SQL Injection Vulnerabilities in Desktop Applications
|
|
|
- Moses Ford
- 9 years ago
- Views:
Transcription
1 Vulnerabilities in Desktop Applications Derek Ditch (lead) Dylan McDonald Justin Miller Missouri University of Science & Technology Computer Science Department April 29, 2008 Vulnerabilities in Desktop Applications
2 Outline Objective: To protect desktop applications and user data from SQL injection attacks 1 Background Akonadi Architecture Akonadi & 2 Types of Attacks Example 3 4 Vulnerabilities in Desktop Applications
3 Background Background Akonadi Architecture Akonadi & Why choose Akonadi? Part of core architecture for upcoming KDE 4.1 release Significant privacy data at risk Lack of protection for Qt applications in general from SQL injection Vulnerabilities in Desktop Applications
4 Akonadi Akonadi Architecture Background Akonadi Architecture Akonadi & Desktop neutral Personal Information Manager (PIM) service Akonadi stores/caches Chat logs Calendars Address Books RSS Feeds Uses MySQL backend Provides IMAP client interface Vulnerabilities in Desktop Applications
5 Akonadi Akonadi & Background Akonadi Architecture Akonadi & <<thread>> nager AkonadiConnection use <<TcpServer>> AkonadiServer 1 rage NotificationCollector 1 <<thread>> CacheCleaner <<interface>> clear old values IMAP <<realize>> handler Handler Append Delete Status send changes 1 build db DataStore DbInitializer Rogue client accesses IMAP socket interface Executes valid IMAP client command, with inter-mixed SQL as user data User data is injected into SQL query SQL is passed through API directly to database layer <<interface>> MySQL Database Vulnerabilities in Desktop Applications
6 Types of Attacks Example SQL injection attacks inject arbitrary text into prepared SQL buffers to perform actions unintended by the developer Even with internal SQL data stores, poorly crafted or protected queries are vulnerable In particular, Akonadi uses a passwordless internal SQL store protected only by file permissions Vulnerabilities in Desktop Applications
7 Types of Attacks Types of Attacks Example Tautology adds logic that is trivially true in order to make query return more results than intended Comment uses special character sequence ( -- or /* ) in input to disable parts of intended query Subqueries inserts a query within a query to change behavior of database server or modify arbitrary data within SQL database Vulnerabilities in Desktop Applications
8 Attack Setup Types of Attacks Example Suppose we have a user table: User Password Admin tauritzd takecs348 T ajfrost hackallatms F justinmiller offtoiowa F Queries like SELECT * FROM users WHERE user = $un AND password = $pwd; are often used to authenticate users when they enter their username and passwords in the application Let s see how ajfrost can become an admin! Vulnerabilities in Desktop Applications
9 Attack Result Types of Attacks Example We will now try an attack by entering SQL logic into an application s password field, resulting in this SQL query: Resulting SQL Query SELECT * FROM users WHERE username = ajfrost AND password = OR 1 = 1 AND admin = T ; We can use any row to be an administrator Vulnerabilities in Desktop Applications
10 Command Line Interface A special interactive mode flag can be passed from the command line for testing multiple queries in short order When in interactive mode, a prompt is displayed and as queries are entered, the provided and cleaned queries are run against a MySQL database Command line and interactive modes both show the impacts of the queries on the database Vulnerabilities in Desktop Applications
11 Example API Example usage: 1 // Create sqlcleaner then autoclean query 2 SQLSanitizer sqlcleaner(query); 3 4 if( true == sqlcleaner.cleaned() ) 5 // Process query 6 query = sqlcleaner.getquery() else 9 // Handle error Vulnerabilities in Desktop Applications
12 Example Output %./sqlsan "SELECT * FROM users WHERE username = ajfrost AND password = OR 1 = 1 AND admin = T ;" SQLSanitizer Test App v1 By: Dylan McDonald, Justin Miller, Derek Ditch Sanitized Query: SELECT * FROM users WHERE = ajfrost AND password = AND admin = T ; Vulnerabilities in Desktop Applications
13 Under the hood What happens to the string? If no parameters are given to the constructor then default, safe behavior is used. The query is automatically processed unless the parameter is set to false. The query is checked for commands that change the schema, subqueries, and tautologies. If all went well, cleaned() returns true. Otherwise, it returns false. Vulnerabilities in Desktop Applications
14 Make the smarter Handle more complex queries Reduce overhead of added protection Give back to community Ensure code conforms to KDE standards Submit patch to KDE developer mailing lists Make additional changes as necessary Publish findings Vulnerabilities in Desktop Applications
SQL Injection Protection by Variable Normalization of SQL Statement
 Page 1 of 9 SQL Injection Protection by Variable Normalization of SQL Statement by: Sam M.S. NG, 0 http://www.securitydocs.com/library/3388 "Make everything as simple as possible, but not simpler." --
Page 1 of 9 SQL Injection Protection by Variable Normalization of SQL Statement by: Sam M.S. NG, 0 http://www.securitydocs.com/library/3388 "Make everything as simple as possible, but not simpler." --
INTRUSION PROTECTION AGAINST SQL INJECTION ATTACKS USING REVERSE PROXY
 INTRUSION PROTECTION AGAINST SQL INJECTION ATTACKS USING REVERSE PROXY Asst.Prof. S.N.Wandre Computer Engg. Dept. SIT,Lonavala University of Pune, [email protected] Gitanjali Dabhade Monika Ghodake Gayatri
INTRUSION PROTECTION AGAINST SQL INJECTION ATTACKS USING REVERSE PROXY Asst.Prof. S.N.Wandre Computer Engg. Dept. SIT,Lonavala University of Pune, [email protected] Gitanjali Dabhade Monika Ghodake Gayatri
Webapps Vulnerability Report
 Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
How I hacked PacketStorm (1988-2000)
