Why do I need a pen test lab? Requirements. Virtual Machine Downloads
|
|
|
- Clemence Norman
- 8 years ago
- Views:
Transcription
1 Why do I need a pen test lab? Hacking and or scanning machines without consent is against the law in most countries To become an effective penetration tester or ethical hacker you need to practice to enhance your skills Freedom to install, run, and configure any tool you like Requirements Hard Disk - 50GB of disk space or more depending on the number of guest operating systems you plan on installing. CPU - I recommend the latest technology but any of the I3/I5/I7 families are ok. The more processing power you have the better Memory - I recommend 8GB or 16GB. Memory is critical. The more memory you have the more virtual systems you will be able to have running at one time Virtualization software I recommend using open source software to start using either VirtualBox or VMPlayer. Eventually you might want to pay for the commercial software such as VMworkstation of if you have a Mac VMfusion Virtual Machine Downloads Kali Linux 2 -Pentesting Environment o Osboxes.org o Metasploitable 2 Vulnerable Machine o Bee-Box Vulnerable Machine o OWASP Brocken Web Applications Project Vulnerable Machine o
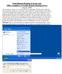
2 Virtualization Software For this class I will be using VirtualBox o o Install the software based on your host operating system Windows, OSX, Linux, or Solaris Folder Structure I recommend creating 2 folders for this work o A folder for the compressed files so that if need be you can recreate the vms in case you end up with a corrupted VM o A folder for the uncompressed Virtual Machines Extracting Files I recommend downloading 7-zip if you don t already have winzip. 7-zip is open source software which can decompress a large number of compressed file types. o Creating Virtual Machines Open Virtual Box Click New Enter the Name and Operating System and Click Next
3 Change the memory size to 512 Use and existing virtual hard disk Click on the folder icon above cancel and select the folder and file that you want to use. Click Open. Then click Create. Select the first file cl1.vmdk
4 Now you will see your virtual machine on the vm list Click on Settings Click on Network. Change Attached to to Nat Network. Name NatNetwork and click OK Click on Start o Wait for the machine to run. You will then be at the login screen. Enter the password of root and the password of owaspbwa
5 You will now be logged in as root and be at the # prompt. This is all you need to do with this VM. Write down the ip address as in this case it is so you can use it later. Create the other VMS just as you did with this one. When you are done you should have a virtual machine list that looks like this: Kali Linux Video 1 Video 2 Start Kali Linux VM Login with the username of root Enter the password of toor if you downloaded the Vm from offensive security Enter the password of osboxes.org if you downloaded the VM from osboxes.org Open up a terminal session
6 Create a new user called user1 o Type useradd m user1 Create a password for user1 o Type passwd user1 o Type root o Retype root Add user1 to the sudo group o Type usermod a G sudo user1 Update Kali Distribution Now let s update our Kali Distribution o Type apt-get update o Once complete and you are back at the # prompt o Type apt-get dist-upgrade o Type y and hit enter o When done type exit
7 Power Settings Now let s turn off power saving Click on the down arrow in the top right of screen then click on settings Click on Power Change Blank screen to Never Close out of Power Settings Privacy Settings Change Privacy Settings Click on Show Applications Type settings in the search bar and hit enter
8 Click Privacy Change Screen Lock by turning off Automatic Screen Lock Close out of screenlock Now let s set our system data and time. Click on settings again Date & Time Click on Date & Time o Turn on Automatic Date & Time o Turn on Automatic Time Zone o Change Time Format to AM/PM
9 Close out of Date & Time Nmap Open a terminal session Test your network connectivity and make sure nmap is working Type nmap scanme.nmap.org Review the results to see the open ports and services found Zenmap At the command line type Zenmap Enter scanme.nmap.org as the target Select the profile of Regular scan and hit the scan button
10 Nmap Scans Run the following scans against scanme.nmap.org Nmap sn scanme.nmap.org (just a ping) Nmap Pn scanme.nmap.org (without a ping stealthy) Nmap A scanme.nmap.org (aggressive scan) Nmap p 80 scanme.nmap.org Nmap can select what ports to scan by simply adding p port,port2,port 3 In this case we will only scan port 80. Nmap p- scanme.nmap.org Scans all ports from port It can also be accomplished by nmap p scanme.nmap.org.
11 Zenmap Scans Enter the target of scanme.nmap.org and select the following profiles and hit the scan button. Look at the commands. Regular Scan Quick traceroute Quick scan Intense scan, all TCP ports Switch user to user1 Login with the username of user1 Enter the password of root Open up a terminal session and notice that now you have a $ prompt as opposed to a # prompt. You are no longer logged in as root so the # is replaced with a $. Now when you run your nmap commands you are going to have to enter sudo before the nmap command
12 Scanning Vulnerable Virtual Machines Bee-Box Start Bee-Box Open up a terminal session Type ifconfig and hit enter You should get an IP address
13 Write down the ip address as you are going to use it throughout the nmap and Zenmap exercises. Mine is Yours will be different Go back to Kali Linux and open up a terminal session Type sudo nmap sn x.x.x.x (ip address from bee-box) Enter the password of user1 - root Type sudo Nmap ip address Type sudo nmap Pn IP address Type sudo nmap F IP Address This scan will scan the top 100 ports. Type sudo Nmap --top-ports 10 ip address This will only scan the top 10 ports. Type sudo nmap open ip address This scan will only display the open ports Type sudo nmap p 80 ip address This will only scan port 80. Type sudo nmap p 80,445 IP Address This will only scan ports 80 and 445. Type sudo nmap p This will scan ports 20 through 600. Type sudo nmap p- ip address This will scan all the TCP ports You can also achieve the same thing by typing sudo nmap p ip address Type sudo nmap sv ip address This will scan the top 1000 ports and provide details about the services. Type sudo nmap O ip address in order to scan the top 1000 ports but also scan for the operating system. Nmap has a database of operating systems it uses to compare to the system Type sudo nmap A ip address in order to perform an aggressive scan which includes, open ports, OS, Services, traceroute, and mac address. This is not a stealthy scan by any means It will take much longer than any of the other scans. Type sudo nmap T5 ip address to run an insane fast scan. The other options are -T4 (aggressive), -T3 (normal), -T2 (polite), -T1 (Sneaky), -T0 (paranoid) Zenmap Enter the target IP address, Profile select regular scan, and hit the scan button Now let s perform a Quick scan by changing the profile to quick scan and hitting the scan button
14 Metasploitable Metasploitable Start Metasploitable Login as msfadmin/msfadmin Type Ifconfig You should get an IP address
