The Importance of an Backbone for Microsoft Exchange and Office 365
|
|
|
- Sheryl Stanley
- 10 years ago
- Views:
Transcription
1 WHITE PAPER The Importance of an Backbone for Microsoft Exchange and Office 365 Gregory Shapiro, VP and CTO
2 Overview Microsoft Exchange is the dominant enterprise system across all organizations. 1 Most large organizations use Exchange on-premises due to the complexity of network topology and the immaturity of cloud service offerings. The Gartner Position on Cloud , published June 1, 2012, found, At the start of 2012, 6% of enterprise users were using public cloud . This paper explores how an on-premises backbone not only helps enable that migration to the cloud, but also explains why a backbone is required even after the migration is complete. At least 75% of these organizations, however, have fewer than 500 users. From that, we can surmise that less than 2% of large enterprise organizations, those with 5000 or more users, have moved to a public cloud offering such as Office 365 s Exchange Online. WHITE PAPER 1 However, that reality is changing quickly as organizations start to look at migrating most, if not all, of their users into cloud-based offerings, particularly Office 365 from Microsoft. The aforementioned Gartner position predicted, By the end of the decade we believe cloud will account for about 65% of the enterprise market. This paper explores how an on-premises backbone not only helps enable that migration to the cloud, but also explains why a backbone is required even after the migration is complete. It also offers guidance on best current practices for an on-premises backbone for groupware services housed on-premises, in the cloud, or in a hybrid mixture of the two. The Backbone The first step in understanding the need for an backbone in an Exchange environment is to understand what an backbone provides and the best practices for deploying that backbone. That deployment would consist of three layers as shown in the figure below. Gateway Security DMZ Backbone Internal Layer Groupware Mailstore Internet Inbound Anti-Spam Anti-Virus Security Protection Simple Routing Outbound Anti-Virus Data Leak Protection Encryption High Volume Bulk Mail Archiving System Mailboxes Calendar Collaboration The first layer provides gateway security and hygiene services such as anti-spam, anti-virus, IP reputation, recipient validation, simple policy protection, and routing. It can exist in an on-premises DMZ or is one of the easiest layers to outsource to the cloud. Spam and virus filtering technologies have become commoditized and there is minimal security risk in having a third-party filter inbound before delivering it to the enduser groupware mailbox. From an OPEX perspective, the hardware required to manage the gateway filtering function can be eliminated along with the costly maintenance, support, and management of those systems.
3 WHITE PAPER The second layer, also known as the internal layer as it is meant to live on the internal corporate network, provides the backbone. As the backbone, it handles transit of all inbound and outbound mail. Inbound mail functions include complex policy-based routing, encryption, outbound anti-virus scanning, and additional inbound protection. As the outbound relay, it is responsible for enforcing outbound policy control with deep content inspection, whether for corporate governance, data leak protection, or compliance/regulatory control. This layer is also responsible for routing and queuing mail from both the groupware layer as well as machine-generated . 2 The third layer is the groupware layer in which the end-user mail store, e.g., Microsoft Exchange, resides. The Groupware Layer (Microsoft Exchange, IBM Lotus Notes, etc.) has proven to be more technically challenging to migrate to the cloud, but it also provides the greatest ROI some enterprises dedicate up to 95 percent of their IT messaging support team to manage this layer. The ROI that can be achieved by moving this layer to the cloud often outweighs some of the perceived security implications. The gateway security and backbone layers may be logically split to provide separate messaging channels for inbound, outbound, and machine-generated (e.g., application) mail. The Need for an Backbone As discussed, commoditization and reduced risk has made moving the gateway security layer to the cloud the easiest to achieve. Office365 s Exchange Online offers a way to move Exchange groupware services into the cloud, as long as the limitations and security risks of doing so are acceptable (see appendix). However, the backbone itself is not suited to move the cloud. Gartner points out, Companies have found that cloud services lack the flexibility to support custom deployments and are unable to meet specific security, content control and application integration needs. 2 Companies have found that cloud services lack the flexibility to support custom deployments and are unable to meet specific security, content control and application integration needs. These concerns include the ability to meet compliance and regulatory needs, access forensics (logs, tracking, auditing), specify diverse policy-based routing, enforce change management/control, and ensure security requirements such as configuring mandatory TLS, and having local access to corporate data and systems of record (e.g., directory) for policy decisions and content modifications. Moving to the cloud further restricts usage and control, presenting the need for a hybrid infrastructure with an on-premises backbone. With this in mind, this leaves three scenarios for architecting an on-premises backbone infrastructure with Exchange: 1. Keeping the Exchange groupware services on premises. 2. Moving a portion of your user population to Exchange Online. 3. Moving all users to Exchange Online. With an on-premises Exchange environment, the first scenario, the backbone layer provides the needed policy and routing functionality described above. Note that although Exchange does provide basic policy control via Transport Hub rules, those policies are limited in both conditions & actions and Exchange does not support more than 100 transport rules, each limited to 4000 characters. 3 It can also be useful for preventing mail storming by enforcing rate limiting on both incoming and internal mail flows into the Exchange servers. In the second scenario, the backbone has the additional challenge of performing policy based routing to support a segmented workforce under a single corporate identity. In other words, having a consistent with delivery to multiple mailbox storage locations depending on the recipient s department, role, location, or other criteria. This ability is also useful in merger situations that require all employees to begin using one corporate identity before merging their separate mailbox environments.
