Enabling Fingerprint Authentication in Embedded Systems for Wireless Applications
|
|
|
- Hugo Griffin
- 10 years ago
- Views:
Transcription
1 Abstract Enabling Authentication in Embedded Systems for Wireless Applications P.S. Cheng, Y.S. Moon, Z.G. Cao, K.C. Chan, T.Y. Tang In this paper, we study different methodologies for implementing fingerprint authentication in embedded systems, namely the DSP and System-on-Chip approaches, for Wireless Applications. Experiments were conducted for evaluation of these approaches. Results show that the SoC system with fixed-point arithmetic support is probably the most ideal candidate. Department of Computer Science and Engineering The Chinese University of Hong Kong Correspondence 1. Introduction With the recent development in mobile commerce, authentication technologies quickly become critical parts in mobile embedded devices like PDAs, cell-phones, etc. Among such technologies, fingerprint matching is the most common method. Yet, fingerprint matching algorithms involve substantial amounts of computation, making it a nontrivial task to achieve in the embedded devices. Several methods can be used to enable the implementation of fingerprint authentication in embedded systems. They include the Application Specific Integrated Circuit (ASIC), Digital Signal Processor (DSP) and System-on-Chip (SoC) methods. In this paper, we will review the fingerprint matching algorithms and study their implementation using DSP and SoC methods experimentally. Our experience should provide a guidance for future development of other biometrics applications in the embedded system environment. 2. embedded systems system can be generally divided, according to their purpose of application, into two types: identification and verification applications. Identification application means identification of a person from a group of individuals. It often searches a database for the identity of a person using the person s fingerprint as index. The database size can range from a few persons (home use) to hundreds of persons. The performance of such system is database size dependent. Access control is a typical identification example. Figure 1 shows the block diagram of a common access control system. Enrollment is conducted when a user first registered a fingerprint in the system. The core part of the system is the authentication device. It needs to handle different connections such as Ethernet, RS232 and Wiegand (an industrial standard security protocol sending bit strings of specified length and specified content) in order to communicate with the enrollment machine, database server and security controller. Since our concern is limited to embedded systems, we will focus on those applications involving only a few fingerprint records so that all the components in Figure 1 are housed in one single embedded system enrollment machine authentication device Figure 1: Block diagram of physical access control system authentication often refers to the verification of a person s identity using his/her fingerprints. It is actually a 1- to-1 fingerprint matching problem. Such a problem can be well handled by a desktop PC in real time. The block diagram of fingerprint verification system is shown in Figure 2. Capture Enrollment phrase Authentication phrase Capture Ethernet Wiegand Security Controller Features extraction Features extraction database server LCD (Output device) Feature Template Door Lock Minutia Matching score Figure 2: verification system In mobile commerce activities, the authentication will be conducted in a PDA or cell-hone. When implementing such an application in an embedded device like a PDA, we encounter difficulties due to slower CPU speeds, absence of cache and most important of all, absence of a floating point unit. While optimizing the authentication, we cannot afford to sacrifice reliability. Thus, a fast, low cost and accurate methodology must be developed for fingerprint matching for embedded applications. 3. basics Matching score A human being s fingerprint contains numerous ridgelines. The end of a ridgeline forms a termination and the merge of
2 two ridgelines forms a bifurcation as shown in Figure 3. A termination or a bifurcation is called a minutia point. The set of the minutia points constitute the features characterizing a fingerprint. The matching of two fingerprints is based on comparing the locations of the minutia points. (a) (b) Figure 3: (a) Bifurcation (b) Termination In this paper, our focus aims at accomplishing the fingerprint verification in embedded processors in real time while for supporting other mobile security. As shown in the lower part of Figure 2, the authentication process is made of three steps. capture is basically an I/O process that can be accomplished in real time without difficulty. Minutia matching is point-matching technique. Its implementation is not complicated so that a smart card processor can be programmed to complete the job in real time [6]. The most time consumption processing is the feature extraction step. It also dominates the accuracy and performance of the authentication process. Feature extraction (The direct gray scale approach) [7] can be divided into several parts. They are image enhancement, segmentation, image orientation, core point location and minutia extraction. a) Image enhancement/filtering This part aims at enhancing the image quality before feature extraction. Common techniques like the application of a directional filter [8] or image normalization [9] is often employed. b) Image segmentation and orientation This part computes the orientation of the fingerprint image and identifies the Region of Interest (ROI) [11]. c) Core point location This part locates a core point [10] for fingerprint alignment and matching. It is computed from the orientations of the ridgelines obtained from step (b). d) Minutia extraction This part traces the ridgeline with the helps of orientation information and find out the bifurcation and termination features [14]. In general, the feature extraction process is a n 3 process, assuming that that fingerprint is a n by n image. Steps (a) to (d) involve intensive floating point calculations, especially approximations of trigonometric functions. Filtering can often be discarded in embedded system implementation of fingerprint verification systems. 4. Implementation Like other embedded systems, the design of a fingerprint matching system requires the considerations of cost, development time and runtime performance. Since real time response is the critical factor in this case, we will focus on the searching of an appropriate implementation strategy that can yield such performance. Previously, we had completed the development of a fingerprint verification software on a desktop PC. The 4000 lines program written in C language runs under the Microsoft Windows environment and can gives response in less than 1 second. When the same program was compiled to run in an embedded Linux environment under a PDA which has a 200 MHz StrongArm CPU, the average run time was more than 20 seconds. The obvious critical task is to reduce the program execution time. In this regard, we investigated two approaches to tackle the problem. They are the DSP and SoC approaches. a. The DSP approach As the cost of the embedded fingerprint system should be as low as possible, we decided to conduct our work using a fixed point DSP rather than a floating point DSP [2]. For experiment purpose, we used a development board driven by a 40 MHz16-bit fixed point TI TMSC320C52 DSP with very limited on-chip data RAM and ROM. The TMS320C52 features a 4K*16-bit programmable ROM on-chip, and carries a 1056*16-bit data RAM on-chip. At the same time, the development board supports 32K*16-bit words of external memory. The DSP was connected to an Axis embedded Linux development board equipped with a 100 MHz embedded processor. There are two methods to implement our fingerprint authentication program on the DSP platform: 1) Translate all the C source code to assembly language manually. This method gives a very high performance. But it is a very time consuming process. 2) Translate all the C source code to machine language under TI s C5X Code Composer Compiler [4]. To shorten the integration time, we decide to use the second method. With this approach, we can simulate the interface of software and hardware components in a short period of time. Although we used the Code Composer as our development software, we still had to process certain modifications when integrating to the DSP platform. First of all, the size of the fingerprint image had to be processed had to be reduced to 64*64 pixels because of memory-limitation. Secondly, our original program generated a lot of intermediate data. These data that were previously stored in dynamically allocated memory locations were reallocated to static memory locations since dynamic memory allocation is a very time consumption procedure in DSP processing. Memory consumption is especially severe. Since the DSP and the host embedded processors operate at different speeds, it would not easy for them to share common memory. Moreover,
