Beth Hennigan. 1 P a g e
|
|
|
- Aldous Franklin
- 10 years ago
- Views:
Transcription
1 1 P a g e
2 Gold - Unit 13 Using Use software tools and techniques to compose and send messages 1.1 I can select and use software tools to compose and format messages, including attachments This is an example of a good as it includes a: subject, attachment, it s formal and it has a description. This also makes the more formal, if these features weren t included, it would appear informal. 2 P a g e
3 1.2 I can determine the message size and how it can be reduced Here I have sorted my s by size so I can check hoe much storage I m using also by sorting your s into size order, you can see who s sent you the that takes up the most space. By knowing this, you can delete whatever you need to provide more space, to send or receive s. Here I can see how much space is being taken up in my working area. By seeing this, you can see what you re sending and receiving, and delete whatever is needed or zip the attachment so it can be added to the I can send messages to individuals and groups 3 P a g e
4 This is me sending an to a group. 1.4 I can describe how to stay safe and respect others when using To stay safe while using , do not download exe files contaminated with viruses. Getting s off of strangers could be vital to your computer/laptop. Opening and downloading unknown files could cause serious damage to your device. These s have the potential to slow down or even destroy data on your computer. Using abusive/offensive language should not be included when sending an . If foul language is included when it considers work, you may not get the job, or be promoted, or even worse, lose your job. This could also lead to you not getting jobs in the future. Using abusive language has the potential to put you in a bad light, causing people not to speak to you. Spamming is also a problem when it comes to s. By spamming people you annoy them and fill up storage on their device, causing irritation with the receiver. With spam filling up your inbox, it ll take a lot of time to clear out. Replying to strangers could also cause serious problems. When strangers ask to meet you, do not respond as it could put you in danger. Strangers usually ask to meet you in private places and attempt to retrieve personal information. Giving this information could become vital to your privacy and safety. 4 P a g e
5 1.5 I can use an address book to organise contact information Group chats allow you to send a message to a number of people, saving you from sending the same continuously to several people. This group, for example includes all of my ICT group. It is a lot easier to send s to this group then sending 26 individual s that are all the same. 5 P a g e
6 Manage incoming effectively 2.1 I can follow guidelines and procedures for using These are the basic rules you need to follow when sending an I can read and respond to messages appropriately Setting an to high importance helps to be seen easier when in your inbox. High importance also tells you that you need to read it as soon as possible. 6 P a g e
7 2.3 I can use software tools and techniques to automate responses Setting up an automatic reply allows your to reply to s that are sent to you, when you re busy. Such as, if you re on holiday the person who sent you the will get a reply saying you re not available, so you don t look ignorant. 2.4 I can describe how to archive messages, including attachments Archiving s mean that you can remove them from your inbox and reduce the storage being used. But, archiving s mean that if you want to retrieve these s, you go onto the folder created, and you are then able to view them. Archiving is for s that clog up your inbox, but you may need them for future use. 2.5 I can organise, store and archive messages effectively Currently, I have a very messy inbox. This makes finding important s extremely difficult and also takes up space. Organising them prevents s that aren t important taking up space. 7 P a g e
8 Now that I have deleted the s that aren t important, my inbox is a lot cleaner. I can fine important s a lot easier, and I now have more space to send and receive s. 2.6 I can respond appropriately to problems 8 P a g e
9 If my wasn t working during school I would check my password several times, and if it still continued to fail, I would go to the ICT support team. If my wasn t working at home, I would again check my password, and if it still didn t work, I would call my provider. 9 P a g e
10 10 P a g e
EDEXCEL FUNCTIONAL SKILLS ICT. Study Module 8. Using ICT to communicate
 EDEXCEL FUNCTIONAL SKILLS ICT Study Module 8 Using ICT to communicate Published by Pearson Education, Edinburgh Gate, Harlow CM20 2JE Pearson Education 2010 All rights reserved. This material may be used
EDEXCEL FUNCTIONAL SKILLS ICT Study Module 8 Using ICT to communicate Published by Pearson Education, Edinburgh Gate, Harlow CM20 2JE Pearson Education 2010 All rights reserved. This material may be used
Connecting to LUA s webmail
 Connecting to LUA s webmail Effective immediately, the Company has enhanced employee remote access to email (Outlook). By utilizing almost any browser you will have access to your Company e-mail as well
Connecting to LUA s webmail Effective immediately, the Company has enhanced employee remote access to email (Outlook). By utilizing almost any browser you will have access to your Company e-mail as well
www.thalesgroup.com Business Ethics Conduct Guide Best practice guidelines for using e-mail
 www.thalesgroup.com Business Ethics Conduct Guide Best practice guidelines for using e-mail Contents PREFACE...3 DID YOU KNOW?...4 Make better use of time... 4 Manage the mass of information... 5 Avoid
www.thalesgroup.com Business Ethics Conduct Guide Best practice guidelines for using e-mail Contents PREFACE...3 DID YOU KNOW?...4 Make better use of time... 4 Manage the mass of information... 5 Avoid
Fighting spam in Australia. A consumer guide
 Fighting spam in Australia A consumer guide Fighting spam Use filtering software Install anti-virus software Use a personal firewall Download security patches Choose long and random passwords Protect your
Fighting spam in Australia A consumer guide Fighting spam Use filtering software Install anti-virus software Use a personal firewall Download security patches Choose long and random passwords Protect your
Webmail Friends & Exceptions Guide
 Webmail Friends & Exceptions Guide Add email addresses to the Exceptions List and the Friends List in your Webmail account to ensure you receive email messages from family, friends, and other important
Webmail Friends & Exceptions Guide Add email addresses to the Exceptions List and the Friends List in your Webmail account to ensure you receive email messages from family, friends, and other important
This document has been produced following a request from the Hft National Speak Out Group for help with staying safe when using the internet.
