Best practices and use cases for consistent, enterprise-wide SIEM security policy management
|
|
|
- Frank Bradford
- 10 years ago
- Views:
Transcription
1 Best practices and use cases for consistent, enterprise-wide SIEM security policy management Bhavika Kothari, QA Lead Victor Lee, Product Manager, CISSP
2 Agenda Introduction Best practices Management tool Use cases Discussion and Q&A 2
3 Introduction
4 HP ArcSight Next Generation Cyber Defense Visualize Search Predict SIEM Analytics Collect Respond Correlate 4
5 Introduction Why is manageability important for security? Ensure security policies are Followed And Enforced Manage the deployment holistically and not just individual elements Monitor, create alert, and maintain the security operations Deliver efficient and timely implementation Enable resources to focus on security analysis 5
6 Best practices
7 Best practice Create Golden Configuration Create Groups Monitor critical events and set alerts Update to the latest ArcSight product release ASAP Backup regularly Review and audit changes Leverage the ArcSight user community in Protect724 7
8 Management tool
9 Management tool What are the benefits of using management tools? Reduce cost Faster and reliable implementation of security policy Increase accuracy Enable resource to focus on security analytics What is the name of the ArcSight management tool? ArcSight Management Center 9
10 HP ArcSight Management Center ArcSight Management Center (ArcMC) delivers centralized enterprise management that simplifies the deployment and maintenance of the desired enterprise security posture in a cost effective and efficient manner. 10
11 ArcSight Management Center (ArcMC) ArcMC Version 2.0 ArcMC ArcMC ConApp Connector Logger 11
12 A few definitions A host is a system that hosts at least on ArcSight product A node is a managed ArcSight product Connector Connector appliance ArcSight Management Center Logger Node can be software or hardware form factor A configuration listed in ArcMC is considered a golden configuration Subscriber are the nodes which can receive the golden configuration. When subscriber s configuration is identical to the golden configuration, it is considered compliant. Otherwise, it is non-compliant. 12
13 ArcMC architecture HTTPs Host 1 ArcMC Agent Logger (SW, Appliance) Client ArcMC Web Client Server ArcMC HTTPs Host 2 ArcMC Agent ArcMC/ConApp (SW, Appliance) Connector Host 3 CWSAPI Connector Connector 13
14 Use cases Configuration management Management using groups Update to the latest Software Monitoring
15 Use cases Configuration management
16 ArcMC paradigm of operation Step 1 Create/import configuration in ArcMC Step 2 Add subscribers to the configuration Step 3 Push configuration to subscribers Step 4 Check compliance 16
17 Use cases Configuration Management 17
18 Use case: Schedule regular configuration backup Configure all the appliances to do backup on same schedule, i.e., every Saturday at 10 p.m. ArcMC 18
19 Use case: Logger filters Logger Filter Add new filter query - Create filters once on one Logger and wants to have the same filters on the rest of Loggers w/o re-creating them on other Loggers ArcMC 19
20 Use case: User management Add new employee - Create the same users on all the Appliances, software or hardware form factor Add new appliances, for example multiple ArcMC or multiple Loggers need to add existing users to the new appliances. ArcMC Software Connector Appliances, logger and ArcMC 20 Connector Appliances, ArcMC, Logger
21 Use case: Window Unified Connector configuration Software Connector HP ArcSight HP ArcSight Push Window Unified Connector configuration to multiple Window Unified Connectors (WUC) HP ArcSight Run compliance check to ensure the configurations are indeed on the SmartConnectors ArcMC 21 Connector Appliances
22 Use case: DNS Management DNS server Add a new DNS server across all ArcSight Appliances Add a new DNS server to a logical group by location or function ArcMC 22
23 Use case: Compliance check X Is my environment compliant with FIPS? Compliance check can be extended, for example, Is the configuration compliant with the baseline golden configuration? following the corporate policy? ArcMC ArcSight ArcSight X X ArcSight ArcSight ArcSight ArcSight X 23
24 Supported Logger configurations Logger Logger Configuration Backup Logger Smart Message Receiver Logger Transport Receiver Logger Storage Group Logger Filter 24
25 Supported Connector and ConApp and ArcMC configurations Connectors FIPS Map Files Parser Override Syslog Connector Window Unified Connector Bluecoat Connector Appliance and ArcMC Conapp/ArcMC Configuration Backup 25
26 Supported System Admin configurations Software Authentication External Authentication Local Password Authentication Session User Configuration SMTP Hardware DNS NTP Network SNMP 26
27 Use cases Management using groups
28 Bulk add host- Import hosts Allows adding hosts in bulk from a Comma Separated Values (.csv) file Background batch job Requirement:.csv file with valid host entries Results of import hosts job will be stored in a text file at <install_dir>/userdata/arcmc/importhosts/ 28
29 Create CSV File for bulk add host 29
30 Bulk add host using import CSV Import Host CSV File 30
31 ArcMC node management A node is a managed ArcSight product Connector Connector Appliance Logger ArcMC Nodes can be software or hardware form factor 31
32 Use cases Update to the latest software
33 Use case: Update software to the latest release New ArcSight software release - Push new versions of software to connectors, ArcMC appliances and logger appliances. HP ArcSight HP ArcSight HP ArcSight ArcMC 33
34 Demo Update software to the latest release 34
35 Use cases Monitoring
36 Monitoring nodes ArcMC 2.0 will support monitoring for Connector Appliance (hardware and software) Logger Appliance (hardware and software) Local and Managed ArcMCs (hardware and software) Smart Connectors 36
