Automatic Network Bandwidth Control Application for Linux-based Internet Connections
|
|
|
- Dylan McCormick
- 10 years ago
- Views:
Transcription
1 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 1 Automatic Network Bandwidth Control Application for Linux-based Internet Connections Korinto Miguel G. Aguinaldo and Joseph Anthony C. Hermocilla. A. Significance of the Study I. INTRODUCTION With the advent of data sharing and synchronization over the internet, many applications have become dependent on bandwidth allocation in order to function properly. Much of current user-friendly software requires frequent to constant internet connection to fully realize their primary function. The usual examples of this are real-time network games such as World of Warcraft and BitTorrent services. These kinds of programs may be given a larger bandwidth allocation, depending on their setting. In a network of computers using a common port gateway, a larger bandwidth allocation for one computer usually generates smaller bandwidth allocation for others. Bandwidth control or traffic shaping is a necessity in maintaining a fair bit-rate for all computers in the network. Through bandwidth control, the bit-rate of a computer can be throttled down in order to give larger bandwidth allocations for other computers. The most important task in network administration is to regulate the connection of the network to internet services and to every connected computer. It is the prerogative of the administrator to be able to know how he or she will achieve a balanced bit-rate for all of the computers and when a computers connection should be sped up or throttled down. Recent Linux distributions have the shell command tc which allows the user to filter and throttle network traffic. However, this tool may present confusion to those who are new to networking concepts because its command syntax may be complicated and hard to understand. The purpose of this project is to produce a user-friendly application that serves as an command generatorfor tc. The application must present tc syntax in a way that is easily understood, and can be modified by keyboard and mouse. Finally, the application must be able to automatically apply tc commands so that the network administrator will not have to constantly monitor the network so that fair bit-rate for all computers is achieved. B. Statement of the Problem Network administration involves regulation of internet use. There are tools available to do this, but these tools are either difficult to be used or too complex to be understood by Presented to the Faculty of the Institute of Computer Science, University of the Philippines Los Baños in partial fulfillment of the requirements for the Degree of Bachelor of Science in Computer Science inexperienced administrators. A simple program that could integrate known tools such that it enables the administrator to easily maintain fair use of the internet connection is ideal. C. Objectives of the Study The general objective of the Special Problem is to alleviate the difficulties involving network administration. Specifically, the aim is: 1) To develop an application that can automate traffic control; and 2) To develop a user-friendly graphical user interface for the application. II. REVIEW OF LITERATURE Linux-based operating systems is popular in computer networking, especially when it is known that the Linux networking attributes are configured and inspected completely. [1] We can infer that popular, even local, networking services are usually run from Linux servers, especially when the functionalities and instructions for handling these programs are explicitly included in their installation. This allows scrutiny for young network administrators. The other computers will be dependent on the server for their internet connection. The server, or router terminal, may allocate bandwidth to itself and other computers, or dependent terminals, in the network. Imagine that these dependent terminals are being used by members of an organization, as employees or students. Fisher implies that most of these kinds of people usually visit social networking sites such as Facebook and Twitter first before proceeding to the actual purpose of their internet access. [2] Also, commonly during their breaks, these people access sites involving streaming media such as entertainment and news sites, which are usually encountered in the internet. [3] According to a statistic shown by a White Paper from Symantec MessageLabs, sites that has streaming media content is one of the highly preferred to be blocked by administrators, along with advertisement and popup-generating sites. [4] The common awareness of why this happens is because these sites take up a lot of bandwidth. Streaming media and other kinds of download services make up an increasing percentage of traffic in the internet. [5] Such high-bandwidth connections take a toll in local networks, especially when many dependent terminals access these sites at the same time such as during breaks. - c 2011 ICS University of the Philippines Los Baños
2 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 2 When these concurrent signals pass through the gateway(s) handled by the router terminal, a large volume of information may result to collisions such that data is lost and errors occur. [6] It is also known that a constant stream of bytes passing unimpeded through the gateway(s) may cause a slowdown since this stream has its own share of bandwidth. [7] According to Tunnicliffe, the access of certain sites must be regulated in order to optimize the bandwidth share for each computer. [8] Though commercial network traffic control tools available, these software do not present the actual configuration that is done on computers. Furthermore, simple techniques can effectively maximize bandwidth allocation with little overhead. [9] A. Theoretical Framework III. MATERIALS AND METHODS 1) Bandwidth: Bandwitdh, is a measure that describes the rate of information transmitted over a connection. [10] This term is commonly used especially when multiple users share a common connection to the internet. In this setup, each user has a share of the bandwidth. However, as as a user starts more programs to connect to the internet, it is possible that these programs expand the computer s bandwidth requirement. A simple analogy of this is being the number of lanes in a highway. More lanes (more bandwidth) mean more cars can pass through (more data can be transferred). [11] The problem arises when many computers connect to the internet at the same time, such that the network cannot fulfill the requirements of all the computers. When this happens the administrator must regulate the network traffic. 2) Traffic Control: Traffic control is to manage the network traffic to maximize the use of network resources and reduce information loss due to congestion. [12] Congestion results from having too many concurrent connections, usually on a few ports, at the same time, so as to exceed the connection limit of the network devices. Congestion may cause loss of packets, since a congested connection may sometimes not serve all the packets that passes through it. In the previous analogy, congestion arises when too many cars are to pass through one highway, and the highway cannot possibly accomodate all of them (Fig. 1). Network administrators must regulate the connections of the computers connected to the internet so that all computers will have a fair share of the bandwidth. The essence of traffic control is controlling how packets are trasmitted. When a Linux computer needs to send or receive packets, it decides which packets are to be sent, delayed or dropped. A buffer or queue where packets that are needed to be trasmitted are stored momentarily is used to achieve this effect. How the packets are stored in this queue is defined by a queueing discipline and is configurable in Linux systems. An example of this in Linux is Stochastic Fairness Queuing, where there are sub-queues and each sub-queue gets a turn to send their packets in a round robin fashion. [13] Setting the queueing discipline for a device or computer also allows setting its transmission rate. 3) Java: The entire application will be consisting of a Linux service and a web application to control it. The service Fig. 1. Congestion. Too many cars wanting to pass will have a hard time going through. will be implemented using Java and the web application will be built using Google Web Toolkit to have a user-friendly Graphical User Interface (GUI). The web application will use Java Servlets to pass commands from the web application host to the service. 4) Command line tool tc: Traffic control in Linux is achieved through the command line tool tc. The tool can show and modify traffic control settings of other computers in the network, and can assign queuing disciplines to devices. 5) Command line tool netstat: This command line tool displays the network connections of a computer. The actual command used is netstat -Wn -tu B. Date and Place of the Study Software construction will be done from November 2011 to February The software will be tested at the laboratories of the Institute of Computer Science, University of the Philippines Los Baños. C. Design and Implementation 1) GUI Design: The overall web application design is constrained by the capabilities of the Google Web Toolkit (GWT), browser Javascript limitations, and the host serving the web application. The GUI is composed of pages handled by clickable tabs. Fig. 2 will illustrate. Though the internal structure of the client-side GUI is design to be deployed to any web server supporting Java Servlets as a Web Archive file, the product application s JAR file contains Jetty, a small web server written in Java, to launch the web application. HTML pages and GWT-compiled