 This document has been produced following a request from the Hft National Speak Out Group for help with staying safe when using the internet. Hft Safeguarding Group commissioned a member of Hft National
This document has been produced following a request from the Hft National Speak Out Group for help with staying safe when using the internet. Hft Safeguarding Group commissioned a member of Hft National
CFASAA231 - Sqa Unit Code H4RT 04 Use IT to support your role
 CFASAA231 - Sqa Unit Code H4RT 04 Overview Handle files, edit, format and check information, search for and use email. This is based on the e-skills UK Areas of Competence export units: General Uses of
CFASAA231 - Sqa Unit Code H4RT 04 Overview Handle files, edit, format and check information, search for and use email. This is based on the e-skills UK Areas of Competence export units: General Uses of
Microsoft Outlook 2010 Hints & Tips
 IT Services Microsoft Outlook 2010 Hints & Tips Contents Introduction... 1 What Outlook Starts Up In... 1 Sending Email Hints... 2 Tracking a Message... 2 Saving a Sent Item... 3 Delay Delivery of a Single
IT Services Microsoft Outlook 2010 Hints & Tips Contents Introduction... 1 What Outlook Starts Up In... 1 Sending Email Hints... 2 Tracking a Message... 2 Saving a Sent Item... 3 Delay Delivery of a Single
Registering at the Securemail site
 Registering at the Securemail site Before using the Secure Mail service for the first time, you must perform a one-time service registration by completing the following steps. 1. When a Secure Mail is
Registering at the Securemail site Before using the Secure Mail service for the first time, you must perform a one-time service registration by completing the following steps. 1. When a Secure Mail is
OCT Training & Technology Solutions [email protected] (718) 997-4875
 OCT Training & Technology Solutions [email protected] (718) 997-4875 Understanding Information Security Information Security Information security refers to safeguarding information from misuse and theft,
OCT Training & Technology Solutions [email protected] (718) 997-4875 Understanding Information Security Information Security Information security refers to safeguarding information from misuse and theft,
How to Use the File Transfer (FTP) Service
 How to Use the File Transfer (FTP) Service How to Use the File Transfer (FTP) Service...1 What is a File Transfer Service?...2 First Steps...2 How to Upload Files to the File Transfer Service...2 How to
How to Use the File Transfer (FTP) Service How to Use the File Transfer (FTP) Service...1 What is a File Transfer Service?...2 First Steps...2 How to Upload Files to the File Transfer Service...2 How to
GUIDEWIRE. Introduction to Using WebMail. macrobatix. Learn how to: august 2008
 macrobatix GUIDEWIRE august 2008 Introduction to Using WebMail Learn how to: Manage Your Inbox Compose a Message Activate Spam Filter Modify Spam Settings Check Held Messages *To download the complete
macrobatix GUIDEWIRE august 2008 Introduction to Using WebMail Learn how to: Manage Your Inbox Compose a Message Activate Spam Filter Modify Spam Settings Check Held Messages *To download the complete
U.S. Bank Secure Mail
 U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
Travel agents guide to SMS messaging. How to use SMS messaging for marketing, booking, and customer support
 Travel agents guide to SMS messaging How to use SMS messaging for marketing, booking, and customer support Why should you use SMS messaging? When was the last time you didn t have your mobile? Chances
Travel agents guide to SMS messaging How to use SMS messaging for marketing, booking, and customer support Why should you use SMS messaging? When was the last time you didn t have your mobile? Chances
Your guide to Gmail. Gmail user guide
 Your guide to Gmail Gmail user guide Welcome to Gmail! This guide outlines some of the key settings and features of Gmail. Getting started How to access your Gmail account page 3 Settings and personalisation
Your guide to Gmail Gmail user guide Welcome to Gmail! This guide outlines some of the key settings and features of Gmail. Getting started How to access your Gmail account page 3 Settings and personalisation
Outlook Web App (OWA) To create a new message:
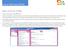 What you ll see in Mail 1. Create a new message by clicking New mail. 2. Folder list. The folder list includes the folders in your mailbox. It may include other folders, such as Favorites and archive folders.
