Vulnerability Assessment Lab
|
|
|
- Jeffrey Randall
- 10 years ago
- Views:
Transcription
1 Vulnerability Assessment Lab Fully assessing a company's security posture is a critical job to maintain intellectual property integrity, and protect customer information. As a security auditor your job is to identify known vulnerabilities and risks that could harm your client's organization. Audits are usually performed in three parts, namely procedure & policy audit, disaster recovery audit, and technical audit. Objective You are tasked with a technical audit of a small group of machines listed below. Part 1 Nessus / OpenVas Scan the Metasploitable VM for vulnerabilities using Nessus and OpenVas vulnerability scanners using the Backtrack5R3 VM (do not run both scans simultaneously). Identify as many vulnerabilities as you can for an audit report. Find proof of concept exploit code for at least two of the vulnerabilities identified for each scanner (four total). Part 2 Nikto Scan the DVWA VM for vulnerabilities using the Nikto Web scanner Turn In Part 1 Nessus / OpenVas A "Technical Report" describing the system's current security posture, risks, and all audit reports. Include answers to the following: How many vulnerabilities did each scanner find? How many open ports /which ones? What services are highly vulnerable? What type of attack is the selected service vulnerable to? What versions of the service are affected by the vulnerability? What security advisories are available for further research on the security bug? Include proof of concept exploits for the four vulnerabilities selected in the objective section. This can be turned in with a link to a site that provides the exploit code. Part 2 Nikto Incorporate the Nikto audit report as part of the write up in part one. Keys to success Read entire lab document Use the Metasploitable, DVWA, and Backtrack5R3 VMs. Use these sites to find exploit code for the vulnerabilities found in the scans:
2 Starting the VMs 1) Start Backtrack5R3 VM (Auditor) IP = Login to BT user: root password: toor Start GUI interface: startx 2) Start Metasploitable VM IP = ) Start DVWA VM IP = ) Verify connectivity between the Backtrack VM and Metatsploitable and DVWA VMs. (use 'ping' command) Nessus Nessus is the industry s most widely-deployed vulnerability and configuration assessment product. Nessus features high-speed discovery, configuration auditing, asset profiling, sensitive data discovery, patch management integration, and vulnerability analysis. It can detect, scan, and profile numerous devices and resources to increase security and compliance across any network. Starting Nessus Open a new terminal, type: /etc/init.d/nessusd start or from the GUI: Application->Backtrack->Vulnerability Assesment->Vulnerability Scanners->Nessus->nessus start To verify nessus service is running you can quickly check what ports are listening on your machine. Nessus daemon operates on port Verify nessus started up correctly: Using Nessus netstat -ant grep LISTEN (should display port 8834 as LISTENING) Open a browser to Login to nessus user: password: lab secure? Click on Scans -> Add Name - metasploitable Type - Run Now Policy - Internal Network Scan Scan Targets
3 Once scan details have been filled in, click on 'Launch' to start scanning the remote system. Once scan finishes click on 'Reports' double-click the completed metasploitable scan or select the scan and click 'Browse' Read through the audit report looking for vulnerabilities and the information needed for the write up in the turn in section.
4 OpenVAS The Open Vulnerability Assessment System (OpenVAS) is a framework of several services and tools offering a comprehensive and powerful vulnerability scanning and vulnerability management solution. The actual security scanner is accompanied with a daily updated feed of Network Vulnerability Tests (NVTs), over 20,000 in total. All OpenVAS products are Free Software. Most components are licensed under the GNU General Public License (GNU GPL). Starting OpenVAS Open a new terminal, and type the startup commands: openvassd (Starts the scanner - will load the signatures available nvts) openvasmd -p a (Starts Openvas Manager - runs as daemon) openvasad -a p 9393 (Starts Openvas Administrator) gsad --http-only --listen= p 9392 (Starts greenbone Security Assistant) Verify openvas service started up correctly: netstat -ant grep LISTEN (ports 9390/9391/9392/9393 should be listening) Using OpenVas Open user: lab password: secure? Once logged in, you have to create a target to scan against, then create a scan task. Target Creation On the Left hand menu, Click on Targets Enter the name and IP address information. Click Create Target
5 Task Creation On the Left hand menu, Click on New Task Enter the Name Under Scan Config Select Full and fast Under Scan Targets Select the target created in previous step Click Create Task Task Initialization On the Left hand menu, Click on Tasks Select the task created in previous step Click on play arrow
6 Scan Report Once the scan has completed. Click on task 'details' or the date of the last completed scan. The scan results should look something like the following diagram. Read through the audit report looking for vulnerabilities and the information needed for the write up in the turn in section.
