|
|
|
- Alfred Hardy
- 8 years ago
- Views:
Transcription
1 Test Case Generation for Ultimately Periodic Paths Joint work with Saddek Bensalem Hongyang Qu Stavros Tripakis Lenore Zuck Accepted to HVC 2007
2 How to find the condition to execute a path? (weakest precondition wp(true)) Put true at end of path. Propagate path backwards. On assignment, relativize (backwards assignment). On yes edge of decision, add decision as conjunction. On no edge, add negation of decision as conjunction. A>1/\B=0 no yes X:=X/A yes A=2\/X>1 no X:=X+1 true
3 How to find the condition to execute a path? Put true at end of path. Propagate path backwards. On assignment, relativize (backwards assignment). On yes edge of decision, add decision as conjunction. On no edge, add negation of decision as conjunction. A>1/\B=0 no yes X:=X/A A 2/\X 1 yes A=2\/X>1 no X:=X+1 true
4 How to find the condition to execute a path? Put true at end of path. Propagate path backwards. On assignment, relativize (backwards assignment). On yes edge of decision, add decision as conjunction. On no edge, add negation of decision as conjunction. A>1/\B=0 no yes A 2/\X/A 1 X:=X/A A 2/\X 1 A=2\/X>1 yes no X:=X+1 true
5 How to find the condition to execute a path? Put true at end of path. Propagate path backwards. On assignment, relativize (backwards assignment). On yes edge of decision, add decision as conjunction. On no edge, add negation of decision as conjunction. A>1/\B=0 no yes A 2/\X 1 A=2\/X>1 no A 2/\X/A 1/\ A>1/\B=0 yes X:=X/A X:=X+1 A 2/\X/A 1 true
6 How to find the transformation of a graph tr(x)? Start with the set of variables that participate. a,b,x A>1/\B=0 no yes X:=X/A A=2\/X>1 no yes X:=X+1
7 How to find the transformation of a graph? Start with the set of variables that participate. Apply transformation syntactically forwards. a,b,x A>1/\B=0 no yes X:=X/A A=2\/X>1 no yes X:=X+1 a,b,(x/a)+1
8 How to find the transformation of a graph? Start with the set of variables that participate. Apply transformation syntactically forwards. a,b,x A>1/\B=0 no yes X:=X/A yes A=2\/X>1 no X:=X+1 a,b,x/a a,b,(x/a)+1
9 How to calculate a path condition for an ultimately periodic path? This is the subject of this work! Of course in general this is an undecidable problem.
10 Test case generation based on LTL specification LTL Aut Compiler Flow chart Model Checker Path Path condition calculation Transitions First order instantiator Test monitoring
11 Goals Verification of software. Compositional verification. Use only a unit of code instead of the whole code. Parameterized verification. Verifies a procedure with any value of parameters in one shot Generating test cases via path conditions: A truth assignment satisfying the path condition. Helps derive the demonstration of errors. Generating appropriate values to missing parameters.
12 Spec: at l 2 U (at l 2 /\ x y /\ ο( at l 2 /\( at l 2 U at l 2 /\ x 2 y ))) Automatic translation of LTL formula into an automaton [Gerth et all] LTL is interpreted over finite sequences. Can use other (linear) specification. Property specifies the path we want to find (SPIN: never claim), not the property that must hold for all paths (for this, take the negation). at l 2 Observation: each node has conjunctions of predicates onprogram variables and program at l 2 /\ counters x y at l 2 at l 2 /\ x 2 y
13 Divide and Conquer Intersect property automaton with the flow chart, regardless of the statements and program variables expressions. Add assertions from the property automaton to further restrict the path condition. Calculate path conditions for sequences found in the intersection. Calculate path conditions on-the-fly. Backtrack when condition is false. Thus, advantage to forward calculation of path conditions (incrementally).
14 Spec: (only program counters here) at l 2 U (at l 2 /\ο at l 2 /\( at l 2 U at l 2 )) at l 2 l 2 :x:=x+z l 2 :x:=x+z at l 2 X at l 2 l 3 :x<t = at l 2 l 3 :x<t Either all executions of a path satisfy the formula or none. at l 2 at l 2 l 1 : at l 2 l 2 :x:=x+z Sifts away paths not satisfying formula. Then calculate path condition.
15 Spec: at l 2 U (at l 2 /\ x y /\ at l 2 ο( at l 2 /\( at l 2 U at l 2 /\ x 2 y ))) x y X l 2 :x:=x+z l 2 :x:=x+z at l 2 /\ x y l 3 :x<t = l 3 :x<t Only some executions of path may satisfy formula at l 2 at l 2 /\ x 2 y l 1 : l 2 :x:=x+z x 2 y Modify calculation of path condition to incorporate property
16 Calculating the intersection of the property automaton and flow graph (abstract variables away). a a s 1 s 2 a q 1 <> a a Acceptance is determined by property automaton. a s 3 q 2 s 1,q 1 a s 2,q 1 s 3,q 2 a a
17 How to generate test cases Take the intersection of an LTL automaton (for a never claim) with the flow graph. Some paths would be eliminated for not satisfying the assertions on the program counters. Seeing same flow chart node does not mean a loop: program variables may value. Use iterative deepening. For each initial path calculate the path condition. Backtrack if condition simplifies to false. Report path condition based on flow graph path+ltl assertions. Always simplify conditions!
18 How the LTL formula directs the search Consider (x=4)u (x=5/\o ) x=4 x=5 false x<5 true y:=7 x:=x+1
19 How the LTL formula directs the search Consider x=4u (x=5/\o ) x=4 x=5 false x<5 true y:=7 x:=x+1
20 How the LTL formula directs the search Consider x=4u (x=5/\o ) x=4 X=4 x=5 false x<5 true y:=7 x:=x+1
21 How the LTL formula directs the search Consider x=4u (x=5/\o ) x=4 X=4 x=5 false x<5 true X=4 y:=7 x:=x+1
22 How the LTL formula directs the search Consider x=4u (x=5/\o ) x=4 X=4 x=5 y:=7 false x<5 true X=4 x:=x+1 This is a contradiction X=4 x<5 true
23 How the LTL formula directs the search Consider x=4u (x=5/\o ) x=4 X=5 x=5 false x<5 true X=4 y:=7 x:=x+1
24 How the LTL formula directs the search Consider x=4u (x=5/\o ) x=4 X=5 x=5 false x<5 true X=4 y:=7 x:=x+1
25 Why use Temporal specification Temporal specification for sequential software? Deadlock? Liveness? No! Captures the tester s intuition about the location of an error: I think a problem may occur when the program runs through the main while loop twice, then the if condition holds, while t>17.
26 Example: GCD a>0/\b>0/\at l 0 /\ at l 7 l 0 l 1 :x:=a l 2 :y:=b l 3 :z:=x rem y at l 0 /\ a>0/\ b>0 l 4 :y:=z l 5 :x:=y at l 7 no l 6 :z=0? yes l 7
27 Example: GCD l 0 l 1 :x:=a l 2 :y:=b a>0/\b>0/\at l 0 /\ at l 7 l 3 :z:=x rem y Path 1: l 0 l 1 l 2 l 3 l 4 l 5 l 6 l 7 a>0/\b>0/\a rem b=0 l 4 :y:=z Path 2: l 0 l 1 l 2 l 3 l 4 l 5 l 6 l 3 l 4 l 5 l 6 l 7 a>0/\b>0/\a rem b 0 no l 5 :x:=y l 6 :z=0? yes l 7
28 Potential explosion Bad point: potential explosion Good point: may be chopped on-the-fly
29 Again: How to deal with the ultimately periodic case?
30 The Equality Method We are looking for the condition to execute a loop indefinitely, after a finite prefix, where in each iteration, the variables obtain the same values. Executing the periodic part ρ once when wp ρ /\X=tr ρ (X). Executing it after the prefix σ is when wp σρ /\wp σ (wp ρ /\X=tr ρ (X)). Simplifying: wp σρ /\wp σ (X=tr ρ (X)).