What you ll see in Mail 1. Create a new message by clicking New mail. 2. Folder list. The folder list includes the folders in your mailbox. It may include other folders, such as Favorites and archive folders.
BULLGUARD SPAMFILTER
 BULLGUARD SPAMFILTER GUIDE Introduction 1.1 Spam emails annoyance and security risk If you are a user of web-based email addresses, then you probably do not need antispam protection as that is already
BULLGUARD SPAMFILTER GUIDE Introduction 1.1 Spam emails annoyance and security risk If you are a user of web-based email addresses, then you probably do not need antispam protection as that is already
AHS Computing. Outlook Seminar Series Session #2
 AHS Computing Outlook Seminar Series Session #2 Introduction Email templates Archiving email Creating Rules Automating Replies Sorting Junk Email Settings Email Templates File with predesigned, customized
AHS Computing Outlook Seminar Series Session #2 Introduction Email templates Archiving email Creating Rules Automating Replies Sorting Junk Email Settings Email Templates File with predesigned, customized
Sibford School Student Computer Acceptable Use Policy
 Introduction Sibford School Student Computer Acceptable Use Policy The use of the latest technology is actively encouraged at Sibford School but with this comes a responsibility to protect both students
Introduction Sibford School Student Computer Acceptable Use Policy The use of the latest technology is actively encouraged at Sibford School but with this comes a responsibility to protect both students
EMAILING USING HOTMAIL
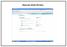 EMAILING USING HOTMAIL Signing into Your Email Account Open up explorer and type in www.hotmail.com in the address bar. Enter your email address. Hit the tab key on the keyboard and enter your password.
EMAILING USING HOTMAIL Signing into Your Email Account Open up explorer and type in www.hotmail.com in the address bar. Enter your email address. Hit the tab key on the keyboard and enter your password.
Use Office 365 on your iphone or ipad
 Use Office 365 on your iphone or ipad Quick Start Guide Check email Set up your iphone or ipad to send and receive mail from your Office 365 account. Check your calendar wherever you are Always know where
Use Office 365 on your iphone or ipad Quick Start Guide Check email Set up your iphone or ipad to send and receive mail from your Office 365 account. Check your calendar wherever you are Always know where
Hint: Best actions: Find out more in videos and FAQ: Hint: Best actions: Find out more in videos and FAQ:
 Game Cheatsheet This is a spam email, an unsolicited and unwanted email from an unknown sender. Hint: Does this offer seem too good to be true? Perhaps you need to know more? Best actions: Delete, Check
Game Cheatsheet This is a spam email, an unsolicited and unwanted email from an unknown sender. Hint: Does this offer seem too good to be true? Perhaps you need to know more? Best actions: Delete, Check
After you've enabled POP/IMAP access in i.mail, you need to configure your email client to download i.mail messages.
 User Guide- i.mail enhancement Configure POP/IMAP access using Outlook and Windows Mail Firstly, you need to enable POP/IMAP on your i.mail account: 1. Log into your i.mail account via web 2. Click Mail
User Guide- i.mail enhancement Configure POP/IMAP access using Outlook and Windows Mail Firstly, you need to enable POP/IMAP on your i.mail account: 1. Log into your i.mail account via web 2. Click Mail
A Guide to Information Technology Security in Trinity College Dublin
 A Guide to Information Technology Security in Trinity College Dublin Produced by The IT Security Officer & Training and Publications 2003 Web Address: www.tcd.ie/itsecurity Email: [email protected] 1 2
A Guide to Information Technology Security in Trinity College Dublin Produced by The IT Security Officer & Training and Publications 2003 Web Address: www.tcd.ie/itsecurity Email: [email protected] 1 2
I.T. Services. Quick Start Guide. E mail at Hope
 Quick Start Guide To E mail at Hope Accessing Google Mail Go to Hope s homepage (www.hope.ac.uk) and click on Current Staff / Students Click on Email The following box will appear on the screen: Enter
Quick Start Guide To E mail at Hope Accessing Google Mail Go to Hope s homepage (www.hope.ac.uk) and click on Current Staff / Students Click on Email The following box will appear on the screen: Enter
Amy wants to use her email to view some photos her friend Sandy sent, from her vacation to Washington DC.
