SECURING SELF-SERVICE PASSWORD RESET
|
|
|
- Lorraine Lang
- 9 years ago
- Views:
Transcription
1 SECURING SELF-SERVICE PASSWORD RESET FUNCTIONALITY IN WEB APPLICATIONS David A. Shpritz July, 2010 INTRODUCTION Many web applications requiring user authentication also provide self-service password reset functionality to help reduce helpdesk calls and in turn support costs. However, sometimes this functionality can introduce new vulnerabilities into an application, allowing brute forcing, username harvesting harvesting or information disclosure and in some cases even exposing the password via web page or . This document aims to provide web application developers with a how to of sorts, providing a process which developers can use to implement password reset functionality into their web applications in a safe and secure manner by incorporating a series of best practices, as well as helping developers avoid pitfalls which have resulted in vulnerabilities in countless web applications. The first aspect to examine is what information will be required from the user. I will cover information needed from the user during the registration process, as well as the information the user will need to initiate the reset of their password. A NOTE ON THE RELIANCE ON The insecurity of is well known and while it is used in this process, it can also be excluded depending on the security posture of the application and organization. is used in this process as described below as a way of confirming the identity of the user as well as for transmission of temporary password reset links, but never the password itself, as the goal is to reset the password, not expose it. As many users will use the same password for multiple web applications, the potential exists that exposure of the existing password, via or display in a web page could compromise not only the user s account for your application, but other applications as well. An additional benefit of using the address currently stored for the user is that it helps form an additional factor for authentication and alerting for the user. As an alternative SMS messages could also be used to provide a token for the user to verify their identity, if the phone number for the SMS message is already being stored by the application. 1
2 SECRET QUESTIONS At registration an application can request that a user answer certain questions to which the answer would not be publicly available. As the answers to these questions are behaving as backup passwords it is important that the same care be used in selecting the questions as one would take in selecting passwords. Some systems will allow a user to craft their own questions, but in my experience this may not be a good idea as the user may select questions to which the answers are easily found. If the questions are hard coded into the application (I would suggest at least three, however it is important to keep in mind the security posture of the organization and application) then the selection of these questions must be taken into consideration. One option is to supply a number of questions which the user can select a few for use with their account. The goal is to make the answer to the question very precise, but at the same time make it very hard to guess. As an example, what is your favorite color, while very personal, does not have very many answers (there are about 100 common colors, and most likely the user would answer in the simplest form, so green, red, blue, knocking that range down even more), making it a poor choice for a question. On the other hand a question like What was the name of your first stuffed animal? has a great many answers, and is not easily guessed at. Additionally, the audience for the application should be taken into account, as a question may work for a user in the United States, but may not be answerable to users in Europe or Asia, and as such cultural differences should be taken into account. Another consideration is that you want to avoid questions which may result in storage of information which may contravene compliance mandates (such as questions relating to Social Security Numbers or Credit Card Numbers) under which your application may fall. In the Resources section you will find links to more information on selecting good security questions. As I mentioned above, these questions and answers are being used as a backup password, so the storage of them should be given the same level of care as the username and passwords for the application. WHAT DOES THE USER NEED TO START THE RESET PROCESS? In some situations the user can provide a username to start the process, while others will require the address for the account. In some situations a user may not remember the username they have on file, so an extra step may be added at the beginning to allow the user to enter an address to have the username on file for the address sent to them. A danger here is that this type of mechanism can turn into a method of harvesting addresses which are valid users of the system. To avoid this do not provide error messages which indicate that an address has a valid user or does not have a valid user. You should indicate that a message has been sent, and provide the error in the instead of on the web page. These types of notifications can also help act as an early warning as users may alert you that they have received notifications of attempts to retrieve their username, and as such it may be useful to also 2
3 include the IP address used for the request or a request ID which may allow you to track down requests which generated them. Another possible mitigation to this threat is using a CAPTCHA to make automated attacks against the system more difficult, however, CAPTCHA implementations and effectiveness vary. It should also be noted that CAPTCHAs are generally disliked by end users, so usability should be taken into consideration. Once a user knows the username for an account, the process to reset the password can begin. Notice that this is resetting the password, not providing it back to the user. In most web applications this may not even be possible if a one way hash is being used. A link is provided in the Resources section below for the OWASP Cryptographic Storage Cheat Sheet which contains guidance for the storage of passwords. ANSWERING QUESTIONS (STARTING THE PASSWORD RESET PROCESS) Once the user has obtained the username the reset process can begin. The user enters the username and address on file and then can be presented with one to three of the security questions selected at registration. The questions can be chosen at random from those stored for the user, and upon an unsuccessful attempt to answer them a different set should be presented. Again there is a danger here of brute forcing usernames or username harvesting, so care must be taken to prevent this. One strategy to prevent username harvesting is to use a tar pit of sorts. When an invalid username is entered, the application presents a set of fake security questions. When submitted, the application always indicates that the answers are incorrect. Keep in mind that while this may frustrate an attacker, it may also frustrate valid users, so developers will need to strike a balance between security and usability appropriate for the application. If multiple questions are used, it is also important to never indicate which answers are correct if any of the answers are wrong, as it allows an attacker to confirm information and drill down to one particular question. After a number of attempts (usually corresponding to the number of attempts used for account lockout functionality) the account should be locked out in similar fashion as failed login attempts. AFTER THE QUESTIONS HAVE BEEN ANSWERED SUCCESSFULLY After a user has succeeded in answering the security questions correctly, a unique link should be sent to the address on file for the user. This link should only be sent to the address on file rather than allowing the user to enter a new address to prevent an attacker from hijacking the account. The link should be unique (for example contain a unique token) to prevent the ability of an attacker to randomly guess at password reset URLs which would allow them to reset the passwords for users without going through the processes above. The link should also 3
