The communication concept of a regional stroke unit network based on encrypted image transmission and the DICOM-Mail standard
|
|
|
- Felicia Ray
- 10 years ago
- Views:
Transcription
1 CARS/Springer. All rights reserved. 612 The communication concept of a regional stroke unit network based on encrypted image transmission and the DICOM-Mail standard Engelmann U a, Schroeter A a, Schweitzer T b, Meinzer HP a a German Cancer Research Center, Division Medical & Biological Informatics Im Neuenheimer Feld 280, D Heidelberg, Germany Mailto: [email protected] b Steinbeis-Transferzentrum Medizinische Informatik, Im Neuenheimer Feld 517, D Heidelberg, Germany, URL: Abstract This paper describes the communication concept for a regional stroke network for the exchange of medical images and reports. The data transfer is realized with regular (SMTP). DICOM images are sent as DICOM compliant attachments. Private key encryption is used to ensure data security and privacy. All used protocols are standardized or de-facto standards and allow vendor-independent communication. Different problems and options of the concept realization are discussed. Keywords: Teleradiology, DICOM, Security, SMTP, Stroke 1. Introduction Time is one of the most important factors in the diagnosis, therapy and prognosis of apoplexy or stroke (time is brain!). The German federal state Rhineland-Palatinate (Rheinland-Pfalz) took the political decision to support the establishment of a state-wide competence network. The main purpose is to enable fast and reliable distribution of medical images for the purpose of stroke diagnosis and therapy. The first step is establishing (and funding) of a pilot network connecting the referring hospitals in Neustadt and Worms with the competence centers in Ludwigshafen and Mannheim. Basic requirements have been defined in the request for proposals (RFP) which was organized by a health care consultant company (Pergis, Ludwigshafen, Germany) and a group of subcontracted teleradiology experts. Key requirements of the RFP were the following: Full DICOM compliance for the exchange of data with imaging modalities. Storage of data in databases, advanced functions for the display and analysis of medical images from different modalities. This means, that not a dedicated special purpose communication system, but an integrated system was required.
2 CARS/Springer. All rights reserved. pp The standard data transfer should be realized via (SMTP) and the new DICOM supplement 54. The main reason for that was that s can be sent through firewalls without any changes in their rule-sets. Another reason was the availability of standard encryption methods for . The system should support autorouting and the automatic protocol conversion between DICOM and SMTP. All transmitted data must be encrypted. All communication channels must work with existing and future firewall solutions without security reductions. Several teleradiology and PACS vendors submitted proposals. The selection process was based on the presentation of the solution and proof of concept with software demonstrations. The winner was the Steinbeis Transferzentrum Medizinische Informatik, a technology transfer company in Heidelberg, Germany, with a dedicated software architecture based on their CHILI (tele-) radiology product family. 2. Method CHILI is a radiological workstation with powerful teleradiology functionality, supporting various protocols and de-facto standards for image distribution and interactive teleconferencing of medical images [1]. One important feature of the system is its security concept and the implemented data protection measures based on symmetric and public key encryption [2]. One of the supported transfer protocols is SMTP (simple mail transfer protocol). Thus, users can submit medical images and additional data as regular s. They can also receive data in different formats (DICOM, JPEG, GIF, etc.) from communication partners who can submit images as attachments from a plain mail client only. Most of the requested functionality of the RFP was already available in the CHILI software. Some additional features had to be implemented for the project, such as the automatic encryption/decryption of mails, and automatic protocol conversions between DICOM/SMTP. Data security measures, key management based on public key encryption and open standards have been implemented. The flexible protocol conversion to and from allows easy extension of the teleradiology network to other data types and can provide the basis for a general telemedicine network. 3. Main concepts The principle components of the network are shown in figure 1. Referring hospitals (without expertise in neuroradiology, neurology and neurosurgery) are equipped with one or several CHILI workstations (PCs running Linux). One is acting as a CHILI server and the other are CHILI clients. The server receives the images from the imaging modalities (e.g. CT), PACS or a DICOM workstation via DICOM protocol [3]. The server stores the data in a relational database. The CHILI clients are connected to this database and can view and process the stored data. Teleconferences between all CHILI workstations are possible.
3 CARS/Springer. All rights reserved. 614 The data is submitted to the competence centers via , using the Simple Mail Transfer Protocol (SMTP) [4, 5]. The first versions of SMTP could only transfer 7-bit text messages. The Multipurpose Internet Mail Extensions (MIME) allows the transmission of multipart messages with many kinds of data [6]. The DICOM standard defines in supplement 54 the DICOM MIME Type [7]. This allows to transmit medical images via e- mail in a standardized way. As DICOM images do contain patient data, it is not allowed (by different national and international laws) to transmit the data as clear text over unprotected communication lines. Thus, data protection measures have to be taken into account. One of the implemented methods of our communication concept is to encrypt and sign the mails, resp. parts of it. Galvin et al. define in RFC 1847: Security Multiparts for MIME how parts of can be signed and encrypted [8]. We used MIME Security with OpenPGP for the realization [9, 10]. The data is signed with the private key of the submitting person to protect authenticity and integrity of the data. The public key of the receiver is used to encrypt the data [2].
