StreamServe Persuasion SP4 Encryption and Authentication
|
|
|
- Morgan Joseph
- 10 years ago
- Views:
Transcription
1 StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A
2 StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of StreamServe, Inc. Information in this document is subject to change without notice. StreamServe Inc. assumes no responsibility or liability for any errors or inaccuracies that may appear in this book. All registered names, product names and trademarks of other companies mentioned in this documentation are used for identification purposes only and are acknowledged as property of the respective company. Companies, names and data used in examples in this document are fictitious unless otherwise noted. StreamServe, Inc. offers no guarantees and assumes no responsibility or liability of any type with respect to third party products and services, including any liability resulting from incompatibility between the third party products and services and the products and services offered by StreamServe, Inc. By using StreamServe and the third party products mentioned in this document, you agree that you will not hold StreamServe, Inc. responsible or liable with respect to the third party products and services or seek to do so. The trademarks, logos, and service marks in this document are the property of StreamServe, Inc. or other third parties. You are not permitted to use the marks without the prior written consent of StreamServe, Inc. or the third party that owns the marks. Use of the StreamServe product with third party products not mentioned in this document is entirely at your own risk, also as regards the StreamServe products. StreamServe Web Site
3 3 Contents About encryption and authentication...5 Digital certificates...6 Security configurations...7 Entropy...8 Trust Server administration Trust Server security configurations...11 Security configuration for an SSL server Security configuration for an SSL client Security configuration for signing s Security configuration for rejecting s from non-trusted addresses Security configuration for encrypting s Security configuration for receiving encrypted s Trust Server scenarios...16 SSL server and SSL client Encrypted s Signed s Encrypted and signed s Legacy security configurations...22 Security configuration for an SSL server (with client authentication) Security configuration for an SSL server (without client authentication) Security configuration for an SSL client (with client authentication) Security configuration for an SSL client (without client authentication) Security configuration for signing s Security configuration for rejecting s from non-trusted addresses Security configuration for encrypting s Security configuration for receiving encrypted s Legacy scenarios...30 SSL server and SSL client with client authentication SSL server and SSL client without client authentication Encrypted s Signed s Signed and encrypted s Security configuration GUI reference...37 Trust Server settings Legacy settings... 38
4 4
5 5 About encryption and authentication A StreamServer application can be configured as an SSL server or SSL client that communicates over an encrypted HTTPS channel. Authentication An SSL server must always authenticate itself to all SSL clients, and the SSL client must authenticate itself to the SSL server if the SSL server requires client authentication. S/MIME Encryption and authentication can also be applied to data sent via , where the StreamServer application uses S/MIME to sign and encrypt/decrypt s.
6 6 Digital certificates About encryption and authentication Digital certificates SSL servers and clients use digital certificates for encryption and authentication. A digital certificate is used to verify that a user sending a message is who he claims to be, and to provide the receiver with the means to encode a reply. Certificate Authority A Certificate Authority (CA) is a trusted third-party organization or company that issues digital certificates. Certificate chain A certificate chain is a tree structure of certificates. The validity of a certificate in a certificate chain is verified by the certificate one level up in the tree. The root node in the tree is the self signed root CA certificate. Before the StreamServer can trust a certificate provided by an SSL server or client, it must verify the complete certificate chain up to the root CA certificate. To be able to do this, it must have access to all certificates in the certificate chain. Certificate chain example In this example, a three level deep certificate chain consists of the following certificates: Root CA certificate (level 1). Intermediate CA certificate (level 2). Subject certificate (level 3). The level 1 and 2 certificates are available to the SSL client in this example, and the level 3 certificate is sent by the SSL server to the SSL client. 1 The SSL client sends a request to an SSL server that returns the level 3 certificate. 2 The SSL client uses the public key embedded i the level 2 certificate to verify the signature of the level 3 certificate, and to verify that the level 3 certificate has not been revoked. 3 If the level 3 certificate is OK, the SSL client uses the public key embedded i the level 1 certificate to verify the signature of the level 2 certificate, and to verify that the level 2 certificate has not been revoked. 4 If the level 2 certificate is OK, the SSL client verifies the self signed level 1 certificate. It uses the public key embedded i the level 1 certificate to verify the signature of the level 1 certificate, and to verify that the level 1 certificate has not been revoked. 5 If all tests are OK, the complete certificate chain can be trusted, and the identity and integrity of the level 3 certificate is verified.
7 Security configurations 7 About encryption and authentication Security configurations In Design Center, digital certificates are managed using a specific resource type called security configuration. There are two types of security configurations: Trust Server all certificate information is retrieved from an XKMS (XML Key Management Specification) compliant Trust Server. Only the certificate chain that verifies the identity of the Trust Server is stored locally. See Trust Server security configurations on page 11. Legacy all certificate and private key data is stored locally. See Legacy security configurations on page 22.
8 8 Entropy About encryption and authentication Entropy When running on a Windows platform, the StreamServer uses a default entropy source to generate randomness for SSL. When running on a UNIX platform, the StreamServer searches for the entropy using the following sources: /dev/random /var/run/egd-pool /dev/egd-pool /etc/egd-pool /etc/entropy /dev/urandom The StreamServer only uses the first source found in the list, starting at the top. You must make sure that the appropriate entropy source is available. Note: If no source is found in the list above, the StreamServer will use an entropy source of low quality.
9 Trust Server administration 9 About encryption and authentication Trust Server administration The Trust Server is installed separately. For information on how to administer the Trust Server, see the documentation included in the Trust Server installation.
10 10 Trust Server administration About encryption and authentication
11 11 You can create security configurations for different purposes. For example, if the StreamServer is both an SSL server (specified using an HTTPS input connector) and an SSL client (specified using an HTTPS Submit output connector or HTTPS Poll input connector), you can create one security configuration for the server and another for the client. Then you connect the server security configuration to the HTTPS input connector, and the client security configuration to the HTTPS Submit output connector. Note: You should be experienced in the area of SSL and S/MIME to be able to create security configurations. Trust Server security configurations If the StreamServer and all involved parties (SSL server/client and sender/ receiver) are registered in a Trust Server, you can use Trust Server security configurations. In this case all certificate information is retrieved from the Trust Server, and only the certificates that verify the identity of the Trust Server are stored locally. Prerequisites The certificates that verify the identity of the Trust Server are added to the same resource set as the security configuration. The certificates for all involved parties (SSL server/client and sender/ receiver) are registered in the Trust Server. To create a Trust Server security configuration 1 In a resource set, create a new Security Configuration resource. 2 Give the security configuration a unique name. 3 Open the security configuration and select the type Trust Server. 4 On the Certificates tab, add all the certificate resources to include in the certificate chain used to verify the identity of the Trust Server. 5 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server.
12 12 Trust Server security configurations Depending on the purpose of the security configuration, you must also configure a number of additional parameters: Security configuration for an SSL server on page 12 Security configuration for an SSL client on page 13 Security configuration for signing s on page 13 Security configuration for rejecting s from non-trusted addresses on page 14 Security configuration for encrypting s on page 14 Security configuration for receiving encrypted s on page 15 Security configuration for an SSL server You can run the StreamServer as an SSL server that communicates with one or more SSL clients. To achieve this, you must create a security configuration and an HTTPS input connector, and connect the security configuration to the HTTPS input connector. To create a security configuration 1 Create a new security configuration. See To create a Trust Server security configuration on page On the HTTP tab, enter the Key name and Passphrase to access the StreamServer private key. To connect the security configuration to the connector 1 Open the HTTPS input Connector Settings dialog box. 2 In the Security configuration field, browse to and select the security configuration.
