Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device
|
|
|
- Cornelia Patterson
- 10 years ago
- Views:
Transcription
1 Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device Jyoti Rao *1,Kishan Mistry #2, Bhumika Mistry #3, Divya Malviya #4, Devesh Gudway #5 # Student & Department of Computer Engineering, Padmashree Dr. D. Y. Patil Institute of Engineering & Technology, Pimpri, Pune, Maharashtra, India. * Faculty & Department of Computer Engineering, Padmashree Dr. D. Y. Patil Institute of Engineering & Technology, Pimpri, Pune, Maharashtra, India. Abstract Every system uses text password but provide poor security. Graphical passwords on the other hand provide greater security and are easy to remember. In this paper we present various authentication schemes using graphical passwords. These provides potential solution to the flaws of text as well as graphical passwords. In this system we present two modes of graphical password authentication system i.e. offline and online. The offline mode consists of a graphical password integrated with sound signature, whereas the online mode focuses on Cued Click Point (CCP) based pattern using encryption and decryption. Keywords Security, Authentication, Sound signature, Graphical password, CCP, handheld devices. I. INTRODUCTION Traditional authentication systems uses text passwords which includes username and password. These passwords fails to provide the desired level of security. Text passwords, once chosen and learned, the user must able to recall it at the time of login, which makes them hard to remember. However if we keep changing our password frequently it is more vulnerable to be forgotten [6]. To reduce brute force attacks the user should select long passwords which include characters as well as numbers. This makes them all the more difficult to remember. Text passwords include risks of shoulder surfing, hidden cameras and spyware attacks. Also they are prone to dictionary attacks and keyboard sniffers. Thus they are not much reliable and hence for greater security we can use graphical passwords. Number of graphical password systems have been developed. Studies shows that text based password suffer with both security and usability problems. According to Picture Superiority Effect Theory, concepts are more likely to be recognized and remembered if they are presented as pictures rather than words. [2]. A graphical password is an image that is uploaded by the user or provided by the server [3]. The user has to click on various points on the image that leads to successful authentication. The user enters the password by clicking on a set of images, specific pixels on an image or by drawing a secret pattern in a predefined manner. A click based graphical password scheme called Cued Click Points uses a sequence of images in which user can select one click point per image or multiple points on a single image. These click points can either be selected by the user or they can be generated randomly by a server at the time of registration. At the time of logging in, the click points selected by the user are verified by the user with the points provided by the user at the time of registration or those provided by the server. If the number of possible pictures is made very large then it offers better resistance to dictionary attacks. It is also difficult to make automated attacks for graphical passwords. Thus graphical passwords presumably a higher usability compared to text based passwords. However in graphical passwords, users have predefined tap regions on one image to form a password. User entered a password by clicking on these regions in a specific order. This scheme is vulnerable to shoulder surfing and suffers from having a predetermined and a very small password space. Visual attention research shows that different people are attracted to the same predictable regions in an image. These regions are known as hotspots. If users select their own click-based graphical passwords without guidance, presence of hotspots will remain an issue. In order to overcome these drawbacks of text as well as graphical passwords, we integrate our system with universal multifactor authentication scheme. Multi-factor authentication is a way of authentication in which two or more independent factors are used as a part of user credentials. Multi-factor authentication is accomplished in our system by combining graphical passwords with another factor. This factors can include smart cards, USB tokens, handheld devices or one-time ISSN: Page 516
2 password token. In our system another factor is provided using sound signature in offline mode and using encryptiondecryption in online mode, both implemented on a handheld device. Having two or more factors strengthens but also complicates the authentication process. The rest of the paper has been organized as follows: Section II describes the various graphical password based system that have already been implemented. Section III describes our system architecture and the methodology that we are going to use. Section IV describes the algorithmic steps for the proposed methodology, and finally we discuss about the future scope of the project and conclude in Section V. II. RELATED WORK Many systems have been implemented that use graphical passwords. The best known of these systems are Passfaces, Click based graphical passwords, Pass-Point system, Persuasive click point systems. Blonder proposed a graphical authentication scheme called graphical password, based on cued recall. In this scheme the user creates a password by clicking on several location on an image, which are stored in the database. The user must click on the approximate areas of location for authentication [4]. Susan Wiedenbeck proposed and enhanced graphical authentication system called Pass-Points [3]. This idea is based on selection of a sequence of multiple click points on a single image as password. At the time of authentication the image is displayed on the screen by the system. The user needs to click on several previously chosen locations in a single image to login. Any pixel value in the image is a candidate for a click point. The problem with this scheme is that the number of predefined regions is small, perhaps a few dozen in a picture, leading to hotspots and pattern formation attacks. The password may have to be having 12 click points for sufficient security, thereby making it difficult for the user to remember. Cued Click Points (CCP) is a proposed alternative to pass points suggested by Sonia et al, designed to reduce patterns and usefulness of hotspots [5]. In CCP, user clicks one point each on multiple images rather than multiple points on a single image. It offers cued recall and introduces visual cues that instantly alerts valid users if they have made a mistake when entering the latest click point (at which they can cancel their attempt and retry from the beginning). Hotspot based attacks become more challenging. Each click results in showing a next image, thus leading users down a path as they click on their sequence of points. A wrong click results in an incorrect path with an explicit indication of authentication failure only after the final click. Real User Corporation developed a graphical authentication technique called Passfaces, in which a user logs onto a system by choosing the required number of faces from a grid of faces, thus proving additional security to a general text based password system. This technique is based on human s verse ability to recognize human faces [4]. R.Dhamija and A.Perrig mentioned a major authentication problem i.e., user s tend to have remembering secure passwords. In order to overcome this problem, he suggested a solution called Déjà vu in which