4 The third scenario, in which all mailboxes are in the cloud, is interesting in that it may lead you to believe that no on-premises infrastructure is necessary. However, in most, if not all, organizations, human-generated is less than 50% of the mail transiting the backbone. Machine-generated from hundreds, possibly thousands, of -enabled applications and systems, many of which are hidden from IT visibility, generate more then half of the backbone traffic. These machine-generating applications require on-premises infrastructure as the cloud may not be able to meet the integration requirements of a number of difficult to integrate applications. Consider, for example, applications that do not know about MX records; or hard code a hostname, or worse an IP address, to contact; or only contact the first IP address returned on a hostname lookup. These applications may also not deal well with latency and availability issues (i.e., may not have queuing abilities or robust timeout handling), necessitating the need for a local submission server. Finally, these applications may not have external network access to connect to a remote infrastructure or may be routing messages to other on-premises applications or systems, making a round trip through the cloud cumbersome and inefficient. WHITE PAPER 3 Although a topic for another paper, moving these applications to the cloud may not be feasible. If the application has years of accumulated and poorly documented business rules embedded in code, and a proliferation of subtle or poorly understood interdependencies with other systems, the risks of breakage when the legacy application is migrated or retired make this a less attractive choice for early cloud adoption. 4 Additionally, applications in the cloud may require opening up external network access to expose internal databases and systems of record. If the application has years of accumulated and poorly documented business rules embedded in code, and a proliferation of subtle or poorly understood interdependencies with other systems, the risks of breakage when the legacy application is migrated or retired make this a less attractive choice for early cloud adoption. For more information on the topic of machine-generated mail, see the Sendmail whitepaper, The Impact of Machine-Generated Messages on Enterprise Infrastructure. Luckily, Microsoft recognizes the need for on-premises backbone infrastructure, even if just for address rewriting, and has provided features for organizations in the last two scenarios in which some or all user mailboxes are in the cloud-based Exchange Online. Microsoft Exchange Online for Enterprises Service Description 5 discusses configuration for both inbound via proper MX record configuration and outbound using the Exchange Online Outbound Smart Host feature. Choosing the Right Backbone With the requirement for an backbone established, the final step is determining the best backbone infrastructure to fulfill that need. This can be accomplished in one of three ways: Internal development via open Employing security 1 source or internally developed appliances, i.e., transforming MTAs, filters, and add-ons 2 point products to act as gateways 3 Using the Sentrion message processing platform Employing the internal development route will provide the lowest up front costs but the highest ongoing development and support costs. For the most simplistic case of creating a choke point between groupware, machine-generated application servers, and inbound/outbound message flows, an open source MTA can be compiled and configured. However, once additional functionality is needed (e.g., rate limiting, policy, DLP, message tracking, reporting, DKIM, etc.), the complexity of finding other open source or point products or writing your own code to fit those needs, integrating them together to function as a unit, and then managing them across multiple servers with configuration control is a daunting task to undertake and will require gurus, coders, and a large system administration staff to maintain. A large investment in time and resources will be spent to build, maintain, troubleshoot, and support the functionality found in a modern messaging platform.
5 WHITE PAPER 4 Using an security appliance as the onsite gateway provides more of the tools necessary to implement policy and control over the mail flow but comes at the cost of locking your abilities down to only what is provided by that security appliance. security appliance point products provide the basic functionality necessary in a closed solution meant to solve specific problems and limiting the configurability to satisfy those problems. Branching out from these limitations is impossible or unsupported in most, if not all, cases. Adding that additional functionality via additional products will still require an in-house integration, resulting in a complex interconnection of appliances and software from multiple vendors to manage. It will not provide a simple backbone with a single management interface for unified configuration and policy control. Challenges will arise such as alternative routing of different classes of mail that require different hygiene and policy handling. End-to-end message tracking and reporting will be difficult to achieve. Finally, a multi-vendor troubleshooting session when something does go wrong can be frustrating. The Sentrion Appliance is an open platform for solving the complex problems found in modern infrastructures. Because the Sentrion is meant to cover all of the complex issues, it is perfectly suited to handle the needs of providing onsite full-content message inspection to enable policy-based control and delivery with unlimited actions on message body, header, and all attachments, as well as complete monitoring and reporting, etc. If functionality isn t included with the base system, the platform allows for extensibility through custom policy extensions, integrated third party applications via the Applications SDK, custom reporting via Premium Reporting, powered by Splunk, etc. Visit the Sendmail Sentrion Application store for further details. Conclusion Regardless of whether Exchange is deployed on-premises, in the cloud using Office 365 s Exchange Online, or a hybrid of the two, an on-premises backbone is a fundamental requirement for a modern messaging infrastructure. That backbone can handle an organization s compliance and regulatory needs, provide access to forensics (logs, tracking, auditing), implement diverse policy-based routing, enforce change management/control, and ensure security requirements, as well as provide