37 Health data monitored ArcMC collects health data from managed products in 1-min, 5-min and 1-hour time intervals to support charting and alert generation. CPU Memory Disk Network EPS In/Out Event and Queue Stats Thread Count Fan, Voltage, Power Supply, Temperature, RAID 37
38 Critical alert generation Breach rules are defined to generate alerts against health data metrics. Example: Generate a FATAL alert for any Logger whose average CPU usage in the past 5 minutes is greater than 90% breach.rule[1].product = LOGGER breach.rule[1].severity = FATAL breach.rule[1].metric = CPU breach.rule[1].aggregation = AVG breach.rule[1].measurement = GREATER breach.rule[1].value = 90 breach.rule[1].timespan = 5 38
39 Monitoring levels Summary Displays alerts / breaches across all the managed products Displays per product severity / alert pie charts 39
40 Monitoring levels Aggregated per managed product Displays alert / breaches of particular product type 40
41 Monitoring levels Individual product Displays alert / breaches on a managed node Displays different health monitor stats (EPS In/ Out, CPU, Memory Utilization, Hardware Stats) 41
42 Discussion and Q&A
43 For more information Attend these sessions TB3067, Connector Appliance Migration to ArcSight Management Center Visit these demos HP ArcSight demo station HP ArcSight Management Center demo station After the event Contact your sales rep Presentations will be posted after Protect at munity/events/protectconference 43
44 Please give me your feedback Session TB3133 Speakers Victor Lee and Bhavika Kothari Please fill out a survey. Hand it to the door monitor on your way out. Thank you for providing your feedback, which helps us enhance content for future events. 44
45 Thank you
46
Security Analytics Topology
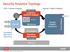 Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
SOFTNIX LOGGER Centralized Logs Management
 SOFTNIX LOGGER Centralized Logs Management STANDARD, RELIABLE, SECURITY Softnix Logger Our goal is not only regulate data follow by cyber law but also focus on the most significant such as to storage data
SOFTNIX LOGGER Centralized Logs Management STANDARD, RELIABLE, SECURITY Softnix Logger Our goal is not only regulate data follow by cyber law but also focus on the most significant such as to storage data
MySQL Enterprise Monitor
 MySQL Enterprise Monitor Lynn Ferrante Principal Sales Consultant 1 Program Agenda MySQL Enterprise Monitor Overview Architecture Roles Demo 2 Overview 3 MySQL Enterprise Edition Highest Levels of Security,
MySQL Enterprise Monitor Lynn Ferrante Principal Sales Consultant 1 Program Agenda MySQL Enterprise Monitor Overview Architecture Roles Demo 2 Overview 3 MySQL Enterprise Edition Highest Levels of Security,
Best of Breed of an ITIL based IT Monitoring. The System Management strategy of NetEye
 Best of Breed of an ITIL based IT Monitoring The System Management strategy of NetEye by Georg Kostner 5/11/2012 1 IT Services and IT Service Management IT Services means provisioning of added value for
Best of Breed of an ITIL based IT Monitoring The System Management strategy of NetEye by Georg Kostner 5/11/2012 1 IT Services and IT Service Management IT Services means provisioning of added value for
SIEM Optimization 101. ReliaQuest E-Book Fully Integrated and Optimized IT Security
 SIEM Optimization 101 ReliaQuest E-Book Fully Integrated and Optimized IT Security Introduction SIEM solutions are effective security measures that mitigate security breaches and increase the awareness
SIEM Optimization 101 ReliaQuest E-Book Fully Integrated and Optimized IT Security Introduction SIEM solutions are effective security measures that mitigate security breaches and increase the awareness
Towards Smart and Intelligent SDN Controller
 Towards Smart and Intelligent SDN Controller - Through the Generic, Extensible, and Elastic Time Series Data Repository (TSDR) YuLing Chen, Dell Inc. Rajesh Narayanan, Dell Inc. Sharon Aicler, Cisco Systems
Towards Smart and Intelligent SDN Controller - Through the Generic, Extensible, and Elastic Time Series Data Repository (TSDR) YuLing Chen, Dell Inc. Rajesh Narayanan, Dell Inc. Sharon Aicler, Cisco Systems
Configuring an ArcSight Smart- Connector to collect events from Kaspersky Admin Kit 8.0
 Configuring an ArcSight Smart- Connector to collect events from Kaspersky Admin Kit 8.0 As part of a comprehensive security monitoring program, many organizations have deployed Security Information Event
Configuring an ArcSight Smart- Connector to collect events from Kaspersky Admin Kit 8.0 As part of a comprehensive security monitoring program, many organizations have deployed Security Information Event
Minder. simplifying IT. All-in-one solution to monitor Network, Server, Application & Log Data
 Minder simplifying IT All-in-one solution to monitor Network, Server, Application & Log Data Simplify the Complexity of Managing Your IT Environment... To help you ensure the availability and performance
Minder simplifying IT All-in-one solution to monitor Network, Server, Application & Log Data Simplify the Complexity of Managing Your IT Environment... To help you ensure the availability and performance
What s New in Security Analytics 10.4. Be the Hunter.. Not the Hunted
 What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
XpoLog Center Suite Log Management & Analysis platform
 XpoLog Center Suite Log Management & Analysis platform Summary: 1. End to End data management collects and indexes data in any format from any machine / device in the environment. 2. Logs Monitoring -
XpoLog Center Suite Log Management & Analysis platform Summary: 1. End to End data management collects and indexes data in any format from any machine / device in the environment. 2. Logs Monitoring -
Using Windows Event Forwarding with the Windows Unified Connector
 Using Windows Event Forwarding with the Windows Unified Connector Steve Maxwell, Solutions Architect #HPProtect Agenda What is Windows Event Forwarding? How does HP ArcSight work with Windows Event Forwarding?
