SoftwareFileProtection.com. File Encryption System Using USB Dongles. User Guide For Mac
|
|
|
- Fay Patterson
- 8 years ago
- Views:
Transcription
1 File Encryption System Using USB Dongles User Guide For Mac 1
2 Contents Page no. 1. General 3 2. Algorithm and versions 4 3. Encrypting and Decrypting Files 5 4. Errors and their resolutions 6 2
3 1. General GoSafe is an on the fly USB Dongle based encryption / decryption security product which allows you to encrypt your files and helps you to protect your important data when you are transferring files online or as an attachment in an . GoSafe is suitable for encryption of all file formats. During file transfers in online chat programs like Skype, Yahoo Messenger, GTalk and others, it is possible for a hacker to hack your files. It is also not very difficult to hack your account and download your important file attachments. To protect your files, one of the best ways is to encrypt them. Normal encryption and protection techniques use password or a text string to encrypt and protect file. This password is saved inside the file itself and hence it is very easy to crack such encryptions and get hold of your data. GoSafe uses an USB Dongle to store the encryption key and also uses three other verification keys stored inside dongle plus a unique hardware serial number of the dongle. This makes it very safe and can even be used in military communication. GoSafe dongles are made in set. The other person receiving the file will require a USB dongle from the same set to decrypt and use the file. Any person getting hold of your files will not be able to use them unless he/she has the USB dongle from the same set. You can order GoSafe with required set of dongles. For example, if you have 500 offices you can order GoSafe with 500 Dongle set. You can also expand the GoSafe dongle set. We will simply need two dongles from the existing set and KYC [Know Your Customer] form filled along with supportive documents and authorization. 3
4 2. Algorithm and versions GoSafe comes with different encryption algorithms: 1. Custom IMSPL Algorithm 2. AES Algorithm The Programs are made with two different options: 1. SF : This will encrypt or decrypt the same file 2. NF : This will create a new file upon encryption or decryption Encrypted file will have _GoSafe added to its name while decrypted file will have _UnSafe added to its name. GoSafe is available as free download from our site [ Notes: You agree to license terms by installing any version of GoSafe. To learn how to use GoSafe SF, GoSafe AES SF, GoSafe NF and GoSafe AES NF, watch Video. 4
5 3. Encrypting and Decrypting Files GoSafe SF [and GoSafe AES SF] SoftwareFileProtection.com Select the file(s) you want to encrypt or decrypt Right click, hover on "More > Automator", click "GoSafe Protection_SF" GoSafe SF and GoSafe AES SF will automatically detect file encryption/decryption status and ask to decrypt if file is already encrypted GoSafe SF and GoSafe AES SF will encrypt or decrypt with the same file GoSafe NF [and GoSafe AES NF] Select the file(s) you want to encrypt or decrypt Right click, hover on " More > Automator ", click "GoSafe Protection_NF" GoSafe NF will create a new file with _GoSafe at the end of name for an encrypted file _UnSafe for a decrypted file. GoSafe NF and GoSafe AES NF will automatically detect file encryption/decryption status. 5
6 When you got this window for the conformation that s you successfully Encrypted/Decrypted your files. After the Encryption/Decryption, you close the application which is in a Dock. Note:You must quit the application when you successfully done Encryption/Decryption files. 6
7 4. Errors and their resolutions Error Numbers Description Resolution 2 Dongle not validated Insert correct dongle 3 Dongle not validated Insert correct dongle 4 Dongle not validated Insert correct dongle 5 Dongle not validated Insert correct dongle 6 Dongle not validated Insert correct dongle 7 Dongle not validated Insert correct dongle 8 Dongle not validated Insert correct dongle 9 Dongle not validated Insert correct dongle 10 Dongle not validated Insert correct dongle 11 Dongle not validated Insert correct dongle 12 Dongle not validated Insert correct dongle 13 Dongle not validated Insert correct dongle 14 File operation Error Your file is corrupt or not usable. 15 Dongle not validated Insert correct dongle 7
8 Contact: Innovative Matrix Softech Pvt. Ltd. 7005, 7th Floor, Emerald House, Sarojini Devi Road, Next to Parklane Hotel, Near State bank of Mysore, Paradise Circle, Hyderabad / Secunderabad India For details visit: s: mail@isohelpline.com, support@isohelpline.com 8
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption!
 Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Encrypting*a*Windows*7*Hard*Disk* with%bitlocker%disk%encryption Thisdocumentcontainsthenecessarystepstoencryptthecontentsofaharddrive usingbitlockerandwindows7. Thefollowinginstructionsarederivedfromdocumentationat:
Secure USB Flash Drive. Biometric & Professional Drives
 Secure USB Flash Drive Biometric & Professional Drives I. CONTENTS II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE FLASH DRIVE... 3 DESCRIPTION... 3 IV. MODULES OF SECURE
Secure USB Flash Drive Biometric & Professional Drives I. CONTENTS II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE FLASH DRIVE... 3 DESCRIPTION... 3 IV. MODULES OF SECURE
Cloudifile Getting Started
 Cloudifile Getting Started 1 Contents About... 3 System Requirements... 3 Cloudifile Recommendations for Use... 4 Cloudifile: How It Works?... 6 [Windows] Getting Started... 8 [Mac OS X] Getting Started...
Cloudifile Getting Started 1 Contents About... 3 System Requirements... 3 Cloudifile Recommendations for Use... 4 Cloudifile: How It Works?... 6 [Windows] Getting Started... 8 [Mac OS X] Getting Started...
Here is a guide on how to encrypt a part of your USB flash drive and access it on any computer:
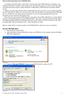 How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
After installation of Rohos Disk Encryption, insert your USB pen drive to the computer and run the Rohos Disk Encryption application.
 Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not
Rohos Disk Encryption - creates hidden and password protected partitions on the computer or USB flash drive. With megabytes of sensitive files and private data on your computer or USB drive you can not
Installation and User Guide. MQLink Version 3.0 (Java)
 Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Installation and User Guide MQLink Version 3.0 (Java) MQLink V3.0 (Java) User Guide Table of Contents 1 Introduction... 2 2 Installation... 2 2.1 Available from 2.2 Where to install 2.3 Installation Pre-requisites
Sticky Password 7. Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet
 Sticky Password 7 Reviewer Guide Introduction Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet simple password manager and form-filler. Its main goal
Sticky Password 7 Reviewer Guide Introduction Sticky Password 7 is the latest, most advanced, portable, cross platform version of the powerful yet simple password manager and form-filler. Its main goal
Guide how to protect your private data with Rohos Disk Encryption
 Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
Guide how to protect your private data with Rohos Disk Encryption 1 Content 1. Encrypt USB drive - Portable Application 2. Encrypt HDD 3. Hide folder 4. Have USB Key for access control 5. Rohos disk options
User's voice NET NANNY. Quite simple to install and configure. Improve messages and possible reactions when a page is blocked. Comprehensibility:
 NAME NET NANNY Company Content Watch Version 6.5.13.1 Type of product Devices supported Operating systems Client Computer Microsoft Windows 7 (32/64 bit) Microsoft Windows Vista (32/64 bit) Microsoft Windows,
NAME NET NANNY Company Content Watch Version 6.5.13.1 Type of product Devices supported Operating systems Client Computer Microsoft Windows 7 (32/64 bit) Microsoft Windows Vista (32/64 bit) Microsoft Windows,
Skype Cheat Sheet. Downloading and Installing Skype
 Skype Cheat Sheet Downloading and Installing Skype Windows: 1. Go to www.skype.com and choose "Get Skype" from the menu. 2. Click the button "Get Skype for Windows". On the next page, select the "Download
Skype Cheat Sheet Downloading and Installing Skype Windows: 1. Go to www.skype.com and choose "Get Skype" from the menu. 2. Click the button "Get Skype for Windows". On the next page, select the "Download
ELECTION COMMISSION OF INDIA NEW DELHI WEBCASTING. Broadcasting over the Internet
 1 ELECTION COMMISSION OF INDIA NEW DELHI WEBCASTING Broadcasting over the Internet Why do we need.? 2 To keep a check on illegal activities such as booth capturing, money distribution and bogus voting
1 ELECTION COMMISSION OF INDIA NEW DELHI WEBCASTING Broadcasting over the Internet Why do we need.? 2 To keep a check on illegal activities such as booth capturing, money distribution and bogus voting
Verbatim Secure Data USB Drive. User Guide. User Guide Version 2.0 All rights reserved
 Verbatim Secure Data USB Drive User Guide User Guide Version 2.0 All rights reserved Table of Contents Table of Contents... 2 1. Introduction to Verbatim Secure Data USB Drive... 3 2. System Requirements...
Verbatim Secure Data USB Drive User Guide User Guide Version 2.0 All rights reserved Table of Contents Table of Contents... 2 1. Introduction to Verbatim Secure Data USB Drive... 3 2. System Requirements...
Secure Data Exchange Solution
 Secure Data Exchange Solution I. CONTENTS I. CONTENTS... 1 II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE DOCUMENT EXCHANGE SOLUTIONS... 3 INTRODUCTION... 3 Certificates
Secure Data Exchange Solution I. CONTENTS I. CONTENTS... 1 II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE DOCUMENT EXCHANGE SOLUTIONS... 3 INTRODUCTION... 3 Certificates
FB Lead Gen: Generate Email Marketing Leads With a Facebook Button - A Closer Look -->>> Click Here
 Facebook application for pc windows xp free download, add facebook link to wordpress sidebar, lead generation tracking software, facebook share button code asp.net. FB Lead Gen: Generate Email Marketing
Facebook application for pc windows xp free download, add facebook link to wordpress sidebar, lead generation tracking software, facebook share button code asp.net. FB Lead Gen: Generate Email Marketing
HELP MANUAL FOR MACHINE SETUP FOR DAE E-TENDERING SYSTEM
 HELP MANUAL FOR MACHINE SETUP FOR DAE E-TENDERING SYSTEM DEPARTMENT OF ATOMIC ENERGY E-Tendering Portal: - http://etenders.dae.gov.in VER: 1.3 Title Description Screenshots 1) Download the required utilities.
HELP MANUAL FOR MACHINE SETUP FOR DAE E-TENDERING SYSTEM DEPARTMENT OF ATOMIC ENERGY E-Tendering Portal: - http://etenders.dae.gov.in VER: 1.3 Title Description Screenshots 1) Download the required utilities.
Software Piracy Overview of Anti-Tampering Technologies. Scott Baeder Sr. Architect Cadence Design Systems baeder@cadence.
 Software Piracy Overview of Anti-Tampering Technologies Scott Baeder Sr. Architect Cadence Design Systems baeder@cadence.com 0 Agenda Quick Review of Piracy Binary Hacking Crackers Workflow First Impressions
Software Piracy Overview of Anti-Tampering Technologies Scott Baeder Sr. Architect Cadence Design Systems baeder@cadence.com 0 Agenda Quick Review of Piracy Binary Hacking Crackers Workflow First Impressions
How can I use the internet to make free calls?
 Keeping in touch 4.3 Making calls on Skype How can I use the internet to make free calls? Skype is a free service that enables anyone to make free voice or video calls between computers regardless of location.
Keeping in touch 4.3 Making calls on Skype How can I use the internet to make free calls? Skype is a free service that enables anyone to make free voice or video calls between computers regardless of location.