4 expire after a short amount of time, preferably 48 hours or less to prevent someone from using an old link to reset a password. Once used, the link should expire as well to prevent reuse. There are some drawbacks to this approach, the main being a reliance on . If this is a concern, the sending of a reset link can be excluded and the user can move on to the process of selecting a new password. As mentioned above, it is possible to use SMS messages to previously known mobile phone numbers as another form of out-of-band verification. SELECTING A NEW PASSWORD Once the user has received the link and visited the page in the application for resetting the password, the link should be expired to prevent reuse. The password can then be reset by the user, applying the same controls in place for the initial password selection or password change process, ensuring that complexity and length requirements are met. AFTER THE PASSWORD HAS BEEN RESET After a new password has been selected a confirmation telling the user that the password has been reset can be displayed. Additionally a confirmation should also be sent to the address on file. This confirmation is used as a way to alert the user in the case that it is an attacker attempting to gain access to their account. After the password has been reset, do not instantly log the user in to the application but instead send them to the standard login page to attempt a login with their new password, providing a check that the user s password has been reset successfully. RESOURCES Below are resources which provide more information on designing and attacking password reset functionality in web applications, as well as suggestions for selecting secret questions for use in the process. Self-service password reset: Good Security Questions: How to Do Password Resets Right: Insecure Implementations Of Challenge Questions Answers (CQA) For Password Resets: Best Practices for Your Forgot Password Feature: ctices_v2.0.pdf 4
5 Testing for Vulnerable Remember Password and Pwd Reset (OWASP-AT-006): %28OWASP-AT-006%29 Authentication Cheat Sheet: Parola secreta?: Insufficient Password Recovery: Username Enumeration Vulnerabilities: Cryptographic Storage Cheat Sheet: Detecting Malice: ACKNOWLEDGEMENTS The author would like to thank the following for their contributions and review: Kees Leune Harry Woodward-Clarke LICENSE This work has been licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. More information is available at the following URL: 5
Application Security Testing. Generic Test Strategy
 Application Security Testing Generic Test Strategy Page 2 of 8 Contents 1 Introduction 3 1.1 Purpose: 3 1.2 Application Security Testing: 3 2 Audience 3 3 Test Strategy guidelines 3 3.1 Authentication
Application Security Testing Generic Test Strategy Page 2 of 8 Contents 1 Introduction 3 1.1 Purpose: 3 1.2 Application Security Testing: 3 2 Audience 3 3 Test Strategy guidelines 3 3.1 Authentication
Reset Virtual Gateway Password Job Aid
 Summary of Job Aid In order to access a Virtual Gateway s business service, you must first log on to the Virtual Gateway (VG). From the Virtual Gateway s website (www.mass.gov/vg), click Logon to Virtual
Summary of Job Aid In order to access a Virtual Gateway s business service, you must first log on to the Virtual Gateway (VG). From the Virtual Gateway s website (www.mass.gov/vg), click Logon to Virtual
Building Secure Multi-Factor Authentication
 Building Secure Multi-Factor Authentication Three best practices for engineering and product leaders Okta Inc. I 301 Brannan Street, Suite 300 I San Francisco CA, 94107 [email protected] I 1-888-722-7871 Introduction
Building Secure Multi-Factor Authentication Three best practices for engineering and product leaders Okta Inc. I 301 Brannan Street, Suite 300 I San Francisco CA, 94107 [email protected] I 1-888-722-7871 Introduction
BASELINE SECURITY TEST PLAN FOR EDUCATIONAL WEB AND MOBILE APPLICATIONS
 BASELINE SECURITY TEST PLAN FOR EDUCATIONAL WEB AND MOBILE APPLICATIONS Published by Tony Porterfield Feb 1, 2015. Overview The intent of this test plan is to evaluate a baseline set of data security practices
BASELINE SECURITY TEST PLAN FOR EDUCATIONAL WEB AND MOBILE APPLICATIONS Published by Tony Porterfield Feb 1, 2015. Overview The intent of this test plan is to evaluate a baseline set of data security practices
RFG Secure FTP. Web Interface
 RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
Topic: ACE Initial Account Access
 What s Inside: Account Creation Automatic e-mail Page 1 Password Retrieval Page 2 Initial Login Page 3 Creating New Password Page 4 Changing Password Page 6 Login Failure Page 6 Additional ACE Resources
What s Inside: Account Creation Automatic e-mail Page 1 Password Retrieval Page 2 Initial Login Page 3 Creating New Password Page 4 Changing Password Page 6 Login Failure Page 6 Additional ACE Resources
Criteria for web application security check. Version 2015.1
 Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Collaborate.ets.org Password Setup & Recovery Guide. Table of Contents
 MyPassword is a self-service password management tool. Collaborate.ets.org Password Setup & Recovery Guide https://mypassword.ets.org/ Table of Contents Create/Edit Your Profile (First time use)... I Change
MyPassword is a self-service password management tool. Collaborate.ets.org Password Setup & Recovery Guide https://mypassword.ets.org/ Table of Contents Create/Edit Your Profile (First time use)... I Change
Business ebanking - User Sign On & Set Up
 About Sign On Business ebanking has two authentication methods that reduce the risk of online identity theft: secure token authentication and out-of-band authentication. The authentication method companies
About Sign On Business ebanking has two authentication methods that reduce the risk of online identity theft: secure token authentication and out-of-band authentication. The authentication method companies
Kentico CMS security facts
 Kentico CMS security facts ELSE 1 www.kentico.com Preface The document provides the reader an overview of how security is handled by Kentico CMS. It does not give a full list of all possibilities in the
Kentico CMS security facts ELSE 1 www.kentico.com Preface The document provides the reader an overview of how security is handled by Kentico CMS. It does not give a full list of all possibilities in the
The Initial Registration Process. During the initial registration process, this guide assumes the user has been provided a login ID.