3 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 3 Fig. 2. Users can select a page by clicking on tabs. Javascript files are put in a folder so they can be loaded by Jetty. The following items can only be viewed in the web application. 2) Welcome Page: In the welcome page, information about the application and the current user is displayed (Fig. 3). If there is no user logged in, the welcome page is grayed out and a log-in dialog box is on top (Fig. 4). Fig. 4. Welcome page with a login dialog box. Each type has a corresponding box, which contents show te current command s parameters and what can be done to that particular type. In the current implementation, tc QDisc, Class and Filter boxes are colored green, blue, and yellow respectively. These boxes are arranged in a tree-like manner, nesting boxes of dependent tc types if necessary. See Fig. 5 for an example. Fig. 3. Welcome page, when a user is logged in. 3) QDiscs and Classes Page: In the QDiscs and Classes Page, the user can edit the tc configuration of the current selected device. The current selected device can be changed from a drop-down list. Each tc configuration command is of three types: 1) tc qdisc (parameters...) 2) tc class (parameters...) 3) tc filter (paramaters...) Fig. 5. A device s tc configuration is shown. The user can edit the contents of each box by clicking the modify button. The parameters of each box is set through a dialog box. Fig. 6 shows an example where a tc QDisc box is edited. The tc configuration of the current selected device can be
4 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 4 5) Actions Page: The Actions page shows criteria each client is tested, the tc configuration used when these criteria is satisfied, and the priority values of this pair (Fig. 9). The user can add and remove entries from this page, and by adding a row, the user can select which tc configuration is to be selected and applied and the criteria for its selection. Fig. 6. Editing a QDisc. saved into the MySQL database as a template. This can be done by clicking tne Save Tree button. Alternatively, the user can also apply previously-saved teemplates to the current selected devices by clicking the Load Tree button and selecting the template name from the dialog box that pops up (see Fig. 7). Fig. 9. A list of actions. Fig. 7. Loading a template. 4) Clients Page: The clients page displays a list of clients that runs a small Linux daemon that sends the results of netstat through a socket. This daemon is contained in a its own JAR file, so that it does not take up space for Java classes it does not use. This daemon is important in the automation process, since this gives the data that is used to know which tc configuration is to be applied. The user may click a client entry s corresponding netstat button anytime to show the current active internet connections (Fig.8). Fig. 8. Using netstat. The Actions page shows the data used in automating the process of applying the tc configuration of a device. For example, anytime a computer in the network is using a Voiceover-Internet Protocol service, we would naturally want a fast internet connection for that computer. Given that the IP addresses and port numbers of the connection is known, the application must be able to detect this information and apply the necessary tc configuration if any. The logic for this is simplified by the following: 1) Get netstat data from each client 2) Find an action staisfying all IP address and port numbercriteria with the highest priority 3) Get tc configuration script and apply 4) Wait for a while and then go back to 1 IV. RESULTS AND DISCUSSION To test the application, two JAR files are made: autotc.jar, which contains the web application and the daemon that automatically apllies tc, and autotc-client.jar which contains the daemon that sends netstat results. First, the file autotc.jar is run on the local machine (we shall call this computer server ). A copy of autotc-client.jar is given to a computer (we shall this client ) with an IP address of and the daemon and the web application are run. The client is then registered into the web application (Fig. 8). In this setup, it is not needed that the client is dependent on the server for its internet connection, since we must only prove that two things are running correctly: 1) That the server is able to get the netstat data from the client, and 2) That the server is able to change the tc configuration based on the netstat data.
5 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 5 Checking if the actual bitrate of the internet connections of clients has changed is not important, since that is restricted to the abilities of the tc command. What the application will consider is whether the tc script generated is run successfully or not. In the test, an action was created to detect the IP address and set the template tbf100bps when the server s daemon detects it from the client (Fig. 10). Fig. 12. The tc configuration as shown from the terminal before accessing Fig. 10. Setting an action. Fig. 11 shows the tc configuration from the web application (on a browser) and Fig. 12 shows the current tc configuration from the terminal. Fig. 13. How the tc configuration looks like after accessing configuration for it. Furthermore, the application has fulfilled its primary objectives, which is being able to automatically apply traffic control commands and having a user-friendly GUI. ACKNOWLEDGMENT Many thanks to my adviser, Joseph Anthony Hermocilla, for his invaluable support for my Undergraduate Special Problem. Fig. 11. How the tc configuration looks like before accessing While the client s daemon is running, it made an access to After about three seconds, the tc configuration on the server changed as shown by Fig. 13 and Fig. 14. V. CONCLUSION As we have seen in the test, the application is able to detect the client s internet connections and apply the necessary tc REFERENCES [1] B. McCarty, Learning Debian GNU/Linux. O Reilly Media. [2] L. Fisher, Study shows social network traffic is the least engaged, [3] How engaged is traffic from social sites? [4] Bandwidth bandits, White Paper, Symantec MessageLabs, Apr [5] J. Kirk, Study: Other network traffic surpassing p2p growth, [6] J. Awe, The five most common network problems,
6 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 6 Fig. 14. The tc configuration as shown from the terminal after accessing [7] S. Lowe, Common causes of network slowdowns, htm, [8] M. J. Tunnicliffe, The measurement of bandwidth: A simulation study, [9] M. Marcon, M. Dischinger, K. P. Gummadi, and A. Vahdat, The local and global effects of traffic shaping in the internet, in Communication Systems and Networks (COMSNETS), 2011 Third International Conference on, Bangalore, Jan. 4 8, 2011, paper /COM- SNETS , pp [10] What is bandwidth? [11] Bandwidth explained, [12] Traffic shaping with linux, shaping with linux.php. [13] J. P. C. Ngo, Qontrol: A linux-based network bandwidth control application, Institute of Computer Science, University of the Philippines Los Baños, BSCS Special Problem Report. Korinto Miguel G. Aguinaldo is an undergraduate student under the BS Computer Science program of the Institute of Computer Science, University of the Philippines Los Baños. He likes programming, the Internet, and well-made coffee.