Create a Basic Skype* Account. Intel Easy Steps 1 2012 Intel Corporation All rights reserved.
 Create a Basic Skype* Account Intel Easy Steps 1 2012 Intel Corporation Using Skype* to Communicate: Create and use a Basic Skype Account There are different ways of communicating and sharing through the
Create a Basic Skype* Account Intel Easy Steps 1 2012 Intel Corporation Using Skype* to Communicate: Create and use a Basic Skype Account There are different ways of communicating and sharing through the
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Using the Orbit Webcam & Skype to Video Conference
 Using the Orbit Webcam & Skype to Video Conference Quick Steps for connecting to a conference call Note: When connecting on a Skype conference call, you will need either the Skype name or the email address
Using the Orbit Webcam & Skype to Video Conference Quick Steps for connecting to a conference call Note: When connecting on a Skype conference call, you will need either the Skype name or the email address
keep your Passwords secure!
 keep your Passwords secure! architectures for secure identity ManageMent: a bottom View Secure Identity Management is is a a key key aspect for corporate security. It It comprises modern technical solutions
keep your Passwords secure! architectures for secure identity ManageMent: a bottom View Secure Identity Management is is a a key key aspect for corporate security. It It comprises modern technical solutions
UniKey Family 0. UniKey Time
 UniKey Family 0 UniKey STD HID based driverless dongle Unique Hardware ID Automatic Protection Remote Update 4k Internal Memory API (for numerous platforms) Offline Licensing Options Customization Service
UniKey Family 0 UniKey STD HID based driverless dongle Unique Hardware ID Automatic Protection Remote Update 4k Internal Memory API (for numerous platforms) Offline Licensing Options Customization Service
Introduction. Keeping Data Safe and Secure. Topics of Interest. Disclaimer. How Is Data Lost In General? Reasons for Data Loss by 3 rd Parties
 Introduction Keeping Data Safe and Secure with Encryption and Online Services This session will look at two aspects of protecting your TRIO program s data through the use of data encryption and online
Introduction Keeping Data Safe and Secure with Encryption and Online Services This session will look at two aspects of protecting your TRIO program s data through the use of data encryption and online
Gold Lock Desktop. User Manual. Follow these simple steps to install, configure, and use Gold Lock Desktop.
 User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
Configuring a YubiKey for the YubiCloud
 Configuring a YubiKey for the YubiCloud With the YubiKey Cross-Platform Personalization Tool April 9, 2013 Configuring a YubiKey for the YubiCloud 2012 Yubico. All rights reserved. Page 1 of 8 Introduction
Configuring a YubiKey for the YubiCloud With the YubiKey Cross-Platform Personalization Tool April 9, 2013 Configuring a YubiKey for the YubiCloud 2012 Yubico. All rights reserved. Page 1 of 8 Introduction
How To Backup Your Hard Drive With Pros 4 Technology Online Backup
 Pros 4 Technology Online Backup Features Introduction Computers are the default storage medium for most businesses and virtually all home users. Because portable media is quickly becoming an outdated and
Pros 4 Technology Online Backup Features Introduction Computers are the default storage medium for most businesses and virtually all home users. Because portable media is quickly becoming an outdated and
Step by step guide how to password protect your USB flash drive
 Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
Step by step guide how to password protect your USB flash drive 1 Content 1. How to create encrypted partition on USB flash drive 2. How to work with encrypted partition on the USB flash drive - Rohos
September 25, 2015. Programming YubiKeys for Okta Adaptive Multi-Factor Authentication
 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication September 25, 2015 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication Page 1 of 14 Copyright 2015 Yubico Inc. All rights
Programming YubiKeys for Okta Adaptive Multi-Factor Authentication September 25, 2015 Programming YubiKeys for Okta Adaptive Multi-Factor Authentication Page 1 of 14 Copyright 2015 Yubico Inc. All rights
Sending Files to a Social Security Laptop
 Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
Sending Files to a Social Security Laptop Introduction There are multiple options to send files to your Social Security laptop. A couple of options are to encrypt files and then send them by email or transfer
BackupAgent Management Console 4.0.1 User Manual
 BackupAgent Management Console 4.0.1 User Manual May 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes
BackupAgent Management Console 4.0.1 User Manual May 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes
Privacy and Encryption in egovernment. Dewey Landrum Technical Architect CSO SLED West Sector CISSP August 11, 2008
 Privacy and Encryption in egovernment Dewey Landrum Technical Architect CSO SLED West Sector CISSP August 11, 2008 Privacy Regulations Health Insurance Portability and Accountability Act (HIPPA) Gramm-Leach-Bliley
Privacy and Encryption in egovernment Dewey Landrum Technical Architect CSO SLED West Sector CISSP August 11, 2008 Privacy Regulations Health Insurance Portability and Accountability Act (HIPPA) Gramm-Leach-Bliley
Personal Information Protection Policy
 Personal Information Protection Policy Thank you very much for visiting yessign website of Korea Financial Telecommunications & Clearings Institute (KFTC). KFTC values the personal information of users
Personal Information Protection Policy Thank you very much for visiting yessign website of Korea Financial Telecommunications & Clearings Institute (KFTC). KFTC values the personal information of users
Online Backup Management Console 3.8 User Manual
 Online Backup Management Console 3.8 User Manual September 2010 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human
Online Backup Management Console 3.8 User Manual September 2010 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human
GoldKey Software. User s Manual. Revision 7.12. WideBand Corporation www.goldkey.com. Copyright 2007-2014 WideBand Corporation. All Rights Reserved.
 GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
SVA Backup Plus Features
 1221 John Q. Hammons Drive Madison, WI 53717 P.O. Box 44966, Madison, WI 53717 P: 608.826.2400 TF: 800.366.9091 F: 608.831.4243 www.sva.com Introduction Computers are the default storage medium for most
1221 John Q. Hammons Drive Madison, WI 53717 P.O. Box 44966, Madison, WI 53717 P: 608.826.2400 TF: 800.366.9091 F: 608.831.4243 www.sva.com Introduction Computers are the default storage medium for most
Evolved Backup Features Computer Box 220 5th Ave South Clinton, IA 52732 www.thecomputerbox.com 563-243-0016
 Evolved Backup Features 1 Contents 3 Introduction 3 Ease-of-Use Simple Installation Automatic Backup Off-Site Storage Scalability File Restoration 24/7 6 Security File Compression Encryption Transmission
Evolved Backup Features 1 Contents 3 Introduction 3 Ease-of-Use Simple Installation Automatic Backup Off-Site Storage Scalability File Restoration 24/7 6 Security File Compression Encryption Transmission
Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device
 Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device Jyoti Rao *1,Kishan Mistry #2, Bhumika Mistry #3, Divya Malviya #4, Devesh Gudway #5 # Student & Department
Multifactor Graphical Password Authentication System using Sound Signature and Handheld Device Jyoti Rao *1,Kishan Mistry #2, Bhumika Mistry #3, Divya Malviya #4, Devesh Gudway #5 # Student & Department
Law College Computer and Technology Information
 Law College Computer and Technology Information Account Creation All law students, faculty and staff must have a University of Toledo authentication domain (UTAD) computer account. This account will allow
Law College Computer and Technology Information Account Creation All law students, faculty and staff must have a University of Toledo authentication domain (UTAD) computer account. This account will allow
eztechdirect Backup Service Features
 eztechdirect Backup Service Features Introduction Portable media is quickly becoming an outdated and expensive method for safeguarding important data, so it is essential to secure critical business assets
eztechdirect Backup Service Features Introduction Portable media is quickly becoming an outdated and expensive method for safeguarding important data, so it is essential to secure critical business assets
How To Use Cmk On An Ipa (Intralinks) On A Pc Or Mac Mac (Apple) On An Iphone Or Ipa On A Mac Or Ipad (Apple Mac) On Pc Or Ipat (Apple
 Intralinks Customer Managed Keys Technical Overview Version 2.0 October 2014 Copyright 2014 Intralinks, Inc. 1 Intralinks Customer Managed Keys, Technical Overview January 5, 2015 About This Document...
Intralinks Customer Managed Keys Technical Overview Version 2.0 October 2014 Copyright 2014 Intralinks, Inc. 1 Intralinks Customer Managed Keys, Technical Overview January 5, 2015 About This Document...
Basics. How can I use the Internet to make free calls?
 Basics Use this document with the glossary A helper should take you through this guide Keeping in touch 4.3 Making calls on Skype How can I use the Internet to make free calls? Skype is a free service
Basics Use this document with the glossary A helper should take you through this guide Keeping in touch 4.3 Making calls on Skype How can I use the Internet to make free calls? Skype is a free service
Where to get help Skype support is available online at http://www.skype.com/help/
 Skype Computer based communication tool Learning Advantages Communicate between computers and telephones at low to no cost Available anywhere if user has a reliable internet connection In addition to computer
Skype Computer based communication tool Learning Advantages Communicate between computers and telephones at low to no cost Available anywhere if user has a reliable internet connection In addition to computer
Security Policy Revision Date: 23 April 2009
 Security Policy Revision Date: 23 April 2009 Remote Desktop Support Version 3.2.1 or later for Windows Version 3.1.2 or later for Linux and Mac 4 ISL Light Security Policy This section describes the procedure
Security Policy Revision Date: 23 April 2009 Remote Desktop Support Version 3.2.1 or later for Windows Version 3.1.2 or later for Linux and Mac 4 ISL Light Security Policy This section describes the procedure
Introduction. Ease-of-Use
 Remote Data Backup Introduction Computers are the default storage medium for most businesses and virtually all home users. Because portable media is quickly becoming an outdated and expensive method for
Remote Data Backup Introduction Computers are the default storage medium for most businesses and virtually all home users. Because portable media is quickly becoming an outdated and expensive method for
PC Surveillance. Hacking. Information Exploitation. Information Interception
 IT INTRUSION FinFisher Product Suite Usage Information Gathering PC Surveillance Hacking Information Exploitation Information Interception 2 Components FinFisher USB Suite FinFisher Remote Hacking Kit
IT INTRUSION FinFisher Product Suite Usage Information Gathering PC Surveillance Hacking Information Exploitation Information Interception 2 Components FinFisher USB Suite FinFisher Remote Hacking Kit
Manual for Android 1.5
 Manual for Android 1.5 1 Table of Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 3 2. Installation... 4 3. Basic functionality... 5 3.1. Setting up Boxcryptor
Manual for Android 1.5 1 Table of Content 1. Scope of Service... 3 1.1 About Boxcryptor Classic... 3 1.2 About this manual... 3 2. Installation... 4 3. Basic functionality... 5 3.1. Setting up Boxcryptor
Comodo Disk Encryption
 Comodo Disk Encryption Version 2.0 User Guide Version 2.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo Disk Encryption Introduction... 3
Comodo Disk Encryption Version 2.0 User Guide Version 2.0.122010 Versi Comodo Security Solutions 525 Washington Blvd. Jersey City, NJ 07310 Table of Contents 1.Comodo Disk Encryption Introduction... 3
Matrix Technical Support Mailer - 72 Procedure for Image Upload through Email Server in SATATYA DVR,NVR & HVR
 Matrix Technical Support Mailer - 72 Procedure for Image Upload through Email Server in SATATYA DVR,NVR & HVR Dear Friends, This mailer will help you configure Email Notification in SATATYA Web Client
Matrix Technical Support Mailer - 72 Procedure for Image Upload through Email Server in SATATYA DVR,NVR & HVR Dear Friends, This mailer will help you configure Email Notification in SATATYA Web Client
CHOOSING THE RIGHT PORTABLE SECURITY DEVICE. A guideline to help your organization chose the Best Secure USB device
 CHOOSING THE RIGHT PORTABLE SECURITY DEVICE A guideline to help your organization chose the Best Secure USB device Introduction USB devices are widely used and convenient because of their small size, huge
CHOOSING THE RIGHT PORTABLE SECURITY DEVICE A guideline to help your organization chose the Best Secure USB device Introduction USB devices are widely used and convenient because of their small size, huge