13 Trust Server security configurations 13 Security configuration for an SSL client You can run the StreamServer as an SSL client that communicates with an SSL server. To achieve this, you must create a security configuration and an HTTPS Submit output connector (or HTTPS Poll input connector), and connect the security configuration to the connector. To create a security configuration 1 Create a new security configuration. See To create a Trust Server security configuration on page If the SSL server requires client authentication, you must also select the HTTP tab and enter the Key name and Passphrase to access the StreamServer private key. To connect the security configuration to an HTTPS Submit output connector 1 Open the HTTPS Submit Output Connector Settings dialog box. 2 Select Use security configuration. 3 In the Security configuration field, browse to and select the security configuration. To connect the security configuration to an HTTPS Poll input connector 1 Open the HTTPS Poll Input Connector Settings dialog box. 2 In the Security configuration field, browse to and select the security configuration. Security configuration for signing s The StreamServer can sign s. The recipients use the signature to verify that the comes from a trusted address. To achieve this you must create a security configuration for each From address, and enable signing of s on the output connector that delivers the s (SMTP (MIME) or SMTP (MIME) for MailOUT). To create a security configuration 1 Create a new security configuration. See To create a Trust Server security configuration on page On the tab, enter the Key name and Passphrase to access the private key for the From address. To enable signing Open the Output Connector Settings dialog box and select Sign.
14 14 Trust Server security configurations Security configuration for rejecting s from nontrusted addresses The StreamServer can reject s from non-trusted addresses. The StreamServer uses the sender s public key to verify the identity of the sender. To achieve this you must create a security configuration, and enable rejection of s on the IN input connector. To create a security configuration Create a new security configuration. See To create a Trust Server security configuration on page 11. To enable rejection 1 Open the IN input Connector Settings dialog box and select Retrieve > Advanced. 2 Select Request signature. Security configuration for encrypting s The StreamServer can encrypt s, and prevent s from being sent to nontrusted addresses. The StreamServer encrypts an with the recipient s public key. To achieve this you must create a security configuration, and enable encryption of s on the output connector that delivers the s (SMTP (MIME) or SMTP (MIME) for MailOUT). To create a security configuration Create a new security configuration. See To create a Trust Server security configuration on page 11. To enable encryption Open the Output Connector Settings dialog box and select Encrypt.
15 Trust Server security configurations 15 Security configuration for receiving encrypted s The StreamServer can decrypt received s, and reject unencrypted s. The StreamServer decrypts s with the private key. To achieve this you must create a security configuration, and enable rejection of unencrypted s on the IN input connector. To create a security configuration 1 Create a new security configuration. See To create a Trust Server security configuration on page On the tab, enter the Key name and Passphrase to access the private key for the recipient address. To enable rejection of unencrypted s 1 Open the IN input Connector Settings dialog box and select Retrieve > Advanced. 2 Select Request encryption.
16 16 Trust Server scenarios Trust Server scenarios SSL server and SSL client This scenario involves the two StreamServers SERVER and CLIENT. The SERVER communicates via an HTTPS input connector, and the CLIENT communicates via an HTTPS Submit output connector. Prerequisites Both SERVER and CLIENT use SSL version SSLv3. Both SERVER and CLIENT have the following resource in the default resource set: TS root.cer the Trust Server CA root certificate. This is the only certificate in the certificate chain. Configuring the SERVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SSL SERVER. 2 Open SSL SERVER and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. 5 On the HTTP tab, enter the Key name and Passphrase to access the SERVER private key. Configure the HTTPS input connector 1 Select security configuration > SSL SERVER. 2 Select SSL Version > SSLv3.
17 Trust Server scenarios 17 Configuring the CLIENT Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SSL CLIENT. 2 Open SSL CLIENT and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. 5 On the HTTP tab, enter the Key name and Passphrase to access the CLIENT private key. Configure the HTTPS Submit output connector 1 Select Use security configuration. 2 Select Security configuration > SSL CLIENT. 3 Select SSL Version > SSLv3. Encrypted s This scenario involves the two StreamServers SENDER and RECEIVER. The SENDER sends encrypted s to the RECEIVER via an SMTP (MIME) output connector, and the RECEIVER receives the s via an IN input connector. Prerequisites Both SENDER and RECEIVER have the following resource in the default resource set: TS root.cer the Trust Server CA root certificate. This is the only certificate in the certificate chain.
18 18 Trust Server scenarios Configuring the SENDER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to ENCRYPT. 2 Open ENCRYPT and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. Configure the SMTP (MIME) output connector Select Encrypt. Configuring the RECEIVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to DECRYPT. 2 Open DECRYPT and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. 5 On the tab, enter the Key name and Passphrase to access the private key for the recipient address. Configure the IN input connector 1 Select Retrieve > Advanced. 2 Select Request encryption.
19 Trust Server scenarios 19 Signed s This scenario involves the two StreamServers SENDER and RECEIVER. The SENDER sends signed s to the RECEIVER via an SMTP (MIME) output connector, and the RECEIVER receives the s via an IN input connector. Prerequisites Both SENDER and RECEIVER have the following resource in the default resource set: TS root.cer the Trust Server CA root certificate. This is the only certificate in the certificate chain. Configuring the SENDER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGN. 2 Open SIGN and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. 5 On the tab, enter the Key name and Passphrase to access the private key for the sender address. Configure the SMTP (MIME) output connector Select Sign. Configuring the RECEIVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGNED. 2 Open SIGNED and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server.
20 20 Trust Server scenarios Configure the IN input connector 1 Select Retrieve > Advanced. 2 Select Request signature. Encrypted and signed s This scenario involves the two StreamServers SENDER and RECEIVER. The SENDER sends signed and encrypted s to the RECEIVER via an SMTP (MIME) output connector, and the RECEIVER receives the s via an IN input connector. Prerequisites Both SENDER and RECEIVER have the following resource in the default resource set: TS root.cer the Trust Server CA root certificate. This is the only certificate in the certificate chain. Configuring the SENDER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGN_ENCRYPT. 2 Open SIGN_ENCRYPT and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. 5 On the tab, enter the Key name and Passphrase to access the private key for the sender address. Configure the SMTP (MIME) output connector Select Sign and Encrypt.
21 Trust Server scenarios 21 Configuring the RECEIVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGNED_ENCRYPTED. 2 Open SIGNED_ENCRYPTED and select the type Trust Server. 3 On the Certificates tab, add the certificate resource TS root.cer. 4 On the Trust Server tab, enter the Trust Server URL, and the User name and Password to access the Trust Server. 5 On the tab, enter the Key name and Passphrase to access the private key for the recipient address. Configure the IN input connector 1 Select Retrieve > Advanced. 2 Select Request signature and Request encryption.
22 22 Legacy security configurations Legacy security configurations If the StreamServer, or any of the involved parties (SSL server/client and sender/receiver), are not registered in a Trust Server, you can create security configurations using locally stored certificates. To create a Legacy security configuration 1 In a resource set, create a new Security Configuration resource. 2 Give the security configuration a unique name. 3 Open the security configuration and select the type Legacy. Depending on the purpose of the security configuration, you must also configure a number of additional parameters: Security configuration for an SSL server (with client authentication) on page 23. Security configuration for an SSL server (without client authentication) on page 24. Security configuration for an SSL client (with client authentication) on page 25. Security configuration for an SSL client (without client authentication) on page 26. Security configuration for signing s on page 27. Security configuration for rejecting s from non-trusted addresses on page 28. Security configuration for encrypting s on page 28. Security configuration for receiving encrypted s on page 29.