 E-mail Attachments Hi, I m Sarah. I m going to show you how to download files people send to you in emails, and how to send your own files to other people using your email. We ll follow along with Amy,
E-mail Attachments Hi, I m Sarah. I m going to show you how to download files people send to you in emails, and how to send your own files to other people using your email. We ll follow along with Amy,
Outlook Data File navigate to the PST file that you want to open, select it and choose OK. The file will now appear as a folder in Outlook.
 Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Secure Email User Guide Receiving Secure Email from Merchants Bank
 Secure Email User Guide Receiving Secure Email from Merchants Bank Contents This document provides a brief, end-user overview of the Cisco Registered Envelope Service Email system which has been implemented
Secure Email User Guide Receiving Secure Email from Merchants Bank Contents This document provides a brief, end-user overview of the Cisco Registered Envelope Service Email system which has been implemented
You can attach email accounts to this domain name (eg. [email protected] or [email protected]) which also increases your corporate branding.
 EMAIL SET UP 1 Your website is placed on the Internet using a domain name (eg. www.acme.com.au). This is your virtual address and it allows people to find your website amongst the millions of websites
EMAIL SET UP 1 Your website is placed on the Internet using a domain name (eg. www.acme.com.au). This is your virtual address and it allows people to find your website amongst the millions of websites
Using the PeaceHealth Secure E-mail System
 1 PeaceHealth is using a Secure E-mail System that allows for secure E-mail communications between individuals with a PeaceHealth E-mail address and individuals with E-mail addresses outside the PeaceHealth
1 PeaceHealth is using a Secure E-mail System that allows for secure E-mail communications between individuals with a PeaceHealth E-mail address and individuals with E-mail addresses outside the PeaceHealth
Managing your e-mail accounts
 Managing your e-mail accounts Introduction While at Rice University, you will receive an e-mail account that will be used for most of your on-campus correspondence. Other tutorials will tell you how to
Managing your e-mail accounts Introduction While at Rice University, you will receive an e-mail account that will be used for most of your on-campus correspondence. Other tutorials will tell you how to
UC Irvine Health Secure Mail Message Center
 UC Irvine Health Secure Mail Message Center UC Irvine Health is committed to protecting the privacy of its member s information, especially their protected health information (PHI). UC Irvine Health is
UC Irvine Health Secure Mail Message Center UC Irvine Health is committed to protecting the privacy of its member s information, especially their protected health information (PHI). UC Irvine Health is
Using Server-Side Filters to Manage/Organize Your E-Mail (Including Accept and Block Lists) Table of Contents Why Use Server-Side Mail Filters INBOX
 Using Server-Side Filters to Manage/Organize Your E-Mail (Including Accept and Block Lists) 1 of 9 U-M Information Technology Central Services S4325 May 2005 You can create server-side mail filters to
Using Server-Side Filters to Manage/Organize Your E-Mail (Including Accept and Block Lists) 1 of 9 U-M Information Technology Central Services S4325 May 2005 You can create server-side mail filters to
[email protected]
 Email Electronic mail is the transmission of mainly text based messages across networks. This can be within a particular network - internal mail - or between networks - external mail. The most common network
Email Electronic mail is the transmission of mainly text based messages across networks. This can be within a particular network - internal mail - or between networks - external mail. The most common network
Email Basics. For more information on the Library and programs, visit www.bcpls.org BCPLS 08/10/2010 PEMA
 Email Basics Email, short for Electronic Mail, consists of messages which are sent and received using the Internet. There are many different email services available that allow you to create an email account
Email Basics Email, short for Electronic Mail, consists of messages which are sent and received using the Internet. There are many different email services available that allow you to create an email account
Welcome to HomeTown Bank s Secure E-mail! User Guide
 Welcome to HomeTown Bank s Secure E-mail! User Guide To access the secure email message center, click the Secure Email link on the www.htbmn.com main web page. Select whether you are a new user of the
Welcome to HomeTown Bank s Secure E-mail! User Guide To access the secure email message center, click the Secure Email link on the www.htbmn.com main web page. Select whether you are a new user of the
Email Etiquette (Netiquette) Guidance
 Email Etiquette (Netiquette) Guidance January 2007 Email Etiquette (Netiquette) Guidance January 2007-1/13 Version Control Version Author(s) Replacement Date 1.0 Timothy d Estrubé Information Governance
Email Etiquette (Netiquette) Guidance January 2007 Email Etiquette (Netiquette) Guidance January 2007-1/13 Version Control Version Author(s) Replacement Date 1.0 Timothy d Estrubé Information Governance
Setting up the Mail Sort Function in Outlook Web App
 2015.8 Organization for Information Management and Communication Setting up the Mail Sort Function in Outlook Web App For Faculty and Staff You can set up certain behavioral patterns regarding how your
2015.8 Organization for Information Management and Communication Setting up the Mail Sort Function in Outlook Web App For Faculty and Staff You can set up certain behavioral patterns regarding how your
WORKING REMOTELY USING OUTLOOK WEB APP
 WORKING REMOTELY USING OUTLOOK WEB APP Allen & Overy LLP 0090001-0000001 TSG:4829238.7 CONTENTS Section Page 1. What is Outlook Web App?...1 1.1 When Should it be Used?...1 1.2 What is Important to Know?...1
WORKING REMOTELY USING OUTLOOK WEB APP Allen & Overy LLP 0090001-0000001 TSG:4829238.7 CONTENTS Section Page 1. What is Outlook Web App?...1 1.1 When Should it be Used?...1 1.2 What is Important to Know?...1
- - Learn More (Please click on one of the links below) What s new? What s changed?