3 the DSP accesses its built-in memory much faster than external memory. Therefore, fingerprint image data captured from a sensor must be transferred from the embedded processor s memory to the DSP before the DSP can process them. In this way, memory requirement is doubled! We had implemented both floating- and fixed-point versions of fingerprint authentication algorithm on the DSP. Figure 4 shows the number of instructions needed for the DSP to process the algorithm in the experiment. Figure 4: Comparison of number of instruction on TMS320C52 on fixed- and floating-point on fingerprint verification implementation The total number of instructions needed for the fixed-point fingerprint algorithm is about 76 million while floating-point fingerprint algorithm needs about 1000 million because the floating-point instructions are emulations only. The time measurement is about 1.9s and 26.1s on fixed-point and floating-point implementation respectively. Obviously, more time will become necessary to run the fingerprint authentication algorithm when the image size is 256*256. Besides the DSP hardware, the embedded Linux system also contains extra hardware like the sensor, display, etc. The additional hardware connections increase the system complexity and reliability. This arrangement increases the overall cost directly. b. SoC Approach Another approach for embedded fingerprint system is the use of System-on-Chip (SoC). SoC is a new type of hardware architecture with complex hardware that integrates different IP cores together. Besides the core processor is inside a SoC, it is also equipped with hardware controllers for different peripherals such as LCD and input/output device controllers. In fact, a SoC processor is more or less like the generalpurpose processor but without floating point coprocessor because of cost and power consumption consideration. The requirement that all processing is performed on the SoC helps to reduce power consumption, minimize chip areas and simplify the hardware and software development process [3]. The ultimate question is to identify a suitable SoC processor and build an associated system capable of verifying fingerprints in real time. Figure 5 shows the software architecture using the SoC design. Like a regular computer system, it can be divided into three layers, hardware layer, kernel layer and application layer [1]. With this approach, we can develop multiple applications on a single kernel for extensibility of the embedded fingerprint system. Besides, we can maximize the reusability on the software code. Nevertheless, we must verify if the layered approach will bring in an overhead that can delay the system response time. In our experiment, we used the Intel StrongARM (206Mhz) embedded processor with Infineon capacitance fingerprint sensor in our system. The resolution of the sensor is 288x244 pixels with 8-bit gray scale image. Host application GUI Kernel services and device drivers Display services, File system, Event Management, Data I/O Hardware SoC chip, fingerprint sensor, LCD display, input device, ram and flash memory Figure 5: Software architecture on embedded fingerprint system design Linking the host application and hardware is the Application Program Interface (API). We had chosen to use embedded Linux as the operating system because its open source code allows us to customize the software architecture for our system. With the use of Linux kernel, we can standardize the API for device drivers, scheduling and messaging services so as to save a lot of development time and effort. For the application layer, we had to translate the fingerprint algorithm for StrongARM platform. As mentioned before, direct cross-complication of the algorithm is possible but can result in poor runtime performance (>20s in our experiment). Therefore we started to develop a software reengineering process to port the software to its new environment. Basically, the reengineering process is made up of five steps: (a) Whenever possible, replace floating-point data by integers; (b) Replace the remaining floating-point calculations by fixed point calculations; (c) Buffer all reusable complex calculations; (d) Avoid the use of subroutines; (e) Recompile using an optimized compiler. The above procedure appears routine and straightforward. Yet, there are numerous domain specific conversions that must be taken care of. In our case, the precisions of the fixed-point system as well as good approximations of the trigonometric functions were our great concerns [12]. Care was taken to ensure the reengineered software yields similar results as the original software. We estimated the errors by applying the reengineered software to a 300 persons database and analyzed the resultant False Acceptance Rates and False
4 Rejection Rates to make sure that they resembled those of the original software. The 4000 lines of C codes took 2-3 months for reengineering. Ultimately, the verification time was cut to one second or less. For the development cost, porting the embedded Linux OS to StrongARM development board and writing drivers to interface the fingerprint sensors took 2 months to finish. Nevertheless, the experience and the source code are reusable. 5. Mobile Security Many factors, like cost, psychology, number of service providers, etc., contribute to the late coming of mobile commerce activities. Among them, mobile security is an important one. The involvement of the Internet is inevitable in mobile commerce, considering the real life mobile commerce transactions involve business-to-customers, business-tobusiness [13]. Under such a consideration, mobile security can involve several issues: (a) protection against unauthorized users; (2) protection during data transmission; (3) protection of data on lost devices; (3) protection of mobile assets; (5) protection of existing security investment [14]. Several of these issues are covered by choices of the wireless protocols like imode, HDML, WAP 1.1, SAT (SIM Application Toolkit), and/or the service providers. To extend the scope of mobile commerce beyond close systems, commercial mobile commerce solutions must migrate smoothly from symmetric algorithms to algorithms, involving Public Key Infrastructure (PKI), for open system frameworks [15]. The current trend of merging the PDAs and wireless telephones merge call for the use of faster embedded processors, like the ARM9 or the StrongArm processors, to support more features, especially those multimedia ones. In this way, these mobile devices are equipped with the hardware features to verify fingerprints. The next problem is to find a safe place to store the fingerprint features template. In this regard, the SIM card becomes an ideal location. The SIM card, which is a smart card itself, is very secure. In fact, the SIM card stores important secret keys, digital certificates as well. The use of fingerprint to protect the SIM card from mis-use enhances the confidence of the confidence of the wireless telephones users to use the devices for mobile transactions. 