transit services to on-premises machine-generated mail. The Sentrion message processing platform is the best-suited choice for providing that modern backbone. Appendix: Office 365 Exchange Online Limitations Migrating portions of your mail infrastructure to the cloud requires compromises based on the cloud provider s limitations. Those limitations can come in the form of usage constraints and your ability to configure and control your environment as needed. It is important to factor these considerations in when deciding which portions of the mail infrastructure make sense to move to the cloud. The Sendmail whitepapers, Moving to the Cloud: Important Things to Consider Before Migrating Your Messaging Infrastructure to the Cloud and Important Information for Enterprises Moving to the Cloud go into detail about the risks, limitations and compromises necessary. However, as it relates to the backbone, lets take a look at some of the limitations of Microsoft s Office 365 offering described in Office 365 s Message and Recipient Limits. 6 These outline a number of limits you must impose to make use of their solution. Many are likely easy to cope with, e.g., no more than 125 attachments per message or 255 characters in a Subject header. However, some will impose severe limits on both users communicating collaboratively as well as mail generating applications: Office 365 does not allow a message, including headers, body, and all attachments, over 25 megabytes. This will require users to find other means of sharing files, possibly outside of policy control of the organization (e.g., external file sharing sites such as DropBox). Mailings can have at most 500 recipients and a sender can send mail to at most 1500 recipients per 24-hour period and only 30 messages per minute. While this may seem reasonable for a human sending mail, it is an unreasonable limitation to place on mail generating applications. Other circumstances can
6 also make this risker. For example: Buggy calendar code creating cancellation request storms, leading to inoperable mailboxes due to users going over the 500 messages per day sending limit. 7 If an attempt is made to overcome those recipient limits via a static distribution group, new restrictions introduce speed bumps in mail delivery once the distribution list reach 5000 members. It also introduces a new maximum message size of only 2 megabytes. An organization can only have up to 100 transport rules. Transport rules are Office 365 s form of policy control and routing. This should be compared to the number of mail routing (e.g., MTA mailertable) entries, mail access table entries (e.g., MTA access database), and distinct policy engine policies in use in your infrastructure. The limit of 100 rules will likely be insufficient to suit an organization s needs. Taken all together, these limitations encourage the use of a hybrid solution in which the person-to-person groupware layer may be appropriate to place in the cloud but the backbone, with its ability to handle flexible policy and routing control, configurable limits, and ability to handle application generated , should remain on-premises or in a tightly coupled private cloud under the organization s control. In fact, you ll find exactly that advice in the Office 365 documentation 8 in which they recognize the need for machine-generated to use an on-premises mail server. WHITE PAPER 5 Footnotes 1. The Museum of and Digital Communication 2. Matthew W. Cain, Combining On-Premises and Cloud Perfect Together?, Published: 5 April 2011, Gartner ID: G Transport Rule Limits, Message and Recipient Limits, 4. Vivek Kundra, U.S. Chief Information Officer, Federal Cloud Computing Strategy, February 8, Matthew W. Cain, Users Share Problems With Office 365 Migration, Published: 26 April 2012, Gartner ID: G
7 About Sendmail, Inc Sendmail provides enterprises with global connectivity, routing, and message delivery between people, systems, and applications. The Sentrion Infrastructure Platform reduces enterprise IT complexity and lowers the cost of integrating critical message content with business processes. Since 1982, thousands of enterprises around the world have relied on Sendmail open source and the award winning Sentrion hard and virtual appliances, and its suite of applications, for intelligent backbone and secure message gateway infrastructure. Unlike proprietary -security appliances, Sentrion provides full-content inspection and policy-based delivery for all collaborative groupware and machine-generated , whether deployed on-premises, in-cloud, or via mobile devices. Sendmail is headquartered in Emeryville, CA with sales and support offices throughout the Americas, Europe, and Asia. Sendmail, Inc Christie Avenue, Suite 350, Emeryville, CA USA Tel: Fax: Copyright Sendmail, Inc. All Rights Reserved. All other company and product names may be trademarks or registered trademarks of their respective organizations. WP
Can an Enterprise Email Backbone Infrastructure be Moved to the Cloud?
 Public Network External Application MTA Can an Enterprise Email Backbone Infrastructure be Moved to the Cloud? Fallback MTA External Corporate MTAs DMZ System 2 External Application MTA Internal Corporate
Public Network External Application MTA Can an Enterprise Email Backbone Infrastructure be Moved to the Cloud? Fallback MTA External Corporate MTAs DMZ System 2 External Application MTA Internal Corporate
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
How To Integrate Hosted Email Security With Office 365 And Microsoft Mail Flow Security With Microsoft Email Security (Hes)
 A Trend Micro Integration Guide I August 2015 Hosted Email Security Integration with Microsoft Office 365» This document highlights the benefits of Hosted Email Security (HES) for Microsoft Office 365
A Trend Micro Integration Guide I August 2015 Hosted Email Security Integration with Microsoft Office 365» This document highlights the benefits of Hosted Email Security (HES) for Microsoft Office 365
Setting up Microsoft Office 365
 Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Email Migration Project Plan for Cisco Cloud Email Security
 Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Cisco Cloud Email Security Interoperability with Microsoft Office 365
 White Paper Cisco Cloud Email Security Interoperability with Microsoft Office 365 We ve all been witness to the cloud evolution and the technologies that have been driven by moving operations and resources
White Paper Cisco Cloud Email Security Interoperability with Microsoft Office 365 We ve all been witness to the cloud evolution and the technologies that have been driven by moving operations and resources