 eopf Account Guide The following processes are covered in this guide: Initial Registration Process (for new users) Forgotten Password Process Forgotten Login ID Process The Initial Registration Process
eopf Account Guide The following processes are covered in this guide: Initial Registration Process (for new users) Forgotten Password Process Forgotten Login ID Process The Initial Registration Process
The 10 step communication plan
 The 10 step communication plan Follow these 10 suggested steps and you will be successful at launching the Specops password reset service. Step 1 Activity: Intranet texts explaining the service Suggested
The 10 step communication plan Follow these 10 suggested steps and you will be successful at launching the Specops password reset service. Step 1 Activity: Intranet texts explaining the service Suggested
EUROPEAN COMMISSION Directorate-General for Education and Culture
 EUROPEAN COMMISSION Directorate-General for Education and Culture Lifelong Learning: policies and programme Coordination of the "Lifelong learning" programme ECAS User Manual The European Commission Authentication
EUROPEAN COMMISSION Directorate-General for Education and Culture Lifelong Learning: policies and programme Coordination of the "Lifelong learning" programme ECAS User Manual The European Commission Authentication
Self-Service Password Manager
 WWW.ROSE-HULMAN.EDU/EIT OFFICE OF ENTERPRISE INFORMATION TECHNOLOGY Self-Service Password Manager Rose-Hulman Institute of Technology has implemented a self-service password manager that provides an easy-to-use
WWW.ROSE-HULMAN.EDU/EIT OFFICE OF ENTERPRISE INFORMATION TECHNOLOGY Self-Service Password Manager Rose-Hulman Institute of Technology has implemented a self-service password manager that provides an easy-to-use
Flexible Identity. Tokenless authenticators guide. Multi-Factor Authentication. version 1.0
 Flexible Identity Multi-Factor Authentication Tokenless authenticators guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services
Flexible Identity Multi-Factor Authentication Tokenless authenticators guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services
Enhanced Security for Online Banking
 Enhanced Security for Online Banking MidSouth Bank is focused on protecting your personal and account information at all times. As instances of internet fraud increase, it is no longer sufficient to use
Enhanced Security for Online Banking MidSouth Bank is focused on protecting your personal and account information at all times. As instances of internet fraud increase, it is no longer sufficient to use
External Network & Web Application Assessment. For The XXX Group LLC October 2012
 External Network & Web Application Assessment For The XXX Group LLC October 2012 This report is solely for the use of client personal. No part of it may be circulated, quoted, or reproduced for distribution
External Network & Web Application Assessment For The XXX Group LLC October 2012 This report is solely for the use of client personal. No part of it may be circulated, quoted, or reproduced for distribution
Provider OnLine. Log-In Guide
 Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
EVALUATION GUIDE. Evaluating a Self-Service Password Reset Tool. Usability. The password reality
 EVALUATION GUIDE Evaluating a Self-Service Password Reset Tool This guide presents the criteria to consider when evaluating a self-service password reset solution and can be referenced for a new implementation
EVALUATION GUIDE Evaluating a Self-Service Password Reset Tool This guide presents the criteria to consider when evaluating a self-service password reset solution and can be referenced for a new implementation
KNPC esourcing Portal. Getting Started - Registration & Authentication. KNPC esourcing Registration & Authentication
 Getting Started - Registration & Authentication Supplier Registration & Authentication Process Any new Supplier (Local or International) who wishes to get Prequalified or participate in Tenders run by
Getting Started - Registration & Authentication Supplier Registration & Authentication Process Any new Supplier (Local or International) who wishes to get Prequalified or participate in Tenders run by
How Board Members and State Employees Utilize the Security Portal to Access PDMP. July 30, 2014 Version 2 Software Release Version 3.4.
 How Board Members and State Employees Utilize the Security Portal to Access PDMP July 30, 2014 Version 2 Software Release Version 3.4.11 Table of Contents How to Access PDMP via the ADPH Security Portal...
How Board Members and State Employees Utilize the Security Portal to Access PDMP July 30, 2014 Version 2 Software Release Version 3.4.11 Table of Contents How to Access PDMP via the ADPH Security Portal...
