratorisresponsibleforenforcing policyandrepresentstheorganization. Securityobjectivesoftensupportahigherlevelorganizationalpolicy,suchasmain- usersattheirdiscretion.thisisafundamentaldierencebetweenrbacanddac. tainingandenforcingtheethicsassociatedwithajudge'schambers,orthelawsandrespect notpossesstheauthoritytopassthattransactionontoanurse. Forexample,adoctorcanbeprovidedwiththetransactiontoprescribemedicine,butdoes policiesarenon-discretionaryinthesensethattheyareunavoidablyimposedonallusers. arederivedfromexistinglaws,ethics,regulations,orgenerallyacceptedpractices.these somuchinaccordancewithdiscretionarydecisionsonthepartofasystemadministrator, butratherincompliancewithorganization-specicprotectionguidelines.thesepolicies Thedeterminationofmembershipandtheallocationoftransactionstoaroleisnot securityrequirements.asdenedinthetcsec,macis Ameansofrestrictingaccesstoobjectsbasedonthesensitivity(asrepresentedby (i.e.clearance)ofsubjectstoaccessinformationofsuchsensitivity.[4] alabel)oftheinformationcontainedintheobjectsandtheformalauthorization RBACisinfactaformofmandatoryaccesscontrol,butitisnotbasedonmultilevel withaccesstofunctionsandinformationthanstrictlywithaccesstoinformation. Rolebasedaccesscontrol,inmanyapplications(e.g.[9],[10],[11]isconcernedmore 3
4 principalconcernisprotectingtheintegrityofinformation:\whocanperformwhatactson onbothreadsandwritesareinsupportofthatrule.withinarole-basedsystem,the ofinformationfromahighleveltoalowlevelistheprincipalconcern.assuch,constraints operationalsensitivities)ofobjectswithinthedod.themilitarypolicyiswithrespecttoone typeofcapability:whocanreadwhatinformation.forthesesystemstheunauthorizedow analogoustotheprocessofclearingusers(grantingmembership)andthelabeling(associate Theactofgrantingmembershipandspecifyingtransactionsforaroleisloosely whatinformation." administrator.suchtransactionsincludetheabilityforadoctortoenteradiagnosis,prescribemedication,andaddaentryto(notsimplymodify)arecordoftreatmentsperformed onapatient.theroleofapharmacistincludesthetransactionstodispensebutnotprescribeprescriptiondrugs.membershipinaroleisalsograntedandrevokedbyasystem Arolecanbethoughtofasasetoftransactionsthatauserorsetofuserscanperformwithinthecontextofanorganization.Transactionsareallocatedtorolesbyasystem maintained.atransactioncanbethoughtofasatransformationprocedure[1](aprogram associatedsetofindividualmembers.asaresult,rbacsprovideameansofnamingand orportionofaprogram)plusasetofassociateddataitems.inaddition,eachrolehasan describingmany-to-manyrelationshipsbetweenindividualsandrights.figure1depictsthe relationshipsbetweenindividualusers,roles/groups,transformationprocedures,andsystem objectsṫhetermtransactionisusedinthispaperasaconveniencetorefertoabindingof Rolesaregrouporiented.Foreachrole,asetoftransactionsallocatedtheroleis transformationprocedureanddatastorageaccess.thisisnotunlikeconventionalusageof thetermincommercialsystems.forexample,asavingsdeposittransactionisaprocedure thatupdatesasavingsdatabaseandtransactionle.atransactionmayalsobequitegeneral, transactions,requiringexactlythesamereadandwriteaccesstothesamelesastheteller. here,becausethereadisnotboundtoaparticulardataitem,as\readsavingsle"is. e.g.\readsavingsle".notehowever,that\read"isnotatransactioninthesenseused Thedierenceistheprocessexecutedandthevalueswrittentothetransactionlogle. leandatransactionlogle.anaccountingsupervisormaybeabletoexecutecorrection access,canbeseenbyconsideringtypicalbankingtransactions.tellersmayexecutea savingsdeposittransaction,requiringreadandwriteaccesstospeciceldswithinasavings TheapplicabilityofRBACtocommercialsystemsisapparentfromitswidespread Theimportanceofcontrolovertransactions,asopposedtosimplereadandwrite use.baldwin[9]describesadatabasesystemusingrolestocontrolaccess.nashandpoland theserolebasedsystemshavebeendevelopedbyavarietyoforganizations,withnocom- [10]discusstheapplicationofrolebasedaccesscontroltocryptographicauthenticationdevicescommonlyusedinthebankingindustry.Workingwithindustrygroups,theNationaquirementsforCryptographicModules,"(FederalInformationProcessingStandard140-1) InstituteofStandardsandTechnologyhasdevelopedaproposedstandard,\SecurityRe- [11]thatwillrequiresupportforaccesscontrolandadministrationthroughroles.Todate, 4
5 User 4 Object 1 trans_a describedinthispaperaddresssecurityprimarilyforapplication-levelsystems,asopposed Figure1:RoleRelationships 1 User 5 3FormalDescriptionofRBAC togeneralpurposeoperatingsystems. monlyagreedupondenitionorrecognitioninformalstandards.rolebasedaccesscontrols trans_b Toclarifythenotionspresentedintheprevioussection,wegiveasimpleformaldescription, intermsofsetsandrelations,ofrolebasedaccesscontrol.noparticularimplementation Object 2 User 6 Eachsubjectmaybeauthorizedtoperformoneormoreroles: mechanismisimplied. Foreachsubject,theactiveroleistheonethatthesubjectiscurrentlyusing: Eachrolemaybeauthorizedtoperformoneormoretransactions: Subjectsmayexecutetransactions.Thepredicateexec(s,t)istrueifsubjectscanexecute transactiontatthecurrenttime,otherwiseitisfalse: AR(s:subject)=ftheactiveroleforsubjectsg RA(s:subject)=fauthorizedfoelsforsubjectsg Threebasicrulesarerequired: 1.Roleassignment:Asubjectcanexecuteatransactiononlyifthesubjecthasselectedor TA(fr:roleg)=ftransactionsauthorizedforrolerg beenassignedarole: exec(s:subject;t:tran)=trueisubjectscanexecutetransactiont. 5 8s:subject;t:tran(exec(s;t))AR(s)6=;) (1)
6 Theidenticationandauthenticationprocess(e.g.login)isnotconsideredatransaction. 2.Roleauthorization:Asubject'sactiverolemustbeauthorizedforthesubject: Allotheruseractivitiesonthesystemareconductedthroughtransactions.Thusallactive usersarerequiredtohavesomeactiverole. With(1)above,thisruleensuresthatuserscantakeononlyrolesforwhichtheyare authorizedforthesubject'sactiverole: authorized. 3.Transactionauthorization:Asubjectcanexecuteatransactiononlyifthetransactionis 8s:subject(AR(s)RA(s)) (2) With(1)and(2),thisruleensuresthatuserscanexecuteonlytransactionsforwhichthey notguaranteeatransactiontobeexecutablejustbecauseitisinta(ar(s)),thesetof thatadditionalrestrictionsmaybeplacedontransactionexecution.thatis,theruledoes transactionspotentiallyexecutablebythesubject'sactiverole.forexample,atraineefora areauthorized.notethat,becausetheconditionalis\onlyif",thisruleallowsthepossibility 8s:subject;t:tran(exec(s;t))t2TA(RA(s))) (3) supervisoryrolemaybeassignedtheroleof\supervisor",buthaverestrictionsappliedto forthesupervisorrole. hisorheruserrolethatlimitaccessibletransactionstoasubsetofthosenormallyallowed transaction. intothetransaction.securityissuesareaddressedbybindingoperationsanddataintoa transactionatdesigntime,suchaswhenprivacyissuesareaddressedinaninsurancequery cedure,plusasetofdataitemsaccessedbythetransformationprocedure.accesscontrolin therulesabovedoesnotrequireanychecksontheuser'srighttoaccessadataobject,oron thetransformationprocedure'srighttoaccessadataitem,sincethedataaccessesarebuilt Intheprecedingdiscussion,atransactionhasbeendenedasatransformationpro- onlytothetransformationprocedure,withoutincludingabindingtoobjects.thiswould requireafourthruletoenforcecontroloverthemodesinwhichuserscanaccessobjects throughtransactionprograms.forexample,afourthrulesuchas Itisalsopossibletoredenethemeaningof\transaction"intheaboverulestorefer couldbedenedusingatransaction(redenedtotransformationprocedure)toobjectaccess functionaccess(r;i;o;x)whichindicatesifitispermissibleforasubjectinrolertoaccess objectoinmodexusingtransactiont,wherexistakenfromsomesetofmodessuchasread, write,append.notethattheclark-wilsonaccesscontroltriplecouldbeimplementedby lettingthemodesxbetheaccessmodesrequiredbytransactiont,andhavingaone-to-one 8s:subject;t:tran;o:object(exec(s;t))access(AR(s);t;o;x)) (4) 6