Train the Trainers. Instructor s Manual
 Train the Trainers Training Program Instructor s Manual Innovative Matrix Softech Pvt. Ltd. A-401, Satellite Township, Opp Sherwood Public School, Pipeline Road, Pet Basheerabad, Jeedimetla (V), Hyderabad
Train the Trainers Training Program Instructor s Manual Innovative Matrix Softech Pvt. Ltd. A-401, Satellite Township, Opp Sherwood Public School, Pipeline Road, Pet Basheerabad, Jeedimetla (V), Hyderabad
How to Setup OSX Mail to POP an Exchange Account
 How to Setup OSX Mail to POP an Exchange Account (Revised 04/27/11) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Opening OS X Mail application The following instructions are written
How to Setup OSX Mail to POP an Exchange Account (Revised 04/27/11) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Opening OS X Mail application The following instructions are written
USB Portable Storage Device: Security Problem Definition Summary
 USB Portable Storage Device: Security Problem Definition Summary Introduction The USB Portable Storage Device (hereafter referred to as the device or the TOE ) is a portable storage device that provides
USB Portable Storage Device: Security Problem Definition Summary Introduction The USB Portable Storage Device (hereafter referred to as the device or the TOE ) is a portable storage device that provides
WiFi and Security Administration
 S&C PulseCloser Outdoor Distribution (15.5 kv, 27 kv, and 38 kv) WiFi and Security Administration Table of Contents Section Page Section Page Introduction Qualified Persons...2 Read this Instruction Sheet....2
S&C PulseCloser Outdoor Distribution (15.5 kv, 27 kv, and 38 kv) WiFi and Security Administration Table of Contents Section Page Section Page Introduction Qualified Persons...2 Read this Instruction Sheet....2
A. USB Portable Storage Device (PSD) Encryption Procedure
 A. USB Portable Storage Device (PSD) Encryption Procedure After installing McAfee Endpoint Encryption software to your Windows PC, you can perform encryption to the USB PSD. I) When the USB PSD is inserted
A. USB Portable Storage Device (PSD) Encryption Procedure After installing McAfee Endpoint Encryption software to your Windows PC, you can perform encryption to the USB PSD. I) When the USB PSD is inserted
Getting Started with Zoom
 Signing in to Zoom Note: this is not necessary to join meetings. Getting Started with Zoom 1. Go to https://trentu.zoom.us. 2. Click Sign In. 3. Login using your Trent username and password. Download the
Signing in to Zoom Note: this is not necessary to join meetings. Getting Started with Zoom 1. Go to https://trentu.zoom.us. 2. Click Sign In. 3. Login using your Trent username and password. Download the
Using TrueCrypt to protect data
 Using TrueCrypt to protect data Password protecting and encrypting files one by one is a certainly an effective way to securely store and share data. However, what if you have a lot of files? Creating
Using TrueCrypt to protect data Password protecting and encrypting files one by one is a certainly an effective way to securely store and share data. However, what if you have a lot of files? Creating
ACTIVATE. Rockwell Software Products
 ACTIVATE Rockwell Software Products All Rockwell Automation software products use an electronic process, called FactoryTalk Activation to activate software. FactoryTalk Activation generates activation
ACTIVATE Rockwell Software Products All Rockwell Automation software products use an electronic process, called FactoryTalk Activation to activate software. FactoryTalk Activation generates activation
AIOLOS net access system
 AIOLOS net access system Global Network Monitoring Services AIOLOS Business Network Monitoring System ANMS Protected log in screen via SSL encrypted connection to the monitoring tool of hotel chains guest
AIOLOS net access system Global Network Monitoring Services AIOLOS Business Network Monitoring System ANMS Protected log in screen via SSL encrypted connection to the monitoring tool of hotel chains guest
USING A VIRTUAL PRIVATE NETWORK FOR REMOTE WORKING FEBRUARY 2013
 USING A VIRTUAL PRIVATE NETWORK FOR REMOTE WORKING FEBRUARY 2013 Table of Contents Introduction...3 What is a Virtual Private Network?...3 Why would I want to use a VPN?...3 How can I obtain a VPN?...4
USING A VIRTUAL PRIVATE NETWORK FOR REMOTE WORKING FEBRUARY 2013 Table of Contents Introduction...3 What is a Virtual Private Network?...3 Why would I want to use a VPN?...3 How can I obtain a VPN?...4
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Encrypting your external USB drive on Windows
 Encrypting your external USB drive on Windows To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Encrypting your external USB drive on Windows To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Instruction Manual for BicDroid QDocument (Mac OS X 10.9 or higher)
 Instruction Manual for BicDroid QDocument (Mac OS X 10.9 or higher) (Basic, Premium, and Professional Editions) Version 1.1 BicDroid.com TABLE OF CONTENTS Installation... 1 Registration. 2 Verification
Instruction Manual for BicDroid QDocument (Mac OS X 10.9 or higher) (Basic, Premium, and Professional Editions) Version 1.1 BicDroid.com TABLE OF CONTENTS Installation... 1 Registration. 2 Verification
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
EnCase Portable Demo P A G E 0
 EnCase Portable Demo P A G E 0 EnCase Portable Easy to Use Collection Solution Brent Botta Director of ediscovery Solution Agenda P A G E 2 EnCase Portable Solution What is it? Business Issues to Utilize
EnCase Portable Demo P A G E 0 EnCase Portable Easy to Use Collection Solution Brent Botta Director of ediscovery Solution Agenda P A G E 2 EnCase Portable Solution What is it? Business Issues to Utilize
Identity Finder Setup
 Identity Finder Information Sheet for MAC This document will walk you through how to install, scan, and secure any SI found on your computer, or storage devices using the Identity Finder Software. This
Identity Finder Information Sheet for MAC This document will walk you through how to install, scan, and secure any SI found on your computer, or storage devices using the Identity Finder Software. This
USER MANUAL DataLocker Enterprise
 USER MANUAL DataLocker Enterprise ------------------------ March 2014 ------------------------ 1 Contents At a Glance Advanced 3 Introduction 17 Special features 5 About the Enterprise 19 Master admin
USER MANUAL DataLocker Enterprise ------------------------ March 2014 ------------------------ 1 Contents At a Glance Advanced 3 Introduction 17 Special features 5 About the Enterprise 19 Master admin
TrustKey Tool User Manual
 TrustKey Tool User Manual 1 Table of Contents 1 Introduction... 5 2 TrustKey Product...6 2.1 TrustKey Tool... 6 2.2 TrustKey function modules...7 2.3 TrustKey using environment...7 3 TrustKey Tool Installation...