4 CARS/Springer. All rights reserved. pp We have to take into account that we are submitting large amounts of data. The mail gateways usually limit the size of mails which are processed. Thus, all data is splitted into several mails of acceptable size automatically. The submission process can be activated either by a user or automatically by a so-called autorouter. Different rules can be defined how and to whom the data should be sent and when. A problem is that no user is sitting at the workstation when data is sent automatically. This means that the submitted data cannot be signed by a person. Thus, we use a private key of the workstation (or institution) to create the signature of the data which protects authenticity and integrity of the data. The transmission starts when the DICOM data has been converted into a set of encrypted s. The CHILI server of the referring hospital (see figure 1) sends the data out to the external network (ISDN or Internet) over an optional firewall. The SMTP port of the firewall is usually open for data exchange. The communication server at the competence center receives and temporary stores the incoming data from the referring hospitals. Usually, this server is located outside the hospital LAN in front of a firewall. The teleradiology servers inside the competence centers (behind the firewall) fetch the data periodically via IMAP from the communication server [11]. The fetched data is removed from the communication server and decrypted and reconverted into standard DICOM files and stored in the database of the local CHILI server. Visible and audible alarms inform the personnel of new incoming data which can be reported directly with the viewer of the CHILI workstation (client or server). The autoroutes can be configured to forward the data to one or several other workstations in the competence center. DICOM workstation can also query and retrieve data from the CHILI server. Results and other information can easily be replied to the sender of the data via the user interface of the CHILI program. The digital signature of the reporting physician is used to ensure the authenticity of the report. The replies are again sent as encrypted s to the communication server in front of the firewall. The CHILI server of the referring hospital is then fetching the answer and integrates the report into the local database where it is stored and viewed with the related series of the image data. It is very important is to control the completeness and correctness of the data transfers. All transfers are logged at both sites. Furthermore, sender and receiver can see the progress of the data transfer. A meta-protocol has been implemented on top of SMTP for reliable and secure transfer of confirmations (logging!) and possible failure repair measures, such as autorouting to another competence center. Automatic fail over between the communications servers at different locations has been implemented in this way. The realized CHILI system is not only a dedicated emergency tool. But also a radiological workstation which can be used for reporting in daily routine. Additional clients can be connected to the server if necessary. All clients can perform interactive teleconferences in-
5 CARS/Springer. All rights reserved. 616 house without the need of sending the data to the other workstation. Other options, such as long term archiving, distribution of images in the intranet, mobile clients, or 3D visualization modules [12,13] can be integrated into the "emergency system" easily. 4. Discussion The system has been implemented as described. It is an open concept and based on standards. This ensures the data exchange with other systems. Nevertheless, there were from time to time several options possible. We used OpenPGP for the data encryption. An alternative to this was S/MIME [14]. We choose OpenPGP because it is at the current state easy to implement and as it was as popular as S/MIME. But the latter will be implemented later (see below). Autorouting of data speeds up the transmission from the modality to the competence center. A limitation of this approach is, that the data is then signed by a machine with a machine signature instead of a person. We think that this is acceptable. Another problem is when many people can be the receiver of the data. This means that the sender has to know the name of the person at the other side. Currently, all public signatures are distributed by the CHILI system itself. The private keys are stored at the workstation and activated by a pass-phrase. The system is prepared to use digital signatures on cards, such as a health professional card. It is not yet clear which trust center will be chosen as provider for the certified signature cards. The price of the signatures is an important issue as a university hospital would need about cards for the radiology department only. A budget has not been foreseen for this so far. The Sphinx project launched by German authorities (BSI) aims to improve secure exchange. The projects technological base is the protocol TeleTrust e.v. MailTrusT Version 2. This includes the standards S/MIME, X.509v3 and others [15]. Proprietary products are already on the way, but with the project Ägypten there is now also a Free Software solution going to be realized for popular mail user agents [16]. The integration of this software into our architecture is planned as well. The aim of the GNU Privacy Project is to develop free encryption software for everybody [17]. This project is supported by two German ministries (Bundesministerium für Wirtschaft und Technologie and Bundesministerium des Inneren). It is planned to integrate the resulting free software tool GNU Privacy Guard as well into our realized infrastructure to achieve as much interoperability as possible. 5. Conclusion The realized teleradiology network meets the requirements of the RFP for the stroke unit network. The network can easily be extended and scaled. Redundancy of all critical system components provides high availability.
6 CARS/Springer. All rights reserved. pp The data security concept and flexible protocol conversion allow an easy extension of the teleradiology network to other data types. They can provide the basis for a general telemedicine network. Acknowledgements The pilot project Teleradiology (Stroke-Unit in Rheinland-Pfalz) is funded by the Ministerium für Arbeit, Soziales, Familie und Gesundheit in Mainz, Rheinland-Pfalz, Germany. References 1. Steinbeis-Transferzentrum Medizinische Informatik. CHILI: Second Generation Teleradiology and Telecardiology Baur HJ, Engelmann U. Saurbier F, Schröter A, Baur U, Meinzer HP. How to deal with Security and Privacy Issues in Teleradiology. Computer Methods and Programs in Biomedicine, 53, 1 (1997) NEMA Standards Publication PS Digital Imaging and Communications in Medicine (DICOM). National Electrical Manufacturers Association, 2101 L Street, N.W., Washington, D.C , Resnick P (ed). RFP 2822: Internet Message Format. April Wood D. Programming Internet . O Reilly: Sebastopol Borenstein N, Freed N. RFC 1521: MIME (Multipurpose Internet Mail Extensions) part one: Mechanisms for specifying and describing the format of Internet message bodies, September DICOM Standards Committee, Digital Imaging and Communications in Medicine (DICOM). Supplement 54: DICOM MIME Type Galvin J, Murphy S, Crocker S, Freed N. RFC 1847: Security multiparts for MIME: Multipart/signed and multipart/encrypted, October Elkins M, Del Torto D, Levien R, Roessler T. RFC 3156: Mime security with openpgp, August Callas J, Donnerhacke L, Finney H, Thayer R. RFC 2440: OpenPGP message format, November Mullet D, Mullet K. Managing IMAP. O'Reilly: Sebastopol Engelmann U, Schröter A, Schwab M, Eisenmann U, Meinzer HP. Openness and Flexibility: From Teleradiology to PACS. In: Lemke HU, Vannier MW, Inamura K, Farman AG (Eds). CARS 99. Amsterdam: Elsevier (1999) Engelmann U, Schröter A, Schwab M, Eisenmann U, Bahner ML, Delorme S, Hahne H, Meinzer HP. The Linux-based PACS project at the German Cancer Research Center. Lemke HU, Inamura K, Farman AG, Doi K (Eds). CARS 2000: Computer Assisted Radiology and Surgery. Proceedings of the 14th International Congress and Exhibition. Amsterdam: Elsevier (2000) Ramsdell, B. RFC 2633: S/MIME Version 3 Message Specification, June Bundesamt für Sicherheit in der Informationstechnik. Sphinx Project The GNU Privacy Guard. Projekt Ägypten Das GNU Privacy Projekt (GnuPP).