 - - - - - existing settings such as preferences (POP settings, password, signature, etc.), and content (calendar, address book, etc.) will remain intact. You will continue to have anytime anywhere access
- - - - - existing settings such as preferences (POP settings, password, signature, etc.), and content (calendar, address book, etc.) will remain intact. You will continue to have anytime anywhere access
Secure Email - Customer User Guide How to receive an encrypted email
 How to receive an encrypted email This guide has been developed for customers/suppliers of Glasgow City Council who are due to receive sensitive information from us. It will explain how to use our secure
How to receive an encrypted email This guide has been developed for customers/suppliers of Glasgow City Council who are due to receive sensitive information from us. It will explain how to use our secure
NEVER guess an e-mail address. Your mail will nearly always go to the wrong person.
 16. WebMail (E-mail) E-mail is a mechanism for sending messages and information between computer users. Individuals are identified by their e-mail address, which is used in much the same way as a postal
16. WebMail (E-mail) E-mail is a mechanism for sending messages and information between computer users. Individuals are identified by their e-mail address, which is used in much the same way as a postal
Email marketing, success by design. The advantages
 Email marketing, success by design Email marketing is a cost-effective and powerful way to communicate with your contacts and increase potential leads and sales. To beat the competition, it is vital you
Email marketing, success by design Email marketing is a cost-effective and powerful way to communicate with your contacts and increase potential leads and sales. To beat the competition, it is vital you
STUDENT WEBMAIL. User Guide. Realise Your Potential
 STUDENT WEBMAIL User Guide Realise Your Potential Email acceptable usage policy & safety tips Email is a wonderful tool for sending and receiving information quickly and securely to tutors, teachers or
STUDENT WEBMAIL User Guide Realise Your Potential Email acceptable usage policy & safety tips Email is a wonderful tool for sending and receiving information quickly and securely to tutors, teachers or
Frequently Asked Questions:
 Frequently Asked Questions: What is a Google Group? A Google Group is an online discussion group or mailing list that helps groups of people communicate using email and the web. Every group has a Google-hosted
Frequently Asked Questions: What is a Google Group? A Google Group is an online discussion group or mailing list that helps groups of people communicate using email and the web. Every group has a Google-hosted
Use your UNNCNetID and password to log in. The first time you login to the system, you may receive the following screen:
 (Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. Personnel at UNMC occasionally need
(Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. Personnel at UNMC occasionally need
Student Mail Access. Introduction. Option One: Using an E-mail Client
 Student Mail Access Introduction There are two ways that you will be able to access your e-mail from any location. You can use an e-mail client or a Web browser (p. 11). These options will be accessible
Student Mail Access Introduction There are two ways that you will be able to access your e-mail from any location. You can use an e-mail client or a Web browser (p. 11). These options will be accessible
Icebox - Sendio SPAM Filter
 Icebox - Sendio SPAM Filter Sendio Icebox The Navajo Department of Information Technology (DIT) installed and implemented a SPAM filter in 2008 to capture unwanted mail before it gets to your email inbox.
Icebox - Sendio SPAM Filter Sendio Icebox The Navajo Department of Information Technology (DIT) installed and implemented a SPAM filter in 2008 to capture unwanted mail before it gets to your email inbox.
Icebox - Sendio SPAM Filter
 Icebox - Sendio SPAM Filter Sendio Icebox The Navajo Department of Information Technology (DIT) installed and implemented a SPAM filter in 2008 to capture unwanted mail before it gets to your email inbox.
Icebox - Sendio SPAM Filter Sendio Icebox The Navajo Department of Information Technology (DIT) installed and implemented a SPAM filter in 2008 to capture unwanted mail before it gets to your email inbox.
Do I need anything special to use it? All you need to use Twitter is an Internet connection or a mobile phone with Internet capability.