FortiMail Email Filtering. Course 221 (for FortiMail v5.0) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
A NATURAL FIT. Microsoft Office 365 TM and Zix TM Email Encryption. By ZixCorp www.zixcorp.com
 Microsoft Office 365 TM and Zix TM Email Encryption A NATURAL FIT By ZixCorp www.zixcorp.com Microsoft Office 365 TM and Zix TM Email Encryption Page 1 INTRODUCTION IT managers and decision makers are
Microsoft Office 365 TM and Zix TM Email Encryption A NATURAL FIT By ZixCorp www.zixcorp.com Microsoft Office 365 TM and Zix TM Email Encryption Page 1 INTRODUCTION IT managers and decision makers are
email management solutions
 Safeguard business continuity and productivity with Mimecast email management solutions Computacenter and Mimecast in partnership Expert software solutions Computacenter and Mimecast help organisations
Safeguard business continuity and productivity with Mimecast email management solutions Computacenter and Mimecast in partnership Expert software solutions Computacenter and Mimecast help organisations
Selecting Your Essential Cloud Services
 DATASHEET Selecting Your Essential Cloud Services Mimecast s flexible and scalable suite of essential cloud services for Microsoft Exchange removes the risks and complexities of business email management
DATASHEET Selecting Your Essential Cloud Services Mimecast s flexible and scalable suite of essential cloud services for Microsoft Exchange removes the risks and complexities of business email management
Top 10 Features: Clearswift SECURE Email Gateway
 Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
Top 10 Features: Clearswift SECURE Email Gateway Top 10 Features: Clearswift SECURE Email Gateway Modern business simply couldn t function without email. However, both incoming and outgoing messages can
FortiMail Email Filtering Course 221-v2.2 Course Overview
 FortiMail Email Filtering Course 221-v2.2 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to design, configure,
FortiMail Email Filtering Course 221-v2.2 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to design, configure,
INTRODUCTION. Tech-Note
 Tech-Note Optimized Message Processing Real-World Use-Cases for Intelligent Email Security, Policy Enforcement, Routing and Delivery in Complex Business Environments INTRODUCTION Today s typical email
Tech-Note Optimized Message Processing Real-World Use-Cases for Intelligent Email Security, Policy Enforcement, Routing and Delivery in Complex Business Environments INTRODUCTION Today s typical email
EMAIL MANAGEMENT SOLUTIONS SAFEGUARD BUSINESS CONTINUITY AND PRODUCTIVITY WITH MIMECAST
 EMAIL MANAGEMENT SOLUTIONS SAFEGUARD BUSINESS CONTINUITY AND PRODUCTIVITY WITH MIMECAST Enabling user efficiency with a cloud-based email platform With productivity, revenues and reputation at stake, an
EMAIL MANAGEMENT SOLUTIONS SAFEGUARD BUSINESS CONTINUITY AND PRODUCTIVITY WITH MIMECAST Enabling user efficiency with a cloud-based email platform With productivity, revenues and reputation at stake, an
Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion
 Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion Many organizations are embracing cloud technology and moving from complex, rigid on-premise infrastructure and software to the simplicity
Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion Many organizations are embracing cloud technology and moving from complex, rigid on-premise infrastructure and software to the simplicity
SESA Securing Email with Cisco Email Security Appliance Parts 1 and 2
 Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Serial Deployment Quick Start Guide
 PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
FortiMail Email Filtering. Course 221 - for FortiMail v4.0. Course Overview
 FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
Selecting Your Essential Cloud Services for Office 365
 DATASHEET Selecting Your Essential Cloud Services for Office 365 Mimecast provides a rich set of cloud services designed to meet the specific needs of Microsoft Office 365 customers. We effectively remove
DATASHEET Selecting Your Essential Cloud Services for Office 365 Mimecast provides a rich set of cloud services designed to meet the specific needs of Microsoft Office 365 customers. We effectively remove
Symantec Protection Suite Add-On for Hosted Email and Web Security
 Symantec Protection Suite Add-On for Hosted Email and Web Security Overview Your employees are exchanging information over email and the Web nearly every minute of every business day. These essential communication
Symantec Protection Suite Add-On for Hosted Email and Web Security Overview Your employees are exchanging information over email and the Web nearly every minute of every business day. These essential communication
Stop Spam. Save Time.
 Stop Spam. Save Time. A Trend Micro White Paper I January 2015 Stop Spam. Save Time. Hosted Email Security: How It Works» A Trend Micro White Paper January 2015 TABLE OF CONTENTS Introduction 3 Solution
Stop Spam. Save Time. A Trend Micro White Paper I January 2015 Stop Spam. Save Time. Hosted Email Security: How It Works» A Trend Micro White Paper January 2015 TABLE OF CONTENTS Introduction 3 Solution
FortiMail Email Filtering. Course 221 (for FortiMail v4.2) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v4.2) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v4.2) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
Email Security.cloud Configuring DLP on to your email flow and applying security to your hosted email deployment
 Email Security.cloud Configuring DLP on to your email flow and applying security to your hosted email deployment Phil Walters Principal Learning Consultant, Technical Field Enablement Email Security.cloud
Email Security.cloud Configuring DLP on to your email flow and applying security to your hosted email deployment Phil Walters Principal Learning Consultant, Technical Field Enablement Email Security.cloud
Solution Brief FortiMail for Service Providers. Nathalie Rivat
 Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Securing enterprise collaboration through email and file sharing on a unified platform
 Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Securing enterprise collaboration through email and file sharing on a unified platform
 Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
Axway MailGate SC Securing enterprise collaboration through email and file sharing on a unified platform Email is the primary collaboration tool employees use to share information and send large files.
