Solution Brief FortiMail for Service Providers. Nathalie Rivat
|
|
|
- Ashley Osborn Lester
- 10 years ago
- Views:
Transcription
1 Solution Brief FortiMail for Service Providers Nathalie Rivat
2 Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam for internal mail servers Free mailboxes for ADSL/3G subscribers Corporate employee mailboxes FortiMail for Mail Service Providers Inbound antispam for enterprise customers Deployment options: Hosted AV/AS - In the cloud Remote AV/AS - As a CPE device Key Features FortiMail Product Line
3 ISP Blacklisting Context When a spammer uses ADSL/3G connection to support his illegal activities: The computer is identified as a source of spam by popular DNSBL services (DNS BlackList) As a result, its IP address is registered in a blacklist database Most Internet MTAs refuse mail from blacklisted IP addresses DNSBL is a popular technique, widely used by antispam GWs SOURCE OF SPAM BLACK IP ADSL NETWORK OUTGOING MAIL INTERNET DNSBL SERVER DATABASE OF BLACK IPs DNSBL QUERY REPLY = IP ADDRESS IS LISTED 3G MOBILE NETWORK SMTP CONNECTION IS DENIED MTA ANTISPAM GW SOURCE OF SPAM
4 ISP Blacklisting Subscriber impact Case #1: the black IP is reassigned to a clean 3G/ADSL subscriber The latter can not send mail Case #2: Even more critical (picture below) Multiple subscribers are NATed behind the same public IP address A single infected computer sends out spam The public IP address is blacklisted All subscribers are impacted and can not send mail 3G ALL SOURCES ARE NATED BEHIND THE SAME PUBLIC IP MTA CLEAN SOURCE MOBILE NETWORK INTERNET SMTP CONNECTIONS ARE REFUSED DENIED 3G FW BLACK IP MTA SOURCE OF SPAM
5 ISP Blacklisting Cost Cost of de-registrating IPs from DNSBL databases Fee paid to DNSBL organizations Recurrent / on a weekly basis / Never ending process Management cost Collecting backlisted IPs Contacting DNSBL services Justifying registration end Etc. User experience Bad quality of service Risk to unsubscribe IP Blacklisting protection is business critical This is achieved by filtering outbound mail flow with FortiMail
6 Outbound antispam User Transparency Outbound scanning must not impact users It is not desirable to change the mail client configuration with an explicit outgoing relay User mobility and ease of use Subscribers should be able to send mail directly to the Internet As they were doing before the antispam deployment The antispam solution must be a transparent Unique and prioprietary FortiMail transparent proxy FortiMail intercepts SMTP sessions even though it is not the destination MTA Destination IP = Internet MTA, not FortiMail
7 Outbond antispam Topology Policy-based routing makes sure SMTP sessions of subscribers are redirected to FortiMail for scanning No need for FortiMail to process web, ftp, pop3, etc. traffic This would result in unecessary resource usage No need to redirect/scan incoming mail flow I.E sessions initiated by Internet MTAs SMTP CLIENTS SUBSCRIBER NETWORK OUTGOING MAIL ROUTERS INCOMING MAIL FIREWALL INTERNET MTAs POLICY-BASED ROUTING OUTGOING SESSIONS --> FORTIMAIL DESTINATION MTAs OF OUTGOING MAIL
8 Outbound antispam Protocol Transparency Unique to FortiMail Transparent in the IP layer FortiMail does not change the client source IP address when relaying sessions No interference in the SMTP negotiation SMTP commands are not altered SMTP AUTH is performed by the destination MTA FortiMail does not queue mail if the destination MTA is unreachable The ISP is not in charge of compensating MTA availability by queueing mail Transparent in the SMTP envelop and headers There are no visibles trace of FortiMail processing
9 Outbound antispam Protocol Transparency SMTP-envelope transparency SMTP COMMANDS ARE NOT ALTERED 220 MAILSERVER.FORTINET.COM 220 MAILSERVER.FORTINET.COM SMTP CLIENT MYDOMAIN.COM EHLO ME.MYDOMAIN.COM EHLO ME.MYDOMAIN.COM 250 MAILSERVER.FORTINET.COM 250 MAILSERVER.FORTINET.COM SMTP SERVER FORTINET.COM IP-layer transparency SOURCE AND DESTINATION IP ADDRESSES ARE NOT ALTERED SMTP CLIENT SOURCE IP = DESTINATION IP = SOURCE IP = DESTINATION IP = SMTP SERVER
10 Outbound antispam Filters Dedicated antispam techniques are required Traditional antispam GWs rely on reputation/score of public IP addresses This technique is not relevant for outbound antispam Subscribers may have private IP addresses Not known by central Internet databases Spam should be blocked before the IP address is blacklisted /score is bad Fortinet research team developed specific techniques to efficiently identify outbound spam
11 Identifying 3G subscribers 3G mobile operators: SIM card and MSISDN An MSISDN is the number associated with a SIM card It uniquely identifies subscribers As opposed to IP addresses that are dynamically assigned FortiMail: the only AS GW that retrieves and processes MSISDN Benefit: MSISDN Realtime monitoring/blocking FortiMail dynamically calculates MSISDN reputation And automatically alerts or blocks offending MSISDNs Benefit: MSISDN Reporting MSISDN statistics: Top senders / Src of spam / Src of virus Thanks to FortiMail MSISDN support ISPs can track bad subscribers
12 Identifying 3G subscribers SUBSCRIBER CONNECTS SUBSCRIBER SENDS A MAIL SGSN GGSN ROUTER 3G SUBSCRIBER INTERNET DESTINATION MTA IP ADDRESS IS ASSIGNED RADIUS SERVER RADIUS SERVER SENDS MSISDN + IP ADDRESS SMTP SESSION IS LOGGED WITH MSISDN MSISDN REPUTATION IS UPDATED FOR OFFENDING MSISDN, ALERT IS SENT OR SESSION IS BLOCKED
13 Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam for internal mail servers Free mailboxes for ADSL/3G subscribers Corporate employee mailboxes FortiMail for Mail Service Providers Inbound antispam for enterprise customers Deployment options: Hosted AV/AS - In the cloud Remote AV/AS - As a CPE device Key Features FortiMail Product Line