the user has to select a particular number of images from a set of random pictures called challenge set. At the time of validation the user has to identify the preselected images. Another approach, known as Drawmetric password scheme, in which the user needs to draw a simple outline of the password at the time of registration and to be authenticated, similar drawing must be redrawn by the user [6]. Cognometric authentication is another approach in which the user has to identify a series of recognized images among a larger set of decoy images [4]. Jermyn introduced an authentication technique called Draw A Secret (D-A-S) which is basically intended for devices with stylus inputs such as Personal Digital Assistants (PDAs). Here, the user shall draw a secret drawing (password) on a 2D grid. The co-ordinates of this drawing on the grid are stored in order and the system verifies the drawing by checking the directions of the drawn stroke on the grid [6]. III. A. System Architecture: PROPOSED METHODOLOGY 1) Offline mode: In the offline mode, we have integrated sound signature along with graphical password. The multifactor authentication scheme here includes click points and handheld device. The idea of sound signature is inspired by human ability to recall objects by listening to a sound related to that particular object. The offline mode consists of basically 3 modules, i.e. Registration, Login and Verification modules. The Registration mode includes registering the user along with its details. These details comprises of a unique user-id (UID), Precision Value, address and phone number. The registration process proceeds further by allowing the user to select images, their respective click points and sound signature. Selection of image can either be done using the handheld device s in-built camera or using the ones that are already present the device. The user can select any click point on the image. Similar to images, selection of sound signature can either be done by choosing one of the already present sounds or by recording one s own voice that helps in recalling the object. Once done the user clicks on the sign up button, thus generating a user profile vector which is stored in the database. The profile vector consists of: User-vector (UID, precision, , Phone number) Image vector (UID, image-id) Click point vector (UID, image-id, click point co-ordinates(x,y)) The precision value helps to draw a circle around the click point which provides a tolerance region in which the user is allowed to click during the time of login. In Login mode, we first enter ISSN: Page 517
3 the user id, which if found, retrieves the respective set of images and the related sound signature from the database. Once the images and the audio are loaded, the user needs to select the click point on each of the image. The sound helps to remember click points (in case the user forgets the click point on a particular image). At this moment, a login vector is created. The login vector comprises of click points selected by the user during the login phase. Once the user selects all the click points, he/she clicks on the validate button in order to verify the click points. This module compares the click points registered in the database with the ones in the login vector. A successful login indicates the exact match of click points. Fig. 1 System Flowchart for Offline mode. 2) Online mode: In this approach, we use a handheld device that acts as a terminal, a server or a challenger which is a typical online web service provider. The server controls storage, retrieval of data and sending of images to the handheld device. This mode also includes 3 modules namely same as in the offline mode. The first screen (in Registration module) on the terminal asks the user for its unique user id, precision value, address, phone number. In the next step the user selects the number of desired click points. Along with that the user also needs to choose the sequence of click points which he/she will have to remember in order to login into the system. Thus a user profile is generated and sent to the server. ISSN: Page 518
4 Fig 2. System Flowchart for Online mode At the time of login, the user needs to enter the registered user id on the terminal side. The terminal sends a request to the server for generating an image with a number of click points on it. The server accepts the request, generates random click points on the image and sends the encrypted image to the handheld device. AES i.e. Advanced Encryption Standard technique is used for encryption. The encrypted image, now received on the terminal, is decrypted. The user now needs to select the click points in the same sequence which he/she had selected during the registration phase. The image provided by the server will have a number of click points each numbered with a single digit. The position of the click points will change every time a server responds to a request, however the sequence of click points is the main key to access login into the system. The addition click points are added just to confuse the unauthorized user. The verification module includes verification of the sequence of click points during the time of login with the one at the time of registration. An exact match of sequence leads to a successful login. ISSN: Page 519
5 IV. ALGORITHM 1. Start. 2. Select mode i.e online or offline mode. 3. If mode selected is offline 3.1. Select operation i.e Registration or Login If operation is Registration Enter user if, precision value, id and phone number Select an image from the device gallery or using camera Select click point and sound signature for that image For more number of images goto step else goto step Create user profile vector Store the user profile vector in the database If operation is Login Enter user-id to fetch image and sound signature from the database Play sound signature Select click point Compare click point including precision value with the one stored in the database for each image If valid for all images, Login successful else failure. 4. If the mode selected is online 4.1. Select Operation i.e Login Or Registration 4.2. If Operation selected is Registration Enter User Id, id, Phone No, and the number of Click Points Enter a sequence for the clicks Create User Profile Vector Store it in Database at Server If Operation selected is Login Enter User Id to request the Server to send a random image Server selects a random image and creates random position for click points which are numbered and send it to the User s handheld device User clicks on the image according to his sequence The sequence is sent to the Server Server verifies the sequence If Match of Sequence occurs,login is successful else failure 5. Stop. V. RESULT The Graphical password scheme used along with sound signature provides a better recall based security system compared to pure text passwords or pure graphical passwords. On the other hand, graphical passwords where the click points are randomly generated avoids shoulder surfing, dictionary attacks. Guessing of passwords in both the cases is difficult. Since we are using encryption technique (AES) for transmission over the network, brute force attacks are avoided. VI. CONCLUSION AND FUTURE SCOPE Text based authentication schemes face usability and security issues even though they are the most commonly used technique worldwide. Graphical passwords are easier to remember than text based passwords, but even the existing graphical password authentication systems have major drawbacks. In this paper, we propose a new graphical password system that overcomes difficulties like hotspot prediction, shoulder surfing, dictionary attacks. The system combines graphical passwords along with a handheld