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8
 WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
Exchange 2007/2010 Journaling for Cryoserver
 Exchange 2007/2010 Journaling for Cryoserver How to set up Exchange 2007 / 2010 Journaling, to capture an archive copy of all inbound/outbound and internal mail, for delivery to the Cryoserver system February
Exchange 2007/2010 Journaling for Cryoserver How to set up Exchange 2007 / 2010 Journaling, to capture an archive copy of all inbound/outbound and internal mail, for delivery to the Cryoserver system February
OpenText Fax Servers and Microsoft Office 365
 OpenText Fax Servers and Microsoft Office 365 Integrating Fax with Office 365 E N T E R P R I S E I N F O R M A T I O N M A N A G E M E N T 1 Abstract Cloud-based information technologies promise a number
OpenText Fax Servers and Microsoft Office 365 Integrating Fax with Office 365 E N T E R P R I S E I N F O R M A T I O N M A N A G E M E N T 1 Abstract Cloud-based information technologies promise a number
Mimecast Email Security
 DATA SHEET Mimecast Email Security A fully integrated email security, continuity and archiving cloud based solution that delivers total end-to-end control of your email, mitigating email risks and reducing
DATA SHEET Mimecast Email Security A fully integrated email security, continuity and archiving cloud based solution that delivers total end-to-end control of your email, mitigating email risks and reducing
Top 10 Reasons Enterprises are Moving Security to the Cloud
 ZSCALER EBOOK Top 10 Reasons Enterprises are Moving Security to the Cloud A better approach to security Albert Einstein defined insanity as doing the same thing over and over again and expecting different
ZSCALER EBOOK Top 10 Reasons Enterprises are Moving Security to the Cloud A better approach to security Albert Einstein defined insanity as doing the same thing over and over again and expecting different
Identity & Access Management in the Cloud: Fewer passwords, more productivity
 WHITE PAPER Strategic Marketing Services Identity & Access Management in the Cloud: Fewer passwords, more productivity Cloud services are a natural for small and midsize businesses, with their ability
WHITE PAPER Strategic Marketing Services Identity & Access Management in the Cloud: Fewer passwords, more productivity Cloud services are a natural for small and midsize businesses, with their ability
FortiMail Email Filtering Course 221-v2.0. Course Overview. Course Objectives
 FortiMail Email Filtering Course 221-v2.0 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to configure,
FortiMail Email Filtering Course 221-v2.0 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to configure,
Trend Micro Hosted Email Security Stop Spam. Save Time.
 Trend Micro Hosted Email Security Stop Spam. Save Time. How it Works: Trend Micro Hosted Email Security A Trend Micro White Paper l March 2010 Table of Contents Introduction...3 Solution Overview...4 Industry-Leading
Trend Micro Hosted Email Security Stop Spam. Save Time. How it Works: Trend Micro Hosted Email Security A Trend Micro White Paper l March 2010 Table of Contents Introduction...3 Solution Overview...4 Industry-Leading
Exchange 2010 migration guide
 HOW-TO GUIDE Exchange 2010 migration guide This guide details the best practices to follow when migrating from Microsoft Exchange 2003 to Microsoft Exchange 2010. The guidelines provided explain how to
HOW-TO GUIDE Exchange 2010 migration guide This guide details the best practices to follow when migrating from Microsoft Exchange 2003 to Microsoft Exchange 2010. The guidelines provided explain how to
Workshop purpose and objective
 Messaging Workshop purpose and objective Workshop purpose Facilitate planning discussions for messaging coexistence Considerations of Office 365 limits and features Objectives Identify Microsoft Office
Messaging Workshop purpose and objective Workshop purpose Facilitate planning discussions for messaging coexistence Considerations of Office 365 limits and features Objectives Identify Microsoft Office
Mod 08: Exchange Online FOPE
 Office 365 for SMB Jump Start Mod 08: Exchange Online FOPE Chris Oakman Managing Partner Infrastructure Team Eastridge Technology Stephen Hall Owner & IT Consultant District Computers 1 Jump Start Schedule
Office 365 for SMB Jump Start Mod 08: Exchange Online FOPE Chris Oakman Managing Partner Infrastructure Team Eastridge Technology Stephen Hall Owner & IT Consultant District Computers 1 Jump Start Schedule
On and off premises technologies Which is best for you?