SECOND GENERATION TELERADIOLOGY
 Reprint of Lemke HU, Inamura K, Vannier MW (Eds): CAR 97: Computer Assisted Radiology and Surgery, 11th International Symposium and Exhibition, Berlin. Amsterdam: Elsevier (1997) 632-637. SECOND GENERATION
Reprint of Lemke HU, Inamura K, Vannier MW (Eds): CAR 97: Computer Assisted Radiology and Surgery, 11th International Symposium and Exhibition, Berlin. Amsterdam: Elsevier (1997) 632-637. SECOND GENERATION
Web-based distribution of radiological images from PACS to EPR
 International Congress Series 1256 (2003) 873 879 Web-based distribution of radiological images from PACS to EPR H. Münch a,b, *, U. Engelmann a, A. Schroeter a,b, H.P. Meinzer a a German Cancer Research
International Congress Series 1256 (2003) 873 879 Web-based distribution of radiological images from PACS to EPR H. Münch a,b, *, U. Engelmann a, A. Schroeter a,b, H.P. Meinzer a a German Cancer Research
MOBILE TELERADIOLOGY: ALL IMAGES EVERYWHERE
 Reprint of: Lemke HU, Vannier MW, Inamura K, Farman AG, Doi K (Eds). CARS 2001: Proceedings of the 15th International Congress and Exhibition. Amsterdam: Elsevier (2001) 798-803. MOBILE TELERADIOLOGY:
Reprint of: Lemke HU, Vannier MW, Inamura K, Farman AG, Doi K (Eds). CARS 2001: Proceedings of the 15th International Congress and Exhibition. Amsterdam: Elsevier (2001) 798-803. MOBILE TELERADIOLOGY:
A teleradiology concept for entire Greenland
 A teleradiology concept for entire Greenland Uwe Engelmann a), H. Münch b), A. Schröter b), T. Schweitzer b), K. Christoph b), R. Eilers c), H. Olesen c), J. Møller Jensen d), H.P. Meinzer a) a Deutsches
A teleradiology concept for entire Greenland Uwe Engelmann a), H. Münch b), A. Schröter b), T. Schweitzer b), K. Christoph b), R. Eilers c), H. Olesen c), J. Møller Jensen d), H.P. Meinzer a) a Deutsches
Teleradiology applications with DICOM-e-mail
 Eur Radiol (2007) 17: 1331 1340 DOI 10.1007/s00330-006-0450-8 COMPUTER APPLICATIONS G. Weisser U. Engelmann S. Ruggiero A. Runa A. Schröter S. Baur M. Walz Teleradiology applications with DICOM-e-mail
Eur Radiol (2007) 17: 1331 1340 DOI 10.1007/s00330-006-0450-8 COMPUTER APPLICATIONS G. Weisser U. Engelmann S. Ruggiero A. Runa A. Schröter S. Baur M. Walz Teleradiology applications with DICOM-e-mail
Teleradiology Building Networks. Dr. Marc Kämmerer. [email protected]
 Teleradiology Building Networks 1 Dr. Marc Kämmerer [email protected] VISUS Company Overview 2 Solution provider for medical image management Comprehensive communication and archiving platform 85+ employees
Teleradiology Building Networks 1 Dr. Marc Kämmerer [email protected] VISUS Company Overview 2 Solution provider for medical image management Comprehensive communication and archiving platform 85+ employees
Teleradiology on a Personal Digital Assistant
 Teleradiology on a Personal Digital Assistant Schweitzer T, Engelmann U, Schröter A, Boraelv E, Meinzer HP www.chili-radiology.com Germany, Sweden Abstract: This paper describes the porting of a teleradiology
Teleradiology on a Personal Digital Assistant Schweitzer T, Engelmann U, Schröter A, Boraelv E, Meinzer HP www.chili-radiology.com Germany, Sweden Abstract: This paper describes the porting of a teleradiology
Secured Mail through PGP Mail Gateway
 Secured Mail through PGP Mail Gateway L. S. Haturusinha, Y. Y. Landersz, A. U. H. Gamage, P. N. Pathiranage, G. T. D. Rodrigo, and M. P. A. W. Gamage Abstract PGP Mail Gateway is a backend server which
Secured Mail through PGP Mail Gateway L. S. Haturusinha, Y. Y. Landersz, A. U. H. Gamage, P. N. Pathiranage, G. T. D. Rodrigo, and M. P. A. W. Gamage Abstract PGP Mail Gateway is a backend server which
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
A Noval Approach for S/MIME
 Volume 1, Issue 7, December 2013 International Journal of Advance Research in Computer Science and Management Studies Research Paper Available online at: www.ijarcsms.com A Noval Approach for S/MIME K.Suganya
Volume 1, Issue 7, December 2013 International Journal of Advance Research in Computer Science and Management Studies Research Paper Available online at: www.ijarcsms.com A Noval Approach for S/MIME K.Suganya
4.1: Securing Applications Remote Login: Secure Shell (SSH) E-Mail: PEM/PGP. Chapter 5: Security Concepts for Networks
 Chapter 2: Security Techniques Background Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application Layer Secure Applications Network Authentication Service: Kerberos 4.1:
Chapter 2: Security Techniques Background Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application Layer Secure Applications Network Authentication Service: Kerberos 4.1:
Image Enabled EMR / EHR
 Image Enabled EMR / EHR A strategic approach to EMR integration and interoperability for diagnostic imaging and related reports The Challenge: In healthcare, imaging is routinely used as a tool for patient
Image Enabled EMR / EHR A strategic approach to EMR integration and interoperability for diagnostic imaging and related reports The Challenge: In healthcare, imaging is routinely used as a tool for patient
The GlobalCerts TM SecureMail Gateway TM
 Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Glob@lCerts PRODUCT OVERVIEW: The GlobalCerts TM SecureMail Gateway TM Automatic encryption and decryption is unique to the SecureMail Gateway. The GlobalCerts SecureMail Gateway is based on a network
Teleradiology in Freiburg
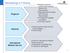 Teleradiology in Freiburg Regional National Regional medical centers with Freiburg Stroke Unit / Neurosurgery Regional trauma surgery with Freiburg Neurosurgery 15 Regional Hospitals connected Very fast