7 Nikto Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/cgis, checks for outdated versions of over 1000 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Installation Nikto is simple a compressed download which when extracted is executable as is. Nikto does not need root access to run. There are many parameters to nikto. To do a simple scan against a web server enter the following command. cd ~/pentest/web/nikto./nikto -host
Vulnerability analysis
 Vulnerability analysis License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents License Contents
Vulnerability analysis License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents License Contents
Vulnerability Assessment. A. Open Vulnerability Assessment (OpenVAS)
 Vulnerability Assessment After target discovery and enumeration, the next step is identifying critical security vulnerabilities in the target systems. Vulnerability assessment depends on the type and OS
Vulnerability Assessment After target discovery and enumeration, the next step is identifying critical security vulnerabilities in the target systems. Vulnerability assessment depends on the type and OS
IDS and Penetration Testing Lab II
 IDS and Penetration Testing Lab II Software Requirements: 1. A secure shell (SSH) client. For windows you can download a free version from here: http://the.earth.li/~sgtatham/putty/latest/x86/putty-0.62-
IDS and Penetration Testing Lab II Software Requirements: 1. A secure shell (SSH) client. For windows you can download a free version from here: http://the.earth.li/~sgtatham/putty/latest/x86/putty-0.62-
IDS and Penetration Testing Lab ISA656 (Attacker)
 IDS and Penetration Testing Lab ISA656 (Attacker) Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible
IDS and Penetration Testing Lab ISA656 (Attacker) Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible
Using Remote Web Workplace Version 1.01
 Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Why do I need a pen test lab? Requirements. Virtual Machine Downloads
 Why do I need a pen test lab? Hacking and or scanning machines without consent is against the law in most countries To become an effective penetration tester or ethical hacker you need to practice to enhance
Why do I need a pen test lab? Hacking and or scanning machines without consent is against the law in most countries To become an effective penetration tester or ethical hacker you need to practice to enhance
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - [email protected] Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - [email protected] Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
1 Scope of Assessment
 CIT 380 Project Network Security Assessment Due: April 30, 2014 This project is a security assessment of a small group of systems. In this assessment, students will apply security tools and resources learned
CIT 380 Project Network Security Assessment Due: April 30, 2014 This project is a security assessment of a small group of systems. In this assessment, students will apply security tools and resources learned
ECE 4893: Internetwork Security Lab 12: Web Security
 Group Number: Member Names: ECE 4893: Internetwork Security Lab 12: Web Security Date: April 6, 2004 Date Due: April 13, 2004 Last Revised: April 2, 2004 Written by: Tom Bean and Valerio Oricchio Goal:
Group Number: Member Names: ECE 4893: Internetwork Security Lab 12: Web Security Date: April 6, 2004 Date Due: April 13, 2004 Last Revised: April 2, 2004 Written by: Tom Bean and Valerio Oricchio Goal:
Installing and Configuring Nessus by Nitesh Dhanjani
 Unless you've been living under a rock for the past few years, it is quite evident that software vulnerabilities are being found and announced quicker than ever before. Every time a security advisory goes
Unless you've been living under a rock for the past few years, it is quite evident that software vulnerabilities are being found and announced quicker than ever before. Every time a security advisory goes
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (Internal Attacker - Beginner version) By: magikh0e - [email protected] Last Edit: July 07 2012 This guide assumes a few things... 1. You have installed Backtrack before
Penetration Testing LAB Setup Guide (Internal Attacker - Beginner version) By: magikh0e - [email protected] Last Edit: July 07 2012 This guide assumes a few things... 1. You have installed Backtrack before
Lab 9: Pen Testing (NESSUS)
 Lab 9: Pen Testing (NESSUS) Aim: To provide a foundation in using NESSUS for vulnerability scanning. Time to complete: Up to 90 minutes. Activities: Complete Lab 9: Introduction to NESSUS. Complete Test
Lab 9: Pen Testing (NESSUS) Aim: To provide a foundation in using NESSUS for vulnerability scanning. Time to complete: Up to 90 minutes. Activities: Complete Lab 9: Introduction to NESSUS. Complete Test
SysAid Remote Discovery Tool
 SysAid Remote Discovery Tool SysAid Release 7 Document Updated: 27-Apr-10 SysAid Remote Discovery Tool The SysAid server comes with a built-in discovery service that performs various network discovery
SysAid Remote Discovery Tool SysAid Release 7 Document Updated: 27-Apr-10 SysAid Remote Discovery Tool The SysAid server comes with a built-in discovery service that performs various network discovery
IDS and Penetration Testing Lab ISA 674
 IDS and Penetration Testing Lab ISA 674 Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible Use
IDS and Penetration Testing Lab ISA 674 Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible Use
EXTRA. Vulnerability scanners are indispensable both VULNERABILITY SCANNER
 Vulnerability scanners are indispensable both for vulnerability assessments and penetration tests. One of the first things a tester does when faced with a network is fire up a network scanner or even several
Vulnerability scanners are indispensable both for vulnerability assessments and penetration tests. One of the first things a tester does when faced with a network is fire up a network scanner or even several
Introduction to Operating Systems
 Introduction to Operating Systems It is important that you familiarize yourself with Windows and Linux in preparation for this course. The exercises in this book assume a basic knowledge of both of these
Introduction to Operating Systems It is important that you familiarize yourself with Windows and Linux in preparation for this course. The exercises in this book assume a basic knowledge of both of these
60467 Project 1. Net Vulnerabilities scans and attacks. Chun Li