31 Example σ: z:=z-1; while ρ: x>0 do begin y:=x; x:=(x*2+z+y)/3 End wp σρ =x>0. tr ρ (x,y,z)=( (x*2+z+x)/3,x,z) x=(x*2+z+x)/3/\y=x, or equivalently, z=0/\y=x. wp σ (z=0/\y=x) is z=1/\y=x. Overall: x>0/\z=1/\y=x.
32 The Monotonicity Method It is sufficient to find a loop invariant such that I wp ρ (I) The weakest such invariant I is I= wp ρ (true). Proof: I true for each I. By monotonicity of wp, wp ρ (I) wp ρ (true). Since I wp ρ (I), it holds that I wp ρ (true), independently of I.
33 Deriving an ultimately periodic condition We set I= wp ρ (true) in the implication I wp ρ (I), obtaining wp ρ (true) wp ρ (wp ρ (true)). This can be rewritten as wp ρ (true) wp ρ (true)[tr ρ (X)/X]. Applying the wp of the prefix, we obtain wp σ (wp ρ (true)) wp σ (wp ρ (true)[tr ρ (X)/X]). The next slide will deal with the 2 nd bullet (and then we need to remember to apply the 3 rd ).
34 The case where wp ρ (true) is e 0 (or e>0). Set e =e[tr ρ (X)/X]. Bullet 2 from previous slide becomes e 0 e 0. A sufficient condition is e e. Other cases: when we have a condition wp ρ (true)=g f, we take e=g-f. In case wp ρ (true)=g 0/\f 0 we have condition g g /\f f. In case wp ρ (true)=g 0\/f 0 it is sufficient that we strengthen to either g g or f f. An equality can be transformed into two inequalities and the disjunction case is applied.
35 Some Mixed and not completely Ultimately Periodic paths While x>1 do begin if PowerTwo(x-1) then x:=4*(x-1) else x:=x-1 end. Example:
36 Conclusions An approach for generating test cases automatically. Also: verification of infinite state systems. Path by path verification rather than state by state. Challenge: the weakest precondition for ultimately periodic sequences in infinite state systems. We suggested several methods (e.g., the equality and monotonicity methods, etc.) Not all of the infinite executions are ultimately periodic.
Algebraic expressions are a combination of numbers and variables. Here are examples of some basic algebraic expressions.
 Page 1 of 13 Review of Linear Expressions and Equations Skills involving linear equations can be divided into the following groups: Simplifying algebraic expressions. Linear expressions. Solving linear
Page 1 of 13 Review of Linear Expressions and Equations Skills involving linear equations can be divided into the following groups: Simplifying algebraic expressions. Linear expressions. Solving linear
Today s Agenda. Automata and Logic. Quiz 4 Temporal Logic. Introduction Buchi Automata Linear Time Logic Summary
 Today s Agenda Quiz 4 Temporal Logic Formal Methods in Software Engineering 1 Automata and Logic Introduction Buchi Automata Linear Time Logic Summary Formal Methods in Software Engineering 2 1 Buchi Automata
Today s Agenda Quiz 4 Temporal Logic Formal Methods in Software Engineering 1 Automata and Logic Introduction Buchi Automata Linear Time Logic Summary Formal Methods in Software Engineering 2 1 Buchi Automata
Testing LTL Formula Translation into Büchi Automata
 Testing LTL Formula Translation into Büchi Automata Heikki Tauriainen and Keijo Heljanko Helsinki University of Technology, Laboratory for Theoretical Computer Science, P. O. Box 5400, FIN-02015 HUT, Finland
Testing LTL Formula Translation into Büchi Automata Heikki Tauriainen and Keijo Heljanko Helsinki University of Technology, Laboratory for Theoretical Computer Science, P. O. Box 5400, FIN-02015 HUT, Finland
Model Checking: An Introduction
 Announcements Model Checking: An Introduction Meeting 2 Office hours M 1:30pm-2:30pm W 5:30pm-6:30pm (after class) and by appointment ECOT 621 Moodle problems? Fundamentals of Programming Languages CSCI
Announcements Model Checking: An Introduction Meeting 2 Office hours M 1:30pm-2:30pm W 5:30pm-6:30pm (after class) and by appointment ECOT 621 Moodle problems? Fundamentals of Programming Languages CSCI
Algorithmic Software Verification
 Algorithmic Software Verification (LTL Model Checking) Azadeh Farzan What is Verification Anyway? Proving (in a formal way) that program satisfies a specification written in a logical language. Formal
Algorithmic Software Verification (LTL Model Checking) Azadeh Farzan What is Verification Anyway? Proving (in a formal way) that program satisfies a specification written in a logical language. Formal
Software Modeling and Verification
 Software Modeling and Verification Alessandro Aldini DiSBeF - Sezione STI University of Urbino Carlo Bo Italy 3-4 February 2015 Algorithmic verification Correctness problem Is the software/hardware system
Software Modeling and Verification Alessandro Aldini DiSBeF - Sezione STI University of Urbino Carlo Bo Italy 3-4 February 2015 Algorithmic verification Correctness problem Is the software/hardware system
Coverability for Parallel Programs
 2015 http://excel.fit.vutbr.cz Coverability for Parallel Programs Lenka Turoňová* Abstract We improve existing method for the automatic verification of systems with parallel running processes. The technique
2015 http://excel.fit.vutbr.cz Coverability for Parallel Programs Lenka Turoňová* Abstract We improve existing method for the automatic verification of systems with parallel running processes. The technique
Rigorous Software Development CSCI-GA 3033-009
 Rigorous Software Development CSCI-GA 3033-009 Instructor: Thomas Wies Spring 2013 Lecture 11 Semantics of Programming Languages Denotational Semantics Meaning of a program is defined as the mathematical
Rigorous Software Development CSCI-GA 3033-009 Instructor: Thomas Wies Spring 2013 Lecture 11 Semantics of Programming Languages Denotational Semantics Meaning of a program is defined as the mathematical
Formal Verification of Software
 Formal Verification of Software Sabine Broda Department of Computer Science/FCUP 12 de Novembro de 2014 Sabine Broda (DCC-FCUP) Formal Verification of Software 12 de Novembro de 2014 1 / 26 Formal Verification
Formal Verification of Software Sabine Broda Department of Computer Science/FCUP 12 de Novembro de 2014 Sabine Broda (DCC-FCUP) Formal Verification of Software 12 de Novembro de 2014 1 / 26 Formal Verification
Software Engineering using Formal Methods
 Software Engineering using Formal Methods Model Checking with Temporal Logic Wolfgang Ahrendt 24th September 2013 SEFM: Model Checking with Temporal Logic /GU 130924 1 / 33 Model Checking with Spin model
Software Engineering using Formal Methods Model Checking with Temporal Logic Wolfgang Ahrendt 24th September 2013 SEFM: Model Checking with Temporal Logic /GU 130924 1 / 33 Model Checking with Spin model
Fundamentals of Software Engineering