Automation of Smartphone Traffic Generation in a Virtualized Environment. Tanya Jha Rashmi Shetty
 Automation of Smartphone Traffic Generation in a Virtualized Environment Tanya Jha Rashmi Shetty Abstract Scalable and comprehensive analysis of rapidly evolving mobile device application traffic is extremely
Automation of Smartphone Traffic Generation in a Virtualized Environment Tanya Jha Rashmi Shetty Abstract Scalable and comprehensive analysis of rapidly evolving mobile device application traffic is extremely
Version 1.0 January 2011. Xerox Phaser 3635MFP Extensible Interface Platform
 Version 1.0 January 2011 Xerox Phaser 3635MFP 2011 Xerox Corporation. XEROX and XEROX and Design are trademarks of Xerox Corporation in the United States and/or other countries. Changes are periodically
Version 1.0 January 2011 Xerox Phaser 3635MFP 2011 Xerox Corporation. XEROX and XEROX and Design are trademarks of Xerox Corporation in the United States and/or other countries. Changes are periodically
14.1. bs^ir^qfkd=obcib`qflk= Ñçê=emI=rkfuI=~åÇ=léÉåsjp=eçëíë
 14.1 bs^ir^qfkd=obcib`qflk= Ñçê=emI=rkfuI=~åÇ=léÉåsjp=eçëíë bî~äì~íáåö=oéñäéåíáçå=ñçê=emi=rkfui=~åç=lééåsjp=eçëíë This guide walks you quickly through key Reflection features. It covers: Getting Connected
14.1 bs^ir^qfkd=obcib`qflk= Ñçê=emI=rkfuI=~åÇ=léÉåsjp=eçëíë bî~äì~íáåö=oéñäéåíáçå=ñçê=emi=rkfui=~åç=lééåsjp=eçëíë This guide walks you quickly through key Reflection features. It covers: Getting Connected
The Problem with TCP. Overcoming TCP s Drawbacks
 White Paper on managed file transfers How to Optimize File Transfers Increase file transfer speeds in poor performing networks FileCatalyst Page 1 of 6 Introduction With the proliferation of the Internet,
White Paper on managed file transfers How to Optimize File Transfers Increase file transfer speeds in poor performing networks FileCatalyst Page 1 of 6 Introduction With the proliferation of the Internet,
Wakanda Studio Features
 Wakanda Studio Features Discover the many features in Wakanda Studio. The main features each have their own chapters and other features are documented elsewhere: Wakanda Server Administration Data Browser
Wakanda Studio Features Discover the many features in Wakanda Studio. The main features each have their own chapters and other features are documented elsewhere: Wakanda Server Administration Data Browser
2X ApplicationServer & LoadBalancer Manual
 2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: [email protected] Information in this document is subject to change without notice. Companies,
2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: [email protected] Information in this document is subject to change without notice. Companies,
Eucalyptus LSS: Load-Based Scheduling on Virtual Servers Using Eucalyptus Private Cloud
 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 1 Eucalyptus LSS: Load-Based Scheduling on Virtual Servers Using Eucalyptus Private Cloud Shenlene A. Cabigting and Prof. Joseph Anthony C. Hermocilla
CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 1 Eucalyptus LSS: Load-Based Scheduling on Virtual Servers Using Eucalyptus Private Cloud Shenlene A. Cabigting and Prof. Joseph Anthony C. Hermocilla
Gigabyte Content Management System Console User s Guide. Version: 0.1
 Gigabyte Content Management System Console User s Guide Version: 0.1 Table of Contents Using Your Gigabyte Content Management System Console... 2 Gigabyte Content Management System Key Features and Functions...
Gigabyte Content Management System Console User s Guide Version: 0.1 Table of Contents Using Your Gigabyte Content Management System Console... 2 Gigabyte Content Management System Key Features and Functions...
Attix5 Pro Server Edition
 Attix5 Pro Server Edition V7.0.3 User Manual for Linux and Unix operating systems Your guide to protecting data with Attix5 Pro Server Edition. Copyright notice and proprietary information All rights reserved.
Attix5 Pro Server Edition V7.0.3 User Manual for Linux and Unix operating systems Your guide to protecting data with Attix5 Pro Server Edition. Copyright notice and proprietary information All rights reserved.
How it works. b) IP addresses are allocated dynamically and may change any time.
 NeoRouter is a cross-platform zero-configuration VPN solution that securely connects Windows, Mac and Linux computers at any locations into a virtual LAN and provides a networking platform for various
NeoRouter is a cross-platform zero-configuration VPN solution that securely connects Windows, Mac and Linux computers at any locations into a virtual LAN and provides a networking platform for various
How To Test Your Web Site On Wapt On A Pc Or Mac Or Mac (Or Mac) On A Mac Or Ipad Or Ipa (Or Ipa) On Pc Or Ipam (Or Pc Or Pc) On An Ip
 Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
Acronis Backup & Recovery 10 Advanced Server Virtual Edition. Quick Start Guide
 Acronis Backup & Recovery 10 Advanced Server Virtual Edition Quick Start Guide Table of contents 1 Main components...3 2 License server...3 3 Supported operating systems...3 3.1 Agents... 3 3.2 License
Acronis Backup & Recovery 10 Advanced Server Virtual Edition Quick Start Guide Table of contents 1 Main components...3 2 License server...3 3 Supported operating systems...3 3.1 Agents... 3 3.2 License
Applications. Network Application Performance Analysis. Laboratory. Objective. Overview
 Laboratory 12 Applications Network Application Performance Analysis Objective The objective of this lab is to analyze the performance of an Internet application protocol and its relation to the underlying
Laboratory 12 Applications Network Application Performance Analysis Objective The objective of this lab is to analyze the performance of an Internet application protocol and its relation to the underlying
Web Dashboard User Guide
 Web Dashboard User Guide Version 10.2 The software supplied with this document is the property of RadView Software and is furnished under a licensing agreement. Neither the software nor this document may
Web Dashboard User Guide Version 10.2 The software supplied with this document is the property of RadView Software and is furnished under a licensing agreement. Neither the software nor this document may
Fax User Guide 07/31/2014 USER GUIDE
 Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Integrate Websense Web Security Gateway (WSG)
 Integrate Websense Web Security Gateway (WSG) EventTracker v7.x Publication Date: June 2, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
Integrate Websense Web Security Gateway (WSG) EventTracker v7.x Publication Date: June 2, 2014 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com Abstract This guide provides instructions
DiskPulse DISK CHANGE MONITOR
 DiskPulse DISK CHANGE MONITOR User Manual Version 7.9 Oct 2015 www.diskpulse.com [email protected] 1 1 DiskPulse Overview...3 2 DiskPulse Product Versions...5 3 Using Desktop Product Version...6 3.1 Product
DiskPulse DISK CHANGE MONITOR User Manual Version 7.9 Oct 2015 www.diskpulse.com [email protected] 1 1 DiskPulse Overview...3 2 DiskPulse Product Versions...5 3 Using Desktop Product Version...6 3.1 Product
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
CONNECTING TO DEPARTMENT OF COMPUTER SCIENCE SERVERS BOTH FROM ON AND OFF CAMPUS USING TUNNELING, PuTTY, AND VNC Client Utilities
 CONNECTING TO DEPARTMENT OF COMPUTER SCIENCE SERVERS BOTH FROM ON AND OFF CAMPUS USING TUNNELING, PuTTY, AND VNC Client Utilities DNS name: turing.cs.montclair.edu -This server is the Departmental Server
CONNECTING TO DEPARTMENT OF COMPUTER SCIENCE SERVERS BOTH FROM ON AND OFF CAMPUS USING TUNNELING, PuTTY, AND VNC Client Utilities DNS name: turing.cs.montclair.edu -This server is the Departmental Server
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
Getting Started with PRTG Network Monitor 2012 Paessler AG
 Getting Started with PRTG Network Monitor 2012 Paessler AG All rights reserved. No parts of this work may be reproduced in any form or by any means graphic, electronic, or mechanical, including photocopying,
Getting Started with PRTG Network Monitor 2012 Paessler AG All rights reserved. No parts of this work may be reproduced in any form or by any means graphic, electronic, or mechanical, including photocopying,
Elluminate Live! Access Guide. Page 1 of 7
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
Quick Start Guide. Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca!
 Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Scan to E-mail Quick Setup Guide
 Xerox WorkCentre M118i Scan to E-mail Quick Setup Guide 701P42574 This guide provides a quick reference for setting up the Scan to E-mail feature on the Xerox WorkCentre M118i. It includes procedures for:
Xerox WorkCentre M118i Scan to E-mail Quick Setup Guide 701P42574 This guide provides a quick reference for setting up the Scan to E-mail feature on the Xerox WorkCentre M118i. It includes procedures for:
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Integration of Voice over Internet Protocol Experiment in Computer Engineering Technology Curriculum
 Integration of Voice over Internet Protocol Experiment in Computer Engineering Technology Curriculum V. Rajaravivarma and Farid Farahmand Computer Electronics and Graphics Technology School of Technology,
Integration of Voice over Internet Protocol Experiment in Computer Engineering Technology Curriculum V. Rajaravivarma and Farid Farahmand Computer Electronics and Graphics Technology School of Technology,
Docufide Client Installation Guide for Windows
 Docufide Client Installation Guide for Windows This document describes the installation and operation of the Docufide Client application at the sending school installation site. The intended audience is
Docufide Client Installation Guide for Windows This document describes the installation and operation of the Docufide Client application at the sending school installation site. The intended audience is
Version 0.1 June 2010. Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP)
 Version 0.1 June 2010 Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP) Thank you for choosing the Xerox WorkCentre 7120. Table of Contents Introduction.........................................
Version 0.1 June 2010 Xerox WorkCentre 7120 Fax over Internet Protocol (FoIP) Thank you for choosing the Xerox WorkCentre 7120. Table of Contents Introduction.........................................
Frequently Asked Questions
 Frequently Asked Questions 1. Q: What is the Network Data Tunnel? A: Network Data Tunnel (NDT) is a software-based solution that accelerates data transfer in point-to-point or point-to-multipoint network
Frequently Asked Questions 1. Q: What is the Network Data Tunnel? A: Network Data Tunnel (NDT) is a software-based solution that accelerates data transfer in point-to-point or point-to-multipoint network
Introduction to Network Security Lab 1 - Wireshark
 Introduction to Network Security Lab 1 - Wireshark Bridges To Computing 1 Introduction: In our last lecture we discussed the Internet the World Wide Web and the Protocols that are used to facilitate communication
Introduction to Network Security Lab 1 - Wireshark Bridges To Computing 1 Introduction: In our last lecture we discussed the Internet the World Wide Web and the Protocols that are used to facilitate communication
AXIGEN Mail Server Reporting Service
 AXIGEN Mail Server Reporting Service Usage and Configuration The article describes in full details how to properly configure and use the AXIGEN reporting service, as well as the steps for integrating it
AXIGEN Mail Server Reporting Service Usage and Configuration The article describes in full details how to properly configure and use the AXIGEN reporting service, as well as the steps for integrating it
Online Backup Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
iview (v2.0) Administrator Guide Version 1.0
 iview (v2.0) Administrator Guide Version 1.0 Updated 5/2/2008 Overview This administrator guide describes the processes and procedures for setting up, configuring, running and administering the iview Operator
iview (v2.0) Administrator Guide Version 1.0 Updated 5/2/2008 Overview This administrator guide describes the processes and procedures for setting up, configuring, running and administering the iview Operator
P-660R-D Series. ADSL2+ Router. Quick Start Guide. Version 3.40 6/2006 Edition 1
 P-660R-D Series ADSL2+ Router Quick Start Guide Version 3.40 6/2006 Edition 1 Copyright 2006 ZyXEL Communications Corporation. All rights reserved. Overview The P-660R-D is an ADSL router. See your User
P-660R-D Series ADSL2+ Router Quick Start Guide Version 3.40 6/2006 Edition 1 Copyright 2006 ZyXEL Communications Corporation. All rights reserved. Overview The P-660R-D is an ADSL router. See your User
Deploying the BIG-IP LTM with the Cacti Open Source Network Monitoring System
 DEPLOYMENT GUIDE Deploying the BIG-IP LTM with the Cacti Open Source Network Monitoring System Version 1.0 Deploying F5 with Cacti Open Source Network Monitoring System Welcome to the F5 and Cacti deployment
DEPLOYMENT GUIDE Deploying the BIG-IP LTM with the Cacti Open Source Network Monitoring System Version 1.0 Deploying F5 with Cacti Open Source Network Monitoring System Welcome to the F5 and Cacti deployment
IceWarp Server. Log Analyzer. Version 10
 IceWarp Server Log Analyzer Version 10 Printed on 23 June, 2009 i Contents Log Analyzer 1 Quick Start... 2 Required Steps... 2 Optional Steps... 2 Advanced Configuration... 5 Log Importer... 6 General...
IceWarp Server Log Analyzer Version 10 Printed on 23 June, 2009 i Contents Log Analyzer 1 Quick Start... 2 Required Steps... 2 Optional Steps... 2 Advanced Configuration... 5 Log Importer... 6 General...