TrustKey Tool User Manual 1 Table of Contents 1 Introduction... 5 2 TrustKey Product...6 2.1 TrustKey Tool... 6 2.2 TrustKey function modules...7 2.3 TrustKey using environment...7 3 TrustKey Tool Installation...
Office of Information Technologies (OIT)
 Office of Information Technologies (OIT) Encrypting File System (EFS) November 14th, 2007 Contents Introduction... 1 Benefits... 1 How it works... 1 Enabling EFS... 2 Step 1: Obtain an EFS key pair...
Office of Information Technologies (OIT) Encrypting File System (EFS) November 14th, 2007 Contents Introduction... 1 Benefits... 1 How it works... 1 Enabling EFS... 2 Step 1: Obtain an EFS key pair...
Online Backup Solution Features
 CCC Technologies, Inc. 700 Nicholas Blvd., Suite 300 Elk Grove Village, IL 60007 877.282.9227 www.ccctechnologies.com Online Backup Solution Features Introduction Computers are the default storage medium
CCC Technologies, Inc. 700 Nicholas Blvd., Suite 300 Elk Grove Village, IL 60007 877.282.9227 www.ccctechnologies.com Online Backup Solution Features Introduction Computers are the default storage medium
Security and Security Certificates for OpenADR systems. Background. Content:
 Security and Security Certificates for OpenADR systems Content: Background... 1 Setup for OpenADR... 2 Test-, Evaluation-, and Production Certificates... 3 Responsibilities... 3 Certificate Requesting
Security and Security Certificates for OpenADR systems Content: Background... 1 Setup for OpenADR... 2 Test-, Evaluation-, and Production Certificates... 3 Responsibilities... 3 Certificate Requesting
Steganos Secure E-Mail Step by Step Instructions. Introduction STEP 1: INSTALLATION
 Steganos Secure E-Mail Step by Step Instructions Introduction Although more and more PC users learn that an e-mail can be read by a third party as easily as a postcard, e-mail encryption is still quite
Steganos Secure E-Mail Step by Step Instructions Introduction Although more and more PC users learn that an e-mail can be read by a third party as easily as a postcard, e-mail encryption is still quite
Technical Description. DigitalSign 3.1. State of the art legally valid electronic signature. The best, most secure and complete software for
 Technical Description DigitalSign 3.1 State of the art legally valid electronic signature The best, most secure and complete software for Adding digital signatures to any document, in conformance with
Technical Description DigitalSign 3.1 State of the art legally valid electronic signature The best, most secure and complete software for Adding digital signatures to any document, in conformance with
USB Driver Installation for Windows XP
 USB Driver Installation for Windows XP USB Serial Converter Driver Installation for Windows XP CAUTION: You must use the drivers on the CD-ROM supplied with your USB Device. DO NOT download drivers from
USB Driver Installation for Windows XP USB Serial Converter Driver Installation for Windows XP CAUTION: You must use the drivers on the CD-ROM supplied with your USB Device. DO NOT download drivers from
Security Testing & Load Testing for Online Document Management system
 1 Security Testing & Load Testing for Online Document Management system Abstract The client is a leading provider of online technical documentation solutions in UK, they wanted to protect their documents
1 Security Testing & Load Testing for Online Document Management system Abstract The client is a leading provider of online technical documentation solutions in UK, they wanted to protect their documents
Installing Superlock on Windows 7 64-bit
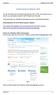 Installing Superlock on Windows 7 64-bit The current Superlock is not directly supported by Win 7, 64 bit. So to make it run on this OS, you can install a Virtual PC with XP Mode from Microsoft. In this
Installing Superlock on Windows 7 64-bit The current Superlock is not directly supported by Win 7, 64 bit. So to make it run on this OS, you can install a Virtual PC with XP Mode from Microsoft. In this
Penetration Test JSPLC. Contact: James, APS (CCNA, CEH) contactep105t@secure- mail.biz
 Contact: James, APS (CCNA, CEH) contactep105t@secure- mail.biz Ok, so this isn t the typical way that a pen test report would start, but we might as well get straight in to it. I am a customer of Sainsbury
Contact: James, APS (CCNA, CEH) contactep105t@secure- mail.biz Ok, so this isn t the typical way that a pen test report would start, but we might as well get straight in to it. I am a customer of Sainsbury
BTD-300 Bluetooth USB Adapter (Version 3.0)
 BTD-300 Bluetooth USB Adapter (Version 3.0) Windows 8, Windows 7, Vista, XP and Mac OS 10.3.9+ Quick Installation Guide 2012 Kinivo LLC. All rights reserved. Kinivo is a trademark of Kinivo LLC. Bluetooth
BTD-300 Bluetooth USB Adapter (Version 3.0) Windows 8, Windows 7, Vista, XP and Mac OS 10.3.9+ Quick Installation Guide 2012 Kinivo LLC. All rights reserved. Kinivo is a trademark of Kinivo LLC. Bluetooth
(C) Global Journal of Engineering Science and Research Management
 DEPENDABLE STORAGE FOR VEHICLE INSURANCE MANAGEMENT THROUGH SECURED ENCRYPTION IN CLOUD COMPUTING Prof.Abhijeet A.Chincholkar *1, Ms.Najuka Todekar 2 *1 M.E. Digital Electronics, JCOET Yavatmal, India.