Using Windows Event Forwarding with the Windows Unified Connector Steve Maxwell, Solutions Architect #HPProtect Agenda What is Windows Event Forwarding? How does HP ArcSight work with Windows Event Forwarding?
Security Operations Metrics Definitions for Management and Operations Teams
 Whitepaper Security Operations Metrics Definitions for Management and Operations Teams Measuring Performance across Business Imperatives, Operational Goals, Analytical Processes and SIEM Technologies Research
Whitepaper Security Operations Metrics Definitions for Management and Operations Teams Measuring Performance across Business Imperatives, Operational Goals, Analytical Processes and SIEM Technologies Research
Centralized Orchestration and Performance Monitoring
 DATASHEET NetScaler Command Center Centralized Orchestration and Performance Monitoring Key Benefits Performance Management High Availability (HA) Support Seamless VPX management Enables Extensible architecture
DATASHEET NetScaler Command Center Centralized Orchestration and Performance Monitoring Key Benefits Performance Management High Availability (HA) Support Seamless VPX management Enables Extensible architecture
- 1 - SmartStor Cloud Web Admin Manual
 - 1 - SmartStor Cloud Web Admin Manual Administrator Full language manuals are available in product disc or website. The SmartStor Cloud Administrator web site is used to control, setup, monitor, and manage
- 1 - SmartStor Cloud Web Admin Manual Administrator Full language manuals are available in product disc or website. The SmartStor Cloud Administrator web site is used to control, setup, monitor, and manage
McAfee Security Information Event Management (SIEM) Administration Course 101
 McAfee Security Information Event Management (SIEM) Administration Course 101 Intel Security Education Services Administration Course The McAfee SIEM Administration course from McAfee Education Services
McAfee Security Information Event Management (SIEM) Administration Course 101 Intel Security Education Services Administration Course The McAfee SIEM Administration course from McAfee Education Services
Scalability in Log Management
 Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com [email protected] Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com [email protected] Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Security Integration Splunk and ArcSight
 Security Integration Splunk and ArcSight Data Integration for IT security Wednesday 14 th January 2015 IT Analytics 15 Agenda Welcome Ray Bruni Eric Blavier Splunk & Nexthink Mostafa Soliman ArcSight &
Security Integration Splunk and ArcSight Data Integration for IT security Wednesday 14 th January 2015 IT Analytics 15 Agenda Welcome Ray Bruni Eric Blavier Splunk & Nexthink Mostafa Soliman ArcSight &
Security Information/Event Management Security Development Life Cycle Version 5
 Security Information/Event Management Security Development Life Cycle Version 5 If your enterprise is like most, you are collecting logs from most every device with security relevance. The flood of events
Security Information/Event Management Security Development Life Cycle Version 5 If your enterprise is like most, you are collecting logs from most every device with security relevance. The flood of events
Introduction to Database as a Service
 Introduction to Database as a Service Exadata Platform Revised 8/1/13 Database as a Service (DBaaS) Starts With The Business Needs Establish an IT delivery model that reduces costs, meets demand, and fulfills
Introduction to Database as a Service Exadata Platform Revised 8/1/13 Database as a Service (DBaaS) Starts With The Business Needs Establish an IT delivery model that reduces costs, meets demand, and fulfills
CA NSM System Monitoring. Option for OpenVMS r3.2. Benefits. The CA Advantage. Overview
 PRODUCT BRIEF: CA NSM SYSTEM MONITORING OPTION FOR OPENVMS Option for OpenVMS r3.2 CA NSM SYSTEM MONITORING OPTION FOR OPENVMS HELPS YOU TO PROACTIVELY DISCOVER, MONITOR AND DISPLAY THE HEALTH AND AVAILABILITY
PRODUCT BRIEF: CA NSM SYSTEM MONITORING OPTION FOR OPENVMS Option for OpenVMS r3.2 CA NSM SYSTEM MONITORING OPTION FOR OPENVMS HELPS YOU TO PROACTIVELY DISCOVER, MONITOR AND DISPLAY THE HEALTH AND AVAILABILITY
Technology Partners. Acceleratio Ltd. is a software development company based in Zagreb, Croatia, founded in 2009.
 Acceleratio Ltd. is a software development company based in Zagreb, Croatia, founded in 2009. We create innovative software solutions for SharePoint, Office 365, MS Windows Remote Desktop Services, and
Acceleratio Ltd. is a software development company based in Zagreb, Croatia, founded in 2009. We create innovative software solutions for SharePoint, Office 365, MS Windows Remote Desktop Services, and
CorreLog: Mature SIEM Solution on Day One Paul Gozaloff, CISSP. Presentation for SC Congress esymposium CorreLog, Inc. Tuesday, August 5, 2014
 CorreLog: Mature SIEM Solution on Day One Paul Gozaloff, CISSP Presentation for SC Congress esymposium CorreLog, Inc. Tuesday, August 5, 2014 Agenda 1. About CorreLog 2. Log Management vs. SIEM 3. The
CorreLog: Mature SIEM Solution on Day One Paul Gozaloff, CISSP Presentation for SC Congress esymposium CorreLog, Inc. Tuesday, August 5, 2014 Agenda 1. About CorreLog 2. Log Management vs. SIEM 3. The
Panorama PANORAMA. Panorama provides centralized policy and device management over a network of Palo Alto Networks next-generation firewalls.