7 ClarkandWilsonaccesscontrolasaspecialcase. relationshipbetweensubjectsandroles.rbac,aspresentedinthispaper,thusincludes requiresbindingthetransactionprogramtanddataobjectsthattcanaccess,andonly doctorcouldbeprovidedwithread/writeaccesstoaprescriptionle,whilethehospital pharmacistmighthaveonlyreadaccess.(recallthatuseoftherstthreerulesalone controlsaccesstothetransactions.)thisalternativeapproachusingthefourthrulemight behelpfulinenforcingcondentialityrequirements. Useofthisfourthrulemightbeappropriate,forexample,inahospitalsetting.A formanyrealsystems,andrbacshouldbeapplicabletosuchsystems. onlyinauthorizedwaysbyauthorizedusers.thisseemstobeareasonablesecurityobjective authorizedwayscanbeascomplexasthetransactionthatdidthemodication.forthis reason,thepracticalapproachisfortransactionstobecertiedandtrusted.iftransactions ofways,butoneaspect[8]ofintegrityisarequirementthatdataandprocessesbemodied Ingeneral,theproblemofdeterminingwhetherdatahavebeenmodiedonlyin AnotheruseofRBACistosupportintegrity.Integrityhasbeendenedinavariety mustbetrustedthenaccesscontrolcanbeincorporateddirectlyintoeachtransaction. inclusionofatransactiontoobjectaccesscontrolfunctioninrbacwouldbeusefulin signicantoverheadforalimitedbenetinenforcingintegrityrequirements.therefore, Requiringthesystemtocontrolaccessoftransactionprogramstoobjectsthroughtheaccess 4CentrallyAdministeringSecurityUsingRBAC some,butnotallapplications. functionusedinrule(4)mightthenbeausefulformofredundancy,butitcouldinvolve RBACisexibleinthatitcantakeonorganizationalcharacteristicsintermsofpolicyand structure.oneofrbac'sgreatestvirtuesistheadministrativecapabilitiesitsupports. tendtoremainrelativelyconstantorchangeslowlyovertime.theadministrativetask consistsofgrantingandrevokingmembershiptothesetofspeciednamedroleswithin membershiptoanexistingrole.whenaperson'sfunctionchangeswithintheorganization, theusermembershiptohisexistingrolescanbeeasilydeletedandnewonesgranted.finally, thesystem.whenanewpersonenterstheorganization,theadministratorsimplygrants whenapersonleavestheorganization,allmembershipstoallrolesaredeleted.foran OncethetransactionsofaRoleareestablishedwithinasystem,thesetransactions organizationthatexperiencesalargeturnoverofpersonnel,arole-basedsecuritypolicyis theonlylogicalchoice. canbecomposedoftheroleshealer,intern,anddoctor.figure2depictsanexampleof membershiptotheinternrole,thisimpliestransactionsoftheinternandhealernotthe sucharelationship. denedbyinternandhealer,aswellasthoseofadoctor.ontheotherhand,bygranting Inaddition,rolescanbecomposedofroles.Forexample,aHealerwithinahospital BygrantingmembershiptotheRoleDoctor,itimpliesaccesstoalltransactions 7
8 Object 1 trans_a User 1 Healer User 2 Object 2 trnas_b User 3 Object 3 trans_c User 4 Intern User 5 Object 4 Figure2:Mult-RoleRelationships trans_d Object 5 trans_e Doctor 8 Object 6 trans_f User 6 User 7 User 8 User 9
9 Doctor.However,bygrantingmembershiptotheHealerrole,thisonlyallowsaccesstothose jectives.[8]theprincipleofleastprivilegerequiresthatauserbegivennomoreprivilege Theprincipleofleastprivilegehasbeendescribedasimportantformeetingintegrityob- resourcesallowedundertherolehealer. 5PrincipleofLeastPrivilege thannecessarytoperformajob.ensuringleastprivilegerequiresidentifyingwhattheuser's jobis,determiningtheminimumsetofprivilegesrequiredtoperformthatjob,andrestrictingtheusertoadomainwiththoseprivilegesandnothingmore.bydenyingtosubjects ofleastprivilegecurrentlyexistswithinthecontextofthetcsec,requirementsrestrict transactionsthatarenotnecessaryfortheperformanceoftheirduties,thosedeniedprivilegescannotbeusedtocircumventtheorganizationalsecuritypolicy.althoughtheconcept thoseprivilegesofthesystemadministrator.throughtheuseofrbac,enforcedminimum ofduties.separationofdutiesisconsideredvaluableindeterringfraudsincefraudcan 6SeparationofDuties RBACmechanismscanbeusedbyasystemadministratorinenforcingapolicyofseparation occurifanopportunityexistsforcollaborationbetweenvariousjobrelatedcapabilities. privilegesforgeneralsystemuserscanbeeasilyachieved. allowedtoexecutealltransactionswithintheset.themostcommonlyusedexamplesare Separationofdutyrequiresthatforparticularsetsoftransactions,nosingleindividualbe theseparatetransactionsneededtoinitiateapaymentandtoauthorizeapayment.no singleindividualshouldbecapableofexecutingbothtransactions.separationofdutyis animportantconsiderationinrealsystems.[1],[12],[13],[14]thesetsinquestion willvarydependingontheapplication.inrealsituations,onlycertaintransactionsneed toberestrictedunderseparationofdutyrequirements.forexample,wewouldexpecta toadministrator"wouldnotbe. transactionfor\authorizepayment"toberestricted,butatransaction\submitsuggestion individualwhocanserveaspaymentinitiatorcouldalsoserveaspaymentauthorizer.this siderthecaseofinitiatingandauthorizingpayments.astaticpolicycouldrequirethatno wherecompliancewithrequirementscanonlybedeterminedduringsystemoperation.the objectivebehinddynamicseparationofdutyistoallowmoreexibilityinoperations.con- allocationoftransactionstoroles.themoredicultcaseisdynamicseparationofduty tionrequirementscanbedeterminedsimplybytheassignmentofindividualstorolesand Separationofdutycanbeeitherstaticordynamic.Compliancewithstaticsepara- couldbeimplementedbyensuringthatnoonewhocanperformtheinitiatorrolecouldalso performtheauthorizerrole.suchapolicymaybetoorigidforcommercialuse,makingthe exibilitycouldbeallowedbyadynamicpolicythatallowsthesameindividualtotakeon costofsecuritygreaterthanthelossthatmightbeexpectedwithoutthesecurity.more 9
10 thatheorshehadinitiated.thestaticpolicycouldbeimplementedbycheckingonlyroles bothinitiatorandauthorizerroles,withtheexceptionthatnoonecouldauthorizepayments ofusers;forthedynamiccase,thesystemmustusebothroleanduseridincheckingaccess totransactions. system.theclark-wilson[1]schemeincludestherequirementthatthesystemmaintainthe aper-userbasis,usingtheuseridfromtheaccesscontroltriple.asdiscussedabove,user separationofdutyrequirementexpressedintheaccesscontroltriples.enforcementison functionscanbeconvenientlyseparatedbyrole,sincemanyusersinanorganizationtypically performthesamefunctionandhavethesameaccessrightsontpsanddata.allocating accessrightsaccordingtoroleisalsohelpfulindeningseparationofdutyinawaythatcan Separationofdutyisnecessarilydeterminedbyconditionsexternaltothecomputer oragencyistheactual\owner"ofsystemobjects,anddiscretionaryaccesscontrolmay 7SummaryandConclusions beenforcedbythesystem. Inmanyorganizationsinindustryandciviliangovernment,theendusersdonot\own" theinformationforwhichtheyareallowedaccess.fortheseorganizations,thecorporation notbeappropriate.role-basedaccesscontrol(rbac)isanondiscretionaryaccesscontrol mechanismwhichallowsandpromotesthecentraladministrationofanorganizationalspecic ofanorganization.arolespeciesasetoftransactionsthatauserorsetofuserscan securitypolicy. performwithinthecontextofanorganization.rbacprovideameansofnamingand describingrelationshipsbetweenindividualsandrights,providingamethodofmeetingthe secureprocessingneedsofmanycommercialandciviliangovernmentorganizations. Accesscontroldecisionsareoftenbasedontherolesindividualuserstakeonaspart ofaccesscontrolsbasedonuserroles. encompassingrbac.assuch,evaluationandtestingprogramsforthesesystemshavenot beenestablishedastheyhaveforsystemsconformingtothetrustedcomputersecurity commercialsystemstoday,butthereisnocommonlyaccepteddenitionorformalstandards EvaluationCriteria.ThispaperproposedadenitionofTherequirementsandaccesscontrol rulesforrbacproposedinthispapercouldbeusedasthebasisforacommondenition Variousformsofrolebasedaccesscontrolhavebeendescribedandsomeareusedin 8References 1D.D.ClarkandD.R.Wilson.AComparisonofCommercialandMilitaryComputer SecurityPolicies.InIEEESymposiumonComputerSecurityandPrivacy,April1987. (draft).computersystemslaboratory,nist,january ComputersatRisk.NationalResearchCouncil,NationalAcademyPress, MinimumSecurityFunctionalityRequirementsforMulti-UserOperatingSystems 10