23 Legacy security configurations 23 Security configuration for an SSL server (with client authentication) You can run the StreamServer as an SSL server that requires client authentication. To achieve this, you must create a security configuration and an HTTPS input connector, and connect the security configuration to the HTTPS input connector. Multiple clients If the StreamServer communicates with multiple clients, you must: Create one security configuration per client. Create one HTTPS input connector per client. These connectors cannot share the same port. Prerequisites The StreamServer private key file is added to the same resource set as the security configuration. The StreamServer CA root certificate is distributed to the clients. The certificates that verify the identity of the client are added to the same resource set as the security configuration. The client certificate is added to the same resource set as the security configuration. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page On the Certificates tab, add all the certificate resources to include in the certificate chain used to verify the identity of the client. 3 Click the HTTP Server tab. 4 Select the StreamServer Private key file and enter the Password to access the private key. 5 Select Client authentication and select the Client certificate. To connect the security configuration to the connector 1 Open the HTTPS input Connector Settings dialog box. 2 In the Security configuration field, browse to and select the security configuration.
24 24 Legacy security configurations Security configuration for an SSL server (without client authentication) You can run the StreamServer as an SSL server that does not require client authentication. To achieve this, you must create a security configuration and an HTTPS input connector, and connect the security configuration to the HTTPS input connector. Prerequisites The StreamServer private key file is added to the same resource set as the security configuration. The StreamServer CA root certificate is distributed to the clients. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page Click the HTTP Server tab. 3 Select the StreamServer Private key file and enter the Password to access the private key. To connect the security configuration to the connector 1 Open the HTTPS input Connector Settings dialog box. 2 In the Security configuration field, browse to and select the security configuration.
25 Legacy security configurations 25 Security configuration for an SSL client (with client authentication) You can run the StreamServer as an SSL client that communicates with an SSL server that requires client authentication. To achieve this, you must create a security configuration and an HTTPS Submit output connector (or HTTPS Poll input connector), and connect the security configuration to the connector. Prerequisites The StreamServer private key file is added to the same resource set as the security configuration. The certificates that verify the identity of the SSL server are added to the same resource set as the security configuration. The StreamServer CA root certificate and client certificate are distributed to the SSL server. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page On the Certificates tab, add all the certificate resources to include in the certificate chain used to verify the identity of the SSL server. 3 Click the and HTTP client tab. 4 Select the StreamServer Private key file and enter the Password to access the private key. To connect the security configuration to an HTTPS Submit output connector 1 Open the HTTPS Submit Output Connector Settings dialog box. 2 Select Use security configuration. 3 In the Security configuration field, browse to and select the security configuration. To connect the security configuration to an HTTPS Poll input connector 1 Open the HTTPS Poll Input Connector Settings dialog box. 2 In the Security configuration field, browse to and select the security configuration.
26 26 Legacy security configurations Security configuration for an SSL client (without client authentication) You can run the StreamServer as an SSL client that communicates with an SSL server that does not require client authentication. To achieve this, you must create a security configuration and an HTTPS Submit output connector (or HTTPS Poll input connector), and connect the security configuration to the connector. Prerequisites The certificates that verify the identity of the SSL server are added to the same resource set as the security configuration. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page On the Certificates tab, add all the certificate resources to include in the certificate chain used to verify the identity of the SSL server. To connect the security configuration to an HTTPS Submit output connector 1 Open the HTTPS Submit Output Connector Settings dialog box. 2 Select Use security configuration. 3 In the Security configuration field, browse to and select the security configuration. To connect the security configuration to an HTTPS Poll input connector 1 Open the HTTPS Poll Input Connector Settings dialog box. 2 In the Security configuration field, browse to and select the security configuration.
27 Legacy security configurations 27 Security configuration for signing s The StreamServer can sign s. recipients use the signature to verify that the comes from a trusted address. To achieve this you must create a security configuration for each From address, and enable signing of s on the output connector that delivers the s (SMTP (MIME) or SMTP (MIME) for MailOUT). Prerequisites The StreamServer private key file is added to the same resource set as the security configuration. The StreamServer CA root certificate is distributed to the recipients. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page Click the and HTTP client tab. 3 Select the StreamServer Private key file and enter the Password to access the private key. To enable signing Open the Output Connector Settings dialog box and select Sign.
28 28 Legacy security configurations Security configuration for rejecting s from nontrusted addresses The StreamServer can reject s from non-trusted addresses. The StreamServer uses the sender s public key to verify the identity of the sender. To achieve this you must create a security configuration, and enable rejection of s on the IN input connector. Prerequisites The certificates that verify the identity of the sender are added to the same resource set as the security configuration. If the senders have different CA root certificates, you must create one security configuration for each CA root certificate. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page On the Certificates tab, add all the certificate resources to include in the certificate chain used to verify the identity of the sender. To enable rejection 1 Open the IN input Connector Settings dialog box and select Retrieve > Advanced. 2 Select Request signature. Security configuration for encrypting s The StreamServer can encrypt s, and prevent s from being sent to nontrusted addresses. The StreamServer encrypts an with the recipient s public key. To achieve this you must create a security configuration, and enable encryption of s on the output connector that delivers the s (SMTP (MIME) or SMTP (MIME) for MailOUT). Prerequisites The encryption certificates for all addresses are added to the same resource set as the security configuration. Each certificate resource must be renamed to < address>.crt, for example arnold_abc.com.crt. Note: You must not use _ instead. To create a security configuration Create a new security configuration. See To create a Legacy security configuration on page 22. To enable encryption Open the Output Connector Settings dialog box and select Encrypt.
29 Legacy security configurations 29 Security configuration for receiving encrypted s The StreamServer can decrypt received s, and reject unencrypted s. The StreamServer decrypts s with the private key. To achieve this you must create a security configuration, and enable rejection of unencrypted s on the IN input connector. Prerequisites The StreamServer private key file is added to the same resource set as the security configuration. The StreamServer certificate is distributed to the senders. To create a security configuration 1 Create a new security configuration. See To create a Legacy security configuration on page Click the and HTTP client tab. 3 Select the StreamServer Private key file and enter the Password to access the private key. To enable rejection of unencrypted s 1 Open the IN input Connector Settings dialog box and select Retrieve > Advanced. 2 Select Request encryption.
30 30 Legacy scenarios Legacy scenarios SSL server and SSL client with client authentication This scenario involves the two StreamServers SERVER and CLIENT. The SERVER communicates via an HTTPS input connector, and the CLIENT communicates via an HTTPS Submit output connector. The CLIENT must authenticate itself to SERVER. Prerequisites Both SERVER and CLIENT use SSL version SSLv3. SERVER has the following resources in the default resource set: Private key.pfx the private key file for SERVER. CLIENT CA root certificate.crt the CA root certificate for CLIENT. This is the only certificate in the certificate chain. CLIENT public key.crt the certificate for CLIENT. CLIENT has the following resources in the default resource set: SERVER CA root certificate.crt the CA root certificate for SERVER. This is the only certificate in the certificate chain. Private key.pfx the private key file for CLIENT.