device and sound signature to form a multifactor authentication system. The generation of random click points during the online mode prevents the shoulder surfing attack as well as dictionary attacks. Storing the images at the server provides better security as compared to offline mode. The scope of the project can be further improved by using various techniques like Sudoku. The passwords can be changed every minute, thus making the user free from remembering passwords. He does not have to register on each and every website. Passwords are automatically generated and changed every time the user has to login. REFERENECES [1] S. Singh, and G. Agarwal, Integration of Sound Signature in Graphical Password Authentication System, IJCA January [2] A. P. Sabzevar, A. Stavrou, Universal Multifactor authentication system using Graphical Password. [3] S. K. Bandyopadhyay, D. Bhattacharyya, P. Das, User Authentication by secured graphical Password Implementation, IEICE [4] S. Malempati, S. Mogalla, Grid based approach for Data Confidentiality, IJCA July 2011 [5] V. Priya darshini, A. Gomathi, N. Saravanaselvam, A Novel based Multilevel Graphical Authentication System, IJARCCE Vol 2, September [6] T. Srinivasa Ravikiran, K.V.S. Rao, M. K. Rao, A. Srisaila, A symbol based graphical schema resistant to peeping attack, IJCSI Vol 10 on September [7] I. Jermyn, A. Mayer, F. Monrose, M. K. Reiter, A.D. Rubin, Design and Analysis of Graphical Password, The USENIX Association. ISSN: Page 520
Securing ATM Using Graphical Password Authentication Scheme
 Securing ATM Using Graphical Password Authentication Scheme Sonia Rathi 1, Raunak Chitnis 2, Ramakant Yadav 3, Mrs. M.V.Bhosle 4 1 (Department Of Information Technology, Marathwada Mitra Mandal s Institute
Securing ATM Using Graphical Password Authentication Scheme Sonia Rathi 1, Raunak Chitnis 2, Ramakant Yadav 3, Mrs. M.V.Bhosle 4 1 (Department Of Information Technology, Marathwada Mitra Mandal s Institute
International Journal of Software and Web Sciences (IJSWS) www.iasir.net
 International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0063 ISSN (Online): 2279-0071 International
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0063 ISSN (Online): 2279-0071 International
ABSTRACT I. INTRODUCTION
 Mobile Backup Web Application Using Image Processing Authentication 1 Walse Reshma S. 2 Khemnar Archana M. 3 Padir Maya S. 4 Prof.K.P.Somase Department Of Computer Engineering, Jcoe(Kuran),Tal:Junnar,Dist:Pune
Mobile Backup Web Application Using Image Processing Authentication 1 Walse Reshma S. 2 Khemnar Archana M. 3 Padir Maya S. 4 Prof.K.P.Somase Department Of Computer Engineering, Jcoe(Kuran),Tal:Junnar,Dist:Pune
Universal Multi-Factor Authentication Using Graphical Passwords
 Universal Multi-Factor Authentication Using Graphical Passwords Alireza Pirayesh Sabzevar, Angelos Stavrou Computer Science Department, George Mason University, Fairfax, Virginia, 22030 {apirayes, astavrou}@gmu.edu
Universal Multi-Factor Authentication Using Graphical Passwords Alireza Pirayesh Sabzevar, Angelos Stavrou Computer Science Department, George Mason University, Fairfax, Virginia, 22030 {apirayes, astavrou}@gmu.edu
Integration of Sound Signature in 3D Password Authentication System
 Integration of Sound Signature in 3D Password Authentication System Mr.Jaywant N. Khedkar 1, Ms.Pragati P. Katalkar 2, Ms.Shalini V. Pathak 3, Mrs.Rohini V.Agawane 4 1, 2, 3 Student, Dept. of Computer
Integration of Sound Signature in 3D Password Authentication System Mr.Jaywant N. Khedkar 1, Ms.Pragati P. Katalkar 2, Ms.Shalini V. Pathak 3, Mrs.Rohini V.Agawane 4 1, 2, 3 Student, Dept. of Computer
3D PASSWORD. Snehal Kognule Dept. of Comp. Sc., Padmabhushan Vasantdada Patil Pratishthan s College of Engineering, Mumbai University, India
 3D PASSWORD Tejal Kognule Yugandhara Thumbre Snehal Kognule ABSTRACT 3D passwords which are more customizable and very interesting way of authentication. Now the passwords are based on the fact of Human
3D PASSWORD Tejal Kognule Yugandhara Thumbre Snehal Kognule ABSTRACT 3D passwords which are more customizable and very interesting way of authentication. Now the passwords are based on the fact of Human
Vishal Kolhe, Vipul Gunjal, Sayali Kalasakar, Pranjal Rathod Department of Computer Engineering, Amrutvahini Collage of Engineering, Sangamner
 Secure Authentication with 3D Password Vishal Kolhe, Vipul Gunjal, Sayali Kalasakar, Pranjal Rathod Department of Computer Engineering, Amrutvahini Collage of Engineering, Sangamner Abstract Providing
Secure Authentication with 3D Password Vishal Kolhe, Vipul Gunjal, Sayali Kalasakar, Pranjal Rathod Department of Computer Engineering, Amrutvahini Collage of Engineering, Sangamner Abstract Providing
One Time Password Generation for Multifactor Authentication using Graphical Password
 One Time Password Generation for Multifactor Authentication using Graphical Password Nilesh B. Khankari 1, Prof. G.V. Kale 2 1,2 Department of Computer Engineering, Pune Institute of Computer Technology,
One Time Password Generation for Multifactor Authentication using Graphical Password Nilesh B. Khankari 1, Prof. G.V. Kale 2 1,2 Department of Computer Engineering, Pune Institute of Computer Technology,
SECUDROID - A Secured Authentication in Android Phones Using 3D Password
 SECUDROID - A Secured Authentication in Android Phones Using 3D Password Ms. Chandra Prabha K M.E. Ph.D. 1, Mohamed Nowfel 2 E S, Jr., Gowtham V 3, Dhinakaran V 4 1, 2, 3, 4 Department of CSE, K.S.Rangasamy
SECUDROID - A Secured Authentication in Android Phones Using 3D Password Ms. Chandra Prabha K M.E. Ph.D. 1, Mohamed Nowfel 2 E S, Jr., Gowtham V 3, Dhinakaran V 4 1, 2, 3, 4 Department of CSE, K.S.Rangasamy
A puzzle based authentication method with server monitoring
 A puzzle based authentication method with server monitoring GRADUATE PROJECT REPORT Submitted to the Faculty of The School of Engineering & Computing Sciences Texas A&M University-Corpus Christi Corpus
A puzzle based authentication method with server monitoring GRADUATE PROJECT REPORT Submitted to the Faculty of The School of Engineering & Computing Sciences Texas A&M University-Corpus Christi Corpus
Dynamic Query Updation for User Authentication in cloud Environment
 Dynamic Query Updation for User Authentication in cloud Environment Gaurav Shrivastava 1, Dr. S. Prabakaran 2 1 Research Scholar, Department of Computer Science, SRM University, Kattankulathur, Tamilnadu,
Dynamic Query Updation for User Authentication in cloud Environment Gaurav Shrivastava 1, Dr. S. Prabakaran 2 1 Research Scholar, Department of Computer Science, SRM University, Kattankulathur, Tamilnadu,
IDRBT Working Paper No. 11 Authentication factors for Internet banking
 IDRBT Working Paper No. 11 Authentication factors for Internet banking M V N K Prasad and S Ganesh Kumar ABSTRACT The all pervasive and continued growth being provided by technology coupled with the increased
IDRBT Working Paper No. 11 Authentication factors for Internet banking M V N K Prasad and S Ganesh Kumar ABSTRACT The all pervasive and continued growth being provided by technology coupled with the increased
3D-WEBAUTHEN: HIGH DEGREE OF AUTHENTICATION FOR WEB APPLICATION DEVELOPMENT
 3D-WEBAUTHEN: HIGH DEGREE OF AUTHENTICATION FOR WEB APPLICATION DEVELOPMENT Waraporn Viyanon Computer Science Program, Department of Mathematics Faculty of Science, Srinakharinwirot University Bangkok,
3D-WEBAUTHEN: HIGH DEGREE OF AUTHENTICATION FOR WEB APPLICATION DEVELOPMENT Waraporn Viyanon Computer Science Program, Department of Mathematics Faculty of Science, Srinakharinwirot University Bangkok,
(IT Journal of Research, Volume 1, May 2010 SECUREZZA. Prof. Gauri Rao, Lecturer Bharati Vidyapeeth College of Engineering, Pune.
