How To Secure An Emr-Link System Architecture
|
|
|
- Baldric Barnaby Short
- 5 years ago
- Views:
Transcription
1 EMR-Link Security Administration Guide Introduction This guide provides an overview of the security measures built into EMR-Link, and how your organization s security policies can be implemented with these mechanisms. All security settings are under control of the admin user(s) in your organization. Security Overview Secure Connections over the Internet EMR-Link is a cloud-based service, running on Liaison servers in secure data centers. These data centers provide strong security to protect the system from unauthorized physical access as well as from unauthorized use over the Internet. Users connect to EMR-Link using a secure SSL connection from a web browser. SSL is enabled automatically and requires no user action. Users authenticate with EMR-Link using a username and password. System-to-system connections with EMR-Link, such as from an EHR or a lab system, is made over an encrypted communications channel. This may be SSL or may be a VPN or other mechanism, depending on the technical details of the system with which EMR-Link is connected. Authentication of both ends of the connection is done via a security key; usage depends on the details of the connection. Security Infrastructure At the EMR-Link data center, a series of firewalls insulates different parts of the system to provide multiple layers of security. Servers storing Protected Health Information are not directly accessible from the Internet, but only from the application servers and through the Liaison administrative VPN. Customer Security Responsibilities Managing security settings and user accounts is delegated to the customer organization, to allow implementation of customer-specific security policies. And because EMR-Link connects with and works in conjunction with the EHR, overall security depends on securing the EHR environment and the customer s networks and workstations, as well as proper use of security settings within EMR-Link. The customer has these specific responsibilities: Configuring EMR-Link security settings in accordance with the customer s security policies. Creating user accounts and assigning appropriate permissions based on the user s role, and modification or termination of user accounts when responsibilities change. Monitoring the EMR-Link audit log for any unauthorized activity. EMR-Link System Architecture 1 Last updated: 3/12/2015
2 EMR-Link Security Settings Passwords The first step in configuring security is to establish a password policy, to determine the complexity of passwords, when they expire, and how to handle login failures that may be evidence of attempts to gain unauthorized access to the system. The screenshot below shows the password settings. Password Expiration this setting controls how long a given password can be used before it must be changed. Good password policy requires periodic password changes, to limit the usability of passwords that might have been compromised in the past. Password Requirements these settings control how complex passwords must be. Complex passwords are more difficult to guess or to attack using brute force methods. The password reuse limit prevents a user from recycling the same small number of passwords, so that new passwords must be selected. Account Lockout this setting helps delay attempts to guess a password, by limiting the number of attempts that can be made in a specific period of time. Since password guessing requires a large number EMR-Link System Architecture 2 Last updated: 3/12/2015
3 of attempts, this feature can make password guessing infeasible. The user account is automatically unlocked after a period of time, or can be manually unlocked by an administrator. Sessions When a user logs in, a new user session is created. Automatic termination of idle sessions is important to help prevent unauthorized use of an unattended workstation. There is also a setting to enable manual locking. This allows a user to lock their EMR-Link session when leaving their workstation, without logging out. The user will then need to re-enter their password to reactivate the session. Other Security Settings Integrated Authentication EMR-Link provides a mechanism to connect to the customer s own authentication system, such as Active Directory. This requires installing a redirection page on the customer s intranet server; EMR-Link Support can assist with configuring this. Mobile Settings these settings control authentication from a mobile device, when using EMR-Link Mobile. Server Side View Authentication Settings these settings control authentication for viewing server-side results via a URL from within the EMR. EMR-Link System Architecture 3 Last updated: 3/12/2015
4 Managing EMR-Link Users Permissions and Roles EMR-Link provides a set of permissions that can be assigned to a user login. Based on the user s permissions, certain features within EMR-Link are enabled or disabled. Users should be provided the minimum access consistent with their job requirements. In particular, there are two functional areas that should be carefully considered for each user: The need to access Protected Health Information; The need to be able to change EMR-Link settings. Creating and Managing Users User accounts are created from the Users navigation tab. When creating a new user account or modifying an existing account, the permission settings below are available. The EMR-Link username must be globally unique across all EMR-Link users, so an address is a good choice. The name field provides the name used in reports and on user screens. Phone is optional and is provided for information only. The field must be populated; this field is used if a user needs to reset his/her own password. A specific password can be entered and this is required when creating a new account. The Require Password Change checkbox should be checked for new user accounts or when an admin manually resets the password, to force the user to select a different password when they log in. There is also an option to manually unlock a locked account. The user permissions for the account should be verified, and modified if needed. The permissions are as follows: Manage Users allows viewing and modifying user accounts. Since this provides the ability to modify (i.e., increase) the permissions of users, it should be set only for admin users who specifically need to manage user accounts. View Users allows visibility of the set of user accounts but not the ability to change them. EMR-Link System Architecture 4 Last updated: 3/12/2015