 provides centralized policy and device management over a network of Palo Alto Networks next-generation firewalls. View a graphical summary of the applications on the network, the respective users, and
provides centralized policy and device management over a network of Palo Alto Networks next-generation firewalls. View a graphical summary of the applications on the network, the respective users, and
alcatel-lucent vitalqip Appliance manager End-to-end, feature-rich, appliance-based DNS/DHCP and IP address management
 alcatel-lucent vitalqip Appliance manager End-to-end, feature-rich, appliance-based DNS/DHCP and IP address management streamline management and cut administrative costs with the alcatel-lucent VitalQIP
alcatel-lucent vitalqip Appliance manager End-to-end, feature-rich, appliance-based DNS/DHCP and IP address management streamline management and cut administrative costs with the alcatel-lucent VitalQIP
Information Technology Policy
 Information Technology Policy Security Information and Event Management Policy ITP Number Effective Date ITP-SEC021 October 10, 2006 Category Supersedes Recommended Policy Contact Scheduled Review [email protected]
Information Technology Policy Security Information and Event Management Policy ITP Number Effective Date ITP-SEC021 October 10, 2006 Category Supersedes Recommended Policy Contact Scheduled Review [email protected]
Panorama Overview. Palo Alto Networks. Panorama Administrator s Guide Version 6.0. Copyright 2007-2015 Palo Alto Networks
 Panorama Overview Palo Alto Networks Panorama Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Panorama Overview Palo Alto Networks Panorama Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Ben Hall Technical Pre-Sales Manager Barry Kew Pre-Sales Consultant
 Ben Hall Technical Pre-Sales Manager Barry Kew Pre-Sales Consultant The Future of LANDESK Management Suite & Security Suite W H AT S N E W i n 9.6 + SP1 + SP2 E N D U S E R WORKSPA C E A C C E L E R AT
Ben Hall Technical Pre-Sales Manager Barry Kew Pre-Sales Consultant The Future of LANDESK Management Suite & Security Suite W H AT S N E W i n 9.6 + SP1 + SP2 E N D U S E R WORKSPA C E A C C E L E R AT
CA NSM System Monitoring Option for OpenVMS r3.2
 PRODUCT SHEET CA NSM System Monitoring Option for OpenVMS CA NSM System Monitoring Option for OpenVMS r3.2 CA NSM System Monitoring Option for OpenVMS helps you to proactively discover, monitor and display
PRODUCT SHEET CA NSM System Monitoring Option for OpenVMS CA NSM System Monitoring Option for OpenVMS r3.2 CA NSM System Monitoring Option for OpenVMS helps you to proactively discover, monitor and display
Maintaining Non-Stop Services with Multi Layer Monitoring
 Maintaining Non-Stop Services with Multi Layer Monitoring Lahav Savir System Architect and CEO of Emind Systems [email protected] www.emindsys.com The approach Non-stop applications can t leave on their
Maintaining Non-Stop Services with Multi Layer Monitoring Lahav Savir System Architect and CEO of Emind Systems [email protected] www.emindsys.com The approach Non-stop applications can t leave on their
SAP Crystal Reports & SAP HANA: Integration & Roadmap Kenneth Li SAP SESSION CODE: 0401
 SAP Crystal Reports & SAP HANA: Integration & Roadmap Kenneth Li SAP SESSION CODE: 0401 LEARNING POINTS Learn about Crystal Reports for HANA Glance at the road map for the product Overview of deploying
SAP Crystal Reports & SAP HANA: Integration & Roadmap Kenneth Li SAP SESSION CODE: 0401 LEARNING POINTS Learn about Crystal Reports for HANA Glance at the road map for the product Overview of deploying
Hands-On Microsoft Windows Server 2008
 Hands-On Microsoft Windows Server 2008 Chapter 10 Managing System Reliability and Availability Using and Configuring Event Viewer Event Viewer Houses the event logs that record information about all types
Hands-On Microsoft Windows Server 2008 Chapter 10 Managing System Reliability and Availability Using and Configuring Event Viewer Event Viewer Houses the event logs that record information about all types
CSS ONEVIEW G-Cloud CA Nimsoft Monitoring
 CSS ONEVIEW G-Cloud CA Nimsoft Monitoring Service Definition 01/04/2014 CSS Delivers Contents Contents... 2 Executive Summary... 3 Document Audience... 3 Document Scope... 3 Information Assurance:... 3
CSS ONEVIEW G-Cloud CA Nimsoft Monitoring Service Definition 01/04/2014 CSS Delivers Contents Contents... 2 Executive Summary... 3 Document Audience... 3 Document Scope... 3 Information Assurance:... 3
CNS Security and Network Monitoring. Managed Services Description
 Page 1 of 20 CNS Security and Network Monitoring Managed Services Description Author(s) [email protected] Date 16 th January,2012 Version V1.00 Page 2 of 20 INDEX 1 DOCUMENT CONTROL...3 1.1 ISSUER
Page 1 of 20 CNS Security and Network Monitoring Managed Services Description Author(s) [email protected] Date 16 th January,2012 Version V1.00 Page 2 of 20 INDEX 1 DOCUMENT CONTROL...3 1.1 ISSUER
1 Data Center Infrastructure Remote Monitoring
 Page 1 of 7 Service Description: Cisco Managed Services for Data Center Infrastructure Technology Addendum to Cisco Managed Services for Enterprise Common Service Description This document referred to
Page 1 of 7 Service Description: Cisco Managed Services for Data Center Infrastructure Technology Addendum to Cisco Managed Services for Enterprise Common Service Description This document referred to
Gold Support for NetFlow Tracker
 Visual Network Systems Gold Support helps you fully leverage your NetFlow Tracker investment and keep it current with regular software upgrades and comprehensive technical assistance. Gold Support for