 Fundamentals of Software Engineering Model Checking with Temporal Logic Ina Schaefer Institute for Software Systems Engineering TU Braunschweig, Germany Slides by Wolfgang Ahrendt, Richard Bubel, Reiner
Fundamentals of Software Engineering Model Checking with Temporal Logic Ina Schaefer Institute for Software Systems Engineering TU Braunschweig, Germany Slides by Wolfgang Ahrendt, Richard Bubel, Reiner
Static Program Transformations for Efficient Software Model Checking
 Static Program Transformations for Efficient Software Model Checking Shobha Vasudevan Jacob Abraham The University of Texas at Austin Dependable Systems Large and complex systems Software faults are major
Static Program Transformations for Efficient Software Model Checking Shobha Vasudevan Jacob Abraham The University of Texas at Austin Dependable Systems Large and complex systems Software faults are major
Formal Verification by Model Checking
 Formal Verification by Model Checking Natasha Sharygina Carnegie Mellon University Guest Lectures at the Analysis of Software Artifacts Class, Spring 2005 1 Outline Lecture 1: Overview of Model Checking
Formal Verification by Model Checking Natasha Sharygina Carnegie Mellon University Guest Lectures at the Analysis of Software Artifacts Class, Spring 2005 1 Outline Lecture 1: Overview of Model Checking
Lecture 9 verifying temporal logic
 Basics of advanced software systems Lecture 9 verifying temporal logic formulae with SPIN 21/01/2013 1 Outline for today 1. Introduction: motivations for formal methods, use in industry 2. Developing models
Basics of advanced software systems Lecture 9 verifying temporal logic formulae with SPIN 21/01/2013 1 Outline for today 1. Introduction: motivations for formal methods, use in industry 2. Developing models
tutorial: hardware and software model checking
 tutorial: hardware and software model checking gerard holzmann and anuj puri { gerard anuj } @research.bell-labs.com Bell Labs, USA outline introduction (15 mins) theory and algorithms system modeling
tutorial: hardware and software model checking gerard holzmann and anuj puri { gerard anuj } @research.bell-labs.com Bell Labs, USA outline introduction (15 mins) theory and algorithms system modeling
Combining Software and Hardware Verification Techniques
 Formal Methods in System Design, 21, 251 280, 2002 c 2002 Kluwer Academic Publishers. Manufactured in The Netherlands. Combining Software and Hardware Verification Techniques ROBERT P. KURSHAN VLADIMIR
Formal Methods in System Design, 21, 251 280, 2002 c 2002 Kluwer Academic Publishers. Manufactured in The Netherlands. Combining Software and Hardware Verification Techniques ROBERT P. KURSHAN VLADIMIR
A Classification of Model Checking-based Verification Approaches for Software Models
 A Classification of Model Checking-based Verification Approaches for Software Models Petra Brosch, Sebastian Gabmeyer, Martina Seidl Sebastian Gabmeyer Business Informatics Group Institute of Software
A Classification of Model Checking-based Verification Approaches for Software Models Petra Brosch, Sebastian Gabmeyer, Martina Seidl Sebastian Gabmeyer Business Informatics Group Institute of Software
Factoring Flow Chart
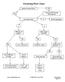 Factoring Flow Chart greatest common factor? YES NO factor out GCF leaving GCF(quotient) how many terms? 4+ factor by grouping 2 3 difference of squares? perfect square trinomial? YES YES NO NO a 2 -b
Factoring Flow Chart greatest common factor? YES NO factor out GCF leaving GCF(quotient) how many terms? 4+ factor by grouping 2 3 difference of squares? perfect square trinomial? YES YES NO NO a 2 -b
http://aejm.ca Journal of Mathematics http://rema.ca Volume 1, Number 1, Summer 2006 pp. 69 86
 Atlantic Electronic http://aejm.ca Journal of Mathematics http://rema.ca Volume 1, Number 1, Summer 2006 pp. 69 86 AUTOMATED RECOGNITION OF STUTTER INVARIANCE OF LTL FORMULAS Jeffrey Dallien 1 and Wendy
Atlantic Electronic http://aejm.ca Journal of Mathematics http://rema.ca Volume 1, Number 1, Summer 2006 pp. 69 86 AUTOMATED RECOGNITION OF STUTTER INVARIANCE OF LTL FORMULAS Jeffrey Dallien 1 and Wendy
CHAPTER 7 GENERAL PROOF SYSTEMS
 CHAPTER 7 GENERAL PROOF SYSTEMS 1 Introduction Proof systems are built to prove statements. They can be thought as an inference machine with special statements, called provable statements, or sometimes
CHAPTER 7 GENERAL PROOF SYSTEMS 1 Introduction Proof systems are built to prove statements. They can be thought as an inference machine with special statements, called provable statements, or sometimes
INF5140: Specification and Verification of Parallel Systems
 INF5140: Specification and Verification of Parallel Systems Lecture 7 LTL into Automata and Introduction to Promela Gerardo Schneider Department of Informatics University of Oslo INF5140, Spring 2007 Gerardo
INF5140: Specification and Verification of Parallel Systems Lecture 7 LTL into Automata and Introduction to Promela Gerardo Schneider Department of Informatics University of Oslo INF5140, Spring 2007 Gerardo
Access Control Based on Dynamic Monitoring for Detecting Software Malicious Behaviours
 Access Control Based on Dynamic Monitoring for Detecting Software Malicious Behaviours K. Adi, L. Sullivan & A. El Kabbal Computer Security Research Laboratory http://w3.uqo.ca/lrsi NCAC'05 1 Motivation
Access Control Based on Dynamic Monitoring for Detecting Software Malicious Behaviours K. Adi, L. Sullivan & A. El Kabbal Computer Security Research Laboratory http://w3.uqo.ca/lrsi NCAC'05 1 Motivation
Optimizations. Optimization Safety. Optimization Safety. Control Flow Graphs. Code transformations to improve program
 Optimizations Code transformations to improve program Mainly: improve execution time Also: reduce program size Control low Graphs Can be done at high level or low level E.g., constant folding Optimizations
Optimizations Code transformations to improve program Mainly: improve execution time Also: reduce program size Control low Graphs Can be done at high level or low level E.g., constant folding Optimizations
1.5. Factorisation. Introduction. Prerequisites. Learning Outcomes. Learning Style
 Factorisation 1.5 Introduction In Block 4 we showed the way in which brackets were removed from algebraic expressions. Factorisation, which can be considered as the reverse of this process, is dealt with
Factorisation 1.5 Introduction In Block 4 we showed the way in which brackets were removed from algebraic expressions. Factorisation, which can be considered as the reverse of this process, is dealt with
PUTNAM TRAINING POLYNOMIALS. Exercises 1. Find a polynomial with integral coefficients whose zeros include 2 + 5.