 On and off premises technologies Which is best for you? We don t mind what you buy, as long as it is YELLOW! Warren Sealey and Paul-Christian Garpe On Premises or in the cloud? 1 Agenda Why Symantec? Email
On and off premises technologies Which is best for you? We don t mind what you buy, as long as it is YELLOW! Warren Sealey and Paul-Christian Garpe On Premises or in the cloud? 1 Agenda Why Symantec? Email
5 ways Mimecast relieves the headache of email
 5 ways Mimecast relieves the headache of email A Paralogic Networks Guide www.scholarisintl.com Introduction Email is one of the core internet technologies; for many businesses in the mid-1990s, the very
5 ways Mimecast relieves the headache of email A Paralogic Networks Guide www.scholarisintl.com Introduction Email is one of the core internet technologies; for many businesses in the mid-1990s, the very
PineApp Anti IP Blacklisting
 PineApp Anti IP Blacklisting Whitepaper 2011 Overview ISPs outbound SMTP Services Individual SMTP relay, not server based (no specific protection solutions are stated between the sender and the ISP backbone)
PineApp Anti IP Blacklisting Whitepaper 2011 Overview ISPs outbound SMTP Services Individual SMTP relay, not server based (no specific protection solutions are stated between the sender and the ISP backbone)
Enabling Business Beyond the Corporate Network. Secure solutions for mobility, cloud and social media
 Enabling Business Beyond the Corporate Network Secure solutions for mobility, cloud and social media 3 Trends Transforming Networks and Security Are you dealing with these challenges? Enterprise networks
Enabling Business Beyond the Corporate Network Secure solutions for mobility, cloud and social media 3 Trends Transforming Networks and Security Are you dealing with these challenges? Enterprise networks
Technology Blueprint. Protect Your Email. Get strong security despite increasing email volumes, threats, and green requirements
 Technology Blueprint Protect Your Email Get strong security despite increasing email volumes, threats, and green requirements LEVEL 1 2 3 4 5 SECURITY CONNECTED REFERENCE ARCHITECTURE LEVEL 1 2 4 5 3 Security
Technology Blueprint Protect Your Email Get strong security despite increasing email volumes, threats, and green requirements LEVEL 1 2 3 4 5 SECURITY CONNECTED REFERENCE ARCHITECTURE LEVEL 1 2 4 5 3 Security
T E C H N I C A L S A L E S S O L U T I O N
 Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Eiteasy s Enterprise Email Filter
 Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Cisco Email Security Appliances
 Data Sheet Cisco Email Security Appliances Product Overview Over the past 20 years, email has evolved from a tool used primarily by technical and research professionals to become the backbone of corporate
Data Sheet Cisco Email Security Appliances Product Overview Over the past 20 years, email has evolved from a tool used primarily by technical and research professionals to become the backbone of corporate
SECURE YOUR DATA EXCHANGE WITH SAFE-T BOX
 SECURE YOUR DATA EXCHANGE SAFE-T BOX WHITE PAPER Safe-T. Smart Security Made Simple. 1 The Costs of Uncontrolled Data Exchange 2 Safe-T Box Secure Data Exchange Platform 2.1 Business Applications and Data
SECURE YOUR DATA EXCHANGE SAFE-T BOX WHITE PAPER Safe-T. Smart Security Made Simple. 1 The Costs of Uncontrolled Data Exchange 2 Safe-T Box Secure Data Exchange Platform 2.1 Business Applications and Data
V1.4. Spambrella Email Continuity SaaS. August 2
 V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
Websense Email Security Transition Guide
 Websense Email Security Transition Guide Websense Email Security Gateway v7.6 2011, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA R140611760 Published August 2011
Websense Email Security Transition Guide Websense Email Security Gateway v7.6 2011, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA R140611760 Published August 2011
Email security Cloud vs. On-premise solutions
 GFI White Paper Email security Cloud vs. On-premise solutions Choosing whether to put your email security in the cloud or host it on premise is a major decision. Hopefully this white paper will help. Contents
GFI White Paper Email security Cloud vs. On-premise solutions Choosing whether to put your email security in the cloud or host it on premise is a major decision. Hopefully this white paper will help. Contents
MICROSOFT EXCHANGE SERVER 2007 upgrade campaign. Telesales script
 MICROSOFT EXCHANGE SERVER 2007 upgrade campaign Telesales script This document was created to help prepare an outbound telesales professional for a Microsoft Exchange Server 2007 upgrade sales call. This
MICROSOFT EXCHANGE SERVER 2007 upgrade campaign Telesales script This document was created to help prepare an outbound telesales professional for a Microsoft Exchange Server 2007 upgrade sales call. This
Why SAAS makes sense: The benefits of Cloud Computing for Email Archiving
 Why SAAS makes sense: The benefits of Cloud Computing for Email Archiving Confidentiality This document contains confidential material that is proprietary to Gradian Systems Ltd. The material, ideas, and
Why SAAS makes sense: The benefits of Cloud Computing for Email Archiving Confidentiality This document contains confidential material that is proprietary to Gradian Systems Ltd. The material, ideas, and
How to Build an Effective Mail Server Defense
 How to Build an Effective Mail Server Defense A multi-stage approach to securing your email communication August, 21 2006 Author: Alin Dobre, Head of Customer Support, AXIGEN GECAD Technologies 10A Dimitrie
How to Build an Effective Mail Server Defense A multi-stage approach to securing your email communication August, 21 2006 Author: Alin Dobre, Head of Customer Support, AXIGEN GECAD Technologies 10A Dimitrie
Mailwall Remote Features Tour Datasheet
 Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN. Albin Penič Technical Team Leader Eastern Europe
 INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN Albin Penič Technical Team Leader Eastern Europe Trend Micro 27 years focused on security software Headquartered