11 ofdefense,1985. Technology,1987. DataIntegrity.SP Natl.Inst.ofStds.andTechnology,1989. IntegrityPolicyinComputerInformationSystems.SP Natl.Inst.ofStds.and 4TrustedComputerSecurityEvaluationCriteria,DOD STD.Department 5Z.G.RuthbergandW.T.Polk,Editors.ReportoftheInvitationalWorkshopon 6S.W.KatzkeandZ.G.Ruthberg,Editors.ReportoftheInvitationalWorkshopon inlargedatabases.inieeesymposiumoncomputersecurityandprivacy,1990. September1991. EmbeddedSystems.InstituteforDefenseAnalyses,HQ /1,October K.R.PolandM.J.Nash.SomeConundrumsConcerningSeparationofDuty.In 8IntegrityinAutomatedInformationSystems.NationalComputerSecurity,Center, 9R.W.Baldwin.NamingandGroupingPrivilegestoSimplifySecurityManagement 7J.E.Roskos,S.R.Welke,J.M.Boone,andT.Mayeld.IntegrityinTacticaland Standard140-1,NationalInstituteofStandardsandTechnology,1992. Technology.InProceedingsof11thNationalComputerSecurityConference,October1988. IEEESymposiumonComputerSecurityandPrivacy,1990. AerospaceComputerSecurityApplicationsConference,December W.R.Shockley.ImplementingtheClark/WilsonIntegrityPolicyUsingCurrent 11SecurityRequirementsforCryptographicModules.FederalInformationProcessing ComputerSecurityandPrivacy,May R.Sandhu.TransactionControlExpressionsforSeparationofDuties.InFourth 14S.WisemanP.Terry.A'New'SecurityPolicyModel.InIEEESymposiumon 11
Role-Based Access Controls
 Role-Based Access Controls Reprinted from 15th National Computer Security Conference (1992) Baltimore, Oct 13-16, 1992. pp. 554-563 David F. Ferraiolo and D. Richard Kuhn National Institute of Standards
Role-Based Access Controls Reprinted from 15th National Computer Security Conference (1992) Baltimore, Oct 13-16, 1992. pp. 554-563 David F. Ferraiolo and D. Richard Kuhn National Institute of Standards
Predictive and Descriptive Approaches to Learning Game Rules from Vision Data
 Predictive and Descriptive Approaches to Learning Game Rules from Vision Data Paulo Santos 1, Simon Colton 2, and Derek Magee 3 1 Department of Electrical Engineering Centro Universitário da FEI, São Paulo,
Predictive and Descriptive Approaches to Learning Game Rules from Vision Data Paulo Santos 1, Simon Colton 2, and Derek Magee 3 1 Department of Electrical Engineering Centro Universitário da FEI, São Paulo,
! PRIVATE!PAGES! DRUPAL!7!WEB!CONTENT!MANAGEMENT!
 UNIVERSITY*OF*CALGARY InformationTechnologies PRIVATEPAGES DRUPAL7WEBCONTENTMANAGEMENT September2015 TableofContents FirstSteps...1 AddingaPrivatePage...2 AccessControl...4 PrivatePages Drupal7WebContentManagement
UNIVERSITY*OF*CALGARY InformationTechnologies PRIVATEPAGES DRUPAL7WEBCONTENTMANAGEMENT September2015 TableofContents FirstSteps...1 AddingaPrivatePage...2 AccessControl...4 PrivatePages Drupal7WebContentManagement
NORTHEAST HISTORIC FILM / MAINE TELEVISION STATIONS
 NORTHEAST HISTORIC FILM / MAINE TELEVISION STATIONS In most cases it takes a multilateral approach to get the job done. The station gives what it can, the archive does its best, but without a third or
NORTHEAST HISTORIC FILM / MAINE TELEVISION STATIONS In most cases it takes a multilateral approach to get the job done. The station gives what it can, the archive does its best, but without a third or
Curriculum Policy of the Graduate School of Engineering
 Curriculum Policy of the Graduate School of Engineering Graduate School of Engineering: Several specific study goals have been established based on the Degree Awarding Policy of the Graduate School of
Curriculum Policy of the Graduate School of Engineering Graduate School of Engineering: Several specific study goals have been established based on the Degree Awarding Policy of the Graduate School of
Tetrahedron 68 (2012) 6018e6031. Contents lists available at SciVerse ScienceDirect. Tetrahedron. journal homepage: www.elsevier.
 Tetrahedron 68 (2012) 6018e6031 Contents lists available at SciVerse ScienceDirect Tetrahedron journal homepage: www.elsevier.com/locate/tet An isomerizationd1,3-dipolar cycloaddition tandem reaction towards
Tetrahedron 68 (2012) 6018e6031 Contents lists available at SciVerse ScienceDirect Tetrahedron journal homepage: www.elsevier.com/locate/tet An isomerizationd1,3-dipolar cycloaddition tandem reaction towards
TRANSERV GLOBAL SERVICE & SUPPORT MAINTENANCE CONTRACTS
 TRANSERV GLOBAL SERVICE & SUPPORT MAINTENANCE CONTRACTS TRANSAS SERVICE DEPARTMENT Worldwide Service The Transas Worldwide Service Network guarantees a rapid response to service enquiries 24 hours a day,
TRANSERV GLOBAL SERVICE & SUPPORT MAINTENANCE CONTRACTS TRANSAS SERVICE DEPARTMENT Worldwide Service The Transas Worldwide Service Network guarantees a rapid response to service enquiries 24 hours a day,
HOKKAIDO UNIVERSITY. Graduate School of Medicine Guidebook of the Doctoral Program. www2.med.hokudai.ac.jp/en/
 HOKKAIDOUNIVERSITY Graduate School of Medicine Guidebook of the Doctoral Program www2.med.hokudai.ac.jp/en/ Early career development as a researcher of basic medicine Early career development as a clinical-practice-oriented
HOKKAIDOUNIVERSITY Graduate School of Medicine Guidebook of the Doctoral Program www2.med.hokudai.ac.jp/en/ Early career development as a researcher of basic medicine Early career development as a clinical-practice-oriented
BLENDER INTRO BLENDER TIPS
 AIG-3D.ps Page 1 AIG-3D.ps Page 2 AIG-3D.ps Page 3 AIG-3D.ps Page 4 AIG-3D.ps Page 5 AIG-3D.ps Page 6 AIG-3D.ps Page 7 AIG-3D.ps Page 8
AIG-3D.ps Page 1 AIG-3D.ps Page 2 AIG-3D.ps Page 3 AIG-3D.ps Page 4 AIG-3D.ps Page 5 AIG-3D.ps Page 6 AIG-3D.ps Page 7 AIG-3D.ps Page 8
Whilecertaintypesofregularities,suchasblock-structure,encapsulation,inheritanceandstrong
 Law-GovernedRegularitiesinObjectSystems; Part2:AConcreteImplementation NaftalyH.Minsky,andParthapratimPaly DepartmentofComputerScience, RutgersUniversity, NewBrunswick, NJ08903USA May1996 regularityisdeclared,itisenforcedbytheenvironmentinwhichthesystemisdeveloped.this
Law-GovernedRegularitiesinObjectSystems; Part2:AConcreteImplementation NaftalyH.Minsky,andParthapratimPaly DepartmentofComputerScience, RutgersUniversity, NewBrunswick, NJ08903USA May1996 regularityisdeclared,itisenforcedbytheenvironmentinwhichthesystemisdeveloped.this
An EDI Testing Strategy Rosemary B. Abell Director, National HIPAA Practice Keane, Inc.