 PUTNAM TRAINING POLYNOMIALS (Last updated: November 17, 2015) Remark. This is a list of exercises on polynomials. Miguel A. Lerma Exercises 1. Find a polynomial with integral coefficients whose zeros include
PUTNAM TRAINING POLYNOMIALS (Last updated: November 17, 2015) Remark. This is a list of exercises on polynomials. Miguel A. Lerma Exercises 1. Find a polynomial with integral coefficients whose zeros include
CS510 Software Engineering
 CS510 Software Engineering Propositional Logic Asst. Prof. Mathias Payer Department of Computer Science Purdue University TA: Scott A. Carr Slides inspired by Xiangyu Zhang http://nebelwelt.net/teaching/15-cs510-se
CS510 Software Engineering Propositional Logic Asst. Prof. Mathias Payer Department of Computer Science Purdue University TA: Scott A. Carr Slides inspired by Xiangyu Zhang http://nebelwelt.net/teaching/15-cs510-se
FACTORING POLYNOMIALS
 296 (5-40) Chapter 5 Exponents and Polynomials where a 2 is the area of the square base, b 2 is the area of the square top, and H is the distance from the base to the top. Find the volume of a truncated
296 (5-40) Chapter 5 Exponents and Polynomials where a 2 is the area of the square base, b 2 is the area of the square top, and H is the distance from the base to the top. Find the volume of a truncated
Name Intro to Algebra 2. Unit 1: Polynomials and Factoring
 Name Intro to Algebra 2 Unit 1: Polynomials and Factoring Date Page Topic Homework 9/3 2 Polynomial Vocabulary No Homework 9/4 x In Class assignment None 9/5 3 Adding and Subtracting Polynomials Pg. 332
Name Intro to Algebra 2 Unit 1: Polynomials and Factoring Date Page Topic Homework 9/3 2 Polynomial Vocabulary No Homework 9/4 x In Class assignment None 9/5 3 Adding and Subtracting Polynomials Pg. 332
Unit 3: Day 2: Factoring Polynomial Expressions
 Unit 3: Day : Factoring Polynomial Expressions Minds On: 0 Action: 45 Consolidate:10 Total =75 min Learning Goals: Extend knowledge of factoring to factor cubic and quartic expressions that can be factored
Unit 3: Day : Factoring Polynomial Expressions Minds On: 0 Action: 45 Consolidate:10 Total =75 min Learning Goals: Extend knowledge of factoring to factor cubic and quartic expressions that can be factored
What does the number m in y = mx + b measure? To find out, suppose (x 1, y 1 ) and (x 2, y 2 ) are two points on the graph of y = mx + b.
 PRIMARY CONTENT MODULE Algebra - Linear Equations & Inequalities T-37/H-37 What does the number m in y = mx + b measure? To find out, suppose (x 1, y 1 ) and (x 2, y 2 ) are two points on the graph of
PRIMARY CONTENT MODULE Algebra - Linear Equations & Inequalities T-37/H-37 What does the number m in y = mx + b measure? To find out, suppose (x 1, y 1 ) and (x 2, y 2 ) are two points on the graph of
Chapter 9. Systems of Linear Equations
 Chapter 9. Systems of Linear Equations 9.1. Solve Systems of Linear Equations by Graphing KYOTE Standards: CR 21; CA 13 In this section we discuss how to solve systems of two linear equations in two variables
Chapter 9. Systems of Linear Equations 9.1. Solve Systems of Linear Equations by Graphing KYOTE Standards: CR 21; CA 13 In this section we discuss how to solve systems of two linear equations in two variables
Temporal Logics. Computation Tree Logic
 Temporal Logics CTL: definition, relationship between operators, adequate sets, specifying properties, safety/liveness/fairness Modeling: sequential, concurrent systems; maximum parallelism/interleaving
Temporal Logics CTL: definition, relationship between operators, adequate sets, specifying properties, safety/liveness/fairness Modeling: sequential, concurrent systems; maximum parallelism/interleaving
Lecture Notes on Static Analysis
 Lecture Notes on Static Analysis Michael I. Schwartzbach BRICS, Department of Computer Science University of Aarhus, Denmark mis@brics.dk Abstract These notes present principles and applications of static
Lecture Notes on Static Analysis Michael I. Schwartzbach BRICS, Department of Computer Science University of Aarhus, Denmark mis@brics.dk Abstract These notes present principles and applications of static
Software Verification and Testing. Lecture Notes: Temporal Logics
 Software Verification and Testing Lecture Notes: Temporal Logics Motivation traditional programs (whether terminating or non-terminating) can be modelled as relations are analysed wrt their input/output
Software Verification and Testing Lecture Notes: Temporal Logics Motivation traditional programs (whether terminating or non-terminating) can be modelled as relations are analysed wrt their input/output
logic language, static/dynamic models SAT solvers Verified Software Systems 1 How can we model check of a program or system?
 5. LTL, CTL Last part: Alloy logic language, static/dynamic models SAT solvers Today: Temporal Logic (LTL, CTL) Verified Software Systems 1 Overview How can we model check of a program or system? Modeling
5. LTL, CTL Last part: Alloy logic language, static/dynamic models SAT solvers Today: Temporal Logic (LTL, CTL) Verified Software Systems 1 Overview How can we model check of a program or system? Modeling
PROPERTECHNIQUEOFSOFTWARE INSPECTIONUSING GUARDED COMMANDLANGUAGE
 International Journal of Computer ScienceandCommunication Vol. 2, No. 1, January-June2011, pp. 153-157 PROPERTECHNIQUEOFSOFTWARE INSPECTIONUSING GUARDED COMMANDLANGUAGE Neeraj Kumar Singhania University,
International Journal of Computer ScienceandCommunication Vol. 2, No. 1, January-June2011, pp. 153-157 PROPERTECHNIQUEOFSOFTWARE INSPECTIONUSING GUARDED COMMANDLANGUAGE Neeraj Kumar Singhania University,
Modular Verification of Dynamically Adaptive Systems
 Modular Verification of Dynamically Adaptive Systems Ji Zhang, Heather J. Goldsby, and Betty H.C. Cheng Department of Computer Science and Engineering, Michigan State University East Lansing, Michigan,
Modular Verification of Dynamically Adaptive Systems Ji Zhang, Heather J. Goldsby, and Betty H.C. Cheng Department of Computer Science and Engineering, Michigan State University East Lansing, Michigan,
Semantics and Verification of Software
 Semantics and Verification of Software Lecture 21: Nondeterminism and Parallelism IV (Equivalence of CCS Processes & Wrap-Up) Thomas Noll Lehrstuhl für Informatik 2 (Software Modeling and Verification)
Semantics and Verification of Software Lecture 21: Nondeterminism and Parallelism IV (Equivalence of CCS Processes & Wrap-Up) Thomas Noll Lehrstuhl für Informatik 2 (Software Modeling and Verification)
Static Analysis. Find the Bug! 15-654: Analysis of Software Artifacts. Jonathan Aldrich. disable interrupts. ERROR: returning with interrupts disabled
 Static Analysis 15-654: Analysis of Software Artifacts Jonathan Aldrich 1 Find the Bug! Source: Engler et al., Checking System Rules Using System-Specific, Programmer-Written Compiler Extensions, OSDI
Static Analysis 15-654: Analysis of Software Artifacts Jonathan Aldrich 1 Find the Bug! Source: Engler et al., Checking System Rules Using System-Specific, Programmer-Written Compiler Extensions, OSDI
This makes sense. t 2 1 + 1/t 2 dt = 1. t t 2 + 1dt = 2 du = 1 3 u3/2 u=5
 1. (Line integrals Using parametrization. Two types and the flux integral) Formulas: ds = x (t) dt, d x = x (t)dt and d x = T ds since T = x (t)/ x (t). Another one is Nds = T ds ẑ = (dx, dy) ẑ = (dy,
1. (Line integrals Using parametrization. Two types and the flux integral) Formulas: ds = x (t) dt, d x = x (t)dt and d x = T ds since T = x (t)/ x (t). Another one is Nds = T ds ẑ = (dx, dy) ẑ = (dy,
Elementary Number Theory and Methods of Proof. CSE 215, Foundations of Computer Science Stony Brook University http://www.cs.stonybrook.