 60467 Project 1 Net Vulnerabilities scans and attacks Chun Li Hardware used: Desktop PC: Windows Vista service pack Service Pack 2 v113 Intel Core 2 Duo 3GHz CPU, 4GB Ram, D-Link DWA-552 XtremeN Desktop
60467 Project 1 Net Vulnerabilities scans and attacks Chun Li Hardware used: Desktop PC: Windows Vista service pack Service Pack 2 v113 Intel Core 2 Duo 3GHz CPU, 4GB Ram, D-Link DWA-552 XtremeN Desktop
Lab Objectives & Turn In
 Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection
 IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
Lab 8: Configuring Backups
 CompTIA Security+ Lab Series Lab 8: Configuring Backups CompTIA Security+ Domain 2 - Compliance and Operational Security Objective 2.7: Execute disaster recovery plans and procedures Document Version:
CompTIA Security+ Lab Series Lab 8: Configuring Backups CompTIA Security+ Domain 2 - Compliance and Operational Security Objective 2.7: Execute disaster recovery plans and procedures Document Version:
Install and Configure RelayFax
 RelayFax Network Fax Manager How To Quick Start Guide Install and Configure RelayFax Welcome to RelayFax Network Fax Manager. This guide is designed to help you quickly install and start using your RelayFax.
RelayFax Network Fax Manager How To Quick Start Guide Install and Configure RelayFax Welcome to RelayFax Network Fax Manager. This guide is designed to help you quickly install and start using your RelayFax.
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link:
 TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Lab 2: Secure Network Administration Principles - Log Analysis
 CompTIA Security+ Lab Series Lab 2: Secure Network Administration Principles - Log Analysis CompTIA Security+ Domain 1 - Network Security Objective 1.2: Apply and implement secure network administration
CompTIA Security+ Lab Series Lab 2: Secure Network Administration Principles - Log Analysis CompTIA Security+ Domain 1 - Network Security Objective 1.2: Apply and implement secure network administration
Intrusion Detection and Prevention: Network and IDS Configuration and Monitoring using Snort
 License Intrusion Detection and Prevention: Network and IDS Configuration and Monitoring using Snort This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons
License Intrusion Detection and Prevention: Network and IDS Configuration and Monitoring using Snort This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons
How to use FTP Commander
 FTP (File Transfer Protocol) software can be used to upload files and complete folders to your web server. On the web, there are a number of free FTP programs that can be downloaded and installed onto
FTP (File Transfer Protocol) software can be used to upload files and complete folders to your web server. On the web, there are a number of free FTP programs that can be downloaded and installed onto
Running a Default Vulnerability Scan
 Running a Default Vulnerability Scan A Step-by-Step Guide www.saintcorporation.com Examine. Expose. Exploit. Welcome to SAINT! Congratulations on a smart choice by selecting SAINT s integrated vulnerability
Running a Default Vulnerability Scan A Step-by-Step Guide www.saintcorporation.com Examine. Expose. Exploit. Welcome to SAINT! Congratulations on a smart choice by selecting SAINT s integrated vulnerability
Smartphone Pentest Framework v0.1. User Guide
 Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Firewalls and Software Updates
 Firewalls and Software Updates License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents General
Firewalls and Software Updates License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents General
Linux Boot Camp. Our Lady of the Lake University Computer Information Systems & Security Department Kevin Barton Artair Burnett
 Linux Boot Camp Our Lady of the Lake University Computer Information Systems & Security Department Kevin Barton Artair Burnett Schedule for the Week Schedule for the Week Mon Welcome from Enrollment Management
Linux Boot Camp Our Lady of the Lake University Computer Information Systems & Security Department Kevin Barton Artair Burnett Schedule for the Week Schedule for the Week Mon Welcome from Enrollment Management
Configuring.NET based Applications in Internet Information Server to use Virtual Clocks from Time Machine
 Configuring.NET based Applications in Internet Information Server to use Virtual Clocks from Time Machine System Details: The development & deployment for this documentation was performed on the following:
Configuring.NET based Applications in Internet Information Server to use Virtual Clocks from Time Machine System Details: The development & deployment for this documentation was performed on the following:
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Secure Web Development Teaching Modules 1. Security Testing. 1.1 Security Practices for Software Verification
 Secure Web Development Teaching Modules 1 Security Testing Contents 1 Concepts... 1 1.1 Security Practices for Software Verification... 1 1.2 Software Security Testing... 2 2 Labs Objectives... 2 3 Lab
Secure Web Development Teaching Modules 1 Security Testing Contents 1 Concepts... 1 1.1 Security Practices for Software Verification... 1 1.2 Software Security Testing... 2 2 Labs Objectives... 2 3 Lab
Using Microsoft Expression Web to Upload Your Site
 Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
Lab 1: Network Devices and Technologies - Capturing Network Traffic
 CompTIA Security+ Lab Series Lab 1: Network Devices and Technologies - Capturing Network Traffic CompTIA Security+ Domain 1 - Network Security Objective 1.1: Explain the security function and purpose of
CompTIA Security+ Lab Series Lab 1: Network Devices and Technologies - Capturing Network Traffic CompTIA Security+ Domain 1 - Network Security Objective 1.1: Explain the security function and purpose of
Running a Default Vulnerability Scan SAINTcorporation.com
 SAINT Running a Default Vulnerability Scan A Step-by-Step Guide www.saintcorporation.com Examine. Expose. Exploit. Install SAINT Welcome to SAINT! Congratulations on a smart choice by selecting SAINT s
SAINT Running a Default Vulnerability Scan A Step-by-Step Guide www.saintcorporation.com Examine. Expose. Exploit. Install SAINT Welcome to SAINT! Congratulations on a smart choice by selecting SAINT s
Managing Qualys Scanners
 Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Browser Client 2.0 Admin Guide
 Browser Client is a web-based application that allows users to point their browser at a URL and view live video from a set of Intellex units. Browser Client 2.0 is compatible with Intellex 3.2 software.