 An EDI Testing Strategy Rosemary B. Abell Director, National HIPAA Practice Keane, Inc. HIPAA Summit IV April 24-26, 2002 Overview Why do you need it and What is it? What should be included in a testing
An EDI Testing Strategy Rosemary B. Abell Director, National HIPAA Practice Keane, Inc. HIPAA Summit IV April 24-26, 2002 Overview Why do you need it and What is it? What should be included in a testing
Traditional Medicine
 Objectives: Students predict U.S.-based providers opinions on traditional medicine. Students apply language skills to considering U.S.- based providers views on traditional medicine. Activity Ideas Activity
Objectives: Students predict U.S.-based providers opinions on traditional medicine. Students apply language skills to considering U.S.- based providers views on traditional medicine. Activity Ideas Activity
APPLICATION FOR CANDIDACY FOR THE DOCTORAL or MFA DEGREE
 APPLICATION FOR CANDIDACY FOR THE DOCTORAL or MFA DEGREE University of New Mexico MSC 03 2180 107 Humanities Building Albuquerque, NM 87131-1041 Telephone (505) 277-2711 Fax (505) 277-7405 This application
APPLICATION FOR CANDIDACY FOR THE DOCTORAL or MFA DEGREE University of New Mexico MSC 03 2180 107 Humanities Building Albuquerque, NM 87131-1041 Telephone (505) 277-2711 Fax (505) 277-7405 This application
Homework Assignment #3 Due 11/20 at 5:00pm EE122 Fall 2012
 Homework Assignment #3 Due 11/20 at 5:00pm EE122 Fall 2012 Please submit your solutions using BSpace (https://bspace.berkeley.edu/). Log in to BSpace with your CalNet ID, click on the EL ENG 122 Fa12 tab,
Homework Assignment #3 Due 11/20 at 5:00pm EE122 Fall 2012 Please submit your solutions using BSpace (https://bspace.berkeley.edu/). Log in to BSpace with your CalNet ID, click on the EL ENG 122 Fa12 tab,
NDMS Risk Compliance Program
 FRAUD THRESHOLDS (At Outlet ) NDMS Risk Compliance Program Fraud Compliance Program Fraud Performance (MFP) Program Global Audit Program (GMAP) US $5,000 of reported cross-border fraud 5 cross-border fraud
FRAUD THRESHOLDS (At Outlet ) NDMS Risk Compliance Program Fraud Compliance Program Fraud Performance (MFP) Program Global Audit Program (GMAP) US $5,000 of reported cross-border fraud 5 cross-border fraud
Presentation of the Euro-Ages Framework Standards
 Presentation of the Euro-Ages Framework Standards Final Conference Budapest, 22.10.2010 Birgit Hanny, ASIIN Consult GmbH Birgit Hanny, M.A., MBA ASIIN Consult GmbH www.euro-ages.eu Content I. Overview
Presentation of the Euro-Ages Framework Standards Final Conference Budapest, 22.10.2010 Birgit Hanny, ASIIN Consult GmbH Birgit Hanny, M.A., MBA ASIIN Consult GmbH www.euro-ages.eu Content I. Overview
A Semantic Web Knowledge Base System that Supports Large Scale Data Integration
 A Semantic Web Knowledge Base System that Supports Large Scale Data Integration Zhengxiang Pan, Yingjie Li and Jeff Heflin Department of Computer Science and Engineering, Lehigh University 19 Memorial
A Semantic Web Knowledge Base System that Supports Large Scale Data Integration Zhengxiang Pan, Yingjie Li and Jeff Heflin Department of Computer Science and Engineering, Lehigh University 19 Memorial
+www.medplusadvantage.com/grad
 Med Plus +www.medplusadvantage.com/grad Advantage Sponsored by the American Medical Association disability income protection AMA-Sponsored Group Insurance for Resident Continuees + Med Plus Advantage Sponsored
Med Plus +www.medplusadvantage.com/grad Advantage Sponsored by the American Medical Association disability income protection AMA-Sponsored Group Insurance for Resident Continuees + Med Plus Advantage Sponsored
Course Schedule for Graduate School of Science. Special Integrated Science Course SISC International Physics Course IPC ( 2015.
 Course Schedule for Graduate School of Science Special Integrated Science CourseSISC International Physics CourseIPC ( 2015.Spring to Fall ) Contents Contents How to Read Course Schedule Spring Semester
Course Schedule for Graduate School of Science Special Integrated Science CourseSISC International Physics CourseIPC ( 2015.Spring to Fall ) Contents Contents How to Read Course Schedule Spring Semester
Reducing)cycle)time)of)test,) development)and)analysis)with)data) virtualization)) May,%2015% David%Chang,%Senior%Vice%President,%Ac<fio%Inc.
 Reducing)cycle)time)of)test,) development)and)analysis)with)data) virtualization)) May,2015 DavidChang,SeniorVicePresident,Ac
Reducing)cycle)time)of)test,) development)and)analysis)with)data) virtualization)) May,2015 DavidChang,SeniorVicePresident,Ac
Assessing the Quality of Doctoral Programs in Criminology in the United States*
 Assessing the Quality of Doctoral Programs in Criminology in the United States* Benjamin Steiner; John Schwartz Journal of Criminal Justice Education; Mar 2007; 18, 1; Research Library pg. 53 Reproduced
Assessing the Quality of Doctoral Programs in Criminology in the United States* Benjamin Steiner; John Schwartz Journal of Criminal Justice Education; Mar 2007; 18, 1; Research Library pg. 53 Reproduced
ENERGY: MODULAR POWER SYSTEM SIMULATOR. BASIC MODULE
 issue:01/11 ENERGY: MODULAR POWER SYSTEM SIMULATOR. BASIC MODULE Ref: 0510 1 / 2 ITEM REFERENCE DESCRIPTION QTY. 1 MPSSC MODULAR POWER SYSTEM SIMULATOR WITH SCADA 1 CONTROL SYSTEM, FORMED BY: SCADA SCADA
issue:01/11 ENERGY: MODULAR POWER SYSTEM SIMULATOR. BASIC MODULE Ref: 0510 1 / 2 ITEM REFERENCE DESCRIPTION QTY. 1 MPSSC MODULAR POWER SYSTEM SIMULATOR WITH SCADA 1 CONTROL SYSTEM, FORMED BY: SCADA SCADA
MAINE STATE LIBRARY. Published by MAINE LEAGUE FOR NURSING COMMITTEE OF CAREERS. In cooperation with BLUE CROSS-BLUE SHIELD
 MAINE STATE LIBRARY Published by MAINE LEAGUE FOR NURSING COMMITTEE OF CAREERS In cooperation with BLUE CROSS-BLUE SHIELD Associated Hospital Service of Main e 509 Forest Ave. Portland, Me. ' For Further
MAINE STATE LIBRARY Published by MAINE LEAGUE FOR NURSING COMMITTEE OF CAREERS In cooperation with BLUE CROSS-BLUE SHIELD Associated Hospital Service of Main e 509 Forest Ave. Portland, Me. ' For Further
IBM MobileFirst Protect (MaaS360) Mobile Enterprise Gateway Migration Guide
 IBM MobileFirst Protect (MaaS360) Mobile Enterprise Gateway Migration Guide Version 2.3.0 Copyright 2015 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change
IBM MobileFirst Protect (MaaS360) Mobile Enterprise Gateway Migration Guide Version 2.3.0 Copyright 2015 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change
Program Outcome 1 demonstrate an understanding of culture impacts international business.