Teleradiology in Freiburg Regional National Regional medical centers with Freiburg Stroke Unit / Neurosurgery Regional trauma surgery with Freiburg Neurosurgery 15 Regional Hospitals connected Very fast
TeamViewer Security Information
 TeamViewer Security Information 2014 TeamViewer GmbH, Last update: 05/2014 Target Group This document is aimed at professional network administrators. The information in this document is of a rather technical
TeamViewer Security Information 2014 TeamViewer GmbH, Last update: 05/2014 Target Group This document is aimed at professional network administrators. The information in this document is of a rather technical
PrivaSphere Gateway Certificate Authority (GW CA)
 PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
Lehrstuhl für Informatik 4 Kommunikation und verteilte Systeme. Firewall
 Chapter 2: Security Techniques Background Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application Layer Chapter 5: Security Concepts for Networks Firewalls Intrusion Detection
Chapter 2: Security Techniques Background Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application Layer Chapter 5: Security Concepts for Networks Firewalls Intrusion Detection
Teleradiology at Freiburg University Hospital
 Teleradiology at Freiburg University Hospital Elmar Kotter, MD, Department of Radiology Maria Onyshchenko-Dubow, International Medical Services Ernst Pelikan, Hospital Computer Centre Universitätsklinikum
Teleradiology at Freiburg University Hospital Elmar Kotter, MD, Department of Radiology Maria Onyshchenko-Dubow, International Medical Services Ernst Pelikan, Hospital Computer Centre Universitätsklinikum
TeamViewer Security Information
 TeamViewer Security Information 2015 TeamViewer GmbH, Last update: 06/2015 Target Group This document is aimed at professional network administrators. The information in this document is of a rather technical
TeamViewer Security Information 2015 TeamViewer GmbH, Last update: 06/2015 Target Group This document is aimed at professional network administrators. The information in this document is of a rather technical
THE BCS PROFESSIONAL EXAMINATIONS BCS Level 6 Professional Graduate Diploma in IT. April 2009 EXAMINERS' REPORT. Network Information Systems
 THE BCS PROFESSIONAL EXAMINATIONS BCS Level 6 Professional Graduate Diploma in IT April 2009 EXAMINERS' REPORT Network Information Systems General Comments Last year examiners report a good pass rate with
THE BCS PROFESSIONAL EXAMINATIONS BCS Level 6 Professional Graduate Diploma in IT April 2009 EXAMINERS' REPORT Network Information Systems General Comments Last year examiners report a good pass rate with
Security-Product by IT SOLUTIONS. Email security at the highest level JULIA. E-Mail Security. Cloud Security
 Security-Product by IT SOLUTIONS Email security at the highest level Cloud Security JULIA MailOffice E-Mail Security wedn Sign Sig To Global protection for your emails Convenience Statistics module: graphic
Security-Product by IT SOLUTIONS Email security at the highest level Cloud Security JULIA MailOffice E-Mail Security wedn Sign Sig To Global protection for your emails Convenience Statistics module: graphic
Using PI to Exchange PGP Encrypted Files in a B2B Scenario
 Using PI to Exchange PGP Encrypted Files in a B2B Scenario Applies to: SAP Net Weaver Process Integration 7.1 (SAP PI 7.1). For more information, visit the SOA Management homepage. Summary This document
Using PI to Exchange PGP Encrypted Files in a B2B Scenario Applies to: SAP Net Weaver Process Integration 7.1 (SAP PI 7.1). For more information, visit the SOA Management homepage. Summary This document
Picture Archiving and Communication systems
 Picture Archiving and Communication systems (PACS) By: Somayeh nabiuni 1 Major limitations of the conventional radiology practice Wasted time - implying diagnostic results many not be obtained in a timely
Picture Archiving and Communication systems (PACS) By: Somayeh nabiuni 1 Major limitations of the conventional radiology practice Wasted time - implying diagnostic results many not be obtained in a timely
SIP Server Requirements
 SIP Server Requirements By Van-Si Nguyen Cyklone CTO and Co-Founder [email protected] 1 Introduction Our company Cyklone is in digital economy business, specialized in video over IP. We are looking for
SIP Server Requirements By Van-Si Nguyen Cyklone CTO and Co-Founder [email protected] 1 Introduction Our company Cyklone is in digital economy business, specialized in video over IP. We are looking for
ELECTRONIC COMMERCE OBJECTIVE QUESTIONS
 MODULE 13 ELECTRONIC COMMERCE OBJECTIVE QUESTIONS There are 4 alternative answers to each question. One of them is correct. Pick the correct answer. Do not guess. A key is given at the end of the module
MODULE 13 ELECTRONIC COMMERCE OBJECTIVE QUESTIONS There are 4 alternative answers to each question. One of them is correct. Pick the correct answer. Do not guess. A key is given at the end of the module
TELE HEALTH CASE STUDY: TELE RADIOLOGY
 TELE HEALTH 2 HealthFore Transforming Healthcare HealthFore Technologies Limited is a global healthcare IT solutions and advisory services company. Our B2B and B2C IT solutions help hospital chains, diagnostic
TELE HEALTH 2 HealthFore Transforming Healthcare HealthFore Technologies Limited is a global healthcare IT solutions and advisory services company. Our B2B and B2C IT solutions help hospital chains, diagnostic