Information Security Basic Concepts
 Information Security Basic Concepts 1 What is security in general Security is about protecting assets from damage or harm Focuses on all types of assets Example: your body, possessions, the environment,
Information Security Basic Concepts 1 What is security in general Security is about protecting assets from damage or harm Focuses on all types of assets Example: your body, possessions, the environment,
How do I enroll in the password portal?
 The self-serve portal is designed to allow you to change your password and unlock your locked account even if you have forgotten your password. You must enroll for this service to be able to use it. You
The self-serve portal is designed to allow you to change your password and unlock your locked account even if you have forgotten your password. You must enroll for this service to be able to use it. You
Single Sign On: Volunteer Connection Support Tree for Administrators Release 2.0
 Single Sign On: Volunteer Connection Support Tree for Administrators Release 2.0 Updated 2/24/2016 Page 1 Single Sign On Volunteer Connection Support Tree for Administrators Purpose General Information
Single Sign On: Volunteer Connection Support Tree for Administrators Release 2.0 Updated 2/24/2016 Page 1 Single Sign On Volunteer Connection Support Tree for Administrators Purpose General Information
How to break in. Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering
 How to break in Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering Time Agenda Agenda Item 9:30 10:00 Introduction 10:00 10:45 Web Application Penetration
How to break in Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering Time Agenda Agenda Item 9:30 10:00 Introduction 10:00 10:45 Web Application Penetration
New Brunswick Internal Services Agency. RSA Self-Service Console User Guide
 New Brunswick Internal Services Agency RSA Self-Service Console User Guide Version: 1.0 Created: November 27, 2013 Modified: November 27, 2013 Table of Contents Introduction...1 Logging on to the RSA Self-Service
New Brunswick Internal Services Agency RSA Self-Service Console User Guide Version: 1.0 Created: November 27, 2013 Modified: November 27, 2013 Table of Contents Introduction...1 Logging on to the RSA Self-Service
Is Drupal secure? A high-level perspective on web vulnerabilities, Drupal s solutions, and how to maintain site security
 Is Drupal secure? A high-level perspective on web vulnerabilities, Drupal s solutions, and how to maintain site security Presented 2009-05-29 by David Strauss Thinking Securely Security is a process, not
Is Drupal secure? A high-level perspective on web vulnerabilities, Drupal s solutions, and how to maintain site security Presented 2009-05-29 by David Strauss Thinking Securely Security is a process, not
Idaho Letter of Intent for 2015 MeF
 Overview Industry Trusted Customer Requirements Idaho Letter of Intent for 2015 MeF The industry, state and IRS partners recognize that even though fraud filings will still occur, we all must be proactive
Overview Industry Trusted Customer Requirements Idaho Letter of Intent for 2015 MeF The industry, state and IRS partners recognize that even though fraud filings will still occur, we all must be proactive
HertSFX. User Guide V2.04. Hertfordshire s Secure File Exchange Portal. (Jan 2014) HertSFX User Guide V2.04 Jan 2014 Page 1 of 17
 Hertfordshire s Secure File Exchange Portal User Guide V2.04 (Jan 2014) HertSFX User Guide V2.04 Jan 2014 Page 1 of 17 CONTENTS 1. About HertSFX... 3 2. HertSFX Limitations... 3 3. Getting Started... 3
Hertfordshire s Secure File Exchange Portal User Guide V2.04 (Jan 2014) HertSFX User Guide V2.04 Jan 2014 Page 1 of 17 CONTENTS 1. About HertSFX... 3 2. HertSFX Limitations... 3 3. Getting Started... 3
Personal Online Banking & Bill Pay. Guide to Getting Started
 Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
LockoutGuard v1.2 Documentation
 LockoutGuard v1.2 Documentation (The following graphics are screen shots from Microsoft ISA Server and Threat Management Gateway which are the property of Microsoft Corp. and are included here for instructive
LockoutGuard v1.2 Documentation (The following graphics are screen shots from Microsoft ISA Server and Threat Management Gateway which are the property of Microsoft Corp. and are included here for instructive
IDRBT Working Paper No. 11 Authentication factors for Internet banking
 IDRBT Working Paper No. 11 Authentication factors for Internet banking M V N K Prasad and S Ganesh Kumar ABSTRACT The all pervasive and continued growth being provided by technology coupled with the increased
IDRBT Working Paper No. 11 Authentication factors for Internet banking M V N K Prasad and S Ganesh Kumar ABSTRACT The all pervasive and continued growth being provided by technology coupled with the increased
How To Use Turna 4Europe Online Education And Training Programmes Online (Eu)
 Carries your information globally USER MANUAL v.2.0 2 TABLE OF CONTENTS TABLE OF CONTENTS... 2 LIST OF FIGURES... 3 1. PURPOSE... 4 2. TURNA... 4 3. TURNA USER INTERFACE... 4 3.1 TURNA Login Page... 4
Carries your information globally USER MANUAL v.2.0 2 TABLE OF CONTENTS TABLE OF CONTENTS... 2 LIST OF FIGURES... 3 1. PURPOSE... 4 2. TURNA... 4 3. TURNA USER INTERFACE... 4 3.1 TURNA Login Page... 4
PrimeSecure Self-Service User Guide Revision 1.2
 PrimeSecure Self-Service User Guide Revision 1.2 1 Table of Contents 1.0 Introduction... 3 2.0 Register with PrimeSecure... 3 3.0 Changing your Password... 6 4.0 Resetting your Password... 8 5.0 Updating
PrimeSecure Self-Service User Guide Revision 1.2 1 Table of Contents 1.0 Introduction... 3 2.0 Register with PrimeSecure... 3 3.0 Changing your Password... 6 4.0 Resetting your Password... 8 5.0 Updating
Where every interaction matters.