5 Manage Config allows an administrator to change EMR-Link settings. This should be reserved for a small number of users who are responsible for managing lab settings, insurance lists, test code maps, and other settings. View Config allows only read access to settings. No editing is allowed. Manage Orders allows a user to create and modify orders. This permission allows access to PHI associated with orders. View Orders allows only read access to order data. PHI is visible, but no editing allowed. Manage Results allows a user to view and manage result reports, including PHI associated with those documents. View Results allows only read access to results data. PHI is visible, but no editing allowed. View Reports enables various reporting functions within EMR-Link. Some reports contain PHI; in that case a user only has access to those reports if they have the appropriate Manage Orders or Manage Results permission. Emergency Access this permission can be provided to a user who may need PHI access under exceptional circumstances, but where this access must be justified and documented on a caseby case basis. Such a user can invoke emergency access but must provide a written reason (which is stored in the audit log). Any user with View/Manage Orders or View/Manage Results is understood to have PHI access. Locations of Care EMR-Link supports multiple locations of care (LOCs) within a single EMR-Link account, and can restrict the ability of a user to access data in more than one location. This serves to modify the Manage Orders and Manage Results permissions. A given user can have access to all LOCs or to only specified ones. Provider List Patient information and lab results are associated with a specific provider from the provider list in EMR- Link. A provider and a user are not the same thing; for example, an MD may be creating orders that are sent through EMR-Link but the actual user logging into EMR-Link is a nurse or phlebotomist, not the MD. EMR-Link System Architecture 5 Last updated: 3/12/2015
6 A user account can be associated with specific providers, or to all providers. If limited to a specific set of providers, the user will see only orders, results and patient data for those specific providers. In addition, there may be data which doesn t explicitly identify a provider or an LOC, and a user may or may not have access to this information. Using the Audit Log All user actions in EMR-Link are logged to the Audit Log. Access to this log is achieved through the Reports tab. The log can be filtered and sorted using the controls below: The acting user or all users can be seen in the report, and the report can be organized by date, user or event type. Selecting next to Event Type provides a screen to select the events of interest: EMR-Link System Architecture 6 Last updated: 3/12/2015
7 Once the desired options have been set, data is displayed in a table and can be exported to a file for other uses. EMR-Link System Architecture 7 Last updated: 3/12/2015
8 Security When Accessing EMR-Link from Your EHR Configuration Information The details of how an EHR connects directly to EMR-Link for sending orders or retrieving results varies from one EHR type to another. The most common method is through use of a client component called FlexConnector, installed on servers or workstations that need access to EMR-Link. FlexConnector uses an auth key to identify the EMR-Link account to which it connects. The auth key must be protected from unauthorized access, and the FlexConnector itself must be protected from tampering, to avoid unauthorized access to EMR-Link. File System Security In most cases results are delivered to the EHR by first downloading them to an inbox folder on the EHR system, and then using the EHR s data import capabilities to move the results into the EHR. These downloaded files contain PHI and depending on the specific EHR, they may or may not be removed once they are imported. The customer should assure that this inbox is protected against unauthorized access and that the lab results files are removed or securely archived once they have been processed. Some EHRs use a corresponding method for sending orders, and these should be protected similarly. EMR-Link System Architecture 8 Last updated: 3/12/2015
9 Workstation Security Because EMR-Link is accessed from a web browser on the user s workstation, security gaps at the workstation can result in unauthorized access to data in EMR-Link. The customer is responsible for appropriate security policies, procedures and technical measures for workstation security, including: Maintaining the system with the appropriate security updates and patches; Use of anti-malware software on each workstation; Network security to prevent access to workstations from outside; Locking screensavers, session timeouts, password policies, and browser security settings as appropriate; Acceptable use and security policies and training of employees on security. EMR-Link System Architecture 9 Last updated: 3/12/2015
ProgressBook CentralAdmin User Guide
 ProgressBook CentralAdmin User Guide ProgressBook CentralAdmin User Guide (This document is current for ProgressBook v14.2.0 or later.) 2013 Software Answers, Inc. All Rights Reserved. All other company
ProgressBook CentralAdmin User Guide ProgressBook CentralAdmin User Guide (This document is current for ProgressBook v14.2.0 or later.) 2013 Software Answers, Inc. All Rights Reserved. All other company
BlackShield ID Agent for Remote Web Workplace
 Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
BlackShield ID Agent for Terminal Services Web and Remote Desktop Web
 Agent for Terminal Services Web and Remote Desktop Web 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication
Agent for Terminal Services Web and Remote Desktop Web 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication
FuseMail- Exchange ControlPanel Admin Guide Feb.27-14 V1.0. Exchange ControlPanel Administration Guide
 Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
FileCloud Security FAQ
 is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
Overview How it works: Features: Page 1
 Overview Tired of having domain administrators resetting user s passwords? Reduce costs and lighten the load of domain admins by delegating this duty to level 1 helpdesk personnel, department managers,
Overview Tired of having domain administrators resetting user s passwords? Reduce costs and lighten the load of domain admins by delegating this duty to level 1 helpdesk personnel, department managers,
How To Secure An Rsa Authentication Agent
 RSA Authentication Agents Security Best Practices Guide Version 3 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA,
RSA Authentication Agents Security Best Practices Guide Version 3 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA,
Introduction to the Mobile Access Gateway
 Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Supplier Information Security Addendum for GE Restricted Data
 Supplier Information Security Addendum for GE Restricted Data This Supplier Information Security Addendum lists the security controls that GE Suppliers are required to adopt when accessing, processing,
Supplier Information Security Addendum for GE Restricted Data This Supplier Information Security Addendum lists the security controls that GE Suppliers are required to adopt when accessing, processing,
Virto Password Reset Web Part for SharePoint. Release 3.1.0. Installation and User Guide
 Virto Password Reset Web Part for SharePoint Release 3.1.0 Installation and User Guide 2 Table of Contents OVERVIEW... 3 SYSTEM REQUIREMENTS... 3 OPERATING SYSTEM... 3 SERVER... 3 BROWSER... 4 INSTALLATION...