15 Write down the ip address as you are going to use it throughout the nmap and Zenmap exercises. Mine is Yours will be different Go back to Kali Linux and open up a terminal session Type sudo nmap sn x.x.x.x (ip address from metasploitable) Type sudo Nmap ip address Type sudo nmap Pn IP address Type sudo nmap F IP Address This scan will scan the top 100 ports. Type sudo Nmap --top-ports 10 ip address This will only scan the top 10 ports. Type sudo nmap open ip address This scan will only display the open ports Type sudo nmap p 80 ip address This will only scan port 80. Type sudo nmap p 80,445 IP Address This will only scan ports 80 and 445. Type sudo nmap p This will scan ports 20 through 600. Type sudo nmap p- ip address This will scan all the TCP ports You can also achieve the same thing by typing sudo nmap p ip address Type sudo nmap sv ip address This will scan the top 1000 ports and provide details about the services. Type sudo nmap O ip address in order to scan the top 1000 ports but also scan for the operating system. Nmap has a database of operating systems it uses to compare to the system Type sudo nmap A ip address in order to perform an aggressive scan which includes, open ports, OS, Services, traceroute, and mac address. This is not a stealthy scan by any means It will take much longer than any of the other scans. Type sudo nmap T5 ip address to run an insane fast scan. The other options are -T4 (aggressive), -T3 (normal), -T2 (polite), -T1 (Sneaky), -T0 (paranoid) Zenmap Enter the tar Enter the target IP address, Profile select regular scan, and hit the scan button Now let s perform a Quick scan by changing the profile to quick scan and hitting the scan button
16 OWASP Your OWASP machine should already be running. You logged in s root with a password of owaspbwa. You should have already written down the ipaddress from earlier Go back to Kali Linux and open up a terminal session Type sudo nmap sn x.x.x.x (ip address from Owasp) Type sudo Nmap ip address Type sudo nmap Pn IP address Type sudo nmap F IP Address This scan will scan the top 100 ports. Type sudo Nmap --top-ports 10 ip address This will only scan the top 10 ports. Type sudo nmap open ip address This scan will only display the open ports Type sudo nmap p 80 ip address This will only scan port 80. Type sudo nmap p 80,445 IP Address This will only scan ports 80 and 445. Type sudo nmap p This will scan ports 20 through 600. Type sudo nmap p- ip address This will scan all the TCP ports You can also achieve the same thing by typing sudo nmap p ip address Type sudo nmap sv ip address This will scan the top 1000 ports and provide details about the services. Type sudo nmap O ip address in order to scan the top 1000 ports but also scan for the operating system. Nmap has a database of operating systems it uses to compare to the system Type sudo nmap A ip address in order to perform an aggressive scan which includes, open ports, OS, Services, traceroute, and mac address. This is not a stealthy scan by any means It will take much longer than any of the other scans. Type sudo nmap T5 ip address to run an insane fast scan. The other options are -T4 (aggressive), -T3 (normal), -T2 (polite), -T1 (Sneaky), -T0 (paranoid) Zenmap Enter the tar Enter the target IP address, Profile select regular scan, and hit the scan button Now let s perform a Quick scan by changing the profile to quick scan and hitting the scan button
17 Scanning all Vulnerable VMs at once Type sudo nmap sn ip , ( use your ip addresses not mine) Type sudo nmap ip , ( use your ip addresses not mine) Type sudo nmap F ( use your ip addresses not mine) Type sudo nmap --top-ports ( use your ip addresses not mine) Zenmap Scanning of Vulnerable VMs Nessus Type sudo zenmap at the command line Enter the ip address of bee-box as the target. Select regular scan and hit the scan button Enter the ip address of metasploitable as the target. Select regular scan and hit the scan button Enter the ip address of OWASP as the target. Select regular scan and hit the scan button Exit Zenmap Activation Code Open google and search for nessus obtain an activation code Click on Obtain an Activation Code Tenable Network Security Under Nessus Home Click Register Now Enter your information and hit Register
18 Wait a few minutes and check your Nessus Download Open up the Iceweasel web browser Search for download nessus and hit search Click Download Nessus Scroll down and Download Nessus Home Select your Operation System Linux
19 Select the file for your operating system 32 or 64 bit. Agree to the Subscription Agreement Click on Save File When the file has downloaded you should see the following: Nessus Installation Close your browser and open a terminal session Type ls Change the directory to Downloads. Type cd Downloads (remember Linux is case sensitive so be sure to type the capital D) Type ls again and you should see the file you just downloaded (Nessus debian6_amd64.deb. If you have a 32 bit operating system the file will be Nessus debian6_i386.deb. Type sudo dpkg i Nessus debian6_amd64.deb (64 bit) (will be a different file if you have a 32 bit OS. In that case type sudo dpkg i Nessus debian6_i386.deb
20 Enter the password for user1 root You should see the following Start Nessus Follow the directions and start nessusd by typing sudo /etc/init.d/nessusd start and hit enter. You should see Starting Nessus:. Nessus Connection and Configuration Now Open Iceweasel and enter and hit enter You should see an error This Connection is Untrusted
21 Click I Understand the Risks Click Add Exception Click Get Certificate and Confirm Security Exception You will be presented with the Nessus welcome screen, Click Continue Initial Account Setup o Username user1 o Password root o Confirm Password root If you are asked if you want to save your password select Never
22 Activation and Plugins Download Enter you activation code from your nessus.txt file and Click Continue Wait for the plugins to download When the update is complete you will be at the logon screen Enter the username of user1 and a password of root then Click Sign In You will now be at the Nessus Main Screen
23 Let s create a new folder for our scans called user1. Click on New Folder, enter user1, and Click on Create You will now see the user1 folder under My scans Now we are ready for scanning Nessus Scan Click on New Scan Select Basic Network Scan Enter the following Information o Name Basic Scan Bee-box o Description Basic Scan bee-box o Folder user1 o Scanner Local Scanner o Targets enter the ip addresses from Bee-Box that you wrote down earlier. Click on Save and Nessus will conduct a scan of the most common ports Wait for the scan to finish and the green circle will be replaced with a gray checkmark. Click on the completed scan and review the results Click on New Scan Select Basic Network Scan Enter the following Information o Name Basic Scan OWASP o Description Basic Scan OWASP o Folder user1 o Scanner Local Scanner o Targets enter the ip addresses from OWASP that you wrote down earlier. Click on Save and Nessus will conduct a scan of the most common ports
24 Wait for the scan to finish and the green circle will be replaced with a gray checkmark. Click on the completed scan and review the results Nessus Scan Two Hosts Click on New Scan Select Basic Network Scan Enter the following Information o Name Basic Scan 2hosts o Description Basic Scan 2hosts o Folder user1 o Scanner Local Scanner o Targets enter the ip addresses from OWASP and Bee-Box that you wrote down earlier. Click on Save and Nessus will conduct a scan of the most common ports Wait for the scan to finish and the green circle will be replaced with a gray checkmark. This will take a while as it is scanning 2 hosts. Click on the completed scan and review the results Report Executive Summary Click on Export Select PDF Accept Executive Summary and Click on Export