 SECUREZZA Prof. Gauri Rao, Lecturer Bharati Vidyapeeth College of Engineering, Pune Abstract The current security systems and authentication systems have much weakness and are prone to break through. Textual
SECUREZZA Prof. Gauri Rao, Lecturer Bharati Vidyapeeth College of Engineering, Pune Abstract The current security systems and authentication systems have much weakness and are prone to break through. Textual
M-Pass: Web Authentication Protocol Resistant to Malware and Phishing
 M-Pass: Web Authentication Protocol Resistant to Malware and Phishing Ajinkya S. Yadav M.E.student, Department of Computer Engineering. Pune University, Pune A. K.Gupta Professor, Department of Computer
M-Pass: Web Authentication Protocol Resistant to Malware and Phishing Ajinkya S. Yadav M.E.student, Department of Computer Engineering. Pune University, Pune A. K.Gupta Professor, Department of Computer
Monalisa P. Kini, Kavita V. Sonawane, Shamsuddin S. Khan
 International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 1410 Secured Authentication Using Mobile Phone as Security Token Monalisa P. Kini, Kavita V. Sonawane, Shamsuddin
International Journal of Scientific & Engineering Research, Volume 5, Issue 7, July-2014 1410 Secured Authentication Using Mobile Phone as Security Token Monalisa P. Kini, Kavita V. Sonawane, Shamsuddin
Reset Virtual Gateway Password Job Aid
 Summary of Job Aid In order to access a Virtual Gateway s business service, you must first log on to the Virtual Gateway (VG). From the Virtual Gateway s website (www.mass.gov/vg), click Logon to Virtual
Summary of Job Aid In order to access a Virtual Gateway s business service, you must first log on to the Virtual Gateway (VG). From the Virtual Gateway s website (www.mass.gov/vg), click Logon to Virtual
Client Server Registration Protocol
 Client Server Registration Protocol The Client-Server protocol involves these following steps: 1. Login 2. Discovery phase User (Alice or Bob) has K s Server (S) has hash[pw A ].The passwords hashes are
Client Server Registration Protocol The Client-Server protocol involves these following steps: 1. Login 2. Discovery phase User (Alice or Bob) has K s Server (S) has hash[pw A ].The passwords hashes are
Single Sign-On Secure Authentication Password Mechanism
 Single Sign-On Secure Authentication Password Mechanism Deepali M. Devkate, N.D.Kale ME Student, Department of CE, PVPIT, Bavdhan, SavitribaiPhule University Pune, Maharashtra,India. Assistant Professor,
Single Sign-On Secure Authentication Password Mechanism Deepali M. Devkate, N.D.Kale ME Student, Department of CE, PVPIT, Bavdhan, SavitribaiPhule University Pune, Maharashtra,India. Assistant Professor,
Application of Neural Network in User Authentication for Smart Home System
 Application of Neural Network in User Authentication for Smart Home System A. Joseph, D.B.L. Bong, D.A.A. Mat Abstract Security has been an important issue and concern in the smart home systems. Smart
Application of Neural Network in User Authentication for Smart Home System A. Joseph, D.B.L. Bong, D.A.A. Mat Abstract Security has been an important issue and concern in the smart home systems. Smart
SECURING SELF-SERVICE PASSWORD RESET
 SECURING SELF-SERVICE PASSWORD RESET FUNCTIONALITY IN WEB APPLICATIONS David A. Shpritz July, 2010 INTRODUCTION Many web applications requiring user authentication also provide self-service password reset
SECURING SELF-SERVICE PASSWORD RESET FUNCTIONALITY IN WEB APPLICATIONS David A. Shpritz July, 2010 INTRODUCTION Many web applications requiring user authentication also provide self-service password reset
Secure Authentication of Distributed Networks by Single Sign-On Mechanism
 Secure Authentication of Distributed Networks by Single Sign-On Mechanism Swati Sinha 1, Prof. Sheerin Zadoo 2 P.G.Student, Department of Computer Application, TOCE, Bangalore, Karnataka, India 1 Asst.Professor,
Secure Authentication of Distributed Networks by Single Sign-On Mechanism Swati Sinha 1, Prof. Sheerin Zadoo 2 P.G.Student, Department of Computer Application, TOCE, Bangalore, Karnataka, India 1 Asst.Professor,
SECURITY ANALYSIS OF PASSWORD BASED MUTUAL AUTHENTICATION METHOD FOR REMOTE USER
 SECURITY ANALYSIS OF PASSWORD BASED MUTUAL AUTHENTICATION METHOD FOR REMOTE USER Mrs. P.Venkateswari Assistant Professor / CSE Erode Sengunthar Engineering College, Thudupathi ABSTRACT Nowadays Communication
SECURITY ANALYSIS OF PASSWORD BASED MUTUAL AUTHENTICATION METHOD FOR REMOTE USER Mrs. P.Venkateswari Assistant Professor / CSE Erode Sengunthar Engineering College, Thudupathi ABSTRACT Nowadays Communication
Review Paper on Two Factor Authentication Using Mobile Phone (Android) ISSN 2319-9725
 Review Paper on Two Factor Authentication Using Mobile Phone (Android) ISSN 2319-9725 Rahul Kale Neha Gore Kavita Nilesh Jadhav Mr. Swapnil Shinde Bachelor s Degree program in Information Technology Engineering
Review Paper on Two Factor Authentication Using Mobile Phone (Android) ISSN 2319-9725 Rahul Kale Neha Gore Kavita Nilesh Jadhav Mr. Swapnil Shinde Bachelor s Degree program in Information Technology Engineering
SECURITY STORAGE MODEL OF DATA IN CLOUD Sonia Arora 1 Pawan Luthra 2 1,2 Department of Computer Science & Engineering, SBSSTC
 SECURITY STORAGE MODEL OF DATA IN CLOUD Sonia Arora 1 Pawan Luthra 2 1,2 Department of Computer Science & Engineering, SBSSTC Ferozepur, Punjab, India Email: 1 [email protected], 2 [email protected]
SECURITY STORAGE MODEL OF DATA IN CLOUD Sonia Arora 1 Pawan Luthra 2 1,2 Department of Computer Science & Engineering, SBSSTC Ferozepur, Punjab, India Email: 1 [email protected], 2 [email protected]