 Outline Recap Secure Programming Lecture 8++: SQL Injection David Aspinall, Informatics @ Edinburgh 13th February 2014 Overview Some past attacks Reminder: basics Classification Injection route and motive
Outline Recap Secure Programming Lecture 8++: SQL Injection David Aspinall, Informatics @ Edinburgh 13th February 2014 Overview Some past attacks Reminder: basics Classification Injection route and motive
SQL Injection for newbie
 SQL Injection for newbie SQL injection is a security vulnerability that occurs in a database layer of an application. It is technique to inject SQL query/command as an input via web pages. Sometimes we
SQL Injection for newbie SQL injection is a security vulnerability that occurs in a database layer of an application. It is technique to inject SQL query/command as an input via web pages. Sometimes we
External Vulnerability Assessment. -Technical Summary- ABC ORGANIZATION
 External Vulnerability Assessment -Technical Summary- Prepared for: ABC ORGANIZATI On March 9, 2008 Prepared by: AOS Security Solutions 1 of 13 Table of Contents Executive Summary... 3 Discovered Security
External Vulnerability Assessment -Technical Summary- Prepared for: ABC ORGANIZATI On March 9, 2008 Prepared by: AOS Security Solutions 1 of 13 Table of Contents Executive Summary... 3 Discovered Security
SQL Injection January 23, 2013
 Web-based Attack: SQL Injection SQL Injection January 23, 2013 Authored By: Stephanie Reetz, SOC Analyst Contents Introduction Introduction...1 Web applications are everywhere on the Internet. Almost Overview...2
Web-based Attack: SQL Injection SQL Injection January 23, 2013 Authored By: Stephanie Reetz, SOC Analyst Contents Introduction Introduction...1 Web applications are everywhere on the Internet. Almost Overview...2
Testing Web Applications for SQL Injection Sam Shober [email protected]
 Testing Web Applications for SQL Injection Sam Shober [email protected] Abstract: This paper discusses the SQL injection vulnerability, its impact on web applications, methods for pre-deployment and
Testing Web Applications for SQL Injection Sam Shober [email protected] Abstract: This paper discusses the SQL injection vulnerability, its impact on web applications, methods for pre-deployment and
Understanding Sql Injection
 Understanding Sql Injection Hardik Shah Understanding SQL Injection Introduction: SQL injection is a technique used by a malicious user to gain illegal access on the remote machines through the web applications
Understanding Sql Injection Hardik Shah Understanding SQL Injection Introduction: SQL injection is a technique used by a malicious user to gain illegal access on the remote machines through the web applications
Advanced Tornado TWENTYONE. 21.1 Advanced Tornado. 21.2 Accessing MySQL from Python LAB
 21.1 Advanced Tornado Advanced Tornado One of the main reasons we might want to use a web framework like Tornado is that they hide a lot of the boilerplate stuff that we don t really care about, like escaping
21.1 Advanced Tornado Advanced Tornado One of the main reasons we might want to use a web framework like Tornado is that they hide a lot of the boilerplate stuff that we don t really care about, like escaping
Serious Threat. Targets for Attack. Characterization of Attack. SQL Injection 4/9/2010 COMP620 1. On August 17, 2009, the United States Justice
 Serious Threat SQL Injection COMP620 On August 17, 2009, the United States Justice Department tcharged an American citizen Albert Gonzalez and two unnamed Russians with the theft of 130 million credit
Serious Threat SQL Injection COMP620 On August 17, 2009, the United States Justice Department tcharged an American citizen Albert Gonzalez and two unnamed Russians with the theft of 130 million credit
Token Sequencing Approach to Prevent SQL Injection Attacks
 IOSR Journal of Computer Engineering (IOSRJCE) ISSN : 2278-0661 Volume 1, Issue 1 (May-June 2012), PP 31-37 Token Sequencing Approach to Prevent SQL Injection Attacks ManveenKaur 1,Arun Prakash Agrawal
IOSR Journal of Computer Engineering (IOSRJCE) ISSN : 2278-0661 Volume 1, Issue 1 (May-June 2012), PP 31-37 Token Sequencing Approach to Prevent SQL Injection Attacks ManveenKaur 1,Arun Prakash Agrawal
MatriXay Database Vulnerability Scanner V3.0
 MatriXay Database Vulnerability Scanner V3.0 (DAS- DBScan) - - - The best database security assessment tool 1. Overview MatriXay Database Vulnerability Scanner (DAS- DBScan) is a professional tool with
MatriXay Database Vulnerability Scanner V3.0 (DAS- DBScan) - - - The best database security assessment tool 1. Overview MatriXay Database Vulnerability Scanner (DAS- DBScan) is a professional tool with
Database Extension 1.5 ez Publish Extension Manual
 Database Extension 1.5 ez Publish Extension Manual 1999 2012 ez Systems AS Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License,Version
Database Extension 1.5 ez Publish Extension Manual 1999 2012 ez Systems AS Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License,Version
This module provides an overview of service and cloud technologies using the Microsoft.NET Framework and the Windows Azure cloud.
 Module 1: Overview of service and cloud technologies This module provides an overview of service and cloud technologies using the Microsoft.NET Framework and the Windows Azure cloud. Key Components of
Module 1: Overview of service and cloud technologies This module provides an overview of service and cloud technologies using the Microsoft.NET Framework and the Windows Azure cloud. Key Components of
The full setup includes the server itself, the server control panel, Firebird Database Server, and three sample applications with source code.
 Content Introduction... 2 Data Access Server Control Panel... 2 Running the Sample Client Applications... 4 Sample Applications Code... 7 Server Side Objects... 8 Sample Usage of Server Side Objects...
Content Introduction... 2 Data Access Server Control Panel... 2 Running the Sample Client Applications... 4 Sample Applications Code... 7 Server Side Objects... 8 Sample Usage of Server Side Objects...