INCREASINGLY, ORGANIZATIONS ARE ASKING WHAT CAN T GO TO THE CLOUD, RATHER THAN WHAT CAN Albin Penič Technical Team Leader Eastern Europe Trend Micro 27 years focused on security software Headquartered
Scalability in Log Management
 Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com [email protected] Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Whitepaper Scalability in Log Management Research 010-021609-02 ArcSight, Inc. 5 Results Way, Cupertino, CA 95014, USA www.arcsight.com [email protected] Corporate Headquarters: 1-888-415-ARST EMEA Headquarters:
Mimecast Large File Send
 DATASHEET Mimecast Large File Send For sending large files, lets go back to email Mimecast Large File Send simplifies large file sharing for users by removing the complexity and frustration associated
DATASHEET Mimecast Large File Send For sending large files, lets go back to email Mimecast Large File Send simplifies large file sharing for users by removing the complexity and frustration associated
ZSCALER EMAIL SECURITY CLOUD FOR LARGE AND MEDIUM ENTERPRISE
 The Leader in Cloud Security DATA SHEET ZSCALER EMAIL SECURITY CLOUD FOR LARGE AND MEDIUM ENTERPRISE OVERVIEW Email volume is growing every day. Administrators struggle with a growing number of appliances
The Leader in Cloud Security DATA SHEET ZSCALER EMAIL SECURITY CLOUD FOR LARGE AND MEDIUM ENTERPRISE OVERVIEW Email volume is growing every day. Administrators struggle with a growing number of appliances
Websense Messaging Security Solutions. Websense Email Security Websense Hosted Email Security Websense Hybrid Email Security
 Websense Email Security Websense Hosted Email Security Websense Hybrid Email Security Websense Messaging Security Solutions The Websense Approach to Messaging Security Websense enables organizations to
Websense Email Security Websense Hosted Email Security Websense Hybrid Email Security Websense Messaging Security Solutions The Websense Approach to Messaging Security Websense enables organizations to
COMBATING SPAM. Best Practices OVERVIEW. White Paper. March 2007
 COMBATING SPAM Best Practices March 2007 OVERVIEW Spam, Spam, More Spam and Now Spyware, Fraud and Forgery Spam used to be just annoying, but today its impact on an organization can be costly in many different
COMBATING SPAM Best Practices March 2007 OVERVIEW Spam, Spam, More Spam and Now Spyware, Fraud and Forgery Spam used to be just annoying, but today its impact on an organization can be costly in many different
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
No per user or mail box pricing restrictions. Bundled pricing integrated with Antispam, Antivirus, Antispyware and Antimalware
 Fortinet Lowers TCO No per user or mail box pricing restrictions Bundled pricing integrated with Antispam, Antivirus, Antispyware and Antimalware Cost on average is approximately 50% less than traditional
Fortinet Lowers TCO No per user or mail box pricing restrictions Bundled pricing integrated with Antispam, Antivirus, Antispyware and Antimalware Cost on average is approximately 50% less than traditional
Evaluation Guide. eprism Messaging Security Suite. 800-782-3762 www.edgewave.com V8.200
 800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
800-782-3762 www.edgewave.com Welcome to EdgeWave Messaging Security! This short guide is intended to help administrators setup and test the EdgeWave Messaging Security Suite for evaluation purposes. A
INTRODUCING isheriff CLOUD SECURITY
 INTRODUCING isheriff CLOUD SECURITY isheriff s cloud-based, multi-layered, threat protection service is the simplest and most cost effective way to protect your organization s data and devices from cyber-threats.
INTRODUCING isheriff CLOUD SECURITY isheriff s cloud-based, multi-layered, threat protection service is the simplest and most cost effective way to protect your organization s data and devices from cyber-threats.
Email Encryption. Administrator Guide
 Email Encryption Administrator Guide Email Encryption Administrator Guide Documentation version: 1.0 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo,
Email Encryption Administrator Guide Email Encryption Administrator Guide Documentation version: 1.0 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo,
Cisco Email Security Appliances
 Data Sheet Cisco Email Security Appliances Product Overview Over the past 20 years, email has evolved from a tool used primarily by technical and research professionals to become the backbone of corporate
Data Sheet Cisco Email Security Appliances Product Overview Over the past 20 years, email has evolved from a tool used primarily by technical and research professionals to become the backbone of corporate
itg CloudBase is a suite of fully managed Hybrid & Private Cloud Services ready to support your business onwards and upwards into the future.
 Web Filtering Email Filtering Mail Archiving Cloud Backup Disaster Recovery Virtual Machines Private Cloud itg CloudBase is a suite of fully managed Hybrid & Private Cloud Services ready to support your
Web Filtering Email Filtering Mail Archiving Cloud Backup Disaster Recovery Virtual Machines Private Cloud itg CloudBase is a suite of fully managed Hybrid & Private Cloud Services ready to support your
Avoid the Hidden Costs of AD FS with Okta
 Okta White paper Avoid the Hidden Costs of AD FS with Okta Okta Inc. 301 Brannan Street, Suite 300 San Francisco CA, 94107 [email protected] 1-888-722-7871 wp-adfs-031413 Table of Contents 1 Challenges of
Okta White paper Avoid the Hidden Costs of AD FS with Okta Okta Inc. 301 Brannan Street, Suite 300 San Francisco CA, 94107 [email protected] 1-888-722-7871 wp-adfs-031413 Table of Contents 1 Challenges of
Google Apps & Chromebooks for Education Deployment Best Practices
 Google Apps & Chromebooks for Education Deployment Best Practices February 3, 2016 Edward Doan @edwardd / google.com/+edwarddoan Topics Google Apps for Education Chromebooks for Education Chrome Device
Google Apps & Chromebooks for Education Deployment Best Practices February 3, 2016 Edward Doan @edwardd / google.com/+edwarddoan Topics Google Apps for Education Chromebooks for Education Chrome Device
How to Avoid the Headache of User Mailbox Quotas
 How to Avoid the Headache of User Mailbox Quotas Email Archiving Top Four Storage Management Challenges and Solutions Executive Summary Corporate email contains business critical information which is relied