Visual Network Systems Gold Support helps you fully leverage your NetFlow Tracker investment and keep it current with regular software upgrades and comprehensive technical assistance. Gold Support for
Netwrix Auditor for Exchange
 Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Vistara Lifecycle Management
 Vistara Lifecycle Management Solution Brief Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
Vistara Lifecycle Management Solution Brief Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
Oracle Big Data SQL Technical Update
 Oracle Big Data SQL Technical Update Jean-Pierre Dijcks Oracle Redwood City, CA, USA Keywords: Big Data, Hadoop, NoSQL Databases, Relational Databases, SQL, Security, Performance Introduction This technical
Oracle Big Data SQL Technical Update Jean-Pierre Dijcks Oracle Redwood City, CA, USA Keywords: Big Data, Hadoop, NoSQL Databases, Relational Databases, SQL, Security, Performance Introduction This technical
Violin Symphony Abstract
 Violin Symphony Abstract This white paper illustrates how Violin Symphony provides a simple, unified experience for managing multiple Violin Memory Arrays. Symphony facilitates scale-out deployment of
Violin Symphony Abstract This white paper illustrates how Violin Symphony provides a simple, unified experience for managing multiple Violin Memory Arrays. Symphony facilitates scale-out deployment of
Migrating your custom settings to version 7.6
 Migrating your custom settings to version 7.6 Webinar July 2011 web security data security email security 2009, Inc. All rights reserved. Webinar Presenter Greg Didier Title: Support Specialist Accomplishments:
Migrating your custom settings to version 7.6 Webinar July 2011 web security data security email security 2009, Inc. All rights reserved. Webinar Presenter Greg Didier Title: Support Specialist Accomplishments:
VitalQIP Appliance Manager (AM)
 VitalQIP Appliance Manager (AM) Ralph Senseny Product Management VitalQIP Strategy Provide a Complete IP Mgmt Software Solution to Enterprises, Gov t and Carriers IP Address, DNS and DHCP Management Data
VitalQIP Appliance Manager (AM) Ralph Senseny Product Management VitalQIP Strategy Provide a Complete IP Mgmt Software Solution to Enterprises, Gov t and Carriers IP Address, DNS and DHCP Management Data
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL
 CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
CONTINUOUS DIAGNOSTICS BEGINS WITH REDSEAL WHAT IS CDM? The continuous stream of high profile cybersecurity breaches demonstrates the need to move beyond purely periodic, compliance-based approaches to
The Bomgar Appliance in the Network
 The Bomgar Appliance in the Network The architecture of the Bomgar application environment relies on the Bomgar Appliance as a centralized routing point for all communications between application components.
The Bomgar Appliance in the Network The architecture of the Bomgar application environment relies on the Bomgar Appliance as a centralized routing point for all communications between application components.
High End Information Security Services
 High End Information Security Services Welcome Trion Logics Security Solutions was established after understanding the market's need for a high end - End to end security integration and consulting company.
High End Information Security Services Welcome Trion Logics Security Solutions was established after understanding the market's need for a high end - End to end security integration and consulting company.
ArcSight Express Administration and Operations Course
 ArcSight ArcSight Express Administration and Operations Course Code: ACBE ACS-EAO Days: 5 Course Description: The ArcSight Express Administration and Operations course provides you with comprehensive training
ArcSight ArcSight Express Administration and Operations Course Code: ACBE ACS-EAO Days: 5 Course Description: The ArcSight Express Administration and Operations course provides you with comprehensive training
Netwrix Auditor for Windows Server
 Netwrix Auditor for Windows Server Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for Windows Server Quick-Start Guide Version: 7.0 7/7/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Enterprise Application Monitoring with
 Enterprise Application Monitoring with 11/10/2007 Presented by James Peel [email protected] / www.altinity.com 1 Who am I? James Peel - [email protected] Job: Managing Director of Altinity
Enterprise Application Monitoring with 11/10/2007 Presented by James Peel [email protected] / www.altinity.com 1 Who am I? James Peel - [email protected] Job: Managing Director of Altinity
Network Monitoring Comparison
 Network Monitoring Comparison vs Network Monitoring is essential for every network administrator. It determines how effective your IT team is at solving problems or even completely eliminating them. Even
Network Monitoring Comparison vs Network Monitoring is essential for every network administrator. It determines how effective your IT team is at solving problems or even completely eliminating them. Even
11.1. Performance Monitoring
 11.1. Performance Monitoring Windows Reliability and Performance Monitor combines the functionality of the following tools that were previously only available as stand alone: Performance Logs and Alerts
11.1. Performance Monitoring Windows Reliability and Performance Monitor combines the functionality of the following tools that were previously only available as stand alone: Performance Logs and Alerts
Administration Guide NetIQ Privileged Account Manager 3.0.1