Browser Client is a web-based application that allows users to point their browser at a URL and view live video from a set of Intellex units. Browser Client 2.0 is compatible with Intellex 3.2 software.
CSSIA CompTIA Security+ Domain. Network Security. Network Security. Network Security. Network Security. Network Security
 Security+ Supported Labs - V1 Lab 1 Network Devices and Technologies - Capturing Network Using tcpdump to Capture Network with Wireshark with Network Miner 2 Secure Network Administration Principles -
Security+ Supported Labs - V1 Lab 1 Network Devices and Technologies - Capturing Network Using tcpdump to Capture Network with Wireshark with Network Miner 2 Secure Network Administration Principles -
How to Configure Active Directory based User Authentication
 How to Configure Active Directory based User Authentication You Must Have: Microsoft server with Active Directory configured. Windows 2000 Server is configured as Active Directory server in this example.
How to Configure Active Directory based User Authentication You Must Have: Microsoft server with Active Directory configured. Windows 2000 Server is configured as Active Directory server in this example.
CIT 480: Securing Computer Systems. Vulnerability Scanning and Exploitation Frameworks
 CIT 480: Securing Computer Systems Vulnerability Scanning and Exploitation Frameworks Vulnerability Scanners Vulnerability scanners are automated tools that scan hosts and networks for potential vulnerabilities,
CIT 480: Securing Computer Systems Vulnerability Scanning and Exploitation Frameworks Vulnerability Scanners Vulnerability scanners are automated tools that scan hosts and networks for potential vulnerabilities,
IEI emerge and Milestone Systems Network Video Recorder. Setup and Integration Guide. Milestone Version 6.5 and emerge Version 3.
 IEI emerge and Milestone Systems Network Video Recorder Setup and Integration Guide Milestone Version 6.5 and emerge Version 3.2 and above CONTENTS Requirements for Milestone NVR/IEI emerge Integration...
IEI emerge and Milestone Systems Network Video Recorder Setup and Integration Guide Milestone Version 6.5 and emerge Version 3.2 and above CONTENTS Requirements for Milestone NVR/IEI emerge Integration...
Configuring a Windows 2003 Server for IAS
 Configuring a Windows 2003 Server for IAS When setting up a Windows 2003 server to function as an IAS server for our demo environment we will need the server to serve several functions. First of all we
Configuring a Windows 2003 Server for IAS When setting up a Windows 2003 server to function as an IAS server for our demo environment we will need the server to serve several functions. First of all we
Using Protection Engine for Cloud Services for URL Filtering, Malware Protection and Proxy Integration Hands-On Lab
 Using Protection Engine for Cloud Services for URL Filtering, Malware Protection and Proxy Integration Hands-On Lab Description In this hands-on session, you will learn how to turn your proxy into a security
Using Protection Engine for Cloud Services for URL Filtering, Malware Protection and Proxy Integration Hands-On Lab Description In this hands-on session, you will learn how to turn your proxy into a security
Acunetix Web Vulnerability Scanner. Getting Started. By Acunetix Ltd.