31 Legacy scenarios 31 Configuring the SERVER Configuring the CLIENT Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SSL SERVER. 2 Open SSL SERVER and select the type Legacy. 3 On the Certificates tab, add the certificate resource CLIENT CA root certificate.crt. 4 On the HTTP Server tab, select Private key file > Private key.pfx and enter the Password to access the private key. 5 Select Client authentication and select Client certificate > CLIENT public key.crt. Configure the HTTPS input connector 1 Select security configuration > SSL SERVER. 2 Select SSL Version > SSLv3. Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SSL CLIENT. 2 Open SSL CLIENT and select the type Legacy. 3 On the Certificates tab, add the certificate resource SERVER CA root certificate.crt. 4 On the and HTTP client tab, select Private key file > Private key.pfx and enter the Password to access the private key. Configure the HTTPS Submit output connector 1 Select Use security configuration. 2 Select Security configuration > SSL CLIENT. 3 Select SSL Version > SSLv3.
32 32 Legacy scenarios SSL server and SSL client without client authentication This scenario involves the two StreamServers SERVER and CLIENT. The SERVER communicates via an HTTPS input connector, and the CLIENT communicates via an HTTPS Submit output connector. The CLIENT does not authenticate itself to SERVER. Prerequisites Both SERVER and CLIENT use SSL version SSLv3. SERVER has the following resource in the default resource set: Private key.pfx the private key file for SERVER. CLIENT has the following resource in the default resource set: SERVER CA root certificate.crt the CA root certificate for SERVER. This is the only certificate in the certificate chain. Configuring the SERVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SSL SERVER. 2 Open SSL SERVER and select the type Legacy. 3 On the HTTP Server tab, select Private key file > Private key.pfx and enter the Password to access the private key. Configure the HTTPS input connector 1 Select security configuration > SSL SERVER. 2 Select SSL Version > SSLv3.
33 Legacy scenarios 33 Configuring the CLIENT Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SSL CLIENT. 2 Open SSL CLIENT and select the type Legacy. 3 On the Certificates tab, add the certificate resource SERVER CA root certificate.crt. Configure the HTTPS Submit output connector 1 Select Use security configuration. 2 Select Security configuration > SSL CLIENT. 3 Select SSL Version > SSLv3. Encrypted s This scenario involves the two StreamServers SENDER and RECEIVER. The SENDER sends encrypted s to the RECEIVER via an SMTP (MIME) output connector, and the RECEIVER receives the s via an IN input connector. Prerequisites SENDER has the following resource in the default resource set: info_abc.com.crt the encryption certificate for RECEIVER. RECEIVER has the following resource in the default resource set: Private key.p12 the private key file for RECEIVER. Configuring the SENDER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to ENCRYPT. 2 Open ENCRYPT and select the type Legacy. Configure the SMTP (MIME) output connector Select Encrypt.
34 34 Legacy scenarios Configuring the RECEIVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to ENCRYPTED. 2 Open ENCRYPTED and select the type Legacy. 3 On the and HTTP client tab, select Private key file > Private key.p12 and enter the Password to access the private key. Configure the IN input connector 1 Select Retrieve > Advanced. 2 Select Request encryption. Signed s This scenario involves the two StreamServers SENDER and RECEIVER. The SENDER sends signed s to the RECEIVER via an SMTP (MIME) output connector, and the RECEIVER receives the s via an IN input connector. Prerequisites SENDER has the following resource in the default resource set: Private key.p12 the private key file for SENDER. RECEIVER has the following resource in the default resource set: SENDER CA root certificate.crt the CA root certificate for SENDER. This is the only certificate in the certificate chain. Configuring the SENDER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGN. 2 Open SIGN and select the type Legacy. 3 On the and HTTP client tab, select Private key file > Private key.p12 and enter the Password to access the private key. Configure the SMTP (MIME) output connector Select Sign.
35 Legacy scenarios 35 Configuring the RECEIVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGNED. 2 Open SIGNED and select the type Legacy. 3 On the Certificates tab, add the certificate resource SENDER CA root certificate.crt. Configure the IN input connector 1 Select Retrieve > Advanced. 2 Select Request signature. Signed and encrypted s This scenario involves the two StreamServers SENDER and RECEIVER. The SENDER sends signed and encrypted s to the RECEIVER via an SMTP (MIME) output connector, and the RECEIVER receives the s via an IN input connector. Prerequisites SENDER has the following resources in the default resource set: info_abc.com.crt the encryption certificate for RECEIVER. Private key.p12 the private key file for SENDER. RECEIVER has the following resources in the default resource set: Private key.p12 the private key file for RECEIVER. SENDER CA root certificate.crt the CA root certificate for SENDER. This is the only certificate in the certificate chain.
36 36 Legacy scenarios Configuring the SENDER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGN ENCRYPT. 2 Open SIGN ENCRYPT and select the type Legacy. 3 On the and HTTP client tab, select Private key file > Private key.p12 and enter the Password to access the private key. Configure the SMTP (MIME) output connector Select Sign and Encrypt. Configuring the RECEIVER Create the Security configuration 1 Add a security configuration to the default resource set and rename it to SIGNED ENCRYPTED. 2 Open SIGNED ENCRYPTED and select the type Legacy. 3 On the Certificates tab, add the certificate resource SENDER CA root certificate.crt. 4 On the and HTTP client tab, select Private key file > Private key.p12 and enter the Password to access the private key. Configure the IN input connector 1 Select Retrieve > Advanced. 2 Select Request signature and Request encryption.
37 Security configuration GUI reference 37 Security configuration GUI reference Security configuration type Trust Server Legacy All certificate information is retrieved from an XKMS (XML Key Management Specification) compliant Trust Server. Only the root CA that verifies the identity of the Trust Server is stored in a file. See Trust Server settings on page 37. All digital certificates are stored locally. See Legacy settings on page 38. Trust Server settings Certificates tab On this tab, you add all certificate resources to include in the certificate chain used to verify the identity of the Trust Server. Trust Server tab On this tab you specify the connection to the Trust Server. Settings URL User Password The Trust Server URL. The user name to access the Trust Server. The password to access the Trust Server. HTTP tab Use this tab when the StreamServer must authenticate itself to SSL clients or SSL servers. On this tab you enable access to the StreamServer private key. Settings Key name Passphrase The key name assigned to the StreamServer when it was registered in the Trust Server. The key name corresponds to a private key. The passphrase the StreamServer must use to access the private key.
38 38 Security configuration GUI reference tab Use this tab when the StreamServer must sign or decrypt s. On this tab you enable access to the StreamServer private key. Settings Key name Passphrase The key name assigned to the StreamServer when it was registered in the Trust Server. The key name corresponds to a private key. The passphrase the StreamServer must use to access the private key. Legacy settings Certificates tab On this tab, you add all certificate resources to include in the certificate chain used to verify the identity of the SSL server or SSL client. HTTP Server tab Use this tab when the StreamServer runs as an SSL server. On this tab you enable access to the StreamServer private key and, if required, the client certificate. Settings Private key file Password Client Authentication Client certificate The private key file the StreamServer must use to authenticate itself. The private key file must be included in the same resource set as the security configuration. The password the StreamServer must use to access the private key file. Select if this StreamServer requires client authentication. The client certificate. The StreamServer must use this certificate to verify the identity of the client. The client certificate must be included in the same resource set as the security configuration.
39 Security configuration GUI reference 39 and HTTP Client tab Use this tab when the StreamServer runs as an SSL client that must authenticate itself to the SSL server, or when it should sign or decrypt s. Settings Private key file Password The private key file the StreamServer must use to authenticate itself or to decrypt s. The private key file must be included in the same resource set as the security configuration. The password the StreamServer must use to access the private key file.