De-Mail. A reliable and secure online communication platform. Armin Wappenschmidt (secunet) More information: www.de-mail.de
 De-Mail A reliable and secure online communication platform Armin Wappenschmidt (secunet) More information: www.de-mail.de 1 Agenda Overview of De-Mail Implementation aspects Current status and outlook
De-Mail A reliable and secure online communication platform Armin Wappenschmidt (secunet) More information: www.de-mail.de 1 Agenda Overview of De-Mail Implementation aspects Current status and outlook
Obtaining a user account and password: To obtain a user account, please submit the following information to AJRR staff:
 AJRR Secure FTP Site Usage www.ajrr-registry.net port 22 Contacts: Randolph Meinzer [email protected] Steve Hamada [email protected] 6300 North River Road Rosemont, IL 60018 p: 847-292-0530 f: 847-292-0531
AJRR Secure FTP Site Usage www.ajrr-registry.net port 22 Contacts: Randolph Meinzer [email protected] Steve Hamada [email protected] 6300 North River Road Rosemont, IL 60018 p: 847-292-0530 f: 847-292-0531
Cornerstones of Security
 Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
7i Imaging on Demand PACS Solution FAQ s
 7i Imaging on Demand PACS Solution FAQ s Standards: 1. Do you use any proprietary software to manage the images? No, our image management software manages the images and is fully DICOM compliant with no
7i Imaging on Demand PACS Solution FAQ s Standards: 1. Do you use any proprietary software to manage the images? No, our image management software manages the images and is fully DICOM compliant with no
SECURE AND EFFICIENT TRANSMISSION OF MEDICAL IMAGES OVER WIRELESS NETWORK
 SECURE AND EFFICIENT TRANSMISSION OF MEDICAL IMAGES OVER WIRELESS NETWORK Deepika.K 1, Varshini Karthik 2 1 Post Graduate Student, Department of BME, SRM University, Tamilnadu, India 2 Assistant Professor,
SECURE AND EFFICIENT TRANSMISSION OF MEDICAL IMAGES OVER WIRELESS NETWORK Deepika.K 1, Varshini Karthik 2 1 Post Graduate Student, Department of BME, SRM University, Tamilnadu, India 2 Assistant Professor,
TeamViewer Security Information
 TeamViewer Security Information 2013 TeamViewer GmbH, Last update: 11/2013 Target Group This document is aimed at professional network administrators. The information in this document is of a rather technical
TeamViewer Security Information 2013 TeamViewer GmbH, Last update: 11/2013 Target Group This document is aimed at professional network administrators. The information in this document is of a rather technical
StreamServe Encryption and Authentication
 StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
Workshop: Defining the Medical Imaging Requirements for a Health Center. Teleradiology and Networking
 Workshop: Defining the Medical Imaging Requirements for a Health Center April 17 2011 E-health and Telemedicine ehealth is the use, in the health sector, of digital data - transmitted, stored and retrieved
Workshop: Defining the Medical Imaging Requirements for a Health Center April 17 2011 E-health and Telemedicine ehealth is the use, in the health sector, of digital data - transmitted, stored and retrieved
Proactively Monitoring Departmental Clinical IT Systems with an Open Source Availability System
 Proactively Monitoring Departmental Clinical IT Systems with an Open Source Availability System C. Toland, C. Meenan, M. Warnock, and P. Nagy The goal of all radiology information technology (IT) support
Proactively Monitoring Departmental Clinical IT Systems with an Open Source Availability System C. Toland, C. Meenan, M. Warnock, and P. Nagy The goal of all radiology information technology (IT) support
Telemedicine, EMR & Remote Connectivity
 Telemedicine, EMR & Remote Connectivity Saroj Mishra, MS, FACS Prof & Head, Dept. of Endocrine Surgery & Faculty I/C, SGPGI Telemedicine Program Sanjay Gandhi Postgraduate Institute of Medical Sciences
Telemedicine, EMR & Remote Connectivity Saroj Mishra, MS, FACS Prof & Head, Dept. of Endocrine Surgery & Faculty I/C, SGPGI Telemedicine Program Sanjay Gandhi Postgraduate Institute of Medical Sciences
Practical Guidance to Implement Meaningful Use Stage 2. Secure Health Transport for Certification and Meaningful Use
 Practical Guidance to Implement Meaningful Use Stage 2 1. Introduction Association Standards and Interoperability Workgroup Meaningful Use (MU) Stage 2 introduces three transport standards for use in healthcare
Practical Guidance to Implement Meaningful Use Stage 2 1. Introduction Association Standards and Interoperability Workgroup Meaningful Use (MU) Stage 2 introduces three transport standards for use in healthcare
An Introduction to Secure Email. Presented by: Addam Schroll IT Security & Privacy Analyst
 An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
A Data Grid Model for Combining Teleradiology and PACS Operations
 MEDICAL IMAGING TECHNOLOGY Vol.25 No.1 January 2007 7 特 集 論 文 / 遠 隔 医 療 と 画 像 通 信 A Data Grid Model for Combining Teleradiology and Operations H.K. HUANG *, Brent J. LIU *, Zheng ZHOU *, Jorge DOCUMET
MEDICAL IMAGING TECHNOLOGY Vol.25 No.1 January 2007 7 特 集 論 文 / 遠 隔 医 療 と 画 像 通 信 A Data Grid Model for Combining Teleradiology and Operations H.K. HUANG *, Brent J. LIU *, Zheng ZHOU *, Jorge DOCUMET
DomainKeys Identified Mail (DKIM) Service Overview
 Network Working Group Request for Comments: 5585 Category: Informational T. Hansen AT&T Laboratories D. Crocker Brandenburg InternetWorking P. Hallam-Baker Default Deny Security, Inc. June 2009 DomainKeys
Network Working Group Request for Comments: 5585 Category: Informational T. Hansen AT&T Laboratories D. Crocker Brandenburg InternetWorking P. Hallam-Baker Default Deny Security, Inc. June 2009 DomainKeys