 Acunetix Web Vulnerability Scanner Getting Started V8 By Acunetix Ltd. 1 Starting a Scan The Scan Wizard allows you to quickly set-up an automated scan of your website. An automated scan provides a comprehensive
Acunetix Web Vulnerability Scanner Getting Started V8 By Acunetix Ltd. 1 Starting a Scan The Scan Wizard allows you to quickly set-up an automated scan of your website. An automated scan provides a comprehensive
Metasploit Unleashed. Class 2: Information Gathering and Vulnerability Scanning. Georgia Weidman Director of Cyberwarface, Reverse Space
 Metasploit Unleashed Class 2: Information Gathering and Vulnerability Scanning Georgia Weidman Director of Cyberwarface, Reverse Space Information Gathering Learning as much as possible about targets Ex:
Metasploit Unleashed Class 2: Information Gathering and Vulnerability Scanning Georgia Weidman Director of Cyberwarface, Reverse Space Information Gathering Learning as much as possible about targets Ex:
LT Auditor+ 2013. Windows Assessment SP1 Installation & Configuration Guide
 LT Auditor+ 2013 Windows Assessment SP1 Installation & Configuration Guide Table of Contents CHAPTER 1- OVERVIEW... 3 CHAPTER 2 - INSTALL LT AUDITOR+ WINDOWS ASSESSMENT SP1 COMPONENTS... 4 System Requirements...
LT Auditor+ 2013 Windows Assessment SP1 Installation & Configuration Guide Table of Contents CHAPTER 1- OVERVIEW... 3 CHAPTER 2 - INSTALL LT AUDITOR+ WINDOWS ASSESSMENT SP1 COMPONENTS... 4 System Requirements...
WEB APPLICATION HACKING. Part 2: Tools of the Trade (and how to use them)
 WEB APPLICATION HACKING Part 2: Tools of the Trade (and how to use them) Jonathan Eddy September 27, 2013 Last Updated September 27, 2013 MAPPING THE APPLICATION 4 2 ENUMERATING CONTENT AND FUNCTIONALITY
WEB APPLICATION HACKING Part 2: Tools of the Trade (and how to use them) Jonathan Eddy September 27, 2013 Last Updated September 27, 2013 MAPPING THE APPLICATION 4 2 ENUMERATING CONTENT AND FUNCTIONALITY
MFPConnect Monitoring. Monitoring with IPCheck Server Monitor. Integration Manual Version 2.05.00 Edition 1
 MFPConnect Monitoring Monitoring with IPCheck Server Monitor Integration Manual Version 2.05.00 Edition 1 TABLE OF CONTENTS 1. INTRODUCTION...3 2. REQUIREMENTS...4 3. RESTRICTIONS...5 4. INSTALLATION...6
MFPConnect Monitoring Monitoring with IPCheck Server Monitor Integration Manual Version 2.05.00 Edition 1 TABLE OF CONTENTS 1. INTRODUCTION...3 2. REQUIREMENTS...4 3. RESTRICTIONS...5 4. INSTALLATION...6
File Transfer with Secure FTP
 File Transfer with Secure FTP The Princeton Review values the security of all client s information and would like to encourage all FTP file transfers to and from our clients be conducted utilizing a Secure
File Transfer with Secure FTP The Princeton Review values the security of all client s information and would like to encourage all FTP file transfers to and from our clients be conducted utilizing a Secure
Configuring Security for FTP Traffic
 2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
Windows Vulnerability Assessment
 Windows Vulnerability Assessment Nowadays every enterprise, be it small or large, depends on information technology (IT) for some or most of its operations, and with IT comes information security. Most
Windows Vulnerability Assessment Nowadays every enterprise, be it small or large, depends on information technology (IT) for some or most of its operations, and with IT comes information security. Most
IEI emerge and On-Net Surveillance Systems (OnSSI) Network Video Recorder Setup and Integration Guide
 IEI emerge and On-Net Surveillance Systems (OnSSI) Network Video Recorder Setup and Integration Guide OnSSI Version 6.5 and IEI emerge Version 3.2 and above CONTENTS Requirements for OnSSI NVR/IEI emerge
IEI emerge and On-Net Surveillance Systems (OnSSI) Network Video Recorder Setup and Integration Guide OnSSI Version 6.5 and IEI emerge Version 3.2 and above CONTENTS Requirements for OnSSI NVR/IEI emerge
User Manual of the Pre-built Ubuntu 9 Virutal Machine
 SEED Document 1 User Manual of the Pre-built Ubuntu 9 Virutal Machine Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
SEED Document 1 User Manual of the Pre-built Ubuntu 9 Virutal Machine Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
Configuring Virtual Switches for Use with PVS. February 7, 2014 (Revision 1)
 Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
User Manual of the Pre-built Ubuntu 12.04 Virutal Machine
 SEED Labs 1 User Manual of the Pre-built Ubuntu 12.04 Virutal Machine Copyright c 2006-2014 Wenliang Du, Syracuse University. The development of this document is/was funded by three grants from the US
SEED Labs 1 User Manual of the Pre-built Ubuntu 12.04 Virutal Machine Copyright c 2006-2014 Wenliang Du, Syracuse University. The development of this document is/was funded by three grants from the US
DC Agent Troubleshooting
 DC Agent Troubleshooting Topic 50320 DC Agent Troubleshooting Web Security Solutions v7.7.x, 7.8.x 27-Mar-2013 This collection includes the following articles to help you troubleshoot DC Agent installation