Chapter 1: Introduction
 Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
7. In the boxed unlabeled field, enter the last 4 digits of your Social Security number.
 CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
Multi-Factor Authentication (MFA)
 The Multi-Factor Authentication (MFA) solution for Inter@ct Statements and Notices has been redesigned and enhanced; customers who directly access the Inter@ct Statements and Notices application to log
The Multi-Factor Authentication (MFA) solution for Inter@ct Statements and Notices has been redesigned and enhanced; customers who directly access the Inter@ct Statements and Notices application to log
Securing e-government Web Portal Access Using Enhanced Two Factor Authentication
 Securing e-government Web Portal Access Using Enhanced Two Factor Authentication Ahmed Arara 1, El-Bahlul Emhemed Fgee 2, and Hamdi Ahmed Jaber 3 Abstract This paper suggests an advanced two-factor authentication
Securing e-government Web Portal Access Using Enhanced Two Factor Authentication Ahmed Arara 1, El-Bahlul Emhemed Fgee 2, and Hamdi Ahmed Jaber 3 Abstract This paper suggests an advanced two-factor authentication
Whitepaper on AuthShield Two Factor Authentication with ERP Applications
 Whitepaper on AuthShield Two Factor Authentication with ERP Applications By INNEFU Labs Pvt. Ltd Table of Contents 1. Overview... 3 2. Threats to account passwords... 4 2.1 Social Engineering or Password
Whitepaper on AuthShield Two Factor Authentication with ERP Applications By INNEFU Labs Pvt. Ltd Table of Contents 1. Overview... 3 2. Threats to account passwords... 4 2.1 Social Engineering or Password
Enhanced Security for Online Banking
 Enhanced Security for Online Banking MidSouth Bank is focused on protecting your personal and account information at all times. As instances of internet fraud increase, it is no longer sufficient to use
Enhanced Security for Online Banking MidSouth Bank is focused on protecting your personal and account information at all times. As instances of internet fraud increase, it is no longer sufficient to use
An Efficient Windows Cardspace identity Management Technique in Cloud Computing
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 3, Ver. VII (May-Jun. 2014), PP 61-66 An Efficient Windows Cardspace identity Management Technique
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 3, Ver. VII (May-Jun. 2014), PP 61-66 An Efficient Windows Cardspace identity Management Technique
A NOVEL GRAPHICAL PASSWORD APPROACH FOR ACCESSING CLOUD & DATA VERIFICATION
 A NOVEL GRAPHICAL PASSWORD APPROACH FOR ACCESSING CLOUD & DATA VERIFICATION Rupal Rawat 1, Sreeja Nair 2 1 M.Tech (CSE), Oriental college of science & Technology, Bhopal, Affiliated to RGPV, Bhopal, M.P,
A NOVEL GRAPHICAL PASSWORD APPROACH FOR ACCESSING CLOUD & DATA VERIFICATION Rupal Rawat 1, Sreeja Nair 2 1 M.Tech (CSE), Oriental college of science & Technology, Bhopal, Affiliated to RGPV, Bhopal, M.P,
The Security Behind Sticky Password
 The Security Behind Sticky Password Technical White Paper version 3, September 16th, 2015 Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and
The Security Behind Sticky Password Technical White Paper version 3, September 16th, 2015 Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and
Multi-Factor Authentication
 Enhancing network security through the authentication process Multi-Factor Authentication Passwords, Smart Cards, and Biometrics INTRODUCTION Corporations today are investing more time and resources on
Enhancing network security through the authentication process Multi-Factor Authentication Passwords, Smart Cards, and Biometrics INTRODUCTION Corporations today are investing more time and resources on
Public Auditing & Automatic Protocol Blocking with 3-D Password Authentication for Secure Cloud Storage
 Public Auditing & Automatic Protocol Blocking with 3-D Password Authentication for Secure Cloud Storage P. Selvigrija, Assistant Professor, Department of Computer Science & Engineering, Christ College
Public Auditing & Automatic Protocol Blocking with 3-D Password Authentication for Secure Cloud Storage P. Selvigrija, Assistant Professor, Department of Computer Science & Engineering, Christ College
Providing Data Protection as a Service in Cloud Computing
 International Journal of Scientific and Research Publications, Volume 3, Issue 6, June 2013 1 Providing Data Protection as a Service in Cloud Computing Sunumol Cherian *, Kavitha Murukezhan ** * Department
International Journal of Scientific and Research Publications, Volume 3, Issue 6, June 2013 1 Providing Data Protection as a Service in Cloud Computing Sunumol Cherian *, Kavitha Murukezhan ** * Department
MULTI-FACTOR AUTHENTICATION SET-UP
 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application TABLE OF CONTENTS Click the link below to go to the section you need: First Time Enrollment Enrolled User Contact information on file
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application TABLE OF CONTENTS Click the link below to go to the section you need: First Time Enrollment Enrolled User Contact information on file
NetIQ Advanced Authentication Framework - Client. User's Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework - Client User's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 4 About This Document 4 NetIQ Advanced Authentication Framework Overview
NetIQ Advanced Authentication Framework - Client User's Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 4 About This Document 4 NetIQ Advanced Authentication Framework Overview
International Journal of Intellectual Advancements and Research in Engineering Computations
 www.ijiarec.com MAY-2015 International Journal of Intellectual Advancements and Research in Engineering Computations CLOUD BASED MULTIFACTOR AUTHENTICATION FOR PERSONAL HEALTH RECORD ABSTRACT ISSN: 2348-2079