25 You will now be asked if you want to save the file. Click Save File Now click on the down arrow and you will see the pdf file. Click on the pdf file to open it The Nessus Report will now display on your screen The executive summary provides the vulnerability information for each host in order of severity. Change the view to be 100% and then click on the first ip address
26 At the top of the screen you will notice the summary of each severity by number Go through the report and look at all the detail it provides. This is an executive summary you can provide to show vulnerabilities by severity so that the client knows what issues they need to address in order of importance. Select the next IP address and look at the detail for that host When you are done looking at the report Close it Thanks for your attention I hope this course has helped you on your way to become an ethical hacker
27
Vulnerability analysis
 Vulnerability analysis License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents License Contents
Vulnerability analysis License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents License Contents
IDS and Penetration Testing Lab ISA656 (Attacker)
 IDS and Penetration Testing Lab ISA656 (Attacker) Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible
IDS and Penetration Testing Lab ISA656 (Attacker) Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible
Using VirtualBox ACHOTL1 Virtual Machines
 Using VirtualBox ACHOTL1 Virtual Machines The steps in the Apache Cassandra Hands-On Training Level One courseware book were written using VMware as the virtualization technology. Therefore, it is recommended
Using VirtualBox ACHOTL1 Virtual Machines The steps in the Apache Cassandra Hands-On Training Level One courseware book were written using VMware as the virtualization technology. Therefore, it is recommended
ECT362 Installing Linux Virtual Machine in KL322
 ECT362 Installing Linux Virtual Machine in KL322 The steps below outline how to install Linux under Windows as a virtual machine. This install uses the Ubuntu 10.04 distribution of Linux along with the
ECT362 Installing Linux Virtual Machine in KL322 The steps below outline how to install Linux under Windows as a virtual machine. This install uses the Ubuntu 10.04 distribution of Linux along with the
Signiant Agent installation
 Signiant Agent installation Release 11.3.0 March 2015 ABSTRACT Guidelines to install the Signiant Agent software for the WCPApp. The following instructions are adapted from the Signiant original documentation
Signiant Agent installation Release 11.3.0 March 2015 ABSTRACT Guidelines to install the Signiant Agent software for the WCPApp. The following instructions are adapted from the Signiant original documentation
Symantec Cyber Readiness Challenge Player s Manual
 Symantec Cyber Readiness Challenge Player s Manual Version 1.6 January 20, 2014 Table of Contents Introduction... 3 1 The Cyber Readiness Challenge... 4 1.1 Your Credentials... 4 1.2 Accessing the Competition...
Symantec Cyber Readiness Challenge Player s Manual Version 1.6 January 20, 2014 Table of Contents Introduction... 3 1 The Cyber Readiness Challenge... 4 1.1 Your Credentials... 4 1.2 Accessing the Competition...
Installing Sun's VirtualBox on Windows XP and setting up an Ubuntu VM
 Installing Sun's VirtualBox on Windows XP and setting up an Ubuntu VM laptop will need to have 10GB of free space to install download the latest VirtualBox software from www.sun.com make sure you pick
Installing Sun's VirtualBox on Windows XP and setting up an Ubuntu VM laptop will need to have 10GB of free space to install download the latest VirtualBox software from www.sun.com make sure you pick
Local Caching Servers (LCS): User Manual
 Local Caching Servers (LCS): User Manual Table of Contents Local Caching Servers... 1 Supported Browsers... 1 Getting Help... 1 System Requirements... 2 Macintosh... 2 Windows... 2 Linux... 2 Downloading
Local Caching Servers (LCS): User Manual Table of Contents Local Caching Servers... 1 Supported Browsers... 1 Getting Help... 1 System Requirements... 2 Macintosh... 2 Windows... 2 Linux... 2 Downloading
Intelligence Gathering. n00bpentesting.com
 Intelligence Gathering Prerequisites Hardware Software Topics Covered A Note Before You Begin Lab 0ne Target Selection and OSINT Scenario Lab Tw0 - Footprinting What s Next? 3 3 3 4 4 4 5 5 13 17 2 Prerequisites
Intelligence Gathering Prerequisites Hardware Software Topics Covered A Note Before You Begin Lab 0ne Target Selection and OSINT Scenario Lab Tw0 - Footprinting What s Next? 3 3 3 4 4 4 5 5 13 17 2 Prerequisites
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (Internal Attacker - Beginner version) By: magikh0e - magikh0e@ihtb.org Last Edit: July 07 2012 This guide assumes a few things... 1. You have installed Backtrack before
Penetration Testing LAB Setup Guide (Internal Attacker - Beginner version) By: magikh0e - magikh0e@ihtb.org Last Edit: July 07 2012 This guide assumes a few things... 1. You have installed Backtrack before
Vulnerability Assessment Lab
 Vulnerability Assessment Lab Fully assessing a company's security posture is a critical job to maintain intellectual property integrity, and protect customer information. As a security auditor your job
Vulnerability Assessment Lab Fully assessing a company's security posture is a critical job to maintain intellectual property integrity, and protect customer information. As a security auditor your job
Introduction to Vulnerability Scanners Lab
 Introduction to Vulnerability Scanners Lab Introduction: Lets take enumeration (and scanning) to the next level and automate what we have been doing manually. Lets use a tool that does just what we have
Introduction to Vulnerability Scanners Lab Introduction: Lets take enumeration (and scanning) to the next level and automate what we have been doing manually. Lets use a tool that does just what we have
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
DraganFly Guardian: API Instillation Instructions
 Setting Up Ubuntu to Run Draganflyer Guardian API Page 1 of 16 \ DraganFly Guardian: API Instillation Instructions Spring 2015 Casey Corrado Setting Up Ubuntu to Run Draganflyer Guardian API Page 2 of
Setting Up Ubuntu to Run Draganflyer Guardian API Page 1 of 16 \ DraganFly Guardian: API Instillation Instructions Spring 2015 Casey Corrado Setting Up Ubuntu to Run Draganflyer Guardian API Page 2 of
Linux Development Environment Description Based on VirtualBox Structure
 Linux Development Environment Description Based on VirtualBox Structure V1.0 1 VirtualBox is open source virtual machine software. It mainly has three advantages: (1) Free (2) compact (3) powerful. At
Linux Development Environment Description Based on VirtualBox Structure V1.0 1 VirtualBox is open source virtual machine software. It mainly has three advantages: (1) Free (2) compact (3) powerful. At
1. Downloading. 2. Installation and License Acquiring. Xilinx ISE Webpack + Project Setup Instructions
 Xilinx ISE Webpack + Project Setup Instructions 1. Downloading The Xilinx tools are free for download from their website and can be installed on your Windowsbased PC s. Go to the following URL: http://www.xilinx.com/support/download/index.htm
Xilinx ISE Webpack + Project Setup Instructions 1. Downloading The Xilinx tools are free for download from their website and can be installed on your Windowsbased PC s. Go to the following URL: http://www.xilinx.com/support/download/index.htm
From a Finder window choose Applications (shown circled in red) and then double click the Tether icon (shown circled in green).