Virto Password Reset Web Part for SharePoint Release 3.1.0 Installation and User Guide 2 Table of Contents OVERVIEW... 3 SYSTEM REQUIREMENTS... 3 OPERATING SYSTEM... 3 SERVER... 3 BROWSER... 4 INSTALLATION...
User Guide. Version R91. English
 AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
Single Sign-On Guide for Blackbaud NetCommunity and The Patron Edge Online
 Single Sign-On Guide for Blackbaud NetCommunity and The Patron Edge Online 062212 2012 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any
Single Sign-On Guide for Blackbaud NetCommunity and The Patron Edge Online 062212 2012 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any
Enterprise Security Interests Require SSL with telnet server from outside the LAN
 Create and Use an SSL on Goals Provide secure and encrypted 5250 data stream conversations with the server (including authentication) use a digital certificate we create with Digital Manager Show a client
Create and Use an SSL on Goals Provide secure and encrypted 5250 data stream conversations with the server (including authentication) use a digital certificate we create with Digital Manager Show a client
White Paper. BD Assurity Linc Software Security. Overview
 Contents 1 Overview 2 System Architecture 3 Network Settings 4 Security Configurations 5 Data Privacy and Security Measures 6 Security Recommendations Overview This white paper provides information about
Contents 1 Overview 2 System Architecture 3 Network Settings 4 Security Configurations 5 Data Privacy and Security Measures 6 Security Recommendations Overview This white paper provides information about
Sonian Getting Started Guide October 2008
 Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Use of Exchange Mail and Diary Service Code of Practice
 Use of Exchange Mail and Diary Service Code of Practice Introduction This code of practice outlines the support mechanisms in place for the security of the Exchange mail and diary service. References are
Use of Exchange Mail and Diary Service Code of Practice Introduction This code of practice outlines the support mechanisms in place for the security of the Exchange mail and diary service. References are
Administering the Web Server (IIS) Role of Windows Server
 Course 10972A: Administering the Web Server (IIS) Role of Windows Server Course Details Course Outline Module 1: Overview and Installing Internet Information Services In this module students will learn
Course 10972A: Administering the Web Server (IIS) Role of Windows Server Course Details Course Outline Module 1: Overview and Installing Internet Information Services In this module students will learn
DATA PROTECTION. OneWorld Encrypted Messages USER GUIDE
 DATA PROTECTION OneWorld Encrypted Messages USER GUIDE Table of Contents 1 Why use Encrypted emails?... 3 2 Activation and Login... 4 2.1 Activating Your New OneWorld Encrypted Messages Account... 4 2.2
DATA PROTECTION OneWorld Encrypted Messages USER GUIDE Table of Contents 1 Why use Encrypted emails?... 3 2 Activation and Login... 4 2.1 Activating Your New OneWorld Encrypted Messages Account... 4 2.2
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication
 DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
DIGIPASS KEY series and smart card series for Juniper SSL VPN Authentication Certificate Based 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 31 Disclaimer Disclaimer of
FirePass SSLVPN Client Software Deployment Guide For Windows Mobile 5 and 6 Devices MAN 0263 01
 FirePass SSLVPN Client Software Deployment Guide For Windows Mobile 5 and 6 Devices MAN 0263 01 Product Version This manual applies to the F5 SSLV client software provided as part of the FirePass 6.0.2,
FirePass SSLVPN Client Software Deployment Guide For Windows Mobile 5 and 6 Devices MAN 0263 01 Product Version This manual applies to the F5 SSLV client software provided as part of the FirePass 6.0.2,
qliqdirect Active Directory Guide
 qliqdirect Active Directory Guide qliqdirect is a Windows Service with Active Directory Interface. qliqdirect resides in your network/server and communicates with qliqsoft cloud servers securely. qliqdirect
qliqdirect Active Directory Guide qliqdirect is a Windows Service with Active Directory Interface. qliqdirect resides in your network/server and communicates with qliqsoft cloud servers securely. qliqdirect
Compliance Guide ISO 27002. Compliance Guide. September 2015. Contents. Introduction 1. Detailed Controls Mapping 2.