Getting Started with. Avaya TM VoIP Monitoring Manager
 Getting Started with Avaya TM VoIP Monitoring Manager Contents AvayaTM VoIP Monitoring Manager 5 About This Guide 5 What is VoIP Monitoring Manager 5 Query Endpoints 5 Customize Query to Filter Based
Getting Started with Avaya TM VoIP Monitoring Manager Contents AvayaTM VoIP Monitoring Manager 5 About This Guide 5 What is VoIP Monitoring Manager 5 Query Endpoints 5 Customize Query to Filter Based
Table of Contents. Welcome... 2. Login... 3. Password Assistance... 4. Self Registration... 5. Secure Mail... 7. Compose... 8. Drafts...
 Table of Contents Welcome... 2 Login... 3 Password Assistance... 4 Self Registration... 5 Secure Mail... 7 Compose... 8 Drafts... 10 Outbox... 11 Sent Items... 12 View Package Details... 12 File Manager...
Table of Contents Welcome... 2 Login... 3 Password Assistance... 4 Self Registration... 5 Secure Mail... 7 Compose... 8 Drafts... 10 Outbox... 11 Sent Items... 12 View Package Details... 12 File Manager...
Elluminate Live! Access Guide. Page 1 of 7
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
P-791R v2. Quick Start Guide. G.SHDSL.bis Router DEFAULT LOGIN. Administrator Password 1234. User Password. Version 1.00 4/2007 Edition 1
 P-791R v2 G.SHDSL.bis Router Quick Start Guide Version 1.00 4/2007 Edition 1 DEFAULT LOGIN IP Address http://192.168.1.1 Administrator Password 1234 User Password user Copyright 2007. All rights reserved.
P-791R v2 G.SHDSL.bis Router Quick Start Guide Version 1.00 4/2007 Edition 1 DEFAULT LOGIN IP Address http://192.168.1.1 Administrator Password 1234 User Password user Copyright 2007. All rights reserved.
User Manual. Call Center - Agent Assistant Application
 User Manual Call Center Agent Assistant Application Release 9.1 April 2013 Legal notice: Alcatel, Lucent, AlcatelLucent and the AlcatelLucent logo are trademarks of AlcatelLucent. All other trademarks
User Manual Call Center Agent Assistant Application Release 9.1 April 2013 Legal notice: Alcatel, Lucent, AlcatelLucent and the AlcatelLucent logo are trademarks of AlcatelLucent. All other trademarks
How To Install An Aneka Cloud On A Windows 7 Computer (For Free)
 MANJRASOFT PTY LTD Aneka 3.0 Manjrasoft 5/13/2013 This document describes in detail the steps involved in installing and configuring an Aneka Cloud. It covers the prerequisites for the installation, the
MANJRASOFT PTY LTD Aneka 3.0 Manjrasoft 5/13/2013 This document describes in detail the steps involved in installing and configuring an Aneka Cloud. It covers the prerequisites for the installation, the
Installation and Configuration Guide. Version 5.2
 Installation and Configuration Guide Version 5.2 June 2015 RESTRICTED RIGHTS Use, duplication, or disclosure by the Government is subject to restrictions as set forth in subparagraph (C)(1)(ii) of the
Installation and Configuration Guide Version 5.2 June 2015 RESTRICTED RIGHTS Use, duplication, or disclosure by the Government is subject to restrictions as set forth in subparagraph (C)(1)(ii) of the
Gigabyte Management Console User s Guide (For ASPEED AST 2400 Chipset)
 Gigabyte Management Console User s Guide (For ASPEED AST 2400 Chipset) Version: 1.4 Table of Contents Using Your Gigabyte Management Console... 3 Gigabyte Management Console Key Features and Functions...
Gigabyte Management Console User s Guide (For ASPEED AST 2400 Chipset) Version: 1.4 Table of Contents Using Your Gigabyte Management Console... 3 Gigabyte Management Console Key Features and Functions...
Status Monitoring. Using Drivers by Seagull to Display Printer Status Information WHITE PAPER
 Status Monitoring Using Drivers by Seagull to Display Printer Status Information WHITE PAPER Contents Printer Communications 3 Drivers by Seagull 3 The Seagull Status Monitor 4 Important Benefits 4 Viewing
Status Monitoring Using Drivers by Seagull to Display Printer Status Information WHITE PAPER Contents Printer Communications 3 Drivers by Seagull 3 The Seagull Status Monitor 4 Important Benefits 4 Viewing
SOA Software API Gateway Appliance 7.1.x Administration Guide
 SOA Software API Gateway Appliance 7.1.x Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names,
SOA Software API Gateway Appliance 7.1.x Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names,
CASHNet Secure File Transfer Instructions
 CASHNet Secure File Transfer Instructions Copyright 2009, 2010 Higher One Payments, Inc. CASHNet, CASHNet Business Office, CASHNet Commerce Center, CASHNet SMARTPAY and all related logos and designs are
CASHNet Secure File Transfer Instructions Copyright 2009, 2010 Higher One Payments, Inc. CASHNet, CASHNet Business Office, CASHNet Commerce Center, CASHNet SMARTPAY and all related logos and designs are
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Attix5 Pro Server Edition
 Attix5 Pro Server Edition V7.0.2 User Manual for Mac OS X Your guide to protecting data with Attix5 Pro Server Edition. Copyright notice and proprietary information All rights reserved. Attix5, 2013 Trademarks
Attix5 Pro Server Edition V7.0.2 User Manual for Mac OS X Your guide to protecting data with Attix5 Pro Server Edition. Copyright notice and proprietary information All rights reserved. Attix5, 2013 Trademarks
Orientation Course - Lab Manual
 Orientation Course - Lab Manual Using the Virtual Managed Workplace site for the lab exercises Your instructor will provide the following information before the first lab exercise begins: Your numerical
Orientation Course - Lab Manual Using the Virtual Managed Workplace site for the lab exercises Your instructor will provide the following information before the first lab exercise begins: Your numerical
Comparison of FTP and Signiant
 Comparison of FTP and Signiant An In depth Comparison of FTP with Methodologies from Signiant Ian Hamilton, CTO, Signiant Abstract FTP (File Transfer Protocol) is used to perform file transfers over Internet
Comparison of FTP and Signiant An In depth Comparison of FTP with Methodologies from Signiant Ian Hamilton, CTO, Signiant Abstract FTP (File Transfer Protocol) is used to perform file transfers over Internet
Dell SonicWALL SRA 7.5 Secure Virtual Meeting and Secure Virtual Assist
 Dell SonicWALL SRA 7.5 Secure Virtual Meeting and Secure Virtual Assist Document Scope This document describes how to configure and use the Dell SonicWALL SRA Secure Virtual Meeting feature and the Dell
Dell SonicWALL SRA 7.5 Secure Virtual Meeting and Secure Virtual Assist Document Scope This document describes how to configure and use the Dell SonicWALL SRA Secure Virtual Meeting feature and the Dell
Running a Program on an AVD
 Running a Program on an AVD Now that you have a project that builds an application, and an AVD with a system image compatible with the application s build target and API level requirements, you can run
Running a Program on an AVD Now that you have a project that builds an application, and an AVD with a system image compatible with the application s build target and API level requirements, you can run
2X ApplicationServer & LoadBalancer & VirtualDesktopServer Manual
 2X ApplicationServer & LoadBalancer & VirtualDesktopServer Manual 2X VirtualDesktopServer Contents 1 2X VirtualDesktopServer Contents 2 URL: www.2x.com E-mail: [email protected] Information in this document
2X ApplicationServer & LoadBalancer & VirtualDesktopServer Manual 2X VirtualDesktopServer Contents 1 2X VirtualDesktopServer Contents 2 URL: www.2x.com E-mail: [email protected] Information in this document
Download and Install the Citrix Receiver for Mac/Linux
 Download and Install the Citrix Receiver for Mac/Linux NOTE: WOW can only be used with Internet Explorer for Windows. To accommodate WOW customers using Mac or Linux computers, a Citrix solution was developed
Download and Install the Citrix Receiver for Mac/Linux NOTE: WOW can only be used with Internet Explorer for Windows. To accommodate WOW customers using Mac or Linux computers, a Citrix solution was developed
Log Analyzer Reference
 IceWarp Unified Communications Log Analyzer Reference Version 10.4 Printed on 27 February, 2012 Contents Log Analyzer 1 Quick Start... 2 Required Steps... 2 Optional Steps... 3 Advanced Configuration...