 Elementary Number Theory and Methods of Proof CSE 215, Foundations of Computer Science Stony Brook University http://www.cs.stonybrook.edu/~cse215 1 Number theory Properties: 2 Properties of integers (whole
Elementary Number Theory and Methods of Proof CSE 215, Foundations of Computer Science Stony Brook University http://www.cs.stonybrook.edu/~cse215 1 Number theory Properties: 2 Properties of integers (whole
Mathematics for Computer Science/Software Engineering. Notes for the course MSM1F3 Dr. R. A. Wilson
 Mathematics for Computer Science/Software Engineering Notes for the course MSM1F3 Dr. R. A. Wilson October 1996 Chapter 1 Logic Lecture no. 1. We introduce the concept of a proposition, which is a statement
Mathematics for Computer Science/Software Engineering Notes for the course MSM1F3 Dr. R. A. Wilson October 1996 Chapter 1 Logic Lecture no. 1. We introduce the concept of a proposition, which is a statement
3. Reaction Diffusion Equations Consider the following ODE model for population growth
 3. Reaction Diffusion Equations Consider the following ODE model for population growth u t a u t u t, u 0 u 0 where u t denotes the population size at time t, and a u plays the role of the population dependent
3. Reaction Diffusion Equations Consider the following ODE model for population growth u t a u t u t, u 0 u 0 where u t denotes the population size at time t, and a u plays the role of the population dependent
Model Checking II Temporal Logic Model Checking
 1/32 Model Checking II Temporal Logic Model Checking Edmund M Clarke, Jr School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 2/32 Temporal Logic Model Checking Specification Language:
1/32 Model Checking II Temporal Logic Model Checking Edmund M Clarke, Jr School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 2/32 Temporal Logic Model Checking Specification Language:
Adding vectors We can do arithmetic with vectors. We ll start with vector addition and related operations. Suppose you have two vectors
 1 Chapter 13. VECTORS IN THREE DIMENSIONAL SPACE Let s begin with some names and notation for things: R is the set (collection) of real numbers. We write x R to mean that x is a real number. A real number
1 Chapter 13. VECTORS IN THREE DIMENSIONAL SPACE Let s begin with some names and notation for things: R is the set (collection) of real numbers. We write x R to mean that x is a real number. A real number
Reducing Clocks in Timed Automata while Preserving Bisimulation
 Reducing Clocks in Timed Automata while Preserving Bisimulation Shibashis Guha Chinmay Narayan S. Arun-Kumar Indian Institute of Technology Delhi {shibashis, chinmay, sak}@cse.iitd.ac.in arxiv:1404.6613v2
Reducing Clocks in Timed Automata while Preserving Bisimulation Shibashis Guha Chinmay Narayan S. Arun-Kumar Indian Institute of Technology Delhi {shibashis, chinmay, sak}@cse.iitd.ac.in arxiv:1404.6613v2
InvGen: An Efficient Invariant Generator
 InvGen: An Efficient Invariant Generator Ashutosh Gupta and Andrey Rybalchenko Max Planck Institute for Software Systems (MPI-SWS) Abstract. In this paper we present InvGen, an automatic linear arithmetic
InvGen: An Efficient Invariant Generator Ashutosh Gupta and Andrey Rybalchenko Max Planck Institute for Software Systems (MPI-SWS) Abstract. In this paper we present InvGen, an automatic linear arithmetic
Investigating a File Transfer Protocol Using CSP and B
 Noname manuscript No. (will be inserted by the editor) Investigating a File Transfer Protocol Using CSP and B Neil Evans, Helen Treharne Department of Computer Science, Royal Holloway, University of London
Noname manuscript No. (will be inserted by the editor) Investigating a File Transfer Protocol Using CSP and B Neil Evans, Helen Treharne Department of Computer Science, Royal Holloway, University of London
Scalable Automated Symbolic Analysis of Administrative Role-Based Access Control Policies by SMT solving
 Scalable Automated Symbolic Analysis of Administrative Role-Based Access Control Policies by SMT solving Alessandro Armando 1,2 and Silvio Ranise 2, 1 DIST, Università degli Studi di Genova, Italia 2 Security
Scalable Automated Symbolic Analysis of Administrative Role-Based Access Control Policies by SMT solving Alessandro Armando 1,2 and Silvio Ranise 2, 1 DIST, Università degli Studi di Genova, Italia 2 Security
Chapter 2: Linear Equations and Inequalities Lecture notes Math 1010
 Section 2.1: Linear Equations Definition of equation An equation is a statement that equates two algebraic expressions. Solving an equation involving a variable means finding all values of the variable
Section 2.1: Linear Equations Definition of equation An equation is a statement that equates two algebraic expressions. Solving an equation involving a variable means finding all values of the variable
Limits and Continuity
 Math 20C Multivariable Calculus Lecture Limits and Continuity Slide Review of Limit. Side limits and squeeze theorem. Continuous functions of 2,3 variables. Review: Limits Slide 2 Definition Given a function
Math 20C Multivariable Calculus Lecture Limits and Continuity Slide Review of Limit. Side limits and squeeze theorem. Continuous functions of 2,3 variables. Review: Limits Slide 2 Definition Given a function
! Solve problem to optimality. ! Solve problem in poly-time. ! Solve arbitrary instances of the problem. !-approximation algorithm.