 ISO 27002 Compliance Guide September 2015 Contents Compliance Guide 01 02 03 Introduction 1 Detailed Controls Mapping 2 About Rapid7 7 01 INTRODUCTION If you re looking for a comprehensive, global framework
ISO 27002 Compliance Guide September 2015 Contents Compliance Guide 01 02 03 Introduction 1 Detailed Controls Mapping 2 About Rapid7 7 01 INTRODUCTION If you re looking for a comprehensive, global framework
Active Directory Self-Service FAQ
 Active Directory Self-Service FAQ General Information: [email protected] Online Support: [email protected] CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
Active Directory Self-Service FAQ General Information: [email protected] Online Support: [email protected] CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
WatchDox SharePoint Beta Guide. Application Version 1.0.0
 Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
Virtual Cabinet Document Portal User Guide
 Virtual Cabinet Document Portal User Guide Contents / Introduction Introduction... 2 What to expect when publishing a document... 3 Having difficulty? Troubleshooting guide.... 7 The Virtual Cabinet Document
Virtual Cabinet Document Portal User Guide Contents / Introduction Introduction... 2 What to expect when publishing a document... 3 Having difficulty? Troubleshooting guide.... 7 The Virtual Cabinet Document
Frequently Asked Questions
 Barclaycard Spend Management Frequently Asked Questions Access/Login 1. Is the user name case-sensitive? The user name is not case-sensitive. It must be a minimum of 6 characters and up to 100 characters.
Barclaycard Spend Management Frequently Asked Questions Access/Login 1. Is the user name case-sensitive? The user name is not case-sensitive. It must be a minimum of 6 characters and up to 100 characters.
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
NetWrix Logon Reporter V 2.0
 NetWrix Logon Reporter V 2.0 Quick Start Guide Table of Contents 1. Introduction... 3 1.1. Product Features... 3 1.2. Licensing... 4 1.3. How It Works... 5 1.4. Report Types Available in the Advanced Mode...
NetWrix Logon Reporter V 2.0 Quick Start Guide Table of Contents 1. Introduction... 3 1.1. Product Features... 3 1.2. Licensing... 4 1.3. How It Works... 5 1.4. Report Types Available in the Advanced Mode...
FileMaker Security Guide The Key to Securing Your Apps
 FileMaker Security Guide The Key to Securing Your Apps Table of Contents Overview... 3 Configuring Security Within FileMaker Pro or FileMaker Pro Advanced... 5 Prompt for Password... 5 Give the Admin Account
FileMaker Security Guide The Key to Securing Your Apps Table of Contents Overview... 3 Configuring Security Within FileMaker Pro or FileMaker Pro Advanced... 5 Prompt for Password... 5 Give the Admin Account
TARGETPROCESS HELP DESK PORTAL
 TARGETPROCESS HELP DESK PORTAL v.2.17 User Guide This document describes TargetProcess Help Desk Portal functionality and provides information about TargetProcess Help Desk Portal usage. 1 HELP DESK PORTAL...2
TARGETPROCESS HELP DESK PORTAL v.2.17 User Guide This document describes TargetProcess Help Desk Portal functionality and provides information about TargetProcess Help Desk Portal usage. 1 HELP DESK PORTAL...2
2. From a control perspective, the PRIMARY objective of classifying information assets is to:
 MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
Netwrix Auditor for Active Directory
 Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Netwrix Auditor for Active Directory Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
Guideline on Auditing and Log Management
 CMSGu2012-05 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Auditing and Log Management National Computer Board Mauritius
CMSGu2012-05 Mauritian Computer Emergency Response Team CERT-MU SECURITY GUIDELINE 2011-02 Enhancing Cyber Security in Mauritius Guideline on Auditing and Log Management National Computer Board Mauritius
RFG Secure FTP. Web Interface
 RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
RFG Secure FTP Web Interface Step 1: Getting to the Secure FTP Web Interface: Open your preferred web browser and type the following address: http://ftp.raddon.com After you hit enter, you will be taken
Smart Card Authentication Client. Administrator's Guide
 Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Quick Reference Guide PAYMENT GATEWAY (Virtual Terminal)
 PAYMENT GATEWAY (Virtual Terminal) Document Version 131227 Copyright 2013 epaymentamerica, Inc. All Rights Reserved Logging in to the Virtual Terminal 1. Open your internet browser; We strongly recommend
PAYMENT GATEWAY (Virtual Terminal) Document Version 131227 Copyright 2013 epaymentamerica, Inc. All Rights Reserved Logging in to the Virtual Terminal 1. Open your internet browser; We strongly recommend
PA-DSS Implementation Guide for. Sage MAS 90 and 200 ERP. Credit Card Processing
 for Sage MAS 90 and 200 ERP Credit Card Processing Version 4.30.0.18 and 4.40.0.1 - January 28, 2010 Sage, the Sage logos and the Sage product and service names mentioned herein are registered trademarks