IceWarp Unified Communications Log Analyzer Reference Version 10.4 Printed on 27 February, 2012 Contents Log Analyzer 1 Quick Start... 2 Required Steps... 2 Optional Steps... 3 Advanced Configuration...
Access the Test Here http://myspeed.visualware.com/index.php
 VoIP Speed Test Why run the test? Running a VoIP speed test is an effective way to gauge whether your Internet connection is suitable to run a hosted telephone system using VoIP technology. A number of
VoIP Speed Test Why run the test? Running a VoIP speed test is an effective way to gauge whether your Internet connection is suitable to run a hosted telephone system using VoIP technology. A number of
Websense Web Security Gateway: What to do when a Web site does not load as expected
 Websense Web Security Gateway: What to do when a Web site does not load as expected Websense Support Webinar November 2011 web security data security email security Support Webinars 2009 Websense, Inc.
Websense Web Security Gateway: What to do when a Web site does not load as expected Websense Support Webinar November 2011 web security data security email security Support Webinars 2009 Websense, Inc.
TransNav Management System Documentation. Management Server Guide
 Force10 Networks Inc. TransNav Management System Documentation Management Server Guide Release TN4.2.2 Publication Date: April 2009 Document Number: 800-0006-TN422 Rev. A Copyright 2009 Force10 Networks,
Force10 Networks Inc. TransNav Management System Documentation Management Server Guide Release TN4.2.2 Publication Date: April 2009 Document Number: 800-0006-TN422 Rev. A Copyright 2009 Force10 Networks,
Call Center - Agent Application User Manual
 Forum 700 Call Center Agent Application User Manual Legal notice: Belgacom and the Belgacom logo are trademarks of Belgacom. All other trademarks are the property of their respective owners. The information
Forum 700 Call Center Agent Application User Manual Legal notice: Belgacom and the Belgacom logo are trademarks of Belgacom. All other trademarks are the property of their respective owners. The information
Visual Firewall Rule Builder
 Visual Firewall Rule Builder Eugen PETAC, Ph.D.*, Tudor UDRESCU** * Ovidius University, Constantza Romania Abstract: The paper that is being submitted deals primarily with the implementation of firewall
Visual Firewall Rule Builder Eugen PETAC, Ph.D.*, Tudor UDRESCU** * Ovidius University, Constantza Romania Abstract: The paper that is being submitted deals primarily with the implementation of firewall
EventTracker: Configuring DLA Extension for AWStats report AWStats Reports
 EventTracker: Configuring DLA Extension for AWStats report AWStats Reports Prism Microsystems Corporate Headquarter Date: October 18, 2011 8815 Centre Park Drive Columbia MD 21045 (+1) 410.953.6776 (+1)
EventTracker: Configuring DLA Extension for AWStats report AWStats Reports Prism Microsystems Corporate Headquarter Date: October 18, 2011 8815 Centre Park Drive Columbia MD 21045 (+1) 410.953.6776 (+1)
Billing System: An Accounting Solution for the Private Cloud with Eucalyptus
 CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 1 Billing System: An Accounting Solution for the Private Cloud with Eucalyptus Regelyn T. Bañacia, Chryss Ann A. Belaguin, Rodolfo N. Duldulao, Jr.
CMSC 190 SPECIAL PROBLEM, INSTITUTE OF COMPUTER SCIENCE 1 Billing System: An Accounting Solution for the Private Cloud with Eucalyptus Regelyn T. Bañacia, Chryss Ann A. Belaguin, Rodolfo N. Duldulao, Jr.
Fluke Networks NetFlow Tracker
 Fluke Networks NetFlow Tracker Quick Install Guide for Product Evaluations Pre-installation and Installation Tasks Minimum System Requirements The type of system required to run NetFlow Tracker depends
Fluke Networks NetFlow Tracker Quick Install Guide for Product Evaluations Pre-installation and Installation Tasks Minimum System Requirements The type of system required to run NetFlow Tracker depends
Smartphone Pentest Framework v0.1. User Guide
 Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Applied Security Lab 2: Personal Firewall
 Applied Security Lab 2: Personal Firewall Network Security Tools and Technology: Host-based Firewall/IDS using Sysgate Name: Due Date: Wednesday (March 3, 2010) by 8:00 a.m. Instructions: The Lab 2 Write-up
Applied Security Lab 2: Personal Firewall Network Security Tools and Technology: Host-based Firewall/IDS using Sysgate Name: Due Date: Wednesday (March 3, 2010) by 8:00 a.m. Instructions: The Lab 2 Write-up
A Scalable Network Monitoring and Bandwidth Throttling System for Cloud Computing
 A Scalable Network Monitoring and Bandwidth Throttling System for Cloud Computing N.F. Huysamen and A.E. Krzesinski Department of Mathematical Sciences University of Stellenbosch 7600 Stellenbosch, South
A Scalable Network Monitoring and Bandwidth Throttling System for Cloud Computing N.F. Huysamen and A.E. Krzesinski Department of Mathematical Sciences University of Stellenbosch 7600 Stellenbosch, South
Volume SYSLOG JUNCTION. User s Guide. User s Guide
 Volume 1 SYSLOG JUNCTION User s Guide User s Guide SYSLOG JUNCTION USER S GUIDE Introduction I n simple terms, Syslog junction is a log viewer with graphing capabilities. It can receive syslog messages
Volume 1 SYSLOG JUNCTION User s Guide User s Guide SYSLOG JUNCTION USER S GUIDE Introduction I n simple terms, Syslog junction is a log viewer with graphing capabilities. It can receive syslog messages
tibbr Now, the Information Finds You.