Thick Client Application Security
 Thick Client Application Security Arindam Mandal ([email protected]) (http://www.paladion.net) January 2005 This paper discusses the critical vulnerabilities and corresponding risks in a two
Thick Client Application Security Arindam Mandal ([email protected]) (http://www.paladion.net) January 2005 This paper discusses the critical vulnerabilities and corresponding risks in a two
SQL Injection. By Artem Kazanstev, ITSO and Alex Beutel, Student
 SQL Injection By Artem Kazanstev, ITSO and Alex Beutel, Student SANS Priority No 2 As of September 2009, Web application vulnerabilities such as SQL injection and Cross-Site Scripting flaws in open-source
SQL Injection By Artem Kazanstev, ITSO and Alex Beutel, Student SANS Priority No 2 As of September 2009, Web application vulnerabilities such as SQL injection and Cross-Site Scripting flaws in open-source
How To Synchronize With Gmail For Business On Shoretel
 Voice Mail Synchronization with Gmail for Business Voice Mail Synchronization with Gmail for Business The Synchronization with Gmail for Business feature automatically synchronizes the state of a ShoreTel
Voice Mail Synchronization with Gmail for Business Voice Mail Synchronization with Gmail for Business The Synchronization with Gmail for Business feature automatically synchronizes the state of a ShoreTel
SQL INJECTION ATTACKS By Zelinski Radu, Technical University of Moldova
 SQL INJECTION ATTACKS By Zelinski Radu, Technical University of Moldova Where someone is building a Web application, often he need to use databases to store information, or to manage user accounts. And
SQL INJECTION ATTACKS By Zelinski Radu, Technical University of Moldova Where someone is building a Web application, often he need to use databases to store information, or to manage user accounts. And
Check list for web developers
 Check list for web developers Requirement Yes No Remarks 1. Input Validation 1.1) Have you done input validation for all the user inputs using white listing and/or sanitization? 1.2) Does the input validation
Check list for web developers Requirement Yes No Remarks 1. Input Validation 1.1) Have you done input validation for all the user inputs using white listing and/or sanitization? 1.2) Does the input validation
Advanced Web Technology 10) XSS, CSRF and SQL Injection 2
 Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 Table of Contents Cross Site Request Forgery - CSRF Presentation
Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 Table of Contents Cross Site Request Forgery - CSRF Presentation
SQL Injection Attack Lab
 Laboratory for Computer Security Education 1 SQL Injection Attack Lab Copyright c 2006-2010 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
Laboratory for Computer Security Education 1 SQL Injection Attack Lab Copyright c 2006-2010 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks
 A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
A SQL Injection : Internal Investigation of Injection, Detection and Prevention of SQL Injection Attacks Abhay K. Kolhe Faculty, Dept. Of Computer Engineering MPSTME, NMIMS Mumbai, India Pratik Adhikari
What is Web Security? Motivation
 [email protected] http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
[email protected] http://www.brucker.ch/ Information Security ETH Zürich Zürich, Switzerland Information Security Fundamentals March 23, 2004 The End Users View The Server Providers View What is Web
Nikolay Zaynelov Annual LUG-БГ Meeting 2015. nikolay.zaynelov.com [email protected]
 Nikolay Zaynelov Annual LUG-БГ Meeting 2015 nikolay.zaynelov.com [email protected] Introduction What is WordPress WordPress is a free and open source content management system (CMS). It is the most
Nikolay Zaynelov Annual LUG-БГ Meeting 2015 nikolay.zaynelov.com [email protected] Introduction What is WordPress WordPress is a free and open source content management system (CMS). It is the most
MGC WebCommander Web Server Manager
 MGC WebCommander Web Server Manager Installation and Configuration Guide Version 8.0 Copyright 2006 Polycom, Inc. All Rights Reserved Catalog No. DOC2138B Version 8.0 Proprietary and Confidential The information
MGC WebCommander Web Server Manager Installation and Configuration Guide Version 8.0 Copyright 2006 Polycom, Inc. All Rights Reserved Catalog No. DOC2138B Version 8.0 Proprietary and Confidential The information
SQL Injection Attack Lab Using Collabtive
 Laboratory for Computer Security Education 1 SQL Injection Attack Lab Using Collabtive (Web Application: Collabtive) Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document
Laboratory for Computer Security Education 1 SQL Injection Attack Lab Using Collabtive (Web Application: Collabtive) Copyright c 2006-2011 Wenliang Du, Syracuse University. The development of this document
Day-Care Environment Communication and Database
 Day-Care Environment Communication and Database Michael Christenson, Nicole Cullen, Zach Lensing, Eric Lund Problem Statement Create an information tracking app to be used by a day care Keep track of Daily
Day-Care Environment Communication and Database Michael Christenson, Nicole Cullen, Zach Lensing, Eric Lund Problem Statement Create an information tracking app to be used by a day care Keep track of Daily
Connecting to a Database Using PHP. Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006
 Connecting to a Database Using PHP Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006 Rationale Most Web applications: Retrieve information from a database to alter their on-screen display Store user
Connecting to a Database Using PHP Prof. Jim Whitehead CMPS 183, Spring 2006 May 15, 2006 Rationale Most Web applications: Retrieve information from a database to alter their on-screen display Store user
CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS
 66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
Concepts Design Basics Command-line MySQL Security Loophole
 Part 2 Concepts Design Basics Command-line MySQL Security Loophole Databases Flat-file Database stores information in a single table usually adequate for simple collections of information Relational Database
Part 2 Concepts Design Basics Command-line MySQL Security Loophole Databases Flat-file Database stores information in a single table usually adequate for simple collections of information Relational Database
Enhanced Model of SQL Injection Detecting and Prevention
 Enhanced Model of SQL Injection Detecting and Prevention Srinivas Baggam, Assistant Professor, Department of Computer Science and Engineering, MVGR College of Engineering, Vizianagaram, India. [email protected]
Enhanced Model of SQL Injection Detecting and Prevention Srinivas Baggam, Assistant Professor, Department of Computer Science and Engineering, MVGR College of Engineering, Vizianagaram, India. [email protected]
SQL Injection 2.0: Bigger, Badder, Faster and More Dangerous Than Ever. Dana Tamir, Product Marketing Manager, Imperva
 SQL Injection 2.0: Bigger, Badder, Faster and More Dangerous Than Ever Dana Tamir, Product Marketing Manager, Imperva Consider this: In the first half of 2008, SQL injection was the number one attack vector
SQL Injection 2.0: Bigger, Badder, Faster and More Dangerous Than Ever Dana Tamir, Product Marketing Manager, Imperva Consider this: In the first half of 2008, SQL injection was the number one attack vector
VIDEO intypedia007en LESSON 7: WEB APPLICATION SECURITY - INTRODUCTION TO SQL INJECTION TECHNIQUES. AUTHOR: Chema Alonso
 VIDEO intypedia007en LESSON 7: WEB APPLICATION SECURITY - INTRODUCTION TO SQL INJECTION TECHNIQUES AUTHOR: Chema Alonso Informática 64. Microsoft MVP Enterprise Security Hello and welcome to Intypedia.