DC Agent Troubleshooting Topic 50320 DC Agent Troubleshooting Web Security Solutions v7.7.x, 7.8.x 27-Mar-2013 This collection includes the following articles to help you troubleshoot DC Agent installation
Building a Penetration Testing Virtual Computer Laboratory
 Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
DocAve Upgrade Guide. From Version 4.1 to 4.5
 DocAve Upgrade Guide From Version 4.1 to 4.5 About This Guide This guide is intended for those who wish to update their current version of DocAve 4.1 to the latest DocAve 4.5. It is divided into two sections:
DocAve Upgrade Guide From Version 4.1 to 4.5 About This Guide This guide is intended for those who wish to update their current version of DocAve 4.1 to the latest DocAve 4.5. It is divided into two sections:
Automated Penetration Testing with the Metasploit Framework. NEO Information Security Forum March 19, 2008
 Automated Penetration Testing with the Metasploit Framework NEO Information Security Forum March 19, 2008 Topics What makes a good penetration testing framework? Frameworks available What is the Metasploit
Automated Penetration Testing with the Metasploit Framework NEO Information Security Forum March 19, 2008 Topics What makes a good penetration testing framework? Frameworks available What is the Metasploit
13.1 Backup virtual machines running on VMware ESXi / ESX Server
 13 Backup / Restore VMware Virtual Machines Tomahawk Pro This chapter describes how to backup and restore virtual machines running on VMware ESX, ESXi Server or VMware Server 2.0. 13.1 Backup virtual machines
13 Backup / Restore VMware Virtual Machines Tomahawk Pro This chapter describes how to backup and restore virtual machines running on VMware ESX, ESXi Server or VMware Server 2.0. 13.1 Backup virtual machines
Sophos Anti-Virus standalone startup guide. For Windows and Mac OS X
 Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Document Exchange Server 2.5
 KOFAX Document Exchange Server 2.5 Administrator s Guide for Fujitsu Network Scanners 10001820-000 2008-2009 Kofax, Inc., 16245 Laguna Canyon Road, Irvine, California 92618, U.S.A. All rights reserved.
KOFAX Document Exchange Server 2.5 Administrator s Guide for Fujitsu Network Scanners 10001820-000 2008-2009 Kofax, Inc., 16245 Laguna Canyon Road, Irvine, California 92618, U.S.A. All rights reserved.
NCS 430 Penetration Testing Lab #2 Tuesday, February 10, 2015 John Salamy
 1 NCS 430 Penetration Testing Lab #2 Tuesday, February 10, 2015 John Salamy 2 Item I. (What were you asked to do?) Complete Metasploit: Quick Test on page 88-108 of the Penetration Testing book. Complete
1 NCS 430 Penetration Testing Lab #2 Tuesday, February 10, 2015 John Salamy 2 Item I. (What were you asked to do?) Complete Metasploit: Quick Test on page 88-108 of the Penetration Testing book. Complete
Quick Start Guide. Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca!
 Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Armitage. Part 1. Author : r45c4l Mail : [email protected]. http://twitter.com/#!/r45c4l
 Armitage H acking Made Easy Part 1 Author : r45c4l Mail : [email protected] http://twitter.com/#!/r45c4l Greetz and shouts to the entire ICW team and every Indian hackers Introduction When I started
Armitage H acking Made Easy Part 1 Author : r45c4l Mail : [email protected] http://twitter.com/#!/r45c4l Greetz and shouts to the entire ICW team and every Indian hackers Introduction When I started
Introduction to Laboratory Assignment 3 Vulnerability scanning with OpenVAS
 Introduction to Laboratory Assignment 3 Vulnerability scanning with OpenVAS Computer Security Course EDA263 / DIT641 Chalmers University of Technology February 12 th, 2015 Vulnerability assessment? Overview
Introduction to Laboratory Assignment 3 Vulnerability scanning with OpenVAS Computer Security Course EDA263 / DIT641 Chalmers University of Technology February 12 th, 2015 Vulnerability assessment? Overview
Setting Up Sharp MX-Color Imagers To Scan To Email
 Setting Up Sharp MX-Color Imagers To Scan To Email MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, MX-M850, MX-M950, MX-M1100 Step 1. Click Start > Run
Setting Up Sharp MX-Color Imagers To Scan To Email MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, MX-M850, MX-M950, MX-M1100 Step 1. Click Start > Run
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Shellshock Security Patch for X86
 Shellshock Security Patch for X86 Guide for Using the FFPS Update Manager October 2014 Version 1.0. Page 1 Page 2 This page is intentionally blank Table of Contents 1.0 OVERVIEW - SHELLSHOCK/BASH SHELL
Shellshock Security Patch for X86 Guide for Using the FFPS Update Manager October 2014 Version 1.0. Page 1 Page 2 This page is intentionally blank Table of Contents 1.0 OVERVIEW - SHELLSHOCK/BASH SHELL
Cisco IPS Tuning Overview
 Cisco IPS Tuning Overview Overview Increasingly sophisticated attacks on business networks can impede business productivity, obstruct access to applications and resources, and significantly disrupt communications.