14 MMS routing for Mobile Operator MMS format MM3: SMTP-based MMS between MMSC and Internet MTAs Used to send out MMS to the Internet MM4: SMTP-based MMS between MMSCs Used to send out MMS to another mobile operator FortiMail relays MM3/MM4 traffic MMSC relays outgoing traffic to FortiMail Incoming traffic is sent to FortiMail before reaching the MMSC MMSC is not directly connected to the Internet or other MMSCs Improved security MM1 MM3 INCOMING INTERNET GRX OUTGOING SUBSCRIBER PHONE MMSC THE SECURE GATEWAY TO CONNECT TO INTERNET & OHTER MMSCs MM4 OTHER OPERATOR MMSC
15 Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam for internal mail servers Free mailboxes for ADSL/3G subscribers Corporate employee mailboxes FortiMail for Mail Service Providers Inbound antispam for enterprise customers Deployment options: Hosted AV/AS - In the cloud Remote AV/AS - As a CPE device Key Features FortiMail Product Line
16 Inbound antispam for ISPs Incoming mail filtering to protect local mailboxes FortiMail provides AV/AS services to filter incoming flow that receives the internal mail servers ISP internal mail server protection Free mailboxes offered to 3G/ADSL subscribers ISP corporate mail server protection Employee mailboxes SUBSCRIBER MAILBOXES EMPLOYEE MAILBOXES SERVICE PROVIDER LOCATION SUBSCRIBER NETWORK OUTGOING SMTP MAIL SERVERS SMTP CLIENTS CORPORATE NETWORK INTERNET INCOMING SMTP SMTP CLIENTS
17 Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam for internal mail servers Free mailboxes for ADSL/3G subscribers Corporate employee mailboxes FortiMail for Mail Service Providers Inbound antispam for enterprise customers Deployment options: Hosted AV/AS - In the cloud Remote AV/AS - As a CPE device Key Features FortiMail Product Line
18 FortiMail for Mail Service Providers Incoming mail filtering AV/AS Protection for enterprise customer domains Deployment option: FortiMail in the cloud Scenario 1: Full hosted services Customer mail servers & FortiMail are located at the ISP site FortiMail protects several customers Scenario 2: Clean pipe only Mailserver located at the customer site FortiMail located at the ISP site protecting several customers Deployment option: FortiMail as CPE device Scenario 3: outsourcing without hosting Mailserver and FortiMail are located at the customer site FortiMail protects a single customer Remote management from Service Provider SOC
19 Mail Service Providers Scenario 1 In the cloud AV/AS services FortiMail is located at the ISP site and handles multiple domains Service Provider delivers clean hosted mailboxes to enterprises Full suite of hosted services (mailserver + AV/AS) ISP offers clean & free hosted mailboxes to ADSL/3G subscribers Internal domain protection Service Provider offers clean mailboxes to employees Corporate domain protection SERVICE PROVIDER LOCATION MAIL SERVERS SMTP CLIENTS CUSTOMER LOCATION OUTGOING SMTP CUSTOMER MAILBOXES INTERNET INCOMING SMTP
20 Mail Service Providers Scenario 2 In the cloud AV/AS services FortiMail is located at the ISP site and handles multiple domains Mail Service Provider delivers clean mail flow to customers = Clean pipes Mailserver is located at the customer premise Hosted AV/AS services FortiMail provides services to remote mail servers SMTP CLIENTS MAIL SERVER OUTGOING SMTP SERVICE PROVIDER LOCATION CUSTOMER LOCATION INTERNET INCOMING SMTP PROTECTION OF MULTIPLE CUSTOMER DOMAINS
21 Mail Service Providers Scenario 3 CPE approach (Customer Premise Equipment) Mail Service Provider remotely managed customer equipments Dedicated FortiMail per customer FortiMail is located at the customer site Remotely managed from Service Provider SOC MAIL SERVER OUTGOING SMTP INCOMING SMTP INTERNET SMTP CLIENTS SERVICE PROVIDER SOC CUSTOMER LOCATION SINGLE CUSTOMER PROTECTION REMOTE MANAGEMENT
22 Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam for internal mail servers Free mailboxes for ADSL/3G subscribers Corporate employee mailboxes FortiMail for Mail Service Providers Inbound antispam for enterprise customers Deployment options: Hosted AV/AS - In the cloud Remote AV/AS - As a CPE device Key Features FortiMail Product Line
23 FortiMail key features for MSP Scalability from SMB to large enterprises & Service Providers Hardware scalability Optional redundant PS, optional hardware RAID, etc. Performance scalability Supports three modes of operation Explicit relay, transparent relay, mail server Supports a high number of domains Up to 20,000 listed domains per box If not explicitely listed: unlimited number of domains Role-based management Per domain configuration rights Per domain logging and reporting
24 FortiMail key features for MSP Same level of features and management through the range Encryption, antispam, antivirus, content filtering, etc. Access to the configuration by GUI or command lines for scripting Large amount of disk storage for logging and spam quarantine even on small appliances From 250GB to several TeraBytes Embedded reporting engine Centralized logging and reporting provided by FortiAnalyzer
25 FortiMail key features for MSP Unique feature-rich HA implementation In addition to traditional configuration synchronization + FortiMail synchronizes mail data for transparent failover Mail queues Mailboxes of quarantined spam + FortiMail provides automatic failover Service availability check (WEB, SMTP, etc.) Interface availability check
26 FortiMail key features for MSP High performance Due to a proprietary MTA development Mail are not queued but processed in real-time Minimizes transmission delay Real-time AV/AS filtering In relay mode, mail are queued ONLY if the destination MTA is not available Minimize size of the queue Simplify queue management