VIDEO intypedia007en LESSON 7: WEB APPLICATION SECURITY - INTRODUCTION TO SQL INJECTION TECHNIQUES AUTHOR: Chema Alonso Informática 64. Microsoft MVP Enterprise Security Hello and welcome to Intypedia.
1. Building Testing Environment
 The Practice of Web Application Penetration Testing 1. Building Testing Environment Intrusion of websites is illegal in many countries, so you cannot take other s web sites as your testing target. First,
The Practice of Web Application Penetration Testing 1. Building Testing Environment Intrusion of websites is illegal in many countries, so you cannot take other s web sites as your testing target. First,
Web Application Security
 Web Application Security John Zaharopoulos ITS - Security 10/9/2012 1 Web App Security Trends Web 2.0 Dynamic Webpages Growth of Ajax / Client side Javascript Hardening of OSes Secure by default Auto-patching
Web Application Security John Zaharopoulos ITS - Security 10/9/2012 1 Web App Security Trends Web 2.0 Dynamic Webpages Growth of Ajax / Client side Javascript Hardening of OSes Secure by default Auto-patching
User Roles & Adding Domains & Users
 User Roles & Adding Domains & Users 1. MME User Roles During the set-up of Match My Email, a MME account is created. That account is for the company, set up by an individual that has administrative privileges
User Roles & Adding Domains & Users 1. MME User Roles During the set-up of Match My Email, a MME account is created. That account is for the company, set up by an individual that has administrative privileges
FINAL DoIT 11.03.2015 - v.4 PAYMENT CARD INDUSTRY DATA SECURITY STANDARDS APPLICATION DEVELOPMENT AND MAINTENANCE PROCEDURES
 Purpose: The Department of Information Technology (DoIT) is committed to developing secure applications. DoIT s System Development Methodology (SDM) and Application Development requirements ensure that
Purpose: The Department of Information Technology (DoIT) is committed to developing secure applications. DoIT s System Development Methodology (SDM) and Application Development requirements ensure that
Video Administration Backup and Restore Procedures
 CHAPTER 12 Video Administration Backup and Restore Procedures This chapter provides procedures for backing up and restoring the Video Administration database and configuration files. See the following
CHAPTER 12 Video Administration Backup and Restore Procedures This chapter provides procedures for backing up and restoring the Video Administration database and configuration files. See the following
Email setup information for most domains hosted with InfoRailway.
 Email setup information for most domains hosted with InfoRailway. Incoming server (POP3): pop.secureserver.net port 995 (SSL) Incoming server (IMAP): imap.secureserver.net port 993 (SSL) Outgoing server
Email setup information for most domains hosted with InfoRailway. Incoming server (POP3): pop.secureserver.net port 995 (SSL) Incoming server (IMAP): imap.secureserver.net port 993 (SSL) Outgoing server
NNT CIS Microsoft SQL Server 2008R2 Database Engine Level 1 Benchmark Report 0514a
 NNT CIS Microsoft SQL Server 2008R2 Database Engine Level 1 Benchmark Report 0514a: WIN- 2LR8M18J6A1 On WIN-2LR8M18J6A1 - By admin for time period 6/10/2014 8:59:44 AM to 6/10/2014 8:59:44 AM NNT CIS Microsoft
NNT CIS Microsoft SQL Server 2008R2 Database Engine Level 1 Benchmark Report 0514a: WIN- 2LR8M18J6A1 On WIN-2LR8M18J6A1 - By admin for time period 6/10/2014 8:59:44 AM to 6/10/2014 8:59:44 AM NNT CIS Microsoft
TO SQL DB. Manual. Page 1 of 7. Manual. Tel & Fax: +39 0984 494277 E-mail: [email protected] Web: www.altilagroup.com
 Page 1 of 7 TO SQL DB Sede opertiva: Piazza Vermicelli 87036 Rende (CS), Italy Page 2 of 7 TABLE OF CONTENTS 1 APP DOCUMENTATION... 3 1.1 HOW IT WORKS 3 1.2 Input data 4 1.3 Output data 4 1.4 Basic workflow
Page 1 of 7 TO SQL DB Sede opertiva: Piazza Vermicelli 87036 Rende (CS), Italy Page 2 of 7 TABLE OF CONTENTS 1 APP DOCUMENTATION... 3 1.1 HOW IT WORKS 3 1.2 Input data 4 1.3 Output data 4 1.4 Basic workflow
Dashboard Admin Guide
 MadCap Software Dashboard Admin Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document
MadCap Software Dashboard Admin Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document
A Brief Introduction to MySQL
 A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
1. What is SQL Injection?
 SQL Injection 1. What is SQL Injection?...2 2. Forms of vulnerability...3 2.1. Incorrectly filtered escape characters...3 2.2. Incorrect type handling...3 2.3. Vulnerabilities inside the database server...4
SQL Injection 1. What is SQL Injection?...2 2. Forms of vulnerability...3 2.1. Incorrectly filtered escape characters...3 2.2. Incorrect type handling...3 2.3. Vulnerabilities inside the database server...4
The release notes provide details of enhancements and features in Cloudera ODBC Driver for Impala 2.5.30, as well as the version history.