 Administration Guide NetIQ Privileged Account Manager 3.0.1 December 2015 www.netiq.com/documentation Legal Notice For information about NetIQ legal notices, disclaimers, warranties, export and other use
Administration Guide NetIQ Privileged Account Manager 3.0.1 December 2015 www.netiq.com/documentation Legal Notice For information about NetIQ legal notices, disclaimers, warranties, export and other use
How To Manage Sourcefire From A Command Console
 Sourcefire TM Sourcefire Capabilities Store up to 100,000,000 security & host events, including packet data Centralized policy & sensor management Centralized audit logging of configuration & security
Sourcefire TM Sourcefire Capabilities Store up to 100,000,000 security & host events, including packet data Centralized policy & sensor management Centralized audit logging of configuration & security
Kevin Hayes, CISSP, CISM MULTIPLY SECURITY EFFECTIVENESS WITH SIEM
 Kevin Hayes, CISSP, CISM MULTIPLY SECURITY EFFECTIVENESS WITH SIEM TODAY S AGENDA Describe the need for SIEM Explore different options available for SIEM Demonstrate a few Use Cases Cover some caveats
Kevin Hayes, CISSP, CISM MULTIPLY SECURITY EFFECTIVENESS WITH SIEM TODAY S AGENDA Describe the need for SIEM Explore different options available for SIEM Demonstrate a few Use Cases Cover some caveats
WhatsUp Gold vs. Orion
 Gold vs. Building the network management solution that will work for you is very easy with the Gold family just mix-and-match the Gold plug-ins that you need (WhatsVirtual, WhatsConnected, Flow Monitor,
Gold vs. Building the network management solution that will work for you is very easy with the Gold family just mix-and-match the Gold plug-ins that you need (WhatsVirtual, WhatsConnected, Flow Monitor,
Xirrus Management System
 DATASHEET Xirrus Management System The Xirrus Management System is a wireless network lifecycle management platform enabling network administrators to efficiently operate, configure and maintain Xirrus
DATASHEET Xirrus Management System The Xirrus Management System is a wireless network lifecycle management platform enabling network administrators to efficiently operate, configure and maintain Xirrus
StruxureWare TM Center Expert. Data
 StruxureWare TM Center Expert Data End to end data center infrastructure management software for monitoring and control of power, cooling, security and energy usage from the building through IT systems
StruxureWare TM Center Expert Data End to end data center infrastructure management software for monitoring and control of power, cooling, security and energy usage from the building through IT systems
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007
 5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
An Introduction to SIEM & RSA envision (Security Information and Event Management) January, 2011
 An Introduction to SIEM & RSA envision (Security Information and Event Management) January, 2011 Brian McLean, CISSP Sr Technology Consultant, RSA Changing Threats and More Demanding Regulations External
An Introduction to SIEM & RSA envision (Security Information and Event Management) January, 2011 Brian McLean, CISSP Sr Technology Consultant, RSA Changing Threats and More Demanding Regulations External
TORNADO Solution for Telecom Vertical
 BIG DATA ANALYTICS & REPORTING TORNADO Solution for Telecom Vertical Overview Last decade has see a rapid growth in wireless and mobile devices such as smart- phones, tablets and netbook is becoming very
BIG DATA ANALYTICS & REPORTING TORNADO Solution for Telecom Vertical Overview Last decade has see a rapid growth in wireless and mobile devices such as smart- phones, tablets and netbook is becoming very
Trusted Geolocation in The Cloud Technical Demonstration
 Trusted Geolocation in The Cloud Technical Demonstration NIST Interagency Report 7904 - Trusted Geolocation in the Cloud: Proof of Concept Implementation Trusted Geolocation in the Cloud Business Business
Trusted Geolocation in The Cloud Technical Demonstration NIST Interagency Report 7904 - Trusted Geolocation in the Cloud: Proof of Concept Implementation Trusted Geolocation in the Cloud Business Business
CA Unified Infrastructure Management
 CA Unified Infrastructure Management Probe Guide for IIS Server Monitoring iis v1.7 series Copyright Notice This online help system (the "System") is for your informational purposes only and is subject
CA Unified Infrastructure Management Probe Guide for IIS Server Monitoring iis v1.7 series Copyright Notice This online help system (the "System") is for your informational purposes only and is subject
IBM InfoSphere Guardium for DB2 on z/os Technical Deep Dive
 IBM InfoSphere Guardium for DB2 on z/os Technical Deep Dive One of a series of InfoSphere Guardium Technical Talks Ernie Mancill Executive IT Specialist Logistics This tech talk is being recorded. If you
IBM InfoSphere Guardium for DB2 on z/os Technical Deep Dive One of a series of InfoSphere Guardium Technical Talks Ernie Mancill Executive IT Specialist Logistics This tech talk is being recorded. If you
Using Microsoft Operations Manager To Monitor And Maintain Your Farm. Michael Noel. [email protected]
 Using Microsoft Operations Manager To Monitor And Maintain Your Farm Michael Noel [email protected] About the Presenter and Convergent Computing Author of SAMS Publishing titles SharePoint 2007 Unleashed,
Using Microsoft Operations Manager To Monitor And Maintain Your Farm Michael Noel [email protected] About the Presenter and Convergent Computing Author of SAMS Publishing titles SharePoint 2007 Unleashed,
PANORAMA. Panorama provides centralized policy and device management over a network of Palo Alto Networks next-generation firewalls.