27 FortiMail key features for MSP 100% Fortinet technology No third party agreement for AS engine or AV engine High optimization of the code Highest possible integration of tasks Such as mail routing + antispam filtering + virus blocking Benefit: Performances & Investment protection Mailbox licence free No headhache tracking number of users Cost performance
28 Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam for internal mail servers Free mailboxes for ADSL/3G subscribers Corporate employee mailboxes FortiMail for Mail Service Providers Inbound antispam for enterprise customers Deployment options: Hosted AV/AS - In the cloud Remote AV/AS - As a CPE device Key Features FortiMail Product Line
29 FortiMail Product Line SMALL ENTERPRISE MEDIUM ENTERPRISE LARGE ENTERPRISE SERVICE PROVIDER RECOMMENDED USERS FORTIGUARD MAIL / HOUR FULL AV/AS MAIL / HOUR FORTIMAIL 100 FORTIMAIL 400B FORTIMAIL 2000A / 4000A 4x 10/ GB HD 4x 10/ x 10/100/ GB HD OPTIONAL HD SW RAID 0/1 4x 10/100/1000 REDUNDANT FANs & PS 6x / 12x 250GB HD HD RAID 0/1/5/10/50 < 250 < 1000 > k 380k 7k 50k 160k
30 FortiMail SKUs MODEL SKU DESCRIPTION FortiMail 100 FortiMail 400B FortiMail 2000A FortiMail 4000A FML-100-BDL-X FML-400B-BDL-X FML-2000A-BDL-X FML-4000A-BDL-X 4x 10/100 ports Single 250GB HDD 2x 10/100 4x 10/100/1000 SW RAID 0/1 Single 500GB HDD (additional disk in option) 4x 10/100/1000 Dual CPU Dual Redundant PS HW RAID 0/1/ 6x 250GB HDD 4x 10/100/1000 Dual CPU Dual Redundant PS HW RAID 0/1/5/10/50 12x 250GB HDD 250GB HD FL-400D2 250GB Hard Drive for FML-2000A and FML-4000A 500GB HD SP-D GB Hard drive for FML-400B
31 Thank you
Technical Note. ISP Protection against BlackListing. FORTIMAIL Deployment for Outbound Spam Filtering. Rev 2.2
 Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
FortiMail Email Filtering Course 221-v2.2 Course Overview
 FortiMail Email Filtering Course 221-v2.2 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to design, configure,
FortiMail Email Filtering Course 221-v2.2 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to design, configure,
FortiMail Email Filtering. Course 221 - for FortiMail v4.0. Course Overview
 FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 - for FortiMail v4.0 Course Overview FortiMail Email Filtering is a 3-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221-v2.0. Course Overview. Course Objectives
 FortiMail Email Filtering Course 221-v2.0 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to configure,
FortiMail Email Filtering Course 221-v2.0 Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed to configure,
FortiMail Email Filtering. Course 221 (for FortiMail v5.0) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v5.0) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering. Course 221 (for FortiMail v4.2) Course Overview
 FortiMail Email Filtering Course 221 (for FortiMail v4.2) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
FortiMail Email Filtering Course 221 (for FortiMail v4.2) Course Overview FortiMail Email Filtering is a 2-day instructor-led course with comprehensive hands-on labs to provide you with the skills needed
Technical Note. FORTIMAIL Configuration For Enterprise Deployment. Rev 2.1
 Technical Note FORTIMAIL Configuration For Enterprise Deployment Rev 2.1 April 7, 2009 Table of Contents 1 Introduction... 3 1.1 Objective... 3 1.2 Network deployment... 3 1.3 Convention... 3 2 System
Technical Note FORTIMAIL Configuration For Enterprise Deployment Rev 2.1 April 7, 2009 Table of Contents 1 Introduction... 3 1.1 Objective... 3 1.2 Network deployment... 3 1.3 Convention... 3 2 System
No per user or mail box pricing restrictions. Bundled pricing integrated with Antispam, Antivirus, Antispyware and Antimalware
 Fortinet Lowers TCO No per user or mail box pricing restrictions Bundled pricing integrated with Antispam, Antivirus, Antispyware and Antimalware Cost on average is approximately 50% less than traditional
Fortinet Lowers TCO No per user or mail box pricing restrictions Bundled pricing integrated with Antispam, Antivirus, Antispyware and Antimalware Cost on average is approximately 50% less than traditional
The Leading Email Security Suites
 The Leading Email Security Suites What is SpamSniper? The Leading Email Security Suites for Your Secure Messaging SpamSniper is the leading email security solution which locates in front of mail server
The Leading Email Security Suites What is SpamSniper? The Leading Email Security Suites for Your Secure Messaging SpamSniper is the leading email security solution which locates in front of mail server
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Serial Deployment Quick Start Guide
 PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
SESA Securing Email with Cisco Email Security Appliance Parts 1 and 2
 Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Course Overview Securing Email with Cisco Email Security Appliance (SESA) combines Parts 1 and 2 (SESA1, SESA2) into a single three day course. Students learn to use Cisco Email Security Appliances (ESA's)
Eiteasy s Enterprise Email Filter
 Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
Eiteasy s Enterprise Email Filter Eiteasy s Enterprise Email Filter acts as a shield for companies, small and large, who are being inundated with Spam, viruses and other malevolent outside threats. Spammer
eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide
 eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide This guide is designed to help the administrator configure the eprism Intercept Anti-Spam engine to provide a strong spam protection
eprism Email Security Appliance 6.0 Intercept Anti-Spam Quick Start Guide This guide is designed to help the administrator configure the eprism Intercept Anti-Spam engine to provide a strong spam protection