 Standard #4 a. Program Outcomes for the International Business Program Graduate International BusinessStudents will be able to : Program Outcome 1 demonstrate an understanding of culture impacts international
Standard #4 a. Program Outcomes for the International Business Program Graduate International BusinessStudents will be able to : Program Outcome 1 demonstrate an understanding of culture impacts international
PERSONAL ACCOUNT OPENING FORM - JOINT APPLICANT
 PERSONAL ACCOUNT OPENING FORM - JOINT APPLICANT A. PERSONAL DETAILS Title: Mr Mrs Miss Minor Family name First name(s) Maiden/ Former name. Marital status Single Married Others If married, spouse full
PERSONAL ACCOUNT OPENING FORM - JOINT APPLICANT A. PERSONAL DETAILS Title: Mr Mrs Miss Minor Family name First name(s) Maiden/ Former name. Marital status Single Married Others If married, spouse full
Reaching adolescents through health services
 November 2015 Reaching adolescents through health services Dr V Chandra-Mouli (chandramouliv@who.int) Training Course in Sexual and Reproductive Health Research Geneva 2015 1 What do we mean by the term
November 2015 Reaching adolescents through health services Dr V Chandra-Mouli (chandramouliv@who.int) Training Course in Sexual and Reproductive Health Research Geneva 2015 1 What do we mean by the term
Abstract. Animportantcharacteristicofthesoftwaredevelopmentprocessisthedegreeofreusabilityofsoftware.Simplyspeaking,knowledgeonceencoded
 Largeheterogeneousknowledgebases RoyalInstituteofTechnology,Sweden EnnTyugu 1Softwarereusability tionlanguageoflargeknowledgebasesareconsidered.higherorder Userrequirements,architectureandinternalknowledgerepresenta-
Largeheterogeneousknowledgebases RoyalInstituteofTechnology,Sweden EnnTyugu 1Softwarereusability tionlanguageoflargeknowledgebasesareconsidered.higherorder Userrequirements,architectureandinternalknowledgerepresenta-
A Look at the New Converged Data Center
 Organizations around the world are choosing to move from traditional physical data centers to virtual infrastructure, affecting every layer in the data center stack. This change will not only yield a scalable
Organizations around the world are choosing to move from traditional physical data centers to virtual infrastructure, affecting every layer in the data center stack. This change will not only yield a scalable
Faster, Cheaper, Better a Hybridization Methodology to Develop Linear Algebra Software for GPUs
 Faster, Cheaper, Better a Hybridization Methodology to Develop Linear Algebra Software for GPUs Emmanuel Agullo Cédric Augonnet Jack Dongarra Hatem Ltaief Raymond Namyst Samuel Thibault Stanimire Tomov
Faster, Cheaper, Better a Hybridization Methodology to Develop Linear Algebra Software for GPUs Emmanuel Agullo Cédric Augonnet Jack Dongarra Hatem Ltaief Raymond Namyst Samuel Thibault Stanimire Tomov
Model-Based Design Environment for Clinical Information Systems
 Model-Based Design Environment for Clinical Information Systems Janos Mathe, Sean Duncavage, Jan Werner, Akos Ledeczi, Bradley Malin, Janos Sztipanovits Vanderbilt University TRUST Review, October 11,
Model-Based Design Environment for Clinical Information Systems Janos Mathe, Sean Duncavage, Jan Werner, Akos Ledeczi, Bradley Malin, Janos Sztipanovits Vanderbilt University TRUST Review, October 11,
Security Rationale of Grid Data Management Systems Security Requirements Analysis, Derivation of Security Policies, and Rationale of Security Services
 Security Rationale of Grid Data Management Systems Security Requirements Analysis, Derivation of Security Policies, and Rationale of Security Services Syed Naqvi 1,2, Philippe Massonet 1, Alvaro Arenas
Security Rationale of Grid Data Management Systems Security Requirements Analysis, Derivation of Security Policies, and Rationale of Security Services Syed Naqvi 1,2, Philippe Massonet 1, Alvaro Arenas
Graduate School of Informatics
 Graduate School of Informatics Admissions Policy '( ) ' ' - Master's Degree Program Major Enrollment Capacity 40 40 Doctor's Degree Program Major Enrollment Capacity 8 1 M. Entrance examination for international
Graduate School of Informatics Admissions Policy '( ) ' ' - Master's Degree Program Major Enrollment Capacity 40 40 Doctor's Degree Program Major Enrollment Capacity 8 1 M. Entrance examination for international
Competency-based Education
 Competency-based Education New Challenges and New Opportunities IATUL Annual Conference July 7, 2015 What is Competency Based Education? Form of education derives from analysis of prospective or actual
Competency-based Education New Challenges and New Opportunities IATUL Annual Conference July 7, 2015 What is Competency Based Education? Form of education derives from analysis of prospective or actual
HIV& AIDS BASIC FACTS. HIV & Drug Use. You are better off knowing if you have HIV. HIV & Sex. What are HIV & AIDS? HIV & Blood Products
 What are HIV &? serious stage of HIV infection, called. stands for Acquired getting and can stay healthy for a long time. your age your sex your race or ethnic origin who you have sex with to a fetus or
What are HIV &? serious stage of HIV infection, called. stands for Acquired getting and can stay healthy for a long time. your age your sex your race or ethnic origin who you have sex with to a fetus or
MONPOLY: Monitoring Usage-control Policies
 MONPOLY: Monitoring Usage-control Policies David Basin, Matúš Harvan, Felix Klaedtke, and Eugen Zălinescu Computer Science Department, ETH Zurich, Switzerland 1 Introduction Determining whether the usage
MONPOLY: Monitoring Usage-control Policies David Basin, Matúš Harvan, Felix Klaedtke, and Eugen Zălinescu Computer Science Department, ETH Zurich, Switzerland 1 Introduction Determining whether the usage
Enabling Legacy Applications on Heterogeneous Platforms
 Enabling Legacy Applications on Heterogeneous Platforms Michela Becchi, Srihari Cadambi and Srimat Chakradhar NEC Laboratories America, Inc. {mbecchi, cadambi, chak}@nec-labs.com Abstract In this paper
Enabling Legacy Applications on Heterogeneous Platforms Michela Becchi, Srihari Cadambi and Srimat Chakradhar NEC Laboratories America, Inc. {mbecchi, cadambi, chak}@nec-labs.com Abstract In this paper
Standard #4. a. Program Outcomes for the Human Resources Program. Students will be able to
 Standard #4 a. Program Outcomes for the Human Resources Program Students will be able to Learning Outcome #1 synthesize the role of human resources management as it supports the success of the organization
Standard #4 a. Program Outcomes for the Human Resources Program Students will be able to Learning Outcome #1 synthesize the role of human resources management as it supports the success of the organization
Strongly Agree or Agree Strongly Disagree or Disagree No response or felt item not applicable to degree
 all survey respondents from the programs within each Academic Unit: 26-, 2-8, and 28- COURSE/ACTIVITY program components: Percentages of ALL survey respondents who were graduates of doctoral programs other
all survey respondents from the programs within each Academic Unit: 26-, 2-8, and 28- COURSE/ACTIVITY program components: Percentages of ALL survey respondents who were graduates of doctoral programs other
THE ROLE OF THE OCCUPATIONAL HEALTH PROVIDER IN PRE- EMPLOYMENT MEDICAL SCREENINGS AND POST WORK INJURY TREATMENT
 THE ROLE OF THE OCCUPATIONAL HEALTH PROVIDER IN PRE- EMPLOYMENT MEDICAL SCREENINGS AND POST WORK INJURY TREATMENT I. Pre-Employment Medical Screenings With the economy showing signs of recovery, it is
THE ROLE OF THE OCCUPATIONAL HEALTH PROVIDER IN PRE- EMPLOYMENT MEDICAL SCREENINGS AND POST WORK INJURY TREATMENT I. Pre-Employment Medical Screenings With the economy showing signs of recovery, it is
Intelligent Service Trading and Brokering for Distributed Network Services in GridSolve
 Intelligent Service Trading and Brokering for Distributed Network Services in GridSolve Aurlie Hurault 1 and Asim YarKhan 2 1 Institut de Recherche en Informatique de Toulouse - UMR 5505 University of
Intelligent Service Trading and Brokering for Distributed Network Services in GridSolve Aurlie Hurault 1 and Asim YarKhan 2 1 Institut de Recherche en Informatique de Toulouse - UMR 5505 University of