 Twitter Guide What is Twitter? Twitter is a real-time communication platform that allows you to quickly share thoughts, opinions, and interesting links with friends, family, and the general public. People
Twitter Guide What is Twitter? Twitter is a real-time communication platform that allows you to quickly share thoughts, opinions, and interesting links with friends, family, and the general public. People
Life after Microsoft Outlook Google Apps
 Welcome Welcome to Gmail! Now that you ve switched from Microsoft Outlook to, here are some tips on beginning to use Gmail. Google Apps What s Different? Here are some of the differences you ll notice
Welcome Welcome to Gmail! Now that you ve switched from Microsoft Outlook to, here are some tips on beginning to use Gmail. Google Apps What s Different? Here are some of the differences you ll notice
What Spammers Don t Want You To Know About Permanently Blocking Their Vicious E-mails
 2000 Linwood Ave Suite 19J Fort Lee, NJ 07024-3012 What Spammers Don t Want You To Know About Permanently Blocking Their Vicious E-mails Following Last Year s Hack Attack At Epsilon, You May Be Overwhelmed
2000 Linwood Ave Suite 19J Fort Lee, NJ 07024-3012 What Spammers Don t Want You To Know About Permanently Blocking Their Vicious E-mails Following Last Year s Hack Attack At Epsilon, You May Be Overwhelmed
EADS up. stop think connect
 EADS up stop think connect table of contents 2 4 8 12 Share with Care Interact with Tact The Protection Connection Word Search You text, you play games, you share photos and video. You update your status,
EADS up stop think connect table of contents 2 4 8 12 Share with Care Interact with Tact The Protection Connection Word Search You text, you play games, you share photos and video. You update your status,
How to Manage Email. Guidance for staff
 How to Manage Email Guidance for staff 1 Executive Summary Aimed at Note Purpose Benefits staff Necessary skills to All staff who use email This guidance does NOT cover basic IT literacy skills. Staff
How to Manage Email Guidance for staff 1 Executive Summary Aimed at Note Purpose Benefits staff Necessary skills to All staff who use email This guidance does NOT cover basic IT literacy skills. Staff
Version 4 Revised 5/2015
 Email Encryption Manual Version 4 Revised 5/2015 This document provides information on sending, receiving, and saving encrypted emails using the WRC Group Message Center. Contents What is Email Encryption...
Email Encryption Manual Version 4 Revised 5/2015 This document provides information on sending, receiving, and saving encrypted emails using the WRC Group Message Center. Contents What is Email Encryption...
Exporting emails from Outlook Version 1.00
 Exporting emails from Outlook Version 1.00 The rapid growth in volume of emails means that there is a growing need to archive old emails to media such as external hard disks and DVD s. The document will
Exporting emails from Outlook Version 1.00 The rapid growth in volume of emails means that there is a growing need to archive old emails to media such as external hard disks and DVD s. The document will
Word Secure Messaging User Guide. Version 3.0
 Word Secure Messaging User Guide Version 3.0 Copyright 2007-2013 WordSecure, LLC. All Rights Reserved. Page 1 of 7 1. Introduction Word Secure Messaging is a program that allows you to exchange encrypted
Word Secure Messaging User Guide Version 3.0 Copyright 2007-2013 WordSecure, LLC. All Rights Reserved. Page 1 of 7 1. Introduction Word Secure Messaging is a program that allows you to exchange encrypted
So you want to create an Email a Friend action
 So you want to create an Email a Friend action This help file will take you through all the steps on how to create a simple and effective email a friend action. It doesn t cover the advanced features;
So you want to create an Email a Friend action This help file will take you through all the steps on how to create a simple and effective email a friend action. It doesn t cover the advanced features;
User Guide: Synei Products
 2013 User Guide: Synei Products LEARN HOW TO USE SYNEI PRODUCTS BRITNEY BILLARY AQUINO SYNEI www.synei.com Page 1 Table of Contents Disclaimer. Page 2 Installing Synei Products.Page 2 How to Use System
2013 User Guide: Synei Products LEARN HOW TO USE SYNEI PRODUCTS BRITNEY BILLARY AQUINO SYNEI www.synei.com Page 1 Table of Contents Disclaimer. Page 2 Installing Synei Products.Page 2 How to Use System
Chatroom and messaging safety Staying away from pornography Avoiding internet bullying. Keeping your child safe on the. internet
 Chatroom and messaging safety Staying away from pornography Avoiding internet bullying Keeping your child safe on the internet AT A GLANCE Using the internet and messaging safely Not everyone who uses
Chatroom and messaging safety Staying away from pornography Avoiding internet bullying Keeping your child safe on the internet AT A GLANCE Using the internet and messaging safely Not everyone who uses
Outlook Web Access (OWA or WebMail) Frequently Asked Questions
 Outlook Web Access (OWA or WebMail) Frequently Asked Questions If you are a part-time staff member, adjunct faculty member, or Villanova student, you will access your Villanova email using a program called
Outlook Web Access (OWA or WebMail) Frequently Asked Questions If you are a part-time staff member, adjunct faculty member, or Villanova student, you will access your Villanova email using a program called