40 40 Security configuration GUI reference
StreamServe Persuasion SP5 Encryption and Authentication
 StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United
StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United
StreamServe Encryption and Authentication
 StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
StreamServe Email. User Guide. 4.1.2 SP2 Rev A
 StreamServe Email User Guide 4.1.2 SP2 Rev A StreamServe Email User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe, Inc. No part of this document may be reproduced
StreamServe Email User Guide 4.1.2 SP2 Rev A StreamServe Email User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe, Inc. No part of this document may be reproduced
StreamServe Persuasion SP4 Service Broker
 StreamServe Persuasion SP4 Service Broker User Guide Rev A StreamServe Persuasion SP4 Service Broker User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No
StreamServe Persuasion SP4 Service Broker User Guide Rev A StreamServe Persuasion SP4 Service Broker User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No
StreamServe Job Gateway
 StreamServe Job Gateway User Guide 4.1.2 SP2 Rev A StreamServe Job Gateway User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe, Inc. No part of this document may
StreamServe Job Gateway User Guide 4.1.2 SP2 Rev A StreamServe Job Gateway User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe, Inc. No part of this document may
StreamServe Persuasion SP5 Control Center
 StreamServe Persuasion SP5 Control Center User Guide Rev C StreamServe Persuasion SP5 Control Center User Guide Rev C OPEN TEXT CORPORATION ALL RIGHTS RESERVED United States and other international patents
StreamServe Persuasion SP5 Control Center User Guide Rev C StreamServe Persuasion SP5 Control Center User Guide Rev C OPEN TEXT CORPORATION ALL RIGHTS RESERVED United States and other international patents
StreamServe Persuasion SP4 StreamServe Connect for SAP - Business Processes
 StreamServe Persuasion SP4 StreamServe Connect for SAP - Business Processes User Guide Rev A StreamServe Persuasion SP4StreamServe Connect for SAP - Business Processes User Guide Rev A SAP, mysap.com,
StreamServe Persuasion SP4 StreamServe Connect for SAP - Business Processes User Guide Rev A StreamServe Persuasion SP4StreamServe Connect for SAP - Business Processes User Guide Rev A SAP, mysap.com,
StreamServe Persuasion SP4 Connectors
 StreamServe Persuasion SP4 Connectors User Guide Rev A StreamServe Persuasion SP4 Connectors User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No part of
StreamServe Persuasion SP4 Connectors User Guide Rev A StreamServe Persuasion SP4 Connectors User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No part of
StreamServe Persuasion SP5 Document Broker Plus
 StreamServe Persuasion SP5 Document Broker Plus User Guide Rev A StreamServe Persuasion SP5 Document Broker Plus User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520
StreamServe Persuasion SP5 Document Broker Plus User Guide Rev A StreamServe Persuasion SP5 Document Broker Plus User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520
StreamServe Persuasion SP5 Upgrading instructions
 StreamServe Persuasion SP5 Upgrading instructions Reference Guide Rev A Upgrading instructionsstreamserve Persuasion SP5 Reference Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States
StreamServe Persuasion SP5 Upgrading instructions Reference Guide Rev A Upgrading instructionsstreamserve Persuasion SP5 Reference Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States
StreamServe Persuasion SP4
 StreamServe Persuasion SP4 Installation Guide Rev B StreamServe Persuasion SP4 Installation Guide Rev B 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No part of this document
StreamServe Persuasion SP4 Installation Guide Rev B StreamServe Persuasion SP4 Installation Guide Rev B 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United States patent #7,127,520 No part of this document
ECA IIS Instructions. January 2005
 ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
WS_FTP Pro. Addendum to User s Guide. Software Version 6.6. Ipswitch, Inc.
 WS_FTP Pro Addendum to User s Guide Software Version 6.6 Ipswitch, Inc. Ipswitch, Inc. Phone: 781-676-5700 81 Hartwell Ave Fax: 781-676-5710 Lexington, MA 02421-3127 Web: http://www.ipswitch.com The information
WS_FTP Pro Addendum to User s Guide Software Version 6.6 Ipswitch, Inc. Ipswitch, Inc. Phone: 781-676-5700 81 Hartwell Ave Fax: 781-676-5710 Lexington, MA 02421-3127 Web: http://www.ipswitch.com The information
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Djigzo S/MIME setup guide
 Author: Martijn Brinkers Table of Contents...1 Introduction...3 Quick setup...4 Create a CA...4 Fill in the form:...5 Add certificates for internal users...5 Add certificates for external recipients...7
Author: Martijn Brinkers Table of Contents...1 Introduction...3 Quick setup...4 Create a CA...4 Fill in the form:...5 Add certificates for internal users...5 Add certificates for external recipients...7
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2007
 Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2010
 Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
StreamServe Persuasion SP5 StreamStudio
 StreamServe Persuasion SP5 StreamStudio Administrator s Guide Rev B StreamServe Persuasion SP5 StreamStudio Administrator s Guide Rev B OPEN TEXT CORPORATION ALL RIGHTS RESERVED United States and other
StreamServe Persuasion SP5 StreamStudio Administrator s Guide Rev B StreamServe Persuasion SP5 StreamStudio Administrator s Guide Rev B OPEN TEXT CORPORATION ALL RIGHTS RESERVED United States and other
MadCap Software. Upgrading Guide. Pulse
 MadCap Software Upgrading Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
MadCap Software Upgrading Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
StoneGate SSL VPN Technical Note 2068. Adding Bundled Certificates
 StoneGate SSL VPN Technical Note 2068 Adding Bundled Certificates Table of Contents Introduction................................... page 3 Overview..................................... page 3 Splitting
StoneGate SSL VPN Technical Note 2068 Adding Bundled Certificates Table of Contents Introduction................................... page 3 Overview..................................... page 3 Splitting
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
RoomWizard Synchronization Software Manual Installation Instructions
 2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
Setting Up SSL on IIS6 for MEGA Advisor
 Setting Up SSL on IIS6 for MEGA Advisor Revised: July 5, 2012 Created: February 1, 2008 Author: Melinda BODROGI CONTENTS Contents... 2 Principle... 3 Requirements... 4 Install the certification authority
Setting Up SSL on IIS6 for MEGA Advisor Revised: July 5, 2012 Created: February 1, 2008 Author: Melinda BODROGI CONTENTS Contents... 2 Principle... 3 Requirements... 4 Install the certification authority
www.novell.com/documentation Jobs Guide Identity Manager 4.0.1 February 10, 2012
 www.novell.com/documentation Jobs Guide Identity Manager 4.0.1 February 10, 2012 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Jobs Guide Identity Manager 4.0.1 February 10, 2012 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
CHAPTER 7 SSL CONFIGURATION AND TESTING
 CHAPTER 7 SSL CONFIGURATION AND TESTING 7.1 Configuration and Testing of SSL Nowadays, it s very big challenge to handle the enterprise applications as they are much complex and it is a very sensitive
CHAPTER 7 SSL CONFIGURATION AND TESTING 7.1 Configuration and Testing of SSL Nowadays, it s very big challenge to handle the enterprise applications as they are much complex and it is a very sensitive
PUBLIC Connecting a Customer System to SAP HCI
 SAP HANA Cloud Integration for process integration 2015-05-10 PUBLIC Connecting a Customer System to SAP HCI Content 1 Introduction....4 2 Overview of Connection Setup, Tasks, and Roles.... 5 3 Operating
SAP HANA Cloud Integration for process integration 2015-05-10 PUBLIC Connecting a Customer System to SAP HCI Content 1 Introduction....4 2 Overview of Connection Setup, Tasks, and Roles.... 5 3 Operating
Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points
 Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points Objective 1. To explore a practical application of cryptography secure e-mail 2. To use public key encryption 3. To gain experience with the various
Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points Objective 1. To explore a practical application of cryptography secure e-mail 2. To use public key encryption 3. To gain experience with the various
Configure Managed File Transfer Endpoints
 Configure Managed File Transfer Endpoints 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise)
Configure Managed File Transfer Endpoints 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording or otherwise)
Configuring the NetBackup 7.7 Cloud Connector for use with StorReduce
 Configuring the NetBackup 7.7 Cloud Connector for use with StorReduce Introduction This document explains how to configure the NetBackup 7.7 Cloud Connector to work with StorReduce. Prerequisites A functioning
Configuring the NetBackup 7.7 Cloud Connector for use with StorReduce Introduction This document explains how to configure the NetBackup 7.7 Cloud Connector to work with StorReduce. Prerequisites A functioning