DEPENDABLE STORAGE FOR VEHICLE INSURANCE MANAGEMENT THROUGH SECURED ENCRYPTION IN CLOUD COMPUTING Prof.Abhijeet A.Chincholkar *1, Ms.Najuka Todekar 2 *1 M.E. Digital Electronics, JCOET Yavatmal, India.
Open-Xchange Guard Major Release v2.0.0. Feature Overview V1.4
 Open-Xchange Guard Major Release v2.0.0 Feature Overview V1.4 2015 Copyright Open-Xchange Inc. This document is the intellectual property of Open-Xchange Inc. The document may be copied in whole or in
Open-Xchange Guard Major Release v2.0.0 Feature Overview V1.4 2015 Copyright Open-Xchange Inc. This document is the intellectual property of Open-Xchange Inc. The document may be copied in whole or in
Sophos SafeGuard Disk Encryption for Mac Startup guide
 Startup guide Document date: January 2011 Content 1 Before you begin... 2 2 Protecting Mac OS X computers... 3 3 Technical support... 4 4 Copyright... 5 1 1 Before you begin 1.1 System requirements Hardware
Startup guide Document date: January 2011 Content 1 Before you begin... 2 2 Protecting Mac OS X computers... 3 3 Technical support... 4 4 Copyright... 5 1 1 Before you begin 1.1 System requirements Hardware
Beyond files forensic OWADE cloud based forensic
 Beyond files forensic OWADE cloud based forensic Elie Bursztein Stanford University Ivan Fontarensky Cassidian Matthieu Martin Stanford University Jean Michel Picod Cassidian 1 The world is moving to the
Beyond files forensic OWADE cloud based forensic Elie Bursztein Stanford University Ivan Fontarensky Cassidian Matthieu Martin Stanford University Jean Michel Picod Cassidian 1 The world is moving to the
RenderStorm Cloud Render (Powered by Squidnet Software): Getting started.
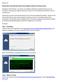 Version 1.0 RenderStorm Cloud Render (Powered by Squidnet Software): Getting started. RenderStorm Cloud Render is an easy to use standalone application providing remote access, job submission, rendering,
Version 1.0 RenderStorm Cloud Render (Powered by Squidnet Software): Getting started. RenderStorm Cloud Render is an easy to use standalone application providing remote access, job submission, rendering,
Guidelines for Developing Cryptographic Service Providers (CSPs) for Acrobat on Windows
 Technical Note Providers (CSPs) for Acrobat C ONTENTS Requirements for Minimal Functionality 1 Recommendations for Maximum Functionality 2 For a Better User Experience Using CSPs in Acrobat 3 Other Recommendations
Technical Note Providers (CSPs) for Acrobat C ONTENTS Requirements for Minimal Functionality 1 Recommendations for Maximum Functionality 2 For a Better User Experience Using CSPs in Acrobat 3 Other Recommendations
Dell NetVault Backup Plug-in for Advanced Encryption 2.2. User s Guide
 Dell Backup Plug-in for Advanced Encryption 2.2 2014 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Dell Backup Plug-in for Advanced Encryption 2.2 2014 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
TATA CONSULTANCY SERVICES LIMITED [ESECURITY - PKI PRODUCTS & SERVICES] ADVANCED TECHNOLOGY CENTRE, DECCANPARK, 1 - SOFTWARE UNITS LAYOUT
![TATA CONSULTANCY SERVICES LIMITED [ESECURITY - PKI PRODUCTS & SERVICES] ADVANCED TECHNOLOGY CENTRE, DECCANPARK, 1 - SOFTWARE UNITS LAYOUT TATA CONSULTANCY SERVICES LIMITED [ESECURITY - PKI PRODUCTS & SERVICES] ADVANCED TECHNOLOGY CENTRE, DECCANPARK, 1 - SOFTWARE UNITS LAYOUT](/thumbs/34/12460172.jpg) DIGITAL CERTIFICATE & IKEY USB TOKEN INSTALLATION - A USER GUIDE CONTACT BRKR BHAVAN, B-BLOCK TANKBUND ROAD HYDERABAD- 500063 WWW.APTS.GOV.IN TATA CONSULTANCY SERVICES LIMITED [ESECURITY - PKI PRODUCTS
DIGITAL CERTIFICATE & IKEY USB TOKEN INSTALLATION - A USER GUIDE CONTACT BRKR BHAVAN, B-BLOCK TANKBUND ROAD HYDERABAD- 500063 WWW.APTS.GOV.IN TATA CONSULTANCY SERVICES LIMITED [ESECURITY - PKI PRODUCTS
Data Superhero Online Backup Whitepaper Data Security
 Data Superhero Online Backup Whitepaper Data Security Cottage Computers Ltd. Page 1 of 5 (April 15, 2008) Table of Contents Contents 1. Data Superhero Offsite Backup Server Secure, Robust and Reliable...