 Cloudera ODBC Driver for Impala 2.5.30 The release notes provide details of enhancements and features in Cloudera ODBC Driver for Impala 2.5.30, as well as the version history. The following are highlights
Cloudera ODBC Driver for Impala 2.5.30 The release notes provide details of enhancements and features in Cloudera ODBC Driver for Impala 2.5.30, as well as the version history. The following are highlights
Security and Control Issues within Relational Databases
 Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Security and Control Issues within Relational Databases David C. Ogbolumani, CISA, CISSP, CIA, CISM Practice Manager Information Security Preview of Key Points The Database Environment Top Database Threats
Web Applications Security: SQL Injection Attack
 Web Applications Security: SQL Injection Attack S. C. Kothari CPRE 556: Lecture 8, February 2, 2006 Electrical and Computer Engineering Dept. Iowa State University SQL Injection: What is it A technique
Web Applications Security: SQL Injection Attack S. C. Kothari CPRE 556: Lecture 8, February 2, 2006 Electrical and Computer Engineering Dept. Iowa State University SQL Injection: What is it A technique
Email: Gmail Or other POP3
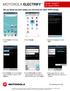 Set up Gmail account (steps are mirrored for other POP3 Email) 1.Touch Email on the home screen. 2.Touch Google. 3.Read the message and touch Next. 4.Touch Create. (Or, if you already have a Google account,
Set up Gmail account (steps are mirrored for other POP3 Email) 1.Touch Email on the home screen. 2.Touch Google. 3.Read the message and touch Next. 4.Touch Create. (Or, if you already have a Google account,
Product: DQ Order Manager Release Notes
 Product: DQ Order Manager Release Notes Subject: DQ Order Manager v7.1.25 Version: 1.0 March 27, 2015 Distribution: ODT Customers DQ OrderManager v7.1.25 Added option to Move Orders job step Update order
Product: DQ Order Manager Release Notes Subject: DQ Order Manager v7.1.25 Version: 1.0 March 27, 2015 Distribution: ODT Customers DQ OrderManager v7.1.25 Added option to Move Orders job step Update order
Oracle Database 11g SQL
 AO3 - Version: 2 19 June 2016 Oracle Database 11g SQL Oracle Database 11g SQL AO3 - Version: 2 3 days Course Description: This course provides the essential SQL skills that allow developers to write queries
AO3 - Version: 2 19 June 2016 Oracle Database 11g SQL Oracle Database 11g SQL AO3 - Version: 2 3 days Course Description: This course provides the essential SQL skills that allow developers to write queries
Link and Sync Guide for Hosted QuickBooks Files
 Link and Sync Guide for Hosted QuickBooks Files A How-To Guide for Syncing QuickBooks Files Table of Contents Hosted QuickBooks Files Overview:... 2 Rules Overview:... 2 Link and Sync Hosted QuickBooks
Link and Sync Guide for Hosted QuickBooks Files A How-To Guide for Syncing QuickBooks Files Table of Contents Hosted QuickBooks Files Overview:... 2 Rules Overview:... 2 Link and Sync Hosted QuickBooks
D61830GC30. MySQL for Developers. Summary. Introduction. Prerequisites. At Course completion After completing this course, students will be able to:
 D61830GC30 for Developers Summary Duration Vendor Audience 5 Days Oracle Database Administrators, Developers, Web Administrators Level Technology Professional Oracle 5.6 Delivery Method Instructor-led
D61830GC30 for Developers Summary Duration Vendor Audience 5 Days Oracle Database Administrators, Developers, Web Administrators Level Technology Professional Oracle 5.6 Delivery Method Instructor-led
Hardened Plone. Making Your Plone Site Even More Secure. Presented by: Nathan Van Gheem
 Hardened Plone Making Your Plone Site Even More Secure Presented by: Nathan Van Gheem Plone Security Flexible and granular ACL/roles-based security model of Zope All input in Plone is validated Plone does
Hardened Plone Making Your Plone Site Even More Secure Presented by: Nathan Van Gheem Plone Security Flexible and granular ACL/roles-based security model of Zope All input in Plone is validated Plone does
MySQL for Beginners Ed 3
 Oracle University Contact Us: 1.800.529.0165 MySQL for Beginners Ed 3 Duration: 4 Days What you will learn The MySQL for Beginners course helps you learn about the world's most popular open source database.
Oracle University Contact Us: 1.800.529.0165 MySQL for Beginners Ed 3 Duration: 4 Days What you will learn The MySQL for Beginners course helps you learn about the world's most popular open source database.
Cloud Elements ecommerce Hub Provisioning Guide API Version 2.0 BETA
 Cloud Elements ecommerce Hub Provisioning Guide API Version 2.0 BETA Page 1 Introduction The ecommerce Hub provides a uniform API to allow applications to use various endpoints such as Shopify. The following
Cloud Elements ecommerce Hub Provisioning Guide API Version 2.0 BETA Page 1 Introduction The ecommerce Hub provides a uniform API to allow applications to use various endpoints such as Shopify. The following
ORACLE BUSINESS INTELLIGENCE WORKSHOP
 ORACLE BUSINESS INTELLIGENCE WORKSHOP Integration of Oracle BI Publisher with Oracle Business Intelligence Enterprise Edition Purpose This tutorial mainly covers how Oracle BI Publisher is integrated with
ORACLE BUSINESS INTELLIGENCE WORKSHOP Integration of Oracle BI Publisher with Oracle Business Intelligence Enterprise Edition Purpose This tutorial mainly covers how Oracle BI Publisher is integrated with
MIGRATIONWIZ SECURITY OVERVIEW
 MIGRATIONWIZ SECURITY OVERVIEW Table of Contents Introduction... 2 Shared Security Approach... 2 Customer Best Practices... 2 Application Security... 4 Database Level Security... 4 Network Security...