for Sage MAS 90 and 200 ERP Credit Card Processing Version 4.30.0.18 and 4.40.0.1 - January 28, 2010 Sage, the Sage logos and the Sage product and service names mentioned herein are registered trademarks
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Microsoft 10972 - Administering the Web Server (IIS) Role of Windows Server
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 10972 - Administering the Web Server (IIS) Role of Windows Server Length 5 days Price $4169.00 (inc GST) Version B Overview This course provides students
1800 ULEARN (853 276) www.ddls.com.au Microsoft 10972 - Administering the Web Server (IIS) Role of Windows Server Length 5 days Price $4169.00 (inc GST) Version B Overview This course provides students
Background Information
 User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
MS 10972A Administering the Web Server (IIS) Role of Windows Server
 MS 10972A Administering the Web Server (IIS) Role of Windows Server Description: Days: 5 Prerequisites: This course provides students with the fundamental knowledge and skills to configure and manage Internet
MS 10972A Administering the Web Server (IIS) Role of Windows Server Description: Days: 5 Prerequisites: This course provides students with the fundamental knowledge and skills to configure and manage Internet
Administration Guide. . All right reserved. For more information about Specops Password Sync and other Specops products, visit www.specopssoft.
 Administration Guide. All right reserved. For more information about Specops Password Sync and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Password Sync is a trademark
Administration Guide. All right reserved. For more information about Specops Password Sync and other Specops products, visit www.specopssoft.com Copyright and Trademarks Specops Password Sync is a trademark
Cloud Services MDM. ios User Guide
 Cloud Services MDM ios User Guide 10/24/2014 CONTENTS Overview... 3 Supported Devices... 3 System Capabilities... 3 Enrollment and Activation... 4 Download the Agent... 4 Enroll Your Device Using the Agent...
Cloud Services MDM ios User Guide 10/24/2014 CONTENTS Overview... 3 Supported Devices... 3 System Capabilities... 3 Enrollment and Activation... 4 Download the Agent... 4 Enroll Your Device Using the Agent...
Security IIS Service Lesson 6
 Security IIS Service Lesson 6 Skills Matrix Technology Skill Objective Domain Objective # Configuring Certificates Configure SSL security 3.6 Assigning Standard and Special NTFS Permissions Enabling and
Security IIS Service Lesson 6 Skills Matrix Technology Skill Objective Domain Objective # Configuring Certificates Configure SSL security 3.6 Assigning Standard and Special NTFS Permissions Enabling and
Administering the Web Server (IIS) Role of Windows Server
 Course 10972B: Administering the Web Server (IIS) Role of Windows Server Page 1 of 7 Administering the Web Server (IIS) Role of Windows Server Course 10972B: 4 days; Instructor-Led Introduction This course
Course 10972B: Administering the Web Server (IIS) Role of Windows Server Page 1 of 7 Administering the Web Server (IIS) Role of Windows Server Course 10972B: 4 days; Instructor-Led Introduction This course
RSA Authentication Manager 7.1 Basic Exercises
 RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
RSA Authentication Manager 7.1 Basic Exercises Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com Trademarks RSA and the RSA logo
Administering the Web Server (IIS) Role of Windows Server 10972B; 5 Days
 Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Administering the Web Server (IIS) Role of Windows Server 10972B; 5 Days
Lincoln Land Community College Capital City Training Center 130 West Mason Springfield, IL 62702 217-782-7436 www.llcc.edu/cctc Administering the Web Server (IIS) Role of Windows Server 10972B; 5 Days
10972-Administering the Web Server (IIS) Role of Windows Server
 Course Outline 10972-Administering the Web Server (IIS) Role of Windows Server Duration: 5 days (30 hours) Target Audience: This course is intended for IT Professionals already experienced in general Windows
Course Outline 10972-Administering the Web Server (IIS) Role of Windows Server Duration: 5 days (30 hours) Target Audience: This course is intended for IT Professionals already experienced in general Windows
Hang Seng HSBCnet Security. May 2016
 Hang Seng HSBCnet Security May 2016 1 Security The Bank aims to provide you with a robust, reliable and secure online environment in which to do business. We seek to achieve this through the adoption of
Hang Seng HSBCnet Security May 2016 1 Security The Bank aims to provide you with a robust, reliable and secure online environment in which to do business. We seek to achieve this through the adoption of
Secret Server Qualys Integration Guide
 Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Portal User Guide. Customers. Version 1.1. May 2013 http://www.sharedband.com 1 of 5
 Portal User Guide Customers Version 1.1 May 2013 http://www.sharedband.com 1 of 5 Table of Contents Introduction... 3 Using the Sharedband Portal... 4 Login... 4 Request password reset... 4 View accounts...