Generating and Installing SSL Certificates on the Cisco ISA500
 Application Note Generating and Installing SSL Certificates on the Cisco ISA500 This application note describes how to generate and install SSL certificates on the Cisco ISA500 security appliance. It includes
Application Note Generating and Installing SSL Certificates on the Cisco ISA500 This application note describes how to generate and install SSL certificates on the Cisco ISA500 security appliance. It includes
Clearswift Information Governance
 Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Management Reporter Integration Guide for Microsoft Dynamics GP
 Microsoft Dynamics Management Reporter Integration Guide for Microsoft Dynamics GP July 2013 Find updates to this documentation at the following location: http://go.microsoft.com/fwlink/?linkid=162565
Microsoft Dynamics Management Reporter Integration Guide for Microsoft Dynamics GP July 2013 Find updates to this documentation at the following location: http://go.microsoft.com/fwlink/?linkid=162565
Installing and Configuring vcenter Multi-Hypervisor Manager
 Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
White Paper. Installation and Configuration of Fabasoft Folio IMAP Service. Fabasoft Folio 2015 Update Rollup 3
 White Paper Fabasoft Folio 2015 Update Rollup 3 Copyright Fabasoft R&D GmbH, Linz, Austria, 2016. All rights reserved. All hardware and software names used are registered trade names and/or registered
White Paper Fabasoft Folio 2015 Update Rollup 3 Copyright Fabasoft R&D GmbH, Linz, Austria, 2016. All rights reserved. All hardware and software names used are registered trade names and/or registered
Server Installation Guide ZENworks Patch Management 6.4 SP2
 Server Installation Guide ZENworks Patch Management 6.4 SP2 02_016N 6.4SP2 Server Installation Guide - 2 - Notices Version Information ZENworks Patch Management Server Installation Guide - ZENworks Patch
Server Installation Guide ZENworks Patch Management 6.4 SP2 02_016N 6.4SP2 Server Installation Guide - 2 - Notices Version Information ZENworks Patch Management Server Installation Guide - ZENworks Patch
User Guide Supplement. S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series
 User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
Integrated SSL Scanning
 Version 9.2 SSL Enhancements Copyright 1996-2008. Finjan Software Inc. and its affiliates and subsidiaries ( Finjan ). All rights reserved. All text and figures included in this publication are the exclusive
Version 9.2 SSL Enhancements Copyright 1996-2008. Finjan Software Inc. and its affiliates and subsidiaries ( Finjan ). All rights reserved. All text and figures included in this publication are the exclusive
How to Secure a Groove Manager Web Site
 How to Secure a Groove Manager Web Site Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the companies, organizations,
How to Secure a Groove Manager Web Site Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the companies, organizations,
How to Install Microsoft Mobile Information Server 2002 Server ActiveSync. Joey Masterson
 How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson Copyright Information
How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson Copyright Information
Adding Digital Signature and Encryption in Outlook
 Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
CA NetQoS Performance Center
 CA NetQoS Performance Center Install and Configure SSL for Windows Server 2008 Release 6.1 (and service packs) This Documentation, which includes embedded help systems and electronically distributed materials,
CA NetQoS Performance Center Install and Configure SSL for Windows Server 2008 Release 6.1 (and service packs) This Documentation, which includes embedded help systems and electronically distributed materials,
NSi Mobile Installation Guide. Version 6.2
 NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
NSi Mobile Installation Guide Version 6.2 Revision History Version Date 1.0 October 2, 2012 2.0 September 18, 2013 2 CONTENTS TABLE OF CONTENTS PREFACE... 5 Purpose of this Document... 5 Version Compatibility...
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Customer Tips. Xerox Network Scanning HTTP/HTTPS Configuration using Microsoft IIS. for the user. Purpose. Background
 Xerox Multifunction Devices Customer Tips June 5, 2007 This document applies to these Xerox products: X WC Pro 232/238/245/ 255/265/275 for the user Xerox Network Scanning HTTP/HTTPS Configuration using
Xerox Multifunction Devices Customer Tips June 5, 2007 This document applies to these Xerox products: X WC Pro 232/238/245/ 255/265/275 for the user Xerox Network Scanning HTTP/HTTPS Configuration using
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on. User Information
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
Ciphermail Gateway PDF Encryption Setup Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway PDF Encryption Setup Guide March 6, 2014, Rev: 5454 Copyright c 2008-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Portal 4 3 PDF encryption
CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway PDF Encryption Setup Guide March 6, 2014, Rev: 5454 Copyright c 2008-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Portal 4 3 PDF encryption
CA Unified Infrastructure Management Server
 CA Unified Infrastructure Management Server CA UIM Server Configuration Guide 8.0 Document Revision History Version Date Changes 8.0 September 2014 Rebranded for UIM 8.0. 7.6 June 2014 No revisions for
CA Unified Infrastructure Management Server CA UIM Server Configuration Guide 8.0 Document Revision History Version Date Changes 8.0 September 2014 Rebranded for UIM 8.0. 7.6 June 2014 No revisions for
www.novell.com/documentation Administration Guide Certificate Server 3.3.8 May 2013
 www.novell.com/documentation Administration Guide Certificate Server 3.3.8 May 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Administration Guide Certificate Server 3.3.8 May 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL
 EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL The following manual will outline the configuration and setup for email access by any staff member. There are multiple ways to configure this
EMAIL CONFIGURATION AND SETUP USER GUIDE AND REFERENCE MANUAL The following manual will outline the configuration and setup for email access by any staff member. There are multiple ways to configure this
Setup Guide Access Manager Appliance 3.2 SP3
 Setup Guide Access Manager Appliance 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS
Setup Guide Access Manager Appliance 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS
Bank of Hawaii Protecting Confidential Email
 1 Bank of Hawaii Protecting Confidential Email Email is commonly used to transmit confidential information such as operational data, legal documents, or financial information. By default emails are sent
1 Bank of Hawaii Protecting Confidential Email Email is commonly used to transmit confidential information such as operational data, legal documents, or financial information. By default emails are sent
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
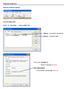 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Personal Secure Email Certificate
 Entrust Certificate Services Personal Secure Email Certificate Enrollment Guide Date of Issue: October 2010 Copyright 2010 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Certificate Services Personal Secure Email Certificate Enrollment Guide Date of Issue: October 2010 Copyright 2010 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
To configure Outlook Express for your InfoMetrics E-mail address:
 To configure Outlook Express for your InfoMetrics E-mail address: 1. Open Outlook Express 2. Click the Tools menu, and select Accounts... 3. Internet Accounts window will open, click Add and menu will
To configure Outlook Express for your InfoMetrics E-mail address: 1. Open Outlook Express 2. Click the Tools menu, and select Accounts... 3. Internet Accounts window will open, click Add and menu will
Management Reporter Integration Guide for Microsoft Dynamics AX
 Microsoft Dynamics Management Reporter Integration Guide for Microsoft Dynamics AX July 2013 Find updates to this documentation at the following location: http://go.microsoft.com/fwlink/?linkid=162565
Microsoft Dynamics Management Reporter Integration Guide for Microsoft Dynamics AX July 2013 Find updates to this documentation at the following location: http://go.microsoft.com/fwlink/?linkid=162565
etoken Enterprise For: SSL SSL with etoken
 etoken Enterprise For: SSL SSL with etoken System Requirements Windows 2000 Internet Explorer 5.0 and above Netscape 4.6 and above etoken R2 or Pro key Install etoken RTE Certificates from: (click on the
etoken Enterprise For: SSL SSL with etoken System Requirements Windows 2000 Internet Explorer 5.0 and above Netscape 4.6 and above etoken R2 or Pro key Install etoken RTE Certificates from: (click on the
How-To Guide SAP NetWeaver Document Version: 1.0-2013-12-22. How To Guide - Configure SSL in ABAP System
 How-To Guide SAP NetWeaver Document Version: 1.0-2013-12-22 Document History Document Version Description 1.0 First official release of this guide Document History 2013 SAP AG or an SAP affiliate company.