6. Conclusions To model the software development cost and time, we employed the Embedded Mode REVIC (Revised Intermediate COCOMO) Model [5], a cost modeling for embedded design system. It models the modern development technology such as re-use driven development, rapid development model, and application composition and generation capability [5]. In brief, the software development effort can be expressed in the following equation. E 15 S = A * B * KSLOC * F (1) E i i = 1 Where S E is the software development effort A is the constant used to compensate the effect of increasing project size E KSLOC is the software size in thousands of source lines of code B is the scale factor accounts for the relative economies or diseconomies of scale Fi is the cost driver (multiplier) representing such project attributes like time constraints, reliability, software tools and application experience. Optimization in DSP development process requires extensive programming experience in the operation of the DSP. This increases the cost driver F i value in equation (1) and the development effort. When we switch to another type of DSP, utilization of the developed DSP code is very low because the algorithm for DSP is usually hardware dependent. From the result, we conclude that the use of SoC is suitable for embedded fingerprint system development. It allows easy control of the peripherals and fast software reengineering time. This can achieve a fast development. Also, the simplicity of the hardware also enables manufacturers to embed fingerprint authentication systems in the future intelligent devices with low costs. References [1] Chang, H.; Cooke; L.; Hunt, M.; Grant. M.; McNelly, A.; Todd, L., Surviving the SOC Revolution, A Guide to Platform-Based Design, Kluwer Academic Publishers, 1999, pp [2] Eyer, J., The Digital Signal Processor Derby, Berkeley Design Technology Inc. IEEE Spectrum, Jun. 2001, pp [3] Rolf, E., Embedded System Architectures, NATO Science Series: Applied Sciences, volume 357 of System-Level Synthesis, pages Il Ciocco, August [4] Pandey, R, Advances in DSP Development Environments, ELECTRO '96. Professional Program. Proceedings, 1996, pp [5] Devnani-Chulani, S.; Clark, B.; Boehm, B., Calibration Approach and Results of the COCOMO II Post- Architecture Model, Center for Software Engineering, University of Southern California [6] Ho, H.C.; Moon, Y.S.; Ng, K.L.; Wan, S.F.; Wong, Collaborative fingerprint authentication by smart card and a trusted host, Electrical and Computer Engineering, 2000 Canadian Conference on, Volume: 1, 2000 Page(s): vol.1 [7] Maio, D.; Maltoni, D., Direct gray-scale minutiae detection in fingerprints, Pattern Analysis and Machine Intelligence, IEEE Transactions on,volume: 19 Issue: 1, Jan 1997 Page(s): 27 40
5 [8] Kamei, T.; Mizoguchi, M., Image filter design for fingerprint enhancement, Computer Vision, Proceedings., International Symposium on, Nov 1995 Page(s): [9] Jain, A.; Lin Hong; Yifei Wan, image enhancement: algorithm and performance evaluation, Pattern Analysis and Machine Intelligence, IEEE Transactions on, Volume: 20 Issue: 8, Aug 1998 Page(s): [10] Asker M. Bazen and Sabih H. Gerez, Extraction of Singular Points from Directional Fields of s, Mobile Communications in Perspective, Annual CTIT Workshop, Enschede, The Netherlands, February 2001 [11] Jain, A.; Lin Hong; Bolle, R., On-line fingerprint verification, Pattern Analysis and Machine Intelligence, IEEE Transactions on, Volume: 19 Issue: 4, April 1997 Page(s): [12] Moon, Y.S.; Luk, T.C.; Tang, T.Y.; Chan, K.C.; The fixed-point implementation of fingerprint minutiae extraction algorithm, manuscript in preparation.. [13] A Definition of Mobile Commerce in M-Commerce Security, Education/Coursework/Mobile_Security_Paper.htm#_To c [14] Neudoerffer, D., 5 Steps to Secure Mobile Data, s ,00.html [15] Mobile Commerce Security: Essential and Analysis, Gemplus, /tech/Gemplus.pdf
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
Embedded Software development Process and Tools: Lesson-4 Linking and Locating Software
 Embedded Software development Process and Tools: Lesson-4 Linking and Locating Software 1 1. Linker 2 Linker Links the compiled codes of application software, object codes from library and OS kernel functions.
Embedded Software development Process and Tools: Lesson-4 Linking and Locating Software 1 1. Linker 2 Linker Links the compiled codes of application software, object codes from library and OS kernel functions.
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Computer and Set of Robots
 Lesson 11:DESIGN PROCESS EXAMPLES Mobile-Phone, Mobile- Computer and Set of Robots 1 Mobile Phone 2 Mobile phone SoC (System-on-Chip) Hardware units Microcontroller or ASIP (Application Specific Instruction
Lesson 11:DESIGN PROCESS EXAMPLES Mobile-Phone, Mobile- Computer and Set of Robots 1 Mobile Phone 2 Mobile phone SoC (System-on-Chip) Hardware units Microcontroller or ASIP (Application Specific Instruction
EEM870 Embedded System and Experiment Lecture 1: SoC Design Overview
 EEM870 Embedded System and Experiment Lecture 1: SoC Design Overview Wen-Yen Lin, Ph.D. Department of Electrical Engineering Chang Gung University Email: [email protected] Feb. 2013 Course Overview
EEM870 Embedded System and Experiment Lecture 1: SoC Design Overview Wen-Yen Lin, Ph.D. Department of Electrical Engineering Chang Gung University Email: [email protected] Feb. 2013 Course Overview
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM
 ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM 1 The ARM architecture processors popular in Mobile phone systems 2 ARM Features ARM has 32-bit architecture but supports 16 bit
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM 1 The ARM architecture processors popular in Mobile phone systems 2 ARM Features ARM has 32-bit architecture but supports 16 bit
Fastboot Techniques for x86 Architectures. Marcus Bortel Field Application Engineer QNX Software Systems
 Fastboot Techniques for x86 Architectures Marcus Bortel Field Application Engineer QNX Software Systems Agenda Introduction BIOS and BIOS boot time Fastboot versus BIOS? Fastboot time Customizing the boot
Fastboot Techniques for x86 Architectures Marcus Bortel Field Application Engineer QNX Software Systems Agenda Introduction BIOS and BIOS boot time Fastboot versus BIOS? Fastboot time Customizing the boot
ARM7 Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology
 ARM7 Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Khatmode Ranjit P 1, Kulkarni Ramchandra V 2, Ghodke Bharat S 3, Prof. P. P. Chitte 4, Prof. Anap S. D 5 1 Student
ARM7 Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Khatmode Ranjit P 1, Kulkarni Ramchandra V 2, Ghodke Bharat S 3, Prof. P. P. Chitte 4, Prof. Anap S. D 5 1 Student
CS 3530 Operating Systems. L02 OS Intro Part 1 Dr. Ken Hoganson
 CS 3530 Operating Systems L02 OS Intro Part 1 Dr. Ken Hoganson Chapter 1 Basic Concepts of Operating Systems Computer Systems A computer system consists of two basic types of components: Hardware components,
CS 3530 Operating Systems L02 OS Intro Part 1 Dr. Ken Hoganson Chapter 1 Basic Concepts of Operating Systems Computer Systems A computer system consists of two basic types of components: Hardware components,
ESE566 REPORT3. Design Methodologies for Core-based System-on-Chip HUA TANG OVIDIU CARNU
 ESE566 REPORT3 Design Methodologies for Core-based System-on-Chip HUA TANG OVIDIU CARNU Nov 19th, 2002 ABSTRACT: In this report, we discuss several recent published papers on design methodologies of core-based
ESE566 REPORT3 Design Methodologies for Core-based System-on-Chip HUA TANG OVIDIU CARNU Nov 19th, 2002 ABSTRACT: In this report, we discuss several recent published papers on design methodologies of core-based
Biometrics in Physical Access Control Issues, Status and Trends White Paper
 Biometrics in Physical Access Control Issues, Status and Trends White Paper Authored and Presented by: Bill Spence, Recognition Systems, Inc. SIA Biometrics Industry Group Vice-Chair & SIA Biometrics Industry
Biometrics in Physical Access Control Issues, Status and Trends White Paper Authored and Presented by: Bill Spence, Recognition Systems, Inc. SIA Biometrics Industry Group Vice-Chair & SIA Biometrics Industry
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines
 Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada [email protected] Micaela Serra
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada [email protected] Micaela Serra
Designing and Embodiment of Software that Creates Middle Ware for Resource Management in Embedded System
 , pp.97-108 http://dx.doi.org/10.14257/ijseia.2014.8.6.08 Designing and Embodiment of Software that Creates Middle Ware for Resource Management in Embedded System Suk Hwan Moon and Cheol sick Lee Department
, pp.97-108 http://dx.doi.org/10.14257/ijseia.2014.8.6.08 Designing and Embodiment of Software that Creates Middle Ware for Resource Management in Embedded System Suk Hwan Moon and Cheol sick Lee Department
The Development of a Pressure-based Typing Biometrics User Authentication System
 The Development of a Pressure-based Typing Biometrics User Authentication System Chen Change Loy Adv. Informatics Research Group MIMOS Berhad by Assoc. Prof. Dr. Chee Peng Lim Associate Professor Sch.