 From a Finder window choose Applications (shown circled in red) and then double click the Tether icon (shown circled in green). You will be presented with a dialog box asking for you to enter an ad-hoc
From a Finder window choose Applications (shown circled in red) and then double click the Tether icon (shown circled in green). You will be presented with a dialog box asking for you to enter an ad-hoc
Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an
 Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an addendum. The first part will be the steps required to
Using Remote Desktop to access your Office Computer or Faculty Remote Desktop Server August, 2005 This document consists of two main parts and an addendum. The first part will be the steps required to
Introduction to Operating Systems
 Introduction to Operating Systems It is important that you familiarize yourself with Windows and Linux in preparation for this course. The exercises in this book assume a basic knowledge of both of these
Introduction to Operating Systems It is important that you familiarize yourself with Windows and Linux in preparation for this course. The exercises in this book assume a basic knowledge of both of these
Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine
 Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine Version 3.0 Please note: This appliance is for testing and educational purposes only; it is unsupported and not
Quick Deployment Step-by-step instructions to deploy Oracle Big Data Lite Virtual Machine Version 3.0 Please note: This appliance is for testing and educational purposes only; it is unsupported and not
HP SDN VM and Ubuntu Setup
 HP SDN VM and Ubuntu Setup Technical Configuration Guide Version: 1 September 2013 Table of Contents Introduction... 2 Option 1: VirtualBox Preconfigured Setup... 2 Option 2: VMware Setup (from scratch)...
HP SDN VM and Ubuntu Setup Technical Configuration Guide Version: 1 September 2013 Table of Contents Introduction... 2 Option 1: VirtualBox Preconfigured Setup... 2 Option 2: VMware Setup (from scratch)...
WA1826 Designing Cloud Computing Solutions. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA1826 Designing Cloud Computing Solutions Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum
WA1826 Designing Cloud Computing Solutions Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Bringing the Eko VM Home (302)
 Liinux Howttos Brriingiing tthe Eko VM Home ((302)) CIIS 90 Sprriing 2011 Bringing the Eko VM Home (302) This Howto shows how to install VirtualBox and create the Linux Eko VM used in the CIS 90 course.
Liinux Howttos Brriingiing tthe Eko VM Home ((302)) CIIS 90 Sprriing 2011 Bringing the Eko VM Home (302) This Howto shows how to install VirtualBox and create the Linux Eko VM used in the CIS 90 course.
How to install/upgrade the LANDesk virtual Cloud service appliance (CSA)
 How to install/upgrade the LANDesk virtual Cloud service appliance (CSA) The upgrade process for the virtual Cloud Services Appliance is a side- by- side install. This document will walk you through backing
How to install/upgrade the LANDesk virtual Cloud service appliance (CSA) The upgrade process for the virtual Cloud Services Appliance is a side- by- side install. This document will walk you through backing
Personal Virtual Server (PVS) Quick Start Guide
 Personal Virtual Server (PVS) Quick Start Guide Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may contain trade
Personal Virtual Server (PVS) Quick Start Guide Copyright 2015 Pegasystems Inc., Cambridge, MA All rights reserved. This document describes products and services of Pegasystems Inc. It may contain trade
Download and Install the Citrix Receiver for Mac/Linux
 Download and Install the Citrix Receiver for Mac/Linux NOTE: WOW can only be used with Internet Explorer for Windows. To accommodate WOW customers using Mac or Linux computers, a Citrix solution was developed
Download and Install the Citrix Receiver for Mac/Linux NOTE: WOW can only be used with Internet Explorer for Windows. To accommodate WOW customers using Mac or Linux computers, a Citrix solution was developed
Using Virtual Machines
 Using Virtual Machines We will use VMs in CIT 130 so that you can access both a Windows 7 and a Linux machine. You will be able to access these from on and off campus (off campus access will require that
Using Virtual Machines We will use VMs in CIT 130 so that you can access both a Windows 7 and a Linux machine. You will be able to access these from on and off campus (off campus access will require that
Linux Boot Camp. Our Lady of the Lake University Computer Information Systems & Security Department Kevin Barton Artair Burnett
 Linux Boot Camp Our Lady of the Lake University Computer Information Systems & Security Department Kevin Barton Artair Burnett Schedule for the Week Schedule for the Week Mon Welcome from Enrollment Management
Linux Boot Camp Our Lady of the Lake University Computer Information Systems & Security Department Kevin Barton Artair Burnett Schedule for the Week Schedule for the Week Mon Welcome from Enrollment Management
BaseManager & BACnet Manager VM Server Configuration Guide
 BaseManager & BACnet Manager VM Server Configuration Guide For Self-Hosted BaseManager & BACnet Manager Servers Deployed as Virtual Machines August 27, 2015 Customer Service 1-866-294-5847 i Baseline Inc.