Customizing the Security Architecture
 Chapter7.fm Page 113 Wednesday, April 30, 2003 4:29 PM CHAPTER7 Customizing the Security Architecture The office of government is not to confer happiness, but to give men opportunity to work out happiness
Chapter7.fm Page 113 Wednesday, April 30, 2003 4:29 PM CHAPTER7 Customizing the Security Architecture The office of government is not to confer happiness, but to give men opportunity to work out happiness
CryptographicallyEnforced
 Cryptographically CryptographicallyEnforced Enforced RBAC RBAC Georg Fuchsbauer (IST Austria) 27 June 2013, CSF joint work with Anna Lisa Ferrara and Bogdan Warinschi (University of Bristol) Overview Cryptographically
Cryptographically CryptographicallyEnforced Enforced RBAC RBAC Georg Fuchsbauer (IST Austria) 27 June 2013, CSF joint work with Anna Lisa Ferrara and Bogdan Warinschi (University of Bristol) Overview Cryptographically
How To Talk to Your Doctor
 How To Talk to Your Doctor Leander R. McDonald, PhD, Richard Ludtke, PhD, Twyla Baker-Demaray, MA, Kim Ruliffson, BA, Ann Miller, Jim LaBelle, MA, George Charles, PhD, Cheryl Easley, PhD, Noreen Mokuau,
How To Talk to Your Doctor Leander R. McDonald, PhD, Richard Ludtke, PhD, Twyla Baker-Demaray, MA, Kim Ruliffson, BA, Ann Miller, Jim LaBelle, MA, George Charles, PhD, Cheryl Easley, PhD, Noreen Mokuau,
CiteSeer x : A Cloud Perspective. Pradeep Teregowda, Bhuvan Urgaonkar, C. Lee Giles Pennsylvania State University
 CiteSeer x : A Cloud Perspective Pradeep Teregowda, Bhuvan Urgaonkar, C. Lee Giles Pennsylvania State University Problem Definition apple Question: How to effectively move a digital library, CiteSeer x,
CiteSeer x : A Cloud Perspective Pradeep Teregowda, Bhuvan Urgaonkar, C. Lee Giles Pennsylvania State University Problem Definition apple Question: How to effectively move a digital library, CiteSeer x,
TIBCO MFT Platform Server for IBM i User Guide. Software Release 7.1.0 April 2013
 TIBCO MFT Platform Server for IBM i User Guide Software Release 7.1.0 April 2013 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO
TIBCO MFT Platform Server for IBM i User Guide Software Release 7.1.0 April 2013 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED OR BUNDLED TIBCO
FLEETVIEW ONLINE THE NEW AND IMPROVED FLEETVIEW ONLINE, NOW INCLUDING:
 FLEETVIEW ONLINE THE NEW AND IMPROVED FLEETVIEW ONLINE, NOW INCLUDING: CHART AND DATA MANAGEMENT FUEL EFFICIENCY MONITORING PIRACY INFORMATION SHIP SECURITY FLEET TRACKING FLEETVIEW ONLINE FleetView Online
FLEETVIEW ONLINE THE NEW AND IMPROVED FLEETVIEW ONLINE, NOW INCLUDING: CHART AND DATA MANAGEMENT FUEL EFFICIENCY MONITORING PIRACY INFORMATION SHIP SECURITY FLEET TRACKING FLEETVIEW ONLINE FleetView Online
Health & Government Module 5 i2p Expedition India
 Health & Government Module 5 i2p Expedition India National Emblem of India : Emblem i2p Expedition India India 2011 1 Take Home Points The United Nations has declared access to basic health care a human
Health & Government Module 5 i2p Expedition India National Emblem of India : Emblem i2p Expedition India India 2011 1 Take Home Points The United Nations has declared access to basic health care a human
Introducing the product
 Introducing the product The challenge Database Activity Monitoring provides privileged user and application access monitoring that is independent of native database logging and audit functions. It can
Introducing the product The challenge Database Activity Monitoring provides privileged user and application access monitoring that is independent of native database logging and audit functions. It can
VALUE ADDED SERVICES ON NAYATEL PHONE LINES Version 1.0
 A Micronet Broad band Company VALUE ADDED SERVICES ON NAYATEL PHONE LINES Version 1.0 Code Barring Call Waiting Call Forwarding Wake up Call Don t Disturb Service Speed Dial 1 Call Transfer Three Way Conference
A Micronet Broad band Company VALUE ADDED SERVICES ON NAYATEL PHONE LINES Version 1.0 Code Barring Call Waiting Call Forwarding Wake up Call Don t Disturb Service Speed Dial 1 Call Transfer Three Way Conference
TRANSFER GUIDELINES TRANSFER GUIDELINES FOR MINISTRY OF HEALTH
 TRANSFER GUIDELINES June 2012 TRANSFER GUIDELINES FOR MINISTRY OF HEALTH 2012 1 Contents FOREWORD 4 Interpretations 5 1.0 Background 6 2.0 Objectives 6 2.1 Definition of transfer 6 3.0 Conditions of transfer
TRANSFER GUIDELINES June 2012 TRANSFER GUIDELINES FOR MINISTRY OF HEALTH 2012 1 Contents FOREWORD 4 Interpretations 5 1.0 Background 6 2.0 Objectives 6 2.1 Definition of transfer 6 3.0 Conditions of transfer
Using Text Analytics to Accurately Segment Workers Compensation Injuries
 Using Text Analytics to Accurately Segment Workers Compensation Injuries Presented by: Amir Biagi Associate, Predictive Modeling March 7, 2012 San Francisco, CA Insurance is a data driven industry, and
Using Text Analytics to Accurately Segment Workers Compensation Injuries Presented by: Amir Biagi Associate, Predictive Modeling March 7, 2012 San Francisco, CA Insurance is a data driven industry, and
Release Notes. Audit Integration Component 6.1. Notice. September 13, 2006
 Release Notes Audit Integration Component 6.1 September 13, 2006 Notice The content in this document represents the current view of Altiris as of the date of publication. Because Altiris responds continually
Release Notes Audit Integration Component 6.1 September 13, 2006 Notice The content in this document represents the current view of Altiris as of the date of publication. Because Altiris responds continually
Medical Professionalism in Lebanon: Challenges and Aspirations. Kamal F Badr, MD Associate Dean for Medical Education American University of Beirut
 Medical Professionalism in Lebanon: Challenges and Aspirations Kamal F Badr, MD Associate Dean for Medical Education American University of Beirut Medical Professionalism in Lebanon: Challenges and Aspirations
Medical Professionalism in Lebanon: Challenges and Aspirations Kamal F Badr, MD Associate Dean for Medical Education American University of Beirut Medical Professionalism in Lebanon: Challenges and Aspirations
For additional information on T.I.P.S. please call us at 818-787-3946 or email tips@nagyprotectionservices.com
 TOTALLY INTEGRATED PROTECTION SERVICES (T.I.P.S) 1 T.I.P.S (Totally Integrated Protection Services) Security Risk Analysis Survey Reports Contract security officer services Special event security services
TOTALLY INTEGRATED PROTECTION SERVICES (T.I.P.S) 1 T.I.P.S (Totally Integrated Protection Services) Security Risk Analysis Survey Reports Contract security officer services Special event security services
The Jini Proxy. 1. Purpose. Esmond Pitt and Neil Belford. White Paper
 16 September 2001 The Jini Proxy Esmond Pitt and Neil Belford White Paper 1. Purpose 1.1 INTRODUCTION This White Paper describes the Jini Proxy, a standard approach to enabling and controlling Jini rmi
16 September 2001 The Jini Proxy Esmond Pitt and Neil Belford White Paper 1. Purpose 1.1 INTRODUCTION This White Paper describes the Jini Proxy, a standard approach to enabling and controlling Jini rmi
5. Graduate Degrees Awarded. Graduate School, Department
 5. Degrees Awarded 2012/5/21 School, Department School of Theology School of Humanities Theology Philosophy Aesthetics Psychology Education Japanese History Western History Japanese English French German
5. Degrees Awarded 2012/5/21 School, Department School of Theology School of Humanities Theology Philosophy Aesthetics Psychology Education Japanese History Western History Japanese English French German
LUCA GAMMAITONI NiPS Laboratory Università di Perugia, Italy. www.nipslab.org
 LUCA GAMMAITONI NiPS Laboratory Università di Perugia, Italy www.nipslab.org Why are we spending time with the subject of Energy Harvesting? Why is Energy Harvesting so difficult? What are fluctuations
LUCA GAMMAITONI NiPS Laboratory Università di Perugia, Italy www.nipslab.org Why are we spending time with the subject of Energy Harvesting? Why is Energy Harvesting so difficult? What are fluctuations
This doesn t seem like much water. Until it s this deep in your offi ce.