The Development of a Pressure-based Typing Biometrics User Authentication System Chen Change Loy Adv. Informatics Research Group MIMOS Berhad by Assoc. Prof. Dr. Chee Peng Lim Associate Professor Sch.
Pre-tested System-on-Chip Design. Accelerates PLD Development
 Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Networking Remote-Controlled Moving Image Monitoring System
 Networking Remote-Controlled Moving Image Monitoring System First Prize Networking Remote-Controlled Moving Image Monitoring System Institution: Participants: Instructor: National Chung Hsing University
Networking Remote-Controlled Moving Image Monitoring System First Prize Networking Remote-Controlled Moving Image Monitoring System Institution: Participants: Instructor: National Chung Hsing University
A Generic Network Interface Architecture for a Networked Processor Array (NePA)
 A Generic Network Interface Architecture for a Networked Processor Array (NePA) Seung Eun Lee, Jun Ho Bahn, Yoon Seok Yang, and Nader Bagherzadeh EECS @ University of California, Irvine Outline Introduction
A Generic Network Interface Architecture for a Networked Processor Array (NePA) Seung Eun Lee, Jun Ho Bahn, Yoon Seok Yang, and Nader Bagherzadeh EECS @ University of California, Irvine Outline Introduction
Keywords: fingerprints, attendance, enrollment, authentication, identification
 Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com 94 POS Terminal
Volume 4, Issue 11, November 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com 94 POS Terminal
Implementation of Wireless Gateway for Smart Home
 Communications and Network, 2013, 5, 16-20 doi:10.4236/cn.2013.51b005 Published Online February 2013 (http://www.scirp.org/journal/cn) Implementation of Wireless Gateway for Smart Home Yepeng Ni 1, Fang
Communications and Network, 2013, 5, 16-20 doi:10.4236/cn.2013.51b005 Published Online February 2013 (http://www.scirp.org/journal/cn) Implementation of Wireless Gateway for Smart Home Yepeng Ni 1, Fang
4.1 Threads in the Server System
 Software Architecture of GG1 A Mobile Phone Based Multimedia Remote Monitoring System Y. S. Moon W. S. Wong H. C. Ho Kenneth Wong Dept of Computer Science & Engineering Dept of Engineering Chinese University
Software Architecture of GG1 A Mobile Phone Based Multimedia Remote Monitoring System Y. S. Moon W. S. Wong H. C. Ho Kenneth Wong Dept of Computer Science & Engineering Dept of Engineering Chinese University
CprE 588 Embedded Computer Systems Homework #1 Assigned: February 5 Due: February 15
 CprE 588 Embedded Computer Systems Homework #1 Assigned: February 5 Due: February 15 Directions: Please submit this assignment by the due date via WebCT. Submissions should be in the form of 1) a PDF file
CprE 588 Embedded Computer Systems Homework #1 Assigned: February 5 Due: February 15 Directions: Please submit this assignment by the due date via WebCT. Submissions should be in the form of 1) a PDF file
Special FEATURE. By Heinrich Munz
 Special FEATURE By Heinrich Munz Heinrich Munz of KUKA Roboter discusses in this article how to bring Microsoft Windows CE and WindowsXP together on the same PC. He discusses system and application requirements,
Special FEATURE By Heinrich Munz Heinrich Munz of KUKA Roboter discusses in this article how to bring Microsoft Windows CE and WindowsXP together on the same PC. He discusses system and application requirements,
ELEC 5260/6260/6266 Embedded Computing Systems
 ELEC 5260/6260/6266 Embedded Computing Systems Spring 2016 Victor P. Nelson Text: Computers as Components, 3 rd Edition Prof. Marilyn Wolf (Georgia Tech) Course Topics Embedded system design & modeling
ELEC 5260/6260/6266 Embedded Computing Systems Spring 2016 Victor P. Nelson Text: Computers as Components, 3 rd Edition Prof. Marilyn Wolf (Georgia Tech) Course Topics Embedded system design & modeling
High Performance or Cycle Accuracy?
 CHIP DESIGN High Performance or Cycle Accuracy? You can have both! Bill Neifert, Carbon Design Systems Rob Kaye, ARM ATC-100 AGENDA Modelling 101 & Programmer s View (PV) Models Cycle Accurate Models Bringing
CHIP DESIGN High Performance or Cycle Accuracy? You can have both! Bill Neifert, Carbon Design Systems Rob Kaye, ARM ATC-100 AGENDA Modelling 101 & Programmer s View (PV) Models Cycle Accurate Models Bringing
OMAP platform security features
 SWPT008 - July 2003 White Paper OMAP platform security features By Harini Sundaresan Applications Engineer, OMAP Security Texas Instruments, Wireless Terminal Business Unit This white paper introduces
SWPT008 - July 2003 White Paper OMAP platform security features By Harini Sundaresan Applications Engineer, OMAP Security Texas Instruments, Wireless Terminal Business Unit This white paper introduces
Microcontroller Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology
 Microcontroller Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Bharath K M, Rohit C V Student of B.E Electronics and Communication Coorg Institute of Technology,
Microcontroller Based Smart ATM Access & Security System Using Fingerprint Recognition & GSM Technology Bharath K M, Rohit C V Student of B.E Electronics and Communication Coorg Institute of Technology,
Enery Efficient Dynamic Memory Bank and NV Swap Device Management
 Enery Efficient Dynamic Memory Bank and NV Swap Device Management Kwangyoon Lee and Bumyong Choi Department of Computer Science and Engineering University of California, San Diego {kwl002,buchoi}@cs.ucsd.edu
Enery Efficient Dynamic Memory Bank and NV Swap Device Management Kwangyoon Lee and Bumyong Choi Department of Computer Science and Engineering University of California, San Diego {kwl002,buchoi}@cs.ucsd.edu
Freescale Semiconductor, I
 nc. Application Note 6/2002 8-Bit Software Development Kit By Jiri Ryba Introduction 8-Bit SDK Overview This application note describes the features and advantages of the 8-bit SDK (software development
nc. Application Note 6/2002 8-Bit Software Development Kit By Jiri Ryba Introduction 8-Bit SDK Overview This application note describes the features and advantages of the 8-bit SDK (software development
Embedded Systems on ARM Cortex-M3 (4weeks/45hrs)
 Embedded Systems on ARM Cortex-M3 (4weeks/45hrs) Course & Kit Contents LEARN HOW TO: Use of Keil Real View for ARM Use ARM Cortex-M3 MCU for professional embedded application development Understanding
Embedded Systems on ARM Cortex-M3 (4weeks/45hrs) Course & Kit Contents LEARN HOW TO: Use of Keil Real View for ARM Use ARM Cortex-M3 MCU for professional embedded application development Understanding
Stream Processing on GPUs Using Distributed Multimedia Middleware
 Stream Processing on GPUs Using Distributed Multimedia Middleware Michael Repplinger 1,2, and Philipp Slusallek 1,2 1 Computer Graphics Lab, Saarland University, Saarbrücken, Germany 2 German Research
Stream Processing on GPUs Using Distributed Multimedia Middleware Michael Repplinger 1,2, and Philipp Slusallek 1,2 1 Computer Graphics Lab, Saarland University, Saarbrücken, Germany 2 German Research
NIOS II Based Embedded Web Server Development for Networking Applications
 NIOS II Based Embedded Web Server Development for Networking Applications 1 Sheetal Bhoyar, 2 Dr. D. V. Padole 1 Research Scholar, G. H. Raisoni College of Engineering, Nagpur, India 2 Professor, G. H.