 Approximation Algorithms Chapter Approximation Algorithms Q Suppose I need to solve an NP-hard problem What should I do? A Theory says you're unlikely to find a poly-time algorithm Must sacrifice one of
Approximation Algorithms Chapter Approximation Algorithms Q Suppose I need to solve an NP-hard problem What should I do? A Theory says you're unlikely to find a poly-time algorithm Must sacrifice one of
Sect 6.1 - Greatest Common Factor and Factoring by Grouping
 Sect 6.1 - Greatest Common Factor and Factoring by Grouping Our goal in this chapter is to solve non-linear equations by breaking them down into a series of linear equations that we can solve. To do this,
Sect 6.1 - Greatest Common Factor and Factoring by Grouping Our goal in this chapter is to solve non-linear equations by breaking them down into a series of linear equations that we can solve. To do this,
NSM100 Introduction to Algebra Chapter 5 Notes Factoring
 Section 5.1 Greatest Common Factor (GCF) and Factoring by Grouping Greatest Common Factor for a polynomial is the largest monomial that divides (is a factor of) each term of the polynomial. GCF is the
Section 5.1 Greatest Common Factor (GCF) and Factoring by Grouping Greatest Common Factor for a polynomial is the largest monomial that divides (is a factor of) each term of the polynomial. GCF is the
Discrete Mathematics and Probability Theory Fall 2009 Satish Rao, David Tse Note 2
 CS 70 Discrete Mathematics and Probability Theory Fall 2009 Satish Rao, David Tse Note 2 Proofs Intuitively, the concept of proof should already be familiar We all like to assert things, and few of us
CS 70 Discrete Mathematics and Probability Theory Fall 2009 Satish Rao, David Tse Note 2 Proofs Intuitively, the concept of proof should already be familiar We all like to assert things, and few of us
A Logic Approach for LTL System Modification
 A Logic Approach for LTL System Modification Yulin Ding and Yan Zhang School of Computing & Information Technology University of Western Sydney Kingswood, N.S.W. 1797, Australia email: {yding,yan}@cit.uws.edu.au
A Logic Approach for LTL System Modification Yulin Ding and Yan Zhang School of Computing & Information Technology University of Western Sydney Kingswood, N.S.W. 1797, Australia email: {yding,yan}@cit.uws.edu.au
Formal verification of contracts for synchronous software components using NuSMV
 Formal verification of contracts for synchronous software components using NuSMV Tobias Polzer Lehrstuhl für Informatik 8 Bachelorarbeit 13.05.2014 1 / 19 Problem description and goals Problem description
Formal verification of contracts for synchronous software components using NuSMV Tobias Polzer Lehrstuhl für Informatik 8 Bachelorarbeit 13.05.2014 1 / 19 Problem description and goals Problem description
FOUNDATIONS OF ALGEBRAIC GEOMETRY CLASS 22
 FOUNDATIONS OF ALGEBRAIC GEOMETRY CLASS 22 RAVI VAKIL CONTENTS 1. Discrete valuation rings: Dimension 1 Noetherian regular local rings 1 Last day, we discussed the Zariski tangent space, and saw that it
FOUNDATIONS OF ALGEBRAIC GEOMETRY CLASS 22 RAVI VAKIL CONTENTS 1. Discrete valuation rings: Dimension 1 Noetherian regular local rings 1 Last day, we discussed the Zariski tangent space, and saw that it
Verification of Imperative Programs in Theorema
 Verification of Imperative Programs in Theorema Laura Ildikó Kovács, Nikolaj Popov, Tudor Jebelean 1 Research Institute for Symbolic Computation, Johannes Kepler University, A-4040 Linz, Austria Institute
Verification of Imperative Programs in Theorema Laura Ildikó Kovács, Nikolaj Popov, Tudor Jebelean 1 Research Institute for Symbolic Computation, Johannes Kepler University, A-4040 Linz, Austria Institute
Absolute Value Equations and Inequalities
 . Absolute Value Equations and Inequalities. OBJECTIVES 1. Solve an absolute value equation in one variable. Solve an absolute value inequality in one variable NOTE Technically we mean the distance between
. Absolute Value Equations and Inequalities. OBJECTIVES 1. Solve an absolute value equation in one variable. Solve an absolute value inequality in one variable NOTE Technically we mean the distance between
Regression Verification: Status Report
 Regression Verification: Status Report Presentation by Dennis Felsing within the Projektgruppe Formale Methoden der Softwareentwicklung 2013-12-11 1/22 Introduction How to prevent regressions in software
Regression Verification: Status Report Presentation by Dennis Felsing within the Projektgruppe Formale Methoden der Softwareentwicklung 2013-12-11 1/22 Introduction How to prevent regressions in software
Specification and Analysis of Contracts Lecture 1 Introduction
 Specification and Analysis of Contracts Lecture 1 Introduction Gerardo Schneider gerardo@ifi.uio.no http://folk.uio.no/gerardo/ Department of Informatics, University of Oslo SEFM School, Oct. 27 - Nov.
Specification and Analysis of Contracts Lecture 1 Introduction Gerardo Schneider gerardo@ifi.uio.no http://folk.uio.no/gerardo/ Department of Informatics, University of Oslo SEFM School, Oct. 27 - Nov.
Introduction to Software Verification
 Introduction to Software Verification Orna Grumberg Lectures Material winter 2013-14 Lecture 4 5.11.13 Model Checking Automated formal verification: A different approach to formal verification Model Checking
Introduction to Software Verification Orna Grumberg Lectures Material winter 2013-14 Lecture 4 5.11.13 Model Checking Automated formal verification: A different approach to formal verification Model Checking
A Classification of Model Checking-Based Verification Approaches for Software Models
 Volt Second Workshop on Verification Of Model Transformations, 2013, A Classification of Model Checking-Based Verification Approaches for Software Models Sebastian Gabmeyer a Petra Brosch a Martina Seidl
Volt Second Workshop on Verification Of Model Transformations, 2013, A Classification of Model Checking-Based Verification Approaches for Software Models Sebastian Gabmeyer a Petra Brosch a Martina Seidl
On strong fairness in UNITY
 On strong fairness in UNITY H.P.Gumm, D.Zhukov Fachbereich Mathematik und Informatik Philipps Universität Marburg {gumm,shukov}@mathematik.uni-marburg.de Abstract. In [6] Tsay and Bagrodia present a correct
On strong fairness in UNITY H.P.Gumm, D.Zhukov Fachbereich Mathematik und Informatik Philipps Universität Marburg {gumm,shukov}@mathematik.uni-marburg.de Abstract. In [6] Tsay and Bagrodia present a correct
Software Engineering. What is a system?
 What is a system? Software Engineering Software Processes A purposeful collection of inter-related components working together to achieve some common objective. A system may include software, mechanical,
What is a system? Software Engineering Software Processes A purposeful collection of inter-related components working together to achieve some common objective. A system may include software, mechanical,
Automata-based Verification - I
 CS3172: Advanced Algorithms Automata-based Verification - I Howard Barringer Room KB2.20: email: howard.barringer@manchester.ac.uk March 2006 Supporting and Background Material Copies of key slides (already
CS3172: Advanced Algorithms Automata-based Verification - I Howard Barringer Room KB2.20: email: howard.barringer@manchester.ac.uk March 2006 Supporting and Background Material Copies of key slides (already
Chapter 11. 11.1 Load Balancing. Approximation Algorithms. Load Balancing. Load Balancing on 2 Machines. Load Balancing: Greedy Scheduling
 Approximation Algorithms Chapter Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should I do? A. Theory says you're unlikely to find a poly-time algorithm. Must sacrifice one
Approximation Algorithms Chapter Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should I do? A. Theory says you're unlikely to find a poly-time algorithm. Must sacrifice one
Automata and Formal Languages
 Automata and Formal Languages Winter 2009-2010 Yacov Hel-Or 1 What this course is all about This course is about mathematical models of computation We ll study different machine models (finite automata,
Automata and Formal Languages Winter 2009-2010 Yacov Hel-Or 1 What this course is all about This course is about mathematical models of computation We ll study different machine models (finite automata,
AUTOMATED TEST GENERATION FOR SOFTWARE COMPONENTS
 TKK Reports in Information and Computer Science Espoo 2009 TKK-ICS-R26 AUTOMATED TEST GENERATION FOR SOFTWARE COMPONENTS Kari Kähkönen ABTEKNILLINEN KORKEAKOULU TEKNISKA HÖGSKOLAN HELSINKI UNIVERSITY OF
TKK Reports in Information and Computer Science Espoo 2009 TKK-ICS-R26 AUTOMATED TEST GENERATION FOR SOFTWARE COMPONENTS Kari Kähkönen ABTEKNILLINEN KORKEAKOULU TEKNISKA HÖGSKOLAN HELSINKI UNIVERSITY OF
Factoring Polynomials
 UNIT 11 Factoring Polynomials You can use polynomials to describe framing for art. 396 Unit 11 factoring polynomials A polynomial is an expression that has variables that represent numbers. A number can
UNIT 11 Factoring Polynomials You can use polynomials to describe framing for art. 396 Unit 11 factoring polynomials A polynomial is an expression that has variables that represent numbers. A number can
Test case design techniques I: Whitebox testing CISS
 Test case design techniques I: Whitebox testing Overview What is a test case Sources for test case derivation Test case execution White box testing Flowgraphs Test criteria/coverage Statement / branch
Test case design techniques I: Whitebox testing Overview What is a test case Sources for test case derivation Test case execution White box testing Flowgraphs Test criteria/coverage Statement / branch
On the Modeling and Verification of Security-Aware and Process-Aware Information Systems
 On the Modeling and Verification of Security-Aware and Process-Aware Information Systems 29 August 2011 What are workflows to us? Plans or schedules that map users or resources to tasks Such mappings may
On the Modeling and Verification of Security-Aware and Process-Aware Information Systems 29 August 2011 What are workflows to us? Plans or schedules that map users or resources to tasks Such mappings may
System modeling. Budapest University of Technology and Economics Department of Measurement and Information Systems
 System modeling Business process modeling how to do it right Partially based on Process Anti-Patterns: How to Avoid the Common Traps of Business Process Modeling, J Koehler, J Vanhatalo, IBM Zürich, 2007.