Data Superhero Online Backup Whitepaper Data Security Cottage Computers Ltd. Page 1 of 5 (April 15, 2008) Table of Contents Contents 1. Data Superhero Offsite Backup Server Secure, Robust and Reliable...
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1
 INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
INFORMATION SECURITY GUIDELINE How to Encrypt Files Using Common Applications Revision 1.1 Contents Introduction... 1 Safely Delivering the Encryption Password to the Recipient... 2 How to Encrypt Files
Zoom Instructions and Information
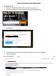 Zoom Instructions and Information 1. Get Zoom set up Everyone call get a free Zoom account, go to http://zoom.us Put in your Andrews University email account and click Sign Up Free Click Sign Up A box
Zoom Instructions and Information 1. Get Zoom set up Everyone call get a free Zoom account, go to http://zoom.us Put in your Andrews University email account and click Sign Up Free Click Sign Up A box
Computer/IT Project LIST. Contact: 9860171201 8796142757
 Computer/IT Project LIST Contact: 9860171201 8796142757 1. Detecting E Banking Phishing Websites Using Associative Classification 2. Vehicle Tracking Using Driver Mobile Gps Tracking 3. Sentiment Analysis
Computer/IT Project LIST Contact: 9860171201 8796142757 1. Detecting E Banking Phishing Websites Using Associative Classification 2. Vehicle Tracking Using Driver Mobile Gps Tracking 3. Sentiment Analysis
2.6.1 Creating an Acronis account... 11 2.6.2 Subscription to Acronis Cloud... 11. 3 Creating bootable rescue media... 12
 USER'S GUIDE Table of contents 1 Introduction...3 1.1 What is Acronis True Image 2015?... 3 1.2 New in this version... 3 1.3 System requirements... 4 1.4 Install, update or remove Acronis True Image 2015...
USER'S GUIDE Table of contents 1 Introduction...3 1.1 What is Acronis True Image 2015?... 3 1.2 New in this version... 3 1.3 System requirements... 4 1.4 Install, update or remove Acronis True Image 2015...
Voice and Video over Wireless LAN
 International Journal of Scientific and Research Publications, Volume 3, Issue 9, September 2013 1 Voice and Video over Wireless LAN Akshay Iyer*, Akshay Badgujar*, Maheshkumar Eaga*, Rohit Iyer* *B.E
International Journal of Scientific and Research Publications, Volume 3, Issue 9, September 2013 1 Voice and Video over Wireless LAN Akshay Iyer*, Akshay Badgujar*, Maheshkumar Eaga*, Rohit Iyer* *B.E
SeChat: An AES Encrypted Chat
 Name: Luis Miguel Cortés Peña GTID: 901 67 6476 GTG: gtg683t SeChat: An AES Encrypted Chat Abstract With the advancement in computer technology, it is now possible to break DES 56 bit key in a meaningful
Name: Luis Miguel Cortés Peña GTID: 901 67 6476 GTG: gtg683t SeChat: An AES Encrypted Chat Abstract With the advancement in computer technology, it is now possible to break DES 56 bit key in a meaningful
Public Auditing for Shared Data in the Cloud by Using AES
 Public Auditing for Shared Data in the Cloud by Using AES 1 Syagamreddy Subbareddy, 2 P.Tejaswi, 3 D.Krishna 1 M.Tech(CSE) Pursuing, 2 Associate Professor, 3 Associate Professor,HOD, 1,2,3 Dept. of Computer
Public Auditing for Shared Data in the Cloud by Using AES 1 Syagamreddy Subbareddy, 2 P.Tejaswi, 3 D.Krishna 1 M.Tech(CSE) Pursuing, 2 Associate Professor, 3 Associate Professor,HOD, 1,2,3 Dept. of Computer
Executable Integrity Verification
 Executable Integrity Verification Abstract Background Determining if a given executable has been trojaned is a tedious task. It is beyond the capabilities of the average end user and even many network
Executable Integrity Verification Abstract Background Determining if a given executable has been trojaned is a tedious task. It is beyond the capabilities of the average end user and even many network
SecureDoc for Mac v6.1. User Manual
 SecureDoc for Mac v6.1 User Manual Copyright 1997-2012 by WinMagic Inc. All rights reserved. Printed in Canada Many products, software and technologies are subject to export control for both Canada and
SecureDoc for Mac v6.1 User Manual Copyright 1997-2012 by WinMagic Inc. All rights reserved. Printed in Canada Many products, software and technologies are subject to export control for both Canada and
DATA PROJECTOR XJ-A146/XJ-A246/XJ-A256
 DATA PROJECTOR XJ-A146/XJ-A246/XJ-A256 E Data Projector Wireless Function Guide Be sure to read the precautions in the Setup Guide that comes with the Data Projector. Be sure to keep all user documentation
DATA PROJECTOR XJ-A146/XJ-A246/XJ-A256 E Data Projector Wireless Function Guide Be sure to read the precautions in the Setup Guide that comes with the Data Projector. Be sure to keep all user documentation
CONNECTING THE RASPBERRY PI TO A NETWORK
 CLASSROOM CHALLENGE CONNECTING THE RASPBERRY PI TO A NETWORK In this lesson you will learn how to connect the Raspberry Pi computer to a network with both a wired and a wireless connection. To complete
CLASSROOM CHALLENGE CONNECTING THE RASPBERRY PI TO A NETWORK In this lesson you will learn how to connect the Raspberry Pi computer to a network with both a wired and a wireless connection. To complete

 Additional information >>> HERE
Additional information >>> HERE  More details >>> HERE
More details >>> HERE