NIOS II Based Embedded Web Server Development for Networking Applications 1 Sheetal Bhoyar, 2 Dr. D. V. Padole 1 Research Scholar, G. H. Raisoni College of Engineering, Nagpur, India 2 Professor, G. H.
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
22 nd NISS Conference
 22 nd NISS Conference Submission: Topic: Keywords: Author: Organization: Tutorial BIOMETRICS - DEVELOPING THE ARCHITECTURE, API, ENCRYPTION AND SECURITY. INSTALLING & INTEGRATING BIOMETRIC SYSTEMS INTO
22 nd NISS Conference Submission: Topic: Keywords: Author: Organization: Tutorial BIOMETRICS - DEVELOPING THE ARCHITECTURE, API, ENCRYPTION AND SECURITY. INSTALLING & INTEGRATING BIOMETRIC SYSTEMS INTO
Mobile Processors: Future Trends
 Mobile Processors: Future Trends Mário André Pinto Ferreira de Araújo Departamento de Informática, Universidade do Minho 4710-057 Braga, Portugal [email protected] Abstract. Mobile devices, such as handhelds,
Mobile Processors: Future Trends Mário André Pinto Ferreira de Araújo Departamento de Informática, Universidade do Minho 4710-057 Braga, Portugal [email protected] Abstract. Mobile devices, such as handhelds,
Development of Attendance Management System using Biometrics.
 Development of Attendance Management System using Biometrics. O. Shoewu, Ph.D. 1,2* and O.A. Idowu, B.Sc. 1 1 Department of Electronic and Computer Engineering, Lagos State University, Epe Campus, Nigeria.
Development of Attendance Management System using Biometrics. O. Shoewu, Ph.D. 1,2* and O.A. Idowu, B.Sc. 1 1 Department of Electronic and Computer Engineering, Lagos State University, Epe Campus, Nigeria.
M-Shield mobile security technology
 Technology for Innovators TM M-Shield mobile security technology making wireless secure Overview As 3G networks are successfully deployed worldwide, opportunities are arising to deliver to end-users a
Technology for Innovators TM M-Shield mobile security technology making wireless secure Overview As 3G networks are successfully deployed worldwide, opportunities are arising to deliver to end-users a
NanopowerCommunications: Enabling the Internet of Things OBJECTS TALK
 NanopowerCommunications: Enabling the Internet of Things OBJECTS TALK When objects can both sense the environment and communicate, they become tools for understanding complexity and responding to it swiftly.
NanopowerCommunications: Enabling the Internet of Things OBJECTS TALK When objects can both sense the environment and communicate, they become tools for understanding complexity and responding to it swiftly.
Lesson 10:DESIGN PROCESS EXAMPLES Automatic Chocolate vending machine, smart card and digital camera
 Lesson 10:DESIGN PROCESS EXAMPLES Automatic Chocolate vending machine, smart card and digital camera 1 Automatic Chocolate Vending Machine (ACVM) 2 Diagrammatic representation of ACVM Keypad for user Interface
Lesson 10:DESIGN PROCESS EXAMPLES Automatic Chocolate vending machine, smart card and digital camera 1 Automatic Chocolate Vending Machine (ACVM) 2 Diagrammatic representation of ACVM Keypad for user Interface
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy
 Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Embedded Systems. introduction. Jan Madsen
 Embedded Systems introduction Jan Madsen Informatics and Mathematical Modeling Technical University of Denmark Richard Petersens Plads, Building 321 DK2800 Lyngby, Denmark [email protected] Wireless Sensor
Embedded Systems introduction Jan Madsen Informatics and Mathematical Modeling Technical University of Denmark Richard Petersens Plads, Building 321 DK2800 Lyngby, Denmark [email protected] Wireless Sensor
A General Framework for Tracking Objects in a Multi-Camera Environment
 A General Framework for Tracking Objects in a Multi-Camera Environment Karlene Nguyen, Gavin Yeung, Soheil Ghiasi, Majid Sarrafzadeh {karlene, gavin, soheil, majid}@cs.ucla.edu Abstract We present a framework
A General Framework for Tracking Objects in a Multi-Camera Environment Karlene Nguyen, Gavin Yeung, Soheil Ghiasi, Majid Sarrafzadeh {karlene, gavin, soheil, majid}@cs.ucla.edu Abstract We present a framework
Embedded and mobile fingerprint. technology. FingerCell EDK
 Embedded and mobile fingerprint identification technology FingerCell EDK FingerCell EDK Embedded and mobile fingerprint identification technology Document updated on August 30, 2010 CONTENTS FingerCell Algorithm
Embedded and mobile fingerprint identification technology FingerCell EDK FingerCell EDK Embedded and mobile fingerprint identification technology Document updated on August 30, 2010 CONTENTS FingerCell Algorithm
4. H.323 Components. VOIP, Version 1.6e T.O.P. BusinessInteractive GmbH Page 1 of 19
 4. H.323 Components VOIP, Version 1.6e T.O.P. BusinessInteractive GmbH Page 1 of 19 4.1 H.323 Terminals (1/2)...3 4.1 H.323 Terminals (2/2)...4 4.1.1 The software IP phone (1/2)...5 4.1.1 The software
4. H.323 Components VOIP, Version 1.6e T.O.P. BusinessInteractive GmbH Page 1 of 19 4.1 H.323 Terminals (1/2)...3 4.1 H.323 Terminals (2/2)...4 4.1.1 The software IP phone (1/2)...5 4.1.1 The software
On Demand Loading of Code in MMUless Embedded System
 On Demand Loading of Code in MMUless Embedded System Sunil R Gandhi *. Chetan D Pachange, Jr.** Mandar R Vaidya***, Swapnilkumar S Khorate**** *Pune Institute of Computer Technology, Pune INDIA (Mob- 8600867094;
On Demand Loading of Code in MMUless Embedded System Sunil R Gandhi *. Chetan D Pachange, Jr.** Mandar R Vaidya***, Swapnilkumar S Khorate**** *Pune Institute of Computer Technology, Pune INDIA (Mob- 8600867094;
Robot Task-Level Programming Language and Simulation
 Robot Task-Level Programming Language and Simulation M. Samaka Abstract This paper presents the development of a software application for Off-line robot task programming and simulation. Such application
Robot Task-Level Programming Language and Simulation M. Samaka Abstract This paper presents the development of a software application for Off-line robot task programming and simulation. Such application
DS1104 R&D Controller Board
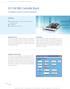 DS1104 R&D Controller Board Cost-effective system for controller development Highlights Single-board system with real-time hardware and comprehensive I/O Cost-effective PCI hardware for use in PCs Application
DS1104 R&D Controller Board Cost-effective system for controller development Highlights Single-board system with real-time hardware and comprehensive I/O Cost-effective PCI hardware for use in PCs Application
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
TCP/IP Jumbo Frames Network Performance Evaluation on A Testbed Infrastructure
 I.J. Wireless and Microwave Technologies, 2012, 6, 29-36 Published Online December 2012 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.2012.06.05 Available online at http://www.mecs-press.net/ijwmt
I.J. Wireless and Microwave Technologies, 2012, 6, 29-36 Published Online December 2012 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijwmt.2012.06.05 Available online at http://www.mecs-press.net/ijwmt
Computer Architecture. Secure communication and encryption.