 tibbr Now, the Information Finds You. - tibbr Integration 1 tibbr Integration: Get More from Your Existing Enterprise Systems and Improve Business Process tibbr empowers IT to integrate the enterprise
tibbr Now, the Information Finds You. - tibbr Integration 1 tibbr Integration: Get More from Your Existing Enterprise Systems and Improve Business Process tibbr empowers IT to integrate the enterprise
Arena Tutorial 1. Installation STUDENT 2. Overall Features of Arena
 Arena Tutorial This Arena tutorial aims to provide a minimum but sufficient guide for a beginner to get started with Arena. For more details, the reader is referred to the Arena user s guide, which can
Arena Tutorial This Arena tutorial aims to provide a minimum but sufficient guide for a beginner to get started with Arena. For more details, the reader is referred to the Arena user s guide, which can
WebEx. Remote Support. User s Guide
 WebEx Remote Support User s Guide Version 6.5 Copyright WebEx Communications, Inc. reserves the right to make changes in the information contained in this publication without prior notice. The reader should
WebEx Remote Support User s Guide Version 6.5 Copyright WebEx Communications, Inc. reserves the right to make changes in the information contained in this publication without prior notice. The reader should
Testing and Restoring the Nasuni Filer in a Disaster Recovery Scenario
 Testing and Restoring the Nasuni Filer in a Disaster Recovery Scenario Version 7.0 July 2015 2015 Nasuni Corporation All Rights Reserved Document Information Testing Disaster Recovery Version 7.0 July
Testing and Restoring the Nasuni Filer in a Disaster Recovery Scenario Version 7.0 July 2015 2015 Nasuni Corporation All Rights Reserved Document Information Testing Disaster Recovery Version 7.0 July
Online Backup Linux Client User Manual
 Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Parallels Plesk Automation. Customer s Guide. Parallels Plesk Automation 11.5
 Parallels Plesk Automation Customer s Guide Parallels Plesk Automation 11.5 Last updated: 17 March 2015 Contents Quick Start with Hosting Panel 4 Set Up Your First Website... 4 1. Create Your Site... 5
Parallels Plesk Automation Customer s Guide Parallels Plesk Automation 11.5 Last updated: 17 March 2015 Contents Quick Start with Hosting Panel 4 Set Up Your First Website... 4 1. Create Your Site... 5
2X ApplicationServer & LoadBalancer Manual
 2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: [email protected] Information in this document is subject to change without notice. Companies,
2X ApplicationServer & LoadBalancer Manual 2X ApplicationServer & LoadBalancer Contents 1 URL: www.2x.com E-mail: [email protected] Information in this document is subject to change without notice. Companies,
Microsoft Labs Online
 Microsoft Labs Online Self-Service Student Guide Welcome to Microsoft Labs Online powered by Xtreme Velocity. This document provides stepby-step instructions on how to: Create an account. Use your virtual
Microsoft Labs Online Self-Service Student Guide Welcome to Microsoft Labs Online powered by Xtreme Velocity. This document provides stepby-step instructions on how to: Create an account. Use your virtual
Remote Desktop In OpenSUSE 10.3
 Only for dummies Remote Desktop In OpenSUSE 10.3 Remote access to Linux GUI Environment from Windows Client Tedy Tirtawidjaja 5/14/2008 In Microsoft Windows environment we know Remote Desktop application
Only for dummies Remote Desktop In OpenSUSE 10.3 Remote access to Linux GUI Environment from Windows Client Tedy Tirtawidjaja 5/14/2008 In Microsoft Windows environment we know Remote Desktop application
ClickDimensions Quick Start Guide For Microsoft Dynamics CRM 2011. 9/1/2011 ClickDimensions
 ClickDimensions Quick Start Guide For Microsoft Dynamics CRM 2011 9/1/2011 ClickDimensions Online Training Resources This guide will explain how to register for and use a ClickDimensions Marketing Automation
ClickDimensions Quick Start Guide For Microsoft Dynamics CRM 2011 9/1/2011 ClickDimensions Online Training Resources This guide will explain how to register for and use a ClickDimensions Marketing Automation
EventTracker: Configuring DLA Extension for AWStats Report AWStats Reports
 EventTracker: Configuring DLA Extension for AWStats Report AWStats Reports Publication Date: Oct 18, 2011 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Abstract
EventTracker: Configuring DLA Extension for AWStats Report AWStats Reports Publication Date: Oct 18, 2011 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Abstract
DiskBoss. File & Disk Manager. Version 2.0. Dec 2011. Flexense Ltd. www.flexense.com [email protected]. File Integrity Monitor
 DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com [email protected] 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
DiskBoss File & Disk Manager File Integrity Monitor Version 2.0 Dec 2011 www.flexense.com [email protected] 1 Product Overview DiskBoss is an automated, rule-based file and disk manager allowing one to
Pharos Control User Guide
 Outdoor Wireless Solution Pharos Control User Guide REV1.0.0 1910011083 Contents Contents... I Chapter 1 Quick Start Guide... 1 1.1 Introduction... 1 1.2 Installation... 1 1.3 Before Login... 8 Chapter
Outdoor Wireless Solution Pharos Control User Guide REV1.0.0 1910011083 Contents Contents... I Chapter 1 Quick Start Guide... 1 1.1 Introduction... 1 1.2 Installation... 1 1.3 Before Login... 8 Chapter
exacqvision Web Server Quick start Guide
 exacqvision Web Server Quick start Guide 11955 Exit 5 Pkwy Building 3 Fishers, IN 46037-7939 USA +1.317.845.5710 phone +1.317.845.5720 fax 1 Basic Installation The exacqvision Web Server works with browsers
exacqvision Web Server Quick start Guide 11955 Exit 5 Pkwy Building 3 Fishers, IN 46037-7939 USA +1.317.845.5710 phone +1.317.845.5720 fax 1 Basic Installation The exacqvision Web Server works with browsers
Load testing with. WAPT Cloud. Quick Start Guide
 Load testing with WAPT Cloud Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. 2007-2015 SoftLogica
Load testing with WAPT Cloud Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. 2007-2015 SoftLogica
Troubleshooting network connection problems for Compro IP cameras
 Release No. Revision Description Applied Products TNN004 v111024 Troubleshooting network connection problems for Compro IP cameras All Compro IP camera products Troubleshooting network connection problems