BaseManager & BACnet Manager VM Server Configuration Guide For Self-Hosted BaseManager & BACnet Manager Servers Deployed as Virtual Machines August 27, 2015 Customer Service 1-866-294-5847 i Baseline Inc.
Virtual Appliance for VMware Server. Getting Started Guide. Revision 2.0.2. Warning and Disclaimer
 Virtual Appliance for VMware Server Getting Started Guide Revision 2.0.2 Warning and Disclaimer This document is designed to provide information about the configuration and installation of the CensorNet
Virtual Appliance for VMware Server Getting Started Guide Revision 2.0.2 Warning and Disclaimer This document is designed to provide information about the configuration and installation of the CensorNet
1. Navigate to Control Panel and click on User Accounts and Family Safety. 2. Click on User Accounts
 This document will guide you through setting up your outgoing server (SMTP) Microsoft Outlook and Windows Live Mail. There is also a section below that guides you through the manual configuration of your
This document will guide you through setting up your outgoing server (SMTP) Microsoft Outlook and Windows Live Mail. There is also a section below that guides you through the manual configuration of your
Addonics T E C H N O L O G I E S. NAS Adapter. Model: NASU2. 1.0 Key Features
 1.0 Key Features Addonics T E C H N O L O G I E S NAS Adapter Model: NASU2 User Manual Convert any USB 2.0 / 1.1 mass storage device into a Network Attached Storage device Great for adding Addonics Storage
1.0 Key Features Addonics T E C H N O L O G I E S NAS Adapter Model: NASU2 User Manual Convert any USB 2.0 / 1.1 mass storage device into a Network Attached Storage device Great for adding Addonics Storage
How to Log in to LDRPS-Web v10 (L10) https://enterprise.strohlservices.com
 How to Log in to LDRPS-Web v10 (L10) https://enterprise.strohlservices.com Contents First Time Login Instructions... 1 1) Use the Internet Explorer (IE) Web browser*... 1 2) Install the.net Framework...
How to Log in to LDRPS-Web v10 (L10) https://enterprise.strohlservices.com Contents First Time Login Instructions... 1 1) Use the Internet Explorer (IE) Web browser*... 1 2) Install the.net Framework...
Creating a Linux Virtual Machine using Virtual Box
 A. Install Virtual Box: Creating a Linux Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer complete.
A. Install Virtual Box: Creating a Linux Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer complete.
Online Backup Client User Manual
 For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
Building a Penetration Testing Virtual Computer Laboratory
 Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
Building a Penetration Testing Virtual Computer Laboratory User Guide 1 A. Table of Contents Collaborative Virtual Computer Laboratory A. Table of Contents... 2 B. Introduction... 3 C. Configure Host Network
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures. Goliath Performance Monitor Installation Guide v11.
 Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.5 (v11.5) Document Date: March 2015 www.goliathtechnologies.com
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.5 (v11.5) Document Date: March 2015 www.goliathtechnologies.com
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection
 IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
IS L06 Protect Servers and Defend Against APTs with Symantec Critical System Protection Description Lab flow At the end of this lab, you should be able to Discover how to harness the power and capabilities
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
DigiDelivery Client Quick Start
 DigiDelivery Client Quick Start Installing the DigiDelivery Client To download and install the DigiDelivery client software: 1 Launch your Web browser and navigate to www.digidesign.com/digidelivery/clients.
DigiDelivery Client Quick Start Installing the DigiDelivery Client To download and install the DigiDelivery client software: 1 Launch your Web browser and navigate to www.digidesign.com/digidelivery/clients.
IDS and Penetration Testing Lab II
 IDS and Penetration Testing Lab II Software Requirements: 1. A secure shell (SSH) client. For windows you can download a free version from here: http://the.earth.li/~sgtatham/putty/latest/x86/putty-0.62-
IDS and Penetration Testing Lab II Software Requirements: 1. A secure shell (SSH) client. For windows you can download a free version from here: http://the.earth.li/~sgtatham/putty/latest/x86/putty-0.62-
Installation Guidelines (MySQL database & Archivists Toolkit client)
 Installation Guidelines (MySQL database & Archivists Toolkit client) Understanding the Toolkit Architecture The Archivists Toolkit requires both a client and database to function. The client is installed
Installation Guidelines (MySQL database & Archivists Toolkit client) Understanding the Toolkit Architecture The Archivists Toolkit requires both a client and database to function. The client is installed
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Post Exploitation. n00bpentesting.com
 Post Exploitation n00bpentesting.com Prerequisites Hardware Software Topics Covered A Note Before You Begin Lab 0ne Post Exploitation What s Next? 3 3 3 4 4 4 5 8 2 Prerequisites Thank you for downloading
Post Exploitation n00bpentesting.com Prerequisites Hardware Software Topics Covered A Note Before You Begin Lab 0ne Post Exploitation What s Next? 3 3 3 4 4 4 5 8 2 Prerequisites Thank you for downloading
60467 Project 1. Net Vulnerabilities scans and attacks. Chun Li
 60467 Project 1 Net Vulnerabilities scans and attacks Chun Li Hardware used: Desktop PC: Windows Vista service pack Service Pack 2 v113 Intel Core 2 Duo 3GHz CPU, 4GB Ram, D-Link DWA-552 XtremeN Desktop
60467 Project 1 Net Vulnerabilities scans and attacks Chun Li Hardware used: Desktop PC: Windows Vista service pack Service Pack 2 v113 Intel Core 2 Duo 3GHz CPU, 4GB Ram, D-Link DWA-552 XtremeN Desktop
Penetration Testing LAB Setup Guide
 Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - magikh0e@ihtb.org Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
Penetration Testing LAB Setup Guide (External Attacker - Intermediate) By: magikh0e - magikh0e@ihtb.org Last Edit: July 06 2012 This guide assumes a few things... 1. You have read the basic guide of this
The BackTrack Successor
 SCENARIOS Kali Linux The BackTrack Successor On March 13, Kali, a complete rebuild of BackTrack Linux, has been released. It has been constructed on Debian and is FHS (Filesystem Hierarchy Standard) complaint.
SCENARIOS Kali Linux The BackTrack Successor On March 13, Kali, a complete rebuild of BackTrack Linux, has been released. It has been constructed on Debian and is FHS (Filesystem Hierarchy Standard) complaint.