Getting Started How To Use an Android Tablet
 Getting Started How To Use an Android Tablet Table of Contents Introduction Page 2 Buttons of the table Page 3 Using the touchscreen Page 4 Using the keyboard Page 4 Connecting to Wi Fi Page 5 Applications
Getting Started How To Use an Android Tablet Table of Contents Introduction Page 2 Buttons of the table Page 3 Using the touchscreen Page 4 Using the keyboard Page 4 Connecting to Wi Fi Page 5 Applications
Use Office 365 on your iphone or ipad
 Use Office 365 on your iphone or ipad Quick Start Guide Check email Set up your iphone or ipad to send and receive mail from your Office 365 account. Check your calendar wherever you are Always know where
Use Office 365 on your iphone or ipad Quick Start Guide Check email Set up your iphone or ipad to send and receive mail from your Office 365 account. Check your calendar wherever you are Always know where
Virtual Office Module. View Calendar. Add Personal Event. Add Global Event. View All. View Personal
 Virtual Office Module This is for internal use only and does not control a website of any kind. The virtual office allows you enter items such as calendar events, contacts, files, emails, message board,
Virtual Office Module This is for internal use only and does not control a website of any kind. The virtual office allows you enter items such as calendar events, contacts, files, emails, message board,
ICTICT103 Use, communicate and search securely on the internet
 ICTICT103 Use, communicate and search securely on the internet Release: 1 ICTICT103 Use, communicate and search securely on the internet Modification History Release Release 1 Comments This version first
ICTICT103 Use, communicate and search securely on the internet Release: 1 ICTICT103 Use, communicate and search securely on the internet Modification History Release Release 1 Comments This version first
What is e-mail? (using Outlook Express)
 What is e-mail? (using Outlook Express) 1. When you want to send a letter to a friend you write it, put it in an envelope, stamp it and put it in the post box. From there the postman picks it up, takes
What is e-mail? (using Outlook Express) 1. When you want to send a letter to a friend you write it, put it in an envelope, stamp it and put it in the post box. From there the postman picks it up, takes
ACS Email Encryption Recipient Guide
 ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
How To Use The Gtokus Secure Mail System
 Department of Banking and Finance (DBF) Secure Message Center DBF Secure E-Mail Procedures This document contains information proprietary to the Georgia Department of Banking and Finance and shall not
Department of Banking and Finance (DBF) Secure Message Center DBF Secure E-Mail Procedures This document contains information proprietary to the Georgia Department of Banking and Finance and shall not
Getting Started (direct link to Lighthouse Community http://tinyurl.com/q5dg5wp)
 Getting Started (direct link to Lighthouse Community http://tinyurl.com/q5dg5wp) If you re already a member, click to login and see members only content. Use the same login ID that you use to register
Getting Started (direct link to Lighthouse Community http://tinyurl.com/q5dg5wp) If you re already a member, click to login and see members only content. Use the same login ID that you use to register
How do I share a file with a friend or trusted associate?
 Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information
Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information
Outlook XP Email Only
 Outlook XP Email Only Table of Contents OUTLOOK XP EMAIL 5 HOW EMAIL WORKS: 5 POP AND SMTP: 5 TO SET UP THE POP AND SMTP ADDRESSES: 6 TO SET THE DELIVERY PROPERTY: 8 STARTING OUTLOOK: 10 THE OUTLOOK BAR:
Outlook XP Email Only Table of Contents OUTLOOK XP EMAIL 5 HOW EMAIL WORKS: 5 POP AND SMTP: 5 TO SET UP THE POP AND SMTP ADDRESSES: 6 TO SET THE DELIVERY PROPERTY: 8 STARTING OUTLOOK: 10 THE OUTLOOK BAR:
Fraud Prevention Guide
 Fraud Prevention Guide Table of Contents Protect your Information 2 Protect your wallet or purse 3 Don t forget around the house 3 Secure your credit cards and debit cards 4 Stop the telemarketing calls
Fraud Prevention Guide Table of Contents Protect your Information 2 Protect your wallet or purse 3 Don t forget around the house 3 Secure your credit cards and debit cards 4 Stop the telemarketing calls
Setting up and controlling E-mail
 Setting up and controlling E-mail Two methods Web based PC based Setting up and controlling E-mail Web based the messages are on the Internet accessed by dial-up or broadband at your Internet Service Provider
Setting up and controlling E-mail Two methods Web based PC based Setting up and controlling E-mail Web based the messages are on the Internet accessed by dial-up or broadband at your Internet Service Provider
Adjust Webmail Spam Settings
 Adjust Webmail Spam Settings An unsolicited bulk email message is known as "spam." Spam, which usually contains some sort of commercial advertising or proposition, is sent to a large number of recipients
Adjust Webmail Spam Settings An unsolicited bulk email message is known as "spam." Spam, which usually contains some sort of commercial advertising or proposition, is sent to a large number of recipients
10/28/2013. Partners Zixmail Web Portal. Provider Training. Let s Get Started!