Processo Civile Telematico (On-line Civil Trial)
 Processo Civile Telematico (On-line Civil Trial) By Giulio Borsari Italian Ministry of Justice IT Department via Crescenzio 7/c Rome Phone +39 051 4200210 (alt. +39 06 68620209) Fax +39 051 4200200 [email protected]
Processo Civile Telematico (On-line Civil Trial) By Giulio Borsari Italian Ministry of Justice IT Department via Crescenzio 7/c Rome Phone +39 051 4200210 (alt. +39 06 68620209) Fax +39 051 4200200 [email protected]
Integration of Digital Teaching files into PACS. MILDENBERGER P, AHLERS C, SCHNEIDER, J, KLOS G (Mainz, Germany)
 Integration of Digital Teaching files into PACS MILDENBERGER P, AHLERS C, SCHNEIDER, J, KLOS G (Mainz, Germany) Situation Conventional film archives obsolete Digital resource for teaching and education
Integration of Digital Teaching files into PACS MILDENBERGER P, AHLERS C, SCHNEIDER, J, KLOS G (Mainz, Germany) Situation Conventional film archives obsolete Digital resource for teaching and education
GlobalComServer Application Interface
 GlobalComServer Application Interface Communication Interface FAX, SMS, Vocal, E-mail, TELEX Introduction The creator of Fax, Voice, E-mail, SMS and telex solutions, AVM Informatique is a leader in the
GlobalComServer Application Interface Communication Interface FAX, SMS, Vocal, E-mail, TELEX Introduction The creator of Fax, Voice, E-mail, SMS and telex solutions, AVM Informatique is a leader in the
Chapter 31 Network Security
 Chapter 31 Network Security Columbus, OH 43210 [email protected] http://www.cis.ohio-state.edu/~jain/ 31-1 Overview Security Aspects Secret Key and Public Key Encryption Firewalls: Packet Filter,
Chapter 31 Network Security Columbus, OH 43210 [email protected] http://www.cis.ohio-state.edu/~jain/ 31-1 Overview Security Aspects Secret Key and Public Key Encryption Firewalls: Packet Filter,
Lecture 31 SSL. SSL: Secure Socket Layer. History SSL SSL. Security April 13, 2005
 Lecture 31 Security April 13, 2005 Secure Sockets Layer (Netscape 1994) A Platform independent, application independent protocol to secure TCP based applications Currently the most popular internet crypto-protocol
Lecture 31 Security April 13, 2005 Secure Sockets Layer (Netscape 1994) A Platform independent, application independent protocol to secure TCP based applications Currently the most popular internet crypto-protocol
RAYSAFE S1 SECURITY WHITEPAPER VERSION B. RaySafe S1 SECURITY WHITEPAPER
 RaySafe S1 SECURITY WHITEPAPER Contents 1. INTRODUCTION 2 ARCHITECTURE OVERVIEW 2.1 Structure 3 SECURITY ASPECTS 3.1 Security Aspects for RaySafe S1 Data Collector 3.2 Security Aspects for RaySafe S1 cloud-based
RaySafe S1 SECURITY WHITEPAPER Contents 1. INTRODUCTION 2 ARCHITECTURE OVERVIEW 2.1 Structure 3 SECURITY ASPECTS 3.1 Security Aspects for RaySafe S1 Data Collector 3.2 Security Aspects for RaySafe S1 cloud-based
StreamServe Persuasion SP4 Encryption and Authentication
 StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United
StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United
Certification Report. Utimaco Safeware AG. debiszert-dsz-itsec-04007-1999. SafeGuard Sign&Crypt, Version 2.0. The Modern Service Provider
 Certification Report SafeGuard Sign&Crypt, Version 2.0 Utimaco Safeware AG debiszert-dsz-itsec-04007-1999 debis IT Security Services The Modern Service Provider SafeGuard Sign&Crypt, Version 2.0 /E2 debiszert
Certification Report SafeGuard Sign&Crypt, Version 2.0 Utimaco Safeware AG debiszert-dsz-itsec-04007-1999 debis IT Security Services The Modern Service Provider SafeGuard Sign&Crypt, Version 2.0 /E2 debiszert
MedBroker A DICOM and HL7 Integration Product. Whitepaper
 MedBroker A DICOM and HL7 Integration Product Whitepaper Copyright 2009, Keymind Computing AS All trademarks and copyrights referred to are the property of their respective owners. Revision 1.0 Oct 19
MedBroker A DICOM and HL7 Integration Product Whitepaper Copyright 2009, Keymind Computing AS All trademarks and copyrights referred to are the property of their respective owners. Revision 1.0 Oct 19
Unifying Information Security. Implementing Encryption on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing Encryption on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 4 2 Encryption Options... 5 3 Basics of Encryption... 7 3.1 Public Key... 7 3.2 Private
Unifying Information Security Implementing Encryption on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 4 2 Encryption Options... 5 3 Basics of Encryption... 7 3.1 Public Key... 7 3.2 Private
StreamServe Persuasion SP5 Encryption and Authentication
 StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United
StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United
Department of Veterans Affairs VHA DIRECTIVE 2011-005 Veterans Health Administration Washington, DC 20420 February 8, 2011
 Department of Veterans Affairs VHA DIRECTIVE 2011-005 Veterans Health Administration Washington, DC 20420 RADIOLOGY PICTURE ARCHIVING AND COMMUNICATION SYSTEMS (PACS) 1. PURPOSE: This Veterans Health Administration
Department of Veterans Affairs VHA DIRECTIVE 2011-005 Veterans Health Administration Washington, DC 20420 RADIOLOGY PICTURE ARCHIVING AND COMMUNICATION SYSTEMS (PACS) 1. PURPOSE: This Veterans Health Administration
Antin Kushnir, Ihor Dutka
 PROJECT PROPOSAL TELERADIOLOGY NETWORK WITHIN POLISH-UKRAINIAN TRANSBOUNDARY COOPERATION Antin Kushnir, Ihor Dutka Meditech Ltd. Lviv, Ukraine Projekt współfinansowany przez Unię Europejską w ramach Europejskiego