MIGRATIONWIZ SECURITY OVERVIEW Table of Contents Introduction... 2 Shared Security Approach... 2 Customer Best Practices... 2 Application Security... 4 Database Level Security... 4 Network Security...
A Tokenization and Encryption based Multi-Layer Architecture to Detect and Prevent SQL Injection Attack
 A Tokenization and Encryption based Multi-Layer Architecture to Detect and Prevent SQL Injection Attack Mr. Vishal Andodariya PG Student C. U. Shah College Of Engg. And Tech., Wadhwan city, India [email protected]
A Tokenization and Encryption based Multi-Layer Architecture to Detect and Prevent SQL Injection Attack Mr. Vishal Andodariya PG Student C. U. Shah College Of Engg. And Tech., Wadhwan city, India [email protected]
An Oracle White Paper June 2014. Security and the Oracle Database Cloud Service
 An Oracle White Paper June 2014 Security and the Oracle Database Cloud Service 1 Table of Contents Overview... 3 Security architecture... 4 User areas... 4 Accounts... 4 Identity Domains... 4 Database
An Oracle White Paper June 2014 Security and the Oracle Database Cloud Service 1 Table of Contents Overview... 3 Security architecture... 4 User areas... 4 Accounts... 4 Identity Domains... 4 Database
Security Test s i t ng Eileen Donlon CMSC 737 Spring 2008
 Security Testing Eileen Donlon CMSC 737 Spring 2008 Testing for Security Functional tests Testing that role based security functions correctly Vulnerability scanning and penetration tests Testing whether
Security Testing Eileen Donlon CMSC 737 Spring 2008 Testing for Security Functional tests Testing that role based security functions correctly Vulnerability scanning and penetration tests Testing whether
Fairsail REST API: Guide for Developers
 Fairsail REST API: Guide for Developers Version 1.02 FS-API-REST-PG-201509--R001.02 Fairsail 2015. All rights reserved. This document contains information proprietary to Fairsail and may not be reproduced,
Fairsail REST API: Guide for Developers Version 1.02 FS-API-REST-PG-201509--R001.02 Fairsail 2015. All rights reserved. This document contains information proprietary to Fairsail and may not be reproduced,
Oracle Database: SQL and PL/SQL Fundamentals NEW
 Oracle University Contact Us: 001-855-844-3881 & 001-800-514-06-97 Oracle Database: SQL and PL/SQL Fundamentals NEW Duration: 5 Days What you will learn This Oracle Database: SQL and PL/SQL Fundamentals
Oracle University Contact Us: 001-855-844-3881 & 001-800-514-06-97 Oracle Database: SQL and PL/SQL Fundamentals NEW Duration: 5 Days What you will learn This Oracle Database: SQL and PL/SQL Fundamentals
Passing PCI Compliance How to Address the Application Security Mandates
 Passing PCI Compliance How to Address the Application Security Mandates The Payment Card Industry Data Security Standards includes several requirements that mandate security at the application layer. These
Passing PCI Compliance How to Address the Application Security Mandates The Payment Card Industry Data Security Standards includes several requirements that mandate security at the application layer. These
Configuring an Alternative Database for SAS Web Infrastructure Platform Services
 Configuration Guide Configuring an Alternative Database for SAS Web Infrastructure Platform Services By default, SAS Web Infrastructure Platform Services is configured to use SAS Framework Data Server.
Configuration Guide Configuring an Alternative Database for SAS Web Infrastructure Platform Services By default, SAS Web Infrastructure Platform Services is configured to use SAS Framework Data Server.
SECURING APACHE : THE BASICS - III
 SECURING APACHE : THE BASICS - III Securing your applications learn how break-ins occur Shown in Figure 2 is a typical client-server Web architecture, which also indicates various attack vectors, or ways
SECURING APACHE : THE BASICS - III Securing your applications learn how break-ins occur Shown in Figure 2 is a typical client-server Web architecture, which also indicates various attack vectors, or ways
ArcGIS Server Security Threats & Best Practices 2014. David Cordes Michael Young
 ArcGIS Server Security Threats & Best Practices 2014 David Cordes Michael Young Agenda Introduction Threats Best practice - ArcGIS Server settings - Infrastructure settings - Processes Summary Introduction
ArcGIS Server Security Threats & Best Practices 2014 David Cordes Michael Young Agenda Introduction Threats Best practice - ArcGIS Server settings - Infrastructure settings - Processes Summary Introduction
Certified PHP/MySQL Web Developer Course
 Course Duration : 3 Months (120 Hours) Day 1 Introduction to PHP 1.PHP web architecture 2.PHP wamp server installation 3.First PHP program 4.HTML with php 5.Comments and PHP manual usage Day 2 Variables,
Course Duration : 3 Months (120 Hours) Day 1 Introduction to PHP 1.PHP web architecture 2.PHP wamp server installation 3.First PHP program 4.HTML with php 5.Comments and PHP manual usage Day 2 Variables,
AUTHENTICATION... 2 Step 1:Set up your LDAP server... 2 Step 2: Set up your username... 4 WRITEBACK REPORT... 8 Step 1: Table structures...