 Partners Zixmail Web Portal Provider Training Let s Get Started! 1 Setting Up Your Partners Zixmail Web Portal There are two methods to begin this process. Option #1 Use the link on the Partners Provider
Partners Zixmail Web Portal Provider Training Let s Get Started! 1 Setting Up Your Partners Zixmail Web Portal There are two methods to begin this process. Option #1 Use the link on the Partners Provider
E-Safety and Computer Security Rules
 E-Safety and Computer Security Rules Process / Signatures Portfolio Team Portfolio Team Lead Principal Chair of Governors Behaviour Safety & Ethos Mrs K Mitford Dr J V Edwards Mrs K Mitford Presented 2
E-Safety and Computer Security Rules Process / Signatures Portfolio Team Portfolio Team Lead Principal Chair of Governors Behaviour Safety & Ethos Mrs K Mitford Dr J V Edwards Mrs K Mitford Presented 2
Haslingden High School
 Haslingden High School ICT Department Year 8 esafety and Web Design homework Student name: Form: ICT teacher: Date issued: Date due: Level Effort House points Teacher feedback: KS3 Target level Parent/Carer
Haslingden High School ICT Department Year 8 esafety and Web Design homework Student name: Form: ICT teacher: Date issued: Date due: Level Effort House points Teacher feedback: KS3 Target level Parent/Carer
Background Information
 User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
Stewart Secure Email User Guide. March 13, 2015
 Stewart Secure Email User Guide March 13, 2015 Table of Contents Introduction... 1 What is secure email?... 1 Why secure email?... 1 What is personal, non-public information?... 1 How is my data protected?...
Stewart Secure Email User Guide March 13, 2015 Table of Contents Introduction... 1 What is secure email?... 1 Why secure email?... 1 What is personal, non-public information?... 1 How is my data protected?...
Email Management CSCU9B2 CSCU9B2 1
 Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
How to use the VCCS Student E-mail System
 Page 1 of 7 How to use the VCCS Student E-mail System How to Access your Email 1. Log onto Blackboard. 2. Click on the Student Connect tab. 3. Click on the View My E-Mail link. 4. Your login name is your
Page 1 of 7 How to use the VCCS Student E-mail System How to Access your Email 1. Log onto Blackboard. 2. Click on the Student Connect tab. 3. Click on the View My E-Mail link. 4. Your login name is your
How to Manage Your Email List Effectively
 How to Manage Your Email List Effectively A short guide by MailWheel 1 Discover What s Inside After you ve acquired enough email addresses and created your opt-in and opt-out forms, you are probably wondering:
How to Manage Your Email List Effectively A short guide by MailWheel 1 Discover What s Inside After you ve acquired enough email addresses and created your opt-in and opt-out forms, you are probably wondering:
SPAM QUARANTINE. Quarantine
 SPAM QUARANTINE Whenever an email is thought to be spam by EOP it will be delivered to a holding area known as quarantine. This area sits outside of your inbox meaning potentially dangerous or annoying
SPAM QUARANTINE Whenever an email is thought to be spam by EOP it will be delivered to a holding area known as quarantine. This area sits outside of your inbox meaning potentially dangerous or annoying
About the Junk E-mail Filter
 1 of 5 16/04/2007 11:28 AM Help and How-to Home > Help and How-to About the Junk E-mail Filter Applies to: Microsoft Office Outlook 2003 Hide All The Junk E-mail Filter in Outlook is turned on by default,
1 of 5 16/04/2007 11:28 AM Help and How-to Home > Help and How-to About the Junk E-mail Filter Applies to: Microsoft Office Outlook 2003 Hide All The Junk E-mail Filter in Outlook is turned on by default,
Online Safety How to Protect Yourself and Your Family
 Online Safety How to Protect Yourself and Your Family Introduction Surfing the internet can be a very positive experience, it opens up a world of possibilities for everyone, expanding our horizons by exposing
Online Safety How to Protect Yourself and Your Family Introduction Surfing the internet can be a very positive experience, it opens up a world of possibilities for everyone, expanding our horizons by exposing
MONTHLY WEBSITE MAINTENANCE PACKAGES
 MONTHLY WEBSITE MAINTENANCE PACKAGES The security and maintenance of your website is serious business, and what you don t know can certainly hurt you. A hacked or spamvertised site can wreak havoc on search
MONTHLY WEBSITE MAINTENANCE PACKAGES The security and maintenance of your website is serious business, and what you don t know can certainly hurt you. A hacked or spamvertised site can wreak havoc on search