 Where every interaction matters. Peer 1 Vigilant Web Application Firewall Powered by Alert Logic The Open Web Application Security Project (OWASP) Top Ten Web Security Risks and Countermeasures White Paper
Where every interaction matters. Peer 1 Vigilant Web Application Firewall Powered by Alert Logic The Open Web Application Security Project (OWASP) Top Ten Web Security Risks and Countermeasures White Paper
Users Guide to Internet Banking Self Service Enrollment
 Users Guide to Internet Banking Self Service Enrollment This document is a guide for customers who wish to use The Bank of Greene County s Self Service Enrollment Utility for Internet Banking The following
Users Guide to Internet Banking Self Service Enrollment This document is a guide for customers who wish to use The Bank of Greene County s Self Service Enrollment Utility for Internet Banking The following
Welcome Guide for MP-1 Token for Microsoft Windows
 Welcome Guide for MP-1 Token for Microsoft Windows Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights reserved. All attempts have been made
Welcome Guide for MP-1 Token for Microsoft Windows Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights reserved. All attempts have been made
Using YSU Password Self-Service
 Using YSU Password Self-Service Using YSU Password Self-Service Password Self-Service Web Interface Required Items: YSU (MyYSU) Directory account, Web browser This guide will assist you with using the
Using YSU Password Self-Service Using YSU Password Self-Service Password Self-Service Web Interface Required Items: YSU (MyYSU) Directory account, Web browser This guide will assist you with using the
How Do I Status My Vendor-Owned Resources in ROSS?
 Page: 1 How Do I Status My Vendor-Owned Resources in ROSS? What do I need to do? How do I do that? 1. Request a new vendor user account Page 2. - Access the NAP environment at https://nap.nwcg.gov/nap/
Page: 1 How Do I Status My Vendor-Owned Resources in ROSS? What do I need to do? How do I do that? 1. Request a new vendor user account Page 2. - Access the NAP environment at https://nap.nwcg.gov/nap/
The City of New York
 The Policy All passwords and personal identification numbers (PINs) used to protect City of New York systems shall be appropriately configured, periodically changed, and issued for individual use. Scope
The Policy All passwords and personal identification numbers (PINs) used to protect City of New York systems shall be appropriately configured, periodically changed, and issued for individual use. Scope
NCUSD 203 Campus Portal Login FAQ
 This document will provide you answers to all of your questions regarding setting up and troubleshooting issues with your Campus Portal Login Account. Please see the list of frequently questions below.
This document will provide you answers to all of your questions regarding setting up and troubleshooting issues with your Campus Portal Login Account. Please see the list of frequently questions below.
Contents. Identity Assurance (Scott Rea Dartmouth College) IdM Workshop, Brisbane Australia, August 19, 2008
 Identity Assurance (Scott Rea Dartmouth College) IdM Workshop, Brisbane Australia, August 19, 2008 Contents Authentication and Identity Assurance The Identity Assurance continuum Plain Password Authentication
Identity Assurance (Scott Rea Dartmouth College) IdM Workshop, Brisbane Australia, August 19, 2008 Contents Authentication and Identity Assurance The Identity Assurance continuum Plain Password Authentication
User Guide for CDC s SAMS Partner Portal. Document Version 1.0
 User Guide for CDC s SAMS Partner Portal Document Version 1.0 Introduction If you are reading this guide, it probably means that you have been (or will be) invited to register with the SAMS Partner Portal.
User Guide for CDC s SAMS Partner Portal Document Version 1.0 Introduction If you are reading this guide, it probably means that you have been (or will be) invited to register with the SAMS Partner Portal.
ACH Alert Positive. User Guide Client Security
 ACH Alert Positive Pay User Guide Client Security 1 TABLE OF CONTENTS Client Security... 2 Initial Login.... 2 Login............................................................... 6 Forgot Password...
ACH Alert Positive Pay User Guide Client Security 1 TABLE OF CONTENTS Client Security... 2 Initial Login.... 2 Login............................................................... 6 Forgot Password...