How-To Guide SAP NetWeaver Document Version: 1.0-2013-12-22 Document History Document Version Description 1.0 First official release of this guide Document History 2013 SAP AG or an SAP affiliate company.
Integrated SSL Scanning
 Software Version 9.0 Copyright Copyright 1996-2008. Finjan Software Inc. and its affiliates and subsidiaries ( Finjan ). All rights reserved. All text and figures included in this publication are the exclusive
Software Version 9.0 Copyright Copyright 1996-2008. Finjan Software Inc. and its affiliates and subsidiaries ( Finjan ). All rights reserved. All text and figures included in this publication are the exclusive
Scenarios for Setting Up SSL Certificates for View
 Scenarios for Setting Up SSL Certificates for View VMware Horizon 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a
Scenarios for Setting Up SSL Certificates for View VMware Horizon 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a
AD RMS Microsoft Federation Gateway Support Installation and Configuration Guide... 3 About this guide... 3
 Contents AD RMS Microsoft Federation Gateway Support Installation and Configuration Guide... 3 About this guide... 3 Microsoft Federation Gateway Support Overview... 4 Deploying and Configuring Microsoft
Contents AD RMS Microsoft Federation Gateway Support Installation and Configuration Guide... 3 About this guide... 3 Microsoft Federation Gateway Support Overview... 4 Deploying and Configuring Microsoft
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
How to request a certificate
 How to request a certificate Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] Introduction You can use self signed certificates, certificates from your own internal Certification Authority or
How to request a certificate Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] Introduction You can use self signed certificates, certificates from your own internal Certification Authority or
Microsoft Dynamics GP. Workflow Installation Guide Release 10.0
 Microsoft Dynamics GP Workflow Installation Guide Release 10.0 Copyright Copyright 2008 Microsoft Corporation. All rights reserved. Complying with all applicable copyright laws is the responsibility of
Microsoft Dynamics GP Workflow Installation Guide Release 10.0 Copyright Copyright 2008 Microsoft Corporation. All rights reserved. Complying with all applicable copyright laws is the responsibility of
Sophos Mobile Control Installation guide. Product version: 3.5
 Sophos Mobile Control Installation guide Product version: 3.5 Document date: July 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...10 4 External
Sophos Mobile Control Installation guide Product version: 3.5 Document date: July 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...10 4 External
Password Management Guide
 www.novell.com/documentation Management Guide Identity Manager 4.0.2 June 2012 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Management Guide Identity Manager 4.0.2 June 2012 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Using TLS Encryption with Microsoft Outlook 2007
 Using TLS Encryption with Microsoft Outlook 2007 This guide is meant to be used with Microsoft Outlook 2007. While the instructions are similar, the menu layouts and options have changed since the previous
Using TLS Encryption with Microsoft Outlook 2007 This guide is meant to be used with Microsoft Outlook 2007. While the instructions are similar, the menu layouts and options have changed since the previous
WatchDox SharePoint Beta Guide. Application Version 1.0.0
 Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
User Guide. MailMarshal Secure 5.5. August 2006
 User Guide MailMarshal Secure 5.5 August 2006 THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON-DISCLOSURE AGREEMENT.
User Guide MailMarshal Secure 5.5 August 2006 THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON-DISCLOSURE AGREEMENT.
Installation Guide. SafeNet Authentication Service
 SafeNet Authentication Service Installation Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Service Installation Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
StreamServe Persuasion SP5 Ad Hoc Correspondence and Correspondence Reviewer
 StreamServe Persuasion SP5 Ad Hoc Correspondence and Correspondence Reviewer User Guide Rev B StreamServe Persuasion SP5 Ad Hoc Correspondence and Correspondence Reviewer User Guide Rev B 2001-2010 STREAMSERVE,
StreamServe Persuasion SP5 Ad Hoc Correspondence and Correspondence Reviewer User Guide Rev B StreamServe Persuasion SP5 Ad Hoc Correspondence and Correspondence Reviewer User Guide Rev B 2001-2010 STREAMSERVE,
Outlook Web Access Guide to Installing Root Certificates, Generating CSR and Installing SSL Certificate
 Outlook Web Access Guide to Installing Root Certificates, Generating CSR and Installing SSL Certificate Copyright. All rights reserved. Trustis Limited Building 273 New Greenham Park Greenham Common Thatcham
Outlook Web Access Guide to Installing Root Certificates, Generating CSR and Installing SSL Certificate Copyright. All rights reserved. Trustis Limited Building 273 New Greenham Park Greenham Common Thatcham
SolarWinds Technical Reference
 SolarWinds Technical Reference Using SSL Certificates in Web Help Desk Introduction... 1 How WHD Uses SSL... 1 Setting WHD to use HTTPS... 1 Enabling HTTPS and Initializing the Java Keystore... 1 Keys
SolarWinds Technical Reference Using SSL Certificates in Web Help Desk Introduction... 1 How WHD Uses SSL... 1 Setting WHD to use HTTPS... 1 Enabling HTTPS and Initializing the Java Keystore... 1 Keys
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication
 DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
SMART Vantage. Installation guide
 SMART Vantage Installation guide Product registration If you register your SMART product, we ll notify you of new features and software upgrades. Register online at smarttech.com/registration. Keep the
SMART Vantage Installation guide Product registration If you register your SMART product, we ll notify you of new features and software upgrades. Register online at smarttech.com/registration. Keep the
DocuShare Email Agent User Guide
 DocuShare Email Agent User Guide Publication date: February 2011 This document supports DocuShare Release 6.6.1 Prepared by: Xerox Corporation DocuShare Business Unit 3400 Hillview Avenue Palo Alto, California
DocuShare Email Agent User Guide Publication date: February 2011 This document supports DocuShare Release 6.6.1 Prepared by: Xerox Corporation DocuShare Business Unit 3400 Hillview Avenue Palo Alto, California
POP3 Connector for Exchange - Configuration
 Eclarsys PopGrabber POP3 Connector for Exchange - Configuration PopGrabber is an excellent replacement for the POP3 connector included in Windows SBS 2000 and 2003. It also works, of course, with Exchange
Eclarsys PopGrabber POP3 Connector for Exchange - Configuration PopGrabber is an excellent replacement for the POP3 connector included in Windows SBS 2000 and 2003. It also works, of course, with Exchange
Instructions for Microsoft Outlook 2003
 ElkhartNet, Inc. is dedicated to providing our email customers with excellent service and support. In a targeted effort to reduce SPAM and to provide more secure and faster email, we are changing our outgoing
ElkhartNet, Inc. is dedicated to providing our email customers with excellent service and support. In a targeted effort to reduce SPAM and to provide more secure and faster email, we are changing our outgoing
Internet Script Editor (ISE)
 ISE Application, page 1 ISE Functionality, page 1 ISE Requirements, page 2 Secure Socket Layer (SSL) Requirements for ISE, page 2 ISE Installation and Upgrades, page 5 Troubleshooting Tools for Internet