Online Backup Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Installing Proview on an Windows XP machine
 Installing Proview on an Windows XP machine This is a guide for the installation of Proview on an WindowsXP machine using VirtualBox. VirtualBox makes it possible to create virtual computers and allows
Installing Proview on an Windows XP machine This is a guide for the installation of Proview on an WindowsXP machine using VirtualBox. VirtualBox makes it possible to create virtual computers and allows
Local Caching Servers (LCS) February 2015
 Local Caching Servers (LCS) February 2015 1.1 Chapter 1: Welcome to LCS The Kansas Interactive Testing Engine (KITE ) is used to deliver standardized tests via testing machines like desktop, laptop, and
Local Caching Servers (LCS) February 2015 1.1 Chapter 1: Welcome to LCS The Kansas Interactive Testing Engine (KITE ) is used to deliver standardized tests via testing machines like desktop, laptop, and
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures. Goliath Performance Monitor Installation Guide v11.
 Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.6 (v11.6) Document Date: August 2015 www.goliathtechnologies.com
Consolidated Monitoring, Analysis and Automated Remediation For Hybrid IT Infrastructures Goliath Performance Monitor Installation Guide v11.6 (v11.6) Document Date: August 2015 www.goliathtechnologies.com
Creating a Windows XP Virtual Machine using Virtual Box
 A. Install Virtual Box: Creating a Windows XP Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer
A. Install Virtual Box: Creating a Windows XP Virtual Machine using Virtual Box 1. Download the Virtualbox installer http://www.virtualbox.org/wiki/downloads 2. Run the installer and have the installer
Information Sheet IS13011A. VS Series - Recovering / Installing the Operating System. (For Software Version 4.x) Issue 1.0...
 Information Sheet IS13011A VS Series - Recovering / Installing the Operating System (For Software Version 4.x) Issue 1.0...20 January 2014 Nautel Limited 10089 Peggy's Cove Road, Hackett's Cove, NS, Canada
Information Sheet IS13011A VS Series - Recovering / Installing the Operating System (For Software Version 4.x) Issue 1.0...20 January 2014 Nautel Limited 10089 Peggy's Cove Road, Hackett's Cove, NS, Canada
VPN: Virtual Private Network Setup Instructions
 VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3)
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3) Manual installation of agents and importing the SCOM certificate to the servers to be monitored:
Step-by-step installation guide for monitoring untrusted servers using Operations Manager ( Part 3 of 3) Manual installation of agents and importing the SCOM certificate to the servers to be monitored:
SHAREPOINT 2013 IN INFRASTRUCTURE AS A SERVICE
 SHAREPOINT 2013 IN INFRASTRUCTURE AS A SERVICE Contents Introduction... 3 Step 1 Create Azure Components... 5 Step 1.1 Virtual Network... 5 Step 1.1.1 Virtual Network Details... 6 Step 1.1.2 DNS Servers
SHAREPOINT 2013 IN INFRASTRUCTURE AS A SERVICE Contents Introduction... 3 Step 1 Create Azure Components... 5 Step 1.1 Virtual Network... 5 Step 1.1.1 Virtual Network Details... 6 Step 1.1.2 DNS Servers
158.738. Implementation & Management of Systems Security. Amavax Project. Ethical Hacking Challenge. Group Project By
 158.738 Implementation & Management of Systems Security Amavax Project Ethical Hacking Challenge Group Project By Nawed Rajeh Mansour Kavin Khan Al Gamdi Al Harthi Palanavel The Amavax project required
158.738 Implementation & Management of Systems Security Amavax Project Ethical Hacking Challenge Group Project By Nawed Rajeh Mansour Kavin Khan Al Gamdi Al Harthi Palanavel The Amavax project required
Quick Scan Features Setup Guide. Scan to E-mail Setup. See also: System Administration Guide: Contains details about E-mail setup.
 Quick Scan Features Setup Guide XE3024EN0-2 This guide includes instructions for: Scan to E-mail Setup on page 1 Scan to Mailbox Setup on page 6 Network Scanning Setup on page 9 Scan to PC Setup on page
Quick Scan Features Setup Guide XE3024EN0-2 This guide includes instructions for: Scan to E-mail Setup on page 1 Scan to Mailbox Setup on page 6 Network Scanning Setup on page 9 Scan to PC Setup on page
SOS SO S O n O lin n e lin e Bac Ba kup cku ck p u USER MANUAL
 SOS Online Backup USER MANUAL HOW TO INSTALL THE SOFTWARE 1. Download the software from the website: http://www.sosonlinebackup.com/download_the_software.htm 2. Click Run to install when promoted, or alternatively,
SOS Online Backup USER MANUAL HOW TO INSTALL THE SOFTWARE 1. Download the software from the website: http://www.sosonlinebackup.com/download_the_software.htm 2. Click Run to install when promoted, or alternatively,
Using. Microsoft Virtual PC. Page 1
 Using Microsoft Virtual PC T4 Page 1 Microsoft Virtual PC Microsoft Virtual PC allows multiple Guest Operating Systems (Virtual Machines) to run using the resources of the Host Operating System (The PC
Using Microsoft Virtual PC T4 Page 1 Microsoft Virtual PC Microsoft Virtual PC allows multiple Guest Operating Systems (Virtual Machines) to run using the resources of the Host Operating System (The PC
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Wanos on Hyper-V Comprehensive guide for a complete lab
 Wanos on Hyper-V Comprehensive guide for a complete lab This document will guide the user in setting up a Wanos appliance using Hyper-V on a Microsoft Windows Server 2012 R2. Four Virtual Machines will
Wanos on Hyper-V Comprehensive guide for a complete lab This document will guide the user in setting up a Wanos appliance using Hyper-V on a Microsoft Windows Server 2012 R2. Four Virtual Machines will
Accessing RCS IBM Console in Windows Using Linux Virtual Machine
 Accessing RCS IBM Console in Windows Using Linux Virtual Machine For Graphics Simulation Experiment, Real Time Applications, ECSE 4760 Quan Wang Department of ECSE, Rensselaer Polytechnic Institute March,
Accessing RCS IBM Console in Windows Using Linux Virtual Machine For Graphics Simulation Experiment, Real Time Applications, ECSE 4760 Quan Wang Department of ECSE, Rensselaer Polytechnic Institute March,
Pearl Echo Installation Checklist
 Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Pearl Echo Installation Checklist Use this checklist to enter critical installation and setup information that will be required to install Pearl Echo in your network. For detailed deployment instructions
Accessing your Staff (N and O drive) files from off campus
 Accessing your Staff (N and O drive) files from off campus It is possible to access your N and O drive files while you are off campus, for example whilst working from home or travelling. This document
Accessing your Staff (N and O drive) files from off campus It is possible to access your N and O drive files while you are off campus, for example whilst working from home or travelling. This document