www.ijiarec.com MAY-2015 International Journal of Intellectual Advancements and Research in Engineering Computations CLOUD BASED MULTIFACTOR AUTHENTICATION FOR PERSONAL HEALTH RECORD ABSTRACT ISSN: 2348-2079
Voice based email system for blinds
 Voice based email system for blinds T.Shabana 1, A.Anam 2, A.Rafiya 3, K.Aisha 4 Assistant Professor, Computer Engineering, M.H. Saboo Siddik College of Engineering, Mumbai, India 1 UG Student, Computer
Voice based email system for blinds T.Shabana 1, A.Anam 2, A.Rafiya 3, K.Aisha 4 Assistant Professor, Computer Engineering, M.H. Saboo Siddik College of Engineering, Mumbai, India 1 UG Student, Computer
Virtual Code Authentication User s Guide. June 25, 2015
 Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Document Digital Signature
 Supplier handbook Software Configuration for Digital Signature and Timestamp to certificate-based signature Document objectives and structure The document aims to support suppliers during the following
Supplier handbook Software Configuration for Digital Signature and Timestamp to certificate-based signature Document objectives and structure The document aims to support suppliers during the following
Application Security Testing. Generic Test Strategy
 Application Security Testing Generic Test Strategy Page 2 of 8 Contents 1 Introduction 3 1.1 Purpose: 3 1.2 Application Security Testing: 3 2 Audience 3 3 Test Strategy guidelines 3 3.1 Authentication
Application Security Testing Generic Test Strategy Page 2 of 8 Contents 1 Introduction 3 1.1 Purpose: 3 1.2 Application Security Testing: 3 2 Audience 3 3 Test Strategy guidelines 3 3.1 Authentication
Assessing the Security of Hardware-Based vs. Software-Based Encryption on USB Flash Drives
 Assessing the Security of Hardware-Based vs. Software-Based Encryption on USB Flash Drives Main Line / Date / Etc. June May 2008 2nd Line 80-11-01583 xx-xx-xxxx Revision 1.0 Tagline Here Table of Contents
Assessing the Security of Hardware-Based vs. Software-Based Encryption on USB Flash Drives Main Line / Date / Etc. June May 2008 2nd Line 80-11-01583 xx-xx-xxxx Revision 1.0 Tagline Here Table of Contents
Step 1. Step 2. Open your browser and go to https://accounts.bestcare.org and you will be presented a logon screen show below.
 Manage your two-factor options through the accounts.bestcare.org website. This website is available internally and externally of the organization. Like other services, if you connect while external of
Manage your two-factor options through the accounts.bestcare.org website. This website is available internally and externally of the organization. Like other services, if you connect while external of
River Valley Credit Union Online Banking
 River Valley Credit Union Online Banking New user setup guide Members can self enroll for the service by answering a few simple questions. Before beginning the process, please make sure you have this information
River Valley Credit Union Online Banking New user setup guide Members can self enroll for the service by answering a few simple questions. Before beginning the process, please make sure you have this information
Dashlane Security Whitepaper
 Dashlane Security Whitepaper November 2014 Protection of User Data in Dashlane Protection of User Data in Dashlane relies on 3 separate secrets: The User Master Password Never stored locally nor remotely.
Dashlane Security Whitepaper November 2014 Protection of User Data in Dashlane Protection of User Data in Dashlane relies on 3 separate secrets: The User Master Password Never stored locally nor remotely.
Keywords Decryption, Encryption,password attack, Replay attack, steganography, Visual cryptography EXISTING SYSTEM OF KERBEROS
 Volume 4, Issue 2, February 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Secure Authentication
Volume 4, Issue 2, February 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Secure Authentication
Connected from everywhere. Cryptelo completely protects your data. Data transmitted to the server. Data sharing (both files and directory structure)
 Cryptelo Drive Cryptelo Drive is a virtual drive, where your most sensitive data can be stored. Protect documents, contracts, business know-how, or photographs - in short, anything that must be kept safe.
Cryptelo Drive Cryptelo Drive is a virtual drive, where your most sensitive data can be stored. Protect documents, contracts, business know-how, or photographs - in short, anything that must be kept safe.
Preventing Identity Theft using Shift Key mechanism and QR Code with Sudoku Puzzle
 DOI 10.4010/2014.282 ISSN-2321-3361 2014 IJESC Research Article Preventing Identity Theft using Shift Key mechanism and QR Code with Sudoku Puzzle R.Saisrikanth Department of Computer Science and Engineering
DOI 10.4010/2014.282 ISSN-2321-3361 2014 IJESC Research Article Preventing Identity Theft using Shift Key mechanism and QR Code with Sudoku Puzzle R.Saisrikanth Department of Computer Science and Engineering
Remote Access Securing Your Employees Out of the Office
 Remote Access Securing Your Employees Out of the Office HSTE-NB0011-RV 1.0 Hypersecu Information Systems, Inc. #200-6191 Westminster Hwy Richmond BC V7C 4V4 Canada 1 (855) 497-3700 www.hypersecu.com Introduction
Remote Access Securing Your Employees Out of the Office HSTE-NB0011-RV 1.0 Hypersecu Information Systems, Inc. #200-6191 Westminster Hwy Richmond BC V7C 4V4 Canada 1 (855) 497-3700 www.hypersecu.com Introduction
(C) Global Journal of Engineering Science and Research Management
 DEPENDABLE STORAGE FOR VEHICLE INSURANCE MANAGEMENT THROUGH SECURED ENCRYPTION IN CLOUD COMPUTING Prof.Abhijeet A.Chincholkar *1, Ms.Najuka Todekar 2 *1 M.E. Digital Electronics, JCOET Yavatmal, India.
DEPENDABLE STORAGE FOR VEHICLE INSURANCE MANAGEMENT THROUGH SECURED ENCRYPTION IN CLOUD COMPUTING Prof.Abhijeet A.Chincholkar *1, Ms.Najuka Todekar 2 *1 M.E. Digital Electronics, JCOET Yavatmal, India.