ISE Application, page 1 ISE Functionality, page 1 ISE Requirements, page 2 Secure Socket Layer (SSL) Requirements for ISE, page 2 ISE Installation and Upgrades, page 5 Troubleshooting Tools for Internet
Novell Identity Manager
 Password Management Guide AUTHORIZED DOCUMENTATION Novell Identity Manager 3.6.1 June 05, 2009 www.novell.com Identity Manager 3.6.1 Password Management Guide Legal Notices Novell, Inc. makes no representations
Password Management Guide AUTHORIZED DOCUMENTATION Novell Identity Manager 3.6.1 June 05, 2009 www.novell.com Identity Manager 3.6.1 Password Management Guide Legal Notices Novell, Inc. makes no representations
Sophos Mobile Control Installation guide. Product version: 3.6
 Sophos Mobile Control Installation guide Product version: 3.6 Document date: November 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...5 3 Set up Sophos Mobile Control...11 4 External
Sophos Mobile Control Installation guide Product version: 3.6 Document date: November 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...5 3 Set up Sophos Mobile Control...11 4 External
How To Install A Citrix Netscaler On A Pc Or Mac Or Ipad (For A Web Browser) With A Certificate Certificate (For An Ipad) On A Netscaler (For Windows) With An Ipro (For
 Deployment Guide Deployment Guide VeriSign Certificate Authority Citrix NetScaler SSL Deployment Guide Notice: The information in this publication is subject to change without notice. THIS PUBLICATION
Deployment Guide Deployment Guide VeriSign Certificate Authority Citrix NetScaler SSL Deployment Guide Notice: The information in this publication is subject to change without notice. THIS PUBLICATION
SafeGuard Enterprise Web Helpdesk. Product version: 6 Document date: February 2012
 SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
Veritas Cluster Server Database Agent for Microsoft SQL Configuration Guide
 Veritas Cluster Server Database Agent for Microsoft SQL Configuration Guide Windows Server 2003, Windows Server 2008 5.1 Veritas Cluster Server Database Agent for Microsoft SQL Configuration Guide Copyright
Veritas Cluster Server Database Agent for Microsoft SQL Configuration Guide Windows Server 2003, Windows Server 2008 5.1 Veritas Cluster Server Database Agent for Microsoft SQL Configuration Guide Copyright
Basic Exchange Setup Guide
 Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
Ciphermail for Android Quick Start Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail for Android Quick Start Guide June 19, 2014, Rev: 5460 Copyright 2011-2014, ciphermail.com 3 CONFIGURATION WIZARD 1 Introduction This quick start guide helps you
CIPHERMAIL EMAIL ENCRYPTION Ciphermail for Android Quick Start Guide June 19, 2014, Rev: 5460 Copyright 2011-2014, ciphermail.com 3 CONFIGURATION WIZARD 1 Introduction This quick start guide helps you
Junio 2015. SSL WebLogic Oracle. Guía de Instalación. Junio, 2015. SSL WebLogic Oracle Guía de Instalación CONFIDENCIAL Página 1 de 19
 SSL WebLogic Oracle Guía de Instalación Junio, 2015 Página 1 de 19 Setting Up SSL on Oracle WebLogic Server This section describes how to configure SSL on Oracle WebLogic Server for PeopleTools 8.50. 1.
SSL WebLogic Oracle Guía de Instalación Junio, 2015 Página 1 de 19 Setting Up SSL on Oracle WebLogic Server This section describes how to configure SSL on Oracle WebLogic Server for PeopleTools 8.50. 1.
Unifying Information Security. Implementing TLS on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Setup Guide Access Manager 3.2 SP3
 Setup Guide Access Manager 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
Setup Guide Access Manager 3.2 SP3 August 2014 www.netiq.com/documentation Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE
How to Install SSL Certificates on Microsoft Servers
 How to Install SSL Certificates on Microsoft Servers Ch apter 3: Using SSL Certificates in Microsoft Internet Information Server... 36 Ins talling SSL Certificates in IIS with IIS Manager... 37 Requesting
How to Install SSL Certificates on Microsoft Servers Ch apter 3: Using SSL Certificates in Microsoft Internet Information Server... 36 Ins talling SSL Certificates in IIS with IIS Manager... 37 Requesting
Email Account Create for Outlook Express
 Email Account Create for Outlook Express Click Start Menu Choose Outlook Express Click Tools menu from Menu Bar and then click Accounts In Internet Account Wizard, Click Add Button and Click Mail. 1 In
Email Account Create for Outlook Express Click Start Menu Choose Outlook Express Click Tools menu from Menu Bar and then click Accounts In Internet Account Wizard, Click Add Button and Click Mail. 1 In
SafeGuard Enterprise Web Helpdesk. Product version: 6.1
 SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
StarWind iscsi SAN Software: Challenge-Handshake Authentication Protocol (CHAP) for Authentication of Users
 StarWind iscsi SAN Software: Challenge-Handshake Authentication Protocol (CHAP) for Authentication of Users www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011.
StarWind iscsi SAN Software: Challenge-Handshake Authentication Protocol (CHAP) for Authentication of Users www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011.
DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO
 DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO Contents Overview...1 System requirements...1 Enterprise Server:...1 Client PCs:...1 Section 1: Before installing...1 Section 2: Download
DESlock+ Basic Setup Guide ENTERPRISE SERVER ESSENTIAL/STANDARD/PRO Contents Overview...1 System requirements...1 Enterprise Server:...1 Client PCs:...1 Section 1: Before installing...1 Section 2: Download
App Orchestration 2.5
 Configuring NetScaler 10.5 Load Balancing with StoreFront 2.5.2 and NetScaler Gateway for Prepared by: James Richards Last Updated: August 20, 2014 Contents Introduction... 3 Configure the NetScaler load
Configuring NetScaler 10.5 Load Balancing with StoreFront 2.5.2 and NetScaler Gateway for Prepared by: James Richards Last Updated: August 20, 2014 Contents Introduction... 3 Configure the NetScaler load
SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014]
![SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014] SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014]](/thumbs/34/16904074.jpg) SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP
SSL Configuration on Weblogic Oracle FLEXCUBE Universal Banking Release 12.0.87.01.0 [August] [2014] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP
Set Up E-mail Setup with Microsoft Outlook 2007 using POP3
 Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Configuring Email Notification for Business Glossary
 Configuring Email Notification for Business Glossary 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Configuring Email Notification for Business Glossary 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Workflow approval via email
 Microsoft Dynamics AX Workflow approval via email White Paper This document highlights the functionality in Microsoft Dynamics AX 2012 R2 that allows workflow to be configured so that a user can take approval
Microsoft Dynamics AX Workflow approval via email White Paper This document highlights the functionality in Microsoft Dynamics AX 2012 R2 that allows workflow to be configured so that a user can take approval
Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows
 Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows SecureZIP for Windows interoperates with leading PKI vendors including Entrust, VeriSign, and RSA to enable the
Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows SecureZIP for Windows interoperates with leading PKI vendors including Entrust, VeriSign, and RSA to enable the