PROJECT PROPOSAL TELERADIOLOGY NETWORK WITHIN POLISH-UKRAINIAN TRANSBOUNDARY COOPERATION Antin Kushnir, Ihor Dutka Meditech Ltd. Lviv, Ukraine Projekt współfinansowany przez Unię Europejską w ramach Europejskiego
The All-in-One Support Solution. Easy & Secure. Secure Advisor
 The All-in-One Support Solution. Easy & Secure. Secure Advisor Secure Advisor - A Perfect Solution for Online Support Fast and easy remote support from anywhere Problems that often sound complicated on
The All-in-One Support Solution. Easy & Secure. Secure Advisor Secure Advisor - A Perfect Solution for Online Support Fast and easy remote support from anywhere Problems that often sound complicated on
A full-featured online DICOM archive built on the same SQL platform as our powerful enterprise grade PACS database. Enterprise Grade DICOM Engine
 DICOM A full-featured online DICOM archive built on the same SQL platform as our powerful enterprise grade PACS database. SQL Database Enterprise Grade DICOM Engine Flexible Archiving Solutions Internet
DICOM A full-featured online DICOM archive built on the same SQL platform as our powerful enterprise grade PACS database. SQL Database Enterprise Grade DICOM Engine Flexible Archiving Solutions Internet
FOR several decades, the security community tried to get
 WHITE PAPER, g10 code GmbH, 2011-10-17 1 STEED Usable End-to-End Encryption Werner Koch, Marcus Brinkmann Abstract End-to-end e-mail encryption is still ignored by almost all users. The mails are left
WHITE PAPER, g10 code GmbH, 2011-10-17 1 STEED Usable End-to-End Encryption Werner Koch, Marcus Brinkmann Abstract End-to-end e-mail encryption is still ignored by almost all users. The mails are left
CIPHERMAIL EMAIL ENCRYPTION. CipherMail white paper
 CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CIPHERMAIL EMAIL ENCRYPTION CipherMail white paper Copyright 2009-2014, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
ADVANCED MEDICAL SYSTEMS PTE LTD Singapore Malaysia India Australia www.amssg.com. JiveX Medical Archive All medical information in one location
 JiveX Medical Archive All medical information in one location JiveX Medical Archive Vendor neutral archiving in medicine 09/2014 EN 2/8 All medical information in one location Medically relevant information
JiveX Medical Archive All medical information in one location JiveX Medical Archive Vendor neutral archiving in medicine 09/2014 EN 2/8 All medical information in one location Medically relevant information
Image Area. View Point. Medical Imaging. Advanced Imaging Solutions for Diagnosis, Localization, Treatment Planning and Monitoring. www.infosys.
 Image Area View Point Medical Imaging Advanced Imaging Solutions for Diagnosis, Localization, Treatment Planning and Monitoring www.infosys.com Over the years, medical imaging has become vital in the early
Image Area View Point Medical Imaging Advanced Imaging Solutions for Diagnosis, Localization, Treatment Planning and Monitoring www.infosys.com Over the years, medical imaging has become vital in the early
WORKFLOW MANAGEMENT FOR THE CLINICAL RADIOLOGY
 RADIOLOGY WORKFLOW SOLUTIONS WORKFLOW MANAGEMENT FOR THE CLINICAL RADIOLOGY RADIOLOGY WORKFLOW MANAGEMENT OPTIMISED WORKFLOW MAXIMUM EFFICIENCY medavis. Your trusted partner for workflow management in
RADIOLOGY WORKFLOW SOLUTIONS WORKFLOW MANAGEMENT FOR THE CLINICAL RADIOLOGY RADIOLOGY WORKFLOW MANAGEMENT OPTIMISED WORKFLOW MAXIMUM EFFICIENCY medavis. Your trusted partner for workflow management in
Fax and Oracle Collaboration Suite. An Oracle White Paper August 2005
 Fax and Oracle Collaboration Suite An Oracle White Paper August 2005 Fax and Oracle Collaboration Suite Introduction... 3 Fax Support in Oracle Collaboration Suite... 4 Outbound Fax Configuration... 7
Fax and Oracle Collaboration Suite An Oracle White Paper August 2005 Fax and Oracle Collaboration Suite Introduction... 3 Fax Support in Oracle Collaboration Suite... 4 Outbound Fax Configuration... 7
VS-NUR FÜR DEN DIENSTGEBRAUCH (RESTRICTED)
 Instruction sheet on the Handling of Protectively Marked Information Classified VS-NUR FÜR DEN DIENSTGEBRAUCH (RESTRICTED) (short title: VS-NfD-Merkblatt; Instructions on the Handling of RESTRICTED information)
Instruction sheet on the Handling of Protectively Marked Information Classified VS-NUR FÜR DEN DIENSTGEBRAUCH (RESTRICTED) (short title: VS-NfD-Merkblatt; Instructions on the Handling of RESTRICTED information)
Medical Information Systems
 Medical Information Systems Introduction The introduction of information systems in hospitals and other medical facilities is not only driven by the wish to improve management of patient-related data for
Medical Information Systems Introduction The introduction of information systems in hospitals and other medical facilities is not only driven by the wish to improve management of patient-related data for
Webmail Using the Hush Encryption Engine
 Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Royal Mail Business Integration Gateway Specification
 FSpec401 FSpec401 Royal Mail Customer Solutions Royal Mail Business Integration Gateway Specification - XB60 The FSpec401 document details, for customers, the various methods of connecting to Royal Mail
FSpec401 FSpec401 Royal Mail Customer Solutions Royal Mail Business Integration Gateway Specification - XB60 The FSpec401 document details, for customers, the various methods of connecting to Royal Mail
The Internet, Intranets, and Extranets. What is the Internet. What is the Internet cont d.