 Computer Architecture. Secure communication and encryption. Eugeniy E. Mikhailov The College of William & Mary Lecture 28 Eugeniy Mikhailov (W&M) Practical Computing Lecture 28 1 / 13 Computer architecture
Computer Architecture. Secure communication and encryption. Eugeniy E. Mikhailov The College of William & Mary Lecture 28 Eugeniy Mikhailov (W&M) Practical Computing Lecture 28 1 / 13 Computer architecture
what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored?
 Inside the CPU how does the CPU work? what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored? some short, boring programs to illustrate the
Inside the CPU how does the CPU work? what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored? some short, boring programs to illustrate the
Wireless Microcontrollers for Environment Management, Asset Tracking and Consumer. October 2009
 Wireless Microcontrollers for Environment Management, Asset Tracking and Consumer October 2009 Jennic highlights Jennic is a fabless semiconductor company providing Wireless Microcontrollers to high-growth
Wireless Microcontrollers for Environment Management, Asset Tracking and Consumer October 2009 Jennic highlights Jennic is a fabless semiconductor company providing Wireless Microcontrollers to high-growth
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
evm Virtualization Platform for Windows
 B A C K G R O U N D E R evm Virtualization Platform for Windows Host your Embedded OS and Windows on a Single Hardware Platform using Intel Virtualization Technology April, 2008 TenAsys Corporation 1400
B A C K G R O U N D E R evm Virtualization Platform for Windows Host your Embedded OS and Windows on a Single Hardware Platform using Intel Virtualization Technology April, 2008 TenAsys Corporation 1400
CSE 237A Final Project Final Report
 CSE 237A Final Project Final Report Multi-way video conferencing system over 802.11 wireless network Motivation Yanhua Mao and Shan Yan The latest technology trends in personal mobile computing are towards
CSE 237A Final Project Final Report Multi-way video conferencing system over 802.11 wireless network Motivation Yanhua Mao and Shan Yan The latest technology trends in personal mobile computing are towards
DsPIC HOW-TO GUIDE Creating & Debugging a Project in MPLAB
 DsPIC HOW-TO GUIDE Creating & Debugging a Project in MPLAB Contents at a Glance 1. Introduction of MPLAB... 4 2. Development Tools... 5 3. Getting Started... 6 3.1. Create a Project... 8 3.2. Start MPLAB...
DsPIC HOW-TO GUIDE Creating & Debugging a Project in MPLAB Contents at a Glance 1. Introduction of MPLAB... 4 2. Development Tools... 5 3. Getting Started... 6 3.1. Create a Project... 8 3.2. Start MPLAB...
Automated Profile Vehicle Using GSM Modem, GPS and Media Processor DM642
 2009 International Conference on Computer Engineering and Applications IPCSIT vol.2 (2011) (2011) IACSIT Press, Singapore Automated Profile Vehicle Using GSM Modem, GPS and Media Processor DM642 Muhammad
2009 International Conference on Computer Engineering and Applications IPCSIT vol.2 (2011) (2011) IACSIT Press, Singapore Automated Profile Vehicle Using GSM Modem, GPS and Media Processor DM642 Muhammad
12. Introduction to Virtual Machines
 12. Introduction to Virtual Machines 12. Introduction to Virtual Machines Modern Applications Challenges of Virtual Machine Monitors Historical Perspective Classification 332 / 352 12. Introduction to
12. Introduction to Virtual Machines 12. Introduction to Virtual Machines Modern Applications Challenges of Virtual Machine Monitors Historical Perspective Classification 332 / 352 12. Introduction to
A Computer Vision System on a Chip: a case study from the automotive domain
 A Computer Vision System on a Chip: a case study from the automotive domain Gideon P. Stein Elchanan Rushinek Gaby Hayun Amnon Shashua Mobileye Vision Technologies Ltd. Hebrew University Jerusalem, Israel
A Computer Vision System on a Chip: a case study from the automotive domain Gideon P. Stein Elchanan Rushinek Gaby Hayun Amnon Shashua Mobileye Vision Technologies Ltd. Hebrew University Jerusalem, Israel
ONLINE HEALTH MONITORING SYSTEM USING ZIGBEE
 ONLINE HEALTH MONITORING SYSTEM USING ZIGBEE S.Josephine Selvarani ECE Department, Karunya University, Coimbatore. Abstract - An on-line health monitoring of physiological signals of humans such as temperature
ONLINE HEALTH MONITORING SYSTEM USING ZIGBEE S.Josephine Selvarani ECE Department, Karunya University, Coimbatore. Abstract - An on-line health monitoring of physiological signals of humans such as temperature
Study and installation of a VOIP service on ipaq in Linux environment
 Study and installation of a VOIP service on ipaq in Linux environment Volkan Altuntas Chaba Ballo Olivier Dole Jean-Romain Gotteland ENSEIRB 2002 Summary 1. Introduction 2. Presentation a. ipaq s characteristics
Study and installation of a VOIP service on ipaq in Linux environment Volkan Altuntas Chaba Ballo Olivier Dole Jean-Romain Gotteland ENSEIRB 2002 Summary 1. Introduction 2. Presentation a. ipaq s characteristics
Which ARM Cortex Core Is Right for Your Application: A, R or M?