Cisco IPS Tuning Overview Overview Increasingly sophisticated attacks on business networks can impede business productivity, obstruct access to applications and resources, and significantly disrupt communications.
Nessus Enterprise Cloud User Guide. October 2, 2014 (Revision 9)
 Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Nessus Cloud User Registration
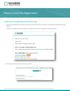 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Configuring MailArchiva with Insight Server
 Copyright 2009 Bynari Inc., All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any
Copyright 2009 Bynari Inc., All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any
Make a folder named Lab3. We will be using Unix redirection commands to create several output files in that folder.
 CMSC 355 Lab 3 : Penetration Testing Tools Due: September 31, 2010 In the previous lab, we used some basic system administration tools to figure out which programs where running on a system and which files
CMSC 355 Lab 3 : Penetration Testing Tools Due: September 31, 2010 In the previous lab, we used some basic system administration tools to figure out which programs where running on a system and which files
Changing Your Cameleon Server IP
 1.1 Overview Technical Note Cameleon requires that you have a static IP address defined for the server PC the Cameleon server application runs on. Even if the server PC has a static IP address, you may
1.1 Overview Technical Note Cameleon requires that you have a static IP address defined for the server PC the Cameleon server application runs on. Even if the server PC has a static IP address, you may
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
During your session you will have access to the following lab configuration. CLIENT1 (Windows XP Workstation) 192.168.0.2 /24
 Introduction The Network Vulnerabilities module provides you with the instruction and Server hardware to develop your hands on skills in the defined topics. This module includes the following exercises:
Introduction The Network Vulnerabilities module provides you with the instruction and Server hardware to develop your hands on skills in the defined topics. This module includes the following exercises:
IBM Security QRadar SIEM Version 7.1.0 MR1. Vulnerability Assessment Configuration Guide
 IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
Web attacks and security: SQL injection and cross-site scripting (XSS)
 Web attacks and security: SQL injection and cross-site scripting (XSS) License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike
Web attacks and security: SQL injection and cross-site scripting (XSS) License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike
Tutorial: Using HortonWorks Sandbox 2.3 on Amazon Web Services
 Tutorial: Using HortonWorks Sandbox 2.3 on Amazon Web Services Sayed Hadi Hashemi Last update: August 28, 2015 1 Overview Welcome Before diving into Cloud Applications, we need to set up the environment
Tutorial: Using HortonWorks Sandbox 2.3 on Amazon Web Services Sayed Hadi Hashemi Last update: August 28, 2015 1 Overview Welcome Before diving into Cloud Applications, we need to set up the environment
INDUSTRIAL CONTROL SYSTEMS CYBER SECURITY DEMONSTRATION
 INDUSTRIAL CONTROL SYSTEMS CYBER SECURITY DEMONSTRATION Prepared for the NRC Fuel Cycle Cyber Security Threat Conference Presented by: Jon Chugg, Ken Rohde Organization(s): INL Date: May 30, 2013 Disclaimer
INDUSTRIAL CONTROL SYSTEMS CYBER SECURITY DEMONSTRATION Prepared for the NRC Fuel Cycle Cyber Security Threat Conference Presented by: Jon Chugg, Ken Rohde Organization(s): INL Date: May 30, 2013 Disclaimer
Vulnerability Assessment and Penetration Testing
 Vulnerability Assessment and Penetration Testing Module 1: Vulnerability Assessment & Penetration Testing: Introduction 1.1 Brief Introduction of Linux 1.2 About Vulnerability Assessment and Penetration
Vulnerability Assessment and Penetration Testing Module 1: Vulnerability Assessment & Penetration Testing: Introduction 1.1 Brief Introduction of Linux 1.2 About Vulnerability Assessment and Penetration
Using Virtual Machines
 Using Virtual Machines We will use VMs in CIT 130 so that you can access both a Windows 7 and a Linux machine. You will be able to access these from on and off campus (off campus access will require that
Using Virtual Machines We will use VMs in CIT 130 so that you can access both a Windows 7 and a Linux machine. You will be able to access these from on and off campus (off campus access will require that
Virtual Appliance for VMware Server. Getting Started Guide. Revision 2.0.2. Warning and Disclaimer
 Virtual Appliance for VMware Server Getting Started Guide Revision 2.0.2 Warning and Disclaimer This document is designed to provide information about the configuration and installation of the CensorNet
Virtual Appliance for VMware Server Getting Started Guide Revision 2.0.2 Warning and Disclaimer This document is designed to provide information about the configuration and installation of the CensorNet
ActiveImage Protector 3.5 for Hyper-V with SHR. User Guide - Back up Hyper-V Server 2012 R2 host and
 ActiveImage Protector 3.5 for Hyper-V with SHR User Guide - Back up Hyper-V Server 2012 R2 host and restore individual virtual machines 2 nd Edition July 7, 2014 Copyright NetJapan, Inc. All Rights Reserved.