Release No. Revision Description Applied Products TNN004 v111024 Troubleshooting network connection problems for Compro IP cameras All Compro IP camera products Troubleshooting network connection problems
EXPLORER. TFT Filter CONFIGURATION
 EXPLORER TFT Filter Configuration Page 1 of 9 EXPLORER TFT Filter CONFIGURATION Thrane & Thrane Author: HenrikMøller Rev. PA4 Page 1 6/15/2006 EXPLORER TFT Filter Configuration Page 2 of 9 1 Table of Content
EXPLORER TFT Filter Configuration Page 1 of 9 EXPLORER TFT Filter CONFIGURATION Thrane & Thrane Author: HenrikMøller Rev. PA4 Page 1 6/15/2006 EXPLORER TFT Filter Configuration Page 2 of 9 1 Table of Content
Using Fuzzy Logic Control to Provide Intelligent Traffic Management Service for High-Speed Networks ABSTRACT:
 Using Fuzzy Logic Control to Provide Intelligent Traffic Management Service for High-Speed Networks ABSTRACT: In view of the fast-growing Internet traffic, this paper propose a distributed traffic management
Using Fuzzy Logic Control to Provide Intelligent Traffic Management Service for High-Speed Networks ABSTRACT: In view of the fast-growing Internet traffic, this paper propose a distributed traffic management
Globalstar 9600. User Guide for Mac
 Globalstar 9600 User Guide for Mac This guide is based on the production version of the Globalstar 9600 and Sat-Fi Apps. Software changes may have occurred after this printing. Globalstar reserves the
Globalstar 9600 User Guide for Mac This guide is based on the production version of the Globalstar 9600 and Sat-Fi Apps. Software changes may have occurred after this printing. Globalstar reserves the
NetVanta 7100 Exercise Service Provider SIP Trunk
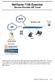 NetVanta 7100 Exercise Service Provider SIP Trunk PSTN NetVanta 7100 FXS 0/1 x2001 SIP Eth 0/0 x2004 SIP Server 172.23.102.87 Hosted by x2003 www.voxitas.com In this exercise, you will create a SIP trunk
NetVanta 7100 Exercise Service Provider SIP Trunk PSTN NetVanta 7100 FXS 0/1 x2001 SIP Eth 0/0 x2004 SIP Server 172.23.102.87 Hosted by x2003 www.voxitas.com In this exercise, you will create a SIP trunk
File S1: Supplementary Information of CloudDOE
 File S1: Supplementary Information of CloudDOE Table of Contents 1. Prerequisites of CloudDOE... 2 2. An In-depth Discussion of Deploying a Hadoop Cloud... 2 Prerequisites of deployment... 2 Table S1.
File S1: Supplementary Information of CloudDOE Table of Contents 1. Prerequisites of CloudDOE... 2 2. An In-depth Discussion of Deploying a Hadoop Cloud... 2 Prerequisites of deployment... 2 Table S1.
Kaspersky Security Center Web-Console
 Kaspersky Security Center Web-Console User Guide CONTENTS ABOUT THIS GUIDE... 5 In this document... 5 Document conventions... 7 KASPERSKY SECURITY CENTER WEB-CONSOLE... 8 SOFTWARE REQUIREMENTS... 10 APPLICATION
Kaspersky Security Center Web-Console User Guide CONTENTS ABOUT THIS GUIDE... 5 In this document... 5 Document conventions... 7 KASPERSKY SECURITY CENTER WEB-CONSOLE... 8 SOFTWARE REQUIREMENTS... 10 APPLICATION
efolder BDR for Veeam Cloud Connection Guide
 efolder BDR for Veeam Cloud Connection Guide Setup Connect Preload Data uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder Cloud for Veeam. Using the efolder Cloud
efolder BDR for Veeam Cloud Connection Guide Setup Connect Preload Data uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder Cloud for Veeam. Using the efolder Cloud
ReadyNAS Remote. User Manual. June 2013 202-11078-03. 350 East Plumeria Drive San Jose, CA 95134 USA
 User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
Virtual Server Installation Manual April 8, 2014 Version 1.8
 Virtual Server Installation Manual April 8, 2014 Version 1.8 Department of Health and Human Services Administration for Children and Families Office of Child Support Enforcement REVISION HISTORY Version
Virtual Server Installation Manual April 8, 2014 Version 1.8 Department of Health and Human Services Administration for Children and Families Office of Child Support Enforcement REVISION HISTORY Version
NMS300 Network Management System
 NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
SETTING UP REMOTE ACCESS ON EYEMAX PC BASED DVR.
 SETTING UP REMOTE ACCESS ON EYEMAX PC BASED DVR. 1. Setting up your network to allow incoming connections on ports used by Eyemax system. Default ports used by Eyemax system are: range of ports 9091~9115
SETTING UP REMOTE ACCESS ON EYEMAX PC BASED DVR. 1. Setting up your network to allow incoming connections on ports used by Eyemax system. Default ports used by Eyemax system are: range of ports 9091~9115
End User Guide The guide for email/ftp account owner
 End User Guide The guide for email/ftp account owner ServerDirector Version 3.7 Table Of Contents Introduction...1 Logging In...1 Logging Out...3 Installing SSL License...3 System Requirements...4 Navigating...4
End User Guide The guide for email/ftp account owner ServerDirector Version 3.7 Table Of Contents Introduction...1 Logging In...1 Logging Out...3 Installing SSL License...3 System Requirements...4 Navigating...4
Introweb Remote Backup Client for Mac OS X User Manual. Version 3.20
 Introweb Remote Backup Client for Mac OS X User Manual Version 3.20 1. Contents 1. Contents...2 2. Product Information...4 3. Benefits...4 4. Features...5 5. System Requirements...6 6. Setup...7 6.1. Setup
Introweb Remote Backup Client for Mac OS X User Manual Version 3.20 1. Contents 1. Contents...2 2. Product Information...4 3. Benefits...4 4. Features...5 5. System Requirements...6 6. Setup...7 6.1. Setup
Microsoft Labs Online
 Microsoft Labs Online Self-Service Student Guide Welcome to Microsoft Labs Online powered by Xtreme Velocity. This document provides stepby-step instructions on how to: Create an account. Use your virtual
Microsoft Labs Online Self-Service Student Guide Welcome to Microsoft Labs Online powered by Xtreme Velocity. This document provides stepby-step instructions on how to: Create an account. Use your virtual
ELIXIR LOAD BALANCER 2
 ELIXIR LOAD BALANCER 2 Overview Elixir Load Balancer for Elixir Repertoire Server 7.2.2 or greater provides software solution for load balancing of Elixir Repertoire Servers. As a pure Java based software
ELIXIR LOAD BALANCER 2 Overview Elixir Load Balancer for Elixir Repertoire Server 7.2.2 or greater provides software solution for load balancing of Elixir Repertoire Servers. As a pure Java based software