 Which ARM Cortex Core Is Right for Your Application: A, R or M? Introduction The ARM Cortex series of cores encompasses a very wide range of scalable performance options offering designers a great deal
Which ARM Cortex Core Is Right for Your Application: A, R or M? Introduction The ARM Cortex series of cores encompasses a very wide range of scalable performance options offering designers a great deal
Fachbereich Informatik und Elektrotechnik SunSPOT. Ubiquitous Computing. Ubiquitous Computing, Helmut Dispert
 Ubiquitous Computing Ubiquitous Computing The Sensor Network System Sun SPOT: The Sun Small Programmable Object Technology Technology-Based Wireless Sensor Networks a Java Platform for Developing Applications
Ubiquitous Computing Ubiquitous Computing The Sensor Network System Sun SPOT: The Sun Small Programmable Object Technology Technology-Based Wireless Sensor Networks a Java Platform for Developing Applications
İSTANBUL AYDIN UNIVERSITY
 İSTANBUL AYDIN UNIVERSITY FACULTY OF ENGİNEERİNG SOFTWARE ENGINEERING THE PROJECT OF THE INSTRUCTION SET COMPUTER ORGANIZATION GÖZDE ARAS B1205.090015 Instructor: Prof. Dr. HASAN HÜSEYİN BALIK DECEMBER
İSTANBUL AYDIN UNIVERSITY FACULTY OF ENGİNEERİNG SOFTWARE ENGINEERING THE PROJECT OF THE INSTRUCTION SET COMPUTER ORGANIZATION GÖZDE ARAS B1205.090015 Instructor: Prof. Dr. HASAN HÜSEYİN BALIK DECEMBER
Smart Cards a(s) Safety Critical Systems
 Smart Cards a(s) Safety Critical Systems Gemplus Labs Pierre.Paradinas [email protected] Agenda Smart Card Technologies Java Card TM Smart Card a specific domain Card Life cycle Our Technical and Business
Smart Cards a(s) Safety Critical Systems Gemplus Labs Pierre.Paradinas [email protected] Agenda Smart Card Technologies Java Card TM Smart Card a specific domain Card Life cycle Our Technical and Business
Computer Automation Techniques. Arthur Carroll
 Computer Automation Techniques Arthur Carroll 1 Three Types of Computers Micro-Controller Single Board Computer Desktop Computer 2 The Micro-Controller Small inexpensive DIP or surface mount chips Roughly
Computer Automation Techniques Arthur Carroll 1 Three Types of Computers Micro-Controller Single Board Computer Desktop Computer 2 The Micro-Controller Small inexpensive DIP or surface mount chips Roughly
Basler. Line Scan Cameras
 Basler Line Scan Cameras High-quality line scan technology meets a cost-effective GigE interface Real color support in a compact housing size Shading correction compensates for difficult lighting conditions
Basler Line Scan Cameras High-quality line scan technology meets a cost-effective GigE interface Real color support in a compact housing size Shading correction compensates for difficult lighting conditions
Accelerate Cloud Computing with the Xilinx Zynq SoC
 X C E L L E N C E I N N E W A P P L I C AT I O N S Accelerate Cloud Computing with the Xilinx Zynq SoC A novel reconfigurable hardware accelerator speeds the processing of applications based on the MapReduce
X C E L L E N C E I N N E W A P P L I C AT I O N S Accelerate Cloud Computing with the Xilinx Zynq SoC A novel reconfigurable hardware accelerator speeds the processing of applications based on the MapReduce
Fingerprint Based Biometric Attendance System
 Fingerprint Based Biometric Attendance System Team Members Vaibhav Shukla Ali Kazmi Amit Waghmare Ravi Ranka Email Id [email protected] [email protected] Contact Numbers 8097031667 9167689265
Fingerprint Based Biometric Attendance System Team Members Vaibhav Shukla Ali Kazmi Amit Waghmare Ravi Ranka Email Id [email protected] [email protected] Contact Numbers 8097031667 9167689265
Figure 1.Block diagram of inventory management system using Proximity sensors.
 Volume 1, Special Issue, March 2015 Impact Factor: 1036, Science Central Value: 2654 Inventory Management System Using Proximity ensors 1)Jyoti KMuluk 2)Pallavi H Shinde3) Shashank VShinde 4)Prof VRYadav
Volume 1, Special Issue, March 2015 Impact Factor: 1036, Science Central Value: 2654 Inventory Management System Using Proximity ensors 1)Jyoti KMuluk 2)Pallavi H Shinde3) Shashank VShinde 4)Prof VRYadav
Operating Systems 4 th Class
 Operating Systems 4 th Class Lecture 1 Operating Systems Operating systems are essential part of any computer system. Therefore, a course in operating systems is an essential part of any computer science
Operating Systems 4 th Class Lecture 1 Operating Systems Operating systems are essential part of any computer system. Therefore, a course in operating systems is an essential part of any computer science
Current and Future Trends in Medical Electronics
 Current and Future Trends in Medical Electronics By Steven Dean, Medical Marketing Director, Texas Instruments www.arrownac.com 800.833.3557 Current and Future Trends in Medical Electronics By Steven Dean,
Current and Future Trends in Medical Electronics By Steven Dean, Medical Marketing Director, Texas Instruments www.arrownac.com 800.833.3557 Current and Future Trends in Medical Electronics By Steven Dean,
Mobile Devices and Systems Lesson 02 Handheld Pocket Computers and Mobile System Operating Systems
 Mobile Devices and Systems Lesson 02 Handheld Pocket Computers and Mobile System Operating Systems Oxford University Press 2007. All rights reserved. 1 Handheld Pocket Computers Come in many manifestations
Mobile Devices and Systems Lesson 02 Handheld Pocket Computers and Mobile System Operating Systems Oxford University Press 2007. All rights reserved. 1 Handheld Pocket Computers Come in many manifestations
Chapter 1 Computer System Overview
 Operating Systems: Internals and Design Principles Chapter 1 Computer System Overview Eighth Edition By William Stallings Operating System Exploits the hardware resources of one or more processors Provides
Operating Systems: Internals and Design Principles Chapter 1 Computer System Overview Eighth Edition By William Stallings Operating System Exploits the hardware resources of one or more processors Provides
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Notes and terms of conditions. Vendor shall note the following terms and conditions/ information before they submit their quote.
 Specifications for ARINC 653 compliant RTOS & Development Environment Notes and terms of conditions Vendor shall note the following terms and conditions/ information before they submit their quote. 1.
Specifications for ARINC 653 compliant RTOS & Development Environment Notes and terms of conditions Vendor shall note the following terms and conditions/ information before they submit their quote. 1.