 PANORAMA Panorama provides centralized policy and device management over a network of Palo Alto Networks next-generation firewalls. Web Interface HTTPS Panorama SSL View a graphical summary of the applications
PANORAMA Panorama provides centralized policy and device management over a network of Palo Alto Networks next-generation firewalls. Web Interface HTTPS Panorama SSL View a graphical summary of the applications
Non-standard use cases for SIEM technology
 Non-standard use cases for SIEM technology Matthew Schnarr Account Manager #HPProtect Introductions 2 It s a misnomer that HP ArcSight technology is only used for information security. Matthew Schnarr,
Non-standard use cases for SIEM technology Matthew Schnarr Account Manager #HPProtect Introductions 2 It s a misnomer that HP ArcSight technology is only used for information security. Matthew Schnarr,
How To Use Arcgis For Free On A Gdb 2.2.2 (For A Gis Server) For A Small Business
 Esri Middle East and Africa User Conference December 10 12 Abu Dhabi, UAE Understanding ArcGIS in Virtualization and Cloud Environments Marwa Mabrouk Powerful GIS capabilities Delivered as Web services
Esri Middle East and Africa User Conference December 10 12 Abu Dhabi, UAE Understanding ArcGIS in Virtualization and Cloud Environments Marwa Mabrouk Powerful GIS capabilities Delivered as Web services
Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual. Document Version 1.0
 Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual Document Version 1.0 Table of Contents 1 SWAF... 4 1.1 SWAF Features... 4 2 Operations and User Manual... 7 2.1 SWAF Administrator
Semantic based Web Application Firewall (SWAF V 1.6) Operations and User Manual Document Version 1.0 Table of Contents 1 SWAF... 4 1.1 SWAF Features... 4 2 Operations and User Manual... 7 2.1 SWAF Administrator
Smart Business Architecture for Midsize Networks Network Management Deployment Guide
 Smart Business Architecture for Midsize Networks Network Management Deployment Guide Introduction: Smart Business Architecture for Mid-sized Networks, Network Management Deployment Guide With the Smart
Smart Business Architecture for Midsize Networks Network Management Deployment Guide Introduction: Smart Business Architecture for Mid-sized Networks, Network Management Deployment Guide With the Smart
XpoLog Center Suite Data Sheet
 XpoLog Center Suite Data Sheet General XpoLog is a data analysis and management platform for Applications IT data. Business applications rely on a dynamic heterogeneous applications infrastructure, such
XpoLog Center Suite Data Sheet General XpoLog is a data analysis and management platform for Applications IT data. Business applications rely on a dynamic heterogeneous applications infrastructure, such
NMS300 Network Management System
 NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
EventSentry Overview. Part I About This Guide 1. Part II Overview 2. Part III Installation & Deployment 4. Part IV Monitoring Architecture 13
 Contents I Part I About This Guide 1 Part II Overview 2 Part III Installation & Deployment 4 1 Installation... with Setup 5 2 Management... Console 6 3 Configuration... 7 4 Remote... Update 10 Part IV
Contents I Part I About This Guide 1 Part II Overview 2 Part III Installation & Deployment 4 1 Installation... with Setup 5 2 Management... Console 6 3 Configuration... 7 4 Remote... Update 10 Part IV
Network Capacity Management with BMC Capacity Optimization
 Network Capacity Management with BMC Capacity Optimization BMC Capacity Optimization supports an automated and proactive approach to network capacity management with capacity analytics, best-practice network
Network Capacity Management with BMC Capacity Optimization BMC Capacity Optimization supports an automated and proactive approach to network capacity management with capacity analytics, best-practice network
What is SIEM? Security Information and Event Management. Comes in a software format or as an appliance.
 Ross Spooner Cyber Security for Government Conference 6 August 2013 What is SIEM? Security Information and Event Management Centralised security log management Long term storage, analysis and reporting
Ross Spooner Cyber Security for Government Conference 6 August 2013 What is SIEM? Security Information and Event Management Centralised security log management Long term storage, analysis and reporting
REASON FOR LOG RETENTION MANAGEMENT
 REASON FOR LOG RETENTION MANAGEMENT COMPUTER LOG RECORD OF COMPUTER ACTIVITY 1. LAW ENFORCEMENT LAW 2. INCREASE SECURITY Centralized Log Server Authorized Only administrator can view and export 3. INCREASE
REASON FOR LOG RETENTION MANAGEMENT COMPUTER LOG RECORD OF COMPUTER ACTIVITY 1. LAW ENFORCEMENT LAW 2. INCREASE SECURITY Centralized Log Server Authorized Only administrator can view and export 3. INCREASE
Energy Management Web-based embedded solution for monitoring of distributed conventional energy applications Type Em 2 -Server
 Energy Management Web-based embedded solution for monitoring of distributed conventional energy applications Type Em 2 -Server Software solution with integrated database and webserver Monitoring and data
Energy Management Web-based embedded solution for monitoring of distributed conventional energy applications Type Em 2 -Server Software solution with integrated database and webserver Monitoring and data
Extreme Networks Security Analytics G2 Risk Manager
 DATA SHEET Extreme Networks Security Analytics G2 Risk Manager Proactively manage vulnerabilities and network device configuration to reduce risk, improve compliance HIGHLIGHTS Visualize current and potential
DATA SHEET Extreme Networks Security Analytics G2 Risk Manager Proactively manage vulnerabilities and network device configuration to reduce risk, improve compliance HIGHLIGHTS Visualize current and potential
Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid clouds.