How to Avoid the Headache of User Mailbox Quotas Email Archiving Top Four Storage Management Challenges and Solutions Executive Summary Corporate email contains business critical information which is relied
TEAL: Transparent Email Archiving Library
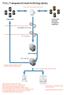 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
Data Sheet: Endpoint Security Symantec Protection Suite Enterprise Edition Trusted protection for endpoints and messaging environments
 Trusted protection for endpoints and messaging environments Overview Symantec Protection Suite Enterprise Edition creates a protected endpoint and messaging environment that is secure against today s complex
Trusted protection for endpoints and messaging environments Overview Symantec Protection Suite Enterprise Edition creates a protected endpoint and messaging environment that is secure against today s complex
WEBSENSE EMAIL SECURITY SOLUTIONS OVERVIEW
 WEBSENSE EMAIL SECURITY SOLUTIONS OVERVIEW Challenge The nature of email threats has changed over the past few years. Gone are the days when email security, better known as anti-spam, was primarily tasked
WEBSENSE EMAIL SECURITY SOLUTIONS OVERVIEW Challenge The nature of email threats has changed over the past few years. Gone are the days when email security, better known as anti-spam, was primarily tasked
Symantec Messaging Gateway 10.5
 Powerful email gateway protection Data Sheet: Messaging Security Overview Symantec Messaging Gateway enables organizations to secure their email and productivity infrastructure with effective and accurate
Powerful email gateway protection Data Sheet: Messaging Security Overview Symantec Messaging Gateway enables organizations to secure their email and productivity infrastructure with effective and accurate
Mimecast Unified Email Management
 DATA SHEET Mimecast Unified Email Management An always-on, cloud-based email security solution that reduces the complexity of protecting your organization from malware, spam and data leakage. Mimecast
DATA SHEET Mimecast Unified Email Management An always-on, cloud-based email security solution that reduces the complexity of protecting your organization from malware, spam and data leakage. Mimecast
Technical Note. ISP Protection against BlackListing. FORTIMAIL Deployment for Outbound Spam Filtering. Rev 2.2
 Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
The Cost Effective Migration to Integrated Hybrid SaaS Email Security
 y The Cost Effective Migration to Integrated SaaS Email Security An Osterman Research White Paper Published July 2010 SPONSORED BY #$!#%&'()*(!!!!"#$!#%&'()*( Osterman Research, Inc. P.O. Box 1058 Black
y The Cost Effective Migration to Integrated SaaS Email Security An Osterman Research White Paper Published July 2010 SPONSORED BY #$!#%&'()*(!!!!"#$!#%&'()*( Osterman Research, Inc. P.O. Box 1058 Black
The Advantages of Security as a Service versus On-Premise Security
 The Advantages of Security as a Service versus On-Premise Security ABSTRACT: This document explores the growing trend of hosted/managed security as a service and why the cloud is quickly becoming the preferred
The Advantages of Security as a Service versus On-Premise Security ABSTRACT: This document explores the growing trend of hosted/managed security as a service and why the cloud is quickly becoming the preferred
INFORMATION PROTECTED
 INFORMATION PROTECTED Symantec Protection Suite Effective, comprehensive threat protection Safeguarding your organization s business-critical assets in today s ever-changing threat landscape has never
INFORMATION PROTECTED Symantec Protection Suite Effective, comprehensive threat protection Safeguarding your organization s business-critical assets in today s ever-changing threat landscape has never
Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs
 Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs P/N 500205 July 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 1 Integrated VPN/firewall Page 2 placed
Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs P/N 500205 July 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 1 Integrated VPN/firewall Page 2 placed
Mail-SeCure for virtualized environment
 OUR INNOVATION YOUR SECURITY Mail-SeCure for virtualized environment OVERVIEW More and more companies are moving towards a virtualized IT-environment, where several network services (email, web surfing
OUR INNOVATION YOUR SECURITY Mail-SeCure for virtualized environment OVERVIEW More and more companies are moving towards a virtualized IT-environment, where several network services (email, web surfing
Advantages of Managed Security Services
 Advantages of Managed Security Services Cloud services via MPLS networks for high security at low cost Get Started Now: 877.611.6342 to learn more. www.megapath.com Executive Summary Protecting Your Network
Advantages of Managed Security Services Cloud services via MPLS networks for high security at low cost Get Started Now: 877.611.6342 to learn more. www.megapath.com Executive Summary Protecting Your Network
Load Balancing Exchange 2007 SP1 Hub Transport Servers using Windows Network Load Balancing Technology
 Load Balancing Exchange 2007 SP1 Hub Transport Servers using Windows Network Load Balancing Technology Introduction Exchange Server 2007 (RTM and SP1) Hub Transport servers are resilient by default. This
Load Balancing Exchange 2007 SP1 Hub Transport Servers using Windows Network Load Balancing Technology Introduction Exchange Server 2007 (RTM and SP1) Hub Transport servers are resilient by default. This
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Email Integration for Open Text Fax Appliance and Open Text Fax Appliance, Premier Edition
 Email Integration for Open Text Fax Appliance and Open Text Fax Appliance, Premier Edition Open Text Fax and Document Distribution Group October 2009 2 White Paper Contents Introduction...3 Who Should
Email Integration for Open Text Fax Appliance and Open Text Fax Appliance, Premier Edition Open Text Fax and Document Distribution Group October 2009 2 White Paper Contents Introduction...3 Who Should