Portal User Guide Customers Version 1.1 May 2013 http://www.sharedband.com 1 of 5 Table of Contents Introduction... 3 Using the Sharedband Portal... 4 Login... 4 Request password reset... 4 View accounts...
RSA Authentication Manager 7.1 Security Best Practices Guide. Version 2
 RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
Introduction to Computing @ WSU
 Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
Online Backup Linux Client User Manual
 Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Configuring User Identification via Active Directory
 Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] User Identification Overview User Identification allows you to create security policies based
Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] User Identification Overview User Identification allows you to create security policies based
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security. www.uscyberpatriot.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
RAYSAFE S1 SECURITY WHITEPAPER VERSION B. RaySafe S1 SECURITY WHITEPAPER
 RaySafe S1 SECURITY WHITEPAPER Contents 1. INTRODUCTION 2 ARCHITECTURE OVERVIEW 2.1 Structure 3 SECURITY ASPECTS 3.1 Security Aspects for RaySafe S1 Data Collector 3.2 Security Aspects for RaySafe S1 cloud-based
RaySafe S1 SECURITY WHITEPAPER Contents 1. INTRODUCTION 2 ARCHITECTURE OVERVIEW 2.1 Structure 3 SECURITY ASPECTS 3.1 Security Aspects for RaySafe S1 Data Collector 3.2 Security Aspects for RaySafe S1 cloud-based
Online Backup Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Knowledge Base. Setup GoogleApps Email in Outlook 2007. 19 Pages. Zeumic Pty Ltd. PO Box 44 Kew, VIC Australia 3101
 Knowledge Base Setup GoogleApps Email in Outlook 2007 19 Pages Zeumic Pty Ltd PO Box 44 Kew, VIC Australia 3101 ABN: 62 116 073 459 Email: [email protected] Ph: 03 9018 1615 Web: http://www.zeumic.com.au
Knowledge Base Setup GoogleApps Email in Outlook 2007 19 Pages Zeumic Pty Ltd PO Box 44 Kew, VIC Australia 3101 ABN: 62 116 073 459 Email: [email protected] Ph: 03 9018 1615 Web: http://www.zeumic.com.au
Global TAC Secure FTP Site Customer User Guide
 Global TAC Secure FTP Site Customer User Guide Introduction This guide is provided to assist you in using the GTAC Secure FTP site. This site resides in the Houston Remote Services Center (RSC), and is
Global TAC Secure FTP Site Customer User Guide Introduction This guide is provided to assist you in using the GTAC Secure FTP site. This site resides in the Houston Remote Services Center (RSC), and is
Agent Configuration Guide
 SafeNet Authentication Service Agent Configuration Guide SAS Agent for Microsoft Internet Information Services (IIS) Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright
SafeNet Authentication Service Agent Configuration Guide SAS Agent for Microsoft Internet Information Services (IIS) Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright
SonicWALL PCI 1.1 Implementation Guide
 Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Outlook Express POP Instructions - Bloomsburg University Students
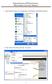 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
User's Guide. Product Version: 2.5.0 Publication Date: 7/25/2011
 User's Guide Product Version: 2.5.0 Publication Date: 7/25/2011 Copyright 2009-2011, LINOMA SOFTWARE LINOMA SOFTWARE is a division of LINOMA GROUP, Inc. Contents GoAnywhere Services Welcome 6 Getting Started
User's Guide Product Version: 2.5.0 Publication Date: 7/25/2011 Copyright 2009-2011, LINOMA SOFTWARE LINOMA SOFTWARE is a division of LINOMA GROUP, Inc. Contents GoAnywhere Services Welcome 6 Getting Started
W H IT E P A P E R. Salesforce CRM Security Audit Guide
 W HITEPAPER Salesforce CRM Security Audit Guide Contents Introduction...1 Background...1 Security and Compliance Related Settings...1 Password Settings... 2 Audit and Recommendation... 2 Session Settings...
W HITEPAPER Salesforce CRM Security Audit Guide Contents Introduction...1 Background...1 Security and Compliance Related Settings...1 Password Settings... 2 Audit and Recommendation... 2 Session Settings...