 C H A P T E R 7 The Internet, Intranets, and Extranets What is the Internet Millions of computers, all linked together on a computer network. A home computer usually links to the Internet using a phone
C H A P T E R 7 The Internet, Intranets, and Extranets What is the Internet Millions of computers, all linked together on a computer network. A home computer usually links to the Internet using a phone
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Arizona Health Information Exchange Marketplace. Requirements and Specifications Health Information Service Provider (HISP)
 Arizona Health Information Exchange Marketplace Requirements and Specifications Health Information Service Provider (HISP) Table of Contents Table of Contents... 1 Introduction... 2 Purpose... 3 Scope...
Arizona Health Information Exchange Marketplace Requirements and Specifications Health Information Service Provider (HISP) Table of Contents Table of Contents... 1 Introduction... 2 Purpose... 3 Scope...
PierianDx - Clinical Genomicist Workstation Software as a Service FAQ s
 PierianDx - Clinical Genomicist Workstation Software as a Service FAQ s Network Security Please describe the preferred connection method(s) between the PierianDx network and a healthcare organization s
PierianDx - Clinical Genomicist Workstation Software as a Service FAQ s Network Security Please describe the preferred connection method(s) between the PierianDx network and a healthcare organization s
GETTING STARTED SECURE FILE TRANSFER PROCEDURES A. Secure File Transfer Protocol (SFTP) Procedures
 A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
Intelligent Solutions for the Highest IT Security Demands
 Intelligent Solutions for the Highest IT Security Demands 3 Information security from the architects of modern cryptographic systems SINA (Secure Inter-Network Architecture) enables the protected processing,
Intelligent Solutions for the Highest IT Security Demands 3 Information security from the architects of modern cryptographic systems SINA (Secure Inter-Network Architecture) enables the protected processing,
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
ETSI TS 102 640-4 V2.1.1 (2010-01) Technical Specification
 TS 102 640-4 V2.1.1 (2010-01) Technical Specification Electronic Signatures and Infrastructures (ESI); Registered Electronic Mail (REM) Part 4: REM-MD Conformance Profiles 2 TS 102 640-4 V2.1.1 (2010-01)
TS 102 640-4 V2.1.1 (2010-01) Technical Specification Electronic Signatures and Infrastructures (ESI); Registered Electronic Mail (REM) Part 4: REM-MD Conformance Profiles 2 TS 102 640-4 V2.1.1 (2010-01)
Teleradiology Security Whitepaper
 Teleradiology Security Whitepaper aycan telerad as DICOM image distribution enhancement for PACS environments. ayc_telerad_security_whitepaper_150417_sp_ds. ID77905 Copyright aycan Digitalsysteme GmbH
Teleradiology Security Whitepaper aycan telerad as DICOM image distribution enhancement for PACS environments. ayc_telerad_security_whitepaper_150417_sp_ds. ID77905 Copyright aycan Digitalsysteme GmbH
Common Remote Service Platform (crsp) Security Concept
 Siemens Remote Support Services Common Remote Service Platform (crsp) Security Concept White Paper April 2013 1 Contents Siemens AG, Sector Industry, Industry Automation, Automation Systems This entry
Siemens Remote Support Services Common Remote Service Platform (crsp) Security Concept White Paper April 2013 1 Contents Siemens AG, Sector Industry, Industry Automation, Automation Systems This entry
PARCA Certified PACS Associate (CPAS) Requirements
 PARCA Certified PACS Associate (CPAS) Requirements Copyright notice: Copyright 2005 PACS Administrators in Radiology Certification Association (PARCA). All rights reserved. All rights reserved. This publication
PARCA Certified PACS Associate (CPAS) Requirements Copyright notice: Copyright 2005 PACS Administrators in Radiology Certification Association (PARCA). All rights reserved. All rights reserved. This publication
WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance
 WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance SEC-STM-072014 07/2014 Contents Patient Choice... 2 Security Protections... 2 Participation Agreement... 2 Controls... 3 Break the Glass...
WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance SEC-STM-072014 07/2014 Contents Patient Choice... 2 Security Protections... 2 Participation Agreement... 2 Controls... 3 Break the Glass...
EUCIP - IT Administrator. Module 5 IT Security. Version 2.0
 EUCIP - IT Administrator Module 5 IT Security Version 2.0 Module 5 Goals Module 5 Module 5, IT Security, requires the candidate to be familiar with the various ways of protecting data both in a single
EUCIP - IT Administrator Module 5 IT Security Version 2.0 Module 5 Goals Module 5 Module 5, IT Security, requires the candidate to be familiar with the various ways of protecting data both in a single
Success of DICOM standard
 International Telecommunication Union Success of DICOM standard Cor Loef Industry Co-Chair DICOM Strategic Advisory Committee Workshop on Standardization in E-health Geneva, 23-25 May 2003 Success of DICOM
International Telecommunication Union Success of DICOM standard Cor Loef Industry Co-Chair DICOM Strategic Advisory Committee Workshop on Standardization in E-health Geneva, 23-25 May 2003 Success of DICOM
Collax Mail Server. Howto. This howto describes the setup of a Collax server as mail server.
 Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
VoIP Security. Seminar: Cryptography and Security. 07.06.2006 Michael Muncan
 VoIP Security Seminar: Cryptography and Security Michael Muncan Overview Introduction Secure SIP/RTP Zfone Skype Conclusion 1 Introduction (1) Internet changed to a mass media in the middle of the 1990s
VoIP Security Seminar: Cryptography and Security Michael Muncan Overview Introduction Secure SIP/RTP Zfone Skype Conclusion 1 Introduction (1) Internet changed to a mass media in the middle of the 1990s