Web. Anti- Spam. Disk. Mail DNS. Server. Backup
 Email Server Appliance N ew generation of Server Appliance, AirLive, is designed for the SMB or enterprise that needs to install an easy maintained and fully functional mail server. It not only preserves
Email Server Appliance N ew generation of Server Appliance, AirLive, is designed for the SMB or enterprise that needs to install an easy maintained and fully functional mail server. It not only preserves
Government of Canada Managed Security Service (GCMSS) Annex A-5: Statement of Work - Antispam
 Government of Canada Managed Security Service (GCMSS) Date: June 8, 2012 TABLE OF CONTENTS 1 ANTISPAM... 1 1.1 QUALITY OF SERVICE...1 1.2 DETECTION AND RESPONSE...1 1.3 MESSAGE HANDLING...2 1.4 CONFIGURATION...2
Government of Canada Managed Security Service (GCMSS) Date: June 8, 2012 TABLE OF CONTENTS 1 ANTISPAM... 1 1.1 QUALITY OF SERVICE...1 1.2 DETECTION AND RESPONSE...1 1.3 MESSAGE HANDLING...2 1.4 CONFIGURATION...2
Email Migration Project Plan for Cisco Cloud Email Security
 Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Sales Tool Email Migration Project Plan for Cisco Cloud Email Security 2014 Cisco and/or its affiliates. All rights reserv ed. This document is Cisco Conf idential. For Channel Partner use only. Not f
Best Practices Revision A. McAfee Email Gateway 7.x Appliances
 Best Practices Revision A McAfee Email Gateway 7.x Appliances COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK ATTRIBUTIONS McAfee, the McAfee logo, McAfee Active Protection,
Best Practices Revision A McAfee Email Gateway 7.x Appliances COPYRIGHT Copyright 2012 McAfee, Inc. Do not copy without permission. TRADEMARK ATTRIBUTIONS McAfee, the McAfee logo, McAfee Active Protection,
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
PowerLink Bandwidth Aggregation Redundant WAN Link and VPN Fail-Over Solutions
 Bandwidth Aggregation Redundant WAN Link and VPN Fail-Over Solutions Find your network example: 1. Basic network with and 2 WAN lines - click here 2. Add a web server to the LAN - click here 3. Add a web,
Bandwidth Aggregation Redundant WAN Link and VPN Fail-Over Solutions Find your network example: 1. Basic network with and 2 WAN lines - click here 2. Add a web server to the LAN - click here 3. Add a web,
eprism Email Security Appliance 6.0 Release Notes What's New in 6.0
 eprism Email Security Appliance 6.0 Release Notes St. Bernard is pleased to announce the release of version 6.0 of the eprism Email Security Appliance. This release adds several new features while considerably
eprism Email Security Appliance 6.0 Release Notes St. Bernard is pleased to announce the release of version 6.0 of the eprism Email Security Appliance. This release adds several new features while considerably
Copyright 2011 Sophos Ltd. Copyright strictly reserved. These materials are not to be reproduced, either in whole or in part, without permissions.
 PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
FortiGate Multi-Threat Security Systems I Administration, Content Inspection and SSL VPN Course #201
 FortiGate Multi-Threat Security Systems I Administration, Content Inspection and SSL VPN Course #201 Course Overview Through this 2-day instructor-led classroom or online virtual training, participants
FortiGate Multi-Threat Security Systems I Administration, Content Inspection and SSL VPN Course #201 Course Overview Through this 2-day instructor-led classroom or online virtual training, participants
INTRODUCTION TO FIREWALL SECURITY
 INTRODUCTION TO FIREWALL SECURITY SESSION 1 Agenda Introduction to Firewalls Types of Firewalls Modes and Deployments Key Features in a Firewall Emerging Trends 2 Printed in USA. What Is a Firewall DMZ
INTRODUCTION TO FIREWALL SECURITY SESSION 1 Agenda Introduction to Firewalls Types of Firewalls Modes and Deployments Key Features in a Firewall Emerging Trends 2 Printed in USA. What Is a Firewall DMZ
Proxies. Chapter 4. Network & Security Gildas Avoine
 Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Symantec Hosted Mail Security Getting Started Guide
 Symantec Hosted Mail Security Getting Started Guide Redirecting Your MX Record You have successfully activated your domain within the Symantec Hosted Mail Security Console. In order to begin the filtration
Symantec Hosted Mail Security Getting Started Guide Redirecting Your MX Record You have successfully activated your domain within the Symantec Hosted Mail Security Console. In order to begin the filtration
MailFoundry Users Manual. MailFoundry User Manual Revision: MF2005071100 Copyright 2005, Solinus Inc. All Rights Reserved
 MailFoundry User Manual Revision: MF2005071100 Copyright 2005, Solinus Inc. All Rights Reserved Page 1 of 91 Chapter 1: Introduction... 4 What are Spam Profiles?... 4 Models Covered In This Manual... 4
MailFoundry User Manual Revision: MF2005071100 Copyright 2005, Solinus Inc. All Rights Reserved Page 1 of 91 Chapter 1: Introduction... 4 What are Spam Profiles?... 4 Models Covered In This Manual... 4
Post Genie TM WebMail Server 2400/2208R
 具 備 容 錯 備 援 機 制 的 網 路 郵 件 伺 服 器 Post Genie TM WebMail Server 2400/2208R October 27, 2004 Presented by Kevin Liou Product Manager, Message Communication QNAP, Member of ICP Electronics In.c (IEI) 1 Agenda
具 備 容 錯 備 援 機 制 的 網 路 郵 件 伺 服 器 Post Genie TM WebMail Server 2400/2208R October 27, 2004 Presented by Kevin Liou Product Manager, Message Communication QNAP, Member of ICP Electronics In.c (IEI) 1 Agenda
Barracuda Spam Firewall User s Guide
 Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2004, Barracuda Networks www.barracudanetworks.com All rights reserved. Use of this product and this manual is subject to license. Information
Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2004, Barracuda Networks www.barracudanetworks.com All rights reserved. Use of this product and this manual is subject to license. Information
Mod 08: Exchange Online FOPE
 Office 365 for SMB Jump Start Mod 08: Exchange Online FOPE Chris Oakman Managing Partner Infrastructure Team Eastridge Technology Stephen Hall Owner & IT Consultant District Computers 1 Jump Start Schedule
Office 365 for SMB Jump Start Mod 08: Exchange Online FOPE Chris Oakman Managing Partner Infrastructure Team Eastridge Technology Stephen Hall Owner & IT Consultant District Computers 1 Jump Start Schedule
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Mailwall Remote Features Tour Datasheet
 Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Management Portal & Dashboard Mailwall Remote Features Tour Datasheet Feature Benefit Learn More Screenshot Cloud based portal Securely manage your web filtering policy wherever you are without need for
Mithi Connect Server deployment options
 Page 1 of 8 Mithi Connect Server deployment options aintroduction 2 Mail servers 2 Single/Standalone server setups 2 Multiple server setups 4 Co-existence with proprietary mailing solutions such as Exchange
Page 1 of 8 Mithi Connect Server deployment options aintroduction 2 Mail servers 2 Single/Standalone server setups 2 Multiple server setups 4 Co-existence with proprietary mailing solutions such as Exchange
Intercept Anti-Spam Quick Start Guide
 Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
T E C H N I C A L S A L E S S O L U T I O N
 Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Trend Micro Email Encryption Gateway 5.0 Deployment Guide January 2009 Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 USA T +1.800.228.5651 / +1.408.257.1500 F +1.408.257.2003 www.trendmicro.com
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Websense Email Security Transition Guide
 Websense Email Security Transition Guide Websense Email Security Gateway v7.6 2011, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA R140611760 Published August 2011
Websense Email Security Transition Guide Websense Email Security Gateway v7.6 2011, Websense Inc. All rights reserved. 10240 Sorrento Valley Rd., San Diego, CA 92121, USA R140611760 Published August 2011
Barracuda Spam&Virus Firewall v5.1 a Web Filter v5.0 Nové funkce, pluginy a uživatelská vylepšení. Jiří Blažek, Product Manager
 Barracuda Spam&Virus Firewall v5.1 a Web Filter v5.0 Nové funkce, pluginy a uživatelská vylepšení Jiří Blažek, Product Manager WEB FILTER - NEW TO VERSION 5.0-1/2 - New role based administration, configurable
Barracuda Spam&Virus Firewall v5.1 a Web Filter v5.0 Nové funkce, pluginy a uživatelská vylepšení Jiří Blažek, Product Manager WEB FILTER - NEW TO VERSION 5.0-1/2 - New role based administration, configurable
Deployment Guide. For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php
 Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Configuring Your Gateman Email Server
 Configuring Your Gateman Email Server Your Gateman Lifestyle Server includes an Email Server that provides users access to email via an email client and via your web browser using your laptop and mobile
Configuring Your Gateman Email Server Your Gateman Lifestyle Server includes an Email Server that provides users access to email via an email client and via your web browser using your laptop and mobile
AntiVirus and AntiSpam email scanning The Axigen-Kaspersky solution
 AntiVirus and AntiSpam email scanning The Axigen-Kaspersky solution The present document offers a comprehensive analysis of the ways to secure corporate email systems. It provides an expert opinion on
AntiVirus and AntiSpam email scanning The Axigen-Kaspersky solution The present document offers a comprehensive analysis of the ways to secure corporate email systems. It provides an expert opinion on
Implementing MDaemon as an Email Security Gateway to Exchange Server
 Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
Implementing MDaemon as an Email Security Gateway to Exchange Server Introduction MDaemon is widely deployed as a very effective antispam/antivirus gateway to Exchange. For optimum performance, we recommend
ZyWALL USG ZLD 3.0 Support Notes
 2012 ZyWALL USG ZLD 3.0 Support Notes CSO ZyXEL 2/1/2012 Scenario 1 - Reserving Highest Bandwidth Management Priority for VoIP Traffic 1.1 Application scenario In an enterprise network, there are various
2012 ZyWALL USG ZLD 3.0 Support Notes CSO ZyXEL 2/1/2012 Scenario 1 - Reserving Highest Bandwidth Management Priority for VoIP Traffic 1.1 Application scenario In an enterprise network, there are various
V1.4. Spambrella Email Continuity SaaS. August 2
 V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
Zscaler Internet Security Frequently Asked Questions
 Zscaler Internet Security Frequently Asked Questions 1 Technical FAQ PRODUCT LICENSING & PRICING How is Zscaler Internet Security Zscaler Internet Security is licensed on number of Cradlepoint devices
Zscaler Internet Security Frequently Asked Questions 1 Technical FAQ PRODUCT LICENSING & PRICING How is Zscaler Internet Security Zscaler Internet Security is licensed on number of Cradlepoint devices
F-Secure Internet Gatekeeper
 F-Secure Internet Gatekeeper TOC F-Secure Internet Gatekeeper Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper...5 1.1 Features...6 Chapter 2: Deployment...8 2.1 System requirements...9 2.2
F-Secure Internet Gatekeeper TOC F-Secure Internet Gatekeeper Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper...5 1.1 Features...6 Chapter 2: Deployment...8 2.1 System requirements...9 2.2
Barracuda Spam Firewall Administrator s Guide
 Barracuda Spam Firewall Administrator s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license.