SonicWALL SSL VPN 3.5: Virtual Assist
 SonicWALL SSL VPN 3.5: Virtual Assist Document Scope This document describes how to use the SonicWALL Virtual Assist add-on for SonicWALL SSL VPN security appliances. This document contains the following
SonicWALL SSL VPN 3.5: Virtual Assist Document Scope This document describes how to use the SonicWALL Virtual Assist add-on for SonicWALL SSL VPN security appliances. This document contains the following
Cybersecurity Health Check At A Glance
 This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
This cybersecurity health check provides a quick view of compliance gaps and is not intended to replace a professional HIPAA Security Risk Analysis. Failing to have more than five security measures not
DIRECTORY PASSWORD V1.2 Quick Start Guide
 DIRECTORY PASSWORD V1.2 Quick Start Guide Directory Password is a self-service password reset / account unlock tool that is an optional add-on for Directory Update v2.5. Directory Update must be installed
DIRECTORY PASSWORD V1.2 Quick Start Guide Directory Password is a self-service password reset / account unlock tool that is an optional add-on for Directory Update v2.5. Directory Update must be installed
Sage 200 Web Time & Expenses Guide
 Sage 200 Web Time & Expenses Guide Sage (UK) Limited Copyright Statement Sage (UK) Limited, 2006. All rights reserved If this documentation includes advice or information relating to any matter other than
Sage 200 Web Time & Expenses Guide Sage (UK) Limited Copyright Statement Sage (UK) Limited, 2006. All rights reserved If this documentation includes advice or information relating to any matter other than
Media Shuttle s Defense-in- Depth Security Strategy
 Media Shuttle s Defense-in- Depth Security Strategy Introduction When you are in the midst of the creative flow and tedious editorial process of a big project, the security of your files as they pass among
Media Shuttle s Defense-in- Depth Security Strategy Introduction When you are in the midst of the creative flow and tedious editorial process of a big project, the security of your files as they pass among
Accessing TP SSL VPN
 Accessing TP SSL VPN This guide describes the steps to install, connect and disconnect the SSL VPN for remote access to TP intranet systems using personal notebooks. A. Installing the SSL VPN client Junos
Accessing TP SSL VPN This guide describes the steps to install, connect and disconnect the SSL VPN for remote access to TP intranet systems using personal notebooks. A. Installing the SSL VPN client Junos
Server Security. Contents. Is Rumpus Secure? 2. Use Care When Creating User Accounts 2. Managing Passwords 3. Watch Out For Aliases 4
 Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Aliases 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical Access
Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Aliases 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical Access
Netwrix Auditor for SQL Server
 Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Netwrix Auditor for SQL Server Quick-Start Guide Version: 7.1 10/26/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from
Virtual Code Authentication User s Guide. June 25, 2015
 Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Chapter 7 Managing Users, Authentication, and Certificates
 Chapter 7 Managing Users, Authentication, and Certificates This chapter contains the following sections: Adding Authentication Domains, Groups, and Users Managing Certificates Adding Authentication Domains,
Chapter 7 Managing Users, Authentication, and Certificates This chapter contains the following sections: Adding Authentication Domains, Groups, and Users Managing Certificates Adding Authentication Domains,
Administration Guide. BlackBerry Enterprise Service 12. Version 12.0
 Administration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2015-01-16 SWD-20150116150104141 Contents Introduction... 9 About this guide...10 What is BES12?...11 Key features of BES12...
Administration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2015-01-16 SWD-20150116150104141 Contents Introduction... 9 About this guide...10 What is BES12?...11 Key features of BES12...
Quick Setup Guide. 2 System requirements and licensing. 2011 Kerio Technologies s.r.o. All rights reserved.