Two Factor Authentication. Software Version (SV) 1.0
 Two Factor Authentication Software Version (SV) 1.0 Property of: Worldwide Interactive Services, Inc. 5025 South Orange Avenue Orlando, FL 32809 The data contained in this documentation is PROPRIETARY
Two Factor Authentication Software Version (SV) 1.0 Property of: Worldwide Interactive Services, Inc. 5025 South Orange Avenue Orlando, FL 32809 The data contained in this documentation is PROPRIETARY
Authentication Types. Password-based Authentication. Off-Line Password Guessing
 Authentication Types Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4:
Authentication Types Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4:
User s Guide [Security Operations]
![User s Guide [Security Operations] User s Guide [Security Operations]](/thumbs/24/3393053.jpg) User s Guide [Security Operations] 010. 6 Ver. 1.01 Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3 1. Security
User s Guide [Security Operations] 010. 6 Ver. 1.01 Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3 1. Security
Journal of Internet Banking and Commerce
 Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/) Journal of Internet Banking and Commerce, April 2012, vol. 17, no. 1 (http://www.arraydev.com/commerce/jibc/)
Journal of Internet Banking and Commerce An open access Internet journal (http://www.arraydev.com/commerce/jibc/) Journal of Internet Banking and Commerce, April 2012, vol. 17, no. 1 (http://www.arraydev.com/commerce/jibc/)
MULTI-FACTOR AUTHENTICATION SET-UP
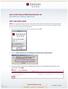 MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
MULTI-FACTOR AUTHENTICATION SET-UP DepositPartner Desktop Application FIRST TIME ENROLLMENT NOTE: Your computer settings cannot be set to clear cookies upon exit, otherwise you will be prompted to enter
Advanced Authentication
 White Paper Advanced Authentication Introduction In this paper: Introduction 1 User Authentication 2 Device Authentication 3 Message Authentication 4 Advanced Authentication 5 Advanced Authentication is
White Paper Advanced Authentication Introduction In this paper: Introduction 1 User Authentication 2 Device Authentication 3 Message Authentication 4 Advanced Authentication 5 Advanced Authentication is
Flexible Identity. Tokenless authenticators guide. Multi-Factor Authentication. version 1.0
 Flexible Identity Multi-Factor Authentication Tokenless authenticators guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services
Flexible Identity Multi-Factor Authentication Tokenless authenticators guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services
2.4: Authentication Authentication types Authentication schemes: RSA, Lamport s Hash Mutual Authentication Session Keys Trusted Intermediaries
 Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application
Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application
ISSN: 2321-7782 (Online) Volume 2, Issue 1, January 2014 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 2, Issue 1, January 2014 International Journal of Advance Research in Computer Science and Management Studies Research Paper Available online at: www.ijarcsms.com New Challenges
ISSN: 2321-7782 (Online) Volume 2, Issue 1, January 2014 International Journal of Advance Research in Computer Science and Management Studies Research Paper Available online at: www.ijarcsms.com New Challenges
White Paper Preventing Man in the Middle Phishing Attacks with Multi-Factor Authentication
 White Paper Preventing Man in the Middle Phishing Attacks with Multi-Factor Authentication Page 1 of 8 Introduction As businesses and consumers grow increasingly reliant on the Internet for conducting
White Paper Preventing Man in the Middle Phishing Attacks with Multi-Factor Authentication Page 1 of 8 Introduction As businesses and consumers grow increasingly reliant on the Internet for conducting
mbank Introduces Personal Security Image MFA* for Consumer on-line banking *Multi-Factor Authentication
 mbank Introduces Personal Security Image MFA* for Consumer on-line banking *Multi-Factor Authentication Enhanced security for your on-line banking activities. Beginning 24 January 2007 all mbank clients
mbank Introduces Personal Security Image MFA* for Consumer on-line banking *Multi-Factor Authentication Enhanced security for your on-line banking activities. Beginning 24 January 2007 all mbank clients
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Liquid Machines Document Control Client Version 7. Helpdesk Run Book and Troubleshooting Guide
 Document Control Client Version 7 OVERVIEW OF LIQUID MACHINES DOCUMENT CONTROL VERSION 7...1 FEATURES...1 Microsoft Windows Rights Management Services (RMS)...1 Policies and Rights...1 Client...1 Policy
Document Control Client Version 7 OVERVIEW OF LIQUID MACHINES DOCUMENT CONTROL VERSION 7...1 FEATURES...1 Microsoft Windows Rights Management Services (RMS)...1 Policies and Rights...1 Client...1 Policy
Protected Cash Withdrawal in Atm Using Mobile Phone
 www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 4 April, 2013 Page No. 1346-1350 Protected Cash Withdrawal in Atm Using Mobile Phone M.R.Dineshkumar
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 4 April, 2013 Page No. 1346-1350 Protected Cash Withdrawal in Atm Using Mobile Phone M.R.Dineshkumar
USER GUIDE FOR CET-2016 ONLINE APPLICATION
 USER GUIDE FOR CET-2016 ONLINE APPLICATION Table content 1. HOME PAGE 1 2. INSTRUCTIONS 2 3. NEW REGISTRATION FORM 3 4. LOGIN FORM 4 5. FORGOT PASSWORD 4 6. STUDENT INFORMATION 5 7. STUDY DETAILS 7 8.
USER GUIDE FOR CET-2016 ONLINE APPLICATION Table content 1. HOME PAGE 1 2. INSTRUCTIONS 2 3. NEW REGISTRATION FORM 3 4. LOGIN FORM 4 5. FORGOT PASSWORD 4 6. STUDENT INFORMATION 5 7. STUDY DETAILS 7 8.
Password Manager with 3-Step Authentication System
 Password Manager with 3-Step Authentication System Zhelyazko Petrov, Razvan Ragazan University of Westminster, London [email protected], [email protected] Abstract: A big
Password Manager with 3-Step Authentication System Zhelyazko Petrov, Razvan Ragazan University of Westminster, London [email protected], [email protected] Abstract: A big
Password regulations for Karolinska Institutet
 Password regulations for Karolinska Institutet Dnr 1-213/2015 Version 2.0 Applicable from 2015-05-18 Password regulations for Karolinska Institutet - Summary Purpose The main purpose of these regulations
Password regulations for Karolinska Institutet Dnr 1-213/2015 Version 2.0 Applicable from 2015-05-18 Password regulations for Karolinska Institutet - Summary Purpose The main purpose of these regulations
This information can be made available in Large Print
 Do you have a question about MyAccounts? Just click on the relevant question from the list below for further information. To download the documents on this page, you must have Adobe Acrobat Reader installed
Do you have a question about MyAccounts? Just click on the relevant question from the list below for further information. To download the documents on this page, you must have Adobe Acrobat Reader installed
Simple Guide to Digital Signatures
 Simple Guide to Digital Signatures Rohas Nagpal Asian School of Cyber Laws About the author Rohas Nagpal is the founder President of Asian School of Cyber Laws. He advises Governments and corporates around
Simple Guide to Digital Signatures Rohas Nagpal Asian School of Cyber Laws About the author Rohas Nagpal is the founder President of Asian School of Cyber Laws. He advises Governments and corporates around
Awase-E: Image-based Authentication for Mobile Phones using User s Favorite Images
 Awase-E: Image-based Authentication for Mobile Phones using User s Favorite Images Tetsuji TAKADA 1 and Hideki KOIKE 2 1 SONY Computer Science Laboratories Muse Bldg. 3-14-13 Higashigotanda, Shinagawa-ku,
Awase-E: Image-based Authentication for Mobile Phones using User s Favorite Images Tetsuji TAKADA 1 and Hideki KOIKE 2 1 SONY Computer Science Laboratories Muse Bldg. 3-14-13 Higashigotanda, Shinagawa-ku,
Multi-factor Authentication Security Enhancement
 Multi-factor Authentication Security Enhancement Contents Overview of Multi-Factor Authentication... 4 Establishing a First Mercantile Multi-Factor User Account... 5 Authentication Questionnaire... 8 Secondary
Multi-factor Authentication Security Enhancement Contents Overview of Multi-Factor Authentication... 4 Establishing a First Mercantile Multi-Factor User Account... 5 Authentication Questionnaire... 8 Secondary
Sticky Password 7. Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet
 Sticky Password 7 Reviewer Guide Introduction Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet simple password manager and form-filler. Its main goal
Sticky Password 7 Reviewer Guide Introduction Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet simple password manager and form-filler. Its main goal
International Journal of Advance Foundation and Research in Computer (IJAFRC) Volume 2, Special Issue (NCRTIT 2015), January 2015.