Barracuda Spam Firewall Administrator s Guide 1 Copyright Copyright 2005, Barracuda Networks www.barracudanetworks.com v3.2.22 All rights reserved. Use of this product and this manual is subject to license.
CipherMail Gateway Quick Setup Guide
 CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
Emergic. A Complete Messaging & Security Suite A COMPLETE MESSAGING AND SECURITY SUITE
 Netcore Solutions Pvt. Ltd. 1 of 6 Emergic MailServ A Complete Messaging & Security Suite ERGIC MAILSERV A COMPLETE MESSAGING AND SECURITY SUITE Netcore's Emergic MailServ ( formerly, NS MailServ ) has
Netcore Solutions Pvt. Ltd. 1 of 6 Emergic MailServ A Complete Messaging & Security Suite ERGIC MAILSERV A COMPLETE MESSAGING AND SECURITY SUITE Netcore's Emergic MailServ ( formerly, NS MailServ ) has
The Network Box Anti-Spam Solution
 NETWORK BOX TECHNICAL WHITE PAPER The Network Box Anti-Spam Solution Background More than 2,000 years ago, Sun Tzu wrote if you know yourself but not the enemy, for every victory gained you will also suffer
NETWORK BOX TECHNICAL WHITE PAPER The Network Box Anti-Spam Solution Background More than 2,000 years ago, Sun Tzu wrote if you know yourself but not the enemy, for every victory gained you will also suffer
Introduction to Computer Security Benoit Donnet Academic Year 2015-2016
 Introduction to Computer Security Benoit Donnet Academic Year 2015-2016 1 Agenda Networking Chapter 1: Firewalls Chapter 2: Proxy Chapter 3: Intrusion Detection System Chapter 4: Network Attacks Chapter
Introduction to Computer Security Benoit Donnet Academic Year 2015-2016 1 Agenda Networking Chapter 1: Firewalls Chapter 2: Proxy Chapter 3: Intrusion Detection System Chapter 4: Network Attacks Chapter
Endian Unified Threat Management
 Endian Unified Threat Management Introduction/Demo to Endian UTM lmarzke Lee Marzke (4AERO.com) Infrastructure Consultant: Software Development organizations Specialize in SCM, Process, PM, Tools Just
Endian Unified Threat Management Introduction/Demo to Endian UTM lmarzke Lee Marzke (4AERO.com) Infrastructure Consultant: Software Development organizations Specialize in SCM, Process, PM, Tools Just
Reliable & Secure Email. Professional, Dependable, Complete Easy to Learn, Use and Grow
 Reliable & Secure Email Professional, Dependable, Complete Easy to Learn, Use and Grow About this Presentation Summarizes primary purposes of email, plus the needs of email providers and users. Introduces
Reliable & Secure Email Professional, Dependable, Complete Easy to Learn, Use and Grow About this Presentation Summarizes primary purposes of email, plus the needs of email providers and users. Introduces
How To Set Up A Barcuda Email Server On A Pc Or Mac Or Mac (For Free) With A Webmail Server (For A Limited Time) With An Ipad Or Ipad (For An Ipa) With The Ip
 Version Barracuda Spam Firewall Administrator s Guide Barracuda Networks Inc. 385 Ravendale Drive Mountain View, CA 94043 http://www.barracudanetworks.com 1 Copyright Notice Copyright 2005, Barracuda Networks
Version Barracuda Spam Firewall Administrator s Guide Barracuda Networks Inc. 385 Ravendale Drive Mountain View, CA 94043 http://www.barracudanetworks.com 1 Copyright Notice Copyright 2005, Barracuda Networks
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Astaro Gateway Software Applications
 Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Unified Threat Management, Managed Security, and the Cloud Services Model
 Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Security Management Mail abuse prevented by Origin-based Anti Spam measures Getting started
 Security Management Put to the test: PineApp Mail-Secure 3.60 Mail abuse prevented by Origin-based Anti Spam measures 15.08.2008 Author: Ulrich Roderer With Mail-Secure, PineApp has delivered a security
Security Management Put to the test: PineApp Mail-Secure 3.60 Mail abuse prevented by Origin-based Anti Spam measures 15.08.2008 Author: Ulrich Roderer With Mail-Secure, PineApp has delivered a security
Cisco Small Business ISA500 Series Integrated Security Appliances
 Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Move over, TMG! Replacing TMG with Sophos UTM
 Move over, TMG! Replacing TMG with Sophos UTM Christoph Litzbach, Pre-Sales Engineer NSG 39 Key Features of TMG HTTP Antivirus/spyware URL Filtering HTTPS forward inspection Web Caching Role based access
Move over, TMG! Replacing TMG with Sophos UTM Christoph Litzbach, Pre-Sales Engineer NSG 39 Key Features of TMG HTTP Antivirus/spyware URL Filtering HTTPS forward inspection Web Caching Role based access
Networking for Caribbean Development
 Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Networking for Caribbean Development BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n o g. o r g N E T W O R K I N G F O R C A R I B B E A N D E V E L O P M E N T BELIZE NOV 2 NOV 6, 2015 w w w. c a r i b n
Global Reputation Monitoring The FortiGuard Security Intelligence Database WHITE PAPER
 Global Reputation Monitoring The FortiGuard Security Intelligence Database WHITE PAPER FORTINET Global Reputation Monitoring PAGE 2 Overview Fortinet s FortiGuard Security Services delivers two essential
Global Reputation Monitoring The FortiGuard Security Intelligence Database WHITE PAPER FORTINET Global Reputation Monitoring PAGE 2 Overview Fortinet s FortiGuard Security Services delivers two essential