Windows Embedded Security and Surveillance Solutions
 Windows Embedded Security and Surveillance Solutions Windows Embedded 2010 Page 1 Copyright The information contained in this document represents the current view of Microsoft Corporation on the issues
Windows Embedded Security and Surveillance Solutions Windows Embedded 2010 Page 1 Copyright The information contained in this document represents the current view of Microsoft Corporation on the issues
AN EVALUATION OF MODEL-BASED SOFTWARE SYNTHESIS FROM SIMULINK MODELS FOR EMBEDDED VIDEO APPLICATIONS
 International Journal of Software Engineering and Knowledge Engineering World Scientific Publishing Company AN EVALUATION OF MODEL-BASED SOFTWARE SYNTHESIS FROM SIMULINK MODELS FOR EMBEDDED VIDEO APPLICATIONS
International Journal of Software Engineering and Knowledge Engineering World Scientific Publishing Company AN EVALUATION OF MODEL-BASED SOFTWARE SYNTHESIS FROM SIMULINK MODELS FOR EMBEDDED VIDEO APPLICATIONS
System-on-a-Chip with Security Modules for Network Home Electric Appliances
 System-on-a-Chip with Security Modules for Network Home Electric Appliances V Hiroyuki Fujiyama (Manuscript received November 29, 2005) Home electric appliances connected to the Internet and other networks
System-on-a-Chip with Security Modules for Network Home Electric Appliances V Hiroyuki Fujiyama (Manuscript received November 29, 2005) Home electric appliances connected to the Internet and other networks
Conclusion and Future Directions
 Chapter 9 Conclusion and Future Directions The success of e-commerce and e-business applications depends upon the trusted users. Masqueraders use their intelligence to challenge the security during transaction
Chapter 9 Conclusion and Future Directions The success of e-commerce and e-business applications depends upon the trusted users. Masqueraders use their intelligence to challenge the security during transaction
Mobile Operating Systems Lesson 03 PalmOS Part 1
 Mobile Operating Systems Lesson 03 PalmOS Part 1 Oxford University Press 2007. All rights reserved. 1 PalmOS An OS for handheld devices Designed for highly efficient running of small productivity programs
Mobile Operating Systems Lesson 03 PalmOS Part 1 Oxford University Press 2007. All rights reserved. 1 PalmOS An OS for handheld devices Designed for highly efficient running of small productivity programs
Performance of Host Identity Protocol on Nokia Internet Tablet
 Performance of Host Identity Protocol on Nokia Internet Tablet Andrey Khurri Helsinki Institute for Information Technology HIP Research Group IETF 68 Prague March 23, 2007
Performance of Host Identity Protocol on Nokia Internet Tablet Andrey Khurri Helsinki Institute for Information Technology HIP Research Group IETF 68 Prague March 23, 2007
Modular Communication Infrastructure Design with Quality of Service
 Modular Communication Infrastructure Design with Quality of Service Pawel Wojciechowski and Péter Urbán Distributed Systems Laboratory School of Computer and Communication Sciences Swiss Federal Institute
Modular Communication Infrastructure Design with Quality of Service Pawel Wojciechowski and Péter Urbán Distributed Systems Laboratory School of Computer and Communication Sciences Swiss Federal Institute
M85 OpenCPU Solution Presentation
 M85 OpenCPU Solution Presentation 2013/09/22 Wireless Solutions Co., Ltd. All rights reserved OUTLINE OpenCPU Summary Advantages Software Architecture What s New? Open Resources Development Requirements
M85 OpenCPU Solution Presentation 2013/09/22 Wireless Solutions Co., Ltd. All rights reserved OUTLINE OpenCPU Summary Advantages Software Architecture What s New? Open Resources Development Requirements
Hardware/Software Co-Design of a Java Virtual Machine
 Hardware/Software Co-Design of a Java Virtual Machine Kenneth B. Kent University of Victoria Dept. of Computer Science Victoria, British Columbia, Canada [email protected] Micaela Serra University of Victoria
Hardware/Software Co-Design of a Java Virtual Machine Kenneth B. Kent University of Victoria Dept. of Computer Science Victoria, British Columbia, Canada [email protected] Micaela Serra University of Victoria
Software Development with Real- Time Workshop Embedded Coder Nigel Holliday Thales Missile Electronics. Missile Electronics
 Software Development with Real- Time Workshop Embedded Coder Nigel Holliday Thales 2 Contents Who are we, where are we, what do we do Why do we want to use Model-Based Design Our Approach to Model-Based
Software Development with Real- Time Workshop Embedded Coder Nigel Holliday Thales 2 Contents Who are we, where are we, what do we do Why do we want to use Model-Based Design Our Approach to Model-Based
Reconfigurable System-on-Chip Design
 Reconfigurable System-on-Chip Design MITCHELL MYJAK Senior Research Engineer Pacific Northwest National Laboratory PNNL-SA-93202 31 January 2013 1 About Me Biography BSEE, University of Portland, 2002
Reconfigurable System-on-Chip Design MITCHELL MYJAK Senior Research Engineer Pacific Northwest National Laboratory PNNL-SA-93202 31 January 2013 1 About Me Biography BSEE, University of Portland, 2002
A Survey on ARM Cortex A Processors. Wei Wang Tanima Dey
 A Survey on ARM Cortex A Processors Wei Wang Tanima Dey 1 Overview of ARM Processors Focusing on Cortex A9 & Cortex A15 ARM ships no processors but only IP cores For SoC integration Targeting markets:
A Survey on ARM Cortex A Processors Wei Wang Tanima Dey 1 Overview of ARM Processors Focusing on Cortex A9 & Cortex A15 ARM ships no processors but only IP cores For SoC integration Targeting markets:
Original Research Articles
 Original Research Articles Researchers Mr.Ramchandra K. Gurav, Prof. Mahesh S. Kumbhar Department of Electronics & Telecommunication, Rajarambapu Institute of Technology, Sakharale, M.S., INDIA Email-
Original Research Articles Researchers Mr.Ramchandra K. Gurav, Prof. Mahesh S. Kumbhar Department of Electronics & Telecommunication, Rajarambapu Institute of Technology, Sakharale, M.S., INDIA Email-
System Design Issues in Embedded Processing
 System Design Issues in Embedded Processing 9/16/10 Jacob Borgeson 1 Agenda What does TI do? From MCU to MPU to DSP: What are some trends? Design Challenges Tools to Help 2 TI - the complete system The
System Design Issues in Embedded Processing 9/16/10 Jacob Borgeson 1 Agenda What does TI do? From MCU to MPU to DSP: What are some trends? Design Challenges Tools to Help 2 TI - the complete system The
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Chapter 1: Introduction. What is an Operating System?
 Chapter 1: Introduction What is an Operating System? Mainframe Systems Desktop Systems Multiprocessor Systems Distributed Systems Clustered System Real -Time Systems Handheld Systems Computing Environments
Chapter 1: Introduction What is an Operating System? Mainframe Systems Desktop Systems Multiprocessor Systems Distributed Systems Clustered System Real -Time Systems Handheld Systems Computing Environments
Keywords ATM Terminal, Finger Print Recognition, Biometric Verification, PIN
 ATM Terminal Security Using Fingerprint Reconition. Prof. B.Jolad, Tejshree Salunkhe, Rutuja Patil, Puja Shindgi Padmashree Dr. D. Y. Patil Institute Of Engineering and Technology,Pimpri,Pune - 411018
ATM Terminal Security Using Fingerprint Reconition. Prof. B.Jolad, Tejshree Salunkhe, Rutuja Patil, Puja Shindgi Padmashree Dr. D. Y. Patil Institute Of Engineering and Technology,Pimpri,Pune - 411018
Achieving Nanosecond Latency Between Applications with IPC Shared Memory Messaging
 Achieving Nanosecond Latency Between Applications with IPC Shared Memory Messaging In some markets and scenarios where competitive advantage is all about speed, speed is measured in micro- and even nano-seconds.
Achieving Nanosecond Latency Between Applications with IPC Shared Memory Messaging In some markets and scenarios where competitive advantage is all about speed, speed is measured in micro- and even nano-seconds.
CS 377: Operating Systems. Outline. A review of what you ve learned, and how it applies to a real operating system. Lecture 25 - Linux Case Study
 CS 377: Operating Systems Lecture 25 - Linux Case Study Guest Lecturer: Tim Wood Outline Linux History Design Principles System Overview Process Scheduling Memory Management File Systems A review of what
CS 377: Operating Systems Lecture 25 - Linux Case Study Guest Lecturer: Tim Wood Outline Linux History Design Principles System Overview Process Scheduling Memory Management File Systems A review of what
ENHANCING ATM SECURITY USING FINGERPRINT AND GSM TECHNOLOGY
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 4, April 2014,