System modeling Business process modeling how to do it right Partially based on Process Anti-Patterns: How to Avoid the Common Traps of Business Process Modeling, J Koehler, J Vanhatalo, IBM Zürich, 2007.
1 if 1 x 0 1 if 0 x 1
 Chapter 3 Continuity In this chapter we begin by defining the fundamental notion of continuity for real valued functions of a single real variable. When trying to decide whether a given function is or
Chapter 3 Continuity In this chapter we begin by defining the fundamental notion of continuity for real valued functions of a single real variable. When trying to decide whether a given function is or
Digital Design Verification
 Digital Design Verification Course Instructor: Debdeep Mukhopadhyay Dept of Computer Sc. and Engg. Indian Institute of Technology Madras, Even Semester Course No: CS 676 1 Verification??? What is meant
Digital Design Verification Course Instructor: Debdeep Mukhopadhyay Dept of Computer Sc. and Engg. Indian Institute of Technology Madras, Even Semester Course No: CS 676 1 Verification??? What is meant
Problem Solving Basics and Computer Programming
 Problem Solving Basics and Computer Programming A programming language independent companion to Roberge/Bauer/Smith, "Engaged Learning for Programming in C++: A Laboratory Course", Jones and Bartlett Publishers,
Problem Solving Basics and Computer Programming A programming language independent companion to Roberge/Bauer/Smith, "Engaged Learning for Programming in C++: A Laboratory Course", Jones and Bartlett Publishers,
Development of global specification for dynamically adaptive software
 Development of global specification for dynamically adaptive software Yongwang Zhao School of Computer Science & Engineering Beihang University zhaoyw@act.buaa.edu.cn 22/02/2013 1 2 About me Assistant
Development of global specification for dynamically adaptive software Yongwang Zhao School of Computer Science & Engineering Beihang University zhaoyw@act.buaa.edu.cn 22/02/2013 1 2 About me Assistant
6.4 Special Factoring Rules
 6.4 Special Factoring Rules OBJECTIVES 1 Factor a difference of squares. 2 Factor a perfect square trinomial. 3 Factor a difference of cubes. 4 Factor a sum of cubes. By reversing the rules for multiplication
6.4 Special Factoring Rules OBJECTIVES 1 Factor a difference of squares. 2 Factor a perfect square trinomial. 3 Factor a difference of cubes. 4 Factor a sum of cubes. By reversing the rules for multiplication
Finding Liveness Errors with ACO
 Hong Kong, June 1-6, 2008 1 / 24 Finding Liveness Errors with ACO Francisco Chicano and Enrique Alba Motivation Motivation Nowadays software is very complex An error in a software system can imply the
Hong Kong, June 1-6, 2008 1 / 24 Finding Liveness Errors with ACO Francisco Chicano and Enrique Alba Motivation Motivation Nowadays software is very complex An error in a software system can imply the
FACTORING ax 2 bx c. Factoring Trinomials with Leading Coefficient 1
 5.7 Factoring ax 2 bx c (5-49) 305 5.7 FACTORING ax 2 bx c In this section In Section 5.5 you learned to factor certain special polynomials. In this section you will learn to factor general quadratic polynomials.
5.7 Factoring ax 2 bx c (5-49) 305 5.7 FACTORING ax 2 bx c In this section In Section 5.5 you learned to factor certain special polynomials. In this section you will learn to factor general quadratic polynomials.
Software Active Online Monitoring Under. Anticipatory Semantics
 Software Active Online Monitoring Under Anticipatory Semantics Changzhi Zhao, Wei Dong, Ji Wang, Zhichang Qi National Laboratory for Parallel and Distributed Processing P.R.China 7/21/2009 Overview Software
Software Active Online Monitoring Under Anticipatory Semantics Changzhi Zhao, Wei Dong, Ji Wang, Zhichang Qi National Laboratory for Parallel and Distributed Processing P.R.China 7/21/2009 Overview Software
Reminder: Complexity (1) Parallel Complexity Theory. Reminder: Complexity (2) Complexity-new
 Reminder: Complexity (1) Parallel Complexity Theory Lecture 6 Number of steps or memory units required to compute some result In terms of input size Using a single processor O(1) says that regardless of
Reminder: Complexity (1) Parallel Complexity Theory Lecture 6 Number of steps or memory units required to compute some result In terms of input size Using a single processor O(1) says that regardless of
Reminder: Complexity (1) Parallel Complexity Theory. Reminder: Complexity (2) Complexity-new GAP (2) Graph Accessibility Problem (GAP) (1)
 Reminder: Complexity (1) Parallel Complexity Theory Lecture 6 Number of steps or memory units required to compute some result In terms of input size Using a single processor O(1) says that regardless of
Reminder: Complexity (1) Parallel Complexity Theory Lecture 6 Number of steps or memory units required to compute some result In terms of input size Using a single processor O(1) says that regardless of
Model-Checking Verification for Reliable Web Service
 Model-Checking Verification for Reliable Web Service Shin NAKAJIMA Hosei University and PRESTO, JST nkjm@i.hosei.ac.jp Abstract Model-checking is a promising technique for the verification and validation
Model-Checking Verification for Reliable Web Service Shin NAKAJIMA Hosei University and PRESTO, JST nkjm@i.hosei.ac.jp Abstract Model-checking is a promising technique for the verification and validation
Good FORTRAN Programs
 Good FORTRAN Programs Nick West Postgraduate Computing Lectures Good Fortran 1 What is a Good FORTRAN Program? It Works May be ~ impossible to prove e.g. Operating system. Robust Can handle bad data e.g.
Good FORTRAN Programs Nick West Postgraduate Computing Lectures Good Fortran 1 What is a Good FORTRAN Program? It Works May be ~ impossible to prove e.g. Operating system. Robust Can handle bad data e.g.