SPAMfighter SMTP Anti Spam Server
 SPAMfighter SMTP Anti Spam Server Users Manual Copyright SPAMfighter ApS 2005 Revised 4/27/2006 1 Table of Contents 2 Terminology...3 3 Technology...4 3.1 Tunneling and Interception...4 3.2 Content Classification...5
SPAMfighter SMTP Anti Spam Server Users Manual Copyright SPAMfighter ApS 2005 Revised 4/27/2006 1 Table of Contents 2 Terminology...3 3 Technology...4 3.1 Tunneling and Interception...4 3.2 Content Classification...5
Cisco IronPort X1070 Email Security System
 Data Sheet Cisco IronPort X1070 Email Security System As the battle to protect the email perimeter continues, two predominant trends emerge: higher mail volumes and more resource-intensive scanning. The
Data Sheet Cisco IronPort X1070 Email Security System As the battle to protect the email perimeter continues, two predominant trends emerge: higher mail volumes and more resource-intensive scanning. The
Firewalls. Securing Networks. Chapter 3 Part 1 of 4 CA M S Mehta, FCA
 Firewalls Securing Networks Chapter 3 Part 1 of 4 CA M S Mehta, FCA 1 Firewalls Learning Objectives Task Statements 1.3 Recognise function of Telecommunications and Network security including firewalls,..
Firewalls Securing Networks Chapter 3 Part 1 of 4 CA M S Mehta, FCA 1 Firewalls Learning Objectives Task Statements 1.3 Recognise function of Telecommunications and Network security including firewalls,..
provides several new features and enhancements, and resolves several issues reported by WatchGuard customers.
 WatchGuard XCS v10.0 Update 1 Release Notes WatchGuard XCS Build 140312 Revision Date 11 November, 2014 Introduction WatchGuard is pleased to announce the release of WatchGuard XCS v10.0 Update 1. This
WatchGuard XCS v10.0 Update 1 Release Notes WatchGuard XCS Build 140312 Revision Date 11 November, 2014 Introduction WatchGuard is pleased to announce the release of WatchGuard XCS v10.0 Update 1. This
Hosted CanIt. Roaring Penguin Software Inc. 26 April 2011
 Hosted CanIt Roaring Penguin Software Inc. 26 April 2011 1 1 Introduction Thank you for selecting Hosted CanIt. This document explains how Hosted CanIt works and how you should configure your network to
Hosted CanIt Roaring Penguin Software Inc. 26 April 2011 1 1 Introduction Thank you for selecting Hosted CanIt. This document explains how Hosted CanIt works and how you should configure your network to
Email Services Deployment. Administrator Guide
 Email Services Deployment Administrator Guide Email Services Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the
Email Services Deployment Administrator Guide Email Services Deployment Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the
SMTPSWITCH MAILER V6 FEATURES
 SMTPSWITCH MAILER V6 FEATURES 22 Powerful Features Packed in a Single Email Marketing/Bulk Mailing Program! Easy and Advanced WYSIWYG/HTML Editing SMTPSwitch Mailer has a powerful built-in WYSIWYG editor
SMTPSWITCH MAILER V6 FEATURES 22 Powerful Features Packed in a Single Email Marketing/Bulk Mailing Program! Easy and Advanced WYSIWYG/HTML Editing SMTPSwitch Mailer has a powerful built-in WYSIWYG editor
A host-based firewall can be used in addition to a network-based firewall to provide multiple layers of protection.
 A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
Lesson Plans Configuring Exchange Server 2007
 Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Comprehensive Anti-Spam Service
 Comprehensive Anti-Spam Service Chapter 1: Document Scope This document describes how to implement and manage the Comprehensive Anti-Spam Service. This document contains the following sections: Comprehensive
Comprehensive Anti-Spam Service Chapter 1: Document Scope This document describes how to implement and manage the Comprehensive Anti-Spam Service. This document contains the following sections: Comprehensive
IronPort C10 for Small and Medium Businesses
 I r o n P o r t A p p l i a n c e s S I M P L E I N S TA L L AT I O N, E A S Y M A N A G E M E N T, A N D P O W E R F U L P R O T E C T I O N F O R Y O U R E M A I L I N F R A S T R U C T U R E. IronPort
I r o n P o r t A p p l i a n c e s S I M P L E I N S TA L L AT I O N, E A S Y M A N A G E M E N T, A N D P O W E R F U L P R O T E C T I O N F O R Y O U R E M A I L I N F R A S T R U C T U R E. IronPort
McAfee(R) Email Security Virtual Appliance 5.6 Installation Guide
 McAfee(R) Email Security Virtual Appliance 5.6 Installation Guide COPYRIGHT Copyright 2011 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored
McAfee(R) Email Security Virtual Appliance 5.6 Installation Guide COPYRIGHT Copyright 2011 McAfee, Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
TEAL: Transparent Email Archiving Library
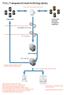 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
The benefits of using a perimeter-based managed service
 W H I T E P A P E R Ensuring Email Security The benefits of using a perimeter-based managed service Ensuring Email Security page 1 Executive Overview With unsolicited email costing businesses millions
W H I T E P A P E R Ensuring Email Security The benefits of using a perimeter-based managed service Ensuring Email Security page 1 Executive Overview With unsolicited email costing businesses millions
anomaly, thus reported to our central servers.