Online Backup Client User Manual
 Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
NAS 249 Virtual Machine Configuration with VirtualBox
 NAS 249 Virtual Machine Configuration with VirtualBox Configure and run Virtual Machines on ASUSTOR Portal with VirtualBox A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you
NAS 249 Virtual Machine Configuration with VirtualBox Configure and run Virtual Machines on ASUSTOR Portal with VirtualBox A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you
LOCKSS on LINUX. CentOS6 Installation Manual 08/22/2013
 LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
Core Protection for Virtual Machines 1
 Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
Core Protection for Virtual Machines 1 Comprehensive Threat Protection for Virtual Environments. Installation Guide e Endpoint Security Trend Micro Incorporated reserves the right to make changes to this
Eclipse installation, configuration and operation
 Eclipse installation, configuration and operation This document aims to walk through the procedures to setup eclipse on different platforms for java programming and to load in the course libraries for
Eclipse installation, configuration and operation This document aims to walk through the procedures to setup eclipse on different platforms for java programming and to load in the course libraries for
Lab Objectives & Turn In
 Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
Student installation of TinyOS
 Jan.12, 2014 Author: Rahav Dor Student installation of TinyOS TinyOs install Automatic installation... 1 Get Linux... 2 Install Ubuntu on a Virtual Machine... 2 Install Ubuntu on VMware... 2 Installing
Jan.12, 2014 Author: Rahav Dor Student installation of TinyOS TinyOs install Automatic installation... 1 Get Linux... 2 Install Ubuntu on a Virtual Machine... 2 Install Ubuntu on VMware... 2 Installing
HOWTO: Set up a Vyatta device with ThreatSTOP in router mode
 HOWTO: Set up a Vyatta device with ThreatSTOP in router mode Overview This document explains how to set up a minimal Vyatta device in a routed configuration and then how to apply ThreatSTOP to it. It is
HOWTO: Set up a Vyatta device with ThreatSTOP in router mode Overview This document explains how to set up a minimal Vyatta device in a routed configuration and then how to apply ThreatSTOP to it. It is
owncloud Configuration and Usage Guide
 owncloud Configuration and Usage Guide This guide will assist you with configuring and using YSUʼs Cloud Data storage solution (owncloud). The setup instructions will include how to navigate the web interface,
owncloud Configuration and Usage Guide This guide will assist you with configuring and using YSUʼs Cloud Data storage solution (owncloud). The setup instructions will include how to navigate the web interface,
Download Virtualization Software Download a Linux-based OS Creating a Virtual Machine using VirtualBox: VM name
 Download Virtualization Software You will first need to download and install a virtualization product. This will allow you to create a virtual machine which you can install a Linux distribution on. I recommend
Download Virtualization Software You will first need to download and install a virtualization product. This will allow you to create a virtual machine which you can install a Linux distribution on. I recommend
The 2013 Experimental Warning Program (EWP) Virtual Weather Event Simulator (WES) Windows & Linux Installation Documentation
 The 2013 Experimental Warning Program (EWP) Virtual Weather Event Simulator (WES) Windows & Linux Installation Documentation National Severe Storms Laboratory (NSSL) Norman, OK Contents I WINDOWS CONFIGURATION
The 2013 Experimental Warning Program (EWP) Virtual Weather Event Simulator (WES) Windows & Linux Installation Documentation National Severe Storms Laboratory (NSSL) Norman, OK Contents I WINDOWS CONFIGURATION
PaperStream Connect. Setup Guide. Version 1.0.0.0. Copyright Fujitsu
 PaperStream Connect Setup Guide Version 1.0.0.0 Copyright Fujitsu 2014 Contents Introduction to PaperStream Connect... 2 Setting up PaperStream Capture to Release to Cloud Services... 3 Selecting a Cloud
PaperStream Connect Setup Guide Version 1.0.0.0 Copyright Fujitsu 2014 Contents Introduction to PaperStream Connect... 2 Setting up PaperStream Capture to Release to Cloud Services... 3 Selecting a Cloud
SysAidTM Freeware Installation Guide
 SysAidTM Freeware Installation Guide Document Updated: 10 November 2009 Introduction SysAid free edition is built for organizations with fewer than 100 computers and users. This document will help you
SysAidTM Freeware Installation Guide Document Updated: 10 November 2009 Introduction SysAid free edition is built for organizations with fewer than 100 computers and users. This document will help you
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Hallpass Instructions for Connecting to Mac with a Mac
 Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
PowerPanel Business Edition Installation Guide
 PowerPanel Business Edition Installation Guide For Automatic Transfer Switch Rev. 5 2015/12/2 Table of Contents Introduction... 3 Hardware Installation... 3 Install PowerPanel Business Edition Software...
PowerPanel Business Edition Installation Guide For Automatic Transfer Switch Rev. 5 2015/12/2 Table of Contents Introduction... 3 Hardware Installation... 3 Install PowerPanel Business Edition Software...
Quick Deployment: Step-by-step instructions to deploy the SampleApp Virtual Machine v406
 Quick Deployment: Step-by-step instructions to deploy the SampleApp Virtual Machine v406 Note: additional supplemental documentation is annotated by Visit us on YouTube at Oracle BI TECHDEMOs for dozens
Quick Deployment: Step-by-step instructions to deploy the SampleApp Virtual Machine v406 Note: additional supplemental documentation is annotated by Visit us on YouTube at Oracle BI TECHDEMOs for dozens
IP Camera Centralization Management. Client Application. (IPCMonitor) May, 2010 Version 1.1. User Manual
 IP Camera Centralization Management Client Application (IPCMonitor) May, 2010 Version 1.1 User Manual INDEX 1 I ntr o d u c ti o n...3 2 C o m p u t e r R e q uir e m e n t...3 3 I n st all ati o n...4
IP Camera Centralization Management Client Application (IPCMonitor) May, 2010 Version 1.1 User Manual INDEX 1 I ntr o d u c ti o n...3 2 C o m p u t e r R e q uir e m e n t...3 3 I n st all ati o n...4
WA2192 Introduction to Big Data and NoSQL. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2192 Introduction to Big Data and NoSQL Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2192 Introduction to Big Data and NoSQL Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2102 Web Application Programming with Java EE 6 - WebSphere 8.5 - RAD 8.5. Classroom Setup Guide. Web Age Solutions Inc. Web Age Solutions Inc.