Quick Start Guide. June 3, 2012
 The ERIGONE Model Checker Quick Start Guide Mordechai (Moti) Ben-Ari Department of Science Teaching Weizmann Institute of Science Rehovot 76100 Israel http://stwww.weizmann.ac.il/g-cs/benari/ June 3, 2012
The ERIGONE Model Checker Quick Start Guide Mordechai (Moti) Ben-Ari Department of Science Teaching Weizmann Institute of Science Rehovot 76100 Israel http://stwww.weizmann.ac.il/g-cs/benari/ June 3, 2012
Boolean Algebra Part 1
 Boolean Algebra Part 1 Page 1 Boolean Algebra Objectives Understand Basic Boolean Algebra Relate Boolean Algebra to Logic Networks Prove Laws using Truth Tables Understand and Use First Basic Theorems
Boolean Algebra Part 1 Page 1 Boolean Algebra Objectives Understand Basic Boolean Algebra Relate Boolean Algebra to Logic Networks Prove Laws using Truth Tables Understand and Use First Basic Theorems
Validated Templates for Specification of Complex LTL Formulas
 Validated Templates for Specification of Complex LTL Formulas Salamah Salamah Department of Electrical, computer, Software, and Systems Engineering Embry Riddle Aeronautical University 600 S. Clyde Morris
Validated Templates for Specification of Complex LTL Formulas Salamah Salamah Department of Electrical, computer, Software, and Systems Engineering Embry Riddle Aeronautical University 600 S. Clyde Morris
Abstract.Weproposetimed(nite)automatatomodelthebehaviorofrealtimesystemsovertime.Ourdenitionprovidesasimple,andyetpowerful,wayto
 ATheoryofTimedAutomata1 Abstract.Weproposetimed(nite)automatatomodelthebehaviorofrealtimesystemsovertime.Ourdenitionprovidesasimple,andyetpowerful,wayto ComputercienceDepartment,tanfordUniversity RajeevAlur2
ATheoryofTimedAutomata1 Abstract.Weproposetimed(nite)automatatomodelthebehaviorofrealtimesystemsovertime.Ourdenitionprovidesasimple,andyetpowerful,wayto ComputercienceDepartment,tanfordUniversity RajeevAlur2
Test Case Design Techniques
 Summary of Test Case Design Techniques Brian Nielsen, Arne Skou {bnielsen ask}@cs.auc.dk Development of Test Cases Complete testing is impossible Testing cannot guarantee the absence of faults How to select
Summary of Test Case Design Techniques Brian Nielsen, Arne Skou {bnielsen ask}@cs.auc.dk Development of Test Cases Complete testing is impossible Testing cannot guarantee the absence of faults How to select
MODEL CHECKING OF SERVICES WORKFLOW RECONFIGURATION: A PERSPECTIVE ON DEPENDABILITY
 MODEL CHECKING OF SERVICES WORKFLOW RECONFIGURATION: A PERSPECTIVE ON DEPENDABILITY 1 Juan Carlos Polanco Aguilar 1 Koji Hasebe 1 Manuel Mazzara 2 Kazuhiko Kato 1 1 University of Tsukuba Department of
MODEL CHECKING OF SERVICES WORKFLOW RECONFIGURATION: A PERSPECTIVE ON DEPENDABILITY 1 Juan Carlos Polanco Aguilar 1 Koji Hasebe 1 Manuel Mazzara 2 Kazuhiko Kato 1 1 University of Tsukuba Department of
Lecture Notes on Linear Search
 Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 29, 2013 1 Introduction One of the fundamental and recurring problems in computer science is
Lecture Notes on Linear Search 15-122: Principles of Imperative Computation Frank Pfenning Lecture 5 January 29, 2013 1 Introduction One of the fundamental and recurring problems in computer science is
T-79.186 Reactive Systems: Introduction and Finite State Automata
 T-79.186 Reactive Systems: Introduction and Finite State Automata Timo Latvala 14.1.2004 Reactive Systems: Introduction and Finite State Automata 1-1 Reactive Systems Reactive systems are a class of software
T-79.186 Reactive Systems: Introduction and Finite State Automata Timo Latvala 14.1.2004 Reactive Systems: Introduction and Finite State Automata 1-1 Reactive Systems Reactive systems are a class of software
Institut für Parallele und Verteilte Systeme. Abteilung Anwendersoftware. Universität Stuttgart Universitätsstraße 38 D-70569 Stuttgart
 Institut für Parallele und Verteilte Systeme Abteilung Anwendersoftware Universität Stuttgart Universitätsstraße 38 D-70569 Stuttgart Diplomarbeit Nr. 3243 Development and Evaluation of a Framework for
Institut für Parallele und Verteilte Systeme Abteilung Anwendersoftware Universität Stuttgart Universitätsstraße 38 D-70569 Stuttgart Diplomarbeit Nr. 3243 Development and Evaluation of a Framework for
Satisfiability Checking
 Satisfiability Checking SAT-Solving Prof. Dr. Erika Ábrahám Theory of Hybrid Systems Informatik 2 WS 10/11 Prof. Dr. Erika Ábrahám - Satisfiability Checking 1 / 40 A basic SAT algorithm Assume the CNF
Satisfiability Checking SAT-Solving Prof. Dr. Erika Ábrahám Theory of Hybrid Systems Informatik 2 WS 10/11 Prof. Dr. Erika Ábrahám - Satisfiability Checking 1 / 40 A basic SAT algorithm Assume the CNF
A Systematic Approach. to Parallel Program Verication. Tadao TAKAOKA. Department of Computer Science. Ibaraki University. Hitachi, Ibaraki 316, JAPAN
 A Systematic Approach to Parallel Program Verication Tadao TAKAOKA Department of Computer Science Ibaraki University Hitachi, Ibaraki 316, JAPAN E-mail: takaoka@cis.ibaraki.ac.jp Phone: +81 94 38 5130
A Systematic Approach to Parallel Program Verication Tadao TAKAOKA Department of Computer Science Ibaraki University Hitachi, Ibaraki 316, JAPAN E-mail: takaoka@cis.ibaraki.ac.jp Phone: +81 94 38 5130
Factoring Quadratic Expressions
 Factoring the trinomial ax 2 + bx + c when a = 1 A trinomial in the form x 2 + bx + c can be factored to equal (x + m)(x + n) when the product of m x n equals c and the sum of m + n equals b. (Note: the
Factoring the trinomial ax 2 + bx + c when a = 1 A trinomial in the form x 2 + bx + c can be factored to equal (x + m)(x + n) when the product of m x n equals c and the sum of m + n equals b. (Note: the
A Systematic Approach to Factoring
 A Systematic Approach to Factoring Step 1 Count the number of terms. (Remember****Knowing the number of terms will allow you to eliminate unnecessary tools.) Step 2 Is there a greatest common factor? Tool
A Systematic Approach to Factoring Step 1 Count the number of terms. (Remember****Knowing the number of terms will allow you to eliminate unnecessary tools.) Step 2 Is there a greatest common factor? Tool
The Model Checker SPIN
 The Model Checker SPIN Author: Gerard J. Holzmann Presented By: Maulik Patel Outline Introduction Structure Foundation Algorithms Memory management Example/Demo SPIN-Introduction Introduction SPIN (Simple(
The Model Checker SPIN Author: Gerard J. Holzmann Presented By: Maulik Patel Outline Introduction Structure Foundation Algorithms Memory management Example/Demo SPIN-Introduction Introduction SPIN (Simple(