 AUTHENTICATION... 2 Step 1:Set up your LDAP server... 2 Step 2: Set up your username... 4 WRITEBACK REPORT... 8 Step 1: Table structures... 8 Step 2: Import Tables into BI Admin.... 9 Step 3: Creating
AUTHENTICATION... 2 Step 1:Set up your LDAP server... 2 Step 2: Set up your username... 4 WRITEBACK REPORT... 8 Step 1: Table structures... 8 Step 2: Import Tables into BI Admin.... 9 Step 3: Creating
Upgrading MySQL from 32-bit to 64-bit
 Upgrading MySQL from 32-bit to 64-bit UPGRADING MYSQL FROM 32-BIT TO 64-BIT... 1 Overview... 1 Upgrading MySQL from 32-bit to 64-bit... 1 Document Revision History... 21 Overview This document will walk
Upgrading MySQL from 32-bit to 64-bit UPGRADING MYSQL FROM 32-BIT TO 64-BIT... 1 Overview... 1 Upgrading MySQL from 32-bit to 64-bit... 1 Document Revision History... 21 Overview This document will walk
An Effective Approach for Detecting and Preventing Sqlinjection Attacks
 An Effective Approach for Detecting and Preventing Sqlinjection Attacks M. Roslinmary 1, S. Sivasakthi 2, A. Shenbaga Bharatha Priya 3 1, 2, 3 PG scholar, Department of IT, Dr. Sivanthi Aditanar College
An Effective Approach for Detecting and Preventing Sqlinjection Attacks M. Roslinmary 1, S. Sivasakthi 2, A. Shenbaga Bharatha Priya 3 1, 2, 3 PG scholar, Department of IT, Dr. Sivanthi Aditanar College
Email Setup Guide. network support pc repairs web design graphic design Internet services spam filtering hosting sales programming
 Email Setup Guide 1. Entourage 2008 Page 2 2. ios / iphone Page 5 3. Outlook 2013 Page 10 4. Outlook 2007 Page 17 5. Windows Live Mail a. New Account Setup Page 21 b. Change Existing Account Page 25 Entourage
Email Setup Guide 1. Entourage 2008 Page 2 2. ios / iphone Page 5 3. Outlook 2013 Page 10 4. Outlook 2007 Page 17 5. Windows Live Mail a. New Account Setup Page 21 b. Change Existing Account Page 25 Entourage
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac?
 Enterprise Computing & Service Management How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend
Enterprise Computing & Service Management How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend
Advanced Web Security, Lab
 Advanced Web Security, Lab Web Server Security: Attacking and Defending November 13, 2013 Read this earlier than one day before the lab! Note that you will not have any internet access during the lab,
Advanced Web Security, Lab Web Server Security: Attacking and Defending November 13, 2013 Read this earlier than one day before the lab! Note that you will not have any internet access during the lab,
TG Web. Technical FAQ
 TG Web Technical FAQ About this FAQ We encourage you to contact us if. You can't find the information you're looking for. You would like to discuss your specific testing requirements in more detail. You
TG Web Technical FAQ About this FAQ We encourage you to contact us if. You can't find the information you're looking for. You would like to discuss your specific testing requirements in more detail. You
Using LDAP for User Authentication
 Using LDAP for User Authentication Product version: 4.50 Document version: 1.1 Document creation date: 03-06-05 Purpose This technical note describes how to configure and set up EPiServer to use an LDAP
Using LDAP for User Authentication Product version: 4.50 Document version: 1.1 Document creation date: 03-06-05 Purpose This technical note describes how to configure and set up EPiServer to use an LDAP
KonyOne Server Installer - Linux Release Notes
 KonyOne Server Installer - Linux Release Notes Table of Contents 1 Overview... 3 1.1 KonyOne Server installer for Linux... 3 1.2 Silent installation... 4 2 Application servers supported... 4 3 Databases
KonyOne Server Installer - Linux Release Notes Table of Contents 1 Overview... 3 1.1 KonyOne Server installer for Linux... 3 1.2 Silent installation... 4 2 Application servers supported... 4 3 Databases
Oracle Database: SQL and PL/SQL Fundamentals
 Oracle University Contact Us: 1.800.529.0165 Oracle Database: SQL and PL/SQL Fundamentals Duration: 5 Days What you will learn This course is designed to deliver the fundamentals of SQL and PL/SQL along
Oracle University Contact Us: 1.800.529.0165 Oracle Database: SQL and PL/SQL Fundamentals Duration: 5 Days What you will learn This course is designed to deliver the fundamentals of SQL and PL/SQL along
An Introduction to SQL Injection Attacks for Oracle Developers. January 2004 INTEGRIGY. Mission Critical Applications Mission Critical Security
 An Introduction to SQL Injection Attacks for Oracle Developers January 2004 INTEGRIGY Mission Critical Applications Mission Critical Security An Introduction to SQL Injection Attacks for Oracle Developers
An Introduction to SQL Injection Attacks for Oracle Developers January 2004 INTEGRIGY Mission Critical Applications Mission Critical Security An Introduction to SQL Injection Attacks for Oracle Developers
Installation and Administration Guide
 Installation and Administration Guide BlackBerry Enterprise Transporter for BlackBerry Enterprise Service 12 Version 12.0 Published: 2014-11-06 SWD-20141106165936643 Contents What is BES12?... 6 Key features
Installation and Administration Guide BlackBerry Enterprise Transporter for BlackBerry Enterprise Service 12 Version 12.0 Published: 2014-11-06 SWD-20141106165936643 Contents What is BES12?... 6 Key features
CSCI-UA:0060-02. Database Design & Web Implementation. Professor Evan Sandhaus [email protected] [email protected]
 CSCI-UA:0060-02 Database Design & Web Implementation Professor Evan Sandhaus [email protected] [email protected] Lecture #27: DB Administration and Modern Architecture:The last real lecture. Database
CSCI-UA:0060-02 Database Design & Web Implementation Professor Evan Sandhaus [email protected] [email protected] Lecture #27: DB Administration and Modern Architecture:The last real lecture. Database
Criteria for web application security check. Version 2015.1
 Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Criteria for web application security check Version 2015.1 i Content Introduction... iii ISC- P- 001 ISC- P- 001.1 ISC- P- 001.2 ISC- P- 001.3 ISC- P- 001.4 ISC- P- 001.5 ISC- P- 001.6 ISC- P- 001.7 ISC-
Lucid Key Server v2 Installation Documentation. www.lucidcentral.org
 Lucid Key Server v2 Installation Documentation Contents System Requirements...2 Web Server...3 Database Server...3 Java...3 Tomcat...3 Installation files...3 Creating the Database...3 Step 1: Create the
Lucid Key Server v2 Installation Documentation Contents System Requirements...2 Web Server...3 Database Server...3 Java...3 Tomcat...3 Installation files...3 Creating the Database...3 Step 1: Create the
Design and Functional Specification
 2010 Design and Functional Specification Corpus eready Solutions pvt. Ltd. 3/17/2010 1. Introduction 1.1 Purpose This document records functional specifications for Science Technology English Math (STEM)
2010 Design and Functional Specification Corpus eready Solutions pvt. Ltd. 3/17/2010 1. Introduction 1.1 Purpose This document records functional specifications for Science Technology English Math (STEM)
KonyOne Server Prerequisites _ MS SQL Server
 KonyOne Server Prerequisites _ MS SQL Server KonyOne Platform Release 5.0 Copyright 2012-2013 Kony Solutions, Inc. All Rights Reserved. Page 1 of 13 Copyright 2012-2013 by Kony Solutions, Inc. All rights
KonyOne Server Prerequisites _ MS SQL Server KonyOne Platform Release 5.0 Copyright 2012-2013 Kony Solutions, Inc. All Rights Reserved. Page 1 of 13 Copyright 2012-2013 by Kony Solutions, Inc. All rights
MySQL Security for Security Audits
 MySQL Security for Security Audits Presented by, MySQL AB & O Reilly Media, Inc. Brian Miezejewski MySQL Principal Consultat Bio Leed Architect ZFour database 1986 Senior Principal Architect American Airlines
MySQL Security for Security Audits Presented by, MySQL AB & O Reilly Media, Inc. Brian Miezejewski MySQL Principal Consultat Bio Leed Architect ZFour database 1986 Senior Principal Architect American Airlines
What about MongoDB? can req.body.input 0; var date = new Date(); do {curdate = new Date();} while(curdate-date<10000)
 Security What about MongoDB? Even though MongoDB doesn t use SQL, it can be vulnerable to injection attacks db.collection.find( {active: true, $where: function() { return obj.credits - obj.debits < req.body.input;
Security What about MongoDB? Even though MongoDB doesn t use SQL, it can be vulnerable to injection attacks db.collection.find( {active: true, $where: function() { return obj.credits - obj.debits < req.body.input;
Oracle Database 12c: Introduction to SQL Ed 1.1
 Oracle University Contact Us: 1.800.529.0165 Oracle Database 12c: Introduction to SQL Ed 1.1 Duration: 5 Days What you will learn This Oracle Database: Introduction to SQL training helps you write subqueries,
Oracle University Contact Us: 1.800.529.0165 Oracle Database 12c: Introduction to SQL Ed 1.1 Duration: 5 Days What you will learn This Oracle Database: Introduction to SQL training helps you write subqueries,
SQL Server. 2012 for developers. murach's TRAINING & REFERENCE. Bryan Syverson. Mike Murach & Associates, Inc. Joel Murach
 TRAINING & REFERENCE murach's SQL Server 2012 for developers Bryan Syverson Joel Murach Mike Murach & Associates, Inc. 4340 N. Knoll Ave. Fresno, CA 93722 www.murach.com [email protected] Expanded
TRAINING & REFERENCE murach's SQL Server 2012 for developers Bryan Syverson Joel Murach Mike Murach & Associates, Inc. 4340 N. Knoll Ave. Fresno, CA 93722 www.murach.com [email protected] Expanded
Introduction to PhPCollab
 Introduction to PhPCollab PhPCollab is an open-source internet-enabled collaboration workspace for project teams. Modeled on Macromedia Sitespring, PhPCollab's architecture allows for the consulting team
Introduction to PhPCollab PhPCollab is an open-source internet-enabled collaboration workspace for project teams. Modeled on Macromedia Sitespring, PhPCollab's architecture allows for the consulting team
SQL Injection. SQL Injection. CSCI 4971 Secure Software Principles. Rensselaer Polytechnic Institute. Spring 2010 ...
 SQL Injection CSCI 4971 Secure Software Principles Rensselaer Polytechnic Institute Spring 2010 A Beginner s Example A hypothetical web application $result = mysql_query(
SQL Injection CSCI 4971 Secure Software Principles Rensselaer Polytechnic Institute Spring 2010 A Beginner s Example A hypothetical web application $result = mysql_query(
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac?
 How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend the MS Remote Desktop for Mac client.
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend the MS Remote Desktop for Mac client.
Customize Mobile Apps with MicroStrategy SDK: Custom Security, Plugins, and Extensions
 Customize Mobile Apps with MicroStrategy SDK: Custom Security, Plugins, and Extensions MicroStrategy Mobile SDK 1 Agenda MicroStrategy Mobile SDK Overview Requirements & Setup Custom App Delegate Custom
Customize Mobile Apps with MicroStrategy SDK: Custom Security, Plugins, and Extensions MicroStrategy Mobile SDK 1 Agenda MicroStrategy Mobile SDK Overview Requirements & Setup Custom App Delegate Custom
SQL Injection Attacks: Detection in a Web Application Environment
 SQL Injection Attacks: Detection in a Web Application Environment Table of Contents 1 Foreword... 1 2 Background... 3 2.1 Web Application Environment... 3 2.2 SQL Attack Overview... 3 2.3 Applications
SQL Injection Attacks: Detection in a Web Application Environment Table of Contents 1 Foreword... 1 2 Background... 3 2.1 Web Application Environment... 3 2.2 SQL Attack Overview... 3 2.3 Applications
Tivoli Endpoint Manager BigFix Dashboard
 Tivoli Endpoint Manager BigFix Dashboard Helping you monitor and control your Deployment. By Daniel Heth Moran Version 1.1.0 http://bigfix.me/dashboard 1 Copyright Stuff This edition first published in
Tivoli Endpoint Manager BigFix Dashboard Helping you monitor and control your Deployment. By Daniel Heth Moran Version 1.1.0 http://bigfix.me/dashboard 1 Copyright Stuff This edition first published in