 WA2102 Web Application Programming with Java EE 6 - WebSphere 8.5 - RAD 8.5 Classroom Setup Guide Web Age Solutions Inc. Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3
WA2102 Web Application Programming with Java EE 6 - WebSphere 8.5 - RAD 8.5 Classroom Setup Guide Web Age Solutions Inc. Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3
Introduction. Installation of SE S AM E BARCODE virtual machine distribution. (Windows / Mac / Linux)
 Installation of SE S AM E BARCODE virtual machine distribution (Windows / Mac / Linux) Introduction A "virtual machine" is a fake computer within a true one. An underlying software (here VirtualBox) is
Installation of SE S AM E BARCODE virtual machine distribution (Windows / Mac / Linux) Introduction A "virtual machine" is a fake computer within a true one. An underlying software (here VirtualBox) is
How to use SURA in three simple steps:
 How to use SURA in three simple steps: Most of SURA s functionality can be accessed through these three steps. 1) Download SURA to your computer Go to the SU Downloads page to obtain the SURA utility.
How to use SURA in three simple steps: Most of SURA s functionality can be accessed through these three steps. 1) Download SURA to your computer Go to the SU Downloads page to obtain the SURA utility.
User guide. Business Email
 User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
Accessing vlabs using the VMware Horizon View Client for OSX
 Accessing vlabs using the VMware Horizon View Client for OSX This document will demonstrate how to download, install, and connect to a virtual lab desktop from a personal Mac OSX computer using the VMware
Accessing vlabs using the VMware Horizon View Client for OSX This document will demonstrate how to download, install, and connect to a virtual lab desktop from a personal Mac OSX computer using the VMware
13.1 Backup virtual machines running on VMware ESXi / ESX Server
 13 Backup / Restore VMware Virtual Machines Tomahawk Pro This chapter describes how to backup and restore virtual machines running on VMware ESX, ESXi Server or VMware Server 2.0. 13.1 Backup virtual machines
13 Backup / Restore VMware Virtual Machines Tomahawk Pro This chapter describes how to backup and restore virtual machines running on VMware ESX, ESXi Server or VMware Server 2.0. 13.1 Backup virtual machines
ISERink Installation Guide
 ISERink Installation Guide Version 1.1 January 27, 2015 First developed to support cyber defense competitions (CDCs), ISERink is a virtual laboratory environment that allows students an opportunity to
ISERink Installation Guide Version 1.1 January 27, 2015 First developed to support cyber defense competitions (CDCs), ISERink is a virtual laboratory environment that allows students an opportunity to
SSL VPN Setup for Windows
 SSL VPN Setup for Windows SSL VPN allows you to connect from off campus to access campus resources such as Outlook email client, file sharing and remote desktop. These instructions will guide you through
SSL VPN Setup for Windows SSL VPN allows you to connect from off campus to access campus resources such as Outlook email client, file sharing and remote desktop. These instructions will guide you through
Lab 9: Pen Testing (NESSUS)
 Lab 9: Pen Testing (NESSUS) Aim: To provide a foundation in using NESSUS for vulnerability scanning. Time to complete: Up to 90 minutes. Activities: Complete Lab 9: Introduction to NESSUS. Complete Test
Lab 9: Pen Testing (NESSUS) Aim: To provide a foundation in using NESSUS for vulnerability scanning. Time to complete: Up to 90 minutes. Activities: Complete Lab 9: Introduction to NESSUS. Complete Test
APPLICATION NOTE. How to build pylon applications for ARM
 APPLICATION NOTE Version: 01 Language: 000 (English) Release Date: 31 January 2014 Application Note Table of Contents 1 Introduction... 2 2 Steps... 2 1 Introduction This document explains how pylon applications
APPLICATION NOTE Version: 01 Language: 000 (English) Release Date: 31 January 2014 Application Note Table of Contents 1 Introduction... 2 2 Steps... 2 1 Introduction This document explains how pylon applications
Deploy the ExtraHop Discover Appliance with Hyper-V
 Deploy the ExtraHop Discover Appliance with Hyper-V 2016 ExtraHop Networks, Inc. All rights reserved. This manual, in whole or in part, may not be reproduced, translated, or reduced to any machine-readable
Deploy the ExtraHop Discover Appliance with Hyper-V 2016 ExtraHop Networks, Inc. All rights reserved. This manual, in whole or in part, may not be reproduced, translated, or reduced to any machine-readable
How To Set Up a VPN Server Using a Mac
 How To Set Up a VPN Server Using a Mac How To Set Up a VPN Server Using a Mac 1 How to Set Up a VPN Server Using a Mac 1.1 1.2 1.3 1.4 1.5 1.6 1.7 1.8 1.9 1.10 Introduction 4 SECTION 1 - Setting Up a Static
How To Set Up a VPN Server Using a Mac How To Set Up a VPN Server Using a Mac 1 How to Set Up a VPN Server Using a Mac 1.1 1.2 1.3 1.4 1.5 1.6 1.7 1.8 1.9 1.10 Introduction 4 SECTION 1 - Setting Up a Static
Desktop : Ubuntu 10.04 Desktop, Ubuntu 12.04 Desktop Server : RedHat EL 5, RedHat EL 6, Ubuntu 10.04 Server, Ubuntu 12.04 Server, CentOS 5, CentOS 6
 201 Datavoice House, PO Box 267, Stellenbosch, 7599 16 Elektron Avenue, Technopark, Tel: +27 218886500 Stellenbosch, 7600 Fax: +27 218886502 Adept Internet (Pty) Ltd. Reg. no: 1984/01310/07 VAT No: 4620143786
201 Datavoice House, PO Box 267, Stellenbosch, 7599 16 Elektron Avenue, Technopark, Tel: +27 218886500 Stellenbosch, 7600 Fax: +27 218886502 Adept Internet (Pty) Ltd. Reg. no: 1984/01310/07 VAT No: 4620143786