ActiveImage Protector 3.5 for Hyper-V with SHR User Guide - Back up Hyper-V Server 2012 R2 host and restore individual virtual machines 2 nd Edition July 7, 2014 Copyright NetJapan, Inc. All Rights Reserved.
WECCNET MESSAGING SYSTEM CLIENT DOCUMENTATION
 TABLE OF CONTENTS WECCNET Messaging System Client Documentation WECCNET MESSAGING SYSTEM CLIENT DOCUMENTATION March 3 rd, 2015 SUPPORT CONTACTS... 2 CLIENT REQUIREMENTS... 2 CLIENT PRECONFIGURATION...
TABLE OF CONTENTS WECCNET Messaging System Client Documentation WECCNET MESSAGING SYSTEM CLIENT DOCUMENTATION March 3 rd, 2015 SUPPORT CONTACTS... 2 CLIENT REQUIREMENTS... 2 CLIENT PRECONFIGURATION...
ScanShell.Net Install Guide
 ScanShell.Net Install Guide Please install the software first - DO NOT PLUG IN THE SCANNER The scanner has been carefully packaged to avoid damage during transportation. Before operating the scanner, please
ScanShell.Net Install Guide Please install the software first - DO NOT PLUG IN THE SCANNER The scanner has been carefully packaged to avoid damage during transportation. Before operating the scanner, please
Symantec Cyber Readiness Challenge Player s Manual
 Symantec Cyber Readiness Challenge Player s Manual Version 1.6 January 20, 2014 Table of Contents Introduction... 3 1 The Cyber Readiness Challenge... 4 1.1 Your Credentials... 4 1.2 Accessing the Competition...
Symantec Cyber Readiness Challenge Player s Manual Version 1.6 January 20, 2014 Table of Contents Introduction... 3 1 The Cyber Readiness Challenge... 4 1.1 Your Credentials... 4 1.2 Accessing the Competition...
NETWORK SETUP GLOSSARY
 GLOSSARY NETWORK SETUP Static IP PPPoE DHCP DDNS Static IP Computers are communicated and recognized by their own unique IP addresses over the Internet. Static IP provided by your ISP (Internet Service
GLOSSARY NETWORK SETUP Static IP PPPoE DHCP DDNS Static IP Computers are communicated and recognized by their own unique IP addresses over the Internet. Static IP provided by your ISP (Internet Service
FlexSim LAN License Server
 FlexSim LAN License Server Installation Instructions Rev. 20150318 Table of Contents Introduction... 2 Using lmtools... 2 1. Download the installation files... 3 2. Install the license server... 4 3. Connecting
FlexSim LAN License Server Installation Instructions Rev. 20150318 Table of Contents Introduction... 2 Using lmtools... 2 1. Download the installation files... 3 2. Install the license server... 4 3. Connecting
IntraVUE Plug Scanner/Recorder Installation and Start-Up
 IntraVUE Plug Scanner/Recorder Installation and Start-Up The IntraVUE Plug is a complete IntraVUE Hardware/Software solution that can plug directly into any network to continually scan and record details
IntraVUE Plug Scanner/Recorder Installation and Start-Up The IntraVUE Plug is a complete IntraVUE Hardware/Software solution that can plug directly into any network to continually scan and record details
How To Install & Use Metascan With Policy Patrol
 Policy Patrol 9 technical documentation June 16, 2014 How To Install & Use Metascan With Policy Patrol No antivirus engine is perfect. With over 220,000 new threats emerging daily, it would be impossible
Policy Patrol 9 technical documentation June 16, 2014 How To Install & Use Metascan With Policy Patrol No antivirus engine is perfect. With over 220,000 new threats emerging daily, it would be impossible
Penetration Testing Lab. Reconnaissance and Mapping Using Samurai-2.0
 Penetration Testing Lab Reconnaissance and Mapping Using Samurai-2.0 Notes: 1. Be careful about running most of these tools against machines without permission. Even the poorest intrusion detection system
Penetration Testing Lab Reconnaissance and Mapping Using Samurai-2.0 Notes: 1. Be careful about running most of these tools against machines without permission. Even the poorest intrusion detection system
How to Install Multiple Monitoring Agents on a Microsoft Operating System. Version StoneGate Firewall/VPN 2.6 and SMC 3.2
 How to Install Multiple Monitoring Agents on a Microsoft Operating System Version StoneGate Firewall/VPN 2.6 and SMC 3.2 INTRODUCTION This document provides detailed instructions for installing multiple
How to Install Multiple Monitoring Agents on a Microsoft Operating System Version StoneGate Firewall/VPN 2.6 and SMC 3.2 INTRODUCTION This document provides detailed instructions for installing multiple