 not just water damage but the real threat of mold patients in the office the next day. It was as if nothing had ever happened. Phn. 757.473.0560 Fax. 757.473.9986 Toll Free 800.743.1714 not just water
not just water damage but the real threat of mold patients in the office the next day. It was as if nothing had ever happened. Phn. 757.473.0560 Fax. 757.473.9986 Toll Free 800.743.1714 not just water
Annual Information Returns Dos and Don ts
 1. Preparation of Annual Information Return (Original AIR) (a) Prepare the return as per the file format notified by ITD. It can be prepared using any in-house/third-party software. You can also use the
1. Preparation of Annual Information Return (Original AIR) (a) Prepare the return as per the file format notified by ITD. It can be prepared using any in-house/third-party software. You can also use the
Question 1 Question 2. Question 3 How many online classes have you taken here at The University of West Florida? answered question skipped question
 Please see the data below for discussion related to student perception of online and traditional classes offered at UWF. Although this is a small percentage of UWF students, I think the contrasts between
Please see the data below for discussion related to student perception of online and traditional classes offered at UWF. Although this is a small percentage of UWF students, I think the contrasts between
MSME Program Educational Objectives
 MSME Program Educational Objectives (1) The Master of Science degree program in Mechanical Engineering will achieve excellence and recognition in teaching and learning at an advanced level. (2) The Master
MSME Program Educational Objectives (1) The Master of Science degree program in Mechanical Engineering will achieve excellence and recognition in teaching and learning at an advanced level. (2) The Master
Financial Advisory Services & Training Financial Services Department www.finance.utoronto.ca/fast
 Work Instruction Budget Movement Report For Fund Centers ZFTR055 When to Use This report is used to view the budget activity and totals for Funds Centers. Report Functionality Report can be run for individual
Work Instruction Budget Movement Report For Fund Centers ZFTR055 When to Use This report is used to view the budget activity and totals for Funds Centers. Report Functionality Report can be run for individual
Security Management System Wiring Diagram Portfolio
 Security Management System Wiring Diagram Portfolio SMS Wiring Portfolio Schlage Management System Table of Contents Section 1 Section 2 Section 3 Section 4 Section 5 Section 6 SMS Reader Controller Configurations
Security Management System Wiring Diagram Portfolio SMS Wiring Portfolio Schlage Management System Table of Contents Section 1 Section 2 Section 3 Section 4 Section 5 Section 6 SMS Reader Controller Configurations
GROUP ASSURANCE APPLICATION FOR DISABILITY BENEFITS
 APPLICATION FO DISABILITY BENEFITS GUIDELINES Please help Old Mutual Group Assurance to assess your claim correctly, and faster, by using these guidelines. 1. Complete the application form in detail as
APPLICATION FO DISABILITY BENEFITS GUIDELINES Please help Old Mutual Group Assurance to assess your claim correctly, and faster, by using these guidelines. 1. Complete the application form in detail as
PROVIDING NATIVE SUPPORT FOR FEDERATED IDENTITY MANAGEMENT IN A BUSINESS-PROCESS-MANAGEMENT SYSTEM
 PROVIDING NATIVE SUPPORT FOR FEDERATED IDENTITY MANAGEMENT IN A BUSINESS-PROCESS-MANAGEMENT SYSTEM Identity Business Processes Jens Müller Faculty of Informatics, Karlsruhe Institute of Technology, Karlsruhe,
PROVIDING NATIVE SUPPORT FOR FEDERATED IDENTITY MANAGEMENT IN A BUSINESS-PROCESS-MANAGEMENT SYSTEM Identity Business Processes Jens Müller Faculty of Informatics, Karlsruhe Institute of Technology, Karlsruhe,
Displaying an innovative approach towards port management
 Displaying an innovative approach towards port management Port Management Information Systems As part of the world trade system, ports are complex entities.they need the full range of solutions to provide
Displaying an innovative approach towards port management Port Management Information Systems As part of the world trade system, ports are complex entities.they need the full range of solutions to provide
The Statement of Fitness for Work from sick note to fit note
 The Statement of Fitness for Work from sick note to fit note Background Information From 6 April 2010 the sick note is changing to become a fit note. Sick notes (or Medical Statements) are the forms issued
The Statement of Fitness for Work from sick note to fit note Background Information From 6 April 2010 the sick note is changing to become a fit note. Sick notes (or Medical Statements) are the forms issued
Content&Security RECOMMENDED(BEST(PRACTICES
 Content&Security RECOMMENDED(BEST(PRACTICES for(production(&(post(production(/(editorial( Version(16.2 MANAGEMENT(CONTROLS PERSONNEL(AND(RESOURCES(/(PRODUCTION(OFFICE ASSET(MANAGEMENT(/(CAMERA(MEDIA PHYSICAL(SECURITY
Content&Security RECOMMENDED(BEST(PRACTICES for(production(&(post(production(/(editorial( Version(16.2 MANAGEMENT(CONTROLS PERSONNEL(AND(RESOURCES(/(PRODUCTION(OFFICE ASSET(MANAGEMENT(/(CAMERA(MEDIA PHYSICAL(SECURITY
Kāhuna Lapaÿau Healers & Food Science
 Kāhuna Lapaÿau Healers & Food Science The field of medicine was one of the greatest strengths of our kūpuna, not only the diagnoses but also the treatments were very skilled procedures. They understood
Kāhuna Lapaÿau Healers & Food Science The field of medicine was one of the greatest strengths of our kūpuna, not only the diagnoses but also the treatments were very skilled procedures. They understood
BEING MOBILE WITH WINDOWS 8.1
 www.realdolmen.com BEING MOBILE WITH WINDOWS 8.1 OCTOBER 28, 2014 SLIDE 1 SPEAKERS INTRO #Name: D Hoker Gino #Function: Technology Expert #Email: gino.dhoker@realdolmen.com #Twitter: @GinoDH #Blog: #Mobile:
www.realdolmen.com BEING MOBILE WITH WINDOWS 8.1 OCTOBER 28, 2014 SLIDE 1 SPEAKERS INTRO #Name: D Hoker Gino #Function: Technology Expert #Email: gino.dhoker@realdolmen.com #Twitter: @GinoDH #Blog: #Mobile:
CARING IN PLACE WEB USER GUIDE
 CARING IN PLACE WEB USER GUIDE Instructions on how to use Caring in Place on the web The purpose of this document is to help you get started with Caring in Place on the web. Caring in Place is also available
CARING IN PLACE WEB USER GUIDE Instructions on how to use Caring in Place on the web The purpose of this document is to help you get started with Caring in Place on the web. Caring in Place is also available
Workforce Development for People with Intellectual Disabilities
 Developing people for health and healthcare Workforce Development for People with Intellectual Disabilities The report of the Kent, Surrey and Sussex Intellectual Disabilities Workforce Scoping Project
Developing people for health and healthcare Workforce Development for People with Intellectual Disabilities The report of the Kent, Surrey and Sussex Intellectual Disabilities Workforce Scoping Project
Fighting autism spectrum disorder: A mother s story
 30/8/2015 (August 8, 2015) The Citizen, Tanzania Fighting autism spectrum disorder: A mother s story In Summary When Grace Lyimo learnt about plans to kill her autistic son, she embarked on a mission to
30/8/2015 (August 8, 2015) The Citizen, Tanzania Fighting autism spectrum disorder: A mother s story In Summary When Grace Lyimo learnt about plans to kill her autistic son, she embarked on a mission to
Department of Defense
 OFFICE OF THE INSPECTOR GENERAL REPORTING OF ACCOUNTS PAYABLE FOR THE NATIONAL GUARD AND RESERVE EQUIPMENT APPROPRIATION ON THE "OTHER DEFENSE ORGANIZATIONS" PORTION OF THE FY 1996 FINANCIAL STATE1\1ENTS
OFFICE OF THE INSPECTOR GENERAL REPORTING OF ACCOUNTS PAYABLE FOR THE NATIONAL GUARD AND RESERVE EQUIPMENT APPROPRIATION ON THE "OTHER DEFENSE ORGANIZATIONS" PORTION OF THE FY 1996 FINANCIAL STATE1\1ENTS
2016 Hospital National Patient Safety Goals
 2016 Hospital The purpose of the is to improve patient safety. The goals focus on problems in Improve staff communication NPSG.02.03.01 Get important test results to the right staff person on time. Use
2016 Hospital The purpose of the is to improve patient safety. The goals focus on problems in Improve staff communication NPSG.02.03.01 Get important test results to the right staff person on time. Use
State of the EHR: The Vendor Perspective
 State of the EHR: The Vendor Perspective AHIMA is the national association of health information management (HIM) professionals. AHIMA s 50,000 members are dedicated to the effective management of personal
State of the EHR: The Vendor Perspective AHIMA is the national association of health information management (HIM) professionals. AHIMA s 50,000 members are dedicated to the effective management of personal
FORMAL METHOD TO IMPLEMENT FUZZY REQUIREMENTS MÉTODO FORMAL PARA IMPLEMENTAR REQUERIMIENTOS DIFUSOS
 FORMAL METHOD TO IMPLEMENT FUZZY REQUIREMENTS MÉTODO FORMAL PARA IMPLEMENTAR REQUERIMIENTOS DIFUSOS MARLENE GONCALVES Ph.D, Universidad Simón Bolívar, Caracas, Venezuela, mgoncalves@usb.ve ROSSELINE RODRÍGUEZ
FORMAL METHOD TO IMPLEMENT FUZZY REQUIREMENTS MÉTODO FORMAL PARA IMPLEMENTAR REQUERIMIENTOS DIFUSOS MARLENE GONCALVES Ph.D, Universidad Simón Bolívar, Caracas, Venezuela, mgoncalves@usb.ve ROSSELINE RODRÍGUEZ
HEALTH ADMINISTRATION
 260 Health Administration DEPARTMENT MISSION STATEMENT HEALTH ADMINISTRATION Health Administration develops and coordinates budgets, policies, and procedures for the County s health care departments in
260 Health Administration DEPARTMENT MISSION STATEMENT HEALTH ADMINISTRATION Health Administration develops and coordinates budgets, policies, and procedures for the County s health care departments in
Snapshot REPORT DEGREE ATTAINMENT. S&E Degrees Becoming More Prevalent. Science and Engineering Degrees as Percentage of All Degrees (2004, 2014)
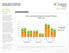 S&E Degrees Becoming More Prevalent From to, science and ineering degrees increased in prevalence for both genders. The trend was driven by growth in the socalled hard sciences. The percentage of bachelor
S&E Degrees Becoming More Prevalent From to, science and ineering degrees increased in prevalence for both genders. The trend was driven by growth in the socalled hard sciences. The percentage of bachelor
What are research, evaluation and audit?