How To Secure An Emr-Link System Architecture
 EMR-Link Security Administration Guide Introduction This guide provides an overview of the security measures built into EMR-Link, and how your organization s security policies can be implemented with these
EMR-Link Security Administration Guide Introduction This guide provides an overview of the security measures built into EMR-Link, and how your organization s security policies can be implemented with these
SECURING YOUR REMOTE DESKTOP CONNECTION
 White Paper SECURING YOUR REMOTE DESKTOP CONNECTION HOW TO PROPERLY SECURE REMOTE ACCESS 2015 SecurityMetrics SECURING YOUR REMOTE DESKTOP CONNECTION 1 SECURING YOUR REMOTE DESKTOP CONNECTION HOW TO PROPERLY
White Paper SECURING YOUR REMOTE DESKTOP CONNECTION HOW TO PROPERLY SECURE REMOTE ACCESS 2015 SecurityMetrics SECURING YOUR REMOTE DESKTOP CONNECTION 1 SECURING YOUR REMOTE DESKTOP CONNECTION HOW TO PROPERLY
Portal Administration. Administrator Guide
 Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Business Banking Customer Login Experience for Enhanced Login Security
 Business Banking Customer Login Experience for Enhanced Login Security User credentials uniquely identify each person who uses the banking platform. The intent of authentication is unequivocal verification
Business Banking Customer Login Experience for Enhanced Login Security User credentials uniquely identify each person who uses the banking platform. The intent of authentication is unequivocal verification
EJGH Email Encryption User Tip Sheet 10-11-2013 1 of 8
 EJGH Email Encryption User Tip Sheet 10-11-2013 1 of 8 External Users Decrypting Secure Messages The following sections describe how users external to EJGH receive and decrypt secure messages. Reading
EJGH Email Encryption User Tip Sheet 10-11-2013 1 of 8 External Users Decrypting Secure Messages The following sections describe how users external to EJGH receive and decrypt secure messages. Reading
Windows Operating Systems. Basic Security
 Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Windows Operating Systems Basic Security Objectives Explain Windows Operating System (OS) common configurations Recognize OS related threats Apply major steps in securing the OS Windows Operating System
Penetration Testing: Lessons from the Field
 Penetration Testing: Lessons from the Field CORE SECURITY TECHNOLOGIES SCS SERVICES May 2009 1 Agenda: About me: Alberto Soliño Director of Security Consulting Services at Core Security One of first five
Penetration Testing: Lessons from the Field CORE SECURITY TECHNOLOGIES SCS SERVICES May 2009 1 Agenda: About me: Alberto Soliño Director of Security Consulting Services at Core Security One of first five
FINRA DR Portal. User Guide for Arbitration and Mediation Case Participants
 FINRA DR Portal for Arbitration and Mediation Case Participants December 2015 Disclaimer These materials are for training and instructional purposes only. No part of this publication may be reproduced,
FINRA DR Portal for Arbitration and Mediation Case Participants December 2015 Disclaimer These materials are for training and instructional purposes only. No part of this publication may be reproduced,
Experian Username and Password Self Service Facility. User Guide
 Experian Username and Password Self Service Facility User Guide Contents 1 Document Control... 3 1.1 Version Control... 3 1.2 Document History... 3 2 New Users... 4 2.1 How to setup your security profile...
Experian Username and Password Self Service Facility User Guide Contents 1 Document Control... 3 1.1 Version Control... 3 1.2 Document History... 3 2 New Users... 4 2.1 How to setup your security profile...
DPH TOKEN SELF SERVICE SITE INSTRUCTIONS:
 DPH TOKEN SELF SERVICE SITE INSTRUCTIONS: The purpose of this document is to provide users with assistance on resolving connection issues with Department of Public Health (DPH) Entrust tokens. These instructions
DPH TOKEN SELF SERVICE SITE INSTRUCTIONS: The purpose of this document is to provide users with assistance on resolving connection issues with Department of Public Health (DPH) Entrust tokens. These instructions
Nessus Cloud User Registration
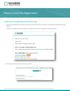 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
NU SSO Account Activation Job Aid NU Employees
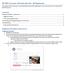 The purpose of this document is to provide National University Single Sign On users with instructions to activate their NU SSO accounts. Contents Employee Activation Self service... 1 Logging in directly...
The purpose of this document is to provide National University Single Sign On users with instructions to activate their NU SSO accounts. Contents Employee Activation Self service... 1 Logging in directly...
Web Application Guidelines
 Web Application Guidelines Web applications have become one of the most important topics in the security field. This is for several reasons: It can be simple for anyone to create working code without security
Web Application Guidelines Web applications have become one of the most important topics in the security field. This is for several reasons: It can be simple for anyone to create working code without security
Remote Access Password Tips
 Introduction: The following document was created to assist Remote Access users with password change and synchronization issues. IT&S has identified the following five (5) scenarios for remote access password
Introduction: The following document was created to assist Remote Access users with password change and synchronization issues. IT&S has identified the following five (5) scenarios for remote access password
Vendor User Accounts managing your NAP User Account
 This guide explains how to request and manage your NAP User Account so that you may access Web Status. Topics include: Reactivating an existing NAP User Account Requesting a NAP User Account Managing your
This guide explains how to request and manage your NAP User Account so that you may access Web Status. Topics include: Reactivating an existing NAP User Account Requesting a NAP User Account Managing your
Global UGRAD Program
 Application Instructions for Global UGRAD 2016-2017 Portal Step-by-Step I. REGISTERING FOR THE PROGRAM Google Chrome and Mozilla Firefox work best when completing the UGRAD application. We do NOT recommend
Application Instructions for Global UGRAD 2016-2017 Portal Step-by-Step I. REGISTERING FOR THE PROGRAM Google Chrome and Mozilla Firefox work best when completing the UGRAD application. We do NOT recommend
SJC Password Self-Service System FAQ 2012
 The San Jacinto College Password Self-Service System enables students to reset their password quickly and conveniently online. By utilizing this service, you can change your password and gain access to
The San Jacinto College Password Self-Service System enables students to reset their password quickly and conveniently online. By utilizing this service, you can change your password and gain access to
National Cyber Security Month 2015: Daily Security Awareness Tips
 National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
Security vulnerabilities in new web applications. Ing. Pavol Lupták, CISSP, CEH Lead Security Consultant
 Security vulnerabilities in new web applications Ing. Pavol Lupták, CISSP, CEH Lead Security Consultant $whoami Introduction Pavol Lupták 10+ years of practical experience in security and seeking vulnerabilities
Security vulnerabilities in new web applications Ing. Pavol Lupták, CISSP, CEH Lead Security Consultant $whoami Introduction Pavol Lupták 10+ years of practical experience in security and seeking vulnerabilities
! Resident of Kauai, Hawaii
 SECURE SDLC Jim Manico @manicode! OWASP Volunteer! Global OWASP Board Member! Manager of several OWASP secure coding projects! Security Instructor, Author! 17 years of web-based, databasedriven software
SECURE SDLC Jim Manico @manicode! OWASP Volunteer! Global OWASP Board Member! Manager of several OWASP secure coding projects! Security Instructor, Author! 17 years of web-based, databasedriven software
Did you know your security solution can help with PCI compliance too?
 Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
Identity as a Service Powered by NetIQ IdentityAccess Service Configuration and Administration Guide
 Identity as a Service Powered by NetIQ IdentityAccess Service Configuration and Administration Guide December 2015 www.netiq.com/documentation Legal Notice For information about NetIQ legal notices, disclaimers,
Identity as a Service Powered by NetIQ IdentityAccess Service Configuration and Administration Guide December 2015 www.netiq.com/documentation Legal Notice For information about NetIQ legal notices, disclaimers,
BlackShield Authentication Service
 BlackShield Authentication Service Guide for Users of CRYPTOCard MP-1 Software Tokens on Smart Phones Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright Copyright 2011.
BlackShield Authentication Service Guide for Users of CRYPTOCard MP-1 Software Tokens on Smart Phones Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright Copyright 2011.
Columbia University Web Security Standards and Practices. Objective and Scope
 Columbia University Web Security Standards and Practices Objective and Scope Effective Date: January 2011 This Web Security Standards and Practices document establishes a baseline of security related requirements
Columbia University Web Security Standards and Practices Objective and Scope Effective Date: January 2011 This Web Security Standards and Practices document establishes a baseline of security related requirements
Secure Email Actions for Email Recipients
 Secure Email Actions for Email Recipients Actions for Email Recipients The recipient cannot forward encrypted email outside the secure system. Each email will only be available to the recipient for 30
Secure Email Actions for Email Recipients Actions for Email Recipients The recipient cannot forward encrypted email outside the secure system. Each email will only be available to the recipient for 30
Administrator's Guide
 Administrator's Guide Copyright SecureAnywhere Mobile Protection Administrator's Guide November, 2012 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere
Administrator's Guide Copyright SecureAnywhere Mobile Protection Administrator's Guide November, 2012 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere
The Real State of WiFi Security in the Connected Home August 25, 2015
 The Real State of WiFi Security in the Connected Home August 25, 2015 1 Abstract Analyzing real-world data can teach us about the state of security in the connected home. RouterCheck, a tool for testing
The Real State of WiFi Security in the Connected Home August 25, 2015 1 Abstract Analyzing real-world data can teach us about the state of security in the connected home. RouterCheck, a tool for testing
Business Online Banking & Bill Pay Guide to Getting Started
 Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Security Information Management System
 Commonwealth of Kentucky Security Information Management System User Guide Release 1.8 February 2016 DISCLAIMER: The Commonwealth is in process of securing a service to allow use of mobile phone numbers
Commonwealth of Kentucky Security Information Management System User Guide Release 1.8 February 2016 DISCLAIMER: The Commonwealth is in process of securing a service to allow use of mobile phone numbers
Host Hardening. Presented by. Douglas Couch & Nathan Heck Security Analysts for ITaP 1
 Host Hardening Presented by Douglas Couch & Nathan Heck Security Analysts for ITaP 1 Background National Institute of Standards and Technology Draft Guide to General Server Security SP800-123 Server A
Host Hardening Presented by Douglas Couch & Nathan Heck Security Analysts for ITaP 1 Background National Institute of Standards and Technology Draft Guide to General Server Security SP800-123 Server A
AD Self Password Reset Installation and configuration
 AD Self Password Reset Installation and configuration AD Self Password Reset Installation 1 Manual v1.4 Table of Contents TABLE OF CONTENTS 2 SUMMARY 3 INSTALLATION 4 REMOVAL 6 AD SELF PASSWORD RESET CONFIGURATION
AD Self Password Reset Installation and configuration AD Self Password Reset Installation 1 Manual v1.4 Table of Contents TABLE OF CONTENTS 2 SUMMARY 3 INSTALLATION 4 REMOVAL 6 AD SELF PASSWORD RESET CONFIGURATION
Columbia University Web Application Security Standards and Practices. Objective and Scope
 Columbia University Web Application Security Standards and Practices Objective and Scope Effective Date: January 2011 This Web Application Security Standards and Practices document establishes a baseline
Columbia University Web Application Security Standards and Practices Objective and Scope Effective Date: January 2011 This Web Application Security Standards and Practices document establishes a baseline
NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS
 NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS Scope and Applicability: These Network and Certificate System Security Requirements (Requirements) apply to all publicly trusted Certification Authorities
NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS Scope and Applicability: These Network and Certificate System Security Requirements (Requirements) apply to all publicly trusted Certification Authorities
Provider Express Obtaining Login Access. Information for Network Providers
 Provider Express Obtaining Login Access Information for Network Providers November 2013 Objectives This presentation will review the following features: How to Log in to Provider Express Retrieve a forgotten
Provider Express Obtaining Login Access Information for Network Providers November 2013 Objectives This presentation will review the following features: How to Log in to Provider Express Retrieve a forgotten
Dynamic Query Updation for User Authentication in cloud Environment
 Dynamic Query Updation for User Authentication in cloud Environment Gaurav Shrivastava 1, Dr. S. Prabakaran 2 1 Research Scholar, Department of Computer Science, SRM University, Kattankulathur, Tamilnadu,
Dynamic Query Updation for User Authentication in cloud Environment Gaurav Shrivastava 1, Dr. S. Prabakaran 2 1 Research Scholar, Department of Computer Science, SRM University, Kattankulathur, Tamilnadu,
Advanced Settings. Help Documentation
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Check list for web developers
 Check list for web developers Requirement Yes No Remarks 1. Input Validation 1.1) Have you done input validation for all the user inputs using white listing and/or sanitization? 1.2) Does the input validation
Check list for web developers Requirement Yes No Remarks 1. Input Validation 1.1) Have you done input validation for all the user inputs using white listing and/or sanitization? 1.2) Does the input validation
How to login with the RSA Token?