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
FortiMail. Comprehensive Email Security. Comprehensive Email Security
 DATA SHEET FortiMail Comprehensive Email Security FortiMail FortiMail 60D, 200D, 400C, 1000D, 3000C and 3000D Comprehensive Email Security Proven Security FortiMail appliances and virtual appliances are
DATA SHEET FortiMail Comprehensive Email Security FortiMail FortiMail 60D, 200D, 400C, 1000D, 3000C and 3000D Comprehensive Email Security Proven Security FortiMail appliances and virtual appliances are
Security Technology: Firewalls and VPNs
 Security Technology: Firewalls and VPNs 1 Learning Objectives Understand firewall technology and the various approaches to firewall implementation Identify the various approaches to remote and dial-up
Security Technology: Firewalls and VPNs 1 Learning Objectives Understand firewall technology and the various approaches to firewall implementation Identify the various approaches to remote and dial-up
MailEnable Scalability White Paper Version 1.2
 MailEnable Scalability White Paper Version 1.2 Table of Contents 1 Overview...2 2 Core architecture...3 2.1 Configuration repository...3 2.2 Storage repository...3 2.3 Connectors...3 2.3.1 SMTP Connector...3
MailEnable Scalability White Paper Version 1.2 Table of Contents 1 Overview...2 2 Core architecture...3 2.1 Configuration repository...3 2.2 Storage repository...3 2.3 Connectors...3 2.3.1 SMTP Connector...3
Microsoft Exchange Server 2007, Upgrade from Exchange 2000/2003 (3938. 3938/5049/5050) Course KC3065 5 Days OVERVIEW COURSE OBJECTIVES AUDIENCE
 Microsoft Exchange, Upgrade from Exchange 2000/2003 COURSE OVERVIEW This instructor-led course offers Microsoft Exchange Server administrators with the skills they need to manage a Microsoft Exchange infrastructure.
Microsoft Exchange, Upgrade from Exchange 2000/2003 COURSE OVERVIEW This instructor-led course offers Microsoft Exchange Server administrators with the skills they need to manage a Microsoft Exchange infrastructure.
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Avira Managed Email Security AMES FAQ. www.avira.com
 Avira Managed Email Security AMES FAQ www.avira.com Can AMES be used immediately after an account for our organization has been set up in the MyAccount user portal? Using your account requires a change
Avira Managed Email Security AMES FAQ www.avira.com Can AMES be used immediately after an account for our organization has been set up in the MyAccount user portal? Using your account requires a change
Training Guide eprism Email Security Appliance 4.0
 Training Guide eprism Email Security Appliance 4.0 2 Lesson 1 Email Security and eprism Contents LESSON 1...5 EMAIL SECURITY AND EPRISM...5 Mail Delivery Process...6 eprism Overview...7 LESSON 2...9 INSTALLING
Training Guide eprism Email Security Appliance 4.0 2 Lesson 1 Email Security and eprism Contents LESSON 1...5 EMAIL SECURITY AND EPRISM...5 Mail Delivery Process...6 eprism Overview...7 LESSON 2...9 INSTALLING
Email Security 7.4 Administrator s Guide
 Email Security 7.4 Administrator s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Email Security 7.4 Administrator s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
DDL Systems, Inc. ACO MONITOR : Managing your IBM i (or AS/400) using wireless devices. Technical White Paper. April 2014
 DDL Systems, Inc. ACO MONITOR : Managing your IBM i (or AS/400) using wireless devices Technical White Paper April 2014 DDL Systems, Inc. PO Box 1262 Valparaiso, IN 46384 Phone: 866 559-0800 Introduction
DDL Systems, Inc. ACO MONITOR : Managing your IBM i (or AS/400) using wireless devices Technical White Paper April 2014 DDL Systems, Inc. PO Box 1262 Valparaiso, IN 46384 Phone: 866 559-0800 Introduction
Symantec Messaging Gateway for Service Providers 10.5. Implementation Guide
 Symantec Messaging Gateway for Service Providers 10.5 Implementation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of
Symantec Messaging Gateway for Service Providers 10.5 Implementation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of
Exim4U. Email Server Solution For Unix And Linux Systems
 Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
WHITE PAPER. Safeguarding your Email Infrastructure INSIDE MODUS TECHNOLOGY
 WHITE PAPER Safeguarding your Email Infrastructure INSIDE MODUS TECHNOLOGY Table of Contents Executive Summary............................................................. 3 Vircom s modus Technology....................................................
WHITE PAPER Safeguarding your Email Infrastructure INSIDE MODUS TECHNOLOGY Table of Contents Executive Summary............................................................. 3 Vircom s modus Technology....................................................
Firewalls P+S Linux Router & Firewall 2013
 Firewalls P+S Linux Router & Firewall 2013 Firewall Techniques What is a firewall? A firewall is a hardware or software device which is configured to permit, deny, or proxy data through a computer network
Firewalls P+S Linux Router & Firewall 2013 Firewall Techniques What is a firewall? A firewall is a hardware or software device which is configured to permit, deny, or proxy data through a computer network
QUESTION 1 You deploy a server that has the Exchange Server 2013 Mailbox server role and Client Access server role installed.
 QUESTION 1 You deploy a server that has the Exchange Server 2013 Mailbox server role and Client Access server role installed. You need to configure anti-spam to meet the following requirements: - Email
QUESTION 1 You deploy a server that has the Exchange Server 2013 Mailbox server role and Client Access server role installed. You need to configure anti-spam to meet the following requirements: - Email