 1 What are research, evaluation and audit? Barbara Sen, Maria J. Grant and Hannah Spring I don t do research. I don t have the time. I am too busy with the day to day running of the library. I do evaluations
1 What are research, evaluation and audit? Barbara Sen, Maria J. Grant and Hannah Spring I don t do research. I don t have the time. I am too busy with the day to day running of the library. I do evaluations
INFORMATION ON DOCTORATE PROGRAMS
 INFORMATION ON DOCTORATE PROGRAMS PH.D. IN CLINICAL-SURGICAL SCIENCES PH.D. IN ENVIRONMENTAL ANALYSIS AND MANAGEMENT PH.D. IN APPLIED ANTHROPOLOGY PH.D. IN BIOENGINEERING PH.D. IN MOLECULAR AND CELLULAR
INFORMATION ON DOCTORATE PROGRAMS PH.D. IN CLINICAL-SURGICAL SCIENCES PH.D. IN ENVIRONMENTAL ANALYSIS AND MANAGEMENT PH.D. IN APPLIED ANTHROPOLOGY PH.D. IN BIOENGINEERING PH.D. IN MOLECULAR AND CELLULAR
Dawn Christie PSYCHIC RETREAT & SPA BALANCING SPIRIT, MIND & BODY
 Dawn Christie PSYCHIC RETREAT & SPA BALANCING SPIRIT, MIND & BODY Dawn Christie Dawn Christie is an internationally acclaimed psychic, spiritual healer, consultant, teacher and lecturer. For over 25 years,
Dawn Christie PSYCHIC RETREAT & SPA BALANCING SPIRIT, MIND & BODY Dawn Christie Dawn Christie is an internationally acclaimed psychic, spiritual healer, consultant, teacher and lecturer. For over 25 years,
Recent&DSU&Successes&
 " Dakota&State&University& College&of&Computing& 820&N&Washington&Ave& East&Hall&104A& Madison,&SD&57042& " Written&Testimony&from:& JoshuaJ.Pauli,Ph.D. ProfessorofCyberSecurity DakotaStateUniversity Josh.Pauli@dsu.edu
" Dakota&State&University& College&of&Computing& 820&N&Washington&Ave& East&Hall&104A& Madison,&SD&57042& " Written&Testimony&from:& JoshuaJ.Pauli,Ph.D. ProfessorofCyberSecurity DakotaStateUniversity Josh.Pauli@dsu.edu
Department. CardholderGuide. Citi Commercial Cards Department of Defense
 Department ofdefense TravelCard CardholderGuide Citi Commercial Cards Department of Defense Index Welcome... 1 Cardholders Benefit... 1 Lost Luggage Insurance... 2 Travel Accident Insurance... 2 Key Responsibilities...
Department ofdefense TravelCard CardholderGuide Citi Commercial Cards Department of Defense Index Welcome... 1 Cardholders Benefit... 1 Lost Luggage Insurance... 2 Travel Accident Insurance... 2 Key Responsibilities...
December 2011 LearningPoint System Learner Workbook Page 1 Center for Learning and Professional Development CLPD
 December 2011 LearningPoint System Learner Workbook Page 1 LearningPoint System Learner Workbook Overview Introduction The purpose of this workbook is to provide an overview of LearningPoint, Brown s new
December 2011 LearningPoint System Learner Workbook Page 1 LearningPoint System Learner Workbook Overview Introduction The purpose of this workbook is to provide an overview of LearningPoint, Brown s new
88-28-6. Fees. Fees for certificates of approval, registration of representatives, and
 . Fees. Fees for certificates of approval, registration of representatives, and certain transcripts shall be collected by the state board in accordance with this regulation. (a) For institutions domiciled
. Fees. Fees for certificates of approval, registration of representatives, and certain transcripts shall be collected by the state board in accordance with this regulation. (a) For institutions domiciled
Select the right solution for identity and access governance
 IBM Security Buyer s Guide June 2015 Select the right solution for identity and access governance Protecting critical assets from unauthorized access 2 Select the right solution for identity and access
IBM Security Buyer s Guide June 2015 Select the right solution for identity and access governance Protecting critical assets from unauthorized access 2 Select the right solution for identity and access
How To Get Insurance In Finland
 Insurance against an accident at work or occupational disease for employees coming to Finland Content: If you are coming to Finland from another EU member state 4 If you are coming to Finland from outside
Insurance against an accident at work or occupational disease for employees coming to Finland Content: If you are coming to Finland from another EU member state 4 If you are coming to Finland from outside
Guide to the San Diego County Medical Society Records. http://oac.cdlib.org/findaid/ark:/13030/kt5k4034br No online items
 http://oac.cdlib.org/findaid/ark:/13030/kt5k4034br No online items Copyright 2007 Special Collections & University Archives. All rights reserved. 2007-12-03 5500 Campanile Dr. MC 8050 San Diego, CA, 92182-8050
http://oac.cdlib.org/findaid/ark:/13030/kt5k4034br No online items Copyright 2007 Special Collections & University Archives. All rights reserved. 2007-12-03 5500 Campanile Dr. MC 8050 San Diego, CA, 92182-8050
Allied Health Professions
 Allied Health Professions Presented By: Dorothy M. Hendrix Assistant Dean College of Science and Health Charles R. Drew University of Medicine and Science HEALTH CAREERS THE ALLIED HEALTH PROFESSIONS The
Allied Health Professions Presented By: Dorothy M. Hendrix Assistant Dean College of Science and Health Charles R. Drew University of Medicine and Science HEALTH CAREERS THE ALLIED HEALTH PROFESSIONS The
TRANSAS DP SIMULATOR
 TRANSAS DP SIMULATOR A NAVI-TRAINER PROFESSIONAL MODULE The maritime industry faces a rapid increase in its need for certified Dynamic Positioning Operators (DPOs). This creates a demand for DPO training
TRANSAS DP SIMULATOR A NAVI-TRAINER PROFESSIONAL MODULE The maritime industry faces a rapid increase in its need for certified Dynamic Positioning Operators (DPOs). This creates a demand for DPO training
Contents. Before you begin. How to work through this learner guide Assessment
 Contents Contents Before you begin How to work through this learner guide Assessment Introduction: Assisting with claims management, rehabilitation and return-to-work programs v v vi 1 Chapter 1: Assisting
Contents Contents Before you begin How to work through this learner guide Assessment Introduction: Assisting with claims management, rehabilitation and return-to-work programs v v vi 1 Chapter 1: Assisting
MODULE 1: Introduction
 MODULE 1: Introduction Materials Flipchart, display material, pens Icebreaker Welcome everyone to the first session. Explain how long the training programme will run and how long each session will run
MODULE 1: Introduction Materials Flipchart, display material, pens Icebreaker Welcome everyone to the first session. Explain how long the training programme will run and how long each session will run
DUAL DEGREE PROGRAMS
 DUAL DEGREE PROGRAMS One of the special features of Brown s MSW program is the opportunity to seek degrees in two professions at the same time. A dual-degree program always takes longer to complete than
DUAL DEGREE PROGRAMS One of the special features of Brown s MSW program is the opportunity to seek degrees in two professions at the same time. A dual-degree program always takes longer to complete than
Allied Health Professions. PRESENTED BY: Harry E. Douglas, III, DPA Interim President Charles R. Drew University of Medicine and Science
 Allied Health Professions PRESENTED BY: Harry E. Douglas, III, DPA Interim President Charles R. Drew University of Medicine and Science November 5, 2004 HEALTH CAREERS THE ALLIED HEALTH PROFESSIONS The
Allied Health Professions PRESENTED BY: Harry E. Douglas, III, DPA Interim President Charles R. Drew University of Medicine and Science November 5, 2004 HEALTH CAREERS THE ALLIED HEALTH PROFESSIONS The
An Approach to Eliminate Semantic Heterogenity Using Ontologies in Enterprise Data Integeration
 Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 3 rd, 2013 An Approach to Eliminate Semantic Heterogenity Using Ontologies in Enterprise Data Integeration Srinivasan Shanmugam and
Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 3 rd, 2013 An Approach to Eliminate Semantic Heterogenity Using Ontologies in Enterprise Data Integeration Srinivasan Shanmugam and
7 Ways OpenStack Enables Automation & Agility for KVM Environments
 7 Ways OpenStack Enables Automation & Agility for KVM Environments Table of Contents 1. Executive Summary 1 2. About Platform9 Managed OpenStack 2 3. 7 Benefits of Automating your KVM with OpenStack 1.
7 Ways OpenStack Enables Automation & Agility for KVM Environments Table of Contents 1. Executive Summary 1 2. About Platform9 Managed OpenStack 2 3. 7 Benefits of Automating your KVM with OpenStack 1.
How LAPACK library enables Microsoft Visual Studio support with CMake and LAPACKE
 How LAPACK library enables Microsoft Visual Studio support with CMake and LAPACKE Julie Langou 1, Bill Hoffman 2, Brad King 2 1. University of Tennessee Knoxville, USA 2. Kitware Inc., USA This article
How LAPACK library enables Microsoft Visual Studio support with CMake and LAPACKE Julie Langou 1, Bill Hoffman 2, Brad King 2 1. University of Tennessee Knoxville, USA 2. Kitware Inc., USA This article