 Android Based E-Voting. Harshad Velapure, Saurabh Rai, Saransh Sharma, Preetam Naiknavre, Pranali Jadhav, Kalyan Bamane Department of Information Technology, D. Y. Patil College of Engineering, Akurdi,
Android Based E-Voting. Harshad Velapure, Saurabh Rai, Saransh Sharma, Preetam Naiknavre, Pranali Jadhav, Kalyan Bamane Department of Information Technology, D. Y. Patil College of Engineering, Akurdi,
PASSWORD MANAGEMENT. February 2008. The Government of the Hong Kong Special Administrative Region
 PASSWORD MANAGEMENT February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
PASSWORD MANAGEMENT February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
An Enhanced Countermeasure Technique for Deceptive Phishing Attack
 An Enhanced Countermeasure Technique for Deceptive Phishing Attack K. Selvan 1, Dr. M. Vanitha 2 Research Scholar and Assistant Professor, Department of Computer Science, JJ College of Arts and Science
An Enhanced Countermeasure Technique for Deceptive Phishing Attack K. Selvan 1, Dr. M. Vanitha 2 Research Scholar and Assistant Professor, Department of Computer Science, JJ College of Arts and Science
Using GhostPorts Multi-Factor Authentication
 Using GhostPorts Multi-Factor Authentication With CloudPassage Halo GhostPorts is a powerful multi-factor authentication feature available with the Halo NetSec and Halo Professional subscription plans.
Using GhostPorts Multi-Factor Authentication With CloudPassage Halo GhostPorts is a powerful multi-factor authentication feature available with the Halo NetSec and Halo Professional subscription plans.
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 7 Access Control Fundamentals
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 7 Access Control Fundamentals Objectives Define access control and list the four access control models Describe logical access control
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 7 Access Control Fundamentals Objectives Define access control and list the four access control models Describe logical access control
Internet Banking Two-Factor Authentication using Smartphones
 Internet Banking Two-Factor Authentication using Smartphones Costin Andrei SOARE IT&C Security Master Department of Economic Informatics and Cybernetics Bucharest University of Economic Studies, Romania
Internet Banking Two-Factor Authentication using Smartphones Costin Andrei SOARE IT&C Security Master Department of Economic Informatics and Cybernetics Bucharest University of Economic Studies, Romania
How To Protect The Time System From Being Hacked
 WISCONSIN TIME SYSTEM Training Materials TIME SYSTEM SECURITY AWARENESS HANDOUT Revised 11/21/13 2014 Security Awareness Handout All System Security The TIME/NCIC Systems are criminal justice computer
WISCONSIN TIME SYSTEM Training Materials TIME SYSTEM SECURITY AWARENESS HANDOUT Revised 11/21/13 2014 Security Awareness Handout All System Security The TIME/NCIC Systems are criminal justice computer
Security Model in E-government with Biometric based on PKI
 Security Model in E-government with Biometric based on PKI Jaafar.TH. Jaafar Institute of Statistical Studies and Research Department of Computer and Information Sciences Cairo, Egypt Nermin Hamza Institute
Security Model in E-government with Biometric based on PKI Jaafar.TH. Jaafar Institute of Statistical Studies and Research Department of Computer and Information Sciences Cairo, Egypt Nermin Hamza Institute
User Manual for e-banking Services for Business Clients
 User Manual for e-banking Services for Business Clients Page 1 of 51 Introduction to e-banking user manual Dear users, This e-banking User Manual will guide you on a step by step basis, on how to use and
User Manual for e-banking Services for Business Clients Page 1 of 51 Introduction to e-banking user manual Dear users, This e-banking User Manual will guide you on a step by step basis, on how to use and
SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTING SECURITY ENVIRONMENT
 SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTING SECURITY ENVIRONMENT K.karthika 1, M. Daya kanimozhi Rani 2 1 K.karthika, Assistant professor, Department of IT, Adhiyamaan College of Engineering, Hosur
SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTING SECURITY ENVIRONMENT K.karthika 1, M. Daya kanimozhi Rani 2 1 K.karthika, Assistant professor, Department of IT, Adhiyamaan College of Engineering, Hosur
Global UGRAD Program
 Application Instructions for Global UGRAD 2016-2017 Portal Step-by-Step I. REGISTERING FOR THE PROGRAM Google Chrome and Mozilla Firefox work best when completing the UGRAD application. We do NOT recommend
Application Instructions for Global UGRAD 2016-2017 Portal Step-by-Step I. REGISTERING FOR THE PROGRAM Google Chrome and Mozilla Firefox work best when completing the UGRAD application. We do NOT recommend
Remote Android Assistant with Global Positioning System Tracking
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. III (Mar-Apr. 2014), PP 95-99 Remote Android Assistant with Global Positioning System Tracking
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. III (Mar-Apr. 2014), PP 95-99 Remote Android Assistant with Global Positioning System Tracking
Provider OnLine. Log-In Guide
 Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