 How to login with the RSA Token? How does the RSA Token work? To log on to your online trading account, you need to enter your existing username and password as usual, followed by the unique security code
How to login with the RSA Token? How does the RSA Token work? To log on to your online trading account, you need to enter your existing username and password as usual, followed by the unique security code
STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON
 STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON 1. Registering with Sabarimala Virtual Q Portal A user can register into the site after a few easy steps. A user needs to register with the site to be
STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON 1. Registering with Sabarimala Virtual Q Portal A user can register into the site after a few easy steps. A user needs to register with the site to be
Flexible Identity. OTP software tokens guide. Multi-Factor Authentication. version 1.0
 Flexible Identity Multi-Factor Authentication OTP software tokens guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services 2 of
Flexible Identity Multi-Factor Authentication OTP software tokens guide version 1.0 Publication History Date Description Revision 2014.02.07 initial release 1.0 Copyright Orange Business Services 2 of
SELF SERVICE RESET PASSWORD MANAGEMENT ADMINISTRATOR'S GUIDE
 SELF SERVICE RESET PASSWORD MANAGEMENT ADMINISTRATOR'S GUIDE Copyright 1998-2015 Tools4ever B.V. All rights reserved. No part of the contents of this user guide may be reproduced or transmitted in any
SELF SERVICE RESET PASSWORD MANAGEMENT ADMINISTRATOR'S GUIDE Copyright 1998-2015 Tools4ever B.V. All rights reserved. No part of the contents of this user guide may be reproduced or transmitted in any
Using Foundstone CookieDigger to Analyze Web Session Management
 Using Foundstone CookieDigger to Analyze Web Session Management Foundstone Professional Services May 2005 Web Session Management Managing web sessions has become a critical component of secure coding techniques.
Using Foundstone CookieDigger to Analyze Web Session Management Foundstone Professional Services May 2005 Web Session Management Managing web sessions has become a critical component of secure coding techniques.
Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device
 Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device Jyoti Rao *1,Kishan Mistry #2, Bhumika Mistry #3, Divya Malviya #4, Devesh Gudway #5 # Student & Department
Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device Jyoti Rao *1,Kishan Mistry #2, Bhumika Mistry #3, Divya Malviya #4, Devesh Gudway #5 # Student & Department
CAPITAL UNIVERSITY PASSWORD POLICY
 1.0 Overview Passwords are an important aspect of computer security. They are the front line of protection for user accounts. A poorly chosen password may result in the compromise of Capital University's
1.0 Overview Passwords are an important aspect of computer security. They are the front line of protection for user accounts. A poorly chosen password may result in the compromise of Capital University's
CSOS Certificate Support Guide. Version: 1.1 Published: October 1, 2006 Publisher: CSOS Certification Authority
 Version: 1.1 Published: October 1, 2006 Publisher: CSOS Certification Authority Document Revision History Version # Revision Sections Summary of Changes Initials Date Affected 1.0 4/27/2006 All Version
Version: 1.1 Published: October 1, 2006 Publisher: CSOS Certification Authority Document Revision History Version # Revision Sections Summary of Changes Initials Date Affected 1.0 4/27/2006 All Version
When you are prompted to enroll, you will be asked to enter a Security Phrase and select/answer three different Challenge Questions.
 IMPORTANT SECURITY INFORMATION We take your online security seriously. Your online banking site contains a security feature called Enhanced Authentication. Everyone will be required to enroll in Enhanced
IMPORTANT SECURITY INFORMATION We take your online security seriously. Your online banking site contains a security feature called Enhanced Authentication. Everyone will be required to enroll in Enhanced
How to set up your NMC Online account. How to set up your NMC Online account
 How to set up your NMC Online account 1 Introduction NMC Online is a secure service which allows you to manage your registration with us online. This guidance explains how you can set up your account.
How to set up your NMC Online account 1 Introduction NMC Online is a secure service which allows you to manage your registration with us online. This guidance explains how you can set up your account.