 Kerio Control VMware Virtual Appliance Quick Setup Guide 2011 Kerio Technologies s.r.o. All rights reserved. This document provides detailed description on installation and basic configuration of the Kerio
Kerio Control VMware Virtual Appliance Quick Setup Guide 2011 Kerio Technologies s.r.o. All rights reserved. This document provides detailed description on installation and basic configuration of the Kerio
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Portal Administration. Administrator Guide
 Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
Portal Administration Administrator Guide Portal Administration Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec
PowerLink for Blackboard Vista and Campus Edition Install Guide
 PowerLink for Blackboard Vista and Campus Edition Install Guide Introduction...1 Requirements... 2 Authentication in Hosted and Licensed Environments...2 Meeting Permissions... 2 Installation...3 Configuring
PowerLink for Blackboard Vista and Campus Edition Install Guide Introduction...1 Requirements... 2 Authentication in Hosted and Licensed Environments...2 Meeting Permissions... 2 Installation...3 Configuring
Marcum LLP MFT Guide
 MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
Internet Remote Access FirePass SSL VPN
 Internet Remote Access FirePass SSL VPN Remote access to select Central Washington Hospital (CWH) information systems is available for hospital workers. Using a Web browser (Internet Explorer, Firefox,
Internet Remote Access FirePass SSL VPN Remote access to select Central Washington Hospital (CWH) information systems is available for hospital workers. Using a Web browser (Internet Explorer, Firefox,
HIPAA Compliance Use Case
 Overview HIPAA Compliance helps ensure that all medical records, medical billing, and patient accounts meet certain consistent standards with regard to documentation, handling, and privacy. Current Situation
Overview HIPAA Compliance helps ensure that all medical records, medical billing, and patient accounts meet certain consistent standards with regard to documentation, handling, and privacy. Current Situation
NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS
 NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS Scope and Applicability: These Network and Certificate System Security Requirements (Requirements) apply to all publicly trusted Certification Authorities
NETWORK AND CERTIFICATE SYSTEM SECURITY REQUIREMENTS Scope and Applicability: These Network and Certificate System Security Requirements (Requirements) apply to all publicly trusted Certification Authorities
Talk Internet User Guides Controlgate Administrative User Guide
 Talk Internet User Guides Controlgate Administrative User Guide Contents Contents (This Page) 2 Accessing the Controlgate Interface 3 Adding a new domain 4 Setup Website Hosting 5 Setup FTP Users 6 Setup
Talk Internet User Guides Controlgate Administrative User Guide Contents Contents (This Page) 2 Accessing the Controlgate Interface 3 Adding a new domain 4 Setup Website Hosting 5 Setup FTP Users 6 Setup
How to Give Admin Rights to Students on the ADGRM Domain
 How to Give Admin Rights to Students on the ADGRM Domain Contents Active Directory User and Computer... 2 Directory Tree Navigation... 3 The Computer folder... 3 The People Folder... 4 Creating a User
How to Give Admin Rights to Students on the ADGRM Domain Contents Active Directory User and Computer... 2 Directory Tree Navigation... 3 The Computer folder... 3 The People Folder... 4 Creating a User
My FreeScan Vulnerabilities Report
 Page 1 of 6 My FreeScan Vulnerabilities Report Print Help For 66.40.6.179 on Feb 07, 008 Thank you for trying FreeScan. Below you'll find the complete results of your scan, including whether or not the
Page 1 of 6 My FreeScan Vulnerabilities Report Print Help For 66.40.6.179 on Feb 07, 008 Thank you for trying FreeScan. Below you'll find the complete results of your scan, including whether or not the
NETWRIX ACCOUNT LOCKOUT EXAMINER
 NETWRIX ACCOUNT LOCKOUT EXAMINER ADMINISTRATOR S GUIDE Product Version: 4.1 July 2014. Legal Notice The information in this publication is furnished for information use only, and does not constitute a
NETWRIX ACCOUNT LOCKOUT EXAMINER ADMINISTRATOR S GUIDE Product Version: 4.1 July 2014. Legal Notice The information in this publication is furnished for information use only, and does not constitute a
Achieving PCI COMPLIANCE with the 2020 Audit & Control Suite. www.lepide.com/2020-suite/
 Achieving PCI COMPLIANCE with the 2020 Audit & Control Suite 7. Restrict access to cardholder data by business need to know PCI Article (PCI DSS 3) Report Mapping How we help 7.1 Limit access to system
Achieving PCI COMPLIANCE with the 2020 Audit & Control Suite 7. Restrict access to cardholder data by business need to know PCI Article (PCI DSS 3) Report Mapping How we help 7.1 Limit access to system
Workflow Templates Library
 Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
Workflow s Library Table of Contents Intro... 2 Active Directory... 3 Application... 5 Cisco... 7 Database... 8 Excel Automation... 9 Files and Folders... 10 FTP Tasks... 13 Incident Management... 14 Security
Cloudfinder for Office 365 User Guide. November 2013
 1 Contents Getting started with Cloudfinder for Office 365 1... 3 Sign up New Cloudfinder user... 3 Sign up Existing Cloudfinder user... 4 Setting the Admin Impersonation... 4 Initial backup... 7 Inside
1 Contents Getting started with Cloudfinder for Office 365 1... 3 Sign up New Cloudfinder user... 3 Sign up Existing Cloudfinder user... 4 Setting the Admin Impersonation... 4 Initial backup... 7 Inside
Configuration Guide. SafeNet Authentication Service. SAS Agent for Microsoft Internet Information Services (IIS)
 SafeNet Authentication Service Configuration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
SafeNet Authentication Service Configuration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information
How to Configure Captive Portal
 How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
10972B: Administering the Web Server (IIS) Role of Windows Server
 10972B: Administering the Web Server (IIS) Role of Windows Server Course Details Course Code: Duration: Notes: 10972B 5 days This course syllabus should be used to determine whether the course is appropriate
10972B: Administering the Web Server (IIS) Role of Windows Server Course Details Course Code: Duration: Notes: 10972B 5 days This course syllabus should be used to determine whether the course is appropriate
Remote Access Procedure. e-governance
 for e-governance Draft DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Document Control S/L Type of Information Document
for e-governance Draft DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Document Control S/L Type of Information Document