 ENTERPRISE MONITORING & LIFECYCLE MANAGEMENT Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
ENTERPRISE MONITORING & LIFECYCLE MANAGEMENT Unify IT Operations Enterprise IT is complex. Today, IT infrastructure spans the physical, the virtual and applications, and crosses public, private and hybrid
Vulnerability Management
 Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
Vulnerability Management Buyer s Guide Buyer s Guide 01 Introduction 02 Key Components 03 Other Considerations About Rapid7 01 INTRODUCTION Exploiting weaknesses in browsers, operating systems and other
SANS Top 20 Critical Controls for Effective Cyber Defense
 WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
TITANXR Multi-Switch Management Software
 TITANXR Multi-Switch Management Software Centralized management of APCON network monitoring switches Features Centralized APCON system management View status and alerts Configurable Dashboards Monitor
TITANXR Multi-Switch Management Software Centralized management of APCON network monitoring switches Features Centralized APCON system management View status and alerts Configurable Dashboards Monitor
Identity and Access Management Integration with PowerBroker. Providing Complete Visibility and Auditing of Identities
 Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
PCI COMPLIANCE ON AWS: HOW TREND MICRO CAN HELP
 solution brief PCI COMPLIANCE ON AWS: HOW TREND MICRO CAN HELP AWS AND PCI DSS COMPLIANCE To ensure an end-to-end secure computing environment, Amazon Web Services (AWS) employs a shared security responsibility
solution brief PCI COMPLIANCE ON AWS: HOW TREND MICRO CAN HELP AWS AND PCI DSS COMPLIANCE To ensure an end-to-end secure computing environment, Amazon Web Services (AWS) employs a shared security responsibility
HP Operations Smart Plug-in for Virtualization Infrastructure
 HP Operations Smart Plug-in for Virtualization Infrastructure for HP Operations Manager for Windows Software Version: 1.00 Deployment and Reference Guide Document Release Date: October 2008 Software Release
HP Operations Smart Plug-in for Virtualization Infrastructure for HP Operations Manager for Windows Software Version: 1.00 Deployment and Reference Guide Document Release Date: October 2008 Software Release
SQL Sentry Essentials
 Master the extensive capabilities of SQL Sentry Overview This virtual instructor-led, three day class for up to 12 students provides the knowledge and skills needed to master the extensive performance
Master the extensive capabilities of SQL Sentry Overview This virtual instructor-led, three day class for up to 12 students provides the knowledge and skills needed to master the extensive performance
HP A-IMC Firewall Manager
 HP A-IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW101-20110805 Legal and notice information Copyright 2011 Hewlett-Packard Development Company, L.P. No part of this
HP A-IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW101-20110805 Legal and notice information Copyright 2011 Hewlett-Packard Development Company, L.P. No part of this
End-user Security Analytics Strengthens Protection with ArcSight
 Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
THE SMARTEST WAY TO PROTECT WEBSITES AND WEB APPS FROM ATTACKS
 THE SMARTEST WAY TO PROTECT WEBSITES AND WEB APPS FROM ATTACKS INCONVENIENT STATISTICS 70% of ALL threats are at the Web application layer. Gartner 73% of organizations have been hacked in the past two
THE SMARTEST WAY TO PROTECT WEBSITES AND WEB APPS FROM ATTACKS INCONVENIENT STATISTICS 70% of ALL threats are at the Web application layer. Gartner 73% of organizations have been hacked in the past two
Understanding ArcGIS Deployments in Public and Private Cloud. Marwa Mabrouk
 Understanding ArcGIS Deployments in Public and Private Cloud Marwa Mabrouk Agenda Back to Basics What are people doing? New Features Using ArcGIS in the Cloud - Private Cloud - Public Cloud Technical Demos
Understanding ArcGIS Deployments in Public and Private Cloud Marwa Mabrouk Agenda Back to Basics What are people doing? New Features Using ArcGIS in the Cloud - Private Cloud - Public Cloud Technical Demos
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for Active Directory
 Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Extreme Networks Security Analytics G2 Vulnerability Manager
 DATA SHEET Extreme Networks Security Analytics G2 Vulnerability Manager Improve security and compliance by prioritizing security gaps for resolution HIGHLIGHTS Help prevent security breaches by discovering
DATA SHEET Extreme Networks Security Analytics G2 Vulnerability Manager Improve security and compliance by prioritizing security gaps for resolution HIGHLIGHTS Help prevent security breaches by discovering
[Document Title] SolarWinds Server & Application Monitor (SAM) [Document Subtitle] Angi Gahler. Share: Author: Manish Chacko
![[Document Title] SolarWinds Server & Application Monitor (SAM) [Document Subtitle] Angi Gahler. Share: Author: Manish Chacko [Document Title] SolarWinds Server & Application Monitor (SAM) [Document Subtitle] Angi Gahler. Share: Author: Manish Chacko](/thumbs/26/8141783.jpg) [Document Title] [Document Subtitle] SolarWinds Server & Application Monitor (SAM) Author: Manish Chacko Angi Gahler Table of Contents The Case for Application & Server Monitoring.. 3 Complete Visibility
[Document Title] [Document Subtitle] SolarWinds Server & Application Monitor (SAM) Author: Manish Chacko Angi Gahler Table of Contents The Case for Application & Server Monitoring.. 3 Complete Visibility
All about Threat Central
 All about Threat Central Ted Ross & Nadav Cohen #HPProtect Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice. This document contains forward
All about Threat Central Ted Ross & Nadav Cohen #HPProtect Forward-looking statements This is a rolling (up to three year) Roadmap and is subject to change without notice. This document contains forward
State of Wisconsin DET File Transfer Protocol Service Offering Definition (FTP & SFTP)
 State of Wisconsin DET File Transfer Protocol Service Offering Definition (FTP & SFTP) Document Revision History Date Version Creator Notes File Transfer Protocol Service Page 2 7/7/2011 Table of Contents
State of Wisconsin DET File Transfer Protocol Service Offering Definition (FTP & SFTP) Document Revision History Date Version Creator Notes File Transfer Protocol Service Page 2 7/7/2011 Table of Contents
Sisense. Product Highlights. www.sisense.com
 Sisense Product Highlights Introduction Sisense is a business intelligence solution that simplifies analytics for complex data by offering an end-to-end platform that lets users easily prepare and analyze
Sisense Product Highlights Introduction Sisense is a business intelligence solution that simplifies analytics for complex data by offering an end-to-end platform that lets users easily prepare and analyze
